
- AppAssessor

Articles by role:
- Consultants
- Business Analysts
By Lucy Mazalon
By Ben McCarthy
- Courses Login
What’s trending
How Does Salesforce’s Agentforce Work?
A Salesforce Professional’s Guide to Process Mapping
SF Ben Salesforce Salary Survey Results 2024-25
5 Important Best Practices for Optimizing Salesforce
Salesforce’s New Free AI Certifications: Your Guide to Courses and Premium Training
UPCOMING EVENTS
Northeast dreamin’.
Manchester, NH
GRAX Dinner & Discover for Salesforce Community
Amsterdam, Netherlands
Have Your Cake and Eat It Too: How to Innovate Faster in Salesforce Without Compromising Quality
6 things to consider before turning on agentforce, elevate your salesforce devops lifecycle with test automation, custom permissions in salesforce: fine-tuning user access.
By Andreea Doroftei
In this post, we will explore how Salesforce Admins can easily set up component visibility and functionality access so that there is no need to even think about hardcoding user IDs or compromising on your current profile setup.
Salesforce Custom Permissions

Create a Custom Permission in Salesforce

Use Cases for Salesforce Custom Permissions
1. validation rules and formulas.

2. Lightning Page Filters

3. In-App Guidance

4. Salesforce Flow

Final Thoughts
Andreea doroftei.
Andreea is a Salesforce Technical Instructor at Salesforce Ben. She is an 18x certified Salesforce Professional with a passion for User Experience and Automation.

More like this:
The ultimate guide to heroku and salesforce integration.
By Richa Pokhriyal
How to Set Up Gamification in Salesforce Experience Cloud to Boost Engagement
By Olesia Melnichenko
Salesforce List Views vs. Reports: Which Is Best to Use?
By Stacy O’Leary
Leave a Reply Cancel reply
Save my name and email in this browser for the next time I comment.
- App Building
- Be Release Ready – Winter ’25
- Integration
- Salesforce Well-Architected ↗
- See all products ↗
- Career Resources
- Salesforce Admin Skills Kit
- Salesforce Admin Enablement Kit
- Career Paths ↗
- Trailblazer Career Marketplace ↗
- Trailblazer Community Online ↗
- Trailblazer Community Group Meetings ↗
Home » Article » Allow Certain Users to Edit Data Using Custom Permissions in Validation Rules

Allow Certain Users to Edit Data Using Custom Permissions in Validation Rules
In a previously published blog post, Why You Should Add Custom Permissions to Your #AwesomeAdmin Tool Belt , I introduced you to custom permissions. This feature has been around since Winter ’15 but remains fairly unknown and underutilized by the admin community. Admins can use this superpower to lock or unlock user access to apps or processes.
In this blog post, we’ll focus on how admins can use custom permissions in validation rules to either permit or deny a user from bypassing the validation rule.
Business problem
Amanda Merkle, Operations Manager, approached admin Addison Dogster and noted that all users are currently able to edit accounts categorized as advisor accounts, which should not be the case. Only selected Operations and Customer Service Rep (CSR) users should have the ability to edit advisor accounts — they should be off limits to everyone else.
The solution
Addison immediately thought of using a validation rule to prevent people from updating these advisor accounts, but she didn’t want to hard code users as the exception. Hard coding references will cause maintenance issues down the road as users change over time. Addison would have to modify the validation rule each time a user is removed or added. (Check out the Why You Should Avoid Hard Coding and Three Alternative Solutions blog post for more information.)
A better design is to use a custom permission to grant selected users access to edit the advisor accounts. As noted in the Why You Should Add Custom Permissions to Your #AwesomeAdmin Tool Belt blog post, in order to grant a custom permission to a user, it must be associated at the profile or permission set level. In this case, since Addison needs to grant access to selected users in the Operations and CSR profile, she needs to associate the custom permission in a permission set which she will then assign to the selected users.
In summary, Addison’s solution comprises of:
- A custom permission
- A permission set
- A validation rule
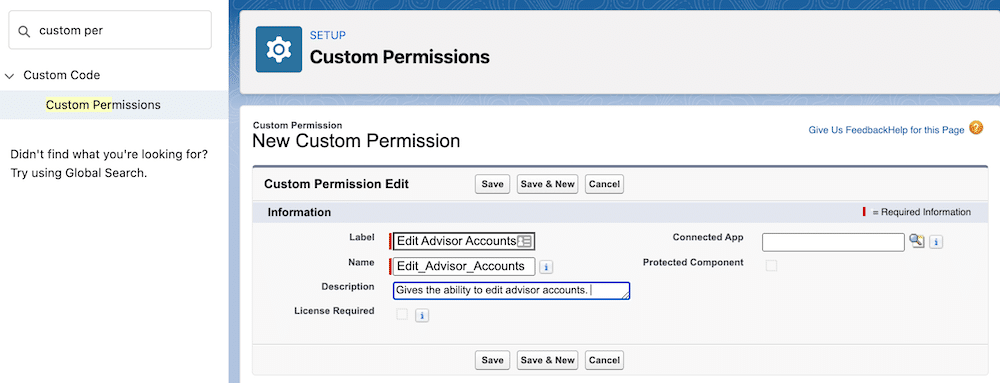
Addison first creates the custom permission. In Setup, search for ‘Custom Permissions’ in the Quick Find box. Create a new custom permission. Provide the label, name (API name), and description. The description should further describe the purpose of the custom permission and possibly where it’s used.
Addison creates the custom permission with these attributes:
- Label: Edit Advisor Accounts
- Name: Edit_Advisor_Accounts
- Description: Gives the ability to edit advisor accounts.
Next, she associates the custom permission to the permission set. In Setup, search for ‘permission sets’ in the Quick Find box.
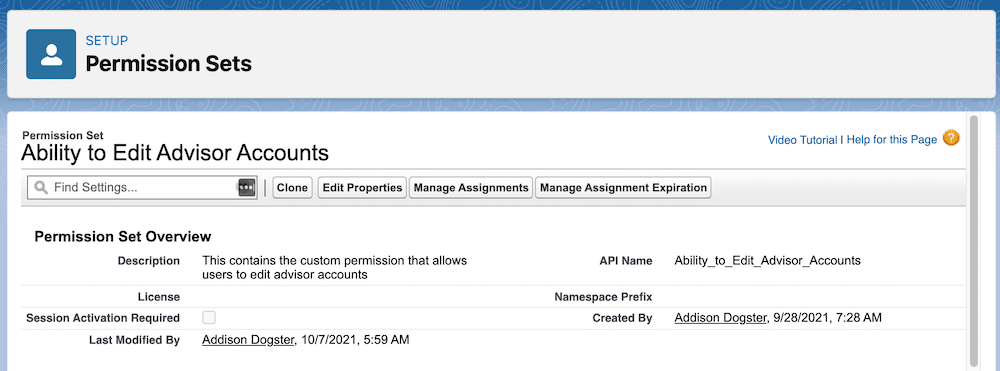
Addison creates a new permission set with these attributes:
- Label: Ability to Edit Advisor Accounts
- API Name: Ability_to_Edit_Advisor_Accounts
- Description: This contains the custom permission that allows users to edit advisor accounts
- License (optional): You can select the specific license to use.
Then, Addison enables the custom permission by adding it to the permission set.
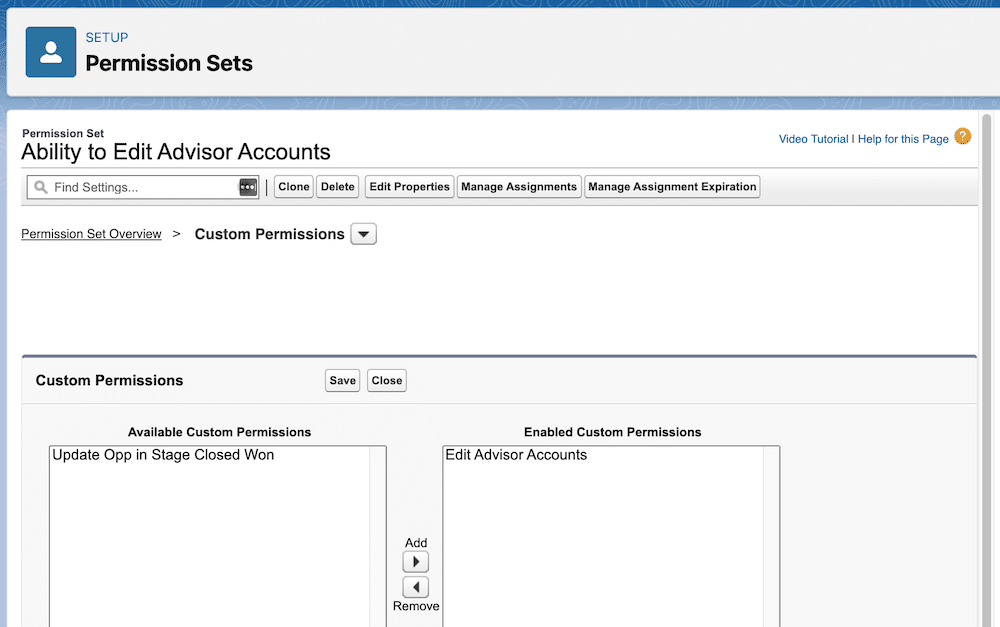
Now, any user she assigns to the permission set will automatically get the custom permission.
Lastly, Addison creates the validation rule that will only permit users with the custom permission to edit advisor accounts. The advisor accounts in Addison’s org are accounts with the Advisor record type. In Setup, navigate to Object Manager | Account | Validation Rule.
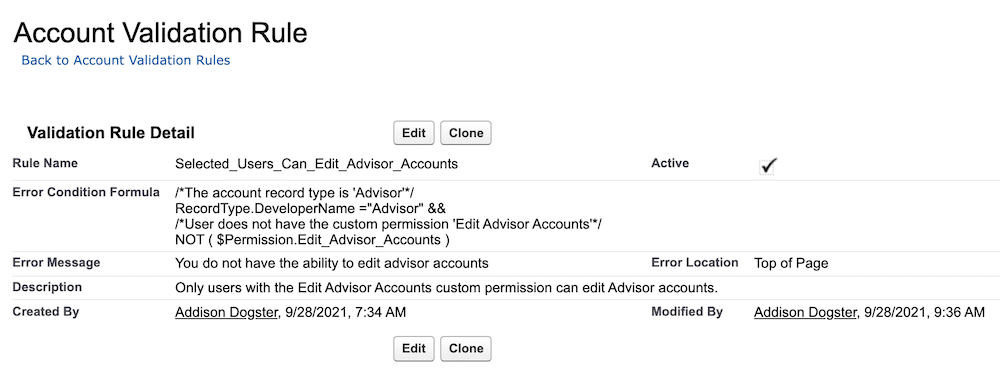
She creates the validation rule with these attributes:
- Rule Name: Selected_Users_Can_Edit_Advisor_Accounts
- Active: Checked
- Description: Only users with the Edit Advisor Accounts custom permission can edit Advisor accounts.
- Error Condition Formula:
/*The account record type is ‘Advisor’*/ RecordType.DeveloperName =”Advisor” && /*User does not have the custom permission ‘Edit Advisor Accounts’*/ NOT ( $Permission.Edit_Advisor_Accounts )
This error condition checks whether the account record type developer name is Advisor AND that the user does not have the custom permission with the API name Edit_Advisor_Accounts. If this is true, it will display the validation rule error. However, for any user with the custom permission, no validation rule error will be displayed.
Pro-tip: Awesome admins reference the developer name or API names when possible as opposed to the field label, as the field label is more subject to change than the API name. You can also add comments in your formula to describe it by using “/*<description>*/.”
- Error Message: You do not have the ability to edit advisor accounts
- Error Location: Top of Page
The below animated gif shows the quick configuration of enabling the custom permission in the permission set and referencing the custom permission in the validation rule.
Business results
With the implementation of this solution, Addison was able to enforce cleaner data by only allowing selected individuals the ability to update the advisor accounts. By referencing the custom permission in the validation rule, Addison implemented a better design that avoided hard-coded permission management in the validation rule. Rather, permission management to edit advisor accounts is done via permission sets, which can be delegated to non-system administrators to manage.
Addison assigned the Edit Advisor Accounts permission set to Jared Dunn. Jared is able to edit the advisor account without issues as he has the Edit Advisor Accounts custom permission, so the validation rule does not fail when it executes. However, when Addison tries to edit the advisor account herself (Note: She is not assigned to the Edit Advisor Accounts permission set), the validation rule error is shown, prohibiting her from modifying the account record.
Now, it’s YOUR TURN!
Now that you know how to configure a custom permission in a validation rule, I want you to try this yourself. I’m sure you have use cases where this admin superpower can come in handy. Share with us how you use custom permissions in a validation rule to grant or deny access to your users on Twitter using #AwesomeAdmin.
- Salesforce Security Guide: Custom Permissions
- Salesforce Admins Blog: Why You Should Add Custom Permissions to Your #AwesomeAdmin Tool Belt
- Salesforce Admins Blog: Why You Should Avoid Hard Coding and Three Alternative Solutions
Jennifer W. Lee
Jennifer is a Lead Admin Evangelist at Salesforce and the host of our live streamed series Automate This! She is Flownatic, 8x certified Application Architect, Trailhead enthusiast, and Golden Hoodie recipient. Prior to joining Salesforce, Jen was a Koa customer, blogger (Jenwlee.com), founding co-host of Automation Hour, and a Salesforce MVP (2016-2021).
- Jen’s Top Winter ’25 Release Features | Be Release Ready
- Jen’s Top Summer ’24 Release Features | Be Release Ready
- Einstein for Formulas | Spring ’24
- Jen’s Top Spring ’24 Release Features
Related Posts

