Threats of the Internet Essay
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment

Introduction
The Internet has become an indispensable part of our lives, gradually entering all the possible spheres and shaping the way we run our errands, communicate with people, and analyze the world around us. It changes our attitudes to work processes, leisure, and even interpersonal relations with the help of algorithms, simple solutions, and easy accessibility. Millions of services, goods, possibilities and infinite terabytes of all kinds of information have become available for a tap on the screen. In theory, all of these things seem to be convenient, progressive, and helpful, but the reality proves them to be also harmful to the well-being of people.
Some of the most relevant problems of today can already foreshadow the challenges we will most probably face in the not distant future. In the article “Our Machine Master” David Brooks predicts two ways for humanity equipped with artificial intelligence (AI). Contrary to many beliefs it will not give rise to humanoids, but it will be integrated into cars, headphones, watches, and other ordinary things that most people use on a daily basis. Such a close coexistence cannot but influence our habits and behavior, and in the end, such non-stop assistance and “external brain” might render people helpless and vulnerable in the face of all the dangers the real world holds.
Despite all the scientific and technical progress, our planet poses many dangers to humanity, some of them are still not thoroughly studied, some remain unknown. Moreover, even our bodies might become the victims of these technologies because less and less physical activities stay difficult enough to be performed by humans only. It is possible to suggest that we will have more free time and it will give a quality change to our lifestyle, but so far the experience of using technologies shows that they become addictive.
Another threat that lies in digital technologies is related to big data and control, which corporations acquire through online services. Such digital giants as Google and Amazon have access to all the personal and behavioral information that we share on the net, and though they claim to use for our benefit, the algorithms of the Internet also misuse in subtle and invisible ways. Searching tools can show us results they think should interest us judging by our previous clicks and views.
It is a powerful mechanism, but some people do not even notice that they are shown a distorted reality or only the part which the code deemed relevant for them. What started as endless freedoms and accessibility of all the information turns out to be pseudo equality and tyranny, in a way. I think that the article “Our Machine Master” by Brookes best argues with statistics and critical thinking, though all the rest also have relevant figures and examples, so none of them is weak.
Today digital media work according to similar principles of collecting big data, and showing the most interesting content for their users. YouTube and Instagram are among the most popular services that provide visual content; they both try to show as many relevant search results that should be interesting for users, based on their search history. Both are complex platforms with a variety of features, but at the same time, they are user-friendly, very appealing to large audiences, useful for sharing visual content and discussing it.
The wide popularity of these two services proves that people find them effective and relevant for their purposes because they succeed in holding the users’ attention and make them come back regularly. The main difference is that YouTube does not deal with photographs and mainly streams music videos and personal vlogs when Instagram also supports pictures, texting, and broadcasting. Instagram has a lower barrier of entry because photos require less preparation and work compared to video, they are easier to share, and do not take much time to be evaluated by other people.
In my personal experience, I use Instagram mostly to follow my friends and relatives and interact with them occasionally. As for YouTube, its audience seems impersonal to me, often there is too much happening in the comments section, and I usually do not contribute to discussions and only watch videos. Both services can steal a lot of my time because in a short period they have adapted to my choices and likes, and manage to provide interesting content I would not have found myself. This tendency is rather alarming, so I try to cut my time online and be mindful about things I come across on the net.
New media and technologies are developing so fast that it is hardly possible to keep up with their pace and stay sane, healthy, and socially acceptable. The biggest problem is that this endless succession of updates, notifications, and news demands all of our attention, and thus robs us of everything happening in the outer world. Attention has become one of the most valuable assets, and the more one spends online, the less connected they stay from their real-life troubles and joys. Apart from that, relying on technologies too much might weaken people and make it harder for them to adjust to the realities of the outer world.
- Instagram: Promotion of Loneliness
- Innovation: Instagram (App)
- How Instagram Claimed Its Users’ Most Intimate Moments
- The Children’s Online Privacy Protection Act (COPPA) and the Children’s Internet
- Wireless Local Area Network and Channel Fading
- The Internet of Things: Technical Description
- The Internet at Individual and Societal Levels
- Mobile Wireless Internet vs. Wi-Fi
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2021, July 18). Threats of the Internet. https://ivypanda.com/essays/threats-of-the-internet/
"Threats of the Internet." IvyPanda , 18 July 2021, ivypanda.com/essays/threats-of-the-internet/.
IvyPanda . (2021) 'Threats of the Internet'. 18 July.
IvyPanda . 2021. "Threats of the Internet." July 18, 2021. https://ivypanda.com/essays/threats-of-the-internet/.
1. IvyPanda . "Threats of the Internet." July 18, 2021. https://ivypanda.com/essays/threats-of-the-internet/.
Bibliography
IvyPanda . "Threats of the Internet." July 18, 2021. https://ivypanda.com/essays/threats-of-the-internet/.
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
You’re Not Powerless in the Face of Online Harassment
- Viktorya Vilk

Eight steps to take.
If you or someone you know is experiencing online harassment, remember that you are not powerless. There are concrete steps you can take to defend yourself and others. First, understand what’s happening to you. If you’re being critiqued or insulted, you can choose to refute it or let it go. But if you’re being abused, naming what you’re experiencing not only signals that it’s a tangible problem, but can also help you communicate with allies, employers, and law enforcement. Next, be sure to document. If you report online abuse and succeed in getting it taken down, you could lose valuable evidence. Save emails, voicemails, and texts. Take screenshots on social media and copy direct links whenever possible. Finally, assess your safety. If you’re being made to feel physically unsafe in any way — trust your instincts. While police may not always be able to stop the abuse (and not all authorities are equally well-trained in dealing with it), at the very least you are creating a record that could be useful later.
Online abuse — from impersonation accounts to hateful slurs and death threats — began with the advent of the internet itself, but the problem is pervasive and growing. A 2017 study from the Pew Research Center found that more than 40% of Americans have experienced online abuse, and more than 60% have witnessed it. People of color and LGBTQ+ people are disproportionately targeted, and women are twice as likely as men to experience sexual harassment online.
- VV Viktorya Vilk is Program Director for Digital Safety and Free Expression at PEN America, where she develops resources, including the Online Harassment Field Manual , and conducts trainings on online abuse, self-defense, and best practices for offering support.
Partner Center
- Call Us: (513) 984-3900
- Send Message: [email protected]

10 Common Internet Security Threats and How to Avoid Them

Are you running a small business? Did you recently fall victim to a cyber-attack? Are you searching for ways to prevent a similar incident from happening again?
Small businesses lose an average of $80,000 annually to cyber-attacks. In some cases, companies bleed millions after losing precious data to cybercriminals.
Hence, reliable computer security is a must. But knowing the enemy is half the battle won, as the saying goes. Thus, before you invest in any computer security service, you must first identify the different internet security threats that can disrupt your business.
But what exactly are these threats? What are the basic steps you can do to avoid them?
Continue reading below for 10 of the most common forms of IT security threats and how to keep them at bay.
1. Computer Viruses
Computer viruses are the most common among internet security threats out there. Viruses enter your computers by attaching to a host file or a system. Once they enter your computer, they can create damage instantly or remain dormant.
The goal of viruses is to infect your other computers and networked systems.
One of the basic steps to protecting your computers from viruses is by setting up a firewall. This firewall works by blocking external access to your network systems.
A firewall is not 100% foolproof. But it will at least deter or slow down cyber attackers.
Another common security threat to your computer systems is malware or ransomware. Malware attacks your files and will only stop until you pay the cybercriminal a hefty ransom.
Studies reveal that malware affects 32% of all the computers in the world.
The attack starts by infecting your database systems. From there, it will encrypt your data then pose a threat to delete all your files.
One of the first signs of a malware attack is the slowing down of your system. If you notice your computers slowing down for no apparent reason, shut it down first. Disconnect them from the internet then reboot your system.
Thereafter, you can install a security product to scan your system for malware. Furthermore, install reputable antivirus software along with your firewall.
3. Phishing
The main targets of a phishing attack include your usernames, passwords, and credit card information.
They steal valuable data by pretending to be banks and financial institutions, and they can also impersonate reputable websites and even some of your personal contacts.
They use emails or instant messages that look legitimate at first glance. Their messages come with URLs that prompt you to input your personal information. In turn, they’ll steal your credentials and use them to access your accounts.
To keep away from phishing attacks, be mindful of the emails and messages you receive. If you don’t know the sender, think twice before opening the message.
Also, check the content of your emails before opening any links. If you see a lot of misspelled words, then a phishing attack is possible.
Additionally, invest in a total security program that offers protection against phishing attacks.
Of all the different forms of internet security threats, this is one of the most dangerous. A botnet is similar to malware. However, it involves a network of computers that hackers compromised.
In turn, hackers use it to control the infected computers within the network. What makes it even more dangerous is that hackers can control the network remotely.
Since the end goal of botnets is to force you to pay a ransom, installing a dependable security program is paramount. And if you discover one of your computers carries a botnet, you must remove the software and run an antivirus scan thereafter.
5. Distributed Denial of Service (DDoS)
A DDoS attack looks to overwhelm hosted servers and force them to become inoperable. And if your business involves an eCommerce shop or heavy use of social media, a DDoS attack can be catastrophic.
Hence, the best way of protecting your business from DDoS threats is to have a strong relationship with your internet service provider. This is crucial especially if you’re using small business email hosting.
Furthermore, if you’re using cloud hosting, make sure to check your network protection. For starters, it is wise to invest in dependable options like Microsoft Azure cloud.
6. Trojan Horse
A Trojan Horse is a program that looks legitimate and harmless. But in reality, it is a vector that carries many harmful viruses. Once it gains network access, it can steal sensitive company data.
The most common method for Trojan Horse attacks is through email. The email usually comes with a link or attachment containing the viruses. Once you open the attachment, it automatically downloads malware to your computer.
Apart from installing cybersecurity software, you should update your software regularly. This also includes your security patches.
7. SQL Injection Attack
Another dangerous threat is an SQL injection attack. It uses malicious code to penetrate your weak security systems. Thereafter, it can steal or destroy your valuable data.
Protection against SQL attacks involves updating all your database software. Make sure to update all security patches. Avoid sharing database accounts using different applications or sites.
Similar to botnets, a rootkit allows hackers to access your system remotely. They do this by placing a collection of tools on your network. Some of the common forms of rootkit attacks include the stealing of passwords and disabling antiviruses, among others.
Rootkits enter your network if your system security is vulnerable. Thus, the solution is to keep your patches up-to-date.
9. Rogue Security Software
This is a form of malicious software that makes you believe that your computer has a virus. Sometimes, it will fool you into believing that your security measures are old.
In turn, they will offer new updates for your security settings. And once you update using their program, that’s the time the malware can enter your computers.
To avoid this attack, you need a dependable security system. Also, do not download updates from dubious sources. Additionally, update through legitimate sites and channels.
10. APT Threats
As for the APT threat, surreptitiously enter your system through coding. Once the APT is inside your system, it will remain there quietly while stealing your financial information.
APT attacks are difficult to detect. Hence, you must pay attention to unusual patterns in your network activity.
Enjoy Topnotch Protection Against Internet Security Threats
Now that you know the most common internet security threats, you can protect your online business more effectively. And if you’re looking for a computer security system you can trust, then you came to the right place.
Connect with us today and request a free quote . Tell us what you need and let’s discuss your options. Give your business the internet security it rightfully deserves.
Share This Article
Related articles.
A Complete Guide to Ransomware: What It is and How to Stop It

What Is Computer Security and What Does It Protect Me From?
Search keywords, latest posts.

A Beginner’s Guide to Understanding VoIP: Everything to Know
November 23, 2020.

Choosing the Best Cloud Service Providers: Comparing Azure vs Private Cloud Hosting

October 5, 2020

8 Tips on Using Azure Hosting for Small Businesses
Social media.

We Are Here to Help!
It’s never been easier to get started with our Managed IT solutions.

