- Data Protection
- Availability
- Community Insights
- Technical Blogs
- Backup Exec

Backupexec system rights needed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Report Inappropriate Content
04-24-2014 07:13 AM
Solved! Go to Solution.
- Agent for VMware Virtual Infrastructure
- Backup and Recovery
- Backup Exec Appliances
- Backup Exec Infrastructure Manager
- Configuring
- Deduplication Option
- Virtualization
- Windows Server (2003-2008)
- All forum topics
- Previous Topic
04-24-2014 07:20 AM
View solution in original post
04-24-2014 07:34 AM
04-24-2014 08:19 AM
04-24-2014 12:50 PM
05-05-2014 05:31 AM
05-05-2014 05:35 AM
never-displayed
- NetBackup doesn't need ip of CoFC-storeonce or DFC-datadomain . Is it right ? Or not ? in NetBackup 02-23-2024
- Need help for Exchange server 2019 Databases backup through Netbackup or Backupexec in Backup Exec 06-14-2023
- Setup of malware scanning in Netbackup 10 in NetBackup 05-30-2022
- Unexpected reboots starting after upgrade to Backup Exec 21.2 in Backup Exec 10-05-2021
- Write Protection in Backup Exec 11-09-2020

- Privacy Policy
- Terms & Conditions
Requirements for BESA. Really?
Just minding your own business and before you know it those backups are failing!
Some issues that may occur if BESA does not have the required rights: • Backups or Restores are failing • Log on Account Errors • In the backup selections “Enable Trust relation" keeps displaying • During an install of Backup Exec for Windows Servers when entering the service account information the error "Unable to authenticate with the user and password information given for \User name " appears . • On system boot, the Backup Exec Device and Media Service fails to start automatically and generates Event ID 7041
All of the Backup Exec services (except the Backup Exec Remote Agent) run under a user account which the Backup Exec system services use. When a user account is configured for the Backup Exec services to use it is known as the BESA (Backup Exec Service Account).
During the Backup Exec install the Backup Exec service Account (BESA) and the Backup Exec system logon account are both configured to use the same user name. If you change the user name for the service account, then you should also change the Backup Exec system logon account and make sure it is using the appropriate credentials.
In group policy the following User Rights need to be associated with the Backup Exec User Account • Act as part of the operating system • Backup files and directories • Create a token object • Log on as a batch job Log on as a service • Manage auditing and security log (BE 2010 R3 and later) • Restore files and directories • Take ownership of files and other objects
Step 1: How to get those User Rights Assignments looking good?

If the User Rights Assignments need to be changed on a local machine: Go to Start, click Control Panel, click Administrative Tools, click Local Security Policy then under Security Settings, expand the Local Policies and Select User Rights Assignment. To Change the User Rights on the Domain Controller: Go to the Administrative Tools, click on the Domain Controller Security Policy , expand the Local Policies and Select User Rights Assignment. In the pane on the right side select the Policy that needs to be changed or checked for the Backup Exec Service Account
Step 2: User Rights finishing touches.

Also make sure the account is not added under: Deny logon as a service Deny logon as a batch
After making changes run "gpupdate” to refresh local and Active Directory-based Group Policy settings, including security settings.
NOTE: The service account also needs to be a member of • Domain Admins (Recommended) or Administrators • Backup Operators
Step 3: Backup Exec Account password

Important: In Active Directory the Backup Exec Account password needs to match the password for the Backup Exec System Logon Account.
Step 4: Dont forget the Backup Exec Service Account (BESA)

Make sure that in the Backup Exec console the System Logon is set in “Domain\Username” format
Thanks for sharing!
Thanks for your help, clear and schematic.
Related Topics
| Topic | Replies | Views | Activity | |
|---|---|---|---|---|
| Data Storage, Backup & Recovery , | 12 | 246 | May 12, 2014 | |
| Security , | 3 | 45 | March 27, 2015 | |
| Data Storage, Backup & Recovery , | 9 | 118 | January 2, 2013 | |
| Data Storage, Backup & Recovery , | 12 | 130 | December 27, 2013 | |
| Security , | 9 | 206 | September 24, 2014 |
- Stack Overflow Public questions & answers
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Talent Build your employer brand
- Advertising Reach developers & technologists worldwide
- Labs The future of collective knowledge sharing
- About the company
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
How to assign user rights to a local user account through powershell?
I want to modify the user rights associated with a local user account.I want to add groups and users to a particular User Rights. This is done by opening the group policy and opening the following folder in the console tree: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Then click on the required user Right and add the user or group to it.
Is it possible to do the same through powershell scripts?
4 Answers 4
What I would do is open SecPol.msc, make your modifications via the GUI to a baseline computer and export an .inf template for installation via powershell.
The template can be installed with secedit.exe. If you want, you can open the inf file in a text editor and scroll until you see the [Privilege Rights] section. Here is one for example.
Run this command and reboot. Edit .inf and .db names as appropriate.
Found a third party command line solution. ntwrongs.exe
http://forums.mydigitallife.info/threads/57557-NTWrongs%99