Connect Teams and Data with the New Salesforce Foundations
By Hannah Freeman | September 17, 2024
As Salesforce Admins, you’re well-versed in delivering Salesforce features to your users and stakeholders. Now, we’re making it even easier for you to get the most out of Salesforce by adding cross-department features built into your existing CRM. The exciting news from Dreamforce ’24 is Salesforce Foundations, which brings built-in, key features to Sales Cloud […]

Closing the Loop on Past True to the Core Sessions: Where Do We Stand Today?
By Tuhina Koppikar | September 12, 2024
True to the Core is a favorite session at Dreamforce and TDX, especially for admins who want an opportunity to connect with Salesforce executives and product managers on the topics that are most important to you. True to the Core offers an unfiltered look into our product development plans, and gives you the chance to […]

Conditional Field Formatting | Winter ’25 Be Release Ready
By Elizabeth Martin | September 4, 2024
Winter ’25 is almost here! Learn more about Conditional Field Formatting and check out Be Release Ready to discover more resources to help you prepare for Winter ’25. The challenge with configuring visual indicators today Creating custom visual indicators to call attention to key fields is a common Salesforce configuration requirement. Visual indicators make it […]


Blog Posts Downloadable Resources Step-by-Step Guides
Step By Step Guide to Custom Permission in Salesforce

Custom Permissions in Salesforce are used to give access to users for certain apps or processes that you have configured and which cannot be controlled by profile or permission set directly.
A profile and a permission set control the users’ access to many entities such as objects, fields, tabs, and Visualforce pages. However, they cannot control a custom process that you have which is unique to your business. For e.g. only specific users should be able to edit an Opportunity once it is Closed Won or save records bypassing validation rules. To manage these granularities, you can leverage Custom Permissions in Salesforce. They let you define checkpoints that can be assigned to users via permission sets or profiles, in the same way how other permissions are assigned to users.
In this guide we will cover how to grant ‘Edit’ on ‘Closed Won’ opportunities to specific users using Custom Permission. After going through this guide, within the next 20 – 25 minutes, you will learn how to:
- Create a Custom Permission
- Create a Permission Set
- Add Custom Permission to Permission Set
- Assign Permission Set to a User
- Create a Validation Rule
- Test Custom Permission
NOTE: Certain sections of the guide will appear as locked in the free preview. You can download the unlocked version of the guide in PDF format by subscribing to our “All Access” Pass through the link below.
Not an “All Access” Pass Member Yet?
Get Download Access to this & 150+ More Step-by-Step Guides with “All Access” Pass. A simple and single plan to access our entire library of courses, guides, workshops & masterclasses on Salesforce.
References & Useful URLs
- Custom Permissions – Help Article (10 mins) – https://help.salesforce.com/articleView?id=sf.custom_perms_overview.htm&type=5
Other Related posts:
- Step By Step Guide To Custom Report Type in Salesforce
- Step by Step Guide to “Custom Error” in Record-Triggered Flow
- Step By Step Guide To Delegated Administration in Salesforce
- Step by Step Guide to Using Data Table in Salesforce Flow
- Data Classification Settings in Salesforce – A Step By Step Guide
8 thoughts on “Step By Step Guide to Custom Permission in Salesforce”
Fantastic!!! Thanks for such great explanation.
My pleasure Lokesh 🙂
Great blog , thank you
Thanks Prithvi!
Clear and to the point. Bravo!
Thanks Sav!
Who knew validation rules could get so specific with the use of custom permissions? Not me. As always, Ashish, thank you for the great step-by-step tutorial!
My pleasure Neil. Thanks for your feedback.
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .


