
Top 13 Thesis Topics in Computer Networking
Computer networking is a multi-disciplinary platform to explore the connections of multiple computing devices and their communication . Generally, a group of computers is interconnected to form the computer networks that share the messages and resources within the network . Based on the context information, computer networks enable investigation on different research domains such as telecommunication, computer engineering, science, information technology, data science, etc. We guide research scholars to formulate innovative thesis topics in computer networking with expert guidance.

Outline of Computer Networking
In computer networking, the connection among systems is established in any of the two ways: wired and wireless . For wired connection, it uses a direct dedicated physical link/cable . For a wireless connection, it uses radio waves or electromagnetic waves . Overall, this computer network has become the baseline for many communication networks . Below, we have given the list of features which different wired and wireless network projects for cse .
Wired Networks
- Security – High Security
- Trustworthiness – Enhanced
- Speed of Links – High speed but not distributed
- Switch Ports – 1 / live channel
- Mobility (User) – Associated to physical channel
- Troubleshoot / Provision – PHY layer
- Configuration Cost – High cost
- Environmental Limitation – length of switch
- Interference of Radio Frequency – No problem
- Structure Reconfiguration – Difficult and Expensive
Wireless Networks
- Security – Less Security
- Trustworthiness – Sometimes Higher and sometimes Lower
- Speed of Links – Low speed
- Switch Ports – 1 / WAP
- Mobility (User) – Unrestricted
- Troubleshoot / Provision – Complicated
- Configuration Cost – Reasonable and Acceptable price
- Environmental Limitation – effect of signal
- Interference of Radio Frequency – Need more focus
- Structure Reconfiguration – Easy and Fast
In modern days, computer networking has gained more attention in the research community due to its incredible improved characteristics. These characteristics help the scholars to enable the design novel thesis topics in computer networking and develop customized real and non-real applications.
Some of those important features are listed below,
What are the characteristics of computer networking?
- Act as utility and commodity for wireless communication applications
- Enable cognitive radio-based data transmission
- Support high (lifespan, coverage, and data rate) and low (cost and delay)
- Conjunction of optical and wireless network technologies
- User-friendly to develop heterogeneous wireless applications for ubiquitous amenities
In fact, the above-specified features play a significant role in each and every area of the wireless networking field. For an illustration purpose, we have given very few globally popular wireless networking applications.
This page primarily focuses on new Thesis Topics in Computer Networking with their supporting technologies and tools!!!
Applications of Wireless Networking
- Wireless Telemedicine and Healthcare in WBAN
- Smart Message Sharing in Vehicular ad hoc network simulator System
- Design and Development of Smart Power Grids
- Multimedia Streaming and Control Appliances in Personal / Home Network
Next, we can see that the different types of computer networking . In other words, we can say that the current emerging research areas of wireless networking. These are comprised of a huge number of thesis topics in the computer networkin g field. Our research team has deep knowledge in all these areas to direct you in the right direction of study and support you in implementing mini project on electronics and telecommunication . Beyond this, we also support you in other enabling technologies.
Types of Computer Networking
- Cognitive Radio Networks (CRN)
- Wireless Sensor Networks (WSN)
- Integration of Vehicle-Infrastructure
- 6G, Beyond 5G and 5G Networking
- Wireless Multimedia Content Sharing
- Wireless Personal Area Network (WPAN)
- Software Defined Networking (SDN)
- Network-on-Chips (Hybrid, Optical and Wireless)
- Radio Access Network (Fog / Edge / Cloud-RAN
- Radio Frequency Identification (RFID) Networks
- Ad-hoc Networks (FANET, VANET and MANET)
- Optical Networking and Communication (OBS and OCS)
- 4G / LTE Networks (LTE-M, LTE-A, LTE-A+)
- Wireless Body Area / Sensor Network (WBAN / WBSN)
- Network Function Virtualization (NFV)
- Wireless Underground and Undersea Communication
In addition, our experts from the research team have highlighted some evolving open research challenges in computer networking . These issues are seeking better solutions than the existing ones. In order to tackle these problems, we have designed several optimal approaches which are sure to yield the best results.
Open Issues of Computer Networking
- Beam Forming and Alignment
- Multiplicity and MIMO
- Network Administration and Control
- Transmission Scheduling and Power Management
- Selection of Channel / Frequency Band
- Diversity in Signaling
- Attainment of QoS
- Interference Prevention and Cancellation
If you are new to this field, make sure you have a fundamental knowledge of the following network terms. Since it is not just the key terminologies, it also creates a strong basement for any kind of computer networking research . We have unlimited resources to make you expertise in core technologies of computer networks.
Key terms in Computer Networking
- Network Model Designing
- Network Topology (Architecture)
- Network Management Systems
- Network and Routing Protocols
- Overall Network Performance Assessment
As mentioned earlier, there are numerous challenges still under the research in computer networking . Below, we have presented few more research challenges along with the appropriate solutions recommended by our experts to craft thesis topics in computer networking . Further, we are also ready to tackle other challenging issues regardless of their complexity levels .
Research Challenges of Computer Networking
- Solution – Use more free spectrum
- Solution – Improve the scalability of adapting UL/DL traffic
- Solution – Increase the unpaired spectrum consumption
- Solution – Increase the spectrum utilization and data transfer rate
- Solution – Harvest the unused energy and minimize the energy usage

How to Choosing a Thesis Topic? Main Steps
So far, we have debated on computer networks, different types of networking, characteristics, types, key terminologies, open issues, and research challenges of computer networking.
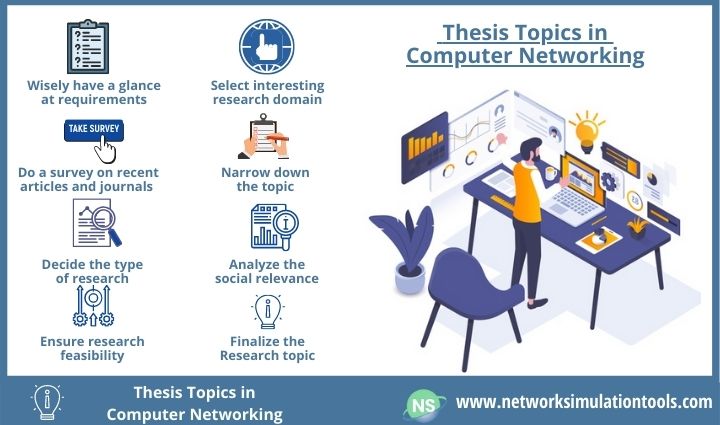
Now, we can see how intelligently the thesis topic in computer networking is needed to be selected. Here, we have given few important key tips to follow while choosing a research topic for networking thesis . And, these instructions are strictly followed by our team for the welfare of our handhold scholars.
- Wisely have glance on requirements – Go through the basic needs of your university on thesis. Since, some may prefer to choose suggested subject areas.
- Select interested research domain – Identify and your interested research area and find its current importance and future scope before confirmation
- Do survey on recent articles and journals – Perform in-depth literature review on recent articles and journals related to your research topic. And, make note on research gaps and unresolved problems
- Narrow down the topic – Be specific in your topic by eliminating the unwanted background information. This help you to find more research materials from different sources
- Decide the type of research – Decide on data acquisition and analysis techniques based on type of research
- Analyze the social relevance – Inspect whether your handpicked research problem solve any real-time issues or did your research create original contribution to the world development or did your research direct the future generation technologies
- Ensure research feasibility – Prior to finalizing topic, check it matches your research needsand you have sufficient time and resources to complete the study within stipulated time
- Finalize the topic – Get the guidance from experts in same field and discuss with them thoroughly before confirming the topic. Once, topic is confirmed then start writing your manuscript
In addition, we have also given some attention-grabbing research topics from top-demanding research areas of computer networking . And, those areas are already listed under “Types of computer networking” in the above sections. Additionally, if you need more Thesis Topics in Computer Networking in other related areas, then approach us.
Overall, we have limitless research ideas to support you in all means.
Trending Thesis Topics in Computer Networking
- Reliable Future Technologies of WBAN Security
- Enhanced QoS Provisioning and Control
- RFID assisted Mobile Devices Identification in WSN
- Node Mobility and Spectrum Handoff Management
- Controlling of Radio Resources for Improved Packet Access
- W-Fi / Wi-Max enabled Vehicular Telematics Applications and Services
- Inventory Maintenance of Fingerprinting and Security Evaluation
- Wireless Heterogeneous Networks Interworking and Management
- Data Protection in Communications using Cryptographic Encryption Technique
- Wireless Information-Centric Accessibility in Vehicular Telematics
- Efficient Computing of Cookie flags, Time and Scope for User Session Management
- New Authorization, Authentication and Accounting (AAA) Mechanisms
For any thesis topic, the proposed solutions are more important. Since it only determines how effectively you tackled your research problems. Also, it needs to positively impact your research work, which is better than the other existing techniques . Our research team is unique in proposing suitable research solutions because of their smart-thinking capabilities. Here, we have itemized few techniques based on key network operations that elevate network performance.
Methods for Computer Networking
- Multi-Agent RL
- Model based RL
- Partitioned
- Hierarchical
- Principal Curves
- T-Distributed SNE
- Non-linear Multiple Dimension Scaling
- Generative Topographic Network Model
- Locally Linear Embedding (LLE)
- Bayesian Models
- Mixture Dissemination
- Hidden Markov Model
- Probabilistic Graph Models
- Matrix Factorization (Non-Negative)
- Factor Examination
Then from the code development aspect, our developers have listed some widely used network simulation tools for computer networking projects . These tools are refined with modern toolboxes, libraries, modules, packages, plug-ins , etc., to construct the best networking models. Also, these tools are effective in measuring the performance of the network. Our developers have regular practice in all below computer networking tools. More than these, we are ready to serve you in other emerging technologies.
Simulation Tools for Computer Networking
- Network Simulator 3
- Network Simulator 2
Experimental Results for Thesis Topics in Computer Networking
Majorly, the network performance is achieved through the simulation and network parameters .
For example, based on the large packet size, we can prove that the proposed model is more efficient for managing any challenging packets (as multimedia streaming with high quality) . In the case of a real-world scenario, the deployed sensors will capture the data from their surroundings. It performs both theoretical design and practical study on proposed issues based on project needs . Next, it combines these results to create an overall simulation model.
Next, we can see that the basic standard for experimental settings depends on our ongoing projects investigation. In order to find the QoE of the simulated model , we need to determine the application and network QoS parameters. Since these two QoS are collectively referred to as quality of experience (QoE) . For instance:
• Application QoS – buffer level, re-buffering events, etc.
• Network QoS – latency, packet loss ratio (PLR), etc.
It is possible to acquire the privilege of a custom-based simulation environment setting that depends on the application’s needs. When the researchers commonly follow the same settings for utilizing protocols, it will be benefited for upcoming scholars in reality. Further, it is also easy to do a comparative study and identify the area’s developments on applying their proposed protocol. And, it saves the time of scholars on using previous experimental settings and enables them to test the application in different scenarios and settings . Below, we have enumerated some performance metrics used to assess the computer network model.
Simulation Parameters for Computer Networking
- Network Topology
- Transmission Power levels
- Node Placement and Type
- Network, Packet and Buffer Size
- Data Rate and Type(Transmission)
- Area of Convergence
- Overall Quantity of Sensor Nodes
- Simulator and Simulation Duration
- Number of Sensors / Sinks (Nodes)
- Mobility Speed and Models
- Link, Antenna and Channel Type
- Traffic and Packet Inter-Arrival Interval
- MAC and Routing Protocols
Thus far, we have completely seen the current research scope of computer networking . Now, we can see future research directions of the computer networking field. Our experts accurately predict these after the long survey and investigation of the current research scope of computer networks in many aspects.
Future Directions of Computer Networking
- MAC and PHY protocol
- Routing and Security Protocol
- Separation of Control Plane form Data Plane
- Enhancing the Speed of Communication
- Efficient Spectrum Sensing and Analysis
- Resource-Aware Spectrum Allocation
- Interference Revocation
- MIMO, Spectrum Sensing and Beamforming Methods
- Advance Traffic Monitoring and Control
- Improved Traffic Load Balancing
- Minimization of Control Signals
- Enhancing Spectrum Usage
- New 3D M-MIMO Technology for Communication
- 3D Beamforming Techniques to Control Beam
- Insider Threats Analysis
- Malicious Attack Detection
- Secure Network Architecture Construction
- New Design for Multi-tier Cells Infrastructure Development
- New Technologies of Heterogeneous Networks
- Adapting Device with Heterogeneity Nature
- Auditing and Accounting
- Security Strategies for Data Privacy
- Interference Avoidance and Control
- Power and Channel Assignments
To the end, we are glad to inform you that we wholeheartedly support you in research thesis topics in computer networking, code development, and thesis writing in the field of computer networking. So, if you are interested in availing of our end-to-end finest research service, then make contact with us.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |
Related Pages
YouTube Channel
Unlimited Network Simulation Results available here.

