Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center


MASTER THESIS ADMINISTRATION OF REMOTE COMPUTER NETWORKS

Related Papers
Bruce Elenbogen
This paper discusses a non-traditional course in computer networking. The course is a laboratory course with substantial hands-on experiences, which can help to prepare students for jobs in industry as soon as they graduate from an undergraduate institution. This course is not meant to replace the traditional network course but to supplement it by teaching how computer networks work in practice and by exploring new topics such as internetworking, high speed networking, client/server computing and security.
International Research Group - IJET JOURNAL
World Scientific
Jawwad Shamsi
Efficient and cost-effective measurement of network characteristics is pivotal for distributed systems deployed on the Internet. The network characteristics are utilized by Internet-based distributed systems to provide better service to the user and enhance performance for the application. This chapter provides a detailed analysis of existing techniques for the measurement of the four important network characteristics which include latency, bandwidth, path detection and loss rate. The chapter describes key concepts related to network measurements, including techniques for clock synchronization, strategies for time stamping of probes, methods for network analysis, difference between active and passive measurements and comparison of round trip vs. one way delay measurements. It elaborates the usefulness of different transport and network layer protocols (i.e. TCP, UDP and ICMP) for obtaining network measurements and continue this discussion to describe some important measurement tools such as Ping, Traceroue, Pathchar, Sting, Scriptroute, Spruce and Paris Traceroute. The chapter explains the effectiveness and limitations of these tools with respect to the measurement of network characteristics.
IOSR Journal of Computer Engineering
azmath mubeen
network administration
Mohd Nazri Ismail
International Journal IJRITCC
Citation/Export MLA Mr. M. B. Patil, Dr. R. S. Kamath, Dr. P. G. Naik, “Design and Development of Network Monitoring and Controlling Tool for Department of Computer Studies CSIBER”, March 15 Volume 3 Issue 3 , International Journal on Recent and Innovation Trends in Computing and Communication (IJRITCC), ISSN: 2321-8169, PP: 1237 - 1243, DOI: 10.17762/ijritcc2321-8169.150376 APA Mr. M. B. Patil, Dr. R. S. Kamath, Dr. P. G. Naik, March 15 Volume 3 Issue 3, “Design and Development of Network Monitoring and Controlling Tool for Department of Computer Studies CSIBER”, International Journal on Recent and Innovation Trends in Computing and Communication (IJRITCC), ISSN: 2321-8169, PP: 1237 - 1243, DOI: 10.17762/ijritcc2321-8169.150376
Kanu Richmond
The need for good and reliable data transmission within computer network and internet forms the basis for management and control of bandwidth. Without bandwidth management, an application or user will not be able to control all available bandwidth and prevent other applications or users from using the networks. It will be impossible to differentiate between various network traffics, and it will also be difficult to control which user or application has priority on the network. Applications which require specific quantity and quality of service may not be predicted in terms of available bandwidth, thus making some applications run poorly due to improper bandwidth allocation. This work focus on the development of an application to combat the challenges facing easy flow of data transmission problems in network design as organization network evolves. PHP Script, Apache Server and MySQL are the development tools used. Keywordsbandwidth management, data transmission, computer networks, ap...
Aung Than Kyaw
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Sujeeth Reddy
Sasikumar Punnekkat
IJSTE - International Journal of Science Technology & Engineering
IJSTE - International Journal of Science Technology and Engineering
prashanth b
IJIREM JOURNAL
Mohmmed Munna
BT Technology Journal
David Parish
Icact Transactions on the Advanced Communications Technology
ASHISH K U M A R JHA
Petros Zerfos
Zenodo (CERN European Organization for Nuclear Research)
anita antwiwaa
Bruce Hallberg
IJRASET Publication
Nwakeze Osita Miracle
NWAKEZE M I R A C L E OSITA , Nwakeze Miracle
International Astronomical Union Colloquium
Guido Russo
Iwan Adhicandra
International Journal of Computer Applications
Global Academic Digital Library (GADL) - Journal of Inventions in Computer Science & Communication Technology (JICSCT)
Transmission Control Protocol Performance Monitoring for Simulated Wired University Computer Network using OPNET
Ammar O . Hasan
Adam Kaliszan
Journal of Computer Sciences and Applications
Karima Velásquez , Eric Gamess
Ata Ul Munim Aseel Shaikh
Springer International Publishing eBooks
Cajetan Akujuobi
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024

Home > Computer Science > CompSci TDs > Masters Theses
Computer Science Masters Theses
Theses from 2024 2024.
