Cyber Crime Essay for Students and Children
500+ words essay on cyber crime.
Cyber Crime Essay – Everybody thinks that only stealing someone’s private data is Cyber Crime. But in defining terms we can say that ‘Cyber Crime refers to the use of an electronic device (computer, laptop, etc.) for stealing someone’s data or trying to harm them using a computer.
Besides, it is an illegal activity that involves a series of issues ranging from theft to using your system or IP address as a tool for committing a crime.


Types of Cyber Crime
Speaking in a broadway we can say that Cyber Crime are categorized into four major types. These are Financial, Privacy, Hacking, and Cyber Terrorism.
The financial crime they steal the money of user or account holders. Likewise, they also stole data of companies which can lead to financial crimes. Also, transactions are heavily risked because of them. Every year hackers stole lakhs and crores of rupees of businessmen and government.
Privacy crime includes stealing your private data which you do not want to share with the world. Moreover, due to it, the people suffer a lot and some even commit suicide because of their data’s misuse.
In, hacking they intentional deface a website to cause damage or loss to the public or owner. Apart from that, they destroy or make changes in the existing websites to diminish its value.
Modern-day terrorism has grown way beyond what it was 10-20 years ago. But cyber terrorism is not just related to terrorists or terrorist organizations. But to threat some person or property to the level of creating fear is also Cyber Terrorism.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Crime in India
Web world or cyberspace is a massive community of millions and billions of users and websites. Also, people access it for different uses like shopping, movies, music, video games, transactions, and e-commerce, etc.

In this Age of Technology and easy access to the internet, anyone can easily reach it. Because of this fast pace growth from the previous decade. Besides, the internet has opened a world of information on which anyone can connect.
Due to, this the rate of crime especially the rate of Cyber Crime has increased much fold. Moreover, the rate of circulation of data is also increased much fold due to the higher speed of internet. Above all, due to all these issues, the Cybersecurity has become a major concern for society.
Laws related to Cyber Crimes
To stop the spread of Cyber Crime and to safeguard the interest of people the government has made several laws related to Cyber Crimes. Also, these laws serve as protection against Cyber Crime. Apart from that, the government has also introduced cyber cells in police stations to counter the problem of Cyber Crime as fast as they can.
Ways of stopping Cyber Crime
Cyber Crime is not something which we cannot deal with our self. Likewise, with little use of our common sense and logic, we can stop Cyber Crimes from happening.
To conclude, we can say that Cyber Crime is a dangerous offense to someone’s privacy or any material. Also, we can avoid Cyber Crime by following some basic logical things and using our common sense. Above all, Cyber Crime is a violation of not only law but of human rights too.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [{ “@type”: “Question”, “name”: “What is the main cause of Cyber Crime?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “The greed for quick money and the desire to get famous quickly are the two main reasons of Cyber Crime. Also, most of the targets of Cyber Crime banks, businessman, financial firms, etc.” } }, { “@type”: “Question”, “name”: “What is the punishment of Cyber Crime in India?”, “acceptedAnswer”: { “@type”: “Answer”, “text”:”If the person is found guilty then there are several punishments based on the level of crime. A simple crime can cost you a fine while a bigger crime can lead you to jail.”} }] }
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App


45,000+ students realised their study abroad dream with us. Take the first step today
Meet top uk universities from the comfort of your home, here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

- School Education /
✍️Essay on Cybercrime: Free Samples in 100, 200, 300 Words

- Updated on
- Apr 26, 2024

The 21st century is a digital age, where any and every task is done on the internet. All thanks to the developments in technology which have been the main factor to ease human life on earth and maybe on other plants in future. But with the benefits of technology, there are several harmful effects, one of them which has recently gained popularity; Cyber Crime.

Cybercrime has emerged as pervasive and evolved as one of the most dangerous threats to humans. There are several users on the internet who indulge in illegal and criminal activities, using computers and networks. To guide you through this hot debate topic, below we have discussed essays on cybercrime.
Table of Contents
- 1 Essay on Cybercrime in 100 Words
- 2 Essay on Cybercrime in 200 Words
- 3 Essay on Cybercrime in 300 Words
- 4 Short Essay on Cybercrime
Also Read: Essay on Student Life
Essay on Cybercrime in 100 Words
Cybercrime involves illegal activities like hacking, ransomware, cyberbullying, online fraud, etc. People who are involved in cybercrime or any similar activities are called hackers, scammers or fraudsters. Cybercrime leads to financial loss for individuals who have fallen victim to one. Cybercrime often invades a person’s privacy by stealing their personal details, including sensitive data, photos, and communication records, which can be used for blackmailing or any malicious purpose.
There are several governmental and non-government organizations which are working
To tackle cybercrime by raising awareness among the masses, cyber security training, implementing robust security protocols, and enacting comprehensive cybercrime laws.
Also Read: I Love My India Essay: 100 and 500+ Words in English for School Students
Essay on Cybercrime in 200 Words
Cybercrime is a criminal activity done online using a computer, network and internet. With the increasing use of the internet and mobile phones, the number of criminal activities has also gained pace. These criminal-minded people steal the personal details of a person, which leads to financial losses and damages the reputation of the victims. Various scams and fraudulent schemes are offered on the internet like online auctions, advance fees, or any investment scam, which are all aimed at deceiving individuals into parting with their money.
Cybercrime is not limited to financial losses or reputational damage, a more discrete term has emerged; cyberbullying. In cyberbullying, a person is harassed, humiliated, or threatened online. This can have severe psychological and emotional consequences. Ethical hackers or white hat hackers can help organizations identify vulnerabilities in their systems before malicious hackers exploit them.
Cybercrime doesn’t have any boundaries and is an international issue and international cooperation is crucial for tracking and prosecuting cybercriminals who operate across borders. To combat cybercrime effectively, a multi-faceted approach is required, involving education, technology, legislation, and international cooperation. As technology continues to advance, our efforts to combat cybercrime must keep pace to protect our increasingly interconnected world.
Also Read : Essay on Winter Season
Essay on Cybercrime in 300 Words
Economists have termed cybercrime as ‘ A Hidden Threat to the Digital World.’ Modern humans are relying on the internet for their day-to-day activities and every macro and micro activity. In this sense, the term cybercrime comes to the front. Cybercrime refers to criminal activities conducted through the use of computers, networks, and the Internet.
Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
The consequences of cybercrime are far-reaching. Financial losses run into 10 digits annually, affecting individuals and organizations alike. Personal privacy is invaded as cybercriminals steal sensitive data, photos, and communication records. In cases of cyberbullying and harassment, victims suffer reputational damages, psychological distress, and emotional trauma, particularly in cases of cyberbullying and harassment.
It’s necessary to look for a multifaceted approach to deal with cybercrime, some of which are.
- Raising public awareness through campaigns where people are informed about the risks of cybercrime and educate them on best practices for online safety.
- Individuals and organizations should implement robust security protocols, regularly update software, and use multi-factor authentication to protect their digital assets.
- Governments should enact and enforce cybercrime laws, providing law enforcement agencies with the resources and expertise needed to prosecute cybercriminals effectively.
- Looking at the global nature of cybercrime, international collaboration is vital. Countries should work together to share threat intelligence and cooperate in the investigation and prosecution of cybercriminals.
- Ethical hackers can help organizations identify and rectify vulnerabilities in their systems before malicious actors exploit them.
Tackling cybercrime requires proactive measures, including education, strong cybersecurity practices, legislation, international cooperation, and the active involvement of ethical hackers.
Also Read: Essay on Green Energy PDF: 150 and 250 Words
Short Essay on Cybercrime
Find the short essay on cyber crime from below:
Cybercrime is an illegal and unethical activity which is done by hackers and fraudsters to gain financial or any other benefits for themselves.
To tackle cybercrime, several measures can be taken. Some of these measures are education and public awareness, research and innovation, ethical hacking, etc.
To write an essay on cybercrime, you need to give details on how it works and the level of danger it poses to humans. Cybercrime consists of various malicious activities like hacking, phishing, ransomware attacks, identity theft, online fraud, and cyberbullying. Hackers, fraudsters, scammers, criminals, and even state-sponsored actors exploit vulnerabilities in digital systems to steal sensitive information, disrupt operations, and cause financial and emotional harm to victims.
Related Articles
For more information about such informative articles, visit our essay writing page and make sure to follow Leverage Edu .
Shiva Tyagi
With an experience of over a year, I've developed a passion for writing blogs on wide range of topics. I am mostly inspired from topics related to social and environmental fields, where you come up with a positive outcome.
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Connect With Us
45,000+ students realised their study abroad dream with us. take the first step today..

Resend OTP in

Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
January 2024
September 2024
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.
Have something on your mind?

Make your study abroad dream a reality in January 2022 with
India's Biggest Virtual University Fair

Essex Direct Admission Day
Why attend .

Don't Miss Out
Essays About Cyber Crime: Top 5 Examples and 8 Prompts
Cybercrime is a severe issue that threatens user security and safety. To help you with this subject , see our essays about cyber crime examples and prompts.
As its name suggests, cyber crime occurs in the digital space beyond our tangible keyboards , computer monitors, and phone screens. This criminal activity happens offline and online , and although many are affected, only 10% to 12% of the victims report these wrongdoings.
You may have encountered cyber crime in the virtual world as a victim or an almost-target. Most of us have the misfortune of being hacked, phished, spoofed, or attacked with a denial of service. At the same time, you may not know that you’ve committed a cyber crime by pirating software , music, movies, books , and other data.
| IMAGE | PRODUCT | |
|---|---|---|
| Grammarly | ||
| ProWritingAid |
5 Essay Examples
1. cyber crime essay for students and children by anonymous on toppr.com, 2. cyber crimes and its effects on youth by anonymous on edubirdie.com, 3. cyber crime by luz owens, 4. cyber crime: a threat to society by ankita yadav, 5. essay on cyber crime by anonymous on vedantu.com, 1. the future of cyber crime, 2. the benefits of cyber crime, 3. cyber crime and its impacts on an industry, 4. cyber crime prevention for the average user, 5. mobile protection from cyber crime, 6. the power of strong passwords to combat cyber crime, 7. laws and cyber crime, 8. my personal experience with cyber crime.
“Cyber Crime is not something which we cannot deal with our self. Likewise, with little use of our common sense and logic, we can stop Cyber Crimes from happening.”
The essay begins with cyber crime ‘s meaning, defining it as an illegal activity to harm others through a computer. The author also discusses the four significant categories of cybercrime : hacking, privacy, financial, and cyber terrorism, and digs into what each type covers.
In the next part of the essay, the writer focuses on cybercrime in India, citing how it’s now a significant concern. So, the government implements cybercrime laws to protect itself and its citizens. You might also be interested in these articles about death penalty .
“Becoming the victim of cyber can have long lasting effects on any one’s life.”
After recognizing cybercrime as the most potent crime today, the author probes its direct connection to the creation of the Internet. Aside from pushing organizations to spend more on their online security to avoid vulnerability, cyber crime also causes lasting effects on its victims’ lives.
The essay provides various instances where criminals exploit unaware individuals through the web. An example is fake emails mimicking legitimate organizations that give criminals access to the victim’s personal information to ruin their financial credibility. Unfortunately, the main targets for these crimes are the youth as they are the most who use the web for their studies.
“In order to diminish cyber crime , all organizations and governments should cooperate, as it has no boundaries.”
Owens compares the new century and the old days when cybercrime didn’t exist. She then describes cyber crime , its different classifications, and how much damage it causes annually. She concedes that this criminal act is difficult to control because most countries don’t have the right laws against it.
Owens also discusses how the youth are more prone to cybercrime exposure because they’re more likely to use technology and be curious. She includes relevant cases and studies that analyze cyber crime , its effects, and how it’s used to the detriment of others.
“Cyber crime is the criminal act which takes place over the internet through computers as tools or targets or other smart devices meant for making our work easier.”
Yadav determines cybercrime as a punishable offense committed via the internet, causing loss to an individual, organization, or government. She lists examples of cybercrime and how everyone falls victim to them, no matter their educational attainment. In her conclusion, Yadav recognizes cybercrime as the most prevalent misdeed today and calls for more severe measures to prevent it.
“Cybercrime or attack is defined as the systematic criminal activity occurring digitally and done by attackers.”
This essay highlights privacy issues connected to the steady rise of smartphones and internet usage. It’s also the reason users should be knowledgeable about cyber crime . The author defines cyber crime and expounds on its adverse effects on individuals, properties, and the government. The author also mentions specific crimes like hacking, theft, and cyberstalking.
Looking for more suggestions? Check out our essays about technology for your next project.
8 Prompts for Essays About Cyber Crime

Cybercrime continuously evolves as more people learn about its potential and countermeasures. Consider this essay prompt if you have several ideas and theories about how cybercrime will adapt to new anti- cybercrime measures.
Don’t forget to research the current state of cybercrime , the capabilities of the criminals that perform it, and the laws made to prevent it. Make sure to include research data and support your theories with relevant studies.
While cybercrime is an umbrella term for illegal acts in cyberspace, it can also lead to positive results. One silver lining example of cybercrime is that it pushes software developers to create more effective protection measures against online attacks. Its rising occurrence among the youth also means that more people are becoming more educated about this issue and can thus actively prevent it from happening.
In this controversial essay topic, discuss the possible benefits of cybercrime . Look into how cybercrime might push technology forwards and improve personal data protection online . Cite relevant case studies and reference platforms with strict security measures, such as Meta .
Whether it’s healthcare, education, or banking, you can always find different and unique cybercrime impacts in various fields. Write an essay about how cyber criminals and their illegal actions can affect a specific industry, depending on your specialty or interest. For example, you can talk about the impacts of cybercrime on students and teachers if you work in the educational field.
One frustrating thing about being an average computer or device user is that you may need more resources to protect yourself from the latest cyber-attacks. With in-depth research and help from field experts, write an essay about how the average Joe can defend himself for a small fee or for free.

Most people spend hours on their smartphones and other mobile devices. Those who use their phones for work, banking, entertainment, and others are always at risk of cyber attacks. For this prompt, research how smartphone users can create a security blanket against cybercrime when they surf the internet, use banking apps, or linger on social media. Tip: If writing an essay sounds like a lot of work, simplify it. Write a simple 5 paragraph essay instead.
If there is one thing cybercriminals hate, it’s a strong and complex password. With this essay prompt, you can discuss creative and memorable ways individuals can create unique passwords.
For example, they can spell their sibling’s name backward and add their favorite number and symbols at the end. Favorite colors, food items, dates, and other things can also work as effective password choices when used with the right symbol, capitalization, and number combinations. There are also helpful apps such as 1password , which creates strong passwords automatically for users.
For this prompt, look for laws worldwide that successfully assist the government in fighting cybercrime . Add your opinion on how your country should adapt these laws and if there are any areas of these proposals you want to change, remove, or improve.
If you’ve had a distressing memory concerning cybercrime , recount the experience in your essay. Tell how it happened and what you did to battle its impact on your life. Similarly, you can also talk about any cybercrime you unintentionally committed and how you worked on stopping yourself from repeating it. Looking for more suggestions? Check out our essays about technology for your next project.
Talk to our experts
1800-120-456-456
- Cyber Crime Essay

Essay on Cyber Crime
Cyber crime is the most discussed issue of the 21st century. The technology sector world wide is witnessing a boom in the consumer of smartphones and the internet which is raising concerns with regard to the privacy and security of the users. Owing to this reason, it is highly essential for all the users to know about cyber crime & security. As a result, thi topic has become the most favorite topic of the examiner and can often be seen asked in the exams. In this view, students must have information on cyber crime and stay prepared to tackle such topics in the essay question in the English paper.
Introduction
Cybercrime is a dangerous attack a company or an individual may face. There are many cases where the cyber attack has brought massive loss to the company and individuals due to the data hack. We live in a technology-driven era, and every piece of information is now fed on computers. Cybercrime involves an attack on computers and digital devices. These cyber-attacks can prove hazardous not just for the organization, but also for the nation. To date, there are many digital attack cases in India and global, pushing for more security measures. These attacks are also affecting the economy of the country if not controlled in the initial stage.
What is Cybercrime?
Cybercrime or attack is defined as the systematic criminal activity occurring digitally
and done by attackers. There are many examples of cybercrime, including fraud,
malware viruses, cyberstalking and others. Due to these, government agencies and
companies are investing more in the maintenance and hiring of cybercrime experts.
Earlier, cybercrime was committed only by individuals or by small groups. However, now a highly complex cybercriminals network work on attacking the system for data
collection.
Three groups of cybercrimes-
This is the form of cyberstalking, trafficking, and grooming. Over the years, this
This type of cybercrime has been taken seriously by law enforcement agencies. It is
now keeping a track over every such attack on an individual.
Similar to the real world where criminals steal the property, in the cyber world,
attackers steal data. Here, the attacker steals a person's bank details and
misuse the credit card for online purchase. By using malicious software, the
attacker attacks the property to disrupt the system of the organization.
These types of crimes are denoted as cyber terrorism. This can be a terror because
the attacker can get hold of essential documents related to government
projects. An enemy nation or terrorist usually makes such attacks. There are
many cases globally where a terrorist hacks government data.
Apart from these, there is a financial crime where the hacker steals the money of the
user account holder. Moreover, they steal company data and finance.
In this type, the computer system of the person is hacked to get personal
information. In many countries, including India, hacking is a punishable act.
It is quite different from ethical hacking. In normal hacking, illegal use
different types of software to enter the system of the target person. Hacker is
then able to monitor every activity done by the person.
This Cybercrime is about violating copyright and downloading music or movies. In
India, many movies before their releases are leaked on the movie download
sites. In other words , theft is also called privacy, which can bring a huge
loss to the organization.
Cyber Stalking
It is online harassment by an individual or a group of people. Normally, these
stalkers target an individual and harass online. There are many cases of
cyberstalking in India, resulting in the target person ending up taking
Malicious Software
These are computer-based cybercrimes where virus-based software is installed in the
target people or organization computers. This is to damage the system and
corrupt the data of the target.
Laws Related to Cybercrime
In India, there are many cybercrime laws enacted to stop this threat. Be it for
the individual or the organization; these laws help to either bring down the
number of cases or eliminate these digital crimes.
Apart from these laws, as an individual, you also need to take steps to stop these
crimes. Like, not providing your login details, installing trust anti-virus
software and keeping your online profile private can help to act against such
Cybercrime is a significant threat that can bring huge loss to the individual and the
organization. It is essential to follow basic online rules to ensure the safety
of self and the organization.
Benefits of Cyber Crime Essay in English provided by Vedantu
The essay on cybercrime provided by Vedantu is prepared by highly qualified teachers which makes it a reliable source of information. This information could be utilized for a variety of reasons. Being a reliable piece of information the essay will benefit everyone curious to know about the topic.
Following are the highlights of its benefits:
Reliable information
Adaptive to the context
Precise language
Fulfills the requirements of the students for english exam questions
Comprehensive and analytical. The article digs in the depth of the issue and analyzes it through a 360 degree perspective.
The essay could also be used by the students for preparing themselves for the essay question in the English paper. This essay is an excellent guide to understand what the examiner is looking for in the exam. Moreover, the topic of cybercrime is quite a recurrent one in the exam. So the students use this essay to deal with the same topic.
The Essay on Cyber Crime is an excellent guide on averting any possibilities of a cyber attack. On today's date, one is mostly on the internet for a variety of reasons. It becomes essential for one to know important tips that can keep one safe from cyberbullies, thieves, or blackmailers. It is also important for one to understand the right course of actions to be taken in an eventuality of such an incident.
Download the cybercrime essay for students in English on the Vedantu website.

