

Essay on Cyber Crime
Students are often asked to write an essay on Cyber Crime in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Cyber Crime
Introduction to cyber crime.
Cybercrime refers to illegal activities conducted through the internet. It’s a fast-growing area of crime, with more criminals exploiting the speed, convenience, and anonymity of the internet.
Types of Cyber Crime
There are many types of cybercrimes. These include hacking, where unauthorized access is gained to a computer system, and identity theft, where personal information is stolen and used fraudulently.
Preventing Cyber Crime
Preventing cybercrime is crucial. This can be achieved by using strong, unique passwords, keeping software and systems updated, and being cautious of suspicious emails or websites.
Cybercrime is a significant issue in today’s digital age. Awareness and proper precautions can help in preventing these crimes.
Also check:
- 10 Lines on Cyber Crime
- Paragraph on Cyber Crime
- Speech on Cyber Crime
250 Words Essay on Cyber Crime
Introduction.
Cybercrime, an umbrella term encompassing a variety of offenses committed using digital technology, poses a significant threat to the modern world. As our reliance on technology increases, so does the potential for misuse, leading to a surge in cybercrimes.
The Nature of Cybercrime
Cybercrimes can range from financial theft, identity theft, cyberstalking, to more complex forms like cyber terrorism and cyber warfare. They exploit the anonymity provided by the internet, making them difficult to trace, investigate, and prosecute.
Impact of Cybercrime
The impact of cybercrime extends beyond financial loss. It can cause significant psychological harm to victims, damage reputations, and even pose threats to national security. In a digital world, the effects of cybercrime are far-reaching and potentially devastating.
Preventing Cybercrime
Preventing cybercrime requires a multi-faceted approach. It involves not only technological solutions but also legal and educational measures. A robust cybersecurity infrastructure, stringent laws, and increased public awareness are crucial to mitigating the risk of cybercrime.
In conclusion, as technology advances, so too does the sophistication of cybercrimes. Combating this growing threat requires a comprehensive approach that combines technology, legislation, and education. The fight against cybercrime is a shared responsibility, requiring collective effort from individuals, organizations, and governments alike.
500 Words Essay on Cyber Crime
In the digital age, our reliance on technology has given rise to a new form of criminal activity known as cyber crime. This term encapsulates any illegal activity that utilizes a computer as its primary means of commission. Cyber crime has become a critical concern due to its widespread impact, affecting individuals, businesses, and even nations.
The Different Forms of Cyber Crime
Cyber crime manifests in various forms, each carrying its unique implications. Identity theft, for instance, involves unauthorized access and use of personal information for fraudulent purposes. Another common type, cyberstalking, uses digital tools to harass or threaten individuals. More complex forms of cyber crime include cyberterrorism and cyber warfare, which target national security and infrastructure.
The Impact of Cyber Crime
The impact of cyber crime is far-reaching and multifaceted. On an individual level, victims may face financial loss, emotional distress, and privacy invasion. For businesses, the implications can be devastating, leading to significant financial losses, reputational damage, and loss of customer trust. On a national level, cyber crime can threaten a country’s security, economy, and infrastructure.
Preventing cyber crime requires a multi-pronged approach. On a personal level, individuals must take precautions such as using strong passwords, regularly updating software, and being cautious of suspicious emails or links. Businesses, on the other hand, need robust cybersecurity measures, including firewalls, intrusion detection systems, and regular employee training. Governments must also play their part, enacting robust cyber crime laws and cooperating internationally to apprehend and prosecute cyber criminals.
Legal and Ethical Considerations
The legal landscape surrounding cyber crime is complex and continually evolving. Jurisdictional issues often arise, given the borderless nature of the internet. Ethically, the debate around privacy and security is pertinent. While law enforcement agencies advocate for backdoors into encrypted systems to combat cyber crime, this raises concerns about potential misuse and invasion of privacy.
The Future of Cyber Crime
As technology advances, so does the sophistication of cyber crimes. Future threats could involve artificial intelligence and machine learning, making detection and prevention even more challenging. Therefore, continuous research, development of advanced cybersecurity measures, and international cooperation are imperative to stay a step ahead of cyber criminals.
In conclusion, cyber crime poses a significant threat in the digital age, affecting all aspects of society. A comprehensive understanding of its forms, impacts, prevention strategies, and the associated legal and ethical considerations is crucial for individuals, businesses, and governments alike. As we move further into the digital era, the fight against cyber crime will undoubtedly remain a pressing issue.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Christmas Celebration in School
- Essay on How I Spent My Christmas Vacation
- Essay on My Aim of Life to Become a Bank Manager
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Why we should all care about cyber crime: the risk to you and me
Associate Professor and head of the Department of Computing, Curtin University
Disclosure statement
Mihai Lazarescu works for the Department of Computing, School of Electrical Engineering and Computing, Curtin University. He is the coordinator for the Computer Science and Cyber Security streams.
Curtin University provides funding as a member of The Conversation AU.
View all partners
In today’s world, the reality is that all individuals and organisations connected to the internet are vulnerable to cyber attack. The number, type and sophistication of attacks continues to grow, as the threat report published last month by the Australian Cyber Security Centre ( ACSC ) points out.
It isn’t only large organisations that are under threat. Even individuals or organisations that don’t believe they have much to offer hackers can be targeted. So even if you think you’re a small target, you might still be at risk.
Illusion of trust
Malicious individuals and groups thrive on gathering information that can be used to enhance their attack strategies. Hackers are becoming more focused on spear-phishing attacks, which are tailored to individual people, and any bit of information about you can be of help.
Key to the hacker is the issue of trust. The information gathered is used to build a profile of the target with the aim to have enough data that allows the hacker to appear trustworthy to you.
In most cases, the hacker will attempt to impersonate an entity that is trusted by you. The more information the hacker has on you, the more likely they will be able to maintain the illusion long enough to achieve their aims.
The effects of a successful attack vary significantly, largely depending on the motivation of the hacker.
For most of us, identity theft is likely to cause the most damage because it badly impacts on our ability to go about our normal daily life. Our credit rating could be severely compromised, for example. To make matters worse, the process of addressing the damage of an attack can be costly, time consuming and emotionally exhausting.
In other cases, the damage could be in the form of confidential information, such as medical history records, ending up in the hands of malicious parties, and thus make the you susceptible to different kinds of blackmail.
The recent breach of the Ashley Madison website is a typical example of confidential information about individuals that could be exploited by malicious parties.
Your access is important to hackers
But specific personal information is not the only driving factor behind cyber attacks. Often, the resources or the access you have to other systems is the overall goal.
A common misconception held by many individuals and organisations is that if they do not have anything of value on their systems, they are not likely to be attacked. Or the hackers have nothing to gain from copying all their information.
The information value may be zero, but the resources are precious commodities which can be easily used in two ways:
to launch more intensive, distributed attacks on the hacker’s primary target
they can be “leased out” in the form of botnets to other parties.
From the point of the user clearance, hackers again can exploit the knowledge about the target to attempt to gain access to difficult to reach systems.
Food for hacking thought
I was told of one case in the US where foreign hackers used the eating habits of the staff of a government organisation (obtained from credit charges) to launch a “ watering hole ” attack.
The hackers were able to easily compromise the server hosting the website of the restaurant frequented by the government employees and replaced the original PDF menus with a new set that had malware embedded in them. Thus, when the government employees were viewing the menus from their secure machines, they were downloading the malware as well.
These are just some of the ways hackers can take advantage of the information gathered from attacks. Unfortunately, the only limiting factor is the creativity of the malicious party. And sadly, hackers are very creative.
Beating cyber attacks
The attitude of individuals and organisations needs to change in order to prevent cyber attacks. There has to be a fundamental understanding that, when online, everyone is a target and that none of us are too small or unimportant.
It is also critical to change the attitude to incident detection and handling. We can only get better at the defence part if we learn from previous experience, painful and costly as that may be. The reason we know about some of the attacks mentioned above is because they were detected and investigated.
Most organisations do not consider incident handling as a core component of cyber defence. And as long as that continues, the improvement in the cyber defences will be slow.
There has to be a concerted effort to treat cyber security seriously rather than an expensive auditing exercise. The vast majority of organisations are looking at cyber security as a compliance task and thus do the minimum possible to achieve that.
The payment card industry’s Data Security Standards for major credit cards is a classic example. It is good that there is a standard, but what is unfortunate is that all organisations try to do is the absolute minimum possible to pass the standard check rather than actually improving their security.
Instead the view should be to use the cyber security requirements as a way to improve overall security and thus avoid costly and damaging incidents in the future.
- Cyberattacks
Postdoctoral Research Associate

Project Manager – Contraceptive Development

Editorial Internship

Integrated Management of Invasive Pampas Grass for Enhanced Land Rehabilitation

Essay on Cyber Crime
Essay generator.
In the digital age, the rapid advancement of technology has reshaped the way we live, work, and interact. However, alongside the countless benefits, this evolution has given rise to a darker phenomenon known as cyber crime. Cyber crime encompasses a wide range of malicious activities carried out through digital means, affecting individuals, organizations, and even nations. This essay delves into the intricacies of cyber crime, exploring its types, causes, impacts, and measures to combat it, offering a comprehensive overview for students participating in essay writing competitions.
Cyber Crime
Cyber crime refers to any criminal activity that involves a computer, networked device, or a network. While most cyber crimes are carried out to generate profit for the criminals, some are done to harm or intimidate individuals, governments, or entire societies. The anonymity, vast reach, and speed of the internet have made cyber crime a highly effective and dangerous tool in the hands of criminals.
Types of Cyber Crime
Cyber crime can be broadly categorized into three types: crimes against individuals, crimes against property, and crimes against governments or society at large.
- Phishing: Phishing involves sending fraudulent emails or messages that appear to be from legitimate sources to deceive individuals into revealing sensitive information, such as passwords, credit card numbers, or personal details.
- Ransomware: Ransomware is a type of malware that encrypts a victim’s files or data, rendering them inaccessible. The attacker demands a ransom payment from the victim to provide the decryption key.
- Malware: Malware (malicious software) includes viruses, Trojans, worms, and spyware designed to infect and compromise computer systems, steal data, or disrupt operations.
- Identity Theft: Cybercriminals steal personal information, such as Social Security numbers or financial data, to impersonate victims for financial gain, fraudulent activities, or accessing accounts.
- Cyberbullying: Cyberbullying involves using digital platforms, such as social media or messaging apps, to harass, threaten, or intimidate individuals, often leading to emotional and psychological distress.
- Online Scams: Various online scams deceive individuals into parting with their money, including advance-fee fraud, lottery scams, and romance scams. These scams exploit trust and gullibility.
- Data Breaches: Data breaches occur when cybercriminals gain unauthorized access to databases or systems, exposing sensitive information, such as customer data, financial records, or trade secrets.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: These attacks overwhelm a target system, website, or network with excessive traffic, rendering it unavailable to legitimate users.
- Cyber Espionage: State-sponsored or corporate espionage involves infiltrating computer systems to steal sensitive information, trade secrets, or government intelligence.
- Child Exploitation: Child exploitation includes online activities like child pornography, grooming, or sextortion, targeting minors and causing severe harm to victims.
- Hacking and Unauthorized Access: Unauthorized access to computer systems, networks, or accounts for the purpose of data theft, vandalism, or disruption is considered hacking.
- Financial Cybercrimes: Financial cybercrimes involve fraud, embezzlement, or theft of funds through various digital means, such as credit card fraud, online banking fraud, or investment scams.
- Online Harassment and Stalking: Cybercriminals engage in online harassment, stalking, or doxxing (publishing private information) to harass and intimidate victims.
- Social Engineering: Social engineering techniques manipulate individuals into divulging confidential information or performing actions that compromise security, often through impersonation or pretexting.
- Botnets and Cyber Attacks: Cybercriminals create botnets, networks of compromised devices, to launch coordinated cyberattacks, such as spam distribution, information theft, or credential stuffing attacks.
- Cryptojacking: Cryptojacking involves using a victim’s computer or device to mine cryptocurrencies without their consent or knowledge, causing system slowdowns and increased energy consumption.
- Online Copyright Infringement: Copyright infringement on the internet involves illegally sharing or distributing copyrighted content, such as movies, music, or software, without authorization.
- Deepfake and Manipulated Media: Deepfake technology creates convincing but fabricated a, video, or text content, leading to misinformation, impersonation, and reputational harm.
Causes of Cyber Crime
Several factors contribute to the prevalence of cyber crime, including:
- Anonymity: The internet provides a level of anonymity that emboldens criminals, making it challenging to trace illegal activities back to the perpetrators.
- Global Reach: Cyber criminals can operate from any location, targeting victims worldwide without ever crossing physical borders.
- Technological Complexity: The complexity and rapid evolution of technology can outpace security measures, leaving vulnerabilities that can be exploited.
- Lack of Awareness: Many users are unaware of the risks associated with their online activities, making them easy targets for cyber criminals.
Impacts of Cyber Crime
The effects of cyber crime are vast and varied, affecting individuals, organizations, and nations.
- Financial Loss: Cyber crime costs the global economy billions of dollars annually through fraud, theft of intellectual property, and other financial crimes.
- Psychological Impact: Victims of cyber crime, such as cyberbullying or identity theft, can experience significant emotional distress.
- Reputation Damage: Businesses and governments can suffer reputational damage due to data breaches, undermining public trust.
- National Security Threats: Cyber attacks on critical infrastructure can pose significant threats to national security, potentially leading to chaos and crisis.
Combating Cyber Crime
Addressing the challenge of cyber crime requires a multi-faceted approach, involving individuals, businesses, governments, and international bodies.
- Legislation: Implementing comprehensive cyber crime laws and regulations is crucial to defining and deterring illegal online activities.
- Cybersecurity Measures: Individuals and organizations must adopt robust cybersecurity practices, including the use of firewalls, antivirus software, and strong passwords.
- Education and Awareness: Raising awareness about the risks of cyber crime and promoting safe online behaviors can significantly reduce vulnerability.
- International Cooperation: Cyber crime is a global issue that necessitates international collaboration to develop strategies for prevention, investigation, and prosecution.
Future Directions
As technology continues to evolve, so too will the nature of cyber crime. The rise of artificial intelligence, the Internet of Things (IoT), and other emerging technologies will introduce new vulnerabilities and challenges. Future efforts to combat cyber crime must focus on advancing cybersecurity technologies, enhancing international legal frameworks, and fostering a culture of security awareness among all internet users.
In conclusion, Cyber crime is a pervasive issue that poses significant challenges to the security, privacy, and well-being of individuals and societies worldwide. Understanding the complexities of cyber crime is the first step toward developing effective strategies to combat it. By fostering collaboration among various stakeholders and embracing a proactive approach to cybersecurity, we can hope to mitigate the risks associated with our increasingly connected world. For students aspiring to make a difference, participating in essay writing competitions on topics such as cyber crime not only raises awareness but also encourages the development of innovative solutions to safeguard our digital future.
Text prompt
- Instructive
- Professional
Generate an essay on the importance of extracurricular activities for student development
Write an essay discussing the role of technology in modern education.
Talk to our experts
1800-120-456-456
- Cyber Crime Essay