- Calculators
- Swot Analysis
- Pestle Analysis
- Five Forces Analysis
- Organizational Structure
- Copywriting
- Research Topics
- Student Resources
Services We Provide

Resources We Provide

Login / Register

- 15 Latest Networking Research Topics for Students
Comparative analysis between snort and suricata IDS software(s)
Description of the topic
The main focus of this research is to conduct a comparative analysis between Snort and Suricata software to determine which IDS software can provide better performance. There are various IDS software(s) available that can be used by organizations but it is difficult to identify which one is best (Aldarwbi et al., 2022). Different organizational structures are often facing problems while setting up an IDS system which results in false positives and intrusions. Through this research, it can be identified which IDS software is better and what secure configuration is required to detect intrusions (Waleed et al., 2022).
Research objectives
- To evaluate Snort and Suricata IDS software(s) to determine the most optimal one.
- To identify the false positive rate of Snort and Suricata on the networked environment.
Research questions
RQ1: Which IDS software can perform better on the production network in terms of performance, security, scalability and reliability?
RQ2: What different ways can be followed to deal with false positive problems in IDS technology?
Research methodology
The given research objectives and research questions can be addressed using quantitative research methodology where an experimental approach can be followed. For the given topic, both Snort and Suricata IDS systems should be configured and tested against different attacks. Depending on the findings, it can be analyzed which IDS software can perform better in terms of performance and security (Shuai & Li, 2021).
- Aldarwbi, M.Y., Lashkari, A.H. and Ghorbani, A.A. (2022) “The sound of intrusion: A novel network intrusion detection system,” Computers and Electrical Engineering , 104, p. 108455.
- Shuai, L. and Li, S. (2021) “Performance optimization of Snort based on DPDK and Hyperscan,” Procedia Computer Science , 183, pp. 837-843.
- Waleed, A., Jamali, A.F. and Masood, A. (2022) “Which open-source ids? Snort, Suricata or Zeek,” Computer Networks , 213, p. 109116.
Role of honeypots and honey nets in network security
Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network. For example, honey pots and honeynet approaches look almost the same and have the same purpose but work differently. Under this research topic, the configuration of honeynets and honeypots can be done to check which one can perform better security in terms of trapping cyber attackers. The entire implementation can be carried out in the cloud-based instance for improved security and it can be identified which type of honey pot technology must be preferred (Maesschalck et al., 2022).
- To set up a honey pot system using Open Canary on the virtual instance to protect against cyber attackers.
- To set up a honeynet system on the virtual instance to assure protection is provided against malicious attackers.
- To test honeypots and honeynets by executing DDoS attacks to check which can provide better security.
RQ1: Why is there a need for using honeypots over honey pots in a production networked environment?
RQ2: What are the differences between cloud-based and local honey pot systems for endpoint protection?
This research can be carried out using the quantitative method of research. At the initial stage, the implementation of honeypots and honeypots can be done on the virtual instance following different security rules. Once the rules are applied, the testing can be performed using a Kali Linux machine to check whether honey pots were effective or honeynets (Gill et al., 2020).
- Feng, H. et al. (2023) “Game theory in network security for Digital Twins in industry,” Digital Communications and Networks [Preprint].
- Gill, K.S., Saxena, S. and Sharma, A. (2020) “GTM-CSEC: A game theoretic model for cloud security based on ids and Honeypot,” Computers & Security , 92, p. 101732
- Maesschalck, S. et al. (2022) “Don’t get stung, cover your ICS in honey: How do honeypots fit within industrial control system security,” Computers & Security , 114, p. 102598.
How do malware variants are progressively improving?
This research can be based on evaluating how malware variants are progressively improving and what should be its state in the coming future. Malware is able to compromise confidential user’s information assets which is why this research can be based on identifying current and future consequences owing to its improvements (Deng et al., 2023). In this field, there is no research work that has been carried out to identify how malware variants are improving their working and what is expected to see in future. Once the evaluation is done, a clear analysis can also be done on some intelligent preventive measures to deal with dangerous malware variants and prevent any kind of technological exploitation (Tang et al., 2023).
- To investigate types of malware variants available to learn more about malware's hidden features.
- To focus on future implications of malware executable programs and how they can be avoided.
- To discuss intelligent solutions to deal with all malware variants.
RQ1: How do improvements in malware variants impact enterprises?
RQ2: What additional solutions are required to deal with malware variants?
In this research, qualitative analysis can be conducted on malware variants and the main reason behind their increasing severity. The entire research can be completed based on qualitative research methodology to answer defined research questions and objectives. Some real-life case studies should also be integrated into the research which can be supported by the selected topic (Saidia Fasci et al., 2023).
- Deng, H. et al. (2023) “MCTVD: A malware classification method based on three-channel visualization and deep learning,” Computers & Security , 126, p. 103084.
- Saidia Fasci, L. et al. (2023) “Disarming visualization-based approaches in malware detection systems,” Computers & Security , 126, p. 103062.
- Tang, Y. et al. (2023) “BHMDC: A byte and hex n-gram based malware detection and classification method,” Computers & Security , p. 103118.
Implementation of IoT - enabled smart office/home using cisco packet tracer
The Internet of Things has gained much more attention over the past few years which is why each enterprise and individual aims at setting up an IoT network to automate their processes (Barriga et al., 2023). This research can be based on designing and implementing an IoT-enabled smart home/office network using Cisco Packet Tracer software. Logical workspace, all network devices, including IoT devices can be used for preparing a logical network star topology (Elias & Ali, 2014). To achieve automation, the use of different IoT rules can be done to allow devices to work based on defined rules.
- To set up an IoT network on a logical workspace using Cisco Packet Tracer simulation software.
- To set up IoT-enabled rules on an IoT registration server to achieve automation (Hou et al., 2023).
RQ: Why is the Cisco packet tracer preferred for network simulation over other network simulators?
At the beginning of this research, a quantitative research methodology can be followed where proper experimental set-up can be done. As a packet tracer is to be used, the star topology can be used to interconnect IoT devices, sensors and other network devices at the home/office. Once a placement is done, the configuration should be done using optimal settings and all IoT devices can be connected to the registration server. This server will have IoT rules which can help in achieving automation by automatically turning off lights and fans when no motion is detected (Baggan et al., 2022).
- Baggan, V. et al. (2022) “A comprehensive analysis and experimental evaluation of Routing Information Protocol: An Elucidation,” Materials Today: Proceedings , 49, pp. 3040–3045.
- Barriga, J.A. et al. (2023) “Design, code generation and simulation of IOT environments with mobility devices by using model-driven development: Simulateiot-Mobile,” Pervasive and Mobile Computing , 89, p. 101751.
- Elias, M.S. and Ali, A.Z. (2014) “Survey on the challenges faced by the lecturers in using packet tracer simulation in computer networking course,” Procedia - Social and Behavioral Sciences , 131, pp. 11–15.
- Hou, L. et al. (2023) “Block-HRG: Block-based differentially private IOT networks release,” Ad Hoc Networks , 140, p. 103059.
Comparative analysis between AODV, DSDV and DSR routing protocols in WSN networks
For wireless sensor networks (WSN), there is a major need for using WSN routing rather than performing normal routines. As WSN networks are self-configured, there is a need for an optimal routing protocol that can improve network performance in terms of latency, jitter, and packet loss (Luo et al., 2023). There are often various problems faced when WSN networks are set up due to a lack of proper routing protocol selection. As a result of this, severe downtime is faced and all links are not able to communicate with each other easily (Hemanand et al., 2023). In this research topic, the three most widely used WSN routing protocols AODV, DSDV and DSR can be compared based on network performance. To perform analysis, three different scenarios can be created in network simulator 2 (Ns2).
- To create three different scenarios on ns2 software to simulate a network for 1 to 100 seconds.
- To analyze which WSN routing is optimal in terms of network performance metrics, including latency, jitter and packet loss.
- To use CBR and NULL agents for all wireless scenarios to start with simulation purposes.
RQ: How do AODV, DSR and DSDV routing protocols differ from each other in terms of network performance?
This research can be carried out using a quantitative research method. The implementation for the provided research topic can be based on Ns2 simulation software where three different scenarios can be created (AODV, DSDV and DSR). For each scenario, NULL, CSR and UDP agents can be done to start with simulation for almost 1 to 100 seconds. For all transmissions made during the given time, network performance can be checked to determine which routing is best (Mohapatra & Kanungo, 2012).
- Human and, D. et al. (2023) “Analysis of power optimization and enhanced routing protocols for Wireless Sensor Networks,” Measurement: Sensors , 25, p. 100610. Available at: https://doi.org/10.1016/j.measen.2022.100610.
- Luo, S., Lai, Y. and Liu, J. (2023) “Selective forwarding attack detection and network recovery mechanism based on cloud-edge cooperation in software-defined wireless sensor network,” Computers & Security , 126, p. 103083. Available at: https://doi.org/10.1016/j.cose.2022.103083.
- Mohapatra, S. and Kanungo, P. (2012) “Performance analysis of AODV, DSR, OLSR and DSDV routing protocols using NS2 Simulator,” Procedia Engineering , 30, pp. 69–76. Available at: https://doi.org/10.1016/j.proeng.2012.01.835.
Securing wireless network using AAA authentication and WLAN controller
Wireless networks often face intrusion attempts due to insecure protocols and sometimes open SSIDs. As a result of this, man-in-the-middle and eavesdropping attacks become easier which results in the loss of confidential information assets (Sivasankari & Kamalakkannan, 2022). When it comes to managing networks in a large area, there are higher chances for attacks that enable cyber attackers in intercepting ongoing communication sessions. However, there is currently no research conducted where the use of AAA authentication has been done with WLAN controllers to make sure a higher level of protection is provided (Nashwan, 2021). The proposed research topic can be based on securing wireless networks with the help of AAA authentication and WLAN controllers. The use of AAA authentication can be done to set up a login portal for users whilst the WLAN controller can be used for managing all wireless access points connected to the network (Nashwan, 2021).
- To set up AAA authentication service on the wireless network simulated on Cisco Packet Tracer for proper access control.
- To set up a WLAN controller on the network to manage all wireless access points effortlessly.
- To use WPA2-PSK protocol on the network to assure guest users are only able to access wireless networks over a secure protocol.
RQ1: What additional benefits are offered by AAA authentication on the WLAN networks?
RQ2: Why are wireless networks more likely to face network intrusions than wired networks?
This research topic is based on the secure implementation of a wireless LAN network using a Cisco packet tracer. Hence, this research can be carried out using a quantitative research method. The implementation can be carried out using AAA authentication which can assure that access control is applied for wireless logins. On the other hand, a WLAN controller can also be configured which can ensure that all WAPs are managed (ZHANG et al., 2012).
- Nashwan, S. (2021) “AAA-WSN: Anonymous Access Authentication Scheme for wireless sensor networks in Big Data Environment,” Egyptian Informatics Journal , 22(1), pp. 15–26.
- Sivasankari, N. and Kamalakkannan, S. (2022) “Detection and prevention of man-in-the-middle attack in IOT network using regression modeling,” Advances in Engineering Software , 169, p. 103126.
- ZHANG, J. et al. (2012) “AAA authentication for Network mobility,” The Journal of China Universities of Posts and Telecommunications , 19(2), pp. 81-86.
OWASP's approach to secure web applications from web application exploits
The research can revolve around the development of web applications by considering OWASP's top 10 rules. Usually, web applications are deployed by organizations depending on their requirements and these applications are vulnerable to various exploits, including injection, broken authentication and other forgery attacks (Poston, 2020). Identifying every single vulnerability is difficult when reference is not taken and often organizations end up hosting a vulnerable server that leads to privacy issues and compromises confidential information easily. In this research, OWASP's top 10 approaches can be followed to develop a secure web application that can be able to protect against top web application exploits. This approach is based on emphasizing severe and minor vulnerabilities which must be patched for protecting against web application attacks (Deepa & Thilagam, 2016).
- The first objective can be setting up an insecure web application on the cloud environment which can be exploited with different techniques.
- The second objective can be to consider all techniques and procedures provided by OWASP's top 10 methodologies.
- The last objective can be applying all fixes to insecure web applications to make them resistant to OWASP top 10 attacks (Sonmez, 2019).
RQ1: What are the benefits of using OWASP's top 10 approaches to harden web applications in comparison to other security approaches?
The research methodology considered for this research project can be quantitative using an experimental approach. The practical work can be done for the selected topic using AWS or the Azure cloud platform. Simply, a virtual web server can be configured and set up with a secure and insecure web application. Following OWASP's top 10 techniques and procedures, the web application can be secured from possible attacks. In addition, insecure applications can also be exploited and results can be evaluated (Applebaum et al., 2021).
- Applebaum, S., Gaber, T. and Ahmed, A. (2021) “Signature-based and machine-learning-based web application firewalls: A short survey,” Procedia Computer Science , 189, pp. 359–367. Available at: https://doi.org/10.1016/j.procs.2021.05.105.
- Deepa, G. and Thilagam, P.S. (2016) “Securing web applications from injection and logic vulnerabilities: Approaches and challenges,” Information and Software Technology , 74, pp. 160–180. Available at: https://doi.org/10.1016/j.infsof.2016.02.005.
- Poston, H. (2020) “Mapping the owasp top Ten to the blockchain,” Procedia Computer Science , 177, pp. 613-617. Available at: https://doi.org/10.1016/j.procs.2020.10.087.
- Sonmez, F.Ö. (2019) “Security qualitative metrics for Open Web Application Security Project Compliance,” Procedia Computer Science , 151, pp. 998-1003. Available at: https://doi.org/10.1016/j.procs.2019.04.140.
Importance of configuring RADIUS (AAA) server on the network
User authentication has become significant nowadays as it guarantees that a legitimate user is accessing the network. But a problem is faced when a particular security control is to be identified for authentication and authorization. These controls can be categorized based on mandatory access controls, role-based access control, setting up captive portals and many more. Despite several other security controls, one of the most efficient ones is the RADIUS server (SONG et al., 2008). This server can authenticate users on the network to make sure network resources are accessible to only legal users. This research topic can be based on understanding the importance of RADIUS servers on the network which can also be demonstrated with the help of the Cisco Packet Tracer. A network can be designed and equipped with a RADIUS server to ensure only legal users can access network resources (WANG et al., 2009).