FAQs on Cyber Crime Essay
1. How Does Cybercrime Work?
Group of people or an individual commits most of these cyber-crimes. These criminals use a systematic process to hack and commit these acts. These criminal communities share strategies and tools to launch attacks. Some of the cybercrime techniques
Fast Flux - In this method, the hacker moves data quickly among computers in a botnet, making it challenging to find the right source.
Social Engineering - This method includes using lies and manipulation to trick people into revealing their personal information.
Skimmers - This involves installing a skimming tool in an ATM and stealing the information. You may find such skimming devices in ATMs.
There are some digital criminals targeting organizations to steal personal information.
2. How Cybercrime Affects Society?
Cybercrime can hugely affect society. In 2018, the US faced a loss of $600 billion. As consumers are increasingly allowing technologies to get into their lives, cyber attackers are getting better access. Some of the essential information available are-
Personal health data, sleep schedules, and geo-locations Shopping history, account information, and passive conversations noticed voice-controlled devices, Private conversations on social media accounts.
Your entire life is now available on social media, making it vulnerable to hack or cyber-attack. Attackers use different techniques including- installing malware, virus, phishing, cyberstalking, etc. These can certainly bring loss of lives and data for individuals and organizations. For society, this is a significant loss in the long run. One needs to be very careful when presenting himself socially.
3. How to stay secure in times of cybercrime?
Cybercrime is a real threat posing to society. It is the 21st-century version of theft and blackmailing. There are certain ways one should adopt to prevent any possibilities of cybercrime. Do not disclose the banking details to random people or fill the CVV of your debit or credit cards on an unknown and unverified website. Keep your passwords always discrete. The camera of the laptop should always be covered.
4. Where can I get a cybercrime essay?
One can find a good quality cyber crime essay on Vedantu's website. The essay which is prepared by the expert teachers describes everything that one needs to know about cybercrime. It is the one-stop solution for all your requirements on the topic. Their essay is available in PDF format on the website and could be downloaded on any device. One downloaded essay could be used in offline mode too. If one finds it feasible, the printout of the PDF could also be taken out.
- Skip to main content
- Skip to secondary menu
- Skip to primary sidebar
- Skip to footer
A Plus Topper
Improve your Grades
Cyber Crime Essay | Essay on Cyber Crime for Students and Children in English
February 14, 2024 by Prasanna
Cyber Crime Essay: A crime that involves a network and a computer is known as computer-oriented crime or cybercrime. Such a crime affects the security of everything, might be a person, institution or even a nation. The computer is either used to commit a crime or is usually a target. Things that are hacked include information, privacy, data and it is often released out in the open to bring someone or some people down. Cybercriminals can be anyone, even your next-door neighbour or a high functional, advanced organization. Like any other form of criminal activity, cybercrime is committed to gain excess money and finish the lives of people without murder.
You can also find more Essay Writing articles on events, persons, sports, technology and many more.
Long and Short Essays on Cyber Crime for Students and Kids in English
We are providing students with essay samples on an extended essay of 500 words and a short piece of 150 words on the topic Cyber Crime for reference.
Long Essay on Cyber Crime 500 Words in English
Long Essay on Cyber Crime is usually given to classes 7, 8, 9, and 10.
There are various forms and types of Cyber Crime all over the world. Cybercrimes are committed by hackers not only for profit but for personal gains and with aims to damage a person, institution or nation. Internationally, both governmental and non-state institutions engage in cybercrime. Cybercrime is known as cyber warfare as soon as it crosses international borders.
Most cybercrimes fall under two broad categories, namely, Criminal Activity that Targets and Criminal Activities that Uses.
Other categories of cybercrime include, cyberterrorism which is is terrorism committed through a network or a computer, Financial Fraud Crimes, Cyber extortion which is when individuals ask for money in return of stopping malicious attacks on a system, Cybersex Trafficking, Online Harassment, Drug Trafficking, etc. Phishing, Malware Attacks, Denial of services and distributed DoS attacks are few of the most common examples of cybercrime.
Online Harassment is something that is not considered as a form of cybercrime by most people, but it, in reality, is what happens in bulk. Under the category of online Harassment also falls the sub-category of cyber crimes against women, which is defined as ‘crimes targeted against women with a motive to intentionally harm them either physically or psychologically, using modern communication networks’.
Tracing a cybercrime delinquent isn’t the most straightforward task to do because of their use of virtual spaces and attacks from various parts. It has been recorded that in 2018 The Internet Crime Complaint Sector received 351,937 complaints alone.
Sine, everything you do on a computer or a network is recorded one way or the other, getting hold of the criminals isn’t impossible.
Since many developing countries like the Philippines have underdeveloped laws regarding cybercrime and cybersecurity, it becomes easy for cybercriminals to use the underdeveloped laws of the developing countries to remain undetectable and anonymous.
With the rise of the increase of technology, cybercrime has become a critical part of the society, and majors like that of Cyber Security have been established in many universities, hence, becoming an integral part of the academic system.
You can now access more Essay Writing on Cyber Crime topic and many more topics.
Since the age of computers and technology is rising every day, our lifestyles are becoming computer-dependent, and everything is stored on there. As the main aim of cybercriminals is the breach of privacy, things become simpler for them.
One major step towards prevention of cybercrime is the spread of Awareness. There are many individuals who aren’t comfortable using a computer, and hence they are more prone to cybercrimes. People don’t know how much and to what extent things can be done with the help of technology and computers; once, people are made aware of all these factors, a little wall of prevention can be created. Updated software and use of reliable anti-virus software are critical practices in preventing cybercrimes.
The phrase, ‘prevention is better than cure might be old but has been relevant since forever and is relevant in today’s technology-dependent world full of all sorts of crime.
Short Essay on Cyber Crime 150 Words in English
Short Essay on Cyber Crime is usually given to classes 1, 2, 3, 4, 5, and 6.
Crime synonymous with the use of computers and network as means or targets is known as computer crime or cybercrime. Cybercrime is not a new word for anyone living in the 21st century, but not many know in how many forms they are present.
Some of the most relevant forms of cybercrime are online Harassment, even though some might not give too much attention to it, it is part of the heinous umbrella term. Drug Trafficking, Cyber Warfare, Cyber Extortions, etc. are a few other famous forms of cybercrime.
The cybercriminal can either use a computer to commit the crime or have another computer as his aim. Most of these criminals commit cybercrimes for money, no matter the reason, their primary objective is to a breach of privacy. Since most people have their lives saved on computers, they need to be extra cautious, which will only be possible through education and Awareness.
10 Lines on Cyber Crime Essay in English
1. Crimes committed by using a network or computer is known as cybercrime. 2. Cybercriminals either use the computer as a tool to commit the crime or aim the computer to commit the crime. 3. Online Harassment, no matter what anyone says, is a significant and ubiquitous form of cybercrime. 4. Most cybercriminals resided in America since America’s development with the computer was faster than that of any other country, but now, no place is devoid of cybercriminals. 5. Cyber-crimes can bring down a person, an institution or even a whole nation with the breach of privacy. 6. Cyber Criminals use underdeveloped laws of the developing countries to manipulate records and remain anonymous; hence laws need to be made stricter. 7. Education and Awareness are the initials steps taken to prevent cybercrimes from taking place. 8. One needs to have a reliable anti-virus service and have all their software updated if they want to prevent cybercrimes. 9. Cyber Security has become an integral part of the curriculum in developed countries in the past few years. 10. Anyone can be a cyber-criminal. They can be a well-structured organization or a novice hacker.
FAQ’s on Cyber Crime Essay
Question 1. How to prevent cyber crimes?
Answer: The best way of prevention is by keeping everything updated and secure with a reliable anti-virus service.
Question 2. How to file cybercrime reports?
Answer: Almost all countries have a cybersecurity cell, and their contact information is available online easily.
Question 3. Is Online Harassment Cyber Crime?
Answer: Yes, it is; please report the individual as soon as possible.
Question 4. Is it very hard to catch cybercriminals?
Answer: Yes, it is hard to catch cybercriminals but not impossible.
- Picture Dictionary
- English Speech
- English Slogans
- English Letter Writing
- English Essay Writing
- English Textbook Answers
- Types of Certificates
- ICSE Solutions
- Selina ICSE Solutions
- ML Aggarwal Solutions
- HSSLive Plus One
- HSSLive Plus Two
- Kerala SSLC
- Distance Education
Home — Essay Samples — Law, Crime & Punishment — Cyber Crimes — Cyber Crime: The Meaning, Types, And Ways To Avoid
Cyber Crime: The Meaning, Types, and Ways to Avoid
- Categories: Cyber Crimes Cyber Security
About this sample

Words: 2343 |
12 min read
Published: May 17, 2022
Words: 2343 | Pages: 5 | 12 min read
Table of contents
Introduction, types of cyber crime.
- Phising/Spoofing: Unlawfully accessing a computer without authorization and sending multiple e-mails; resending multiple commercial email messages with the intent to deceive recipients; or falsifying header information in multiple email messages.
- Blackmail/Extortion: Using the Internet to threaten to cause damage with the intent to extort from any person any money or other thing of value.
- Accessing Stored Communications: Intentionally accessing, without authorization, a facility through which an electronic communication service is provided.
- Sports Betting: Engaging in the business of betting or wagering on any sporting event or contest over the Internet.
- Non-Delivery of Merchandise: Devising any scheme to defraud, or for obtaining money or property by means of false or fraudulent pretenses, or promises, and using the Internet for the purpose of executing the scheme.
- Electronic Harassment: Anonymously using the Internet to annoy, abuse, threaten, or harass the person who receives the communication.
- Child Pornography: Using the Internet to transmit child pornography.
- Prostitution: Persuading, inducing, enticing, or coercing any individual to travel in interstate commerce to engage in prostitution.
- Drug Trafficking: Delivering, distributing, or dispensing a controlled substance by means of the Internet.
- Criminal Copyright Infringement: Infringing a copyright for financial gain...or by distributing a work being prepared for commercial distribution on a computer network.
Avoiding Cyber Crime
Anti-virus software.
- It became common to distribute software and updates via downloads from the Internet,
- Hackers developed viruses that were delivered inside macros for Microsoft Word, which malicious macros could be hidden inside a document sent by e-mail, and
- Hackers developed malicious computer programs that were commonly distributed as attachments to e-mail: clicking on the attachment executed the malicious computer program and infected the victim's computer.
- Never open an executable attachment.
- Never open any attachment from an unknown source.
- Be cautious of any attachment that has a double file extension, especially when the rightmost file extension is an executable file type.
Avoiding harassment
- https://www.slideshare.net/bharadwajchetan/an-introduction-to-cyber-law-it-act-2000-india
- https://cybercrime.org.za/definition
- http://www.cyberlawsindia.net/cyber-india.html
- Dorothy E. Denning, Information Warfare and Security, Addison- Wesley Publishing Co., 1998.
- Dorothy E. Denning and Peter J. Denning, Internet Besieged, Addison- Wesley Publishing Co., 1997.
- Peter J. Denning (editor), Computers Under Attack, Addison- Wesley Publishing Co., 1990.
- Peter G. Neumann, Computer –Related Risks, Addison – Wesley Publishing Co., 1995.

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Law, Crime & Punishment Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
3 pages / 1254 words
2 pages / 947 words
3 pages / 1529 words
1 pages / 1357 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online

Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Cyber Crimes
Lee, S. (2017). Encrypted Messaging: Keeping Your Conversations Secure. Security Boulevard.Smirnoff, V., & Turner, S. (2019). Symmetric Encryption: Definition, Types, and Examples. SecurityTrails.Almeida, R. (2019). Asymmetric [...]
In our increasingly interconnected world, where technology is deeply woven into the fabric of our daily lives, the specter of computer threats looms large. From malware attacks to hacking and data breaches, the digital landscape [...]
Cybersecurity has become a very familiar term that has drawn increasing awareness of the danger of leaving cybercrimes unpunished. Because the world is moving more toward online trading and e-commerce, and basically living [...]
There are myriad ways for the bad guys to get your information and use it for all sorts of nefarious purposes — mainly, stealing your money, althoughoccasionally for other kinds of fraud or to cover their tracks when committing [...]
The problem of preventing cybercrime on an international scale has received considerable attention from many different countries. This essay analyzes cybercrime law. It aims to review past legislation and how it affected the [...]
A popular controversial issue today is whether children who are at risk for abuse remain with their families or not. Many people feel differently about this issue. Some people feel that it would be best for the children to [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

- Games & Quizzes
- History & Society
- Science & Tech
- Biographies
- Animals & Nature
- Geography & Travel
- Arts & Culture
- On This Day
- One Good Fact
- New Articles
- Lifestyles & Social Issues
- Philosophy & Religion
- Politics, Law & Government
- World History
- Health & Medicine
- Browse Biographies
- Birds, Reptiles & Other Vertebrates
- Bugs, Mollusks & Other Invertebrates
- Environment
- Fossils & Geologic Time
- Entertainment & Pop Culture
- Sports & Recreation
- Visual Arts
- Demystified
- Image Galleries
- Infographics
- Top Questions
- Britannica Kids
- Saving Earth
- Space Next 50
- Student Center
- Introduction
Defining cybercrime
- Identity theft and invasion of privacy
- Internet fraud
- File sharing and piracy
- Counterfeiting and forgery
- Child pornography
- Computer viruses
- Denial of service attacks
- Spam, steganography, and e-mail hacking

Our editors will review what you’ve submitted and determine whether to revise the article.
- College of DuPage Digital Press - Computers and Criminal Justice - Introduction to Cybercrime
- Academia - Cyber Crimes: An Overview
- Table Of Contents
Recent News
cybercrime , the use of a computer as an instrument to further illegal ends, such as committing fraud , trafficking in child pornography and intellectual property, stealing identities , or violating privacy. Cybercrime, especially through the Internet , has grown in importance as the computer has become central to commerce, entertainment, and government.
Because of the early and widespread adoption of computers and the Internet in the United States , most of the earliest victims and villains of cybercrime were Americans. By the 21st century, though, hardly a hamlet remained anywhere in the world that had not been touched by cybercrime of one sort or another.
New technologies create new criminal opportunities but few new types of crime. What distinguishes cybercrime from traditional criminal activity? Obviously, one difference is the use of the digital computer , but technology alone is insufficient for any distinction that might exist between different realms of criminal activity. Criminals do not need a computer to commit fraud, traffic in child pornography and intellectual property, steal an identity, or violate someone’s privacy. All those activities existed before the “cyber” prefix became ubiquitous . Cybercrime, especially involving the Internet, represents an extension of existing criminal behaviour alongside some novel illegal activities.
Most cybercrime is an attack on information about individuals, corporations, or governments. Although the attacks do not take place on a physical body, they do take place on the personal or corporate virtual body, which is the set of informational attributes that define people and institutions on the Internet. In other words, in the digital age our virtual identities are essential elements of everyday life: we are a bundle of numbers and identifiers in multiple computer databases owned by governments and corporations. Cybercrime highlights the centrality of networked computers in our lives, as well as the fragility of such seemingly solid facts as individual identity.
An important aspect of cybercrime is its nonlocal character: actions can occur in jurisdictions separated by vast distances. This poses severe problems for law enforcement since previously local or even national crimes now require international cooperation. For example, if a person accesses child pornography located on a computer in a country that does not ban child pornography, is that individual committing a crime in a nation where such materials are illegal? Where exactly does cybercrime take place? Cyberspace is simply a richer version of the space where a telephone conversation takes place, somewhere between the two people having the conversation. As a planet-spanning network, the Internet offers criminals multiple hiding places in the real world as well as in the network itself. However, just as individuals walking on the ground leave marks that a skilled tracker can follow, cybercriminals leave clues as to their identity and location, despite their best efforts to cover their tracks. In order to follow such clues across national boundaries, though, international cybercrime treaties must be ratified.
In 1996 the Council of Europe , together with government representatives from the United States, Canada, and Japan, drafted a preliminary international treaty covering computer crime. Around the world, civil libertarian groups immediately protested provisions in the treaty requiring Internet service providers (ISPs) to store information on their customers’ transactions and to turn this information over on demand. Work on the treaty proceeded nevertheless, and on November 23, 2001, the Council of Europe Convention on Cybercrime was signed by 30 states. The convention came into effect in 2004. Additional protocols , covering terrorist activities and racist and xenophobic cybercrimes, were proposed in 2002 and came into effect in 2006. In addition, various national laws, such as the USA PATRIOT Act of 2001, have expanded law enforcement’s power to monitor and protect computer networks .
Types of cybercrime
Cybercrime ranges across a spectrum of activities. At one end are crimes that involve fundamental breaches of personal or corporate privacy, such as assaults on the integrity of information held in digital depositories and the use of illegally obtained digital information to harass, harm, or blackmail a firm or individual. These new cybercapabilities have caused intense debate. Pegasus spyware, for instance, according to its creator, the Israeli cyber-intelligence firm NSO Group, is sold exclusively to government security and law enforcement agencies and only for the purpose of aiding rescue operations and battling criminals, such as money launderers , sex- and drug-traffickers, and terrorists. Yet, the smartphone-attached spyware, which can steal private data without leaving an obvious trace of its activities, has been widely used covertly by governments to track politicians, government leaders, human rights activists, dissidents , and journalists. It was even used to track Saudi journalist and U.S. resident Jamal Khashoggi months before his murder and dismemberment by Saudi agents in October 2018. Also at this end of the spectrum is the growing crime of identity theft .
Midway along the spectrum lie transaction-based crimes such as fraud , trafficking in child pornography , digital piracy , money laundering , and counterfeiting . These are specific crimes with specific victims, but the criminal hides in the relative anonymity provided by the Internet . Another part of this type of crime involves individuals within corporations or government bureaucracies deliberately altering data for either profit or political objectives. At the other end of the spectrum are those crimes that involve attempts to disrupt the actual workings of the Internet. These range from spam , hacking, and denial of service attacks against specific sites to acts of cyberterrorism—that is, the use of the Internet to cause public disturbances and even death. Cyberterrorism focuses upon the use of the Internet by nonstate actors to affect a nation’s economic and technological infrastructure . Since the September 11 attacks of 2001, public awareness of the threat of cyberterrorism has grown dramatically.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Springer Nature - PMC COVID-19 Collection