Essay on Cyber Crime
Cyber crime is the most discussed issue of the 21st century. The technology sector world wide is witnessing a boom in the consumer of smartphones and the internet which is raising concerns with regard to the privacy and security of the users. Owing to this reason, it is highly essential for all the users to know about cyber crime & security. As a result, thi topic has become the most favorite topic of the examiner and can often be seen asked in the exams. In this view, students must have information on cyber crime and stay prepared to tackle such topics in the essay question in the English paper.
Introduction
Cybercrime is a dangerous attack a company or an individual may face. There are many cases where the cyber attack has brought massive loss to the company and individuals due to the data hack. We live in a technology-driven era, and every piece of information is now fed on computers. Cybercrime involves an attack on computers and digital devices. These cyber-attacks can prove hazardous not just for the organization, but also for the nation. To date, there are many digital attack cases in India and global, pushing for more security measures. These attacks are also affecting the economy of the country if not controlled in the initial stage.
What is Cybercrime?
Cybercrime or attack is defined as the systematic criminal activity occurring digitally
and done by attackers. There are many examples of cybercrime, including fraud,
malware viruses, cyberstalking and others. Due to these, government agencies and
companies are investing more in the maintenance and hiring of cybercrime experts.
Earlier, cybercrime was committed only by individuals or by small groups. However, now a highly complex cybercriminals network work on attacking the system for data
collection.
Three groups of cybercrimes-
This is the form of cyberstalking, trafficking, and grooming. Over the years, this
This type of cybercrime has been taken seriously by law enforcement agencies. It is
now keeping a track over every such attack on an individual.
Similar to the real world where criminals steal the property, in the cyber world,
attackers steal data. Here, the attacker steals a person's bank details and
misuse the credit card for online purchase. By using malicious software, the
attacker attacks the property to disrupt the system of the organization.
These types of crimes are denoted as cyber terrorism. This can be a terror because
the attacker can get hold of essential documents related to government
projects. An enemy nation or terrorist usually makes such attacks. There are
many cases globally where a terrorist hacks government data.
Apart from these, there is a financial crime where the hacker steals the money of the
user account holder. Moreover, they steal company data and finance.
In this type, the computer system of the person is hacked to get personal
information. In many countries, including India, hacking is a punishable act.
It is quite different from ethical hacking. In normal hacking, illegal use
different types of software to enter the system of the target person. Hacker is
then able to monitor every activity done by the person.
This Cybercrime is about violating copyright and downloading music or movies. In
India, many movies before their releases are leaked on the movie download
sites. In other words , theft is also called privacy, which can bring a huge
loss to the organization.
Cyber Stalking
It is online harassment by an individual or a group of people. Normally, these
stalkers target an individual and harass online. There are many cases of
cyberstalking in India, resulting in the target person ending up taking
Malicious Software
These are computer-based cybercrimes where virus-based software is installed in the
target people or organization computers. This is to damage the system and
corrupt the data of the target.
Laws Related to Cybercrime
In India, there are many cybercrime laws enacted to stop this threat. Be it for
the individual or the organization; these laws help to either bring down the
number of cases or eliminate these digital crimes.
Apart from these laws, as an individual, you also need to take steps to stop these
crimes. Like, not providing your login details, installing trust anti-virus
software and keeping your online profile private can help to act against such
Cybercrime is a significant threat that can bring huge loss to the individual and the
organization. It is essential to follow basic online rules to ensure the safety
of self and the organization.
Benefits of Cyber Crime Essay in English provided by Vedantu
The essay on cybercrime provided by Vedantu is prepared by highly qualified teachers which makes it a reliable source of information. This information could be utilized for a variety of reasons. Being a reliable piece of information the essay will benefit everyone curious to know about the topic.
Following are the highlights of its benefits:
Reliable information
Adaptive to the context
Precise language
Fulfills the requirements of the students for english exam questions
Comprehensive and analytical. The article digs in the depth of the issue and analyzes it through a 360 degree perspective.
The essay could also be used by the students for preparing themselves for the essay question in the English paper. This essay is an excellent guide to understand what the examiner is looking for in the exam. Moreover, the topic of cybercrime is quite a recurrent one in the exam. So the students use this essay to deal with the same topic.
The Essay on Cyber Crime is an excellent guide on averting any possibilities of a cyber attack. On today's date, one is mostly on the internet for a variety of reasons. It becomes essential for one to know important tips that can keep one safe from cyberbullies, thieves, or blackmailers. It is also important for one to understand the right course of actions to be taken in an eventuality of such an incident.
Download the cybercrime essay for students in English on the Vedantu website.
FAQs on Cyber Crime Essay
1. How Does Cybercrime Work?
Group of people or an individual commits most of these cyber-crimes. These criminals use a systematic process to hack and commit these acts. These criminal communities share strategies and tools to launch attacks. Some of the cybercrime techniques
Fast Flux - In this method, the hacker moves data quickly among computers in a botnet, making it challenging to find the right source.
Social Engineering - This method includes using lies and manipulation to trick people into revealing their personal information.
Skimmers - This involves installing a skimming tool in an ATM and stealing the information. You may find such skimming devices in ATMs.
There are some digital criminals targeting organizations to steal personal information.
2. How Cybercrime Affects Society?
Cybercrime can hugely affect society. In 2018, the US faced a loss of $600 billion. As consumers are increasingly allowing technologies to get into their lives, cyber attackers are getting better access. Some of the essential information available are-
Personal health data, sleep schedules, and geo-locations Shopping history, account information, and passive conversations noticed voice-controlled devices, Private conversations on social media accounts.
Your entire life is now available on social media, making it vulnerable to hack or cyber-attack. Attackers use different techniques including- installing malware, virus, phishing, cyberstalking, etc. These can certainly bring loss of lives and data for individuals and organizations. For society, this is a significant loss in the long run. One needs to be very careful when presenting himself socially.
3. How to stay secure in times of cybercrime?
Cybercrime is a real threat posing to society. It is the 21st-century version of theft and blackmailing. There are certain ways one should adopt to prevent any possibilities of cybercrime. Do not disclose the banking details to random people or fill the CVV of your debit or credit cards on an unknown and unverified website. Keep your passwords always discrete. The camera of the laptop should always be covered.
4. Where can I get a cybercrime essay?
One can find a good quality cyber crime essay on Vedantu's website. The essay which is prepared by the expert teachers describes everything that one needs to know about cybercrime. It is the one-stop solution for all your requirements on the topic. Their essay is available in PDF format on the website and could be downloaded on any device. One downloaded essay could be used in offline mode too. If one finds it feasible, the printout of the PDF could also be taken out.

Home — Essay Samples — Law, Crime & Punishment — Cyber Crimes — Cyber Crime: The Meaning, Types, And Ways To Avoid
Cyber Crime: The Meaning, Types, and Ways to Avoid
- Categories: Cyber Crimes Cyber Security
About this sample

Words: 2343 |
12 min read
Published: May 17, 2022
Words: 2343 | Pages: 5 | 12 min read
Table of contents
Introduction, types of cyber crime.
- Phising/Spoofing: Unlawfully accessing a computer without authorization and sending multiple e-mails; resending multiple commercial email messages with the intent to deceive recipients; or falsifying header information in multiple email messages.
- Blackmail/Extortion: Using the Internet to threaten to cause damage with the intent to extort from any person any money or other thing of value.
- Accessing Stored Communications: Intentionally accessing, without authorization, a facility through which an electronic communication service is provided.
- Sports Betting: Engaging in the business of betting or wagering on any sporting event or contest over the Internet.
- Non-Delivery of Merchandise: Devising any scheme to defraud, or for obtaining money or property by means of false or fraudulent pretenses, or promises, and using the Internet for the purpose of executing the scheme.
- Electronic Harassment: Anonymously using the Internet to annoy, abuse, threaten, or harass the person who receives the communication.
- Child Pornography: Using the Internet to transmit child pornography.
- Prostitution: Persuading, inducing, enticing, or coercing any individual to travel in interstate commerce to engage in prostitution.
- Drug Trafficking: Delivering, distributing, or dispensing a controlled substance by means of the Internet.
- Criminal Copyright Infringement: Infringing a copyright for financial gain...or by distributing a work being prepared for commercial distribution on a computer network.
Avoiding Cyber Crime
Anti-virus software.
- It became common to distribute software and updates via downloads from the Internet,
- Hackers developed viruses that were delivered inside macros for Microsoft Word, which malicious macros could be hidden inside a document sent by e-mail, and
- Hackers developed malicious computer programs that were commonly distributed as attachments to e-mail: clicking on the attachment executed the malicious computer program and infected the victim's computer.
- Never open an executable attachment.
- Never open any attachment from an unknown source.
- Be cautious of any attachment that has a double file extension, especially when the rightmost file extension is an executable file type.
Avoiding harassment
- https://www.slideshare.net/bharadwajchetan/an-introduction-to-cyber-law-it-act-2000-india
- https://cybercrime.org.za/definition
- http://www.cyberlawsindia.net/cyber-india.html
- Dorothy E. Denning, Information Warfare and Security, Addison- Wesley Publishing Co., 1998.
- Dorothy E. Denning and Peter J. Denning, Internet Besieged, Addison- Wesley Publishing Co., 1997.
- Peter J. Denning (editor), Computers Under Attack, Addison- Wesley Publishing Co., 1990.
- Peter G. Neumann, Computer –Related Risks, Addison – Wesley Publishing Co., 1995.

