- Artificial Intelligence
- Generative AI
- Cloud Computing
- CPUs and Processors
- Data Center
- Edge Computing
- Enterprise Storage
- Virtualization
- Enterprise Buyer’s Guides
- Internet of Things
- Network Management Software
- Network Security
- United States
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Copyright Notice
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights

Our Network
- Computerworld

802.1X: What you need to know about this LAN-authentication standard
The ieee 802.1x standard allows network switches and access points to hand off device authentication to a specialized server so it can be managed and updated centrally..

When devics on enterprise LANs need to connect to other devices, they need a standard method for identifying each other to ensure they are communicating with the device they want to, and that’s what 802.1x does. This article tells where it came from and how it works.
802.1x defined
IEEE 802.1X is a standard that defines how to provide authentication for devices that connect with other devices on local area networks (LANs).
It provides a mechanism by which network switches and access points can hand off authentication duties to a specialized authentication server, like a RADIUS server, so that device authentication on a network can be managed and updated centrally, rather than distributed across multiple pieces of networking hardware.
Although the standard’s name might remind you of the IEEE 802.11 standards that make up Wi-Fi, 802.1X dates from the old day of all-wired networking and today is used to secure both wired and wireless networks . Because the protocol relies on a centralized authentication server, it’s generally found in the world of enterprise LANs rather than small home networks.
PPP, EAP and EAPOL
Old-school internet users remember point-to-point protocol (PPP) as how they got online in the days of dialup modems, although the protocol also had use as a tunneling method over DSL and as part of some VPNs. One piece of PPP defined a username/password-based authentication mechanism. This was fine for home users, but enterprises generally required something more robust.
Extensible authentication protocol (EAP) was designed to meet those needs. EAP sat inside of PPP’s authentication protocol and provided a generalized framework for several different authentication methods. EAP was supposed to head off proprietary authentication systems and let everything from passwords to challenge-response tokens and public-key infrastructure certificates all work smoothly with PPP.
With standardized EAP, interoperability and compatibility of authentication methods became simpler. For example, when you dialed into a remote-access server (RAS) that used EAP for security, the RAS didn’t need to know any of the details about the authentication system; it just had to coordinate things between you and the authentication server. By supporting EAP authentication, the RAS server got out of the business of acting as middleman. It just packaged and repackaged EAP packets to hand off to a RADIUS server (or some other server supported by EAP), which did the actual authentication.
This brings us to IEEE 802.1X, which includes a standard called EAP encapsulation over LANs (EAPOL). As the name implies, this is a standard for passing EAP over a wired or wireless local area network. With 802.1X, you package EAP messages in Ethernet frames and don’t use PPP at all. It’s authentication and nothing more. 802.1X is still widely used today, while PPP is largely obsolete. You can also use 802.1X with protocols other than TCP/IP.
How 802.1X authentication works
To understand 802.1x, you need to understand three terms:
- Supplicant: The user or client that wants to be authenticated
- Authentication server: The actual server doing the authentication, typically a RADIUS server
- Authenticator: The device in between the supplicant and the authentication server, such as a wireless access point
One of the key benefits of 802.1X is that the authenticator can be simple and dumb—the brains only have to be in the supplicant and the authentication server. This makes 802.1X ideal for wireless access points, which typically have little by way of memory and processing power.
EAPOL is defined for Ethernet-like LANs, including 802.11 wireless, as well as token ring LANs such as FDDI. EAPOL is not particularly sophisticated. There are a number of modes of operation, but the most common authentication sequence would look something like this:
- The authenticator sends an “EAP-Request/Identity” packet to the supplicant as soon as it detects that the link is active (e.g., as the supplicant system associates with the access point).
- The supplicant sends an “EAP-Response/Identity” packet to the authenticator, which passes it on to the authentication (RADIUS) server.
- The authentication server sends back a challenge to the authenticator, such as with a token password system. The authenticator unpacks this from IP and repackages it into EAPOL and sends it to the supplicant. Different authentication methods will vary this message and the total number of messages. EAP supports client-only authentication and strong mutual authentication; only strong mutual authentication is considered appropriate for wireless networks.
- The supplicant responds to the challenge via the authenticator, which passes the response on to the authentication server.
- If the supplicant provides proper identity, the authentication server responds with a success message, which is passed to the supplicant. The authenticator now allows access to the LAN, though this can be restricted, based on attributes that come back from the authentication server. For example, the authenticator might switch the supplicant to a particular virtual LAN or invoke a set of firewall rules.
802.1X and wireless security
The Wired Equivalent Privacy (WEP) protocol was the security protocol widely used in the early days of Wi-Fi, but it was badly broken from the beginning and was never well regarded by enterprise security and networking pros.
In response to the WEP fiasco, many wireless LAN vendors latched onto IEEE 802.1X standard to patch up the holes. For example, one of the biggest problems with WEP was the long life of the cryptographic keys it used, which were shared among many users and were well known. With 802.1X, each station could have a unique WEP key for every session. The authenticator (the wireless access point, in this case) could also choose to change the WEP key frequently, such as once every 10 minutes or every 1,000 frames. If you see 802.1X on a list of encryption types available for your wireless network, that’s probably referring to legacy support for this type of arrangement.
However, WEP has long been abandoned by the industry, and today almost all networking equipment uses Wi-Fi Protected Access, or WPA, with WPA3 being the latest version. It includes WPA3-Personal, which provides more individualized encryption, and WPA3-Enterprise, which boosts cryptographic strength for networks transmitting sensitive data.
A major improvement with WPA3-Enterprise is the requirement that the client must ensure it is actually communicating with the authentication server, not a rogue server, before sending its login credentials. In WPA2-Enteprise, that verification was optional.
MAB for bypassing 802.1X
One final note: some client devices, such as wireless printers, don’t have the capability of acting as an 802.1X supplicant, but you might want to allow them access to your 802.1X-secured network anyway. Some network equipment vendors allow you to do this by means of what’s called MAC authentication by pass (MAB) . With MAB, your authentication server can authenticate a client device by means of its MAC address rather than via the EAPOL authentication process outlined above.
There are two important things to keep in mind. One is that MAB is not a standard; it’s implemented differently by different networking vendors, and some vendors don’t support it at all. The other is that a device that accesses your network via MAB is bypassing important layers of security. So make to limit as much as possible the access that such devices have to networks and services.
Related content
Alkira expands naas platform with ztna capabilities, ibm launches platform to protect data from ai and quantum risks, gartner: top 10 strategic technology trends for 2025, has the time come for integrated network and security platforms, newsletter promo module test.

Josh Fruhlinger is a writer and editor who lives in Los Angeles.
More from this author
What is a digital twin and why is it important to iot, download our zero trust network access (ztna) enterprise buyer’s guide, dns explained: how the domain name system works, what is ipv6, and why is adoption taking so long, ztna buyer’s guide: who is selling zero trust network access and what do you get, what is sdn and where is it going, what is 5g fast wireless technology for enterprises and phones, what is power over ethernet (poe).
Snyder, a Network World Test Alliance partner, is a senior partner at Opus One in Tucson, Ariz. He can be reached at
Slow Internet? Firebind can sniff out the problem
Graylog review: open source log management for the dedicated do-it-yourselfer, first look: netbeez net management tool creates a buzz, first look: amazon echo: novelty item or ready-for-prime-time part of your digital life, review: dell wyse delivers android-on-a-stick, oh, bi the way…, first look: cisco aci re-imagines the enterprise data center network, first look: cisco nexus 9000, show me more, ai networking draws a crowd at onug summit.