Research trends in cybercrime victimization during 2010–2020: a bibliometric analysis
Huong thi ngoc ho.
1 School of Journalism and Communication, Huazhong University of Science and Technology, Wuhan, Hubei China
Hai Thanh Luong
2 School of Global, Urban and Social Studies, RMIT University, Melbourne, Australia
Associated Data
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
Research on cybercrime victimization is relatively diversified; however, no bibliometric study has been found to introduce the panorama of this subject. The current study aims to address this research gap by performing a bibliometric analysis of 387 Social Science Citation Index articles relevant to cybercrime victimization from Web of Science database during the period of 2010–2020. The purpose of the article is to examine the research trend and distribution of publications by five main fields, including time, productive authors, prominent sources, active institutions, and leading countries/regions. Furthermore, this study aims to determine the global collaborations and current gaps in research of cybercrime victimization. Findings indicated the decidedly upward trend of publications in the given period. The USA and its authors and institutions were likely to connect widely and took a crucial position in research of cybercrime victimization. Cyberbullying was identified as the most concerned issue over the years and cyber interpersonal crimes had the large number of research comparing to cyber-dependent crimes. Future research is suggested to concern more about sample of the elder and collect data in different countries which are not only European countries or the USA. Cross-nation research in less popular continents in research map was recommended to be conducted more. This paper contributed an overview of scholarly status of cybercrime victimization through statistical evidence and visual findings; assisted researchers to optimize their own research direction; and supported authors and institutions to build strategies for research collaboration.
Introduction
To date, the debate of cybercrime definition has been controversial which is considered as one of the five areas of cyber criminology (Ngo and Jaishankar 2017 ; Drew 2020 ). 1 Several terms are used to illustrate ‘cybercrime’, such as ‘high-tech crime’ (Insa 2007 ), ‘computer crime’ (Choi 2008 ; Skinner and Fream 1997 ), ‘digital crime’ (Gogolin 2010 ), or ‘virtual crime’ (Brenner 2001 ). ‘Cybercrime’, however, has been the most popular in the public parlance (Wall 2004 ). A propensity considers crime directly against computer as cybercrime, while other tendency asserts that any crime committed via internet or related to a computer is cybercrime (Marsh and Melville 2008 ; Wall 2004 ). Hence, there is a distinction between ‘true cybercrime’ or ‘high-tech’ cybercrime and ‘low-tech’ cybercrime (Wagen and Pieters 2020 ). Council of Europe defines ‘any criminal offense committed against or with the help of a computer network’ as cybercrime (Abdullah and Jahan 2020 , p. 90). Despite different approaches, cybercrime generally includes not only new types of crimes which have just occurred after the invention of computer and internet (Holt and Bossler 2014 ; Drew 2020 ) but also traditional types of crimes which took the advantages of information communication technology (ICT) as vehicle for illegal behaviors (Luong 2021 ; Nguyen and Luong 2020 ; Luong et al. 2019 ). Two main cybercrime categories identified, respectively, are cyber-dependent crime (hacking, malware, denial of service attacks) and cyber-enable crime (phishing, identity theft, cyber romance scam, online shopping fraud). Nevertheless, there are several different classifications of cybercrime such as cybercrime against certain individuals, groups of individuals, computer networks, computer users, critical infrastructures, virtual entities (Wagen and Pieters 2020 ); cyber-trespass, cyber-deceptions, cyber-pornography, and cyber-violence (Wall 2001 ).
Due to the common prevalence of cybercrime, the increasing threats of cybercrime victimization are obviously serious. Cybercrime victimization has become a crucial research subfield in recent years (Wagen and Pieters 2020 ). It is difficult to differ “forms of online victimization” and “acts that actually constitute a crime”, then it is usual for researchers to focus less on perspective of criminal law and consider any negative experiences online as cybercrime (Näsi et al. 2015 , p. 2). It was likely to lead to practical gaps between theory and practice in terms of investigating the nexus of offender and victims on cyberspace. In the light of literature review, numerous specific aspects of cybercrime victimization were investigated by questionnaire surveys or interview survey such as the prevalence of cybercrime victimization (Näsi et al. 2015 ; Whitty and Buchanan 2012 ); causes and predictors of cybercrime victimization (Abdullah and Jahan 2020 ; Algarni et al. 2017 ; Ilievski 2016 ; Jahankhani 2013 ; Kirwan et al. 2018 ; Näsi et al. 2015 ; Reyns et al. 2019 ; Saad et al. 2018 ); and the relationship between social networking sites (SNS) and cybercrime victimization (Das and Sahoo 2011 ; Algarni et al. 2017 ; Benson et al. 2015 ; Seng et al. 2018 ). To some extent, therefore, the current study examines cybercrime victimization in the large scale, referring to any negative experiences on cyberspace or computer systems. Nevertheless, no bibliometric analysis was found to show the research trend and general landscape of this domain.
Bibliometric is a kind of statistical analysis which uses information in a database to provide the depth insight into the development of a specified area (Leung et al. 2017 ). The present study aims to address this research gap by providing a bibliometric review of the relevant SSCI articles in WoS database during the period of 2010–2020. The pattern of publications, the productivity of main elements (authors, journals, institutions, and countries/regions), statistic of citations, classification of key terms, research gaps, and other collaborations will be presented and discussed in section four and five after reviewing literatures and presenting our methods conducted. This article contributes an overview of research achievements pertaining to cybercrime victimization in the given period through statistical evidence and visual findings; assists researchers to perceive clearly about the key positions in research maps of this field, and obtain more suggestions to develop their own research direction.
Literature review
Cybercrime victimization.
Cybercrime victimization may exist in two levels including institutional and individual level (Näsi et al. 2015 ). For the former, victim is governments, institutions, or corporations, whereas for the latter, victim is a specific individual (Näsi et al. 2015 ). A wide range of previous studies concerned about individual level of victim and applied Lifestyle Exposure Theory (LET), Routine Activity Theory (RAT) and General Theory of Crime to explain cybercrime victimization (Choi 2008 ; Holt and Bossler 2009 ; Ngo and Paternoster 2011 ). Basing on these theories, situational and individual factors were supposed to play an important role in understanding cybercrime victimization (Choi 2008 ; Van Wilsem 2013 ). However, there was another argument that situational and individual factors did not predict cybercrime victimization (Ngo and Paternoster 2011 ; Wagen and Pieters 2020 ). Overall, most of those studies just focused only one distinctive kind of cybercrime such as computer viruses, malware infection, phishing, cyberbullying, online harassment, online defamation, identity theft, cyberstalking, online sexual solicitation, cyber romance scams or online consumer fraud. Referring to results of the prior research, some supported for the applicability of mentioned theories but other did not share the same viewpoint (Leukfeldt and Yar 2016 ). It was hard to evaluate the effect of LET or RAT for explanation of cybercrime victimization because the nature of examined cybercrime were different (Leukfeldt and Holt 2020 ; Leukfeldt and Yar 2016 ).
Previous research determined that cybercrime victimization was more common in younger group compared to older group because the young is the most active online user (Näsi et al. 2015 ; Oksanen and Keipi 2013 ) and males tended to become victims of cybercrime more than females in general (Näsi et al. 2015 ). However, findings might be different in research which concerned specific types of cybercrime. Women were more likely to be victims of the online romance scam (Whitty and Buchanan 2012 ) and sexual harassment (Näsi et al. 2015 ), while men recorded higher rate of victimization of cyber-violence and defamation. Other demographic factors were also examined such as living areas (Näsi et al. 2015 ), education (Oksanen and Keipi 2013 ; Saad et al. 2018 ) and economic status (Oksanen and Keipi 2013 ; Saad et al. 2018 ). Furthermore, several prior studies focus on the association of psychological factors and cybercrime victimization, including awareness and perception (Ariola et al. 2018 ; Saridakis et al. 2016 ), personality (Kirwan et al. 2018 ; Orchard et al. 2014 ; Parrish et al. 2009 ), self-control (Ilievski 2016 ; Ngo and Paternoster 2011 ; Reyns et al. 2019 ), fear of cybercrime (Lee et al. 2019 ), online behaviors (Al-Nemrat and Benzaïd 2015 ; Saridakis et al. 2016 ). Psychological factors were assumed to have effects on cybercrime victimization at distinctive levels.
Another perspective which was much concerned by researchers was the relationship between cybercrime victimization and SNS. SNS has been a fertile land for cybercriminals due to the plenty of personal information shared, lack of guard, the availability of communication channels (Seng et al. 2018 ), and the networked nature of social media (Vishwanath 2015 ). When users disclosed their personal information, they turned themselves into prey for predators in cyberspace. Seng et al. ( 2018 ) did research to understand impact factors on user’s decision to react and click on suspicious posts or links on Facebook. The findings indicated that participants’ interactions with shared contents on SNS were affected by their relationship with author of those contents; they often ignored the location of shared posts; several warning signals of suspicious posts were not concerned. Additionally, Vishwanath ( 2015 ) indicated factors that led users to fall victims on the SNS; Algarni et al. ( 2017 ) investigated users’ susceptibility to social engineering victimization on Facebook; and Kirwan et al. ( 2018 ) determined risk factors resulting in falling victims of SNS scam.
Bibliometric of cybercrime victimization
“Bibliometric” is a term which was coined by Pritchard in 1969 and a useful method which structures, quantifies bibliometric information to indicate the factors constituting the scientific research within a specific field (Serafin et al. 2019 ). Bibliometric method relies on some basic types of analysis, namely co-authorship, co-occurrence, citation, co-citation, and bibliographic coupling. This method was employed to various research domains such as criminology (Alalehto and Persson 2013 ), criminal law (Jamshed et al. 2020 ), marketing communication (Kim et al. 2019 ), social media (Chen et al. 2019 ; Gan and Wang 2014 ; Leung et al. 2017 ; Li et al. 2017 ; You et al. 2014 ; Zyoud et al. 2018 ), communication (Feeley 2008 ), advertising (Pasadeos 1985 ), education (Martí-Parreño et al. 2016 ).
Also, there are more and more scholars preferring to use bibliometric analysis on cyberspace-related subject such as: cyber behaviors (Serafin et al. 2019 ), cybersecurity (Cojocaru and Cojocaru 2019 ), cyber parental control (Altarturi et al. 2020 ). Serafin et al. ( 2019 ) accessed the Scopus database to perform a bibliometric analysis of cyber behavior. All documents were published by four journals: Cyberpsychology, Behavior and Social Networking (ISSN: 21522723), Cyberpsychology and Behavior (ISSN: 10949313) , Computers in Human Behavior (ISSN: 07475632) and Human–Computer Interaction (ISSN: 07370024), in duration of 2000–2018. Findings indicated the use of Facebook and other social media was the most common in research during this period, while psychological matters were less concerned (Serafin et al. 2019 ). Cojocaru and Cojocaru ( 2019 ) examined the research status of cybersecurity in the Republic of Moldavo, then made a comparison with the Eastern Europe countries’ status. This study employed bibliometric analysis of publications from three data sources: National Bibliometric Instrument (database from Republic of Moldavo), Scopus Elsevier and WoS. The Republic of Moldavo had the moderate number of scientific publications on cybersecurity; Russian Federation, Poland, Romania, Czech Republic, and Ukraine were the leading countries in Eastern Europe area (Cojocaru and Cojocaru 2019 ). Altarturi et al. ( 2020 ) was interested in bibliometric analysis of cyber parental control, basing on publications between 2000 and 2019 in Scopus and WoS. This research identified some most used keywords including ‘cyberbullying’, ‘bullying’, ‘adolescents’ and ‘adolescence’, showing their crucial position in the domain of cyber parental control (Altarturi et al. 2020 ). ‘Cyber victimization’ and ‘victimization’ were also mentioned as the common keywords by Altarturi et al. ( 2020 ). Prior research much focus on how to protect children from cyberbullying. Besides, four online threats for children were determined: content, contact, conduct and commercial threats (Altarturi et al. 2020 ).
Generally, it has been recorded several published bibliometric analyses of cyber-related issues but remained a lack of bibliometric research targeting cybercrime victimization. Thus, the present study attempts to fill this gap, reviewing the achievements of existed publications as well as updating the research trend in this field.
In detail, our current study aims to address four research questions (RQs):
What is overall distribution of publication based on year, institutions and countries, sources, and authors in cybercrime victimization?
Which are the topmost cited publications in terms of cybercrime victimization?
Who are the top co-authorships among authors, institutions, and countries in research cybercrime victimization?
What are top keywords, co-occurrences and research gaps in the field of cybercrime victimization?
Data collection procedure
Currently, among specific approaches in cybercrime’s fileds, WoS is “one of the largest and comprehensive bibliographic data covering multidisciplinary areas” (Zyoud et al. 2018 , p. 2). This paper retrieved data from the SSCI by searching publications of cybercrime victimization on WoS database to examine the growth of publication; top keywords; popular topics; research gaps; and top influential authors, institutions, countries, and journals in the academic community.
This paper employed Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) for data collection procedure. For timeline, we preferred to search between 2010 and 2020 on the WoS system with two main reasons. First, when the official update of the 2009 PRISMA Statement had ready upgraded with the specific guidelines and stable techniques, we consider beginning since 2010 that is timely to test. Secondly, although there are several publications from the early of 2021 to collect by the WoS, its updated articles will be continued until the end of the year. Therefore, we only searched until the end of 2020 to ensure the full updates.
To identify publications on cybercrime victimization, the study accessed WoS and used two keywords for searching: ‘cybercrime victimization’ or ‘cyber victimization’ after testing and looking for some terminology-related topics. Accordingly, the paper applied a combination of many other searching terms besides two selected words such as “online victimization”, “victim of cybercrime”, “phishing victimization”, “online romance victimization”, “cyberstalking victim”, “interpersonal cybercrime victimization”, or “sexting victimization”, the results, however, were not really appropriate. A lot of papers did not contain search keywords in their titles, abstracts, keywords and were not relavant to study topic. After searching with many different terms and comparing the results, the current study selected the two search terms for the most appropriate articles. The query result consisted of 962 documents. Basing on the result from preliminary searching, retrieved publications were refined automatically on WoS by criteria of timespan, document types, language, research areas, and WoS Index as presented in Table Table1. 1 . Accordingly, the criteria for automatic filter process were basic information of an articles and classified clearly in WoS system so the results reached high accuracy. The refined results are 473 articles.
Criteria for automatic filter
| Criteria | |
|---|---|
| Timespan | 2010–2020 |
| Document types | Article (Exclude early access) |
| Language | English |
| Research areas | Psychology; Criminology penology |
| WoS index | Social Sciences Citation Index (SSCI) |
After automatic filters, file of data was converted to Microsoft Excel 2016 for screening. The present study examined titles and abstracts of 473 articles to assess the eligibility of each publication according to the relevance with given topic. There are 387 articles are eligible,while 86 irrelevant publications were excluded.
Data analysis
Prior to data analysis, the raw data were cleaned in Microsoft Excel 2016. Different forms of the same author’s name were corrected for consistency, for example “Zhou, Zong-Kui” and “Zhou Zongkui”, “Van Cleemput, Katrien” and “Van Cleemput, K.”, “Williams, Matthew L.” and “Williams, Matthew”. Similarly, different keywords (single/plural or synonyms) used for the same concept were identified and standardized such as “victimization” and “victimisation”; “adolescent” and “adolescents”; “cyber bullying”, “cyber-bullying” and “cyberbullying”; “routine activity theory” and “routine activities theory”.
The data were processed by Microsoft Excel 2016 and VOS Viewer version 1.6.16; then it was analyzed according to three main aspects. First, descriptive statistic provided evidence for yearly distribution and growth trend of publications, frequency counts of citations, the influential authors, the predominant journals, the top institutions and countries/territories, most-cited publications. Second, co-authorship and co-occurrence analysis were constructed and visualized by VOS Viewer version 1.6.16 to explore the network collaborations. Finally, the current study also investigated research topics through content analysis of keywords. The authors’ keywords were classified into 15 themes, including: #1 cybercrime; #2 sample and demographic factors; #3 location; #4 theory; #5 methodology; #6 technology, platforms and related others; #7 psychology and mental health; #8 physical health; #9 family; #10 school; #11 society; #12 crimes and deviant behaviors; #13 victim; #14 prevention and intervention; and #15 others. Besides, the study also added other keywords from titles and abstracts basing on these themes, then indicated aspects examined in previous research.
In this section, all findings corresponding with four research questions identified at the ouset of this study would be illustrated (Fig. 1 ).

PRISMA diagram depicts data collection from WoS database
Distribution of publication
Distribution by year, institutions and countries.
Basing on retrieved data, it was witnessed an increasing trend of articles relevant to cybercrime victimization in SSCI list during the time of 2010–2020 but it had slight fluctuations in each year as shown in Fig. 2 . The total number of articles over this time was 387 items, which were broken into two sub-periods: 2010–2014 and 2015–2020. It is evident that the latter period demonstrated the superiority of the rate of articles (79.33%) compared to the previous period (20.67%). The yearly quantity of publications in this research subject was fewer than forty before 2015. Research of cybercrime victimization reached a noticeable development in 2016 with over fifty publications, remained the large number of publications in the following years and peaked at 60 items in 2018.

Annual distribution of publications
Distribution by institutions and countries
Table Table2 2 shows the top contributing institutions according to the quantity of publications related to cybercrime victimization. Of the top institutions, four universities were from the USA, two ones were from Spain, two institutions were from Australia and the rest ones were from Czech Republic, Belgium, Greece, and Austria. Specifically, Masaryk University (17 documents) became the most productive publishing institution, closely followed by Michigan State University (16 documents). The third and fourth places were University of Antwerp (13 documents) and Weber State University (10 documents). Accordingly, the institutions from The USA and Europe occupied the vast majority.
Top contributing institutions based on total publications
| Institutions | Countries | TP | TC | AC |
|---|---|---|---|---|
| Masaryk University | Czech Republic | 17 | 191 | 11.24 |
| Michigan State University | USA | 16 | 290 | 18.13 |
| University of Antwerp | Belgium | 13 | 285 | 21.92 |
| Weber State University | USA | 10 | 265 | 26.50 |
| Pennsylvania State University | USA | 9 | 83 | 9.22 |
| Democritus University of Thrace | Greece | 8 | 214 | 26.75 |
| University of Cordoba | Spain | 8 | 484 | 60.50 |
| University of Vienna | Austria | 8 | 109 | 13.63 |
| Edith Cowan University | Australia | 7 | 256 | 36.57 |
| University of Cincinnati | USA | 7 | 254 | 36.29 |
| University of Seville | Spain | 7 | 495 | 70.71 |
| University of Victoria | Australia | 7 | 188 | 26.86 |
TP total publications, TC total citations for the publications reviewed, AC average citations per document
In Table Table2, 2 , University of Seville (total citations: 495, average citations: 70.71) ranked first and University of Cordoba (total citations: 484, average citations: 60.50) stayed at the second place in both total citations and average citations.
Referring to distribution of publications by countries, there were 45 countries in database contributing to the literature of cybercrime victimization. The USA recorded the highest quantity of papers, creating an overwhelming difference from other countries (159 documents) as illustrated in Fig. 3 . Of the top productive countries, eight European countries which achieved total of 173 publications were England (39 documents), Spain (34 documents), Germany (22 documents), Netherlands (18 documents), Italy (17 documents) and Czech Republic (17 documents), Belgium (14 documents), Greece (12 documents). Australia ranked the fourth point (32 documents), followed by Canada (30 documents). One Asian country which came out seventh place, at the same position with Netherlands was China (18 documents).

