The Essentials of Effective Project Risk Assessments
By Kate Eby | September 19, 2022
- Share on Facebook
- Share on LinkedIn
Link copied
Performing risk assessments is vital to a project’s success. We’ve gathered tips from experts on doing effective risk assessments and compiled a free, downloadable risk assessment starter kit.
Included on this page, you’ll find details on the five primary elements of risk , a comprehensive step-by-step process for assessing risk , tips on creating a risk assessment report , and editable templates and checklists to help you perform your own risk assessments.

What Is a Project Risk Assessment?
A project risk assessment is a formal effort to identify and analyze risks that a project faces. First, teams identify all possible project risks. Next, they determine the likelihood and potential impact of each risk.
During a project risk assessment, teams analyze both positive and negative risks. Negative risks are events that can derail a project or significantly hurt its chances of success. Negative risks become more dangerous when teams haven’t identified them or created a plan to deal with them.
A project risk assessment also looks at positive risks. Also called opportunities, positive risks are events that stand to benefit the project or organization. Your project team should assess those risks so they can seize on opportunities when they arise.
Your team will want to perform a project risk assessment before the project begins. They should also continually monitor for risks and update the assessment throughout the life of the project.
Some experts use the term project risk analysis to describe a project risk assessment. However, a risk analysis typically refers to the more detailed analysis of a single risk within your broader risk assessment. For expert tips and information, see this comprehensive guide to performing a project risk analysis.
Project risk assessments are an important part of project risk management. Learn more from experts about best practices in this article on project risk management . For even more tips and resources, see this guide to creating a project risk management plan .
How Do You Assess Risk in a Project?
Teams begin project risk assessments by brainstorming possible project risks. Avoid missing important risks by reviewing events from similar past projects. Finally, analyze each risk to understand its time frame, probability, factors, and impact.
Your team should also gather input from stakeholders and others who might have thoughts on possible risks.
In general terms, consider these five important elements when analyzing risks:
- Risk Event: Identify circumstances or events that might have an impact on your project.
- Risk Time Frame: Determine when these events are most likely to happen. This might mean when they happen in the lifecycle of a project or during a sales season or calendar year.
- Probability: Estimate the likelihood of an event happening.
- Impact: Determine the impact on the project and your organization if the event happens.
- Factors: Determine the events that might happen before a risk event or that might trigger the event.
Project Risk Assessment Tools
Project leaders can use various tools and methodologies to help measure risks. One option is a failure mode and effects analysis. Other options include a finite element analysis or a factor analysis and information risk.
These are some common risk assessment tools:
- Process Steps: Identify all steps in a process.
- Potential Problems: Identify what could go wrong with each step.
- Problem Sources: Identify the causes of the problem.
- Potential Consequences: Identify the consequences of the problem or failure.
- Solutions: Identify ways to prevent the problem from happening.
- Finite Element Analysis (FEA): This is a computerized method for simulating and analyzing the forces on a structure and the ways that a structure could break. The method can account for many, sometimes thousands, of elements. Computer analysis then determines how each of those elements works and how often the elements won’t work. The analysis for each element is then added together to determine all possible failures and the rate of failure for the entire product.
- Factor Analysis of Information Risk (FAIR): This framework helps teams analyze risks to information data or cybersecurity risk.
How to Conduct a Project Risk Assessment
The project manager and team members will want to continually perform risk assessments for a project. Doing good risk assessments involves a number of steps. These steps include identifying all possible risks and assessing the probability of each.
Most importantly, team members must fully explore and assess all possible risks, including risks that at first might not be obvious.

“The best thing that a risk assessment process can do for any project, over time, is to be a way of bringing unrecognized assumptions to light,” says Mike Wills , a certified mentor and coach and an assistant professor at Embry-Riddle Aeronautical University’s College of Business. “We carry so many assumptions without realizing how they constrain our thinking.”
Steps in a Project Risk Assessment
Experts recommend several important steps in an effective project risk assessment. These steps include identifying potential risks, assessing their possible impact, and formulating a plan to prevent or respond to those risks.
Here are 10 important steps in a project risk assessment:
Step 1: Identify Potential Risks
Bring your team together to identify all potential risks to your project. Here are some common ways to help identify risks, with tips from experts:
- Review Documents: Review all documents associated with the project.
- Consider Industry-Specific Risks: Use risk prompt lists for your industry. Risk prompt lists are broad categories of risks, such as environmental or legal, that can occur in a project.
- Revisit Previous Projects: Use checklists from similar projects your organization has done in the past.

- “What I like to do for specific types of projects is put together a checklist, a taxonomy of old risks that you've identified in other projects from lessons learned,” says Wendy Romeu, President and CEO of Alluvionic . “Say you have a software development program. You would pull up your template that includes all the risks that you realized in other projects and go through that list of questions. Then you would ask: ‘Do these risks apply to our project?’ That's kind of a starting point.” “You do that with your core project team,” Romeu says, “and it gets their juices flowing.” Learn more about properly assessing lessons learned at the end of a project in this comprehensive guide to project management lessons learned .
- Consult Experts: Conduct interviews with experts within and, in some cases, outside your organization.
- Brainstorm: Brainstorm ideas with your team. “The best scenario, which doesn't usually happen, is the whole team comes together and identifies the risks,” says Romeu.
- Stick to Major Risks: Don’t try to identify an unrealistic or unwieldy number of risks. “You want to identify possible risks, but you want to keep the numbers manageable,” says Wills. “The more risks you identify, the longer you spend analyzing them. And the longer you’re in analysis, the fewer decisions you make.”
- Look for Positive Risks: Identify both positive risks and negative ones. It’s easy to forget that risks aren’t all negative. There can be unexpected positive events as well. Some people call these opportunities , but in a risk assessment, experts call them positive risks.

- “A risk is a future event that has a likelihood of occurrence and an impact,” says Alan Zucker, founding principal of Project Management Essentials , who has more than two decades of experience managing projects in Fortune 100 companies. “Risks can both be opportunities — good things — and threats. Most people, when they think about risk assessment, they always think about the negatives. I really try to stress on people to think about the opportunities as well.” Opportunities, or positive risks, might include your team doing great work on a project and a client wanting the team to do more work. Positive risks might include a project moving forward more quickly than planned or costing less money than planned. You’ll want to know how to respond in those situations, Zucker says. Learn more about project risk identification and find more tips from experts in this guide to project risk identification .
Step 2: Determine the Probability of Each Risk
After your team has identified possible risks, you will want to determine the probability of each risk happening. Your team can make educated guesses using some of the same methods it used to identify those risks.
Determine the probability of each identified risk with these tactics:
- Brainstorm with your team.
- Interview experts.
- Review similar past projects.
- Review other projects in the same industry.
Step 3: Determine the Impact of Each Risk
Your team will then determine the impact of each risk should it occur. Would the risk stop the project entirely or stop the development of a product? Or would the risk occurring have a relatively minor impact?
Assessing impact is important because if it’s a positive risk, Romeu says, “You want to make sure you’re doing the things to make it happen. Whereas if it's a high risk and a negative situation, you want to do the things to make sure it doesn't happen.”
There are two ways to measure impact: qualitative and quantitative. “Are we going to do just a qualitative risk assessment, where we're talking about the likelihood and the probability or the urgency of that risk?” asks Zucker. “Or are we going to do a quantitative risk assessment, where we're putting a dollar figure or a time figure to those risks?”
Most often, a team will analyze and measure risk based on qualitative impact. The team will analyze risk based on a qualitative description of what could happen, such as a project being delayed or failing. The team may judge that impact as significant but won’t put a dollar figure on it.
A quantitative risk assessment, on the other hand, estimates the impact in numbers, often measured in dollars or profits lost, should a risk happen. “Typically, for most projects, we don’t do a quantitative risk assessment,” Zucker says. “It’s usually when we’re doing engineering projects or big, federal projects. That’s where we're doing the quantitative.”
Step 4: Determine the Risk Score of Each Event
Once your team assesses possible risks, along with the risk probability and impact, it’s time to determine a risk score for each potential event. This score allows your organization to understand the risks that need the most attention.
Often, teams will use a simple risk matrix to determine that risk score. Your team will assign a score based on the probability of each risk event. It will then assign a second score based on the impact that event would have on the organization. Those two figures multiplied will give you each event or risk a risk score.
Zucker says he prefers to assign the numbers 1, 5, and 10 — for low, medium, and high — to both the likelihood of an event happening and its impact. In that scenario, an event with a low likelihood of happening (level of 1) and low impact (level of 1) would have a total risk score of 1 (1 multiplied by 1). An event with a high likelihood of happening (level of 10) and a large impact (level of 10) would have a total risk score of 100.
Zucker says he prefers using those numbers because a scale as small as one to three doesn't convey the importance of high-probability and high-impact risks. “A nine doesn't feel that bad,” he says. “But if it's 100, it's like, ‘Whoa, I really need to worry about that thing.’”
While these risk matrices use numbers, they are not really quantitative. Your teams are making qualitative judgments on events and assigning a rough score. In some cases, however, teams can determine a quantitative risk score.
Your team might determine, based on past projects or other information, that an event has a 10 percent chance of happening. For example, if that event will diminish your manufacturing plant’s production capacity by 50 percent for one month, your team might determine that it will cost your company $400,000. In that case, the risk would have a risk score of $40,000.
At the same time, another event might have a 40 percent chance of happening. Your team might determine the cost to the business would be $10,000. In that case, the risk score is $4,000.
“Just simple counts start to give you a quantifiable way of looking at risk,” says Wills. “A risk that is going to delay 10 percent of your production capacity is a different kind of risk than one that will delay 50 percent of it. Because you have a number, you can gather real operational data for a week or two and see how things support the argument. You can start to compare apples to apples, not apples to fish.”
Wills adds, “Humans, being very optimistic and terrible at predicting the future, will say, ‘Oh, I don't think it'll happen very often.’ Quantitative techniques help to get you away from this gambler fallacy kind of approach. They can make or break your argument to a stakeholder that says, ‘I've looked at this, and I can explain mechanically, count by the numbers like an accountant, what's going on and what might go wrong.’”
Step 5: Understand Your Risk Tolerance
As your team considers risks, it must understand the organization’s risk tolerance. Your team should know what kinds of risks that organizational leaders and stakeholders are willing to take to see a project through.
Understanding that tolerance will also help your team decide how and where to invest time and resources in order to prevent certain negative events.
Step 6: Decide How to Prioritize Risks
Once your team has determined the risk score for each risk, it will see which potential risks need the most attention. These are risks that are high impact and that your organization will want to work hard to prevent.
“You want to attack the ones that are high impact and high likelihood first,” says Romeu.
“Some projects are just so vital to what you do and how you do it that you cannot tolerate the risk of derailment or major failure,” says Wills. “So you're willing to spend money, time, and effort to contain that risk. On other projects, you're taking a flier. You're willing to lose a little money, lose a little effort.”
“You have to decide, based on your project, based on your organization, the markets you're in, is that an ‘oh my gosh, it's gonna keep me up every night’ kind of strategic risk? Or is it one you can deal with?” he says.
Step 7: Develop Risk Response Strategies
Once your team has assessed all possible risks and ranked them by importance, you will want to dive deeper into risk response strategies. That plan should include ways to respond to both positive and negative risks.
These are the main strategies for responding to threats or negative risks:
- Mitigate: These are actions you will take to reduce the likelihood of a risk event happening or that will reduce the impact if it does happen. “For example, if you’re building a datacenter, we might have backup power generators to mitigate the likelihood or the impact of a power loss,” says Zucker. You can learn more, including more tips from experts, about project risk mitigation .
- Avoid: If a certain action, new product, or new service carries an unacceptably high risk, you might want to avoid it entirely.
- Transfer: The most common way that organizations transfer risk is by buying insurance. A common example is fire insurance for a building. Another is cybersecurity insurance that would cover your company in the event of a data breach. An additional option is to transfer certain risks to other companies that can do the work and assume its risks for your company. “It could be if you didn't want to have the risk of running a datacenter anymore, you transfer that risk to Jeff Bezos (Amazon Web Services) or to Google or whoever,” Zucker says.
These are the main strategies for responding to opportunities or positive risks:
- Share: Your company might partner with another company to work together on achieving an opportunity, and then share in the benefits.
- Exploit: Your company and team work hard to make sure an event happens because it will benefit your company.
- Enhance: Your company works to improve the likelihood of something happening, with the understanding that it might not happen.
These are the main strategies for responding to both threats and opportunities, or negative and positive risks:
- Accept: Your company simply accepts that a risk might happen but continues on because the benefits of the action are significant. “You're not ignoring the risks, but you're saying, ‘I can't do anything practical about them,’” says Wills. “So they're there. But I'm not going to spend gray matter driving myself crazy thinking about them.”
- Escalate: This is when a project manager sees a risk as exceptionally high, impactful, and beyond their purview. The project manager should then escalate information about the risk to company leaders. They can then help decide what needs to happen. “Some project managers seem almost fearful about communicating risks to organization leaders,” Romeu says. “It drives me nuts. It's about communicating at the right level to the right people. At the executive level, it’s about communicating what risks are happening and what the impact of those risks are. If they happen, everybody knows what the plan is. And people aren't taken by surprise.”
Step 8: Monitor Your Risk Plans
Your team will want to understand how viable your organization’s risk plans are. That means you might want to monitor how they might work or how to test them.
A common example might be all-hands desktop exercises on a disaster plan. For example, how will a hospital respond to a power failure or earthquake? It’s like a fire drill, Zucker says. “Did we have a plan? Do people know what to do when the risk event occurs?”
Step 9: Perform Risk Assessments Continually
Your team will want to continually assess risks to the project. This step should happen throughout your project, from project planning to execution to closeout.
Zucker explains that the biggest mistake teams tend to make with project risk assessment: “People think it's a one-and-done event. They say, ‘I’ve put together my risk register, we’ve filed it into the documents that we needed to file, and I'm not worrying about it.’ I think that is probably the most common issue: that people don't keep it up. They don't think about it.”
Not thinking about how risks change and evolve throughout a project means project leaders won’t be ready for something when it happens. That’s why doing continual risk assessment as a primary part of risk management is vital, says Wills.
“Risk management is a process that should start before you start doing that activity. As you have that second dream about doing that project, start thinking about risk management,” he says. “And when you have completely retired that thing — you've shut down the business, you've pensioned everybody off, you’re clipping your coupons and working on your backstroke — that's when you're done with risk management. It's just a living, breathing, ongoing thing.”
Experts say project managers must learn to develop a sense for always assessing and monitoring risk. “As a PM, you should, in every single meeting you have, listen for risks,” Romeu says. “A technical person might say, ‘Well, this is going to be difficult because of X or Y or Z.’ That's a risk. They don't understand that's a risk, but as a PM, you should be aware of that.”
Step 10: Identify Lessons Learned
After your project is finished, your team should come together to identify the lessons learned during the project. Create a lessons learned document for future use. Include information about project risks in the discussion and the final document.
By keeping track of risks in a lessons learned document, you allow future leaders of similar projects to learn from your successes and failures. As a result, they can better understand the risks that could affect their project.
“Those lessons learned should feed back into the system — back into that original risk checklist,” Romeu says. “So the next software development project knows to look at these risks that you found.”
How to Write a Project Risk Assessment Report
Teams will often track risks in an online document that is accessible to all team members and organization leaders. Sometimes, a project manager will also create a separate project risk assessment report for top leaders or stakeholders.
Here are some tips for creating that report:
- Find an Appropriate Template for Your Organization, Industry, and Project: You can find a number of templates that will help guide you in creating a risk assessment report. Find a project risk assessment report template in our project risk assessment starter kit.
- Consider Your Audience: As you create the report, remember your audience. For example, a report for a technical team will be more detailed than a report for the CEO of your company. Some more detailed reports for project team members might include a full list of risks, which would be 100 or more. “But don't show executives that list; they will lose their mind,” says Romeu.
Project Risk Assessment Starter Kit
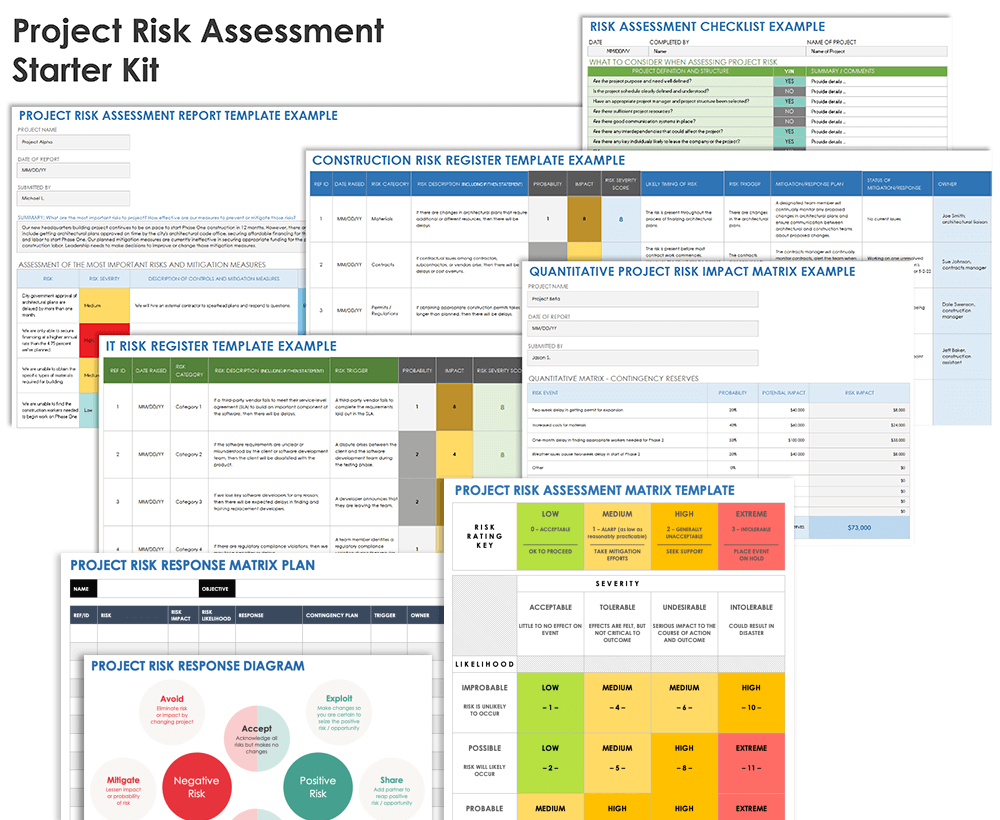
Download Project Risk Assessment Starter Kit
This starter kit includes a checklist on assessing possible project risks, a risk register template, a template for a risk impact matrix, a quantitative risk impact matrix, a project risk assessment report template, and a project risk response table. The kit will help your team better understand how to assess and continually monitor risks to a project.
In this kit, you’ll find:
- A risk assessment checklist PDF document and Microsoft Word to help you identify potential risks for your project. The checklist included in the starter kit is based on a document from Alluvionic Project Management Services.
- A project risk register template for Microsoft Excel to help you identify, analyze, and track project risks.
- A project risk impact assessment matrix for Microsoft Excel to assess the probability and impact of various risks.
- A quantitative project risk impact matrix for Microsoft Excel to quantify the probability and impact of various risks.
- A project risk assessment report template for Microsoft Excel to help you communicate your risk assessment findings and risk mitigation plans to company leadership.
- A project risk response diagram PDF document and Microsoft Word to better understand how to respond to various positive and negative risks.
Expertly Assess and Manage Project Risks with Real-Time Work Management in Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Discover why over 90% of Fortune 100 companies trust Smartsheet to get work done.
Introduction to Risk Assessment in Project Management
Project Management Institute’s (PMI) inclusion of risk management skills in multiple PMI certifications indicates the importance of risk across industries and in all projects. The risk management process includes risk identification and risk assessment. During an assessment, the project manager uses standard risk tools and quality data to help the team better avert later problems, manage the project cost, and keep project work on schedule. Risk assessment is the process by which the identified risks are systematically analyzed to determine their probability of occurrence and the potential impact of that occurrence.
On this page:
What is a risk assessment?
What are risk assessment pmp and risk reassessment pmp, when is a risk assessment needed, why is a risk assessment important, example use of risk assessment: hurricane impacting town, what inputs are needed for a risk assessment, what is a risk data quality assessment pmp, what outputs does a risk assessment generate, how to create a risk assessment, risk assessment matrix, risk assessment best practices, risk assessment pmp and risk reassessment pmp.
Get Your Comprehensive Guide to Risk Management
Learn how to manage risk in every project.
Project teams use risk assessment, a qualitative measure using risk data and the parameters of probability and impact, to identify, categorize, prioritize, and manage risks before they happen.
A “risk reassessment” is the work done to update the original risk assessment due to changes in the project or overall risk management efforts.
For the original and subsequent assessments, the quality of data used to determine the impact directly correlates to the accuracy of the risk assessment and resulting decisions.
Project Management Professional (PMP)® credential holders have shown their knowledge of a risk assessment and their understanding of the high cost of a failure to do a risk assessment. For the PMP certification exam, students need to know the importance of a risk assessment and how to use a probability and impact scoring matrix to help inform the priority of the risk.
Within the PMP exam context, “risk assessment PMP” and “risk reassessment PMP” are informal terms referring to taking identified risks and assessing them using qualitative data, such as the probability of occurrence, to determine the potential impact. From that, project managers determine the risk score, which is an input to subsequent risk response activities.
Risk identification should happen early in the project , closely followed by the risk assessment. Project teams should conduct risk reassessment throughout the life of a project. Updating the risk register is a good reminder to update the corresponding risk assessment. The project’s scope and risk management plan will inform how frequently the reassessment should be conducted (projects of bigger scope should have more reassessments; similarly, smaller scope requires fewer reassessments).
Performing a risk assessment is critical to ensuring the success of a project because it puts the project team in a state of preparedness. When done with verified tools and quality inputs, risk assessment may take time but can prevent problems from negative risks and enable opportunities from positive risks. As shared in the PMI conference paper Risk Assessments—developing the right assessment for your organization , “The best project organizations are those who realize that a risk assessment template is a valuable asset in managing the organization’s bottom line.” Risk assessment connects to managing cost, timelines, and quality.
For an example of how a risk assessment can be used, we use the example of a small municipality located on the east coast of North Carolina. The coastal town has been impacted by natural disasters in the form of hurricanes several times in the past fifty years. A hurricane is a storm that starts in the ocean and moves inland, causing all levels of flooding, electrical storms, and damaging winds. The National Weather Service provides annual forecasts of which geographic regions are predicted to have hurricanes, as well as the number of occurrences and strength of hurricanes.
The town manager (“project manager”) and the town administration (“project team”) know a hurricane will happen but not when or how strong it may be. In the risk category of weather events, the project manager and project team identify the risk type of hurricane storm. Then the project team identifies specific potential risks, such as flooding that may cause building damage. The team assesses each risk in terms of probability (or how likely it is to occur), the impact if it occurs, and the probability-impact score (weighing the significance of the risk on the project). The information is captured in a risk assessment matrix as part of the project management and risk management documentation.
For example, they do a risk assessment after the project manager and team identify the risk of water damage to downtown buildings due to hurricane-induced flooding. The team uses standard tools to determine the probability of that specific risk (flooding) and the impact if it occurs (water damage to buildings). The project team uses verified data, like National Weather Service hurricane projections, for probability estimates. For the potential impact, the project team uses cost and quality data like town records to determine what could happen to town property. The data and risk scoring are organized in the project risk assessment matrix and communicated to stakeholders.
Continuing our example of the identified risk of water damage to ground floors, if the assessment indicates the risk is highly likely to occur with a high impact of damage, it will have a higher risk score. That can mean more time invested in risk response planning (such as securing funding to buy and store sandbag materials during flooding to reduce the impact of water damage on buildings). The risk response plan would likely include purchasing sandbag materials before a hurricane, storing them in an accessible space, and training the town staff to set up the sandbags to protect critical buildings when a hurricane is imminent. The cost of buying and storing sandbag materials to protect the buildings is much lower than the cost of fully repairing water-damaged buildings.
In this risk example, the project team:
- determined the appropriate risk categories (natural disasters)
- determined the types within the category (hurricane storms)
- identified a risk event (hurricane bringing flooding to downtown buildings),
- assessed the impact of that risk (flooding damages ground floors),
- assessed the probability of the impact (flooding may be higher or lower but always occurs with hurricanes),
- documented the risk information, including risk scores in the risk assessment matrix,
- communicated the risk assessment results to the team and stakeholders, and then
- used the risk assessment matrix as an input for risk response planning (making sandbag materials available when needed and training people to set them up).
With this example, you should see the risk assessment allows the project team to identify, categorize, prioritize, and mitigate/avoid/exploit risks prior to their occurrence. A risk assessment is a proactive approach in which the risk is identified and assessed to manage cost, reduce negative impact, and protect the project (in this example, town buildings).
A risk assessment should be customized to fit the project context. Standard risk assessment inputs include:
- Project management plan
- Risk management plan
- Risk assessment methodology
- Risk parameter definitions
- Risk tolerance levels
- Risk probability and impact matrix template
- Risk assessment scale (what criteria are used to determine if the risk score is high, mid, or low)
- Risk assessment matrix template
Project managers and project management students use what is informally referred to as the “assessment of other risk parameters PMP” to tailor their risk assessment to a specific project. While probability and impact values are used in all risk assessments, additional parameters, like cost or schedule, can be standalone matrices.
Risk assessment is a qualitative assessment. Therefore, risk data quality (sometimes referred to as “risk data quality assessment PMP”) always impacts the risk assessment quality. A risk data audit helps ensure the quality of data used in the risk assessment. Project managers may use experts or previous project documentation as part of the risk data quality assessment to ensure the accuracy of the overall risk assessment.
The risk assessment outputs are part of the overall project and risk management documentation. A risk assessment can generate the following:
- Project Management Plan updates
- Project document updates
- Risk Management Plan updates
- Risk Register updates
- Risk Response Plan updates
Risk assessment should occur throughout the project. With each iteration, known as a risk reassessment, the risk documentation should be updated accordingly.
For the PMP exam, students need to know the importance of a risk assessment and how to use a probability and impact scoring matrix to help inform the priority of the risk. Project Managers and PMP credential holders should know the seven steps to risk assessment.
1. Identify applicable risk types and organize them
You cannot assess risk if you have not identified it. Begin your risk assessment with risk identification. With your project team, identify potential scenarios that could harm your project. Risks can be of any size and with internal or external triggers. Your team may identify risks that include computer viruses, manufacturing defects, natural disasters, or shipping delays. Each risk is identified and documented in the risk register. The risk may be organized by different factors (internal or external triggers, for example) or by categories (environmental, regulatory, technology, or staffing, for example).
2. Determine how these risks will be qualified and quantified
With risks identified and organized, the project manager should conduct a risk assessment. Each risk must be qualified and quantified. The project manager will use a probability and impact matrix to document the probability of each risk and the impact if it does happen. Remember, the quality of the data used in the assessment impacts its accuracy.
3. Determine your organization’s risk tolerance
Every organization has a risk tolerance level, with variances due to the type of risk, the specific stakeholders of a project, and the scope of the project. Additionally, there are industries with negligible risk tolerance (such as health care) and others with an acceptance of some level of risk (like software development). While every organization has a risk tolerance level, so the project manager should get stakeholder input to determine risk tolerance for each project.
4. Determine the final output format of the risk assessment
Within the risk management activities, determine during the risk planning process how the risk assessment output should be documented and communicated. Spreadsheet programs are often used for the ease of organizing large data sets. However, a company may have risk assessment output requirements, such as storing it on a secure server or capturing it in a shareable file, determining the output format. How the risk assessment output is documented is important because it determines how the information is made available to the project team and stakeholders.
5. Create a plan to maximize the risk assessments applicability to every project
Within a risk assessment and the resulting risk response plan, project managers have a wealth of knowledge that can protect the active project and future projects.
Project managers should have a plan to document the risk assessment, the result of risk responses applied to risks that occur, and the risk assessment matrices with the appropriate risk parameters. Maintaining a consistent and detailed project documentation archive helps ensure a project’s lessons learned are available to other project managers with similar projects, which can reduce the impact of negative risks. The plan should include documentation format requirements, how assessment documentation will be accessed, and how the assessment (and reassessments) will be communicated to the project team and stakeholders.
6. Create a final risk assessment that is flexible and scalable
Knowing the project manager and team will be doing reassessments throughout the project as part of risk reassessment, the process must be flexible and scalable. You may have to add risks throughout the project or incorporate other criteria to ensure the accuracy of the probability and impact scores. Additionally, the risk assessment should work for projects of different scopes. The risk assessment should be flexible enough to remain aligned with project changes and scalable enough to be used in multiple projects.
7. Determine the process to update the risk assessment
PMP credential holders know the importance of risk assessment and reassessment in managing the project cost. Without a process to update risk assessments, the project is vulnerable when risks occur. Changes are inevitable, and a risk assessment that is not current is not effective. Project managers should have a consistent risk assessment update process within their overall risk management activities.
Risk management documentation, such as the risk assessment matrix, is part of the overall project management documentation. The risk matrix documents at least four core areas for each identified risk: (1) risk name, (2) probability, (3) impact, and (4) risk level/ranking. The risk assessment also includes the calculated overall Project Risk score (the project’s probability-impact, or PI, score). The risk assessment matrix is an output of the Risk Assessment process and an input to the Risk Response process.
In a risk assessment matrix, each identified risk is listed along with its corresponding information.:
RISK CATEGORY
- Risk category : from a standardized list of risk categories (e.g., technology, natural disaster, regulations, transportation, etc.), the ones that most closely align with the project are used; not all projects have risks in all categories; therefore, each project will have a different combination of risk categories in its matrix
PROBABILITY
- Probability criteria : used to assign the probability values for a risk category; criteria should come from a standardized list but customized for each project
- Probability (“P”) score : a value given to each risk driven by the probability criteria; the matrix’s score scale will state the parameters for the minimum and maximum value of a P score; the project manager and project team use data and criteria to assign the P score to each risk
- Impact criteria : used to assign the impact values for a risk category; criteria should come from a standardized list but customized for each project
- Impact (“I”) score : a value given to each risk driven by the impact criteria; the matrix’s score scale will state the parameters for the minimum and maximum value of an I score; the project manager and project team use data and criteria to assign the I score to each risk
PROBABILITY AND IMPACT VALUES
- Probability-to-Impact (“PI”) score : the Probability score multiplied by the Impact score results in the PI score; the PI score is the overall risk assessment score; the PI score is used to rank all project risks by lowest probability and impact to highest, so resources are assigned accordingly
- Total Project Risk : all PI scores are added, and then that sum is divided by the quantity (total number of risks) of risks to determine the average; the project’s PI average value of PI scores is the Total Project Risk value.
Probability and impact are integral data points for risk assessment. Project risk tailoring occurs within the specifics of the risk categories, probability criteria, and impact criteria.
Risk Assessment Matrix Example
Project Manager Kestel’s PMI conference paper “ Risk assessments—developing the risk assessment for your organization ” includes an example risk assessment matrix:
From the completed risk assessment matrix, the project manager communicates the total Project Risk score to the team and stakeholders. Communication is part of risk assessment and helps ensure commonly understood terms are used for standardized risk assessment processes.
The risk matrix template ensures key data is consistently defined and included in the project documentation. For a risk matrix , project managers work with the project team and stakeholders to determine the specific risk criteria and refine the criteria for probability and impact. The format of the risk matrix should be determined early in the project and use company standards for project tools when available. The risk matrix should be stored with other project documentation, along with all risk reassessments for a project.
Project managers should complete the risk assessment as part of their risk management activities for all projects. Best practices for risk assessment include:
- Risk assessments should use quality data.
- Risk assessments incorporate expertise and knowledge from the project team and stakeholders.
- Risk data should undergo an audit to determine quality.
- Risk reassessment is conducted frequently throughout the life of a project.
- Risk assessments should use tailored and scalable tools.
- Risk assessment results, including the overall project risk score, are communicated to the team and stakeholders.
Project Managers should:
- lead the risk assessment efforts using standard tools
- customize the risk assessment matrix to the specific needs of the project,
- document the probability and impact of each risk,
- use standard data and terms for risk audit efforts, and
- communicate risk assessment progress and results to the project team and stakeholders.
Project managers should customize the risk assessment criteria to the project type. For example, you would not assess the risk of a particular weather event occurring using the criteria for the probability of manufacturing defects.
Additionally, project managers should use organizational templates and project management office (PMO) standards when available in their company. Customization of a project’s risk assessment should be balanced against the need for standards to contribute to knowledge sharing. No single tool will ensure quality assessment for all projects, but there are standards shared by all projects.
To prepare for the PMP exam, students need to know the importance of risk assessment and how to use a probability and impact scoring matrix to help inform the priority of the risk. Students should understand that a risk assessment is a tool to help manage the project’s cost by closely monitoring highly probable and high (negative or positive) impact risks.
American billionaire fund manager and philanthropist Bruce Kovner is credited with saying, “Risk management is the most important thing to be well understood.” A project manager with the PMP credential has demonstrated knowledge of risk assessment and the role it serves within risk management. Remember these components of creating a risk assessment:
- identify applicable risk types and organize them
- determine how risks will be qualified and quantified
- determine your organization’s risk tolerance
- determine the final output format of the risk assessment
- create a plan to maximize the risk assessment’s applicability to every project
- create a final risk assessment that is flexible and scalable
- determine a process to update the risk assessment
Project Managers managing risk using a scalable risk assessment template and standard processes consistently have successful projects. In addition to earning PMI’s Project Management Professional (PMP) certification, you may continue your certification journey by pursuing the PMI Risk Management Professional (PMP-RMP)® certification to advance your risk project management skills further.
- Megan Bell #molongui-disabled-link What is a Project Schedule Network Diagram?
- Megan Bell #molongui-disabled-link Scheduling Methodology: Build & Control Your Project Schedule
- Megan Bell #molongui-disabled-link Schedule Baseline: How to Create, Use, and Optimize
- Megan Bell #molongui-disabled-link How to Use Agile in Project Management as a PMP® Credential Holder
Popular Courses
PMP Exam Preparation
PMI-ACP Exam Preparation
Lean Six Sigma Green Belt Training
CBAP Exam Preparation
Corporate Training
Project Management Training
Agile Training
Read Our Blog
Press Release
Connect With Us
PMI, PMBOK, PMP, CAPM, PMI-ACP, PMI-RMP, PMI-SP, PMI-PBA, The PMI TALENT TRIANGLE and the PMI Talent Triangle logo, and the PMI Authorized Training Partner logo are registered marks of the Project Management Institute, Inc. | PMI ATP Provider ID #3348 | ITIL ® is a registered trademark of AXELOS Limited. The Swirl logo™ is a trademark of AXELOS Limited | IIBA ® , BABOK ® Guide and Business Analysis Body of Knowledge ® are registered trademarks owned by International Institute of Business Analysis. CBAP ® , CCBA ® , IIBA ® -AAC, IIBA ® -CBDA, and ECBA™ are registered certification marks owned by International Institute of Business Analysis. | BRMP ® is a registered trademark of Business Relationship Management Institute.
ConnectedGRC
Drive a Connected GRC Program for Improved Agility, Performance, and Resilience
BusinessGRC
Power Business Performance and Resilience
- Enterprise Risk
- Operational Risk
- Operational Resilience
- Business Continuity
- Observation
- Regulatory Change
- Regulatory Engagement
- Case and Incident
- Compliance Advisory
- Internal Audit
- SOX Compliance
- Third-Party Risk
Manage IT and Cyber Risk Proactively
- IT & Cyber Risk
- IT & Cyber Compliance
- IT & Cyber Policy
- IT Vendor Risk
Enable Growth with Purpose
AI-based Knowledge Centric GRC
- Integration
- Marketplace
- Developer Portal
Latest Release