Enabling Smart Healthcare Applications Through Visible Light Communication Networks , Jack Manhardt
Time series anomaly detection using generative adversarial networks , Shyam Sundar Saravanan
Learn from the Past: using Peer Data to Improve Course Recommendations in Personalized Education , Colton Walker
Theses from 2023 2023
Dynamic Discounted Satisficing Based Driver Decision Prediction in Sequential Taxi Requests , Sree Pooja Akula
MAT: Genetic Algorithms Based Multi-Objective Adversarial Attack on Multi-Task Deep Neural Networks , Nikola Andric
Computer Vision in Adverse Conditions: Small Objects, Low-Resoltuion Images, and Edge Deployment , Raja Sunkara
Theses from 2022 2022
Maximising social welfare in selfish multi-modal routing using strategic information design for quantal response travelers , Sainath Sanga
Man-in-the-Middle Attacks on MQTT based IoT networks , Henry C. Wong
Theses from 2021 2021
Biochemical assay invariant attestation for the security of cyber-physical digital microfluidic biochips , Fredrick Eugene Love II
Theses from 2020 2020
On predicting stopping time of human sequential decision-making using discounted satisficing heuristic , Mounica Devaguptapu
Theses from 2019 2019
Advanced techniques for improving canonical genetic programming , Adam Tyler Harter
Evolved parameterized selection for evolutionary algorithms , Samuel Nathan Richter
Design and implementation of applications over delay tolerant networks for disaster and battlefield environment , Karthikeyan Sachidanandam
Theses from 2018 2018
Mixed-criticality real-time task scheduling with graceful degradation , Samsil Arefin
CARD: Concealed and remote discovery of IoT devices in victims' home networks , Sammie Lee Bush
Multiple security domain non deducibility in the FREEDM smart grid infrastructure , Manish Jaisinghani
Reputation and credit based incentive mechanism for data-centric message delivery in delay tolerant networks , Himanshu Jethawa
Solidification rate detection through solid-liquid interface tracking , Wei Luo
Cloud transactions and caching for improved performance in clouds and DTNs , Dileep Mardham
Cyber-physical security of an electric microgrid , Prashanth Palaniswamy
An approach for formal analysis of the security of a water treatment testbed , Sai Sidharth Patlolla
Analyzing large scale trajectory data to identify users with similar behavior , Tyler Clark Percy
Precise energy efficient scheduling of mixed-criticality tasks & sustainable mixed-criticality scheduling , Sai Sruti
A network tomography approach for traffic monitoring in smart cities , Ruoxi Zhang
Improved CRPD analysis and a secure scheduler against information leakage in real-time systems , Ying Zhang
Theses from 2017 2017
Cyber-physical security of a chemical plant , Prakash Rao Dunaka
UFace: Your universal password no one can see , Nicholas Steven Hilbert
Multi stage recovery from large scale failure in interdependent networks , Maria Angelin John Bosco
Multiple security domain model of a vehicle in an automated vehicle system , Uday Ganesh Kanteti
Personalizing education with algorithmic course selection , Tyler Morrow
Decodable network coding in wireless network , Junwei Su
Multiple security domain nondeducibility air traffic surveillance systems , Anusha Thudimilla
Theses from 2016 2016
Automated design of boolean satisfiability solvers employing evolutionary computation , Alex Raymond Bertels
Care-Chair: Opportunistic health assessment with smart sensing on chair backrest , Rakesh Kumar
Theses from 2015 2015
Dependability analysis and recovery support for smart grids , Isam Abdulmunem Alobaidi
Sensor authentication in collaborating sensor networks , Jake Uriah Bielefeldt
Argumentation based collaborative software architecture design and intelligent analysis of software architecture rationale , NagaPrashanth Chanda
A Gaussian mixture model for automated vesicle fusion detection and classification , Haohan Li
Hyper-heuristics for the automated design of black-box search algorithms , Matthew Allen Martin
Aerial vehicle trajectory design for spatio-temporal task satisfaction and aggregation based on utility metric , Amarender Reddy Mekala
Design and implementation of a broker for cloud additive manufacturing services , Venkata Prashant Modekurthy
Cyber security research frameworks for coevolutionary network defense , George Daniel Rush
Energy disaggregation in NIALM using hidden Markov models , Anusha Sankara
Theses from 2014 2014
Crime pattern detection using online social media , Raja Ashok Bolla
Energy efficient scheduling and allocation of tasks in sensor cloud , Rashmi Dalvi
A cloud brokerage architecture for efficient cloud service selection , Venkata Nagarjuna Dondapati
Access control delegation in the clouds , Pavani Gorantla
Evolving decision trees for the categorization of software , Jasenko Hosic
M-Grid : A distributed framework for multidimensional indexing and querying of location based big data , Shashank Kumar
Privacy preservation using spherical chord , Doyal Tapan Mukherjee
Top-K with diversity-M data retrieval in wireless sensor networks , Kiran Kumar Puram
On temporal and frequency responses of smartphone accelerometers for explosives detection , Srinivas Chakravarthi Thandu