Cite this Essay
To export a reference to this article please select a referencing style below:
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Law, Crime & Punishment Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
1 pages / 485 words
1 pages / 1682 words
1 pages / 551 words
2 pages / 914 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online

Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Cyber Crimes
In our increasingly interconnected world, where technology is deeply woven into the fabric of our daily lives, the specter of computer threats looms large. From malware attacks to hacking and data breaches, the digital landscape [...]
Lee, S. (2017). Encrypted Messaging: Keeping Your Conversations Secure. Security Boulevard.Smirnoff, V., & Turner, S. (2019). Symmetric Encryption: Definition, Types, and Examples. SecurityTrails.Almeida, R. (2019). Asymmetric [...]
Cybersecurity has become a very familiar term that has drawn increasing awareness of the danger of leaving cybercrimes unpunished. Because the world is moving more toward online trading and e-commerce, and basically living [...]
Cybercrime is emerging as a very serious threat in today’s world. The internet brings happiness to our lives but at the same time, it has some negative sides too. The cybercriminal is always in a search to find out the new ways [...]
Generally for protecting secrecy of information of parties while sharing information through internet via computer or any other electronic device forms an agreement about the procedure of handling of information and to not to [...]
I would like to express my special thanks to my Contemporary Crimes And The Law Professor Mrs. RuchiSinha for bringing me such an interesting topic to study. It is a great opportunity for me to write about the subject like [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

Essay on Cyber Crime | 500+ Words
Cybercrime is like a shadow lurking in the digital world, ready to harm us. In this essay, we will explore the world of cybercrime, its types, consequences, and how we can protect ourselves in the digital age.
Defining Cybercrime:
Cybercrime involves illegal activities conducted online. These crimes can harm individuals, organizations, and even entire nations.
The Digital Revolution
The rise of technology has brought convenience but also vulnerabilities. Cybercriminals exploit these vulnerabilities for personal gain.
Types of Cybercrime
Cybercrime takes many forms, including hacking, identity theft, online scams, and cyberbullying. Each poses unique risks and challenges.
Hacking and Data Breaches
Hackers gain unauthorized access to computer systems, stealing valuable data. These breaches can lead to financial loss and privacy violations.
Identity Theft
Identity theft involves stealing personal information for fraudulent purposes. Victims can face financial ruin and emotional distress.
Online Scams
Scammers trick people into giving away money or personal information. Awareness and skepticism are key defenses against these scams.
Cyberbullying
Cyberbullying involves using the internet to harass or harm others. It can have devastating effects on mental and emotional well-being.
The Impact of Cybercrime
Cybercrime has far-reaching consequences, affecting individuals, businesses, and governments. It erodes trust and security in the digital world.
Financial Loss
Victims of cybercrime often suffer financial losses. Recovering stolen funds can be challenging, and the impact can be long-lasting.
Emotional Toll
The emotional toll of cybercrime can be severe. Victims may experience fear, anxiety, and a loss of trust in online interactions.
Expert Opinions on Cybercrime
Experts in cybersecurity emphasize the importance of vigilance, education, and strong security measures in protecting against cyber threats.
Cybersecurity Measures
Protecting against cybercrime requires cybersecurity measures like strong passwords, antivirus software, and regular software updates.
The Role of Education
Education about online safety is vital. Schools and organizations should teach digital literacy and cybersecurity from an early age.
Online Privacy
Protecting online privacy means being cautious about sharing personal information and understanding the importance of data protection laws.
Reporting Cybercrime
Reporting cybercrime to law enforcement is crucial. It helps track down cybercriminals and prevent further harm.
International Cooperation
Cybercrime is a global issue. International cooperation and laws are essential to combating it effectively.
The Future of Cybersecurity
As technology evolves, so do cyber threats. Ongoing research and innovation in cybersecurity are essential to staying ahead of cybercriminals.
Conclusion of Essay on Cyber Crime
In conclusion, cybercrime is a digital menace that affects us all. Whether it’s hacking, scams, or cyberbullying, the consequences can be devastating. However, we can protect ourselves by staying informed, practicing good cybersecurity habits, and reporting cybercrime when it occurs.
The digital age has brought us incredible opportunities, but it has also brought risks. It is our responsibility to navigate this digital world with caution and vigilance. By doing so, we can reduce the impact of cybercrime and make the internet a safer place for everyone. Cybersecurity is not just a personal responsibility; it’s a collective effort to keep our digital world secure and trustworthy.
Also Check: The Essay on Essay: All you need to know

45,000+ students realised their study abroad dream with us. Take the first step today
Meet top uk universities from the comfort of your home, here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

- School Education /
✍️Essay on Cybercrime: Free Samples in 100, 200, 300 Words

- Updated on
- Apr 26, 2024

The 21st century is a digital age, where any and every task is done on the internet. All thanks to the developments in technology which have been the main factor to ease human life on earth and maybe on other plants in future. But with the benefits of technology, there are several harmful effects, one of them which has recently gained popularity; Cyber Crime.
Cybercrime has emerged as pervasive and evolved as one of the most dangerous threats to humans. There are several users on the internet who indulge in illegal and criminal activities, using computers and networks. To guide you through this hot debate topic, below we have discussed essays on cybercrime.
Table of Contents
- 1 Essay on Cybercrime in 100 Words
- 2 Essay on Cybercrime in 200 Words
- 3 Essay on Cybercrime in 300 Words
- 4 Short Essay on Cybercrime
Also Read: Essay on Student Life
Essay on Cybercrime in 100 Words
Cybercrime involves illegal activities like hacking, ransomware, cyberbullying, online fraud, etc. People who are involved in cybercrime or any similar activities are called hackers, scammers or fraudsters. Cybercrime leads to financial loss for individuals who have fallen victim to one. Cybercrime often invades a person’s privacy by stealing their personal details, including sensitive data, photos, and communication records, which can be used for blackmailing or any malicious purpose.
There are several governmental and non-government organizations which are working
To tackle cybercrime by raising awareness among the masses, cyber security training, implementing robust security protocols, and enacting comprehensive cybercrime laws.
Also Read: I Love My India Essay: 100 and 500+ Words in English for School Students
Essay on Cybercrime in 200 Words
Cybercrime is a criminal activity done online using a computer, network and internet. With the increasing use of the internet and mobile phones, the number of criminal activities has also gained pace. These criminal-minded people steal the personal details of a person, which leads to financial losses and damages the reputation of the victims. Various scams and fraudulent schemes are offered on the internet like online auctions, advance fees, or any investment scam, which are all aimed at deceiving individuals into parting with their money.
Cybercrime is not limited to financial losses or reputational damage, a more discrete term has emerged; cyberbullying. In cyberbullying, a person is harassed, humiliated, or threatened online. This can have severe psychological and emotional consequences. Ethical hackers or white hat hackers can help organizations identify vulnerabilities in their systems before malicious hackers exploit them.
Cybercrime doesn’t have any boundaries and is an international issue and international cooperation is crucial for tracking and prosecuting cybercriminals who operate across borders. To combat cybercrime effectively, a multi-faceted approach is required, involving education, technology, legislation, and international cooperation. As technology continues to advance, our efforts to combat cybercrime must keep pace to protect our increasingly interconnected world.
Also Read : Essay on Winter Season
Essay on Cybercrime in 300 Words
Economists have termed cybercrime as ‘ A Hidden Threat to the Digital World.’ Modern humans are relying on the internet for their day-to-day activities and every macro and micro activity. In this sense, the term cybercrime comes to the front. Cybercrime refers to criminal activities conducted through the use of computers, networks, and the Internet.
Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
The consequences of cybercrime are far-reaching. Financial losses run into 10 digits annually, affecting individuals and organizations alike. Personal privacy is invaded as cybercriminals steal sensitive data, photos, and communication records. In cases of cyberbullying and harassment, victims suffer reputational damages, psychological distress, and emotional trauma, particularly in cases of cyberbullying and harassment.
It’s necessary to look for a multifaceted approach to deal with cybercrime, some of which are.
- Raising public awareness through campaigns where people are informed about the risks of cybercrime and educate them on best practices for online safety.
- Individuals and organizations should implement robust security protocols, regularly update software, and use multi-factor authentication to protect their digital assets.
- Governments should enact and enforce cybercrime laws, providing law enforcement agencies with the resources and expertise needed to prosecute cybercriminals effectively.
- Looking at the global nature of cybercrime, international collaboration is vital. Countries should work together to share threat intelligence and cooperate in the investigation and prosecution of cybercriminals.
- Ethical hackers can help organizations identify and rectify vulnerabilities in their systems before malicious actors exploit them.
Tackling cybercrime requires proactive measures, including education, strong cybersecurity practices, legislation, international cooperation, and the active involvement of ethical hackers.
Also Read: Essay on Green Energy PDF: 150 and 250 Words
Short Essay on Cybercrime
Find the short essay on cyber crime from below:
Cybercrime is an illegal and unethical activity which is done by hackers and fraudsters to gain financial or any other benefits for themselves.
To tackle cybercrime, several measures can be taken. Some of these measures are education and public awareness, research and innovation, ethical hacking, etc.
To write an essay on cybercrime, you need to give details on how it works and the level of danger it poses to humans. Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
Related Articles
For more information about such informative articles, visit our essay writing page and make sure to follow Leverage Edu .
Shiva Tyagi
With an experience of over a year, I've developed a passion for writing blogs on wide range of topics. I am mostly inspired from topics related to social and environmental fields, where you come up with a positive outcome.
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Connect With Us
45,000+ students realised their study abroad dream with us. take the first step today..

Resend OTP in


Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
January 2025
September 2025
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.
Have something on your mind?

Make your study abroad dream a reality in January 2022 with
India's Biggest Virtual University Fair

Essex Direct Admission Day
Why attend .