Explore the right questions to ask before buying a Cyber Governance, Risk & Compliance solution.
Discover ConnectedGRC Solutions for Enterprise and Operational Resilience
- Enterprise GRC
- Integrated Risk Management
- CyberSecurity
- Corporate Compliance
- Supplier Risk and Performance
- Digital Risk
- IT and Security Compliance, Policy and Risk
- UK SOX Compliance
- Privacy Compliance
- IDW PS 340 n.F.
- Banking and Financial Services
- Life Sciences

Learn about the EU’s Digital Operational Resilience Act (DORA) and how you can prepare for it.
Explore What Makes MetricStream the Right Choice for Our Customers
Customer Stories
- GRC Journey
- Training & Certification
- Compliance Online

Robert Taylor from LSEG shares his experience on implementing an integrated GRC program with MetricStream
Discover How Our Collaborative Partnerships Drive Innovation and Success
- Our Partners
- Want to become a Partner?

Watch Lucia Roncakova from Deloitte Central Europe, speak on how the partnership with MetricStream provides collaborative GRC solutions
Find Everything You Need to Build Your GRC Journey and Thrive on Risk
Featured Resources
- Analyst Reports
- Case Studies
- Infographics
- Product Overviews
- Solution Briefs
- Whitepapers

Download this report to explore why cyber risk is rising in significance as a business risk.
Learn about our mission, vision, and core values

Gurjeev Sanghera from Shell explains why they chose MetricStream to advance on the GRC journey

6 Risk Assessment Methodologies Types and How to Choose?
Introduction.
Navigating the complex terrain of modern business demands a vigilant approach to protecting an organization’s sensitive information, which is constantly under the threat of various security risks. However, not all risks carry the same weight, and mitigation options vary in terms of both cost and efficacy. The dilemma then becomes: How does one navigate these choices to make well-informed decisions? Here is where risk assessment comes into play.
What is Risk Assessment?
Risk assessment is a systematic process of evaluating potential risks or uncertainties that could affect an organization's objectives, projects, operations, or assets. It involves identifying, analyzing, and prioritizing risks to determine their potential impact and likelihood of occurrence. The goal of risk assessment is to provide decision-makers with valuable information to make informed choices about risk mitigation strategies, resource allocation, and overall risk management .
A good risk assessment examines everything - market volatility, regulatory compliance , IT security, operational disruptions, financial fluctuations, and even natural disasters. These evaluations create a base for an organization to formulate a sturdy action plan.
So, when risks do crop up, businesses aren't left flat-footed; they're agile, adaptable, and resilient.
What are Risk Assessment Methodologies?
Risk assessment methodologies can be considered as your business's secret roadmap, guiding you through an unpredictable world, and ensuring you avoid all the potholes and pitfalls along the way.
They provide systematic, step-by-step procedures to identify, analyze, evaluate, and control potential hazards or threats that might disrupt a business’s functionality or growth.
This particular risk assessment process is essential, helping your company transform abstract concerns into concrete action items. It’s about looking at risks in black and white and choosing the best strategy to ensure you get from Point A to Point B with minimum damage. And just like there isn’t a one-size-fits-all suit, risk assessment methodologies vary, each catering to a different need and nature of risks.
Types of Risk Assessment Methodologies
Quantitative .
This methodology employs numerical data and statistical techniques to quantify risks. It involves the use of various mathematical models, simulations, and decision tree analysis to objectively calculate potential risks. This approach has its charm as it cuts through subjective opinions and potential biases by presenting cold hard facts. Risks are objectively measured, generally in financial terms, based on their potential cost to the organization and the probability of their occurrence. This kind of analytical clarity enables precise decision-making and facilitates easier comparisons between different risks. Quantitative methodology is indeed a practical tool, especially when financial loss and benefits must be meticulously calculated and analyzed. However, just like relying solely on a compass and measuring tape on a mountain trail can miss out on certain elements, quantitative risk assessment also has its limitations, specifically when dealing with non-quantifiable or more complex, subtle risks.
Qualitative
Unlike a hard-science approach, this method allows for judgment based on perception rather than numbers. It maps out possible risks based on subjectivity, where elements like risk severity, potential impact, and probability are ranked using ordinal scales (low, medium, high, or often numbers 1 to 5). Its real strength lies in the flexibility and adaptability that this method brings to the table. Indeed, this approach won't always provide the black-and-white, clear-cut results of a quantitative method, and the danger of bias does exist due to the level of subjectivity. Yet, this human-oriented approach might be your knight in shining armor when dealing with intricate, hard-to-quantify aspects such as reputational risks.
Semi-Quantitative
This approach manages to weave together elements of both qualitative and quantitative methods , possessing the simplicity and familiarity of the former, while allowing for more consistency and better comparative analysis through an injection of numbers. Here, risks are not just subjectively classified but are also numerically rated to obtain more specific risk scores. With these scores, it's like having a scale to weigh each risk factor according to its assigned value. As a result, the assessment provides more refined risk profiles than a purely qualitative approach. In this manner, a semi-quantitative methodology could be the choice for those wanting a broader risk image without drowning in an ocean of data or statistical uncertainty.
Asset-Based
With this method, every individual asset is closely inspected for possible risks, which might affect its functionality, value, or lifecycle. From physical assets like buildings or machines to intangible ones such as brand reputation or patents, each has unique vulnerabilities and threats associated with it. It typically involves four steps:
- Asset Identification: Identify and categorize critical assets, ranging from physical equipment to sensitive data
- Threat Identification: Identify potential threats that could impact the previously mentioned assets, covering scenarios like natural disasters, cyberattacks, or human error.
- Vulnerability Identification: Identify weaknesses that could be exploited by the identified threats, such as outdated software or inadequate security protocols.
- Risk Determination: Analyze the potential impact and likelihood of identified risks to prioritize and determine suitable risk response strategies.
The core of this method is identifying what is crucial to your organizational functionality, ensuring that if a threat does materialize, your most significant assets remain secure and your journey towards your organizational goals continues smoothly.
Vulnerability-Based
Your objective is to find where your organization could be compromised and to evaluate those points in light of their impact on your overall risk scenario. Vulnerabilities could be your business operations that are more prone to disruption, fragile IT systems that can easily be breached, or critical production machinery that lacks adequate preventive maintenance. You must keep a keen eye on both your physical and cyber assets. With the advancing digital landscape, threats could lurk within both domains.
When adopting this approach, identifying all assets is vital, since every business has various resources which are essential for its successful functioning. Post-asset identification, pinpoint the vulnerabilities and evaluate their potential impact, that is, the harm that would follow if a particular vulnerability were exploited. In essence, you're doing an 'integrity check' on your systems, wherein they become sturdier, and your peace of mind, as a business leader, magnifies.
Threat-Based
Threat-based risk assessment is a structured approach to evaluating and mitigating risks that focuses on identifying potential threats or hazards that could impact an organization's assets, operations, or objectives.
It functions by categorizing threats into intentional and unintentional categories, understanding each from an extensive standpoint. For example, consider intentional threats, including everything from organized cybercriminal groups trying to breach your company’s IT defenses to lone hackers manipulating vulnerabilities in the network. Unintentional threats, however, encompass natural disasters, data breaches due to employee negligence, and similar unforeseen incidents.
Factors to Consider When Choosing a Relevant Methodology
Business objectives.
Your organization is a unique entity with distinctive needs. Hence, a 'one-size-fits-all' risk assessment methodology may not be effective. Assess your needs based on your industry, size, culture, and the specific risk landscape you operate within.
Consider the breadth and depth of risk analysis you need. While some methodologies might provide an exhaustive understanding, they may not drill down into intricate details. Select a method that gives the right balance of broad overview and detail-driven insights.
Time and Resources
You need to account for the time, workforce, and financial resources available to you. This will help you choose between an automated tool versus a more manual process, each of which has its unique advantages.
Data Quality
Your decision is as good as the data backing it up. Select a methodology that can ensure accurate, reliable, and up-to-date information is consistently available for assessment.
Your team’s level of proficiency and the organization’s learning culture should guide your decision. An overly complex methodology could pose unnecessary challenges if your team lacks the expertise to operate it efficiently.
Scalability
Your business will evolve with time, and so should your risk assessment methodology. Choose a model that's as agile and adaptable as your ambitions.
As is often the case, your final choice should blend seamlessly into your broader strategic vision and contribute actively to it, becoming less of an afterthought and more of a defining attribute. Balancing rigor and fluidity, strategic direction, and adaptability, the right risk assessment methodology for your organization is a strong defense that aids in fostering an atmosphere of proactive risk management and goal-oriented growth for your business.
How to Choose the Best Risk Assessment Methodology
Top 7 risk management strategies with examples, what is a risk management framework and its components, how to create a successful risk management plan, essential elements of a successful integrated risk management program.

Subscribe for Latest Updates

Ready to get started?

A Comprehensive Guide to Risk Assessment Methodology
August 16, 2023

Risk assessment methodology , an aspect of any risk management process , encompasses various approaches to determining the potential impact of identified risks.
This comprehensive guide aims to elucidate the different methodologies, spanning from quantitative, qualitative, semi-quantitative, asset-based, and vulnerability-based to threat-based.
Each methodology, distinct in its approach, bears its own strengths and limitations, thus necessitating careful selection based on the specific context and objectives of the risk assessment .
The subsequent sections delve into the nuances of each methodology, providing a detailed analysis of their application, usefulness, and potential drawbacks.
This exploration endeavors to equip readers with the necessary knowledge to make informed decisions when choosing the most suitable risk assessment methodology for their needs and circumstances.

What is a Risk Assessment Methodology
A risk assessment methodology is a systematic approach used to identify, evaluate, and manage potential hazards or risks in a given environment, playing a crucial role in the decision-making process.
This methodology is a key component of risk management , as it helps organizations prioritize their resources effectively.
The risk assessment process typically involves a qualitative method, which involves subjective judgment based on expert opinion, and a quantitative method, which is numerical and involves statistical data.
These methods form the basis of different types of risk analysis, which can range from simple hazard identification to complex risk modelling.
The purpose of the methodology is not only to identify potential risks but also to estimate potential impacts, thereby aiding in the development of robust mitigation strategies.
Business associates should take corrective actions to address negative risks and capitalize on positive risks. A list of risks can help with a deeper understanding and effects analysis, especially for core elements such as remote access, the supply chain, and the development life cycle.
Senior management at financial institutions should ensure that additional controls are in place to meet acceptable levels of risk at the organizational and executive levels.
A detailed report with additional guidance can provide a more accurate risk assessment and help determine risk acceptability criteria, including simple risk assessment and residual risk acceptance criteria.
Companies should consider risk avoidance and various risk treatment options to manage information security risk. Sources for risk analysis, including bicyclist risk assessment methods and critical risk elements, should be incorporated into the project risk assessment report.
The highest-level risks should be identified, with a plan for verification and effective action plans. Implementation plans and security assessment plans should be included in the security plan, with consideration for the impact cost and potential threat events.
Framework and guidance documents can be helpful for larger companies to establish a company culture that prioritizes risk management and addresses high-risk failure modes.
Experts recommend considering potential failures during development and using a digital template for risk assessments . Finally, it’s important to proofread and check for spelling, grammar, and punctuation errors before sharing or downloading the document.d Template
Quantitative
Quantitative approaches to evaluating potential hazards employ numerical data and statistical methods, providing precision and objectivity in the analysis.
This type of risk assessment methodology, or quantitative risk assessment , uses specific metrics such as risk matrix, risk levels, and risk values to measure a given risk’s potential consequences and financial impact.
– Quantitative Risk Assessment: – Risk Matrix: This tool prioritizes risks based on their likelihood and potential impact, thus enabling more focused risk management.
– Risk Levels and Values: These metrics provide numerical risk estimates, which can be used to determine the severity and financial implications of potential risks.
The quantitative risk analysis process is a critical component of comprehensive risk management, offering an empirical approach to understanding and mitigating risks.
Qualitative
Contrasting with the numeric approach, qualitative strategies involve a more subjective and interpretive evaluation of potential hazards, relying on expert judgment rather than strictly numerical data.
The qualitative risk assessment method is often employed to identify and categorize kinds of risks in a less structured, more exploratory manner.
The qualitative assessment is central to effective risk communication as it allows for nuanced descriptions of potential hazards and their effects.
Employing a qualitative analysis when assessing risk provides a comprehensive understanding of the various aspects of potential hazards, including their causes, impacts, and possible mitigation strategies.
In essence, the qualitative approach to risk assessment offers an in-depth, interpretive insight into potential risks beyond what can be ascertained from a purely numerical evaluation.
Semi-Quantitative
Semi-quantitative strategies offer a unique approach to investigating potential hazards by bridging the gap between numeric and interpretive evaluations.
This risk assessment guide outlines the semi-quantitative method, which combines aspects of both qualitative and quantitative techniques to provide a more comprehensive guide to risk assessment methodology.
It allows for evaluating risks based on numerical scores and descriptive categories, aiding the risk management process.
Semi-quantitative methods facilitate risk mitigation strategies by assigning a numerical value to the severity of potential threats. These methods improve the understanding of the potential consequences, enhancing the ability to manage and mitigate the threats.
Asset-Based
Asset-based approaches are of utmost importance in the field of hazard investigation. They provide a focused evaluation and identification of assets susceptible to potential threats.
This methodology is typically employed during the risk assessment phase of a formal risk assessment process.
The approach entails systematically identifying potential hazards associated with the asset and analyzing the residual risks . This data is then used to populate a risk management file, which serves as a comprehensive repository of risks associated with the asset.
Asset-based risk assessment methodology provides a structured framework for identifying potential risks and formulating appropriate mitigation strategies.
The method’s inherent focus on asset-specific hazards ensures a comprehensive and detailed risk profile, aiding overall risk management .

Vulnerability-Based
Shifting the focus from assets to vulnerabilities, the vulnerability-based approach to hazard investigation concentrates on the weaknesses that potential threats could exploit.
This security risk assessment method emphasizes identifying vulnerabilities within a system, which can be subjected to unauthorized access or potential incidents.
This risk analysis approach necessitates an in-depth evaluation of the system’s security controls and their effectiveness in mitigating risks. It involves determining the potential impact levels of various threats exploiting existing vulnerabilities.
The ultimate goal is to strengthen these weak points to prevent any potential breaches, thus enhancing the overall security posture.
This proactive measure is crucial in the ever-evolving landscape of security threats, ensuring a comprehensive and robust risk management strategy .
Threat-Based
Contrasting the vulnerability-based approach, the threat-based perspective of analyzing security prioritizes potential dangers that could compromise information systems’ integrity , confidentiality, or availability.
This methodology focuses not only on the assessment of risk but also on the business impact analysis of potential security incidents.
The threat-based approach involves rigorous penetration testing to simulate security risks and identify possible weak points. It anticipates environmental threats that can negatively affect the system and measures to prevent inappropriate access.
Understanding potential threats is vital in this approach as it helps create effective risk mitigation strategies.
Therefore, the threat-based methodology provides a more comprehensive and strategic approach to risk assessment in information systems, ensuring a secure and stable system.
Choosing the Right Methodology
Determining the most suitable approach for evaluating information system security necessitates a thorough understanding of the distinct characteristics and benefits of vulnerability and threat-based methodologies.
Selecting a comprehensive guide to risk assessment methodology is pivotal in the risk management cycle. It is the cornerstone for achieving an effective risk treatment process.
Factors influencing the choice of methodology include the nature of the entity undergoing evaluation, the resources available, and the desired level of detail in the risk evaluation.
Scalable risk assessment methods provide flexibility, accommodating varying scopes and complexities.
The chosen methodology’s sophistication level should match the system’s complexity under scrutiny.
Therefore, choosing the right methodology is a vital step in the approach to risk management , significantly influencing the effectiveness of the risk evaluation.
Frequently Asked Questions
What are the necessary qualifications to conduct a risk assessment.
Conducting a risk assessment necessitates a thorough understanding of the subject matter, analytical skills, and proficiency in data interpretation.
Relevant qualifications may include degrees in risk management , statistics, or related fields, supplemented by professional experience.
How frequently should a risk assessment be conducted in a business environment?
The frequency of conducting a risk assessment in a business environment depends on various factors, such as changes in operational processes, the introduction of new equipment, or after an incident or accident.
What is the typical cost associated with conducting a comprehensive risk assessment?
The cost of conducting a comprehensive risk assessment can vary widely, dependent on factors such as the industry, size of the organization, and complexity of operations. Typically, it ranges from $10,000 to $50,000.
How does the risk assessment methodology change in different industries?
Risk assessment methodologies vary across industries due to differing risk factors and regulatory requirements. Industries with higher inherent risks , such as mining or construction, may employ more robust and thorough assessment techniques.
What are some common mistakes to avoid when implementing a risk assessment methodology?
Common mistakes when implementing a risk assessment methodology include: overlooking potential risks, failing to update risk assessments regularly, not involving all stakeholders, and neglecting to incorporate risk mitigation strategies into business planning.