Top productive countries based on the number of publications
Distribution by sources
Table Table3 3 enumerates the top leading journals in the number of publications relevant to cybercrime victimization. The total publications of the first ranking journal— Computers in Human Behavior were 56, over twice as higher as the second raking journal— Cyberpsychology, Behavior and Social Networking (24 articles). Most of these journals have had long publishing history, starting their publications before 2000. Only three journals launched after 2000, consisting of Journal of School Violence (2002), Cyberpsychology: Journal of Psychosocial Research on Cyberspace (2007) and Frontiers in Psychology (2010). Besides, it is remarked that one third of the top journals focuses on youth related issues: Journal of Youth and Adolescence , Journal of Adolescence, School Psychology International and Journal of School Violence .
Top leading journals based on the quantity of publications
| Journal Titles | TP | TC | AC | SPY |
|---|---|---|---|---|
| Computers in Human Behavior | 56 | 2055 | 36.70 | 1985 |
| Cyberpsychology, Behavior and Social Networking | 24 | 554 | 23.08 | 1999 |
| Journal of Youth and Adolescence | 19 | 1285 | 67.63 | 1972 |
| Aggressive Behavior | 15 | 661 | 44.07 | 1974 |
| Journal of Interpersonal Violence | 14 | 370 | 26.43 | 1986 |
| Cyberpsychology: Journal of Psychosocial Research on Cyberspace | 13 | 73 | 5.62 | 2007 |
| Journal of Adolescence | 12 | 538 | 44.83 | 1978 |
| Journal of School Violence | 12 | 302 | 25.17 | 2002 |
| Frontiers in Psychology | 11 | 85 | 7.73 | 2010 |
| School Psychology International | 9 | 531 | 59.00 | 1979 |
SPY Started Publication Year
In Table Table3, 3 , relating to total citations, Computers in Human Behavior remained the first position with 2055 citations. Journal of Youth and Adolescence had total 1285 citations, ranked second and followed by Aggressive Behavior with 661 citations. In terms of average citations per documents, an article of Journal of Youth and Adolescence was cited 67.63 times in average, much higher than average citations of one in Computers in Human Behavior (36.70 times). The other journals which achieved the high number of average citations per document were School Psychology International (59.00 times), Journal of Adolescence (44.83 times) and Aggressive Behavior (44.07 times).
Distribution by authors
Table Table4 4 displays ten productive authors based on article count; total citations of each author and their average citations per document are also included. Michelle F. Wright from Pennsylvania State University ranked first with twenty publications, twice as higher as the second positions, Thomas J. Holt (10 articles) from Michigan State University and Bradford W. Reyns (10 articles) from Weber State University. Rosario Ortega-Ruiz from University of Cordoba stayed at the third place in terms of total publications but the first place in aspect of total citations (483 citations) and the average citations (60.38 times).
Top productive authors based on article count
| Authors | TP | TC | AC |
|---|---|---|---|
| Wright, Michelle F | 20 | 315 | 15.75 |
| Holt, Thomas J | 10 | 250 | 25.00 |
| Reyns, Bradford W | 10 | 265 | 26.50 |
| Holfeld, Brett | 8 | 110 | 13.75 |
| Kokkinos, Constantinos M | 8 | 214 | 26.75 |
| Ortega-Ruiz, Rosario | 8 | 483 | 60.38 |
| Vandebosch, Heidi | 8 | 185 | 23.13 |
| Yanagida, Takuya | 8 | 78 | 9.75 |
| Leukfeldt, Rutger | 7 | 165 | 23.57 |
| Spiel, Christiane | 7 | 107 | 15.29 |
Of the most productive authors based on total publications, there were three authors from universities in the USA; one from the university in Canada (Brett Holfeld); the others were from institutions in Euro, including Spain (Rosario Ortega-Ruiz), Greece (Constantinos M. Kokkinos) and Belgium (Heidi Vandebosch), Netherlands (Rutger Leukfeldt) and Austria (Takuya Yanagida and Christiane Spiel).
Most-cited publications
The most-cited literature items are displayed in Table Table5. 5 . The article which recorded the highest number of citations was ‘Psychological, Physical, and Academic Correlates of Cyberbullying and Traditional Bullying’ (442 citations) by Robin M. Kowalski et al. published in Journal of Adolescent Health , 2013. Seven of ten most-cited articles were about cyberbullying; focused on youth population; made comparisons between cyberbullying and traditional bullying; analyzed the impact of several factors such as psychological, physical, academic factors or use of Internet; discussed on preventing strategies. The other publications studied victimization of cyberstalking and cyber dating abuse. All most-cited articles were from 2015 and earlier.
The most-cited publications in subject of cybercrime victimization during 2010–2020
| Title | Author | Source title | Year | TC |
|---|---|---|---|---|
| Psychological, Physical, and Academic Correlates of Cyberbullying and Traditional Bullying | Kowalski et al. | Journal of Adolescent Health | 2013 | 442 |
| The Nature of Cyberbullying, and Strategies for Prevention | Slonje et al. | Computers in Human Behavior | 2013 | 323 |
| Associations among Bullying, Cyberbullying, and Suicide in High School Students | Bauman et al. | Journal of Adolescence | 2013 | 289 |
| Longitudinal and Reciprocal Relations of Cyberbullying With Depression, Substance Use, and Problematic Internet Use Among Adolescents | Gamez-Guadix | Journal of Adolescent Health | 2013 | 253 |
| Peer and Cyber Aggression in Secondary School Students: The Role of Moral Disengagement, Hostile Attribution Bias, and Outcome Expectancies | Pornari et al. | Aggressive Behavior | 2010 | 234 |
| Cyber Bullying and Internalizing Difficulties: Above and Beyond the Impact of Traditional Forms of Bullying | Bonanno et al. | Journal of Youth and Adolescence | 2013 | 205 |
| The Rate of Cyber Dating Abuse Among Teens and How It Relates to Other Forms of Teen Dating Violence | Zweig et al. | Journal of Youth and Adolescence | 2013 | 180 |
| The Overlap Between Cyberbullying and Traditional Bullying | Waasdorp et al. | Journal of Adolescent Health | 2015 | 178 |
| A Longitudinal Study of Cyberbullying: Examining Risk and Protective Factors | Fanti et al. | European Journal of Developmental Psychology | 2012 | 177 |
| Being Pursued Online: Applying Cyberlifestyle-Routine Activities Theory to Cyberstalking Victimization | Reyns et al. | Criminal Justice and Behavior | 2011 | 172 |
Of the top productive authors, only Bradford W. Reyns had an article appeared in the group of most-cited publications. His article ‘Being Pursued Online: Applying Cyberlifestyle-Routine Activities Theory to Cyberstalking Victimization’ (2011) was cited 172 times.
Co-authorship analysis
“Scientific collaboration is a complex social phenomenon in research” (Glänzel and Schubert 2006 , p. 257) and becomes the increasing trend in individual, institutional and national levels. In bibliometric analysis, it is common to assess the productivity and international collaboration of research; identify key leading researchers, institutions, or countries (E Fonseca et al. 2016 ) as well as potential collaborators in a specific scientific area (Romero and Portillo-Salido 2019 ) by co-authorship analysis which constructs networks of authors and countries (Eck and Waltman 2020 ).
This section analyses international collaboration relevant to research of cybercrime victimization among authors, institutions, and countries during 2010–2020 through visualization of VOS Viewer software.
Collaboration between authors
Referring to the threshold of choose in this analysis, minimum number of documents of author is three and there were 80 authors for final results. Figure 4 illustrates the relationships between 80 scientists who study in subject of cybercrime victimization during 2010–2020. It shows several big groups of researchers (Wright’s group, Vandebosch’s group, or Holt’s group), while numerous authors had limited or no connections to others (Sheri Bauman, Michelle K. Demaray or Jennifer D. Shapka).

Collaboration among authors via network visualization (threshold three articles for an author, displayed 80 authors)
Figure 5 displayed a significant network containing 23 authors who were active in collaboration in detail. The displayed items in Fig. 5 are divided into five clusters coded with distinctive colors, including red, green, blue, yellow, and purple. Each author item was represented by their label and a circle; the size of label and circle are depended on the weight of the item, measured by the total publications (Eck and Waltman 2020 ). The thickness of lines depends on the strength of collaboration (Eck and Waltman 2020 ).

Collaboration among authors via network visualization (threshold three articles for an author, displayed 23 authors)
The most significant cluster was red one which is comprised of six researchers: Michelle F. Wright, Sebastian Wachs, Yan Li, Anke Gorzig, Manuel Gamez-Guadix and Esther Calvete. The remarked author for the red cluster was Michelle F. Wright whose value of total link strength is 24. She had the strongest links with Sebastian Wachs; closely link with Yan Li, Anke Gorzig, Manuel Gamez-Guadix and collaborated with authors of yellow cluster, including Shanmukh V. Kamble, Li Lei, Hana Machackova, Shruti Soudi as well as Takuya Yanagida of blue cluster. Michelle F. Wright who obtained the largest number of published articles based on criteria of this study made various connections with other scholars who were from many different institutions in the world. This is also an effective way to achieve more publications.
Takuya Yanagida was the biggest node for the blue cluster including Petra Gradinger, Daniel Graf, Christiane Spiel, Dagmar Strohmeier. Total link strength for Takuya Yanagida was 28; twelve connections. It is observed that Takuya Yanagida’ s research collaboration is definitely active. Besides, other research groups showed limited collaborations comparing with the red and blue ones.
Collaboration between institutions
The connections among 156 institutions which published at least two documents per one are shown in Fig. 6 . Interestingly, there is obvious connections among several distinctive clusters which were coded in color of light steel blue, orange, purple, steel blue, green, red, yellow, light red, dark turquoise, light blue, brown and light green. These clusters created a big chain of connected institutions and were in the center of the figure, while other smaller clusters or unlinked bubbles (gray color) were distributed in two sides. The biggest chain consisted of most of productive institutions such as Masaryk University, Michigan State University, University of Antwerp, Weber State University, University of Cordoba, Edith Cowan University, University of Cincinnati, University of Victoria, University of Vienna, and University of Seville.

Collaboration among institutions via network visualization (threshold two articles for an institution, 156 institutions were displayed)
Light steel blue and orange clusters presented connections among organizations from Australia. Light green included institutions from Netherland, while turquoise and light blue consisted of institutions from the USA. Yellow cluster was remarked by the various collaborations among institutions from China and Hong Kong Special Administrative Region (Renmin University of China and South China Normal University, University of Hong Kong, the Hong Kong Polytechnic University and the Chinese University of Hong Kong), the USA (University of Virginia), Cyprus (Eastern Mediterranean University), Japan (Shizuoka University), India (Karnataka University) and Austria (University Applied Sciences Upper Austria). Central China Normal University is another Chinese institution which appeared in Fig. 5 , linking with Ministry of Education of the People’s Republic of China, Suny Stony Brook and University of Memphis from the USA.
Masaryk University and Michigan State University demonstrated their productivity in both the quantity of publications and the collaboration network. They were active in research collaboration, reaching twelve and eleven links, respectively, with different institutions, but focused much on networking with institutions in the USA and Europe.
Collaboration between countries
The collaboration among 45 countries which published at least one SSCI documents of cybercrime victimization during the given period was examined in VOS Viewer but just 42 items were displayed via overlay visualization. Figure 7 depicts the international collaborations among significant countries. The USA is the biggest bubble due to its biggest number of documents and shows connections with 26 countries/regions in Euro, Asia, Australia, Middle East. Excepting European countries, England collaborate with the USA, Australia, South Korea, Japan, Thailand, Singapore, Sri Lanka, and Colombia. Spain and Germany almost focus on research network within Euro. China has the strongest tie with the USA, link with Australia, Germany, Czech Republic, Austria, Cyprus and Turkey, Japan, Indian, Vietnam.