Don't Miss Out
- CBSE Class 10th
- CBSE Class 12th
- UP Board 10th
- UP Board 12th
- Bihar Board 10th
- Bihar Board 12th
Top Schools
- Top Schools in India
- Top Schools in Delhi
- Top Schools in Mumbai
- Top Schools in Chennai
- Top Schools in Hyderabad
- Top Schools in Kolkata
- Top Schools in Pune
- Top Schools in Bangalore
Products & Resources
- JEE Main Knockout April
- Free Sample Papers
- Free Ebooks
- NCERT Notes
- NCERT Syllabus
- NCERT Books
- RD Sharma Solutions
- Navodaya Vidyalaya Admission 2024-25
- NCERT Solutions
- NCERT Solutions for Class 12
- NCERT Solutions for Class 11
- NCERT solutions for Class 10
- NCERT solutions for Class 9
- NCERT solutions for Class 8
- NCERT Solutions for Class 7
- JEE Main Exam
- JEE Advanced Exam
- BITSAT Exam
- View All Engineering Exams
- Colleges Accepting B.Tech Applications
- Top Engineering Colleges in India
- Engineering Colleges in India
- Engineering Colleges in Tamil Nadu
- Engineering Colleges Accepting JEE Main
- Top IITs in India
- Top NITs in India
- Top IIITs in India
- JEE Main College Predictor
- JEE Main Rank Predictor
- MHT CET College Predictor
- AP EAMCET College Predictor
- GATE College Predictor
- KCET College Predictor
- JEE Advanced College Predictor
- View All College Predictors
- JEE Advanced Cutoff
- JEE Main Cutoff
- GATE Registration 2025
- JEE Main Syllabus 2025
- Download E-Books and Sample Papers
- Compare Colleges
- B.Tech College Applications
- JEE Main Question Papers
- View All Management Exams
Colleges & Courses
- Top MBA Colleges in India
- MBA College Admissions
- MBA Colleges in India
- Top IIMs Colleges in India
- Top Online MBA Colleges in India
- MBA Colleges Accepting XAT Score
- BBA Colleges in India
- XAT College Predictor 2025
- SNAP College Predictor
- NMAT College Predictor
- MAT College Predictor 2024
- CMAT College Predictor 2025
- CAT Percentile Predictor 2024
- CAT 2024 College Predictor
- Top MBA Entrance Exams 2024
- NMAT Registration
- GD Topics for MBA
- CAT 2024 Admit Card
- Download Helpful Ebooks
- List of Popular Branches
- QnA - Get answers to your doubts
- IIM Fees Structure
- AIIMS Nursing
- Top Medical Colleges in India
- Top Medical Colleges in India accepting NEET Score
- Medical Colleges accepting NEET
- List of Medical Colleges in India
- List of AIIMS Colleges In India
- Medical Colleges in Maharashtra
- Medical Colleges in India Accepting NEET PG
- NEET College Predictor
- NEET PG College Predictor
- NEET MDS College Predictor
- NEET Rank Predictor
- DNB PDCET College Predictor
- NEET Syllabus 2025
- NEET Study Material 2024
- NEET Cut off
- NEET Exam Date 2025
- Download Helpful E-books
- Colleges Accepting Admissions
- Top Law Colleges in India
- Law College Accepting CLAT Score
- List of Law Colleges in India
- Top Law Colleges in Delhi
- Top NLUs Colleges in India
- Top Law Colleges in Chandigarh
- Top Law Collages in Lucknow
Predictors & E-Books
- CLAT College Predictor
- MHCET Law ( 5 Year L.L.B) College Predictor
- AILET College Predictor
- Sample Papers
- Compare Law Collages
- Careers360 Youtube Channel
- CLAT Syllabus 2025
- Free CLAT Practice Test
- NID DAT Exam
- Pearl Academy Exam
Predictors & Articles
- NIFT College Predictor
- UCEED College Predictor
- NID DAT College Predictor
- NID DAT 2025
- NID DAT Syllabus 2025
- Design Colleges in India
- Top NIFT Colleges in India
- Fashion Design Colleges in India
- Top Interior Design Colleges in India
- Top Graphic Designing Colleges in India
- Fashion Design Colleges in Delhi
- Fashion Design Colleges in Mumbai
- Top Interior Design Colleges in Bangalore
- NIFT Cutoff
- NIFT Fees Structure
- NIFT Syllabus 2025
- Free Design E-books
- List of Branches
- Careers360 Youtube channel
- IPU CET BJMC 2024
- JMI Mass Communication Entrance Exam 2024
- IIMC Entrance Exam 2024
- MICAT Exam 2025
- Media & Journalism colleges in Delhi
- Media & Journalism colleges in Bangalore
- Media & Journalism colleges in Mumbai
- List of Media & Journalism Colleges in India
- CA Intermediate
- CA Foundation
- CS Executive
- CS Professional
- Difference between CA and CS
- Difference between CA and CMA
- CA Full form
- CMA Full form
- CS Full form
- CA Salary In India
Top Courses & Careers
- Bachelor of Commerce (B.Com)
- Master of Commerce (M.Com)
- Company Secretary
- Cost Accountant
- Charted Accountant
- Credit Manager
- Financial Advisor
- Top Commerce Colleges in India
- Top Government Commerce Colleges in India
- Top Private Commerce Colleges in India
- Top M.Com Colleges in Mumbai
- Top B.Com Colleges in India
- IT Colleges in Tamil Nadu
- IT Colleges in Uttar Pradesh
- MCA Colleges in India
- BCA Colleges in India
Quick Links
- Information Technology Courses
- Programming Courses
- Web Development Courses
- Data Analytics Courses
- Big Data Analytics Courses
- RUHS Pharmacy Admission Test
- Top Pharmacy Colleges in India
- Pharmacy Colleges in Pune
- Pharmacy Colleges in Mumbai
- Colleges Accepting GPAT Score
- Pharmacy Colleges in Lucknow
- List of Pharmacy Colleges in Nagpur
- GPAT Result
- GPAT 2024 Admit Card
- GPAT Question Papers
- NCHMCT JEE 2024
- Mah BHMCT CET
- Top Hotel Management Colleges in Delhi
- Top Hotel Management Colleges in Hyderabad
- Top Hotel Management Colleges in Mumbai
- Top Hotel Management Colleges in Tamil Nadu
- Top Hotel Management Colleges in Maharashtra
- B.Sc Hotel Management
- Hotel Management
- Diploma in Hotel Management and Catering Technology
Diploma Colleges
- Top Diploma Colleges in Maharashtra
- UPSC IAS 2024
- SSC CGL 2024
- IBPS RRB 2024
- Previous Year Sample Papers
- Free Competition E-books
- Sarkari Result
- QnA- Get your doubts answered
- UPSC Previous Year Sample Papers
- CTET Previous Year Sample Papers
- SBI Clerk Previous Year Sample Papers
- NDA Previous Year Sample Papers
Upcoming Events
- NDA 2 Admit card 2024
- SSC CGL Admit card 2024
- CDS 2 Admit card 2024
- UGC NET Admit card 2024
- HP TET Result 2024
- SSC CHSL Result 2024
- UPTET Notification 2024
- SBI PO Notification 2024
Other Exams
- SSC CHSL 2024
- UP PCS 2024
- UGC NET 2024
- RRB NTPC 2024
- IBPS PO 2024
- IBPS Clerk 2024
- IBPS SO 2024
- Top University in USA
- Top University in Canada
- Top University in Ireland
- Top Universities in UK
- Top Universities in Australia
- Best MBA Colleges in Abroad
- Business Management Studies Colleges
Top Countries
- Study in USA
- Study in UK
- Study in Canada
- Study in Australia
- Study in Ireland
- Study in Germany
- Study in China
- Study in Europe
Student Visas
- Student Visa Canada
- Student Visa UK
- Student Visa USA
- Student Visa Australia
- Student Visa Germany
- Student Visa New Zealand
- Student Visa Ireland
- CUET PG 2025
- UP B.Ed JEE 2024
- TS EDCET Exam
- IIT JAM 2025
- AP PGCET Exam
- Universities in India
- Top Universities in India 2024
- Top Colleges in India
- Top Universities in Uttar Pradesh 2024
- Top Universities in Bihar
- Top Universities in Madhya Pradesh 2024
- Top Universities in Tamil Nadu 2024
- Central Universities in India
- CUET DU Cut off 2024
- IGNOU Date Sheet 2024
- CUET DU CSAS Portal 2024
- CUET 2025 Syllabus
- CUET PG Syllabus 2025
- CUET Participating Universities 2025
- CUET Previous Year Question Paper
- IGNOU Result 2024
- E-Books and Sample Papers
- CUET College Predictor 2024
- CUET Exam Date 2025
- CUET Cut Off 2024
- NIRF Ranking 2024
- IGNOU Exam Form 2024
- CUET Syllabus
- CUET Counselling 2025
Engineering Preparation
- Knockout JEE Main 2024
- Test Series JEE Main 2024
- JEE Main 2024 Rank Booster
Medical Preparation
- Knockout NEET 2024
- Test Series NEET 2024
- Rank Booster NEET 2024
Online Courses
- JEE Main One Month Course
- NEET One Month Course
- IBSAT Free Mock Tests
- IIT JEE Foundation Course
- Knockout BITSAT 2024
- Career Guidance Tool
Top Streams
- IT & Software Certification Courses
- Engineering and Architecture Certification Courses
- Programming And Development Certification Courses
- Business and Management Certification Courses
- Marketing Certification Courses
- Health and Fitness Certification Courses
- Design Certification Courses
Specializations
- Digital Marketing Certification Courses
- Cyber Security Certification Courses
- Artificial Intelligence Certification Courses
- Business Analytics Certification Courses
- Data Science Certification Courses
- Cloud Computing Certification Courses
- Machine Learning Certification Courses
- View All Certification Courses
- UG Degree Courses
- PG Degree Courses
- Short Term Courses
- Free Courses
- Online Degrees and Diplomas
- Compare Courses
Top Providers
- Coursera Courses
- Udemy Courses
- Edx Courses
- Swayam Courses
- upGrad Courses
- Simplilearn Courses
- Great Learning Courses
Cyber Crime Essay
The unlawful act of gaining unauthorised access to computer systems or digital devices is known as cybercrime. A detailed grasp of how to stop or recover from cyberattacks is provided by cyber security. Online courses offer guidance on how to avoid, safeguard against, and recover from cybercrime risks. Here are a few sample essays on the topic ‘Cyber Crime’.
100 Words Essay on Cyber Crime
200 words essay on cyber crime, 500 words essay on cyber crime.

Cybercrime is the most discussed problem in the twenty-first century. The usage of cellphones and the internet is increasing dramatically over the world, which is generating questions about consumers' security and privacy. Because of this, it is crucial for all users to understand cybercrime and security. Cybercrime is defined as organised criminal conduct carried out by attackers online. Cybercrime comes in numerous forms, such as fraud, computer viruses, cyberstalking, and others. Due to these, businesses and government organisations are spending more on maintaining and employing professionals in cybercrime.
There are millions and billions of users and websites in the vast community known as cyberspace. People utilise it for a variety of activities including e-commerce, transactions, shopping, movies, music, and video games. Anyone can simply access anything online in the current technological era owing to accessible internet connection. As a result, crime in general and cybercrime in particular have surged dramatically. Additionally, the faster internet connection has greatly boosted the rate of data circulation. All of these problems are responsible as to why cyber security has grown to be a significant issue for society.
The government has created a number of cybercrime-related laws in an effort to curb the spread of the crime and to protect people's interests. These laws also provide defence against cybercrime. Aside from that, the government has established cyber cells in police stations to combat cybercrime as quickly as possible.
Cybercrime is an attack that can be harmful to both an individual and a business. There have been several instances where a cyber attack led to a data leak that caused a significant loss for a business or a person. These cyber-attacks could have negative effects on the country and the business. The countless instances of cyberattacks that have taken place in India and other nations have necessitated increased security measures. There are four main categories of cybercrime, according to a popular definition—hacking, money, privacy, and cyber terrorism.
Cybercrime is a type of crime in which illegal activities are carried out online or using computers. Cybercrime comes in a variety of forms which involves harassing online users. Cybercrime is the most serious and rapidly expanding type of crime in this day and age. Any person's life may be negatively impacted for a very long time by becoming a cyber victim. Cybercrimes have a wide range of repercussions on financial and investment activity in digital organisations.
One typical tactic used by criminals is to lure online users in by creating attractive websites and sending phoney emails purporting to be from banks or other organisations and asking for personal information. It makes it easier for criminals to access a person's bank account and personal data. Due to viruses, mail fraud, account hacking, and software piracy, people have been victims of cybercrimes. They also run into problems with unauthorised access mailing, threats from pornographic emails, and video transmission.
Types of Cyber Crime
Cyberstalking | It is the use of electronic communication to track down a person or to make repeated attempts to get in touch with them in order to foster personal interaction despite their blatant lack of interest. Anyone who monitors the internet, email, or any other form of electronic communication is guilty of stalking.
Phishing | It is a sort of fraud that includes collecting personal data from recipients of emails that seem to be coming from a reliable source, including Customer ID, IPIN, Credit/Debit Card number, Card expiration date, CVV number, etc.
Vishing | It is an attempt when criminals attempt to obtain personal information over the phone, such as Customer ID, Net Banking password, ATM PIN, OTP, Card expiration date, CVV, etc.
Smishing | It is a sort of fraud that employs text messages sent to mobile devices to entice victims into dialling a fake phone number, going to a fake website, or downloading harmful software.
Impersonation And Identity Theft | This includes the dishonest or fraudulent use of another person's electronic signature, password, or other distinctive identification trait.
Virus, Worms, Trojan | A computer virus is a programme designed to infiltrate your computer, corrupt your files and data, and spread itself. Worms are malicious software applications that repeatedly duplicate themselves on local drives, network shares, etc. Trojan is a malicious programme that mimics a legitimate application. Trojans offer unauthorised people and applications access to your computer through a backdoor entry, allowing them to steal sensitive data.
How to Prevent Cyber Crime
Backup every piece of information—data, systems, and considerations—to make it easier for businesses to recover from unforeseen events with the help of prior data.
Pick a firewall that offers protection from viruses, malware, and dishonest hackers.
Never divulge private information to a stranger since they might exploit it for fraud.
To avoid cybercrime, check your security settings—in order to determine if someone has logged into your computer, a cyber firewall analyses your network settings.
Antivirus software aids in identifying potential threats and malware before they infect a computer system. Never use software that has been cracked since it poses a serious risk of data loss or malware attack.
Keep your information protected when accessing untrusted websites—information can readily bypass the data through phishing websites.
Applications for Admissions are open.

VMC VIQ Scholarship Test
Register for Vidyamandir Intellect Quest. Get Scholarship and Cash Rewards.

