Case study: Facebook–Cambridge Analytica data breach scandal
18 Apr 2022
Cambridge Analytica is a federal data analytics, marketing, and consulting firm based in London, UK, that is accused of illegally obtaining Facebook data and using it to determine a variety of federal crusades. These crusades include those of American Senator Ted Cruz and, to an extent, Donald Trump and the Leave-EU Brexit campaign, which resulted in the UK’s withdrawal from the EU. In 2018, the Facebook–Cambridge Analytica data scandal was a major disgrace, with Cambridge Analytica collecting the private data of millions of people’s Facebook profiles without their permission and using it for Political Advertising. It was defined as a watershed flash in the country’s understanding of private data, prompting a seventeen (17) per cent drop in Facebook’s cut-rate and summons for stricter laws governing tech companies’ usage of private data.

Background Information
Fotis International Law Firm aims to provide our readers with a brief overview of the Facebook Data Breach that happened. A lot of people took a survey in 2014 that looked similar and included not only the user’s personally identifiable information or data but also the data of the user’s Facebook friends with the Company that worked for President Trump’s 2016 campaign. This is where Cambridge Analytica (CA) entered the picture, partnering with Aleksandr Kogan, a UK research academic who was using Facebook for research purposes. Kogan’s survey, which appeared innocuous and included over 100 personality traits with which surveyees could agree or disagree, was sent to 3L Americans.
But there’s a catch: to take the survey, surveyee’s must log in or sign up for Facebook, giving Kogan access to the user’s profile, birth date, and location. Kogan created a psychometric model, which is similar to a personality profile, by combining the survey results with the user’s Facebook data. The data was then combined with voter records and sent to CA by Kogan. CA claimed that the results of this survey, combined with the personal traits of various users and models, were crucial in determining how they profiled a user’s psychoneurosis and other susceptible traits.
In only a few months, two lakh twenty thousand people took part in the survey of Kogan, and data from up to 87 million Facebook user profiles were harvested, accounting for nearly a quarter of all Facebook users in the United States. The goal was to use the data to target users/surveyees with political messaging that would aid Trump’s campaign strategy, but the campaign objected. Even though Kogan’s work was for academic research, he shared the formulated data with CA, which is against Facebook’s policy. In response to the violation, Facebook CEO Mark Zuckerberg stated that it was not a data breach because no passwords were stolen or any systems were infiltrated, but it was a violation of the terms of service. In response to the breach, the CEO of Facebook who is Mark Zuckerberg stated that it was not a data breach because no passwords were stolen or any systems were infiltrated, but rather a breach of contravention between Facebook and its users. The Federal Trade Commission of the US took up the investigation after that.
Facebook Data Breach
CA’s illegitimate procurement of personally identifiable data was first revealed in December 2015 by Harry Davies, a Guardian journalist. CA was working for US Senator Ted Cruz, according to Harry, and had obtained data from millions of Facebook accounts without their permission. Facebook declined to comment on the story other than to say that it was looking into it. The scandal finally blew up in March 2018 when a conspirator, Christopher Wylie, an ex-CA employee, was exposed. Christopher was an unidentified source for Cadwalladr’s article “The Great British Brexit Robbery” in 2017. This report was well-received, but it was met with scepticism in some quarters, prompting sceptical responses in publications such as The New York Times. In March 2018, the news organizations released their stories concurrently, causing a massive public outcry that resulted in more than $100 billion being deducted from Facebook’s retail funding in a matter of days. Senators from the US and the UK have demanded answers from Facebook CEO Mark Zuckerberg. Following the scandal, Mark Zuckerberg agreed to testify in front of the US Congress.
Summary of the Case
CA’s parent company, Strategic Communication Laboratories Group, was a private British behavioural and strategic research communication corporation. In the US and other countries, SCL sparked public outrage by obtaining data through data mining and data analysis on its users with the help of a university researcher named Aleksandr Kogan, who was tasked with developing an app called “This is your digital life” and along with that, he was told to create a survey on the behavioural patterns of users that he had obtained from Facebook’s social media users, to use the data for electoral/political purposes without the approval of Facebook or the users of Facebook, since the data was detailed enough to create a profile that implied which type of advertisement would be most effective in influencing them. Based on the findings, the data would be carefully targeted to key audience associations to change behaviour in line with SCL’s client’s objective, resulting in a breach of trust between Facebook and its users.
Legal Implications
As a result, the Facebook CEO was questioned, and the stock price dropped by seventeen (17) per cent. He was also requested to enforce strict regulations on the protection of users’ data. Users were afterwards told that the access they had provided for various applications had been withdrawn and reviewed in the settings, as well as there being audit trials on breach investigation. Meanwhile, Facebook has vowed to create an app that would require users to delete all of their Facebook web search data. CA has been the subject of multiple baseless allegations in past years, and despite the firm’s efforts to improve the record, it has been chastised for actions that are not only legal but also generally acknowledged as a routine component of internet promotion in both the federal and industrial sectors.
Julian Malins, a third-party auditor, was appointed by CA to look into the allegations of wrongdoing. According to the firm, the inquiry determined that the charges were not supported by the facts. Despite CA’s constant belief that its employees have acted ethically and lawfully, a belief that is now completely supported by Mr Malin’s declaration, the Company’s clients and suppliers have been driven away implicitly as a result of the media coverage. As a result, in May 2018, it was decided that continuing to manage the firm was no longer practicable, leaving CA with no practical alternative for bringing the firm into government.
The General Data Protection Regulation (GDPR), which had come into effect in May 2018, establishes logical data security laws across Europe. It applies to all companies that prepare private data about EU citizens, regardless of where they are situated. Processing is a comprehensive term that refers to everything linked to private data, such as how a company handles and uses data, such as settling, saving, using, and destroying it.
While many of the GDPR’s requirements are based on EU data protection regulations, the GDPR has a greater reach, more precise standards, and ample penalties. For example, it necessitates a higher level of consent for the use of certain types of data and enhances people’s rights to request and shifting their data. Failure to comply with the GDPR can result in significant penalties, including fines of up to 4% of worldwide annual income for multiple violations or infringements. In terms of policy changes, data may only be accessed by others, including developers. If permissions are granted, data settings are stricter, and a research tool is used to scrutinize the search.
Regardless matter how many changes or updates are made to specific applications, the user of that platform should be aware of the types of personal data and apps to which rights should be granted. In addition, maintaining a check, such as evaluating account activity, revoking access to illegal applications, and monitoring its settings at regular intervals, is critical to keeping their data safe and being aware of the repercussions of a breach. The case of CA is the precedent. Countries should create a legal framework that will severely restrict the operations of firms like CA and prevent the globally uncontrolled exploitation of personal data on social media. No one can guarantee that a government would resist the temptation to utilize technology for its ends. It’s quite probable that it’s going on right now.
MIT Technology Review
- Newsletters
What you need to know about the Facebook data leak
The data trove, uncovered by security researcher Alon Gal, includes phone numbers, email addresses, hometowns, full names, and birth dates.
- Charlotte Jee archive page

The news: The personal data of 533 million Facebook users in more than 106 countries was found to be freely available online last weekend. The data trove, uncovered by security researcher Alon Gal , includes phone numbers, email addresses, hometowns, full names, and birth dates. Initially, Facebook claimed that the data leak was previously reported on in 2019 and that it had patched the vulnerability that caused it that August. But in fact, it appears that Facebook did not properly disclose the breach at the time. The company finally acknowledged it on Tuesday, April 6, in a blog post by product management director Mike Clark. How it happened: In the blog post, Clark said that Facebook believes the data was scraped from people’s profiles by “malicious actors” using its contact importer tool, which uses people’s contact lists to help them find friends on Facebook. It isn’t clear exactly when the data was scraped, but Facebook says it was “prior to September 2019.” One complicating factor is that it is very common for cyber criminals to combine different data sets and sell them off in different chunks, and Facebook has had many different data breaches over the years (most famously the Cambridge Analytica scandal).
Why the timing matters: The General Data Protection Regulation came into force in European Union countries in May 2018. If this breach happened after that, Facebook could be liable for fines and enforcement action because it failed to disclose the breach to the relevant regulators within 72 hours, as the GDPR stipulates. Ireland’s Data Protection Commission is investigating the breach. In the US, Facebook signed a deal two years ago that gave it immunity from Federal Trade Commission fines for breaches before June 2019, so if the data was stolen after that, it could face action there too.
Keep Reading
Most popular, how a simple circuit could offer an alternative to energy-intensive gpus.
The creative new approach could lead to more energy-efficient machine-learning hardware.
- Sophia Chen archive page
This classic game is taking on climate change
What the New Energies edition of Catan says about climate technology today.
- Casey Crownhart archive page
An AI startup made a hyperrealistic deepfake of me that’s so good it’s scary
Synthesia's new technology is impressive but raises big questions about a world where we increasingly can’t tell what’s real.
- Melissa Heikkilä archive page
This AI-powered “black box” could make surgery safer
A new smart monitoring system could help doctors avoid mistakes—but it’s also alarming some surgeons and leading to sabotage.
- Simar Bajaj archive page
Stay connected
Get the latest updates from mit technology review.
Discover special offers, top stories, upcoming events, and more.
Thank you for submitting your email!
It looks like something went wrong.
We’re having trouble saving your preferences. Try refreshing this page and updating them one more time. If you continue to get this message, reach out to us at [email protected] with a list of newsletters you’d like to receive.
Facebook data breach: what happened and why it’s hard to know if your data was leaked
Associate Dean (Computing and Security), Edith Cowan University
Disclosure statement
Paul Haskell-Dowland does not work for, consult, own shares in or receive funding from any company or organisation that would benefit from this article, and has disclosed no relevant affiliations beyond their academic appointment.
Edith Cowan University provides funding as a member of The Conversation AU.
View all partners
Over the long weekend reports emerged of an alleged data breach, impacting half a billion Facebook users from 106 countries.
And while this figure is staggering, there’s more to the story than 533 million sets of data. This breach once again highlights how many of the systems we use aren’t designed to adequately protect our information from cyber criminals.
Nor is it always straightforward to figure out whether your data have been compromised in a breach or not.
What happened?
More than 500 million Facebook users’ details were published online on an underground website used by cyber criminals.
It quickly became clear this was not a new data breach, but an older one which had come back to haunt Facebook and the millions of users whose data are now available to purchase online.
The data breach is believed to relate to a vulnerability which Facebook reportedly fixed in August of 2019 . While the exact source of the data can’t be verified, it was likely acquired through the misuse of legitimate functions in the Facebook systems .
Such misuses can occur when a seemingly innocent feature of a website is used for an unexpected purpose by attackers, as was the case with a PayID attack in 2019.
Read more: PayID data breaches show Australia's banks need to be more vigilant to hacking
In the case of Facebook, criminals can mine Facebook’s systems for users’ personal information by using techniques which automate the process of harvesting data.
This may sound familiar. In 2018 Facebook was reeling from the Cambridge Analytica scandal . This too was not a hacking incident , but a misuse of a perfectly legitimate function of the Facebook platform.
While the data were initially obtained legitimately — as least, as far as Facebook’s rules were concerned — it was then passed on to a third party without the appropriate consent from users.
Read more: We need to talk about the data we give freely of ourselves online and why it's useful
Were you targeted?
There’s no easy way to determine if your details were breached in the recent leak. If the website concerned is acting in your best interest, you should at least receive a notification. But this isn’t guaranteed .
Even a tech-savvy user would be limited to hunting for the leaked data themselves on underground websites.
The data being sold online contain plenty of key information. According to haveibeenpwned.com, most of the records include names and genders, with many also including dates of birth, location, relationship status and employer.
Although, it has been reported only a small proportion of the stolen data contained a valid email address (about 2.5 million records).
This is important since a user’s data are less valuable without the corresponding email address. It’s the combination of date of birth, name, phone number and email which provides a useful starting point for identity theft and exploitation .
If you’re not sure why these details would be valuable to a criminal, think about how you confirm your identity over the phone with your bank, or how you last reset a password on a website.
Haveibeenpwned.com creator and web security expert Troy Hunt has said a secondary use for the data could be to enhance phishing and SMS-based spam attacks.
How to protect yourself
Given the nature of the leak, there is very little Facebook users could have done proactively to protect themselves from this breach. As the attack targeted Facebook’s systems, the responsibility for securing the data lies entirely with Facebook.
On an individual level, while you can opt to withdraw from the platform, for many this isn’t a simple option. That said, there are certain changes you can make to your social media behaviours to help reduce your risk from data breaches.
1) Ask yourself if you need to share all your information with Facebook
There are some bits of information we inevitably have to forfeit in exchange for using Facebook, including mobile numbers for new accounts (as a security measure, ironically). But there are plenty of details you can withhold to retain a modicum of control over your data.
2) Think about what you share
Apart from the leak being reported, there are plenty of other ways to harvest user data from Facebook. If you use a fake birth date on your account, you should also avoid posting birthday party photos on the real day. Even our seemingly innocent photos can reveal sensitive information.
3) Avoid using Facebook to sign in to other websites
Although the “sign-in with Facebook” feature is potentially time-saving (and reduces the number of accounts you have to maintain), it also increases potential risk to you — especially if the site you’re signing into isn’t a trusted one. If your Facebook account is compromised, the attacker will have automatic access to all the linked websites.
4) Use unique passwords
Always use a different password for each online account, even if it is a pain. Installing a password manager will help with this (and this is how I have more than 400 different passwords). While it won’t stop your data from ever being stolen, if your password for a site is leaked it will only work for that one site.
If you really want a scare, you can always download a copy of all the data Facebook has on you . This is useful if you’re considering leaving the platform and want a copy of your data before closing your account.
Read more: New evidence shows half of Australians have ditched social media at some point, but millennials lag behind
- Social media
- Online security
- Cybersecurity
- Data breaches
- Online data
- cyber criminals
Senior Research Fellow - Curtin Institute for Energy Transition (CIET)