- Bachelor’s Degrees
- Master’s Degrees
- Doctorate Degrees
- Certificate Programs
- Nursing Degrees
- Cybersecurity
- Human Services
- Science & Mathematics
- Communication
- Liberal Arts
- Social Sciences
- Computer Science
- Admissions Overview
- Tuition and Financial Aid
- Incoming Freshman and Graduate Students
- Transfer Students
- Military Students
- International Students
- Early Access Program
- About Maryville
- Our Faculty
- Our Approach
- Our History
- Accreditation
- Tales of the Brave
- Student Support Overview
- Online Learning Tools
- Infographics
Home / Blog
How to Prevent Cyberattacks: Top Ways to Protect Yourself
March 17, 2021
According to a 2020 Verizon report, 86% of global data breaches are financially motivated. Now more than ever, individuals and businesses must proactively maintain their cybersecurity because the cost of a cyberattack can run well into the millions — a price few are able or willing to pay.
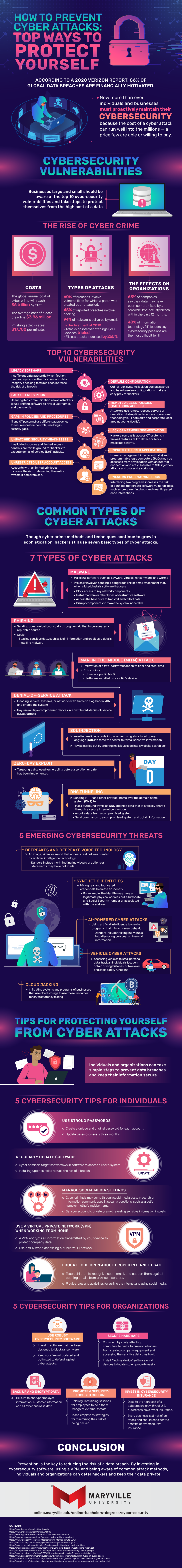
To learn more, check out the infographic below, created by Maryville University’s Online Bachelor of Science in Cybersecurity program.
Add This Infographic to Your Site
Cybersecurity vulnerabilities.
Businesses large and small should be aware of the top 10 cybersecurity vulnerabilities and take steps to protect themselves from the high cost of a data breach.
The rise of cybercrime
Cybercrime is expensive. The average cost of a data breach is $3.86 million, with the global annual cost of cybercrime estimated to reach $6 trillion by 2021. Phishing attacks, for example, steal a jaw-dropping $17,700 per minute.
Hackers use a variety of techniques, but trends are revealing which tactics they prefer. Six out of 10 breaches involve vulnerabilities for which a patch was created but not applied, while 45% of reported breaches involve hacking and 94% of malware is delivered by email.
In the first half of 2019, attacks on internet of things (IoT) devices tripled and fileless attacks increased by 265%.
Organizations of all sizes are being affected by data breaches, with 63% of companies saying their data may have been compromised by a hardware-level security breach within the past 12 months. Some 40% of information technology (IT) leaders say cybersecurity positions are the most difficult to fill.
Top 10 cybersecurity vulnerabilities
Businesses should be aware of the most common cybersecurity vulnerabilities; these include legacy software, default configuration, lack of encryption, remote access policies (backdoor access), gaps in policies and procedures, lack of network segmentation, unpatched security weaknesses, unprotected web applications, unrestricted user account access, and unknown programming bugs.
Common types of cyberattacks
Though cybercrime methods and techniques continue to grow in sophistication, hackers still use seven basic types of cyberattacks.
7 types of cyberattacks
During a malware attack , a hacker sends a dangerous link or email attachment that, when clicked, installs software that can block access to key network components, install malware or other types of destructive software, access the hard drive to transmit and collect data, and disrupt components to make the system inoperable.
A phishing attack involves sending communication, usually through email, that impersonates a reputable source. The goals of this attack may be to steal sensitive data, such as login information and credit card details, and to install malware.
A man-in-the-middle (MitM) attack occurs when a hacker infiltrates a two-party transaction with the intent to filter and steal data. Common entry points for this type of attack include unsecure public Wi-Fi and software installed on a victim’s device.
During a denial-of-service attack , a bad actor floods servers, systems, or networks with traffic to clog bandwidth and cripple the system. This type of attack may use multiple compromised devices in a distributed-denial-of-service (DDoS) attack.
An SQL injection involves inserting malicious code into a server using structured query language (SQL) to force the server to reveal sensitive information. The cybercriminal may enter malicious code into a website search box to carry out this type of attack.
A zero-day exploit attack involves targeting a disclosed vulnerability before a solution or patch has been implemented. Organizations that fail to act quickly may find themselves the target of this type of attack.
DNS tunneling occurs when a bad actor sends HTTP and other protocol traffic over the domain name system (DNS) to mask outbound traffic as DNS and hide data that is typically shared through a secure internet connection; acquire data from a compromised system; and send commands to a compromised system and obtain information.
5 emerging cybersecurity threats
Deepfakes and deepfake voice technology use artificial intelligence technology to create an image, video, or sound that appears real. The dangers of this threat include incriminating individuals of actions or statements they have not made.
A similar cybersecurity threat is the mixing of real and fabricated credentials to create a synthetic identity. For example, the identity may have a legitimate physical address but a birthdate and Social Security number unassociated with the address.
AI-powered cyberattacks use artificial intelligence to create programs that mimic human behavior. When successful, this type of attack can trick individuals into disclosing personal or financial information.
Vehicle cyberattacks may involve accessing vehicles to steal personal data, track an individual’s location, obtain driving histories, or take over or disable safety functions.
Cybercriminals may also engage in cloud jacking by infiltrating systems and programs of businesses that use cloud storage to use these resources for cryptocurrency mining.
Tips for protecting yourself from cyberattacks
Individuals and organizations can take simple steps to prevent data breaches and keep their information secure.
5 cybersecurity tips for individuals
The first and most basic step in maintaining cybersecurity is to create a unique and original password for each account. Users should also remember to update passwords every three months.
Keeping up with software updates is important, as cybercriminals often target known flaws in software to access a user’s system.
Cybercriminals may comb through social media posts in search of information commonly used in security questions, such as a pet’s name or mother’s maiden name. To combat this risk, social media users should set their account to private or avoid revealing sensitive information in posts.
A virtual private network (VPN) is a great way to protect sensitive data, especially when accessing a public Wi-Fi network. A VPN encrypts all information transmitted by your device and helps prevent many types of cyberattacks.
And finally, teachers and parents should educate children about proper internet usage. Children and teens should know what the rules and guidelines are for surfing the internet and using social media.
5 cybersecurity tips for organizations
To protect business data, it’s important to secure hardware, back up and encrypt data, invest in cybersecurity insurance, promote a security-focused culture, and use robust cybersecurity software. Taking these steps will help reduce risk and keep the business operating without interruption.
Reducing risk
Prevention is the key to reducing the risk of a data breach. By investing in cybersecurity software, using a VPN, and being aware of common attack methods, individuals and organizations can deter hackers and keep their data private.
Check Point, “Top 10 Critical Infrastructure And SCADA/ICS Cybersecurity Vulnerabilities And Threats”
Cisco, “What Are The Most Common Cyber Attacks”
Compuquip, “Top 9 Cybersecurity Threats And Vulnerabilities”
CSO Online, “Top Cybersecurity Facts, Figures and Statistics”
Cybercrime Magazine, “Cybercrime To Cost The World $10.5 Trillion Annually By 2025”
Dell Technologies, “BIOS Security — The Next Frontier for Endpoint Protection”
Entrepreneur, “Five Ways To Protect Your Company Against Cyber Attacks”
F-Secure, “Attack Landscape: H1 2019”
IBM, “Data Breach”
IDG, “2020 State of the CIO”
Norton, “11 Ways to Help Protect Yourself Against Cybercrime”
Norton, “Cyberthreat Trends: 15 Cybersecurity Threats For 2020”
RiskIQ, “The Evil Internet Minute 2019”
ServiceNow, “Costs and Consequences of Gaps in Vulnerability Response”
Verizon, “2019 Data Breach Investigations Report”
Verizon, “2020 Data Breach Investigations Report”
Bring us your ambition and we’ll guide you along a personalized path to a quality education that’s designed to change your life.
Take Your Next Brave Step
Receive information about the benefits of our programs, the courses you'll take, and what you need to apply.
- Entertainment
- Environment
- Information Science and Technology
- Social Issues
Home Essay Samples Information Science and Technology Internet
Strategies To Tackle Threats From The Internet
*minimum deadline
Cite this Essay
To export a reference to this article please select a referencing style below

- Effects of Computers
- Modern Technology
- Computer Science
- Computer Security
- Cloud Computing
Related Essays
Need writing help?
You can always rely on us no matter what type of paper you need
*No hidden charges
100% Unique Essays
Absolutely Confidential
Money Back Guarantee
By clicking “Send Essay”, you agree to our Terms of service and Privacy statement. We will occasionally send you account related emails
You can also get a UNIQUE essay on this or any other topic
Thank you! We’ll contact you as soon as possible.
Staying Safe Online: 6 Threats, 9 Tips, & 1 Infographic
Before the current pandemic, we used the Internet to do a lot of things. Now, however, with everyone confined to their homes, we have been doing almost everything online. We’re not only talking about shopping. People from all around the world can connect via video calls. They can even work or study online. The Internet has become an essential tool to participate in modern life. However, it’s important to remember that online connection comes with a price.

“Stay home, stay safe” is the current motto. But the more time you spend online, the greater the risk of cyber threats. During the pandemic, the frequency of online crimes has risen exponentially. According to an FBI report of 2020, the number of instances has doubled compared to previous years. Since we can’t stop using the Internet entirely, how can we protect ourselves?
This article:
- examines the six main threats you face online
- provides a list of nine effective tips on how to stay safe
- contains an infographic that is easy to print out
- Top 6 Cybersecurity Threats
9 Internet Safety Tips
- Internet Safety Infographic
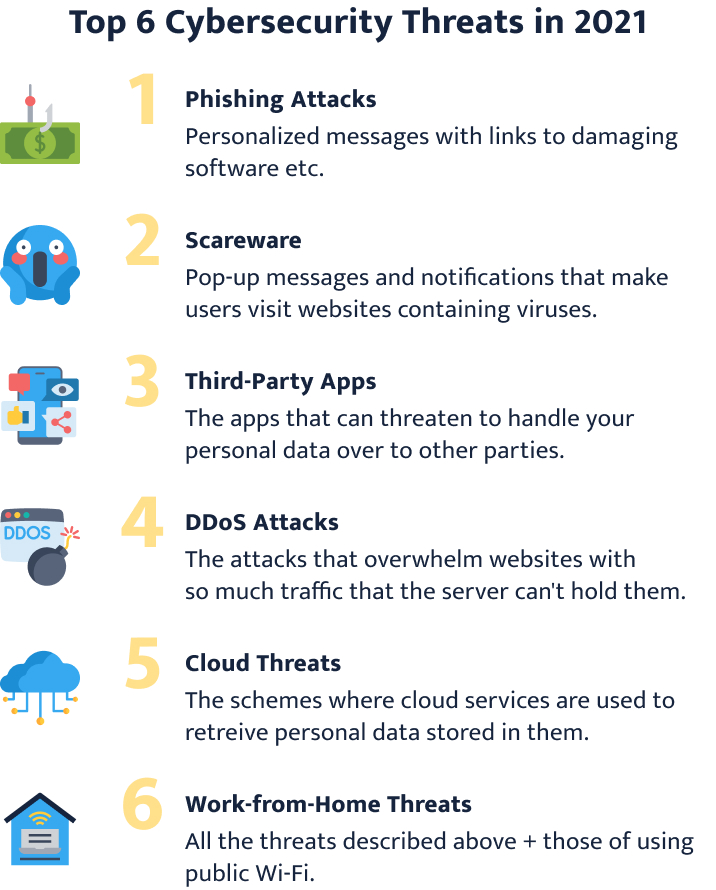
Top 6 Cybersecurity Threats in 2024
The FBI released a report created by the Internet Crime Complaint Center. It revealed that in 2020 the number of registered cybercrimes almost doubled compared to the previous year. Victims have lost large quantities of money due to different types of online scams. What caused such a drastic rise in online crimes?
One theory is that those who have been left unemployed have begun to make money as cybercriminals. These job seekers are so desperate that they agree to work for organized groups of criminals who scam Internet users. Unfortunately, this is the new reality that the high unemployment rates from the pandemic have created.
Online frauds are becoming more and more sophisticated. Now, successful hackers also use tactics from human psychology and social engineering . Cybercriminals find weaknesses by applying psychological tricks. They blackmail people through social media or their phones. To keep yourself and your money safe, you need to be aware of all the online threats described below.
- Phishing Attacks Phishing is one of the most popular types of cyber-attacks. The method works by sending out personalized messages to people and inviting them to click a link. These links damage the victim’s operating system by installing harmful software or even compromising the victim’s safety through the exposure of private information. Since most people are aware of such attacks, cybercriminals have had to develop new methods to trick users. Now, they use machine learning to create even more convincing messages. The main goal is to fool employees into disclosing sensitive information , such as passwords to the organization’s systems or credit card data.
- Scareware Like phishing, this type of cybercrime is based on social engineering. Scareware describes all software that tricks users into visiting websites that contain viruses. These can be especially dangerous because they can mimic notifications from antivirus software . They show up in the form of pop-up messages that claim to have detected a virus on your computer. Such notifications look authentic. Users don’t think twice before paying for the installation of the software that can fix the supposed problem. However, what they receive instead is malware that intends to steal private data. Often, scareware saves your credit card information so that cybercriminals can use it for identity theft.
- Third-Party Apps Even though third-party apps may have some benefits, they still carry potential risks to your privacy. Such apps ask for your permission to access your accounts. For example, some post on your social media accounts via other apps. This saves time and seems handy, right? Not so fast! There have been many cases where third-party apps have spammed and posted messages on people’s accounts. However, that’s not the worst thing they can do. Those apps can potentially hand your personal data over to other parties . Your security and privacy are undermined with third-party apps.
- DDoS Attacks Distributed denial-of-service (DDoS) attacks are usually aimed at websites or online services. These attacks try to overwhelm a website with so much traffic that the server can’t withstand the assault. This can be in the form of an enormous number of requests or incoming messages. As a result, the website crashes and fails to operate normally. Sometimes, these attacks are mild or demand that you transfer money. However, with attacks powerful enough, hackers can take control of huge international services, such as Amazon, Netflix, or even Visa. Another way cybercriminals use DDoS attacks is to initiate them as a distraction. While the company or organization is trying to get things under control, the criminal steals data or installs malicious software.
- Cloud Threats The idea behind cloud threats is simple – hackers use cloud services to retrieve personal data stored there. Sometimes accessing cloud data is just a first step in their plan to perform a DDoS attack or blackmail the users. Many companies and organizations have been the victims of these attacks. In 2020, the situation worsened. Individual users and big organizations have been reporting more and more cases of data loss through cloud attacks. Sometimes, cybercriminals remain unnoticed in the cloud system until much later. The time they spend preparing the attacks helps them evade security measures.
- Work-from-Home Threats Since the start of the pandemic, many people have started working from home, which means that they receive less protection from their employers in regards to cybersecurity. The risks have increased for employees, which has IT specialists pretty worried. In addition to all the threats described above, users are exposed to the risks of using public Wi-Fi . Those who work from home are suffering from more phishing attacks as well. In part, this is due to the more active use of email and messaging apps.
All of these threats seem quite dangerous to your privacy, don’t they? What can you do to protect yourself from cyber-attacks? You don’t have to become an IT expert. Just following a few simple rules is enough.
Here are our main tips on how to keep cybercriminals away:
- Capital letters
- Unique signs
There are tools that can make this process easier. For example, password generators provide you with solid and secure passwords in just a few seconds.
- Don’t share personal data on your social media accounts. Sharing pictures of major life events or everyday moments on social media may seem fairly innocent. However, you should probably be more careful. Everyone has access to that information. Skilled cybercriminals have no trouble tracking down your relationships and other details about your life. They may use what they find to trick your friends into giving up sensitive information. It’s not hard to find out dates of birth, email addresses, interests, and details about family members, which makes it even easier for hackers to break into your account (see the first tip to avoid this!).
- Visit only secure websites. Sometimes, website content may seem too appealing not to visit. You might even go ahead and create a profile, sharing your personal information. You should be careful, though, because not all websites are safe places. Who knows what malicious programs and scams are hidden there? Before doing anything, make sure you check the website address. URLs beginning with “https” are safer than ones with “http” because the letter “s” stands for security. Another thing to look out for is a small lock sign near the URL . Nowadays, web browsers are able to recognize safe websites and mark them as secure with this sign.
- Use legitimate software. Yes, we understand that it carries a high price tag, but do you really want to take risks? Going to unsafe websites and using third parties to get free software is not the best idea nor the most ethical practice. Whenever you want to get an app or a program, you should do it through an official provider’s website, whether or not you pay. This ensures the authenticity of the software. Otherwise, you risk downloading a virus or malicious program instead. Don’t forget to keep everything updated!
- Be careful when using credit cards. It is estimated that for every $100 spent by credit card users, about $10 is lost due to fraud . There are many dangers in using your cards for online shopping, but these tips will help you avoid those traps. First of all, try not to use debit cards that are directly linked to your bank account, and use only one card to purchase things online. Another thing to consider is adding a second layer of protection, which is usually offered by your bank. For example, not only will you be asked to put in a password, but a code sent to your email or phone will be required. Lastly, don’t forget to check if the website is safe.
- Use two-step verification. It’s easy for hackers to guess your password and steal your personal data unless they have to verify that they are the rightful owners. How is this done? The most common solution is a process called two-step verification. For example, Google offers this option to all of its users. Instead of simply typing in your password, you also need to enter a code that is sent to your phone in order to log in to your account. Many websites and services offer these security measures (such as banks, which we highlighted in the previous tip).
- Steer clear of phishing scams. Chances are that at least once in your life, you have received a message with questionable content. Keep an eye out for similar ones and never respond or click on any links! Typically, the message contains some irresistible offer or could allegedly be sent from a website you trust. Sometimes, they can appear as notifications about an issue, calling for you to take some action. It is essential to recognize whether the sender of these messages is someone you actually know. Always remember to follow the tips described above, such as using two-step verification and legitimate software.
- After getting a router from your provider, make sure you change its name and password . It is not hard to do by yourself, and such a measure can provide additional security.
- It is also a good idea to see whether your new router has the most recent security protocols since these make it harder for cybercriminals to hack into it.
- Don’t forget to log out. The convenience of staying logged in to your favorite websites is high, but it is dangerous for the security of your personal information. Not only can online services keep you logged in at all times, but they can also save all of your data. Sometimes, websites don’t even ask if you want them to remember passwords. We know that it is more difficult to enter long passwords every time you enter a website, especially from your phone, but this provides additional security. Think about these issues carefully and determine your priorities. We are only here to help you.
Internet Safety Tips: Infographic
In this infographic, we have put together all the best tips to help you stay safe online. These nine tips are easy to incorporate into your daily life. Read over this list of small things you can do every day to protect your private information (it’s easy to print out, too!).