Think. Build. Salesforce Solutions.
Salesforce Consulting Services across Salesforce Clouds & Across App Lifecycles
Home / Resources / Blog
Salesforce Custom Permissions
Custom permissions let you define your own permissions for use in Salesforce. In Salesforce access is defined in many ways more generally in terms of profile, role, sharing roles, permission sets, etc for different entities like Objects, fields, tabs, vf pages, Records.
But for Custom processes and apps access cannot be defined by permission sets and profiles.
Custom permissions let you define access checks that can be assigned to users via permission sets or profiles, similar to how you assign user permissions and other access permissions.
Custom permissions can be used in
1. Validation Rules 2. Apex 3. Lightning Components 4. In formula fields(Automations like Workflow, Processbuilder, Flows field)
Points to Remember
- Enable Custom Permissions in Profiles
- Enable Custom Permissions in Permission Set
- Define dependencies between your Custom Permissions
- Assign Custom Permission to users
Creating Custom Permissions
1. Go to Setup 2. Quick find to filter to Custom Permission 3. Click New 4. Enter a Label & Name 5. Click Save
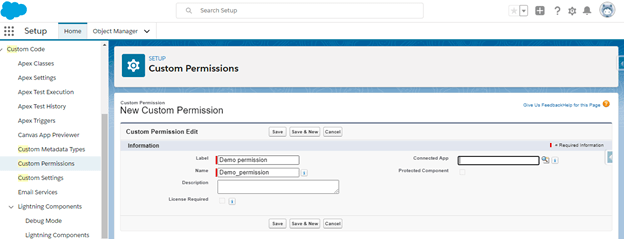
Enable Custom permissions at profile
1. Go to Profiles 2. Go to Enable Custom permissions
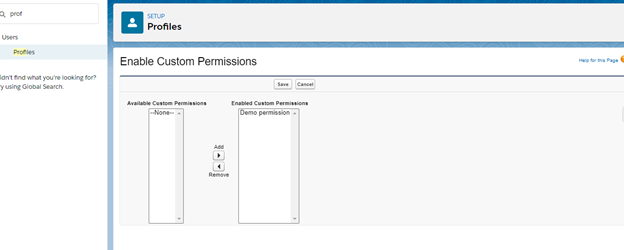
HOW to Query Custom Permissions in Apex
Use the CustomPermission object to determine users’ access to custom permissions.
Select Id, DeveloperName from CustomPermission where DeveloperName=’Demo permission’
Where to Use Custom Permissions
Let’s imagine a scenario where you want to control your Lightning component visibility if user have specific permission set.
Steps to Achieve:
1. Create a custom Permission (named as Demo Permission) 2. Add that custom Permission to permission set 3. Assign that permission to set to user 4. In Lightning Component visibility Filter go to
Permissions—> custom Permission—–> Demo Permission
Leave A Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Andy in the Cloud
From bbc basic to force.com and beyond….

Creating, Assigning and Checking Custom Permissions
January 14, 2015 by Andrew Fawcett 21 Comments
I have been wanting to explore Custom Permissions for a little while now, since they are now GA in Winter’15 i thought its about time i got stuck in. Profiles, Permission Sets have until recently, been focusing on granting permissions to entities only known to the platform, such as objects , fields , Apex classes and Visualforce pages . In most cases these platform entities map to a specific feature in your application you want to provide permission to access.
However there are cases where this is not always that simple. For example consider a Visualforce page you that controls a given process in your application, it has three buttons on it Run , Clear History and Reset . You can control access to the page itself, but how do you control access to the three buttons? What you need is to be able to teach Permission Sets and Profiles about your application functionality , enter Custom Permissions !

NOTE: That you can also define dependencies between your Custom Permissions, for example Clear History and Reset permissions might be dependent on a Manage Important Process custom permission in your package.
Once these have been created, you can reference them in your packaged Permission Sets and since they are packaged themselves, they can also be referenced by admins managing your application in a subscriber org.

The next step is to make your code react to these custom permissions being assigned or not.
New Global Variable $Permission
You can use the $Permission from a Visualforce page or as SFDCWizard points out here from Validation Rules ! Here is the Visualforce page example given by Salesforce in their documentation.
Referencing Custom Permissions from Apex
IMPORTANT UPDATE : Since API 41 (Winter’18) there is now a native way to read Custom Permissions. The following may still be useful if you have requirements not met by the native method. FeatureManagement.checkPermission .
In the case of object and field level permissions, the Apex Describe API can be used to determine if an object or field is available and for what purpose , read or edit for example. This is not going help us here, as custom permissions are not related to any specific object or field. The solution is to leverage the Permission Set Object API to query the SetupEntityAccess and CustomPermission records for Permission Sets or Profiles that are assigned to the current user.
The following SOQL snippets are from the CustomPermissionsReader class i created to help with reading Custom Permissions in Apex (more on this later). As you can see you need to run two SOQL statements to get what you need. The first to get the Id’s the second to query if the user actually has been assigned a Permission Set with them in.
Now personally i don’t find this approach that appealing for general use, firstly the Permission Set object relationships are quite hard to get your head around and secondly we get charged by the platform to determine security through the SOQL governor. As a good member of the Salesforce community I of course turned my dislike into an Idea “Native Apex support for Custom Permissions” and posted it here to recommend Salesforce include a native class for reading these, similar to Custom Labels for example.
Introducing CustomPermissionReader
In the meantime I have set about creating an Apex class to help make querying and using Custom Permissions easier. Such a class might one day be replaced if my Idea becomes a reality or maybe its internal implementation just gets improved. One things for sure, i’d much rather use it for now than seed implicit SOQL’s throughout a code base!
Its pretty straight forward to use, construct it in one of two ways, depending if you want all non-namespaced Custom Permissions or if your developing a AppExchange package, give it any one of your packaged Custom Objects and it will ensure that it only ever reads the Custom Permissions associated with your package.
You can download the code and test for CustomPermissionsReader here.
Like any use of SOQL we must think in a bulkified way, indeed its likely that for average to complex peaces of functionality you may want to check at least two or more custom permissions once you get started with them. As such its not really good practice to make single queries in each case.
For this reason the CustomPermissionsReader was written to load all applicable Custom Permissions and act as kind of cache. In the next example you’ll see how i’ve leveraged the Application class concept from the Apex Enterprise Patterns conventions to make it a singleton for the duration of the Apex execution context.
Here is an example of an Apex test that creates a PermissionSet , adds the Custom Permission and assigns it to the running user to confirm the Custom Permission was granted.
Seperation of Concerns and Custom Permissions
Those of you familiar with using Apex Enterprise Patterns might be wondering where checking Custom Permission fits in terms of separation of concerns and the layers the patterns promote.
The answer is at the very least in or below the Service Layer , enforcing any kind of security is the responsibility of the Service layer and callers of it are within their rights to assume it is checked. Especially if you have chosen to expose your Service layer as your application API.
This doesn’t mean however you cannot improve your user experience by using it from within Apex Controllers, Visualforce pages or @RemoteAction methods to control the visibility of related UI components, no point in teasing the end user!
Integrating CustomerPermissionsReader into your Application class
The following code uses the Application class concept i introduced last year and at Dreamforce 2014 , which is a single place to access your application scope concepts, such as factories for selectors, domain and service class implementations (it also has a big role to play when mocking).
This approach ensures their is only one instance of the CustomPermissionsReader per Apex Execution context and also through the properties it exposes gives a compiler checked way of referencing the Custom Permissions, making it easier for application developers code to access them.
Finally, as a future possibility, this approach gives a nice injection point for mocking the status of Custom Permissions in your Apex Unit tests , rather than having to go through the trouble of setting up a Permission Set and assigning it in your test code every time as shown above.
Call to Action: Ideas to Upvote
While writing this blog I created one Idea and came across a two others, i’d like to call you the reader to action on! Please take a look and of course only if you agree its a good one, give it the benefit of your much needed up vote!
- Idea: Make a “PackageInfo” Apex class available for managed code to call at runtime
- Idea: Display the Profiles & Permissions Sets with Custom Permissions on Page
- Idea: Native Apex support for Custom Permissions
Share this:
21 thoughts on “ creating, assigning and checking custom permissions ”.
Leave a comment
Nice, this will come in handy until some of those ideas get implemented. I wrote a similar utility for reverse searching profiles and permission sets. This could be used for listing the profiles and permission sets for a particular custom permission. A stop gap tool till something gets implemented in the platform. https://kksfblog.wordpress.com/2015/01/08/salesforce-metadata-analyzer-audit-all-you-want/
Nice thanks for sharing!
Reblogged this on SutoCom Solutions .
I may be missing something here, but will the reader class picks up CustomPermissions if they are directly added to the profile, without using Permission sets?
Yes it will, Profiles are actually stored as read-only Permission Sets by the platform. So the same queries apply.
Hi Andrew, have you tried using Custom Permissions with Validation Rules and noticed any performance issues ? Have a look at this post: https://www.salesfix.com.au/custom-permissions-validation-rules-and-apex-cpu-limits/ I’d appreciate your comments.
Wow, this has to be a bug in my view, not that it carries “some” overhead so much, but that there is not Apex in sight and that the overhead is not something I would consider acceptable (I have just read your post briefly while traveling).
Hi Andrew. While migration class where i am using customPermissionsReader i am facing below error (change set migration from sandbox to sandbox)
Invalid type: customPermissionsReader
Also i tried to copy paste code from one org to other org but still same issue. I did created custom permission in org and gave access to profile. Could you please help me what might be the cause
Did you include that class in the changeset?
@Andrew – Thanks for this. I’ll be making use of it. However, I have a questions. What are the advantages of using a Custom Permission vs. Hierarchical Custom Setting. It seems a custom setting might achieve the same as a custom permission. If I remember correctly, custom settings don’t count against Query Limit. However, I’m not sure if you can use custom setting in Validation rule too. Maybe that’s the benefit of a Custom Permission. Any thoughts?
The two are different things. One is helping you implement your own security checks, the other is a storage solution for your configuration.
When a user is using our app, we need to check a certain Custom Permission. However, these users are getting the error “No access to SetupEntityAccess” when our APEX code checks to see if they have a certain custom permission. If we enable “View Setup & Configuration” in their profile or PS, they don’t get this error. Does that mean that these users MUST be given “View Setup” in order to make use of custom permissions, or is this permission required?
I would assume the CustomPermissionReader class would be bound by this same restriction if that’s the case. Right? Or am I missing something? Is there some way around having the “View Setup” permission that I’m just not aware of?
Is your code reading the SetupEntjtyAcesss object?
Hi Andrew, nice write up. I’ve used Custom Permissions in VF in the past and am now evaluating using them in Lighting Components. I don’t believe the LCF supports $Permission (yet) – is this your understanding as well? In order to leverage custom permissions in a Lightning Component do we need to go to Apex like you’ve modeled here? BTW – picked up the latest version of your book. Nice work.
That is indeed the current case, you will have to do this via a apex controller. https://developer.salesforce.com/docs/atlas.en-us.lightning.meta/lightning/expr_source.htm . Glad you picked up the book! Enjoy! 🙂
for those of us who have adopted fflib, why not add fflib_CustomPermissionsReader.cls including updating the fflib_Application.cls? Then we have mock support builtin on a par with the other layers.
Good idea, happy to accept a PR for this if you fancy, otherwise please log the issue as an enhancement and I will take a look next time I have a burst of time
Pingback: Custom Permissions, Validation Rules and Apex CPU Limits - SalesFix
This is indeed a great article. Glad I was able to refer for my current problem. I have a requirement where I need to check for permission set in lookup filter which I see is not possible. So I am trying to create a formula field on the user that can read if the user is assigned the permission set and use this field in the lookup filter.
Actually I am creating custom permission and have it assigned to the permission set. Now in the formula field on the user I am trying to check if the user has this custom permission from the assigned permission set – IF($permission.custom_Permission, ‘isAssigned’, ‘noAccess’) – but this is always giving me noAccess even when I have assigned the permission set to the user. I am not sure where I am doing wrong. If it could work I can then use this formula field in the lookup filter.
Can you give some light to achieve this? Is there an alternative to achieve this?
Perhaps try to output the value of the $permisson.custom_permission just as a text formula field so you can see its value, maybe it’s not the value your logic is expecting?
Pingback: Custom Permissions, Validation Rules and Apex CPU Limits – SalesFix
Leave a comment Cancel reply