Knowing the pros and cons of each risk assessment method is crucial for making the right decision.
Quantitative, qualitative, semi-quantitative, asset-based, vulnerability-based, and threat-based methodologies each offer distinct advantages for different contexts.
It is essential to select a methodology that matches the precise needs of the risk assessment to guarantee a complete, precise, and valuable assessment of probable risks.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.
Information Security Risk Assessment
A Detailed Guide To Audit Risk Assessment For Effective Financial Management
Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Reach out to understand more about Enterprise Risk Management, Project Management and Business Continuity.
© 2024 Risk Management

- SOFTWARE CATEGORIES
- FOR REMOTE WORK
- Project Management Software
Project Risk Assessment in 2024: Guide With Templates & Examples

You are organizing a product rollout, the premier milestone of your company this year. You have invited a thousand guests, expecting to witness a big gala event. Everything seems to be perfect before the event begins until you get two phone calls.
Your keynote speaker didn’t make it to her flight, and your caterer won’t be arriving due to some kitchen situation.
What do you do?
Just like life, your projects often throw some unexpected crises at you. These are what we call risks. And you should never allow yourself to ask what to do when risks happen because, by then, it’s too late and the damage will be significant. What you can and should do is to conduct a project risk assessment to anticipate such scenarios.
Don’t worry, even if you lack formal training in project management, risk assessment is quite straightforward. In this article, we’ll show you how with a few project risk assessment templates to help you follow the process.

Project Risk Assessment Guide Table of Contents
- Identify Risks
- Analyze Risks
- Determine Risk Response
- Document Risks
- Factors to consider when creating project risk assessment
As the Project Management Institute (PMI) defines it, risk is an unexpected event that can have an effect on your project, including its stakeholders, processes, and resources. Risk can affect your project positively or negatively. Take note that risk assessment is just one aspect of your life as the project leader. But it is a critical part of your strategy whatever project management methodology you’re using.

As a manager, you have your fair share of exposure to risks at varying levels.
Sometimes, risks are mistaken as issues, but there is a significant difference. Issues are events or problems that are already currently happening. Examples of issues include lack of manpower to work on a project, insufficient funding, and an immensely tight timeline.
Meanwhile, risks are problems that may happen in the future. The last-minute no-show of the performers and the caterer in the scenario above is an example of risk. We can also consider the immediate mass resignation of significant staff members a risk. Here are more examples of risks vs. issues in project management .
The purpose of preparing for project risk assessment is to acquire an awareness of the kinds of risks your project may encounter and the degree of damage they may bring. The following tips below will walk you through the important parts of this endeavor, including properly framing the project risk assessment definition.
To help you make a more accurate risk assessment and streamline its tedious process, you can turn to project management software with risk management; for example, what you’ll find in monday.com features .

Try out monday.com with their free trial
Project Risk Assesment Guide
1. identify risks.
Identifying of risk should be done as early as possible in the project and carried out throughout the project timeline, as risks affect significant project milestones. Throughout the years, you or your predecessors might have created a catalog of risks in the company server that the business have encountered in completed projects.
However, risks can also be identified during brainstorming with seasoned project members and other stakeholders. You can use the Crawford Slip method, where during a meeting, an attendee writes one suggestion per each piece of paper. This is a very simple yet effective way of gathering and collating suggestions and ideas. Just a note, you’ll need the cooperation of teams from other departments to get the best ideas. If you’re getting less-than-ideal attention from them, a shrug of the shoulder here and there, that’s one of the signs you need project management software or upgrade to a better one to optimize collaboration across the board.
In identifying risks, a risk category document is very useful in determining areas that are prone to risks. Risks may fall under the following categories:
- Organizational
- Project management.
Your project risk assessment checklist should include the relevant stakeholder accountable to action for each.
Here’s a sample risk category checklist:

Credits: northam.wa.gov.au
2. Analyze risks
This step entails examining the probability of a risk, how a risk event may impact project objectives and outcomes, and the appropriate steps that can be taken to mitigate the negative effects of risk. Here are the two things to consider at this stage:
- Likelihood. How probable will a certain risk occur in your project? PMI identifies the likelihood of risk occurrence as high, medium-high, medium-low, and low. Knowing the likelihood a certain risk will occur will help your team to prepare for it. For example, it is more probable for the bank to reject your loan application for funding than for that same bank to be set on fire by a lightning.
- Impact. An effective project planning will have a project risk assessment matrix of the various levels of impacts of a risk (categorized as catastrophic, critical, and marginal) on cost, schedule, scope, and quality of outcome. This will allow your team to identify which area of the project will bear the brunt of the risk with the biggest impact. This, in turn, will enable you to allocate manpower, budget, or technology for prevention or solution. An example of a catastrophic risk is the last-minute cancellation of a venue, which will greatly affect the whole event.
A project risk assessment matrix helps you analyze each risk based on the two factors above. You can vary the model, but essentially here’s how this template looks like (pay most attention to the red boxes):

Credits: The Program Manager
3. Determine risk response
Project risk assessment planning tools offered by some project management sites, such as monday.com, target to achieve the following results: eliminate the risk, reduce the probability of the occurrence of risk, and weaken the impact of the risk on the project. However, while it is best to develop a workflow to avoid the risk, it is still a rational move to set up a risk response guide for every project. This may mean factoring the risk in the project plan and schedule, increasing the funding or budget, and adding manpower and resources to the project, among other things.
It is simply not possible to completely eliminate all of the risk in a project. Some risks will persist at lower levels with weaker effects. These are called residual risks. Despite the diminished impact, residual risks need to be identified and assessed as you do the big-impact risks.
Here’s a project risk assessment example with an action plan, illustrating clearly what to do per risk occurrence:

4. Document risks
It is not enough, that you as project manager are able to identify, plan for, and solve risks events. A project folder or file needs to be created at the end of each project to provide transparency and awareness of the project’s timeline, workflow, and risks. This document sums up the reports above, plus adds insights on and citation of best practices on how the risks were handled. It will help other managers get a glimpse of the ins and outs of a project similar to yours. Having a cloud-based project management software like monday.com helps you to collate these details in one place for future reference.
Factors to consider when creating a project risk assessment
Being a project manager is not all about fighting and putting out fires. Here are more tips to get your project moving despite the hiccups.
- Make risk assessment the mainstay of your projects. It is ignorance to assume that projects will never encounter risks. An effective project risk assessment and management is essential in the success of any project. Although this will incur an additional step on your part, the benefit you will reap from embedding risk assessment and management can never be underestimated.
- Inform stakeholders about risks. In the “Attack by Stratagem” chapter of the Art of War, one of the best books for project managers , Sun Tzu declared that the source of an army’s strength is in unity, not size. Risk managers can learn a nugget of wisdom here. Sometimes, upper management is unaware of the details of failed projects. And there are instances where the instrument to solve the problem is already available but wasn’t used because the team has not been informed of its availability nor existence. Remember to include communicating risks and mitigation plans to other stakeholders in your project. You can do this during project update meetings as a default part of the agenda. This way, you clearly communicate that risks are vital parts of the project and should be given sufficient attention.
- Clarify ownership. Most projects involve different departments and stakeholders. It is important that stakeholders are clear with their ownership of the project or phase of the project. And this should be done at the beginning of the project or before a risk occurs. This way, each stakeholder will carry out tasks to decrease occurrences of risks on their part and will not be surprised by any additional expenses incurred.
Get the right tool for project risk assessment
While some managers have a wealth of experiences under their belt that help them to instinctively carry out steps and processes in analyzing and managing risks in their projects, it does not hurt for new managers to do some research as well as to adopt and utilize project risk assessment tools, checklists, and templates from websites. An example is monday.com.
monday.com is an online project management software that empowers managers to drive projects and teams effectively. It offers project risk assessment tools and templates that will save you time on the paperwork and give you more time to keep your team focused on achieving project success.

By Stephanie Seymour
Stephanie Seymour is a senior business analyst and one of the crucial members of the FinancesOnline research team. She is a leading expert in the field of business intelligence and data science. She specializes in visual data discovery, cloud-based BI solutions, and big data analytics. She’s fascinated by how companies dealing with big data are increasingly embracing cloud business intelligence. In her software reviews, she always focuses on the aspects that let users share analytics and enhance findings with context.
Top Project Management Software of 2024
Related posts

Efficient Project Management Approach in 2024: A Guide with Techniques, Examples & Templates

15 Best Free Remote Computer Monitoring Software and Tools in 2024

20 Best Drawing Software for 2024

How to Check a Paper for Plagiarism With Grammarly in 2024?

10 Best Open Source Applicant Tracking Systems (ATS) for 2024

15 Best Free Shopping Cart for Websites in 2024

List of 10 Best Sales Software Tools in 2024

A Breakdown of HubSpot CRM Free Features & Limitations in 2024

20 Best ERP Software for Manufacturing in 2024

Sisense: Pros & Cons of the Top Business Intelligence Software in 2024

20 Best EHS Software for Oil and Gas Refinery for 2024

5 Top Uses of Project Management Software: How To Benefit from Them in 2024

15 Best Business Intelligence Tools for Small and Big Business in 2024

Pros and Cons of FreshBooks: Is It The Best Accounting Software in 2024?

What is mLearning? How Mobile Learning Apps Can Help Your Business
20 Best SaaS Applicant Tracking Systems (ATS) for 2024

20 Best Digital Asset Management (DAM) Tools for 2024

15 Best VPN Extensions for Mozilla Firefox in 2024

Pros & Cons of EngageBay: Analysis of a Leading CRM Software

10 Best Shopping Cart Software Systems for Your Business
Leave a comment!
Add your comment below.
Be nice. Keep it clean. Stay on topic. No spam.
Why is FinancesOnline free?
FinancesOnline is available for free for all business professionals interested in an efficient way to find top-notch SaaS solutions. We are able to keep our service free of charge thanks to cooperation with some of the vendors, who are willing to pay us for traffic and sales opportunities provided by our website. Please note, that FinancesOnline lists all vendors, we’re not limited only to the ones that pay us, and all software providers have an equal opportunity to get featured in our rankings and comparisons, win awards, gather user reviews, all in our effort to give you reliable advice that will enable you to make well-informed purchase decisions.
No time for detailed research?
Get the best project management software solution!

EU Office: Grojecka 70/13 Warsaw, 02-359 Poland
US Office: 120 St James Ave Floor 6, Boston, MA 02116
- Add Your Product
- Research Center
- Research Team
- Terms of Use
- Privacy Policy
- Cookies Policy
- Scoring Methodology
- Do not sell my personal information
- Write For Us
- For Small Business
- Top Software
- Software reviews
- Software comparisons
- Software alternatives
Copyright © 2024 FinancesOnline. All B2B Directory Rights Reserved.
- Contact sales
Start free trial
The Risk Management Process in Project Management

When you start the planning process for a project, one of the first things you need to think about is: what can go wrong? It sounds negative, but pragmatic project managers know this type of thinking is preventative. Issues will inevitably come up, and you need a mitigation strategy in place to know how to manage risks when project planning .
But how do you work towards resolving the unknown? It sounds like a philosophical paradox, but don’t worry—there are practical steps you can take. In this article, we’ll discuss strategies that let you get a glimpse at potential risks, so you can identify and track risks on your project.
What Is Risk Management on Projects?
Project risk management is the process of identifying, analyzing and responding to any risk that arises over the life cycle of a project to help the project remain on track and meet its goal. Risk management isn’t reactive only; it should be part of the planning process to figure out the risk that might happen in the project and how to control that risk if it in fact occurs.
A risk is anything that could potentially impact your project’s timeline, performance or budget. Risks are potentialities, and in a project management context, if they become realities, they then become classified as “issues” that must be addressed with a risk response plan . So risk management, then, is the process of identifying, categorizing, prioritizing and planning for risks before they become issues.
Risk management can mean different things on different types of projects. On large-scale projects, risk management strategies might include extensive detailed planning for each risk to ensure mitigation strategies are in place if project issues arise. For smaller projects, risk management might mean a simple, prioritized list of high, medium and low-priority risks.
Get your free
Risk Matrix Template
Use this free Risk Matrix Template for Excel to manage your projects better.
How to Manage Project Risk
To begin managing risk, it’s crucial to start with a clear and precise definition of what your project has been tasked to deliver. In other words, write a very detailed project charter , with your project vision, objectives, scope and deliverables. This way risks can be identified at every stage of the project. Then you’ll want to engage your team early in identifying any and all risks.
Don’t be afraid to get more than just your team involved to identify and prioritize risks, too. Many project managers simply email their project team and ask to send them things they think might go wrong on the project. But to better plot project risk, you should get the entire project team, your client’s representatives, and vendors into a room together and do a risk identification session.
With every risk you define, you’ll want to log it somewhere—using a risk tracking template helps you prioritize the level of risk. Then, create a risk management plan to capture the negative and positive impacts of the project and what actions you will take to deal with them. You’ll want to set up regular meetings to monitor risk while your project is ongoing. Transparency is critical.
Project management software can help you keep track of risk. ProjectManager is online software that helps you identify risks, track them and calculate their impact. With our Risk view, you can make a risk list with your team and stay on top of all the risks within your project. Write a description, add tags, identify a resolution, mark impact and likelihood, even see a risk matrix—all in one place. Get started today with a free trial.
What Is Positive Risk In Project Management?
Not all risk is created equally. Risk can be either positive or negative, though most people assume risks are inherently the latter. Where negative risk implies something unwanted that has the potential to irreparably damage a project, positive risks are opportunities that can affect the project in beneficial ways.
Negative risks are part of your risk management plan, just as positive risks should be, but the difference is in approach. You manage and account for known negative risks to neuter their impact, but positive risks can also be managed to take full advantage of them.
There are many examples of positive risks in projects: you could complete the project early; you could acquire more customers than you accounted for; you could imagine how a delay in shipping might open up a potential window for better marketing opportunities, etc. It’s important to note, though, that these definitions are not etched in stone. Positive risk can quickly turn to negative risk and vice versa, so you must be sure to plan for all eventualities with your team.
Managing Risk Throughout the Organization
Can your organization also improve by adopting risk management into its daily routine? Yes! Building a risk management protocol into your organization’s culture by creating a consistent set of risk management tools and templates, with training, can reduce overhead over time. That way, each time you start a new project, it won’t be like having to reinvent the wheel.
Things such as your organization’s records and history are an archive of knowledge that can help you learn from that experience when approaching risk in a new project. Also, by adopting the attitudes and values of your organization to become more aware of risk, your organization can develop a risk culture . With improved governance comes better planning, strategy, policy and decisions.
Free Risk Matrix Template
To manage project risks throughout your organization, it’s important to create a risk matrix. A risk matrix is going to help you organize your risks by severity and likelihood, so you can stay on top of potential issues that threaten the greatest impact. Try this free risk matrix template for Excel so you and your team can organize project risks.
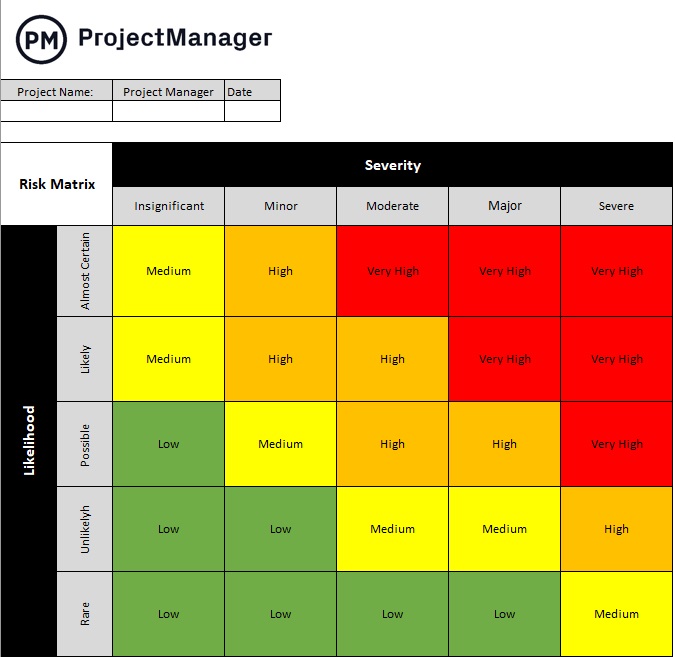
6 Steps in the Risk Management Process
So, how do you handle something as seemingly elusive as project risk management? You make a risk management plan. It’s all about the process. Turn disadvantages into an advantage by following these six steps.
Identify the Risk
You can’t resolve a risk if you don’t know what it is. There are many ways to identify risk. As you do go through this step, you’ll want to collect the data in a risk register .
One way is brainstorming with your team, colleagues or stakeholders. Find the individuals with relevant experience and set up interviews so you can gather the information you’ll need to both identify and resolve the risks. Think of the many things that can go wrong. Note them. Do the same with historical data on past projects. Now your list of potential risks has grown.
Make sure the risks are rooted in the cause of a problem. Basically, drill down to the root cause to see if the risk is one that will have the kind of impact on your project that needs identifying. When trying to minimize risk, it’s good to trust your intuition. This can point you to unlikely scenarios that you just assume couldn’t happen. Use a risk breakdown structure process to weed out risks from non-risks.
Analyze the Risk
Analyzing risk is hard. There is never enough information you can gather. Of course, a lot of that data is complex, but most industries have best practices, which can help you with your risk analysis . You might be surprised to discover that your company already has a framework for this process.
When you assess project risk you can ultimately and proactively address many impacts, such as avoiding potential litigation, addressing regulatory issues, complying with new legislation, reducing your exposure and minimizing impact.
So, how do you analyze risk in your project? Through qualitative and quantitative risk analysis, you can determine how the risk is going to impact your schedule and budget.
Project management software helps you analyze risk by monitoring your project. ProjectManager takes that one step further with real-time dashboards that display live data. Unlike other software tools, you don’t have to set up our dashboard. It’s ready to give you a high-level view of your project from the get-go. We calculate the live date and then display it for you in easy-to-read graphs and charts. Catch issues faster as you monitor time, costs and more.
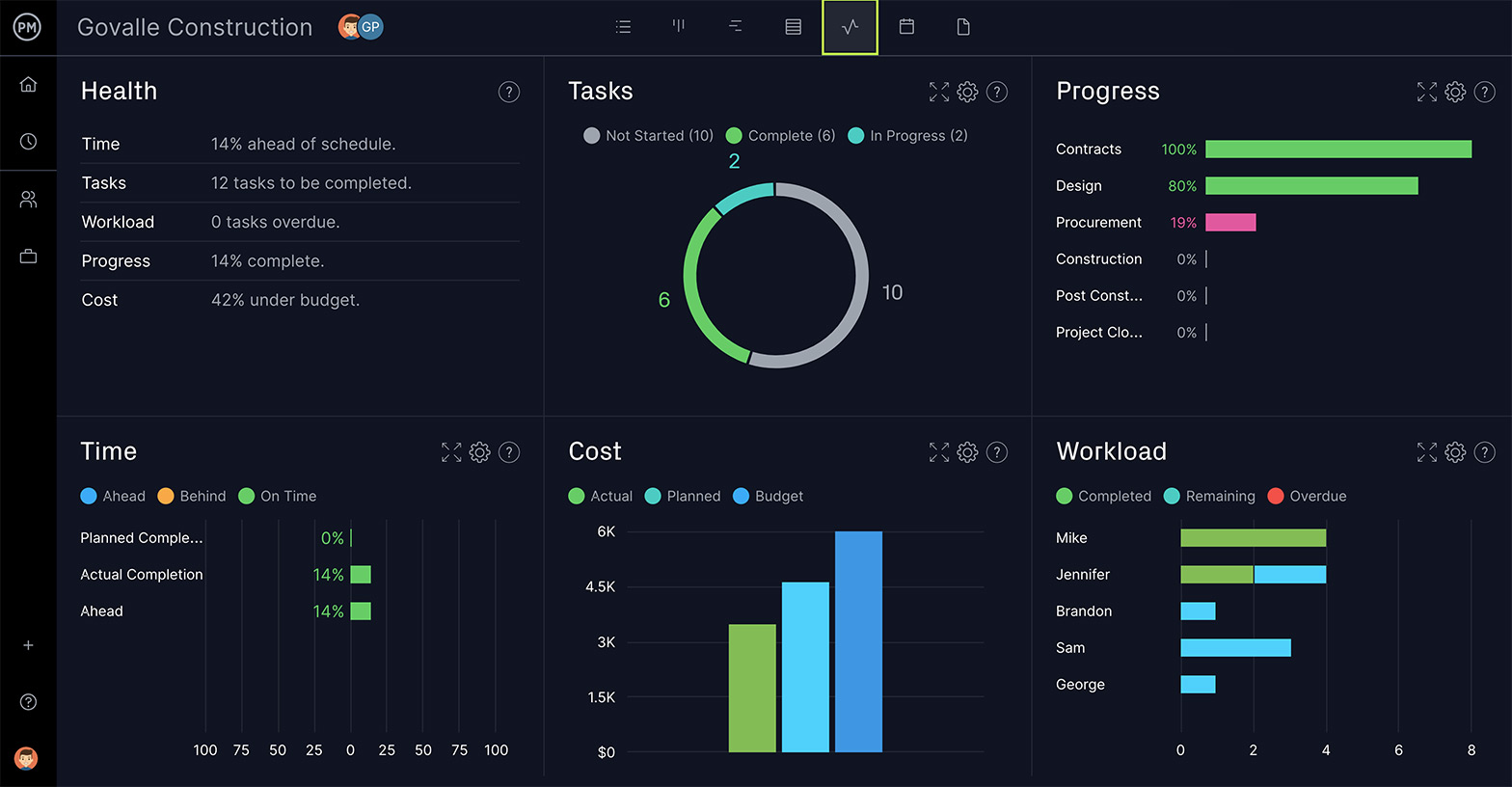
Prioritize Risks & Issues
Not all risks are created equally. You need to evaluate the risk to know what resources you’re going to assemble towards resolving it when and if it occurs.
Having a large list of risks can be daunting. But you can manage this by simply categorizing risks as high, medium or low. Now there’s a horizon line and you can see the risk in context. With this perspective, you can begin to plan for how and when you’ll address these risks. Then, if risks become issues, it’s advisable to keep an issue log so you can keep track of each of them and implement corrective actions.
Some risks are going to require immediate attention. These are the risks that can derail your project. Failure isn’t an option. Other risks are important, but perhaps do not threaten the success of your project. You can act accordingly. Then there are those risks that have little to no impact on the overall project’s schedule and budget . Some of these low-priority risks might be important, but not enough to waste time on.
Assign an Owner to the Risk
All your hard work identifying and evaluating risk is for naught if you don’t assign someone to oversee the risk. In fact, this is something that you should do when listing the risks. Who is the person who is responsible for that risk, identifying it when and if it should occur and then leading the work toward resolving it?
That determination is up to you. There might be a team member who is more skilled or experienced in the risk. Then that person should lead the charge to resolve it. Or it might just be an arbitrary choice. Of course, it’s better to assign the task to the right person, but equally important in making sure that every risk has a person responsible for it.
Think about it. If you don’t give each risk a person tasked with watching out for it, and then dealing with resolving it when and if it should arise, you’re opening yourself up to more risk. It’s one thing to identify risk, but if you don’t manage it then you’re not protecting the project.
Respond to the Risk
Now the rubber hits the road. You’ve found a risk. All that planning you’ve done is going to be put to use. First, you need to know if this is a positive or negative risk. Is it something you could exploit for the betterment of the project? If not you need to deploy a risk mitigation strategy .
A risk mitigation strategy is simply a contingency plan to minimize the impact of a project risk. You then act on the risk by how you prioritize it. You have communications with the risk owner and, together, decide on which of the plans you created to implement to resolve the risk.
Monitor the Risk
You can’t just set forces against risk without tracking the progress of that initiative. That’s where the monitoring comes in. Whoever owns the risk will be responsible for tracking its progress towards resolution. However, you’ll need to stay updated to have an accurate picture of the project’s overall progress to identify and monitor new risks.
You’ll want to set up a series of project meetings to manage the risks. Make sure you’ve already decided on the means of communication to do this. It’s best to have various channels dedicated to communication.
Whatever you choose to do, remember to always be transparent. It’s best if everyone in the project knows what is going on, so they know what to be on the lookout for and help manage the process.
In the video below, Jennifer Bridges, professional project manager (PMP) dives deeper into the steps in the risk management process.
Risk Management Templates
We’ve created dozens of free project management templates for Excel and Word to help you manage projects. Here are some of our risk management templates to help you as you go through the process of identifying, analyzing, prioritizing and responding to risks.
Risk Register Template
A risk register is a risk management document that allows project managers to identify and keep track of potential project risks. Using a risk register to list down project risks is one of the first steps in the risk management process and one of the most important because it sets the stage for future risk management activities.
A risk matrix is a project management tool that allows project managers to analyze the likelihood and potential impact of project risks. This helps them prioritize project risks and build a risk mitigation plan to respond to those risks if they were to occur.
Managing Risk With ProjectManager
Using a risk-tracking template is a start, but to gain even more control over your project risks you’ll want to use project management software. ProjectManager has a number of tools including risk management that let you address risks at every phase of a project.
Make an Online Risk Register
Identify and track all the risks for your project in one place. Unlike other project management software, you can manage risks alongside your project rather than in a separate tool. Set due dates, mark priority, identify resolutions and more.