To sum up, in today’s world, you need to stay alert even when you are at home using your laptop. Being aware of the ways hackers steal your sensitive data is essential. Besides, we highly recommend making good use of the tips we provided in this article. You can start making your online life safer right now!
- Share to Facebook
- Share to Twitter
- Share to LinkedIn
- Share to email
![how to avoid internet threats essay UniPapers Review—Trustworthy Academic Service [10+ Years of Experience]](https://custom-writing.org/blog/wp-content/uploads/2021/04/close-up-woman-working-laptop-284x153.jpg)
The issue of students struggling with home assignments and seeking additional help always causes active discussions. Especially when academic assistance services are involved in the talks. We can’t deny that homework help websites have been surrounded by controversies for quite a while (more than a decade, actually). Some people see...

Have you ever felt like you could use some additional help with assignments? If the answer is yes, then you’re not alone. The number of students who struggle with their academic tasks is a lot bigger than you might expect. The main problem here is that curriculums in high schools,...

Every student has their own good reasons to be looking for help with assignments. Overload with too much homework, other tasks and responsibilities to take care of, part-time job, lack of information or resources, insufficient language skills in ESL students… The list can go on and on. The fact that...

How do you deal with criticism? The first reaction many of us have is to defend ourselves, or worse, fight back. We can feel offended, seeing negative feedback as a dismissal of our work. Yet, while criticism can feel hurtful and demoralizing, it can also be viewed in a positive...

This infographic contains all the basic information on the benefits of mindfulness for students. It also describes 6 simple mindfulness techniques you can use in your daily life. In order to find the best ways of applying those thecniques, you can take a learning style quiz for students to find...

This infographic contains nine tips on organizing your study space so that you could work without any distractions. Wondering how to choose the furniture, organize and decorate your place, and what colors to use? Here you’ll find the answers!

The winter holidays are a much-anticipated break for everyone, particularly for school and college students. It’s an opportunity to get some much-needed rest and refresh their minds. Afterward, students can get back to class, full of strength and inspiration. While relaxation is essential during this period, it is also possible...

When you participate in face-to-face communication, your appearance, tone of voice, and word choice determine the impression you make. In the era of globalization, the internet allows us to contact people we have never seen and might never meet. This online interaction can impact our lives even more than our...

You’ve graduated high school and got admitted to college or university. Or maybe you’ve already been on that continued path to getting a degree for some time. Whatever the case is, let’s face it—studies can get unbearably tough.

Are you wondering what the most effective study methods are? Do you want to know how to study fast in less time? Do you require more time for extracurricular activities but have to reserve to get prepared for exams? With our scientifically proven study tips and tricks for college students,...

Learning English as a second language and want to make progress but don’t know how? Spend a lot of money on ESL textbooks and classes? You can find many free or affordable resources for ESL students online! Our team listed ESL websites for listening, reading, speaking, and writing to develop...

According to recent statistics, approximately 72% of adults are passive job-seekers. That means that hundreds of candidates are aiming for your potential job. And they might be more experienced and skilled than you. We’re sure there are many advantages to hiring you. But to beat all those competitors, you, yesterday’s...
Not only would I give the tips you gave but for eachvone as a teacher I would try to find concrete examples of how people accomplish the cyber acts. I use to find many in my junk mail. Illustrate to the students how they are worded and take advantage of the innocent.
Home — Essay Samples — Law, Crime & Punishment — Cyber Crimes — Cybercrimes & Ways To Prevent Them
Cybercrimes & Ways to Prevent Them
- Categories: Cyber Crimes Cyber Security
About this sample

Words: 482 |
Published: Mar 3, 2020
Words: 482 | Page: 1 | 3 min read
Works Cited
- Cert NZ. (2022). Protecting Yourself Online. Retrieved from https://www.cert.govt.nz/individuals/get-sorted/how-to-be-safe-online/
- Federal Bureau of Investigation. (n.d.). Cyber Crime. Retrieved from https://www.fbi.gov/investigate/cyber
- Cybersecurity & Infrastructure Security Agency. (2021). Cybersecurity Overview. Retrieved from https://www.cisa.gov/cybersecurity
- United States Department of Justice. (n.d.). Cyber Crime. Retrieved from https://www.justice.gov/criminal-ccips/cybercrime
- National Cyber Security Alliance. (2022). Stay Safe Online. Retrieved from https://staysafeonline.org/
- Mitnick, K., & Simon, W. L. (2017). The Art of Invisibility: The World's Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data. Back Bay Books.
- Schneier, B. (2015). Data and Goliath: The Hidden Battles to Collect Your Data and Control Your World. W. W. Norton & Company.
- Anderson, R. (2015). Security Engineering: A Guide to Building Dependable Distributed Systems. Wiley.
- SANS Institute. (2022). Cyber Security Resources. Retrieved from https://www.sans.org/resources/
- Department of Homeland Security. (n.d.). Stop. Think. Connect. Retrieved from https://www.dhs.gov/stopthinkconnect

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Dr Jacklynne
Verified writer
- Expert in: Law, Crime & Punishment Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
3 pages / 1254 words
3 pages / 1166 words
4 pages / 1624 words
4 pages / 1788 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online

Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Cyber Crimes
In our increasingly interconnected world, where technology is deeply woven into the fabric of our daily lives, the specter of computer threats looms large. From malware attacks to hacking and data breaches, the digital landscape [...]
Lee, S. (2017). Encrypted Messaging: Keeping Your Conversations Secure. Security Boulevard.Smirnoff, V., & Turner, S. (2019). Symmetric Encryption: Definition, Types, and Examples. SecurityTrails.Almeida, R. (2019). Asymmetric [...]
Cybersecurity has become a very familiar term that has drawn increasing awareness of the danger of leaving cybercrimes unpunished. Because the world is moving more toward online trading and e-commerce, and basically living [...]
Cybercrime is emerging as a very serious threat in today’s world. The internet brings happiness to our lives but at the same time, it has some negative sides too. The cybercriminal is always in a search to find out the new ways [...]
The problem of preventing cybercrime on an international scale has received considerable attention from many different countries. This essay analyzes cybercrime law. It aims to review past legislation and how it affected the [...]
Drunk driving is a serious issue and is the reason for numerous deaths every year. Add drugs into that equation and you have yourself an even more deadly combination. On the more personal side, drunk driving deaths can change [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

- Get started with computers
- Learn Microsoft Office
- Apply for a job
- Improve my work skills
- Design nice-looking docs
- Getting Started
- Smartphones & Tablets
- Typing Tutorial
- Online Learning
- Basic Internet Skills
- Online Safety
- Social Media
- Zoom Basics
- Google Docs
- Google Sheets
- Career Planning
- Resume Writing
- Cover Letters
- Job Search and Networking
- Business Communication
- Entrepreneurship 101
- Careers without College
- Job Hunt for Today
- 3D Printing
- Freelancing 101
- Personal Finance
- Sharing Economy
- Decision-Making
- Graphic Design
- Photography
- Image Editing
- Learning WordPress
- Language Learning
- Critical Thinking
- For Educators
- Translations
- Staff Picks
- English expand_more expand_less
Internet Safety - How to Avoid Malware
Internet safety -, how to avoid malware, internet safety how to avoid malware.

Internet Safety: How to Avoid Malware
Lesson 5: how to avoid malware.
/en/internetsafety/avoiding-spam-and-phishing/content/
How to avoid malware
Malware is one of the most common hazards to your computer when you're online, but it's easy to avoid. Developing safe and smart browsing habits can protect you from malware and other threats, like viruses. Securing your computer and learning how to identify and avoid suspicious links are the fundamentals of safe browsing habits.
Secure your computer
Limiting your computer's vulnerability to malware is a crucial safe browsing habit. You can protect your computer by running antivirus and antimalware software like Bitdefender or Norton . These programs can block malware from being installed and can remove it if it does get onto your computer. Even if you don't see signs of malware on your computer, running regular scans can catch any malware that has escaped notice.
Many malware programs take advantage of security flaws in Windows and other software. Keeping your OS, browser, and other programs updated is an important step in protecting your computer. The security patches in these updates make your computer immune to many threats.
Learn more in our lesson on How to update your software .
Back up your files
Some malware can delete or corrupt data on your drives. Preparing for the possibility of data loss is much easier and cheaper than attempting to recover data after a malware attack. The two most common ways of doing this are copying your data to an external drive and using an online backup service.
Learn more in our lesson on Backing Up Your Files .
Avoid suspicious links
Most malware requires you to click something to download and install it. These links are often disguised as something they are not. If you are aware of what suspicious links can look like, you can avoid them. Here are some examples of misleading links concealing malware downloads.
- Ads can look like messages saying you have won a prize and instructing you to click to claim it.
- Pop-up windows frequently contain malware or attempt to lead you to a less secure site. Most reputable sites don't use pop-up windows. Many browsers block pop-up windows by default.
- If you are prompted to download something you weren't expecting—or if it seems to be unrelated to the page you were on—it's probably malware.
- Headlines that are ambiguous and sensational that encourage you to click to read more are called clickbait . Sites that use lots of clickbait headlines are more likely to contain links to malware.
Identify suspicious sites
If you're ever unsure whether a website or download is safe, close it and investigate the site before returning to it. It's always a good idea to be cautious when browsing unfamiliar sites.
- Ask your friends if the site is reputable or if they have any experiences with the site.
- Search for information about the site . Use a search engine to find news about the organization that runs the site, or look for posts on forums about other people's experiences with that site.
- Check the address bar in your browser . Some malicious websites are designed to look like other well-known sites, but your address bar will tell you which site you're actually on. If you are no longer on the site you expected to be, it's suspicious.
/en/internetsafety/safe-online-shopping/content/
- Home Products
- Small Business 1-49 employees
- Medium Business 50-999 employees
- Enterprise 1000+ employees
What are web threats?