Efficient data access in mobile cloud computing , Siva Naga Venkata Chaitanya Vemulapalli
An empirical study on symptoms of heavier internet usage among young adults , SaiPreethi Vishwanathan
Theses from 2013 2013
Sybil detection in vehicular networks , Muhammad Ibrahim Almutaz
Argumentation placement recommendation and relevancy assessment in an intelligent argumentation system , Nian Liu
Security analysis of a cyber physical system : a car example , Jason Madden
Efficient integrity verification of replicated data in cloud , Raghul Mukundan
Search-based model summarization , Lokesh Krishna Ravichandran
Hybridizing and applying computational intelligence techniques , Jeffery Scott Shelburg
Secure design defects detection and correction , Wenquan Wang
Theses from 2012 2012
Robust evolutionary algorithms , Brian Wesley Goldman
Semantic preserving text tepresentation and its applications in text clustering , Michael Howard
Vehicle path verification using wireless sensor networks , Gerry W. Howser
Distributed and collaborative watermarking in relational data , Prakash Kumar
Theses from 2011 2011
A social network of service providers for trust and identity management in the Cloud , Makarand Bhonsle
Adaptive rule-based malware detection employing learning classifier systems , Jonathan Joseph Blount
A low-cost motion tracking system for virtual reality applications , Abhinav Chadda
Optimization of textual affect entity relation models , Ajith Cherukad Jose
MELOC - memory and location optimized caching for mobile Ad hoc networks , Lekshmi Manian Chidambaram
A framework for transparent depression classification in college settings via mining internet usage patterns , Raghavendra Kotikalapudi
An incentive based approach to detect selfish nodes in Mobile P2P network , Hemanth Meka
Location privacy policy management system , Arej Awodha Muhammed
Exploring join caching in programming codes to reduce runtime execution , Swetha Surapaneni
Theses from 2010 2010
Event detection from click-through data via query clustering , Prabhu Kumar Angajala
Population control in evolutionary algorithms , Jason Edward Cook
Dynamic ant colony optimization for globally optimizing consumer preferences , Pavitra Dhruvanarayana
EtherAnnotate: a transparent malware analysis tool for integrating dynamic and static examination , Joshua Michael Eads
Representation and validation of domain and range restrictions in a relational database driven ontology maintenance system , Patrick Garrett. Edgett
Cloud security requirements analysis and security policy development using a high-order object-oriented modeling technique , Kenneth Kofi Fletcher
Multi axis slicing for rapid prototyping , Divya Kanakanala
Content based image retrieval for bio-medical images , Vikas Nahar
2-D path planning for direct laser deposition process , Swathi Routhu
Contribution-based priority assessment in a web-based intelligent argumentation network for collaborative software development , Maithili Satyavolu
An artificial life approach to evolutionary computation: from mobile cellular algorithms to artificial ecosystems , Shivakar Vulli
Intelligent computational argumentation for evaluating performance scores in multi-criteria decision making , Rubal Wanchoo
Minimize end-to-end delay through cross-layer optimization in multi-hop wireless sensor networks , Yibo Xu
Theses from 2009 2009
Information flow properties for cyber-physical systems , Rav Akella
Exploring the use of a commercial game engine for the development of educational software , Hussain Alafaireet
Automated offspring sizing in evolutionary algorithms , André Chidi Nwamba
Theses from 2008 2008
Image analysis techniques for vertebra anomaly detection in X-ray images , Mohammed Das
Cross-layer design through joint routing and link allocation in wireless sensor networks , Xuan Gong
A time series classifier , Christopher Mark Gore
An economic incentive based routing protocol incorporating quality of service for mobile peer-to-peer networks , Anil Jade
Incorporation of evidences in an intelligent argumentation network for collaborative engineering design , Ekta Khudkhudia
PrESerD - Privacy ensured service discovery in mobile peer-to-peer environment , Santhosh Muthyapu
Co-optimization: a generalization of coevolution , Travis Service
Critical infrastructure protection and the Domain Name Service (DNS) system , Mark Edward Snyder
Co-evolutionary automated software correction: a proof of concept , Joshua Lee Wilkerson
Theses from 2007 2007
A light-weight middleware framework for fault-tolerant and secure distributed applications , Ian Jacob Baird
Advanced Search
- Notify me via email or RSS
- Collections
- Disciplines
- All Authors
- Faculty Authors
Author Corner
Useful links.
- Library Resources

Thesis Locations
- View these on map
- View these in Google Earth
Home | About | FAQ | My Account | Accessibility Statement
Privacy Copyright
- Bibliography
- More Referencing guides Blog Automated transliteration Relevant bibliographies by topics
- Automated transliteration
- Relevant bibliographies by topics
- Referencing guides
Computer Science Dissertations and Theses
Theses/dissertations from 2024 2024.
