What are Computer Viruses?
Learn about the types of computer viruses, examples, and tips to prevent them.
Global Threat Landscape Report 2H 2023

Speak with an Expert

Computer Virus Definition
Chances are you’ve heard how important it is to keep viruses out, but what is a computer virus exactly? A computer virus is a type of malicious software, or malware, that spreads between computers and causes damage to data and software.
Computer viruses aim to disrupt systems, cause major operational issues, and result in data loss and leakage. A key thing to know about computer viruses is that they are designed to spread across programs and systems. Computer viruses typically attach to an executable host file, which results in their viral codes executing when a file is opened. The code then spreads from the document or software it is attached to via networks, drives, file-sharing programs, or infected email attachments.
Common Signs of Computer Viruses
1. speed of system.
A computer system running slower than usual is one of the most common signs that the device has a virus. This includes the system itself running slowly, as well as applications and internet speed suffering. If a computer does not have powerful applications or programs installed and is running slowly, then it may be a sign it is infected with a virus.
2. Pop-up windows
Unwanted pop-up windows appearing on a computer or in a web browser are a telltale sign of a computer virus. Unwanted pop-ups are a sign of malware, viruses, or spyware affecting a device.
3. Programs self-executing
If computer programs unexpectedly close by themselves, then it is highly likely that the software has been infected with some form of virus or malware. Another indicator of a virus is when applications fail to load when selected from the Start menu or their desktop icon. Every time that happens, your next step should be to perform a virus scan and remove any files on programs that might not be safe to use.
4. Accounts being logged out
Some viruses are designed to affect specific applications, which will either cause them to crash or force the user to automatically log out of the service.
5. Crashing of the device
System crashes and the computer itself unexpectedly closing down are common indicators of a virus. Computer viruses cause computers to act in a variety of strange ways, which may include opening files by themselves, displaying unusual error messages, or clicking keys at random.
6. Mass emails being sent from your email account
Computer viruses are commonly spread via email. Hackers can use other people's email accounts to spread malware and carry out wider cyberattacks. Therefore, if an email account has sent emails in the outbox that a user did not send, then this could be a sign of a computer virus.
7. Changes to your homepage
Any unexpected changes to a computer—such as your system’s homepage being amended or any browser settings being updated—are signs that a computer virus may be present on the device.
FortiGuard Labs Global Threat Landscape Report 2H 2023 shows Cybercriminals Exploiting New Industry Vulnerabilities 43% Faster than 1H 2023.
How Do Computer Viruses Attack and Spread?
In the early days of computers, viruses were spread between devices using floppy disks. Nowadays, viruses can still be spread via hard disks and Universal Serial Bus (USB) devices, but they are more likely to be passed between devices through the internet.
Computer viruses can be spread via email, with some even capable of hijacking email software to spread themselves. Others may attach to legitimate software, within software packs, or infect code, and other viruses can be downloaded from compromised application stores and infected code repositories. A key feature of any computer virus is it requires a victim to execute its code or payload, which means the host application should be running.
Types of Computer Viruses
1. resident virus.
Viruses propagate themselves by infecting applications on a host computer. A resident virus achieves this by infecting applications as they are opened by a user. A non-resident virus is capable of infecting executable files when programs are not running.
2. Multipartite virus
A multipartite virus uses multiple methods to infect and spread across computers. It will typically remain in the computer’s memory to infect the hard disk, then spread through and infect more drives by altering the content of applications. This results in performance lag and application memory running low.
Multipartite viruses can be avoided by not opening attachments from untrusted sources and by installing trusted antivirus software. It can also be prevented by cleaning the boot sector and the computer’s entire disk.
3. Direct action
A direct action virus accesses a computer’s main memory and infects all programs, files, and folders located in the autoexec.bat path, before deleting itself. This virus typically alters the performance of a system but is capable of destroying all data on the computer’s hard disk and any USB device attached to it. Direct action viruses can be avoided through the use of antivirus scanners. They are easy to detect, as is restoring infected files.
4. Browser hijacker
A browser hijacker manually changes the settings of web browsers, such as replacing the homepage, editing the new tab page, and changing the default search engine. Technically, it is not a virus because it cannot infect files but can be hugely damaging to computer users, who often will not be able to restore their homepage or search engine. It can also contain adware that causes unwanted pop-ups and advertisements.
Browser hijackers typically attach to free software and malicious applications from unverified websites or app stores, so only use trusted software and reliable antivirus software.
5. Overwrite virus
Overwrite viruses are extremely dangerous. They can delete data and replace it with their own file content or code. Once files get infected, they cannot be replaced, and the virus can affect Windows, DOS, Linux, and Apple systems. The only way this virus can be removed is by deleting all of the files it has infected, which could be devastating. The best way to protect against the overwrite virus is to use a trusted antivirus solution and keep it updated.
6. Web scripting virus
A web scripting virus attacks web browser security, enabling a hacker to inject web-pages with malicious code, or client-side scripting. This allows cyber criminals to attack major websites, such as social networking sites, email providers, and any site that enables user input or reviews. Attackers can use the virus to send spam, commit fraudulent activity, and damage server files.
Protecting against web scripting is reliant on deploying real-time web browser protection software, using cookie security, disabling scripts, and using malicious software removal tools.
7. File infector
A file infector is one of the most common computer viruses. It overwrites files when they are opened and can quickly spread across systems and networks. It largely affects files with .exe or .com extensions. The best way to avoid file infector viruses is to only download official software and deploy an antivirus solution.
8. Network Virus
Network viruses are extremely dangerous because they can completely cripple entire computer networks. They are often difficult to discover, as the virus could be hidden within any computer on an infected network. These viruses can easily replicate and spread by using the internet to transfer to devices connected to the network. Trusted, robust antivirus solutions and advanced firewalls are crucial to protecting against network viruses.
9. Boot Sector Virus
A boot sector virus targets a computer’s master boot record (MBR). The virus injects its code into a hard disk’s partition table, then moves into the main memory when a computer restarts. The presence of the virus is signified by boot-up problems, poor system performance, and the hard disk becoming unable to locate. Most modern computers come with boot sector safeguards that restrict the potential of this type of virus.
Steps to protecting against a boot sector virus include ensuring disks are write-protected and not starting up a computer with untrusted external drives connected.
Exampes of Computer Viruses
Is trojan a virus.
A Trojan horse is a type of program that pretends to be something it is not to get onto a device and infect it with malware. Therefore, a Trojan horse virus is a virus disguised to look like something it is not. For example, viruses can be hidden within unofficial games, applications, file-sharing sites, and bootlegged movies.
Is a worm a virus?
A computer worm is not a virus. Worms do not need a host system and can spread between systems and networks without user action, whereas a virus requires users to execute its code.
Is ransomware a virus?
Ransomware is when attackers lock victims out of their system or files and demand a ransom to unlock access. Viruses can be used to carry out ransomware attacks.
Is rootkit a virus?
A rootkit is not a virus. Rootkits are software packages that give attackers access to systems. They cannot self-replicate or spread across systems.
Is a software bug a virus?
"Bug" is a common word used to describe problems with computers, but a software bug is not a virus. A bug is a flaw or mistake in software code, which hackers can exploit to launch a cyberattack or spread malware .
How To Prevent Your Computer From Viruses
1. use a trusted antivirus product.
Trusted computer antivirus products are crucial to stop malware attacks and prevent computers from being infected with viruses. These antivirus concepts will protect devices from being infected through regular scans and identifying and blocking malware.
2. Avoid clicking pop-up advertisements
Unwanted pop-up advertisements are more than likely to be linked to computer viruses and malware. Never click on pop-up advertisements because this can lead to inadvertently downloading viruses onto a computer.
3. Scan your email attachments
A popular way to protect your device from computer viruses is to avoid suspicious email attachments, which are commonly used to spread malware. Computer antivirus solutions can be used to scan email attachments for potential viruses.
4. Scan the files that you download using file-sharing programs
File-sharing programs, particularly unofficial sites, are also popular resources for attackers to spread computer viruses. Avoid downloading applications, games, or software from unofficial sites, and always scan files that have been downloaded from any file-sharing program.
Cybersecurity Resources
- Cybersecurity
- Types of Cyber Attacks
- IT vs OT Cybersecurity
- AI Cybersecurity
- Cyber Threat Intelligence
- Cybersecurity Management
- Network Security
- Data Security
- Email Security
- Endpoint Security
- Web Security
- Enterprise Security
- Cybersecurity Mesh
Quick Links
- Fortinet Products
- Fortinet Demos
- Analyst Reports
Please fill out the form and a knowledgeable representative will get in touch with you soon.
By clicking submit you agree to the Fortinet Terms and Conditions & Privacy Policy .
- Services & Software
Article updated on June 21, 2024 at 4:00 PM PDT
Best Antivirus Software for 2024
Protect your computers and precious data from virus attacks and malware with ones of the best antivirus software options around.
Our Experts

- National Silver Azbee Award for Impact/Investigative Journalism; National Gold Azbee Award for Online Single Topic Coverage by a Team; National Bronze Azbee Award for Web Feature Series