Gantt Charts for Risk Management Plans
Use our award-winning Gantt charts to create detailed risk management plans to prevent risks from becoming issues. Schedule, assign and monitor project tasks with full visibility. Gantt charts allow team members add comments and files to their assigned tasks, so all the communication happens on the project level—in real time.
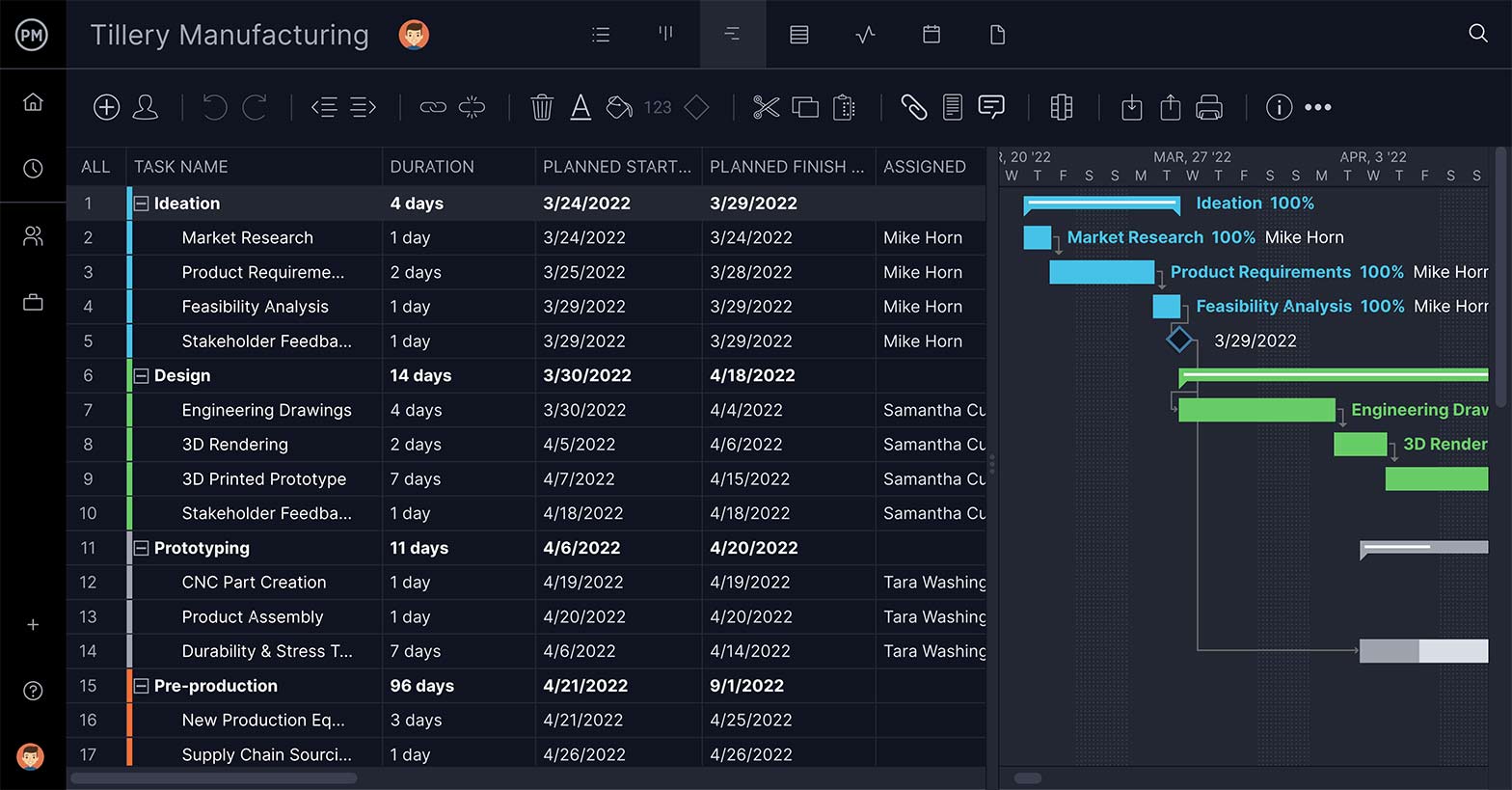
Risk management is complicated. A risk register or template is a good start, but you’re going to want robust project management software to facilitate the process of risk management. ProjectManager is an online tool that fosters the collaborative environment you need to get risks resolved, as well as provides real-time information, so you’re always acting on accurate data. Try it yourself and see, take this free 30-day trial.

Deliver your projects on time and under budget
Start planning your projects.
- Advisera Home
- ISO in General
Partner Panel
ISO 27001 Documentation Toolkits
Iso 27001 training.
- Documentation Toolkits
- White Papers
- Templates & Tools
Where to Start
New ai tool.
- Live Consultations
- Consultant Directory
- For Consultants

Dejan Kosutic
- Get Started
ISO 27001 Risk Assessment, Treatment, & Management: The Complete Guide

Table of contents
What is risk management? 6 phases in risk management Risk methodology Tips for smaller companies Risks & opportunities
How to perform risk assessment Key steps for risk assessment Assets, threats, and vulnerabilities Risk owners Consequence and likelihood Calculating risk Risk evaluation Example of a risk assessment
What is risk treatment? Purpose Methods/options Safeguards implementation Example of risk treatment Risk report Risk treatment process vs. Risk Treatment Plan
What is risk management, and why is it important?
Risk management is probably the most complex part of ISO 27001 implementation; but, at the same time, it is the most important step at the beginning of your information security project – it sets the foundations for information security in your company.
Risk management consists of two main elements: risk assessment (often called risk analysis) and risk treatment.
What actually are risk assessment and treatment, and what is their purpose? Risk assessment is a process during which an organization should identify information security risks and determine their likelihood and impact. Plainly speaking, the organization should recognize all the potential problems with their information, how likely they are to occur, and what the consequences might be.
The purpose of risk treatment is to find out which security controls (i.e., safeguards) are needed in order to avoid those potential incidents – selection of controls is called the risk treatment process, and in ISO 27001 they are chosen from Annex A, which specifies 93 controls.
- Risk management methodology
- Risk assessment
- Risk treatment
- Risk assessment and treatment report
- Statement of Applicability
- Risk treatment plan
ISO 27001 risk assessment & treatment – six main steps
Although risk management in ISO 27001 is a complex job, it is very often unnecessarily mystified. These six basic steps will shed light on what you have to do:
1) ISO 27001 risk assessment methodology
This is the first step on your voyage through risk management in ISO 27001. You need to define the rules for how you are going to perform the risk management, because you want your whole organization to do it the same way – the biggest problem with risk assessment happens if different parts of the organization perform it in different ways. Therefore, you need to define whether you want qualitative or quantitative risk assessment, which scales you will use for qualitative assessment, what the acceptable level of risk will be, etc.
2) Risk assessment implementation
Once you know the rules, you can start finding out which potential problems could happen to you – you need to list all your assets, then threats and vulnerabilities related to those assets, assess the impact and likelihood for each combination of assets/threats/vulnerabilities, and finally calculate the level of risk.
In my experience, companies are usually aware of only 30% of their risks. Therefore, you’ll probably find this kind of exercise quite revealing – when you are finished, you’ll start to appreciate the effort you’ve made.
3) Risk treatment implementation
Of course, not all risks are created equal – you have to focus on the most important ones, the so-called “unacceptable risks.”
When implementing the risk treatment in ISO 27001, there are four options you can choose from to handle (i.e., mitigate) each unacceptable risk, as explained further in this article.
4) Risk Assessment and Treatment Report
Unlike previous steps, this one is quite boring – you need to document everything you’ve done so far. This is not only for the auditors, as you may want to check these results for yourself in a year or two.
5) Statement of Applicability
This document actually shows the security profile of your company – based on the results of the risk treatment in ISO 27001, you need to list all the controls you have implemented, why you have implemented them, and how. This document is also very important because the certification auditor will use it as the main guideline for the audit.
For details about this document, see this article: Statement of Applicability in ISO 27001 – What is it and why does it matter?
6) Risk Treatment Plan
This is the step where you have to move from theory to practice. Let’s be frank – up to now, this whole risk management job was purely theoretical, but now it’s time to show some concrete results.
This is the purpose of the Risk Treatment Plan – to define exactly who is going to implement each control, in which timeframe, with what budget, etc. I would prefer to call this document an “Implementation Plan” or “Action Plan,” but let’s stick to the terminology used in ISO 27001.
And this is it – you’ve started your journey from not knowing how to set up your information security all the way to having a very clear picture of what you need to implement. The point is – ISO 27001 forces you to make this journey in a systematic way.
How does ISO 27005 help with risk management?
ISO/IEC 27005 is a standard dedicated solely to information security risk management. It is very helpful if you want to get deeper insight into information security risk assessment and treatment – that is, if you want to work as a consultant or perhaps as an information security / risk manager on a permanent basis.
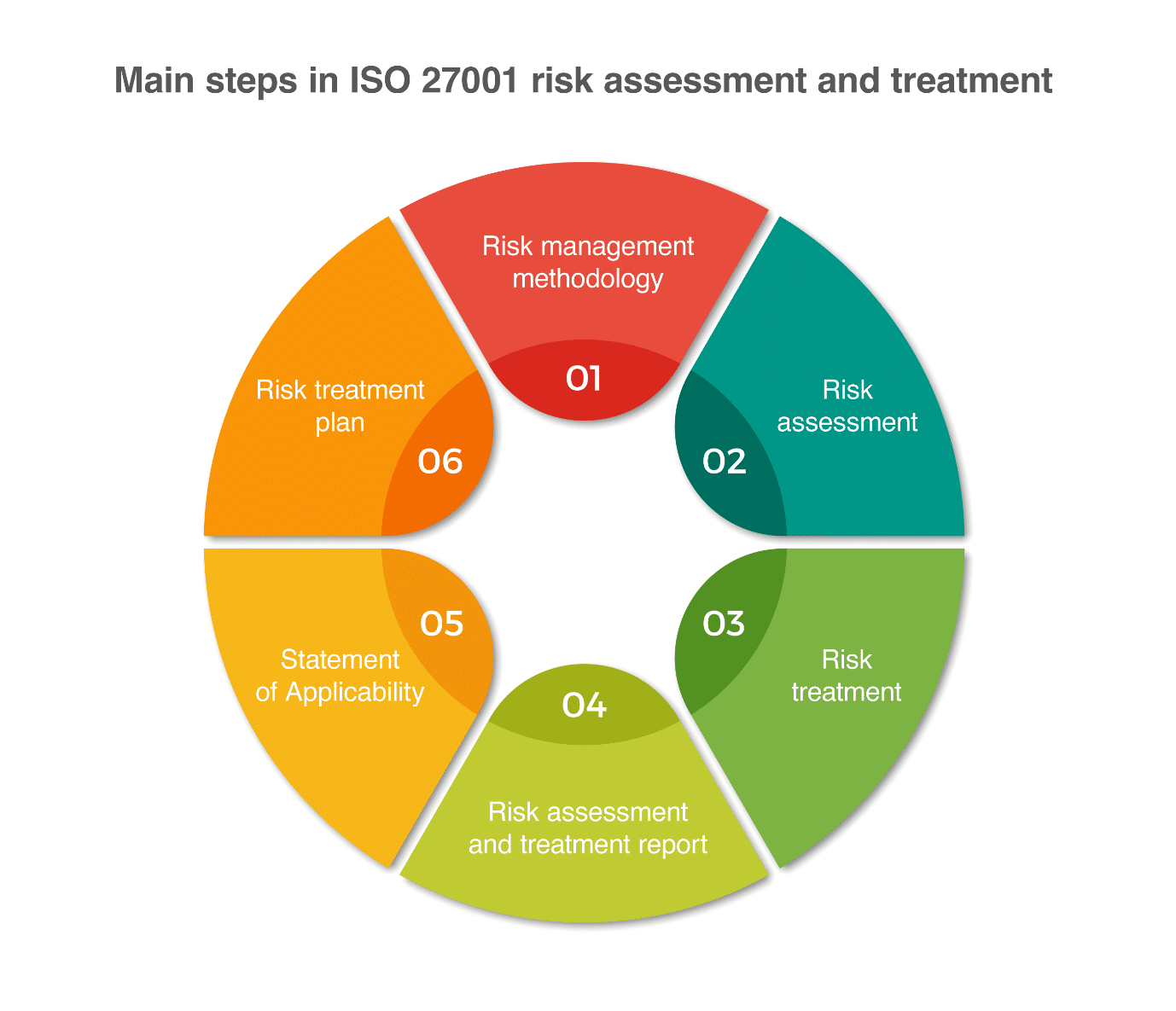
How to write ISO 27001 risk assessment methodology
Many companies make risk assessment and treatment too difficult by defining the wrong ISO 27001 risk assessment methodology and process (or by not defining the methodology at all).
What does ISO 27001 really require?
ISO 27001 requires you to document the whole process of risk assessment (clause 6.1.2), and this is usually done in the document called Risk Assessment Methodology. Unfortunately, this is where too many companies make the first big mistake: they start implementing the risk assessment without the methodology – in other words, without any clear rules on how to do it.
There are many myths regarding what the risk assessment should look like, but in reality, ISO 27001:2022 requirements are not very difficult – here is what clause 6.1.2 requires:
- Define how to identify the risks that could cause the loss of confidentiality, integrity, and/or availability of your information.
- Define how to identify the risk owners.
- Define the criteria for assessing consequences and assessing the likelihood of the risk.
- Define how the risk will be calculated.
- Define the criteria for accepting risks.
So essentially, you need to define these five elements – anything less won’t be enough, but more importantly, anything more is not needed, which means: don’t complicate things too much.
And yes – you need to ensure that the risk assessment results are consistent – that is, you have to define such methodology that will produce comparable results in all the departments of your company.
Which options are available?
Of course, there are many options available for the above five elements – here is what you can choose from:
Risk identification. The current 2022 revision of ISO 27001 does not prescribe a methodology for risk identification, which means you can identify risks based on your processes, based on your departments, using only threats and not vulnerabilities, or any other methodology you like; however, my personal preference is still the good old assets-threats-vulnerabilities method defined in the 2005 revision of the standard. (See also the article Catalogue of threats & vulnerabilities .)
Risk owners. Basically, you should choose a person who is both interested in resolving a risk, and positioned highly enough in the organization to do something about it. See also this article: Risk owners vs. asset owners in ISO 27001 .
Assessing consequences and likelihood. You should assess separately the consequences and likelihood for each of your risks; you are completely free to use whichever scales you like – e.g., Low-Medium-High, or 1 to 5, or 1 to 10 – whatever suits you best. Of course, if you want to make it simple, go for Low-Medium-High.
Method of risk calculation. This is usually done through addition (e.g., 2 + 5 = 7) or through multiplication (e.g., 2 x 5 = 10). If you use the Low-Medium-High scale, then this is the same as using the 1-2-3 scale, so you still have numbers for calculation.
Criteria for accepting risks. If your method of risk calculation produces values from 2 to 10, then you can decide that an acceptable level of risk is, e.g., 7 – this would mean that only the risks valued at 8, 9, and 10 need treatment. Alternatively, you can examine each individual risk and decide which should be treated or not based on your insight and experience, using no pre-defined values. This article will also help you: Why is residual risk so important?
In the section “Risk assessment,” you’ll find details on how to perform the risk assessment.
Methodology first, everything else afterwards
So, the point is this: you shouldn’t start assessing the risks using some sheet you downloaded somewhere from the Internet – this sheet might be using a methodology that is completely inappropriate for your company. You shouldn’t start using the methodology prescribed by the risk assessment tool you purchased; instead, you should choose the risk assessment tool that fits your methodology. (Or you may decide you don’t need a tool at all, and that you can do it using simple Excel sheets.)
In any case, you should not start assessing the risks before you adapt the methodology to your specific circumstances and to your needs.
Risk management tips for smaller companies
I have seen quite a lot of smaller companies trying to use risk management software as part of their ISO 27001 implementation project that is probably much more appropriate for large corporations. The result is that it usually takes too much time and money with too little effect.
Here are some tips on how to make risk management more manageable for smaller companies:
- Choose the right methodology. The methodology needs to be simplified and contain only the five elements that are required by ISO 27001. If you end up using a methodology that you copied from some large corporation, you’ll be doing risk assessment and treatment for months instead of in a couple of days.
- Choose the right tool. Find the software that follows your (simplified) methodology, not the other way around. In some cases, a good Excel template will do a better job than complicated software.
- Include the right people. You shouldn’t try to do this on your own; you should include the heads of all of your departments because they know their processes the best, which means that they know where potential problems could happen.
- Do not try to be perfect. Do not try to find all the risks the first time you do this – it will only slow you down; instead, you should finish your risk assessment and treatment, and come back later on to add any risks that were missing.
To conclude: risk assessment and treatment really are the foundations of information security / ISO 27001, but that does not mean they have to be complicated. You can do it in a simple way, and your common sense is what really counts.
How to address opportunities in ISO 27001 risk management using ISO 31000
When organizations think about risks, they generally focus on what could go wrong, and take measures to prevent that, or at least to minimize its effects. But risks can also mean that something good can happen, and by not being ready to take advantage of the situation, you can miss the benefits.
This section will present how to consider and handle positive risks, also known as opportunities, in the context of ISO 27001 . By including opportunities in an ISMS approach, organizations may increase the benefits of information security.
How ISO 27001 defines and treats risks
For ISO 27001, risk is the “effect of uncertainty on objectives,” and the “uncertainty” is the reason we cannot completely control all risks (after all, you cannot defend against what you do not know or understand).
ISO 27001 itself does not prescribe how to treat risks, while the supporting standard, ISO 27005, suggests four options: risk modification, risk retention, risk avoidance, and risk sharing. Detailed information about these risk treatment options can be found further in the article, but in short, all the options aim to decrease the likelihood of a risk happening and/or minimize its effects; i.e., they consider scenarios when something may go wrong.
Although this approach may have been appropriate in the early days of the standard, organizations today can no longer simply think in terms of what can go wrong in relation to their information security.
Opportunity options for information security
In the ISO’s most comprehensive standard about risk management, ISO 31000 – Risk management – Guidelines, besides options to handle negative risks, an organization may also consider taking or increasing the risk in order to pursue an opportunity, which can be achieved by:
- Risk enhancing – This includes taking measures to increase the probability of a risk happening. This one can be considered as the counterpart of the risk mitigation option for negative risks. For example, to take the opportunity to increase productivity, an organization decides to implement remote access by sharing existing resources and personnel to build and run the service which, in effect, increases risks.
- Risk exploiting – This means taking every possible action to ensure the risk will happen. It differs from the risk enhancing option in the fact that it involves more effort and resources, to effectively ensure the risk will happen. This one can be considered as the counterpart of the risk avoidance option for negative risks. For example, you intend a risk with a small impact to materialize because you would like to test how your incident response procedure works.
Additionally, risk sharing and risk acceptance also may be used in the context of handling opportunities.
- Sharing opportunities . When an organization realizes that, by itself, it cannot harness the benefits of an opportunity, it may share the risk, seeking a partner to split costs and efforts, so both can share the opportunity that neither of them could take advantage of by themselves. This differs from sharing negative risks, because in this last case the organization only transfers the costs of a negative impact to a third party. A joint venture between a system development company and a project management services provider is a good example of risk sharing considering opportunities.
- Do nothing . The organization may also consciously decide to do nothing about the opportunity (if it does occur, all the better, but considering the effort it would take to make it happen, it is not worth pursuing) – this is similar to accepting the negative risks.
When is it acceptable to increase risks?
The answer may seem obvious… and, in fact, it is: when the rewards are greater than the potential losses, and you can accept the losses if they occur.
In the remote access example, you will have to consider not only lost opportunity related to a failure in implementing the service (e.g., loss of team time and effort), but also potential losses related to risks arising from the use of the remote access itself (e.g., loss of information confidentiality).
If these potential losses can be accepted by the organization, if they were to occur, and they are smaller than the potential gains from increasing productivity, why not take the risk?
Don’t only hope for the best; be prepared for it
“Hope for the best and prepare for the worst” is a common motto for risk planning, but in a time when organizations demand the best use of resources, and every opportunity is crucial, simply hoping for the best does not work anymore.
By adopting the opportunity treatment approaches from ISO 31000 and introducing them into the ISO 27001 risk management process, organizations may unveil and take advantage of a new set of opportunities that can not only improve internal operations, but also increase profits and market visibility.
How to perform ISO 27001 risk assessment
Normally, doing the ISO 27001 risk assessment is a headache only when doing this for the first time – which means that risk assessment doesn’t have to be difficult once you know how it’s done.
So, how can you prepare yourself to make this headache smaller?