A Deep Learning Framework for Blockage Mitigation in mmWave Wireless , Ahmed Hazaa Almutairi (Dissertation)
Design and Test of Asynchronous Systems Using the Link and Joint Model , Ebelechukwu Esimai (Dissertation)
Automatic Measurement of Dialogue Engagingness in Multilingual Settings , Amila Ferron (Thesis)
Resource-constrained 2D Scene Recovery with Single-Photon Cameras , Daphne Ariadne Kurzenhauser (Thesis)
MmWave RAT Optimization: MAC Layer Initial Access Design and Transport Layer Integration , Suresh Srinivasan (Dissertation)
Designing for Deployable, Secure, and Generic Machine Learning Systems , Li-Yun Wang (Dissertation)
Theses/Dissertations from 2023 2023
Seeing in the Dark: Towards Robust Pedestrian Detection at Nighttime , Afnan Althoupety (Dissertation)
A Deep Hierarchical Variational Autoencoder for World Models in Complex Reinforcement Learning Environments , Sriharshitha Ayyalasomayajula (Thesis)
Toward Efficient Rendering: A Neural Network Approach , Qiqi Hou (Dissertation)
Energy Auction with Non-Relational Persistence , Michael Ramez Howard (Thesis)
Implementing a Functional Logic Programming Language via the Fair Scheme , Andrew Michael Jost (Dissertation)
Multi-Agent Deep Reinforcement Learning for Radiation Localization , Benjamin Scott Totten (Thesis)
Theses/Dissertations from 2022 2022
Using Intrinsically-Typed Definitional Interpreters to Verify Compiler Optimizations in a Monadic Intermediate Language , Dani Barrack (Thesis)
An Automated Zoom Class Session Analysis Tool to Improve Education , Jack Arlo Cannon II (Thesis)
Scaling EPA-RIMM with Multicore System Management Interrupt Handlers , Alexander K. Freed (Thesis)
Unpaired Style Transfer Conditional Generative Adversarial Network for Scanned Document Generation , David Jonathan Hawbaker (Thesis)
Toward Analyzing the Diversity of Extractive Summaries , Aaron David Hudson (Thesis)
Making Curry with Rice: An Optimizing Curry Compiler , Steven Libby (Dissertation)
Domain Knowledge as Motion-Aware Inductive Bias for Deep Video Synthesis: Two Case Studies , Long Mai (Dissertation)

Theses/Dissertations from 2021 2021
Efficient Neuromorphic Algorithms for Gamma-Ray Spectrum Denoising and Radionuclide Identification , Merlin Phillip Carson (Thesis)
Storing Intermediate Results in Space and Time: SQL Graphs and Block Referencing , Basem Ibrahim Elazzabi (Dissertation)
Automated Test Generation for Validating SystemC Designs , Bin Lin (Dissertation)
Forecasting Optimal Parameters of the Broken Wing Butterfly Option Strategy Using Differential Evolution , David Munoz Constantine (Thesis)
Situate: An Agent-Based System for Situation Recognition , Max Henry Quinn (Dissertation)
Theses/Dissertations from 2020 2020
Multiple Diagram Navigation , Hisham Benotman (Dissertation)
Smart Contract Vulnerabilities on the Ethereum Blockchain: a Current Perspective , Daniel Steven Connelly (Thesis)
Extensible Performance-Aware Runtime Integrity Measurement , Brian G. Delgado (Dissertation)
Novel View Synthesis - a Neural Network Approach , Hoang Le (Dissertation)
Exploring the Potential of Sparse Coding for Machine Learning , Sheng Yang Lundquist (Dissertation)
Workflow Critical Path: a Data-Oriented Path Metric for Holistic HPC Workflows , Daniel D. Nguyen (Thesis)
Novel View Synthesis in Time and Space , Simon Niklaus (Dissertation)
Balancing Security, Performance and Deployability in Encrypted Search , David Joel Pouliot (Dissertation)
Theses/Dissertations from 2019 2019
A Secure Anti-Counterfeiting System using Near Field Communication, Public Key Cryptography, Blockchain, and Bayesian Games , Naif Saeed Alzahrani (Dissertation)
Spectral Clustering for Electrical Phase Identification Using Advanced Metering Infrastructure Voltage Time Series , Logan Blakely (Thesis)
Local Radiance , Scott Peter Britell (Dissertation)
Correct-by-Construction Typechecking with Scope Graphs , Katherine Imhoff Casamento (Thesis)
Versatile Binary-level Concolic Testing , Bo Chen (Dissertation)
Crumpled and Abraded Encryption: Implementation and Provably Secure Construction , Scott Sherlock Griffy (Thesis)
Knowing Without Knowing: Real-Time Usage Identification of Computer Systems , Leila Mohammed Hawana (Thesis)
Design and Experimental Evaluation of DeepMarket: an Edge Computing Marketplace with Distributed TensorFlow Execution Capability , Soyoung Kim (Thesis)
Localizing Little Landmarks with Transfer Learning , Sharad Kumar (Thesis)
Context-Aware Wi-Fi Infrastructure-based Indoor Positioning Systems , Huy Phuong Tran (Dissertation)
Theses/Dissertations from 2018 2018
Bounding Box Improvement with Reinforcement Learning , Andrew Lewis Cleland (Thesis)
Sensing Building Structure Using UWB Radios for Disaster Recovery , Jeong Eun Lee (Dissertation)
Annotation-Enabled Interpretation and Analysis of Time-Series Data , Niveditha Venugopal (Thesis)