- To configure RADIUS (AAA) server on the network which can be able to authenticate users who try to access network resources.
- To simulate a network on a packet tracer simulation software and verify network connectivity.
RQ1: What are other alternatives to RADIUS (AAA) authentication servers for network security?
RQ2: What are the common and similarities between RADIUS and TACACS+ servers?
As a logical network is to be designed and configured, a quantitative research methodology can be followed. In this research coursework, a secure network design can be done using a packet tracer network simulator, including a RADIUS server along with the DMZ area. The configuration for the RADIUS server can be done to allow users to only access network resources by authenticating and authorizing (Nugroho et al., 2022).
- Nugroho, Y.S. et al. (2022) “Dataset of network simulator related-question posts in stack overflow,” Data in Brief , 41, p. 107942.
- SONG, M., WANG, L. and SONG, J.-de (2008) “A secure fast handover scheme based on AAA protocol in Mobile IPv6 Networks,” The Journal of China Universities of Posts and Telecommunications , 15, pp. 14-18.
- WANG, L. et al. (2009) “A novel congestion control model for interworking AAA in heterogeneous networks,” The Journal of China Universities of Posts and Telecommunications , 16, pp. 97-101.
Comparing mod security and pF sense firewall to block illegitimate traffic
Firewalls are primarily used for endpoint security due to their advanced features ranging from blocking to IDS capabilities and many more. It is sometimes challenging to identify which type of firewall is best and due to this reason, agencies end up setting up misconfigured firewalls (Tiwari et al., 2022). This further results in a cyber breach, destroying all business operations. The research can be emphasizing conducting a comparison between the two most widely used firewalls i.e. Mod Security and pF sense. Using a virtualized environment, both firewalls can be configured and tested concerning possible cyber-attacks (Lu & Yang, 2020).
- To use the local environment to set up Mod security and pF sense firewall with appropriate access control rules.
- To test both firewalls by executing distributed denial of service attacks from a remote location.
- To compare which type of firewall can provide improved performance and robust security.
RQ: How do Mod security and pF sense differ from each other in terms of features and performance?
The practical experimentation for both firewalls can be done using a virtualized environment where two different machines can be created. Hence, this research can be carried out using a quantitative research method . The first machine can have Mod security and the second machine can have pF sense configured. A new subnet can be created which can have these two machines. The third machine can be an attacking machine which can be used for testing firewalls. The results obtained can be then evaluated to identify which firewall is best for providing security (Uçtu et al., 2021).
- Lu, N. and Yang, Y. (2020) “Application of evolutionary algorithm in performance optimization of Embedded Network Firewall,” Microprocessors and Microsystems , 76, p. 103087.
- Tiwari, A., Papini, S. and Hemamalini, V. (2022) “An enhanced optimization of parallel firewalls filtering rules for scalable high-speed networks,” Materials Today: Proceedings , 62, pp. 4800-4805.
- Uçtu, G. et al. (2021) “A suggested testbed to evaluate multicast network and threat prevention performance of Next Generation Firewalls,” Future Generation Computer Systems , 124, pp. 56-67.
Conducting a comprehensive investigation on the PETYA malware
The main purpose of this research is to conduct a comprehensive investigation of the PETYA malware variant (McIntosh et al., 2021). PETYA often falls under the category of ransomware attacks which not only corrupt and encrypt files but can compromise confidential information easily. Along with PETYA, there are other variants also which lead to a security outage and organizations are not able to detect these variants due to a lack of proper detection capabilities (Singh & Singh, 2021). In this research, a comprehensive analysis has been done on PETYA malware to identify its working and severity level. Depending upon possible causes of infection of PETYA malware, some proactive techniques can also be discussed (Singh & Singh, 2021). A separation discussion can also be made on other malware variants, their features, and many more.
- The main objective of this research is to scrutinize the working of PETYA malware because a ransomware attack can impact the micro and macro environment of the organizations severely.
- The working of PETYA malware along with its source code can be reviewed to identify its structure and encryption type.
- To list all possible CVE IDs which are exploited by the PETYA malware.
RQ1: How dangerous is PETYA malware in comparison to other ransomware malware?
This research can be based on qualitative research methodology to evaluate the working of PETYA malware from various aspects, the methodology followed and what are its implications. The research can be initiated by evaluating the working of PETYA malware, how it is triggered, what encryption is applied and other factors. A sample source code can also be analyzed to learn more about how cryptography is used with ransomware (Abijah Roseline & Geetha, 2021).
- Abijah Roseline, S. and Geetha, S. (2021) “A comprehensive survey of tools and techniques mitigating computer and mobile malware attacks,” Computers & Electrical Engineering , 92, p. 107143.
- McIntosh, T. et al. (2021) “Enforcing situation-aware access control to build malware-resilient file systems,” Future Generation Computer Systems , 115, pp. 568-582.
- Singh, J. and Singh, J. (2021) “A survey on machine learning-based malware detection in executable files,” Journal of Systems Architecture , 112, p. 101861.
Setting up a Live streaming server on the cloud platform
Nowadays, various organizations require a live streaming server to stream content depending upon their business. However, due to a lack of proper hardware, organizations are likely to face high network congestion, slowness and other problems (Ji et al., 2023). Referring to the recent cases, it has been observed that setting up a streaming server on the local environment is not expected to perform better than a cloud-based streaming server configuration (Martins et al., 2019). This particular research topic can be based on setting up a live streaming server on the AWS or Azure cloud platform to make sure high network bandwidth is provided with decreased latency. The research gap analysis would be conducted to analyze the performance of live streaming servers on local and cloud environments in terms of network performance metrics (Bilal et al., 2018).
- To set up a live streaming server on the AWS or Azure cloud platform to provide live streaming services.
- To use load balancers alongside streaming servers to ensure the load is balanced and scalability is achieved.
- To use Wireshark software to test network performance during live streaming.
RQ1: Why are in-house streaming servers not able to provide improved performance in comparison to cloud-based servers?
RQ2: What additional services are provided by cloud service providers which help in maintaining network performance?
The implementation is expected to carry out on the AWS cloud platform with other AWS services i.e. load balancer, private subnet and many more (Efthymiopoulou et al., 2017). Hence, this research can be carried out using a quantitative research method. The configuration of ec2 instances can be done which can act as a streaming server for streaming media and games. For testing this project, the use of OBS studio can be done which can help in checking whether streaming is enabled or not. For network performance, Wireshark can be used for testing network performance (George et al., 2020).
- Bilal, KErbad, A. and Hefeeda, M. (2018) “QoE-aware distributed cloud-based live streaming of multi-sourced Multiview Videos,” Journal of Network and Computer Applications , 120, pp. 130-144.
- Efthymiopoulou, M. et al. (2017) “Robust control in cloud-assisted peer-to-peer live streaming systems,” Pervasive and Mobile Computing , 42, pp. 426-443.
- George, L.C. et al. (2020) “Usage visualization for the AWS services,” Procedia Computer Science , 176, pp. 3710–3717.
- Ji, X. et al. (2023) “Adaptive QoS-aware multipath congestion control for live streaming,” Computer Networks , 220, p. 109470.
- Martins, R. et al. (2019) “Iris: Secure reliable live-streaming with Opportunistic Mobile Edge Cloud offloading,” Future Generation Computer Systems , 101, pp. 272-292.
Significance of using OSINT framework for Network reconnaissance
Network reconnaissance is becoming important day by day when it comes to penetration testing. Almost all white hat hackers are dependent on the OSINT framework to start with network reconnaissance and footprinting when it comes to evaluating organizational infrastructure. On the other hand, cyber attackers are also using this technique to start fetching information about their target. Currently, there is no investigation carried out to identify how effective the OSINT framework is over traditional reconnaissance activities (Liu et al., 2022). This research is focused on using OSINT techniques to analyze victims using different sets of tools like Maltego, email analysis and many other techniques. The analysis can be based on fetching sensitive information about the target which can be used for conducting illegal activities (Abdullah, 2019).
- To use Maltego software to conduct network reconnaissance on the target by fetching sensitive information.
- To compare the OSINT framework with other techniques to analyze why it performs well.
RQ1: What is the significance of using the OSINT framework in conducting network reconnaissance?
RQ2: How can the OSINT framework be used by cyber hackers for conducting illegitimate activities?
The OSINT framework is easily accessible on its official website where different search options are given. Hence, this research can be carried out using a quantitative research method. Depending upon the selected target, each option can be selected and tools can be shortlisted for final implementation. Once the tools are shortlisted, they can be used to conduct network reconnaissance (González-Granadillo et al., 2021). For example, Maltego can be used as it is a powerful software to fetch information about the target.
- Abdullah, S.A. (2019) “Seui-64, bits an IPv6 addressing strategy to mitigate reconnaissance attacks,” Engineering Science and Technology , an International Journal, 22(2), pp. 667–672.
- Gonzalez-Granadillo, G. et al. (2021) “ETIP: An enriched threat intelligence platform for improving OSINT correlation, analysis, visualization and sharing capabilities,” Journal of Information Security and Applications , 58, p. 102715.
- Liu, W. et al. (2022) “A hybrid optimization framework for UAV Reconnaissance Mission Planning,” Computers & Industrial Engineering , 173, p. 108653.
Wired and wireless network hardening in cisco packet tracer
At present, network security has become essential and if enterprises are not paying attention to the security infrastructure, there are several chances for cyber breaches. To overcome all these issues, there is a need for setting up secure wired and wireless networks following different techniques such as filtered ports, firewalls, VLANs and other security mechanisms. For the practical part, the use of packet tracer software can be done to design and implement a highly secure network (Sun, 2022).
- To use packet tracer simulation software to set up secure wired and wireless networks.
- Use different hardening techniques, including access control rules, port filtering, enabling passwords and many more to assure only authorized users can access the network (Zhang et al., 2012).
RQ: Why is there a need for emphasizing wired and wireless network security?
Following the quantitative approach, the proposed research topic implementation can be performed in Cisco Packet Tracer simulation software. Several devices such as routers, switches, firewalls, wireless access points, hosts and workstations can be configured and interconnected using Cat 6 e cabling. For security, every device can be checked and secure design principles can be followed like access control rules, disabled open ports, passwords, encryption and many more (Smith & Hasan, 2020).
- Smith, J.D. and Hasan, M. (2020) “Quantitative approaches for the evaluation of Implementation Research Studies,” Psychiatry Research , 283, p. 112521.
- Sun, J. (2022) “Computer Network Security Technology and prevention strategy analysis,” Procedia Computer Science , 208, pp. 570–576.
- Zhang, YLiang, R. and Ma, H. (2012) “Teaching innovation in computer network course for undergraduate students with a packet tracer,” IERI Procedia , 2, pp. 504–510.
Different Preemptive ways to resist spear phishing attacks
When it comes to social engineering, phishing attacks are rising and are becoming one of the most common ethical issues as it is one of the easiest ways to trick victims into stealing information. This research topic is based on following different proactive techniques which would help in resisting spear phishing attacks (Xu et al., 2023). This can be achieved by using the Go-Phish filter on the machine which can automatically detect and alert users as soon as the phished URL is detected. It can be performed on the cloud platform where the apache2 server can be configured along with an anti-phishing filter to protect against phishing attacks (Yoo & Cho, 2022).
- To set up a virtual instance on the cloud platform with an apache2 server and anti-phishing software to detect possible phishing attacks.
- To research spear phishing and other types of phishing attacks that can be faced by victims (Al-Hamar et al., 2021).
RQ1: Are phishing attacks growing just like other cyber-attacks?
RQ2: How effective are anti-phishing filters in comparison to cyber awareness sessions?
The entire research can be conducted by adhering to quantitative research methodology which helps in justifying all research objectives and questions. The implementation of the anti-phishing filter can be done by creating a virtual instance on the cloud platform which can be configured with an anti-phishing filter. Along with this, some phishing attempts can also be performed to check whether the filter works or not (Siddiqui et al., 2022).
- Al-Hamar, Y. et al. (2021) “Enterprise credential spear-phishing attack detection,” Computers & Electrical Engineering , 94, p. 107363.
- Siddiqui, N. et al. (2022) “A comparative analysis of US and Indian laws against phishing attacks,” Materials Today: Proceedings , 49, pp. 3646–3649.
- Xu, T., Singh, K. and Rajivan, P. (2023) “Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks,” Applied Ergonomics , 108, p. 103908.
- Yoo, J. and Cho, Y. (2022) “ICSA: Intelligent chatbot security assistant using text-CNN and multi-phase real-time defense against SNS phishing attacks,” Expert Systems with Applications , 207, p. 117893.
Evaluating the effectiveness of distributed denial of service attacks
The given research topic is based on evaluating the effectiveness of distributed denial of service attacks on cloud and local environments. Hence, this research can be carried out using a quantitative research method. Cyber attackers find DDoS as one of the most dangerous technological exploitation when it comes to impacting network availability (Krishna Kishore et al., 2023). This research can revolve around scrutinizing the impact of DDoS attacks on the local environment and cloud environment. This can be done by executing DDoS attacks on a simulated environment using hoping or other software(s) to check where it has a higher magnitude (de Neira et al., 2023).
- To set up a server on the local and cloud environment to target using DDoS attacks for checking which had experienced slowness.
- To determine types of DDoS attack types, their magnitude and possible mitigation techniques.
RQ: Why do DDoS attacks have dynamic nature and how is it likely to sternly impact victims?
The experimentation for this research can be executed by creating a server on the local and cloud environment. Hence, this research can be carried out using a quantitative research method. These servers can be set up as web servers using apache 2 service. On the other hand, a Kali Linux machine can be configured with DDoS execution software. Each server can be targeted with DDoS attacks to check its effectiveness (Benlloch-Caballero et al., 2023).
- Benlloch-Caballero, P., Wang, Q. and Alcaraz Calero, J.M. (2023) “Distributed dual-layer autonomous closed loops for self-protection of 5G/6G IOT networks from distributed denial of service attacks,” Computer Networks , 222, p. 109526.
- de Neira, A.B., Kantarci, B. and Nogueira, M. (2023) “Distributed denial of service attack prediction: Challenges, open issues and opportunities,” Computer Networks , 222, p. 109553.
- Krishna Kishore, P., Ramamoorthy, S. and Rajavarman, V.N. (2023) “ARTP: Anomaly-based real time prevention of distributed denial of service attacks on the web using machine learning approach,” International Journal of Intelligent Networks , 4, pp. 38–45.
Recommended Readings
Latest Web Development Research Topics
Top Management Research Topics
Newest AI Research Topics