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar
About 10 mins
Learning Objectives
The basics of permission set groups, benefits of permission set groups, use permission set groups in package development, calculating permissions in a permission set group.
- Challenge +100 points
Looking for Help?
Discover more, get started with permission set groups.
After completing this unit, you’ll be able to:
- State what a permission set group is.
- Describe two use cases for using permission set groups.
- Explain how permissions are calculated in a permission set group.
As an admin, it’s very possible that you have many permission sets that you assign to users. And you likely spend a lot of time managing the permissions that users require while trying to ensure that they have only the permissions that they need to perform their work. For example, your assignment structure might resemble this image, where you must assign several users to several permission sets.
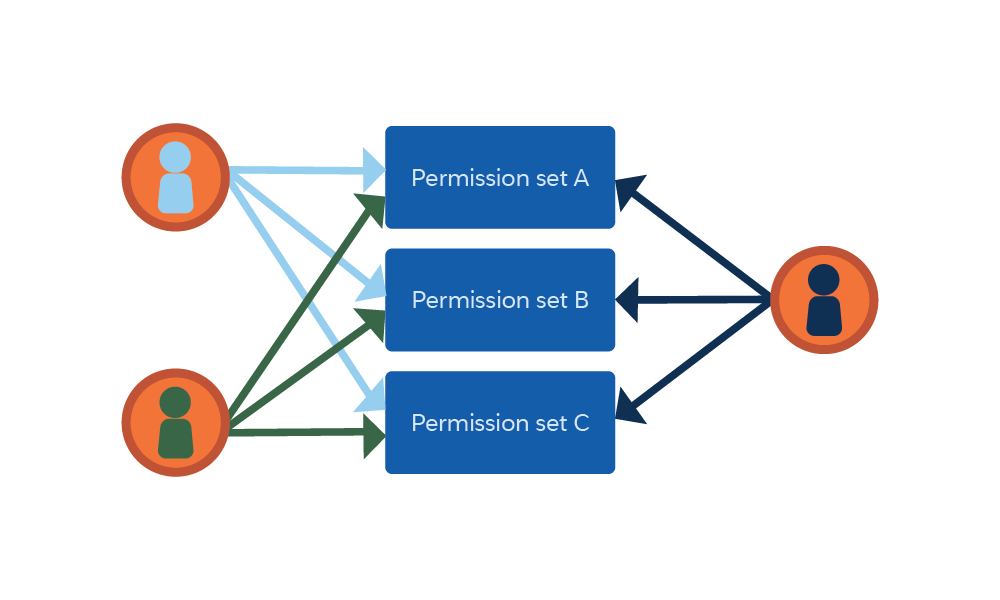
Given how quickly permission sets can multiply, you may have wondered how to simplify permission set management while maintaining the principle of least privilege to protect your org. Well, we have a solution for you: permission set groups. With permission set groups, you can bundle permission sets together based on a job function. A permission set group includes all permissions in the permission sets. You can even include a permission set in more than one permission set group.

Granting permissions to users based on the tasks they perform in their different job functions becomes much simpler.
Assigning permissions to users via permission set groups does look simpler, but how does grouping permission sets make your job easier and help you to enforce assignments based on least privilege?
Let’s say that the vice president of your sales department, E.J. Agarwal, has users who require permissions to create, edit, and delete surveys; create and customize list views and reports; and create and edit price books. These users all perform work involving price surveys.
There are a couple of ways that you can provide E.J.’s users with what they need. You can create a new permission set with all of the permissions needed for this job function. However, permission sets should remain fairly limited—in general, you don’t want a permission set with too many permissions. Alternatively, you can grant the permissions by individually assigning users to permission sets that include permissions for each task, but this is a messy approach and becomes challenging to manage.
Complicating our scenario further is that the users who need permissions for price surveys have different job titles and responsibilities.
- Maria Hernandez, Consultant
- Shaun Chen, Sales Manager
- Aaron Jones, Sales Service Director
By using permission set groups, you create a single group that contains the permission sets with the permissions needed for the price surveys job function. The individual permission sets in the group can also be used outside of the group.
There’s more, too: E.J. has informed you of other changes coming. Maria’s consultancy ends next month, and a contractor will soon require the same permissions that Maria has. And two new hires also need permissions to manage price surveys. Streamlining how you assign user permissions becomes more important as the team continues to change and grow.
For example, you could create a single permission set group called Price Surveys organized around the requirements of the price surveys job function. With this approach, you can ease the user assignment process now and as the team grows.
Just assign the Price Surveys permission set group to users who need permissions to create, edit, and delete surveys; create and customize list views and reports; and create and edit price books. There’s no need to create a new permission set specific to price surveys or to add users to several permission sets.