EPA-RIMM-V: Efficient Rootkit Detection for Virtualized Environments , Tejaswini Ajay Vibhute (Thesis)
Theses/Dissertations from 2017 2017
Improved Scoring Models for Semantic Image Retrieval Using Scene Graphs , Erik Timothy Conser (Thesis)
Refining Bounding-Box Regression for Object Localization , Naomi Lynn Dickerson (Thesis)
Fully Generic Programming Over Closed Universes of Inductive-Recursive Types , Larry Diehl (Dissertation)
Communicating at Terahertz Frequencies , Farnoosh Moshirfatemi (Dissertation)
Designing In-Headset Authoring Tools for Virtual Reality Video , Cuong Nguyen (Dissertation)
Certifying Loop Pipelining Transformations in Behavioral Synthesis , Disha Puri (Dissertation)
Power-Aware Datacenter Networking and Optimization , Qing Yi (Dissertation)
Theses/Dissertations from 2016 2016
Identifying Relationships between Scientific Datasets , Abdussalam Alawini (Dissertation)
Information Representation and Computation of Spike Trains in Reservoir Computing Systems with Spiking Neurons and Analog Neurons , Amin Almassian (Thesis)
Investigations of an "Objectness" Measure for Object Localization , Lewis Richard James Coates (Thesis)
Image Stitching: Handling Parallax, Stereopsis, and Video , Fan Zhang (Dissertation)
Theses/Dissertations from 2015 2015
Novel Methods for Learning and Adaptation in Chemical Reaction Networks , Peter Banda (Dissertation)
Post-silicon Functional Validation with Virtual Prototypes , Kai Cong (Dissertation)
Novel Cryptographic Primitives and Protocols for Censorship Resistance , Kevin Patrick Dyer (Dissertation)
Hardware/Software Interface Assurance with Conformance Checking , Li Lei (Dissertation)
Leveraging Contextual Relationships Between Objects for Localization , Clinton Leif Olson (Thesis)
The Performance of Random Prototypes in Hierarchical Models of Vision , Kendall Lee Stewart (Thesis)
Tweakable Ciphers: Constructions and Applications , Robert Seth Terashima (Dissertation)
Scalable Equivalence Checking for Behavioral Synthesis , Zhenkun Yang (Dissertation)
Theses/Dissertations from 2014 2014
The Nax Language: Unifying Functional Programming and Logical Reasoning in a Language based on Mendler-style Recursion Schemes and Term-indexed Types , Ki Yung Ahn (Dissertation)
Using Spammers' Computing Resources for Volunteer Computing , Thai Le Quy Bui (Thesis)
Towards Constructing Interactive Virtual Worlds , Francis Chang (Dissertation)
System-wide Performance Analysis for Virtualization , Deron Eugene Jensen (Thesis)
Advances in Piecewise Smooth Image Reconstruction , Ralf Juengling (Dissertation)
Interpretable Machine Learning and Sparse Coding for Computer Vision , Will Landecker (Dissertation)
Optimizing Data Movement in Hybrid Analytic Systems , Patrick Michael Leyshock (Dissertation)
Ranked Similarity Search of Scientific Datasets: An Information Retrieval Approach , Veronika Margaret Megler (Dissertation)
Using GIST Features to Constrain Search in Object Detection , Joanna Browne Solmon (Thesis)
The Role of Prototype Learning in Hierarchical Models of Vision , Michael David Thomure (Dissertation)
Theses/Dissertations from 2013 2013
Object Detection and Recognition in Natural Settings , George William Dittmar (Thesis)
Trust-but-Verify: Guaranteeing the Integrity of User-generated Content in Online Applications , Akshay Dua (Dissertation)
Equivalence Checking for High-Assurance Behavioral Synthesis , Kecheng Hao (Dissertation)
Type Classes and Instance Chains: A Relational Approach , John Garrett Morris (Dissertation)
Theses/Dissertations from 2012 2012
Using Dataflow Optimization Techniques with a Monadic Intermediate Language , Justin George Bailey (Thesis)
A Survey and Analysis of Solutions to the Oblivious Memory Access Problem , Erin Elizabeth Chapman (Thesis)
A Data-Descriptive Feedback Framework for Data Stream Management Systems , Rafael J. Fernández Moctezuma (Dissertation)
Extending Relativistic Programming to Multiple Writers , Philip William Howard (Dissertation)
The Basic Scheme for the Evaluation of Functional Logic Programs , Arthur Peters (Thesis)
The Link Between Image Segmentation and Image Recognition , Karan Sharma (Thesis)
Relativistic Causal Ordering A Memory Model for Scalable Concurrent Data Structures , Josh Triplett (Dissertation)
Theses/Dissertations from 2011 2011
Conceptual Modeling of Data with Provenance , David William Archer (Dissertation)
Low-latency Estimates for Window-Aggregate Queries over Data Streams , Amit Bhat (Thesis)
Information Processing in Two-Dimensional Cellular Automata , Martin Cenek (Dissertation)
Scalable and Efficient Tasking for Dynamic Sensor Networks , Thanh Xuan Dang (Dissertation)
On the Effect of Topology on Learning and Generalization in Random Automata Networks , Alireza Goudarzi (Thesis)
HOLCF '11: A Definitional Domain Theory for Verifying Functional Programs , Brian Charles Huffman (Dissertation)