Research in every field is becoming more and more essential because of constant developments around the world. Similar is the case in the field of networking. This is the reason; students who are preparing to master the field of networking need to keep their knowledge of the current state of the art in the field up to date.
However, choosing the right research topic often becomes a tough task for students to carry out their research effectively. That being the case, this list contains 15 latest research topics in the field of networking. Whether you are a seasoned researcher or just starting, this list can provide you with ample inspiration and guidance to drive your research forward in the dynamic and evolving field of Networking.
Copyright © 2023 CrowJack. All Rights Reserved
Get Instant Help From 5000+ Experts For
101 best computer networking thesis topics.

Writing a thesis in computer networking involves exploring the intricate world of interconnected systems, data transmission, network protocols, security, and emerging technologies. It requires a deep understanding of network infrastructures, protocols, and the ability to analyze complex networking problems critically. Here’s an introductory overview of computer networking thesis writing:
Introduction to Computer Networking Thesis Writing
A computer networking thesis is a scholarly pursuit that delves into the realm of designing, analyzing, and improving network infrastructures, protocols, and technologies. It involves research, experimentation, and innovative thinking to address challenges and contribute new insights to the field of computer networks.
Importance and Purpose of a Computer Networking Thesis
- Advancement of Networking Knowledge: A networking thesis contributes new insights, methodologies, or technological advancements, fostering innovation and improvement in networking practices.
- Critical Analysis and Research Skills: Writing a networking thesis develops critical thinking skills, research acumen, and the ability to analyze and propose solutions to complex networking problems.
- Real-World Applications: Thesis findings may have practical implications in enhancing network performance, security, scalability, or in shaping future networking technologies and standards.
101 Computer Networking Thesis Topics
- Software-Defined Networking (SDN) and its Impact on Network Architecture
- Network Function Virtualization (NFV) in Modern Networks
- Internet of Things (IoT) Security Protocols in Network Environments
- Blockchain Technology for Secure Data Transmission in Networks
- Network Slicing for 5G and Beyond
- Edge Computing and its Influence on Network Performance
- Wireless Sensor Networks for Environmental Monitoring
- Quantum Networking: Challenges and Opportunities
- Network Traffic Analysis using Machine Learning Techniques
- Fog Computing and its Role in Distributed Networks
- Software-Defined Wide Area Networks (SD-WAN) Deployment Strategies
- Next-Generation Network Protocols for Low-Latency Communications
- Network Security in Cloud Environments
- Energy-Efficient Networking Solutions for IoT Devices
- Network Management and Orchestration in Multi-Vendor Environments
- Cognitive Radio Networks for Dynamic Spectrum Access
- Cyber-Physical Systems and their Impact on Network Infrastructures
- Network Congestion Control Mechanisms in High-Speed Networks
- Federated Learning for Privacy-Preserving Networks
- Self-Healing Networks: Autonomic Fault Management
- Mobile Edge Computing and its Role in Mobile Networks
- Internet Traffic Engineering and Quality of Service (QoS)
- Network Function Chaining (NFC) for Service Optimization
- Network Resilience and Reliability in Adverse Conditions
- Software-Defined Radio (SDR) Applications in Networking
- Network Security Threats and Countermeasures
- Dynamic Spectrum Sharing Techniques in Wireless Networks
- Hybrid Cloud Networking Architectures
- Content-Centric Networking (CCN) for Future Internet Architectures
- Network Automation and Intent-Based Networking
- Security Challenges in IoT-Enabled Networks
- Network Slicing for Resource Management in 5G Networks
- Blockchain-Based Identity Management in Networks
- Application of Artificial Intelligence in Network Traffic Analysis
- Federated Cloud Networking Solutions
- Virtual Private Network (VPN) Security Protocols
- Network Performance Monitoring and Optimization Techniques
- 6G Networks: Future Trends and Challenges
- Network Coding for Improved Data Transmission Efficiency
- Network Function Placement and Resource Allocation in Edge Computing
- Network-on-Chip (NoC) Architectures in Multi-Core Processors
- Secure Routing Protocols in Wireless Sensor Networks
- Green Networking: Energy-Efficient Network Infrastructures
- Multi-Access Edge Computing (MEC) for Latency-Sensitive Applications
- Network Slicing for Industrial IoT (IIoT) Applications
- Network Anomaly Detection using Machine Learning Algorithms
- Optical Networking Technologies and Advancements
- Fog-to-Cloud Data Offloading Techniques
- Network Traffic Prediction using Data Analytics
- Network Slicing for Ultra-Reliable Low-Latency Communications (URLLC)
- Network Function Placement in Virtualized Environments
- Trust Management in Wireless Sensor Networks
- Energy-Efficient Routing Protocols in MANETs
- Multi-Tier Network Security Approaches
- Social Networks and their Impact on Network Structures
- Network Functionality Orchestration and Automation
- SDN-Based Network Management and Control
- Network Virtualization in Data Centers
- Network Resilience in Disaster Management Scenarios
- Security Challenges in Edge Computing Environments
- Secure Data Transmission in Vehicular Ad Hoc Networks (VANETs)
- Future Challenges in Network Design and Scalability
- Network Slicing for Mission-Critical Services
- Energy Harvesting Techniques in Wireless Sensor Networks
- Network Traffic Optimization in IoT Environments
- Network Security Policies and Enforcement Mechanisms
- Wireless Power Transfer for IoT Devices in Networks
- Network Infrastructure Design for Smart Cities
- Cognitive Radio Networks for Spectrum Sharing
- Network Management Strategies in Software-Defined Data Centers
- Network Function Virtualization Orchestration (NFVO) Strategies
- Quantum Key Distribution for Secure Communication in Networks
- Network Virtualization and Service Function Chaining (SFC)
- Blockchain-Based Smart Contracts for Network Management
- AI-Driven Predictive Maintenance in Networking
- Network Traffic Engineering in SDN Environments
- Security Aspects of 5G Networks
- Network Security Analysis using Intrusion Detection Systems
- IoT Device Management and Security in Networks
- Network Slicing for Resource Optimization in IoT
- Network Resilience in Cyber-Physical Systems
- Network Traffic Optimization using Edge Intelligence
- Network Convergence Strategies for Future Communication Technologies
- Network Security in Cloud-Based Environments
- Network Virtualization in Edge Computing Infrastructures
- Network Coding for Robust Data Transmission
- Dynamic Spectrum Access Techniques in Cognitive Radio Networks
- Network Function Chaining for Service Optimization in SDN
- IoT Device Authentication and Access Control in Networks
- Resilient Networking Solutions for Critical Infrastructure Protection
- Secure Routing Protocols in Wireless Mesh Networks
- Network Slice Lifecycle Management (NSLM)
- Security Challenges in 6G Networks
- Network Virtualization and Containerization
- Blockchain-Based Decentralized Networks
- AI-Based Threat Detection in Network Security
- Quantum-Secure Communication Protocols in Networks
- Edge Computing Offloading Strategies in IoT Networks
- Network Service Function Placement Optimization
- Privacy-Preserving Techniques in Network Communication
- Network Traffic Management in Next-Generation Networks
These topics cover various aspects of computer networking, including emerging technologies, security challenges, optimization strategies, and future trends, providing a wide array of options for research and exploration.
If you are stuck with your Computer Networking Thesis writing , send your requirement to [email protected] and get instant Computer Networking Thesis Help .
Book Your Assignment
Recent Posts

How To Prepare An Excellent Thesis Defense?
How to restate a thesis – a detailed guide, explanatory thesis: examples and guide for clear writing, how to write 3 types of thesis statements, how to effectively prepare for your thesis defense, popular categories, get assignment help from subject matter experts.
4.7/5 rating | 10,000+ happy students | Great tutors 24/7
ONLINE TO HELP YOU 24X7
OR GET MONEY BACK!
OUT OF 38983 REVIEWS
- How it works

Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Computer Networking Dissertation Topics
Published by Carmen Troy at January 5th, 2023 , Revised On May 16, 2024
A dissertation is an essential aspect of completing your degree program. Whether you are pursuing your master’s or are enrolled in a PhD program, you will not be awarded a degree without successfully submitting a thesis. To ensure that your thesis is submitted successfully without any hindrances, you should first get your topic and dissertation outline approved by your professor. When approving, supervisors focus on a lot of aspects.
However, relevance, recency, and conciseness play a huge role in accepting or rejecting your topic.
As a computer networking student, you have a variety of networking topics to choose from. With the field evolving with each passing day, you must ensure that your thesis covers recent computer networking topics and explores a relevant problem or issue. To help you choose the right topic for your dissertation, here is a list of recent and relevant computer networking dissertation topics.
List Of Trending Ideas For Your Computer Networking Dissertation
- Machine learning for proactive network anomaly detection
- The role of software-defined-networking (SDN) for network performance and security
- Applications and challenges of 6G technologies
- How to ensure fairness and efficiency in Multi-Access Edge Computing (MEC)
- Denial-of-Service (DoS) Attacks in the Age of Distributed Denial-of-Service (DDoS) Attacks
- Applications and rise of Low-Power Wide Area Networks (LPWANs)
- Efficient Resource Allocation and Quality-of-Service (QoS) Management
- Ethical Implications of Artificial Intelligence (AI) in Network Management
- The best ways to use Blockchain for Tamper-Proof Evidence Collection and Storage
- Role of Network Operators in Cloud Gaming
Computer Networking Dissertation Topics For Your Research
Topic 1: an evaluation of the network security during machine to machine communication in iot.
Research Aim: The research aims to evaluate the network security issues associated with M2M communication in IoT.
Objectives:
- To evaluate the factors affecting the network security of IoT devices.
- To determine the methods for increasing data integrity in M2M communication against physical tampering and unauthorised monitoring.
- To evaluate the network security issues associated with M2M communication in IoT and offer suitable recommendations for improvement.
Topic 2: An analysis of the cybersecurity challenges in public clouds and appropriate intrusion detection mechanisms.
Research Aim: The aim of the research is to analyse the cybersecurity challenges in public clouds and the appropriate intrusion detection mechanisms.
Objectives:
- To analyse the types of cybersecurity threats impacting public clouds.
- To determine some of the competent intrusion detection techniques that can be used in cloud computing.
- To investigate the cybersecurity challenges in public clouds and offer mitigating with appropriate intrusion detection techniques.
Topic 3: Investigating the impact of SaaS cloud ERP on the scalability and cost-effectiveness of business.
Research Aim: The research aims to investigate the impact of SaaS cloud ERP on the scalability and cost-effectiveness of business.
- To analyse the benefits of SaaS ERP over traditional ERP.
- To evaluate the characteristics of SaaS architecture in cloud computing and determine its varieties.
- To investigate how SaaS cloud ERP impacts business scalability and cost-effectiveness.
Topic 4: An evaluation of the requirements of cloud repatriation and the challenges associated with it.
Research Aim: The research aims to evaluate the requirements of cloud repatriation in organisations and the associated challenges
- To analyse the key factors of cloud repatriation.
- To determine the challenges associated with cloud repatriation from public clouds.
- To evaluate the need for cloud repatriation in organisations and the associated complexities
Topic 5: An examination of the security mechanisms in decentralised networks and the ways of enhancing system robustness
Research Aim: The research aims to investigate the security mechanisms in decentralised networks and the ways of enhancing system robustness.
- To analyse the concept of decentralised networks and understand their difference from centralised networks.
- To analyse the security mechanisms in decentralised networks to determine how it offers visibility and traceability.
- To investigate the security mechanisms in decentralised networks and how system robustness can be increased for better privacy and security.
Latest Computer Networking Dissertation Topics
Exploring the importance of computer networking in today’s era.
Research Aim: Even though computer networking has been practised for a few years now, its importance has increased immensely over the past two years. A few main reasons include the use of technology by almost every business and the aim to offer customers an easy and convenient shopping experience. The main aim of this research will be to explain the concepts of computer networking, its benefits, and its importance in the current era. The research will also discuss how computer networking has helped businesses and individuals perform their work and benefit from it. The research will then specifically state examples where computer networking has brought positive changes and helped people achieve what they want.
Wireless Networks in Business Settings – An Analysis
Research Aim: Wireless networks are crucial in computer networking. They help build networks seamlessly, and once the networks are set up on a wireless network, it becomes extremely easy for the business to perform its daily activities. This research will investigate all about wireless networks in a business setting. It will first introduce the various wireless networks that can be utilised by a business and will then talk about how these networks help companies build their workflow around them. The study will analyse different wireless networks used by businesses and will conclude how beneficial they are and how they are helping the business.
Understanding Virtual Private Networks – A Deep Analysis of Their Challenges
Research Aim: Private virtual networks (VPN) are extremely common today. These are used by businesses and individuals alike. This research aims to understand how these networks operate and how they help businesses build strong and successful systems and address the challenges of VPNs. A lot of businesses do not adopt virtual private networks due to the challenges that they bring. This research will address these challenges in a way that will help businesses implement VPNs successfully.