Web threats definition
Web-based threats, or online threats, are a category of cybersecurity risks that may cause an undesirable event or action via the internet.
Web threats are made possible by end-user vulnerabilities, web service developers/operators, or web services themselves. Regardless of intent or cause, the consequences of a web threat may damage both individuals and organizations.
This term typically applies to — but is not limited to — network-based threats in the following categories:
- Private network threats - impact sub-networks connected to the wider global internet. Typical examples can include home Wi-Fi or ethernet networks, corporate intranets, and national intranets.
- Host threats - impact specific network host devices. The term host often refers to corporate endpoints and personal devices, such as mobile phones, tablets, and traditional computers.
- Web server threats - impact dedicated hardware and software that serve web infrastructure and services.
Internet-based threats expose people and computer systems to harm online. A broad scope of dangers fits into this category, including well-known threats like phishing and computer viruses . However, other threats, like offline data theft, can also be considered part of this group.
Web threats are not limited to online activity but ultimately involve the internet at some stage for inflicted harm. While not all web threats are created deliberately, many are intended — or have the potential — to cause:
- Access denial. Prevention of entry to a computer and/or network services .
- Access acquisition. Unauthorized or unwanted entry into a private computer and/or network services.
- Unauthorized or unwanted use of computer and/or network services.
- Exposing private data without permission, such as photos, account credentials, and sensitive government information.
- Unauthorized or undesired changes to a computer and/or network services.
In recent years, the landscape of web threats has grown significantly. Technologies like smart devices and high-speed mobile networks have allowed for an always-connected vector of malware, fraud, and other complications. Also, web adoption in areas like communications and productivity via the Internet of Things (IoT) has outpaced user security awareness.
As we continue to rely more on the web for daily living, it will keep exponentially rising as an attractive attack option for malicious parties. Convenience and a lack of caution around web use are among the top concerns that continue to pose new risks to privacy and security.
While targets are typically computer-based, human victims ultimately experience the lasting effects of a web threat.
How do web threats work?
When a web threat arises, certain circumstances align to make it a point-of-concern.
Namely, there are a few basic components to any web threat:
- Threat motives give an intentional threat agent a reason or goal to cause harm. Some threat agents don’t act intentionally or act autonomously and may, therefore, be absent of motive.
- Threat agents are anything or anyone that can negatively impact — with the internet either as a threat vector or a target itself.
- Vulnerabilities include any human behavior weakness, technology systems, or other resources that can lead to a damaging exploit or incident.
- Threat outcomes are the negative results of a threat agent acting against one or more vulnerabilities.
As these components interact, a threat becomes an attack on computer systems. Threat motives can include any of the following: financial, surveillance, information, retaliation, sabotage, and more.
Threat agents are typically people with malicious intent. By extension, agents may also be anything that is manipulated into acting in favor of the original threat agent. However, some threat agents — such as destructive nature events — act entirely without human intervention.
The types of threat agents include:
- Non-human agents: Examples include malicious code (viruses, malware, worms, scripts), natural disasters (weather, geological), utility failure (electrical, telecom), technology failure (hardware, software), and physical hazards (heat, water, impact).
- Intentional human agents: Based on malicious intent. Can be internal (employees, contractors, family, friends, acquaintances) and external (professional and amateur hackers, nation-state actors and agencies, competitor corporations)
- Accidental human agents: Based on human error. Similar to intentional threats, this type can include internal and external agents.
- Negligence-based human agents: Based on careless behaviors or safety oversights. Again, this category can also include internal and external agents.
Vulnerabilities may be points of weakness where someone or something can be manipulated. Vulnerabilities can be considered a web threat and a concern that enables other threats. This area typically includes some form of human or technical weakness that can lead to penetration, misuse, or destruction of a system.
Threat outcomes may lead to disclosed private info, deceived users, disrupted computer system use, or seized access privileges. Web threats often result in, but are not limited to, causing:
- Reputation damage: Loss of trust from clients and partners, search engine blacklisting, humiliation, defamation, etc.
- Operations disruption: Operational downtime, access denial to web-based services such as blogs or message boards, etc.
- Theft: Financial, identity, sensitive consumer data, etc.
Cybercriminals will use almost any vulnerability within an operating system (OS) or an application to conduct an attack. However, most cybercriminals will develop web threats that deliberately target some of the most common operating systems/applications, including:
- Java: Because Java is installed on over 3 billion devices (that are running under various operating systems) exploits can be created to target specific Java vulnerabilities on several different platforms/operating systems.
- Adobe Reader: Although many attacks have targeted Adobe Reader, Adobe has implemented tools to protect the program against exploit activity. However, Adobe Reader is still a common target.
- Windows and Internet Explorer: Active exploits still target vulnerabilities that were detected as far back as 2010 – including MS10-042 in Windows Help and Support Center, and MS04-028, which is associated with incorrect handling of JPEG files.
- Android: Cybercriminals use exploits to gain root privileges. Then, they can achieve almost complete control over the targeted device.
How do internet web threats spread?
The most concerning internet threats travel the web to attack more systems. These threat agents often use a mix of human manipulation and technical commands to reach their targets.
Web threats of this nature use the internet's many communications channels to spread. Larger threats use the global internet to respond to threats, while more targeted threats may directly infiltrate private networks.
Typically, these threats are distributed through web-based services. Malicious actors prefer to place these threats in locations where users will often engage with them. Public websites, social media, web forums, and email are often ideal for spreading a web threat.
Users are affected when they engage with malicious URLs, downloads, or provide sensitive info to websites and message senders. This engagement may also trigger infection and spread of web threats to other users and networks. It’s not uncommon for innocent users to unknowingly become threat agents themselves .

How to spot web threats
Despite the unending scope of web-based dangers, it is possible to spot some general traits of web threats. However, spotting a web threat requires a vigilant eye to catch subtle details.
Some web threats are clearly of concern to web infrastructure hardware, such as water and heat. While those are easier to spot, others require careful attention. Any time you are browsing websites and receiving digital messages are when you should be most cautious.
Here are some tips to guide you:
- Grammar: Malicious actors may not always carefully craft their messages or web content when assembling an attack. Look for typos, odd punctuation, and unusual phrasing.
- URLs: Harmful links can be masked under decoy anchor text — the visible text that’s displayed. You can hover over a link to inspect its true destination.
- Poor quality images : The use of low-resolution or unofficial images may indicate a malicious webpage or message.
Types of web security threats
As mentioned previously, web threats typically include human and technical manipulation in order to attack. Be aware there tends to be overlap between web threats, and some may occur simultaneously. Some of the most common web threats may include the following.
Social engineering
Social engineering involves deceiving users to act unknowingly against their own best interests. These threats usually involve gaining the trust of users to deceive them. Manipulating users in this way can include:
- Phishing: Posing as legitimate institutions or people to get them to divulge personal details.
- Watering hole attacks: Exploiting popular websites to fool users into exposing themselves to harm.
- Network spoofing: Fraudulent access points that mimic legitimate ones.
Malicious code
Includes malware and harmful scripts (lines of computer programming commands) to create or exploit technical vulnerabilities. Where social engineering is the human side of web threats, malicious code is the technical side. These threats can include but are not limited to:
- Injection attacks: Insertion of harmful scripts into legitimate applications and websites. Examples include SQL injection and cross-site scripting (XSS).
- Botnet: Hijacking a user device for remote, automated use in a network of similar “zombies.” These are used to accelerate spam campaigns, malware attacks, and more.
- Spyware: Tracking programs that monitor user actions on a computer device. The most common examples are keyloggers.
- Computer worms: Scripts that run, replicate, and spread autonomously without the help of a related program.
Exploits are intentional abuses of vulnerabilities that may lead to an undesirable incident.
- Brute force attacks: Manual or automated attempts to breach security “gates” and vulnerabilities. This may typically involve generating all possible passwords to a private account.
- Spoofing: Masking a real identity to manipulate legitimate computer systems. Examples include IP spoofing, DNS spoofing, and cache poisoning.
Cybercrime refers to any unlawful activity conducted via computer systems. These threats often use the web to enact their plans.
- Cyberbullying: Mental abuse of victims using threats and harassment.
- Unauthorized data disclosure involves the release of private information, such as email leaks, intimate photos, and significant corporate data leaks.
- Cyber libel : Also known as online defamation, this can involve attacking individuals or organizations' reputations. This can be done through disinformation (deliberate distribution of inaccurate information) or misinformation (mistaken distribution of inaccurate information).
- Advanced Persistent Threats (APTs): Malicious actors gain access to a private network and establish ongoing access. They combine social engineering, malicious code, and other threats to exploit vulnerabilities and gain this access.
Typically, web threats refer to malware programs that can target you when you're using the internet. These browser-based threats include a range of malicious software programs that are designed to infect victims’ computers. The main tool behind such browser-based infections is the exploit pack – which gives cybercriminals a route to infecting computers that either:
- Do not have a security product installed
- Contain a commonly used operating system or application that is vulnerable – because the user hasn’t applied the latest updates, or a new patch has yet to be issued by the software vendor
Kaspersky’s Internet security experts have identified the most active malicious software programs involved in web threats. The list includes the following types of online threats:
- Malicious websites. Kaspersky identifies these websites by using cloud-based heuristic detection methods. Most malicious URL detections are for websites that contain exploits.
- Malicious scripts. Hackers inject malicious scripts into the code of legitimate websites that have had their security compromised. Such scripts are used to perform drive-by attacks – in which visitors to the website are unknowingly redirected to malicious online resources.
- Download and launch other malicious software programs
- Carry a payload that steals data from online banking and social network accounts or steals login and user account details for other services
- Trojan-Downloaders. These Trojan viruses deliver various malicious programs to users’ computers.
- Exploits and exploit packs. Exploits target vulnerabilities and try to evade the attention of Internet security software.
- Adware programs. Often, the adware will simultaneously install when a user starts to download a freeware or shareware program.
Examples of web threats
Among the many examples of web threats, here are some of the more well-known examples:
WannaCry ransomware
In May 2017, the WannaCry ransomware spread to many networks and locked down countless Windows PCs. This threat was particularly dangerous because of its worm functionality, allowing it to spread completely autonomously. WannaCry exploited a native communication language within Windows to spread this malicious code.
Celebrity iCloud phishing
A spear-phishing attack led to the breach of numerous celebrity iCloud accounts . This breach ultimately resulted in the unauthorized leak of countless private photos from these accounts.
While the attacker was eventually located and prosecuted, the victims are still suffering from their intimate photos being made public — without their permission. This has become one of the most well-known phishing attacks of the decade.
How to protect yourself against web threats
Most threats are successful due to two main weaknesses:
- Human error
- Technical error
Full protection from web threats means you will need to find ways to cover these weak points.
General tips to follow for both end-users and web service providers include:
- Always create backups : All valuable data should be copied and stored safely to prevent data loss in case of an incident. Websites, device drives, and even web servers can be backed up.
- Enable multi-factor authentication (MFA): MFA allows for additional layers of user authentication on top of traditional passwords. Organizations should enable this protection for users, while end-users should be sure to make use of it.
- Scan for malware: Regular scans for infections will keep your computer devices secured. Personal devices can all be covered through an antivirus solution like Kaspersky Total Security. Enterprise endpoint machines and computer networks should use this protection as well.
- Keep all tools, software, and OS up to date: Computer systems are more vulnerable when they’ve been unpatched against undiscovered holes in their programming. Software developers regularly probe for weaknesses and issue updates for this purpose. Protect yourself by downloading these updates.
Service providers like website owners and server operators are where true comprehensive security starts. These parties will need to take precautions for better protection. They can do this by:
- Monitoring web traffic to gauge for normal volumes and patterns.
- Implementing firewalls to filter and restrict unpermitted web connections.
- Network infrastructure distribution to decentralize data and services. This includes aspects like backups for various resources and geo server rotations.
- Internal probing to investigate for unpatched vulnerabilities. This might, for example, involve self-attacking with SQL injection attack tools.
- Proper security configuration for access rights and session management.
Users should protect themselves by doing the following:
- Scan downloads for malware.
- Vet links before clicking, only clicking links if you are positive the destination is safe and trusted.
- Make strong, secure passwords, and avoid duplicates. Use a secure Password Manager to help manage all of your accounts and passwords.
- Throttle login attempts by triggering account lockdown after a limited number of tries.
- Look out for phishing red flags in texts, email, and other communications.
Kaspersky Internet Security received two AV-TEST awards for the best performance & protection for an internet security product in 2021 . In all tests Kaspersky Internet Security showed outstanding performance and protection against cyberthreats.
Related Links:
- What are the different types of ransomware?
- How do computer viruses work?
- What is the difference between free antivirus software and paid antivirus software?
- How to detect spyware to safeguard your privacy
Featured Articles

HTML Attachments: A Gateway for Malware?