Business Advisor

Laboratory Head - RNA Biology

Head of School, School of Arts & Social Sciences, Monash University Malaysia

Chief Operating Officer (COO)
Meta fined $276 million over Facebook data leak involving more than 533 million users
The april 2021 leak exposed the phone numbers, locations, and birthdates of facebook users on the platform from 2018 to 2019..
By Emma Roth , a news writer who covers the streaming wars, consumer tech, crypto, social media, and much more. Previously, she was a writer and editor at MUO.
Share this story
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/23951342/STK040_VRG_Illo_N_Barclay_6_facebook.jpg)
Ireland’s Data Protection Commission hit Meta with a €265 million fine (about $276 million USD) after an April 2021 data leak exposed the information of more than 533 million users. The DPC started the investigation shortly after news of the leak broke and involved an examination into whether Facebook complied with Europe’s General Data Protection Regulation (GDPR) laws.
The leaked information, spotted by Insider , was posted to an online hacking forum and included the full names, phone numbers, locations, and birthdates of users on the platform from 2018 to 2019. At the time, Meta said the bad actor obtained the information through a vulnerability that the company fixed in 2019 and that this was the same information involved in a prior leak reported by Motherboard in January 2021.
This marks the third fine the DPC imposed on Meta this year. In March, the DPC fined Meta $18.6 million USD for bad record-keeping in relation to a series of 2018 data breaches that exposed the information of up to 30 million Facebook users. The European regulator also slapped Meta with a $402 million fine in September following an investigation into Instagram’s handling of teenagers’ data.
Meta has been fined nearly $700 million by the DPC in 2022 — and that doesn’t include the $267 million fine WhatsApp incurred for violating Europe’s data privacy laws last year. In a statement obtained by Newstalk reporter Jess Kelly , an unidentified Meta spokesperson said:
We made changes to our systems during the time in question, including removing the ability to scrape our features in this way using phone numbers. Unauthorised data scraping is unacceptable and against our rules and we will continue working with our peers on this industry challenge. We are reviewing this decision carefully.
Meta didn’t immediately respond to The Verge ’s request for comment. The company highlighted what it does to combat data scraping in a blog post from last year , noting that it tasks its External Data Misuse (EDM) team with detecting, blocking, and preventing scraping.
The Light Phone 3 is a little less light — but a lot more useful
All three game console makers have now abandoned x integration, apple wwdc 2024: the 13 biggest announcements, mobile driver’s licenses are coming to new york state starting june 11th, apple intelligence: every new ai feature coming to the iphone and mac.
More from Tech
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/23925998/acastro_STK054_03.jpg)
The Nintendo Switch 2 will now reportedly arrive in 2025 instead of 2024
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/19336098/cwelch_191031_3763_0002.jpg)
The best Presidents Day deals you can already get
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/25289959/Command_Line_Site_Post_Dylan_Field_Figma.jpg)
Interview: Figma’s CEO on life after the company’s failed sale to Adobe
:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/25289972/vudu.jpg)
Vudu’s name is changing to ‘Fandango at Home’
- Get Surfshark
- Products Surfshark VPN Surfshark Antivirus Surfshark Search Surfshark Alert Alternative ID OTHER PRODUCTS Incogni
- Trust Center
- Media Center
- Cybersecurity
- All things VPN
- Internet censorship
- Entertainment
- Digital Quality of Life Index 2023
- Data breach world map
- Internet shutdowns tracker
- Smart Home Privacy Checker
- Data vulnerability thermometer
- Surfshark One
- VPN for Teams
A deep dive into the leaked data of 533 million Facebook users

On April 3rd, a security expert announced the discovery of a massive data leak that affected 533 million Facebook users. But if you’re worried about your email being compromised , you probably shouldn’t be – fewer than 10% of the profiles had their addresses exposed. On the other hand, nearly 90% of the users suffered from phone number leaks. But that’s not all, and that’s why our independent research partners dug into the details to illustrate the scope of the breach.

Now, this wasn’t a fresh leak – Facebook claims that this data was gained via a vulnerability that was patched up in August 2019 . Portions of this data had already appeared on sale in January 2021. But the full package only surfaced this month.
Overall, the leak produced 2,837,793,637 data points – meaning that the hackers, on average, exposed 5 types of data per user. “It includes their phone numbers, Facebook IDs, full names, locations, birthdates, bios, and — in some cases — email addresses,” said Vytautas Kaziukonis, CEO of Surfshark when talking about the breach.
While the big worry online is about email addresses, this is not the part that should cause the most concern as a comparatively small 4,76% of the profiles had their email addresses exposed . However, 89.01% of affected users had their phone numbers leaked .
Disclaimer: The data set for Facebook’s data breach was extremely large and complex to analyze; therefore, the probability of false positives and possible discrepancies should be taken into account.
All in all, 11 types of data points were exposed, with specifics varying from user to user. Here’s a chart that breaks it all down by type. Keep in mind that we’re counting the percentage of people affected by the breach:
Leaked data to feed SMS phishing attempts
What is the biggest, most worrying implication of this data? Its usefulness for SMS phishing . Scammers looking to impersonate actual services to steal your money and data can now match the names and the phone numbers of 89.01% of people exposed in the leak.
The data set also allows matching names and phone numbers with additional data like location (60.58%) and employer name (18.30%) that helps to both choose the targets (especially for spear-phishing attempts targeting specific companies) or to make hacking attacks more believable.
Facebook users from Egypt were the most affected
Of more than 530 million compromised profiles, 32,315,291 were American . Egypt is the definite #1 victim of this hack, with the accounts of 45,183,147 Egyptian users being exposed . In general, the top 10 countries by breaches make up 50% of all the breach cases .
If we wanted to compare which data point made up what percentage of data exposed by country, we can see that the types of data leaked are very similar worldwide. For example, phone numbers are always around 16-18% of all data points. Conversely, emails take up less than 1% of all data points per country.
This is a call for users to be more cautious of phishing attempts. Whether it’s by SMS, email, or other means, always carefully check the sender, beware of any link and file attachments, look out for tell-tale grammar mistakes, and be suspicious of both the tone of urgency and offers that are too good to be true.
Why is so much information being leaked?
Data leaks are becoming more common: from mid 2020 to mid 2021, 1 billion people worldwide were affected by information breaches . These numbers are especially concerning since the hazards come from large corporations and social media sites.
This means that people have essentially no control over the security of their data, and can’t use privacy tools like VPNs to protect themselves. Most often, these companies won’t provide their services to you unless you give them your real information.
It’s easy to tell someone to “not use such services.” But in a lot of cases, our social (social media, chatting platforms) and physical (healthcare, insurance) well-being depend on it.
Essentially, the problem boils down to people not having actual control over their privacy. Data is being collected at every corner, but is not being adequately protected.
Rate and share this article
Hand picked related articles
How to secure your email: 8 tips to keep your inbox safe.

Avoiding hackers on social media: tips and tricks for 2024

What is the best VPN for iPhone?

Your comment is awaiting moderation.
VPN deal that Rocks
- Skip to main content
- Keyboard shortcuts for audio player
After Data Breach Exposes 530 Million, Facebook Says It Will Not Notify Users

Emma Bowman

The leaked data includes personal information from 533 million Facebook users in106 countries. Olivier Douliery/AFP via Getty Images hide caption
The leaked data includes personal information from 533 million Facebook users in106 countries.
Facebook decided not to notify over 530 million of its users whose personal data was lifted in a breach sometime before August 2019 and was recently made available in a public database. Facebook also has no plans to do so, a spokesperson said.
Phone numbers, full names, locations, some email addresses, and other details from user profiles were posted to an amateur hacking forum on Saturday, Business Insider reported last week.
The leaked data includes personal information from 533 million Facebook users in 106 countries.
In response to the reporting, Facebook said in a blog post on Tuesday that "malicious actors" had scraped the data by exploiting a vulnerability in a now-defunct feature on the platform that allowed users to find each other by phone number.

National Security
After a major hack, u.s. looks to fix a cyber 'blind spot'.
The social media company said it found and fixed the issue in August 2019 and its confident the same route can no longer be used to scrape that data.
"We don't currently have plans to notify users individually," a Facebook spokesman told NPR.
According to the spokesman, the company does not have complete confidence in knowing which users would need to be notified. He also said that in deciding whether to notify users, Facebook weighed the fact that the information was publicly available and that it was not an issue that users could fix themselves.
The information did not include financial information, health information or passwords, Facebook said, but the data leak still leaves users vulnerable, security experts say.
"Scammers can do an enormous amount with little information from us," says CyberScout founder Adam Levin, a cybersecurity expert and consumer protection advocate. In the case of this breach, he said, "It's serious when phone numbers are out there. The danger when you have phone numbers in particular is a universal identifier."
Phone numbers are increasingly used to connect people to their digital presence, including the use of two-factor authentication via text message and phone calls to verify one's identity.

FTC To Hold Facebook CEO Mark Zuckerberg Liable For Any Future Privacy Violations
The misuse of its user data is a familiar battle for Facebook, and its handling of user privacy has endured scrutiny.
In July 2019, months before patching up the aforementioned issue, Facebook reached a $5 billion settlement with the U.S. Federal Trade Commission for violating an agreement with the agency to protect user privacy.
To find out whether your personal information was leaked in the breach, you can check the data tracking tool, HaveIBeenPwnd . Its creator, Troy Hunt, updated the site with the latest data from the Facebook leak. Hunt said that 65% of the latest batch of data had already been added to the tracker from previous leaks.
Editor's note: Facebook is among NPR's financial supporters.
To revisit this article, visit My Profile, then View saved stories .
- Backchannel
- Newsletters
- WIRED Insider
- WIRED Consulting
Issie Lapowsky
Facebook Exposed 87 Million Users to Cambridge Analytica

Facebook now says the data firm Cambridge Analytica gained unauthorized access to up to 87 million users' data, mainly in the United States. This figure is far higher than the 50 million users that were previously reported.
Facebook's chief technology officer Mike Schroepfer shared this figure at the end of a lengthy—and somewhat unrelated— blog post Wednesday that laid out a slew of changes Facebook is making to restrict access to user data.
"In total, we believe the Facebook information of up to 87 million people—mostly in the US—may have been improperly shared with Cambridge Analytica," Schroepfer wrote toward the bottom of the post. Schroepfer noted that beginning April 9, Facebook will make it possible for users to see if their data was exposed to Cambridge Analytica. Unlike the well-hidden tool Facebook created to tell users whether they'd interacted with Russian trolls in the past, the new Cambridge Analytica disclosure will appear at the top of users' News Feeds.
In mid-March The New York Times , along with The Guardian and The Observer , reported that Cambridge Analytica and its British counterpart SCL had harvested the data of 50 million Facebook users through an app called thisisyourdigitallife, which offered personality quizzes. At the time, when Facebook users installed apps connected to the platform, they also exposed data from many of their friends to the app developer. When the news broke, Facebook confirmed only that 270,000 people had downloaded that app, but until now had never refuted reports that 50 million users' data had been accessed.
Facebook CEO Mark Zuckerberg, who is scheduled to testify before the House Energy and Commerce Committee next week, addressed the updated numbers in a call with reporters Wednesday afternoon. Zuckerberg explained that over the last few days, the company took stock of all of the people who used the thisisyourdigitallife app and analyzed the maximum number of friends they had during the period of time when the app was live. "We didn't put out the 50 million number. That came from other parties. We wanted to wait until we had the full understanding," Zuckerberg explained, adding, "I'm quite confident it’s not more than 87 million."
This is not the first time Facebook has had to publicly increase previous estimates of misdoings on its platform. On Tuesday, as news broke of an active shooting at YouTube's San Bruno headquarters , Facebook published another blog post announcing it had uncovered and shut down nearly 300 additional Facebook and Instagram accounts and pages linked to the Russian propaganda group Internet Research Agency . It has also previously left Instagram out of its published numbers of how many people were exposed to Russian propaganda, only to update those figures without public notice later.
While Facebook has cracked down specifically on Cambridge Analytica, it is clear that company is only a convenient example of a far more pervasive problem.
"By tacking 37 million more people to an API-focused news update from the CTO, Facebook's willingness to obscure and bury key details about the inappropriate use of their platform continues," says Jonathan Albright, research director at Columbia University's Tow Center for Digital Journalism, who has become one of Facebook's chief watchdogs and critics. Albright was the first to suggest that Russian propaganda had reached millions more people than the initial 10 million Facebook initially acknowledged last fall.
In addition to fleshing out the new disclosure about Cambridge Analtyica, Zuckerberg also spoke with reporters about the changes Facebook has made regarding data access recently, including new restrictions to its APIs which previously allowed app developers to scrape data on everything from people’s religious preference and political affiliation to the guests lists of the events they RSVPed to. Going forward, Facebook will individually approve any app that asks users to share their check-ins, likes, photos, posts, videos, events, and groups. It will also prevent apps from using Facebook Login to collect users’ personal information, including details like their religious or political views, relationship status, education and work history, and more.
Zuckerberg also noted that the company is shutting down the ability to search for users' profiles by using their phone numbers. In an alarming revelation, he said that recent investigations into data privacy have revealed malicious actors cycling through hundreds of thousands of IP addresses in order to search for users by their phone numbers and scrape their public profile information. Until now, users have had to opt out of making their profiles searchable by phone number. Most, Zuckerberg said, never opted out.