Predictable AWS cloud deployment resources allow full account takeover

Billion-dollar fine against Intel annulled, says EU Court of Justice

Has the hype around ‘Internet of Things’ paid off? | Ep. 145

Episode 1: Understanding Cisco’s Converged SDN Transport

Episode 2: Pluggable Optics and the Internet for the Future

How to use the diff3 command

How to use the colordiff command

How to use the CMP command

Sponsored Links
- Get Cisco UCS X-Series Chassis and Fabric Interconnects offer.
What Is 802.1X Authentication?
Understand what 802.1X authentication is, how it works, and various use cases.
802.1X Authentication Definition
Like all authentication, 802.1X authentication involves making sure something interfacing with the system is actually what it claims it is. When someone wants to gain access to a network using 802.11 and variants like 802.11n, b, or g, 802.1x authentication acts as a protocol that verifies the person connecting is who they say they are. It works for both wireless and wired devices.
The IEEE 802.1X Working Group endeavors to improve 802.1X authentication, as well as other technologies that impact 802 architecture. This article will discuss 802.1 authentication step by step, as well as how it can be used.
What are the main parts of 802.1X authentication?
Supplicant (client-end user).
Devices that are trying to connect to an 802.1X network need to have software installed on them, and this is referred to as the supplicant. The supplicant is needed because it initiates the connection by engaging in an Extensible Authentication Protocol (EAP) transaction between the supplicant and the controller or switch. The supplicant gathers the credentials of the user together in a way that corresponds with what 802.1X can read.
Authenticator (access point or a switch)
An authenticator refers to a device on the network that supplies data links that connect the network and the client. It also blocks or allows traffic as it tries to flow between the client and the network. A wireless access point and an Ethernet switch are examples of authenticators.
Authentication server (usually a RADIUS server)
The authentication server is one that receives requests asking for access to the network and responds to them. It is able to tell the authenticator whether the connection is going to be allowed, as well as the settings used to interact with the client’s connections.
Authentication servers tend to run software that supports Remote Authentication Dial-In User Service (RADIUS) and EAP protocols. The authentication server can also be run within authenticator hardware.
Global Threat Landscape Report 2H 2023
FortiGuard Labs Global Threat Landscape Report 2H 2023 shows Cybercriminals Exploiting New Industry Vulnerabilities 43% Faster than 1H 2023.
How Does 802.1X Authentication Work?
During the initiation phase, the authenticator sends EAP request identity frames, which are tools used to convey a request to identify the device trying to connect. These are sent to a Layer 2 address on the local network or virtual local-area network (VLAN). Layer 2 is the data link layer, such as Point-to-Point Protocol (PPP), and it controls how data moves through the physical connections in your network.
The authenticator then takes the identity information, packages it, and sends it to the authentication server. Understanding authentication is important to configuring Fortinet 802.1X authentication settings .
Authentication
Once there is agreement between the supplicant and the authentication server in the initiation phase, EAP responses and requests get transferred between the authentication server and the supplicant, and the authentication server replies with either a success or failure message.
If the authentication process succeeds, the authenticator then designates the port as “authorized.” This state enables normal traffic to pass through. If the process does not succeed, the port maintains a state of being “unauthorized.” This results in all non-EAP traffic getting blocked.
Authorization
Once the user enrolls for a public key infrastructure (PKI) certificate or confirms the validity of their credentials, they are authorized to access the network. RADIUS checks to make sure they have the right certificate or the necessary credentials every time they connect. This helps prevent illegitimate users from getting on the network.
Accounting within the 802.1X RADIUS system records the information pertaining to the devices that get authenticated and the length of the session. Device information is sent to the accounting server as the session starts. The server also gets a message when the session has ended.
Termination
Accounting within the 802.1x RADIUS system records the information pertaining to the devices that get authenticated and the length of the session. Device information is sent to the accounting server as the session starts. The server also gets a message when the session has ended.
What Can You Do with 802.1X Authentication?
Pre-admission control—blocks unauthenticated messages.
802.1X authentication prevents messages that have not been authenticated by the system. This protects the network from hackers that may try to penetrate it with devices that have not been authenticated or do not have the proper PKI certificate.
Device and user detection—identifies users and devices with predefined credentials or Machine IDs
You can issue the credentials needed to connect to the network to a select group of users. This way, those you have not sent the credentials to cannot gain access. As a result, you can keep the list of those who access the network small, limiting it to trusted individuals and devices.
Authentication and authorization—verifies and provides access
With 802.1X authentication, you have a reliable tool to ensure only those with the rights to access the network can connect. You are also able to verify that each user is who they say they are. With port-based 802.1X authentication , the media access control (MAC) service is used to establish a connection.
Onboarding—provisions a device with security, management, or host-checking software
The onboarding process allows you to vet all those who connect to your network. Because you control which devices get the credentials they need, you can ensure unauthorized devices are kept off your network.
Profiling—scans endpoint devices
Thanks to the profiling process, the device has to reveal information about its identity and connection such as its MAC address and the number of the port it is using.
Policy enforcement—applies role and permission-based access
802.1X authentication allows you to create and enforce policies that can restrict access according to an individual’s role or their permissions. This not only prevents breaches but also keeps well-intentioned but unauthorized users from accidentally connecting and messing up an element of the network.
Post-admission control—enforces session termination and cleanup
802.1X authentication also allows you to end sessions and remove users from the network. This way, a device can be disconnected after the user leaves, preventing a different user from using the device’s credentials to access the network in the first user’s absence.
802.1X Authentication FAQs
What is 802.1x authentication.
802.1X authentication involves making sure something interfacing with the system is actually what it claims it is. When someone wants to gain access to a network using 802.11 and variants like 802.11n, b, or g, 802.1X authentication acts as a protocol that verifies the person connecting is who they say they are. It works for both wireless and wired devices.
The main parts of 802.1X authentication include: Supplicant, Authenticator and Authentication server.
Cybersecurity Resources
- Cybersecurity
- Types of Cyber Attacks
- IT vs OT Cybersecurity
- AI Cybersecurity
- Cyber Threat Intelligence
- Cybersecurity Management
- Network Security
- Data Security
- Email Security
- Endpoint Security
- Web Security
- Enterprise Security
- Cybersecurity Mesh
Quick Links
- Fortinet Products
- Fortinet Demos
- Analyst Reports
Speak with an Expert
Please fill out the form and a knowledgeable representative will get in touch with you soon.
By clicking submit you agree to the Fortinet Terms and Conditions & Privacy Policy .
- Help center
- Chinese (traditional)
Learn more
- Case Study
- Knowledge Center
- Glossary
Getting Started (193)
Product Updates (157)
News & Announcements (60)
Self Service (10)
Configuration Guide (9)
Hear It from Experts (9)
Troubleshooting Guide (6)
Client Reviews (4)
Installation Guide (4)
Product Testing (4)
Switches (162)
Optics and Transceivers (113)
Networking Devices (108)
Network Cabling and Wiring (97)
Optical Networking (42)
Networking (125)
Fiber Optic Communication (64)
Data Center (50)
General (37)
Wireless and Mobility (13)
Business Type (9)
Routing and Switching (6)
United Kingdom (13)
Singapore (11)
Australia (8)
Central & Northern Europe (3)
- Product Updates
- Networking Devices
- Case Study
- Knowledge Center
802.1X Authentication: A Port-based Network Access Control Protocol
The background of 802.1x protocol.
In the early IEEE 802 LAN protocols, users can access devices or resources in a LAN as long as they can access the control device (for example, an access switch ) in the LAN. This obviously brings security risks. To resolve security issues on wireless LANs (WLANs), the IEEE 802 committee proposed the 802.1X protocol to control the network access rights of users. This protocol effectively prevents unauthorized users from transmitting and receiving data. Due to its good universality, 802.1X has also been widely used on wired LANs.
802.1X Authentication Definition
802.1X authentication is a network access control standard that provides a framework for securing and controlling access to a local area network (LAN) or a wireless LAN (WLAN). It is defined in the IEEE 802.1X standard and is widely used to ensure that only authorized devices and users can connect to a network. In 802.1X protocol , the authentication process involves three main entities:
Supplicant : The device (such as a computer or smartphone) that is attempting to connect to the network.
Authenticator : The network device (such as a switch or Wi-Fi access point) that controls physical access to the network.
Authentication Server : A server that verifies the credentials provided by the supplicant. This server is often a RADIUS (Remote Authentication Dial-In User Service) server.
The IEEE 802.1X Working Group endeavors to improve 802.1X authentication, as well as other technologies that impact 802 architecture. This article will discuss 802.1 authentication step by step, as well as how it can be used.