Understanding BlackCat ransomware: Threat overview and protective measures

Black Friday Scams: How to Shop Safely Online

What is a dark web scan?

How to protect yourself while on the Internet
There is a lot of wrong information, bad people, bad websites, and cybercrime on the Internet. Below are steps and suggestions everyone should follow to safeguard their computers and personal information while connected to the Internet, and protect themselves from computer crime.
The following information and precautions should be followed by all computer users, regardless of the computer or operating system used to reduce the risk of threats. If you shop online, send and receive e-mail, download files, or browse the Internet, keeping your computer and yourself safe and secure is important.
Verify data is encrypted

We also suggest making sure the URL (uniform resource locator) begins with https , as shown above.
While the lock is in the locked position, data is encrypted , which helps prevent anyone from understanding the data if it's intercepted. When no lock is visible or in the unlocked position, all information is plain text and could be read if intercepted. If a web page is not secure (e.g., an online forum), use a password you wouldn't use with protected sites like your online banking website, or for purchases made on a shopping website.
Use a safe password
Websites that store confidential data, such as an online bank site, need to use strong passwords . Also, we recommend you use a different password for each website that requires a login. If you need help remembering your passwords, consider using a password manager .
- What is a safe way to remember my passwords?
When available always enable two-factor authentication
Two-factor authentication adds additional protection by requiring an additional step in verifying a login. With two-factor authentication, after verifying your password, if the service does not recognize your computer, it sends your phone a text message with a verification code. If someone had your password but did not have your phone, even with a valid password, they cannot access your account.
Two-factor authentication should at the very least be enabled on your e-mail account. Most account passwords can be reset using the forgot password feature, which sends a new password or link to reset the password to the e-mail address on file. If anyone has access to your e-mail account, they could get the new password for your account.
Keep your operating system and software up-to-date
Many of the updates released by developers of operating systems are related to computer security-related issues. Make sure your operating system is always running the latest updates and is still supported by the developer. Older operating systems, like Microsoft Windows XP, are no longer supported by Microsoft and therefore no longer get updates.
Always be cautious of e-mail links and attachments
One of the most common methods of spreading viruses , malware , and ransomware is through e-mail attachments and hyperlinks sent through e-mail. Always be extremely cautious when dealing with any attachments or links in e-mails you've received from anyone (even friends and family).
- How does a computer get infected with a virus or spyware?
E-mail is not encrypted
Never transmit confidential data over e-mail , such as passwords, credit card information, etc. E-mail is not encrypted , and if intercepted by a third-party, it could be read.
Be aware of phishing scams

Familiarize yourself with phishing scams and techniques , which trick you into divulging your account information. Online banking sites, PayPal, eBay, Amazon, and other popular sites that require logins are popular targets for theft and other fraudulent activity.
It's also helpful to familiarize yourself and people who use your computer with other social engineering tactics.
Use caution when accepting or agreeing to prompts
When browsing, if you're prompted to install any program or add-on, make sure to read and understand the agreement before clicking the OK button. If you do not understand the agreement or feel it is not necessary to install the program, cancel or close the window.
Additionally, when installing any program, watch for any check box that asks if it's ok to install a third-party program, toolbar, etc. These are never required and often introduce threats. Leave these boxes unchecked.
Be cautious where you're logging in from
Your place of work can install key loggers or use other methods of monitoring the computer while online. Someone who has access to this information could read these logs and gather usernames and passwords. Also, do not store any passwords in your browser if your computer is shared with other co-workers.
Wireless network
When on a wireless network , realize that all information sent to and from your computer can be intercepted and read by someone nearby. Prevent this from happening by only logging onto a secure network using WEP (Wired Equivalent Privacy) or WPA (Wi-Fi Protected Access) (only use WEP if WPA is not available). If this is a home wireless network, make sure it is secure.
- How to secure your home wireless network router.
Friend's house
Be concerned when logging in to an account on a friend's computer. A computer or network you are not familiar with could intentionally or unintentionally log usernames and passwords. Finally, when logging into any site on a friend's computer, never save the password information on their browser.
Use an alternative browser

Older versions of Internet Explorer are notoriously insecure. If you are using Internet Explorer as your browser, consider an alternative browser such as Google Chrome or Mozilla Firefox . If you are running Windows 10 and want to continue to use a Microsoft browser, consider using Microsoft Edge instead of Internet Explorer.
Always think before you share something
Social networking sites like Facebook are a great place to connect with friends and family online. However, it is also very easy for people to over share personal information about themselves or others. Before sharing something on a social network or any place on the Internet, make sure it is something you wouldn't mind if everyone saw. Everything you share on the Internet should be thought of as public because it is possible for something you believe is shared privately to be leaked out publicly. If you're thinking about sharing something you think could offend someone or embarrass you, maybe consider not putting it on the Internet.
- What does Facebook know about me?
Be aware of those around you
While at work, school, library, or any public area with people around you that could look at your screen, be cautious of anyone shoulder surfing . Someone could watch you type in your password, which would give them access to your account.
If you need information displayed on the screen to remain private, consider a privacy filter for the display.
Watch out for fake support and fake products
When dealing with technical support or help with your computer make sure you're dealing with a legitimate company and not fake tech support . Also, when looking for security protection services, make sure you're downloading and installing legitimate software and not a fake antivirus .
Update Internet browser plugins
Often many attackers find security vulnerabilities through browser plugins , such as Adobe Flash . Make sure all installed Internet plug-ins are up-to-date .
Secure saved passwords
Make sure to store passwords and login information in a secure area. Never write login information on a sticky note or in a text file that is not encrypted.
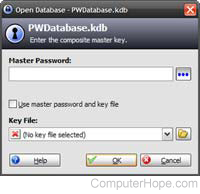
To save your passwords, we recommend using a password manager , which stores all login information and securely encrypts and password protects that information.
When saving password information in a browser, it may be visible to anyone who has access to your Internet browser. For example, without a master password setup in Firefox, anyone can see all stored passwords .
Protect yourself against malware, spyware, and viruses
Protect your computer from viruses by installing an antivirus program onto the computer. If you do not want to install antivirus protection and your computer is running a newer version of Windows, at least have Windows Defender running on the computer. Also, having a malware protection program, such as Malwarebytes , is also a good method of protecting your computer against malware and spyware .
Make backups of important data
There is no such thing as 100% computer security , which is why it's also important to make backups of important data. If something happened to your computer while it was on the Internet, having a backup prevents lost data.
- How to back up your computer.
Protect sensitive information in your home and office
Be cautious of sensitive information you may have around your computer and who might see that information. For example, if a cleaner cleans around your computer and they see a note containing your password and username, they could use that information.
Also, if you work in an area where others can see and use your computer, make sure to lock your computer any time you step away. A co-worker could access or see sensitive information and have complete control of an unlocked computer while you're away on a lunch or bathroom break.
Verify the checksum of downloaded files
If you've downloaded a program from a website that also lists a file checksum , make sure the checksum matches the file that you've downloaded. Verifying the checksum of a downloaded program helps confirm that the program you are installing is what you want to install.
- How to verify the checksum of an installer file.
Don't always trust what you read online
Realize that it's possible for anyone to create a website on the Internet and that someone may only be creating a site for malicious intentions. For example, a website could be created to help spread fear, lies, or malware .
Fake information and stories are also often spread through e-mail, e.g., through chainmail .
- How to know if a news story is fake news.
- How to know if an account is real or fake.
Related information
- How to prevent unauthorized computer access.
- How to set a browser to Incognito or private mode.
- How to default launch a browser in private or incognito mode.
- Protect children from harmful material and people on the Internet.
- Is online banking safe?
- How to protect my webcam from being hacked.
- How to know if a computer was hacked.
- Can I get a virus from Facebook or MySpace?
- How do I know what websites I can trust?
- How to be anonymous on the Internet.
- Anonymous alternatives to popular online services.
- Top 10 computer mistakes beginners make.
- Internet help and support.