By Mark Harris

By Adam Bumas

By Boone Ashworth

By Christopher Null
"It's reasonable to expect if you had that setting turned on that at some point in the last several years, someone has accessed your public information," Zuckerberg said.
Though the CEO accepted blame for all of these data privacy and trust issues, saying, "It was my mistake," he also often put the onus on Facebook users to know better. He mentioned, for instance, that the only information that bad actors would be able to scrape using a phone number was information that was public on Facebook user profiles. Of the researcher who built the data-scraping app for Cambridge Analytica, Zuckerberg said, "Yes, he broke the policy, he broke people’s expectations, but also, people chose to share that data with him."
And yet it was Zuckerberg and the company he built that made people's data privacy settings so open by default, and made it difficult to find, understand, and adjust those settings . It was Facebook that made it possible for app developers to ask users for so much of their data as the cost of admission. And it was Zuckerberg and his lieutenants that failed to take action for over a year after finding out that one—but likely more—of those app developers misused that valuable data.
Just as the culture that created the Cambridge Analytica scandal took years to develop, Zuckerberg acknowledged it will take at least as long to undo. "I wish I could snap my fingers and in six months or even two months have solved all of these issues," Zuckerberg said. "I do think this is a multi-year effort."
- The Cambridge Analytica scandal has continued to evolve since it was first reported weeks ago
- Facebook had previously avoided identifying how many people followed Russian propaganda on Instagram altogether
- If all this leaves you wanting to adjust your privacy settings—or delete Facebook altogether—here's how

Luca Zorloni

Morgan Meaker

Louise Matsakis

Paresh Dave

Caroline Haskins

Will Knight

Lauren Goode

Partner Overview
Join Us for Growth, Innovation and Cybersecurity Excellence.
Become a Channel Partner
Be a Valued Partner and Embark on a Journey of Profitability.
Partner Portal
Unified Security Platform
Latest Content and Resources
Threat Report 2023
NRGi Holding Case Study
Everything You Need to Know About the 2021 Facebook Data Breach
Why the 2021 Facebook Data Breach Is A Serious Matter and How You Can Protect Your Personal Information.
Last updated on May 6, 2021

Earlier this month, it was revealed that the personal information of 533 million Facebook users, approximately 20% of all accounts, was leaked online.
Although the data is 2 years old, the 2021 Facebook data breach is an extremely serious matter, since the leaked data is still valuable to cybercriminals who use people’s personal information to impersonate them or scam them into handing over login credentials.
Personal data from over 500M Facebook users leaked online https://t.co/WW8JWeA3A0 by @joseadorno — 9to5Mac.com (@9to5mac) April 3, 2021
What Kind of Data Was Leaked and How Was It Done?
Private information of users was primarily obtained by exploiting Facebook’s contact importer feature that allows users to find friends on the social media app using their phone’s contact list.
The publicly accessible database had personal details of Facebook users with phone numbers, Facebook IDs, full names, locations, birthdates, bios, and, in some cases, email addresses. Even Facebook CEO Mark Zuckerberg’s own private credentials were reportedly leaked in the process.
Threat actors then leaked this data on the dark web. Information on users’ finance and password were not divulged.
According to Business Insider, a Facebook spokesperson confirmed that the data had been scraped due to a vulnerability that the company patched in 2019 . Facebook said it fixed the contact importer flaw after it discovered it was being exploited. The company said that it’s important to mention that attackers did not hack its systems by injecting malicious code that would weaken the company’s security defenses. Instead, the attackers scraped the data from its service.
Scraping data using features meant to help people violates our terms. We have teams across the company working to detect and stop these behaviors. We’re focused on protecting people’s data by working to get this data set taken down and will continue to aggressively go after malicious actors who misuse our tools wherever possible.
Critics allege that this is nothing more than Facebook’s attempt to downplay the severity of the leak. Facebook apologized for the 2019 data loss, but never directly informed users their accounts had been compromised.
Hudson Rock ’s Chief Technology Officer Alon Gal said that the leaked data could benefit cybercriminals who use people’s personal information to impersonate them or scam them into handing over login credentials.
Gal is the one who discovered the leak in January when a user in the same hacking forum advertised an automated bot that could provide phone numbers for hundreds of millions of Facebook users for money.
All 533,000,000 Facebook records were just leaked for free. This means that if you have a Facebook account, it is extremely likely the phone number used for the account was leaked. I have yet to see Facebook acknowledging this absolute negligence of your data. https://t.co/ysGCPZm5U3 pic.twitter.com/nM0Fu4GDY8 — Alon Gal (Under the Breach) (@UnderTheBreach) April 3, 2021
How Is Facebook’s 2021 Leak Unique?
The personal information that was leaked online included over 32 million records on users in the U.S., 11.5 million in the U.K., and 6 million in India.
The 2021 Facebook data breach is similar to LinkedIn’s security incident where data from over 500 million users has been sold online by an unknown hacker who had dumped two million users’ data as proof.
According to Raj Samani, Chief Scientist at cybersecurity firm McAfee, in the case of LinkedIn, it was affirmed that data was scraped, meaning someone violated the terms of service to gather public profile data and data from other websites.
The information leaked is in many ways similar to the Facebook incident, but it contains other professional information that might add another layer of sensitivity, Samani says.
Facebook’s stolen data first appeared on a hacking community in June 2020 when a member began selling the Facebook data to other members, but what made the leak stand out was the fact that the data contained member information that can be scraped from public profiles and private mobile numbers associated with the accounts.
How Can the Leaked Data Be Used?
Alon Gal confirmed that data from the 2021 Facebook data breach was now being sold on multiple groups on the cloud-based messaging app Telegram. What’s more, the data set seems to appear on various hacker forums all over the Internet.
The stolen information can be used for email fraud , scam phone calls , phishing attacks , SIM swapping , and target advertising. It can be used to plot and execute various nefarious online fraud schemes. Hackers can impersonate users and make money transfers on their behalf, without their knowledge or approval.
The database of private information is available on the dark web for anyone to sift through.
All Facebook users should be wary of strange emails or texts that are requesting further information or instructing the user to click on enclosed links.
How to Protect Your Data
Everyone is talking about the 2021 Facebook data breach and we all should take a few moments of reflection about the privacy of our data on the Internet. Users even started deleting their Facebook accounts following the leak, urging people to leave the social network, while others may be really concerned about the exploitation of personal data.
Users seeking to know whether their data has been leaked or compromised can visit HaveIBeenPwned.com . The website was updated to show compromised phone numbers and emails. All they have to do is to key in their email ID and check.
If you’re among the people who were impacted by the data leak, the first thing you should do is update your password. You can use a security service like 1Password to help manage multiple, strong passwords across different apps.
Facebook also recommended that users should enable two-factor authentication on their accounts in order to access them, as a means of protection.
The FB breach has certainly generated some interest, currently doing 40k-45k requests per min on @haveibeenpwned (up about 6x on normal baseline traffic) pic.twitter.com/Rpa8itUwsh — Troy Hunt (@troyhunt) April 4, 2021
It is understandable that Facebook users are becoming more and more frustrated with yet another report of mismanaged data. They are tired of apologies followed by statements about how seriously the social media giant takes their privacy.
However, if you aren’t ready to delete your Facebook account, or you don’t see this as a viable solution, please check my colleague’s article on how to use Facebook in the safest way and take control of privacy settings.
It’s worth reminding that Facebook will (still) know things about you, but at least you can limit its access to your private data.
Final Thoughts
Facebook has a long history of failing to protect customer data and has been in the news for massive breaches that seem to be getting bigger each year.
The news about the Cambridge Analytica firm harvesting personal data taken from millions of Facebook without user consent hit the headlines back in 2015 when the third-party app developer improperly harvested data on 87 million users. The same data was used to micro-target voters in the 2016 U.S. presidential election and British Brexit voters. Facebook was fined by U.S. and British regulators for mishandling user data and changed its policy around the information shared with third-party app developers.
As for the 2021 Facebook data breach, Cory Doctorow of the Electronic Frontier Foundation (EFF) said dominance in the tech industry directly contributed to hacks like these.
Privacy does not come from monopoly. Facebook’s data breach problems are the inevitable result of monopoly, in particular the knowledge that it can heap endless abuses on its users and retain them.
Ireland’s Data Protection Commission, which is the European Union’s lead regulator for Facebook, said it had contacted the company about the data leak, but received “no proactive communication from Facebook”. However, they are now in contact.
Cezarina Dinu
Head of Marketing Communications & PR
Cezarina is the Head of Marketing Communications and PR within Heimdal® and a cybersecurity enthusiast who loves bringing her background in content marketing, UX, and data analysis together into one job. She has a fondness for all things SEO and is always open to receiving suggestions, comments, or questions.
Related Articles
Hello, there have been impersonators and my identity stolen on Facebook, whom they continue to use my data and make stores and subdomains opening and use my artwork since 2019, and I have tried everything I cannot even contact Facebook because of my framework on my identity. I, if anyone deserve to be compensated, and have a right to speak! I don’t know how to get ahold of them because I am rerouted always!! My phone is also hacked, so is my Google identity. But this is so stressful! I just wanted to say how unfairly I’ve been treated, especially from government and Google and Facebook. Those are the 2 major people who I cannot seem to get help from and they address me as a 13 year old child. Also BOOST MOBILE, I told them and they didn’t even MENTION A BREACH TO ME!! So I have no choice but to keep letting it happen! I’d like to take a course so I can learn more on how to protect myself. I’ve been studying now for a year.. still not there yet!!
I can’t log in my fb account
Leave a Reply (Cancel Reply)
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
CHECK OUR SUITE OF 11 CYBERSECURITY SOLUTIONS
- Cyber Resources And Beginners
- Cyber Security Glossary
- The Daily Security Tip
- Cyber Security For Small Business Owners
- Cybersecurity Webinars
- About Heimdal®
- Press Center
- Partner with us
- Affiliate Program
© 2024 Heimdal ®
Vat No. 35802495, Vester Farimagsgade 1, 2 Sal, 1606 København V

Facebook is garnering headlines for another data leak putting users' privacy at risk. The latest incident involves the personal information of 533 million Facebook users from 106 different countries as apparently discovered by Alon Gal, co-founder and CTO of cybercrime intelligence firm Hudson Rock .
In an April 3 tweet , Gal said the data, which includes Facebook members' account creation date, bio, birthdate, Facebook IT, full name, location, past location and relationship status, has been made available free to members of a hacking forum.
In a January 14 post, he said an early 2020 vulnerability that exposed the phone numbers linked to every Facebook account had been exploited and that a hacker had advertised a paid bot that would allow users to query the database. Facebook claims the data must have been scraped prior to September 2019, before the vulnerability was addressed.
Facebook has no plans to notify individuals whose information was exposed because the company claims it does not know who was affected. Despite the patch in September 2019, 419 million records were leaked which contained user IDs and phone numbers that same month . Then in December 2019, a Ukrainian researcher discovered a database on the open Internet which included the personal information of more than 267 million Facebook users.
Interestingly, in July 2019, the FTC announced that it had completed a year-long investigation and concluded that Facebook had "used deceptive disclosures and settings to undermine users' privacy preferences" in violation of a 2012 FTC order . Specifically, third-party apps were allowed to collect the personal information of Facebook members whose friends had downloaded the apps.
According to the new 20-year settlement order :
With more than 140,000 members, Cyber Security Hub is the vibrant community connecting cyber security professionals around the world.
- Facebook must pay a $5 bn fine which the FTC claims is unprecedented.
- Facebook's board must form an independent privacy committee "removing unfettered control by Facebook's CEO Mark Zuckerberg over decisions affecting user privacy."
- Zuckerberg and Facebook compliance officers must independently file certifications with the FTC quarterly, which state the company is complying with the order.
- A third-party assessor must make biennial assessments of Facebook's privacy program to identify any gaps and report to the new privacy board on a quarterly basis.
- The FTC can monitor Facebook's compliance using discovery tools provided by the Federal Rules of Civil Procedure .
- Every new or modified Facebook, Instagram, or WhatsApps product, service or practice must undergo a privacy review before it's implemented.
- If the data of 500 or more users has been compromised by a breach, the incident must be documented and shared with the FTC and the assessor within 20 days of the incident.
Other requirements can be found here , but yet another database of Facebook user information was just discovered .
Data privacy is a serious issue that organizations need to address proactively. While behemoths like Facebook can weather a $5 bn fine , lesser fines could be fatal to smaller organizations. A responsible approach to privacy should include:
- Privacy by design so the right guardrails are built into products and services.
- Penetration testing to identify weak areas.
- Patching to avoid unnecessary vulnerabilities.
- Board-level oversight to ensure that privacy is given the attention it deserves.
- Compliance officers or a compliance officer, depending on the size of the company, whose job it is to ensure compliance.
- Data governance to avoid data misuse.
- Continuous monitoring to prevent or minimize data exfiltration.
- Scenario planning in case a breach occurs.
- A plan to notify affected victims and law enforcement should a PII leak occur.
- Ongoing security awareness training for IT and non-technical personnel to reduce the risk of inadvertent mistakes.
FIND CONTENT BY TYPE
- Case Studies
- White Papers
Cyber Security Hub COMMUNITY
- Advertise with us
- Cookie Policy
- User Agreement
- Become a Contributor
- All Access from CS Hub
- Become a Member Today
- Media Partners
ADVERTISE WITH US
Reach Cyber Security professionals through cost-effective marketing opportunities to deliver your message, position yourself as a thought leader, and introduce new products, techniques and strategies to the market.
JOIN THE Cyber Security Hub COMMUNITY
Join CSHUB today and interact with a vibrant network of professionals, keeping up to date with the industry by accessing our wealth of articles, videos, live conferences and more.