How Does 802.1X Authentication Work?
802.1X authentication works through a series of steps involving the supplicant (device trying to connect), authenticator (network device controlling access), and authentication server. Here's a detailed explanation of the process:
Initiation :Initially, the port on the network device (authenticator) is in a "closed" or unauthorized state.The supplicant (device) initiates the authentication process by sending an EAP (Extensible Authentication Protocol) start message to the authenticator.
Authentication :Once there is agreement between the supplicant and the authentication server in the initiation phase, EAP responses and requests get transferred between the authentication server and the supplicant, and the authentication server replies with either a success or failure message. If the authentication process succeeds, the authenticator then designates the port as “authorized.” This state enables normal traffic to pass through. If the process does not succeed, the port maintains a state of being “unauthorized.” This results in all non-EAP traffic getting blocked.
Authorization :Once the user enrolls for a public key infrastructure certificate or confirms the validity of their credentials, they are authorized to access the network. RADIUS checks to make sure they have the right certificate or the necessary credentials every time they connect. This helps prevent illegitimate users from getting on the network.
What Can You Do with 802.1X Authentication?
802.1X authentication provides a robust framework for controlling access to a network, offering several benefits and capabilities. Here are some of the things you can achieve with 802.1X authentication:

Enhanced Network Security
802.1X helps in preventing unauthorized devices from gaining access to the network. Only devices with valid credentials are allowed to connect, enhancing overall network security.
User Authentication
Users or devices connecting to the network need to provide valid credentials (such as usernames and passwords) for authentication. This ensures that only authorized users can access network resources.
Device Authentication
Beyond user authentication, 802.1X can be used to authenticate devices based on their unique identifiers, such as MAC addresses or digital certificates. This is particularly useful for IoT (Internet of Things) devices.
Centralized Authentication
802.1X allows for centralized authentication through an authentication server (often a RADIUS server). This centralization simplifies user management and ensures consistent authentication policies across the network.
Dynamic VLAN Assignment
Based on the authentication result, 802.1X can dynamically assign devices to specific VLANs. This enables network segmentation and enhances security by isolating devices into appropriate network segments.

In conclusion, 802.1X authentication is a powerful tool for securing network access, enforcing policies, and ensuring that only authorized entities connect to the network. Do you want to know more about us? FS offers a range of solutions for your business. Book a demo or sign up for a free trial .
- # Networking Devices
- # LAN Access Switch
You might be interested in

Email Address
Please enter your email address.
Please make sure you agree to our Privacy Policy and Terms of Use.

PicOS® Switch Software

AmpCon™ Management Platform
- Network Cabling and Wiring
- Buying Guide
- Fiber Optic Communication
- Optics and Transceivers
- Data Center
- Network Switch
- Ethernet Patch Cords
- Business Type
- Routing and Switching
- Optical Networking

Fiber Optic Cable Types: Single Mode vs Multimode Fiber Cable
May 10, 2022

Layer 2 vs Layer 3 Switch: Which One Do You Need?
Oct 6, 2021

Multimode Fiber Types: OM1 vs OM2 vs OM3 vs OM4 vs OM5
Sep 22, 2021

Running 10GBASE-T Over Cat6 vs Cat6a vs Cat7 Cabling?
Mar 18, 2024

PoE vs PoE+ vs PoE++ Switch: How to Choose?
May 30, 2024

IEEE 802.1X
Sep 20, 2014
340 likes | 706 Views
IEEE 802.1X. Port Based Network Access Control. Definition. “Port-based network access control allows a network administrator to restrict the use of IEEE 802 LAN service access points (ports) to secure communication between authenticated and authorized devices.”
Share Presentation
- radius server
- access point
- authentication server
- extensible authentication protocol
- radius authentication server receives

Presentation Transcript
IEEE 802.1X Port Based Network Access Control
Definition • “Port-based network access control allows a network administrator to restrict the use of IEEE 802 LAN service access points (ports) to secure communication between authenticated and authorized devices.” • “IEEE Std 802.1X specifies an architecture, functional elements, and protocols that support mutualauthentication between the clients of ports attached to the same LAN and secure communication between the ports.”
Definition • “Port-based network access control allows a network administrator to restrict the use of IEEE 802 LAN service access points (ports) to secure communication between authenticated and authorized devices.” • “IEEE Std 802.1X specifies an architecture, functional elements, and protocols that support mutualauthentication between the clients of ports attached to the same LAN and secure communication between the ports.” • Layer 2 Access to the medium. • Access control applied to ports. • Authentication. • Secure communication.
Basic Topology • There are three elements: • The Supplicantwhich in this example is a wireless 802.11 Client A. • The Authenticator which in this case is a wireless 802.11 access point WAP. • The Authentication Server.
Extensible Authentication Protocol EAP • The IEEE 802.1X standard specifies the use of EAP, the Extensible Authentication Protocol (RFC 3748) to support authentication using a centrally administered Authentication Server. • The implementation of EAP was initially defined for PPP protocols; however, our main focus is in the use in LAN networks. • Consequently, the standard also defines EAP encapsulation over LANs (EAPoL) to convey the necessary exchanges between the supplicant and the authenticator.
EAPoL Format • Nothing more than an EAP message encapsulated by an Ethernet Frame. • That’s all . Destination Source Type 888EH EAP Message Version Type Length Value
Association Phase All traffic • Client A, the supplicant, associates with the Wireless Access Point WAP. • This is equivalent to connecting a cable to a LAN switch port. In such case, there are electrical signals, but nothing more significant is going on. • All traffic is blocked at the WAP Authenticator.
Jargon EAP • In the initial stage of authentication, only EAP messages are accepted. • The technical jargon for this is Open Uncontrolled Virtual Port. • Any other traffic is blocked and ignored at the authenticator. • The technical jargon for this is Closed Controlled Virtual Port. • In reality, the ports do not even exist, this is just technical babble. • It is simply that the Authenticator listens to authentication messages and ignores/blocks anything else, that’s all. Other traffic
EAP Transactions EAPoL-Start Other traffic • The supplicant sends a EAP message start encapsulated inside a WLAN frame (EAPoL). • The message is an EAPoL-start.
EAP Transactions EAP-request-id Other traffic • The WLAN Authenticator reply with an EAP-request-identity. • The supplicant client responds with the username in clear-text EAP-response-id
EAP Transactions EAP-response-id Other traffic RADIUS or TACACS+ • The Authenticator sends now a RADIUS or TACACS+ message. • Let’s assume that we are just using RADIUS for simplicity of the explanation.
EAP Transactions EAP Other traffic RADIUS or TACACS+ • EAP messages do not continue unchanged toward the authentication server. • The authenticator talks another protocol, like RADIUS or TACACS+ to the Authentication Server. • So, in one hand, the authenticator talks EAP and in the other RADIUS or TACACS+. • WAP is a proxy or translator or intermediary.
EAP Transactions EAP-response-id Other traffic RADIUS –access-request • The EAP response with the username, triggers a RADIUS message access request. • RADIUS Authentication Server receives the message and checks the policies and user database to find a match. • RADIUS server prepares a reply message.
EAP Transactions Other traffic • RADIUS server prepares a reply message. • Radius server replies with an Access Challenge. • The WAP authenticator translates the RADIUS message to an EAP message which is sent to the supplicant. RADIUS –access-challenge
EAP Transactions Other traffic • The WAP authenticator translates the RADIUS message to an EAP message which is sent to the supplicant as an EAP challenge-request. • The Supplicant receives the message and it prepares an answer. EAP challenge RADIUS –access-challenge
EAP Transactions EAP challenge • The Supplicant receives the message and it prepares an answer. • It hashes a password with a well known algorithm. telecomS144 RADIUS –access-challenge MD5 AX1Z05FE2CD48
EAP Transactions • The Supplicant receives the message and it prepares an answer. • It hashes a password with a well known algorithm. • It answers the challenge with a EAP-Challenge-Response. telecomS144 Challenge Response MD5 AX1Z05FE2CD48
EAP Transactions RADIUS-Access-Request • The authenticator sends a RADIUS message Access-Request that contains the HASH to the Radius Server. • The Radius Server runs an stored password thru the same algorithm to find if the result matches the HASH received. telecomS144 Challenge Response MD5 AX1Z05FE2CD48
EAP Transactions RADIUS-Access-Request • The authenticator sends a RADIUS message Access-Request that contains the HASH to the Radius Server. • The Radius Server runs an stored password thru the same algorithm to find if the result matches the received HASH. telecomS144 telecomS144 Challenge Response MD5 MD5 AX1Z05FE2CD48 AX1Z05FE2CD48
EAP Transactions RADIUS –access-accept EAP success • The supplicant receives the approval of authentication. • The final part of the authentication process is the creation of a dynamic encryption key. • IEEE 802.11i describes this process which is called Robust Security Network (RSN) with two new protocols, the 4-Way Handshake and the Group Key Handshake
Radius TACACS+ IEEE 802.1X
IEEE 802.1x • IEEE 802.1X is the IEEE standard for Port based Network Access Control . • It provides an authentication mechanism to devices attaching to LAN or WLAN infrastructure. • IEEE 802.1X defines the encapsulation of the Extensible Authentication Protocol over Ethernet type networks. • 802.1X authentication involves three parties: • A supplicant (which is a CLIENT) • An authenticator (an access point) • An authentication server (a RADIUS server)
IEEE 802.1x • The authenticator (access point) acts like a security guard to a protected network. • The supplicant (CLIENT) is not allowed access through the authenticator (access point) to the protected side of the network until the supplicant’s identity has been validated and authorized.
IEEE 802.1x • The supplicant presents credentials, (user name / password or a digital certificate), to the authenticator. • The authenticator forwards the credentials to the authentication server for verification. • If the authentication server determines the credentials are valid, the supplicant (client device) is allowed to access resources located on the protected side of the network.
Cisco Support • Cisco implementation of RADIUS is compatible with Microsoft PEAP-MS-CHAP-v2 and PEAP-GTC. • Cisco proprietary product ACS includes Radius and TACACS+ implementation. • TACACS+ is Cisco only.
RADIUS/TACACS+ • RADIUS is a distributed client/server system that secures networks against unauthorized access. • RADIUS clients run on Cisco routers and relays authentication requests to a central RADIUS server that contains all user authentication and network service access information.
- More by User