JEE Main Important Physics formulas
As per latest 2024 syllabus. Physics formulas, equations, & laws of class 11 & 12th chapters

JEE Main Important Chemistry formulas
As per latest 2024 syllabus. Chemistry formulas, equations, & laws of class 11 & 12th chapters

TOEFL ® Registrations 2024
Accepted by more than 11,000 universities in over 150 countries worldwide

Pearson | PTE
Register now for PTE & Unlock 20% OFF : Use promo code: 'C360SPL20'. Valid till 15th NOV'24! Trusted by 3,500+ universities globally

JEE Main high scoring chapters and topics
As per latest 2024 syllabus. Study 40% syllabus and score upto 100% marks in JEE
Download Careers360 App's
Regular exam updates, QnA, Predictors, College Applications & E-books now on your Mobile
Certifications
We Appeared in
Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.

Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

An official website of the United States government
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Publications
- Account settings
- Advanced Search
- Journal List

A systematic literature review on cybercrime legislation
Shereen khan, tajneen saleh, magiswary dorasamy, nasreen khan, olivia tan swee leng, rossanne gale vergara.
- Author information
- Article notes
- Copyright and License information
Email: [email protected]
No competing interests were disclosed.
Accepted 2022 Jul 8; Collection date 2022.
This is an open access article distributed under the terms of the Creative Commons Attribution Licence, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Background : Cybercrime is a fast-growing digital crime and legislation falling behind with the fast-moving advancement of technology. One important factor projected by literature in combating cybercrime is legislation. In order to combat cybercrime, the role of cybercrime legislation is a challenge that has not been clearly studied before. This paper thus aims to recapitulate the literature on cybercrime legislation in combating cybercrime. The literature in this context emphasises on existing studies relating to cybercrime legislation and addressing the importance of adequate and efficient responses in place in order to combat cybercrime efficiently.
Methods : This paper finds an extensive literature review using the “Preferred Reporting Items for Systematic Review and Meta-Analysis” method based on legislation to combat cybercrime and explains a systematic analysis of the legislation in most advanced countries in both technology and legal framework. The study was done by selecting keywords, validated by the experts to discover research trends of cybercrime legislation. A search was then run across seven academic databases, including the ACM Digital Library, Emerald, Hein Online, ProQuest, ScienceDirect, Scopus, and Westlaw Asia. Initially, five hundred and forty-eight articles were retrieved and out of which seventy-two studies met the inclusion criteria and were fully reviewed.
Results : The findings of the study revealed that comprehensive cybercrime legislation plays a vital role in combating cybercrime and cybercrime legislation should be strengthened, enhanced, and made up to date with the rapid advancement of technology in order to address the rising number of cybercrime.
Discussion : This systematic review is timely and highlights future research directions to improve a comprehensive legal framework to combat the rising of cybercrime effectively. To fill the research gap, the findings also have fundamental practical implications for the policy makers, in enacting an up to date cybercrime legislation by highlighting the role of legislation in combating cybercrime.
Keywords: Cybercrime, Legislation, Cybersecurity, Cyber legislation, Online crime, Systematic literature review, Combating, Legal Framework, Online Fraud
Introduction
The year 2020 had been an unprecedented challenging year especially from cybercrime perspectives. Not only that the world has to face the threats from global pandemic outbreak, but also from the increasingly sophisticated cyber-attacks. Global pandemic outbreak has resulted in more than 600% rise in cybercrime. 1 The more sophisticated and advanced the technology is, the higher the number of cybercrimes and the more difficult to comprehend the issue. Cybercriminals use the advanced technology to do criminal activities such as hacking, phishing, spamming, and child pornography and hate crimes resulting in massive losses suffered by individuals as well as corporations and even pose danger to national security in some cases.
According to the report by Reuters on 5 th July 2021, when the information technology firm from the United States was attacked by cybercriminals, around 800 to 1,500 businesses were affected around the world. It was reported by the FBI that 791,790 cybercrime complaints resulting in more than US$4.1 billion losses were received by the Internet Crime Complaint Centre in 2020 and that number of reported cases has increased 69 percent compared to the reported cases in 2019. It is not only that there is an increase in cybercrime cases, the level of sophistication of the technology used also has increased tremendously. The 2020 “SolarWinds” attack confirmed the reality of the sophistication of the technology involved. “SolarWinds” attack in 2020 was by the state sponsored attack since Russian military hackers accessed and sabotaged the United States Government databases and buried a software called SolarWinds. The latest attack being the largest online theft reported by CNN on the 12 th August was about the hackers who had stolen US$600million worth of cryptocurrencies from the decentralised finance platform of Poly Network. It shows how sophisticated the technology has become and how weak the legislation is to comprehend and deter these attacks.
Cybercrime can be categorised as crimes exclusive to internet and use of computer and traditional crimes. Crimes such as stalking, harassing, fraud or scam committed using social media such as Facebook, Instagram, Twitter can be regarded as traditional crimes which are committed entirely in new ways. Criminal acts done by using electronic communications and information systems are generally considered as cybercrime which consists of a variety of criminal acts. It can be individual acts as well as state sponsored cybercrime. There is no definition of cybercrime which has been accepted globally. However, the term cybercrime has been used to describe a range of crimes excluding traditional crimes but crimes committed using the computer network system. Because of the complexity of the nature of crime, a single act of cybercrime can cause overly high damages. Cybercrime currently contributes to the highest percentage of all crime. Historically, legislation has been used as a way to combat the challenges posed by cybercrime. For instance, the United States and European Union have legislation in an effort to deal with cybercrime. 2
However, there is no study being done on how legislation was used to combat cybercrime through systematic literature review (SLRs). Combating cybercrime requires a range of ways including developing new legislation and regulation as well as awareness raising campaigns.
Thus, this paper discusses the systematic literature review of the use of legislation to combat cybercrime as SLRs can provide a valuable summarization of cybercrime legislation and allow for the identification of existing knowledge gaps and consequently, avenues for future research. In essence, this paper attempts to contribute to the current literature on cybercrime legislation in two ways; firstly by providing a thematically organised classification of the studies from the perspective of application of legislation, limitations, and recommendations and secondly the finding of this SLR can be used to propose a detailed framework to conduct a future research.
Three research questions are addressed in order to make these contributions:
What is the legislation to combat cybercrime in selected jurisdictions?
How is the legislation used to combat cybercrime in these jurisdictions?
What are the other approaches taken to combat cybercrime?
The objectives of this proposal are as follows:
To identify the legislation to combat cybercrime in selected jurisdictions.
To examine the legislation used to combat cybercrime in these jurisdictions.
To investigate the other approaches taken to combat cybercrime.
This SLR research paper is complementary to the existing research and attempts to provide the following contributions for those having an interest in cybercrime and cybercrime legislation to further their work.
A total of 548 papers related to cybercrime legislation until the year 2021 were identified as initial studies ( Figure 1 ). Out of these papers, a total of 72 papers were further selected as primary studies for quality assessment to provide suitable benchmarks for comparative analysis towards related research. A comprehensive analysis was conducted on these 72 studies to present the ideas and considerations in the field of cybercrime legislation. A meta-analysis was conducted to improve the cybercrime legislation.
Figure 1. Attrition of papers through processing.
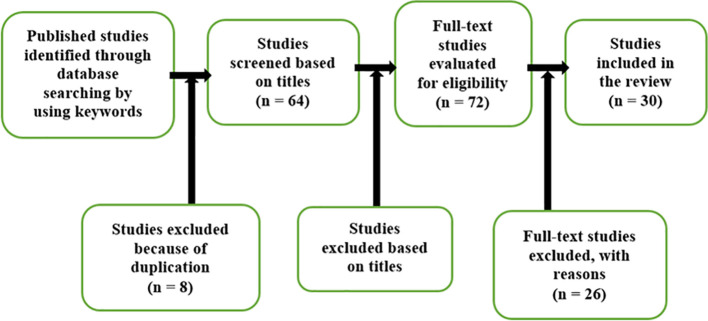
This paper analyses on how the international legal framework was used to combat cybercrime. The international legal framework can reduce the differences existing among the national laws as well as introducing new authorities and promoting international cooperation. The paper focuses on the necessity in international cooperation and implementation of international awareness as well as incorporating international norms into national legislation. The review study views cybercrime from a broader scope. All kinds of cybercrimes in general were looked into rather than a specific cybercrime such as cyber fraud. Different approaches were explored in raising cybercrime awareness and their effects, and investigating cyber legislation effectiveness along with the cybercrimes. No other review study is similar in work and scope. In essence, combating cybercrime requires a holistic understanding of the aspects involved and related interrelationships and there is a need to study the effectiveness of cybercrime legal framework. This article is based on an extensive analysis involving 72 papers relating to cybercrime legislation. This article contributes towards a comprehensive analysis on legal elements of cybercrime legislation and provides a summary of findings and the implications of this study for stakeholders to enhance the ability to successfully prosecute cybercrime offences.
The remainder of this paper followed on explanation of the methodology used for SLR in this paper and further on the discussion of the findings with continuation on a detailed discussion and reflection of the implications of the insights derived from the findings, then on the discussion of limitations and future recommendations on scope of research and finally 6 on concluding remarks.
In order to meet the aims of answering the research questions, SLR analysis was conducted by applying several steps from the data collection to the synthesis of research findings. Figure 2 above shows the flowchart related to the stages of structure of the methods adopted for this SLR.
Figure 2. Structure of the method.
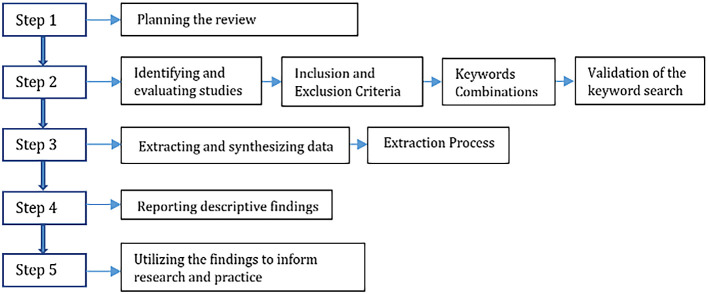
Stage 1. Planning the review
The PRISMA analysis was applied including the suggested phases 3 during the data collection and data processing such as identification, screening, eligibility and included (see the detailed description in Table 2 ). The efficiency and effectiveness of the keyword search was investigated by the measurement of the relative number of articles which are relevant when the search was conducted by the additional keywords. If there is no increase in the relevant papers after adding the additional keywords, it is considered that the initial keyword used is valid. Once research questions and hypotheses are formulated, a topic modelling approach has been used to uncover the main topics which are then re-analyse to answer the research questions.
Table 2. Criterion on inclusion and exclusion.
Stage 2. identifying and evaluating studies.
Primary study was done by using selected keywords to discover research trends of cybercrime legislation through systematic review from seven academic databases. To answer the research questions, keywords were selected by using AND and OR such as “cybercrime” OR “cyber-crime” OR “legislation” AND “combating”. The search platforms used were ACM Digital Library, Emerald, Hein Online, ProQuest, ScienceDirect, Scopus, and Westlaw Asia. The searches were conducted by using the keywords as stated above on these search backgrounds and filtered through the exclusion/inclusion criteria as stated in Table 2 .
Inclusion and exclusion criteria
The empirical findings on case studies and cybercrime legislations and commentaries on the application and implementation of legislation in combating cybercrime are included in the studies. All the studies were written in English and peer-reviewed. The details of criterion for inclusion and exclusion can be seen in the table below.
The above criteria was adopted in order to select the papers to be used for this SLR analysis. To be selected in the study, the paper needs to fulfil all the criteria stated as inclusion and the paper will be excluded if it fulfils one of the excluded criteria.
Keywords combination
To identify the right set of key words and achieve the research objectives, seven electronic research databases such as ACM Digital Library, Emerald, Hein Online, ProQuest, ScienceDirect, Scopus and Westlaw Asia were searched by using the main keywords such as “cybercrime”, “cybercrime” AND “legislation”, “cybercrime” AND “legislation” AND “combating”, “cybercrime” AND “legislation” AND “cybersecurity”, and lastly “cybercrime” AND “legislation” AND “cybersecurity” AND “combating”. Searches were conducted until no new studies were identified within the scope of selected criteria
Validation of keywords search
A total of (72) studies were identified from the search of primary keywords in the databases as stated in Table 3 . It was then reduced to (64) once duplicate studies were removed. By applying the inclusion/exclusion criteria, the papers were reduced to (56). All these (56) papers were analysed in detail and again the inclusion/exclusion method was applied and reduced to (46). These selected (46) papers were then reviewed in full and assessed for eligibility to be included in this SLR review. Further 16 papers were excluded for focusing on irrelevant issues and too general in nature. Finally, (30) papers were selected and used in this study.
Table 3. Database search summary.
Stage 3. extracting and synthesising data.
All the selected papers then had their data extricated to evaluate the comprehensiveness of information to achieve the research objectives. The extraction process also provides the details of the studies for review and to be specific about how the paper can address the research question. It was done based on the selection process as discussed above. The data extracted are then categorised and then recorded in a worksheet.