TIP : If you need to create a new permission set for a permission set group, you can. However, we strongly suggest that you limit the permissions within a permission set to a few related tasks. In the next unit, we cover strategies for thinking about and modeling permission sets and permission set groups to maximize their functionality.
There’s one more thing. If you’re a subscriber to an app with permission set groups, you can add managed permission sets to your local group. Or, you can add a local permission set to a managed group. Why are these options so great? The package development team might include permission changes in a package upgrade; if so, you can receive important updates while making sure that your users retain the access that they need.
You can also take advantage of a function we call muting, which comes in handy when you’re working with managed packages in your org. We go into detail about muting in an upcoming unit.
You might ask how the permissions in a permission set group are determined, especially if you update permission sets within the group. For example, in the Price Surveys permission set group, we have three permission sets.
- Survey Creator Standard Permission Set
- A Custom Permission Set for List Views and Reports Access
- A Custom Permission Set for Price Book Access
Let’s say that E.J comes to you and says that he forgot to tell you something: Users in the price surveys permission set group also need to delete price books. You add delete permission to the permission set for price books. When you add the permission, you kick off a permission set recalculation. A recalculation propagates the change you make in the permission set through to the permission set groups that contain the permission set.
While a permission set group recalculates, assigned users retain the permissions as of the last completed recalculation.
Changes that trigger a recalculation of a permission set group include:
- Changing existing permission sets
- Adding permission sets
- Removing permission sets
The status of a permission set group appears in the Status column of the Permission Set Groups list view page.
Valid statuses are Updated, Outdated, Updating, and Failed.
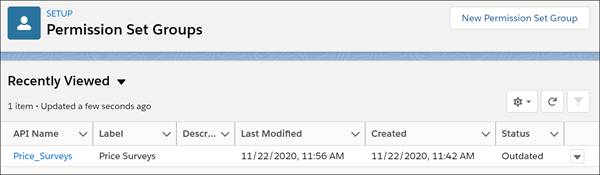
IMPORTANT : When you update permissions in a permission set, review the business requirements of all users assigned to the permission set and related permission set groups.
In the next unit, you create a permission set group and assign it to users.
- Salesforce Help : Permission Set Groups
- Trailhead : Data Security
We'd love to hear about your experience with Trailhead - you can now access the new feedback form anytime from the Salesforce Help site.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Azure custom roles
- 12 contributors
If the Azure built-in roles don't meet the specific needs of your organization, you can create your own custom roles. Just like built-in roles, you can assign custom roles to users, groups, and service principals at management group, subscription, and resource group scopes.
Custom roles can be shared between subscriptions that trust the same Microsoft Entra tenant. There is a limit of 5,000 custom roles per tenant. (For Microsoft Azure operated by 21Vianet, the limit is 2,000 custom roles.) Custom roles can be created using the Azure portal, Azure PowerShell, Azure CLI, or the REST API.
Steps to create a custom role
Here are the basic steps to create a custom role.
Determine the permissions you need.
When you create a custom role, you need to know the actions that are available to define your permissions. Typically, you start with an existing built-in role and then modify it for your needs. You will add the actions to the Actions or NotActions properties of the role definition . If you have data actions, you will add those to the DataActions or NotDataActions properties.
For more information, see the next section How to determine the permissions you need .
Decide how you want to create the custom role.
You can create custom roles using Azure portal , Azure PowerShell , Azure CLI , or the REST API .
Create the custom role.
The easiest way is to use the Azure portal. For steps on how to create a custom role using the Azure portal, see Create or update Azure custom roles using the Azure portal .
Test the custom role.
Once you have your custom role, you have to test it to verify that it works as you expect. If you need to make adjustments later, you can update the custom role.
How to determine the permissions you need
Azure has thousands of permissions that you can potentially include in your custom role. Here are some methods that can help you determine the permissions you will want to add to your custom role:
Look at existing built-in roles .
You might want to modify an existing role or combine permissions used in multiple roles.
List the Azure services you want to grant access to.
Determine the resource providers that map to the Azure services .
Azure services expose their functionality and permissions through resource providers . For example, the Microsoft.Compute resource provider supplies virtual machine resources and the Microsoft.Billing resource provider supplies subscription and billing resources. Knowing the resource providers can help you narrow down and determine the permissions you need for your custom role.
When you create a custom role using the Azure portal, you can also determine the resource providers by searching for keywords. This search functionality is described in Create or update Azure custom roles using the Azure portal .

Search the available permissions to find permissions you want to include.
When you create a custom role using the Azure portal, you can search for permissions by keyword. For example, you can search for virtual machine or billing permissions. You can also download all of the permissions as a CSV file and then search this file. This search functionality is described in Create or update Azure custom roles using the Azure portal .