Collaboration among countries via overlay visualization
Color bar in Fig. 7 is determined by the average publication year of each country and the color of circles based on it. It is unsurprised that the USA, Australia, England, or Spain shows much research experience in this field and maintain the large number of publications steadily. Interestingly, although the average publication year of South Korea or Cyprus was earlier than other countries (purple color), their quantities of documents were moderate. The new nodes (yellow circles) in the map included Vietnam, Norway, Pakistan, Ireland, Scotland, Switzerland.
Keywords and co-occurrence
The present paper examined the related themes and contents in research of cybercrime victimization during 2010–2020 through collecting author keywords, adding several keywords from tiles and abstracts. Besides, this study also conducted co-occurrence analysis of author keywords to show the relationships among these keywords.
The keywords were collected and categorized into 15 themes in Table Table6, 6 , including cybercrime; sample and demographic factors; location; theory; methodology; technology, platform, and related others; psychology and mental health; physical health; family; school; society; crimes and other deviant behaviors; victim; prevention and intervention; and others.
Statistic of keywords in themes
| No. | Themes | Keywords |
|---|---|---|
| 1 | Cybercrime | Cyber-interpersonal violence, cyber/online bullying, workplace cyberbullying, technologically facilitated violence, cyber/online/digital/internet aggression, proactive cyber aggression, reactive cyber aggression, cyber discrimination, cyber-ostracism, cyber hate, cyber trolling, cyberstalking, cyber grooming, cyber/online harassment, cyber/online sexual harassment, cyber dating abuse/violence, non-consensual pornography, image-based sexual abuse, revenge porn, sexting, virtual theft, cyber/online identity theft, online/internet fraud, pet scams, phishing, cyber/digital abuse, computer focused crimes, cyber-dependent crime, ransomware, hacking, malicious software, malware, computer exploits, port scans, and denial of service (dos) attacks |
| 2 | Sample and demographic factors | Young children, primary school children, elementary school children, post-primary, children and youth, secondary school students, secondary education, post secondary, school students, university students, college students, undergraduate, latino students, student leaders, higher education, juveniles, adolescent, pre-adolescent, early adolescent, late adolescent, youth, young adults, youth adults, adults, emerging adult, emerging adulthood, elder, gender, age, gender stereotype trait, gender typicality, gender junior-high, demographic differences |
| 3 | Location | Australia, Canada, Colombia, India, Northern Ireland, Republic of Ireland, Pakistan, Vietnam, Thailand, Spain, Italia, China, Hong Kong, the USA, Litva, Japan, Belgium, Romania, Turkey, Norway, South Korea, Netherland, Singapore, Portugal, Chile, Cyprus, England, Germany, Sweden, Hungary, Israel, Greece, Austria, Malaysia, Great Britain, United Kingdom, six countries (Germany, India, South Korea, Spain, Thailand and the USA), three countries (Israel, Litva, Luxembourg), four countries (the USA, the UK, Germany and Finland), four countries (Netherland, Germany, Thailand, The USA), two countries (Canada And Tazania), six countries (China, Cyprus, the Czech Republic, India, Japan and The USA), eight countries (Australia, Canada, Germany, Hong Kong, Netherlands, Sweden, The UK, and The USA), six Europe countries (Spain, Germany, Italy, Poland, the UK, and Greece), two countries (Canada and the USA) |
| 4 | Theory | Ciminological theory, routine activities theory, lifestyle-routine activities theory, lifestyle exposure theory, cyber-routine activities theory, criminal opportunity theory, general strain theory (strain theory), actor-network theory, theory of reasoned action (TRA), attribution theory, behavior change theories, buffering effect, bystander intervention model, evolutionary theory, health belief model, multi-theoretical, parent-child communication, perception modeling, protection motivation theory, rational choice theory, risk interpretation model, spillover effect, socio-ecological approach, social identity theory, self-determination theory, self-control theory, person-oriented approach, big five, compensatory social interaction model, the general aggression model, a multi-dimensional measurement model, dark triad personality traits, the cyclic process model |
| 5 | Methodology | Qualitative interviews, mix method design, survey method, questionnaire, question order, natural experiment, systematic review, meta-analysis, social network analysis, thematic analysis, factor analysis, contextual analyses, state-level analysis, multi-level analyses, latent class analysis, confirmatory factor analysis, multi-level analysis, latent profile analysis, latent transition analysis, macro-level crime analysis, panel survey/study, cross-lagged panel design, ex post facto study, longitudinal study, longitudinal cohort, longitudinal data, longitudinal patterns, cross-lagged panel model, daily methods, scale development, validity, bayesian profile regression, bootstrap mediation, class-level variables, classification, co-occurrence, construct validity, construct, convergent, correlates, country comparison, cross-national comparison, cross-sectional survey, cross-national data, cross-national research, multi-nation study, factor structure, frequency, functional magnetic resonance imaging, multiple mediators, individual variables, measurement invariance, methodological challenges, methods of counting crime, national crime victimization survey, self-reports, Quebec longitudinal study of child development. dass-21, European cyberbullying intervention project questionnaire (ECIPQ), SDQ (the strengths and difficulties questionnaire), affective styles, attribution style, CDAQ (cyber dating abuse questionnaire), SN-PEQ (the social networking-peer experiences questionnaire), the submissive behavior scale, the cyber bullying scale, the cyber victimization scale, the moral disengagement scale, the cyber-peer experiences questionnaire, school refusal assessment scale revised, the screening of harassment among peers, the moods and feeling questionnaire, the cambridge friendship questionnaire, online aggression scale, the cyberbullying triangulation questionnaire, the Warwick-Edinburgh mental well-being scale, the cyber dating violence inventory, the cyber aggression questionnaire for adolescents, violence tendency scale, revised cyber bullying inventory, the partner cyber abuse questionnaire, the patient health questionnaire-9, e-victimization scale, e-bullying scale |
| 6 | Technology, platforms and related others | Social media, internet, social networking sites, facebook, kakaotalk, instagram, technology, new technologies, adoption of technology, anonymity, smartphone, protocol, botnet, clickbait, computer-mediated communication, digital devices, electronic communication technology, information and communication technologies (icts), technological infrastructure, technology use, problematic internet use, media, media use, internet attachment, internet and abuse, internet communication, online, online intimidation, online lifestyle, online research, online risk behavior, online risks, online routine activity, overt narcissism, online activity, online behavior, online communication, online/electronic/mobile games, online disclosure, online disinhibition, personal information privacy, virtual, texting, text messaging, technical mediation, information/techical/cyber security, screen time, security notices, security seals, technical mediation, internet frequency, self-disclosure, media violence exposure |
| 7 | Psychology and mental health | Self-esteem, self-compassion, self-control, self-concept, self-efficacy, ict self-efficacy, self-harming, anxiety, symptoms of anxiety, depressive symptoms, childhood stress, hopelessness, moral, moral identity, moral disengagement, mental health, loneliness, externalizing problems, internalizing problems, internalizing symptoms, psychometrics, fear of crime, fear of victimization, fear of cybercrime, nomophobia, trust, attribution, hostile attribution bias, autism, personality profile, empathic accuracy, affective empathy, empathy, cognitive empathy, developmental trajectories, impulsivity, intellectual disability, internet addiction, motivation, cyber-relationship motives, narcissism, personality, psychopathic traits, psychopathy, psychosocial adjustment, school psychology, sensation seeking, psychological well-being, subjective well-being, well-being, active–passive patterns, asperger's syndrome, attention deficit hyperactivity disorder (ADHD), attitudes, attitudes toward Facebook, attitudes toward school, cyberbullying attitudes, autism spectrum disorder, avoidance of rest, awareness, overweight preoccupation, body dissatisfaction, body esteem, callous-unemotional traits, chronic pain, cognitive reappraisal, compulsive internet use, control beliefs, coping self-efficacy, covert narcissism, cyber incivility, cyberpsychology, decision-making, digital data security awareness, distress, eating disorders psychopathology, emotion regulation, emotional problems, emotion dysregulation, emotion perception accuracy, emotion perception bias, emotional adjustment, emotional competence, emotional distress, emotional impact, emotional intelligence, socio-emotional factors, social and emotional competencies, epidemiology, expressive suppression, general self-efficacy, harmful intention, intentionality, incivility, life satisfaction, mental health difficulties, metacognitive awareness, mimicry, internet use motives, motivational valence, normative beliefs about aggression, need for stimulation, belief in a just world, normative belief, normative belief about helping, normative beliefs, optimism, social cognition, social competence, perceptions, perceived acceptance, perceived burdensomeness, perceived emotional intelligence, perceived popularity, perceived risk, perceived social support, perceptions of blame, perceptions of peers, anger rumination, anger, state anger, trait anger, perpetration trait anger, persistence, physical and psychological problems, post-traumatic stress symptoms, psychological and behavioral health problems, psychological disease, psychological distress, psychological symptoms, psychopathology symptoms, psychometric properties, romantic jealousy, rumination, vulnerabilities, violence tendency, externalizing behaviors, antisocial behavior, behavior activation, behavior, behavior problems, behavior measures, bystanders behavior, cyberbullying behavior, high-risk internet behaviors, school refusal behavior, submissive behavior, helping behavior, controlling behavior, cyber behavior, promiscuity |
| 8 | Physical health | Sex, sex difference, sexual double standard, sexual orientation, sexual pressure, suicide ideation, suicide attempt, suicidality, adolescent health, physical disabilities, physical health, diet, disability, health risks, paedosexual, adolescent development |
| 9 | Family | Parental mediation, parents, family climate, household activity, in-law conflict, parent-adolescent communication, parent-adolescent information sharing, parent–child communication, parental awareness, parental control, parental mediation of media, parental monitoring, parental monitoring of cyber behavior, parental style |
| 10 | School | school bonding, school context, school record, value of learning, university, teacher bonding, teacher justice, teachers, peer education, peer influence, peer rejection, peer relations, peer nominations, peers, prosocial peer affiliation, friendship networks, classmate justice, friendship quality, high school, middle school, peer nomination, peer attachment, peers/peer relations, school climate, academic performance, academic problems, school adjustment, schools |
| 11 | Society | Social standing, social relationships, norms, social norms, injunctive norms, subjective norm, descriptive norms, moral norms, interpersonal relationships, collectivism, individualism, contextual factors, controllers, cross-cultural, social information processing, social exclusion, social engagement, social desirability, social coping, social bonds, social belongingness, socialization, machiavellianism, femininity, masculinity, fun-seeking tendencies, help-seeking, helpfulness, cryptomarkets, cultural values, ethno-cultural groups, social learning, social skills, culture, bystander, cyber bystander, social support |
| 12 | Crimes and deviant behaviors | Violence, offline violence, gendered violence, dating violence, sexual violence, teen dating violence, intimate partner violence, domestic violence, youth violence, bullying, school bullying, offline bullying, covert bullying, workplace bullying, face-to-face bullying, non-physical bullying, traditional face-to-face bullying, traditional bullying perpetration, sibling bullying, perpetrators of bullying, substance use, adolescent substance use, smoking, alcohol use, fraud, scam, white-collar crime, property crime, abuse, addiction, verbal aggression, aggressive behavior, aggressor, physical aggression, face-to-face aggression, anti-muslim hate crime, hate speech, disability hate crime, crime, crime drop, delinquency, elder abuse, juvenile delinquency, perpetration, offender, online deviance, troubled offline behavior, sexual solicitation, partner abuse, sexual harassment, sexual orientation-based harassment, peer harassment, race-based harassment |
| 13 | Victim | Victim blaming, recurring victimization, relational victimization, victims of bullying, bullying victimization, traditional bully victimization, face-to-face victimization, family victimization, traditional victimization, school victimization, peer victimization, threat victimization, cybercrime victimization, cyberstalking victimization, cyber-theft victimization, cyber victims, aggressive victim |
| 14 | Prevention and intervention | Uniform crime reporting program, solutions, social problem-solving, safety, intervention, intervention strategies, intervention success, prevention, coping strategies, predictors, protective factors, police, policing, anti-bullying program, Canadian 24-h movement guidelines, capable guardianship, control, control balance, coping efficacy, national incident-based reporting system, crime reporting, reporting, cyber witnessing, cyberbullying intervention, bullying prevention, cyberbullying reduction, eurobarometer, evidence-based intervention, safety, prediction, preventive behavior, super controllers, counseling, guardianship, whole-school program trial, psychological service providers, risk and protective factors, intrusion prevention system, risk management, risk factors, mediation, restrictive mediation, instructive mediation, moderation, |
| 15 | Others | Routine activities, validation, opportunity, popularity, prevalence, agency, associations, assessment, attachment, causes, certs, victim-offender overlap, coronavirus, covid-19, definition, definitional issues, judgments, multiple risk exposure, multiple informants, outcome expectancies, participant roles, physical activity, publicity, reliability, resistance, response decision, response evaluation, role continuity, sustainability, sleep, similarities, severity |
These keywords were most of author keyword, adding a few selected keywords from the titles and abstracts by the author of this current study
In the theme of cybercrime, there were numerous types of cybercrimes such as cyberbullying, cyber aggression, cyberstalking, cyber harassment, sextortion and other cyber dating crimes, cyber fraud, identity theft, phishing, hacking, malware, or ransomware. Generally, the frequency of interpersonal cybercrimes or cyber-enable crimes was much higher than cyber-dependent crimes. Cyberbullying was the most common cybercrime in research.
Relating to sample and demographic factors, there were sample of children, adolescent, adults, and the elder who were divided into more detail levels in each research; however, adolescent was the most significant sample. Besides, demographic factor of gender received a remarked concern from scholars.
It is usual that most of the research were carried out in one country, in popular it was the USA, Spain, Germany, England, Australia, Canada or Netherland but sometimes the new ones were published such as Chile, Vietnam, Thailand or Singapore. It was witnessed that some studies showed data collected from a group of countries such as two countries (Canada and the United State), three countries (Israel, Litva, Luxembourg), four countries (the USA, the UK, Germany, and Finland), or six Europe countries (Spain, Germany, Italy, Poland, the United Kingdom and Greece).
A wide range of theories were applied in this research focusing on criminological and psychological theories such as Routine Activities Theory, Lifestyle—Routine Activities Theory, General Strain Theory, the Theory of Reasoned Action or Self-control Theory.
Table Table6 6 indicated a lot of different research methods covering various perspective of cybercrime victimization: systematic review, questionnaire survey, interview, experiment, mix method, longitudinal study, or cross-national research; many kinds of analysis such as meta-analysis, social network analysis, latent class analysis, confirmatory factor analysis; and a wide range of measurement scales which were appropriate for each variable.
Topic of cybercrime victimization had connections with some main aspects of technology (information and communication technologies, internet, social media or technology related activities), psychology (self-esteem, fear, attitude, personality, psychological problems, empathy, perceptions or emotion), physical health, family (parents), school (peers, school climate), society (norms, culture, social bonds), victim, other crimes (violence, substance use), prevention and intervention.
Co-occurrence analysis was performed with keywords suggested by authors and the minimum number of occurrences per word is seven. The result showed 36 frequent keywords which clustered into five clusters as illustrated in Fig. 8 .