CNET’s expert staff reviews and rates dozens of new products and services each month, building on more than a quarter century of expertise.
What to consider
Effectiveness
Antivirus software runs virus scans for known viruses and malware, watches for shady websites, offers ransomware protection and monitors unexpected behavior that may be a sign of new viruses and malware. You want antivirus software that can successfully identify these unknown online threats without flagging too many false positives.
Light on system resources
You don't want antivirus software that taxes your PC's resources. If after you install the program, websites open slowly, apps download or open sluggishly or file copies take longer than expected, you may want to try another service.
Cost and discounts
Before you buy, check for discounts on a company's website. Another way to save: The prices we list above are for 10 devices -- if the company offered that package -- but you can trim your cost with antivirus packages if you need to cover three or five devices.
Companies say they anonymize this technical data as much as possible to protect your privacy. The security companies on our list post privacy policies on their websites, so read their privacy statements to learn what the companies do with the information you share.
Protection for other platforms
Microsoft is by far the biggest target for viruses and malware. Android is second, with just under 1% of apps installed on Android devices with Google Play Protect in the potentially harmful app category.
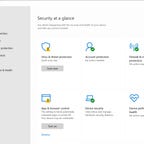
It’s always a good idea to add a layer of protection to your devices to keep your data safe. In an era where your data is always susceptible to getting hacked, having good antivirus software is a must. The best antivirus software does it all: identity protection, malware protection and virus protection. They allow you to keep your computer running smoothly, and all your private information and data safe. Good antivirus solutions even help keep scammers at bay. Using one means your computer will likely have a longer life and you'll be better protected.
Windows is the most popular operating system for computers today, running on over 70% of all laptops and desktops, according to the latest data from Statcounter . That unfortunately also makes Windows the biggest target for a large number of viruses and malware attacks. As such, all our antivirus software recommendations work on Windows.
What's the best antivirus software overall?
Currently, CNET's top pick for the best antivirus software is Microsoft Defender , the tech giant's free antivirus solution built into Windows 10 and Windows 11 machines. At CNET, we've spent years testing and researching dozens of online security and privacy tools like VPNs, password managers and antivirus software to help readers find the best solutions for their needs. Take a look through our recommended antivirus services below to see which one fits you best.
Note: Pricing for antivirus services can be complicated since providers frequently offer low introductory prices to entice you to sign up for their services. After the first billing period -- typically a year or two, depending on the plan you purchase -- the amount you pay for the service may increase substantially (sometimes double the introductory rate). Be sure to check the terms of the subscription plan before you buy, so you won't get an unwelcome surprise when your subscription renews.
Best antivirus software of 2024
- Built into Windows 10 and 11 and enabled by default
- Regularly updated
- Real-time protection
- Resource-intensive
- No option to schedule scans from the UI
- Basic feature set
Best free antivirus for Windows
Microsoft defender.
If you practice safe computing -- you keep your software up to date, you use strong passwords (with the help of a password manager ), you steer clear of unsolicited emails and you don't click suspicious links that may be phishing attempts -- you probably can avoid zero-day attacks and ransomware attacks. With the free Microsoft Defender Antivirus software running on your Windows PC, you have a malware protection safety net if you do let your guard down. It is one of the best antivirus software options, and the best free antivirus software out there.
(Note: Microsoft changed the name of Windows Defender to Microsoft Defender and has expanded the service to other platforms.) This free antivirus program is built into Windows, and it's turned on by default, the antivirus engine does its thing, and this antivirus solution will cover the basics of internet security. Microsoft pushes new updates frequently. Defender also lets you tune the level of protection you want, giving you control over blocking potentially unwanted apps and protecting folders and files from a ransomware attack.
Windows 10 and 11 will automatically disable its own Windows Defender antivirus when you install third-party antivirus. If you uninstall the third-party protection, Windows will turn on its own antivirus again.
- Full suite of online security tools
- Up to 10 users on one subscription
- Parental controls
- Limited set of features on MacOS and iOS
- Price jumps significantly after first year
- No free version available
Best antivirus subscription
Norton 360 with lifelock select.
Norton LifeLock has consistently earned high marks from AV-Test , AV-Comparatives and SE Labs for virus and malware detection. Norton antivirus provides excellent security software for PC, Mac and mobile devices. The company's products include Antivirus Plus, Norton Secure VPN, Norton 360 for Gamers, Norton 360 with LifeLock Select and more. A 10-device subscription for Norton 360 with LifeLock Select is normally $180 per year, but you can get your first year for $80 off. In addition to malware and virus protection for your computer and mobile device, this security suite provides 100GB of backup to the cloud, safe-browsing tools, a secure VPN, a password manager, parental controls and LifeLock identity theft protection and fraud alert. While not all of those services are necessarily best in their respective class, getting them all in one package is a compelling option. Topping it off, Norton offers a free seven-day test drive of the suite, as well as a full refund "within 60 days of purchase for annual subscriptions and within 14 days of purchase for monthly subscriptions," according to Norton's site .
- Excellent free antivirus protection
- Lightweight and easy on PC resources
- Live customer support available for free users
- Free version only available on Windows
- Fewer features on MacOS and iOS with paid version
- Can't schedule scans
Best free antivirus
Bitdefender antivirus free edition.
If you'd like to take a step up in securing your PC without taxing your wallet, it's hard to beat Bitdefender's free antivirus software for Windows 10 and 11. The Windows security software offers real-time monitoring for viruses, malware, spyware and ransomware protection. Bitdefender Antivirus Free Edition is easy to set up and stays out of your way until you need it. And the protection this antivirus product offers is solid. Bitdefender antivirus software consistently earns top marks for its antivirus protection and usability from respected independent antivirus testing labs like the AV-Test lab. The free antivirus version covers one Windows PC. For broader protection, you can choose Bitdefender Total Security or Bitdefender Antivirus Plus. The subscription antivirus suite lets you protect five or 10 devices (Windows, MacOS, iOS and Android), set up parental controls on a kid's computer and run a VPN.

- Includes Browser Guard for web browsers
- Easy to use, customizable interface
- Certain protections only available for Windows
- Free trial is only seven days for mobile devices
- Free version doesn't include real-time protection
Best malware removal service
Malwarebytes.
Malwarebytes protects your PC from viruses or malware attacks, scoring reasonably well in recent independent testing for guarding against malware threats. That's not really what Malwarebytes is known for. If you find yourself in trouble, the go-to disinfectant for many is Malwarebytes. You can get protection and disinfection for one device for $38 a year (regularly $45) . To cover five devices -- any combination of Windows, MacOS and Android -- it's $100 for a year of antivirus software. To get the antivirus company's free antivirus version, download this trial version , which "downgrades" to a no-fee on-demand cleaner with fewer features that detects and removes viruses and malware when you run an on-demand antivirus scan after 14 days.

Other antivirus software to consider
In addition to the four antivirus apps we recommend above, a handful of other anti-malware tools are worth considering among the best antivirus protection if you find them at a better price or just prefer to use one over our picks above.
Good choice for antivirus subscription
Mcafee total protection.
It feels like McAfee Antivirus has been around forever, first on its own in the '80s, then as part of Intel starting in 2010, and then again on its own when Intel spun it off in 2017. And McAfee Total Protection has been around forever because quarter after quarter it creates solid, modern antivirus software that protects your PC. (In recent evaluations by AV-Test, it had high scores on both protection and performance.) McAfee Total Protection guards devices against viruses and offers ransomware protection, wards off malicious websites and includes a password manager for $50 for the first year. If you agree to auto-renew your antivirus suite subscription, you get access to McAfee ID Theft Protection Essentials, which monitors for ID fraud.

Best antivirus subscription for businesses
Trend micro maximum security.
Maybe this antivirus provider isn't as well known to consumers because of its focus on enterprise security, but Trend Micro antivirus security quietly brings its business expertise to the home with its Trend Micro Maximum Security tools. Trend Micro's software earns high marks from AV-Test -- consistently scoring well for detecting zero-day attacks and widespread viruses and malware. Trend Micro also does a good job of not taxing system resources.

Easy setup antivirus subscription
Eset nod32 antivirus.
If you're looking for something easy to set up and use, ESET NOD32 antivirus may meet your needs. It earns high scores for usability and offers solid virus protection. A five-device option is $70 for a year, with a 30-day free trial.

Free anti-malware antivirus
Sophos home.
The free antivirus version of Sophos Home gives you virus protection for 10 Windows PCs or MacOS devices and unlimited Android and iOS devices -- using the company's high-scoring anti-malware tool -- plus a 30-day trial of the company's malware removal tool. Annual subscriptions typically cost $60, but right now you can sign up for less.