Cyber Security Hub, a division of IQPC
Careers With IQPC | Contact Us | About Us | Cookie Policy
Become a Member today!
PLEASE ENTER YOUR EMAIL TO JOIN FOR FREE
Already an IQPC Community Member? Sign in Here or Forgot Password Sign up now and get FREE access to our extensive library of reports, infographics, whitepapers, webinars and online events from the world’s foremost thought leaders.
We respect your privacy, by clicking 'Subscribe' you will receive our e-newsletter, including information on Podcasts, Webinars, event discounts, online learning opportunities and agree to our User Agreement. You have the right to object. For further information on how we process and monitor your personal data click here . You can unsubscribe at any time.
Watch CBS News
Hundreds of millions of Facebook user records were exposed on Amazon cloud server
By Jason Silverstein
Updated on: April 4, 2019 / 11:35 AM EDT / CBS News
More than 540 million records about Facebook users were publicly exposed on Amazon's cloud computing service, according to a cybersecurity research firm. A report out Wednesday by UpGuard said two third-party Facebook app developers posted the records in plain sight, causing yet another major data breach for the world's biggest social network.
According to UpGuard, a Mexico-based media company called Cultura Colectiva was responsible for the biggest leak. It exposed 146 gigabytes of Facebook user data, including account names, IDs and details about comments and reactions to posts. It's unclear how many individual users had data exposed.
Separately, an app called At the Pool exposed databases that appeared to include data about user IDs, friends, photos and location check ins, as well as unprotected Facebook passwords for 22,000 users. The app — which was meant to help people meet up for offline activities — shut down in 2014.
- Facebook extends hate speech ban to include white nationalism
UpGuard said it alerted Cultura Colectiva and Amazon about the breaches from Cultura Colectiva in January, but no action was taken until Wednesday morning. After Bloomberg reached out to Facebook for a comment about that breach, an Amazon "storage bucket" with the data from Cultura Colectiva was secured.
The data from At the Pool went offline before UpGuard reached out about it.
Facebook is under federal criminal investigation for deals it struck with electronics manufacturers to access user data, and it has been hit a series of security breaches over the past year. The British analytics firm Cambridge Analytica, which worked with the Trump campaign in the 2016 election, got access to data from more than 87 million users ; and Facebook last September said that an attack on its networks exposed information from nearly 50 million users. Facebook said it has more than 2.3 billion active monthly users worldwide.
- Mark Zuckerberg
- Cambridge Analytica
Jason Silverstein is the supervising politics producer for the CBS News social media team, working with teams in New York and Washington, D.C. to oversee coverage of national politics and the 2024 campaign.
More from CBS News

At least 49 killed as boat carrying migrants sinks off Yemen, U.N. says

Fed set to make another decision on rates. What are the odds of a cut?

National Amusements ends Paramount merger talks with Skydance Media

Councilwoman shot dead outside her home in Mexico
BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more

Losing Face: Two More Cases of Third-Party Facebook App Data Exposure

UpGuard Team
Table of contents, join 27,000+ cybersecurity newsletter subscribers.
The UpGuard Cyber Risk team can now report that two more third-party developed Facebook app datasets have been found exposed to the public internet. One, originating from the Mexico-based media company Cultura Colectiva , weighs in at 146 gigabytes and contains over 540 million records detailing comments, likes, reactions, account names, FB IDs and more. This same type of collection, in similarly concentrated form, has been cause for concern in the recent past , given the potential uses of such data.
A separate backup from a Facebook-integrated app titled “At the Pool” was also found exposed to the public internet via an Amazon S3 bucket. This database backup contained columns for fk_user_id, fb_user, fb_friends, fb_likes, fb_music, fb_movies, fb_books, fb_photos, fb_events, fb_groups, fb+checkins, fb_interests, password, and more. The passwords are presumably for the “At the Pool” app rather than for the user’s Facebook account, but would put users at risk who have reused the same password across accounts.

The At the Pool discovery is not as large as the Cultura Colectiva dataset, but it contains plaintext (i.e. unprotected) passwords for 22,000 users. At the Pool ceased operation in 2014 (last non-redirect web archived capture here ), and even the parent company’s website is currently returning a 404 error notice. This should offer little consolation to the app’s end users whose names, passwords, email addresses, Facebook IDs, and other details were openly exposed for an unknown period of time.

Each of the data sets was stored in its own Amazon S3 bucket configured to allow public download of files.
The data sets vary in when they were last updated, the data points present, and the number of unique individuals in each. What ties them together is that they both contain data about Facebook users, describing their interests, relationships, and interactions, that were available to third party developers. As Facebook faces scrutiny over its data stewardship practices, they have made efforts to reduce third party access. But as these exposures show, the data genie cannot be put back in the bottle. Data about Facebook users has been spread far beyond the bounds of what Facebook can control today. Combine that plenitude of personal data with storage technologies that are often misconfigured for public access, and the result is a long tail of data about Facebook users that continues to leak.

Incident Response
These two separate discoveries demonstrated two polar opposite ends of the spectrum when it comes to the ease, or difficulty, of seeing them secured. With regard to the Cultura Colectiva data, our first notification email went out to Cultura Colectiva on January 10th, 2019. The second email to them went out on January 14th. To this day there has been no response.
Due to the data being stored in Amazon’s S3 cloud storage, we then notified Amazon Web Services of the situation on January 28th. AWS sent a response on February 1st informing us that the bucket’s owner was made aware of the exposure.
When February 21st rolled around and the data was still not secured, we again sent an email to Amazon Web Services. AWS again responded on that same day stating they would look into further potential ways to handle the situation.
It was not until the morning of April 3rd, 2019, after Facebook was contacted by Bloomberg for comment, that the database backup, inside an AWS S3 storage bucket titled “cc-datalake,” was finally secured.
On the flip side of the coin, the data stemming from “At the Pool” had been taken offline during the time UpGuard was looking into the likely data origin, and prior to a formal notification email being sent. It is unknown if this is a coincidence, if there was a hosting period lapse, or if a responsible party became aware of the exposure at that time. Regardless, the application is no longer active and all signs point to its parent company having shut down.
These two situations speak to the inherent problem of mass information collection: the data doesn’t naturally go away, and a derelict storage location may or may not be given the attention it requires.
For app developers on Facebook, part of the platform’s appeal is access to some slice of the data generated by and about Facebook users. For Cultura Colectiva, data on responses to each post allows them to tune an algorithm for predicting which future content will generate the most traffic. The data exposed in each of these sets would not exist without Facebook, yet these data sets are no longer under Facebook’s control. In each case, the Facebook platform facilitated the collection of data about individuals and its transfer to third parties, who became responsible for its security. The surface area for protecting the data of Facebook users is thus vast and heterogenous, and the responsibility for securing it lies with millions of app developers who have built on its platform.
How UpGuard can help detect and prevent data breaches and data leaks
Companies like Intercontinental Exchange , Taylor Fry , The New York Stock Exchange , IAG, First State Super, Akamai, Morningstar, and NASA use UpGuard's security ratings to protect their data, prevent data breaches and assess their security posture.
UpGuard Vendor Risk can minimize the amount of time your organization spends assessing related and third-party information security controls by automating vendor questionnaires and providing vendor questionnaire templates .
We can help you continuously monitor your vendors' external security controls and provide an unbiased security rating.
We can also help you instantly benchmark your current and potential vendors against their industry, so you can see how they stack up.
For the assessment of your information security controls, UpGuard BreachSight can monitor your organization for 70+ security controls providing a simple, easy-to-understand security rating and automatically detect leaked credentials and data exposures in S3 buckets, Rsync servers, GitHub repos and more.
The major difference between UpGuard and other security ratings vendors is that there is very public evidence of our expertise in preventing data breaches and data leaks .
Our expertise has been featured in the likes of The New York Times , The Wall Street Journal , Bloomberg , The Washington Post , Forbes , Reuters , and TechCrunch.
You can read more about what our customers are saying on Gartner reviews , and read our customer case studies here .
If you'd like to see your organization's security rating, click here to request your free security rating .
Book a demo of the UpGuard platform today .
Protect your organization
Related breaches.

Florida County Database Mistake: Election Officials’ Logins Among Exposed Data

By Design: How Default Permissions on Microsoft Power Apps Exposed Millions

Student Applications: How an Education Software Company Exposed Millions of Files
%20(1).jpg)
Veritone AI: How Two Open Servers Exposed US Government Data
.jpg)
Stolen Data: National PTA Database Available on Dark Web

Cloud Leak: How A Verizon Partner Exposed Millions of Customer Accounts
Sign up for our newsletter, free instant security score, how secure is your organization.
- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity
- Entertainment
Data Of One Lakh Facebook Users Leaked, Cyber Security Researchers Gave Shocking Information
Cyber security researchers have provided information about a data leak involving Facebook users’ data. According to the latest report by IANS, this data leak includes data from at least one lakh Facebook users, which has surfaced on the breach forum.
Facebook Users’ Data Leaked
The team of CyberPeace, a New Delhi-based non-profit organization, has alleged that data of 1,00,000 new users from Facebook has surfaced on the breach forum. CyberPeace has said this tampered data includes full name, profile, email, phone number and location information.
What Will Happen Due To Leakage Of Personal Information
The leak of Facebook users’ personal information will directly mean that these people can become victims of phishing attacks. Cybercriminals can also use their information to commit crimes. According to the latest report, the people who leaked Facebook users’ data have not been identified yet.
What Did Facebook Say On The Matter
Facebook has not yet commented on CyberPeace’s claims. Researchers say an investigation is being conducted to determine whether the breach was carried out by a cybercriminal group or someone who performs online malware activities.
Cybersecurity Researchers Expressed Concern
Cybersecurity researchers have said that Facebook is facing reputational damage due to growing concerns about data security, affecting users’ trust. This data breach highlights the challenges cyber threats pose in the digital sector.
Researchers have said that this incident emphasizes the need for organizations to strengthen further cybersecurity measures to protect users’ data and maintain public trust.
Latest News
Anushka sharma danced on india’s victory, celebrated pakistan’s defeat like this.

This One Over Proved Costly For Pakistan, Babar’s Army Lost The Winning Match

Mumbai Braces for Heavy Rains, Red Alert Issued for Parts of Maharashtra

Google Slides Gets New Features, Now Work Will Become Easier Than Before

Big News For HDFC Bank Customers; These Services Will Remain Closed Today and On June 16
Stay connected.
Sign in to your account
Username or Email Address
Remember Me

- Advanced Search
Lessons learned from studying third-party data leaks in web services
Department of Computing, University of Turku, Finland
New Citation Alert added!
This alert has been successfully added and will be sent to:
You will be notified whenever a record that you have chosen has been cited.
To manage your alert preferences, click on the button below.
New Citation Alert!
Please log in to your account
- Publisher Site
- View all Formats
ICISE 2023: 2023 8th International Conference on Information Systems Engineering

The rise of digitalization has led to a surge in the utilization of web services. Online services offer a convenient way to carry out many everyday tasks. However, third-party web analytics used in many essential web services cause privacy issues as confidential personal data may inadvertently be transmitted to these third parties. In this paper, we examine the reasons for third-party data leaks in web-based services from a software engineering point of view based on our earlier studies as well as the existing literature. We also offer several recommendations and guidelines for developers to alleviate these privacy issues in the future.
Index Terms
Security and privacy
Software and application security
Web application security
Recommendations
From whistle to echo: data leaks in web-based whistleblowing channels.
Whistleblowing refers to reporting misconduct to responsible authorities. With accelerating digitalization and the European Union’s new whistleblower directive, large numbers of whistleblowing channels and company web pages that act as gateways to ...
How not to design an online pharmacy: A case study
In today’s digitized society, essential web-based healthcare services such as online pharmacies play a crucial role. This paper presents a case study on the third-party services used in an online pharmacy. We perform a network traffic analysis for the ...
Alternative to third-party cookies: investigating persistent PII leakage-based web tracking
Many popular websites give users the ability to sign up for their services, which requires personally identifiable information (PII). However, these websites embed third-party tracking and advertising resources, and as a consequence, the authentication ...
Login options
Check if you have access through your login credentials or your institution to get full access on this article.
Full Access
- Information
- Contributors
Published in

Copyright © 2023 Owner/Author
This work is licensed under a Creative Commons Attribution-NoDerivatives International 4.0 License.
In-Cooperation
Association for Computing Machinery
New York, NY, United States