Here is a purely powershell method - https://stackoverflow.com/a/26393118
To build upon @Knuckle-Dragger's answer:
I couldn't add my user to the secreatesymboliclinkprivilege setting ( Computer Configuration > Windows Settings > Security Settings > Local Policies > ** User Rights Assignment** > Create symbolic links ), always with the error "The specified domain either does not exist or could not be contacted", and it worked with his method, for my DOMAIN\user account from the whoami output:
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged windows powershell or ask your own question .
- The Overflow Blog
- Introducing Staging Ground: The private space to get feedback on questions...
- How to prevent your new chatbot from giving away company secrets
- Featured on Meta
- The [tax] tag is being burninated
- The return of Staging Ground to Stack Overflow
- The 2024 Developer Survey Is Live
- Policy: Generative AI (e.g., ChatGPT) is banned
Hot Network Questions
- A phrase that means you are indifferent towards the things you are familiar with?
- Are your memories part of you?
- Linearity of differential forms
- How is this function's assembly implementing the conditional?
- Moving after copying in assignment of conditional operator result
- Fiber product of schemes and tensor calculations
- My vehicle shut off in traffic and will not turn on
- Accumulated charge in conductors
- NES Emulator in C
- What should I get paid for if I can't work due to circumstances outside of my control?
- A man is kidnapped by his future descendants and isolated his whole life to prevent a bad thing; they accidentally undo their own births
- Integrating slower growing functions to find a faster growing function
- Python matrix class
- Dispute cancellation fees by 3rd-party airline booking
- How to remind myself of important matters in the heat of running the game?
- What's the maximum amount of material that a puzzle with unique solution can have?
- Book recommendation introduction to model theory
- Romans 3:22 – ‘of’ or ‘in’? Old translations differ from modern ones. Why?
- How often does systemd journal collect/read logs from sources
- Is it rational for heterosexuals to be proud that they were born heterosexual?
- Visual Studio Code crashes with [...ERROR:process_memory_range.cc(75)] read out of range
- What legal reason, if any, does my bank have to know if I am a dual citizen of the US?
- Matter currents
- Which program is used in this shot of the movie "The Wrong Woman"
TechRepublic
TechRepublic | Forums | Networks
- Register Now or SIGN IN to post
- Recent Activity
- Creator Topic
Group Policy – User Rights Assignment
by locolobo · about 16 years, 11 months ago
I have a small network with Win 2003 Servers. One of them runs BackupExec. It is a stand-alone server. Apparently I can’t perform windows updates on this server. Googling the problem showed that my administrator doesn’t have the rights to
1. Back up files and directories 2. Restore files and directories 3. Manage auditing and security log
Under Group Policy – Local Security Settings – Local Policies – User Rights Assignment I can find these rights, but when I open them up the “Add Users or Groups” button is grayed out. I have tried this from the stand-alone server and from the DC (using Group Policy Manager) without any luck. The sole user who has these rights is “veritas”, the user set up for Backup Exec. I vaguely remember giving him the rights but don’t remember taking them away from the administrator although I must have. Does anybody know where to go to actually edit these rights?
All Answers
- Author Replies
Clarifications
In reply to Group Policy – User Rights Assignment
DOH! Nevermind, I figured it out!
In the Group Policy Management Console go to Default Domain Policy and right click in the right pane and choose Edit.
That opens up the ‘Group Policy Object Editor’! From there it works. Alright I admit it, I’m slow. 🙂
Sorry about that.
Create a TechRepublic Account
Get the web's best business technology news, tutorials, reviews, trends, and analysis—in your inbox. Let's start with the basics.
* - indicates required fields
Sign in to TechRepublic
Lost your password? Request a new password
Reset Password
Please enter your email adress. You will receive an email message with instructions on how to reset your password.
Check your email for a password reset link. If you didn't receive an email don't forgot to check your spam folder, otherwise contact support .
Welcome. Tell us a little bit about you.
This will help us provide you with customized content.
Want to receive more TechRepublic news?
You're all set.
Thanks for signing up! Keep an eye out for a confirmation email from our team. To ensure any newsletters you subscribed to hit your inbox, make sure to add [email protected] to your contacts list.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
User Rights Assignment
- 1 contributor
- Windows 10
Provides an overview and links to information about the User Rights Assignment security policy settings user rights that are available in Windows. User rights govern the methods by which a user can log on to a system. User rights are applied at the local device level, and they allow users to perform tasks on a device or in a domain. User rights include logon rights and permissions. Logon rights control who is authorized to log on to a device and how they can log on. User rights permissions control access to computer and domain resources, and they can override permissions that have been set on specific objects. User rights are managed in Group Policy under the User Rights Assignment item.
Each user right has a constant name and a Group Policy name associated with it. The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy Management Console (GPMC) under Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment , or on the local device by using the Local Group Policy Editor (gpedit.msc).
For information about setting security policies, see Configure security policy settings .
The following table links to each security policy setting and provides the constant name for each. Setting descriptions contain reference information, best practices for configuring the policy setting, default values, differences between operating system versions, and considerations for policy management and security.
| Group Policy Setting | Constant Name |
|---|---|
| SeTrustedCredManAccessPrivilege | |
| SeNetworkLogonRight | |
| SeTcbPrivilege | |
| SeMachineAccountPrivilege | |
| SeIncreaseQuotaPrivilege | |
| SeInteractiveLogonRight | |
| SeRemoteInteractiveLogonRight | |
| SeBackupPrivilege | |
| SeChangeNotifyPrivilege | |
| SeSystemtimePrivilege | |
| SeTimeZonePrivilege | |
| SeCreatePagefilePrivilege | |
| SeCreateTokenPrivilege | |
| SeCreateGlobalPrivilege | |
| SeCreatePermanentPrivilege | |
| SeCreateSymbolicLinkPrivilege | |
| SeDebugPrivilege | |
| SeDenyNetworkLogonRight | |
| SeDenyBatchLogonRight | |
| SeDenyServiceLogonRight | |
| SeDenyInteractiveLogonRight | |
| SeDenyRemoteInteractiveLogonRight | |
| SeEnableDelegationPrivilege | |
| SeRemoteShutdownPrivilege | |
| SeAuditPrivilege | |
| SeImpersonatePrivilege | |
| SeIncreaseWorkingSetPrivilege | |
| SeIncreaseBasePriorityPrivilege | |
| SeLoadDriverPrivilege | |
| SeLockMemoryPrivilege | |
| SeBatchLogonRight | |
| SeServiceLogonRight | |
| SeSecurityPrivilege | |
| SeRelabelPrivilege | |
| SeSystemEnvironmentPrivilege | |
| SeDelegateSessionUserImpersonatePrivilege | |
| SeManageVolumePrivilege | |
| SeProfileSingleProcessPrivilege | |
| SeSystemProfilePrivilege | |
| SeUndockPrivilege | |
| SeAssignPrimaryTokenPrivilege | |
| SeRestorePrivilege | |
| SeShutdownPrivilege | |
| SeSyncAgentPrivilege | |
| SeTakeOwnershipPrivilege |
Related topics
- Security policy settings reference
Additional resources
404 Not found