Do it alone or hire a consultant?
Since risk assessment and treatment are quite time-consuming and complex, you can decide whether they will be managed by the project manager/chief information security officer alone, or with the help of some hired expert (e.g., a consultant). A consultant could be quite helpful for larger companies, not only to guide the coordinator through the whole process, but also to perform part of the process – e.g., a consultant could do the workshops and/or interviews, compile all the information, write reports, etc., whereas the coordinator should manage the whole process and coordinate people within the company.
Larger companies will usually have project teams for the implementation of ISO 27001, so this same project team will take part in the risk assessment process – members of the project team could be the ones doing the interviews.
Smaller companies do not need to have a consultant or a project team – yes, the project manager will have to get some education first, but with the appropriate documentation and/or tools, this process can be done without expert help.
Should you use a tool for risk assessment?
Tools can speed up the process of risk assessment and treatment because they should have built-in catalogs of assets, threats, and vulnerabilities; they should be able to compile results semi-automatically; and producing the reports should also be easy – all of which makes them a very good choice for larger companies.
However, for smaller companies, the price of such tools could be an obstacle, though in my opinion an even bigger barrier is the fact that such tools are sometimes too complex for smaller companies. In other words, the time needed to learn to work with such a tool is usually much longer than it would take to handle dozens of Excel sheets. Not to mention that such tools usually require you to follow overly complex risk assessment methodology, which could be overkill for smaller companies.
In other words, if you are a smaller company, choose the risk assessment tool carefully and make sure it is easy to use for smaller organizations .
Options for gathering the information
Risk assessment means that you have to get quite a lot of input from your employees – essentially, there are three ways to do it:
- Perform risk assessment through interviews – this means that the coordinator will interview the responsible person(s) from each department, where he will explain the purpose of risk assessment first, and make sure that every decision of the responsible person about the level of risk (consequence and likelihood) makes sense and is not biased.
- Perform workshops with responsible persons – in these workshops, the coordinator explains to all responsible persons the purpose of risk assessment, and through several real-life examples, shows how to identify risks and assess their level.
- Send the sheets with detailed explanation – here you don’t help the responsible persons directly, but you send them risk assessment methodology or some other instructions on how to fill in the risk assessment sheets, and they do it themselves.
The last option is probably the easiest from the perspective of the coordinator, but the problem is that the information gathered this way will be of low quality. If the risk assessment process is not very clear to you, be certain that it will be even less clear to other employees in your company, no matter how nice your written explanation is.
Of course, performing interviews will probably yield better results; however, this option is often not feasible because it requires a large investment of the coordinator’s time. So performing workshops very often turns out to be the best solution.
Who decides on the level of risk?
The decision about the level of risk (consequence and likelihood) should always be left to those persons responsible for the activities – the coordinator will never know the assets, processes, and environment well enough to make such decisions, but the persons working there will certainly have a better idea.
However, the coordinator has another important function during the risk assessment process – once he starts receiving the risk assessment results, he has to make sure they make sense and that the criteria between different departments are uniform. Even though the workshops have been performed, or an explanation was given during the interview to the responsible person, they will always tend to give much larger importance (meaning higher risks) to their own department – in such cases, the coordinator must question such assessment and ask this person to reconsider his or her decision.
Don’t be a perfectionist
Risk management in general, but especially risk assessment and risk analysis, may seem like a perfect opportunity to make things complicated – since the requirements of ISO 27001 are rather simplistic, you can add numerous elements in trying to make your approach more “scientific.”
But you have to ask yourself one question: is your goal to create a perfect risk assessment that will need to be performed for several months or maybe years (because it is extremely hard to list all potential risks that there could be), or is your goal to finish this process in a reasonable timeframe, knowing that it won’t be 100% accurate?
If you choose the latter approach, you will identify the main risks, and will get your people to start thinking about the necessity of protecting company information. And you will always have the opportunity to add the other risks later on, once you finish your initial implementation. This is what ISO 27001 requires from you anyway, as part of continual improvement.
Main steps in ISO 27001 risk assessment
ISO 27001 requires that risk assessment have five main steps, the same ones that are explained in the section about the risk assessment methodology:
- Risk identification (listing assets, threats, and vulnerabilities)
- Assigning risk owners (persons responsible for risk)
- Risk analysis (assessing consequences and likelihood)
- Risk calculation (determining the level of risk)
- Risk evaluation (accepting the risks based on criteria)
Each of these steps is described in the following sections.
How to match assets, threats, and vulnerabilities
The current 2022 revision of ISO 27001 allows you to identify risks using any methodology you like; however, the methodology called “asset-based risk assessment” (defined by the old 2005 revision of ISO 27001) is still dominating, and it requires identification of assets, threats, and vulnerabilities.
So, how do you combine assets, threats, and vulnerabilities in order to identify risks?
How to identify risks
To make your risk assessment easier, you can use a sheet or software that will list assets, threats, and vulnerabilities in columns; you should also include some other information like risk ID, risk owners, impact and likelihood, etc.
If you use a sheet, I found it the easiest to start listing items column by column, not row by row – this means you should list all of your assets first, and only then start finding a couple of threats for each asset, and finally, find a couple of vulnerabilities for each threat.
To learn which types of assets you should take into account, read this article: Asset management according to ISO 27001: How to handle an asset register / asset inventory , and click here to see a catalog of threats and vulnerabilities appropriate for smaller and mid-sized companies.
Relationship between assets, threats, and vulnerabilities
So, let’s see what this matching of the three components could look like – for example:
Asset – paper document :
- threat : fire; vulnerability : document is not stored in a fire-proof cabinet (risk related to the loss of availability of the information)
- threat : fire; vulnerability : there is no backup of the document (potential loss of availability)
- threat : unauthorized access; vulnerability : document is not locked in a cabinet (potential loss of confidentiality)
Asset – digital document :
- threat : disk failure; vulnerability : there is no backup of the document (potential loss of availability)
- threat : virus; vulnerability : anti-virus program is not properly updated (potential loss of confidentiality, integrity, and availability)
- threat : unauthorized access; vulnerability : access control scheme is not properly defined (potential loss of confidentiality, integrity, and availability)
- threat : unauthorized access; vulnerability : the access was given to too many people (potential loss of confidentiality, integrity, and availability)
Asset – system administrator (a person):
- threat : unavailability of this person; vulnerability : there is no replacement for this position (potential loss of availability)
- threat : frequent errors; vulnerability : lack of training (potential loss of integrity and availability)
This might seem complicated at first glance, but once you start doing it, you’ll see that it goes rather quickly.
Grouping the assets
In order to speed up the process, you should group your assets so that you have fewer items to do the risk assessment with – for example:
- If you have several laptops in your company, you should use one item called “laptops.”
- If you have several servers, you can group them into, e.g., “physical servers” and “virtual servers,” or perhaps “servers for internal use” and “production servers with customer data.”
- If you use several SaaS applications, you can group them into, e.g., “marketing & sales SaaS,” “software development SaaS,” etc.
- You can group your employees into, e.g., “top management,” “IT system administrators,” and “other employees.”
How many risks are enough?
Very often, people ask me how many risks they should list. If they start being really thorough, for each asset they could find 10 threats, and for each threat at least five vulnerabilities – this is quite overwhelming, isn’t it? If you are a small company with 50 assets, this would mean you would end up with 2,500 risks, which would probably be overkill for this size of a company.
This is why you should focus only on the most important threats and vulnerabilities – e.g., three to five threats per asset, and one or two vulnerabilities per threat.
So the number of risks should depend roughly on the number of employees in your company:
There are other factors that will influence the number of risks – for example, if you are a financial institution, or you provide services to the military, you should probably make additional effort to identify more risks than displayed above.
Of course, over time you’ll find out other risks that you did not identify before – you should add these to your list of risks later on. After all, this is what continual improvement in ISO 27001 is all about.
Why is this methodology still good?
I personally like this assets-threats-vulnerabilities methodology quite a bit, because I think it gives a good balance between doing the risk assessment quickly, and at the same time doing it both systematically and detailed enough so that one can pinpoint where the potential security problem is.
And this is what risk assessment is really about: find out about a potential problem before it actually happens. In other words, ISO 27001 tells you: better safe than sorry .
Assigning the risk owners
Once you have a list of your risks, you need to define who’s responsible for each of them.
In very small companies, you can nominate only one person to be the risk owner for all risks; however, for both big and small companies, a much better approach would be to consider each risk separately and to define risk owners based on these factors:
- the person who knows the asset the best, and
- the person who has the power to make the necessary changes
For example, the risk owner of a risk related to personnel records might be the head of the HR department, because this person knows best how these records are used and what the legal requirements are, and they have enough authority to pursue the changes in processes and technology necessary for protection.
How to determine consequences and likelihood
The next step is to calculate how big each risk is – this is achieved through assessing the consequences (also called the impact) if the risk materializes and assessing how likely the risk is to happen; with this information, you can easily calculate the level of risk.
ISO 27001 doesn’t really tell you how to do your risk assessment, but it does tell you that you must assess consequences and likelihood, and determine the level of risk – therefore, it’s up to you to decide what is the most appropriate approach for you.
Based on ISO 27005, there are essentially two ways to analyze the risks using the qualitative method – simple risk assessment, and detailed risk assessment – you’ll find their explanation below. ISO 27005 also suggests some other approaches to risk assessment, but they are more complicated and are not covered in this article.
You’ll find an explanation on why the quantitative risk assessment cannot be used in normal practice later on in this article.
Simple (or basic) risk assessment
In simple risk assessment, you assess the consequences and the likelihood directly – once you identify the risks, you simply have to use scales to assess separately the consequences and the likelihood of each risk. For example, you can use the scale of 0 to 4, where 0 would be very low, 1 low, 2 medium, and so on, or the scale 1 to 10, or Low-Medium-High, or any other scale. The larger the scale, the more precise the results you will have, but also the more time you will spend performing the assessment.
So, for example, in simple risk assessment you might have something like this:
- Asset: laptop
- Threat: theft
- Vulnerability: employees do not know how to protect their mobile devices
- Consequences: 3 (on a scale from 0 to 4)
- Likelihood: 4 (on a scale from 0 to 4)
Detailed risk assessment
In the detailed risk assessment, instead of assessing two elements (consequences and likelihood), you assess three elements: asset value, threat, and vulnerability. So, here’s an example of this detailed risk assessment:
- Asset value: 3 (on a scale from 0 to 4)
- Threat value: 2 (on a scale from 0 to 2)
- Vulnerability value: 2 (on a scale from 0 to 2)
When you think about this more closely, through these three elements in detailed risk assessment, you will indirectly assess the consequences and likelihood: by assessing the asset value, you are simply assessing which kind of damage (i.e., consequence) could happen to this asset if its confidentiality, integrity, or availability is endangered; both threats and vulnerabilities directly influence the likelihood – the higher the threat and the higher the vulnerability, the more likely the risk will happen, and vice versa.
And basically, this is it – if you’re a smaller company, simple risk assessment will be enough for you; if you’re a mid-size or a larger company, detailed risk assessment will do the job. And you don’t need to add any more elements, because that would only make your job more difficult.
Why is evaluating both assets and consequences wrong?
Very often, I see companies implementing simple risk assessment (i.e., they directly assess consequences and likelihood), but they also add the asset value to this assessment.
Why is this wrong? Because of the simple fact that they already assessed the consequences once, so they don’t need to assess them again through the asset value.
So, again – don’t try to outsmart yourself and create something complex just because it looks nice.
How to calculate the level of risk
Calculating risk is actually very simple – this is usually done through addition (e.g., 2 + 5 = 7) or through multiplication (e.g., 2 x 5 = 10) of consequences and likelihood. If you use a Low-Medium-High scale, then this is the same as using 1-2-3, so you still have numbers for calculation.
So, using the examples from the previous section, here is how to calculate the risk using addition:
- Simple risk assessment: Consequences (3) + Likelihood (4) = Risk (7)
- Detailed risk assessment: Asset value (3) + Threat value (2) + Vulnerability value (2) = Risk (7)
In the detailed risk assessment explained in the previous section, you’ll notice that I used the 0 to 4 scale for assessing the asset value, and the smaller 0 to 2 scale for assessing threats and vulnerabilities. This is because the weight of consequence should be the same as the weight of likelihood – since threats and vulnerabilities jointly “represent” the likelihood, their maximum added value is 4, the same as for the asset (i.e., consequence) value.
Risk evaluation
After you’ve calculated the risks, you have to evaluate whether they are acceptable or not.
This step is easy – you simply have to compare the level of risk that you calculated with the acceptable level from your risk assessment methodology. For example, if your level of risk is 7, and the acceptable level of risk is 5, this means your risk is not acceptable.
All the unacceptable risks must go to the next phase – the risk treatment in ISO 27001; all acceptable risks do not need to be treated further.
Example of risk assessment
In the table below, you’ll see an example of a simple risk assessment using an asset-based approach.
What is risk treatment?
ISO 27001 risk treatment refers to the process of modifying a risk, by changing its likelihood and/or its impact. In most cases, this would mean decreasing the risk by reducing the likelihood of an incident (e.g., by using nonflammable building materials), and/or reducing the impact on assets (e.g., by using automatic fire-suppression systems).
The purpose of risk treatment
Most people think risk assessment is the most difficult part of implementing ISO 27001 – true, risk assessment is probably the most complex, but risk treatment is definitely the one that is more strategic and more costly.
The purpose of risk treatment according to ISO 27001 seems rather simple: to control the risks identified during the risk assessment.
During the risk treatment, the organization should focus on those risks that are not acceptable; otherwise, it would be difficult to define priorities and to finance the mitigation of all the identified risks.
Four most common treatment options
Once you have a list of unacceptable risks from the risk assessment phase, you have to go one by one and decide how to treat each – usually, these options are applied:
- Decrease the risk – this option is the most common, and it includes implementation of safeguards (controls) – e.g., by implementing backup you will decrease the risk of data loss.
- Avoid the risk – stop performing certain tasks or processes if they incur such risks that are simply too big to mitigate with any other options – e.g., you can decide to ban the usage of laptops outside of the company premises if the risk of unauthorized access to those laptops is too high (because, e.g., such hacks could halt the complete IT infrastructure you are using).
- Share the risk – this means you transfer the risk to another party – e.g., you buy an insurance policy for your physical server against fire, and therefore you transfer part of your financial risk to an insurance company. Unfortunately, this option does not have any influence on the incident itself, so the best strategy is to use this option together with options 1) or 2).
- Retain (accept) the risk – this is the least desirable option, and it means your organization accepts the risk without doing anything about it. This option should be used only if the mitigation cost would be higher than the damage an incident would incur.
Decreasing the risks is the most common option for treating the risks, and for that purpose the controls from ISO 27001 Annex A are used (and any other controls that a company thinks are appropriate). See here how the controls are organized: Understanding the ISO 27001 controls from Annex A .
Implementation of security controls
Before starting your implementation process, you should be aware of unacceptable risks from the risk assessment, but also your available budget for the current year, because sometimes the controls will require an investment.
When selecting new controls, there are basically three types of controls:
- Defining new rules: rules are documented through plans, policies, procedures, instructions, etc., although you don’t have to document some less-complex processes.
- Implementing new technology: for example, backup systems, disaster recovery locations for alternative data centers, etc.
- Changing the organizational structure: in some cases, you will need to introduce a new job function, or change the responsibilities of an existing position.
Deciding which controls to select
ISO 27001 risk treatment is a step where you normally wouldn’t include a very wide circle of people – you will have to brainstorm on each treatment option with specialists in your company who focus on certain areas. For example, if the treatment has to do with IT, you will speak to your IT guys; if it is about new trainings, you will speak to human resources, etc.
Of course, the final decision about any new treatment option will require a decision from the appropriate management level – sometimes the CISO will be able to make such decisions, sometimes it will be your project team, sometimes you will have to go to the department head in charge of a particular field (e.g., head of the legal department if you ask for additional clauses in the contracts with your partners), or perhaps to the executive level for larger investments. If you have doubts regarding who can decide what, consult your project sponsor.
Residual risk
If you choose to measure residual risks, i.e., the risks that will remain after you apply the controls, it should be done together with the responsible persons in each department. You have to show these people which treatment options you have planned for, and based on this information, and using the same scales as for the risk assessment, assess the residual risk for every unacceptable risk identified earlier during risk assessment.
So, for instance, if you had identified a consequence of level 4 and likelihood of level 5 during your risk assessment (which would mean risk of 9 by the method of addition), your residual risk may be 5 if you assessed that the consequence would lower to 3 and likelihood to 2 due to, e.g., safeguards you planned to implement.
The most expensive security controls are not always the best
When considering the ISO 27001 risk treatment options, and particularly safeguards that involve an investment in technology, please beware of the following: very often, the first idea that comes to mind will be the most expensive. However, sometimes alternatives will exist that will be equally effective, but at a lower cost – therefore, think hard before you purchase some expensive new system.
Also, be aware that most of the risks exist because of human behavior, not because of machines – therefore, it is questionable whether a machine is the solution to a human problem.
In other words, when treating risks you need to get creative – you need to figure out how to decrease the risks with minimum investment. It would be the easiest if your budget was unlimited, but that is never going to happen.
Example of risk treatment
An example of a risk treatment table might look something like this:
How to write a risk assessment and treatment report
ISO 27001 doesn't specify the contents of the Risk Assessment Report; it only says that the results of the risk assessment and risk treatment process need to be documented – this means that whatever you have done during this process needs to be written down. Therefore, this report is not only about assessment – it is also about treatment.
The report includes all the risks that were identified, risk owners, their impact and likelihood, level of risk, risks that are not acceptable, and treatment options for each unacceptable risk.
Typically, the report is written in short form (e.g., in one page), to which a detailed list of risks and controls is attached.
Risk Treatment Plan vs. risk treatment process – What’s the difference?
The Risk Treatment Plan is one of the key documents in ISO 27001; however, it is very often confused with the documentation that is produced as the result of a risk treatment process. Here’s the difference.
What is the risk treatment process?
The risk treatment process is only one phase in the risk management process that follows the risk assessment phase – in the risk assessment, all the risks need to be identified, and risks that are not acceptable must be selected. The main task in the risk treatment step is to select one or more options for treating each unacceptable risk, i.e., to decide how to mitigate all these risks.
As explained in the sections above, there are usually four treatment options available for companies: decrease the risk, avoid the risk, share the risk, and retain the risk.
According to ISO 27001, it is required to document the risk treatment results in the Risk Assessment Report, and those results are the main inputs for writing the Statement of Applicability. This means that the results of risk treatment are not directly documented in the Risk Treatment Plan.
How do you write a Risk Treatment Plan?
So, where is the Risk Treatment Plan in this whole process? The answer is: it can be written only after the Statement of Applicability is completed.
Why is this so? To start thinking about the Risk Treatment Plan, it would be easier to think of it is an “Action plan” or “Implementation plan,” because ISO 27001 requires you to list the following elements in this document:
- which security controls and other activities you need to implement
- who is responsible for the implementation
- what are the deadlines
- which resources (i.e., financial and human) are required for the implementation, and
- how will you evaluate if the implementation was done correctly
But in order to write such a document, you first need to decide which controls need to be implemented, and this is done (in a very systematic way) through the Statement of Applicability.
The purpose of the Risk Treatment Plan
The question is – why didn’t ISO 27001 require the results from the risk treatment process to be documented directly in the Risk Treatment Plan? Why was this step in between needed, in the form of the Statement of Applicability (SoA)?
In my view, the authors of ISO 27001 wanted to encourage companies to get a comprehensive picture of information security – when deciding which controls are applicable and which are not – through the Statement of Applicability. For the SoA, the result of risk treatment is not the only input – other inputs are legal, regulatory and contractual requirements, other business needs, etc. In other words, the SoA is a more strategic document that defines the security profile of an organization, while the Risk Treatment Plan is the implementation plan of that strategy.
Once you’ve written this document, it is crucial to get your management’s approval because it will take considerable time and effort (and money) to implement all the controls that you have planned here. And, without their commitment, you won’t get any of these.
To conclude – the Risk Treatment Plan is the point where theory stops, and real life begins according to ISO 27001. A good risk assessment and risk treatment process, as well as a comprehensive Statement of Applicability, will produce the foundations for finding out what you have to do with your security, but the Risk Treatment Plan is where you need to start doing the real thing. But you can’t start doing the real thing before you figure out the right thing to do.
ISO 27001 gap analysis vs. risk assessment
Very often, I see people confuse gap analysis with risk assessment – which is understandable, since the purpose of both is to identify deficiencies in their company’s information security. However, from the perspective of ISO 27001 , and from the perspective of a certification auditor, these two are quite different.
What is ISO 27001 gap analysis?
Gap analysis is nothing but reading each clause of ISO 27001 and analyzing if that requirement is already implemented in your company. When you do so, you can either say Yes or No, or you could use a scale similar to this:
- 0 – requirement not implemented nor planned
- 1 – requirement is planned but not implemented
- 2 – requirement is implemented only partially, so that full effects cannot be expected
- 3 – requirement is implemented, but measurement, review, and improvement are not performed
- 4 – requirement is implemented, and measurement, review, and improvement are performed regularly
Gap analysis is not mandatory in ISO 27001; it is done indirectly when developing your Statement of Applicability – clause 6.1.3 d) says you need to determine “… whether they [the necessary controls] are implemented or not.”
Therefore, you don’t need to perform the gap analysis for clauses of the main part of the standard – only for the controls from Annex A. Further, gap analysis doesn’t need to be performed before the start of ISO 27001 implementation – you must do it as part of your Statement of Applicability, only after the risk assessment and treatment.
The difference between gap analysis and risk assessment
Gap analysis tells you how far you are from ISO 27001 requirements/controls; it doesn’t tell you which problems can occur or which controls to implement. Risk assessment tells you which incidents can happen and which controls to implement, but it doesn’t give you an overview of which controls are already implemented.
While risk assessment is crucial for ISO 27001 implementation, gap analysis is only indirectly done when writing the Statement of Applicability – therefore, one is not a replacement for the other, and both are required, but in different phases of implementation and with different purposes.
Sometimes companies perform gap analysis before the start of ISO 27001 implementation, in order to get a feel for where they are right now, and to find out which resources they will need to employ in order to implement ISO 27001. However, the usefulness of such approach is doubtful, since only risk assessment will show the real extent of what needs to be implemented and in which form.
Risk assessment vs. internal audit
Quite often, I see people searching for ISO 27001 checklists for performing the internal audit; however, they expect those checklists to help them with, e.g., what information the organization has, who has access to it, how it is protected, how confidential it is, etc.
The problem is – these kinds of things are not part of an internal audit; this is part of the risk assessment.
The difference in timing
The purpose of risk assessment is to find out which problems can arise with your information and/or operations – that is, what can jeopardize the confidentiality, integrity, and availability of your information, or what can threaten the continuity of your operations.
Consequently, risk assessment needs to be done at the beginning of the ISO 27001 project, while the internal audit is done only after the implementation has been completed.
How is the internal audit done?
The internal audit is nothing more than listing all the rules and requirements, and then finding out if those rules and requirements are complied with.
Typically, rules and requirements are the following:
- Requirements of ISO 27001, ISO 22301 (or any other ISO standard)
- Requirements of interested parties (see: Who are interested parties, and how can you identify them according to ISO 27001 and ISO 22301? )
- Rules set by the company’s own policies and procedures
When performing an internal audit, you need to check if each and every rule and requirement was complied with, in the whole scope of your Information Security Management System or Business Continuity Management System.
This is done by using various techniques:
- Examining all the documentation and records
- Interviewing the employees
- Personal observations (e.g., walking around the premises)
See also: ISO 27001 Internal Auditor course .
The main differences between the two
So, I would say that one of the main differences is in the mindset: risk assessment is thinking about the (potential) things that could happen in the future, while the internal audit is dealing with how things were done in the past.
The second major difference is that the internal audit focuses on compliance with various rules and requirements, while risk assessment is nothing but analysis that provides a basis for building up certain rules.
The third difference is that the risk assessment is done before you start applying the security controls, while the internal audit is performed once these are already implemented.
However, they (unfortunately) do have one thing in common: they are both very often neglected in companies because they are perceived as only a bureaucratic exercise with no real value. However, the people who think this don’t realize they are both crucial for building up your information security.
Can ISO 27001 risk assessment be used for ISO 22301 business continuity?
A few days ago, I received the following question from one of our clients: “What is the difference between ISMS Risk Assessment and BCM Risk Assessment?” And, although the answer to this question might seem easy, in actuality it is not.
Here’s the rest of his question: “… Because on your blog I found that if I’ve done ISMS it should be fine for BCM. On the other hand, ISO 22301 recommends to use the ISO 31000 standard.”
Why the ISO 27001 risk management framework is a good solution
It is true that ISO 22301 refers to ISO 31000 regarding risk assessment, but so does ISO 27001 – this does not mean you can actually use ISO 31000 for implementation, because this standard is written very generally since it covers all kinds of risks – not only business continuity and information security, but also financial, market, credit, and other risks.
On the other hand, the risk assessment framework is described much better in ISO 27001, and even more precisely in ISO 27005; the focus of information security risk assessment is on preserving confidentiality, integrity, and availability. And availability is the key link between information security and business continuity – when performing ISMS risk assessment, all the business continuity risks will be taken into account as well.
And the good thing is, risk assessment as it is described in ISO 27001 and ISO 27005 is perfectly aligned with ISO 31000.
Possible differences in approach
But this is where it might get complicated – my client had another question, because he wanted everything to be cleared out: “I think that another difference between those two Risk Assessment approaches is – with ISMS we deal with assets (both primary and supportive); however, with BCM we deal with critical activities and processes.”
And he was basically right – business continuity risk assessment does not have to be so detailed; it can be made high-level for activities and processes. But, in my view, the problem is in the implementation – how can you mitigate the risks if you don’t know exactly where the problems are?
This is where I think the ISO 27001 risk assessment framework is better – it forces you to pinpoint where the weaknesses are, which assets should be protected better, etc. If you kept the risk assessment on the process level you probably wouldn’t get all this valuable information.
Risk mitigation compatibility
It is worth mentioning here – ISO 27001 risk treatment options are completely aligned with the risk mitigation requirements in ISO 22301 and ISO 31000. Basically, business continuity mitigation comes down to the four options described in this article above. There are no options listed in ISO 22301, while in ISO 31000 they are named a bit differently and organized a bit differently, but they are essentially the same.
And to finish with this: there is another good thing about ISO 27001 – in Annex A it gives you a catalogue of possible safeguards to choose from; this is something that neither ISO 22301 nor ISO 31000 has.
Risk assessment vs. business impact analysis
If you are implementing ISO 27001, or especially ISO 22301 , for the first time, you are probably puzzled by the risk assessment and business impact analysis. What is their purpose? How are they different? Can they be performed at the same time?
To put it briefly, risk assessment will show you which kinds of incidents you might face, while business impact analysis will show you how quickly you need to recover your activities from incidents to avoid larger damage.
The purpose of risk assessment
The purpose of this assessment is to systematically find out which incidents can happen to your organization, and then through the process of risk treatment to prepare in order to minimize the damage of such incidents.
In my experience, the employees (and the organization as a whole) are usually aware of only 25 to 40% of risks – therefore, it is not possible to try to remember all the risks by heart, and this identification needs to be done in a systematic way.
The purpose of business impact analysis (BIA)
Business impact analysis is mandatory for the implementation of business continuity according to ISO 22301, but not for ISO 27001.
The purpose of the BIA is primarily to give you an idea of (1) the timing of your recovery, and (2) the timing of your backup, since the timing is crucial – the difference of only a couple of hours could mean life or death for certain companies if hit by a major incident.
More precisely, business impact analysis will help you determine the Maximum Acceptable Outage/Recovery Time Objective, Maximum Data Loss/Recovery Point Objective, required resources, and other important information that will help you develop the business continuity strategy for each of your activities. Learn more here: How to implement business impact analysis (BIA) according to ISO 22301 .
The difference between the two
As already concluded, BIA is usually used only in business continuity / ISO 22301 implementation; it could be done for information security, but it wouldn’t make much sense. Risk assessment (RA) is mandatory for both ISO 27001 and for ISO 22301.
Secondly, the outputs from RA are a bit different from those of BIA – RA gives you a list of risks together with their values, whereas BIA gives you timing within which you need to recover (RTO) and how much information you can afford to lose (RPO).
So, although these two are related because they have to focus on the organization’s assets and processes, they are used in different contexts.
Which comes first – risk assessment or business impact analysis?
Actually, ISO 22301 allows both approaches, and you might hear many theories on which is better. However, I prefer to do risk assessment first because this way, you will have a better impression of which incidents can happen (which risks you’re exposed to), and therefore be better prepared for doing the business impact analysis (which focuses on the consequences of those incidents); further, if you choose the asset-based approach for risk assessment, you will have an easier time identifying all the resources later on in the business impact analysis. What you definitely shouldn’t do is perform risk assessment and business impact analysis at the same time, because each of them separately is already complex enough – combining them normally means trouble.
ISO 27001 2013 revision vs. 2022 revision – has anything changed?
The good news is that there were no changes in risk assessment requirements, so whatever you were doing to be compliant with the 2013 revision will still make you compliant with the 2022 revision.
Let’s remember a couple of myths related to risk management that have developed around the previous version, ISO 27001:2013, that are still myths when it comes to ISO 27001:2022:
- “We have to use ISO 31000 for risk management.” False – ISO 31000 is only mentioned in ISO 27001:2022, but it is not mandatory. (See also ISO 31000 and ISO 27001 – How are they related? )
- “We have to delete assets, threats, and vulnerabilities from our risk assessment in ISO 27001.” False again – you can keep your old methodology if you like it, because ISO 27001:2022 still leaves you the freedom to identify risks any way you want.
- “We do not have to identify asset owners anymore.” Another false statement – the 2022 version of the standard does require you to do it in control A.5.9. (See also Risk owners vs. asset owners in ISO 27001 ).
- “The identification of risks based on confidentiality, integrity, and availability (C-I-A) is a new concept.” False – this concept still exists in ISO 27001:2022, too; actually, the whole standard is based on the concept of protecting the C-I-A from the very beginning.
So, as you can see, there are no changes in risk assessment and treatment, and you’ll find the transition to the 2022 revision of ISO 27001 relatively easy. All you need to do is keep identifying risk owners for each risk, and give them the responsibility to make decisions about the risks.
Qualitative vs. quantitative risk assessment
In the risk assessment process, one common question asked by organizations is whether to go with a quantitative or a qualitative approach. The good news is that you can use the easier approach (qualitative approach) and be fully compliant with ISO 27001; you can also use both approaches if you want to take a step forward in making your risk assessment highly advanced.
Qualitative risk assessment
In qualitative risk assessment, the focus is on interested parties’ perceptions about the probability of a risk occurring and its impact on relevant organizational aspects (e.g., financial, reputational, etc.). This perception is represented in scales such as “low-medium-high” or “1-2-3-4-5,” which are used to define the risk’s final value.
Since it has little mathematical dependency (risk may be calculated through a simple sum, multiplication, or other form of non-mathematical combination of probability and consequence values), qualitative risk assessment is easy and quick to perform.
One problem with qualitative assessment is that it is highly biased, both in terms of probability and impact definition, by those who perform it.
For example, for HR people, HR impacts will be more relevant than IT impacts, and vice versa. Regarding a bias in probability, a lack of understanding of the timeframes of other processes may lead someone to think errors and failures occur more often in his own process than in the others, and this may not be true.
This situation with bias generally makes the qualitative assessment more useful in the local context where it is performed, because people outside the context probably will have divergences regarding impact value definition.
Quantitative risk assessment
On the other hand, quantitative risk assessment focuses on factual and measurable data to calculate probability and impact values, normally expressing risk values in monetary terms, which makes its results useful outside the context of the assessment (loss of money is understandable for any business unit). To reach a monetary result, quantitative risk assessment often makes use of these concepts:
- SLE (Single Loss Expectancy): money expected to be lost if the incident occurs one time.
- ARO (Annual Rate of Occurrence): how many times in a one-year interval the incident is expected to occur.
- ALE (Annual Loss Expectancy): money expected to be lost in one year considering SLE and ARO (ALE = SLE * ARO). For quantitative risk assessment, this is the risk value.
By relying on factual and measurable data, quantitative risk assessment has as its main benefits the presentation of very precise results about risk value, and the maximum investment that would make risk treatment worthwhile, so that it is profitable for the organization. Below is an example of how risk values are calculated through quantitative risk assessment:
- Database value: $2.5 million (SLE)
- Manufacturer statistics show that a database catastrophic failure (due to software or hardware) occurs one time every 10 years (1/10 = 0.1) (ARO)
- Risk value: $2,500,000 x 0.1 = $250,000 (ALE)
That is, in this case, the organization has an annual risk of suffering a loss of $250K in the event of the loss of its database. So, any implemented control (e.g., backup, patch management, etc.) that costs less than this value would be profitable.
The problem with quantitative assessment is that, in most cases, there is no sufficient data about SLE and ARO, or obtaining such data costs too much.
Combining approaches
As you may notice, qualitative and quantitative assessments have specific characteristics that make each one better for a specific risk assessment scenario, but in the big picture, combining both approaches can prove to be the best alternative for a risk assessment process.
By using the qualitative approach first, you can quickly identify most of the risks. After that, you can use the quantitative approach on the highest risks, to have more detailed information for decision making.
A general example would be a medical appointment. The doctor first asks a few simple questions, and from patient answers he decides which more detailed exams to perform, instead of trying every exam he knows at the beginning.
Adapt your approach to optimize your effort and results
Risk assessment is one of the most critical parts of risk management, and also one of the most complex – affected by human, technical, and administrative issues. If not done properly, it could compromise all efforts to implement an ISO 27001 Information Security Management System, which makes organizations think about whether to perform qualitative or quantitative assessments. But you do not need to rely on a single approach, because ISO 27001 allows both qualitative and quantitative risk assessment to be performed.
If your company needs quick and easy risk assessment, you can go with qualitative assessment (and this is what 99% of the companies do). However, if you need to make some really big investment that is critical for security, perhaps it makes sense to invest time and money into quantitative risk assessment.
In short, by adopting a combined approach considering the information and time response needed, and data and knowledge available, you can enhance the effectiveness of the ISO 27001 information security risk assessment process, and also take a step further from what the standard requires.
What are the different types of risk assessment?
The 2022 version of ISO 27001 does not prescribe any particular approach or methodology for performing the risk assessment.
While this provides more freedom for organizations to choose the risk identification approach that better fits their needs, the absence of such orientation is the source of a lot of confusion for organizations about how to approach risk identification.
Here I’ll explain how ISO 31010 (a standard focused on risk assessment) can help you, by presenting some of its risk identification approaches that can be used to find, recognize, and describe risks. Even though the approach suggested by ISO 31010 is not mandatory for ISO 27001, companies that want to explore other approaches to risk assessment might find it useful.
The risk identification step
According to ISO 31010, the purpose of risk identification is to identify what could happen, or which situations could exist, that may affect the achievement of proposed objectives. Considering information security, some practical examples are:
- A power surge may cause a storage unit to fail, leading to data loss.
- A lack of attention may cause an employee to send a report to the wrong person, leading to unauthorized information disclosure.
- A change in environmental conditions may cause a device to make erroneous readings, leading to a compromise of data integrity.
Once a risk is identified, the organization should also identify any existing controls affecting that risk, and proceed to the next steps of the risk assessment (risk analysis and risk evaluation).
Potential methodologies for identifying risks
According to ISO 31010, a risk description must contain some elements:
- risk sources : elements in the scenario that, isolated or combined, have the potential to affect the expected results (e.g., the electricity to power the storage unit)
- event : a specific set of circumstances (e.g., the storage unit failure)
- cause : the initial condition that starts the event (e.g., the power surge)
- consequence : the result of the event affecting the objective (e.g., the data loss, affecting the information availability)
ISO 31010 suggests the following risk identification methodologies that help collect all risk elements:
Brainstorming: a group creativity technique for collecting a large amount of information to find a conclusion for a specific situation. Because of its strong emphasis on imagination, it is useful to identify risks in situations that require a quick response and have few formal data available (e.g., selection of less harmful measures to contain an ongoing attack), or are new to the organization, like risks involving the entrance in a new market segment.
Interview: a conversation where pre-defined questions are presented to an interviewee to understand his perception of a given situation (e.g., market trends, processes performance, product expectations, etc.), and by that identify risks considering his perspective. It is recommended when detailed particular opinions are required (e.g., from the CEO, CFO, clients, etc.).
Delphi method: an anonymous collaborative technique used to combine different expert opinions in a reliable and unbiased way toward a consensus (e.g., selecting a security supplier, defining a protection strategy). It differs from brainstorming because it works to eliminate solutions during its realization, instead of creating them. It should be considered in situations where the characteristics of participants may affect the opinions of others (e.g., all agree/disagree with someone just because of his position).
Checklist: a technique where a list of items is elaborated to ensure that the most common topics, as well as the critical ones, on the subject matter are not forgotten during risk identification (e.g., common failures in software development, or protections required by contract). This increases the consistency and completeness of risk identification. Its use is recommended in cases where historical information, market references, and knowledge of previous situations are widely available.
Scenario analysis: methodology that uses models describing possible future scenarios to identify risks considering possible outcomes, strategies and actions leading to the outcomes, and possible implications to the business. A common approach in information security is, e.g., the use of permissive, restrictive, and balanced scenarios to identify risks in access control. It should be considered in situations where multiple solutions are available or results can present great variation.
What about the asset-threat-vulnerability approach?
Although asset-based methodology is not mandatory in the ISO 27001:2022 standard, it still is a valid approach that is used in a large majority of compliance projects. Of course, organizations that have already implemented an asset-based approach and think it is a good fit for them can continue to use it normally.
However, if you would like to use a different approach that can take the most advantage of the situation and the available information, your organization can consider some other approaches to risk identification and make your risk assessment more advanced.
To see how to use the ISO 27001 Risk Register with catalogs of assets, threats, and vulnerabilities, and get automated suggestions on how they are related, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.