802.1X Misuses
802.1X Misuses. David Johnston [email protected]. An Appeal for Simplicity. We have spent a lot of time fiddling with details of our authentication mechanism. A lot more needs to be done to fill in the gaps There may be simpler architectures that achieve our ends with less complexity
604 views • 35 slides
IEEE 802 Response to FDIS comments on IEEE 802.1AE and IEEE 802.1X
IEEE 802 Response to FDIS comments on IEEE 802.1AE and IEEE 802.1X. 16 December 2013. Authors:. This presentation provides responses to comments on IEEE 802.1X & IEEE 802.1AE during FDIS ballots. The FDIS voting results on IEEE 802.1X are in N15771
866 views • 58 slides

– Chapter 5 (B) – Using IEEE 802.1x
– Chapter 5 (B) – Using IEEE 802.1x. Purpose: port authentication access control An IEEE standard http://standards.ieee.org/getieee802/download/802.1X-2001.pdf Used in both wired and wireless networks
375 views • 19 slides

An Initial Security Analysis of the IEEE 802.1x Standard
An Initial Security Analysis of the IEEE 802.1x Standard. Tsai Hsien Pang 2004/11/4. Outline. Introduction IEEE 802.1x Standard Man-in-Middle, Session Hijack attack Proposed solution Conclusion Reference. 802.11 Security.
505 views • 30 slides

An Initial Security Analysis of the IEEE 802.1x Standard. 965002102 徐振翔 975002013 陳昱任 975002039 許琇筑 2011/11/17. Outline. Introduction IEEE 802.1x Standard Man-in-Middle, Session Hijack attack Proposed solution Conclusion Reference. Introduction.
510 views • 28 slides

802.1X Authentication
802.1X Authentication. Deniz Kaya Microsoft, Cisco, Ironport Trainer CCSI, CCNP, MCT, MCSE, ICSI, ICSP. Airport. …While the Assets Needing to be Protected are Expanding. 831. Cable Provider. Teleworker. VPN Head-End. Service Provider/ Internet. Partner/Vendor. City Hall. Library.
1.1k views • 30 slides

802.1x deployment meeting 11 April 2005. 802.1x. Agenda. Welcome and Introductions (5 mins) JFH – the 802.1x protocol (20 mins) Andy Cattell – the Oddessy client (20 mins) General discussion (to lunchtime). Introduction to 802.1x.
922 views • 32 slides

802.1X. Terry Simons Formerly of The University of Utah. University of Utah Background . 28,000+ student campus EAP-TTLS 802.1X movement was “grass roots” Proof of concept Wireless Whitepaper RADIUS “Mesh” (More of a star topology) “Give to get” mentality
295 views • 11 slides

Secure Handover for IEEE 802.1x Wireless Networks
By: Alex Feldman. Secure Handover for IEEE 802.1x Wireless Networks. What’s the environment?. A mobile station is connected to the network wirelessly through another device. In case of WiFi (IEEE 802.11) this would be an access point .
261 views • 18 slides

802.1X Configuration
802.1X Configuration. Ter ena 802.1X workshop t he Net herlands, Amsterdam, March 30 th. Paul Dekkers. Overview. EAP. What makes EAP flexible. Man-in-the-Middle attack. That’s why we need a good EAP mechanism!. RADIUS proxy-ing. RADIUS. Client-Server model
437 views • 28 slides
IEEE 802.1X and RADIUS Security
IEEE 802.1X and RADIUS Security. Bernard Aboba Ashwin Palekar Microsoft. Outline. Introduction to RADIUS security RADIUS security vulnerabilities Vulnerabilities of RADIUS and IEEE 802.1X Suggested Fixes. RADIUS Security Features. RADIUS application layer security
389 views • 14 slides

IEEE 802.1X For Wireless LANs
IEEE 802.1X For Wireless LANs. Bernard Aboba, Tim Moore, Microsoft John Roese, Ravi Nalmati, Cabletron Albert Young, 3Com Carl Temme, Bill McFarland T-Span David Halasz, Aironet Paul Congdon, HP Andrew Smith, Extreme Networks. Outline. Deployment issues with 802.11
399 views • 27 slides