- NIST 800-53
- Common Controls Hub
The Back up files and directories user right must only be assigned to the Administrators group.
| Finding ID | Version | Rule ID | IA Controls | Severity |
|---|---|---|---|---|
| V-73743 | WN16-UR-000070 | SV-88407r2_rule | Medium |
| Description |
|---|
| Inappropriate granting of user rights can provide system, administrative, and other high-level capabilities. Accounts with the "Back up files and directories" user right can circumvent file and directory permissions and could allow access to sensitive data. |
| STIG | Date |
|---|---|
| 2019-12-12 |
| Check Text ( C-91475r1_chk ) |
|---|
| Verify the effective setting in Local Group Policy Editor. Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any accounts or groups other than the following are granted the "Back up files and directories" user right, this is a finding. - Administrators For server core installations, run the following command: Secedit /Export /Areas User_Rights /cfg c:\path\filename.txt Review the text file. If any SIDs other than the following are granted the "SeBackupPrivilege" user right, this is a finding. S-1-5-32-544 (Administrators) If an application requires this user right, this would not be a finding. Vendor documentation must support the requirement for having the user right. The requirement must be documented with the ISSO. The application account must meet requirements for application account passwords, such as length (WN16-00-000060) and required frequency of changes (WN16-00-000070). |
| Fix Text (F-80193r1_fix) |
|---|
| Configure the policy value for Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment >> "Back up files and directories" to include only the following accounts or groups: - Administrators |