Publication History
- Published: 11 June 2024
Check for updates
Author tags.
- online privacy
- third parties
- web security
- research-article
- Refereed limited
Funding Sources
Other metrics.
- Bibliometrics
- Citations 0
Article Metrics
- 0 Total Citations View Citations
- 0 Total Downloads
- Downloads (Last 12 months) 0
- Downloads (Last 6 weeks) 0
This publication has not been cited yet
View or Download as a PDF file.
View online with eReader.
Digital Edition
View this article in digital edition.
HTML Format
View this article in HTML Format .
Share this Publication link
https://dl.acm.org/doi/abs/10.1145/3641032.3641043
Share on Social Media
- 0 References
Export Citations
- Please download or close your previous search result export first before starting a new bulk export. Preview is not available. By clicking download, a status dialog will open to start the export process. The process may take a few minutes but once it finishes a file will be downloadable from your browser. You may continue to browse the DL while the export process is in progress. Download
- Download citation
- Copy citation
We are preparing your search results for download ...
We will inform you here when the file is ready.
Your file of search results citations is now ready.
Your search export query has expired. Please try again.
- WWDC 2024: Everything announced
- Summer Game Fest 2024
- Amazon Prime Day is coming in July
- Samsung Galaxy Watch AI features
- 13-inch MacBook Air M2 deal
Leaked Google database reveals its secret privacy and security failures
The company confirmed to engadget the authenticity of the data, acquired by 404 media..
A collection of leaked internal Google privacy cases provides a rare glimpse into the company’s volume and handling of breaches, accidents and other incidents. 404 Media obtained and pored through the database, which covers thousands of internally flagged privacy and security issues from 2013 to 2018.
Google verified the trove’s authenticity with Engadget but claimed some of the reports were related to third-party services or didn’t end up being cause for concern. “At Google employees can quickly flag potential product issues for review by the relevant teams,” a company spokesperson wrote to Engadget. “When an employee submits the flag they suggest the priority level to the reviewer. The reports obtained by 404 are from over six years ago and are examples of these flags — every one was reviewed and resolved at that time. In some cases, these employee flags turned out not to be issues at all or were issues that employees found in third party services.”
404 Media writes that, when taken on an individual level, many cases only impacted a few people or were fixed quickly. “Taken as a whole, though, the internal database shows how one of the most powerful and important companies in the world manages, and often mismanages, a staggering amount of personal, sensitive data on people’s lives,” 404 Media ’s Joseph Cox wrote.
Examples include a potential security issue where a government client of a Google cloud service had its sensitive data accidentally transitioned to a consumer-level product. Google’s internal report added that, as a consequence, a US-based location for the data was “no longer guaranteed for this customer,” according to the report.
In 2016, another case flagged a glitch in Google Street View, where a filter in the service’s transcription software designed to omit captured license plate numbers failed to do its job. “As a result, our database of objects detected from Street View now inadvertently contains a database of geolocated license plate numbers and license plate number fragments,” the report acquired by 404 Media details. (Oops!) That report said the data was purged.
Another incident highlighted a case where a bug in a Google speech service accidentally captured and logged an estimated 1,000 hours of children’s speech data for about an hour. That case report claimed the team deleted all of the data.
Other cases in the database range from “a person” modifying customer accounts on Google’s ad platform to manipulate affiliate tracking codes to YouTube recommending videos based on users’ deleted watch histories. One report even highlights how a Google employee (unintentionally, according to the report) accessed Nintendo’s private YouTube videos and leaked info ahead of the video game company’s announcements.
The full report from 404 Media , which details more of the internal reports, is worth reading for anyone curious about the types of privacy and security incidents a company of Google’s magnitude faces — or causes itself — and how it addresses them.
- Advertisement
- Kitchen & Household
You May Not Be Able to Smell Your Gas Stove Leaking, New Data Shows
The alarming new study shows natural gas odorant is insufficient and inconsistent, and that a significant number of leaks are undetectable by an average sense of smell.

A new study shows that a sizable number of gas leaks are undetectable to the average nose.
It's more bad news for owners of natural gas stoves. Another alarming study has been published calling into question the safety of natural gas. The peer-reviewed research conducted by PSE Healthy Energy and Stanford University found that natural gas odorant levels were not standardized and odorant was often underused to a degree that someone with "an average sense of smell" could not detect a leak.
Odorant is added to natural gas, sometimes called methane gas, before being pumped into homes and acts as the only real line of defense against toxic leaks.
Researchers collected and analyzed 587 samples of natural gas from 481 residences through 17 North American cities. Samples were tested for methane, benzene, hazardous air pollutants and sulfur-based odorants. Researchers modeled the amount of gas that could leak undetected by a resident with an average sense of smell.

It's more bad news for owners of natural gas stoves.
CNET spoke with an administrator of the study, PSE scientist Sebastian Rowland, who said plainly that the inconsistent and often too low levels of odorant found in natural gas is "a major cause for concern" and another in a long line of reported hazards related to natural gas.
"While these smaller leaks are not large enough to cause gas explosions, hard-to-smell leaks are common," Rowland said. "The fact that they are so small makes them hard to identify and fix, which can lead to a persistent indoor source of benzene and methane."
Rowland stopped short of calling for a ban on natural gas but stressed that these studies should be taken seriously and those with natural gas stoves would be wise to enact precautions against tainted breathing air.
Benzene levels in Vancouver are 50 times greater than some cities

A 2022 study found that gas stoves were leaking more than previously thought.
The study also showed major discrepancies in the amount of benzene present in natural gas across North American cities. On average, gas delivered to homes in Vancouver, Los Angeles, Calgary and Denver had twice the benzene levels of other cities. Benzene levels in Vancouver were particularly high, nearly 50 times greater than that of Boston, the city with the lowest concentration.
Benzene is a chemical found in natural gas known to cause respiratory complications, acute myeloid leukemia and non-Hodgkin lymphoma.
Read more: Two Shocking Studies That Likely Sparked a Gas Stove Ban Debate
Study after study shows natural gas stoves may be dangerous

Natural gas stoves have come under fire in the past several years.
Other studies published in the last several years have called into question the safety of natural gas in the home. One found natural gas stoves to leak more than previously thought, while another study showed that elevated levels of natural gas in the home led to increased cases of childhood asthma. Just this May, Stanford published a study showing the risk to be far greater among those who live in small residences and apartments compared to large homes.
A recent class-action lawsuit filed against Whirlpool claims the appliance giant concealed the risk of gas stove emissions. To protect yourself, we devised this gas stove safety guide to mitigate your risk of contamination.
TechRepublic

8 Best Data Science Tools and Software
Apache Spark and Hadoop, Microsoft Power BI, Jupyter Notebook and Alteryx are among the top data science tools for finding business insights. Compare their features, pros and cons.

EU’s AI Act: Europe’s New Rules for Artificial Intelligence
Europe's AI legislation, adopted March 13, attempts to strike a tricky balance between promoting innovation and protecting citizens' rights.

10 Best Predictive Analytics Tools and Software for 2024
Tableau, TIBCO Data Science, IBM and Sisense are among the best software for predictive analytics. Explore their features, pricing, pros and cons to find the best option for your organization.

Tableau Review: Features, Pricing, Pros and Cons
Tableau has three pricing tiers that cater to all kinds of data teams, with capabilities like accelerators and real-time analytics. And if Tableau doesn’t meet your needs, it has a few alternatives worth noting.

Top 6 Enterprise Data Storage Solutions for 2024
Amazon, IDrive, IBM, Google, NetApp and Wasabi offer some of the top enterprise data storage solutions. Explore their features and benefits, and find the right solution for your organization's needs.
Latest Articles

OpenAI, Anthropic Research Reveals More About How LLMs Affect Security and Bias
Anthropic opened a window into the ‘black box’ where ‘features’ steer a large language model’s output. OpenAI dug into the same concept two weeks later with a deep dive into sparse autoencoders.

Some Generative AI Company Employees Pen Letter Wanting ‘Right to Warn’ About Risks
Both the promise and the risk of "human-level" AI has always been part of OpenAI’s makeup. What should business leaders take away from this letter?

Cisco Talos: LilacSquid Threat Actor Targets Multiple Sectors Worldwide With PurpleInk Malware
Find out how the cyberespionage threat actor LilacSquid operates, and then learn how to protect your business from this security risk.

IBM’s Think 2024 News That Should Help Skills & Productivity Issues in Australia
TechRepublic interviewed IBM’s managing director for Australia about how announcements from the recent Think event could impact the tech industry in particular.

Cisco Live 2024: New Unified Observability Experience Packages Cisco & Splunk Insight Tools
The observability suite is the first major overhaul for Splunk products since the Cisco acquisition. Plus, Mistral AI makes a deal with Cisco’s incubator.

Top Tech Conferences & Events to Add to Your Calendar in 2024
A great way to stay current with the latest technology trends and innovations is by attending conferences. Read and bookmark our 2024 tech events guide.

Intel Lunar Lake NPU Brings 48 TOPS of AI Acceleration
Competition for AI speed heats up. Plus, the first of the two new Xeon 6 processors is now available, and Gaudi 3 deals have been cinched with manufacturers.

Cisco Live 2024: Cisco Unveils AI Deployment Solution With NVIDIA
A $1 billion commitment will send Cisco money to Cohere, Mistral AI and Scale AI.

The 5 Best Udemy Courses That Are Worth Taking in 2024
Udemy is an online platform for learning at your own pace. Boost your career with our picks for the best Udemy courses for learning tech skills online in 2024.

What Is Data Quality? Definition and Best Practices
Data quality refers to the degree to which data is accurate, complete, reliable and relevant for its intended use.

TechRepublic Premium Editorial Calendar: Policies, Checklists, Hiring Kits and Glossaries for Download
TechRepublic Premium content helps you solve your toughest IT issues and jump-start your career or next project.

What is the EU’s AI Office? New Body Formed to Oversee the Rollout of General Purpose Models and AI Act
The AI Office will be responsible for enforcing the rules of the AI Act, ensuring its implementation across Member States, funding AI and robotics innovation and more.

What is Data Science? Benefits, Techniques and Use Cases
Data science involves extracting valuable insights from complex datasets. While this process can be technically challenging and time-consuming, it can lead to better business decision-making.

Gartner’s 7 Predictions for the Future of Australian & Global Cloud Computing
An explosion in AI computing, a big shift in workloads to the cloud, and difficulties in gaining value from hybrid cloud strategies are among the trends Australian cloud professionals will see to 2028.

OpenAI Adds PwC as Its First Resale Partner for the ChatGPT Enterprise Tier
PwC employees have 100,000 ChatGPT Enterprise seats. Plus, OpenAI forms a new safety and security committee in their quest for more powerful AI, and seals media deals.
Create a TechRepublic Account
Get the web's best business technology news, tutorials, reviews, trends, and analysis—in your inbox. Let's start with the basics.
* - indicates required fields
Sign in to TechRepublic
Lost your password? Request a new password
Reset Password
Please enter your email adress. You will receive an email message with instructions on how to reset your password.
Check your email for a password reset link. If you didn't receive an email don't forgot to check your spam folder, otherwise contact support .
Welcome. Tell us a little bit about you.
This will help us provide you with customized content.
Want to receive more TechRepublic news?
You're all set.
Thanks for signing up! Keep an eye out for a confirmation email from our team. To ensure any newsletters you subscribed to hit your inbox, make sure to add [email protected] to your contacts list.
- Skip to content
- Skip to search
- Skip to footer
Products, Solutions, and Services
Want some help finding the Cisco products that fit your needs? You're in the right place. If you want troubleshooting help, documentation, other support, or downloads, visit our technical support area .
Contact Cisco
- Get a call from Sales
Call Sales:
- 1-800-553-6387
- US/CAN | 5am-5pm PT
- Product / Technical Support
- Training & Certification
Products by technology

- Software-defined networking
- Cisco Silicon One
- Cloud and network management
- Interfaces and modules
- Optical networking
- See all Networking

Wireless and Mobility
- Access points
- Outdoor and industrial access points
- Controllers
- See all Wireless and Mobility

- Secure Firewall
- Secure Endpoint
- Secure Email
- Secure Access
- Multicloud Defense
- See all Security

Collaboration
- Collaboration endpoints
- Conferencing
- Cisco Contact Center
- Unified communications
- Experience Management
- See all Collaboration

Data Center
- Servers: Cisco Unified Computing System
- Cloud Networking
- Hyperconverged infrastructure
- Storage networking
- See all Data Center
- Nexus Dashboard Insights
- Network analytics
- Cisco Secure Network Analytics (Stealthwatch)

- Video endpoints
- Cisco Vision
- See all Video

Internet of Things (IoT)
- Industrial Networking
- Industrial Routers and Gateways
- Industrial Security
- Industrial Switching
- Industrial Wireless
- Industrial Connectivity Management
- Extended Enterprise
- Data Management
- See all industrial IoT
- Cisco+ (as-a-service)
- Cisco buying programs
- Cisco Nexus Dashboard
- Cisco Networking Software
- Cisco DNA Software for Wireless
- Cisco DNA Software for Switching
- Cisco DNA Software for SD-WAN and Routing
- Cisco Intersight for Compute and Cloud
- Cisco ONE for Data Center Compute and Cloud
- See all Software
- Product index
Products by business type

Service providers

Small business

Midsize business
Cisco can provide your organization with solutions for everything from networking and data center to collaboration and security. Find the options best suited to your business needs.
- By technology
- By industry
- See all solutions
CX Services
Cisco and our partners can help you transform with less risk and effort while making sure your technology delivers tangible business value.
- See all services
Design Zone: Cisco design guides by category
Data center
- See all Cisco design guides
End-of-sale and end-of-life
- End-of-sale and end-of-life products
- End-of-Life Policy
- Cisco Commerce Build & Price
- Cisco Software Central
- Cisco Feature Navigator
- See all product tools
- Cisco Mobile Apps
- Design Zone: Cisco design guides
- Cisco DevNet
- Marketplace Solutions Catalog
- Product approvals
- Product identification standard
- Product warranties
- Cisco Security Advisories
- Security Vulnerability Policy
- Visio stencils
- Local Resellers
- Technical Support
- Financial Information
- Our History
- Our Leadership
- The Casey Philanthropies
- Workforce Composition
- Child Welfare
- Community Change
- Economic Opportunity
- Equity and Inclusion
- Evidence-Based Practice
- Juvenile Justice
- Leadership Development
- Research and Policy
- Child Poverty
- Foster Care
- Juvenile Probation
- Kinship Care
- Racial Equity and Inclusion
- Two-Generation Approaches
- See All Other Topics
- Publications
- KIDS COUNT Data Book
- KIDS COUNT Data Center
2024 KIDS COUNT Data Book
2024 state trends in child well-being.