Threat Assessment: School Threats, Social Media, Texting and Rumors
Study finds rapid escalation of violent school threats, schools face new wave of violent threats sent by social media and other electronic means, study says.
Bomb threats sent by Facebook. School shooting threats sent through international proxy servers. A death threat scribbled on a restroom wall that triggers texting rumors throughout the school community. Parents and media scrambling to your school doorsteps. What should a principal and superintendent do?
A nationwide epidemic of violent school threats is breeding fear, anxiety and frustration for educators, children and parents. While the vast majority of these threats are anonymous and turn out to be hoaxes, they have to be investigated and taken seriously. Hundreds of schools are losing classroom teaching time, police are wasting resources, children are frightened, and parents are angry and alarmed.
“School threats are a fast growing problem. They send fear and panic through a community” says Ken Trump, President of National School Safety and Security Services, who directed a new study of school threats across the country.
We reviewed 812 school threats across the country, from August 1 to December 31, 2014 – the first half of this school year. Based on available data, threats are up 158% since last year, when we did the first survey of this kind. This rapid escalation of school threats requires urgent attention.
Click here to learn more from our groundbreaking research of school threats.
Learn more about our new STAT – School Threat Assessment Training: Assessing and Managing School Threats workshop
Ken shares insights from our study of rapidly escalating violent school threats and what school leaders can do to prevent and manage them:
School Threats, School Violence Rumors and School Threat Assessment
One of the lasting lessons and legacies of the 1999 attack on Columbine High School, and subsequent school shootings, is that school and public safety officials must treat threats seriously. They must have protocols in place for assessing and managing threats to school safety.
School threat assessment is a gray area and administrators often find themselves walking a tightrope. Nine out of 10 threats may turn out to be unfounded, but no school administrator wants to be number 10.
Three common questions to begin assessing school threats:
- What is the motivation of the threat maker and credibility of the threat?
- Could the threat maker have the information on how to carry out the threat (such as information on how to make bombs or homemade weapons, for example)?
- Could the threat maker have access to the tools, and the capability to carry out the threat?
Today, we know the answers to questions two and three could easily be, “Yes.” Information on how to carry out many threats is easy to find on the Internet. The tools to carry out the threat can be as close as the local hardware, discount or other home supply store.
So educators and safety officials are often left focusing on the first question: What is the motivation of the threat maker and credibility of the threat? Unfortunately, this requires assessing human behavior and making a judgment call accordingly, which is not an easy task for even the most skilled criminologist, psychologist, psychiatrist or other student of human behavior.
The Importance of Making Cognitive, not Emotional, Responses to Threats
It is very understandable for school officials to make emotional decisions when faced with a threat to the safety of their children. However, it is at this time that cognitive, analytical decision-making must take over.
While school administrators may be emotionally tempted to quickly evacuate a school or close down schools, this may not be the most appropriate action, especially if the credibility of the threat is in question. Although we do not believe schools need “paralysis-by-analysis” guiding their decision-making process, we do believe that threat assessment protocols should be in place for a joint evaluation of threats by school officials working with law enforcement and other public safety officials.
It is critical that school officials follow emergency guidelines for managing bomb threats and other threats. Emergency guidelines help school leaders make cognitive decisions focused on the facts of the actual threat at hand. Such plans should be developed through a collaborative process with first responders and community partners. They should train staff thoroughly and practice, at a minimum, with tabletop exercises.
Schools should also develop separate crisis communications plans for getting out accurate information in a timely manner to parents, the media, and the broader community when rumors and threats occur. Given the viral nature of social media and text messaging, schools do not have the luxury of developing strategy during a crisis. School leaders should discuss these types of situations and have a crisis communications plan in place well ahead of an actual incident.
School Threat Assessment: Predicting Student and Youth Behavior
The good news is that school and police officials are getting much better at preventing high-profile tragedies. The bad news is that we will never be 100% successful because we are dealing with human behavior.
Adult behavior is difficult to predict and no one can do it with 100% certainty. Youth behavior is even more difficult to predict. Adolescent behavior is, by its nature, experimental and fluctuating.
In reviewing high-profile school shootings, we have made a number of observations:
- Adults tend to recognize radical, dramatic changes in youth behavior. However, adults continue to have difficulty in recognizing smaller, incremental changes in youth behavior.
- Early intervention to prevent violent incidents is complicated further because so many people have pieces of information about a child. The pieces are rarely put together to get the whole picture until after a crisis occurs.
- The majority of high-profile school shootings and other types of violence do not occur spontaneously. Most involve some kind of prior planning. They typically stem from the culmination of a series of deteriorating events experienced by the offender. The resulting violence often reflects an “end of road” action by the offender.
School Threat Assessment and Threat Management Basic Principles
The team at National School Safety and Security Services has more than 30 years of experience in addressing student and adult threats in school settings. We address these issues in-depth in our school safety, security, and crisis preparedness training programs .
What should I do if I find a “hit list” in a student’s possession? How should we deal with the kid who says he plans to kill other students and staff? How should we confront a situation when a kid says, “I’ll kill you,” to another student or staff?
While each school district and school should have its own threat assessment teams and school threat protocols, some basic guiding principals include:
- Treat all threats seriously.
- Investigate the incident promptly and efficiently.
- Use support staff and external resources as a part of a multidisciplinary threat assessment team to evaluate threats.
- Take appropriate disciplinary and criminal enforcement steps.
- Document the threats and actions taken.
- Enhance security measures, as appropriate, to insure the safety of all students, staff, and facilities.
It is important for school personnel to establish a threat assessment protocol to insure consistency and thoroughness in evaluating and responding to student and adult-originated threats. We believe that threat assessment involves analyzing the behavior process of the person making the threat, rather than using a “profile” checklist of specific characteristics as criteria.
A variety of questions focusing on the motivation, context, and other factors of the threat must be asked in each threat case. We recommend that educators know:
- What questions should be asked of witnesses? Victims? Suspects?
- Who should be involved in the assessment process?
- What questions should be asked in the assessment process?
- Which teachers and staff are in the best positions to detect early warning indicators of such threats?
Many experts are quick to point out that acts of violence, such as bombings, have occurred in our society without any threat or warning at all. The presence of a threat does not guarantee violence, nor does the absence of a threat guarantee that nothing will occur.
Very generally speaking, the general rule of thumb when assessing the credibility of threats focuses on the detail and specificity of the threat, and the behavioral actions toward planning and carrying out the threat. The more detailed and specific the threat, the more credible it may be. The more evidence of planning (hit lists, maps, specific times and locations documented, etc.) and action steps to carry out the threat (stockpiling of weapons, creation of suicide notes or videos, etc.), the more credibility given to the threat.
Assessing school-based threats is different from investigating threats against the President, for example. Unlike most law enforcement or military-type threat assessments, in schools we are dealing with kids. The key is striking a balance between the “kids will be kids” mentality of ignoring threats, or having teams of secret agents with dark glasses and trench coats following kids around. Schools are unique and there are school-specific recommendations for answering these and related questions.
The School Psychological Perspective on School Closing Due to Threats and Rumors
Dr. Scott Poland, Professor at the Center for Psychological Studies at Nova University, and an internationally recognized expert in school violence and school psychology, has expressed concern about the closing of schools too quickly during times of vague threats and rumors. Dr. Poland notes that it is widely known that K-12 school students often are unsupervised or less supervised when at home during the workday than when they are in school. He has also written about the importance of continuity of the educational process for maintaining “normalcy” for children.
Dr. Poland told the Chicago Tribune in April 2008 that schools should close as a last resort.
He said, “We shouldn’t close schools every time there is a threat of violence. In fact, in most instances, say of a bomb threat or something, you deal with the issue but then return to the operation of the school.”
Additional thoughts provided by Dr. Poland to National School Safety and Security Services:
“We need to remember that many threats of violence at school are made with the intent of disrupting education. The number of threats at schools often increases in the spring due to awareness of the anniversary of Columbine and other high profile tragedies. Students who have been bullied or harassed at school and who have experienced an unsuccessful school year may be especially frustrated and angry by the spring.
“School safety is an “inside job” and it is important to have all students involved in their own safety through classroom discussions and student participation on school safety task forces. There is also no substitute for knowing students and knowing them well. School personnel are encouraged to develop positive relationships with all students and if a threat is made the increased visibility of school staff and police at school will go a long way to alleviate both student and parent concerns about school safety.”
Dr. Poland’s advice reinforces the importance of schools having threat assessment protocols in place and having advance discussions among school and public safety officials about how they will respond if they face threats and rumors of school violence.
How School Leaders Can Communicate on School Safety in a World on Digital Steroids
“Social media that spread rumors like wildfire must be countered by school officials who have a solid crisis communications plan for managing rapidly escalating rumors around school safety issues,” said Ken Trump, President of National School Safety and Security Services. Trump says there are three critical communications components to countering fast moving rumors and school violence threats:
- Accurate – While there is growing pressure on school officials to release information quickly in a crisis or in periods of high rumors, accuracy is the most important factor. Whatever information school officials release must be accurate to the best of their knowledge at the time is it released
- Timely – Release information in a timely manner at the on-set of the rumors with periodic updates as necessary and appropriate
- Redundant in dissemination – Educators and safety officials must send the same information out on all school channels, including parent alert systems, social media, text messaging, school website, letters sent home and mass media. Not all parents and people in the community get their information from the same source. See recommendation #3 below for specific examples.
Recommendations to help school and safety officials manage vague threats, text message rumors of school violence and the rapid spread of fear include:
- Anticipate you will have an issue that accelerates like wildfire at some time in your school. Identify ahead of time what strategies you will use to counter it.
- Have redundancy in communications: Web site, direct communications to students and staff, mass parent notifications, letters to go home, etc. Messages from school officials must be put out in a timely and accurate manner with appropriate updates as incidents unfold.
- Discuss some potential scenarios with your district and building administrators and crisis teams to evaluate what the threshold will be for going full speed on your communications. If you go full speed on every single rumor, you might need two full-time employees just to counter rumors in one average secondary school. Try to get a feel for when a situation might rise to the level of being so disruptive or distracting that it warrants a full-fledged communications counter assault.
- School and police officials should have unified communications so as to send consistent messages. We train in our emergency preparedness programs for the use of joint information centers (JICs) in a major critical incident response. But even on lower scale incidents, it is important for school leaders to be sending a message consistent with that of public safety officials.
- Have a formal crisis communications plan and professionally train your administrators and crisis team members on communicating effectively with media and parents. Professional communications consultants and district communications staff (for those with such in-house resources) can help develop and audit crisis communications plans and train staff.
- School leaders should review their board policies, student handbooks and discipline policies to make sure they have solid legal and administrative provisions for disciplinary action to address students who make threats, or send text messages that are disruptive to the educational process. School administrators and boards should have proactive discussions about the firm, fair and consistent enforcement of these rules if and when incidents arise.
- Educate students about their role and behavioral expectations related to preventing and reporting rumors and threats of violence, as well as cell phone and text messaging use, especially during an emergency. Students need to know that responsible behavior is expected of them, that consequences will occur for inappropriate behavior, and that starting, spreading and fueling rumors are serious offenses that jeopardize school safety.
- Discuss with teachers the importance of heightened awareness and monitoring student use of cell phones and texting in classrooms and school common areas. Procedures should be in place for teachers to notify school administrators and security personnel of misuse and abuse. Administrators should be prepared to enforce disciplinary rules firmly, fairly and consistently.
- Communicate with your parents proactively and in advance about how your district will address rumors, threats and other school violence concerns. Parents and others in the school community must be told ahead of time that school officials have plans in place to respond to rumors, investigate them, administer disciplinary consequences. Parents also need to know that, when necessary, you will call police to investigate threats, make arrests and heighten security.
- Consider how your security and preparedness technology can be used in times of rumors and threats. Can your surveillance cameras be used to monitor hallways to help identify persons going in and out of restrooms where threats have been written on bathroom walls? One school reportedly used their cameras to identify students in the hallways who were using cell phones to record fights in the hallways. After dealing with the actual fight incident, administrators went back to the cameras and followed up with disciplinary action against those recording the fights, against school rules banning cell phones in school.
Historical Look at Increased School Threats, Text Messaging Violence Rumors and School Closings
National School Safety and Security Services is tracking more and more school incidents across the nation where rumors have disrupted schools and have resulted in dramatic declines in school attendance and even school closures. The issues of text messaging in particular, and cell phones in general, were credited with often creating more anxiety and panic than any actual threats or incidents that may have triggered the rumors.
“We are now dealing with ‘Generation Text’,” said Ken Trump, President of National School Safety and Security Services. “The rumors typically become greater than the issue, problem, or incident itself. Rumors fly in minutes, not hours, attendance can drop dramatically overnight and some school officials seem increasingly quick to shut down schools,” he noted.
Following the Columbine High School attack on April 20, 1999, each subsequent year has brought a heightened sensitivity to threats, plots and rumors in many schools leading up to the anniversary date. It is not uncommon to see a spike in threats, foiled plots, and rumors of violence, especially during the months of March and April.
We detail the issue of school threats in 2013-2014 with our study of more 300 violent threats to schools which found more than 1/3 of the threats delivered by social media and other electronic forms
Additional School Threat Assessment Resources
See a related story on school threats and cell phones in USA Today.
Also visit our page on Early Warning Signs of Youth Violence for related information.
For more information on this topic and our training programs on assessing and managing threats, email Ken Trump .
Subscribe to our newsletter...
...and have blog posts delivered straight to your inbox:
Ken Trump’s Blog
- School security is being sold to the highest bidders. Private equity and venture capital investors are hijacking the school safety field. Will a passion for profits overshadow a passion for school safety?
- If the school safety presenter at your conference is paid for by a security vendor, will their message be truly independent? School leaders in the audience need to look behind the curtains to learn about the potential wizards in the wings
- Exposed emails show a leading AI weapons detection system missed its own test gun “a few times with the cameras rolling” during a media demo in a school district that signed $11 million contract for their systems. But the local news report did not show it missing a gun. Are parents being left in the dark?
- Cell phones and school safety: They are often disruptive to the educational process and can create unsafe conditions in an emergency. Yet many students and parents want them. Now, some politicians want to ban their use in schools.
- Superintendents, principals and other school leaders share a common struggle: How to communicate with parents about school safety. The good news is we can help them to communicate better.

June 04, 2024
Share this page
How to prevent online identity theft
Life online is more common than ever. It’s where we do our banking and schoolwork, find entertainment, and connect with friends. And it's a convenient, safe way to do things—until it's not. Most online activities require using personal information to create, log into, and manage digital accounts, which can leave you vulnerable to internet identity theft.
The good news is it's easy to take precautions to prevent online identity theft with security-protection tools like those in Microsoft Edge .
What is identity theft, and how do you recognize it?
When someone gains access to your financial or personal information—from email logins to bank accounts—without your permission, it's called identity theft.
Hackers and thieves are sneaky, so you may not immediately know if you've been affected by identity theft. Warning signs may include:
- Unexpected charges to your bank account
- Errors on your credit report
- Getting locked out of your online accounts
- Having your tax return rejected
- Receiving calls from debt collectors
Strengthen online safety with password management tools
A good first step to keeping your online presence safe is managing your passwords. By regularly identifying potential password-related security risks, you can avoid issues that may occur.
Any list of password dos and don'ts will tell you that using the same password for multiple accounts is a big no-no. Why? Simply put, if a hacker gets into one of those accounts, they can get into all of them. Password Health can check if you're using the same password and if it might be weak, vulnerable, leaked, or reused by bad actors. Another great tool is Password Monitor , which checks if any saved passwords have been part of a data breach that could affect you and your personal or financial information every time a username-password combination is used (saved or auto-filled). If one or both signal an issue, you should change your passwords ASAP.
Create safe, secure passwords with Password Generator
With so many passwords across online accounts, it's hard to remember them all and come up with new ones. That's where Password generator can help. This tool will help you create, remember, and autofill your passwords across all the devices you're signed into and syncing with your Microsoft Edge account.
Protect your online identity with Microsoft Defender SmartScreen
Another way to prevent online identity theft is to avoid malicious websites, links, and downloads that can compromise your personal information. Microsoft Defender SmartScreen is a built-in Microsoft Edge feature that helps you stay safe online by warning you about potentially harmful sites and files. It also checks the reputation of websites and downloads, blocks them if they are known to be unsafe, and alerts you if it detects anything suspicious.
Want more protection? If you’re a Microsoft 365 Personal or Family subscriber, you get exclusive access to an all-in-one, easy-to-use security app that helps protect online identities (US only), data, and devices from online threats. Learn more .
Stay safer and more secure online with Microsoft Edge
With these tools and features from Microsoft Edge , you can help prevent online identity theft and enjoy a safer, more secure browsing experience. That way, you can worry less about how to avoid identity theft online and spend more time enjoying what matters most.
Try Microsoft Edge to enjoy these built-in identity theft protections today.
Products featured in this article
Microsoft Edge
Microsoft edge app.

Microsoft Defender SmartScreen
More articles.

What is a password manager?
Learn about the benefits of using a password manager and how you can get started with one.

What are the most common threats to your online security?
Learn to defend yourself from attacks using Microsoft Edge and its latest defense software.