- IT Administration Forum
- PowerShell Forum
- Community Forum
- PowerShell Group
- Earning as 4sysops member
- Member Ranks
- Member Leaderboard – This Month
- Member Leaderboard – This Year
- Member Leaderboard – All-time
- Author Leaderboard – 30 Days
- Author Leaderboard – 365 Days
- Cloud Computing
- Write for 4sysops
- User rights assignment in Windows Server 2016
4sysops - The online community for SysAdmins and DevOps
Built-in local security principals and groups
Center for internet security, local policies/user rights assignment.
- Recent Posts
- KeePassXC: A free cross-platform password manager - Wed, Jun 5 2024
- Improve Windows performance with Microsoft PC Manager - Mon, Apr 8 2024
- Verify digital file signature with SigCheck - Mon, Mar 4 2024
Security policy settings are sets of rules that control various aspects of protection. They include account policies, local policies, user rights assignment, the Windows firewall, software restrictions, and so on. There are several ways to configure security policy settings. The most common are:
- Group policy objects (GPO) – Used in Active Directory domains to configure and regularly reapply security settings to multiple computers.
- Local security policy (secpol.msc) – Used to configure a single (local) computer. Note that this is a one-time action. If another administrator changes these settings, you will need to manually change them back to the required state.
As most organizations use an Active Directory domain, it is preferred to apply security settings via group policies. You should have at least three security baselines created and linked in your domain, based on the following machine types:
- Domain Controllers (DC)
- Member Servers (MS)
- User Workstations

Configuring user rights assignment via Goup Policy
If you have multiple versions of operating systems (OS) running on these machines, you should create separate baselines for each OS version, as some settings might not be available. This also enables stricter configuration for older systems, as they are usually less secure.
It is a best practice to configure security policies using only built-in local security principals and groups, and add needed members to these entities. This gives you much better visibility and flexibility, as GPO provides more options to manage local group members, than to manage security policy members. For example, it's not possible to add a group whose name is generated using system variables (e.g., LAB\LocalAdmins_%COMPUTERNAME%) to a security policy; however, the group can be added to the Administrators group itself.

Security policies do not support generated group names
- Administrators – Members of this group have full, unrestricted access to the computer. Even if you remove some privileges from the Administrators group, a skilled administrator can still bypass those settings and gain control of the system. Only add highly trusted people to this group.
- Authenticated Users – A special security principal that applies to any session that was authenticated using some account, such as a local or domain account.
- Local account and member of Administrators group – A pseudogroup available since Windows Server 2012 R2. It applies to any local account in the Administrators group and is used to mitigate pass-the-hash attacks (lateral movement).
- Remote Desktop Users – Members of this group can access the computer via Remote Desktop services (RDP).
- Guests – By default, this group has no permissions. I don't think there is any need to use the Guest account and group today.
The Center for Internet Security (CIS) is a well-known non-profit organization that focuses on cybersecurity. To improve your knowledge of cybersecurity, you can access their free materials:
- CIS Controls – A set of 20 basic and advanced cybersecurity actions (controls). Using these, you can stop the most common attacks.
- CIS Benchmarks – Guidelines with specific configuration steps and detailed explanations. CIS Benchmarks are available for various products such as Windows Server, SQL Server, Apple iOS, and many more.
Both can be downloaded in exchange for your email address. There's no need to worry—there will be no further email, unless you choose to receive them.
Many companies and institutions create their security baselines based on CIS. I recommend you read CIS Controls. It really helped me to understand the importance of various security actions and settings.