A Functional Approach to Memory-Safe Operating Systems , Rebekah Leslie (Dissertation)
Factoring Semiprimes Using PG2N Prime Graph Multiagent Search , Keith Eirik Wilson (Thesis)
High Speed Wireless Networking for 60GHz , Candy Yiu (Dissertation)
Theses/Dissertations from 2010 2010
Extensible Scheduling in a Haskell-based Operating System , Kenneth William Graunke (Thesis)
Addressing Automated Adversaries of Network Applications , Edward Leo Kaiser (Dissertation)
An Automata-Theoretic Approach to Hardware/Software Co-verification , Juncao Li (Dissertation)
Practical Type Inference for the GADT Type System , Chuan-kai Lin (Dissertation)
Scalable event tracking on high-end parallel systems , Kathryn Marie Mohror (Dissertation)
Advanced Search
- Notify me via email or RSS
- Featured Collections
- All Authors
- Schools & Colleges
- Dissertations & Theses
- PDXOpen Textbooks
- Conferences
- Collections
- Disciplines
- Faculty Expert Gallery
- Submit Research
- Faculty Profiles
- Terms of Use
- Feedback Form
Home | About | My Account | Accessibility Statement | Portland State University
Privacy Copyright
UT Electronic Theses and Dissertations
Permanent URI for this collection https://hdl.handle.net/2152/11
This collection contains University of Texas at Austin electronic theses and dissertations (ETDs). The collection includes ETDs primarily from 2001 to the present. Some pre-2001 theses and dissertations have been digitized and added to this collection, but those are uncommon. The library catalog is the most comprehensive list of UT Austin theses and dissertations.
Since 2010, the Office of Graduate Studies at UT Austin has required all theses and dissertations to be made publicly available in Texas ScholarWorks; however, authors are able to request an embargo of up to seven years. Embargoed ETDs will not show up in this collection. Most of the ETDs in this collection are freely accessible to all users, but some pre-2010 works require a current UT EID at point of use. Please see the FAQs for more information. If you have a question about the availability of a specific ETD, please contact [email protected].
Some items in this collection may contain offensive images or text. The University of Texas Libraries is committed to maintaining an accurate and authentic scholarly and historic record. An authentic record is essential for understanding our past and informing the present. In order to preserve the authenticity of the historical record we will not honor requests to redact content, correct errors, or otherwise remove content, except in cases where there are legal concerns (e.g. potential copyright infringement, inclusion of HIPAA/FERPA protected information or Social Security Numbers) or evidence of a clear and imminent threat to personal safety or well-being.
This policy is in keeping with the American Library Association code of ethics to resist efforts to censor library resources, and the Society of American Archivists code of ethics that states "archivists may not willfully alter, manipulate, or destroy data or records to conceal facts or distort evidence."
Recent Submissions
- 1 (current)
Blog The Education Hub
https://educationhub.blog.gov.uk/2024/08/20/gcse-results-day-2024-number-grading-system/
GCSE results day 2024: Everything you need to know including the number grading system

Thousands of students across the country will soon be finding out their GCSE results and thinking about the next steps in their education.
Here we explain everything you need to know about the big day, from when results day is, to the current 9-1 grading scale, to what your options are if your results aren’t what you’re expecting.
When is GCSE results day 2024?
GCSE results day will be taking place on Thursday the 22 August.
The results will be made available to schools on Wednesday and available to pick up from your school by 8am on Thursday morning.
Schools will issue their own instructions on how and when to collect your results.
When did we change to a number grading scale?
The shift to the numerical grading system was introduced in England in 2017 firstly in English language, English literature, and maths.
By 2020 all subjects were shifted to number grades. This means anyone with GCSE results from 2017-2020 will have a combination of both letters and numbers.
The numerical grading system was to signal more challenging GCSEs and to better differentiate between students’ abilities - particularly at higher grades between the A *-C grades. There only used to be 4 grades between A* and C, now with the numerical grading scale there are 6.
What do the number grades mean?
The grades are ranked from 1, the lowest, to 9, the highest.
The grades don’t exactly translate, but the two grading scales meet at three points as illustrated below.