A Survey of the Application of Wireless Sensor Networks
Research Aim: Wireless sensor networks are self-configured, infrastructure-less wireless networks to pass data. These networks are now extremely popular amongst businesses because they can solve problems in various application domains and possess the capacity to change the way work is done. This research will investigate where wireless sensor networks are implemented, how they are being used, and how they are performing. The research will also investigate how businesses implement these systems and consider factors when utilising these wireless sensor networks.
Computer Network Security Attacks – Systems and Methods to Respond
Research Aim: With the advent of technology today, computer networks are extremely prone to security attacks. A lot of networks have security systems in place. However, people with nefarious intent find one way to intrude and steal data/information. This research will address major security attacks that have impacted businesses and will aim to address this challenge. Various methods and systems will be highlighted to protect the computer networks. In addition to this, the research will also discuss various methods to respond to attacks and to keep the business network protected.
Preventing a Cyberattack – How Can You Build a Powerful Computer Network?
Research Aim: Cyberattacks are extremely common these days. No matter how powerful your network is, you might be a victim of phishing or hacking. The main aim of this research will be to outline how a powerful computer network can be built. Various methods to build a safe computer network that can keep data and information will be outlined, and the study will also highlight ways to prevent a cyberattack. In addition to this, the research will talk about the steps that should be taken to keep the computer network safe. The research will conclude with the best way and system to build a powerful and safe computer network.
Types of Computer Networks: A Comparison and Analysis
Research Aim: There are different types of computer networks, including LAN, WAN, PAN, MAN, CAN, SAN, etc. This research will discuss all the various types of computer networks to help readers understand how all these networks work. The study will then compare the different types of networks and analyse how each of them is implemented in different settings. The dissertation will also discuss the type of computer networks that businesses should use and how they can use them for their success. The study will then conclude which computer network is the best and how it can benefit when implemented.
Detecting Computer Network Attacks by Signatures and Fast Content Analysis
Research Aim: With technological advancement, today, many computer network attacks can be detected beforehand. While many techniques are utilised for detecting these attacks, the use of signatures and fast content analysis are the most popular ones. This research will explore these techniques in detail and help understand how they can detect a computer network attack and prevent it. The research will present different ways these techniques are utilised to detect an attack and help build powerful and safe computer networks. The research will then conclude how helpful these two techniques are and whether businesses should implement them.
Overview of Wireless Network Technologies and their Role in Healthcare
Research Aim: Wireless network technologies are utilised by several industries. Their uses and benefits have helped businesses resolve many business problems and assisted them in conducting their daily activities without any hindrance. This networking topic will help explore how wireless network technologies work and will talk about their benefits. This research aims to find out how wireless technologies help businesses carry out their daily routine tasks effortlessly. For this research, the focus will be on the healthcare industry. The study will investigate how wireless network technology has helped the healthcare sector and how it has benefited them to perform their daily tasks without much effort.
Setting up a Business Communication System over a Computer Network
Research Aim: Communication is an essential aspect of every business. Employees need to communicate effectively to keep the business going. In the absence of effective communication, businesses suffer a lot as the departments are not synchronised, and the operations are haphazard. This research will explore the different ways through which network technologies help conduct smooth and effective communication within organisations. This research will conclude how wireless networks have helped businesses build effective communication systems within their organisation and how they have benefited from it. It will then conclude how businesses have improved and solved major business problems with the help of these systems.
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find computer networking dissertation topics.
To find computer networking dissertation topics:
- Follow industry news and emerging technologies.
- Investigate unresolved networking challenges.
- Review recent research papers.
- Explore IoT, cybersecurity , and cloud computing.
- Consider real-world applications.
- Select a topic aligned with your expertise and career aspirations.
You May Also Like
Need interesting and manageable construction engineering dissertation topics or thesis? Here are the trending construction engineering dissertation titles so you can choose the most suitable one.
Consumer psychology has always been a well-known yet understudied field in psychology. The psychology of consumption describes how people adopt, use, and eventually dispose of goods, services, or concepts.
Need interesting and manageable Economics dissertation topics? Here are the trending Economics dissertation titles so you can choose the most suitable one.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works

Thesis proposals on computer networking (DISCO)
Below you find open thesis proposals related to the research group DISCO (Distributed Systems and Communications) within Computer Science at Karlstad University.

The list of topics below is outdated and will be removed soon. You find currently open master thesis topics here .
- Application form
Send your application form to [email protected]
- Master Thesis on Network Configuration with TimeCritical Networks AB
- Performance evaluation of container runtimes for real-time application workloads in Kubernetes-based edge infrastructure
- Congestion Control of WebRTC, video streaming over Wireless networks
- Massive Multipathing
- Browser Based Remote Control of Raspberry Pi enabled RC Car
- HTTP3 in cluster networking (Red Hat)
- Multipath Packet Scheduling for 5G Systems
- The Great Journey - computer game studio
- Enhanced radio scheduling for eXtended Reality (XR) applications in 5G and beyond-5G networks (Ericsson)
- Integrating cBPF into eBPF for packet matching (Red Hat)
- Implementing a BPF NAT gateway (Red Hat)
- Thesis proposal by Tieto Evry
- Thesis in the area of Transport Protocols for 5G Networks
- Machine Learning for Renewable Energy Management (Glava Energy Center)
- Programmable Packet Scheduling in P4 (Ericsson)
- Software Defined Networking Configuration Automation for TSN (Ericsson)
- Thingsboard, Uddeholm
- GOOSE and Smart Grid Control Signaling over 5G
- CloudMAC on P4 Steroids
- Statefull Layer 4 Load balancing with P4
- Programmable Congestion Control with P4
- Master's thesis within a research project
- Optimized Rescheduling of Cloud-Native Network Functions in Telecom Cloud
- 5G & Machine-to-Machine Communication
- A study on scaling and load balancing for 5G core network using Kubernetes
- Design and implementation of auto-scaling solution for 5G user plane functions
| |
Welcome to the on-line version of the UNC dissertation proposal collection. The purpose of this collection is to provide examples of proposals for those of you who are thinking of writing a proposal of your own. I hope that this on-line collection proves to be more difficult to misplace than the physical collection that periodically disappears. If you are preparing to write a proposal you should make a point of reading the excellent document The Path to the Ph.D., written by James Coggins. It includes advice about selecting a topic, preparing a proposal, taking your oral exam and finishing your dissertation. It also includes accounts by many people about the process that each of them went through to find a thesis topic. Adding to the Collection This collection of proposals becomes more useful with each new proposal that is added. If you have an accepted proposal, please help by including it in this collection. You may notice that the bulk of the proposals currently in this collection are in the area of computer graphics. This is an artifact of me knowing more computer graphics folks to pester for their proposals. Add your non-graphics proposal to the collection and help remedy this imbalance! There are only two requirements for a UNC proposal to be added to this collection. The first requirement is that your proposal must be completely approved by your committee. If we adhere to this, then each proposal in the collection serves as an example of a document that five faculty members have signed off on. The second requirement is that you supply, as best you can, exactly the document that your committee approved. While reading over my own proposal I winced at a few of the things that I had written. I resisted the temptation to change the document, however, because this collection should truely reflect what an accepted thesis proposal looks like. Note that there is no requirement that the author has finished his/her Ph.D. Several of the proposals in the collection were written by people who, as of this writing, are still working on their dissertation. This is fine! I encourage people to submit their proposals in any form they wish. Perhaps the most useful forms at the present are Postscript and HTML, but this may not always be so. Greg Coombe has generously provided LaTeX thesis style files , which, he says, conform to the 2004-2005 stlye requirements.
Many thanks to everyone who contributed to this collection!
Greg Coombe, "Incremental Construction of Surface Light Fields" in PDF . Karl Hillesland, "Image-Based Modelling Using Nonlinear Function Fitting on a Stream Architecture" in PDF . Martin Isenburg, "Compressing, Streaming, and Processing of Large Polygon Meshes" in PDF . Ajith Mascarenhas, "A Topological Framework for Visualizing Time-varying Volumetric Datasets" in PDF . Josh Steinhurst, "Practical Photon Mapping in Hardware" in PDF . Ronald Azuma, "Predictive Tracking for Head-Mounted Displays," in Postscript Mike Bajura, "Virtual Reality Meets Computer Vision," in Postscript David Ellsworth, "Polygon Rendering for Interactive Scientific Visualization on Multicomputers," in Postscript Richard Holloway, "A Systems-Engineering Study of the Registration Errors in a Virtual-Environment System for Cranio-Facial Surgery Planning," in Postscript Victoria Interrante, "Uses of Shading Techniques, Artistic Devices and Interaction to Improve the Visual Understanding of Multiple Interpenetrating Volume Data Sets," in Postscript Mark Mine, "Modeling From Within: A Proposal for the Investigation of Modeling Within the Immersive Environment" in Postscript Steve Molnar, "High-Speed Rendering using Scan-Line Image Composition," in Postscript Carl Mueller, " High-Performance Rendering via the Sort-First Architecture ," in Postscript Ulrich Neumann, "Direct Volume Rendering on Multicomputers," in Postscript Marc Olano, "Programmability in an Interactive Graphics Pipeline," in Postscript Krish Ponamgi, "Collision Detection for Interactive Environments and Simulations," in Postscript Russell Taylor, "Nanomanipulator Proposal," in Postscript Greg Turk, " Generating Textures on Arbitrary Surfaces ," in HTML and Postscript Terry Yoo, " Statistical Control of Nonlinear Diffusion ," in Postscript
| | |
M.Tech/Ph.D Thesis Help in Chandigarh | Thesis Guidance in Chandigarh