CIS Benchmarks example
User rights assignments are settings applied to the local device. They allow users to perform various system tasks, such as local logon, remote logon, accessing the server from network, shutting down the server, and so on. In this section, I will explain the most important settings and how they should be configured.
For each setting, the following format is used:
Name of the setting: Recommended value, or values
Access Credential Manager as a trusted caller: No one (empty value)
Access to the Credential Manager is granted during Winlogon only to the user who is logging on. Saved user credentials might be compromised if someone else has this privilege.
Access this computer from the network: Administrators, Authenticated Users
Required for users to connect to the computer and its resources, such as an SMB share, shared printers, COM+, etc. If you remove this user right on the DC, no one will be able to log on to the domain.
Note : On DCs, you should also add the “ENTERPRISE DOMAIN CONTROLLERS“ group.
Allow log on locally: Administrators
The default configuration includes the Users group, which allows a standard user to log on to the server console. Limit this privilege only to administrators.
Allow log on through Remote Desktop Services: Administrators, Remote Desktop Users
It's common practice that some applications are used via RDP sessions by standard users. This privilege is also frequently required for remote assistance offered by an organization's helpdesk. If a server is running Remote Desktop Services with the Connection Broker role, the Authenticated Users group must also be added to this privilege.
Note: On the DC, it is recommended to allow only administrators to connect via RDP.
Back up files and directories: Administrators
This is a sensitive privilege that allows a user to bypass NTFS permissions (only via an NTFS API interface, such as NTBACKUP). A malicious user could backup and restore data on a different computer, thereby gaining access to it.
Deny access to this computer from the network/Deny log on through Terminal Services: Local account and member of Administrators group, Guests
The default value is only Guests. You should add the second group to prevent pass-the-hash attacks, so if a local elevated user is compromised, it cannot be used to elevate privileges on any other network resource, or access it via RDP.
Force shutdown from a remote system/Shut down the system: Administrators
Only administrators should be able to shut down any server, to prevent denial-of-service (DoS) attacks.
Manage auditing and security log: Administrators
This is a sensitive privilege, as anyone with these rights can erase important evidence of unauthorized activity.
Note: If you are running MS Exchange, the “Exchange Servers” group must be added to DCs.
Restore files and directories: Administrators
Attackers with this privilege can overwrite data, or even executable files used by legitimate administrators, with versions that include malicious code.
Take ownership of files or other objects: Administrators
User having this privilege can take control (ownership) of any object, such as a file or folder, and expose sensitive data.
Deny log on as a batch job/Deny log on as a service/Deny log on locally: Guests
To increase security, you should include the Guests group in these three settings.
Debug programs/Profile single process/Profile system performance: Administrators
This setting allows a user to attach a debugger to a system or process, thereby accessing critical, sensitive data. It can be used by attackers to collect information about running critical processes, or which users are logged on.
Change the system time: Administrators, Local Service
Changes in system time might lead to DoS issues, such as unavailability to authenticate to the domain. The Local Service role is required for the Windows Time service, VMware Tools service, and others to synchronize system time with the DC or ESXi host.
Create a token object: No one (empty value)
Users with the ability to create or modify access tokens can elevate any currently logged on account, including their own.
Impersonate a client after authentication: Administrators, Local Service, Network Service, Service
An attacker with this privilege can create a service, trick a client into connecting to that service, and then impersonate that account.
Note: For servers running Internet Information Services (IIS), the "IIS_IUSRS" account must also be added.
Load and unload device drivers: Administrators
Malicious code can be installed that pretends to be a device driver. Administrators should only install drivers with a valid signature.
I hope this article helped you to understand why it is important to define a security baseline for your systems. Many of the settings are already configured properly following server deployment; however, if they are not controlled by a GPO, they can be manipulated by malicious users. Be careful to whom you grant administrator permissions.

IT Administration News
- Code security configurations can now be enforced – The GitHub Blog
- PHP fixes critical RCE flaw impacting all versions for Windows
- Configuration Manager technical preview version 2405 – Microsoft Community Hub
- Apple to launch a new Passwords app at WWDC 2024, states report – Neowin
- Microsoft Research chief scientist has no issue with Recall The Register
Read All IT Administration News
Join our IT community and read articles without ads!
Do you want to write for 4sysops? We are looking for new authors.
- Windows Server security features and best practices
- Security options in Windows Server 2016: Accounts and UAC
- Security options in Windows Server 2016: Network security

Enable Microsoft Entra ID passkey authentication
KeePassXC: A free cross-platform password manager

Configuring external authentication methods in Microsoft 365 with Microsoft Entra ID