Co-occurrence between author keywords via network visualization (the minimum number of occurrences per word is seven, 36 keywords were displayed)
Figure 8 illustrates some main issues which were concerned in subject of cybercrime victimization, as well as the relationship among them. Fifteen most frequent keywords were presented by big bubbles, including: ‘cyberbullying’ (174 times), ‘cyber victimization’ (90 times), ‘adolescent’ (79 times), ‘bullying’ (66 times), ‘victimization’ (56 times), ‘cybercrime’ (40 times), ‘cyber aggression’ (37 times), ‘depression’ (23 times), ‘aggression’ (14 times), ‘routine activities theory’ (13 times), ‘cyberstalking’ (11 times), ‘gender’ (11 times), ‘longitudinal’ (10 times), ‘peer victimization’ (10 times) and ‘self-esteem’ (10 times).
‘Cyberbullying’ linked with many other keywords, demonstrating the various perspectives in research of this topic. The thick lines which linked ‘cyberbullying’ and ‘bullying’, ‘adolescent’, ‘cyber victimization’, ‘victimization’ showed the strong connections between them; there were close relationship between ‘cyber aggression’, ‘bystander”, ‘self-esteem’ or ‘moral disengagement’ and ‘cyberbullying’.
‘Cybercrime’ had strong links with ‘victimization’, ‘routine activities theory’. In Fig. 8 , the types of cybercrime which occurred at least seven times were: cyberbullying, cyber aggression, hacking, cyberstalking, and cyber dating abuse.
The increasing trend over the years reveals the increasing concern of scholarly community on this field, especially in the boom of information technology and other communication devices and the upward trend in research of cyberspace-related issues (Altarturi et al. 2020 ; Leung et al. 2017 ; Serafin et al. 2019 ). It predicts the growth of cybercrime victimization research in future.
Psychology was the more popular research areas in database, defeating criminology penology. As part of the ‘human factors of cybercrime’, human decision-making based on their psychological perspectives plays as a hot topic in cyber criminology (Leukfeldt and Holt 2020 ). Then, it is observed that journals in psychology field was more prevalent in top of productive sources. Besides, journal Computers in Human Behavior ranked first in total publications, but Journal of Youth and Adolescence ranked higher place in the average citations per document. Generally, top ten journals having highest number of publications on cybercrime victimization are highly qualified ones and at least 10 years in publishing industry.
The USA demonstrated its leading position in the studied domain in terms of total publications as well as the various collaborations with other countries. The publications of the USA occupied much higher than the second and third countries: England and Spain. It is not difficult to explain for this fact due to the impressive productivity of institutions and authors from the USA. A third of top twelve productive institutions were from the USA. Three leading positions of top ten productive authors based on document count were from institutions of the USA, number one was Michelle F. Wright; others were Thomas J. Holt and Bradford W. Reyns.
Furthermore, these authors also participated in significant research groups and become the important nodes in those clusters. The most noticeable authors in co-authors network were Michelle F. Wright. The US institutions also had strong links in research network. The USA was likely to be open in collaboration with numerous countries from different continents in the world. It was assessed to be a crucial partner for others in the international co-publication network (Glänzel and Schubert 2006 ).
As opposed to the USA, most of European countries prefer developing research network within Europe and had a limited collaboration with other areas. Australia, the USA, or Japan was in a small group of countries which had connections with European ones. Nevertheless, European countries still showed great contributions for research of cybercrime victimization and remained stable links in international collaboration. The prominent authors from Euro are Rosario Ortega-Ruiz, Constantinos M. Kokkinos or Rutger Leukfeldt.
It is obvious that the limited number of publications from Asia, Middle East, Africa, or other areas resulted in the uncomprehensive picture of studied subject. For example, in the Southeast Asia, Malaysia and Vietnam lacked the leading authors with their empirical studies to review and examine the nature of cybercrimes, though they are facing to practical challenges and potential threats in the cyberspace (Lusthaus 2020a , b ). The present study indicated that Vietnam, Ireland, or Norway was the new nodes and links in research network.
Several nations which had a small number of publications such as Vietnam, Thailand, Sri Lanka, or Chile started their journey of international publications. It is undeniable that globalization and the context of global village (McLuhan 1992 ) requires more understanding about the whole nations and areas. Conversely, each country or area also desires to engage in international publications. Therefore, new nodes and clusters are expected to increase and expand.
The findings indicated that cyberbullying was the most popular topic on research of cybercrime victimization over the given period. Over a half of most-cited publications was focus on cyberbullying. Additionally, ‘cyberbullying’ was the most frequent author keyword which co-occurred widely with distinctive keywords such as ‘victimization’, ‘adolescents’, ‘bullying’, ‘social media’, ‘internet’, ‘peer victimization’ or ‘anxiety’.
By reviewing keywords, several research gaps were indicated. Research samples were lack of population of the children and elders, while adolescent and youth were frequent samples of numerous studies. Although young people are most active in cyberspace, it is still necessary to understand other populations. Meanwhile, the elderly was assumed to use information and communication technologies to improve their quality of life (Tsai et al. 2015 ), their vulnerability to the risk of cybercrime victimization did not reduce. Those older women were most vulnerable to phishing attacks (Lin et al. 2019 ; Oliveira et al. 2017 ). Similarly, the population of children with distinctive attributes has become a suitable target for cybercriminals, particularly given the context of increasing online learning due to Covid-19 pandemic impacts. These practical gaps should be prioritized to focus on research for looking the suitable solutions in the future. Besides, a vast majority of research were conducted in the scope of one country; some studies collected cross-national data, but the number of these studies were moderate and focused much on developed countries. There are rooms for studies to cover several countries in Southeast Asia or South Africa.
Furthermore, although victims may be both individuals and organizations, most of research concentrated much more on individuals rather than organizations or companies. Wagen and Pieters ( 2020 ) indicated that victims include both human and non-human. They conducted research covering cases of ransomware victimization, Bonet victimization and high-tech virtual theft victimization and applying Actor-Network Theory to provide new aspect which did not aim to individual victims. The number of this kind of research, however, was very limited. Additionally, excepting cyberbullying and cyber aggression were occupied the outstanding quantity of research, other types of cybercrime, especially, e-whoring, or social media-related cybercrime should still be studied more in the future.
Another interesting topic is the impact of family on cybercrime victimization. By reviewing keyword, it is clear that the previous studies aimed to sample of adolescent, hence, there are many keywords linking with parents such as ‘parent-adolescent communication’, ‘parent-adolescent information sharing’, ‘parental mediation’, ‘parental monitoring of cyber behavior’, ‘parental style’. As mentioned above, it is necessary to research more on sample of the elder, then, it is also essential to find out how family members affect the elder’s cybercrime victimization.
It is a big challenge to deal with problems of cybercrime victimization because cybercrime forms become different daily (Näsi et al. 2015 ). Numerous researchers engage in understanding this phenomenon from various angles. The current bibliometric study assessed the scholarly status on cybercrime victimization during 2010–2020 by retrieving SSCI articles from WoS database. There is no study that applied bibliometric method to research on the examined subject. Hence, this paper firstly contributed statistical evidence and visualized findings to literature of cybercrime victimization.
Statistical description was applied to measure the productive authors, institutions, countries/regions, sources, and most-cited documents, mainly based on publication and citation count. The international collaborations among authors, institutions, and countries were assessed by co-authors, while the network of author keywords was created by co-occurrence analysis. The overall scholarly status of cybercrime victimization research was drawn clearly and objectively. The research trend, popular issues and current gaps were reviewed, providing numerous suggestions for policymakers, scholars, and practitioners about cyber-related victimization (Pickering and Byrne 2014 ). Accordingly, the paper indicated the most prevalent authors, most-cited papers but also made summary of contributions of previous research as well as identified research gaps. First, this article supports for PhD candidates or early-career researchers concerning about cybercrime victimization. Identifying the leading authors, remarked journals, or influencing articles, gaps related to a specific research topic is important and useful task for new researchers to start their academic journey. Although this information is relatively simple, it takes time and is not easy for newcomers to find out, especially for ones in poor or developing areas which have limited conditions and opportunities to access international academic sources. Thus, the findings in the current paper provided for them basic but necessary answers to conduct the first step in research. Secondly, by indicating research gaps in relevance to sample, narrow topics or scope of country, the paper suggests future study fulfilling them to complete the field of cybercrime victimization, especial calling for publications from countries which has had a modest position in global research map. Science requires the balance and diversity, not just focusing on a few developed countries or areas. Finally, the present study assists researchers and institutions to determined strategy and potential partners for their development of research collaborations. It not only improve productivity of publication but also create an open and dynamic environment for the development of academic field.
Despite mentioned contributions, this study still has unavoidable limitations. The present paper just focused on SSCI articles from WoS database during 2010–2020. It did not cover other sources of databases that are known such as Scopus, ScienceDirect, or Springer; other types of documents; the whole time; or articles in other languages excepting English. Hence it may not cover all data of examined subject in fact. Moreover, this bibliometric study just performed co-authorship and co-occurrence analysis. The rest of analysis such as citation, co-citation and bibliographic coupling have not been conducted. Research in the future is recommended to perform these kinds of assessment to fill this gap. To visualize the collaboration among authors, institutions, countries, or network of keywords, this study used VOS Viewer software and saved the screenshots as illustrations. Therefore, not all items were displayed in the screenshot figures.
Data availability
Declarations.
The authors declare that they have no competing interest.
1 In the ‘commemorating a decade in existence of the International Journal of Cyber Criminoogy’, Ngo and Jaishankar ( 2017 ) called for further research with focusing on five main areas in the Cyber Criminiology, including (1) defining and classifying cybercrime, (2) assessing the prevalence, nature, and trends of cybercrime, (3) advancing the field of cyber criminology, (4) documenting best practices in combating and preventing cybercrime, and (5) cybercrime and privacy issues.
Contributor Information
Huong Thi Ngoc Ho, Email: moc.liamg@252nhgnouH .
Hai Thanh Luong, Email: [email protected] .
- Abdullah ATM, Jahan I. Causes of cybercrime victimization: a systematic literature review. Int J Res Rev. 2020; 7 (5):89–98. [ Google Scholar ]
- Al-Nemrat A, Benzaïd C (2015) Cybercrime profiling: Decision-tree induction, examining perceptions of internet risk and cybercrime victimisation. In: Proceedings—14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, TrustCom 2015, vol 1, pp 1380–1385. 10.1109/Trustcom.2015.534
- Alalehto TI, Persson O. The Sutherland tradition in criminology: a bibliometric story. Crim Justice Stud. 2013; 26 (1):1–18. doi: 10.1080/1478601X.2012.706753. [ CrossRef ] [ Google Scholar ]
- Algarni A, Xu Y, Chan T. An empirical study on the susceptibility to social engineering in social networking sites: the case of Facebook. Eur J Inf Syst. 2017; 26 (6):661–687. doi: 10.1057/s41303-017-0057-y. [ CrossRef ] [ Google Scholar ]
- Altarturi HHM, Saadoon M, Anuar NB. Cyber parental control: a bibliometric study. Child Youth Serv Rev. 2020 doi: 10.1016/j.childyouth.2020.105134. [ CrossRef ] [ Google Scholar ]
- Ariola B, Laure ERF, Perol ML, Talines PJ. Cybercrime awareness and perception among Students of Saint Michael College of Caraga. SMCC Higher Educ Res J. 2018; 1 (1):1. doi: 10.18868/cje.01.060119.03. [ CrossRef ] [ Google Scholar ]
- Benson V, Saridakis G, Tennakoon H. Purpose of social networking use and victimisation: are there any differences between university students and those not in HE? Comput Hum Behav. 2015; 51 :867–872. doi: 10.1016/j.chb.2014.11.034. [ CrossRef ] [ Google Scholar ]
- Brenner SW. Is there such a thing as “rough”? Calif Crim Law Rev. 2001; 4 (1):348–349. doi: 10.3109/09637487909143344. [ CrossRef ] [ Google Scholar ]
- Chen X, Wang S, Tang Y, Hao T. A bibliometric analysis of event detection in social media. Online Inf Rev. 2019; 43 (1):29–52. doi: 10.1108/OIR-03-2018-0068. [ CrossRef ] [ Google Scholar ]
- Choi K. Computer Crime Victimization and Integrated Theory: an empirical assessment. Int J Cyber Criminol. 2008; 2 (1):308–333. [ Google Scholar ]
- Cojocaru I, Cojocaru I (2019) A bibliomentric analysis of cybersecurity research papers in Eastern Europe: case study from the Republic of Moldova. In: Central and Eastern European E|Dem and E|Gov Days, pp 151–161
- Das B, Sahoo JS. Social networking sites—a critical analysis of its impact on personal and social life. Int J Bus Soc Sci. 2011; 2 (14):222–228. [ Google Scholar ]
- Drew JM. A study of cybercrime victimisation and prevention: exploring the use of online crime prevention behaviours and strategies. J Criminol Res Policy Pract. 2020; 6 (1):17–33. doi: 10.1108/JCRPP-12-2019-0070. [ CrossRef ] [ Google Scholar ]
- E Fonseca B, Sampaio, de Araújo Fonseca MV, Zicker F (2016). Co-authorship network analysis in health research: method and potential use. Health Res Policy Syst 14(1):1–10. 10.1186/s12961-016-0104-5 [ PMC free article ] [ PubMed ]
- Feeley TH. A bibliometric analysis of communication journals from 2002 to 2005. Hum Commun Res. 2008; 34 :505–520. doi: 10.1111/j.1468-2958.2008.00330.x. [ CrossRef ] [ Google Scholar ]
- Gan C, Wang W. A bibliometric analysis of social media research from the perspective of library and information science. IFIP Adv Inf Commun Technol. 2014; 445 :23–32. doi: 10.1007/978-3-662-45526-5_3. [ CrossRef ] [ Google Scholar ]
- Glänzel W, Schubert A. Analysing scientific networks through co-authorship. Handb Quant Sci Technol Res. 2006 doi: 10.1007/1-4020-2755-9_12. [ CrossRef ] [ Google Scholar ]
- Gogolin G. The digital crime tsunami. Digit Investig. 2010; 7 (1–2):3–8. doi: 10.1016/j.diin.2010.07.001. [ CrossRef ] [ Google Scholar ]
- Holt TJ, Bossler AM. Examining the applicability of lifestyle-routine activities theory for cybercrime victimization. Deviant Behav. 2009; 30 (1):1–25. doi: 10.1080/01639620701876577. [ CrossRef ] [ Google Scholar ]
- Holt TJ, Bossler AM. An assessment of the current state of cybercrime scholarship. Deviant Behav. 2014; 35 (1):20–40. doi: 10.1080/01639625.2013.822209. [ CrossRef ] [ Google Scholar ]
- Ilievski A. An explanation of the cybercrime victimisation: self-control and lifestile/routine activity theory. Innov Issues Approaches Soc Sci. 2016; 9 (1):30–47. doi: 10.12959/issn.1855-0541.iiass-2016-no1-art02. [ CrossRef ] [ Google Scholar ]
- Insa F. The Admissibility of Electronic Evidence in Court (A.E.E.C.): Fighting against high-tech crime—results of a European study. J Digital Forensic Pract. 2007; 1 (4):285–289. doi: 10.1080/15567280701418049. [ CrossRef ] [ Google Scholar ]
- Jahankhani H. Developing a model to reduce and/or prevent cybercrime victimization among the user individuals. Strategic Intell Manag. 2013 doi: 10.1016/b978-0-12-407191-9.00021-1. [ CrossRef ] [ Google Scholar ]
- Jamshed J, Naeem S, Ahmad K (2020) Analysis of Criminal Law Literature: a bibliometric study from 2010–2019. Library Philos Pract
- Kim J, Kang S, Lee KH (2019) Evolution of digital marketing communication: Bibliometric analysis and networs visualization from key articles. J Bus Res
- Kirwan GH, Fullwood C, Rooney B. Risk factors for social networking site scam victimization among Malaysian students. Cyberpsychol Behav Soc Netw. 2018; 21 (2):123–128. doi: 10.1089/cyber.2016.0714. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Lee S-S, Choi KS, Choi S, Englander E. A test of structural model for fear of crime in social networking sites A test of structural model for fear of crime in social networking sites. Int J Cybersecur Intell Cybercrime. 2019; 2 (2):5–22. doi: 10.52306/02020219SVZL9707. [ CrossRef ] [ Google Scholar ]
- Leukfeldt R, Holt T, editors. The human factor of cybercrime. New York: Routledge; 2020. [ Google Scholar ]
- Leukfeldt ER, Yar M. Applying routine activity theory to cybercrime: a theoretical and empirical analysis. Deviant Behav. 2016; 37 (3):263–280. doi: 10.1080/01639625.2015.1012409. [ CrossRef ] [ Google Scholar ]
- Leung XY, Sun J, Bai B. Bibliometrics of social media research: a co-citation and co-word analysis. Int J Hosp Manag. 2017; 66 :35–45. doi: 10.1016/j.ijhm.2017.06.012. [ CrossRef ] [ Google Scholar ]
- Li Q, Wei W, Xiong N, Feng D, Ye X, Jiang Y. Social media research, human behavior, and sustainable society. Sustainability. 2017; 9 (3):384. doi: 10.3390/su9030384. [ CrossRef ] [ Google Scholar ]
- Lin T, Capecci DE, Ellis DM, Rocha HA, Dommaraju S, Oliveira DS, Ebner NC. Susceptibility to spear-phishing emails: effects of internet user demographics and email content. ACM Trans Comput-Hum Interact. 2019; 26 (5):1–28. doi: 10.1145/3336141. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Luong TH. Prevent and combat sexual assault and exploitation of children on cyberspace in Vietnam: situations, challenges, and responses. In: Elshenraki H, editor. Combating the exploitation of children in cyberspace: emerging research and opportunities. Hershey: IGI Global; 2021. pp. 68–94. [ Google Scholar ]
- Luong HT, Phan HD, Van Chu D, Nguyen VQ, Le KT, Hoang LT. Understanding cybercrimes in Vietnam: from leading-point provisions to legislative system and law enforcement. Int J Cyber Criminol. 2019; 13 (2):290–308. doi: 10.5281/zenodo.3700724. [ CrossRef ] [ Google Scholar ]
- Lusthaus J (2020a) Cybercrime in Southeast Asia: Combating a Global Threat Locally. Retrieved from Canberra, Australia: https://s3-ap-southeast-2.amazonaws.com/ad-aspi/202005/Cybercrime%20in%20Southeast%20Asia.pdf?naTsKQp2jtSPYsWpSo4YmE1sVBNv_exJ
- Lusthaus J. Modelling cybercrime development: the case of Vietnam. In: Leukfeldt R, Holt T, editors. The human factor of cybercrime. New York: Routledge; 2020. pp. 240–257. [ Google Scholar ]
- Marsh I, Melville G. Crime justice and the media. Crime Justice Med. 2008 doi: 10.4324/9780203894781. [ CrossRef ] [ Google Scholar ]
- Martí-Parreño J, Méndez-Ibáñezt E, Alonso-Arroyo A (2016) The use of gamification in education: a bibliometric and text mining analysis. J Comput Assist Learn
- McLuhan M. The Global Village: Transformations in World Life and Media in the 21st Century (Communication and Society) Oxford: Oxford University Press; 1992. [ Google Scholar ]
- Näsi M, Oksanen A, Keipi T, Räsänen P. Cybercrime victimization among young people: a multi-nation study. J Scand Stud Criminol Crime Prev. 2015 doi: 10.1080/14043858.2015.1046640. [ CrossRef ] [ Google Scholar ]
- Ngo F, Jaishankar K. Commemorating a decade in existence of the international journal of cyber criminology: a research agenda to advance the scholarship on cyber crime. Int J Cyber Criminol. 2017; 11 (1):1–9. [ Google Scholar ]
- Ngo F, Paternoster R. Cybercrime victimization: an examination of individual and situational level factors. Int J Cyber Criminol. 2011; 5 (1):773. [ Google Scholar ]
- Nguyen VT, Luong TH. The structure of cybercrime networks: transnational computer fraud in Vietnam. J Crime Justice. 2020 doi: 10.1080/0735648X.2020.1818605. [ CrossRef ] [ Google Scholar ]
- Oksanen A, Keipi T. Young people as victims of crime on the internet: a population-based study in Finland. Vulnerable Child Youth Stud. 2013; 8 (4):298–309. doi: 10.1080/17450128.2012.752119. [ CrossRef ] [ Google Scholar ]
- Oliveira D, Rocha H, Yang H, Ellis D, Dommaraju S, Muradoglu M, Weir D, Soliman A, Lin T, Ebner N (2017) Dissecting spear phishing emails for older vs young adults: on the interplay of weapons of influence and life domains in predicting susceptibility to phishing. In: Conference on Human Factors in Computing Systems—Proceedings, 2017-May, 6412–6424. 10.1145/3025453.3025831
- Orchard LJ, Fullwood C, Galbraith N, Morris N. Individual differences as predictors of social networking. J Comput-Mediat Commun. 2014; 19 (3):388–402. doi: 10.1111/jcc4.12068. [ CrossRef ] [ Google Scholar ]
- Parrish JL, Jr, Bailey JL, Courtney JF. A personality based model for determining susceptibility to phishing attacks. Little Rock: University of Arkansas; 2009. pp. 285–296. [ Google Scholar ]
- Pasadeos Y. A bibliometric study of advertising citations. J Advert. 1985; 14 (4):52–59. doi: 10.1080/00913367.1985.10672971. [ CrossRef ] [ Google Scholar ]
- Pickering C, Byrne J. The benefits of publishing systematic quantitative literature reviews for PhD candidates and other early-career researchers. Higher Educ Res Devel ISSN. 2014; 33 (3):534–548. doi: 10.1080/07294360.2013.841651. [ CrossRef ] [ Google Scholar ]
- Reyns BW, Fisher BS, Bossler AM, Holt TJ. Opportunity and Self-control: do they predict multiple forms of online victimization? Am J Crim Justice. 2019; 44 (1):63–82. doi: 10.1007/s12103-018-9447-5. [ CrossRef ] [ Google Scholar ]
- Romero L, Portillo-Salido E. Trends in sigma-1 receptor research: a 25-year bibliometric analysis. Front Pharmacol. 2019 doi: 10.3389/fphar.2019.00564. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Saad ME, Huda Sheikh Abdullah SN, Murah MZ. Cyber romance scam victimization analysis using Routine Activity Theory versus apriori algorithm. Int J Adv Comput Sci Appl. 2018; 9 (12):479–485. doi: 10.14569/IJACSA.2018.091267. [ CrossRef ] [ Google Scholar ]
- Saridakis G, Benson V, Ezingeard JN, Tennakoon H. Individual information security, user behaviour and cyber victimisation: an empirical study of social networking users. Technol Forecast Soc Change. 2016; 102 :320–330. doi: 10.1016/j.techfore.2015.08.012. [ CrossRef ] [ Google Scholar ]
- Seng S, Wright M, Al-Ameen MN (2018) Understanding users’ decision of clicking on posts in facebook with implications for phishing. Workshop on Technology and Consumer Protection (ConPro 18), May, 1–6
- Serafin MJ, Garcia-Vargas GR, García-Chivita MDP, Caicedo MI, Correra JC. Cyberbehavior: a bibliometric analysis. Annu Rev Cyber Ther Telemed. 2019; 17 :17–24. doi: 10.31234/osf.io/prfcw. [ CrossRef ] [ Google Scholar ]
- Skinner WF, Fream AM. A social learning theory analysis of computer crime among college students. J Res Crime Delinq. 1997; 34 (4):495–518. doi: 10.1177/0022427897034004005. [ CrossRef ] [ Google Scholar ]
- Tsai H, Yi S, Shillair R, Cotten SR, Winstead V, Yost E. Getting grandma online: are tablets the answer for increasing digital inclusion for older adults in the US? Educ Gerontol. 2015; 41 (10):695–709. doi: 10.1080/03601277.2015.1048165. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- van Eck NJ, Waltman L (2020) Manual for VOSviewer version 1.6.16
- Van Wilsem J. “Bought it, but never got it” assessing risk factors for online consumer fraud victimization. Eur Sociol Rev. 2013; 29 (2):168–178. doi: 10.1093/esr/jcr053. [ CrossRef ] [ Google Scholar ]
- van der Wagen W, Pieters W. The hybrid victim: re-conceptualizing high-tech cyber victimization through actor-network theory. Eur J Criminol. 2020; 17 (4):480–497. doi: 10.1177/1477370818812016. [ CrossRef ] [ Google Scholar ]
- Vishwanath A. Habitual Facebook use and its impact on getting deceived on social media. J Comput-Mediat Commun. 2015; 20 (1):83–98. doi: 10.1111/jcc4.12100. [ CrossRef ] [ Google Scholar ]
- Wall D. Crime and the Internet: Cybercrime and cyberfears. 1. London: Routledge; 2001. [ Google Scholar ]
- Wall D. What are cybercrimes? Crim Justice Matters. 2004; 58 (1):20–21. doi: 10.1080/09627250408553239. [ CrossRef ] [ Google Scholar ]
- Whitty MT, Buchanan T. The online romance scam: a serious cybercrime. Cyberpsychol Behav Soc Netw. 2012; 15 (3):181–183. doi: 10.1089/cyber.2011.0352. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- You GR, Sun X, Sun M, Wang JM, Chen YW (2014) Bibliometric and social network analysis of the SoS field. In: Proceedings of the 9th International Conference on System of Systems Engineering: The Socio-Technical Perspective, SoSE 2014, 13–18. 10.1109/SYSOSE.2014.6892456
- Zyoud SH, Sweileh WM, Awang R, Al-Jabi SW. Global trends in research related to social media in psychology: Mapping and bibliometric analysis. Int J Ment Health Syst. 2018; 12 (1):1–8. doi: 10.1186/s13033-018-0182-6. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
Cybercrime as the Top IT Threat Essay
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment
Introduction
Reference list.
Cybercrime refers to a crime of any kind that involves the combination of a network and a computer. Cyber-criminals use the computer to commit electronic crimes. The computer may also serve as a target for the criminals. Cybercrime is a threat to any organization as it avails private and confidential data to criminals. The criminals in turn use the data to destroy fundamental organizational structures such as databases, reputation and even steal assets such as money, electronically.
Ignoring or paying insignificant attention to cybercrime can be very costly. For instance, the attack on Sony Pictures by hackers in December 2014 demonstrates how devastating cybercrime can be to any company (Durbin, 2015).
Cybercrime is a collective term that encompasses a host of electronic crimes such as email spoofing, hacking, data diddling, password sniffing, software piracy and denial of service. If the threat is not dealt with, every crime that constitutes a cybercrime could lead to a different form of damage to the organization that is unique and different from the others.
Cybercrime can be detected by an organization through the use of a myriad of intrusion detection techniques. For instance, operating system commands, tripwires, and anomaly detection techniques are some of the methods that could be used to detect cybercrime. The process of identifying cybercrime and taking appropriate action can be rigorous and expensive.
Each organization needs to have in place an IT department with qualified security personnel to determine and act appropriately on the threat whenever need arises. The target organization may also consider hiring the services of an independent computer forensics investigator who will provide insights as to the prevention and detection of future e-crimes.
Cybercrime is one of the top current IT threats, and every organization must establish the necessary up to date counter mechanisms for security purposes.
Durbin, S. (2014). View: The top five IT threats of 2015 – FT. The Financial Times. Web.
- Cybercrime: Gary McKinnon's Hacking Event
- Cyber-Crime - New Ways to Steal Identity and Money
- Concept of Hyperventilation Anomaly in Medicine
- Miranda vs. Arizona Case - Criminal Law
- Banning the Possession of Guns
- Sexual Harassment in Workplace
- Prison in the USA: Solutions to Reducing Overpopulation
- Brian Terry's Death: Difficulties of Investigation
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2020, May 2). Cybercrime as the Top IT Threat. https://ivypanda.com/essays/cybercrime-as-the-top-it-threat/
"Cybercrime as the Top IT Threat." IvyPanda , 2 May 2020, ivypanda.com/essays/cybercrime-as-the-top-it-threat/.
IvyPanda . (2020) 'Cybercrime as the Top IT Threat'. 2 May.
IvyPanda . 2020. "Cybercrime as the Top IT Threat." May 2, 2020. https://ivypanda.com/essays/cybercrime-as-the-top-it-threat/.
1. IvyPanda . "Cybercrime as the Top IT Threat." May 2, 2020. https://ivypanda.com/essays/cybercrime-as-the-top-it-threat/.
Bibliography
IvyPanda . "Cybercrime as the Top IT Threat." May 2, 2020. https://ivypanda.com/essays/cybercrime-as-the-top-it-threat/.
The Main Aspects of the Impact of Cybercrimes on the Business Environment in the Digital Era: Literature Review
- First Online: 27 August 2023
Cite this chapter

- Sorinel Căpușneanu 2 ,
- Dan Ioan Topor 3 ,
- Ileana-Sorina Rakoș 4 ,
- Cristina-Otilia Țenovici 5 &
- Mihaela Ștefan Hint 3
Part of the book series: Contributions to Finance and Accounting ((CFA))
297 Accesses
The aim of this research is to identify the main aspects of the impact of cybercrime on the business environment through quantitative research and comparative analysis by reviewing international literature. The applied research methodology also consisted of processing and analysing information gathered from the literature of international regulatory bodies, which formed the basis for syntheses and extracts of judgements and findings. The results obtained revealed a significant increase in cybercrime over the last decade, which is why several measures to combat cybercrime in business were proposed and discussed. The chapter concludes with the authors’ conclusions, the limitations of this study and future research directions proposed by them.
The importance of this chapter is aimed at both academic and business specialists, as well as at all readers interested in learning more about the subject.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Durable hardcover edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Similar content being viewed by others

A Systematic Literature Review on the Impact of Cybersecurity Threats on Corporate Governance During the Covid-19 Era