Custom role example
The following shows what a custom role looks like as displayed using Azure PowerShell in JSON format. This custom role can be used for monitoring and restarting virtual machines.
The following shows the same custom role as displayed using Azure CLI.
Custom role properties
The following table describes what the custom role properties mean.
| Property | Required | Type | Description |
|---|---|---|---|
| | Yes | String | The display name of the custom role. While a role definition is a management group or subscription-level resource, a role definition can be used in multiple subscriptions that share the same Microsoft Entra tenant. This display name must be unique at the scope of the Microsoft Entra tenant. Can include letters, numbers, spaces, and special characters. Maximum number of characters is 512. |
| | Yes | String | The unique ID of the custom role. For Azure PowerShell and Azure CLI, this ID is automatically generated when you create a new role. |
| | Yes | String | Indicates whether this is a custom role. Set to or for custom roles. Set to or for built-in roles. |
| | Yes | String | The description of the custom role. Can include letters, numbers, spaces, and special characters. Maximum number of characters is 2048. |
| | Yes | String[] | An array of strings that specifies the control plane actions that the role allows to be performed. For more information, see . |
| | No | String[] | An array of strings that specifies the control plane actions that are excluded from the allowed . For more information, see . |
| | No | String[] | An array of strings that specifies the data plane actions that the role allows to be performed to your data within that object. If you create a custom role with , that role can't be assigned at management group scope. For more information, see . |
| | No | String[] | An array of strings that specifies the data plane actions that are excluded from the allowed . For more information, see . |
| | Yes | String[] | An array of strings that specifies the scopes that the custom role is available for assignment. Maximum number of is 2,000. For more information, see . |
Permission strings are case-insensitive. When you create your custom roles, the convention is to match the case that you see for permissions in Azure resource provider operations .
Wildcard permissions
Actions , NotActions , DataActions , and NotDataActions support wildcards ( * ) to define permissions. A wildcard ( * ) extends a permission to everything that matches the action string you provide. For example, suppose that you wanted to add all the permissions related to Azure Cost Management and exports. You could add all of these action strings:
Instead of adding all of these strings, you could just add a wildcard string. For example, the following wildcard string is equivalent to the previous five strings. This would also include any future export permissions that might be added.
It's recommended that you specify Actions and DataActions explicitly instead of using the wildcard ( * ) character. The additional access and permissions granted through future Actions or DataActions may be unwanted behavior using the wildcard.
Who can create, delete, update, or view a custom role
Just like built-in roles, the AssignableScopes property specifies the scopes that the role is available for assignment. The AssignableScopes property for a custom role also controls who can create, delete, update, or view the custom role.
| Task | Action | Description |
|---|---|---|
| Create/delete a custom role | Users that are granted this action on all the of the custom role can create (or delete) custom roles for use in those scopes. For example, and of management groups, subscriptions, and resource groups. | |
| Update a custom role | Users that are granted this action on all the of the custom role can update custom roles in those scopes. For example, and of management groups, subscriptions, and resource groups. | |
| View a custom role | Users that are granted this action at a scope can view the custom roles that are available for assignment at that scope. All built-in roles allow custom roles to be available for assignment. |
Even if a role is renamed, the role ID does not change. If you are using scripts or automation to create your role assignments, it's a best practice to use the unique role ID instead of the role name. Therefore, if a role is renamed, your scripts are more likely to work.
Find role assignments to delete a custom role
Before you can delete a custom role, you must remove any role assignments that use the custom role. If you try to delete a custom role with role assignments, you get the message: There are existing role assignments referencing role (code: RoleDefinitionHasAssignments) .
Here are steps to help find the role assignments before deleting a custom role:
- List the custom role definition .
- In the AssignableScopes section, get the management groups, subscriptions, and resource groups.
- Iterate over the AssignableScopes and list the role assignments .
- Remove the role assignments that use the custom role.
- If you are using Microsoft Entra Privileged Identity Management , remove eligible custom role assignments.
- Delete the custom role .
For information about how to find unused custom roles, see Symptom - No more role definitions can be created .
Custom role limits
The following list describes the limits for custom roles.
- Each tenant can have up to 5000 custom roles.
- Microsoft Azure operated by 21Vianet can have up to 2000 custom roles for each tenant.
- You cannot set AssignableScopes to the root scope ( "/" ).
- You cannot use wildcards ( * ) in AssignableScopes . This wildcard restriction helps ensure a user can't potentially obtain access to a scope by updating the role definition.
- You can have only one wildcard in an action string.
- You can define only one management group in AssignableScopes of a custom role.
- Azure Resource Manager doesn't validate the management group's existence in the role definition's AssignableScopes .
- Custom roles with DataActions can't be assigned at the management group scope.
- You can create a custom role with DataActions and one management group in AssignableScopes . You can't assign the custom role at the management group scope itself; however, you can assign the custom role at the scope of the subscriptions within the management group. This can be helpful if you need to create a single custom role with DataActions that needs to be assigned in multiple subscriptions, instead of creating a separate custom role for each subscription.
For more information about custom roles and management groups, see What are Azure management groups? .
Input and output formats
To create a custom role using the command line, you typically use JSON to specify the properties you want for the custom role. Depending on the tools you use, the input and output formats will look slightly different. This section lists the input and output formats depending on the tool.
Azure PowerShell
To create a custom role using Azure PowerShell, you must provide following input.
To update a custom role using Azure PowerShell, you must provide the following input. Note that the Id property has been added.
The following shows an example of the output when you list a custom role using Azure PowerShell and the ConvertTo-Json command.
To create or update a custom role using Azure CLI, you must provide following input. This format is the same format when you create a custom role using Azure PowerShell.
The following shows an example of the output when you list a custom role using Azure CLI.
To create or update a custom role using the REST API, you must provide following input. This format is the same format that gets generated when you create a custom role using the Azure portal.
The following shows an example of the output when you list a custom role using the REST API.
- Tutorial: Create an Azure custom role using Azure PowerShell
- Tutorial: Create an Azure custom role using Azure CLI
- Understand Azure role definitions
- Troubleshoot Azure RBAC
Was this page helpful?
Additional resources
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to programmatically determine in APEX if a custom permission is assigned to a given permission set?
Background: I am trying to make a UI that will simplify managing assignments of some custom permissions against permission sets in my managed package. This section of the managed package would only be used by an admin.
Here is what I'm trying to figure out:
What is the best way to programmatically determine in APEX if a custom permission is assigned to a given permission set?
Once I know what custom permissions a permission set has, how do I programmatically add or remove custom permissions to it?
I hope that all of the above could be done with some simple SOQL queries once I understand how it fits together.
- permission-sets
- custom-permission
While I was composing this question I figured it out.
Since it took me longer to figure out than I would have liked, I will share what I learned in case it helps someone else down the road.
It turns out that the connection between CustomPermission and the PermissionSet is made via the object called SetupEntityAccess .
You can look up if a custom permission is enabled to a permission set like so:
To add/remove a custom permission from a permission set:
- 1 N.B. see also andyinthecloud blog on this subject with a set of classes and, somewhat related, for checking if Custom Permission is enabled for the running user FeatureManagement class – cropredy Commented Jan 30, 2020 at 19:28
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged apex soql permission-sets custom-permission ..
- The Overflow Blog
- Is this the real life? Training autonomous cars with simulations
- Featured on Meta
- Preventing unauthorized automated access to the network
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network...
Hot Network Questions
- Why is my USB 3.0 SD card reader from Amazon being detected as USB 2.0?
- Sets that project to zero measure on all lines except one
- What is the action economy required to retrieve an item from stowage?
- How best to transport Uttarkuru Firestones in bulk
- What is the general expectation for the availability/retention of the experimental data?
- Behaviour of regression toward the mean
- How can I support butcherblock shelves without seeing brackets
- Can the size of a force field be manipulated?
- Can I give access to my Xbox while prohibiting purchases?
- Reviewing a paper that's badly written such that reading it takes a long time
- Is it possible to extrude a bone only from either head or tail but not both?
- ABRSM Grade 8 theory true or false question
- How do I tell a powerline apart from other wires?
- In Spider-Man: No Way Home, how come Sandman was aware of one specific detail of this event?
- How to test batteries number of cycles (manufacturing quality assurance)
- What was the poison gas created in "Armadale" by Wilkie Collins?
- Is grounding an outlet only to its box enough?
- Convolution of non-differentiable function with uniform density
- Can I vacuum seal my homemade bone broth in a Ball jar?
- Reality Check - How possible is it for a single human to reach "Space Engineers" level of technological prowess?
- How would an ancient Chinese necromancer delay their zombies from rotting?
- Translating manorial court rolls: is interesse a noun?
- Is the weight of a floating body zero?
- What type of firearm is ideal in zero gravity infantry asteroid combat?
Permissions for Custom User Accounts
You can create a separate user account in vSphere for backup and restore operations.
When you create a user account, the following system permissions are automatically added to the account:
| Category | Permission |
|---|---|
| System |
If you are creating a user account other than administrator, you can assign permissions to the role that is associated with the user account. The following tables show which vCenter permissions are required (√) for each Commvault role or component.
The vCenter user account must have permissions on the vCenter, datacenter, ESX server, resource pool, VM folder, and virtual machine levels for any virtual machines to be backed up and restored. The backup for a virtual machine fails if the user does not have permission on the vCenter, datacenter, and ESX server where the virtual machine resides. When you assign a user and role for a specific entity, select the option to propagate permissions to child objects, so that operations for virtual machines that use those entities are successful.
To ensure that backups and restores are successful, use the vSphere Client or Web Client to assign user permissions on each required entity.
To hide resources from a user, you can assign a "No access" user role to the entity.
To enable restores, assign both backup and restore permissions for the type of restore (from streaming or IntelliSnap backups).
By default, the following tables display settings for vSphere 7.0, but differences for earlier versions of vSphere are noted. Settings that are not available in vSphere 4.1 might be needed for features that require vSphere 5.0 or a more recent version.
When using VM File Recovery Plug-In, VM Provisioning, or Live Mount, assign permissions that are required for backups or restores and permissions for using that feature.
Live Recovery operations that use a File Recovery Enabler for Linux require the same permissions as IntelliSnap operations.
The guidance in this topic is derived from information in vSphere Security: ESXi 6.0 and vCenter Server 6.0 and is updated through vSphere 7.0. For detailed and current information about vSphere privileges and permissions, refer to the appropriate VMware documentation. Commvault is not responsible for, and does not validate or confirm, the correctness or accuracy of any information provided here. All content in this section is provided "AS IS" and is not warranted by Commvault in any way.
- Alarms Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Acknowledge alarm Required for vCenter 6.0 or later, to enable suppression of actions on triggered alarms. |
|
| ||||||
| Set alarm status Required for vCenter 6.0 or later, to change the status of a configured alarm for an event. |
|
| ||||||
- Cryptographic Operations Permissions
To back up and restore virtual machines using VMware VM-level encryption, the user account for the vCenter virtualization client must have the following permissions:
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Add Disk |
|
|
|
|
|
| ||
| Direct Access |
|
| ||||||