+91-9465330425

Thesis and Research Topics in Computer Networking
Students who find programming complex and challenging mostly go for networking field in computer science engineering. But even after indulging in this field they are often confused about which topic to choose for the project or for an M.Tech thesis. Here is the list of some of the good topics in computer networking with a basic introduction which you can choose for your project or thesis. You can also get thesis help and thesis guidance on these topics from experts. In the infographic below you will find the list of latest thesis and research topics in computer networking .
List of the best thesis topics in networking:
Wireless Sensor Networks
Wireless Ad hoc Network
Vehicular Ad hoc Networks
Network Security
- Evaluate and implement energy efficient protocol for data aggregation in wireless sensor networks
- Node Localization Approach in underwater acoustic network using bio-inspired method
- Evaluate and implement sink hole attack isolation method in wireless sensor networks
- The three level hierarchical routing protocol for data aggregation in wireless sensor networks
- Design and implement black hole attack isolation method in wireless sensor networks
- The clock synchronization method in wireless sensor network for the efficient data transmission method
- The efficient channel sensing scheme for wireless body area network
- Design secure scheme for data transmission in opportunistic routing in wireless sensor networks
- The misdirection attack isolation scheme in multilevel hierarchical routing protocol in WSN
- To propose fault tolerance scheme for wireless sensor networks
- To propose novel approach to maintain quality of service in the network for link failure
- To propose hybrid routing protocol based on the bio-inspired methods in mobile ad hoc network
- The threshold based mechanism for the isolation of worm hole attack in mobile ad hoc networks
- Evaluate and implement clustering based method for the isolation of black hole attack in mobile ad hoc network
- The novel method for the congestion avoidance in mobile ad hoc network to maintain quality of service in the network ‘
- The multicasting scheme for the path establishment in mobile ad hoc networks
- Implement and evaluate Sybil attack isolation scheme for vehicular ad hoc networks ‘
- To propose novel scheme for the detection of DDOS attack in vehicular ad hoc networks
- The zonal based routing scheme for path establishment in vehicular ad hoc networks
- The secure and efficient message authentication scheme for vehicular ad hoc networks
- The location based routing scheme for path establishment in vehicular ad hoc networks
- The tree based multicasting scheme in vehicular ad hoc network for data transmission
TCP/IP Protocol
Now our systems computer, laptop, mobiles, and other internet devices are connected to one node to communicate with each other and to get internet access, and this whole process called a network system. They all are connected with the physical medium so that’s why they can be guided as wireless network system or copper wire network system to provide calculated data speed in the notes time frame. It spreads motions as electromagnetic waves or light pulses. The direct connection between two nodes are considered as guided medium and is more reliable and the occurrence of error has very less as compared to another medium. Un-guided medium is used in so many systems to provide multiple outputs at the same time. But in this system error rate is high.
To send or receive the internet signal, the two nodes follow a set of protocol which is known as IP (internet protocol). Each system is designed to follow this set of rules itself to generate maximum speed with a time limit. These protocols are designed in a manner that they follow these rules one by one. Each layer follows the protocol of the upper layer to provide services and then that layer follows the upper layer, this process will continue until data is transmitted or received. Lower layer always follows the basic set of rules and upper layer follows the advanced set of rules. Service provided by both layer will be different in terms of protocol instructions.
First data is sent or received in the application layer and then in the transport layer, after following the set of rules data then is sent to network layer to link layer and after that data has been sent to physical layer to the user. Data is divided into small packet format to provide consistency. Common internet protocol is RTP (Real-time Transport Protocol). which is used to provide information at the time of gaming, movie or music streaming. first two-layer are used to transmit or receive the information in small data packets.
Two main internet protocols are UDP (user datagram protocol) and TCP (transport control protocol). UDP and TCP both have their advantages and disadvantages of use. UDP is used because of their simplicity and with the use of UDP data can be sent immediately. But at the same time, it is unreliable as compared to TCP. TCP, then again, directs the sending rate concerning the client’s ability – stream control – and with respect to the limit of the system – clog control. It conveys the information altogether and guarantees that all information achieve the beneficiary. The hidden layers, similar to the system layer, are not required to perform solid conveyance.
TCP(Transmission Control Protocol) is a set of rules to access the Internet with the interconnection of various Internet-based devices. We can say it is a communication protocol in which there is a host with access to the Internet. This is a good topic for an M.Tech thesis in networking. If you are planning to choose this networking topic for research, then here is some basic introduction to this.
TCP/IP provides end to end data transmission between devices along with some other functionalities like addressing, mapping and acknowledgment. TCP/IP is a combination of two protocols. TCP controls the messages by dividing them into packets. IP controls the transmission of these packets from the sender to the receiver.
TCP/IP protocol layers
Following are the four layers of TCP/IP:
Application layer
Transport layer
Internet layer
Physical layer
Working of TCP/IP protocol
Client/Server model is used as a mode of communication by TCP/IP. It works in the following way:
Application layer consists of various applications for data exchange with use of protocols like HTTP(Hypertext Transfer Protocol), FTP(File Transfer Protocol), SMTP(Simple Mail Transfer Protocol)
The transport layer provides end-to-end communication between the host and the user. It uses protocol UDP(User Datagram Protocol).
Internet layer is responsible for the transfer of packets over the network and uses IP(Internet Protocol) for this purpose.
The physical layer provides interconnection between the nodes.
Advantages of TCP/IP protocol
It can be easily modified.
It is compatible with all the operating systems.
It is scalable in determining the most appropriate path.
Thus it is a good topic for M.Tech thesis as well as for research. A student can get thesis help on this topic from experts specialized in thesis guidance. You can also explore the Internet for further details on this topic.
Network Simulation Tools
Here is the list of commonly used network simulators having different features:
Another good computer networking topic for an M.Tech thesis is NS2 . NS stands for Network Simulator. It is an open-source, discrete-event based network simulator mainly used for research purpose and for teaching. It provides help in simulating routing protocols like IP, TCP, UDP, etc. It creates a simulation environment for studying the network. Following steps are followed while creating a simulation environment:
Topology Definition
Development of the model
The configuration of the link
Analysis of the problem
Visualization
NS2 create network topologies and then examines the behavior of the network under any event. The behavior is analyzed by tracing down the events. NS2 provides text-based as well as animation-based simulations.
Advantages of NS2
It has the ability to support multiple protocols.
It can represent network traffic graphically.
It can also support multiple algorithms for routing and queuing.
NS2 is a very good topic for an M.Tech thesis in the computer networking field. You will not only get theoretical knowledge but also practical experience of network simulator tool. You can get thesis guidance about NS2 from an expert who has practical knowledge about how to use this tool.
MANET stands for mobile ad hoc Network and is another good choice for an M.Tech thesis topic in networking. In MANET, the nodes are self-configurable and have the ability to move freely in any direction and can link with other devices frequently. MANET was originally used as a military project in defense. MANET have the challenges of weak signal strength, reliability, power consumption along with some other problems.
Characteristics of MANET
Each node is independent in nature i.e. each node act as the host as well as the router.
It is based on the distributed nature of operation for security and configuration.
The network is dynamic in nature i.e each node can join and exit the network at any time.
The nodes in the network are associated with less memory and power.
In MANET, the bandwidth remains fluctuating.
MANET creates a symmetric environment such that all the nodes have identical features like responsibilities and capabilities.
Hurdles in the path of MANET
There are certain hurdles in the path of MANET, which it has to overcome. Some of these are:
The reliability of the transmission is affected by certain factors like data loss, interference, and blockage.
The rate of transmission is limited to a certain range thus there is a reduced data rate.
Packet loss can occur while transmission of data.
Frequent path breaks.
Lack of firewall results in security issues in the network.
This was just the introduction to MANET to give an overview of what it is if you are going with this topic for your M.Tech thesis.
Network Security is the set of rules to ensure the safety of the network of an organization or personal network. You can choose this topic for your M.Tech thesis if you have a complete understanding of how the data is transferred over the network. Network Security also include security of physical hardware devices. Network Security in software means providing authorized access to the network by means of ids and passwords.
Whenever a user tries to access the network, his authenticity is checked by means of ids and passwords. This is done to prevent any malicious user from entering the network by the motive of hacking it.
Types of attacks to network
Active Attack – In this type of attack, a hacker tries to make changes to data while it is being sent from one node to another.
Passive Attack – In this type of attack, an outsider monitors system of the organization consistently to find vulnerable ports.
Network Security Tools
Following are some of the tools employed in network security:
Thus if you really have significant knowledge(practical + theoretical) of networking tools, security
measures then you should choose this topic for M.Tech thesis. Besides, you will get thesis help as well as guidance on this topic from computer networking experts.
Network Topologies
Network Topology is the arrangement of nodes in the network both physical and logical. It is an easy topic for M.Tech thesis. Following are some of the common physical topologies:
Bus – In the bus topology, each node is connected to the main cable known as bus such that every node is directly connected to every other node.
Star – In the star topology, each node is connected to a central hub such that all the nodes are indirectly connected to each other.
Ring – In this topology, the nodes form a closed loop such that the adjacent nodes are in direct connection with each other.
Token Ring – In the token ring topology, a protocol is used. A token is passed from one node to another. A node that wants to transfer data should acquire the token.
Mesh – In the mesh network, each node is directly connected to every other node. It can be a full mesh or partial mesh network.
Tree – It is the interconnection of bus topology and star topology.
Daisy Chain – In this topology, each node is connected to two other nodes but do not form a closed loop like ring topology.
Hybrid – It is a combination of two or more topologies.
If you are afraid of complex topics in networking for M.Tech thesis, then this topic is for. It is relatively simple to understand and work on. Just go for it.
It is another major topic in computer networking and also a good choice for a thesis or project. Ipv4 is the fourth version of Internet protocol while Ipv6 is the sixth version of Internet protocol.
Characteristics of IPv4
It uses a 32-bit address.
The address is written in decimal separated by dots.
The header includes a checksum.
Broadcast addresses are used to send data packets to other nodes.
In this the Internet Protocol Security is optional.
Characteristics of Ipv6
It uses a 128-bit address.
The address is written in hexadecimal separated by colons.
The header does not include a checksum.
Broadcast addresses are not used to send data packets.
The Internet Security Protocol is compulsory.
It is a good area to study how data transfer takes place over the internet. You will study the IP data packets of Ipv4 and Ipv6. You can select this as your M.Tech thesis topic.
OSI stands for open system interconnection. It is another good topic for an M.Tech thesis in the computer networking field. It provides a networking framework to implement protocols in layers. There are seven layers of OSI Model:
Physical Layer – This layer is responsible for transferring digital data from the source to the destination.
Data Link Layer – This layer checks error in data along with the MAC address. It turns bits into data frames.
Network Layer – This layer checks whether the data has reached the destination or not by examining the source and the destination address.
Transport Layer – This layer transfers data over the network by using the TCP protocol.
Session Layer – This layer manages the events and keeps them in sequence. It supports multiple types of connections.
Presentation Layer – It looks after the syntax along with encryption and decryption for the application layer above it.
Application Layer – It provides end-to-end user applications using protocols like HTTP, FTP, SMTP.
It is different from the TCP/IP model. You will get a thesis guide on this topic from computer networking experts.
However, with the change of social economy, computer networking system changes a lot and have also changed people’s lifestyle in a lot of aspects. As we know with the increasing demand for network speed, a number of network provider has been also increased. Due to the maximum number of the provider, one can easily access the high speed of the internet at a low cost. Local area network which is used in lots more other sectors like medical, military, education and science. Now we can see every-one need their own personal LAN (Local Area Network). Now LAN is not only for big enterprises but it is also available for small schools and families which are looking for high speed of data in the minimum amount.
The current speed of LAN is not enough for a user so that’s why companies are doing more research and study to provide the data at higher speed without the use of high bandwidth. But as we know if we want higher speed in a short time with a wide area, bandwidth will be increased to 30% to 300%. Now one of the very well known company called Huawei launched its 5G network, which is faster than the USA 5G network. So with this network Bandwidth also increased by 300%. It is beneficial for us but at the same time, a higher bandwidth is also not good for human life.
Various exploratory and early business LAN innovations were created during the 1970s. But then a new term called WLAN is introduced to the world in 1997 to provide a wireless network. This technology got famous in a very short span of time with the name of WiFi (Wireless Fidelity).
It stands for Wireless Local Area Network. It can be another good choice for an M.Tech thesis topic in computer networking. It is a wireless distribution method that uses high-frequency radio waves with a single access point to the Internet. In other words, it is wireless communication between two or more devices such that users can move around in a limited range area. It is most commonly used in homes or offices. The component connected to WLAN is referred to as the station. There are two types of stations – Access Point, Client.
Access Points are the base stations that transmit and receive radio frequencies for wireless-enabled devices. Clients are mobile phones, laptops, desktops connected to the wireless network.
Modes of Operation of WLAN
There are two modes of operation of WLAN:
Infrastructure – In infrastructure mode, base station act as the access point and all the nodes communicate through this point.
Ad hoc – In Ad hoc mode, mobile devices transmit data directly using peer to peer method. In this, there is no base station.
WLAN Advantages
It can support a large number of devices.
It is easy to set up wireless LAN than installing cables for the wired network.
It is easier to access a wireless network than a wired network.
WLAN Disadvantages
It is difficult to expand the network.
It faces security issues like hacking.
Interference is another problem with WLAN.
WLAN is another easier topic for an M.Tech thesis. It is used everywhere. You can take thesis help on this topic from networking professionals.
Cryptography
It is the science of maintaining the privacy of data. It is also an easy topic to choose for your M.Tech thesis in networking. There are three main objectives of cryptography used in transferring data over the network:
Confidentiality
Authentication

Cryptography employs two techniques for maintaining the privacy of data:
Encryption – In encryption, the plain text is converted into some other form known as ciphertext.
Decryption – In this technique, the converted text i.e the ciphertext is translated back to the original text.
There are two algorithms for cryptography. In a symmetric key, both the sender and the receiver share the same key for encryption and decryption.
In an asymmetric key, both the users have different keys respectively for encryption and decryption.
This is a familiar topic and very easy to understand. Take the guidance of a thesis expert about this area to start with this topic.
IEEE stands for Institute of Electrical and Electronics Engineers. IEEE 802 is a very challenging and a very good topic for your thesis. IEEE 802 comes under IEEE and deal with LAN(Local Area Network) and MAN(Metropolitan Area Network). It specifies certain services and protocols for the data link layer and physical layer of the OSI model. IEEE is further subdivided into 22 parts that cover a wide range of services.
IEEE 802 subdivides data link layer into two layers namely: Logical Link Layer(LLC)
Media Access Control(MAC)
You can choose any of its subfields as a part of your project or thesis. It is a very good area to explore.
These were some of the few topics for an M.Tech thesis in computer networking. You can also choose any one of these for research in networking or for your project. You can explore more on these topics.
If you need help with thesis topics in computer networking, you can contact us . You can call us on this number +91-9465330425 or email us at [email protected] for M.Tech and Ph.D. thesis help in computer networking. You can also fill the query form on the website.
For more details Contact Us. You can call us on this number +91-9465330425 or drop an email at [email protected] for any type of dissertation help in India. You can also fill the query form on the website.
You can also visit our website Techsparks and follow us on Pinterest , Facebook , Twitter, YouTube and Linkedin for latest thesis blog.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Quick Enquiry
Get a quote, share your details to get free.

Click here to place an order for topic brief service to get instant approval from your professor.
Best 59 Networking Dissertation Topics Ideas & Examples
Table of Contents
The Most Conclusive Networking Dissertation Topics That Will Help Students in writing their Final Year Dissertations
In recent years, Networking has grown by leaps and bounds.
Networking is a complicated term. It has evolved over the years after the advent of the computer. In information technology, networking is the construction, design, and use of a network, including the physical (cabling, hub, bridge, switch, router, and so on), the selection and use of telecommunication protocol and computer software for using and managing the network, and the establishment of operation policies and procedures related to the network. The basic purpose of networking is the sharing of information and is based on a reliable and fast communication network.
Importance of Networking
Inevitably, networking has taken the center stage in the world. The different kinds of networking systems i.e. local area networking , working in a particular locality within a radius of a few kilometers; metropolitan area networking , working in a large city; and wide area networking , covering thousands of kilometers in the radius are in place. No one can live without it, for everything is now interconnected and dependent on one another. Hence any failure in communication can lead to a massive disorder.
Networking Dissertation Topics Ideas
This importance of networking gives a good prospect to any student who specializes in networking . Networking dissertation then becomes inevitable for them. However, there starts the confusion as to which topic should be selected. Nonetheless, in the topic selection for the dissertation, students must prefer the current requirement of networking. They may take general topics as well as social networking dissertation topics .
This not only helps them to create their interest in the dissertation but also helps the world community to protect vulnerable networking issues. Some of the important and appealing/interesting networking dissertation topics are listed below.
- The impact of 5G technology on mobile networks
- The use of software-defined networking in data centers
- The security of IoT networks
- The use of network virtualization in cloud computing
- The impact of edge computing on network architecture
- The use of network function virtualization in telecommunications
- The security of industrial control systems networks
- The use of network slicing in 5G networks
- The impact of artificial intelligence on network management
- The use of network-as-a-service in cloud computing
- The security of wireless networks
- The use of network coding in wireless networks
- The impact of network traffic on network performance
- The use of network-on-chip in embedded systems
- The security of software-defined networks
- The use of network function chaining in 5G networks
- The impact of blockchain technology on network security
- The use of network orchestration in 5G networks
- The security of mesh networks
- The use of network-attached storage in cloud computing
- The impact of quantum computing on network security
- The use of network-as-a-platform in cloud computing
- The security of mobile ad-hoc networks
- The use of network-on-demand in cloud computing
- The impact of AI-based network optimization and automation on network performance.
- The importance of networking in the current era
- The history of the wireless networks
- The future prospect of the wireless networks
- How has networking become inevitable in present times?
- Analyzing the rapid increase in the market for the wireless networking
- Comparing wireless and wire-based networks – which one is more important
- Giving an overview of the terms, technology, and legal issues in the wireless networking
- How is networking important in an institution
- An overall categorization of networking systems
- The different aspects of networking: pros and cons
- The newly arising security issues in the networking
- The new technical aspects which allow people to communicate with machines
- The inflow of different social networks
- How to improve the security of networks i.e. protection of intellectual property rights etc
- Design a secure scheme for data transmission in opportunistic routing in wireless sensor networks
- The novel method for congestion avoidance in mobile ad hoc networks to maintain quality of service in the network ‘
- Comparing three wireless networking types i.e. LAN, WAN, and MAN
- The importance of wireless networks in mobile communications
- The fundamental working of broadband and Bluetooth technologies
- The world economy and the input of networking
- The importance of networking in the internet industry
- How are the security issues affecting the banking industry?
- Networking – indispensable for the marketing
- The growth of media and the networking
- Online competitions
- The new conferencing trends i.e. video conferencing
- The different concepts of network management
Other related posts
- IT Dissertation Topics
- Computer science dissertation topics
- Information systems dissertation topics
Custom Topics Brief Service from experts
These are the best networking dissertation topics if you are still searching for some unique dissertation topics on networking fill out the form below and get we customize dissertation topic brief service from our experts.
WhatsApp and Get 35% off promo code now!
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Download Free PDF
Campus Network Design proposal