Theoretical semi-quantitative risk assessment methodology for tunnel design and construction processes
- ORIGINAL ARTICLE
- Published: 10 May 2024
Cite this article

- Ozgur Satici ORCID: orcid.org/0000-0003-4709-4334 1 , 2 &
- Esra Satici ORCID: orcid.org/0000-0002-6784-182X 1
Explore all metrics
All engineering projects involve risk management applications. Sometimes, risks cannot be effectively managed, leading to catastrophic consequences. Engineers must consciously or unconsciously manage these risks. Regardless of how risks are handled, project risks need to be systematically evaluated. Therefore, risk management procedures must be implemented in every project, particularly in geo-engineering projects, to mitigate undesirable consequences and achieve project objectives. However, the use of risk management procedures in underground excavation projects is not common. Numerous commonly employed underground excavation techniques lack assessment of risks, notably geotechnical risks. Most of them only evaluate rock structures and excavation stability in accordance with the geological structure. This paper combines a universal risk management perspective with the underground engineering discipline. The tunnel engineering design and construction steps were evaluated for uncertainties using Scenario Structuring Modeling techniques to identify both technical and non-technical risks associated with underground excavation. Bayesian Network models were employed to identify connections that contribute to risk. To achieve this, objective and quantitative risk assessment tables have been devised using risk management philosophy, in accordance with tunnel design engineering principles and Turkish procurement laws. The primary objective of this study is to increase awareness of the use of risk management processes in tunnel construction projects and introduce a systematic approach to risk assessment in tunnel engineering projects. As a result, a semi-quantitative risk assessment method based on risk management philosophy is proposed for tunnel design and construction for the first time, evaluating not only geotechnical and engineering risks but also human, financial, and various other sources of risks.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions

Bai C, Xue Y, Qiu D, Su M, Ma X, Liu H (2021) Analysis of factors affecting the deformation of soft rock tunnels by data envelopment analysis and a risk assessment model. Tunn Undergr Space Technol. https://doi.org/10.1016/j.tust.2021.104111
Article Google Scholar
Barton NR, Lien R, Lunde J (1974) Engineering classification of rock masses for the design of tunnel support. Rock Mech 6(4):189–239. https://doi.org/10.1007/BF01239496
Bayes T (1763) An essay towards solving a problem in the doctrine of chance. Philosophical Transactions Royal Society of London 53: 370–418. https://doi.org/10.1098/rstl.1763.0053
Bieniawski ZT (1989) Engineering rock mass classifications: a complete manual for engineers and geologists in mining civil and petroleum engineering. John Wiley and Sons, xii, New York, p p251
Google Scholar
Brierley G (2014) http://tunnelingonline.com/tunneling-historical-perspective/
Brown TE (2012) Risk assessment and management in underground rock engineering—an overview. J Rock Mech Geotech Eng 4(3):193–204. https://doi.org/10.3724/SP.J.1235.2012.00193
Charles River Analytics (2008) About Bayesian belief networks. Charles River Analytics Inc., Cambridge MA
Chung H, Park J, Kim B-K, Kwon K, Lee I-M, Choi H (2021) A causal network-based risk matrix model applicable to shield TBM tunneling projects. Sustainability 13(9):4846. https://doi.org/10.3390/su13094846
Conrady S, Jouffe L., Introduction to Bayesian Networks: Practical and Technical Perspectives, Franklin TN: Conrady Applied Science, 2011
Daller J (2006) Risk control at the design of long railway tunnel in Austria geotechnical risks in rock tunnels. Taylor & Francis Group, London, pp 155–163
Book Google Scholar
Deng M (2018) Challenges and thoughts on risk management and control for the group construction of a super-long tunnel by TBM. Engineering 4:112–122. https://doi.org/10.1016/j.eng.2017.07.001
Eskesen DS, Tengborg P, Kampman J, Veichherts HT (2004) Guidelines for tunneling risk management: international tunneling association, working group . 2. Tunn Undergr Space Technol 19:217–237
Guo DS, Meng FY, Wu HN, Yang XX, Liu Z (2024) Risk assessment of shield tunneling crossing building based on variable weight theory and cloud model. Tunn Undergr Space Technol. https://doi.org/10.1016/j.tust.2024.105593
Gutierrez-Fernandez JD, Rodriguez SS, Gonzalo-Orden H, Perez-Acebo H (2021) Analysis of rock mass classifications for safer infrastructures. Transp Res Proced 58:606–613
Haimes YY (2006) On the definition of vulnerabilities in measuring risks to infrastructures. Risk Anal. https://doi.org/10.1111/j.1539-6924.2006.00755.x
Haimes YY (2009a) On the complex definition of risk: a systems-based approach. Risk Anal 29:1647–1654. https://doi.org/10.1111/j.1539-6924.2009.01310.x
Haimes YY (2009b) On the definition of resilience in systems. Risk Anal 29:498–501. https://doi.org/10.1111/j.1539-6924.2009.01216.x
Hillson D (2009) Managing risk in projects Fundamentals of Project Management. Gower Publishing, Aldershot, p 127
Hopkin P (2018) Fundamentals of Risk Management, Understanding Evaluating and Implementing Effective Risk Management, The Institute of Risk Management, Kogan Page Limited; London, p385
Hyun K-C, Min S, Choi H, Park J, Lee I-M (2015) Risk analysis using fault-tree analysis (FTA) and analytic hierarchy process (AHP) applicable to shield TBM tunnels. Tunn Undergr Space Technol 49:121–129. https://doi.org/10.1016/j.tust.2015.04.007
Jaynes ET (1996) Probability Theory with Applications in Science and Engineering, Posthumous manuscript, placed online, http://bayes.wustl.edu/etj/science.pdf.html
Kaplan S, Garrick BJ (1981) On the quantitative definition of risk. Risk Anal 1:11–27. https://doi.org/10.1111/j.1539-6924.1981.tb01350.x
Karakus M, Fowell RJ (2004) An insight into the new austrian tunneling method (NATM). Bölgesel Kaya Mekaniği Sempozyumu, Sivas, Türkiye
Kim J, Kim C, Kim G, Kim I, Abbas Q, Lee J (2022) Probabilistic tunnel collapse risk evaluation model using analytical hierarchy process (ahp) and delphi survey technique. Tunn Undergr Space Technol. https://doi.org/10.1016/j.tust.2021.104262
Koohathongsumrit N, Meethom W (2024) Risk analysis in underground tunnel construction with tunnel boring machines using the best-worst method and data envelopment analysis. Heliyon. https://doi.org/10.1016/j.heliyon.2023.e23486
Koseoglu Balta GC, Dikmen I, Birgonul MT (2021) Bayesian network-based decision support for predicting and mitigating delay risk in TBM tunnel projects. Autom Constr 129:103819. https://doi.org/10.1016/j.autcon.2021.103819
Lee E, Park Y, Shin JG (2009) Large engineering project risk management using a bayesian belief network. Expert Syst Appl 36(3):5880–5887. https://doi.org/10.1016/j.eswa.2008.07.057
Lei X (2020) Risk assessment model of underground engineering based on delphi-AHP, In: 2nd International conference on oil & gas engineering and geological sciences, IOP Conf. Series: earth and environmental science 558, 032029, https://doi.org/10.1088/1755-1315/558/3/032029
Li X, Zhang L, Zhang S (2018) Efficient bayesian networks for slope safety evaluation with large quantity monitoring information. Geosci Front 9(6):1679–1687. https://doi.org/10.1016/j.gsf.2017.09.009
Lin SS, Zhou A, Shen SL (2024a) Multi-status bayesian network for analyzing collapse risk of excavation construction. Autom Constr. https://doi.org/10.1016/j.autcon.2023.105193
Lin D, Zhou Z, Weng M, Broere W, Cui J (2024b) Metro systems: construction, operation and impacts. Tunn Undergr Space Technol. https://doi.org/10.1016/j.tust.2023.105373
Lowrance WW (1976) Of acceptable risk. William Kaufmann, Los Altos, CA
Lunardi P (2008) Design and construction of tunnels, analysis of controlled deformation in rock and soils (ADECO-RS). Springer, New york
Mahmoodzadeh A, Zare S (2016) Probabilistic prediction of expected ground condition and construction time and costs in road tunnels. J Rock Mech Geotech Eng 8(5):734–745. https://doi.org/10.1016/j.jrmge.2016.07.001
Moradi MR, Farsangi MAE (2014) Application of the risk matrix method for geotechnical risk analysis and prediction of the advance rate in rock TBM tunneling. Rock Mech Rock Eng 47(5):1951–1960. https://doi.org/10.1007/s00603-013-0464-x
Munier N (2013) Project management for environmental construction and manufacturing engineers, a manuel for putting theory into practice. Springer, New york, p 262
Ou GZ, Jiao YY, Zhang GH, Zou JP, Tan F, Zhang WS (2021) Collapse risk assessment of deep-buried tunnel during construction and its application. Tunn Undergr Space Technol. https://doi.org/10.1016/j.tust.2021.104019
Özdemir L (2006) North American tunneling. Taylor&Francis, Washington, DC, p p246 ( ISBN 0-415-40128-3 )
Palmstrom A (1996) RMi-a system for characterizing rock mass strength for use in rock engineering. J Rock Mech Tunn Technol 1:69–108
Platon V, Constantinescu A (2014) Monte carlo method in risk analysis for investment projects. Proced Econ Finance 15:393–400. https://doi.org/10.1016/S2212-5671(14)00463-8
Poeschl I, Kleberger J (2006) Geotechnical risk in rock mass characterization—a concept, geotechnical risks in rock tunnels. Taylor & Francis Group, London, pp 145–154 ( ISBN 0-415-40005-8 )
Prasanta KD (2012) Project risk management using multiple criteria decision-making technique and decision tree analysis: a case study of indian oil refinery. Prod Plan Control 23(12):903–921. https://doi.org/10.1080/09537287.2011.586379
Proag V., 2014, The concept of vulnerability and resilience, In: 4th International conference on building resilience, Procedia Economics and Finance, v18, pp369–376
Rabcewicz L (1964) The new Austrian tunneling method, part one, water power , 453–457, part two, Water Power, pp511–515
Rabcewicz L (1965) The new Austrian tunneling method part three. Water Power 5:19–24
Sandström GE (1963) The history of tunneling, underground workings through the ages, barrie and rockliff
Satıcı Ö (2021) Projeler nasil başarili olur, mühendisler için risk yönetim rehberi, seçkin yayinevi, Ankara, 156s
Satici O, Topal T (2015) Evaluation of tunnel excavation methods in accordance with engineering geology and rock mass classification systems, Jour. Of Geo. Eng. 39 (1)
Schubert P (2006) Geotechnical risk management in tunneling, geotechnical risks in rock tunnels. Taylor & Francis Group, London, pp 53–62 ( ISBN-0-415-40005-8 )
Schuyler J (2001) Risk and decision analysis in projects, 2nd edn. Project Management Institute Publication, Newtown Square, p p278
Sharafat A, Latif K, Seo J (2021) Risk analysis of tbm tunneling projects based on generic bow tie risk analysis approach in difficult ground conditions. Tunn Undergr Space Technol 111:103860. https://doi.org/10.1016/j.tust.2021.103860
Shahriar K, Sharifzadeh M, Hamidi JK (2008) Geotechnical risk assessment based approach for rock tbm selection in difficult ground conditions. Tunn Undergr Space Technol 23(3):318–325. https://doi.org/10.1016/j.tust.2007.06.012
Shelake AG, Gogate NG, Rajhans NR (2022) An integrated approach for identification and prioritization of risk factors in tunnel construction. Mater Today: Proceed 65:1805–1812. https://doi.org/10.1016/j.matpr.2022.04.855
Sousa RL (2010) Risk analysis for tunneling projects. PhD thesis. Massachusetts Institute of Technology
Sousa RL, Einstein HH (2012) Risk analysis during tunnel construction using bayesian networks: porto metro case study. Tunn Undergr Space Technol 27:86–100. https://doi.org/10.1016/j.tust.2011.07.003
Sousa LR, Miranda T, Sousa RL, Tinoco J (2017) The use of data mining techniques in rockburst risk assessment. Engineering 3:552–558. https://doi.org/10.1016/J.ENG.2017.04.002
Spross J, Olsson L, Stille H (2018) The Swedish geotechnical society’s methodology for risk management: a tool for engineers in their everyday work. Georisk Assess Manag Risk Eng Syst Geohazards 12(3):183–189. https://doi.org/10.1080/17499518.2017.1416643
Taleb NN (2008) The black swan: the impact of the highly improbable. Penguin Books Ltd, London, p p480
Tidlund M, Spross J, Larsson S (2022) Observational method as risk management tool the hvalfjörður tunnel project Iceland. Georisk: Assess Manag Risk Eng Syst Geohazards. https://doi.org/10.1080/17499518.2022.2046784
Tonon F (2010) Sequential excavation, NATM and ADECO: what they have in common and how they differ, tunneling and underground. Space Technol 25(3):245–265. https://doi.org/10.1016/j.tust.2009.12.004
Vydrova CL (2015) Comparison of tunneling methods NATM and ADECO-RS. Civil Eng J. https://doi.org/10.14311/CEJ.2015.01.0003
Wang L, Chen H, Liu Y, Li H, Zhang W (2023) Application of Copula-Based Bayesian Network Method to Water Leakage Risk Analysis in Cross River Tunnel of Wuhan Rail Transit Line 3. Adv Eng Inform. https://doi.org/10.1016/j.aei.2023.102056
Zeng Y, Guy P, Njock A, Xiong W, Zhang XL, Shen SL (2023) Risks analysis of large diameter slurry shield tunneling in urban area. Underground Space 13:281–300. https://doi.org/10.1016/j.undsp.2023.05.001
Zhang C, Liu N, Chu W (2016) Key technologies and risk management of deep tunnel construction at jinping II hydropower station. J Rock Mech Geotech Eng 8:499–512
Zhou Z, Liu S, Qi H (2022) Mitigating subway construction collapse risk using bayesian network modeling. Autom Constr. https://doi.org/10.1016/j.autcon.2022.104541
Download references
Author information
Authors and affiliations.
Karayollari Genel Mudurlugu, Inonu Bulvari No: 14, Yücetepe, 06100, Çankaya, Ankara, Turkey
Ozgur Satici & Esra Satici
Social Sciences University of Ankara, Ankara, Turkey
Ozgur Satici
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Ozgur Satici .
Ethics declarations
Conflict of interest.
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Consent to participate
On behalf of all authors, the corresponding author states that there is no research in this study involving Human Participants and/or Animals.
Informed consent
On behalf of all authors, the corresponding author states that there are no case reports requiring ethical approval.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix 1 Risk assessment and analysis workflow

Appendix 2 Work breakdown structure for a highway tunnel construction

Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Satici, O., Satici, E. Theoretical semi-quantitative risk assessment methodology for tunnel design and construction processes. Int J Syst Assur Eng Manag (2024). https://doi.org/10.1007/s13198-024-02348-1
Download citation
Received : 06 December 2023
Revised : 14 March 2024
Accepted : 15 April 2024
Published : 10 May 2024
DOI : https://doi.org/10.1007/s13198-024-02348-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Bayesian network
- Risk assessment
- Scenario structuring modeling
- Tunnel construction
- Find a journal
- Publish with us
- Track your research
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

5 IT risk assessment frameworks compared
Formal risk assessment methodologies can help take guesswork out of evaluating it risks if applied appropriately. here is real-world feedback on using cobit, octave, fair, nist rmf, and tara..

From a cybersecurity standpoint, organizations are operating in a high-risk world. The ability to assess and manage risk has perhaps never been more important. “Having a risk management framework is essential, because risk can never be totally eliminated; it can only be effectively managed,” says Arvind Raman, CISO at telecommunications company Mitel Networks. “When it isn’t, organizations will likely find themselves the target of a data breach or ransomware attack, or be vulnerable to any number of other security issues.”
The most critical consideration in selecting a framework is ensuring that it’s “fit for purpose” and best suited for the intended outcomes, says Andrew Retrum, managing director in the cybersecurity and privacy practice at consulting firm Protiviti. “It’s also beneficial to select frameworks that are well known and understood already within the organization,” Retrum says. “This enables more consistent and efficient use of the framework and allows individuals across the organization to speak a consistent language.”
There’s no shortage of risk-assessment frameworks organizations can leverage to help guide security and risk executives. Here’s a look at some of the most prominent of these frameworks, each designed to address specific risk areas.
NIST Risk Management Framework
The Risk Management Framework (RMF) from the National Institute of Standards and Technology (NIST) provides a comprehensive, repeatable, and measurable seven-step process organizations can use to manage information security and privacy risk. It links to a suite of NIST standards and guidelines to support the implementation of risk management programs to meet the requirements of the Federal Information Security Modernization Act (FISMA) .
RMF provides a process that integrates security, privacy, and supply chain risk management activities into the system development lifecycle, according to NIST. It can be applied to new and legacy systems, any type of system or technology including internet of things (IoT) and control systems, and within any type of organization regardless of size or sector. The seven RMF steps are:
- Prepare, including essential activities to prepare the organization to manage security and privacy risks.
- Categorize, which involves sorting systems and information that’s processed, stored, and transmitted based on an impact analysis.
- Select, which is selecting the set of NIST SP 800-53 controls to protect systems based on risk assessment;
- Implement, deploying the controls and documenting how they are deployed.
- Assess, to determine if the controls are in place, operating as intended, and producing the desired results.
- Authorize, where a senior executive makes a risk-based decision to authorize the system to operate.
- Monitor, which involves continuously monitoring control implementation and risks to systems.
“NIST RMF can be tailored to organizational needs,” Raman says. It is frequently assessed and updated, and many tools support the standards developed. It’s vital that IT professionals “understand when deploying NIST RMF it is not an automated tool, but a documented framework that requires strict discipline to model risk properly.”
NIST has produced several risk-related publications that are easy to understand and applicable to most organizations, says Mark Thomas, president of Escoute Consulting and a speaker for the Information Systems Audit and Control Association (ISACA). “These references provide a process that integrates security, privacy, and cyber supply chain risk management activities that assists in control selection and policy development,” he says. “Sometimes thought of as guides for government entities, NIST frameworks are powerful reference for government, private, and public enterprises.”
The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) , developed by the Computer Emergency Readiness Team (CERT) at Carnegie Mellon University, is a framework for identifying and managing information security risks. It defines a comprehensive evaluation method that allows organizations to identify the information assets that are important to their goals, the threats to those assets, and the vulnerabilities that might expose those assets to the threats.
By putting together the information assets, threats, and vulnerabilities, organizations can begin to understand what information is at risk. With this understanding, they can design and deploy strategies to reduce the overall risk exposure of information assets.
Two versions of OCTAVE are available. One is OCTAVE-S, a simplified methodology designed for smaller organizations that have flat hierarchical structures. The other is OCTAVE Allegro, which is a more comprehensive framework suitable for large organizations or those that have complex structures.
“OCTAVE is a well-designed risk assessment framework because it looks at security from a physical, technical, and human resource perspective,” Raman says. “It identifies assets that are mission-critical for any organization and uncovers threats and vulnerabilities. However, it can be very complex to deploy and it solely quantifies from a qualitative methodology.”
The flexibility of the methodology “allows teams from operations and IT to work together to address the security needs of the organization,” Thomas says.
Control Objectives for Information and related Technology (COBIT) , from ISACA, is a framework for IT management and governance. It is designed to be business focused and defines a set of generic processes for the management of IT. Each process is defined together with process inputs and outputs, key activities, objectives, performance measures and an elementary maturity model.
The latest version, COBIT 2019, offers more implementation resources, practical guidance and insights, as well as comprehensive training opportunities, according to ISACA. It says implementation is now more flexible, enabling organizations to customize their governance via the framework.
COBIT is a “high-level framework aligned to IT management processes and policy execution,” says Ed Cabrera, chief cybersecurity officer at security software provider Trend Micro and former CISO of the United States Secret Service. “The challenge is that COBIT is costly and requires high knowledge and skill to implement.”
The framework “is the only model that addresses the governance and management of enterprise information and technology, which includes an emphasis [on] security and risk,” Thomas says. “Although the primary intent of COBIT is not specifically in risk, it integrates multiple risk practices throughout the framework and refers to multiple globally accepted risk frameworks.”
Threat Assessment and Remediation Analysis (TARA) is an engineering methodology used to identify and assess cybersecurity vulnerabilities and deploy countermeasures to mitigate them, according to MITRE, a not-for-profit organization that works on research and development in technology domains including cybersecurity.
The framework is part of a MITRE’s portfolio of systems security engineering (SSE) practices. “The TARA assessment approach can be described as conjoined trade studies, where the first trade identifies and ranks attack vectors based on assessed risk, and the second identifies and selects countermeasures based on assessed utility and cost,” the organization claims.
Unique aspects of the methodology include use of catalog-stored mitigation mappings that preselect possible countermeasures for a given range of attack vectors, and the use of countermeasure strategies based on the level of risk tolerance.
“This is a practical method to determine critical exposures while considering mitigations, and can augment formal risk methodologies” to include important information about attackers that can result in an improved risk profile, Thomas says.
Factor Analysis of Information Risk (FAIR) is a taxonomy of the factors that contribute to risk and how they affect each other. Developed by Jack Jones, former CISO of Nationwide Mutual Insurance, the framework is mainly concerned with establishing accurate probabilities for the frequency and magnitude of data loss events.
FAIR is not a methodology for performing an enterprise or individual risk assessment. But it provides a way for organizations to understand, analyze, and measure information risk. The framework’s components include a taxonomy for information risk, standardized nomenclature for information-risk terms, a method for establishing data-collection criteria, measurement scales for risk factors, a computational engine for calculating risk, and a model for analyzing complex risk scenarios.
FAIR “is one of the only methodologies that provides a solid quantitative model for information security and operational risk,” Thomas says. “This pragmatic approach to risks provides a solid foundation to assessing risks in any enterprise.” However, while FAIR provides a comprehensive definition of threat, vulnerability, and risk, “it’s not well documented, making it difficult to implement,” he says.
The model differs from other risk frameworks “in that the focus is on quantifying risks into actual dollars, as opposed to the traditional ‘high, medium, low’ scoring of others,” Retrum says. “This is gaining traction with senior leaders and board members, enabling a more thoughtful business discussion by better quantifying risks in a meaningful way.”
Editor’s note: This article, originally published May 3, 2010, has been updated with current information.
Related content
Low-tech tactics still top the it security risk chart, download the sase and sse enterprise buyer’s guide, intelbroker steals classified data from the europol website, ridding your network of ntlm, from our editors straight to your inbox.

Bob Violino is a freelance writer who covers a variety of technology and business topics.
More from this author
How attackers exploit qr codes and how to mitigate the risk, 5 key considerations for your 2023 cybersecurity budget planning, 7 top challenges of security tool integration, 5 top hybrid cloud security challenges, most popular authors.

Show me more
Cisa inks 68 tech vendors to secure-by-design pledge — but will it matter.