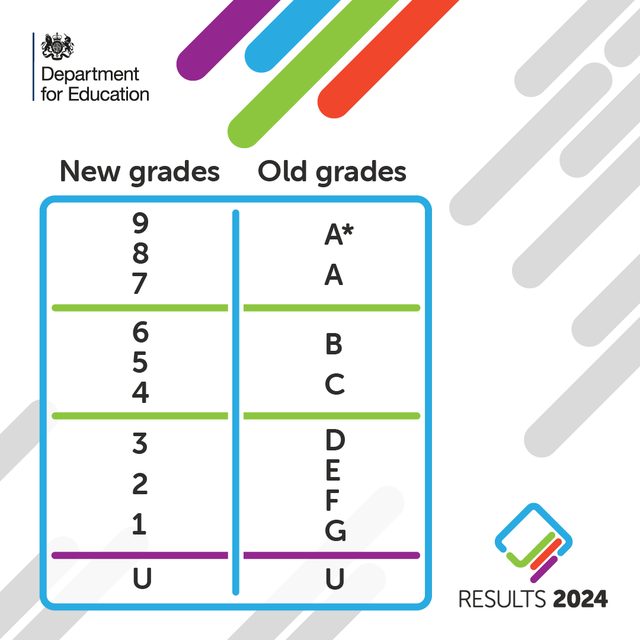
The bottom of grade 7 is aligned with the bottom of grade A, while the bottom of grade 4 is aligned to the bottom of grade C.
Meanwhile, the bottom of grade 1 is aligned to the bottom of grade G.
What to do if your results weren’t what you were expecting?
If your results weren’t what you were expecting, firstly don’t panic. You have options.
First things first, speak to your school or college – they could be flexible on entry requirements if you’ve just missed your grades.
They’ll also be able to give you the best tailored advice on whether re-sitting while studying for your next qualifications is a possibility.
If you’re really unhappy with your results you can enter to resit all GCSE subjects in summer 2025. You can also take autumn exams in GCSE English language and maths.
Speak to your sixth form or college to decide when it’s the best time for you to resit a GCSE exam.
Look for other courses with different grade requirements
Entry requirements vary depending on the college and course. Ask your school for advice, and call your college or another one in your area to see if there’s a space on a course you’re interested in.
Consider an apprenticeship
Apprenticeships combine a practical training job with study too. They’re open to you if you’re 16 or over, living in England, and not in full time education.
As an apprentice you’ll be a paid employee, have the opportunity to work alongside experienced staff, gain job-specific skills, and get time set aside for training and study related to your role.
You can find out more about how to apply here .
Talk to a National Careers Service (NCS) adviser
The National Career Service is a free resource that can help you with your career planning. Give them a call to discuss potential routes into higher education, further education, or the workplace.
Whatever your results, if you want to find out more about all your education and training options, as well as get practical advice about your exam results, visit the National Careers Service page and Skills for Careers to explore your study and work choices.
You may also be interested in:
- Results day 2024: What's next after picking up your A level, T level and VTQ results?
- When is results day 2024? GCSEs, A levels, T Levels and VTQs
Tags: GCSE grade equivalent , gcse number grades , GCSE results , gcse results day 2024 , gsce grades old and new , new gcse grades
Sharing and comments
Share this page, related content and links, about the education hub.
The Education Hub is a site for parents, pupils, education professionals and the media that captures all you need to know about the education system. You’ll find accessible, straightforward information on popular topics, Q&As, interviews, case studies, and more.
Please note that for media enquiries, journalists should call our central Newsdesk on 020 7783 8300. This media-only line operates from Monday to Friday, 8am to 7pm. Outside of these hours the number will divert to the duty media officer.
Members of the public should call our general enquiries line on 0370 000 2288.
Sign up and manage updates
Follow us on social media, search by date.
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | |||
| 5 | 7 | 8 | 9 | 10 | 11 | |
| 13 | 14 | 15 | 16 | 17 | 18 | |
| 21 | 22 | 23 | 24 | 25 | ||
| 26 | 27 | 29 | 31 | |||
Comments and moderation policy

COMMENTS
Software-defined networking (SDN) promises flexible control of computer networks by or-chestrating switches in the network dataplane through a centralized controller. However, despite this promise, operators used to fast and fault-tolerant routing using traditional proto-cols face three important problems while deploying SDN.
distances in computer networks. There are many notions of "distance" in networks, for exam-ple the latency between points, the bandwidth, the hop count, the IGP distance, etc. For some applications these distances are crucial (e.g. routing), and for others they are nice to know for op-timization reasons (e.g. content-distribution networks).
network via cables or radio waves to share information or data is called data network. Computers on a network are called nodes. Computer network provides many ad-vantages such as resource sharing, exchanging emails, internet, IP phones, video con-ferences and many more. Examples of computer network are personal area network
CSMA/CA MAC has three common problems to deal with: the hidden node problem, the. exposed node problem, and the capture problem, as shown in Figure 2.3. There are two. common techniques utilized by CSMA/CA MAC protocols to solve these problems. These. two techniques are out-of-band signaling and controlled handshaking.
1. Overview of the thesis Learning of network protocols has been studied in a project-based, internationally distributed, university course in computer systems taught jointly by two universities. The work presented in this thesis concerns students' understanding of network protocols1. Insights into the
This thesis analyzed techniques for measuring, analyzing, presenting and inter-preting the different properties for the administration of remote computer network. In this way system administrators can benet from this thesis when administrating their remote computer networks. i
The three case studies together demonstrated all aspects of quality of service measurements, and together with the analysis and presentation methods described in this thesis, the network and system administrators should be able to administrate remote computer networks. 72 fBibliography [1] Andrew S. Tanenbaum.