Related papers
The need for a reliable communication network within a university campus is not a luxury; it is a necessity. Currently, no such network exists at the Federal University of Technology Owerri (FUTO) in Nigeria. This project addresses the situation by using a top-down approach to design a campus network of adequate network performance to support bandwidth-intensive applications such as teleconferencing. The campus network design, carried out after analysis of the user and technical network requirements, was partitioned into logical and physical domains. Network simulation was carried out with the aid of the Cisco Packet Tracer 5.3 software. SIP-based client software, FUTO Messenger, was developed to run on the network. The software supports text, voice and video chats. A prototype network system was implemented to test the network design and also to verify the functionality of the developed software. The system had 6 workstations comprising 2 teleconferencing PCs, 2 non-teleconferencin...
This research work will provide the needs for the Faculty of Natural & and Applied Sciences of Umaru Musa Yar'adua University Katsina Nigeria (FNAS-UMYUK) departments to communicate among themselves, in order to share and search on vital and useful information's which will enhance and promote research and learning. This work is strictly based on the movement of data in the seven layers of the Open System Interconnection (OSI) Model and IPv4 is the protocol used in this work. The design variation are based on primarily layer 2 and layer 3 to the access switches with different variations of design which Spaning Tree Protocol (STP) design used for loop avoidance, Virtual Trucking Protocol (VTP) design used for trucking protocol, RIP for routing protocol and server farm design for resource services. The configuration processes of the various design models are based on the packet tracer simulator, and the simulation is conducted and we obtained the result that we are expected for...
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Networking Thesis Proposal
Networking is an often-emerging domain which encompasses extensive areas that are probably relevant for carrying out significant research. The team at phdprojects.org effectively conducts thesis proposals in all networking areas. All work is initiated from the beginning to ensure zero plagiarism.
On the subject of network thesis, we discuss multiple research areas that are supported with certain issues and key objective of research:
- Network Security
- Issue: In opposition to network framework, the expansive growth of cyber-attacks is the main concern of network security.
- Research Focus: To detect innovative attack vectors in actual time, use machine learning techniques that enhance the modernized intrusion detection systems.
- Software-Defined Networking (SDN) and Network Functions Virtualization (NFV)
- Issue: Considering the rapidly evolving demands of contemporary data centers and cloud services, the conventional architecture finds it hard to address.
- Research Focus: For resource distribution, it highlights the development of algorithms to develop more portable, programmable and adaptable network frameworks by investigating the synthesization of SDN (Software-Defined Networking) and NFV (Network Functions Virtualization).
- Internet of Things (IoT) Connectivity and Management
- Issue: Regarding the huge amount of IoT devices, it is difficult to assure trustworthy and secure connections.
- Research Focus: Assist device management in IoT ecosystems, data storage and effective communication through creating adaptable network protocols and models.
- 5G Networks and Beyond
- Issue: 5G applications like mMTC (massive Machine-Type Communications), eMBB (enhanced mobile broadband) and URLLC (Ultra-Reliable and Low-Latency Communications) are highly challenging to address the multiple demands.
- Research Focus: To improve the potential, coverage and capability of 5G networks like edge computing synthesization, network slicing and enhanced antenna systems, conduct an extensive research on new applications and protocols.
- Wireless Mesh Networks
- Issue: In adverse environmental conditions like rural sectors or disaster recovery events, it is difficult to offer productive and extensible wireless community.
- Research Focus: Based on evolving circumstances and requirements, model and assess self-forming and automatic healing wireless mesh networks.
- Quantum Networking
- Issue: Specifically on the basis of security, it suppresses the constraints of traditional networking by utilizing quantum technologies.
- Research Focus: Considering the ultra-secure communication networks, analyze the advancement of QKD (Quantum Key Distribution).In addition to that, it mainly focuses on exploration of synthesizing quantum with conventional networks.
- Energy-Efficient Networking
- Issue: It promotes more operational expenses and ecological implications due to the extensive usage of energy in network systems.
- Research Focus: For the purpose of modeling and handling energy-efficient networking protocols and hardware components, this study seeks to implement novel techniques. In data centers or wireless networks, decrease energy usage by incorporating efficient tactics.
- Network Virtualization
- Issue: To assist various technologies and services, it is challenging to handle and produce virtual network services.
- Research Focus: This research aims to enhance performance, portability and dependability by exploring developed methods for establishing the virtual network.
- Blockchain for Network Security and Management
- Issue: The key concern in networking operations and transactions to assure reliability and clarity.
- Research Focus: For secure network management techniques such as access control and decentralized identity management, design blockchain-oriented findings.
- Next-Generation Internet Protocols
- Issue: In accordance with problems involving performance, security and scalability, the current IP (Internet Protocol) finds it difficult to adopt.
- Research Focus: Include probable novel resolving tactics, security algorithms and routing methods in developing and estimating the future generation protocols which solves these kinds of issues.
What are some PhD research areas in IoT as well as the tools needed for the research?
For performing a PhD study in the IoT (Internet of Things) field, you should crucially examine the topic’s relevance and its impacts on the real-time environment. Among IoT sector, some of the hopeful and deserving research areas are provided here which is accompanied with deployed tools in that particular areas:
- IoT Security and Privacy
- Research Aim: As opposed to cyber-attacks and data vulnerabilities, secure IoT devices and networks by creating effective security systems and privacy-preserving algorithms.
- Required Tools: Programming languages like Rust for system-level programming,
Python and C, IoT simulation tools such as OMNeT++ and Cooja for Contiki OS, cryptographic libraries for instance OpenSSL and Security analysis tools like Wireshark and Nessus are the essential tools involved in this study.
- Edge Computing and IoT
- Research Aim: In IoT technologies, assisting real-time decision making decreases response time and enhances capability through developing data processes at the edge of the network.
- Required Tools: This project primarily needs network simulation tools such as Mininet and NS-3, programming languages like Python and Go, edge computing programs such as AWS Greengrass, Azure IoT Edge and containerization tools as an example kubernetes, docker.
- IoT and Machine Learning
- Research Aim: To derive information from huge amounts of IoT- produced data which access intelligent automation, outlier identification and predictive maintenance, deploy machine learning techniques.
- Required Tools: As regards data collection process in this research, it uses IoT platforms like MQTT and Apache Kafka, Machine learning libraries such as TensorFlow, PyTorch and data processing models like Apache Spark and Hadoop.
- IoT in Healthcare
- Research Aim: For clinical information systems, patient care and health monitoring systems, this study intends to enhance results and availability by designing IoT-based findings.
- Required Tools: To assure data protection, it demands security and compliance tools like HIPAA compliance checkers, health data analysis tools such as R, Python with pandas, NumPy and wearable device development kits.
- Energy-Efficient IoT
- Research Aim: Assist constant implementation in a broad scope and extend the battery life in IoT devices by modeling energy-efficient protocols and systems.
- Required Tools: This project includes energy modeling tools like Matlab and Simulink, network simulators such as NS-3 with IoT extensions, OMNeT++ and for device firmware; it requires programming languages like C and Rust.
- IoT and Blockchain
- Research Aim: Considering the secure and decentralized technologies like smart contracts and supply chain management, this study intends to investigate the synthesization of blockchain technology with IoT.
- Required Tools: It incorporates efficient tools like distributed ledger technologies, blockchain platforms such as Ethereum and Hyperledger Fabric, IoT environments like ThingSpeak, IBM Watson IoT and smart contract development languages, for eg) solidity.
- IoT Standards and Protocols
- Research Aim: In order to assure integrity, adaptability and compatibility in IoT networks, formulate and improve the communication protocols and measures.
- Required Tools: Programming environments for IoT protocols like Contiki OS and RIOT OS, network simulation and testing tools such as Cooja, GNS3 and Protocol analysers like Wireshark, Tcpdump are the involved tools.
- IoT in Smart Cities
- Research Aim: To enhance urban lifestyle scenarios, model efficient IoT findings for city issues involving energy efficiency, traffic management and waste management.
- Required Tools: Data visualization tools such as Tableau and Power BI, urban simulation models like UrbanSim and CitySim, GIS software such as ArcGIS and QGIS and IoT development platforms like Arduino and Raspberry Pi are the encompassed tools in this study.
- Human-Computer Interaction (HCI) in IoT
- Research Aim: Improve user control and approachability in IoT devices and systems through developing smart and user-friendly interfaces.
- Required Tools: It requires programming languages for app creation like Kotlin for Android and Swift for IOS, voice interface development kits such as Amazon Alexa Skills Kit, prototyping tools like Figma, Invision and UI/UX design software such as Adobe XD and sketch.
- IoT for Environmental Monitoring
- Research Aim: For observing the ecological metrics like wildlife behavior, water quality and air quality as well as assist maintenance and propose ecological conservation measures by making use of IoT modern applications.
- Required Tools: In this research, the tools involved such as IoT platforms for data aggregation like LoRaWAN and Sigfox, environmental sensor kits, data analytics and visualization tools such as Python and R.
Networking Thesis Proposal Topics & Ideas
Read some of the interesting Networking Thesis Proposal Topics & Ideas we have listed below, if you are in desperate need of experts help for your paper writing then phdprojects.org will be your best partner.
- A QoS multicast routing protocol for clustering mobile ad hoc networks
- Worm spreading model on two-dimensional ad hoc communication networks
- An address autoconfiguration protocol for IPv6 hosts in a mobile ad hoc network
- Detecting unauthorized and compromised nodes in mobile ad hoc networks
- On the Delay of Reactive-Greedy-Reactive Routing in Unmanned Aeronautical Ad-hoc Networks
- FORK: A novel two-pronged strategy for an agent-based intrusion detection scheme in ad-hoc networks
- Network nodes play a game – a routing alternative in multihop ad-hoc environments
- Dual decomposition method for optimal and fair congestion control in Ad Hoc networks: Algorithm, implementation and evaluation
- A better approximation for constructing virtual backbone in 3D wireless ad-hoc networks
- Two-terminal reliability of a mobile ad hoc network under the asymptotic spatial distribution of the random waypoint model
- On-siteDriverID: A secure authentication scheme based on Spanish eID cards for vehicular ad hoc networks
- Performance evaluation of an anonymity providing protocol for wireless ad hoc networks
- A three round authenticated group key agreement protocol for ad hoc networks
- Delay Prediction in Mobile Ad Hoc Network using Artificial Neural Network
- Connectivity management in mobile ad hoc networks using particle swarm optimization
- Improvised dynamic network connectivity model for Vehicular Ad-Hoc Networks (VANETs)
- Location-aided routing with uncertainty in mobile ad hoc networks: A stochastic semidefinite programming approach
- A virtual subnet scheme on clustering algorithms for mobile ad hoc networks
- Cache invalidation strategies for Internet-based vehicular ad hoc networks
- PHD Guidance
- PHD PROJECTS UK
- PHD ASSISTANCE IN BANGALORE
- PHD Assistance
- PHD In 3 Months
- PHD Dissertation Help
- PHD IN JAVA PROGRAMMING
- PHD PROJECTS IN MATLAB
- PHD PROJECTS IN RTOOL
- PHD PROJECTS IN WEKA
- PhD projects in computer networking
- COMPUTER SCIENCE THESIS TOPICS FOR UNDERGRADUATES
- PHD PROJECTS AUSTRALIA
- PHD COMPANY
- PhD THESIS STRUCTURE
- PHD GUIDANCE HELP
- PHD PROJECTS IN HADOOP
- PHD PROJECTS IN OPENCV
- PHD PROJECTS IN SCILAB
- PHD PROJECTS IN WORDNET
- NETWORKING PROJECTS FOR PHD
- THESIS TOPICS FOR COMPUTER SCIENCE STUDENTS
- IEEE JOURNALS IN COMPUTER SCIENCE
- OPEN ACCESS JOURNALS IN COMPUTER SCIENCE
- SCIENCE CITATION INDEX COMPUTER SCIENCE JOURNALS
- SPRINGER JOURNALS IN COMPUTER SCIENCE
- ELSEVIER JOURNALS IN COMPUTER SCIENCE
- ACM JOURNALS IN COMPUTER SCIENCE
- INTERNATIONAL JOURNALS FOR COMPUTER SCIENCE AND ENGINEERING
- COMPUTER SCIENCE JOURNALS WITHOUT PUBLICATION FEE
- SCIENCE CITATION INDEX EXPANDED JOURNALS LIST
- THOMSON REUTERS INDEXED JOURNALS
- DOAJ COMPUTER SCIENCE JOURNALS
- SCOPUS INDEXED COMPUTER SCIENCE JOURNALS
- SCI INDEXED COMPUTER SCIENCE JOURNALS
- SPRINGER JOURNALS IN COMPUTER SCIENCE AND TECHNOLOGY
- ISI INDEXED JOURNALS IN COMPUTER SCIENCE
- PAID JOURNALS IN COMPUTER SCIENCE
- NATIONAL JOURNALS IN COMPUTER SCIENCE AND ENGINEERING
- MONTHLY JOURNALS IN COMPUTER SCIENCE
- SCIMAGO JOURNALS LIST
- THOMSON REUTERS INDEXED COMPUTER SCIENCE JOURNALS
- RESEARCH PAPER FOR SALE
- CHEAP PAPER WRITING SERVICE
- RESEARCH PAPER ASSISTANCE
- THESIS BUILDER
- WRITING YOUR JOURNAL ARTICLE IN 12 WEEKS
- WRITE MY PAPER FOR ME
- PHD PAPER WRITING SERVICE
- THESIS MAKER
- THESIS HELPER
- DISSERTATION HELP UK
- DISSERTATION WRITERS UK
- BUY DISSERTATION ONLINE
- PHD THESIS WRITING SERVICES
- DISSERTATION WRITING SERVICES UK
- DISSERTATION WRITING HELP
- PHD PROJECTS IN COMPUTER SCIENCE
- DISSERTATION ASSISTANCE
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
- Starting the research process
- How to Write a Research Proposal | Examples & Templates
How to Write a Research Proposal | Examples & Templates
Published on October 12, 2022 by Shona McCombes and Tegan George. Revised on September 5, 2024.
A research proposal describes what you will investigate, why it’s important, and how you will conduct your research.
The format of a research proposal varies between fields, but most proposals will contain at least these elements:
Introduction
Literature review.
- Research design
Reference list
While the sections may vary, the overall objective is always the same. A research proposal serves as a blueprint and guide for your research plan, helping you get organized and feel confident in the path forward you choose to take.
Table of contents
Research proposal purpose, research proposal examples, research design and methods, contribution to knowledge, research schedule, other interesting articles, frequently asked questions about research proposals.
Academics often have to write research proposals to get funding for their projects. As a student, you might have to write a research proposal as part of a grad school application , or prior to starting your thesis or dissertation .
In addition to helping you figure out what your research can look like, a proposal can also serve to demonstrate why your project is worth pursuing to a funder, educational institution, or supervisor.
| Show your reader why your project is interesting, original, and important. | |
| Demonstrate your comfort and familiarity with your field. Show that you understand the current state of research on your topic. | |
| Make a case for your . Demonstrate that you have carefully thought about the data, tools, and procedures necessary to conduct your research. | |
| Confirm that your project is feasible within the timeline of your program or funding deadline. |
Research proposal length
The length of a research proposal can vary quite a bit. A bachelor’s or master’s thesis proposal can be just a few pages, while proposals for PhD dissertations or research funding are usually much longer and more detailed. Your supervisor can help you determine the best length for your work.
One trick to get started is to think of your proposal’s structure as a shorter version of your thesis or dissertation , only without the results , conclusion and discussion sections.
Download our research proposal template
Here's why students love Scribbr's proofreading services
Discover proofreading & editing
Writing a research proposal can be quite challenging, but a good starting point could be to look at some examples. We’ve included a few for you below.
- Example research proposal #1: “A Conceptual Framework for Scheduling Constraint Management”
- Example research proposal #2: “Medical Students as Mediators of Change in Tobacco Use”
Like your dissertation or thesis, the proposal will usually have a title page that includes:
- The proposed title of your project
- Your supervisor’s name
- Your institution and department
The first part of your proposal is the initial pitch for your project. Make sure it succinctly explains what you want to do and why.
Your introduction should:
- Introduce your topic
- Give necessary background and context
- Outline your problem statement and research questions
To guide your introduction , include information about:
- Who could have an interest in the topic (e.g., scientists, policymakers)
- How much is already known about the topic
- What is missing from this current knowledge
- What new insights your research will contribute
- Why you believe this research is worth doing
Prevent plagiarism. Run a free check.
As you get started, it’s important to demonstrate that you’re familiar with the most important research on your topic. A strong literature review shows your reader that your project has a solid foundation in existing knowledge or theory. It also shows that you’re not simply repeating what other people have already done or said, but rather using existing research as a jumping-off point for your own.
In this section, share exactly how your project will contribute to ongoing conversations in the field by:
- Comparing and contrasting the main theories, methods, and debates
- Examining the strengths and weaknesses of different approaches
- Explaining how will you build on, challenge, or synthesize prior scholarship
Following the literature review, restate your main objectives . This brings the focus back to your own project. Next, your research design or methodology section will describe your overall approach, and the practical steps you will take to answer your research questions.
| ? or ? , , or research design? | |
| , )? ? | |
| , , , )? | |
| ? |
To finish your proposal on a strong note, explore the potential implications of your research for your field. Emphasize again what you aim to contribute and why it matters.
For example, your results might have implications for:
- Improving best practices
- Informing policymaking decisions
- Strengthening a theory or model
- Challenging popular or scientific beliefs
- Creating a basis for future research
Last but not least, your research proposal must include correct citations for every source you have used, compiled in a reference list . To create citations quickly and easily, you can use our free APA citation generator .
Some institutions or funders require a detailed timeline of the project, asking you to forecast what you will do at each stage and how long it may take. While not always required, be sure to check the requirements of your project.
Here’s an example schedule to help you get started. You can also download a template at the button below.
Download our research schedule template
| Research phase | Objectives | Deadline |
|---|---|---|
| 1. Background research and literature review | 20th January | |
| 2. Research design planning | and data analysis methods | 13th February |
| 3. Data collection and preparation | with selected participants and code interviews | 24th March |
| 4. Data analysis | of interview transcripts | 22nd April |
| 5. Writing | 17th June | |
| 6. Revision | final work | 28th July |
If you are applying for research funding, chances are you will have to include a detailed budget. This shows your estimates of how much each part of your project will cost.
Make sure to check what type of costs the funding body will agree to cover. For each item, include:
- Cost : exactly how much money do you need?
- Justification : why is this cost necessary to complete the research?
- Source : how did you calculate the amount?
To determine your budget, think about:
- Travel costs : do you need to go somewhere to collect your data? How will you get there, and how much time will you need? What will you do there (e.g., interviews, archival research)?
- Materials : do you need access to any tools or technologies?
- Help : do you need to hire any research assistants for the project? What will they do, and how much will you pay them?
If you want to know more about the research process , methodology , research bias , or statistics , make sure to check out some of our other articles with explanations and examples.
Methodology
- Sampling methods
- Simple random sampling
- Stratified sampling
- Cluster sampling
- Likert scales
- Reproducibility
Statistics
- Null hypothesis
- Statistical power
- Probability distribution
- Effect size
- Poisson distribution
Research bias
- Optimism bias
- Cognitive bias
- Implicit bias
- Hawthorne effect
- Anchoring bias
- Explicit bias
Once you’ve decided on your research objectives , you need to explain them in your paper, at the end of your problem statement .
Keep your research objectives clear and concise, and use appropriate verbs to accurately convey the work that you will carry out for each one.
I will compare …
A research aim is a broad statement indicating the general purpose of your research project. It should appear in your introduction at the end of your problem statement , before your research objectives.
Research objectives are more specific than your research aim. They indicate the specific ways you’ll address the overarching aim.
A PhD, which is short for philosophiae doctor (doctor of philosophy in Latin), is the highest university degree that can be obtained. In a PhD, students spend 3–5 years writing a dissertation , which aims to make a significant, original contribution to current knowledge.
A PhD is intended to prepare students for a career as a researcher, whether that be in academia, the public sector, or the private sector.
A master’s is a 1- or 2-year graduate degree that can prepare you for a variety of careers.
All master’s involve graduate-level coursework. Some are research-intensive and intend to prepare students for further study in a PhD; these usually require their students to write a master’s thesis . Others focus on professional training for a specific career.
Critical thinking refers to the ability to evaluate information and to be aware of biases or assumptions, including your own.
Like information literacy , it involves evaluating arguments, identifying and solving problems in an objective and systematic way, and clearly communicating your ideas.
The best way to remember the difference between a research plan and a research proposal is that they have fundamentally different audiences. A research plan helps you, the researcher, organize your thoughts. On the other hand, a dissertation proposal or research proposal aims to convince others (e.g., a supervisor, a funding body, or a dissertation committee) that your research topic is relevant and worthy of being conducted.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
McCombes, S. & George, T. (2024, September 05). How to Write a Research Proposal | Examples & Templates. Scribbr. Retrieved September 28, 2024, from https://www.scribbr.com/research-process/research-proposal/
Is this article helpful?
Shona McCombes
Other students also liked, how to write a problem statement | guide & examples, writing strong research questions | criteria & examples, how to write a literature review | guide, examples, & templates, "i thought ai proofreading was useless but..".
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”