Is it safe to store your credit card in Microsoft Edge?
Microsoft Edge encrypts your credit card data to store your information safer.
- Share full article
For more audio journalism and storytelling, download New York Times Audio , a new iOS app available for news subscribers.
The Government Takes On Ticketmaster
Explaining a case that could reshape the multibillion-dollar live entertainment industry..
This transcript was created using speech recognition software. While it has been reviewed by human transcribers, it may contain errors. Please review the episode audio before quoting from this transcript and email [email protected] with any questions.
Hi, everybody, it’s Sabrina. Before we start today, we wanted to invite you to something special. The Tribeca Festival is starting a brand new annual gala to celebrate excellence in audio. For this, the inaugural year, they’ve chosen to celebrate “The Daily.” We know you, our incredible audience, live all over the world, but we’d like to invite you to join us.
The gala is in New York, on June 9, at 5:00 pm. You can get all the details and buy tickets at tribecafil.com/thedaily. That’s tribecafilm.com/thedaily. I’ll be there, Michael too, along with a bunch of us from the show. Mo Rocca is going to host it. So if you’re in the area or you’re visiting, we’d love to see you there. OK, on with today’s show. From “The New York Times,” I’m Sabrina Tavernise. And this is “The Daily.”
I have got a bone to pick, as usual, with Ticketmaster.
The biggest problem that I have right now is not getting tickets to the Era Tour.
Loading, loading, loading. Want them so bad. Want them so bad. Want them so bad. Nope.
I looked at my account and the tickets are gone.
Over the past few years, few companies have provoked as much anger —
I cannot afford $1,500 tickets.
— among music fans.
Oh, my god.
— as Ticketmaster.
I literally hate Ticketmaster. Like, there is no company I think I hate more than Ticketmaster.
Ticketmaster ought to look in the mirror and say, I’m the problem. It’s me.
Last week, the Department of Justice announced it was taking the company to court. Today, my colleague David McCabe, on how the government’s case could reshape America’s multi-billion dollar live music industry.
It’s Thursday, May 30.
So, David, good to have you back. You have become a beloved guest at “The Daily,” because the government keeps bringing these huge antitrust cases and we keep turning to you to explain them.
Well, it’s a pleasure to be back. And today I have a question for you, which is, what was the first concert you ever went to?
Oh, my gosh. The first concert I ever went to? Oh, my god, I think it was Van Halen in the 1980s, which maybe is before you were born.
You know, no comment, but that’s a pretty good first concert.
And the case that we’re here to talk about today is actually all about shows like a Van Halen concert in 1980.
OK, I’m ready. So let’s get into it. This case, as you and I both know, is about Ticketmaster. So tell us about this case.
So anyone who attends concerts regularly or even irregularly probably knows about Ticketmaster. It’s kind of the ubiquitous digital box office. And those people are probably also familiar with the ubiquitous fan complaints about Ticketmaster — that the company puts high fees that they don’t entirely explain onto tickets, that tickets will sell out really fast during these sort of frantic pre-sales for tours, and that the website doesn’t always work very well.
And probably the most infamous Ticketmaster incident in recent memory was a couple of years ago when the pre-sale began for Taylor Swift’s massive Eras Tour. And fans got locked out, couldn’t get tickets and were absolutely furious. And it really put in the spotlight the power of this company over the ability to buy a ticket to a live music event.
So the DOJ is pointing the finger at this company for all this consumer angst at Ticketmaster.
Well, and when you say this company, it’s not just Ticketmaster. It’s the company that owns Ticketmaster, a company called Live Nation Entertainment. We’ll say Live Nation for short. And it’s a giant company. And to think about just how gigantic and how expansive Live Nation is, I think it’s helpful to think about the fan experience of going to a concert.
[MUSIC PLAYING]
It starts with buying a ticket. And maybe you buy a group of tickets for you and your friends. And then one of your friends can’t make it. They’ve got other plans. You resell their tickets so you can make your money back. And then the day of the show you go, it’s this big production. It’s at a venue. Someone has booked the artist to appear. You go, you buy a beer, you have a good time.
Live Nation is involved in many parts of that process, and that starts with being a major concert promoter. They’re the one putting it on, arranging the event. They’re also selling the tickets through Ticketmaster. Sometimes they’re also involved in reselling the tickets when your friend can’t make it.
And not only that, they actually sometimes manage the artists. And they own or operate the venues where the show is happening. So even down to that beer you’re drinking to enjoy with the show, they might be involved in picking the person who sells that beer to you.
So, basically, they’re everywhere.
They’re everywhere. And the Justice Department says that’s a big part of the problem, that its power is bad for fans.
Good morning. Earlier today, the Department of Justice —
And we really heard that come through at the press conference last week that the Justice Department held to announce this case —
People always remember the first time that they were transformed by live music.
— where Merrick Garland, the Attorney General, really personalized this issue.
I still remember, as a senior in college, going to a Bonnie Raitt concert and seeing a —
He told this story about going to a Bonnie Raitt concert in college.
Merrick Garland did?
Yeah, Merrick Garland did.
I don’t think of Merrick Garland and Bonnie Raitt together in the same sentence.
Well, apparently, in college he attended a Bonnie Raitt show. And the thing he highlighted was that the opener was a young Bruce Springsteen.
We all knew that we had just seen the future of rock and roll.
And in that story, the attorney general seems to be getting at two important threads of this case. The first is that concerts are formative for the people who attend them. And the second is that concerts are an important way that artists reach their fans. That young Bruce Springsteen went on to now be one of the biggest touring artists in the world.
The Justice Department filed this lawsuit on behalf of fans who should be able to go to concerts without a monopoly standing in their way. We have filed this lawsuit on behalf of artists who should be able —
And so the Justice Department is responding here to a feeling that Live Nation, this giant company, has become a gatekeeper for both artists and fans. And that has allowed it to pay artists less sometimes, but also charge fans those fees that they’re so mad about.
It is time for fans and artists to stop paying the price for Live Nation’s monopoly. Thank you.
So help us understand how things have gotten to this point, where Live Nation is so powerful that the DOJ feels the need to sue them.
Well, this company has a long history of tangling with the Justice Department. And that really starts in 2009, when Live Nation and Ticketmaster announced that they were going to merge. And this merger, this big corporate deal, will marry Live Nation’s concert promotion business, the business of putting on shows, with Ticketmaster’s experience as an online ticketing platform.
And the Justice Department — a big part of its job is looking at corporate mergers to figure out if they will substantially lessen competition in the economy. So the Justice Department reviews this merger, and in 2010 decides we will let this merger go through. But we do have some concerns that it might reduce competition in the industry of ticketing. And so we’re going to reach a legal settlement with Live Nation and Ticketmaster that puts conditions on the deal, that requires the company to sell some assets to kind of lessen its footprint. And so the merger goes through. And that creates the sort of modern day Live Nation, Ticketmaster combination.
So the government ultimately actually just lets it happen.
That’s right. They put conditions on the merger, but ultimately they let it go through. And the company continues to tangle with the Justice Department over the next 15 or so years. But mostly they keep getting bigger. They keep growing their footprint across this ecosystem that creates some of the biggest concert tours in the country.
So just how big has the company actually become? Give me some numbers.
Well, let’s start here. Every year, they sell about 600 million tickets.
600 million tickets? That’s more than the number of people in the United States of America.
Yeah. And that is a global number, but it’s a lot of tickets. Right? The Department of Justice estimates that in the United states, Live Nation controls about percent of ticketing to major venue concerts.
So that’s a big percentage. They also own or control, like, in excess of 250 venues, including a big percentage, the Justice Department says, of major amphitheaters, the kind of big outdoor concert venues that are ultimately kind of in between a nightclub and the size of a big football stadium. And they manage hundreds of artists. They have this direct relationship with artists. And so this company is wide and it is deep into this industry.
So ultimately, the Justice Department says that — and I’m going to quote here — it’s the, quote, “gatekeeper for delivery of nearly all live music in America today.”
OK, it’s big. But as we know from other DOJ cases — and this is something that you have taught me, David — the cases against Apple and Google, just being big is not in and of itself a problem.
That’s right. Where companies run afoul of the law is when they use their power as a monopoly against their competitors in order to stay powerful or get more powerful.
And the Justice Department says that Live Nation has built a complex machine to do just that.
We’ll be right back.
So what does the DOJ say that Live Nation is able to do because it is so big? How does it use its bigness?
So the most prominent allegation is that Live Nation uses its power as a concert promoter to entrench its power in ticketing. As a reminder, when you put together a concert, a promoter works with an artist to book the show. They book the show at a venue. And that venue, for all of its shows, has to choose a ticketing provider, a digital box office where people can buy their way into the shows.
And what the Justice Department is arguing here is that Live Nation is able to wield its big artists, the tours that it promotes, as a cudgel to force venues to use Ticketmaster, its ticketing service. So the Justice Department says that in an instance in which a venue switched away from using Ticketmaster, that Live Nation routed tours around that venue, which of course means less money for that venue and a problem for their business.
Interesting. So basically, Live Nation is saying, look, if you want Taylor Swift in your little amphitheater over there, you’re going to have to use Ticketmaster. It’s Ticketmaster or no Taylor Swift.
That is effectively the behavior the Justice Department is arguing has happened here. They’re saying that Live Nation does this in veiled ways and that, more importantly, it’s really understood by venues throughout the industry that if you don’t use Ticketmaster, that you really risk out on losing important Live Nation managed tours. And then once these venues do choose Ticketmaster, Live Nation locks them into these long, exclusive ticketing contracts, which can last for as long as 14 years.
14 years? That’s pretty long. What else is DOJ alleging that Live Nation has done?
Another thing the Justice Department says that Live Nation does is use its power as an owner of venues to get away with paying artists less money for their tours.
So how does that work?
Basically, the argument is that because Live Nation controls so many of certain types of venues, that there are instances in which an artist’s tour might largely be dominated by Live Nation owned venues. And the Justice Department is saying that Live Nation knows that artists don’t have a lot of other options for where to play their concerts and, as a result, is able to pay those artists less. Because there’s not competitive pressure when they’re booking those tours.
That seems pretty unfair to artists who would really benefit from other venues owned by other people competing for them.
And that’s exactly what the Justice Department is saying, that artists lose out, not just fans. And there’s a striking story in the complaint that I think crystallizes how the Justice Department sees these streams of power coming together.
And it concerns a concert, which the lawsuit doesn’t name, in 2021. My colleague Ben Sisario has reported that it was a Kanye West concert featuring Drake. It was a benefit show, and it was taking place at the LA Coliseum in Los Angeles.
One of the companies involved in putting on this show was a firm called TEG. They do promotion and ticketing of the kind that Live Nation does. And the government says that Live Nation saw this as a threat, that they saw this company TEG involved in this show, and they were worried about what it would mean for them, and that they then undertook steps to put pressure on TEG and make their life difficult in a couple of ways.
The first was that TEG had reached a deal to sell some tickets, according to the complaint, through StubHub. StubHub is a secondary resale market. You can buy tickets to shows when people aren’t going to use them.
Right, and competitor to Ticketmaster, right?
And competitor to Ticketmaster. And the Justice Department says that Live Nation found out about that and said, well, we have the exclusive ticketing contract for this venue. And so we will make sure that if you bought your ticket on StubHub, you won’t be allowed to come in to this show.
Really? Like, they couldn’t come into the concert?
Well, and ultimately, the complaint says that StubHub had to work with Ticketmaster to fulfill the tickets that had already been sold, that they stopped selling new tickets, and that hundreds of people who bought their tickets on StubHub didn’t get into the show.
That seems very unfair. Like, they bought a ticket.
Well, and according to the Justice Department, it didn’t stop there, that Live Nation used its industry connections to pressure an investor in TEG, this company that it viewed as a threat, and that it pushed that investor to pull back from its relationship with TEG, which obviously would have weakened this potential competitor.
So these are very strong armed tactics. What is the DOJ saying is the result of all of this? What does all of this amount to?
It says that all of this adds up to higher fees for consumers and a worse product, a worse quality ticketing experience when fans go to buy. Because Live Nation doesn’t have to compete with anyone. It doesn’t have to innovate in response to competitors. So, among other things, the Justice Department wants to break this company up, at the very least by separating Ticketmaster, the ticketing unit, the box office unit, from the rest of Live Nation that does all these other things — promotes concerts, owns venues, et cetera.
So in other words, go back to the way it was in the beginning.
Yeah, or as much as you can.
And why does that fix the problem?
Well, the Justice Department doesn’t say a lot on this point. But it’s clear that what they want to do with this lawsuit is disrupt this cycle where Live Nation’s power reinforces itself again, and again, and again.
And what does Live Nation say in response? I imagine they disagree with all of this.
They do. They’ve said a lot. And they start out by saying something that will be familiar to you, because other companies that have been accused of antitrust violations say it as well, which is that they don’t fit the profile of a monopoly, that their overall profit margins are lower than those of companies like Meta, or Apple, or Google, and that even if you look at Ticketmaster specifically, they take a smaller percentage of every sale than a lot of other digital platforms. So they say basically the numbers show that we don’t have the kind of power you would normally associate with a monopoly.
And then they say, listen, we know that there are things that fans don’t like about the ticketing experience. There may be fixes to those. But largely, it’s not Live Nation’s fault, they say. They say that artists generally set the prices they want people to pay for tickets.
Really? So artists themselves do it.
Right, that artists sign off on how much a ticket will cost to their shows.
And they also say that demand sometimes drives ticket prices up. If there are more people who want to see a show than there are seats or standing room to see that show, the prices will be higher. And finally, they say that there’s this kind of pernicious outside force of scalpers, people who resell tickets, that use bots to hoover up way more tickets than they could possibly use and then resell them at a higher price. And so they say that all of these things may contribute to a fan experience that people don’t like, but that it’s not necessarily Live Nation’s fault.
I mean, to me, this makes certain sense. I guess if you think of a Taylor Swift show and lots of people trying to buy tickets, one reason why those tickets are expensive is not necessarily because there’s something nefarious going on, but because lots of people want to buy tickets. And there’s a market, and supply and demand has a role here.
Well, and a clear question here that I have, that other people have asked, is how much does the Justice Department think ticket prices have gone up because of this alleged Live Nation monopoly? And the Justice Department hasn’t answered that question.
They haven’t disentangled it with all of the other stuff that’s around — market forces, everything?
That’s right. And there’s another element of Live Nation’s response that we should mention, which is that the company basically says this lawsuit is politically motivated, that this administration, the Biden administration, is bringing lawsuits that don’t hold a lot of water but are anti-business. That’s what Live Nation is saying.
I mean, it does sort of ring true in some sense. Right? This has been the tilt of this administration toward cracking down on big companies. The DOJ has changed in this respect. They’re filing a lawsuit to break up a merger that a previous DOJ had actually approved.
Well, you’re right. This Department of Justice, this administration more broadly, has a different view about antitrust. They think that antitrust law can be a more expansive tool to address problems in the economy. And they’ve put that into practice. They’ve sued Google for violating anti-monopoly laws. They’ve sued Apple for violating anti-monopoly laws.
But I think ultimately what they believe is that they’re responding to a change in the economy, that these companies have gotten much bigger, that they have gotten more powerful. And they are responding to the way the companies broke the law on their way to becoming that big.
So, David, when you and I talked about Google and Apple — you referenced them here — you know, we talked about how there were broad repercussions for the future on American society. What would you say the implications are in this case?
This case ultimately, for the Justice Department, is about the market for culture and creativity. You know, a few years ago, the Justice Department successfully blocked Penguin Random House, a big publisher, from buying Simon and Schuster, another publisher. And they said that one problem with this merger was that it would reduce how much authors got paid, and that it would create a market where fewer books and fewer types of stories broke through.
This Justice Department is embracing an idea that the more concentrated the economy gets, the more it stifles creative expression, the ability of artists to make art and get it to the public and the ability of the public to consume it. And that, they say, is a central question of democracy. Because things like music are how we talk about big social issues or big political issues. So that is, they say, what’s at the heart of this case, that it is not just about the fees, it’s not just about how much an artist gets paid. But it’s about whether or not there is a fair marketplace for ideas, and whether or not consumers are able to access it.
David, thank you.
Thank you. [MUSIC PLAYING]
Here’s what else you should know today. On Wednesday, Supreme Court Justice Samuel Alito declined to recuse himself from two cases arising from the January 6, 2021, attack on the Capitol after “The Times” reported that flags displayed outside his houses appeared to support the Stop the Steal movement. In letters to Democratic members of Congress who had demanded his recusal, Justice Alito said that the flags, at his home in Virginia and a beach house in New Jersey, were flown by his wife, Martha Ann, and that he had had nothing to do with it.
And a group of 12 New York jurors deliberated for more than four hours in the final stretch of the criminal trial of Donald Trump, in which the former president is accused of falsifying business records. The jurors asked for portions of the testimony from two witnesses to be read back to them, as well as the judge’s instructions. They were then dismissed for the day and will resume deliberations today.
Today’s episode was produced by Will Reid, Rob Szypko and Rachelle Bonja. It was edited by Michael Benoit and Brendan Klinkenberg, contains original music by Marion Lozano, Dan Powell, and Will Reid, and was engineered by Alyssa Moxley. Our theme music is by Jim Brunberg and Ben Landsverk of Wonderly.
That’s it for “The Daily.” I’m Sabrina Tavernise. See you tomorrow.