Historical Evolutions of Cybercrime: From Computer Crime to Cybercrime

Akdemir, N., Sungur, B., & Bașaranel, B. U. (2020). Examining the challenges of policing economic cybercrime in the UK. Güvenlik Bilimleri Derg. (Int. Secur. Congr. Spec. Issue), Özel Sayı, (pp. 113–134).
Google Scholar
Akhtar, N., & Perwej, Y. (2020). The internet of nano things (IoNT) existing state and future prospects, for published in the GSC. Advanced Research and Reviews, 5 (2), 131–150.
Article Google Scholar
Alecu, I., Ciuchi, C., Cîmpeanu, T., Coman, I., Găbudeanu, Larisa, Mihai, I.-C., Moghior, C., Munteanu, N., Petrică, G., Stoica, I., & Zețu C. (2021). Ghid de securitate cibernetică, Retrieved from: https://www.cyberlearning.ro/documents/Ghid-securitate-cibernetica.pdf .
Appiah, K. A. (2021). The prophet of maximum productivity. New York Review of Books, 14 , 51–54.
Black, A., Lumsden, K., & Hadlington, L. (2019). Why don’t you block them? Police officers’ constructions of the ideal victim when responding to reports of interpersonal cybercrime. In K. Lumsden & E. Harmer (Eds.), Online othering: Exploring violence and discrimination on the Web (pp. 355–378). Palgrave Macmillan.
Chapter Google Scholar
Broadhead, S. (2018). The contemporary cybercrime ecosystem: A multi-disciplinary overview of the state of affairs and developments. Computer Law and Security Review, 34 , 1180–1196.
Camic, C. (2020). Veblen: The making of an economist who unmade economics . Harvard University Press.
Book Google Scholar
Chen, P., Desmet, L., & Huygens, C. (2014). A study on advanced persistent threats. In IFIP international conference on communications and multimedia security (pp. 63–72). Springer.
Christensen, J. (2015). On her majesty’s secrecy service. In D. Whyte (Ed.), How corrupt is Britain? Pluto.
Clark, R., Reed, J., & Sunderland, T. (2018). Bridging funding gaps: Pitfalls, progress and potential private finance. Land Use Policy, 71 , 335–346.
Collin, B. (1996). The future of cyber terrorism, proceedings of 11th annual international symposium on criminal justice issues . The University of Illinois at Chicago.
Council of Europe. (2001). Convention on Cybercrime; European Treaty Series No. 185 (pp. 1–25); Council of Europe: Budapest, Hungary. Available online: https://rm.coe.int/1680081561 (Accessed on 16 October 2022).
Commission of the European Communities. (2007). Communication from the Commission to the European Parliament, the Council and the Committee of the Regions: Towards a general policy on the fight against cyber crime (vol 267); Commission of the European Communities: Brussels, Belgium.
Check Point Software Technologies Ltd. (CPST). (2021). Cele mai mari provocări de securitate în cloud din 2021. Retrieved from: https://www.checkpoint.com/cyber-hub/cloud-security/what-is-cloud-native-security/the-biggest-cloud -provocări-securitate-în-2021/ .
Krazytech. (2022). Accessed on September 22, 2022. Retrieved from https://krazytech.com/technical-papers/cyber-crime
Dewar, R. (2014). The triptych of cyber security: A classification of active cyber defense’. 6th international conference on cyber security (pp. 7–21), NATO CCD COE Publications, Tallinn.
Donalds, C., & Osei-Bryson, K. M. (2019). Toward a cybercrime classification ontology: A knowledge-based approach. Computers in Human Behavior, 92 , 403–418.
Dunn-Cavelty, M. (2010). Cyber security. In A. Collins (Ed.), Contemporary security studies . OUP.
European Commission. (2013). Joint communication to the European Parliament, the Council, the European Economic and Social Committee and the Committee of the Regions. Cybersecurity strategy of the European Union: An open, safe and secure cyberspace; European Commission: Brussels, Belgium.
Faysel, M. A., & Haque, S. S. (2010). Towards cyber defense: Research in intrusion detection and intrusion prevention systems. IJCSNS International Journal of Computer Science and Network Security, 10 (7), 316–325.
Garfinkel, S. L. (2010). Digital forensics research: The next 10 years. Digital Investigation, 7 (supplement), S64–S73.
Global Witness. (2021). The true price of palm oil: How global finance funds deforestation, violence and human rights abuses in Papua New Guinea, www.globalwitness.org/en/campa igns/fores ts/true-price- palm-oil/
Gordon, S., & Ford, R. (2006). On the definition and classification of cybercrime. Journal in Computer Virology, 2 , 13–20.
Guo, H., Jin, B., & Huang, D. (2010). Research and review on computer forensics, forensics in telecommunications, information, and multimedia, international conference on forensics in telecommunications, information, and multimedia (pp. 224–233).
Halder, D., & Jaishankar, K. (2011). Cyber crime and the victimization of women: Laws, rights and regulations . IGI-Global.
Hatole, P. P., & Bawiskar, D. S. K. (2017). Literature review of email forensics. Imperial Journal of Interdisciplinary Research, 3 (4).
Iqbal, J., & Beigh, B. M. (2017). Cybercrime in India: Trends and challenges. International Journal of Innovations & Advancement in Computer Science, 6 (12), 187–196.
Jensen, M., Schwenk, J., Gruschka, N., & Iacono, L. L. (2009). On technical security issues in cloud, IEEE 2009 international conference on cloud computing (pp. 109–116), IEEE, 21–25 September 2009.
Jin, X., Sun, W., Liang, Y., Guo, J., & Xie, Z. (2011). Design and implementation of intranet safety monitoring platform for power secondary system. Automation of Electric Power Systems, 35 (16), 99–104.
Kamruzzaman, M., Ashraful Islam, M., Shahidul Islam, M., Shakhawat Hossain, M., & Abdul Hakim, M. (2016). Plight of youth perception on cyber crime in South Asia. American Journal of Information Science and Computer Engineering, 2 (4), 22–28.
Kaur, M., Kaur, N., & Khurana, S. (2016). A literature review on cyber forensic and its analysis tools. International Journal of Advanced Research in Computer and Communication Engineering, 5 (1), 23–28.
Kowtha, S., Nolan, L. A., & Daley, R. A. (2012). Cyber security operations center characterization model and analysis, IEEE conference on technologies for Homeland security (HST) (pp. 470–475).
Krishna Viraja, V., & Purandare, P. (2021). A qualitative research on the impact and challenges of cybercrimes. Journal of Physics: Conference Series, 1964 , 042004.
Krombholz, K., Hobel, H., Huber, M., & Weippl, E. (2015). Advanced social engineering attacks. Journal of Information Security and applications, 22 , 113–122.
Krugman, P. (2020). Arguing with zombies . W.W. Norton & Company.
Kumar Goutam, R., & Kumar Verma, D. (2015). Top five cyber frauds. International Journal of Computer Applications, 119 (7), 23–25.
Le Compte, A., Elizondo, D., & Watson, T. (2015). A renewed approach to serious games for cyber security, 7th international conference on cyber conflict: Architectures in cyberspace, IEEE (pp. 203–216), 26–29 May 2015.
Leukfeldt, E. R., Kleemans, E. R., Kruisbergen, E. W., & Roks, R. A. (2019). Criminal networks in a digitized world: On the nexus of borderless opportunities and local embeddedness. Trends in Organized Crime, 22 (3), 324–345.
Mativat, F., & Tremblay, P. (1997). Counterfeiting credit cards. British Journal of Criminology, 37 (2), 165–183.
McAfee. (2017). Economic Impact of Cybercrime-No Slowing Down. Retrieved from: https://www.mcafee.com/enterprise/en-us/assets/executive-summaries/es-economic-impact-cybercrime.pdf .
McGuire, M. (2020). It ain’t what it is, it’s the way that they do it? Why we still don’t understand cybercrime. In R. Leukfeldt & T. J. Holt (Eds.), The human factor of cybercrime (pp. 3–28). Routledge.
Mirkovic, J., Dietrich, S., Dittrich, D., & Reiher, P. (2004). Internet denial of service attack and defense mechanisms. Pearson education: The Radia Pertman series in computer networking and security. Retrieved from https://books.google.com/books?isbn=0132704544 .
Mostafa, A. A. N. (2022). Cyber crime in business: Review paper. International Journal of Academic Research in Business and Social Sciences., 12 (6), 962–972.
Mshana, J. A. (2015). Cybercrime: An empirical study of its impact in the society—a case study of Tanzania, Huria. Journal of the Open University of Tanzania, 19 (1), 72–87.
Nesvetailova, A., & Palan, R. (2013). Sabotage in the financial system: Lessons from Veblen. Business Horizons, 56 , 723–732.
OECD (Organization for Economic Cooperation and Development). (2021). The momentum around sustainable finance taxonomies, OECD. https://www.oecd-ilibrary.org/sites/235eb800-en/index.html?itemId=/content/component/235eb800-en .
Ong, Y. J., Qiao, M., Routray, R., & Raphael, R. (2017). Context-aware data loss prevention for cloud storage services, 2017 IEEE 10th international conference on CLOUD computing (CLOUD), IEEE, 25–30 June 2017.
Paoli, L., Visschers, J., Verstraete, C., & Van Hellemont, E. (2018). The impact of cybercrime on Belgian businesses . Cambridge.
Parwej, F., Akhtar, N., & Perwej, Y. (2019). An empirical analysis of web of things (WoT). International Journal of Advanced Research in Computer Science, 10 (3), 32–40.
Pasqualetti, F., Dorfler, F., & Bullo, F. (2013). Attack detection and identification in cyber-physical systems. IEEE Transactions on Automatic Control, 58 (11), 2715–2729.
Pathak, P. B. (2016). Cybercrime: A global threat to cybercommunity. Ijcset.Com, 7 (3), 46–49.
Pawar, S. C., Mente, R. S., & Chendage, B. D. (2021). Cyber crime, cyber space and effects of cyber crime. International Journal of Scientific Research in Computer Science, Engineering and Information Technology, 7 (1), 210–214.
Perwej, Y. (2018a). The ambient scrutinize of scheduling algorithms in big data territory. International Journal of Advanced Research, 6 (3), 241–258.
Perwej, Y. (2018b). A pervasive review of Blockchain technology and its potential applications. Open Science Journal of Electrical and Electronic Engineering, New York, USA, 5 (4), 30–43.
Perwej, Y., Hannan, S. A., Parwej, F., & Nikhat Akhtar, N. (2014). A posteriori perusal of mobile computing. International Journal of Computer Applications Technology and Research, 3 (9), 569–578.
Perwej, Y., Kerim, B., Adrees, M. S., & Sheta, O. E. (2017). An empirical exploration of the yarn in big data. International Journal of Applied Information Systems, Foundation of Computer Science FCS, New York, USA, 12 (9), 19–29.
Perwej, Y., Nikhat Akhtar, N., & Parwej, F. (2018). A technological perspective of Blockchain security. International Journal of Recent Scientific Research, 9 (11A), 29472–29493.
Perwej, Y., Haq, K., Parwej, F., & Mohamed Hassan, M. M. (2019a). The internet of things (IoT) and its application domains. International Journal of Computer Applications (IJCA) USA, 182 (49), 36–49.
Perwej, A., Haq, K., & Perwej, Y. (2019b). Blockchain and its influence on market. International Journal of Computer Science Trends and Technology, 7 (5), 82–91.
Phillips, K., Davidson, J. C., Farr, R. R., Burkhardt, C., Caneppele, S., & Aiken, M. P. (2022). Conceptualizing cybercrime: Definitions, typologies and taxonomies. Forensic Sciences, 2 (2), 379–398.
Ponemon Institute. (2012). The impact of cybercrime on business. Studies of IT practitioners in the United States, United Kingdom, Germany, Hong Kong and Brazil. Retrieved October 16, 2022 from https://www.ponemon.org/local/.../Impact_of_Cybercrime_on_Business_FINAL.pdf
Ruggiero, V. (2017a). Dirty money . Oxford University Press.
Ruggiero, V. (2017b). Networks of greed. Justice, Power and Resistance, 1 , 3–23.
Ruggiero, V. (2020). Killing environmental campaigners. Criminological Encounters, 3 (1), 92–105.
Ruggiero, V. (2022). Sustainability and financial crime. International Criminology, 2 , 143–151.
Sarre, R., Lau, L. Y. C., & Chang, L. Y. (2018). Responding to cybercrime: Current trends. Police Practice and Research, 19 , 515–518.
Sachdeva, S., Raina, B. L., & Sharma, A. (2020). Analysis of digital forensic tools. Journal of Computational and Theoretical Nanoscience, 17 (6), 2459–2467.
Schiller, C., & Binkley, J. R. (2007). Botnets: The killer web applications (1st ed.) Syngress.
Shui, Y. (2013). Distributed denial of service attack and defense. Chapter 1, (pp. 1–5). Springer brief in computer science. Springer.com : Google Books online. Retrieved from October 24, 2022, https://books.google.com.tr/books?isbn=1461494915 .
Simou, S., Kalloniatis, C., Kavakli, E., & Gritzalis, S. (2014). Cloud forensics solutions: A review. Advanced Information Systems Engineering Workshops , 299–309.
Stallings, W. (2014). Cryptography and network security: Principles and practice, International Edition: Principles and Practice. Pearson Higher Ed.
Tan, Z., Jamdagni, A., He, X., Nanda, P., & Liu, R. P. (2014). A system for denial-of-service attack detection based on multivariate correlation analysis. IEEE Transactions on Parallel and Distributed Systems, 25 (2), 447–456.
Teelink, S., & Erbacher, R. (2006). Improving the computer forensic analysis process through visualization. Communications of the ACM, 49 (2), 71–75.
Tsakalidis, G., & Vergidis, K. (2017). A systematic approach toward description and classification of cybercrime incidents. IEEE Transactions on Systems, Man, and Cybernetics Systems, 49 , 710–729.
UN. (2017). Work of the statistical commission pertaining to the 2030 agenda for sustainable development, Resolution Adopted by the General Assembly on 6 July, UN.
United Kingdom National Cyber Security Centre (UKNCSC). (2017). Cyber crime: Understanding the online business model, Report. https://www.ncsc.gov.uk/content/files/protected_files/news_files/Cyber% 20crime%20-%20understabnding%20the%20online%20business%20model.pdf
Viano, E. C. (2017). Cybercrime: Definition, typology, and criminalization. In E. C. Viano (Ed.), Cybercrime, organized crime, and societal responses (pp. 3–22). Springer.
Yar, M., & Steinmetz, K. F. (2019). Cybercrime and society (3rd ed.). SAGE Publications Ltd..
Yasin, I., Ahmad, N., & Chaudhary, M. A. (2021). The impact of financial development, political institutions and urbanization on environmental degradation. Environment, Development and Sustainability, 23 , 6698–6721.
Zadek, S. (2018). Aligning the financial system with sustainable development. In N. Saab & A.-K. Sadik (Eds.), Financing sustainable development in Arab countries . Arab Forum for Environment and Development.
Download references
Author information
Authors and affiliations.
Faculty of Economic Sciences, Titu Maiorescu University, Bucharest, Romania
Sorinel Căpușneanu
Faculty of Economic Sciences, University of Alba-Iulia, Alba-Iulia, Romania
Dan Ioan Topor & Mihaela Ștefan Hint
Faculty of Sciences, University of Petroșani, Petroșani, Romania
Ileana-Sorina Rakoș
Faculty Marketing Management in Economic Affairs, Pitești, Romania
Cristina-Otilia Țenovici
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Dan Ioan Topor .
Editor information
Editors and affiliations.
Faculty of Economics and Business Administration, Babeș-Bolyai University, Cluj-Napoca, Romania
Monica Violeta Achim
Rights and permissions
Reprints and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Căpușneanu, S., Topor, D.I., Rakoș, IS., Țenovici, CO., Hint, M.Ș. (2023). The Main Aspects of the Impact of Cybercrimes on the Business Environment in the Digital Era: Literature Review. In: Achim, M.V. (eds) Economic and Financial Crime, Sustainability and Good Governance. Contributions to Finance and Accounting. Springer, Cham. https://doi.org/10.1007/978-3-031-34082-6_7
Download citation
DOI : https://doi.org/10.1007/978-3-031-34082-6_7
Published : 27 August 2023
Publisher Name : Springer, Cham
Print ISBN : 978-3-031-34081-9
Online ISBN : 978-3-031-34082-6
eBook Packages : Economics and Finance Economics and Finance (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

Internet Crime Complaint Center (IC3)

Protect one another.
The Internet Crime Complaint Center, or IC3, is the Nation’s central hub for reporting cyber crime. It is run by the FBI, the lead federal agency for investigating cyber crime. Here on our website, you can take two vital steps to protecting cyberspace and your own online security.
First, if you believe you have fallen victim to cyber crime, file a complaint or report. Your information is invaluable to helping the FBI and its partners bring cybercriminals to justice.
Second, get educated about the latest and most harmful cyber threats and scams. By doing so, you will be better able to protect yourself, your family, and your place of work.
Anyone can become a victim of internet crime. Take action for yourself and others by reporting it. Reporting internet crimes can help bring criminals to justice and make the internet a safer place for us all.
With your help, the FBI can respond faster, better defend cyber networks, and more effectively protect our nation.

Read about recent trends and announcements that may affect you.