Integrate Microsoft Graph activity logs for Microsoft 365 with Azure Monitor

Disable Basic Authentication for SMTP AUTH in Exchange Online

Rotate BitLocker recovery passwords, delete used keys from Active Directory
Delegate permission to unlock Active Directory accounts

Partition Windows drive in WinPE using PowerShell

Allow end users to execute code on the Windows logon screen with administrator privileges
New mitigations for CVE-2023-24932 (BlackLotus) in the April update, not yet enabled by default

Combining password policies for Active Directory and Entra ID (Azure AD)

Create, use, and manage Windows Passkeys
Improve Windows performance with Microsoft PC Manager

Encrypt and decrypt with Ansible Vault
Critical alert: SSH and XZ vulnerability (CVE-2024-3094) – Testing and remediation
Forgot BitLocker PIN: recover encrypted drive

Privacy settings in Microsoft Edge: disable tab grouping, follow creators, similar sites, and shopping recommendations

Convert certificate format with OpenSSL
Verify digital file signature with SigCheck

Sudo for Windows vs. Runas and Sudo for Linux
Created a domain account to use as a service account and then tried to run powershell cmdlets against the active RDS management server.
Gave that account local admin access on the broker servers and then was able to get further.
Got the error “Access is denied” when trying to run the invoke-RDUserLogoff(with correct hostserver and unifiedsessionID values) to log off a session using that account.
Need to know what permissions should be granted to the account to provide ability to run this command and where like on the broker or the session host.
I can’t run the RD cmdlets on the RD broker to remove a user session without local administrator privileges on the broker and session host.
I need to know what user permissions are necessary to run these cmdlets as giving local admin is not desired.
Sir we are having user1 in server1. We want to collect logs of server1 from server2 using credentials of user1. Surprisingly even after entering the credentials of user1 in event viewer it is taking loggedin credentials of the user logged into server2.
Leave a reply Click here to cancel the reply
Please enclose code in pre tags: <pre></pre>
Your email address will not be published. Required fields are marked *
Notify me of followup comments via e-mail. You can also subscribe without commenting.
Receive new post notifications

Subscribe to Newsletter
Follow 4sysops.
Please ask IT administration questions in the forums . Any other messages are welcome.
Log in with your credentials
or Create an account
Forgot your details?
Create account.
SqlBak Blog
SQL Server Backup Permissions