245 views • 19 slides

178 views • 11 slides

311 views • 30 slides
Understanding 802.1X Authentication
This document describes the basic principles of 802.1x authentication., overview of 802.1x authentication, 802.1x authentication protocol, 802.1x authentication process, 802.1x authorization, 802.1x re-authentication, logout of 802.1x-authenticated users, 802.1x timers.
802.1X defines a port-based network access control and authentication protocol that prevents unauthorized clients from connecting to a LAN through publicly accessible ports unless they are properly authenticated.
- 802.1X is a Layer 2 protocol and does not involve Layer 3 processing. It does not require high performance of access devices, reducing network construction costs.
- Authentication packets and data packets are transmitted through different logical interfaces, improving network security.
802.1X Authentication System
As shown in Figure 1-1 , the 802.1X authentication system uses a standard client/server architecture with three components: client, access device, and authentication server.
- The client is usually a user terminal. The user triggers 802.1X authentication using client software. The client must support Extensible Authentication Protocol over LAN (EAPoL).
- The access device is usually a network device that supports the 802.1X protocol. It provides a port, either physical or logical, for the client to access the LAN.
- The authentication server, typically a RADIUS server, carries out authentication, authorization, and accounting on users.
In the 802.1X authentication system, the client, access device, and authentication server exchange information using the Extensible Authentication Protocol (EAP). EAP can run without an IP address over various bottom layers, including the data link layer and upper-layer protocols (such as UDP and TCP). This offers great flexibility to 802.1X authentication.
- The EAP packets transmitted between the client and access device are encapsulated in EAPoL format and transmitted across the LAN.
- EAP termination mode: The access device terminates EAP packets and encapsulates them into RADIUS packets. The authentication server then uses the standard RADIUS protocol to implement authentication, authorization, and accounting.
- EAP relay mode: The access device directly encapsulates the received EAP packets into RADIUS using EAP over RADIUS (EAPoR) packets, and then transmits these packets over a complex network to the authentication server.
EAPoL Packet
EAPoL is a packet encapsulation format defined by the 802.1X protocol. EAPoL is mainly used to transmit EAP packets over a LAN between the client and access device. The following figure shows the format of an EAPoL packet.
To support EAP relay, the following attributes are added to the RADIUS protocol:
- EAP-Message: is used to encapsulate EAP packets.
- Message-Authenticator: is used to authenticate and verify authentication packets to protect against spoofing of invalid packets.
The following figure shows the format of an EAPoR packet.
Guidelines for Selecting Authentication Modes
- The EAP relay mode simplifies the processing on the access device and supports various authentication methods. However, the authentication server must support EAP and have high processing capability. The commonly used authentication modes include EAP-TLS, EAP-TTLS, and EAP-PEAP. EAP-TLS has the highest security because it requires a certificate to be loaded on both the client and authentication server. EAP-TTLS and EAP-PEAP are easier to deploy since the certificate needs to be loaded only on the authentication server, but not the client.
- The EAP termination mode is advantageous in that mainstream RADIUS servers support Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP) authentication, eliminating the need for server upgrade. However, the workload on the access device is heavy because it needs to extract the client authentication information from the EAP packets sent by the client and encapsulate the information using the standard RADIUS protocol. In addition, the access device does not support other EAP authentication methods except MD5-Challenge. In CHAP authentication, passwords are transmitted in cipher text; in PAP authentication, passwords are transmitted in plain text. CHAP provides higher security and is recommended.
Triggering of 802.1X Authentication
802.1X authentication can be triggered in one of the following scenarios:
- A client sends an EAPoL-Start packet.
- A client sends a DHCP, ARP, DHCPv6, ND, or any packet.
- The device sends an EAP-Request/Identity packet.
Authentication Processes in EAP Relay and EAP Termination Modes
In the 802.1X authentication system, the access device exchanges information with the RADIUS server in EAP relay or EAP termination mode. Figure 1-5 and Figure 1-6 respectively show the 802.1X authentication processes in EAP relay and EAP termination modes. In both processes, authentication is initiated by the client.
- To access an extranet, a user starts the 802.1X client program, enters the applied and registered user name and password, and initiates a connection request. At this time, the client sends an EAPoL-Start packet to the access device to start the authentication process.
- After receiving the EAPoL-Start packet, the access device returns an EAP-Request/Identity packet to the client for its identity.
- Upon receipt of the EAP-Request/Identity packet, the client sends an EAP-Response/Identity packet that contains the user name to the access device.
- The access device encapsulates the EAP-Response/Identity packet into a RADIUS Access-Request packet and sends the RADIUS packet to the authentication server.
- After receiving the user name forwarded by the access device, the RADIUS server searches the user name table in the database for the corresponding password, encrypts the password with a randomly generated MD5 challenge, and sends a RADIUS Access-Challenge packet containing the MD5 challenge to the access device.
- The access device forwards the MD5 challenge sent by the RADIUS server to the client.
- Upon receipt of the MD5 challenge, the client encrypts the password with the MD5 challenge, generates an EAP-Response/MD5-Challenge packet, and sends the packet to the access device.
- The access device encapsulates the EAP-Response/MD5-Challenge packet into a RADIUS Access-Request packet and sends the RADIUS packet to the RADIUS server.
- The RADIUS server compares the received encrypted password with the locally encrypted password. If the two passwords match, the user is considered to be valid and the RADIUS server sends a RADIUS Access-Accept packet (authentication is successful) to the access device.
- After receiving the RADIUS Access-Accept packet, the access device sends an EAP-Success packet to the client, changes the port state to authorized, and allows the user to access the network through the port.
- When the user is online, the access device periodically sends a handshake packet to the client to monitor the user.
- After receiving a handshake packet, the client sends a response packet to the access device, indicating that the user is still online. By default, the access device disconnects the user if it does not receive any response from the client after sending two consecutive handshake packets. The handshake mechanism allows the access device to detect unexpected user disconnections.
- To go offline, the client sends an EAPoL-Logoff packet to the access device.
- The access device changes the port state from authorized to unauthorized and sends an EAP-Failure packet to the client.
In EAP termination mode, the MD5 challenge for encrypting the user password is randomly generated by the access device, instead of the authentication server in EAP relay mode. Besides, in EAP termination mode, the access device uses the CHAP protocol to encapsulate the user name, challenge, and password encrypted by the client into standard RADIUS packets and sends them to the authentication server for authentication. In EAP relay mode, in contrast, the access device is only responsible for encapsulating EAP packets into RADIUS packets and transparently transmitting them to the authentication server.
Authentication checks whether the identity of the user who attempts to access the network is valid. Authorization specifies the network access rights that the authorized user can have, that is, the resources that the authorized user can access. VLANs, ACLs, and UCLs are often used for authorization. RADIUS authorization is used as an example. For details about other authorization methods and more authorization parameters, see 授权方案.
To prevent unauthenticated users from accessing restricted network resources, the restricted network resources and unauthenticated users are allocated to different VLANs. After a user is authenticated, the authentication server returns an authorized VLAN to the user. The access device then changes the VLAN to which the user belongs to the authorized VLAN, with the interface configuration remaining unchanged. The authorized VLAN takes precedence over the VLAN configured on the interface. That is, the authorized VLAN takes effect after the authentication succeeds, and the configured VLAN takes effect after the user goes offline. When the RADIUS server assigns an authorized VLAN, the following standard RADIUS attributes must be used together:
- Tunnel-Type : This attribute must be set to VLAN or 13.
- Tunnel-Medium-Type : This attribute must be set to 802 or 6.
- Tunnel-Private-Group-ID : The value can be a VLAN ID or VLAN description.
After a user is authenticated, the authentication server assigns an ACL to the user. Then, the access device controls the user packets according to the ACL.
- If the user packets match the permit rule in the ACL, the packets are allowed to pass through.
- If the user packets match the deny rule in the ACL, the packets are discarded.
The RADIUS server can assign an ACL to a user in either of the following modes:
- Static ACL assignment: The RADIUS server uses the standard RADIUS attribute Filter-Id to assign an ACL ID to the user. In this mode, the ACL and corresponding rules are configured on the access device in advance.
- Dynamic ACL assignment: The RADIUS server uses the RADIUS attribute HW-Data-Filter extended by Huawei to assign an ACL ID and corresponding rules to the user. In this mode, the ACL ID and ACL rules are configured on the RADIUS server.