How we test antivirus software
We're here to help you find the antivirus software that best fits your needs. These picks of the best antivirus programs are a combination of recommendations from independent third-party labs AV-Test , AV-Comparatives and SE Labs , as well as CNET's anecdotal hands-on testing.
Note that antivirus software is only one piece of the cybersecurity puzzle. Cybercriminals are becoming more sophisticated, and the more steps you take to lock down your online security, the safer you'll be. A secure virtual private network can help protect your internet privacy, and a password manager can help protect your personal information.
Why we don't recommend Avast
Test after test, Avast Antivirus for Windows performs well for malware detection with options ranging from Avast free antivirus software to Avast Premium Security. We've included its antivirus in our list of recommended security app options before. Avast was in the news for several months for its non-antivirus business, so we looked at the company, specifically reports at the end of 2019 that Avast allegedly collected user data with its browser plug-ins and antivirus software and then sold data it collected through its Jumpshot subsidiary in early 2020.
In response to the reports that his company gathered and sold the details of its customers' online activities, Avast CEO Ondrej Vlcek said in a statement that he understood that his company's actions raised questions of trust in his company. To address that, Avast terminated Jumpshot data collection in January 2020 and closed its operations because the data collection business wasn't in line with Avast's privacy priorities.
Those reports followed another in 2019 from Avast that its internal network was breached , possibly to insert malware into its CCleaner software, similar to an earlier CCleaner hack that occurred before Avast acquired the Windows utility.
Avast started saying the right things about taking its customers' privacy seriously , but it only came to that point after reacting to investigative reporting that revealed the Jumpshot practices. (The CCleaner revelations, while concerning, were self-disclosed, which is important to building user trust.) We hope Avast's more privacy-friendly policies mean that there will be no further Jumpshot-style activities and that it returns to glory as one of the best antivirus software options. In the meantime, we'd recommend using one of the many other solid choices in this realm (listed above).
What about Kaspersky?
Let's talk about Kaspersky Lab, specifically about the 2024 federal ban , announced on June 20, prohibiting Kaspersky from directly or indirectly selling antivirus or cybersecurity software or services in the US or to US citizens. This sweeping ban follows a more limited one in 2017 that prohibited Kaspersky software and services on federal government computers because of alleged ties between Kaspersky and the Russian government.
Based in Moscow, Kaspersky Lab has for years produced some of the highest-rated antivirus software for business antivirus needs and home customers. Its software consistently earned top scores and awards for virus and malware detection and endpoint protection from independent testing labs.
“Russia has shown time and again they have the capability and intent to exploit Russian companies, like Kaspersky Lab, to collect and weaponize sensitive US information, and we will continue to use every tool at our disposal to safeguard US national security and the American people," Secretary of Commerce Gina Raimondo said in the official announcement of the ban.
In a statement , Kaspersky said it "does not engage in activities which threaten US national security and, in fact, has made significant contributions with its reporting and protection from a variety of threat actors that targeted US interests and allies."
The Commerce Department recommends those who use Kaspersky software switch to replacement software from other security companies as soon as possible. To aid Kaspersky customers with the transition, Kaspersky will be allowed to provide antivirus updates to its software till Sept. 29, 2024, the department said.
Antivirus basics: What to look for
Picking the best antivirus software for Windows means finding one that keeps your PC safe, doesn't take up a lot of system resources, is easy to use and stays out of the way till you need it. Here's what to look for.
Effectiveness: Antivirus software runs virus scans for known viruses and malware and can offer real-time protection. It watches for shady websites and suspicious links to keep you out of trouble. It can also offer ransomware protection and monitor unexpected behavior that may be a sign of new and not-yet-identified viruses and malware. You want antivirus software that can successfully identify these unknown online threats without flagging too many false positives.
Light on system resources: You don't want antivirus software that taxes your PC's resources. If after you install the program, websites open slowly, apps download or open sluggishly or file copies take longer than expected, you may want to try another service. The good news is that all our picks offer a free trial or money-back guarantee to let you try out the antivirus program, so if your system feels sluggish after installation, you may want to keep looking.
Cost and discounts: Don't just pay the sticker price for antivirus protection. Before you buy, check for discounts on a company's website. Another way to save: The prices we list above are for 10 devices -- if the company offered that package -- but you can trim your cost with antivirus packages if you need to cover three or five devices. You may also find discounts on an app's Amazon page.
Privacy: To be effective, antivirus software needs to monitor what's going on with your PC, check in with company servers about unusual behavior and provide sound banking protection. The companies say they anonymize this technical data as much as possible to protect your privacy. If you want to know more, the security companies on our list post privacy policies on their websites, so read their privacy statements to learn what the companies do with the information you share.
Protection for other platforms: Microsoft is by far the biggest target for viruses and malware. Android is second , with just under 1% of apps installed on Android devices with Google Play Protect in the potentially harmful app, or PHA, category.
The threat to MacOS and especially iOS is low, in part because of the tight control Apple has over its app stores. While the Mac does come under attack via side-loaded apps, it's rare, and if you download apps only from the Mac and iOS app stores and keep your guard up when clicking links and downloading files, you should be OK without an antivirus app on Apple devices.
Antivirus FAQ
Can antivirus protect against phishing.
To a degree, yes. Some antivirus programs can do things like warn you or block you from visiting a suspected phishing site. Others may also automatically block suspicious emails that appear to come from a malicious sender or contain phrasing common in phishing emails. You cannot count on an antivirus program to be a failsafe solution for phishing protection. You still need to be vigilant and know what to look out for on your own when it comes to phishing because an antivirus program won't be able to catch everything.
Will antivirus slow down my computer?
Any program running on your computer will require a certain amount of processing power to work, which can affect your computer's overall performance. If an antivirus program is just running in the background, it shouldn't have any effect on your computer's performance. When actively running a scan of your system, antivirus software can noticeably slow down your computer . If this is the case, try to schedule antivirus scans at night, or at a time when you're not using your computer.
Does my Mac need antivirus?
There is a common misconception that Macs are inherently immune to malware. As Macs continue to increase in popularity, they're increasingly attractive targets for cybercriminals looking to deploy malware designed for the MacOS operating system. MacOS has a built-in antivirus solution called XProtect that can detect and remove malware. It works in the background and updates automatically to keep up with the latest threats, but it still may not catch everything that a third-party antivirus program will. So if you want to play it safe and boost the malware protection on your Mac, it's a good idea to add a third-party antivirus solution.
Services and Software Guides
- Best iPhone VPN
- Best Free VPN
- Best Android VPN
- Best Mac VPN
- Best Mobile VPN
- Best VPN for Firestick
- Best VPN for Windows
- Fastest VPN
- Best Cheap VPN
- Best Password Manager
- Best Antivirus
- Best Identity Theft Protection
- Best LastPass Alternative
- Best Live TV Streaming Service
- Best Streaming Service
- Best Free TV Streaming Service
- Best Music Streaming Services
- Best Web Hosting
- Best Minecraft Server Hosting
- Best Website Builder
- Best Dating Sites
- Best Language Learning Apps
- Best Weather App
- Best Stargazing Apps
- Best Cloud Storage
- Best Resume Writing Services
- New Coverage on Operating Systems
- Home Products
- Small Business 1-49 employees
- Medium Business 50-999 employees
- Enterprise 1000+ employees
A Brief History of Computer Viruses & What the Future Holds

When it comes to cybersecurity, there are few terms with more name recognition than "computer viruses." Despite the prevalence of these threats and their wide-spread impact, however, many users don't know about the basic nature of viruses. What follows is a brief history of the computer virus, and what the future holds for this widespread cyber threat.
Theory of Self-Replicating Automata
What is a computer virus? This idea was first discussed in a series of lectures by mathematician John von Neumann in the late 1940s and a paper published in 1966, Theory of Self-Reproducing Automata . The paper was effectively a thought experiment that speculated that it would be possible for a "mechanical" organism—such as a piece of computer code—to damage machines, copy itself and infect new hosts, just like a biological virus.
The Creeper Program
As noted by Discovery, the Creeper program, often regarded as the first virus, was created in 1971 by Bob Thomas of BBN. Creeper was actually designed as a security test to see if a self-replicating program was possible. It was—sort of. With each new hard drive infected, Creeper would try to remove itself from the previous host. Creeper had no malicious intent and only displayed a simple message: "I'M THE CREEPER. CATCH ME IF YOU CAN!"
The Rabbit Virus
According to InfoCarnivore , the Rabbit (or Wabbit) virus was developed in 1974, did have malicious intent and was able to duplicate itself. Once on a computer, it made multiple copies of itself, severely reducing system performance and eventually crashing the machine. The speed of replication gave the virus its name.
The First Trojan
Called ANIMAL, the first Trojan (although there is some debate as to whether this was a Trojan, or simply another virus) was developed by computer programmer John Walker in 1975, according to Fourmilab . At the time, "animal programs," which try to guess which animal the user is thinking of with a game of 20 questions, were extremely popular. The version Walker created was in high demand, and sending it to his friends meant making and transmitting magnetic tapes. To make things easier, Walker created PERVADE, which installed itself along with ANIMAL. While playing the game, PREVADE examined all computer directories available to the user and then made a copy of ANIMAL in any directories where it wasn't already present. There was no malicious intent here, but ANIMAL and PREVADE fit the definition of a Trojan: Hiding inside ANIMAL was another program that carried out actions without the user's approval.
The Brain Boot Sector Virus
Brain, the first PC virus, began infecting 5.2" floppy disks in 1986. As Securelist reports, it was the work of two brothers, Basit and Amjad Farooq Alvi, who ran a computer store in Pakistan. Tired of customers making illegal copies of their software, they developed Brain, which replaced the boot sector of a floppy disk with a virus. The virus, which was also the first stealth virus, contained a hidden copyright message, but did not actually corrupt any data.
The LoveLetter Virus
The introduction of reliable, speedy broadband networks early in the 21st century changed the way malware was transmitted. No longer confined to floppy disks or company networks, malware was now able to spread very quickly via email, via popular websites or even directly over the Internet. As a result, modern malware began to take shape. The threat landscape became a mixed environment shared by viruses, worms and Trojans—hence the name "malware" as an umbrella term for malicious software. One of the most serious epidemics of this new era was the LoveLetter, which appeared on May 4, 2000.
As Securelist notes, it followed the pattern of earlier email viruses of the time, but unlike the macro viruses that had dominated the threat landscape since 1995, it didn't take the form of an infected Word document, but arrived as a VBS file. It was simple and straightforward, and since users hadn't learned to be suspicious of unsolicited emails, it worked. The subject line was "I Love You," and each email contained an attachment, "LOVE-LETTER-FOR-YOU-TXT.vbs." The ILOVEYOU creator, Onel de Guzman, designed his worm to overwrite existing files and replace them with copies of itself, which were then used to spread the worm to all the victims' email contacts. Since the message often came to new victims from someone familiar, they were more likely to open it, making ILOVEYOU a proof-of-concept for the effectiveness of social engineering.
The Code Red Virus
The Code Red worm was a "file less" worm—it existed only in memory and made no attempt to infect files on the system. Taking advantage of a flaw in the Microsoft Internet Information Server, the fast-replicating worm wreaked havoc by manipulating the protocols that allow computers to communicate and spread globally in just hours. Eventually, as noted in Scientific American , compromised machines were used to launch a distributed denial of service attack on the Whitehouse.gov website.
One of the most recent of the major viruses came out in 2014, Heartbleed burst onto the scene and put servers across the Internet at risk. Heartbleed, unlike viruses or worms, stems from a vulnerability in OpenSSL, a general purpose, open source cryptographic library used by companies worldwide. OpenSSL periodically sends out "heartbeats" to ensure that secure endpoints are still connected. Users can send OpenSSL a specific amount of data and then ask for the same amount back—for example, one byte. If users claim they're sending the maximum allowed, 64 kilobytes, but only send a single byte, the server will respond with the last 64 kilobytes of data stored in RAM, notes security technologist, Bruce Schneier , which could include anything from user names to passwords to secure encryption keys.
The Future of Computer Viruses
For more than 60 years, computer viruses have been part of collective human consciousness, however what was once simply cyber vandalism has turned quickly to cybercrime. Worms, Trojans and viruses are evolving. Hackers are motivated and clever, always willing push the boundaries of connection and code to devise new infection methods. The future of cybercrime seems to involve more PoS (point of sale) hacks, and, perhaps, the recent Moker remote access Trojan is a good example of what's to come. This newly-discovered malware is hard to detect, difficult to remove and bypasses all known defenses. Nothing is certain—change is the lifeblood of both attack and defense.
Other helpful reads and links related to Computer Viruses
- What is a Computer Virus or a Computer Worm?
- How to Fend Off a Computer Virus
- What is a Trojan Virus?
- What is a Boot Sector Virus?
- What is a Stealth Virus?
- What is a Macro Virus?
A Brief History of Computer Viruses & What the Future Holds
Featured articles.