Thematic synthesis was used as recommended by 4 to synthesize the results. An integrated approach to the synthesis process also was used to ensure that all the research objectives were achieved. The findings are described in the following section. Table 3 explains the number of papers at each phase of the process by the keywords search changes on each of the data platforms to focus on the final selection of papers.
A substantial number of papers connected to cybercrime were identified based on the initial keyword searched. After going through the section process, only (30) papers were identified and analysed in detail. All the selected papers were read in full and relevant data were extracted and summarised in the table below. All primary studies focused on legislation relating to cybercrime in combating it.
RQ1: What is the legislation to combat cybercrime?
Through the first research question (What is the legislation to combat cybercrime?) ( Table 1 ), it was aimed to identify the common legislation used to charge the cybercriminals. It is vital to note that this systematic literature review intends to focus on legislation used to combat cybercrime and no other type of legislation and thus the selection process focuses solely on the studies relating to cybercrime legislation. There are a number of studies regarding cybercrime in general and other aspects of it. However, studies on cybercrime legislation itself is very much limited.
Table 1. Research questions.
There are a few international or regional instruments as stated in Table 5 . The Convention on Cybercrime which is also known as Budapest Convention is the first and only binding international instrument on cybercrime and it also serves as a basic guideline for any country which is developing cybercrime related legislation to combat cybercrime. 5 However, not all the countries are a party or signatory to these conventions and harmonise with the international instruments ( Table 4 ). Although the Convention is under the auspices of the European Council, it is open to all the countries. The Convention focuses on Cybercrime & electronic evidence and provides a comprehensive, operational and functional solution for the investigation and prosecution of cybercrime both domestically and between Parties, with a global reach.
Table 5. List of model laws.
Table 4. treaties & international agreements on cybercrime..
In addition to these international instruments, there are Model cybercrime laws which propose to implement the best practice principles of substantive offences expressed by the Convention. Model Laws are usually developed by international organisations through the inter-governmental process of negotiations and formal procedure. Apart from the Commonwealth Model Law, the rest of the Model Laws did not go through the inter-governmental process. The table below explains the Model Laws currently implemented.
These ITU-EU led Models assisted the countries in Caribbean, Pacific and Sub-Sharan Africa region in drafting and adopting the legislation relating to cybercrime. 6 Their framework is based upon Commonwealth Model Law which is based upon the Budapest Convention. The common thing is to improve the legal framework of cybercrime legislation and create awareness on the importance of criminalising and adopting a specialised cybercrime law. In essence, these Models assist the countries in harmonising their legislation on cybercrime and attempt to redefine many aspects of cybercrime and jurisdictional matters. 7
The United States and the European Union criminal law are on the same path relating to criminal offences in cyberspace. 8 In fact, all countries should aim to pursue a common criminal policy in order to deter the cybercriminals effectively by coordinating in facilitating the detection of cybercrime, collecting the evidence, investigating and finally prosecuting the case successfully. Cybercrime has been on the rise due to the fact that there are loopholes in both national and international legislation that the existing legal framework cannot deter or effectively combat the rise of cybercrimes.
Based on the data retrieved from the United Nations Conference on Trade and Development, 9 a total of 154 countries have already enacted the cybercrime legislation whereas 13 percent of countries in the world do not have any legislation relating to cybercrime and 5% of countries have draft legislation. There was no data found on the two percent of countries ( Figure 3 ).
Figure 3. Percentage of countries with cybercrime legislation.
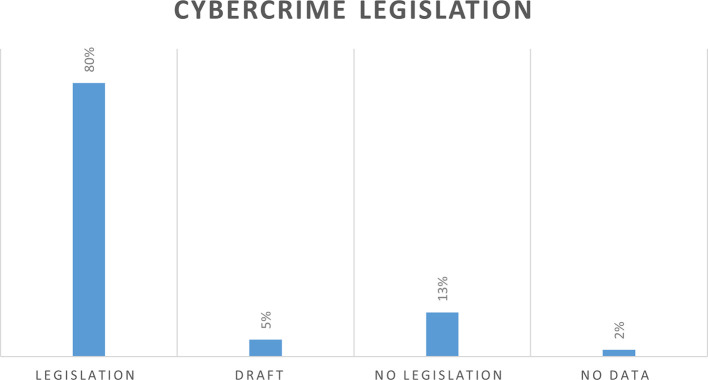
In the Africa region of 54 countries, 39 countries (72%) have cybercrime legislation, two countries (4%) have draft legislation, 12 countries (22%) do not have legislation and there is no data for one country (2%). (Siyanda, 2019) ( Figure 4 ).
Figure 4. Cybercrime legislation in Africa region.
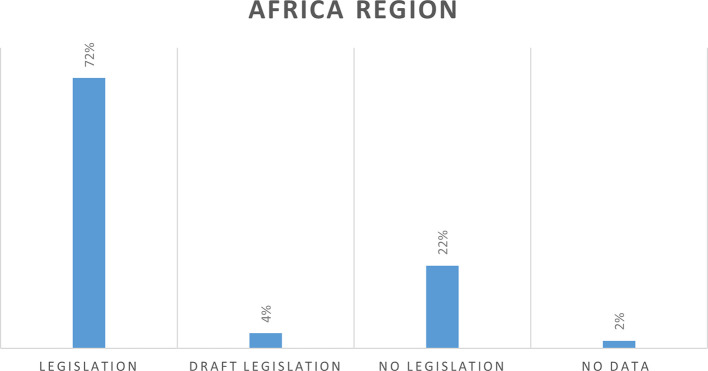
In the Americas which include 35 countries, 30 countries (86%) have cybercrime legislation, 1 country (3%) has draft legislation, and 4 countries (11%) do not have legislation ( Figure 5 ).
Figure 5. Cybercrime legislation in Americas region.
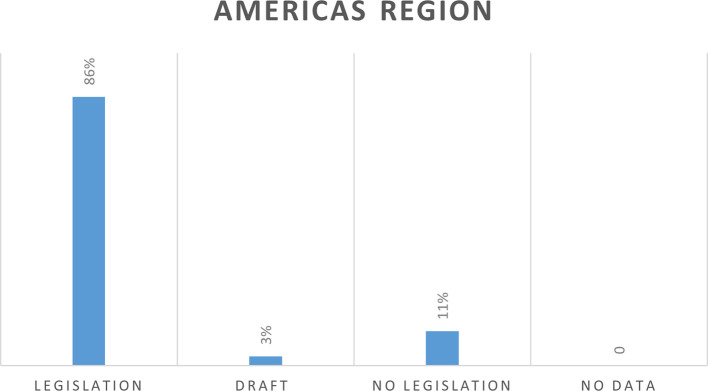
In the Asia Pacific region with 60 countries, 46 countries (77%) have legislation, seven countries (12%) have draft legislation, and seven countries (12%) do not have legislation ( Figure 6 ).
Figure 6. Cybercrime legislation in Asia-Pacific regio.
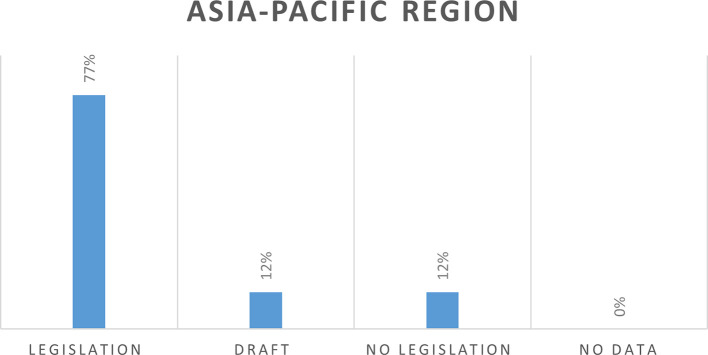
In Europe, out of 45 countries, 40 countries (89%) have legislation, three countries (7%) do not have legislation and no data for two countries (4%) ( Figure 7 ).
Figure 7. Cybercrime legislation in Europe region.
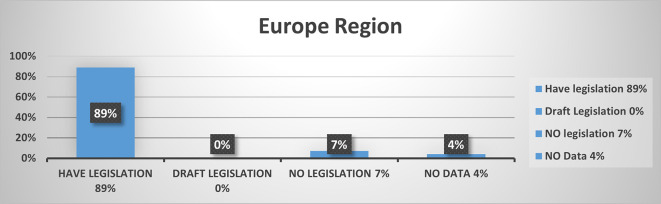
Even among the least developed countries, 31 countries (66%) have legislation, four countries (9%) have draft legislation and 12 countries (26%) have no legislation. Based on these statistics, it can be concluded that the majority of the countries in the world do have legislation relating to cybercrime. However, these legislations are obviously not efficient in deterring or combating the cybercrime effectively and the number of cybercrime cases have been on the rise constantly.
Different jurisdictions have used different types of legislation in charging/prosecuting the cybercriminals. 10 Some jurisdictions have specified cybercrime legislations and some had only relied on the legislation intended for traditional crimes. The table below shows an overview of the list of countries which have cybercrime legislation in English. Countries with the cybercrime bill, cybercrime draft legislation and cybercrime related legislation in non-English languages are excluded. It is essential to note that some jurisdictions used cybercrime as computer or digital crime. There are ways to improve the existing legislation relating to cybercrime and almost half of all published studies suggest harmonising national law with international law.
RQ2: How is the legislation used to combat cybercrime?
Legislation plays a major role in combating cybercrime and empowering the authority in dealing with the challenges posed by cybercrime ( Table 6 ). Legislation involves both the national and international law relating to cybercrime. While traditional legislation focuses on physical objects, cybercrime is largely associated with data or information which are electronic in nature and thus traditional law cannot be used effectively in combating cybercrime. 11 Thus, national laws need specialised legislation to criminalise cybercrime.
Table 6. List of countries with legislation in relating to cybercrime.
With the exception of spam offences, most of the jurisdictions in some western and European countries have criminalised and imposed criminal penalty on cybercrime cases such as misusing of computer tools and towards racism, xenophobia and online solicitation or exploitation of children. 12 However, the penalties imposed are not strong enough in deterring the cybercriminals from committing the crimes in cyberspace that there is a constant rising of cybercrime cases around the world. 13 Cybercrimes relating to integrity, confidentiality and accessibility of computer systems are mostly regarded as specific cyber offenses in many jurisdictions, whereas offences such as fraud, breach of privacy and identity offences are regarded as general cyber offences. 14 Those countries which impose criminal penalties or criminalise cybercrime use different methodology in application such as Finland regulates cyber offences via the new chapters of penal code. The evolving nature of cybercrime cannot be controlled efficiently unless the legislation is updated enough to be used to investigate, prosecute and adjudicate the cybercrime offenders. The cooperation from the internet service providers and internet industry players also play a crucial part in order for the law enforcement officers to detect, prevent and respond to the cybercrimes. Thus it is material that effective and updated legislation in par with the rapid advancement of technology must be in place in order to combat ever rising cybercrime globally. With this view in mind, the United States House of Representative Tom Graves sponsored a bill named Active Cyber Defense Certainty (“ACDC”) Act to update the Computer Fraud and Abuse Act under which the organisations can take active measures to go beyond the boundaries of their own networks. Procedural laws should also be enhanced or amended to ensure that issues related to cybercrime such as digital evidences are to be easily collected, stored and presented at the Court without any difficulty like any other traditional crimes. 15 Urgent International collaboration is needed to take every possible approach to criminalise all types of cybercrimes and to adopt specific procedural rules and investigation powers to investigate and prosecute cybercrimes specifically ( Figure 8 ). 16
Figure 8. Essential Instruments Involved in Combating Cybercrime.
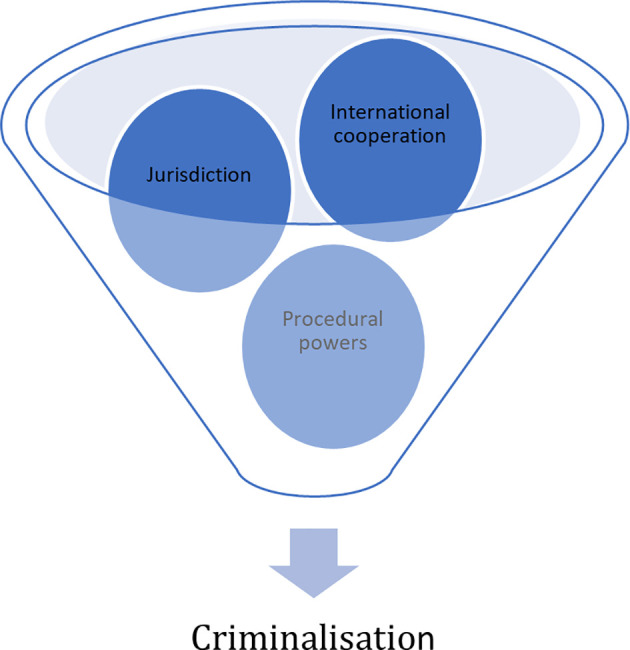
In the United Kingdom, the Computer Misuse Act 1990 which has been amended several times imposes criminal sanctions for cybercrime. Also under the Serious Crime Act 2015, criminal penalties can be imposed for an unauthorised act of causing serious damage to security or to the economy of the country. Even though the purpose is to punish and deter the criminals from committing the cybercrime, it does not deter the cybercriminals effectively since there still is a constant rise in cybercrime cases. 17
Thus, to use legislation as an effective tool to combat cybercrime, cybercrime legislation must cover an extensive list of offences committed in cyberspace like some jurisdictions focus only on selective cybercrimes such as child pornography and child protection as criminal offences. 18 Only a limited number of jurisdictions address and impose the duty on the service providers to monitor and voluntary supply of information as well as taking down the notifications and liability of access. Eighty percent of European countries have criminalised the cybercrimes compared to the other parts of the world whereas approximately only sixty percent of these countries criminalise the cybercrimes. 19 , 20
RQ3: What are the other approaches taken to combat cybercrime?
In addition to the enhancement of existing legislation, there is also a necessity to focus on the development of methodological manuals on the investigation of cyber related crimes in law enforcement. A substantial number of primary studies suggest that public awareness, technical approaches and ethical online education are as important as having efficient legislation in combating cybercrime. There is also a need for the international community to come together as one united nation to voice and be united in combating this cybercrime.
Even with the best possible legal framework, to address the technical vulnerabilities, private sectors must also contribute in fighting the rise of cybercrime by addressing technological vulnerabilities in the system and collaborating in operating the system with other jurisdictions. With the rapid development of technology, it is imperative to prevent and combat cybercrime by both public and private sectors. The role played by the criminal justice system is also important and thus have to ensure that justice officers are well equipped with the latest technology development. Thus, it is important to have cybercrime strategies in order to meet the challenges of law enforcement and prosecution. Raising public awareness of cybercrime, cooperation of private-public partnerships, criminal law enforcement and justice capacity are the areas that should be addressed as the cybercrime strategies. The importance of raising public awareness of cybercrime was highlighted in the United Nations Guidelines for Prevention of Crime. Most jurisdictions are aware of the importance of raising public awareness of cybercrime and engage in awareness campaigns. 21 , 22
Efforts have been made in all the jurisdictions to amend the existing legislation to address the need for higher standards of law enforcement. However, due to the nature of cybercrime, it is difficult to determine the jurisdiction of the court in practice. Firstly, it is not restricted to a particular country or territory. It can happen in any part of the world and involve multiple jurisdictions. Secondly, cybercrime can take place in any jurisdiction and it is not possible to exclude the jurisdiction of the states even though the legislation of that particular state is very weak. For example, if malicious cyber activities have been committed by using the cyber infrastructure of the country whose cyber legislation is very weak and attack on the other states, it is none to impossible to prosecute the cybercriminal in that particular jurisdiction.
It should be noted that preventing the crime is always better than waiting for it to happen since it effectively reduces the damages suffered as a result of the crime. 23 Cybercrime is complex and prevention of it generally involves a high degree of collaboration both at national and international levels between private and public sectors. 24 Technologies and networks are crucial infrastructure in preventing crime. 25 At the moment, there is no definite figure of losses suffered by cybercrimes though it is obvious that billions of damages have occurred every year. The availability of cyber security insurance may mitigate the losses suffered as a result of cybercrime. No doubt, there is a serious need to promote the implementation of precautionary actions in all the jurisdictions. 26 It has to be acknowledged that there are some limitations on this study since the findings were interpreted based on the articles written in English only. Some other important points may have been found if the research was extended to cover other languages. Also there may be some other articles which were not listed in the data cases that these studies have based upon. However, the findings of this research can be concluded as a reasonable representation of current and latest literature available and could serve as a pertinent reference to the policymakers.
Future research and recommendation