The 35th edition of the Annie E. Casey Foundation's KIDS COUNT ® Data Book examines the unprecedented declines in student math and reading proficiency brought on by the COVID-19 pandemic's effect on education . The latest data from the National Assessment of Educational Progress reveals that between 2019 and 2022, fourth-grade reading and eighth-grade math scores plummeted, representing decades of lost progress. This alarming trend underscores the urgent need for action to address the growing academic disparities among U.S. students.
Today's students, who will comprise America's future workforce, are ill-prepared for the high-level reading, math and problem-solving skills required in a competitive global economy. The failure to adequately prepare our children will have dire consequences for their futures and for the economic vitality of our nation.
Learn more about pandemic learning loss and Casey's recommendations to ensure student success
National Trends in Child Well-Being
In 2022, as COVID-19 restrictions eased, the impact of the pandemic on child well-being became evident. Six indicators worsened between 2019 and 2022, including educational achievement and the child and teen death rate. Between 2019 and 2021, the percentage of children scoring proficient or above in reading and math declined sharply. While this trend may have stabilized in 2022, the data indicate a significant setback in educational attainment. The child and teen death rate also remained elevated in 2022, with 17.0 deaths per 100,000 children and adolescents, compared to 14.7 in 2019.
However, some positive trends emerged:
- Parents' economic security improved significantly, with 62.4% of children living in economically secure homes in 2022, compared to 58.4% in 2021.
- The child poverty rate decreased from 17.2% in 2021 to 15.9% in 2022, returning to pre-pandemic levels.
Health and Family
Positive trends were also observed in the family and community domains. Fewer children lived with parents lacking a high school diploma, and the number of children living in high-poverty communities decreased. The teen birth rate reached a record low in 2021 and remained stable in 2022 at 14 births per 1,000 teen females.
These positive changes demonstrate how effective policies that address the root causes of challenges can contribute to significant improvements and create a brighter future for young people.
Trends in Racial Inequities
Racial inequities in America persist, with American Indian/Alaska Native, Black and Latino children facing significant disparities. Nearly all well-being indicators show disparate outcomes by race and ethnicity, with American Indian/Alaska Native children and Black children experiencing the lowest well-being levels.
Generations of inequity and discrimination contribute to these disparities. Black children have higher rates of single-parent households and poverty, while American Indian/Alaska Native children are more likely to lack health insurance and live in resource-limited neighborhoods. Latino children have higher rates of obesity and live in households where the head may lack a high school diploma.
And despite overall better outcomes for Asian and Pacific Islander children, disaggregated data reveal significant disparities within this population. Burmese, Mongolian and Thai children experience higher rates of poverty and lack of high school diplomas in their households. Today, children of color constitute the majority of the nation's children, highlighting the importance of ensuring their success for the future of America.
Data Book Extras
- 2024 KIDS COUNT Data Book Interactive
- National News Release
- Comunicado de prensa nacional en español
- State News Releases
- Auxiliary Data Tables
- Copyright Information
- Other reports in this series
State Data Profiles on Child Well-Being
View the national data profile or download your state's data profile as a PDF below:
- Connecticut
- Massachusetts
- Mississippi
- New Hampshire
- North Carolina
- North Dakota
- Pennsylvania
- Puerto Rico
- Rhode Island
- South Carolina
- South Dakota
- Washington, D.C.
- West Virginia
State Data Profiles on Child Well-Being in Spanish
View the 2024 national data profile in Spanish or download your state's data profile as a PDF below:
- Distrito de Columbia
- Nuevo Hampshire
- Nueva Jersey
- Nuevo México
- Carolina del Norte
- Dakota del Norte
- Pensilvania
- Carolina del Sur
- Dakota del Sur
- Virginia Occidental
State Trends in Overall Child Well-Being
The Foundation calculates a composite index of overall child well-being for each state by combining data across four domains: (1) Economic Well-Being, (2) Education, (3) Health and (4) Family and Community. These scores are then translated into state rankings. Explore overall child well-being in the interactive KIDS COUNT Data Book .
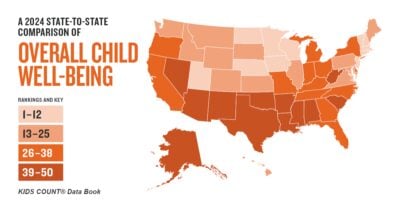
Northeast States Rank High for Overall Well-Being
Distinct regional patterns emerge from the state rankings. Five of the top 10 states in terms of overall child well-being are in the Northeast — Vermont (fourth), New Jersey (sixth) and Connecticut (eighth).
Household Income Has a Direct Effect on Well-Being
States in Appalachia, as well as the Southeast and Southwest — where families have the lowest levels of household income — populate the bottom of the overall rankings. In fact, except for Alaska, the 15 lowest-ranked states are in these regions.
Some States' Rankings Vary Dramatically
Although most state rankings did not vary dramatically across domains, there are a few exceptions. For example, North Dakota ranks 40th in Education but first for Economic Well-Being. New York ranks 44th in Economic Well-Being and 8th for Health. For all states, the index identified bright spots and room for improvement.
Economic Well-Being
To help children grow into prepared, productive adults, parents need jobs with family-sustaining pay, affordable housing and the ability to invest in their children’s future. Explore economic well-being in the interactive KIDS COUNT Data Book .
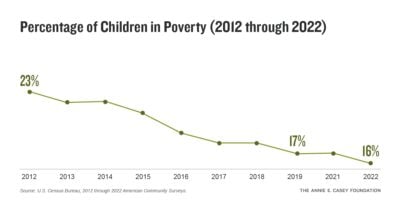
The Child Poverty Rate Has Improved
Nationally, 16% of children (11.6 million) lived in families below the poverty line. The child poverty rate has improved since 2019 (17%).
When parents are unemployed or earn low wages, their access to resources to support their kids’ development is more limited, which can undermine their children’s health and prospects for success in school and beyond. The negative effects of poverty on kids can extend into their teenage years and young adulthood, as they are more likely to contend with issues such as teen pregnancy and failing to graduate from high school.
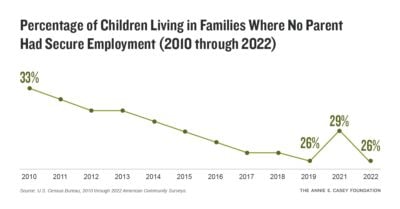
Parental Employment Instability Returned to the Pre-Pandemic Rate
In 2022, 26% or 18.6 million children lived in families where no parent had full-time, year-round employment. The large increase seen between 2019 and 2021 in parental employment instability was erased by the economic recovery the country experienced in 2022. The rate in 2022 returned to the pre-pandemic rate.
Secure employment is a key contributor to families' financial stability and well-being. The COVID-19 pandemic pushed the unemployment rate to near-record highs and caused millions to leave the labor market. In 2022, job openings reached a record high as the labor market recovered. Even so, employment insecurity is a reality for more than a quarter of families living in the United States. It disrupts daily living and relationships and limit families’ access to resources to invest in their children’s development, which can, in turn, diminish children’s achievement in school and chances of future success.
High Housing-Cost Burden Remains Unchanged
In 2022, 30% of children (21.8 million) lived in families with a high housing cost burden. The rate remained unchanged since 2019.
Housing is typically one of the largest family expenses. High housing costs weigh more heavily on low-income families, who are more likely to struggle with finding affordable housing, often spending more than 30% of pretax income on a home, whether they rent or own. Paying too much for housing limits the resources families have for other necessities such as child care, food, health care and transportation as well as their ability to save and achieve financial stability.
The early years of a child’s life lay the foundation for lifelong success. Establishing the conditions that promote educational achievement for children is critical. Explore educational well-being in the interactive KIDS COUNT Data Book .
Low-Income Families Continue to Lack Access to High-Quality Early Education
During 2018–2022, 4.3 million children, ages 3 to 4 were not in school. That accounts for more than half of all children in that age group (54%).
High-quality preschool programs for 3- to 4-year-olds help set the stage for future skill development, well-being and learning, particularly for those from low-income households. These programs play an important role in preparing children for success and lead to higher levels of educational attainment, career advancement and earnings. Although Head Start and the expansion of state-funded programs since the 1990s have increased access to preschool and kindergarten, many kids — especially 3-year-olds and children living in low-income families — continue to be left out, exacerbating socioeconomic differences in educational achievement.
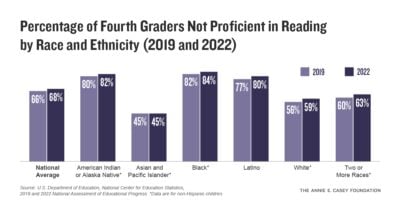
Improvements in Fourth-Grade Reading Mastery Erased by Pandemic
Sixty-eight percent of fourth graders in public schools were not proficient readers in 2022, an alarming rate that increased from 2019, when 66% were not proficient. Any improvement made over the past decade was erased by the pandemic.
Reading proficiency by the end of third grade is a critical marker in a child’s educational development. By fourth grade, children use reading to learn other subjects. Therefore, reading mastery at this level becomes important for students to keep up academically. Children who reach fourth grade without being able to read proficiently are more likely to struggle academically and eventually drop out of school. Low reading proficiency also can reduce earning potential and chances for career success as adults. Although there have been some improvements since the early 1990s, progress has been slow on literacy gains, and racial and income disparities remain. Unfortunately, the pandemic has erased progress made in reading proficiency levels.
Match Achievement Worsened Across Eighth Grade Groups
Eighth-grade math achievement worsened across all racial and ethnic groups between 2019 and 2022. The largest percentage point drops in proficiency were seen among white and multiracial students.
As technology continues to transform the economy, the demand grows for a workforce with aligned math and science skills and training that can keep pace with technological advancement. Students with strong math and science skills are more likely to graduate from high school, attend and complete college, earn higher incomes and take advantage of future opportunities. Even for young people who do not attend college, basic math skills and numerical literacy help with everyday tasks and personal financial management and improve employability. Ensuring kids have early and ongoing access to high-quality math education is critical for their success in school and life.
Children’s good health is fundamental to their overall development, and ensuring kids are born healthy is the first step toward improving their life chances. Poor health in childhood affects other critical aspects of children’s lives, such as school readiness and attendance, and can have lasting consequences on their future health and well-being. Explore health indicators in the interactive KIDS COUNT Data Book .
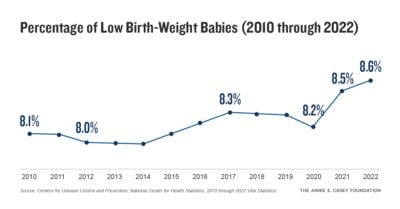
The Rate of Low Birth-Weight Babies Increased
Nationally, low birth-weight babies represented 8.6% of all live births in 2022. An increase from 2019 (8.3%). This is the highest rate witnessed in the last decade.
Birth weight is an important indicator of an infant’s health. Babies born at a low birth weight (less than 5.5 pounds) have a high probability of experiencing developmental problems and short- and long-term disabilities. They also are at greater risk of dying within the first year of life. Infections, multiple births, obesity, poor nutrition, poverty, smoking, stress and violence can increase the chances of a baby being born at a low birth weight. Compared with other affluent countries, the United States has among the highest percentage of babies born at a low birth weight, right behind Japan, Greece and Colombia.
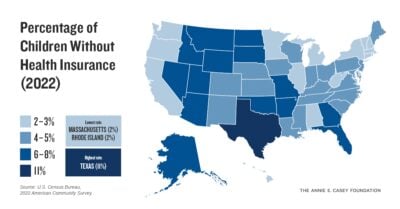
Close to Four Million Children Lacked Health Insurance
Across the nation, 5% of children aged 18 and under (3.9 million) lacked health insurance in 2022.
Children with health insurance are more likely to have a regular source of health care they can access for preventive care services and developmental screenings, to treat acute and chronic conditions or to address injuries when they occur. Children without coverage are less likely than insured children to receive care when they need it. Having health insurance can protect families from financial crisis when a child experiences a serious or chronic illness and can help kids remain active, healthy and in school ready to learn.
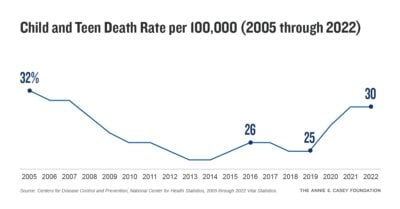
Child and Teen Mortality Rate Increase Stalled
In 2022, 23,137 children and youth ages 1 to 19 died in the United States, which translates into a mortality rate of 30 deaths per 100,000 children and teens. After seeing a 20% increase between 2019 and 2021, the child and teen mortality rate increase stalled in 2022.
Accidents, primarily those involving motor vehicles, were the leading cause of death for children and youth, accounting for 28% of all deaths among children ages 1 to 14.46 As children move further into their teenage years, they encounter new, and potentially deadly, risks. In 2022, accidents, homicides and suicides accounted for 76% of deaths for teens ages 15 to 19.47. For the second year, in a row firearm-related deaths are the leading cause of death among teens.
Family and Community
Children who live in nurturing families and supportive communities have stronger personal connections and higher academic achievement. Explore familial and community well-being in the interactive KIDS COUNT Data Book .
The Percentage of Children in Single-Parent Families Did Not Change
The percentage of children living in single-parent families remains unchanged between 2019 and 2022, at 34%. In 2022, 23.3 million children lived in single-parent families.
Even with the best efforts of parents, children growing up in single-parent families typically have access to fewer economic resources and valuable time with adults than children in two-parent families in which child-raising responsibilities can be shared. For example, in 2022, 28% of single-parent families had incomes below the poverty line, compared with 6% of married couples with children. The effects of growing up in single-parent families go beyond economics, increasing the likelihood of children dropping out of school, being disconnected from the labor market and becoming teen parents.
The Rate of Parents Who Lacked a High School Diploma Improved
In 2022, 11% of children lived in households headed by an adult without a high school diploma. This is a slight improvement from 2019, where the rate was 12%. While this is only a slight improvement, the rate has been cut in half since 1990, when 22% of children lived with parents who lacked a high school diploma.
Children growing up in households with highly educated adults are better positioned for future success. These parents often are better able to provide the financial stability and security they need to foster their children’s development. Higher levels of parental education are strongly associated with better outcomes for children, including kids’ own higher educational attainment and achievement.
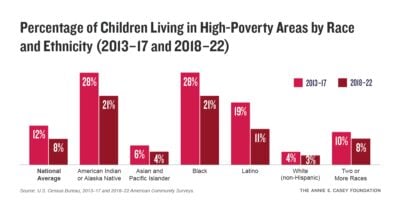
Fewer than 10% of Children Lived in High-Poverty Areas from 2018–2022
During the period from 2018–2022, 8% of children lived in high-poverty areas, representing a total of 5.7 million children.
High-poverty neighborhoods — where poverty rates for the total population are 30% or more — come with several challenges that affect the children and families who live there. Residents of these neighborhoods contend with poorer health, higher rates of crime and violence, poor-performing schools due to inadequate funding and limited access to support networks and job opportunities. They also experience higher levels of financial instability. These barriers make it much harder for families to move up the economic ladder.
Additional Resources on Child Well-Being
- About KIDS COUNT
- KIDS COUNT State Organizations
- The KIDS COUNT Data Center
Copyright of the text materials contained in this website is owned by the Annie E. Casey Foundation, and any use should include an appropriate citation. Read More .
How We Create the Data Book
- The KIDS COUNT Index
- Definitions and Sources
Subscribe to our newsletter to get our data, reports and news in your inbox.
A massive leak of Google Search documents sparks fury across the SEO industry: 'This is another level of war'
- Thousands of leaked documents offer the first real glimpse under the hood of Google Search.
- It's set off a frenzy among SEO experts who've been dissecting the thousands of documents.
- One expert said the documents gave SEO watchers validation. Google said they were lacking context.