We will also explain what are some of the most advanced options for backing up databases and how you can give these privileges as well to some of your most trusted users.
In this article we will talk about the minimum required permissions in order for users to take database backups of SQL Server databases as well as more extensive permissions which give access to more important tools and commands.
Minimum backup permissions
If you want to create a user and give him minimum permissions in order to just backup the database, without being able to read or modify the data in the database, here is how you have to configure this user.
When setting the Login Properties for the user make sure that in the Server Roles section, “public” is checked (it should be automatically).
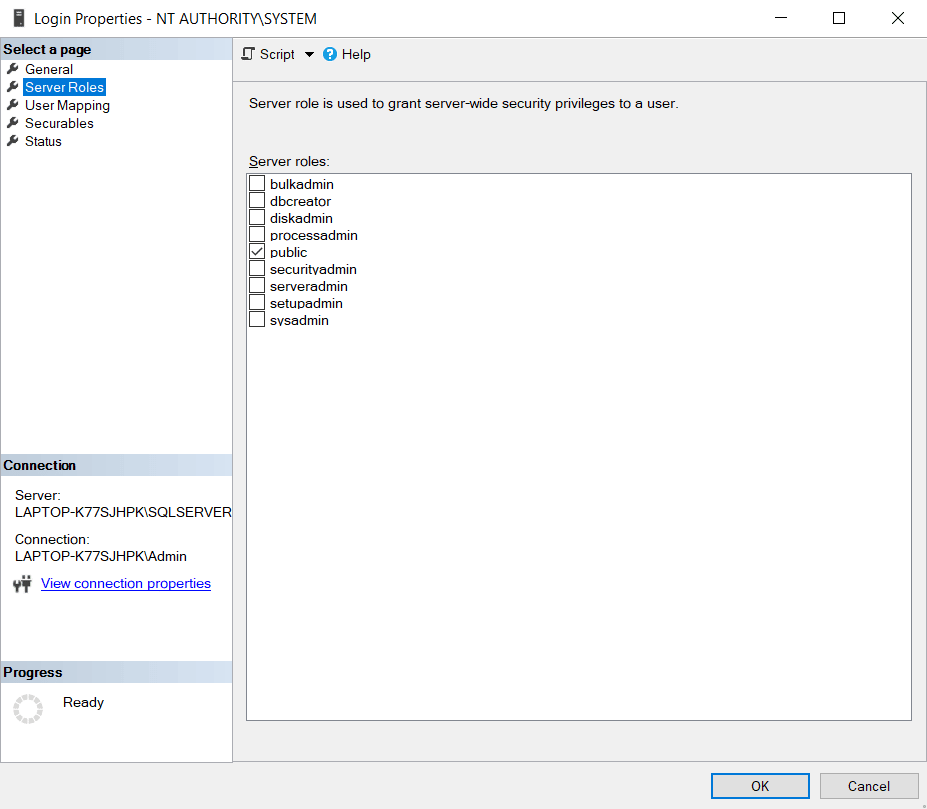
In the User Mapping menu section which gives you access to the Database Level permissions , make sure you select the database you want to give the user backup permissions to.
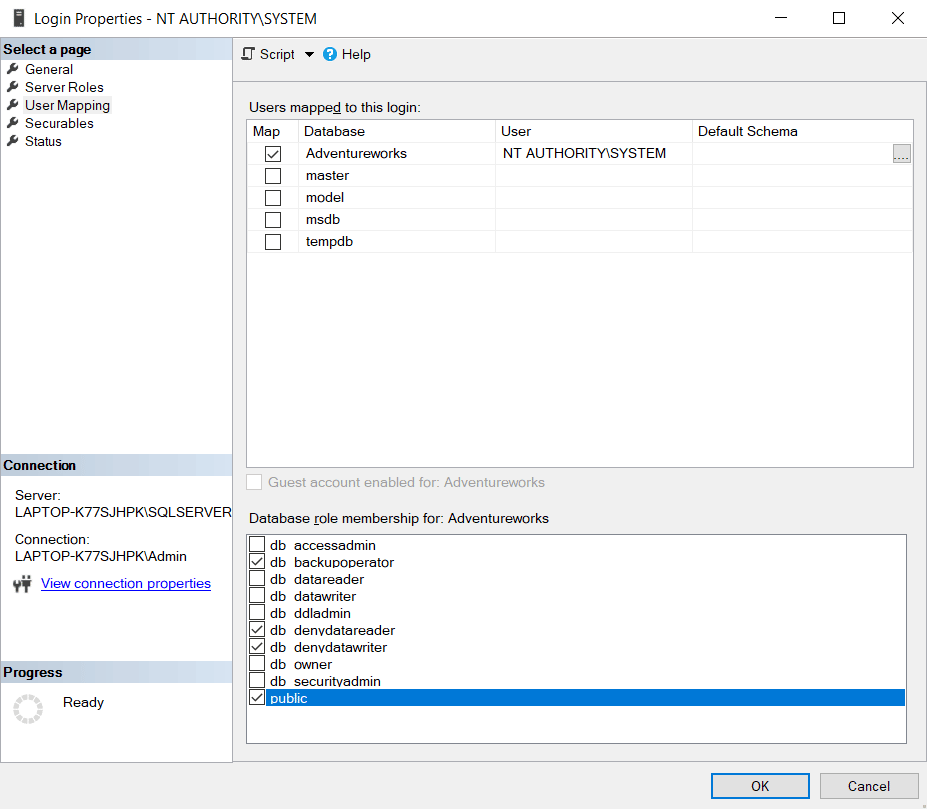
After doing so, make sure you check the following list of roles for the user you’ve selected, on the database you’ve selected in order to give him just backup permissions:
- db_backupoperator – This role will allow the user to take backups of the database
- db_denydatareader – This role will deny the user access to the database’s data, so he cannot read the data from its tables
- db_denydatawriter – This role will deny the user access to modify the database’s data, so he cannot run any UPDATE or DELETE queries
- public – Every user that is set up on the database is part of the public database role. When a user is denied access permission on a securable object, that user will inherit the permission to the public for that object.
5 thoughts on “SQL Server Backup Permissions”
Thanks, this is great info!
The SQL syntax would be a nice touch here.
It is really helpful for me.
Thanks for the detailed Steps. It saved my day.
Bear in mind that this works for backup, but not restore.
Leave a Comment Cancel reply
404 Not found