It is important to have adequate and efficient responses in place in order to combat cybercrime efficiently. Because of the nature of cybercrime which is borderless in nature, it is pertinent that there is a harmonisation of national law with the international law as well as a strong cooperation among the states. One of the most important factors is to criminalise the computer related offenses and having a special cybercrime legislation to govern these types of crime specifically and not to just merely rely on the traditional crime legislation. Cybercrime legislation must clearly spell out the cyber offences to ensure that cybercrime offenders can be prosecuted successfully.
Analysis of United Nation documents show that integrity, confidentiality and accessibility of computer systems are criminalised as core specific cyber offences in many countries whereas fraud or forgery, breach of privacy and identity offences are more often criminalised as general cyber offences. At the same time, sufficient procedural powers must be given to investigate the cybercrime efficiently. There should be proper steps to ensure key evidence is properly kept to prove the crime. Challenges faced by law enforcement to prosecute the cybercrimes have to be addressed. However, it is not sufficient. Need to criminalise all types of cybercrime and urgently need to fill the gap in the existing legislation by strengthening the legal response in facing the challenges of cybercrime.
Cybercrime in general involves multi-jurisdictional issues and thus combating cybercrime is bound to a number of challenges both to public and private sector; public sector issues involve legislation, investigation and prosecution whereas private sector issues involve technical vulnerabilities of the system in its design and operational aspects. In essence, there has to be specialised enforcement in investigation and prosecution involving cybercrimes due to the nature of electronic evidence involved which is different from traditional crimes. Resources should be centralised in one place in order to build capacity on specialised investigation and analysing the electronic evidence. At the same time, law enforcement authorities have to be trained consistently to ensure that they are abreast with all the latest technology.
Many countries have imposed criminal sanctions on crimes related to internet related crimes in order words called as cybercrimes as a legal response. Based on the INTERPOL’s ASEAN cyber threat assessment in January 2021, it was predicted that the growing trend in cybercrime is expected to continue since cybercriminals are well-organised and share resources and knowledge to their benefit. Thus, it is essential that there is a collaboration among the law enforcement agencies across the region. Since cybercrime is evolving constantly, it is vital for all the countries to enhance their legislation as well as the responses to the ever-evolving cybercrime threat in the digital era of the century. It is increasingly important to harmonise cybercrime legislation which cannot be achieved without the cooperation of the international operation. Those countries which do not criminalise cybercrime need to do so on an urgent basis by either enacting new legislation or amend the existing legislation and incorporate the provisions relating to cybercrime. Aggravated punishment should be meted out ensuring that effective penalties are imposed on cybercrime offenders. Public awareness and education programmes should be enhanced.
There are divergent national approaches globally because of the dissimilarities in the legal system historically and socio-cultural backgrounds. Thus, it is essential to have a truly effective legal response by cooperating among the international communities by coming up with an international legislation endorsed by industry executives, government officials, security professionals both from public and private sectors to come together and at the same time increase the much needed public awareness of the cybercrime. In essence, there is a need to have a bigger and better international cooperation on evidence collection, information sharing and criminal prosecution of those involved in cybercrimes. However, all these could not be done unless all the nations to begin with must have substantive provisions in the respective legislation which criminalise the cybercrimes. There are more questions than answers based on analysis of legal framework in combating cybercrime and it is indisputable that the legal framework of cybercrime has to be constantly adjusted and evolved to the extremely fast and highly complicated technical challenges.
Data availability
Figshare. Data_Excelfile.xlsx DOI: https://doi.org/10.6084/m9.figshare.20097614.v1 . 27 This project contains the following underlying data:
The data from the selected publications were extracted to assess the comprehensiveness and meet the study objectives which have been subsequently classified and entered into a spreadsheet.
Figshare: PRISMA checklist: A systematic literature review on cybercrime legislation. DOI: https://doi.org/10.6084/m9.figshare.20218730.v1
Figshare: Data_Excelfile
DOI: https://doi.org/10.6084/m9.figshare.20097614.v1
Data are available under the terms of the Creative Commons Attribution 4.0 International license (CC-BY 4.0).
Author contributions
Shereen Khan: Conceptualization, Formal Analysis, Investigation, Methodology, Validation, Visualization, and Writing – Original Draft Preparation
Tajneen Affnaan Saleh: Writing – Review & Editing
Magiswary Dorasamy: Conceptualization, Project Administration, Validation, Visualization, and Review
Nasreen Khan: Investigation, and Methodology
Olivia Tan Swee Leng: Conceptualization, and Methodology
Rossanne Gale Vergara: Data Curation, and Resources
Acknowledgement
We thank the Multimedia University, Malaysia, for funding the page charges and proofreading fee for this paper.
Funding Statement
We thank the Ministry of Higher Education, Malaysia for awarding us the Fundamental Research Grant Fund (FRGS/1/2019/SSI10/MMU/03/15) to conduct this research assigned to Dr. Shereen Khan. The conceptual framework presented in this paper is the proposed framework in this project.
[version 1; peer review: 2 approved]
- 1. Bechara FR, Schuch SB: Cybersecurity and Global Regulatory Challenges. Journal of Financial Crime. 2021;28(2):359–374. 10.1108/JFC-07-2020-0149 [ DOI ] [ Google Scholar ]
- 2. Redford M, Jefferson T: U.S. and EU Legislation on Cybercrime. European Intelligence and Security Informatics Conference. 2011;34–37. 10.1109/EISIC.2011.38 [ DOI ] [ Google Scholar ]
- 3. Moher D, Liberati A, Tetzlaff J, et al. : Preferred reporting items for systematic reviews and meta-analyses: the PRISMA statement. PLoS Medicine. 2009;6(7):e1000097. 10.1371/journal.pmed.1000097 [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- 4. Cruzes DS, Dyba T: Recommended steps for thematic synthesis in software engineering. International Symposium on Empirical Software Engineering and Measurement. 2011;275–284. [ Google Scholar ]
- 5. Clough J: A World of Difference: The Budapest Convention on Cybercrime and the Challenges of Harmonisation. Monash University Law Review. 2013;40(3):698–736. [ Google Scholar ]
- 6. Vertes-Olteanu A: Evolution of the criminal legal frameworks for preventing and combating cybercrime. Journal of Eastern-European Criminal Law. 2014;1:84–96. [ Google Scholar ]
- 7. Vorobets K: The main directions of cybercrime prevention in Ukraine. European Journal of Law and Public Administration. 2019;6(1):74–88. 10.18662/eljpa/65 [ DOI ] [ Google Scholar ]
- 8. United Nations Office on Drugs and Crime (UNODC): Comprehensive Study on Cybercrime. New York: United Nations;2013. Reference Source [ Google Scholar ]
- 9. United Nations Conference on Trade and Development: Cybercrime Legislation Worldwide, United Nations, Editor. New York: United Nations Publication;2018. [ Google Scholar ]
- 10. Sviatun O, Goncharuk O, Roman C, et al. : Combating Cybercrime: Economic and Legal Aspects. WSEAS Trans. Bus. Econ. 2021;18(18):751–762. 10.37394/23207.2021.18.72 [ DOI ] [ Google Scholar ]
- 11. Duryana Binti M: Combating the threats of cybercrimes in Malaysia: The efforts, the cyberlaws and the traditional laws. Computer Law & Security Review. 2013;29(1):66–76. 10.1016/j.clsr.2012.11.005 [ DOI ] [ Google Scholar ]
- 12. Christou G: The challenges of cybercrime governance in the European Union. European Politics and Society. 2018;19(3):355–375. 10.1080/23745118.2018.1430722 [ DOI ] [ Google Scholar ]
- 13. Cassim FF: Protecting personal information in the era of identity theft: Just how safe is our personal information from identity thieves. Potchefstroom Electronic Law Journal. 2015;18(2):68–110. 10.4314/pelj.v18i2.02 [ DOI ] [ Google Scholar ]
- 14. Correia SG: Responding to victimisation in a digital world: a case study of fraud and computer misuse reported in Wales. Crime Science. 2019;8(4). 10.1186/s40163-019-0099-7 [ DOI ] [ Google Scholar ]
- 15. Giuseppe C, Damian AT, Willem-Jan Van Den H: Cybercrime threat intelligence: A systematic multi-vocal literature review. Computers & Security. 2021;105:102258. 10.1016/j.cose.2021.102258 [ DOI ] [ Google Scholar ]
- 16. Chigada J, Madzinga R: Cyberattacks and threats during Covid-19: A Systematic Literature Review. South African Journal of Information Management. 2021;23(1):a1277. [ Google Scholar ]
- 17. Catherine F, Marek P: Fighting Cybercrime: A Review of the Irish Experience. International Journal of Cyber Criminology. 2020;14(2):383–399. 10.5281/zenodo.4766528 [ DOI ] [ Google Scholar ]
- 18. Quayyum F, Cruzes DS, Jaccheri L: Cybersecurity awareness for children: A systematic literature review. International Journal of Child-Computer Interaction. 2021;30:100343. 10.1016/j.ijcci.2021.100343 [ DOI ] [ Google Scholar ]
- 19. Calderoni F: The European legal framework on cybercrime: striving for an effective implementation. Crime, Law and Social Change. 2010;54(5):339–357. 10.1007/s10611-010-9261-6 [ DOI ] [ Google Scholar ]
- 20. Buono L: Gearing up the fight against cybercrime in the European Union: new set of rules and the establishment of the European cybercrime centre (ec3). New Journal of European Criminal Law. 2012;3(3-4):332–343. 10.1177/203228441200300307 [ DOI ] [ Google Scholar ]
- 21. Aloul FA: The need for effective awareness. Journal of Advances. 2012;3(3):176–183. 10.4304/jait.3.3.176-183 [ DOI ] [ Google Scholar ]
- 22. Catherine F, Lorraine BG, Jennifer K, et al. : Fighting Cybercrime: A Review of the Irish Experience. International Journal of Cyber Criminology. 2021;14(2). [ Google Scholar ]
- 23. Majid Y, Jacqueline D: Image-Based abuse, Non-consensual Pornography, Revenge Porn: A Study of Criminalization and Crime Prevention in Australia and England & Wales. International Journal of Cyber Criminology. 2019;13(2):578–594. [ Google Scholar ]
- 24. Mohammed SA: Global Surge in Cybercrimes – Indian Response and Empirical Evidence on Need for a Robust Crime Prevention System. International Journal of Cyber Criminology. 2020;14(2). [ Google Scholar ]
- 25. Jayasekara SD, Abeysekara I: Digital forensics and evolving cyber law: case of BIMSTEC countries. Journal of Money Laundering Control. 2019;22(4):744–752. 10.1108/JMLC-02-2019-0019 [ DOI ] [ Google Scholar ]
- 26. Moise A: Modernization of Romanian Legislation on Preventing and Combating Cybercrime and Implementation gap at European level. Revista de Stiinte Politice. 2015;45:186–199. [ Google Scholar ]
- 27. Khan S, Affnaan T, Dorasamy M, et al. : Data_Excelfile.xlsx. figshare. Dataset. 2022. 10.6084/m9.figshare.20097614.v1 [ DOI ]
Reviewer response for version 1
Duryana mohamed.
Competing interests: No competing interests were disclosed.
This is an open access peer review report distributed under the terms of the Creative Commons Attribution Licence, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
I found this research very interesting and new to me. As someone from a legal background and with some knowledge on cybercrime and Cyberlaws, I usually study and analyze the problem based on laws and cases then comment on whether the regulatory frameworks are adequate or not. Sometimes, I do a comparative analysis with other common law jurisdictions.
This research focuses on the SLR of cybercrime legislations of three regions which I think are quite comprehensive though they cover only English versions.
Overall, they can be considered as acceptable as I have not seen this kind of research before. Nevertheless, I found the findings are quite common and mostly similar to what have or had been recommended by most authors who wrote on regulatory frameworks of Cybercrimes, their adequacy, or their effectiveness.
Are the rationale for, and objectives of, the Systematic Review clearly stated?
Is the statistical analysis and its interpretation appropriate?
If this is a Living Systematic Review, is the ‘living’ method appropriate and is the search schedule clearly defined and justified? (‘Living Systematic Review’ or a variation of this term should be included in the title.)
Are sufficient details of the methods and analysis provided to allow replication by others?
Are the conclusions drawn adequately supported by the results presented in the review?
Reviewer Expertise:
cybercrime, cyber laws, professional ethics and electronic evidence.
I confirm that I have read this submission and believe that I have an appropriate level of expertise to confirm that it is of an acceptable scientific standard.
Sagwadi Mabunda
This article begins with an overview of the rise of cybercrime since the advent of the pandemic, detailing the losses encountered. It rightly expresses a lack of studies cataloging cybercrime legislation and regulations. The paper seeks to do two things: 1. provide thematically organised classification of legislation etc. through a systematic literature review (SLR) and 2. using the outcome of the SLR to propose a detailed framework to conduct future research.
The authors have identified appropriate research questions which are in line with the objectives they seek to achieve. Further, they have adequately defined their methodology by identifying the keywords employed and the sources consulted. There also appears to be a substantial number of sources consulted which makes for an expectation of credible results. The authors have identified the legislation, policies, conventions and model laws expected to be included in a study such as this. The analysis is not limited a particular region, but rather takes a global approach from which the reader can use as a starting point for their own research. The graphs and tables provided are clear and easy to comprehend.
The authors also provided insight into the substance of the legislation such as how jurisdictions criminalise and prosecute some cybercrimes.
While not fatal to the quality of the paper, it would benefitted from a more robust discussion section. Of the two things sought to be done by the authors, I am of the view that no.1 was successfully executed but no.2 could benefit for more exploration. The information contained in the paper makes a good contribution to the literature and as such is deserving of being indexed.
Cybercrime, criminal law, anti-money laundering, & anti-corruption law.
Associated Data
This section collects any data citations, data availability statements, or supplementary materials included in this article.
Data Availability Statement
- View on publisher site
- PDF (851.7 KB)
- Collections
Similar articles
Cited by other articles, links to ncbi databases.
- Download .nbib .nbib
- Format: AMA APA MLA NLM
Add to Collections