| Encrypt |
|
|
|
|
|
| ||
- Datastore Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Allocate space Required to allocate space for a virtual machine, snapshot, clone, or virtual disk. |
|
|
|
|
| |||
| Browse datastore Required to browse files on a datastore. Used to locate VM files on disk and verify that files exist. |
|
|
|
|
| |||
| Configure datastore Required to configure a datastore. |
|
|
| |||||
| Low level file operations Required to perform read, write, delete, or rename operations for the datastore. Used to read virtual machine configuration files. |
|
|
|
|
| |||
| Remove datastore (deprecated) Required to remove a datastore. The user or group privilege must be set for both the object and its parent object. |
|
|
| |||||
| Rename datastore Required to change the name of a datastore. |
|
| ||||||
| Remove file (deprecated; use Low level file operations) Required to delete files in the datastore. |
| |||||||
| Update virtual machine files Required to update virtual machine file paths on a datastore after a datastore resignature operation. |
|
|
| |||||
- Extension Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Register extension Required to register a plug-in. |
|
|
| |||||
| Unregister extension Required to unregister a plug-in. |
| |||||||
| Update extension Required to update a plug-in. |
| |||||||
- Global Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Cancel task Required to cancel a running or queued task; used to cancel a relocation task if a restore job is killed. |
|
| ||||||
| Diagnostics Required to get lists of diagnostic files, log headers, binary files, or diagnostic bundles. For security, limit this privilege to the vCenter Server Administrator role. |
| |||||||
| Disable methods Required to disable specific operations on vCenter entities. |
|
|
|
| ||||
| Enable methods Required to enable specific operations on vCenter entities. |
|
|
|
| ||||
| Licenses Required to view installed licenses and to add or remove licenses. |
|
|
|
| ||||
| Log event Required to enable logging of user-defined events against a managed entity. |
| |||||||
| Manage custom attributes Required to add, remove, or rename custom field definitions. |
|
|
|
| ||||
| Set custom attribute Required to view, create, or remove custom attributes for a managed entity. |
|
|
|
|
| |||
- Host - Configuration Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Advanced settings For live file recovery, Commvault software increases the NFS heartbeat timeout and the Max failures setting for additional resilience when mounting the datastore on the ESX server. |
|
| ||||||
| Connection Required to change the connection status of a host (connected or disconnected). Used to confirm whether the ESX host is connected within the vCenter inventory. |
|
| ||||||
| Network configuration Required to modify network, firewall or vMotion network settings. Used to configure destination network. |
| |||||||
| Storage partition configuration Required for management of VMFS datastores and diagnostic partitions. This privilege enables users to scan for new storage devices and manage iSCSI. Used to rescan and check for new VMFS partitions and HBAs, and to refresh the datastore list when mounting a datastore to the ESX server during IntelliSnap operations. |
|
| ||||||
| System Management Used to download VM configuration files directly from an ESX host. (If files cannot be downloaded directly, they are accessed through the vCenter.) |
|
|
|
| ||||
- Network Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Assign network Required to assign a network to a virtual machine. Used to create a virtual machine on a network. |
|
|
| |||||
- Profile-driven storage Permissions
Required for vCenter 6.0 or later, to restore VM storage policies as part of a full VM restore.
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Profile-driven storage update Required to create and update storage capabilities and virtual machine storage profiles. |
|
| ||||||
| Profile-driven storage view Required to view storage capabilities and storage profiles. |
|
| ||||||
- Resource Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Assign vApp to resource pool Required to assign a vApp to a resource pool during restores. |
|
| ||||||
| Assign virtual machine to resource pool Required to assign a virtual machine to a resource pool. Required when registering a virtual machine to a resource pool during backups or when restoring to a resource pool. |
|
|
|
|
| |||
| Migrate powered on virtual machine Required to use vMotion to migrate a powered on virtual machine to a different resource pool or host. |
|
| ||||||
| Migrate powered off virtual machine ("Migrate" in vSphere 4.1) Required to use vMotion to migrate a powered off virtual machine to a different resource pool or host. |
|
|
| |||||
- vApp Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Import Required to import a vApp into vSphere. |
|
|
| |||||
| vApp application configuration Required to modify vApp application properties; used when reconfiguring an existing File Recovery Enabler for Linux. |
|
|
| |||||
| vApp instance configuration Required to modify a vApp instance; used when reconfiguring an existing File Recovery Enabler for Linux. |
|
|
| |||||
- Virtual machine - Change Configuration Permissions
This category was formerly called "Virtual machine - Configuration."
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Acquire Disk lease (formerly "Disk lease") Required to perform disk lease operations for a virtual machine. |
|
|
|
| ||||
| Add existing disk Required to add an existing virtual disk to a virtual machine. |
|
|
|
|
| |||
| Add new disk Required to create a new virtual disk to add to a virtual machine. |
|
|
|
|
| |||
| Add or remove device Required to add or remove any non-disk device. Used to add a SCSI controller or to restore non-disk device configuration. |
|
|
|
|
| |||
| Advanced configuration (formerly "Advanced") Required to add or modify advanced parameters in a virtual machine configuration file. |
|
|
|
| ||||
| Change CPU count Required to change the number of virtual CPUs during restores. |
|
|
| |||||
| Change Memory (formerly "Memory") Required to change the amount of memory allocated to a virtual machine. |
|
|
| |||||
| Change resource Required to change the resource configuration of a set of virtual machine nodes in a given resource pool. |
|
|
|
|
| |||
| Change Settings (formerly "Settings") Required to change general virtual machine settings. |
|
|
|
|
| |||
| Change Swapfile placement (formerly "Swapfile placement") Required to change the swapfile placement policy for a virtual machine. |
|
|
| |||||
| Configure Host USB device (formerly "Host USB device") Required to attach a host-based USB device to a virtual machine. |
|
| ||||||
| Configure managedBy Marks a virtual machine as being managed by Commvault during a restore. |
|
| ||||||
| Configure Raw device (formerly "Raw device") Required to add or remove a raw disk mapping or SCSI pass through device (overrides other privileges for modifying raw devices, including connection states). |
|
|
| |||||
| Display connection settings (not in vSphere 4.1) Required to configure virtual machine remote console options. |
| |||||||
| Extend virtual disk Required to expand the size of a virtual disk. |
|
|
| |||||
| Modify device settings Required to change the properties of an existing device. |
|
|
| |||||
| Reload from path Required to change a virtual machine configuration path while preserving the identity of the virtual machine; used during failover and failback operations. |
|
|
| |||||
| Remove disk Required to remove a virtual disk. |
|
|
|
|
| |||
| Rename Required to rename a virtual machine or modify notes for a virtual machine. |
|
|
|
|
| |||
| Reset guest information Required to edit the guest operating system information for a virtual machine. |
|
|
| |||||
| Set annotation (not in vSphere 4.1) Required to add or edit a virtual machine annotation. Used to set up a backup server annotation that records last backup times for target VMs in vSphere. |
|
|
|
|
| |||
| Toggle Disk change tracking (formerly "Disk change tracking") Required to enable or disable change tracking for virtual machine disks. |
|
|
|
| ||||
| Unlock virtual machine (only required for vCenter 6.0 or earlier versions) Required to decrypt a virtual machine. |
| |||||||
| Upgrade virtual machine compatibility ("Upgrade virtual hardware" in vSphere 4.1) Required to upgrade a virtual machine's compatibility version (virtual hardware version). |
|
|
| |||||
- Virtual Machine - Edit Inventory Permissions
This category was formerly called "Virtual Machine - Inventory."
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Create new Required to create and allocate resources for a virtual machine. |
|
|
| |||||
| Create from existing Required to create a virtual machine, by cloning an existing virtual machine or by deploying from a template. |
| |||||||
| Move Required to relocate a virtual machine in the hierarchy. The privilege must be set for both the source and the destination. |
|
| ||||||
| Register Required to add an existing virtual machine to a vCenter Server or host inventory. Required for IntelliSnap backups with metadata collection enabled, and to register a restored VM with the vCenter or host. |
|
|
| |||||
| Remove Required to delete a virtual machine and remove the underlying files from disk. The user or group privilege must be set for both the object and its parent object. Required for IntelliSnap backups with metadata collection enabled. |
|
|
|
|
| |||
| Unregister Required to unregister a virtual machine from a vCenter Server or host inventory. The user or group privilege must be set for both the object and its parent object. Required for IntelliSnap backups with metadata collection enabled, and to unregister a VM so that it can be registered to a different location. |
|
|
| |||||
- Virtual Machine - Guest Operations Permissions (Not in vSphere 4.1)
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Guest Operation Modifications Required to perform virtual machine guest operations that modify the guest operating system, such as transferring a file to the virtual machine or restoring files to a target VM that does not have a file system agent installed. |
|
|
| |||||
| Guest Operation Program Execution Required to perform virtual machine guest operations that execute a program in the virtual machine, such as a restore command. |
|
|
| |||||
| Guest Operation Queries Required to perform virtual machine guest operations that query the guest operating system, such as listing files in the guest operating system. Used when the target VM does not have a file system agent installed. |
|
|
| |||||
- Virtual Machine - Interaction Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Connect devices (formerly "Device connection") Required to change the connected state of virtual machine devices that can be disconnected. |
|
|
| |||||
| Power Off Required to power off the guest operating system of a powered on virtual machine. Used when restoring data to VMDKs. |
|
|
|
|
| |||
| Power On Required to power on a powered off virtual machine or resume a suspended virtual machine. |
|
|
|
| ||||
| Reset Required to reset a virtual machine and reboot the guest operating system. |
| |||||||
| Suspend Required to suspend a powered on virtual machine and put the guest in standby mode. |
| |||||||
- Virtual Machine - Provisioning Permissions
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Allow disk access Required to open a disk on a virtual machine for random read and write access. Used for remote disk mounting and restoring data. |
|
|
| |||||
| Allow read-only disk access Required to open a disk on a virtual machine for random read access; used for remote disk mounting. |
|
|
|
|
| |||
| Allow virtual machine download Required for read operations on files associated with a virtual machine, including vmx, disks, logs, and NVRAM. |
|
|
|
|
| |||
| Clone template Required to clone a template. |
| |||||||
| Clone virtual machine Required to clone an existing virtual machine and allocate resources. Used to create a linked clone from a source VM snapshot during backup. |
|
|
|
|
| |||
| Customize guest (formerly "Customize") Required to customize a virtual machine's guest operating system without moving the virtual machine. |
| |||||||
| Deploy template Required to deploy a virtual machine from a template. |
| |||||||
| Mark as template Required to mark an existing powered off virtual machine as a template. Used to restore a virtual machine template. |
|
| ||||||
| Mark as virtual machine Required to mark an existing template as a virtual machine. |
| |||||||
| Modify customization specification Required to create, modify, or delete customization specifications. |
| |||||||
| Promote disks Required to promote operations on virtual machine disks. |
| |||||||
| Read customization specifications Required to read a customization specification. |
| |||||||
- Virtual machine - Snapshot management Permissions ("Virtual machine - State" in vSphere 4.1)
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Create snapshot Required to create a snapshot from a virtual machine's current state. |
|
|
|
|
| |||
| Remove Snapshot Required to remove a snapshot from the snapshot history. |
|
|
|
|
| |||
| Rename Snapshot Required to change the name or description of a snapshot. |
| |||||||
| Revert to snapshot Required to set a virtual machine to the state it was in for a specified snapshot. |
|
|
| |||||
- vSphere Tagging Permissions
Required for vCenter 6.5 or later, to restore tags as part of a full VM restore.
| Permissions | Streaming | IntelliSnap and Live Recovery | Streaming and IntelliSnap | VM Lifecycle Management Provisioning | Live Mount | |||
|---|---|---|---|---|---|---|---|---|
| Backups and VM Archiving | Restores and Live Sync | Backups | Restores and Live Sync | Deploy File Recovery Enabler for Linux | VM File Recovery Plug-In | |||
| Assign or Unassgn vSphere Tag Required to change the assignment of a tag for an object in the vCenter Server inventory. |
|
| ||||||
| Create vSphere Tag Required to create a tag for a restored VM. |
|
| ||||||
| Create vSphere Tag Category Required to create a tag category. |
|
| ||||||
| Edit vSphere Tag Required to edit a tag. |
|
| ||||||
| Edit vSphere Tag Category Required to edit a tag category. |
|
| ||||||
| Modify UsedBy Field For Category Required to modify the UsedBy field for a tag category. |
|
| ||||||
| Modify UsedBy Field For Tag Required to modify the UsedBy field for a tag. |
|
| ||||||