HTML Attachments: A Gateway for Malware?

Understanding BlackCat ransomware: Threat overview and protective measures

Black Friday Scams: How to Shop Safely Online

What is a dark web scan?

Optogenetics, the Big Revolution in Brain Study
Intellectual abilities of artificial intelligence, openmind books, scientific anniversaries, edward o. wilson and island biodiversity, featured author, latest book, the history of computer viruses.
On November 10, 1983, a handful of seminar attendees at Lehigh University, Pennsylvania, USA, heard for the first time the term “virus” applied to computing. The use of the word was strange. The virus that was then on everyone’s mind was the one isolated a few months earlier at the Pasteur Institute in Paris that could be the cause of a new disease called AIDS. In the digital world, talking about viruses was almost nonsense. The first PC had been launched on the market just two years earlier and only the most technologically informed were running an Apple II computer or one of its early competitors.

However, when on that day the graduate student from the University of Southern California Fred Cohen inserted a diskette into a VAX11/750 mainframe computer, the attendees noted how code hidden in a Unix program installed itself and took control in a few minutes , replicating and spreading to other connected machines, similar to a biological virus.
Cohen tells OpenMind that it was on November 3 when a conversation with his supervisor, Leonard Adleman, led to the idea of giving the name of virus to that code capable of infecting a network of connected computers. The Cohen virus was simple: “The code for reproduction was perhaps a few lines and took a few minutes to write,” says the author. “The instrumentation and controls took almost a day.”
Cohen published his creation in 1984, in an article that began: “This paper defines a major computer security problem called a virus.” But though the extensive research of Cohen and Adleman in the specialized literature would draw attention to their existence, the truth is that before that first virus defined as such appeared, there had already been earlier cases.
Interactive timeline: A malware history
[+] Full screen
Catch me if you can
In 1971, Robert Thomas, from the company BBN, created Creeper , a program that moved between computers connected to ARPANET and that displayed the message “I’m the creeper: catch me if you can.” According to David Harley, IT security consultant and researcher for the ESET company, “in the research community, we usually consider the experimental program Creeper to be the first virus and/or worm.”
Moreover, a year before Cohen’s seminar, 15-year-old Rich Skrenta developed Elk Cloner, the first computer virus—not named that yet—that spread outside a laboratory. Skrenta created it as a joke for his friends, whose Apple II computers became infected by inserting a diskette with a game that hid the virus.
So, Cohen was not really the first one. But according what computer security expert Robert Slade explains to OpenMind, the special thing in Cohen’s case was not so much his programming as his method. “He was doing the original academic research on the concept; his structure of antiviral software is still comprehensive despite all the developments since.” Cohen also introduced an informal definition of virus: “a program that can infect other programs by modifying them to include a, possibly evolved, version of itself.”
Those first viruses were technological demonstrations. The motivation of their creators was research and their codes were not malicious. Cohen points out that the objective of his program was “to measure spread time, not to attack.” In the case of Creeper , it was about designing a mobile application that could move to the machine where the data resided, instead of going the other way. As the professor of Computer Science at the University of Calgary (Canada) John Aycock points out to OpenMind, computer viruses were born as “a natural product of human curiosity.” And as such, “their invention was inevitable.”
The first malicious codes
It was also inevitable that the first malicious codes would soon emerge. In 1986, Brain appeared, a virus created by two Pakistani brothers whose purpose was to punish the users of IBM computers who installed a pirated copy of software developed by them. However, the effects of Brain were slight and the virus included the contact information of its authors so that those affected could contact them and request a cure. Spread by means of diskettes, Brain reached international diffusion, giving rise to the birth of the first antivirus companies.

At the end of the 1980s, codes began to proliferate that erased data or disabled systems. In 1988, the worm created by Robert Morris infected many of the computers connected to the then nascent Internet, especially in research institutions, causing a drop in email services. Its effects were more damaging than anticipated by Morris himself, who became the first person to be prosecuted in the US under the Computer Fraud and Abuse Act of 1986.
In this way, so-called malware began to diversify into different families: worms are programs that move from one computer to another without hiding in another application, while Trojans are harmful programs with an innocent appearance. In 1995, WM/Concept appeared, which infected Word documents. “It opened the door for a plague of document-borne malware that dominated the threat landscape for several years after,” says Harley. The expert lists other typologies that have emerged over time, such as bots that manipulate other people’s systems to launch spam campaigns, send malware or denial of service attacks; or ransomware , codes that hijack a system and force the payment of a ransom, such as the recent case of WannaCry , which in May 2017 infected hundreds of thousands of computers in more than 150 countries.

To this threat landscape we must add the current media, such as social networks, which facilitate the expansion of malware. As explained to OpenMind by Jussi Parikka, expert in technological culture at the Winchester School of Art of the University of Southampton (United Kingdom) and author of Digital Contagions: A Media Archeology of Computer Viruses (2nd ed., Peter Lang Publishing, 2016), “the online platforms for communication and interaction are themselves part of the problem due to their various security issues.”
But despite the many headaches caused by the malware, experts point out that these developments can benefit other technologies. Cohen argues that “benevolent” viruses can, for example, be useful in maintaining and updating systems. “I think artificial life (reproducing programs) still have enormous potential, largely unrealized as of today,” he reflects. “History will tell, but I still hold hope that viral computation will be a benefit to humanity in the future.”
Javier Yanes
More publications related to this article, more about technology, artificial intelligence, digital world, visionaries, more publications about ventana al conocimiento (knowledge window), comments on this publication.
Morbi facilisis elit non mi lacinia lacinia. Nunc eleifend aliquet ipsum, nec blandit augue tincidunt nec. Donec scelerisque feugiat lectus nec congue. Quisque tristique tortor vitae turpis euismod, vitae aliquam dolor pretium. Donec luctus posuere ex sit amet scelerisque. Etiam sed neque magna. Mauris non scelerisque lectus. Ut rutrum ex porta, tristique mi vitae, volutpat urna.
Sed in semper tellus, eu efficitur ante. Quisque felis orci, fermentum quis arcu nec, elementum malesuada magna. Nulla vitae finibus ipsum. Aenean vel sapien a magna faucibus tristique ac et ligula. Sed auctor orci metus, vitae egestas libero lacinia quis. Nulla lacus sapien, efficitur mollis nisi tempor, gravida tincidunt sapien. In massa dui, varius vitae iaculis a, dignissim non felis. Ut sagittis pulvinar nisi, at tincidunt metus venenatis a. Ut aliquam scelerisque interdum. Mauris iaculis purus in nulla consequat, sed fermentum sapien condimentum. Aliquam rutrum erat lectus, nec placerat nisl mollis id. Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Nam nisl nisi, efficitur et sem in, molestie vulputate libero. Quisque quis mattis lorem. Nunc quis convallis diam, id tincidunt risus. Donec nisl odio, convallis vel porttitor sit amet, lobortis a ante. Cras dapibus porta nulla, at laoreet quam euismod vitae. Fusce sollicitudin massa magna, eu dignissim magna cursus id. Quisque vel nisl tempus, lobortis nisl a, ornare lacus. Donec ac interdum massa. Curabitur id diam luctus, mollis augue vel, interdum risus. Nam vitae tortor erat. Proin quis tincidunt lorem.
Echolocation: The Sixth Sense of Humans?
Do you want to stay up to date with our new publications.
Receive the OpenMind newsletter with all the latest contents published on our website
OpenMind Books
- The Search for Alternatives to Fossil Fuels
- View all books
About OpenMind
Connect with us.
- Keep up to date with our newsletter
Close panel
Press Enter
Predictive Search
- Analysis and Opinion
- Sustainability
- Life and Culture
- Coronavirus
- Seeds for the future
- BBVA Earnings
- Corporate information
- BBVA financial information
- Financial calendar
- Latest news
- BBVA Podcast
- Customer service via social networks
- Special reports
- Careers at BBVA
- Social media
- Vulnerability Disclosure Program
- Chair’s message
- CEO’s message
- History of BBVA
- BBVA in the world
- Organizational chart
- Sustainability and responsible banking model
- Corporate Presentation
- Code of Conduct
- BBVA’s tax strategy
- BBVA Due Diligence
- BBVA in 2023
- Annual Report
- Financial reports
- Relevant events
- Issuances and programs
- Biographies
- Photos Directors / Executive Leadership Team
- Download center
- Seeds the future
- The road to economic recovery: the evolution of COVID-19´s impact on consumption
- BBVA in Asia
- Sustainable Development Goals
- Annual General Meeting
- Trading floor
- Ciudad BBVA
- BBVA's Historical Archive
- BBVA Research
- Open Innovation
- BBVA Foundation
- Full website list
- English Español
- BBVA in brief
- Organization chart
- Business areas
- Strategy: BBVA’s transformation
- Presentations
- Financial data
- Risk management
- Share information
- Capital information
- Shareholders remuneration
- Equity analysts
- Significant events
Shareholders
- Financial products
- Shareholders club
- Shareholders and Investors Communication and Contact Policy
Debt investors
- Issuing companies
- Maturity profile
- Fixed Income Analysts
- Contact debt investors
Sustainability and Responsible Banking
- Sustainability strategy
- Sustainable Financing
- Principles and policies
- Presentation and Reports
- Sustainability ratings
- Responsible taxation
- Average payment period suppliers
- Contacts Responsible Banking
Corporate Governance and Remuneration Policy
- Corporate Bylaws
- General Meeting Regulations
- Information related AGM held
- Board Regulations
- Board of Directors
- Board Committees
- Director's Remuneration
- Information related to Identified Staff
- Annual Corporate Governance Report
- Information Circular 2/2016 of Bank of Spain
- BBVA Policy on Conduct in the Securities Markets
- Information related to integration transactions
- Shareholders and investors
- BBVA in the World
Antivirus software guide: what are they for and how to use them
To browse the internet safely and keep their computers properly up to date, users have a great ally: antivirus software. This quick guide will help you understand the value these tools provide, the protection they offer, and how to make the most out of them.