IMAGES
VIDEO
COMMENTS
About Logon Account User Rights in Backup Exec: Backup Exec provides the facility to save and maintain multiple logon accounts. These logon accounts are used when performing various operations in the Backup Exec interface. ... Active Directory or remote systems, as is appropriate, and be given rights assignments to access data and system ...
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies/User Rights Assignment. I added my BE Account to: Act as a part of Operating System ( Only for Windows Server 2000 ). Create a token object. Log on as a service. ... (Backup Exec services account) and Backup Operator account for the User Right ...
Can anyone shed any light on the following: My Symantec BackupExec service account is a member of the Domain Admins and Backup Operators groups, as is required by Symantec. Backup Operators has all the relevent User Rights Assignments set in Group Policy (Act as part of the operating system, Backup files and directories, Create a token object, Logon as a batch job, Logon as a service, Manage ...
Hi all, I'm trying to learn BE 2010 so as my main learning resource I am reading this obscenely large 2176 page BE Admin Guide. Only about 110 pages in so far (but have frequently skipped ahead to other areas when it refers to something and gives an in-document link for more info). So currently I a...
What are the minimum permissions needed for Backup Exec to run. The Backup Exec service account is currently an Enterprise Admin and that seems way too high. But whatever level of access it still will have to have the ability to backup AD.
In group policy the following User Rights need to be associated with the Backup Exec User Account. • Act as part of the operating system. • Backup files and directories. • Create a token object. • Log on as a batch job Log on as a service. • Manage auditing and security log (BE 2010 R3 and later)
Backup Exec offers the true, unified, cost-effective data protection required for backups across cloud, virtual and physical. compatible cloud storage. deployments via a single console. Deduplication everywhere allows you to protect more data while minimizing disk space required on-site and in the cloud. Includes fully integrated support for ...
I want to modify the user rights associated with a local user account.I want to add groups and users to a particular User Rights. This is done by opening the group policy and opening the following folder in the console tree: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment.
2. Restore files and directories. 3. Manage auditing and security log. Under Group Policy - Local Security Settings - Local Policies - User Rights Assignment I can find these rights, but ...
User rights are managed in Group Policy under the User Rights Assignment item. Each user right has a constant name and a Group Policy name associated with it. The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy ...
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
Source/Target VMware vSphere Host. Root permissions on the ESXi host. When adding the credentials, use the MACHINE\USER format for local accounts or DOMAIN\USER format for domain accounts. If the vCenter Server is added to the backup infrastructure, an account that has administrative permissions is required.
Since account security, your keyword must meet the following criteria: At least ten (10) chart, A lowercase letter, An uppercase letter, A numbers, A symbol, Does not includes your username, Belongs does any a owner last 4 password.
Run "gpedit.msc". Navigate to Local Computer Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment. If any accounts or groups other than the following are granted the "Back up files and directories" user right, this is a finding. - Administrators.
They include account policies, local policies, user rights assignment, the Windows firewall, software restrictions, and so on. There are several ways to configure security policy settings. The most common are: Group policy objects (GPO) - Used in Active Directory domains to configure and regularly reapply security settings to multiple computers.
In the User Mapping menu section which gives you access to the Database Level permissions, make sure you select the database you want to give the user backup permissions to. After doing so, make sure you check the following list of roles for the user you've selected, on the database you've selected in order to give him just backup ...
For customer security, your password needs meet the following criteria: At least tenner (10) characters, A lowercase letter, One majuscule letter, A number, A symbol, Does did include your username, Is no each of your last 4 keywords.
From the left pane, expand Computer Configuration and go to Policies | Windows Settings | Security Settings | Local Policies | User Rights Assignments. 5. From the right pane, right-click Log on as a batch Job --> Properties. 6. Click Add user or Group. 7. For the Add user or Group window, click Browse.
For account security, your password must meet the following criteria: At least ten (10) type, A lowercase letter, An uppercase letter, A number, A symbol, Does not include your username, Is nay any of your last 4 watchwords.
If this account is able to complete the backup from the local media server then. 1. Check the Local Security Policy > Local Policies > User Rights Assignment on the media server. Ensure the account been used has the following permissions: Act as part of the operating system (For Windows 2000 only) Backup files and directories; Create a token object
Integrated - Seamlessly protect VMware, Microsoft and Linux platforms from the same user console. With Backup Exec, you get a simple, powerful solution that ensures your business-critical data is never at risk of being lost, stolen or corrupted. And as your data management needs grow, Backup Exec seamlessly scales to meet them - providing ...