Google Chrome gets a patch for actively exploited zero-day vulnerability

Dell data breach exposes data of 49 million customers

CSO Executive Sessions: The personality of cybersecurity leaders

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
Read the May magazine issue on food and climate change
Formal risk assessments and nuclear arms control: exploring the value of modern methodologies
By Vicki Bier , Robert J. Budnitz , Olli Heinonen , Richard C. Lanza , Ronald F. Lehman , Sally Leivesley , Charles F. McMillan , George H. Miller , Anita Nilsson , John Organek , Robert N. Schock | May 13, 2024
- Copy link Linked copied
Numerous technological, geostrategic, economic, and demographic changes challenge the stability of the international-security architecture and its arms-control structures. Factors leading to a reexamination of arms-control strategies include the post-post-Cold War environment, an increase in the number and diversity of international actors that have (or could have) nuclear capabilities, and new weapons capabilities. Information warfare, hybrid warfare, cyber operations, dependence on fragile space-based capabilities, hypersonic and stealth delivery systems, speed-of-light technologies — and even the deliberate violation of previously agreed rules as a means of signaling and intimidation — are all accelerating the erosion of international norms related to international security. Hypersonic boost-glide vehicles (HBGVs) constitute one of many such challenges. They make an interesting case study because they can carry either nuclear or non-nuclear payloads and combine the high speed of ballistic missiles with the maneuverability of cruise missiles. Their hybrid performance and multi-mission role complicate missile defense and further illustrate the complexity of the overall security situation.
Comparative risk is always a major consideration in arms control, but formal risk assessments are generally not performed, despite decades of advancement in risk-analysis methods that have been applied successfully in other fields (e.g., nuclear reactors). Most assessments of risk in nuclear arms control rely on intuitive and experiential methods, which can produce highly variable results, especially given that arms-control initiatives are intentionally competitive or even confrontational (and not purely cooperative), and different actors may have widely different perceptions of risk. Here we explore the application of formal risk tools to arms-control issues, looking at how arms-control risk assessments related to HBGVs or other advanced weapons could have a positive impact on future negotiations and treaties, reducing the likelihood and consequences of war, especially nuclear war.
Analyzing risk
Risk is generally understood to encompass both likelihood and harm. An outcome that is guaranteed to occur may not be considered risky even if it is undesirable, while a prospect with uncertain outcomes may not be viewed as risky if all outcomes are favorable (e.g., a lottery in which the only uncertainty is the size of a prize). More specifically, “risk” is often defined (National Research Council, 2010) as a function of threat (potentially adverse event), vulnerability (the chance that the event results in harm), and consequence (the extent or nature of the harm).
Formal risk assessments are widely used and have advanced significantly over the last several decades. Industries vulnerable to major hazards, such as nuclear power, frequently rely on quantitative risk assessments. Many risk-assessment methodologies exist, each with their own advantages and disadvantages. Modern risk-assessment methods, typically applied quantitatively to engineered systems (e.g., nuclear reactors or aerospace applications), might also be used to support attempts to achieve useful nuclear arms-control agreements.
There are large differences between engineered and non-engineered systems, especially in their levels of complexity and uncertainty. Non-engineered systems involving complex human behaviors often include intangible interactions and feedback mechanisms that may not lend themselves to probabilistic analysis. So, risk assessments of non-engineered systems typically rely heavily on intuition. However, this may not completely negate the utility of a structured, formal approach to risk assessment in the arms control arena. Like the intuitive approaches currently used in nuclear arms control, formal methods can also reflect objective conditions, support declared goals, and provide agility in adapting to new information or changed circumstances. Both approaches can in principle address the core issue in all risk-management challenges (namely, to support good decision making in the face of uncertainties), and both can be shaped by the norms and values (and biases) of their users. The strengths and weaknesses of each approach must therefore be considered.
While some believe that quantitative risk assessment is both feasible and useful for nuclear arms control even in its simplest form, others believe that such applications are either impossible or wrong (Hellman and Cerf, 2021). Internet pioneer and Turing Award winner Vinton Cerf argues (along with Hellman) that quantification is not necessary to understand that the consequences of nuclear war are unacceptable, and that urgent actions to reduce the likelihood should therefore be taken without waiting for the results of quantitative analysis. Advocates for intuitive risk assessments point out that living beings evolved their instincts to survive risks, and that this should be recognized and respected.
Critics of such intuitive approaches, however, note that intuition can also lead people astray. Numerous studies in psychology and behavioral economics have demonstrated the effects of phenomena such as recency bias and even how risks are presented (e.g., verbally or graphically) on intuitions (Gonzalez and Wallsten, 1992; Solomon, 2022). Likewise, intuitive evaluations of risk tend to overestimate the probability of extremely rare events (prospect theory; Kahneman and Tversky, 1979), while the “boiling frog” analogy suggests that the opposite can also occur—namely, that slow increases in risk may not create the level of alarm needed to inspire protective action. Finally, in the context of nuclear arms control, if adversaries have differing or even incommensurate intuitive narratives about risk, this can result in protracted or even unresolvable conflicts or stalemates in negotiations.
These challenges have inspired the authors of this paper to explore the possible benefits of probabilistic risk assessment (Bier, 1997; Cox and Bier, 2017) in arms control, given that the use of quantitative methods has helped to identify the most serious causes of risk and the most effective risk-reduction actions in a wide variety of fields. Risk assessments of engineered systems typically involve a set of possible “scenarios,” whose consequences and likelihood can each be analyzed. The value of such methods lies not only in the quantitative or numerical results, but also in the ability of these methods to identify the range of possible scenarios, structure or group those scenarios in a tractable manner, facilitate an understanding of newly identified risks or new technologies, and ensure a reasonable degree of completeness. This systematic approach may therefore also be useful in non-engineered, policy-oriented risk assessment, as in arms-control or other negotiations.
Application of abstract concepts to complex human-related matters, however, doesn’t always prove practical. While early applications of game theory to nuclear deterrence in the late 1960s fed expectations that it could be applied to arms control, Schelling (1966) and Harsanyi (1967) and others achieved only limited success in applying game theory, due to human diversity and the complexity of arms-control issues. Risk-analysis results can also be difficult for decision-makers to interpret. Therefore, persuading potential decision makers or arms-control negotiators of the utility of using formal risk-assessment methods would benefit from a compelling “existence proof,” which does not appear to exist currently. We speculate that HBGVs (which are rapidly growing in importance as an issue in nuclear arms control) might provide a useful case study to analyze using formal risk-assessment methods as the basis for such a proof.
HBGVs as an example
Currently, hypersonic boost-glide vehicles are primarily used in regional weapons systems rather than global strategic systems, but some intercontinental systems have already been deployed. Moreover, even regional dynamics can affect global strategy, especially in escalation scenarios (where an initially regional conflict becomes broader). Furthermore, the need to defend against regional HBGVs could result in missile-defense advances that threaten traditional strategic systems. Some HBGV developments could also have qualitative capabilities (e.g., against early warning, defense, and/or communications systems) that could be either advantageous or destabilizing, both regionally and globally.
Perhaps the key feature of HBGVs is that they are more maneuverable than traditional intercontinental ballistic missiles. Russia, China, North Korea, the United States, and other nations have different priorities for HBGVs, but together they encompass nuclear, conventional, and unarmed payloads on intercontinental, intermediate, and short-range delivery systems. As of early 2024, the only nuclear arms-control treaty that would limit any of these systems is New START, but that applies only if a nuclear warhead is placed on the systems that are already considered accountable under the treaty, or that would be accountable if treated as treaty-defined ballistic or cruise missiles. Some intercontinental delivery systems would not be considered treaty-accountable (for example, if they did not follow a ballistic trajectory over at least half their range, or were not self-propelled and aerodynamic over at least half their range). Views differ on how these hypersonic systems might impact nuclear stability and whether they need to be addressed in arms control. In the short term, intercontinental hypersonic weapons would be limited in number, but intermediate and shorter-range conventional (non-nuclear) systems may see wider deployment in regional conflicts.
Scenario structuring in risk assessment
Any risk assessment is likely to be scenario-based, so the first step in the HBGV case involves delineating the specific scenarios to be studied. The level of detail of the scenarios can be tailored to support the decisions to be made based on an analysis. Recognizing the need to address both uncertainty and consequences (e.g., in a nuclear exchange or in a negotiation), risk assessment generally focuses on three key questions (Kaplan and Garrick, 1981):
- What can go wrong?
- What is the likelihood of each possible scenario?
- What are the consequences?
Tools are available to help in scenario structuring. These include hazard and operability studies (Kletz, 1999; see International Electrotechnical Commission, 2016); hierarchical holographic modeling (Haimes, 1981); and the theory of scenario structuring (Kaplan et al., 2001). While any risk-assessment methodology has limitations and disadvantages, scenario structuring provides greater clarity than many other assessment methods. For example, even without quantifying the probabilities of the events in a fault tree or event tree, the effort of constructing the tree can highlight events that could otherwise be overlooked or underestimated. The thought process can help identify relationships among events (e.g., how the occurrence of one event or condition can influence the probabilities of subsequent events).
Hypothetical risk assessment of nuclear-armed hypersonic weapons
There is at least one significant advantage of quantitative methods such as those described above: They make explicit the scenarios that can lead to favorable or unfavorable outcomes. This approach is complementary to traditional approaches to arms-control analysis (which tend to be more narrative-based). In other words, the use of quantitative risk assessment is not intended to be a principal basis for decisions, or to replace the knowledge and understanding of key decision makers, negotiators, etc. But traditional approaches may provide little basis for resolution of differences if two groups have different intuitive perceptions of risk (e.g., about the likelihood that nuclear weapons will be used in a given conflict). By contrast, if two scenario-based risk assessments come to different conclusions about risk, that paves the way for a discussion about the reasons. Do they make different assumptions, or rely on different data? Does one omit some scenarios that play a role in the other?
HBGVs are not the only problem that would merit analysis using quantitative scenario-based methods, or the most important such problem, or even uniquely suited to the application of these methods. What we present here merely illustrates how the methods could be applied to a significant problem.
Fault tree for nuclear-armed hypersonic weapons
Some methods of risk assessment are particularly appropriate for analyzing the likelihood of rare events (Bier et al., 1999) for which little, if any, empirical data are available, since the undesired event for which data are sparse or unavailable (e.g., nuclear war) can be decomposed into constituent events whose likelihoods may be easier to estimate. For example, fault trees and event trees are frequently used to model the risks of nuclear-power plants, using inductive or “top-down” logic (beginning with a hypothesized failure or undesired event, and working backward to identify which combinations of events might give rise to that event), and deductive or “bottom-up” logic (beginning by hypothesizing an initiating event , and working forward in time to identify all possible combinations of subsequent events that could lead to an undesirable outcome). A decision tree can be thought of as a variant of an event tree that includes decision options, each of which can lead to one or more possible outcomes, often quantified by probabilities.
A simple hypothetical fault tree is shown in Figure 1 for use of nuclear-armed hypersonic weapons in a situation prior to a nuclear war.

Vicki Bier is professor emerita in the Department of Industrial and Systems Engineering and Department of Engineering Physics at University of... Read More
Robert J. Budnitz
Robert J. Budnitz has long been involved with nuclear-reactor safety and radioactive-waste safety. He is a member of the National Academy of... Read More
Olli Heinonen
Olli Heinonen is a distinguished fellow at the Stimson Center, Washington DC. Before that he was a senior fellow from 2010 at the Harvard Kennedy... Read More
Richard C. Lanza
Richard C. Lanza is a senior research scientist in the Department of Nuclear Science and Engineering at MIT. His work over more than 40 years at MIT... Read More
Ronald F. Lehman
Amb. Ronald F. Lehman works at Lawrence Livermore National Laboratory, chairs the Governing Board of the International Science and Technology Center,... Read More
Sally Leivesley
Sally Leivesley, managing director at Newrisk Limited (www.newrisk.com) is an independent adviser and international media commentator on... Read More
Charles F. McMillan
Charles F. McMillan was the 10th director of Los Alamos National Laboratory from 2011 to 2017, contributing significantly to the Department of... Read More
George H. Miller
George H. Miller, a physicist, was the 10th Director of Lawrence Livermore National Laboratory, a position he assumed in March 2006. After a long and... Read More
Anita Nilsson
Anita Nilsson served at the International Atomic Energy Agency as Senior Coordinator for Safeguards and Director for Nuclear Security until 2011,... Read More
John Organek
Professional Engineer John Organek is a retired US Army Corps of Engineers Officer now serving as Director of Operational Architecture and Water... Read More
Robert N. Schock
Robert N. Schock retired from the Lawrence Livermore National Laboratory after over 50 years of service there, associate director for advanced energy... Read More
Receive Email Updates
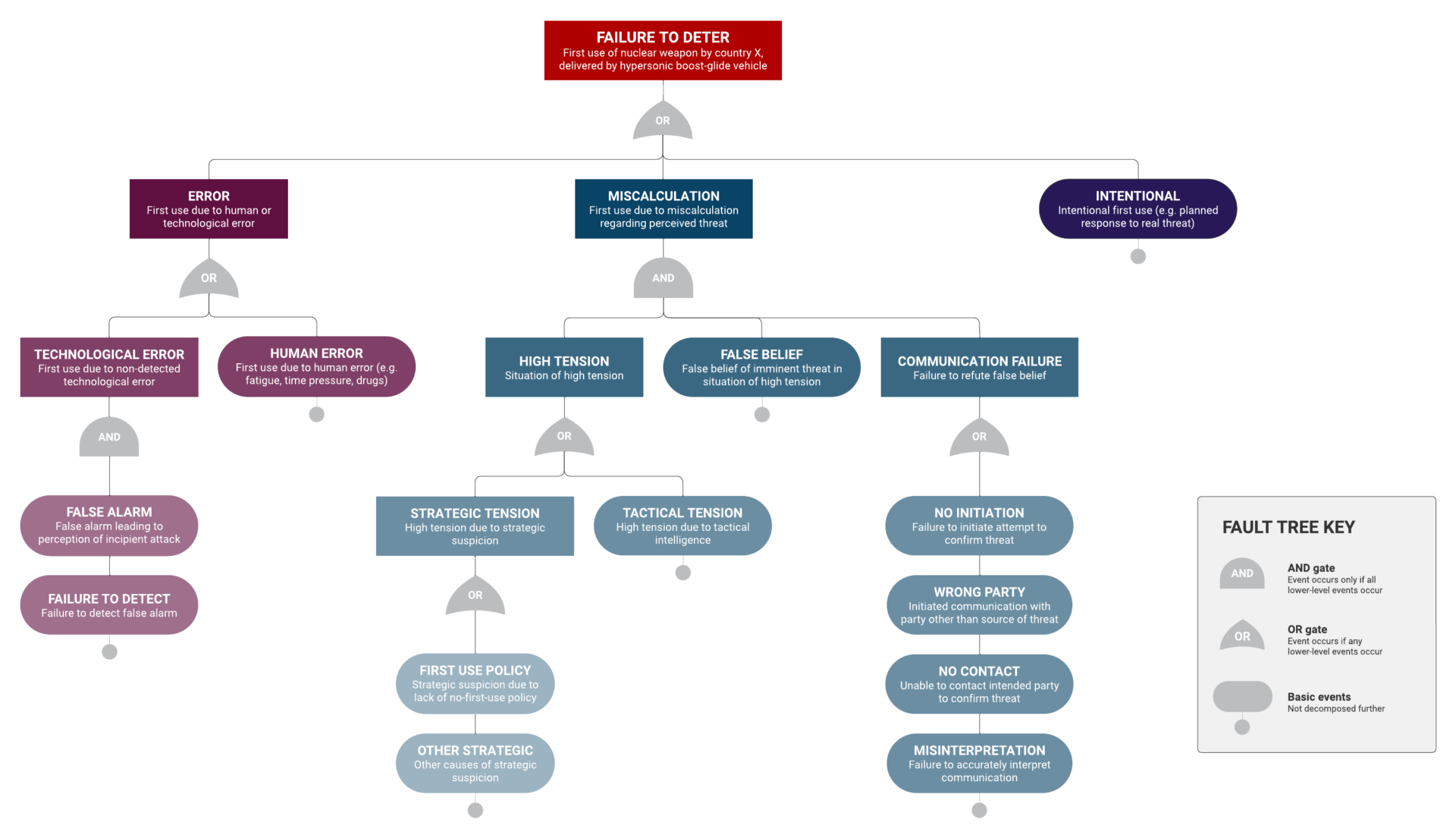
This fault tree is incomplete (a realistic fault tree for this problem would have many more branches), and we do not claim that it is definitive or accurate. (Another team might draw a significantly different tree with other event descriptions.) However, a concrete example makes the advantages and disadvantages of using risk assessment methods clearer and easier to understand.
To illustrate the interpretation of this tree, the top level of the tree (an OR gate) postulates three ways by which use of nuclear-armed HBGVs could arise: human or technological error; or deliberate use based on a miscalculation of the perceived threat; or intentional use in response to an actual threat. Here, the difference between error and miscalculation is essentially whether the nature of the event would be evident to an informed observer almost immediately (error), versus only in retrospect, with additional background or context (miscalculation). Each of these paths is then further decomposed into its contributing factors. For example, “error” could be either human error, or technological error. Technological errors in turn (as modeled using an AND gate) are shown as requiring both a false alarm and failure to detect that the alarm is false. Human error could, if desired, be further subdivided into various possible causes (fatigue, time pressure, drug or alcohol use, mental illness, etc.). However, that level of detail is suppressed here. Similarly, “miscalculation” is here modeled as requiring a situation of high tension (which could arise due to either strategic or tactical considerations), and a false belief that there was an imminent threat, and failure to refute that false belief (e.g., due to lack of communication). Finally, intentional use of nuclear-armed HBGVs could in turn be subdivided into various possible reasons for such use—for example, because of pressure to act (“use-it-or-lose-it”) or intentional escalation of a conventional (non-nuclear) conflict.
Note that the methods used for assigning numerical values to the various events in the fault tree (and the uncertainties about those values) may differ. For example, some could perhaps be estimated based on historical data (such as failure of detection), while others could be estimated only judgmentally (e.g., the likelihood that foreign governments have a false belief). However, using the subjectivist theory of probability, both could be estimated quantitatively (at least in principle).
If the probabilities of some events in the fault tree seem too difficult to estimate accurately, some could perhaps be ranked on a purely ordinal basis—that is to say, rating some as more likely than others. Even this process can make critical assumptions explicit and facilitate discussion and debate if differences of opinion emerge. For example, some analysts might argue that the availability of nuclear-armed hypersonic weapons would improve survivability of a country’s nuclear capability, thereby reducing the probability of preemptive attack in situations of high tension. Conversely, others might argue that the availability of nuclear-armed hypersonic weapons would make nuclear use more likely—for example, because of the greater maneuverability of such weapons (compared to intercontinental ballistic missiles), or if the use of non-nuclear hypersonic weapons on the battlefield reduces the psychological barriers to use of nuclear hypersonic weapons. Although use of risk-analysis models might not provide immediate answers to key questions, even this simple hypothetical fault tree shows that it can highlight those questions, help to differentiate among similar scenarios, encourage analysts to make their assumptions explicit, and help to identify areas of disagreement or need for further information.
Risk assessment: advantages and disadvantages
One advantage of risk assessment is obvious: The mere act of scenario-structuring can provide clarity. For example, even without quantifying the probabilities of the events in a fault tree or an event tree, the effort of constructing the tree can highlight events that had been previously overlooked or underestimated. Likewise, the thought process can help to identify relationships among events (for example, the key role of situations of high tension in miscalculations, in the hypothetical fault tree above). And for some applications, a full and complete risk assessment may not be needed; rather, the use of risk assessment “tools” to perform a partial analysis might be sufficient.
In a wide variety of fields, risk assessment is used as a basis for improved risk-reduction decisions. Even without well-defined robability estimates, scenarios afford the opportunity to rank-order risks. After the most important risks have been identified (based on likelihood, severity, or some combination of both), the risk assessment also supports identifying which aspects or elements of the scenario(s) are most important. After these dominant contributors have been identified, one can then review the various details involved in those scenarios to identify opportunities for risk reduction (for example, methods to improve communication between potential arms-control adversaries, or more reliable ways to detect threats).
In cases where risk reductions cannot be achieved unilaterally, risk assessment information would also allow negotiators to focus on mitigating or managing the highest-order risks, while possibly paying less attention to scenarios that (while theoretically possible) may not be important contributors to the overall level of risk. These types of insights, although relying on quantitative analyses, can often be summarized qualitatively, making the results more broadly accessible. Consequently, risk assessments provide a relatively reproducible method that can help to define leadership decision pathways, giving negotiators a range of options and illustrating ways to assess their outcomes. In addition to informing arms-control negotiators and their staff about the most important risks, risk assessments can also provide a communication platform for negotiators. For example, risk assessments could help both arms-control negotiators and their staffs to understand how best to represent the threats they perceive, or how particular measures might increase or decrease the likelihood of particular events in the risk assessment.
Alternatively, risk assessments could be used as input to further analysis. For example, risk assessment could estimate the likelihood of particular outcomes or actions in a game-theoretic analysis of competition or cooperation between nations or could help prioritize the most important uncertainties for future research or intelligence-gathering. To achieve these goals, it is important to keep risk assessments up to date as circumstances change, as so-called “living risk assessments” (Goble and Bier, 2013), “running estimates” in the military context (US Army, 2019), or simply ongoing situation assessment. Risk assessments may need to be updated for reasons ranging from the advent of novel technologies, to a change in leadership in an adversary nation, to transitory changes in circumstances (such as local skirmishes). The importance of maintaining a living risk assessment may be even greater in the context of arms-control negotiations than in other domains, since different parties may have changing understandings of the risks over time, and a once-agreed-to risk assessment may come to be viewed as obsolete over time.
There are, of course, also potential disadvantages of risk assessment. First, the logic and assumptions behind an engineering-style analysis may not always be straightforward and easily understood, especially for subject-matter experts who may be knowledgeable about the problem at hand but not familiar with risk methods. For example, in the hypothetical fault tree, assumptions about adversary actions appear in multiple parts of the fault tree (under both intentional use and miscalculation). It is arguable that greater understanding might result from putting actions and behavior by a particular group of nations into a single framework rather than having them scattered throughout the tree. In principle, however, these different types of analysis (e.g., engineering-style risk methods along with more traditional narrative methods) could perhaps be used in tandem, as in so-called “plural analysis” (Brown and Lindley, 1986).
Risk assessment can also lead to mistaken interpretations in the face of well-known decision maker biases. For example, in a phenomenon known as “probability neglect” (Sunstein, 2002), either extremely small probabilities can be overweighted (Kahneman and Tversky, 1979), or such low-probability events can be neglected as essentially impossible. People are also often insensitive to the magnitude of a bad outcome—for example, 1,000 deaths may be viewed as almost as bad as 100,000 deaths (Slovic et al., 2013, on “psychic numbing”). Moreover, risk assessments themselves can have biases. This problem is perhaps more extreme for open systems such as arms control, where most actions involve highly uncertain human behavior, and probabilities cannot be easily estimated based on past failure data or component testing.
In addition, especially on arms-control issues, the scenario approach to risk assessment can generate enormous numbers of possible pathways. Overly numerous or detailed scenarios can generate detailed insights, but could also distract from recognizing important overarching qualitative aspects of the problem. Such elaborate analyses can also be difficult to use as a basis for decisions in real time (as in a crisis situation, or while actively engaged in arms-control negotiations), suggesting that such analyses are perhaps better done offline, far in advance of when the resulting insights or recommendations are likely to be needed. They can then be boiled down to higher-level and less-complex risk assessments that are easier for decision makers to digest and use.
Another concern is that a decision maker might take the results or insights from a risk assessment more seriously than is merited (for example, if other sources of information and expertise, such as the insights from area studies, are not adequately considered in the risk assessment). It is well-known that risk assessments can cause people to fixate on the parts of the analysis that can be easily quantified (e.g., the probability of false alarms) rather than parts that are difficult to quantify (Brown, 2002), and to focus on the scenarios that are shown in the analysis rather than on those that were inadvertently omitted (Fischhoff et al., 1978). This is problematic in analyzing systems that are highly complex or open-ended, as with “non-engineered” systems where human actions play a key role, in which even a reasonably complete enumeration of important scenarios may be impractical or difficult to achieve (Perrow, 1984). For this reason, in situations of great complexity, Leveson (2012) argues against attempting to apply probabilistic risk assessment, and instead recommends both eliminating risks where possible and reducing complexity (making risks clearer and easier to understand and mitigate).
Care must also be taken if the risk assessment (e.g., fault tree) is shared with the adversary in arms-control negotiations, to ensure that important information or assumptions are not inadvertently revealed. In addition, the use of risk assessment could paradoxically serve to derail negotiation instead of supporting it. For example, disagreements about minor aspects of the risk assessment could distract attention from overarching goals, or could be deliberately exploited to delay negotiations.
Despite these potential shortcomings, including possible oversimplification or even misuse of results, the potential benefits of risk assessment justify attempting to develop and apply it to support the broader objective of advancing international security and, where useful, achieving arms-control agreements. It is also important to recognize that methods exist for mitigating some of the pitfalls just mentioned. For example, formal methods of scenario identification and structuring (e.g., Kaplan and Garrick, 1981; Kaplan et al., 2001) can reduce problems of incompleteness; plural analysis (Brown and Lindley, 1986) can ensure sufficient attention to scenarios that are difficult to quantify; formal methods of expert elicitation can improve the calibration of probability estimates, and reduce the pitfalls of groupthink (Janis, 1982); and precursor analysis can use data on “near misses” or other undesired events to help inform risk assessments. There is literature on how best to communicate risk results (including uncertainties) to decision-makers, potentially mitigating difficulties such as probability neglect (Bier, 2001; Solomon, 2022).
A path forward could include a risk assessment test case for nuclear arms control
There may be considerable value in undertaking detailed risk assessment of the issues related to nuclear arms control for two key reasons. First, the structural formality of these methods provides a way to make explicit the often-implicit assumptions of interlocutors. Second, risk methods provide a pre-analyzed framework into which new information can be integrated as it becomes available, and that framework can be useful in getting multiple team members (or even adversaries) thinking along consistent lines. Without arguing for replacing the more qualitative types of analyses that have been done or for basing decisions primarily on risk assessment, we do believe that structured, engineering-style risk assessments would complement the qualitative types of analyses that have been done in the past, yielding ways of viewing the problem that can supplement and inform the more intuitive understanding of decision makers. Under some circumstances, risk assessment could even be used in near real time (for example, to support arms-control negotiators), despite the complexities of a scenario-based approach. Once a detailed analysis has been completed, the results could be simplified or condensed in a manner that would make them useful and usable in such situations.
The hypothetical fault-tree analysis of HBGVs presented here is intended only to illustrate these potential benefits, falling short of the type of compelling “existence proof” that might persuade potential decision-makers or arms-control negotiators of the utility of a formal risk-assessment process. In addition to fault trees and event trees, numerous additional methods of risk assessment, both qualitative and quantitative, could be explored (and some have already been applied to problems of nuclear-arms control). Examples are pathway analysis, war gaming, red teaming, game theory, agent-based modeling, exchange analysis, stability analysis, and network analysis. The strengths and weaknesses of many of these are discussed in Risk Analysis Methods for Nuclear War and Nuclear Terrorism (National Academies of Sciences, Engineering, and Medicine 2023, ch. 6). All are ways of modeling or understanding the relationships between two or more nations or organizations. Causal methods recently applied in the fields of statistics and economics could also be beneficial in arms control—for example, by providing automated methods of compliance verification. Chaos theory and other methods of understanding complex systems could help to understand whether a given security or arms-control regime contributes to stability in arms-race dynamics.
A desirable step forward would be for one or more organizations (either governmental or non-governmental) to select a specific issue or problem (such as the impact of HBGVs on arms control) and sponsor a project to explore the applicability of risk-assessment methods and develop the sort of risk assessment suggested here. Such an analysis would be resource-intensive and take considerable time to develop and would perhaps best be done by a dedicated group of analysts, working closely with (or at least informed by) decision makers or past arms-control negotiators. Given recent and ongoing geopolitical changes at a level not seen in many decades, it may be time to apply modern techniques of risk assessment to nuclear arms control to identify new ideas, improve understanding, and provide useful insights–increasing the security of all parties to negotiations. (The advance of “big data” and artificial intelligence/machine learning may also help to support the types of analyses suggested here.) Such a study could serve not only as an “existence proof” of the efficacy of the approach (if successfully demonstrated), but also as a way to ensure that end-users (for example, arms-control policymakers and negotiators) are aware of the types of insights that could be provided by this type of analysis.
The authors would like to gratefully acknowledge Siegfried Hecker, who provided valuable insights into benefits and communication of risk analyses, and to Gorgiana Alonzo for her editorial intelligence, which improved thought communication. In addition, William Barletta provided numerous suggestions on professionals to interact with in this field.
References
- Bier, V.M. (1997) “An overview of probabilistic risk analysis for complex engineered systems,” Fundamentals of Risk Analysis and Risk Management (V. Molak, editor), Boca Raton, FL: Lewis Publishers.
- Bier, V. M., Y. Y. Haimes, J. H. Lambert, N. C. Matalas, and R. Zimmerman, (1999) “Assessing and Managing the Risk of Extremes,” Risk Analysis , Vol. 19, pp. 83-94.
- Bier, V. M., (2001) “On the State of the Art: Risk Communication to Decision-Makers,” Reliability Engineering and System Safety , Vol. 71, pp. 151-157.
- Brown, R.V., (2002) “Environmental regulation: Developments in setting requirements and verifying compliance.” Systems Engineering and Management for Sustainable Development (A.P. Sage, editor).
- Brown, R.V., and D.V. Lindley, (1986) “Plural analysis: Multiple approaches to quantitative research,” Theory and Decision Volume 20, pages 133-154.
- Cox, L.A., and V.M. Bier, (2017) “Probabilistic Risk Analysis,” Risk in Extreme Environments: Preparing, Avoiding, Mitigating, and Managing (V. M. Bier, editor), Routledge, pp. 9-32.
- Fischhoff, B., P. Slovic, and S. Lichtenstein, (1978) “Fault Trees: Sensitivity of Estimated Failure Probabilities to Problem Representation,” Journal of Experimental Psychology: Human Perception and Performance Vol. 4, No. 2, 330-344.
- Goble, R., and V.M. Bier, (2013) “Risk Assessment Can Be a Game-Changing Information Technology—But Too Often It Isn’t,” Risk Analysis , Vol. 33, pp. 1942-1951.
- Gonzalez C.C., and T.S. Wallsten, (1992) “The effects of communication mode on preference reversal and decision quality,” Journal of Experimental Psychology: Learning, Memory, and Cognition ;18:855±64.
- Haimes, Y.Y., (1981), Hierarchical holographic modeling, IEEE Transactions on Systems, Man, and Cybernetics 11 (9): 606-617
- Harsanyi, John, (1967). “A Game-theoretical Analysis of Arms Control and Disarmament Problems.” In Development of Utility Theory for Arms Control and Disarmament: Models of Gradual Reduction of Arms. Report to Arms Control and Disarmament Agency. Contract no. ACDA/ST-116. Princeton: Mathematica.
- Hellman, M.E., and V.G. Cerf, (2021) “An existential discussion: What is the probability of nuclear war?” Bulletin of the Atomic Scientists , March 18. Available at: https://thebulletin.org/2021/03/an-existential-discussion-what-is-the-probabilityof-nuclear-war/ .
- International Electrotechnical Commission (IEC), (2016) Hazard and operability studies (HAZOP studies) - Application guide , IEC 61882.
- Janis, Irving L., (1982) Groupthink: Psychological Studies of Policy Decisions and Fiascoes , Cengage Learning.
- Kahneman, D., and A. Tversky, (1979) “Prospect Theory: An Analysis of Decision under Risk,” Econometrica Vol. 47, No. 2, pp. 263-292.
- Kaplan, S., and B.J. Garrick, (1981) “On the quantitative definition of risk,” Risk Analysis , 1 (1): 11-27
- Kaplan, S., Y.Y. Haimes, and B.J. Garrick, (2001) “Fitting hierarchical holographic modeling into the theory of scenario structuring and a resulting refinement of the quantitative definition of risk,” Risk Analysis , 21 (5): 807-815.
- Kletz, T. (1999) Hazop and Hazan. Identifying and Assessing Process Industry Hazard s (4th ed.). Rugby: IChemE . ISBN 978-0-85295-506-2 .
- Leveson, N., (2012) Engineering a Safer World: Applying Systems Thinking to Safety, MIT Press,
- National Academies of Sciences, Engineering, and Medicine. (2023) Risk Analysis Methods for Nuclear War and Nuclear Terrorism . Washington, DC: The National Academies Press.
- National Research Council. (2010) Review of the Department of Homeland Security's Approach to Risk Analysis. Washington, DC: The National Academies Press.
- Perrow, Charles. (1984) Normal Accidents: Living with High-Risk Technologies New York: Basic Books.
- Schelling, Thomas C., (1966) Arms and Influence , Yale University Press.
- Slovic, P., D. Zionts, A.K. Woods, R. Goodman, and D. Jinks, (2013) “Psychic Numbing and Mass Atrocity,” In E. Shafir (Ed.), The behavioral foundations of public policy (pp. 126–142). NJ: Princeton University Press.
- Solomon, JD, (2022) Communicating Reliability, Risk & Resiliency to Decision Makers: How To Get Your Boss's Boss To Understand , , JD Solomon, Inc.
- Sunstein, C.R. (2002) “Probability neglect: Emotions, worst cases, and law,” Yale Law Journal 112(1), 61-107.
- U.S. Army, (2019) Army Doctrine Publication 3-0, Operations , Army Publishing Directorate.
Keywords: HBGV , arms control , hypersonic boost-glide vehicle , hypersonic glide vehicles , hypersonic weapons , nuclear arms control , nuclear risk reduction , risk assessment Topics: Nuclear Risk , Nuclear Weapons
Bulletin Daily

