- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture

Presentation Layer in OSI model
Prerequisite : OSI Model
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network. The main responsibility of this layer is to provide or define the data format and encryption. The presentation layer is also called as Syntax layer since it is responsible for maintaining the proper syntax of the data which it either receives or transmits to other layer(s).
Functions of Presentation Layer :
The presentation layer, being the 6th layer in the OSI model, performs several types of functions, which are described below-
- Presentation layer format and encrypts data to be sent across the network.
- This layer takes care that the data is sent in such a way that the receiver will understand the information (data) and will be able to use the data efficiently and effectively.
- This layer manages the abstract data structures and allows high-level data structures (example- banking records), which are to be defined or exchanged.
- This layer carries out the encryption at the transmitter and decryption at the receiver.
- This layer carries out data compression to reduce the bandwidth of the data to be transmitted (the primary goal of data compression is to reduce the number of bits which is to be transmitted).
- This layer is responsible for interoperability (ability of computers to exchange and make use of information) between encoding methods as different computers use different encoding methods.
- This layer basically deals with the presentation part of the data.
- Presentation layer, carries out the data compression (number of bits reduction while transmission), which in return improves the data throughput.
- This layer also deals with the issues of string representation.
- The presentation layer is also responsible for integrating all the formats into a standardized format for efficient and effective communication.
- This layer encodes the message from the user-dependent format to the common format and vice-versa for communication between dissimilar systems.
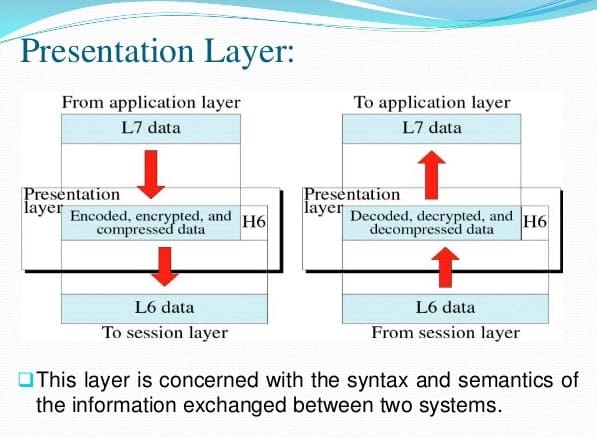
- This layer deals with the syntax and semantics of the messages.
- This layer also ensures that the messages which are to be presented to the upper as well as the lower layer should be standardized as well as in an accurate format too.
- Presentation layer is also responsible for translation, formatting, and delivery of information for processing or display.
- This layer also performs serialization (process of translating a data structure or an object into a format that can be stored or transmitted easily).
Features of Presentation Layer in the OSI model: Presentation layer, being the 6th layer in the OSI model, plays a vital role while communication is taking place between two devices in a network.
List of features which are provided by the presentation layer are:
- Presentation layer could apply certain sophisticated compression techniques, so fewer bytes of data are required to represent the information when it is sent over the network.
- If two or more devices are communicating over an encrypted connection, then this presentation layer is responsible for adding encryption on the sender’s end as well as the decoding the encryption on the receiver’s end so that it can represent the application layer with unencrypted, readable data.
- This layer formats and encrypts data to be sent over a network, providing freedom from compatibility problems.
- This presentation layer also negotiates the Transfer Syntax.
- This presentation layer is also responsible for compressing data it receives from the application layer before delivering it to the session layer (which is the 5th layer in the OSI model) and thus improves the speed as well as the efficiency of communication by minimizing the amount of the data to be transferred.
Working of Presentation Layer in the OSI model : Presentation layer in the OSI model, as a translator, converts the data sent by the application layer of the transmitting node into an acceptable and compatible data format based on the applicable network protocol and architecture. Upon arrival at the receiving computer, the presentation layer translates data into an acceptable format usable by the application layer. Basically, in other words, this layer takes care of any issues occurring when transmitted data must be viewed in a format different from the original format. Being the functional part of the OSI mode, the presentation layer performs a multitude (large number of) data conversion algorithms and character translation functions. Mainly, this layer is responsible for managing two network characteristics: protocol (set of rules) and architecture.
Presentation Layer Protocols : Presentation layer being the 6th layer, but the most important layer in the OSI model performs several types of functionalities, which makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there in a closed network. Presentation Layer, for performing translations or other specified functions, needs to use certain protocols which are defined below –
- Apple Filing Protocol (AFP): Apple Filing Protocol is the proprietary network protocol (communications protocol) that offers services to macOS or the classic macOS. This is basically the network file control protocol specifically designed for Mac-based platforms.