A User Control List (UCL) is a collection of network terminals such as PCs and smartphones. The administrator can add users having the same network access requirements to a UCL, and configure a network access policy for the UCL, greatly reducing the administrator's workload. The RADIUS server assigns a UCL to a specified user in either of the following modes:
- Assigns the UCL name through the standard RADIUS attribute Filter-Id .
- Assigns the UCL ID through the RADIUS attribute HW-UCL-Group extended by Huawei.
You must configure the UCL and its network access policy on the access device in advance regardless of the UCL authorization mode used.
A free rule allows users to obtain certain network access rights before they are authenticated, to meet basic network access requirements.
You can configure either a common free rule or an ACL-defined free rule. A common free rule is determined by parameters such as the IP address, MAC address, interface, and VLAN, while an ACL-defined free rule is determined by ACL rules. Both the rules can specify the destination IP address that users can access before being authenticated. An ACL-based free rule can also define the name of a destination domain that users can access before being authenticated.
Sometimes, defining a free rule by domain name is simpler and more convenient than defining a free rule by IP address. This is because a domain name is easier to remember. For example, some users who do not have an authentication account must first log in to the official website of a carrier and apply for a member account, or log in using a third-party account such as a Twitter or Facebook account. In this case, you can configure ACL-defined free rules to specify domain names of the websites that users can access before they are authenticated.
Re-authentication for 802.1X-authenticated Users
If the administrator modifies parameters such as access rights and authorization attributes of an online user on the authentication server, the user must be re-authenticated to ensure user validity. If re-authentication is configured for online 802.1X-authenticated users, the access device sends user authentication parameters (saved after users go online) to the authentication server for re-authentication. If the user authentication information on the authentication server remains unchanged, the user keeps online. If the information has been modified, the user is disconnected and needs to be re-authenticated. Table 1-5 lists the re-authentication modes for 802.1X-authenticated users.
Re-authentication for Users in Abnormal Authentication State
The access device records entries for users in pre-connection state (that is, users who have not been authenticated or have failed the authentication), and grants corresponding network access rights to the users. You can configure the access device to re-authenticate these users based on user entries, so that they can obtain normal network access rights in a timely manner.
If a user fails the re-authentication before the user entry aging time expires, the access device deletes the user entry and reclaims the granted network access rights. If a user is successfully re-authenticated before the user entry aging time expires, the access device adds a user-authenticated entry and grants corresponding network access rights to the user. Table 1-6 lists the methods of configuring re-authentication modes for users in abnormal authentication state.
When users go offline but the access device and RADIUS server do not detect the offline events, the following problems may occur:
- The RADIUS server still performs accounting for the users, causing incorrect accounting.
- Unauthorized users may spoof IP addresses and MAC addresses of authorized users to access the network.
- If there are many offline users, these users are still counted as access users of the device. As a result, other users may fail to access the network.
The access device needs to detect user logout immediately, delete the user entry, and instruct the RADIUS server to stop accounting.
A user may log out in the following scenarios: The user proactively logs out on the client, the access device controls user logout, and the RADIUS server logs out the user.
A Client Logs Out
A user sends an EAPoL-Logoff packet through the client software to log out. Upon receipt of the packet, the access device returns an EAP-Failure packet to the client and changes the port status from authorized to unauthorized.
The Access Device Controls User Logout
The access device controls user logout in either of the following ways:
- Run the cut access-user command to force a user to go offline.
- Configure user detection to check whether a user is online. If the user does not respond within a specified period, the access device considers the user to be offline and deletes the user entry.
If an administrator detects that an unauthorized user is online or wants a user to go offline and then go online again during a test, the administrator can run the cut access-user command on the access device to force the user to go offline. For a user in normal access state, the access device checks the online status of the user through ARP probing. If the access device detects that the user goes offline, it logs the user out and deletes the user entry.
Assume that the handshake period of a user is 3T, which can be set by running the authentication timer handshake-period handshake-period command. Here, T = handshake-period /3.
- The user sends any packet to trigger 802.1X authentication, and the detection timer starts.
- Within several T periods, the access device receives traffic from the client and the user keeps online.
- The user sends the last packet. When the current T period expires, the access device determines that the user is online because traffic is still received from the client, and resets the detection timer.
- The access device does not receive traffic from the client within a T period, and sends the first ARP request packet. The client does not respond.
- The access device does not receive traffic from the client within another T period, and sends the second ARP request packet. The client does not respond.
- The access device does not receive traffic from the client within a third T period. The access device determines that ARP probing fails and deletes the user entry.
The RADIUS Server Forces a User to Log Out
The RADIUS server forces a user to log out using either of the following methods:
- Sends a Disconnect Message (DM) to an access device to force a user to go offline.
- Uses the standard RADIUS attributes Session-Timeout and Termination-Action . The Session-Timeout attribute specifies the online duration timer of a user. The value of Termination-Action is set to 0, indicating that the user is disconnected by the RADIUS server when the online duration timer expires.
802.1X relies on several timers to control the number of packet retransmission times and timeout interval. This section outlines the timers on the device that are relevant to the 802.1X authentication process.
Timeout Timers for EAP-Request/Identity Packets
This section discusses the timers that control the timeout and retry behavior of an 802.1X-enabled interface for sending EAP-Request/Identity packets.
During 802.1X authentication, the device sends an EAP-Request/Identity packet for the user name. The device waits for a period of time defined by a timer, and then sends another EAP-Request/Identity packet if no response is received. The number of times it resends the EAP-Request/Identity packets is defined by the dot1x retry max-retry-value variable.
Figure 1-9 shows the operation of the timer when MAC address bypasss authentication is not configured. If EAP-Request/Identity packets time out, the device sends an EAP failure packet to the client and starts a failover mechanism (Portal authentication or granting specified access permissions) if configured. In this situation, the timer is defined by the dot1x timer tx-period tx-period command. The total time it takes for 802.1X to time out is determined by the following formula:
Timeout = ( max-retry-value +1) x tx-period-value
Figure 1-10 shows the operation of the timer when MAC address bypass authentication is configured. The device performs 802.1X authentication first and starts the timer defined by the dot1x timer mac-bypass-delay delay-time-value command. If 802.1X authentication is not successful before the timer expires, the device performs MAC address authentication for terminals. In this situation, the interval at which the device resends an EAP-Request/Identity packet is the integer of the result calculated as follows: delay-time-value /( max-retry-value +1).
Timeout Timers for EAP-Request/MD5 Challenge Packets
This section discusses the timers that control the timeout and retry behavior of an 802.1X-enabled interface for sending EAP-Request/MD5 Challenge packets.
During 802.1X authentication, the device sends an EAP-Request/MD5 Challenge packet to request the client's password in ciphertext. It waits for a period of time defined by the client timeout timer, and then sends another EAP-Request/MD5 Challenge packet. The number of times it resends the EAP-Request/MD5 Challenge packets is defined by the dot1x retry max-retry-value variable. This prevents repeated retransmission of authentication requests, which occupies lots of resources.
As shown in Figure 1-11 , EAP-Request/MD5 Challenge packets time out, and then the device sends an EAP Failure packet to the client and starts a failover mechanism (MAC address authentication, Portal authentication, or granting specified access permissions) if configured. The total time it takes for EAP-Request/MD5 Challenge packets to time out is determined by the following formula:
Timeout = ( max-retry-value + 1) x client-timeout-value
Quiet Timer
This section discusses the timer that controls when 802.1X restarts after the number of failed 802.1X authentication attempts within 60 seconds reaches the value specified by the dot1x quiet-times fail-times command.
If 802.1X fails and there are no failover mechanisms enabled, the device waits for a period of time known as the quiet-period (configured by the dot1x timer quiet-period quiet-period-value command). During this period of time, the device discards users' 802.1X authentication request packets, avoiding frequent authentication failures.
Related Documents
WLAN Country Codes and Channels Compliance
How an AP Joins an AC and Troubleshooting Any Join Failures
What Are 802.11ac and 802.11ac Wave 2