This thesis discusses the history and efforts to programmable and active networks, the early practices towards separating the control plane and data plane. Highlighting the architectural concepts in networking that software defined networks emanated as well as the history and evolution of software defined networking.
Malware is an often-used method in cyber criminality. Malware is malicious software used to accomplish identity theft, cyber espionage, and disruptions in systems. Malware appears in the form of viruses, Trojan horses, and ransomware [24]. In contrast to a typical bug, malware is an attempt designed to cause harm.
network security protocols, in several instances identifying serious security vulnerabilities. The second problempertains to the computationalsoundnessof symbolic protocolanal-ysis. At a high-level, this means that a logical method for protocol analysis should have an associated soundness theorem, which guarantees that a completely symbolic ...
hypergraph based wireless system area networks for multi-computer systems PhD thesis. ... This thesis cannot be reproduced or quoted extensively from without first obtaining permission in writing from the Author The content must not be changed in any way or sold commercially in any ... PDF ProbabilityDensityFunction PHY PhysicalLayer PLL Phase ...
Developing Computer Networks Students' Computational ... Thesis submitted for the Degree of Doctor of Education Institute of Education Steve Mvalo September 2018 . ii Declaration of original authorship I confirm that this is my own and use of all material from other sources has been properly and
Computer networks are a. system of i nterconnected computers for the purpose of. sharing digital information. The computer network. enables to analyze, organize and disseminate the. information ...
Department of Mathematics and Computer Science. Hayward, CA 94542-3092, USA. ABSTRACT. In this paper, we discuss the advantages and. disadvantages of using network simulators to teach. networking ...
PDF. Design and implementation of applications over delay tolerant networks for disaster and battlefield environment, Karthikeyan Sachidanandam. Theses from 2018 PDF. Mixed-criticality real-time task scheduling with graceful degradation, Samsil Arefin. PDF. CARD: Concealed and remote discovery of IoT devices in victims' home networks, Sammie ...
Computer Networking Thesis Sample - Free download as PDF File (.pdf), Text File (.txt) or read online for free. The document discusses writing a thesis on computer networking and describes the challenges involved. It then introduces HelpWriting.net as offering expert assistance for every step of the thesis writing process. Their experienced writers specialize in computer networking and can ...
Computer Networking Thesis Topics - Free download as PDF File (.pdf), Text File (.txt) or read online for free. The document discusses the challenges of writing a computer networking thesis and provides an overview of the assistance available from HelpWriting.net. Crafting a high-quality networking thesis requires extensive research, understanding advanced concepts, and clearly presenting ...
Consult the top 50 dissertations / theses for your research on the topic 'SDN - Software-Defined Networking.'. Next to every source in the list of references, there is an 'Add to bibliography' button. Press on it, and we will generate automatically the bibliographic reference to the chosen work in the citation style you need: APA, MLA, Harvard ...
Phd Thesis Topics in Networking - Free download as PDF File (.pdf), Text File (.txt) or read online for free. This document discusses some of the challenges involved in selecting and developing a compelling PhD thesis topic in networking. Choosing the right topic requires an in-depth understanding of the current state of the field as well as emerging trends.
Theses/Dissertations from 2019. PDF. A Secure Anti-Counterfeiting System using Near Field Communication, Public Key Cryptography, Blockchain, and Bayesian Games, Naif Saeed Alzahrani (Dissertation) PDF. Spectral Clustering for Electrical Phase Identification Using Advanced Metering Infrastructure Voltage Time Series, Logan Blakely (Thesis) PDF.
The Accelerated Bachelors/Master's (ABM) degree program allows exceptional undergraduate students at NC State an opportunity to complete the requirements for both the Bachelor's and Master's degrees at an accelerated pace. These undergraduate students may double count up to 12 credits and obtain a non-thesis Master's degree in the same ...
Computer Network Thesis PDF - Free download as PDF File (.pdf), Text File (.txt) or read online for free. Scribd is the world's largest social reading and publishing site.
Two computer codes were developed for this purpose. The linear method of analysis uses the conventional direct stiffness method of solution and considers linear material behavior. The AASHTO moment magnifier method was used to approximate second order effects. The design forces from the linear analysis were compared with those from the TSDHPT ...
Mark Zuckerberg, CEO of Meta, said in a letter to the House Judiciary committee on Monday that his teams were "pressured" by the Biden White House to censor some content around the Covid-19 ...
Networking Projects Thesis - Free download as PDF File (.pdf), Text File (.txt) or read online for free. The document discusses the challenges students face when writing networking projects theses and introduces an organization that provides assistance with thesis writing. It states that crafting a comprehensive and well-researched thesis on networking projects requires significant time ...
Thousands of students across the country will soon be finding out their GCSE results and thinking about the next steps in their education.. Here we explain everything you need to know about the big day, from when results day is, to the current 9-1 grading scale, to what your options are if your results aren't what you're expecting.