Nowadays, it’s hard to find a personal or corporate computers that doesn’t run some sort of antivirus software. Users are familiar with the updates that are periodically executed. But, do we take advantage of all the possibilities that AV software offers? This article reviews the main features of this type of security software that you should be aware of to make the most of them.
When was the first antivirus created?
The history of antivirus software is, of course, linked to the history of computer viruses or 'malware'. Prior to the 1980s, some experiments had been conducted with programs able to automatically spread between computers, but it was during this decade when the first viruses capable of deleting data or disabling systems were created and launched. The first commercial antivirus software programs hit the stores shortly after. One of the pioneering companies was G Data , a German company that in 1987 developed a product to safeguard Atari computers. That same year, McAfee released the first iteration of its wildly popular 'antimalware' suite, VirusScan .

How do antivirus software programs work?
The main purpose of AV software is to is to detect, neutralize or eradicate malware (or 'malicious software) from computers and devices, even before the system becomes infected.
To identify a malicious attack, an antivirus software will run scans comparing the files stored in the operating system of its host computer with a database containing the distinctive features (or 'signatures') of previously detected instances of 'malware'. This database must be updated regularly to include the signatures of the new types of 'malware' that constantly emerge.. Some antivirus software, in addition, have the ability to detect threats by identifying patterns in files, locating system alterations and monitoring computer component behavior.
Today’s antivirus software packages therefore fulfill a double mission: analyzing, one by one, the files stored in the computer against the signature database, and monitoring the device to detect any unusual activity.
Contrary to what one might think, having more than one antivirus installed on the same device is detrimental . This is because antivirus packages can mistakenly detect as 'malware' - and therefore attempt to block - each other, leaving devices unprotected.
What threats do antivirus programs keep us safe from?
Antivirus software programs protect against several types of malware:
- Viruses are malicious software in camouflaged as user files. They are designed to access computers without consent or knowledge from users and usually intended to steal information, delete documents or change settings.
- Computer worms are programs capable o f replicating functional copies of themselves through a network , with the aim of causing both computers and computer networks to collapse. One of the most successful worm attacks took place in 2000 and infected over 50 million computers, causing losses totaling over €5 billion. It spread as an 'email' message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs.” Opening the attachment executed the code, hijacking the host computer and forwarding the message to all the user's email addresses. Thus, it spread across the world in just 24 hours.
- 'Trojans' are a type of 'malware' concealed under the appearance of legitimate software which work properly. When executed, a Trojan allows the attacker to access the computer, and even to control it remotely.

- 'Spyware' is, as its own name indicates, a spy program that infects computers and devices to collect all sort of user information: habits, personal information, bank information, etc. Keyloggers are a type of spyware: a malicious program that, once installed, records all keystrokes made by the user. This technique is widely used to steal credentials.
- Ransomware is a type of malware that hijacks the information stored in the computer, perpetually encrypting and blocking the files unless their Rightful owners pay a ransom. The biggest 'ransomware' attack took place in 2017. The WannaCry ransomware cryptoworm infected thousands of computers in more than one hundred countries and resulted in costs estimated at more than €200 million.
How do viruses spread?
The most common way viruses find their way onto computers is through emails. All it takes is for the user to download an attachment or install a program downloaded via a malicious link to get the host computer infected with malicious code. To prevent this from happening, it is very important:
- Be wary of emails that may seem in any way suspicious (from unknown senders, unexpected emails urging to take action, containing an unusual amount of spelling errors or awkward sentences.)
- Activate 'antispam' filters to block unwanted or harmful mail and be careful when opening an email tagged as such.
- Think twice before downloading attachments.
- Before clicking on a link included in an emails, hover over the mouse to check the address to which it redirects.
Another typical vector of infections is any piece of software downloaded from unofficial sources devices when downloading and installing programs that come from untrustworthy sites, that appear in pop-up windows or in advertising or included in emails from unknown senders.
Plugging infected external devices to your computer - normally a 'pendrive', disk drive, or any device that you are not sure where it came from or lent to you by other people - is another typical way of getting your computer infected. And also vice versa: When you plug your devices to unknown sources such as public charging stations.
How effective are antivirus?
There are no fully effective methods to protect users against 100 percent of online 'malware' threats. Cybercrime is a very lucrative, ever evolving business. To keep up, antivirus companies need to constantly update their signature databases and quickly come up with new detection algorithms to detect new threats as they emerge.
An antivirus alone is not enough to protect your computer. You need to develop safe habits and never let your guard down against social engineering attacks, such as phishing emails and vishing attacks via phone call. In short, an antivirus cannot protect you against deception techniques used in social engineering assaults.
On which devices should you install an antivirus?
The number of connected devices and appliances grows on a daily basis and they are all exposed to being infected with some type of 'malware'.
Besides laptop and desktop computers, it is highly advisable to use antivirus software on mobile devices such as 'smartphones' and tablets , and on any connected devices. There are already some antivirus programs that monitor household data traffic to protect cameras, SmartTVs, printers, consoles, etc.
Which antivirus should you choose?
There are plenty of free and paid security alternatives in the market. The Internet Security Office publishes a comprehensive analysis of the free antivirus suites available and their features, to help users choose the one that better meets their needs . Most of these free antivirus also offer subscription services for additional features such as password managers and automatic program updates. In addition, paid antivirus platforms do not show ads.
Users can also check many articles online that rank the best antivirus suites based on the results they have earned in technical tests. One example is the list published by specialized publication Virus Bulletin or trustedantivirusreview.com , which also collects user opinions.
For more generic advice on computer, tablet and smartphone maintenance, American nonprofit Privacy Rights Clearinghouse has published a comprehensive privacy protection guide on its website.
And finally, what type of maintenance does an antivirus require?
The only maintenance antivirus software programs require is to enable periodic updates. New virus threats emerge every day from all across the globe. As soon as they are detected and analyzed, antivirus publishers include them in their signature databases to effectively protect users’ computers, devices and objects connected to the Internet.
In conclusion, antivirus programs are becoming increasingly sophisticated and provide a very high level of security: they are, without a doubt, the best ally users can rely on to protect themselves from 'malware' attacks and their consequences. But remember: the first link in the security chain is still the individual.
Keep reading about
- Cybersecurity
Share on Mastodon
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

education technology
239 templates
computer technology
306 templates

ai technology
186 templates
cyber security
10 templates

meet the teacher
30 templates
first day of school
70 templates
Protecting Your Computer: Antivirus
It seems that you like this template, protecting your computer: antivirus presentation, free google slides theme, powerpoint template, and canva presentation template.
Having the right antivirus installed on your computer is a must. Everyone knows this, yet some people still choose not to install some antivirus software and protect their computers. This is when your antivirus presentation comes into action! Help others choose to protect their computers by informing them on the risks of cyberattacks and viruses they can suffer without the right protection. Capture everyone’s attention with these cute flat illustrations of users, computers and potential viruses. Download this template now and present the importance of antivirus!
Features of this template
- 100% editable and easy to modify
- 36 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides, Canva, and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the resources used
How can I use the template?
Am I free to use the templates?
How to attribute?
Attribution required If you are a free user, you must attribute Slidesgo by keeping the slide where the credits appear. How to attribute?
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access