- Lightweight Presentation Protocol (LPP): Lightweight Presentation Protocol is that protocol which is used to provide ISO presentation services on the top of TCP/IP based protocol stacks.
- NetWare Core Protocol (NCP): NetWare Core Protocol is the network protocol which is used to access file, print, directory, clock synchronization, messaging, remote command execution and other network service functions.
- Network Data Representation (NDR): Network Data Representation is basically the implementation of the presentation layer in the OSI model, which provides or defines various primitive data types, constructed data types and also several types of data representations.
- External Data Representation (XDR): External Data Representation (XDR) is the standard for the description and encoding of data. It is useful for transferring data between computer architectures and has been used to communicate data between very diverse machines. Converting from local representation to XDR is called encoding, whereas converting XDR into local representation is called decoding.
- Secure Socket Layer (SSL): The Secure Socket Layer protocol provides security to the data that is being transferred between the web browser and the server. SSL encrypts the link between a web server and a browser, which ensures that all data passed between them remains private and free from attacks.

Similar Reads
Please login to comment..., improve your coding skills with practice.
What kind of Experience do you want to share?
All Subjects
study guides for every class
That actually explain what's on your next test, presentation layer, from class:, information systems.
The presentation layer is the sixth layer of the OSI model that formats and presents data for the application layer. It acts as a translator between the application layer and the network by ensuring that data is presented in a usable format, such as encoding, compression, and encryption, allowing for effective communication between systems with different data representations.
congrats on reading the definition of Presentation Layer . now let's actually learn it.
5 Must Know Facts For Your Next Test
- The presentation layer is responsible for translating between different data formats, ensuring that data from the application layer can be understood by other layers in the OSI model.
- Common functions of the presentation layer include data translation, formatting, encryption, and compression, which are essential for secure and efficient data transmission.
- The presentation layer also handles issues related to character encoding, such as converting between ASCII and EBCDIC formats.
- It allows different applications on diverse systems to communicate seamlessly by standardizing how data is formatted and presented.
- Examples of protocols that operate at the presentation layer include JPEG for images, MIDI for music, and SSL/TLS for secure communications.
Review Questions
- The presentation layer facilitates communication by acting as a translator between various data formats used by different systems and applications. It ensures that the data is correctly formatted and presented so that both sender and receiver can interpret it accurately. By handling tasks like character encoding and data translation, the presentation layer allows seamless interaction among diverse applications, even if they use different internal representations for the same information.
- Key functions of the presentation layer include data encryption and compression, which are vital for secure data transmission. Encryption helps protect sensitive information from unauthorized access during transfer over networks. Meanwhile, compression reduces the amount of data being sent, making it faster to transmit while preserving quality. Together, these functions enhance both security and efficiency in communication across networks.
- The presentation layer significantly impacts network interoperability by standardizing how data is formatted and transmitted across different systems. By ensuring that various applications can communicate effectively regardless of their underlying architectures or data representations, it enhances overall user experience by providing seamless access to information. This interoperability is crucial in today's diverse technology landscape where systems often use different protocols and formats, allowing users to interact with multiple platforms without compatibility issues.
Related terms
Application Layer : The application layer is the seventh layer of the OSI model that interfaces directly with end-user applications, providing network services to those applications.
Data Encryption : Data encryption is the process of converting information into a code to prevent unauthorized access, ensuring data security during transmission.
Data Compression : Data compression is the technique used to reduce the size of data, making it easier and faster to transmit over networks without losing quality.
" Presentation Layer " also found in:
Subjects ( 2 ).
- Computer Networks: A Systems Approach
- Network Security and Forensics
© 2024 Fiveable Inc. All rights reserved.
Ap® and sat® are trademarks registered by the college board, which is not affiliated with, and does not endorse this website..
Presentation Layer
Last Edited
What is the Presentation Layer?
Presentation Layer is the Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model . The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission. This layer is responsible for data encryption, data compression, character set conversion, interpretation of graphics commands, and so on. The network redirector also functions at this layer.

Presentation Layer functions
- Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. Layer 6 is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats the network requires and the format the computer.
- Encryption: Encryption at the transmitter and decryption at the receiver
- Compression: Data compression to reduce the bandwidth of the data to be transmitted. The primary role of data compression is to reduce the number of bits to be transmitted. Multimedia files, such as audio and video, are bigger than text files and compression is more important.
Role of Presentation Layer in the OSI Model
This layer is not always used in network communications because its functions are not always necessary. Translation is only needed if different types of machines need to talk with each other. Encryption is optional in communication. If the information is public there is no need to encrypt and decrypt info. Compression is also optional. If files are small there is no need for compression.