IMAGES
VIDEO
COMMENTS
Custom permissions let you define access checks that can be assigned to users via permission sets or profiles, similar to how you assign user permissions and other access settings. For example, you can define access checks in Apex that make a button on a Visualforce page available only if a user has the appropriate custom permission. ...
Custom permissions let you define access checks that can be assigned to users via permission sets or profiles, similar to how you assign user permissions and other access settings. For example, you can define access checks in Apex that make a button on a Visualforce page available only if a user has the appropriate custom permission. ...
Select the custom report type created for custom permission set and permission set group assignments. To see all records, adjust your filters so that Show Me is set to All permission set assignments. Under Columns, select which fields to display. Group rows to help with your analysis. For example, group by a custom permission set or permission ...
Custom Permissions in Salesforce represent a control mechanism for custom functionality, which is not readily available within permission sets or profiles. However, once the custom permission is created, it can be enabled in a permission set or a profile to allow access to a certain item or process - such as a button on a custom page or limit ...
A custom permission can be assigned to a user either through a permission set or their profile. She also learned that custom permissions can be referenced in Flow. Addison can have her flow check to see if the user who updated the record has this custom permission and, if so, assign a task to the shift manager to review their order. Problem solved!
The custom permissions feature lets you define access checks to your apps or processes. Custom permissions can be assigned to users via permission sets or profiles, similar to how you assign user permissions and other access settings. Custom permissions are commonly used by developers in Apex. For example, if there's a button on a Visualforce ...
5. Custom Permission cannot be assigned to the user directly. That could be done by means of assigning Permission Set to the user. Custom Permission should already be assigned to the Permission Set : PermissionSetAssignment assignment = new PermissionSetAssignment(); assignment.AssigneeId = userId; assignment.PermissionSetId= permissionSetId;
A validation rule. Addison first creates the custom permission. In Setup, search for 'Custom Permissions' in the Quick Find box. Create a new custom permission. Provide the label, name (API name), and description. The description should further describe the purpose of the custom permission and possibly where it's used.
35. Update. Please note that for the running user, you can use the FeatureManagement class: Boolean isEnabled = FeatureManagement.checkPermission('My_Permission_Api_Name'); Surprisingly, I don't think you can do it more simply than the below. Execution. public static List<User> getUsersWithCustomPermission(String name) {. Set<Id ...
After going through this guide, within the next 20 - 25 minutes, you will learn how to: Create a Custom Permission. Create a Permission Set. Add Custom Permission to Permission Set. Assign Permission Set to a User. Create a Validation Rule. Test Custom Permission.
Create a Permission Set. Now that you have a custom permission, you need to assign it to a permission set and assign the permission set to a user. In Setup Quick Find, enter Permission Sets. Click Permission Sets. Click New. Fill in the following information: Label: Bypass Lead Validation Rules; Name: Bypass_Lead_Validation_Rules
Create a custom Permission (named as Demo Permission) 2. Add that custom Permission to permission set. 3. Assign that permission to set to user. 4. In Lightning Component visibility Filter go to. Permissions—> custom Permission—-> Demo Permission. Salesforce Education Cloud - Time is Now Call Tracking Tools (CTI)
The following SOQL snippets are from the CustomPermissionsReader class i created to help with reading Custom Permissions in Apex (more on this later). As you can see you need to run two SOQL statements to get what you need. The first to get the Id's the second to query if the user actually has been assigned a Permission Set with them in.
A Custom Permission Set for Price Book Access Let's say that E.J comes to you and says that he forgot to tell you something: Users in the price surveys permission set group also need to delete price books. You add delete permission to the permission set for price books. When you add the permission, you kick off a permission set recalculation.
Steps to create a custom role. Here are the basic steps to create a custom role. Determine the permissions you need. When you create a custom role, you need to know the actions that are available to define your permissions. Typically, you start with an existing built-in role and then modify it for your needs.
From Setup, enter Permission Sets in the Quick Find box, then select Permission Sets.; Select a permission set, or create one. On the permission set overview page, click Custom Permissions.; Click Edit.; To enable custom permissions, select them from the Available Custom Permissions list and then click Add.To remove custom permissions from the permission set, select them from the Enabled ...
From Setup, enter Permission Sets in the Quick Find box, then select Permission Sets.; Select a permission set, or create one. On the permission set overview page, click Custom Permissions.; Click Edit.; To enable custom permissions, select them from the Available Custom Permissions list and then click Add.To remove custom permissions from the permission set, select them from the Enabled ...
To create custom permissions: Manage Custom Permissions. From Setup, enter Custom Permissions in the Quick Find box, then select Custom Permissions. Click New. Enter the permission information: Label —the permission label that appears in permission sets. Name —the unique name that's used by the API and managed packages.
Background: I am trying to make a UI that will simplify managing assignments of some custom permissions against permission sets in my managed package. This section of the managed package would only be used by an admin. ... Once I know what custom permissions a permission set has, how do I programmatically add or remove custom permissions to it?
When you assign a user and role for a specific entity, select the option to propagate permissions to child objects, so that operations for virtual machines that use those entities are successful. To ensure that backups and restores are successful, use the vSphere Client or Web Client to assign user permissions on each required entity.
Select a profile. Depending on which user interface you're using, do one of the following. In the enhanced profile user interface, click Custom Permissions, and then click Edit. In the original profile user interface, in the Enabled Custom Permissions related list, click Edit. To enable custom permissions, select them from the Available ...
To open a permission set overview page, from Setup, enter Permission Sets in the Quick Find box, then select Permission Sets and select the permission set you want to view. To see the permission set's enabled object, user, field, and custom permissions and which permission set groups it's included in, click View Summary.
Manage Permission Set Assignments. You can assign permission sets to a single user from the user detail page or assign multiple users to a permission set from any permission set page. Available in: both Salesforce Classic (not available in all orgs) and Lightning Experience. Available in: Essentials, Contact Manager, Professional, Group ...
Assign all members on this team the Minimum Access - Salesforce profile. To configure the permissions required to complete these tasks, create these permission sets. View and Edit Accounts, which includes read and edit permissions for accounts. You also set the account field permissions so that the team can view and edit the fields required for ...