This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Microsoft Defender Antivirus in Windows Overview
- 4 contributors
Applies to:
- Microsoft Defender for Endpoint Plans 1 and 2
- Microsoft Defender for Business
- Microsoft Defender Antivirus
Microsoft Defender Antivirus is available in Windows 10 and Windows 11, and in versions of Windows Server.
Microsoft Defender Antivirus is a major component of your next-generation protection in Microsoft Defender for Endpoint. This protection brings together machine learning, big-data analysis, in-depth threat resistance research, and the Microsoft cloud infrastructure to protect devices (or endpoints) in your organization. Microsoft Defender Antivirus is built into Windows, and it works with Microsoft Defender for Endpoint to provide protection on your device and in the cloud.
As a companion to this article, see our Security Analyzer setup guide to review best practices and learn to fortify defenses, improve compliance, and navigate the cybersecurity landscape with confidence. For a customized experience based on your environment, you can access the Security Analyzer automated setup guide in the Microsoft 365 admin center.
Microsoft Defender Antivirus capabilities
Microsoft Defender Antivirus provides anomaly detection, a layer of protection for malware that doesn't fit any predefined pattern. Anomaly detection monitors for process creation events or files that are downloaded from the internet. Through machine learning and cloud-delivered protection, Microsoft Defender Antivirus can stay one step ahead of attackers. Anomaly detection is on by default and can help block attacks such as 3CX Security Alert for Electron Windows App . Microsoft Defender Antivirus started blocking this malware four days before the attack was registered in VirusTotal.
Modern malware requires modern solutions. In 2015, Microsoft Defender Antivirus moved away from using a static signature-based engine to a model that uses predictive technologies such as, machine learning, applied science, and artificial intelligence as this is what's necessary to keep you and your organizations safe from the complexity of today's ever-evolving malware landscape.
Microsoft Defender Antivirus can block almost all malware at first sight, in milliseconds.
We've also designed our antivirus solution to work in both online and offline scenarios. For offline scenarios, the latest dynamic intelligence from the Intelligence Security Graph is provisioned to the endpoint regularly throughout the day. When connected to the cloud, it's fed real-time intelligence from the Intelligent Security Graph .
Microsoft Defender Antivirus can also stop threats based on their behaviors and process trees even when the threat has started execution. A common example of these kinds of attacks is fileless malware. Microsoft's Next-generation protection features work together to identify and block malware based on abnormal behavior. To learn more, see Behavioral blocking and containment .
Compatibility with other antivirus products
If you're using a non-Microsoft antivirus/antimalware product on your device, you might be able to run Microsoft Defender Antivirus in passive mode alongside the non-Microsoft antivirus solution. It depends on the operating system used and whether your device is onboarded to Defender for Endpoint. To learn more, see Microsoft Defender Antivirus compatibility .
Microsoft Defender Antivirus processes and services
The following table summarizes Microsoft Defender Antivirus processes and services. You can view them in Task Manager in Windows.
| Process or service | Where to view its status |
|---|---|
| ( ) | - tab: - tab: - tab: |
| ( ) | - tab: - tab: - tab: |
| ( ) | - tab: - tab: - tab: |
| - tab: N/A - tab: - tab: N/A | |
| - tab: N/A - tab: - tab: N/A |
To learn more about the Microsoft Defender Core service, please visit Microsoft Defender Core service overview .
For Microsoft Endpoint Data Loss Prevention (Endpoint DLP), the following table summarizes processes and services. You can view them in Task Manager in Windows.
| Process or service | Where to view its status |
|---|---|
| ( ) | - tab: - tab: - tab: |
| - tab: N/A - tab: - tab: N/A |
Comparing active mode, passive mode, and disabled mode
The following table describes what to expect when Microsoft Defender Antivirus is in active mode, passive mode, or disabled.
| Mode | What happens |
|---|---|
| Active mode | In active mode, Microsoft Defender Antivirus is used as the primary antivirus app on the device. Files are scanned, threats are remediated, and detected threats are listed in your organization's security reports and in your Windows Security app. |
| Passive mode | In passive mode, Microsoft Defender Antivirus is not used as the primary antivirus app on the device. Files are scanned, and detected threats are reported, but threats are not remediated by Microsoft Defender Antivirus. : Microsoft Defender Antivirus can run in passive mode only on endpoints that are onboarded to Microsoft Defender for Endpoint. See . |
| Disabled or uninstalled | When disabled or uninstalled, Microsoft Defender Antivirus is not used. Files are not scanned, and threats are not remediated. In general, we do not recommend disabling or uninstalling Microsoft Defender Antivirus. |
To learn more, see Microsoft Defender Antivirus compatibility .
Check the state of Microsoft Defender Antivirus on your device
You can use one of several methods, such as the Windows Security app or Windows PowerShell, to check the state of Microsoft Defender Antivirus on your device.
Beginning with platform version 4.18.2208.0 and later : If a server has been onboarded to Microsoft Defender for Endpoint, the "Turn off Windows Defender" group policy setting will no longer completely disable Windows Defender Antivirus on Windows Server 2012 R2 and later. Instead, it will place it into passive mode. In addition, the tamper protection feature will allow a switch to active mode but not to passive mode.
- If "Turn off Windows Defender" is already in place before onboarding to Microsoft Defender for Endpoint, there will be no change and Defender Antivirus will remain disabled.
- To switch Defender Antivirus to passive mode, even if it was disabled before onboarding, you can apply the ForceDefenderPassiveMode configuration with a value of 1 . To place it into active mode, switch this value to 0 instead.
Note the modified logic for ForceDefenderPassiveMode when tamper protection is enabled: Once Microsoft Defender Antivirus is toggled to active mode, tamper protection will prevent it from going back into passive mode even when ForceDefenderPassiveMode is set to 1 .
Use the Windows Security app to check the status of Microsoft Defender Antivirus
On your Windows device, select the Start menu, and begin typing Security . Then open the Windows Security app in the results.
Select Virus & threat protection .
Under Who's protecting me? , choose Manage Providers .
You'll see the name of your antivirus/antimalware solution on the security providers page.
Use PowerShell to check the status of Microsoft Defender Antivirus
Select the Start menu, and begin typing PowerShell . Then open Windows PowerShell in the results.
Type Get-MpComputerStatus .
In the list of results, look at the AMRunningMode row.
Normal means Microsoft Defender Antivirus is running in active mode.
Passive mode means Microsoft Defender Antivirus running, but is not the primary antivirus/antimalware product on your device. Passive mode is only available for devices that are onboarded to Microsoft Defender for Endpoint and that meet certain requirements. To learn more, see Requirements for Microsoft Defender Antivirus to run in passive mode .
EDR Block Mode means Microsoft Defender Antivirus is running and Endpoint detection and response (EDR) in block mode , a capability in Microsoft Defender for Endpoint, is enabled. Check the ForceDefenderPassiveMode registry key. If its value is 0, it is running in normal mode; otherwise, it is running in passive mode.
SxS Passive Mode means Microsoft Defender Antivirus is running alongside another antivirus/antimalware product, and limited periodic scanning is used .
To learn more about the Get-MpComputerStatus PowerShell cmdlet, see the reference article Get-MpComputerStatus .
Performance tip Due to a variety of factors (examples listed below) Microsoft Defender Antivirus, like other antivirus software, can cause performance issues on endpoint devices. In some cases, you might need to tune the performance of Microsoft Defender Antivirus to alleviate those performance issues. Microsoft's Performance analyzer is a PowerShell command-line tool that helps determine which files, file paths, processes, and file extensions might be causing performance issues; some examples are:
- Top paths that impact scan time
- Top files that impact scan time
- Top processes that impact scan time
- Top file extensions that impact scan time
- top files per extension
- top paths per extension
- top processes per path
- top scans per file
- top scans per file per process
You can use the information gathered using Performance analyzer to better assess performance issues and apply remediation actions. See: Performance analyzer for Microsoft Defender Antivirus .
Get your antivirus/antimalware platform updates
It's important to keep Microsoft Defender Antivirus (or any antivirus/antimalware solution) up to date. Microsoft releases regular updates to help ensure that your devices have the latest technology to protect against new malware and attack techniques. To learn more, see Manage Microsoft Defender Antivirus updates and apply baselines .
If you're looking for Antivirus related information for other platforms, see:
- Set preferences for Microsoft Defender for Endpoint on macOS
- Microsoft Defender for Endpoint on Mac
- macOS Antivirus policy settings for Microsoft Defender Antivirus for Intune
- Set preferences for Microsoft Defender for Endpoint on Linux
- Microsoft Defender for Endpoint on Linux
- Configure Defender for Endpoint on Android features
- Configure Microsoft Defender for Endpoint on iOS features
- Performance analyzer for Microsoft Defender Antivirus
- Microsoft Defender Antivirus management and configuration
- Evaluate Microsoft Defender Antivirus protection
- Exclusions for Microsoft Defender for Endpoint and Microsoft Defender Antivirus
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community .
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Computer Virus and its Types
A computer virus is a kind of malicious computer program, which when executed, replicates itself and inserts its own code. When the replication is done, this code infects the other files and program present on your system.
These computer viruses are present in various types and each of them can infect a device in a different manner.
In this article, we shall discuss in detail what is a computer virus and what are its different types. Also, we will read on to know what is an Anti-virus and how it can nullify a virus in our computer devices, along with some sample questions from the competitive exam point of view.
To know more about the Fundamentals of Computer , visit the linked article.
Apart from being aware of what a computer virus is, this topic is even important for candidates preparing for Government exams. Major competitive exams in the country comprise Computer Knowledge as an integral part of the syllabus and questions based on virus and anti-virus can also be expected in these exams.
Thus, to excel in the upcoming Govt exams, aspirants must go through this article in detail and carefully study the different types of viruses.
|
|
What is a Computer Virus?
A computer virus is a program which can harm our device and files and infect them for no further use. When a virus program is executed, it replicates itself by modifying other computer programs and instead enters its own coding. This code infects a file or program and if it spreads massively, it may ultimately result in crashing of the device.
Across the world, Computer viruses are a great issue of concern as they can cause billions of dollars’ worth harm to the economy each year.