Explaining Layer 6 in video
Most real-world protocol suites, such as TCP/IP , do not use separate presentation layer protocols. This layer is mostly an abstraction in real-world networking.
An example of a program that loosely adheres to layer 6 of OSI is the tool that manages the Hypertext Transfer Protocol (HTTP) — although it’s technically considered an application-layer protocol per the TCP/IP model.
However, HTTP includes presentation layer services within it. HTTP works when the requesting device forwards user requests passed to the web browser onto a web server elsewhere in the network.
It receives a return message from the web server that includes a multipurpose internet mail extensions (MIME) header. The MIME header indicates the type of file – text, video, or audio – that has been received so that an appropriate player utility can be used to present the file to the user.
In short, the presentation layer
Makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there, in a closed network.
- ensures proper formatting and delivery to and from the application layer;
- performs data encryption; and
- manages serialization of data objects.
Computer Network
- Introduction
- Architecture
- Computer Network Types
- Transmission Modes
- TCP/IP Model
Physical Layer
- Digital Transmission
- Transmission Media
- Guided Media
- UnGuided Media
- Multiplexing
- Switching Modes
- Switching Techniques
- Data Link layer
- Error Detection
- Error Correction
- Data Link Controls
- Network Layer
- Network Addressing
- Network Layer Protocols
- Routing Algorithm
- Distance Vector
- Link State Routing
- Transport Layer
- Transport Layer Protocols
- Application Layer
- Client & Server Model
Application Protocols
Network security.
- Digital Signature
- What is Router
- OSI vs TCP/IP
- IPv4 vs IPv6
- ARP Packet Format
- Working of ARP
- FTP Commands
- I2P Protocol
- Sliding Window Protocol
- SPI Protocol
- ARP Commands
- ARP Request
- ARP - Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN Protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT Protocol
- OSPF Protocol
- Stop & Wait Protocol
- IMAP Protocol
- POP Protocol
- Go-Back-N ARQ
- Connection-Oriented vs Connectionless Service
- CDMA vs GSM
- What is MAC Address
- Modem vs Router
- Switch vs Router
- USB 2.0 vs USB 3.0
- CSMA CA vs CSMA CD
- Multiple Access Protocols
- IMAP vs. POP3
- SSH Meaning
- Status Code 400
- MIME Protocol
- What is a proxy server and how does it work
- How to set up and use a proxy server
- What is network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology vs Ring topology
- Bus topology vs Star topology
- Circuit Switching vs Packet switching
- star vs ring topology
- Router vs Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- ASA features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID) in Computer Network
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM) in Computer Network
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- How does BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Functions, Advantages and Disadvantages of the Physical Layer
- Types of Internet Connection
- Noisy and Noiseless Channel
- Advantages and Disadvantages of Bus Topology
- Advantages and Disadvantages of Ring Topology
- Advantages and Disadvantages of Star Topology
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security and Software security
- Information security and Network security
- Security Engineer and Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
- Difference Between Infrastructure and Infrastructure Less Network
- Collision Avoidance in Wireless Networks
- Difference Engine and Analytical Engine
- Hotspot 2.0
- Intrusion Prevention System (IPS)
- Modes of Connection Bluetooth
- Noisy Channel protocols
- Parzen Windows density Estimation Technique
- Principle of Information System Security
- What are Bots, Botnets, and Zombies
- Windows Memory Management
- Wireless dos attack on Wifi
- Design Principles of Security in Distributed Systems
- MAC Filtering
- Principles of Network Applications
- Time-to-Live (TTL)
- What is 1000 BASE-T
- What is the difference between 802.11ac and 802.11ax
- Differentiate between Circuit Switching, Message Switching, and Packet Switching
- What is Web 3.0
- Collision Detection in CSMA/CD
- Ipv4 Header in Computer Networks
- Layered Architecture in Computer Networks
- Define URL in Computer Networks
- MAN in Computer Networks
- Routing Protocols in Computer Networks
- Flooding in Computer Network
- CRC in Computer Network
- Application of Computer Network
- Computer Network Architect
- Design Issues for the Layers of Computer Networks
- What is AMD (Advanced Micro Devices)
- Protocol in Computer Network
- Computer Network Projects
- Different Types of Routers
- Wireless Distribution System (WDS)
- Network Time Protocol
- Address Resolution Protocol (ARP) and its types in Computer Network
- Automatic Repeat ReQuest (ARQ) in Computer Networks
- Bluetooth in Computer Networks
- Circuit Switching in Computer Network
- Computer Hardware and Networking Course
- Ring Topology in a Computer Network
- Token Ring in Computer Networks
- Medium Access Control in Computer Network