- June 4, 2024 • 29:17 A Conversation With President Zelensky
- June 3, 2024 • 32:07 How Trump’s Conviction Could Reshape the Election
- May 31, 2024 • 31:29 Guilty
- May 30, 2024 • 25:21 The Government Takes On Ticketmaster
- May 29, 2024 • 29:46 The Closing Arguments in the Trump Trial
- May 28, 2024 • 25:56 The Alitos and Their Flags
- May 24, 2024 • 25:18 Whales Have an Alphabet
- May 23, 2024 • 34:24 I.C.C. Prosecutor Requests Warrants for Israeli and Hamas Leaders
- May 22, 2024 • 23:20 Biden’s Open War on Hidden Fees
- May 21, 2024 • 24:14 The Crypto Comeback
- May 20, 2024 • 31:51 Was the 401(k) a Mistake?
- May 19, 2024 • 33:23 The Sunday Read: ‘Why Did This Guy Put a Song About Me on Spotify?’
Hosted by Sabrina Tavernise
Featuring David McCabe
Produced by Will Reid , Rob Szypko and Rachelle Bonja
Edited by Brendan Klinkenberg and Michael Benoist
Original music by Marion Lozano , Dan Powell and Will Reid
Engineered by Alyssa Moxley
Listen and follow The Daily Apple Podcasts | Spotify | Amazon Music | YouTube
Over recent years, few companies have provoked more anger among music fans than Ticketmaster. Last week, the Department of Justice announced it was taking the business to court.
David McCabe, who covers technology policy for The Times, explains how the case could reshape America’s multibillion-dollar live music industry.
On today’s episode

David McCabe , a technology policy correspondent for The New York Times.

Background reading
The government is accusing Ticketmaster’s corporate parent, Live Nation Entertainment, of violating antitrust laws .
Here’s a guide to the emails at the heart of the government’s case .
There are a lot of ways to listen to The Daily. Here’s how.
We aim to make transcripts available the next workday after an episode’s publication. You can find them at the top of the page.
The Daily is made by Rachel Quester, Lynsea Garrison, Clare Toeniskoetter, Paige Cowett, Michael Simon Johnson, Brad Fisher, Chris Wood, Jessica Cheung, Stella Tan, Alexandra Leigh Young, Lisa Chow, Eric Krupke, Marc Georges, Luke Vander Ploeg, M.J. Davis Lin, Dan Powell, Sydney Harper, Mike Benoist, Liz O. Baylen, Asthaa Chaturvedi, Rachelle Bonja, Diana Nguyen, Marion Lozano, Corey Schreppel, Rob Szypko, Elisheba Ittoop, Mooj Zadie, Patricia Willens, Rowan Niemisto, Jody Becker, Rikki Novetsky, John Ketchum, Nina Feldman, Will Reid, Carlos Prieto, Ben Calhoun, Susan Lee, Lexie Diao, Mary Wilson, Alex Stern, Sophia Lanman, Shannon Lin, Diane Wong, Devon Taylor, Alyssa Moxley, Summer Thomad, Olivia Natt, Daniel Ramirez and Brendan Klinkenberg.
Our theme music is by Jim Brunberg and Ben Landsverk of Wonderly. Special thanks to Sam Dolnick, Paula Szuchman, Lisa Tobin, Larissa Anderson, Julia Simon, Sofia Milan, Mahima Chablani, Elizabeth Davis-Moorer, Jeffrey Miranda, Renan Borelli, Maddy Masiello, Isabella Anderson, Nina Lassam and Nick Pitman.
David McCabe covers tech policy. He joined The Times from Axios in 2019. More about David McCabe
Advertisement

COMMENTS
In this essay, we will be discussing common threats faced daily by users of the internet, email, mobile devices and cloud technologies, and the strategies that can prevent each of them from happening. The first point we are discussing is about internet threats. Internet threats involve malware and frauds that utilizes all the HTTP protocols.
A threat is defined as a potential risk to one's assets leading to a loss of value. This essay will explore other internet threats that can be prevented through the use of certain programs. Internet security must be in place to deter any harm or danger that comes your way when using the internet and to learn how to stay safe online. It relies ...
Introduction. The Internet has become an indispensable part of our lives, gradually entering all the possible spheres and shaping the way we run our errands, communicate with people, and analyze the world around us. It changes our attitudes to work processes, leisure, and even interpersonal relations with the help of algorithms, simple ...
Summary. If you or someone you know is experiencing online harassment, remember that you are not powerless. There are concrete steps you can take to defend yourself and others. First, understand ...
Essential Internet Safety Tips. To avoid all of these dangers, we recommend following our essential internet safety tips when you or your family are online: 1. Make sure you're using a secure internet connection. Although using public Wi-Fi is not recommended, it's sometimes unavoidable when you are out and about.
2. Malware. Another common security threat to your computer systems is malware or ransomware. Malware attacks your files and will only stop until you pay the cybercriminal a hefty ransom. Studies reveal that malware affects 32% of all the computers in the world. The attack starts by infecting your database systems.
A virtual private network (VPN) is a great way to protect sensitive data, especially when accessing a public Wi-Fi network. A VPN encrypts all information transmitted by your device and helps prevent many types of cyberattacks. And finally, teachers and parents should educate children about proper internet usage.
Grade: 5. Download. The purpose of this how do you keep yourself safe and secure online essay is to enlighten the reader about how to keep your information as secure as possible on the Internet. Today, when the use of technology is part of our everyday life, young people's awareness on how to act in the virtual world to avoid potential dangers ...
These opens up opportunity for threats that most users are unaware of, therefore we must learn to prevent such threats from happening. In the following essay I will be covering the possible threats and strategies that users might face surfing the internet, email, mobile devices and cloud technology.
Understanding Computer Threats. Computer threats come in various forms, each with the potential to wreak havoc on our digital lives. Malware, phishing, and hacking are just a few examples of the tactics used by malicious actors to compromise systems and steal sensitive information.
Top 6 Cybersecurity Threats in 2024. The FBI released a report created by the Internet Crime Complaint Center. It revealed that in 2020 the number of registered cybercrimes almost doubled compared to the previous year. Victims have lost large quantities of money due to different types of online scams.
A password management application can help you to keep your passwords locked down. 3. Keep your software updated. This is especially important with your operating systems and internet security software. Cybercriminals frequently use known exploits, or flaws, in your software to gain access to your system.
Learn how to use the Internet, keep your eyes open for good and bad actors, and make the most of what the Internet offers. 2. Keep your private life private. Keep your personal information separate from your professional role. Use different personas for different roles. 3. Protect communications.
Cybercrime is a criminal activity that uses a computer as an object over a network to commit a crime. Cybercriminals may include professional hackers, employees, children etc. BAL bharti case is an example of cybercrime committed by a juvenile. Harassment of friends was the reason. Email bombing is a technique of cybercrime.
Here's how you can protect your devices from malware: Install an antivirus program on all the devices you use, including your phone and tablet. Make sure to keep it up to date. Use a firewall to control which programs have access to the internet. Your firewall can prevent an infected program from broadcasting your sensitive data.
Run a Google safe browsing diagnostic on the site. Copy and paste the URL of a site into the search box on the diagnostic page, then click the search button. This will display a site safety report. Continue. Learn how to remove malware and how to avoid malware in this free Internet safety lesson.
Web threats definition. Web-based threats, or online threats, are a category of cybersecurity risks that may cause an undesirable event or action via the internet. Web threats are made possible by end-user vulnerabilities, web service developers/operators, or web services themselves. Regardless of intent or cause, the consequences of a web ...
Pages: 2 (702 words) Views: 2150. Grade: 5. Download. The internet is full of potential threats to us and contains a lot of various information of each users and many people often don't like the informations to leaked so in order to hide their real identity and away from significant threat in the internet world they create dummy accounts.
1. Install antivirus software. If you want to avoid getting a virus on your devices from the internet, installing and running antivirus software is important. Cyberthreats have evolved, and everyday activities like online banking, shopping, and browsing can make you vulnerable to cyberthreats. Viruses are a major cyberthreat, which is why it ...
Decent Essays. 739 Words. 3 Pages. Open Document. Threats to our Internet We use the internet for everything. We learn, we work, we communicate, we entertain our self, and do many other things with it. It is one of the Uttermost essential tool we have, to be able to properly function as members of our society.
(www.britannica.com) 81% of Net users are concerned about threats to their privacy while online. The greatest threat to privacy comes from the construction of e-commerce alone, and not from state agents. E-commerce is structured on the copy and trade of intimate personal information and therefore, a threat to privacy on the Internet.
Note. The following information and precautions should be followed by all computer users, regardless of the computer or operating system used to reduce the risk of threats. If you shop online, send and receive e-mail, download files, or browse the Internet, keeping your computer and yourself safe and secure is important.
Study finds rapid escalation of violent school threats Schools face new wave of violent threats sent by social media and other electronic means, study says Bomb threats sent by Facebook. School shooting threats sent through international proxy servers. A death threat scribbled on a restroom wall that triggers texting rumors throughout the school community. Parents and media […]
That's where Password generator can help. This tool will help you create, remember, and autofill your passwords across all the devices you're signed into and syncing with your Microsoft Edge account. Protect your online identity with Microsoft Defender SmartScreen. Another way to prevent online identity theft is to avoid malicious websites ...
Produced by Nina Feldman , Clare Toeniskoetter , Rob Szypko and Diana Nguyen. With Michael Simon Johnson. Edited by Lisa Chow. Original music by Marion Lozano , Elisheba Ittoop and Sophia Lanman ...
Last week, Donald J. Trump became the first U.S. former president to be convicted of a crime when a jury found that he had falsified business records to conceal a sex scandal. Nate Cohn, who is ...
Produced by Will Reid , Rob Szypko and Rachelle Bonja. Edited by Brendan Klinkenberg and Michael Benoist. Original music by Marion Lozano , Dan Powell and Will Reid. Engineered by Alyssa Moxley ...