For more than 25 years, precisely how Google organizes the web has been one of the internet's greatest unsolved mysteries.
Google is the front door to the internet through which so many businesses are dependent, yet its constantly evolving algorithms have remained closely guarded behind lock and key.
Until this week, when the black box was finally opened.
A trove of 2,500 documents containing highly coveted secrets about how Google ranks its search results began circulating among a handful of search-engine-optimization experts, who shared them more widely on Monday . The company has confirmed the material is real.
The already-frenetic SEO community went into overdrive, with social-media sites and industry forums buzzing over the trove.
Soon the frenzy boiled into fury, with some SEO experts saying the documents showed Google hadn't always been honest when answering questions about how it was ranking websites.
"This is another level of war between SEOs and Googlers," said Lily Ray, a vice president at the SEO agency Amsive.
Erfan Azimi, the CEO of the SEO agency EA Eagle Digital, who said he first stumbled on the documents online, released a dramatic 13-minute YouTube video . For Azim and many others in the SEO community, some details in the leak appear to confirm their suspicions: Google may not have been entirely honest about the most important signals that determine which sites appear at the coveted top half of the search-engine results page.
"For over a decade, we've been lied to," Azimi said, staring down the barrel of the camera lens. "The truth needs to come out."
Still, the most dedicated SEO code crackers have yet to determine how up-to-date the information is or which of the apparent 14,000 ranking factors even saw the light of day.
A Google spokesperson said that the documents lacked context and that the way its systems worked could change frequently. They declined to comment on specific fields in the data.
"We would caution against making inaccurate assumptions about Search based on out-of-context, outdated, or incomplete information," a Google spokesperson said in a statement. "We've shared extensive information about how Search works and the types of factors that our systems weigh, while also working to protect the integrity of our results from manipulation."
The leak has stoked more distrust in Google just as it prepares to rewrite the rulebook. With Google promising to " do the Googling for you " with its summaries powered by generative artificial intelligence, many website owners are preparing for a future in which the company hoovers up their content and delivers no visitors in return .
"As AI is taking over the world, does anyone know how it works?" said Gareth Hoyle, the managing director of the marketing agency Marketing Signals. "Who guards the guards?"
Why Google keeps Search secret
Google employees are given strict instructions to keep quiet regarding Search. An internal presentation for employees , which surfaced last year during Google's Department of Justice search antitrust trial, told staff to keep discussions about the company's most prized product "on a need-to-know basis."
Related stories
"Everything we leak will be used against us by SEOs, patent trolls, competitors, etc.," the presentation read. "Search issues can inflame world leaders who have power over Google, demand Congressional hearings, etc." it added.
Here's what we do know. At its most basic level, Google uses web crawlers — bots that read websites, map their link structures, and track various keywords. Those crawlers are designed to ensure Google's search results return the most relevant and up-to-date information to the user.
Beyond that, how Google determines "good" or "helpful" content, where keywords should be placed, and how high links should appear on web pages have been an ever-evolving mystery. Enter the world of SEO, in which practitioners employ rigorous testing, swap tips and theories at conferences, and press their Google reps and its dedicated "Public Search Liaison" on the ranking factors to which they should give the most weight. For some SEOs, the documents show they would have been better off sticking to their own assumptions.
Take clicks. SEO experts have long believed that Google analyzes when and how frequently a website gets clicks to determine its ranking. The leaked documents refer to "goodClicks" and "unsquashedClicks," terms SEOs believe might show that Google measures clicks more heavily than it's let on in the past.
"One thing I took away from all of this is that Google does, in fact, use click data much more than we thought they did," said Grace Frohlich, an SEO consultant at the digital-marketing agency Brainlabs.
Then, there's domain authority — an assessment of a site's quality and trustworthiness to a relevant topic. Google has previously said it doesn't use domain authority as a ranking factor, yet the documents reference a factor named "siteAuthority."
The documents also reference the signifiers "isElectionAuthority" and "isCovidLocalAuthority," suggesting Google may rank certain sites more authoritative on those topics.
Or take Google's Chrome browser. The company has said in the past that it doesn't use browsing data hoovered up by Chrome to rank websites . But several references to Chrome in the documents have SEO experts convinced that Google has, in fact, used its popular browser to help rank the web (given how much regulators are scrutinizing Google's possible use self-preferencing tactics to boost search and its ad business, you can see why the company may be coy about this one).
"The bigger picture is just highlighting those areas where we were right, and Google was telling us that we were wrong," said Michael King, the founder and CEO of the digital-marketing agency iPullRank.
Some in the SEO community are cautious about reading too much into the leak. Aleyda Solís, the founder of the SEO firm Orainti, where she's an SEO consultant, warned that some people might see what they wanted in the documents and that it was unclear how Google "weighs" factors such as clicks or other values.
"We don't even know if all of them are taken into account as actual ranking factors," Solís said.
'We're already on thin ice'
The relationship between SEOs and Google had already turned frosty. Some business owners have reported catastrophic website-traffic drops following two recent major Google Search algorithm updates in the span of months, while sites such as Reddit and Quora have flooded the top of search results pages .
Google's workforce trimming has also reduced the number of human representatives SEOs can access. While Google holds plush soirées for its advertising clients, such as the star-studded YouTube Brandcast , it doesn't make similar investments in events for the SEO community. This has left some in the community lamenting a breakdown in the relationship between the search giant and the experts who helped it organize all that information.
"We're already on very thin ice with them," Amsive's Ray said.
All this comes as Google plows full steam ahead with generative-AI search . Its recent testing of AI-generated summaries in search results in the US became a laughing stock when the search engine drew from satirical websites and Reddit posts to suggest eating rocks for nutritional purposes and using glue to make cheese stick to pizza . Google initially claimed that AI was spitting out such answers only for uncommon queries but later said it was "taking swift action" to manually remove bad answers that violated its content policy.
While the search leak may not dramatically change how websites play the Google game and may not necessarily reflect how Google ranks the web today, SEOs are set to be carefully watching whether the rules gleaned from the documents will apply in the new world order of AI search. For example, Rand Fishkin, the CEO and cofounder of the audience-research firm SparkToro, wrote that the documents showed Google had been on an "inexorable path" to pushing more traffic to big-brand websites over smaller publishers.
Eric Hoover, the SEO director at the digital agency Jellyfish, said the leak confirmed quality content should always win over attempting to game the algorithm.
"That doesn't really change with generative AI," Hoover said.
For now, Google still dominates the search landscape, leaving plenty of time for SEOs to continue trying to crack the code within the reams of documents now in full public view. They're not counting on anyone at the company to lend them a helping hand.
"I think it's going to ultimately inform better correlation studies that we do in our space," King said. "But I think it may also mean Google talking to us less."
Watch: Why the Pentagon leak is embarrassing for the US government
- Main content
The state of AI in early 2024: Gen AI adoption spikes and starts to generate value
If 2023 was the year the world discovered generative AI (gen AI) , 2024 is the year organizations truly began using—and deriving business value from—this new technology. In the latest McKinsey Global Survey on AI, 65 percent of respondents report that their organizations are regularly using gen AI, nearly double the percentage from our previous survey just ten months ago. Respondents’ expectations for gen AI’s impact remain as high as they were last year , with three-quarters predicting that gen AI will lead to significant or disruptive change in their industries in the years ahead.
About the authors
This article is a collaborative effort by Alex Singla , Alexander Sukharevsky , Lareina Yee , and Michael Chui , with Bryce Hall , representing views from QuantumBlack, AI by McKinsey, and McKinsey Digital.
Organizations are already seeing material benefits from gen AI use, reporting both cost decreases and revenue jumps in the business units deploying the technology. The survey also provides insights into the kinds of risks presented by gen AI—most notably, inaccuracy—as well as the emerging practices of top performers to mitigate those challenges and capture value.
AI adoption surges
Interest in generative AI has also brightened the spotlight on a broader set of AI capabilities. For the past six years, AI adoption by respondents’ organizations has hovered at about 50 percent. This year, the survey finds that adoption has jumped to 72 percent (Exhibit 1). And the interest is truly global in scope. Our 2023 survey found that AI adoption did not reach 66 percent in any region; however, this year more than two-thirds of respondents in nearly every region say their organizations are using AI. 1 Organizations based in Central and South America are the exception, with 58 percent of respondents working for organizations based in Central and South America reporting AI adoption. Looking by industry, the biggest increase in adoption can be found in professional services. 2 Includes respondents working for organizations focused on human resources, legal services, management consulting, market research, R&D, tax preparation, and training.
Also, responses suggest that companies are now using AI in more parts of the business. Half of respondents say their organizations have adopted AI in two or more business functions, up from less than a third of respondents in 2023 (Exhibit 2).
Gen AI adoption is most common in the functions where it can create the most value
Most respondents now report that their organizations—and they as individuals—are using gen AI. Sixty-five percent of respondents say their organizations are regularly using gen AI in at least one business function, up from one-third last year. The average organization using gen AI is doing so in two functions, most often in marketing and sales and in product and service development—two functions in which previous research determined that gen AI adoption could generate the most value 3 “ The economic potential of generative AI: The next productivity frontier ,” McKinsey, June 14, 2023. —as well as in IT (Exhibit 3). The biggest increase from 2023 is found in marketing and sales, where reported adoption has more than doubled. Yet across functions, only two use cases, both within marketing and sales, are reported by 15 percent or more of respondents.
Gen AI also is weaving its way into respondents’ personal lives. Compared with 2023, respondents are much more likely to be using gen AI at work and even more likely to be using gen AI both at work and in their personal lives (Exhibit 4). The survey finds upticks in gen AI use across all regions, with the largest increases in Asia–Pacific and Greater China. Respondents at the highest seniority levels, meanwhile, show larger jumps in the use of gen Al tools for work and outside of work compared with their midlevel-management peers. Looking at specific industries, respondents working in energy and materials and in professional services report the largest increase in gen AI use.
Investments in gen AI and analytical AI are beginning to create value
The latest survey also shows how different industries are budgeting for gen AI. Responses suggest that, in many industries, organizations are about equally as likely to be investing more than 5 percent of their digital budgets in gen AI as they are in nongenerative, analytical-AI solutions (Exhibit 5). Yet in most industries, larger shares of respondents report that their organizations spend more than 20 percent on analytical AI than on gen AI. Looking ahead, most respondents—67 percent—expect their organizations to invest more in AI over the next three years.
Where are those investments paying off? For the first time, our latest survey explored the value created by gen AI use by business function. The function in which the largest share of respondents report seeing cost decreases is human resources. Respondents most commonly report meaningful revenue increases (of more than 5 percent) in supply chain and inventory management (Exhibit 6). For analytical AI, respondents most often report seeing cost benefits in service operations—in line with what we found last year —as well as meaningful revenue increases from AI use in marketing and sales.
Inaccuracy: The most recognized and experienced risk of gen AI use
As businesses begin to see the benefits of gen AI, they’re also recognizing the diverse risks associated with the technology. These can range from data management risks such as data privacy, bias, or intellectual property (IP) infringement to model management risks, which tend to focus on inaccurate output or lack of explainability. A third big risk category is security and incorrect use.
Respondents to the latest survey are more likely than they were last year to say their organizations consider inaccuracy and IP infringement to be relevant to their use of gen AI, and about half continue to view cybersecurity as a risk (Exhibit 7).
Conversely, respondents are less likely than they were last year to say their organizations consider workforce and labor displacement to be relevant risks and are not increasing efforts to mitigate them.
In fact, inaccuracy— which can affect use cases across the gen AI value chain , ranging from customer journeys and summarization to coding and creative content—is the only risk that respondents are significantly more likely than last year to say their organizations are actively working to mitigate.
Some organizations have already experienced negative consequences from the use of gen AI, with 44 percent of respondents saying their organizations have experienced at least one consequence (Exhibit 8). Respondents most often report inaccuracy as a risk that has affected their organizations, followed by cybersecurity and explainability.
Our previous research has found that there are several elements of governance that can help in scaling gen AI use responsibly, yet few respondents report having these risk-related practices in place. 4 “ Implementing generative AI with speed and safety ,” McKinsey Quarterly , March 13, 2024. For example, just 18 percent say their organizations have an enterprise-wide council or board with the authority to make decisions involving responsible AI governance, and only one-third say gen AI risk awareness and risk mitigation controls are required skill sets for technical talent.
Bringing gen AI capabilities to bear
The latest survey also sought to understand how, and how quickly, organizations are deploying these new gen AI tools. We have found three archetypes for implementing gen AI solutions : takers use off-the-shelf, publicly available solutions; shapers customize those tools with proprietary data and systems; and makers develop their own foundation models from scratch. 5 “ Technology’s generational moment with generative AI: A CIO and CTO guide ,” McKinsey, July 11, 2023. Across most industries, the survey results suggest that organizations are finding off-the-shelf offerings applicable to their business needs—though many are pursuing opportunities to customize models or even develop their own (Exhibit 9). About half of reported gen AI uses within respondents’ business functions are utilizing off-the-shelf, publicly available models or tools, with little or no customization. Respondents in energy and materials, technology, and media and telecommunications are more likely to report significant customization or tuning of publicly available models or developing their own proprietary models to address specific business needs.
Respondents most often report that their organizations required one to four months from the start of a project to put gen AI into production, though the time it takes varies by business function (Exhibit 10). It also depends upon the approach for acquiring those capabilities. Not surprisingly, reported uses of highly customized or proprietary models are 1.5 times more likely than off-the-shelf, publicly available models to take five months or more to implement.
Gen AI high performers are excelling despite facing challenges
Gen AI is a new technology, and organizations are still early in the journey of pursuing its opportunities and scaling it across functions. So it’s little surprise that only a small subset of respondents (46 out of 876) report that a meaningful share of their organizations’ EBIT can be attributed to their deployment of gen AI. Still, these gen AI leaders are worth examining closely. These, after all, are the early movers, who already attribute more than 10 percent of their organizations’ EBIT to their use of gen AI. Forty-two percent of these high performers say more than 20 percent of their EBIT is attributable to their use of nongenerative, analytical AI, and they span industries and regions—though most are at organizations with less than $1 billion in annual revenue. The AI-related practices at these organizations can offer guidance to those looking to create value from gen AI adoption at their own organizations.
To start, gen AI high performers are using gen AI in more business functions—an average of three functions, while others average two. They, like other organizations, are most likely to use gen AI in marketing and sales and product or service development, but they’re much more likely than others to use gen AI solutions in risk, legal, and compliance; in strategy and corporate finance; and in supply chain and inventory management. They’re more than three times as likely as others to be using gen AI in activities ranging from processing of accounting documents and risk assessment to R&D testing and pricing and promotions. While, overall, about half of reported gen AI applications within business functions are utilizing publicly available models or tools, gen AI high performers are less likely to use those off-the-shelf options than to either implement significantly customized versions of those tools or to develop their own proprietary foundation models.
What else are these high performers doing differently? For one thing, they are paying more attention to gen-AI-related risks. Perhaps because they are further along on their journeys, they are more likely than others to say their organizations have experienced every negative consequence from gen AI we asked about, from cybersecurity and personal privacy to explainability and IP infringement. Given that, they are more likely than others to report that their organizations consider those risks, as well as regulatory compliance, environmental impacts, and political stability, to be relevant to their gen AI use, and they say they take steps to mitigate more risks than others do.
Gen AI high performers are also much more likely to say their organizations follow a set of risk-related best practices (Exhibit 11). For example, they are nearly twice as likely as others to involve the legal function and embed risk reviews early on in the development of gen AI solutions—that is, to “ shift left .” They’re also much more likely than others to employ a wide range of other best practices, from strategy-related practices to those related to scaling.
In addition to experiencing the risks of gen AI adoption, high performers have encountered other challenges that can serve as warnings to others (Exhibit 12). Seventy percent say they have experienced difficulties with data, including defining processes for data governance, developing the ability to quickly integrate data into AI models, and an insufficient amount of training data, highlighting the essential role that data play in capturing value. High performers are also more likely than others to report experiencing challenges with their operating models, such as implementing agile ways of working and effective sprint performance management.
About the research
The online survey was in the field from February 22 to March 5, 2024, and garnered responses from 1,363 participants representing the full range of regions, industries, company sizes, functional specialties, and tenures. Of those respondents, 981 said their organizations had adopted AI in at least one business function, and 878 said their organizations were regularly using gen AI in at least one function. To adjust for differences in response rates, the data are weighted by the contribution of each respondent’s nation to global GDP.
Alex Singla and Alexander Sukharevsky are global coleaders of QuantumBlack, AI by McKinsey, and senior partners in McKinsey’s Chicago and London offices, respectively; Lareina Yee is a senior partner in the Bay Area office, where Michael Chui , a McKinsey Global Institute partner, is a partner; and Bryce Hall is an associate partner in the Washington, DC, office.
They wish to thank Kaitlin Noe, Larry Kanter, Mallika Jhamb, and Shinjini Srivastava for their contributions to this work.
This article was edited by Heather Hanselman, a senior editor in McKinsey’s Atlanta office.
Explore a career with us
Related articles.