- Collaboration
- Data Center
- Managed Services
- Assess and Design
- Wireless Surveys Assessments
- Project Management
- Lifecycle Management
- Integration Center
- Locations Serviced
- Wireless Survey Assessment
- +1 925-566-3480

- Free Consultation
Home Blog Cisco ISE: Wired and Wireless 802.1X Network Authentication
Cisco Security security cybersecurity Cisco ISE Identity Services Engine identity and authentication authentication network authentication
Cisco Identity Services Engine Blog Series
This is the first entry in a series of blog posts that will discuss the various facets of Cisco’s Identity Services Engine (ISE). The first topic, explored here, is wired and wireless 802.1X network authentication. In this entry, Authenticate all the things! We will review the 802.1X authentication architecture and its high-level components.
What is 802.1X?
The first thing that should be understood about 802.1X is that it is not a single thing or protocol. Furthermore, 802.1X itself is a component of an even larger system of network access controls, commonly referred to in the industry as NAC solutions. Cisco ISE is an example of one such NAC system. 802.1X is a network level authentication and authorization framework that serves as a fundamental component of any comprehensive NAC solution. This 802.1X authentication framework involves a system of hardware/software components and protocols. IP networks employ 802.1X for the purpose of requiring endpoint users and/or endpoint devices to authenticate themselves before being granted (potentially) differentiated levels of access to a wired or wireless network connection. Figure 1 below provides an illustration of the components and protocols that comprise an 802.1X architecture.
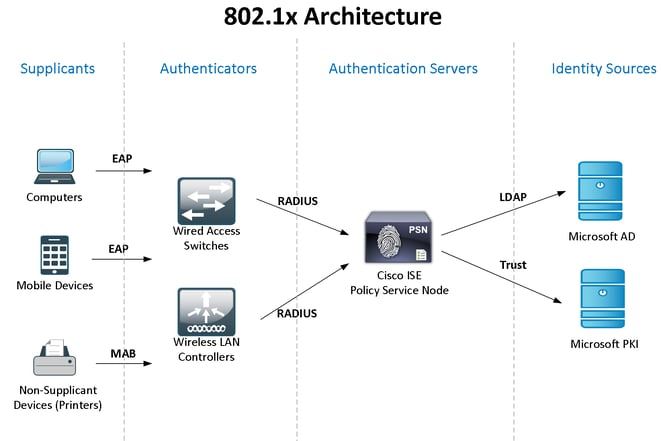
A Supplicant is a piece of software running on an endpoint. The supplicant is responsible for providing the user/device authentication credential to the authentication server. This credential is provided, by the supplicant, to the Authenticator via the Extensible Authentication Protocol (EAP). EAP is a link local protocol (meaning it is only transmitted over the direct link between two devices; an endpoint and a switch or an endpoint and a wireless AP/controller). As such, it is the authenticators role to proxy this EAP data from the supplicant to the authentication server using RADIUS encapsulation, which is a routable protocol capable of being transmitted to any reachable destination on an IP network. Authentication Servers are responsible for validating/authenticating the credential received in the RADIUS message and returning an authorization result back to the authenticator. The credential presented to the authentication server can be representative of the device or user requesting connection to the network, or in some case, both. Identity Sources are identity stores/directories that an authentication server (Cisco ISE) can use to validate authentication credentials provided by the supplicant. Additionally, they can be used to retrieve additional attributes (such as Windows Security Group membership in the case of Microsoft AD) to make decisions about what permissions the endpoint should have on the network (otherwise put --> what they are authorized to do). While Cisco ISE can host an internal user/endpoint directory, it is most common that an existing directory/identity store will be leveraged for user authentication and attribute retrieval.
What's Next?
In our next entry to this series, we will delve deeper into 802.1X EAP Authentication Types to get a better understanding of the authentication options (user authentication vs. computer authentication and usernames/passwords vs. certificates, etc..) available.

Written By: Dominic Zeni, LookingPoint Consulting Services SME - CCIE #26686
If you are interested in LookingPoint installing ISE into your network, feel free to contact us here!

- cybersecurity
- collaboration
- cisco webex
Latest Tweets
Subscribe to our blog, get new unique posts.

- Privacy Policy
Looking Point Inc. 2019
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Advanced troubleshooting 802.1X authentication
- 4 contributors
Try our Virtual Agent - It can help you quickly identify and fix common Wireless technology issues.
Applies to: Windows 10
This article includes general troubleshooting for 802.1X wireless and wired clients. While troubleshooting 802.1X and wireless, it's important to know how the flow of authentication works, and then figure out where it's breaking. It involves many third-party devices and software. Most of the time, we have to identify where the problem is, and another vendor has to fix it. We don't make access points or switches, so it's not an end-to-end Microsoft solution.
This troubleshooting technique applies to any scenario in which wireless or wired connections with 802.1X authentication are attempted and then fail to establish. The workflow covers Windows 7 through Windows 10 (and Windows 11) for clients, and Windows Server 2008 R2 through Windows Server 2012 R2 for NPS.
Known issues
Data collection.
See Advanced troubleshooting 802.1X authentication data collection .
Troubleshooting
Viewing NPS authentication status events in the Windows Security event log is one of the most useful troubleshooting methods to obtain information about failed authentications.
NPS event log entries contain information about the connection attempt, including the name of the connection request policy that matched the connection attempt and the network policy that accepted or rejected the connection attempt. If you don't see both success and failure events, see the NPS audit policy section later in this article.
Check the Windows Security event log on the NPS Server for NPS events that correspond to the rejected ( event ID 6273 ) or the accepted ( event ID 6272 ) connection attempts.
In the event message, scroll to the bottom, and then check the Reason Code field and the text that's associated with it.

The WLAN AutoConfig operational log lists information and error events based on conditions detected by or reported to the WLAN AutoConfig service. The operational log contains information about the wireless network adapter, the properties of the wireless connection profile, the specified network authentication, and, if connectivity problems occur, the reason for the failure. For wired network access, the Wired AutoConfig operational log is an equivalent one.
On the client side, go to Event Viewer (Local)\Applications and Services Logs\Microsoft\Windows\WLAN-AutoConfig/Operational for wireless issues. For wired network access issues, go to ..\Wired-AutoConfig/Operational . See the following example:

Most 802.1X authentication issues are because of problems with the certificate that's used for client or server authentication. Examples include invalid certificate, expiration, chain verification failure, and revocation check failure.
First, validate the type of EAP method that's used:

If a certificate is used for its authentication method, check whether the certificate is valid. For the server (NPS) side, you can confirm what certificate is being used from the EAP property menu. In NPS snap-in , go to Policies > Network Policies . Select and hold (or right-click) the policy, and then select Properties . In the pop-up window, go to the Constraints tab, and then select the Authentication Methods section.

The CAPI2 event log is useful for troubleshooting certificate-related issues. By default, this log isn't enabled. To enable this log, expand Event Viewer (Local)\Applications and Services Logs\Microsoft\Windows\CAPI2 , select and hold (or right-click) Operational , and then select Enable Log .

For information about how to analyze CAPI2 event logs, see Troubleshooting PKI Problems on Windows Vista .
When troubleshooting complex 802.1X authentication issues, it's important to understand the 802.1X authentication process. Here's an example of wireless connection process with 802.1X authentication:

If you collect a network packet capture on both the client and the server (NPS) side, you can see a flow like the one below. Type EAPOL in the Display Filter for a client-side capture, and EAP for an NPS-side capture. See the following examples:

Client-side packet capture data

NPS-side packet capture data
If you have a wireless trace, you can also view ETL files with network monitor and apply the ONEX_MicrosoftWindowsOneX and WLAN_MicrosoftWindowsWLANAutoConfig Network Monitor filters. If you need to load the required parser , see the instructions under the Help menu in Network Monitor. Here's an example:

Audit policy
By default, NPS audit policy (event logging) for connection success and failure is enabled. If you find that one or both types of logging are disabled, use the following steps to troubleshoot.
View the current audit policy settings by running the following command on the NPS server:
If both success and failure events are enabled, the output should be:
If it says, "No auditing," you can run this command to enable it:
Even if audit policy appears to be fully enabled, it sometimes helps to disable and then re-enable this setting. You can also enable Network Policy Server logon/logoff auditing by using Group Policy. To get to the success/failure setting, select Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Logon/Logoff > Audit Network Policy Server .
More information
- Troubleshooting Windows Vista 802.11 Wireless Connections
- Troubleshooting Windows Vista Secure 802.3 Wired Connections
Was this page helpful?
Additional resources
Home > Network Security > Use IEEE 802.1x Authentication for Your Network > Configure IEEE 802.1x Authentication for Your Network Using Web Based Management (Web Browser)