IMAGES
VIDEO
COMMENTS
Trending Thesis Topics in Computer Networking. Reliable Future Technologies of WBAN Security. Enhanced QoS Provisioning and Control. RFID assisted Mobile Devices Identification in WSN. Node Mobility and Spectrum Handoff Management. Controlling of Radio Resources for Improved Packet Access.
For network performance, Wireshark can be used for testing network performance (George et al., 2020). References. Bilal, KErbad, A. and Hefeeda, M. (2018) "QoE-aware distributed cloud-based live streaming of multi-sourced Multiview Videos," Journal of Network and Computer Applications, 120, pp. 130-144.
101 Computer Networking Thesis Topics. These topics cover various aspects of computer networking, including emerging technologies, security challenges, optimization strategies, and future trends, providing a wide array of options for research and exploration. If you are stuck with your Computer Networking Thesis writing, send your requirement ...
Therefore, I propose the following research topic for a thesis written in the field of computer networks: Improving security, procedures and techniques to protect sensitive information residing in ...
Topic 1: An evaluation of the network security during machine to machine communication in IoT. Research Aim: The research aims to evaluate the network security issues associated with M2M communication in IoT. Objectives: To evaluate the factors affecting the network security of IoT devices. To determine the methods for increasing data integrity ...
Thesis Proposal Streamlining Reuse with Concern-Speci c Modelling Languages Student Maximilian Schiedermeier Supervisors ... Prof. Martin Robillard - Software Technology Lab Prof. Muthucumaru Maheswaran - Advanced Networking Research Lab Presented for the Thesis Proposal and Area Examination, Fall 2021 School of Computer Science November 26 ...
Below you find open thesis proposals related to the research group DISCO (Distributed Systems and Communications) within Computer Science at Karlstad University. The list of topics below is outdated and will be removed soon. You find currently open master thesis topics here. Application form. Send your application form to [email protected].
Computer networks are a. system of i nterconnected computers for the purpose of. sharing digital information. The computer network. enables to analyze, organize and disseminate the. information ...
In this thesis, a wireless local area networking technique is developed, which is intended for use in a device monitoring system. A full review of the current wireless local communications protocols 802.11, 802.11a, 802.11b, 802.11g, HomeRF, Bluetooth, and Ultrawideband is presented. A detailed comparison of these techniques is performed with
CSSA Sample PhD proposals. Purpose. Welcome to the on-line version of the UNC dissertation proposal collection. The purpose of this collection is to provide examples of proposals for those of you who are thinking of writing a proposal of your own. I hope that this on-line collection proves to be more difficult to misplace than the physical ...
In this master thesis a realisation of a DT into the P4 switches will be tested. First a functioning DT based on a real data traffic dataset will be implemented. Both variations (per-packet/per-flow) will be taken into consideration. The second step will be to translate the algorithm into the P4 switches.
This thesis starts out with an overview of how insecurity came into the picture on networking and it also brings to the attention security challenges network administrator are facing as a result of the needed growth by the organization. It progresses on to include the study of the problem at hand as well as how the ...
You can explore more on these topics. If you need help with thesis topics in computer networking, you can contact us. You can call us on this number +91-9465330425 or email us at [email protected] for M.Tech and Ph.D. thesis help in computer networking. You can also fill the query form on the website.
Some of the important and appealing/interesting networking dissertation topics are listed below. The impact of 5G technology on mobile networks. The use of software-defined networking in data centers. The security of IoT networks. The use of network virtualization in cloud computing. The impact of edge computing on network architecture.
Fidelity or Li-Fi [2], is an emerging piece of technology that uses Visible Light Communication (VLC) technology. instead of radio wav es to send data as a remedy to these shortcomings. Compared ...
Network simulation was carried out with the aid of the Cisco Packet Tracer 5.3 software. SIP-based client software, FUTO Messenger, was developed to run on the network. The software supports text, voice and video chats. A prototype network system was implemented to test the network design and also to verify the functionality of the developed ...
Networking Thesis Proposal. Networking is an often-emerging domain which encompasses extensive areas that are probably relevant for carrying out significant research. The team at phdprojects.org effectively conducts thesis proposals in all networking areas. All work is initiated from the beginning to ensure zero plagiarism.
This thesis evaluates the performance of the 802.11 wireless network. The newly defined DCF+ protocol performance is studied and compared with the DCF protocol under different traffic conditions. A service differentiation mechanism is also applied to both protocols for basic access mechanism and the efficiency of the protocols is examined.
This thesis will try to address in depth the security limitations of WEP included in IEEE 802.11b specifications. To combat the WEP vulnerability for WLAN security, I plan to investigate the following solutions: IEEE 802.1x, VPN (Virtual Private Network), Cisco LEAP (Light Weight Authentication Protocol), and SSL (Secure Socket Layer).
The Networked Digital Library of Theses and Dissertations (NDLTD) is an international organization dedicated to promoting the adoption, creation, use, dissemination, and preservation of electronic theses and dissertations (ETDs). We support electronic publishing and open access to scholarship in order to enhance the sharing of knowledge worldwide.
Example research proposal #1: "A Conceptual Framework for Scheduling Constraint Management" Example research proposal #2: "Medical Students as Mediators of Change in Tobacco Use" Title page. Like your dissertation or thesis, the proposal will usually have a title page that includes: The proposed title of your project; Your name
This dissertation focuses particularly on the topic of graph neural networks (GNNs) as the main machine learning model for successfully addressing problems involving graph data. GNNs are nonlinear representation maps that exploit the underlying graph structure to improve learning and achieve better performance.