IMAGES
VIDEO
COMMENTS
Speech on Cyber Crime; 250 Words Essay on Cyber Crime Introduction. Cybercrime, an umbrella term encompassing a variety of offenses committed using digital technology, poses a significant threat to the modern world. As our reliance on technology increases, so does the potential for misuse, leading to a surge in cybercrimes. The Nature of Cybercrime
Instead the view should be to use the cyber security requirements as a way to improve overall security and thus avoid costly and damaging incidents in the future. If you think you're not at risk ...
Sample Essay on Cyber Crime in 100-180 Words. Cyber crime is a growing threat in today's digital world. It refers to any criminal activity that is carried out using computers or the internet. This includes hacking, identity theft, phishing scams, and online fraud.
cybercrime, the use of a computer as an instrument to further illegal ends, such as committing fraud, trafficking in child pornography and intellectual property, stealing identities, or violating privacy. Cybercrime, especially through the Internet, has grown in importance as the computer has become central to commerce, entertainment, and ...
This essay delves into the intricacies of cyber crime, exploring its types, causes, impacts, and measures to combat it, offering a comprehensive overview for students participating in essay writing competitions. Cyber Crime. Cyber crime refers to any criminal activity that involves a computer, networked device, or a network.
The Essay on Cyber Crime is an excellent guide on averting any possibilities of a cyber attack. On today's date, one is mostly on the internet for a variety of reasons. It becomes essential for one to know important tips that can keep one safe from cyberbullies, thieves, or blackmailers.
2. Proliferation and Commercialization (1990s-2000s) Explosion of Malware: Malicious software, including viruses, worms, and trojans, became more prevalent in the 1990s. Commercial Exploitation: Cyber Crime became increasingly profit-driven with the advent of financial fraud, identity theft, and the rise of the cyber black market. 3.
Terms including cybercrime, cyber-crime, computer crime, ... Matza describes the importance of subcultures, a loosening of binds to law and morality and a neutralisation of crime through a perception that the victim, the crime or the authority policing it are in some way invalid or inapplicable (see also Sykes and Matza, 1957).
Cyber crime evolved since 1990 when computers and networks came in to being. The types of attacks gradually grew from "Morris code worm" in 1997 to "Torjan" in 2004 and to "Ransom ware " attack in 2013. When computers and networks came into being in the 1990s, hacking was done basically to get more information about the systems.
Experts in cybersecurity emphasize the importance of vigilance, education, and strong security measures in protecting against cyber threats. ... Conclusion of Essay on Cyber Crime. In conclusion, cybercrime is a digital menace that affects us all. Whether it's hacking, scams, or cyberbullying, the consequences can be devastating. ...
Long and Short Essays on Cyber Crime for Students and Kids in English. We are providing students with essay samples on an extended essay of 500 words and a short piece of 150 words on the topic Cyber Crime for reference. Long Essay on Cyber Crime 500 Words in English. Long Essay on Cyber Crime is usually given to classes 7, 8, 9, and 10.
In 2020, the FBI reported 791,790 cases of cybercrimes, up from 300,000 in 2019 [9].Cybersecurity Ventures estimated that the global damage from cybercrimes in 2015 reached US$3 trillion and forecast an increase in damages to US$10.5 trillion in 2025 [10].As of 2020, phishing and similar crimes ranked as the most reported cybercrimes in the US, followed by the nondelivery of products [11].
Abstract. 'Cybercrime' is an umbrella concept used by criminologists to refer to traditional crimes that are enhanced via the use of networked technologies (i.e. cyber-enabled crimes) and newer forms of crime that would not exist without networked technologies (i.e. cyber-dependent crimes). Cybersecurity is similarly a very broad concept ...
Essay on Cybercrime in 100 Words. Cybercrime involves illegal activities like hacking, ransomware, cyberbullying, online fraud, etc. People who are involved in cybercrime or any similar activities are called hackers, scammers or fraudsters. Cybercrime leads to financial loss for individuals who have fallen victim to one.
500 Words Essay on Cyber Crime. Cybercrime is a type of crime in which illegal activities are carried out online or using computers. Cybercrime comes in a variety of forms which involves harassing online users. Cybercrime is the most serious and rapidly expanding type of crime in this day and age. Any person's life may be negatively impacted ...
Cybercrime victimization has become a 'routinized experience' for entire populations and contributes significantly to fear of crime (Cook et al. 2023; Levi 2022). The online harms generated by this digital pandemic are more pervasive than generally assumed, even when financial institutions cover victims' losses.
Cyber Security Essay. Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software.
Dr. Tamar Berenblum is the research director of the The Federmann Cyber Security Center - Cyber Law Program, Faculty of Law, the Hebrew University of Jerusalem, Israel, and the co-chair of the European Society of Criminology (ESC) Working Group on Cybercrime. Tamar is also a Post-Doc Research Fellow at the Netherlands Institute for the Study of Crime and Law Enforcement (NSCR), Netherlands ...
Cybersecurity is an industry that encompasses various measures and practices that safeguard computer systems and networks from unauthorized access, damage or theft, and it involves implementing strong security protocols, complex encryption methods and proactive countermeasures. By prioritizing cybersecurity, organizations can mitigate the risk ...
This essay discusses the importance of cyber security in today's digitally enabled world, citing a range of academic sources. ... "In 2017, cyber-crime costs accelerated with organizations spending nearly 23 percent more than 2016 — on average about $11.7 million." (varonis.com, 2019). ...
Abstract. Background: Cybercrime is a fast-growing digital crime and legislation falling behind with the fast-moving advancement of technology.One important factor projected by literature in combating cybercrime is legislation. In order to combat cybercrime, the role of cybercrime legislation is a challenge that has not been clearly studied before.