Configure IEEE 802.1x Authentication for Your Network Using Web Based Management (Web Browser)
- If you configure your machine using EAP-TLS authentication, you must install the client certificate issued by a CA before you start configuration. Contact your network administrator about the client certificate. If you have installed more than one certificate, we recommend writing down the certificate name you want to use.
- Before you verify the server certificate, you must import the CA certificate issued by the CA that signed the server certificate. Contact your network administrator or your Internet Service Provider (ISP) to confirm whether a CA certificate import is necessary.
You can also configure IEEE 802.1x authentication using the Wireless Setup Wizard from the control panel (Wireless network).
- Start your web browser.
For example:
https://192.168.1.2
Your machine's IP address can be found in the Network Configuration Report.
Click Wired > Wired 802.1x Authentication .
Click Wireless > Wireless (Enterprise) .
- To enable IEEE 802.1x authentication for wired networks, select Enabled for Wired 802.1x status on the Wired 802.1x Authentication page.
- If you are using EAP-TLS authentication, you must select the client certificate installed (shown with certificate name) for verification from the Client Certificate drop-down list.
- If you select EAP-FAST , PEAP , EAP-TTLS , or EAP-TLS authentication, select the verification method from the Server Certificate Verification drop-down list. Verify the server certificate using the CA certificate, imported to the machine in advance, issued by the CA that signed the server certificate.
- Use IEEE 802.1x Authentication for Your Network
- Security Certificate Features Overview
- Configure Certificates for Device Security
Please do not include any personal information in your comment. This form is used for feedback only.
Thank you for your feedback.
en-US/US US ENG
Legal | Privacy Policy | Global Site
© 2024 Brother Industries, Ltd. All rights reserved.
- 802.1x Configuration
The Presentation System have built-in support for the 802.1X standard (an IEEE network standard designed to enhance the security of wireless and Ethernet LANs. The standard relies on the exchange of messages between the device and the network's host, or authentication server), allowing communication with the authentication server and access to protected corporate networks.

- To Configure Presentation System for 802.1X Authentication
- Move the IEEE 802.1X Authentication slider to enabled. This will enable all options on the 802.1X dialog.
- Select the Authentication method : EAP-TLS Certificate or EAP-MSCHAP V2 Password according to the network administrator's requirement.
- Do either one of the following:
- Select EAP-TLS Certificate. Click Action/Manage Certificates to upload the required machine certificate. The machine certificate is an encrypted file that will be supplied by the network administrator, along with the certificate password.
- Select EAP-MSCHAP V2 Password . Enter the Username and Password supplied by the network administrator into the Username and Password fields. This method does not require the use of a machine certificate, only the user name and password credentials.
Select the check box next to each CA whose certificate can be used for server validation, as specified by the network administrator.
NOTE : If the network does not use any of the listed certificates, the network administrator must provide a certificate, which must be uploaded manually via the Manage Certificates functionality.
- If required, type the domain name of the network in the Domain field.
- When the 802.1X settings are configured as desired, click Save Changes to save the changes to the device and reboot it. Click Revert to cancel any changes.
© 2022 Crestron Electronics, Inc.
All brand names, product names and trademarks are the property of their respective owners. Certain trademarks, registered trademarks, and trade names may be used to refer to either the entities claiming the marks and names or their products. Crestron disclaims any proprietary interest in the marks and names of others. Crestron is not responsible for errors in typography or photography. Specifications are subject to change without notice.
Patents | Legal | Crestron Europe Terms | Privacy Policy | Terms of Use | Support

COMMENTS
It's authentication and nothing more. 802.1X is still widely used today, while PPP is largely obsolete. You can also use 802.1X with protocols other than TCP/IP. How 802.1X authentication works.
Wired access deployment requires server certificates for each NPS server that performs 802.1X authentication. A server certificate is a digital document that is commonly used for authentication and to help secure information on open networks. A certificate securely binds a public key to the entity that holds the corresponding private key.
When IEEE 802.1X port-based authentication is enabled and the device attempting to authenticate is IEEE 802.1x-capable (meaning it supports the supplicant functionality), this event occurs: If the supplicant identity is valid and the IEEE 802.1X authentication succeeds, the router grants the supplicant access to the network.
Devices that are trying to connect to an 802.1X network need to have software installed on them, and this is referred to as the supplicant. The supplicant is needed because it initiates the connection by engaging in an Extensible Authentication Protocol (EAP) transaction between the supplicant and the controller or switch.
IEEE 802.1X is an IEEE Standard for port-based network access control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN.. The standard directly addresses an attack technique called Hardware Addition [1] where an attacker posing as a guest, customer or staff smuggles a hacking device into the ...
802.1X Authentication Definition. 802.1X authentication is a network access control standard that provides a framework for securing and controlling access to a local area network (LAN) or a wireless LAN (WLAN). It is defined in the IEEE 802.1X standard and is widely used to ensure that only authorized devices and users can connect to a network.
Analysis of 4-way handshake protocol in IEEE 802.11i Changhua He Stanford University Mar. 04, 2004 Scenario: 802.11 An example of a 802.11 wireless local area network History of Security Concerns 802.11b (WEP) Wired Equivalent Protocol Many attacks found WPA: Wi-Fi Protected Access Proposed by Wi-Fi Alliance Short-term solution based on 802.1x 802.11i Standards approved Oct. 2003 Long-term ...
• 802.1X authentication involves three parties: • A supplicant (which is a CLIENT) • An authenticator (an access point) • An authentication server (a RADIUS server) IEEE 802.1x • The authenticator (access point) acts like a security guard to a protected network. • The supplicant (CLIENT) is not allowed access through the ...
This document describes the basic principles of 802.1X authentication.
Understanding 802.1X Port-Based Authentication 802.1X defines 802.1X port-based authentication as a client-server based access control and authentication protocol that restricts unauthorized clients from connecting to a LAN through publicly accessible ports. An authentication server validates each supplicant (client) connected to an
Times New Roman Comic Sans MS Wingdings 宋体 Arial Narrow my presentation Security Analysis and Improvements for IEEE 802.11i Outline Wireless Threats IEEE 802.11i 802.11i: Confidentiality & Integrity 802.11i: Mutual Authentication RSNA Conversations Outline Security Level Rollback Attack Security Rollback: solutions Reflection Attack ...
This 802.1X authentication framework involves a system of hardware/software components and protocols. IP networks employ 802.1X for the purpose of requiring endpoint users and/or endpoint devices to authenticate themselves before being granted (potentially) differentiated levels of access to a wired or wireless network connection.
Extensible Authentication Protocol-Tunneled Transport Layer Security (EAP-TTLS) has been developed by Funk Software and Certicom. EAP-TTLS creates a similar encrypted SSL tunnel to PEAP, between a client and an authentication server, for sending a user ID and password. EAP-TTLS provides mutual authentication between the server and the client.
When troubleshooting complex 802.1X authentication issues, it's important to understand the 802.1X authentication process. Here's an example of wireless connection process with 802.1X authentication: If you collect a network packet capture on both the client and the server (NPS) side, you can see a flow like the one below.
To enable IEEE 802.1x authentication for wired networks, select Enabled for Wired 802.1x status on the Wired 802.1x Authentication page. If you are using EAP-TLS authentication, you must select the client certificate installed (shown with certificate name) for verification from the Client Certificate drop-down list.
Step 1. Navigate to Policy > Authentication€as shown in the image. Step 2. Insert a new authentication rule as shown in the image. Step 3. Enter the values. This authentication rule allows all the protocols listed under the Default Network Access€list. This applies to Also, choose the Identity source for the clients that match this ...
The Presentation System have built-in support for the 802.1X standard (an IEEE network standard designed to enhance the security of wireless and Ethernet LANs. The standard relies on the exchange of messages between the device and the network's host, or authentication server), allowing communication with the authentication server and access to ...