Moving past gen AI’s honeymoon phase: Seven hard truths for CIOs to get from pilot to scale

A generative AI reset: Rewiring to turn potential into value in 2024
Implementing generative AI with speed and safety

IMAGES
VIDEO
COMMENTS
Facebook said Tuesday that the data was scraped as a result of an address book contacts import feature. JASON HENRY/The New York Times/Getty Images. Since Saturday, a massive trove of Facebook ...
Case study: Facebook-Cambridge Analytica data breach scandal. 18 Apr 2022. Cambridge Analytica is a federal data analytics, marketing, and consulting firm based in London, UK, that is accused of illegally obtaining Facebook data and using it to determine a variety of federal crusades. ... Facebook Data Breach. CA's illegitimate procurement ...
April 7, 2021. AP. The news: The personal data of 533 million Facebook users in more than 106 countries was found to be freely available online last weekend. The data trove, uncovered by security ...
Overview. Aleksandr Kogan, a data scientist at the University of Cambridge, was hired by Cambridge Analytica, an offshoot of SCL Group, to develop an app called "This Is Your Digital Life" (sometimes stylized as "thisisyourdigitallife"). Cambridge Analytica then arranged an informed consent process for research in which several hundred thousand Facebook users would agree to complete a survey ...
If your Facebook account is compromised, the attacker will have automatic access to all the linked websites. 4) Use unique passwords. Always use a different password for each online account, even ...
Ireland's Data Protection Commission hit Meta with a €265 million fine (about $276 million USD) after an April 2021 data leak exposed the information of more than 533 million users. The DPC ...
Facebook first learned of the leak in 2015, tracing the violation back to a Cambridge University psychology professor who harvested data of Facebook users through an app to create a personality ...
Tens of millions of American Facebook users had their data harvested by Cambridge Analytica and a British-based researcher. Here's how it happened. More from...
The series is based on internal Facebook documents that were leaked by a whistleblower to Jeff Horwitz. Let's talk about Instagram, which is owned by Facebook. Internal research from Facebook ...
Surfshark in Cybersecurity, Internet Security. 2021, December 2 · 5 min read. On April 3rd, a security expert announced the discovery of a massive data leak that affected 533 million Facebook users. But if you're worried about your email being compromised, you probably shouldn't be - fewer than 10% of the profiles had their addresses ...
Its creator, Troy Hunt, updated the site with the latest data from the Facebook leak. Hunt said that 65% of the latest batch of data had already been added to the tracker from previous leaks.
533 million Facebook users' phone numbers and personal data have been leaked online. Aaron Holmes. Apr 3, 2021, 7:41 AM PDT. Facebook CEO Mark Zuckerberg. AP Photo/Andrew Harnik. The personal data ...
The data leak was first discovered and fixed in 2019, but was recently made easily available online for free. ... Responding to DRI's legal case, a Facebook spokesman said: "We understand people's ...
Guillermo Gutierrez/Bloomberg/Getty Images. Facebook now says the data firm Cambridge Analytica gained unauthorized access to up to 87 million users' data, mainly in the United States. This figure ...
The personal information that was leaked online included over 32 million records on users in the U.S., 11.5 million in the U.K., and 6 million in India. The 2021 Facebook data breach is similar to LinkedIn's security incident where data from over 500 million users has been sold online by an unknown hacker who had dumped two million users ...
Posted in Securities Litigation. The U.S. Supreme Court has agreed to take up a case involving risk factor disclosures in connection with the alleged misuse of Facebook user data by Cambridge Analytica. The case will address a Circuit Court split on the question of what companies must disclose in its risk factors about past instances where ...
Facebook is garnering headlines for another data leak putting users' privacy at risk. The latest incident involves the personal information of 533 million Facebook users from 106 different countries as apparently discovered by Alon Gal, co-founder and CTO of cybercrime intelligence firm Hudson Rock.. The Facts. In an April 3 tweet, Gal said the data, which includes Facebook members' account ...
The recent scandal over the appropriation of users' data from the Facebook platform serves to surface wider concerns about 'big data', relating inter alia to the ways in which personal data are obtained, stored and used for commercial purposes. This article outlines some of the issues involved, and sketches some of the ways in which theologically inspired reflection and action might ...
According to UpGuard, a Mexico-based media company called Cultura Colectiva was responsible for the biggest leak. It exposed 146 gigabytes of Facebook user data, including account names, IDs and ...
Issues. The case is structured to achieve the following teaching objectives: Analyze the ethical issues arising out of the Facebook data breach scandal.. Understand the role of security in social networking. Study the impact of the data scandal on Facebook. Identify the various challenges Facebook is likely to face post the data scandal.
The UpGuard Cyber Risk team can now report that two more third-party developed Facebook app datasets have been found exposed to the public internet. One, originating from the Mexico-based media company Cultura Colectiva, weighs in at 146 gigabytes and contains over 540 million records detailing comments, likes, reactions, account names, FB IDs ...
Facebook Users' Data Leaked. The team of CyberPeace, a New Delhi-based non-profit organization, has alleged that data of 1,00,000 new users from Facebook has surfaced on the breach forum. CyberPeace has said this tampered data includes full name, profile, email, phone number and location information.
In this paper, we examine the reasons for third-party data leaks in web-based services from a software engineering point of view based on our earlier studies as well as the existing literature. We also offer several recommendations and guidelines for developers to alleviate these privacy issues in the future.
Updated Mon, Jun 3, 2024, 2:32 PM · 3 min read. Google. A collection of leaked internal Google privacy cases provides a rare glimpse into the company's volume and handling of breaches ...
The alarming new study shows natural gas odorant is insufficient and inconsistent, and that a significant number of leaks are undetectable by an average sense of smell. A new study shows that a ...
8 Best Data Science Tools and Software. Apache Spark and Hadoop, Microsoft Power BI, Jupyter Notebook and Alteryx are among the top data science tools for finding business insights. Compare their ...
Cisco+ (as-a-service) Cisco buying programs. Cisco Nexus Dashboard. Cisco Networking Software. Cisco DNA Software for Wireless. Cisco DNA Software for Switching. Cisco DNA Software for SD-WAN and Routing. Cisco Intersight for Compute and Cloud. Cisco ONE for Data Center Compute and Cloud.
The 35th edition of the Annie E. Casey Foundation's KIDS COUNT® Data Book examines the unprecedented declines in student math and reading proficiency brought on by the COVID-19 pandemic's effect on education. The latest data from the National Assessment of Educational Progress reveals that between 2019 and 2022, fourth-grade reading and eighth ...
A massive leak of Google Search documents sparks fury across the SEO industry: 'This is another level of war'. Hugh Langley and Lara O'Reilly. May 31, 2024, 2:00 AM PDT. A leak has exposed some of ...
If 2023 was the year the world discovered generative AI (gen AI), 2024 is the year organizations truly began using—and deriving business value from—this new technology.In the latest McKinsey Global Survey on AI, 65 percent of respondents report that their organizations are regularly using gen AI, nearly double the percentage from our previous survey just ten months ago.