Since the computer virus only hits the programming of the device, it is not visible. But there are certain indications which can help you analyse that a device is virus-hit. Given below are such signs which may help you identify computer viruses:
- Speed of the System – In case a virus is completely executed into your device, the time taken to open applications may become longer and the entire system processing may start working slowly
- Pop-up Windows – One may start getting too many pop up windows on their screen which may be virus affected and harm the device even more
- Self Execution of Programs – Files or applications may start opening in the background of the system by themselves and you may not even know about them
- Log out from Accounts – In case of a virus attack, the probability of accounts getting hacked increase and password protected sites may also get hacked and you might get logged out from all of them
- Crashing of the Device – In most cases, if the virus spreads in maximum files and programs, there are chances that the entire device may crash and stop working
The first thing which you might notice in case of virus attack is the speed with which your system shall process. And then gradually other changes can also be observed.
Types of Computer Virus
Discussed below are the different types of computer viruses:
- Boot Sector Virus – It is a type of virus that infects the boot sector of floppy disks or the Master Boot Record (MBR) of hard disks. The Boot sector comprises all the files which are required to start the Operating system of the computer. The virus either overwrites the existing program or copies itself to another part of the disk.
- Direct Action Virus – When a virus attaches itself directly to a .exe or .com file and enters the device while its execution is called a Direct Action Virus. If it gets installed in the memory, it keeps itself hidden. It is also known as Non-Resident Virus.
- Resident Virus – A virus which saves itself in the memory of the computer and then infects other files and programs when its originating program is no longer working. This virus can easily infect other files because it is hidden in the memory and is hard to be removed from the system.
- Multipartite Virus – A virus which can attack both, the boot sector and the executable files of an already infected computer is called a multipartite virus. If a multipartite virus attacks your system, you are at risk of cyber threat.
- Overwrite Virus – One of the most harmful viruses, the overwrite virus can completely remove the existing program and replace it with the malicious code by overwriting it. Gradually it can completely replace the host’s programming code with the harmful code.
- Polymorphic Virus – Spread through spam and infected websites, the polymorphic virus are file infectors which are complex and are tough to detect. They create a modified or morphed version of the existing program and infect the system and retain the original code.
- File Infector Virus – As the name suggests, it first infects a single file and then later spreads itself to other executable files and programs. The main source of this virus are games and word processors.
- Spacefiller Virus – It is a rare type of virus which fills in the empty spaces of a file with viruses. It is known as cavity virus. It will neither affect the size of the file nor can be detected easily.
- Macro Virus – A virus written in the same macro language as used in the software program and infects the computer if a word processor file is opened. Mainly the source of such viruses is via emails.
Government exam aspirants can check the links given below for the detailed section-wise syllabus for the other subjects apart from Computer Awareness:
How To Protect Your Computer from Virus?
The most suitable way of making your computer virus-free is by installing an Anti-virus software. Such software help in removing the viruses from the device and can be installed in a computer via two means:
- Online download
- Buying an Anti-virus software and installing it
Further below, we bring to you details as to what anti-virus is and what are its different types along with a few examples.
Moving further, candidates can also refer to the following links to learn more about Computer Knowledge and prepare themselves accordingly:
- Difference Between RAM and ROM
- Difference Between MS Excel and MS Word
- Difference Between IPV4 and IPV 6
- Difference Between Firewall and Antivirus
- Difference Between WWW and Internet
- Difference Between Notepad and WordPad
- Difference Between Virus and Malware
What is an Anti-Virus?
An anti-virus is a software which comprises programs or set of programs which can detect and remove all the harmful and malicious software from your device. This anti-virus software is designed in a manner that they can search through the files in a computer and determine the files which are heavy or mildly infected by a virus.
Given below is a list of few of the major antivirus software which is most commonly used:
- Norton Antivirus
- F-Secure Antivirus
- Kaspersky Antivirus
- AVAST Antivirus
- Comodo Antivirus
- McAfee Antivirus
These are few of the many anti-virus software widely used to remove viruses from a device.
Sample Questions on Computer Virus and Anti-Virus
As discussed above, Computer Awareness is a common topic for major Government exams and questions based on Computer Virus and Antivirus may also be asked in the exam.
Thus, given below are a few sample computer virus questions and answers for the assistance of aspirants.
Q 1. Which of the following is not a type of computer virus?
- Polymorphic virus
- Space filler virus
- Multipartite virus
- Boot sector virus
Answer: (4) Trojan
Q 2. Which of these was the first computer virus?
- Crypto Locker
- Morris Worm
Answer: (1) Creeper
Solution: Creeper was the first-ever computer virus and was an experimental self-replicating virus released in the year 1971.
Q 3. Which of the following is not a source of the virus entering your system?
- All of the above
- None of the above
Answer: (5) All of the above
Q 4. The other name for Non-Resident virus is _________
- Direct Action Virus
- Boot Sector Virus
- Multipartite Virus
- Overwrite Virus
- Polymorphic Virus
Answer: (1) Direct Action Virus
Q 5. Which of the following viruses is also known as “Cavity Virus”?
- Space Filler Virus
Answer: (2) Space Filler Virus
For more questions to ace the upcoming competitive exams, aspirants can visit the articles given below:
- Free Online Government Exam Quiz
- Free Online Mock Test Series with Solutions
- Previous Year Govt Exam Question Papers PDF with Solutions
Also, to get the best Preparation Strategy for Competitive exams , candidates can visit the linked article.
Get the latest exam information and study material at BYJU’S and keep yourself updated.
Frequently Asked Questions on Computer Virus and its Types
Q 1. what is the definition of a computer virus, q 2. what are the main computer viruses.
Ans. The main types of computer virus are as follows:
- Resident Virus
- File Infector Virus
Q 3. What is the Creeper Virus?
Q 4. what are the examples of a computer virus.
Ans. Given below are a few examples of a computer virus:
- CryptoLocker
Q 5. How to secure a computer system from a virus attack?

| Government Exams Related Links | |
Leave a Comment Cancel reply
Your Mobile number and Email id will not be published. Required fields are marked *
Request OTP on Voice Call
Post My Comment
Connect with us for Free Preparation
Get access to free crash courses & video lectures for all government exams., register with byju's & download free pdfs, register with byju's & watch live videos.
Get the Reddit app
Best free anti virus according to reddit in 2024.
I've seen various recommendations on here for the best free antivirus software. After doing some research, I think these are the top options: Avast Free Antivirus, AVG AntiVirus Free, and Avira Free Security. They all offer solid features like real-time protection and malware detection. However, I'm having trouble deciding which one to choose, so I'm hoping you can help:
1. Avast Free Antivirus: Known for its robust features, including real-time protection, anti-phishing, and a Wi-Fi inspector. Users often praise its user-friendly interface and regular updates.
2. AVG AntiVirus Free: Offers excellent malware detection and features like email scanning and web protection. Its simple interface and decent performance make it a solid choice.
3. Avira Free Security: Recognized for its strong malware detection capabilities and low system impact. It also includes a VPN service and a privacy-focused browser extension.
While these options seem promising, I'm struggling to make a final decision. Have you had any experiences with these antivirus programs, or do you have other recommendations that have worked well for you? Please share your thoughts and insights – your input could help many of us make a more informed choice in our quest for a reliable free antivirus solution.
Kaspersky released a free Linux virus removal tool - but is it necessary?

No operating system is 100% safe. As long as your computer is connected to a network, there is always the possibility that it can be compromised. These compromises can come by way of viruses, malware, or ransomware , each of which holds a particular danger.
Such a possibility is why Kaspersky released its Virus Tool for Linux. According to the official announcement the "application can scan system memory, startup objects, boot sectors, and all files in the operating system for known malware. It scans files of all formats -- including archived ones."
Antivirus solutions for the Linux operating system are not plentiful, and for good reason. I've been vocal about this topic for years, landing on the side that Linux doesn't need such solutions .
Also: Do you need antivirus on Linux?
But for those migrating from Windows, antivirus tools are ingrained in the psyche, and using the OS without them may feel like a danger no one should take. On top of that, virus creators are getting more sophisticated to the point where the security of nothing (not even Linux) is certain. Although Linux itself is about as safe an operating system as you'll ever use, malicious code is finding its way into open-source projects. Should a malicious application make its way to your Linux desktop, there's no guarantee the operating system alone will be able to prevent bad things from happening.
I decided to kick the tires of Kaspersky's new tool, with the help of the EICAR malware test files to see if it could catch anything. I saved the files to my home directory and then copied the .txt version of the file to /usr/lib. I also downloaded the EICAR COM and ZIP files (saving them to the same directories).
To my surprise, the Kaspersky tool did not detect any of the EICAR files in my ~/ directory but did catch all files copied to /usr/lib. Once found, it gave me the options to Disinfect, Delete, Copy to Quarantine, or Skip. It then gave me the option to disinfect with or without a reboot.
Also: The NSA advises you to turn your phone off and back on once a week - here's why
It didn't take me long to figure out why the EICAR files in the home directory weren't found. By default, the Kaspersky tool for Linux doesn't scan user's home directories. To make that happen, you have to go to Settings and then add /home as an object.
Once I did that, the app caught the files in my home directory and gave me the same options it did when it discovered them in /usr/lib.
I'm not saying you should shrug off the idea of an antivirus solution for Linux because who knows what the future holds. But that Kaspersky has created a free tool for Linux users shouldn't be discounted.
You can download the new Kaspersky tool from the official download page . Once you've downloaded it, you'll need to give it executable permissions with the command:
To run the application, you can either right-click the downloaded file and select Run As Program, or issue the command (from within the directory housing the file):
You'll be asked for your sudo password before the app will run.
If you're paranoid about viruses on your computer, this is certainly as good an antivirus option as you'll find for Linux. The one caveat is that the Kaspersky Antivirus for Linux doesn't work in real-time (you have to run it manually every time). Even so, it's good to know companies like Kaspersky have Linux's back.
The best antivirus software and apps you can buy
Thinking about switching to linux 10 things you need to know, the us bans kaspersky products, citing security risks - what this means for you.
- Ultimate Combo

- Sign Out Sign Out Sign In
35 Best Antivirus-Themed Templates for PowerPoint & Google Slides
With over 6 million presentation templates available for you to choose from, crystalgraphics is the award-winning provider of the world’s largest collection of templates for powerpoint and google slides. so, take your time and look around. you’ll like what you see whether you want 1 great template or an ongoing subscription, we've got affordable purchasing options and 24/7 download access to fit your needs. thanks to our unbeatable combination of quality, selection and unique customization options, crystalgraphics is the company you can count on for your presentation enhancement needs. just ask any of our thousands of satisfied customers from virtually every leading company around the world. they love our products. we think you will, too" id="category_description">crystalgraphics creates templates designed to make even average presentations look incredible. below you’ll see thumbnail sized previews of the title slides of a few of our 35 best antivirus templates for powerpoint and google slides. the text you’ll see in in those slides is just example text. the antivirus-related image or video you’ll see in the background of each title slide is designed to help you set the stage for your antivirus-related topics and it is included with that template. in addition to the title slides, each of our templates comes with 17 additional slide layouts that you can use to create an unlimited number of presentation slides with your own added text and images. and every template is available in both widescreen and standard formats. with over 6 million presentation templates available for you to choose from, crystalgraphics is the award-winning provider of the world’s largest collection of templates for powerpoint and google slides. so, take your time and look around. you’ll like what you see whether you want 1 great template or an ongoing subscription, we've got affordable purchasing options and 24/7 download access to fit your needs. thanks to our unbeatable combination of quality, selection and unique customization options, crystalgraphics is the company you can count on for your presentation enhancement needs. just ask any of our thousands of satisfied customers from virtually every leading company around the world. they love our products. we think you will, too.
Widescreen (16:9) Presentation Templates. Change size...