- Need for Computer Network
- Repeater in Computer Network
- Computer Networking: a Top Down Approach
- What is Multiplexing in Computer Network
- Body Area Network (BAN)
- INS AND OUT OF DATA STREAMING
- Streaming stored video
- Cellular Network
- How can devices on a Network be identified
- How Does the Internet Work
- Authentication Server
- What is Cloud Backup and How does it Work
- Communication Protocols In System Design
- Extensible Authentication Protocol (EAP)
- Role-Based Access Control (RBAC)
- Network Enumeration Tools
- Network Protocol Testing
- Windows Networking Commands
- Advantages and Disadvantages of WLAN
- Anonymous File Transfer Protocol (AFTP)
- Automatic Private IP Addressing
- What is Deep Web
- USB-C (USB Type C)
- User Authentication
- What is a vCard
- ipv4 Headers
- Difference between Token ring and Ethernet Token Ring
- Server Message Block protocol (SMB protocol)
- Session Border Controllers (SBC)
- Short Message Service Center (SMSC)
- What is a Mail Server
- What are Communication Networks
- Initialization Vector
- What is Fiber Optics
- Open Networking
- Access Ports Vs Trunk Ports
- Edge Routers
- IPTV (Internet Protocol Television)
- Wireless Internet Service Provider (WISP)
- Wireless Backhaul
- Define Protocol in Computer Network
- Virtual Network Adapter
- Virtual Routing and Forwarding
- Virtual Switches(vSwitches)
- VLAN (Virtual LAN)
- Wireless Mesh Network (WMN)
- What is Gateway in Computer Network
- Radio Access Network (RAN)
- What is File Sharing
- Passive Optical Network (PON)
- Private IP address
- Public Key Certificate
- What is Bridge in Computer Network
- Ping Sweep (ICMP Sweep)
- Print Server
- WIFI Pineapple
- Walled Garden
- Wireless ISP (wireless Internet service provider or WISP)
- Bridge vs Repeater
- Hardware Security Module (HSM)
- Public Switched Telephone Network
- Analog Telephone Adapter (ATA)
- Host Bus Adapter (HBA)
- ISCSI initiator
- Simplest Protocol
- Telecommunication Networks
- What is WPS in Wi-Fi
- What are the Most Important Email Security Protocols
- What is Data Governance and Why does it Matter
- Carrier Network
- Most Secure Network Protocol
- Network SMB
- BGP vs. EIGRP: What's the Difference
- Wireless Security: WEP, WPA, WPA2 and WPA3 differences
- Cloud Radio Access Network (C-RAN)
- Bits Per Second (bps or bit/sec)
- Blade Server
- command-and-control server (C&C server)
- Computer Network MCQ
- Computer Network MCQ Part2
Interview Questions
- Networking Questions
Latest Courses
We provides tutorials and interview questions of all technology like java tutorial, android, java frameworks
Contact info
G-13, 2nd Floor, Sec-3, Noida, UP, 201301, India
[email protected] .
Latest Post
PRIVACY POLICY
Online Compiler

IMAGES
VIDEO
COMMENTS
Presentation layer in the OSI model, as a translator, converts the data sent by the application layer of the transmitting node into an acceptable and compatible data format based on the applicable network protocol and architecture.
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts.
What is the presentation layer? The presentation layer resides at Layer 6 of the Open Systems Interconnection communications model and ensures that communications that pass through it are in the appropriate form for the recipient application. In other words, the presentation layer presents the data in a readable format from an application layer ...
The seven layers that make up the OSI are: Layer 7: The application layer, where users interact with applications connected to the internet. Layer 6: The presentation layer, where data is partially encrypted and translated into a transmittable format. Layer 5: The session layer: which controls ports and sessions and maintains connections ...
What Does Presentation Layer Mean? The presentation layer is layer 6 of the 7-layer Open Systems Interconnection (OSI) model. It is used to present data to the application layer (layer 7) in an accurate, well-defined and standardized format.
The presentation layer is the sixth layer of the OSI model. It is primarily used to convert different file formats between the sender and the receiver. The OSI model is a reference model that is used to define communication standards between two devices within a network.
Definition. The presentation layer is the sixth layer of the OSI model that formats and presents data for the application layer. It acts as a translator between the application layer and the network by ensuring that data is presented in a usable format, such as encoding, compression, and encryption, allowing for effective communication between ...
Layer 6 in the OSI model - the presentation layer - translates, compresses, and encrypts data across networks. In this article, we’ll explain what the presentation layer is, how it works, and its functions and protocols.
What is the Presentation Layer? Presentation Layer is the Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model. The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission.
The presentation layer is the 6 th layer from the bottom in the OSI model. This layer presents the incoming data from the application layer of the sender machine to the receiver machine.