By Vicki Bier , Robert J. Budnitz , Olli Heinonen , Richard C. Lanza , Ronald F. Lehman , Sally Leivesley , Charles F. McMillan , George H. Miller , Anita Nilsson , John Organek , Robert N. Schock | Nuclear Risk , Nuclear Weapons
How one Oregon county plans to make big oil pay for the 2021 heat dome
By Jeffrey B. Simon | Climate Change

France wants to extend its nuclear umbrella to Europe. But is Macron ready to trade Paris for Helsinki?
By Carine Guerout , Jason Moyer | Nuclear Weapons , Opinion

Israel to perform at Eurovision. Expect protests, machine guns, and drones
By Erik English | Analysis

May issue: The future of food in a time of climate change
By Dan Drollette Jr | Climate Change , Special Topics

Ukrainian journalist Illia Ponomarenko on the horror and absurdity of Russia’s senseless, existential war
By Susan D’Agostino | Analysis , Book Review , Nuclear Risk

What India’s MIRV test adds to the ‘strategic trilemma’ in South Asia
By Huma Rehman | Nuclear Weapons

Trump says he’d disband the pandemic preparedness office—again
By Erik English | Biosecurity
Copenhagen Center for Disaster Research
- Student experience in ...
Student experience in the Vulnerability and Risk Assessment Methods course, Chennai 2024
- Public health
Supported and guided by community facilitators, Tamil interpreters, and our course instructors, we set out in two research teams to employ various investigative methods—such as semi-structured interviews, seasonal calendars, and transect walks—to closely examine both the physical environment of the resettlement area and the multidimensional experiences of its inhabitants. Over the week in the field, we engaged more than 70 participants in Perumbakkam through a range of EVCA tools. Talking to a tailor, a fish seller, and a group of neighbours each brought insight into how debt is accumulated with disasters, how heat affects living wages, and how floods affect children’s safety, respectively.

As part of the Master of Disaster Management programme, this year’s Vulnerability and Risk Assessment Methods (VRAM) elective was hosted in Chennai, Tamil Nadu, India in partnership with the Indian Institute of Technology Madras (IITM) School of Sustainability and Okapi Research and Advisory .
The course consisted of a week of theory-based lectures, a week of fieldwork, and a week of organisational visits to area disaster risk reduction (DRR) stakeholders and experts. For the fieldwork component, students utilised methods from the IFRC Enhanced Vulnerability and Capacity Assessment (EVCA) toolkit to analyse flood and heat-related disaster risk in Perumbakkam, a resettlement colony on the outskirts of Chennai, with guidance from COPE Director Emmanuel Raju and PhD Fellow Suchismita Goswami. The course was also situated within the DFF funded project on Disaster Risk Creation in Urban Resettlement Processes which is led by Assoc. Prof. Emmanuel Raju.
In this year’s VRAM cohort, we were six students from all different professional backgrounds ranging across insurance, security, medicine, meteorology, refugee support services, and INGO administration. The course offered a possibility to put theory into practice but also presented an opportunity to learn through interdisciplinary teamwork. Several months prior to our arrival in Chennai, India, the area had experienced a major flooding event in December 2023 following the passage of Cyclone Michaung . Flooding and waterlogging pose a persistent disaster risk for the city, whose vulnerability is shaped by a multitude of factors , including coastal hazards, colonial history, rapid urbanisation, and poor water management. As part and parcel of local flood risk reduction strategy, there have been government efforts to relocate informal settlements from along Chennai’s waterways into “resettlement colonies” around the city and its periphery. These en-masse evictions of urban poor communities are conducted with the expressed intention to shield people from disasters and rehabilitate water bodies. However this resettlement narrative, which emphasises the safety offered by the towering concrete apartment buildings of the colonies, functionally serves to expropriate waterfront land for high-income real estate development and overlooks vital social and human elements critical to the wellbeing of resettled populations, including access to jobs, education, and social infrastructure.

Roughly 25 km south of the city centre, the resettlement colony of Perumbakkam was especially impacted by the 2023 floods and subsequent waterlogging. It is additionally vulnerable to a range of other hazards disrupting infrastructure and daily life, as well as presenting serious health and safety risks. Among these, we chose to focus on both flood risk and heatwave risk in our VCA, the latter being a hazard that is critically understudied outside of high-income countries and projected to be severe in Chennai due to the city’s overstretched water resources and high humidity. The intense heat of Chennai's summers already puts a significant strain on water and electricity infrastructure, a challenge played down by a common refrain we heard repeated by many throughout our three weeks of the course: “Chennai has three seasons— hot, hotter, hottest.” Grasping the full scope of disaster risks in Chennai’s resettlement colonies necessitates a deep dive into the vulnerabilities and capacities of these communities, which we endeavoured to achieve during the three weeks of the VRAM elective. This involved employing EVCA tools to identify underlying issues, foster community engagement, and collect primary data on how Perumbakkam’s residents perceive and want to manage their own risks as an evidence base to inform future DRR measures and policies. Supported and guided by community facilitators, Tamil interpreters, and our course instructors, we set out in two research teams to employ various investigative methods—such as semi-structured interviews, seasonal calendars, and transect walks—to closely examine both the physical environment of the resettlement area and the multidimensional experiences of its inhabitants. Over the week in the field, we engaged more than 70 participants in Perumbakkam through a range of EVCA tools. Talking to a tailor, a fish seller, and a group of neighbours each brought insight into how debt is accumulated with disasters, how heat affects living wages, and how floods affect children’s safety, respectively. Here are some other key themes that emerged through our fieldwork as areas for exploration through future research:
- While the state disaster management plan for heat is still under development, area health centres and NGOs are observing trends in health problems among Perumbakkam’s population during the hot season. Area healthcare providers reported an increased prevalence of sleep problems, chickenpox, skin rashes, and dehydration during the hot season and highlighted pregnant/lactating mothers and their infants as an especially vulnerable group. A domestic workers’ focus group emphasised that extreme heat exacerbates menstrual hygiene challenges that workers routinely face due lack of access to adequate WASH facilities at their workplace and on long public transit commutes to work. Despite the clear impact of heat on health and livelihoods uncovered using the EVCA tools, the assessment found a low level of heat awareness among the population.
- Flooding and waterlogging in the wake of cyclones occurs during a seasonal pattern of reduced incomes for Perumbakkam’s residents, amplifying the financial impact of disaster events in the rainy season. Many residents take high-interest (15-25%) loans from unlicensed moneylenders throughout the year for routine household expenses, especially between October and January due to reduced employment opportunities in the wet season. Additional loans taken out for flood recovery thus heighten the risk of entrapment in a cycle of borrowing to pay off other debts, where residents’ earnings are increasingly spent on interest and loan repayments rather than basic needs.
- Social cohesion and strength of social networks played a substantial role in determining whether a resident interviewed for the project had received the early warning for the December 2023 floods and whether their apartment block association had organised relief or response efforts. Many residents described their sense of community and social relationships being upended in the process of resettlement, with implications for the reach of early warning systems and efficacy of disaster response coordination in Perumbakkam.
- In an environment where many residents have experienced one or more waves of forced displacement as a result of government responses to disasters (including the 2004 Indian Ocean tsunami and 2015 floods), VCA tools should be implemented with sensitivity to how core DRR concepts and frameworks can over-emphasise “community” identity and resources . Many in Perumbakkam were eager to talk about macro-scale issues related to structural violence and discrimination, while the primary goal and framing of the VCA are micro-scale, “community”-level vulnerabilities and capacities. Both were important to capture in the scope of the assessment.
This type of community-based knowledge, acquired through qualitative interviews, focus groups, and other VCA tools, is far from something we could have otherwise learned through a literature review and is crucial for our future work in the sector. The opportunity to delve into these nuances through participatory risk assessment methods makes the VRAM course a particularly rewarding elective to consider within the MDMa curriculum.

Committee for Risk Assessment
- Members of the RAC
- Members of the RAC Drinking Water Working Group
The Committee for Risk Assessment (RAC) prepares the opinions of ECHA related to the risks of substances to human health and the environment in the following REACH and CLP processes. The final decisions are taken by the European Commission.
Harmonised Classification and Labelling
RAC examines the proposals for harmonised classification and labelling and gives an opinion on the proposed harmonised classification of substances as carcinogenic, mutagenic, toxic for reproduction or as a respiratory sensitiser, as well as other effects on a case-by-case basis.
Restriction
The Committee evaluates whether the proposed restriction on manufacture, placing on the market or use of a substance is appropriate in reducing the risk to human health and the environment. This includes the assessment of comments submitted by third parties.
Authorisation
RAC assesses the risk of a substance arising from the uses of a substance when an application for authorisation is submitted. This includes an assessment of the appropriateness and effectiveness of the risk management measures as described in the authorisation application, and if relevant, of the risks of possible alternatives. Third party contributions linked to the application will also be assessed.
Occupational Exposure Limits (OELs)
The Committee supports the European Commission by giving scientific opinions on occupational exposure limits. It has taken over this responsibility from the Commission’s Scientific Committee on Occupational Exposure Limits (SCOEL).
Drinking Water
Starting in 2026, the Committee will evaluate the safety of certain substances used in materials that come into contact with drinking water. When an application is made to ECHA to use these substances in the manufacture of such materials, RAC will assess their potential risks. RAC’s evaluation will include how these substances are used, their potential to transfer into the drinking water, and their toxicological properties. Additionally, any comments by third parties on the application will be considered.
ECHA's Executive Director's requests
RAC gives an opinion on request from the Executive Director of ECHA relating to risks to human health and the environment on any other aspects concerning the safety of substances on their own, in preparations or in articles.
The Committee also provides scientific support to improve the cooperation between the Community, its Member States, international organisations and third countries relating to the safety of substances, as well as active participation in technical assistance and capacity building activities on the sound management of chemicals in developing countries.
Composition
The members of RAC are appointed by ECHA's Management Board based on candidates nominated by the Members States for a renewable term of three years.
Latest news
- Highlights from March RAC and SEAC meetings 21 March 2024
- Highlights from November RAC and SEAC meetings 7 December 2023
- ECHA’s Risk Assessment Committee: banning secondary uses of creosote-treated wood necessary 20 September 2023

Chair of the RAC is Roberto Scazzola.
- Declaration of Interests [PDF]
Deputy Chair of the RAC is Piotr Sosnowski.
- Declaration of Interests
Committee's activities
- List of nominees for membership in RAC [PDF]
- Meetings (dates, agendas and minutes)
- List of RAC members with their CVs and Declarations of interest
- RAC work programme, March 2024
- Final report of the retrospective evaluation of ECHA committees [PDF]
Harmonised Classification and Labelling
- Mandate of a WG of RAC [PDF]
- Current public consultations
- RAC opinions
- Asessing physical hazards as part of CLP [PDF]
- Addressing developmental neurotoxicity and neurotoxicity under the current CLP hazard classes [PDF]
Restrictions
- Restrictions under consideration
Applications for Authorisation
- AfA A-listing criteria [PDF]
- Mandate for a working group of RAC
- Evaluating applications (including DNELs and dose-responses)
Occupational Exposure Limits
- Current consultations
Drinking Water Directive
- Mandate of a WG of RAC
- Opinions adopted under specific ECHA's Executive Director requests
Committee's procedures
- Rules of procedure of RAC [PDF]
- Rules for accessing S-CIRCABC interest groups [PDF]
- Working procedure for the appointment of rapporteurs [PDF]
- Agreement on the RAC Working Groups (RAC-47) [PDF]
- Framework for RAC opinion development [PDF]
- Procedure for agreement seeking (A-listing) [PDF]
- RAC working procedure on the conformity check [PDF]
- RAC working procedure on opinion development [PDF]
- Framework for conformity check and opinion development
- Recommendations
- Conformity check
- RAC working procedure for developing opinions [PDF]
- RAC Working procedure for scientific evaluation of OELs
- Understanding OELs
- Framework for Article 77(3)(c) requests [PDF]
- RAC: Working Procedure on setting of risk estimates such as DNELs and dose response functions [PDF]
Stakeholders
- Procedure for admission of ASO observers [PDF]
- List of the agreed RAC ASO observers [PDF]
Welcome to the ECHA website. This site is not fully supported in Internet Explorer 7 (and earlier versions). Please upgrade your Internet Explorer to a newer version.
Close Do not show this message again
This website uses cookies to ensure you get the best experience on our websites.
Close Find out more on how we use cookies.

IMAGES
VIDEO
COMMENTS
A project risk assessment is a formal effort to identify and analyze risks that a project faces. First, teams identify all possible project risks. Next, they determine the likelihood and potential impact of each risk. During a project risk assessment, teams analyze both positive and negative risks. Negative risks are events that can derail a ...
To conduct a quantitative risk analysis on a business process or project, high-quality data, a definite business plan, a well-developed project model and a prioritized list of business/project risk are necessary. Quantitative risk assessment is based on realistic and measurable data to calculate the impact values that the risk will create with ...
The risk management process includes risk identification and risk assessment. During an assessment, the project manager uses standard risk tools and quality data to help the team better avert later problems, manage the project cost, and keep project work on schedule. Risk assessment is the process by which the identified risks are ...
Risk analysis is the process that determines how likely it is that risk will arise in a project. It studies the uncertainty of potential risks and how they would impact the project in terms of schedule, quality and costs if, in fact, they were to show up. Two ways to analyze risk are quantitative and qualitative.
Abstract. Risk Analysis and Management is a key project management practice to ensure that the least number of surprises occur while your project is underway. While we can never predict the future with certainty, we can apply a simple and streamlined risk management process to predict the uncertainties in the projects and minimize the ...
process, this guide divides the overall process into two constituents or stages: risk analysis and risk management. Risk analysis is the combination of the estimate and evaluate sub-phases within the Assess phase in Figure 1. Risk analysis This stage of the process is generally split into two 'sub-stages': a qualitative analysis 'sub-
Through the process of quantitative risk management, project managers can convert the impact of risk on the project into numerical terms, which is often used to determine the cost and time contingencies of the project. This paper provides an overview of quantitative risk assessment methods and a real world example of how QRAs were effectively used on a capital project in the mining industry.
Risk assessment methodologies can be considered as your business's secret roadmap, guiding you through an unpredictable world, and ensuring you avoid all the potholes and pitfalls along the way. They provide systematic, step-by-step procedures to identify, analyze, evaluate, and control potential hazards or threats that might disrupt a business ...
When conducting a risk assessment for your project, it's important to recognise that each project has its own unique combination of potential risks. Project risk management is the process of predicting and preventing potential problems with a project that could affect its scope, cost, schedule, or quality. It involves both identifying existing ...
A risk assessment methodology is a systematic approach used to identify, evaluate, and manage potential hazards or risks in a given environment, playing a crucial role in the decision-making process. This methodology is a key component of risk management, as it helps organizations prioritize their resources effectively.
Some of the limitations of the present project risk management processes are reported in the literature are as follows: The most risk assessment studies focused mainly on delivering risk ratings, and there is a need of comprehensive methodology that could help the management in avoiding construction time overrun [].Risks are different for a different phase of the project, so, one-time risk ...
There are options on the tools and techniques that can be seamlessly incorporated into a business' process. The four common risk assessment tools are: risk matrix, decision tree, failure modes and effects analysis (FMEA), and bowtie model. Other risk assessment techniques include the what-if analysis, failure tree analysis, and hazard ...
Applying a reusable risk assessment tool could help a project manager to quickly identify, qualify, and quantify a project's uncertainty. This paper examines a step-by-step process for creating one such tool, a customized risk assessment tool that would enable project manager to track those particular risks which they and their organizations view as most threatening to a project's success.
Risk Assessment Methodologies. Organizations can take several approaches to assess risks—quantitative, qualitative, semi-quantitative, asset-based, vulnerability-based, or threat-based. Each methodology can evaluate an organization's risk posture, but they all require tradeoffs.
To do a project risk assessment you have to perform its four key elements: identifying risks, analyzing risks, determining risk response and documenting risks. ... To help you make a more accurate risk assessment and streamline its tedious process, you can turn to project management software with risk management; for example, ...
Project management software can help you keep track of risk. ProjectManager is online software that helps you identify risks, track them and calculate their impact. With our Risk view, you can make a risk list with your team and stay on top of all the risks within your project. Write a description, add tags, identify a resolution, mark impact ...
Get started for free . Project Risk Assessment Process . The project risk assessment framework outlines that effective operational risk assessment should be carried out by someone involved with the project and revolving around the context of the project and taking into consideration the characteristics of the person. The Project context describes the nature of the project such as its working ...
As shown in Figure 2, the Agile risk management process is an adaptive and iterative cycle that is repeated per sprint, enabling tailoring at the "setting context" phase to identify project and enterprise risk management techniques for managing the risk context at a project (e.g., project financing) and sprint level (e.g., meeting timelines).
Types of Risk Assessment Methodologies. Risk assessments can be either of two types: quantitative or qualitative. Quantitative risk refers to the numerical value of the probability and potential impact of a threat. This type of risk assessment requires data collection and statistical analysis to arrive at those numbers.
The suggested risk assessment procedure is composed of four steps of identifying, analyzing, evaluating, and managing the risks inherent in construction projects. The main tool of the proposed risk assessment methodology is the risk analysis software. The risk analysis software is built upon an uncertainty model based on fuzzy concept.
The current 2022 revision of ISO 27001 allows you to identify risks using any methodology you like; however, the methodology called "asset-based risk assessment" (defined by the old 2005 revision of ISO 27001) is still dominating, and it requires identification of assets, threats, and vulnerabilities.
All engineering projects involve risk management applications. Sometimes, risks cannot be effectively managed, leading to catastrophic consequences. Engineers must consciously or unconsciously manage these risks. Regardless of how risks are handled, project risks need to be systematically evaluated. Therefore, risk management procedures must be implemented in every project, particularly in geo ...
Formal risk assessment methodologies can help take guesswork out of evaluating IT risks if applied appropriately. Here is real-world feedback on using COBIT, OCTAVE, FAIR, NIST RMF, and TARA.
Many risk-assessment methodologies exist, each with their own advantages and disadvantages. Modern risk-assessment methods, typically applied quantitatively to engineered systems (e.g., nuclear reactors or aerospace applications), might also be used to support attempts to achieve useful nuclear arms-control agreements.
In the evolving construction landscape, this study introduces a novel methodology leveraging Building Information Modeling (BIM) to revolutionize safety management across diverse projects. By transitioning from traditional, reactive approaches to a proactive, comprehensive framework, BIM's integration into the design and execution phases enables the dynamic assessment and mitigation of risks ...
Risk Assessment Methodology. Risk management is the process of identifying areas of risk that could negatively impact the success of the project and proactively managing those areas. Risk is analyzed during the initial stages of the project to lay the foundation for success and on an ongoing basis throughout the project. Risk assessments are ...
Quantitative microbial risk assessment (QMRA) is a framework that integrates information about pathogen occurrence, transport, exposure, and health effects to understand and quantify risks of infection or illness. 8,10 Using an iterative process consisting of problem formulation (hazard identification), exposure and health effects assessments, and risk characterization, disease transmission ...
As part of the Master of Disaster Management programme, this year's Vulnerability and Risk Assessment Methods (VRAM) elective was hosted in Chennai, Tamil Nadu, India in partnership with the Indian Institute of Technology Madras (IITM) School of Sustainability and Okapi Research and Advisory.. The course consisted of a week of theory-based lectures, a week of fieldwork, and a week of ...
RAC assesses the risk of a substance arising from the uses of a substance when an application for authorisation is submitted. This includes an assessment of the appropriateness and effectiveness of the risk management measures as described in the authorisation application, and if relevant, of the risks of possible alternatives.