Antivirus artery bacteria biology blood cell in blue

A shield with binary numbers in the background

Presentation enhanced with composite of letters and numbers with grid patterns over cloudscape copy space nature antivirus abstract danger spyware computer virus and technology concept

PPT layouts consisting of hand touching antivirus inscription cybersecurity concept

Presentation theme consisting of mysterious man with antivirus inscription online security concept

Presentation theme consisting of faceless hacker with antivirus inscription on a binary code background

Presentation with group of people having a meeting with antivirus insciption web security concept

Slide set featuring man dressed as a businessman posing in a studio on a gray background medical face mask rear view a light striped shirt and tie - casual office wear concept of quarantine and antivirus protection

Theme featuring young handsome business man engineer in businessman hold rainbow colored umbrella in server datacenter room and representing security and antivirus sofware protection concept

Slides featuring young handsome business man engineer in businessman hold rainbow colored umbrella in server datacenter room and representing security and antivirus sofware protection concept background

Theme consisting of young handsome business man engineer in businessman hold rainbow colored umbrella in server datacenter room and representing security and antivirus sofware protection concept background

PPT theme enhanced with man dressed as a businessman posing in a studio on a gray background medical face mask glasses a light striped shirt and tie - casual office wear concept of quarantine and antivirus protection

PPT layouts consisting of man dressed as a businessman posing in a studio on a gray background medical face mask rear view a light striped shirt and tie - casual office wear concept of quarantine and antivirus protection

PPT theme featuring man puts on protective medical gloves dressed as a businessman posing in studio on gray background medical face mask glasses shirt and tie - concept of quarantine and antivirus protection

PPT theme consisting of man puts on protective medical gloves dressed as a businessman posing in studio on gray background medical face mask glasses shirt and tie - concept of quarantine and antivirus protection backdrop

Presentation design consisting of man with a mask on his face for antivirus individual protection showing a pill - healthcare and medicine concept prevention tips background

Slide deck featuring man with a mask on his face for antivirus individual protection showing a pill - healthcare and medicine concept prevention tips

Slide deck consisting of man with a mask on his face for antivirus individual protection showing a pill - healthcare and medicine concept prevention tips

Theme enhanced with man dressed as a businessman posing in a studio on a gray background medical face mask glasses a light striped shirt and tie - casual office wear concept of quarantine and antivirus protection

Slides with man dressed as a businessman posing in a studio on a gray background medical face mask glasses a light striped shirt and tie - casual office wear concept of quarantine and antivirus protection

Slide set featuring man with a mask on his face for antivirus individual protection showing a pill - healthcare and medicine concept prevention tips

Slides featuring man with a mask on his face for antivirus individual protection puts on medical sterile gloves - healthcare and medicine concept prevention tips backdrop

Theme consisting of man puts on protective medical gloves dressed as a businessman posing in studio on gray background medical face mask glasses shirt and tie - concept of quarantine and antivirus protection

Slide deck featuring asian woman in antivirus mask stands in the middle of a deserted street in cloudy weather

PPT theme having man with a mask on his face for antivirus individual protection showing a pill - healthcare and medicine concept prevention tips

PPT theme enhanced with man with a mask on his face for antivirus individual protection showing a pill - healthcare and medicine concept prevention tips

Slide deck with man dressed as businessman posing in studio on gray background medical face mask and protective gloves shirt and tie demonstrate hand sanitizer - concept of quarantine and antivirus protection

Theme enhanced with asian woman in antivirus mask stands in the middle of a deserted street in cloudy weather young multicultural female pandemic covid-19 coronovirus backdrop

Presentation design featuring man with a mask on his face for antivirus individual protection showing a pill - healthcare and medicine concept prevention tips

Theme featuring rear view of a businessman with antivirus inscription cyber security concept

Presentation having man dressed as businessman posing in studio on gray background medical face mask and protective gloves shirt and tie demonstrate hand sanitizer - concept of quarantine and antivirus protection

Presentation with ambulance concept - technologies healthcare data recovering online help antivirus

Theme having business people and cyber protection concept - close up of man with virtual antivirus program shield icon over gray background

Slide set with man in an antivirus mask is talking on the phone walking down a city street background
More antivirus presentation templates.

Company Info

IMAGES
VIDEO
COMMENTS
Definition, types, and benefits. Antivirus software monitors your devices for known threats and eliminates or stops them from infecting your devices as quickly as possible. With reliable security software like Norton AntiVirus Plus, your personal data will be better protected from hackers, malware, viruses, and other online threats.
Updated June 11, 2024. An academic paper in 1984 coined the term "computer virus," and antivirus companies quickly sprang up to fight this scourge. More than 35 years ago, back in the DOS days ...
A computer virus is a type of malware that can spread to your computer and cause damage. Computer viruses can steal sensitive information, sap your device's performance, or completely disable it. Read on to learn what the different types of computer virus are, how they work, and how a cutting-edge antivirus solution like Avira Free Security ...
Antivirus software (abbreviated to AV software ), also known as anti-malware, is a computer program used to prevent, detect, and remove malware . Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect against other ...
A virus infects a file or system. Computer viruses attach themselves to a piece of software, an online program, a file, or a piece of code. They can spread through email and text message attachments, files you download online, or scam links sent on social media. 2. An unsuspecting user executes the virus's code.
A computer virus is a type of malicious software, or malware, that spreads between computers and causes damage to data and software. Computer viruses aim to disrupt systems, cause major operational issues, and result in data loss and leakage. A key thing to know about computer viruses is that they are designed to spread across programs and systems.
Norton LifeLock has consistently earned high marks from AV-Test, AV-Comparatives and SE Labs for virus and malware detection. Norton antivirus provides excellent security software for PC, Mac and ...
Hex dump of the Brain virus, generally regarded as the first computer virus for the IBM Personal Computer (IBM PC) and compatibles. A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus ...
The Rabbit Virus. According to InfoCarnivore, the Rabbit (or Wabbit) virus was developed in 1974, did have malicious intent and was able to duplicate itself. Once on a computer, it made multiple copies of itself, severely reducing system performance and eventually crashing the machine. The speed of replication gave the virus its name.
A computer virus works by inserting or attaching itself to a legitimate program or document that supports macros. Once the virus has successfully attached, it lies dormant until certain conditions trigger its execution. Once a virus has infected a program, file, or document, it remains inactive until the infected program is run.
Cohen tells OpenMind that it was on November 3 when a conversation with his supervisor, Leonard Adleman, led to the idea of giving the name of virus to that code capable of infecting a network of connected computers. The Cohen virus was simple: "The code for reproduction was perhaps a few lines and took a few minutes to write," says the author.
Antivirus software programs protect against several types of malware: Viruses are malicious software in camouflaged as user files. They are designed to access computers without consent or knowledge from users and usually intended to steal information, delete documents or change settings. Computer worms are programs capable o f replicating ...
A virus which hides its presence from the computer user and anti-virus programs, usually by trapping interrupt services. Transmission Control Protocol/Internet Protocol. The collective name for the standard internet protocols. computer program with (undesirable) effects that are not described in its specification.
antivirus software to each computer in your organization may not be sufficient. Recent outbreaks have spread with alarming speed, faster than the software industry's ability to detect, identify, and deliver antivirus tools that are capable of protecting against attack. The techniques demonstrated by the latest forms of
Free Google Slides theme, PowerPoint template, and Canva presentation template. Having the right antivirus installed on your computer is a must. Everyone knows this, yet some people still choose not to install some antivirus software and protect their computers. This is when your antivirus presentation comes into action!
A computer virus is a piece of code that gets implanted in a program and is constructed with the ability to self-replicate; affecting other programs on a computer. It's just like how humans get a cold or flu, it can remain dormant within the system and get activated when you least expect it. A virus has the potential to cause unexpected ...
Introduction Antivirus software consists of computer programs that attempt to identify, thwart and eliminate computer viruses and other malicious software (malware). Malware or Malicious Software is software designed to infiltrate or damage a computer system without the owner's informed consent. Types of malware include spyware, adware, Trojan ...
Use PowerShell to check the status of Microsoft Defender Antivirus. Select the Start menu, and begin typing PowerShell. Then open Windows PowerShell in the results. Type Get-MpComputerStatus. In the list of results, look at the AMRunningMode row. Normal means Microsoft Defender Antivirus is running in active mode.
Presentation on computer viruses - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. Computer viruses have become a major news topic with the rise of internet usage making it easier for viruses to spread. A computer virus is a program that can self-replicate and spread ...
Since all the products we're looking at offer virus and malware protection, we'll focus on the extra features they have, along with pricing, awards, and pros and cons. Here are the antivirus software solutions we'll cover: Norton 360 Deluxe. Avast Premium Security. Avira Antivirus Pro. Bitdefender Total Security.
Microsoft Defender isn't bad, but it's still not enough to fully protect your PC. You don't have to pay extra, though. We've tested and ranked the top free antivirus apps.
An anti-virus is a software which comprises programs or set of programs which can detect and remove all the harmful and malicious software from your device. This anti-virus software is designed in a manner that they can search through the files in a computer and determine the files which are heavy or mildly infected by a virus.
Restart your computer. When you see the computer manufacturer's logo, press and hold the F8 key. On the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking, and then press Enter. 4. 5. Log on to your computer with a user account that has administrator rights.
Since the initial scare of early computer viruses, these antivirus programs have been deemed a necessity. However, that isn't necessarily true. These days, antivirus software is a frivolous ...
3. Unusually slow performance. If your computer was hacked and malware is running on it, you may see slow performance. Applications may take a long time to open, web pages may take a long time to ...
New viruses are created and released often, and without antivirus software, the files and folders on the computer are at risk. If antivirus software is installed on your computer, you might need to update your antivirus software definitions. Many HP and Compaq computers with Windows come with Windows Security.
1. Avast Free Antivirus: Known for its robust features, including real-time protection, anti-phishing, and a Wi-Fi inspector. Users often praise its user-friendly interface and regular updates. 2. AVG AntiVirus Free: Offers excellent malware detection and features like email scanning and web protection. Its simple interface and decent ...
No operating system is 100% safe. As long as your computer is connected to a network, there is always the possibility that it can be compromised. These compromises can come by way of viruses ...
Founded in Moscow in 1997, Kaspersky Lab grew into one of the world's most successful anti-virus software companies alongside American rivals like McAfee and Symantec.
35 Best Antivirus-Themed Templates. CrystalGraphics creates templates designed to make even average presentations look incredible. Below you'll see thumbnail sized previews of the title slides of a few of our 35 best antivirus templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text.