Knowledge is the key to prevention. Educate yourself about threats to individuals and business and ways to protect yourself.
Between staying connected with family and friends, shopping and banking online, and working remotely, we all depend on security in our interconnected digital world. Criminals from every corner of the globe attack our digital systems on a near constant basis. They strike targets large and small—from corporate networks to personal smart phones. No one—and no device—is immune from the threat. The only way forward is together. In cyber security, where a single compromise can impact millions of people, there can be no weak links. Every organization and every individual needs to take smart, reasonable steps to protect their own devices and systems and to learn how to spot and avoid scams.
Combined with other data, it allows the FBI to investigate reported crimes, track trends and threats, and, in some cases, even freeze stolen funds. Just as importantly, IC3 shares reports of crime throughout its vast network of FBI field offices and law enforcement partners, strengthening our nation’s collective response both locally and nationally.
Due to the massive number of complaints we receive each year, IC3 cannot respond directly to every submission, but please know we take each report seriously. With your help, we can and will respond faster, defend cyber networks better, and more effectively protect our nation.
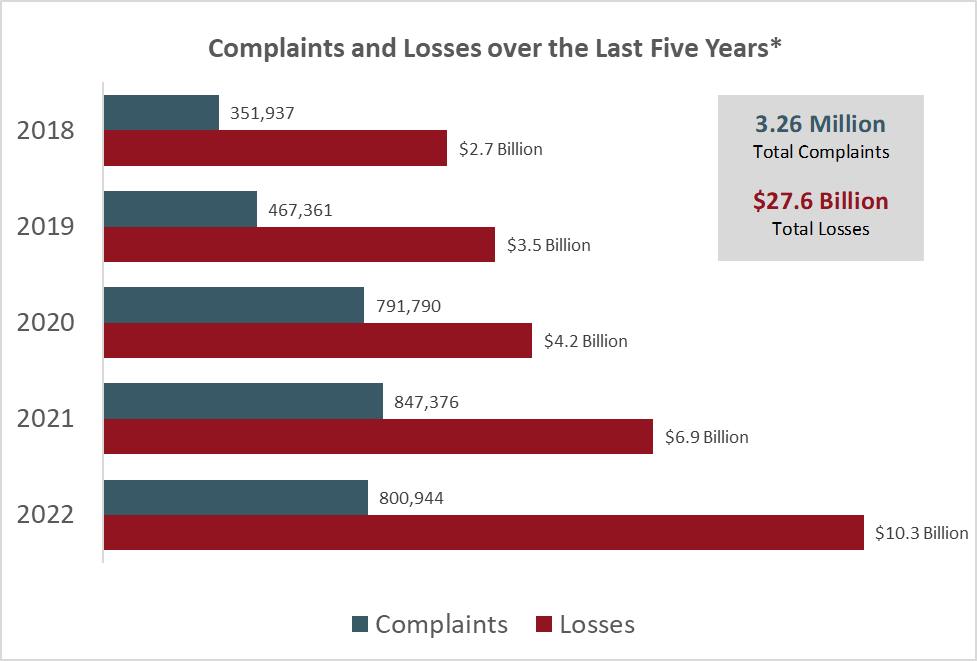
Chart includes yearly and aggregate data for complaints and losses over the years 2018 to 2022. Over that time, IC3 received a total of 3.26 million complaints, reporting a loss of $27.6 billion.
Tue, 25 Jun 2024
Mon, 24 Jun 2024
Tue, 04 Jun 2024
Wed, 29 May 2024
Thu, 16 May 2024
Tue, 18 Jun 2024
Tue, 14 May 2024
Sat, 11 May 2024
- COVID-19 Full Coverage
- Cover Stories
- Ulat Filipino
- Special Reports
- Personal Finance
- Other sports
- Pinoy Achievers
- Immigration Guide
- Science and Research
- Technology, Gadgets and Gaming
- Chika Minute
- Showbiz Abroad
- Family and Relationships
- Art and Culture
- Health and Wellness
- Shopping and Fashion
- Hobbies and Activities
- News Hardcore
- Walang Pasok
- Transportation
- Missing Persons
- Community Bulletin Board
- GMA Public Affairs
- State of the Nation
- Unang Balita
- Balitanghali
- News TV Live

Top 5 cybercrimes complaints in the Philippines, according to PNP
- The PNP ACG website: www.acg.pnp.gov.ph
- Text: 0998-568-9082
- The hotline: 414-1560 / 723-0401 loc 5313
- E-mail: [email protected]
24/7 writing help on your phone
To install StudyMoose App tap and then “Add to Home Screen”
The Cybercrime Law of the Philippines
Save to my list
Remove from my list

The Cybercrime Law of the Philippines. (2017, Feb 09). Retrieved from https://studymoose.com/the-cybercrime-law-of-the-philippines-essay
"The Cybercrime Law of the Philippines." StudyMoose , 9 Feb 2017, https://studymoose.com/the-cybercrime-law-of-the-philippines-essay
StudyMoose. (2017). The Cybercrime Law of the Philippines . [Online]. Available at: https://studymoose.com/the-cybercrime-law-of-the-philippines-essay [Accessed: 26 Jun. 2024]
"The Cybercrime Law of the Philippines." StudyMoose, Feb 09, 2017. Accessed June 26, 2024. https://studymoose.com/the-cybercrime-law-of-the-philippines-essay
"The Cybercrime Law of the Philippines," StudyMoose , 09-Feb-2017. [Online]. Available: https://studymoose.com/the-cybercrime-law-of-the-philippines-essay. [Accessed: 26-Jun-2024]
StudyMoose. (2017). The Cybercrime Law of the Philippines . [Online]. Available at: https://studymoose.com/the-cybercrime-law-of-the-philippines-essay [Accessed: 26-Jun-2024]
- Cybercrime - computer crime Pages: 7 (2051 words)
- The Cybercrime Prevention Act of 2012 Pages: 2 (588 words)
- Avoid Becoming a Victim of Cybercrime Pages: 5 (1308 words)
- The Rising Threat of Cybercrime: A Government Concern Pages: 2 (347 words)
- Effects Of Social Media On The Cybercrime and Cyberbullying Pages: 6 (1719 words)
- Canada's Methods of Protecting Against Identity Theft and Cybercrime Pages: 4 (922 words)
- How Social Media Has Contributed to Spread Of Cybercrime Pages: 7 (2070 words)
- Illegal Recruitment Law in the Philippines Pages: 11 (3110 words)
- Batas Militar - Martial Law in the Philippines Pages: 5 (1340 words)
- Moral Law Vs Natural Law In The Scarlet Letter Pages: 7 (1830 words)

👋 Hi! I’m your smart assistant Amy!
Don’t know where to start? Type your requirements and I’ll connect you to an academic expert within 3 minutes.

Essay on Cyberbullying
Students are often asked to write an essay on Cyberbullying in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Cyberbullying
What is cyberbullying.
Cyberbullying is when someone uses the internet, cell phones, or other devices to send or post text or images intended to hurt or embarrass another person. It can happen through a message, email, or on social media sites.
Forms of Cyberbullying
Cyberbullying can take many forms. It can be public or private. Some examples are mean text messages, rumors sent by email or posted on social networking sites, and embarrassing pictures or videos.
Effects of Cyberbullying
Cyberbullying can make a person feel sad, lonely, or scared. They may want to avoid school or social events. In severe cases, it might lead to depression or even suicide.
Preventing Cyberbullying
To prevent cyberbullying, don’t share private information online, and think before you post. Always treat others with respect. If you’re a victim, don’t respond or retaliate. Instead, save the evidence and report it.
Role of Schools and Parents
250 words essay on cyberbullying.
Cyberbullying is when someone uses the internet to hurt, embarrass, or scare another person. It can happen on social media, in online games, or in messages. The person doing the bullying might send mean messages, share personal information, or post embarrassing photos.
Cyberbullying can make a person feel sad, scared, or alone. They might not want to go to school or spend time with friends. It can also affect their grades and their health. Some people might even think about hurting themselves because of cyberbullying.
How to Deal with Cyberbullying
If you are being bullied online, tell a trusted adult. This could be a parent, teacher, or school counselor. You can also report the bullying to the website or app where it happened. Most websites and apps have rules against bullying and can take action.
To help stop cyberbullying, be kind online. Think before you post or send a message. Ask yourself, “Would I want someone to say this to me?” If the answer is no, don’t post it. Also, stand up for others. If you see someone being bullied online, report it.
Remember, everyone deserves to feel safe and respected, both in person and online. By understanding and taking action against cyberbullying, we can make the internet a better place for everyone.
500 Words Essay on Cyberbullying
How cyberbullying happens.
Cyberbullying can happen in many ways. It can take place through social media sites, chat rooms, text messages, and emails. Sometimes, it can be public, like a mean comment on a social media post. Other times, it can be private, like a threatening text message. Cyberbullies can even create fake accounts to harass someone without revealing their identity.
Cyberbullying can hurt people deeply. It can make them feel scared, sad, or angry. It can also make them feel alone, like no one understands what they’re going through. Some people may even feel unsafe or worry about their reputation. In severe cases, cyberbullying can lead to mental health problems like depression and anxiety, or even self-harm.
There are many ways to prevent cyberbullying. One of the most important is to be kind and respectful online. Remember, the words you type can have a big impact on others. It’s also important to keep personal information private and to think before you post. If you wouldn’t say something in person, don’t say it online.
What to Do If You’re Cyberbullied
Cyberbullying is a serious problem that can hurt people both emotionally and mentally. But by being respectful online, protecting our personal information, and knowing how to respond if we’re bullied, we can help stop cyberbullying. Remember, everyone deserves to feel safe and respected, both in person and online.
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply

- Subscribe Now
Online libel tops cybercrime cases in the Philippines for 2016
Already have Rappler+? Sign in to listen to groundbreaking journalism.
This is AI generated summarization, which may have errors. For context, always refer to the full article.

MANILA, Philippines – From 2013 to 2015, online scams consistently topped the list of most common cybercrimes reported to the Philippine National Police-Anti-Cybercrime Group (PNP-ACG).
But in 2016 – a year of heated political debates that also took place in cyberspace – online libel emerged as the top complaint of Filipino internet users, with 494 complaints recorded compared to 311 recorded in 2015. It comprised 26.49% of the 1,865 cybercrime complaints for 2016.
Meanwhile, online scam complaints came in at second place, with 444 complaints in 2016, up from the 334 complaints recorded in 2015.
Rounding up the top 5 complaints were identity theft, online threats, and violation of the anti-photo and video voyeurism act.
The number of complaints on online threats, online scams, and identity theft has also been increasing since 2013, based on data from the PNP-ACG.
From double-digit figures in 2013, the numbers have been steadily rising to 3-digit figures until last year.
Common modus
According to PNP-ACG Assistant Chief PSupt Jay Guillermo, online threats and libel complaints mostly make use of social media sites like Facebook and Twitter. But threats made using cellular phones, like the “gun for hire” modus operandi reported in recent months, also fall under their scope of investigation.
In this extortion scheme, a caller purports to be a hired assassin tapped to kill the victim and his family.
The alleged killer would then supposedly have a change of heart and would offer to call off the operation if the victim pays up.
To some victims, the caller sounds believable because he would often have personal information on the victim to back up his claims. But Guillermo pointed out that this information could be easily obtained online.
On social media, Guillermo said those who reported receiving online threats also tend to know the person harassing them, having been in a previous relationship or involved in some degree of affinity.
Difficulty in getting evidence
How long does it take to investigate cybercrime complaints? According to Guillermo, the process differs on a case-to-case basis, and can also be dependent on the evidence gathered by investigators.
This is why complaints involving money – such as in online scams – and those with photographic evidence – such as photo and video voyeurism – tend to be easier to solve because of the wealth of evidence that could be obtained.
Online threat complaints can take months, such as in the case of climate action advocate Renee Karunungan. In May last year, she filed 34 complaints against social media users who harassed her online because she wrote a post critical of then-presidential candidate Rodrigo Duterte.
Karunungan received hate messages on her Facebook account, with strangers wishing death on her and her loved ones, and some even threatening rape. (READ: ‘Sana ma-rape ka’: Netizens bully anti-Duterte voter )
Eight months since the cases were filed, however, Karunungan said the cases remain under investigation.
For online threats and online libel, Guillermo said evidence-gathering tends to be difficult without help from telecommunications companies and internet service providers (ISPs).
“In investigating online threats, we can’t get details from telcos. Especially if [the phones used are] prepaid, it’s very hard to get information,” Guillermo said.
ISPs too do not readily provide information without a court order. But to get a court order, police would first need evidence to back up their request.
“In terms of cooperation with telcos and ISPs, we don’t have a positive reply, they’re always asking for a court order. But the requirement for a court order is having evidence before filing a case,” Guillermo said.
What it takes
Despite this, Guillermo said cyber cops still have their own ways of investigating leads. In cases of child pornography, for instance, Guillermo said the PNP gets tips from foreign intelligence networks.
Securing digital evidence is also a challenge for the police, since it’s easy to delete incriminating posts and messages. While victims can provide screenshots of their conversations, Guillermo said investigators must do the evidence-gathering so that these would be admissible in court.

Clearing cases
Not all complaints lodged with the PNP-ACG result in an arrest, especially if they involve online threat or libel.
In these cases, Guillermo said victims usually file a complaint just to have a record of the case. The evidence gathered by investigators is then turned over to prosecutors, who take charge of the case.
At this level, getting results may take months, and some victims choose to withdraw especially if money is not involved in their complaints.
Of the 1,804 complaints recorded by the PNP-ACG between January to November 2016, only 4.66% – 84 cases – have reached the prosecutor’s office. 728 cases (40.35%) have been cleared or closed, while 928 cases (51.44%) remain under investigation.
Meanwhile, 40 police operations last year resulted in the arrest of 150 individuals, most of whom were involved in extortion, cybersex operations, and violation of the anti-photo and video voyeurism act. These operations resulted in the filing of 61 cases and the rescue of 6 minors.
With cybercrime cases on the rise, Guillermo advises the public to exercise caution online and to immediately report cases to the cybercrime units or to local police. (READ: How to protect your computer vs cyberattacks ) – Rappler.com
Add a comment
Please abide by Rappler's commenting guidelines .
There are no comments yet. Add your comment to start the conversation.
How does this make you feel?
Related Topics
Recommended stories, {{ item.sitename }}, {{ item.title }}.
Checking your Rappler+ subscription...
Upgrade to Rappler+ for exclusive content and unlimited access.
Why is it important to subscribe? Learn more
You are subscribed to Rappler+
Cyber Protection Applications of Quantum Computing: A Review
- Ahmed, Ummar
- Sipola, Tuomo
- Hautamäki, Jari
Quantum computing is a cutting-edge field of information technology that harnesses the principles of quantum mechanics to perform computations. It has major implications for the cyber security industry. Existing cyber protection applications are working well, but there are still challenges and vulnerabilities in computer networks. Sometimes data and privacy are also compromised. These complications lead to research questions asking what kind of cyber protection applications of quantum computing are there and what potential methods or techniques can be used for cyber protection? These questions will reveal how much power quantum computing has and to what extent it can outperform the conventional computing systems. This scoping review was conducted by considering 815 papers. It showed the possibilities that can be achievedif quantum technologies are implemented in cyber environments. This scoping review discusses various domains such as algorithms and applications, bioinformatics, cloud and edge computing, the organization of complex systems, application areas focused on security and threats, and the broader quantum computing ecosystem. In each of these areas, there is significant scope for quantum computing to be implemented and to revolutionize the working environment. Numerous quantum computing applications for cyber protection and a number of techniques to protect our data and privacy were identified. The results are not limited to network security but also include data security. This paper also discusses societal aspects, e.g., the applications of quantum computing in the social sciences. This scoping review discusses how to enhance the efficiency and security of quantum computing in various cyber security domains. Additionally, it encourages the reader to think about what kind of techniques and methods can be deployed to secure the cyber world.
- Computer Science - Cryptography and Security;
- Computer Science - Emerging Technologies

IMAGES
VIDEO
COMMENTS
500+ Words Essay on Cyber Crime. Cyber Crime Essay- Everybody thinks that only stealing someone's private data is Cyber Crime.But in defining terms we can say that 'Cyber Crime refers to the use of an electronic device (computer, laptop, etc.) for stealing someone's data or trying to harm them using a computer.
116 CyberCrime Topics & Essay Samples. Updated: Mar 2nd, 2024. 9 min. If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper. Table of Contents. These days, people are asking more and more questions about cybercrime. The most straightforward definition is ...
Essay on Cybercrime in 100 Words. Cybercrime involves illegal activities like hacking, ransomware, cyberbullying, online fraud, etc. People who are involved in cybercrime or any similar activities are called hackers, scammers or fraudsters. Cybercrime leads to financial loss for individuals who have fallen victim to one.
Cybercrime is a severe issue that threatens user security and safety. To help you with this subject, see our essays about cyber crime examples and prompts.. As its name suggests, cyber crime occurs in the digital space beyond our tangible keyboards, computer monitors, and phone screens.This criminal activity happens offline and online, and although many are affected, only 10% to 12% of the ...
Essay on Cyber Crime. Cyber crime is the most discussed issue of the 21st century. The technology sector world wide is witnessing a boom in the consumer of smartphones and the internet which is raising concerns with regard to the privacy and security of the users. Owing to this reason, it is highly essential for all the users to know about ...
Cyber Crime Essay: A crime that involves a network and a computer is known as computer-oriented crime or cybercrime. Such a crime affects the security of everything, might be a person, institution or even a nation. ... It has been recorded that in 2018 The Internet Crime Complaint Sector received 351,937 complaints alone. Sine, everything you ...
complaints, which was a 7% increase from 2020, with potential losses exceeding $6.9 billion. Among the 2021 complaints received, ransomware, business e-mail compromise (BEC) schemes, and the criminal use of ... THE IC3 ROLE IN COMBATING CYBER CRIME1 What we do Partner with Private Sector and with Local, State, Federal, and International Agencies
500 Words Essay on Cybercrime Complaints In The Philippines Introduction to Cybercrime. Cybercrime is a term we use for crimes that use computers and the internet. These crimes can include things like stealing personal information, spreading harmful content, or disrupting digital systems. The Philippines, like other countries, has seen a rise ...
Effects of Cyber Crime on Social Media. 2 pages / 933 words. The issue of cyber Crime has risen rapidly as a result of increased access to computers in the recent years compared to the past. Cyber Crime refers to criminal activities, which are carried out by the use of computers or the internet.
Cybercrime, or the use of computer technology or online networks to commit crimes, ranges from fraud and identity theft to threats and intimidation. Cybercrime and its many manifestations has clearly increased over the past 20 years. For example, cybercrime costs increased from approximately $3 trillion in 2015 to more than $6 trillion in 2021 ...
Introduction. Cyber crime evolved since 1990 when computers and networks came in to being. The types of attacks gradually grew from "Morris code worm" in 1997 to "Torjan" in 2004 and to "Ransom ware " attack in 2013. When computers and networks came into being in the 1990s, hacking was done basically to get more information about ...
It is widely accepted that cybercrime is highly prevalent and increasing. A recent report suggests that Internet Service Providers (ISPs) record around 80 billion automated scans daily by online perpetrators with the aim of identifying targets for cybercrime (Lewis, 2018), and in the year ending September 2019, 1 million 'computer misuse' crimes were reportedly committed against households ...
Get a custom Essay on Cybercrime and Law Enforcement Strategies. Thus, cybercrime - the use of computers and the Internet for unlawful acts - is a growing phenomenon that becomes more elaborate and more dangerous every minute (Aggarwal et al. 48). Cybercrime has many types because the Internet offers a variety of services to its users.
Types of cybercrime. Cybercrime ranges across a spectrum of activities. At one end are crimes that involve fundamental breaches of personal or corporate privacy, such as assaults on the integrity of information held in digital depositories and the use of illegally obtained digital information to harass, harm, or blackmail a firm or individual. These new cybercapabilities have caused intense ...
Introduction. To date, the debate of cybercrime definition has been controversial which is considered as one of the five areas of cyber criminology (Ngo and Jaishankar 2017; Drew 2020). 1 Several terms are used to illustrate 'cybercrime', such as 'high-tech crime' (Insa 2007), 'computer crime' (Choi 2008; Skinner and Fream 1997), 'digital crime' (Gogolin 2010), or 'virtual ...
Introduction. Cybercrime refers to a crime of any kind that involves the combination of a network and a computer. Cyber-criminals use the computer to commit electronic crimes. The computer may also serve as a target for the criminals. Cybercrime is a threat to any organization as it avails private and confidential data to criminals.
Importantly for readers of Police Practice and Research, Diarmaid Harkin, Chad Whelan and Lennon Chang in 'The challenges facing specialist police cyber-crime units: An empirical analysis' review the significant challenges facing police organisations by the growing threat of cybercrime. The next two papers discuss cybercrime victimization ...
Mostafa, A. A. N. (2022). Cyber crime in business: Review paper. International Journal of Academic Research in Business and Social Sciences., 12(6), 962-972. Article Google Scholar Mshana, J. A. (2015). Cybercrime: An empirical study of its impact in the society—a case study of Tanzania, Huria.
Cybercrime complaints in the Philippines - Free download as Word Doc (.doc / .docx), PDF File (.pdf), Text File (.txt) or read online for free. According to a press release from the Philippine National Police Anti-Cybercrime Group, they received 1,211 cybercrime complaints from 2013-2015. The top five complaints were online scams (366), online libel (240), online threats (129), identity theft ...
The Internet Crime Complaint Center, or IC3, is the Nation's central hub for reporting cyber crime. It is run by the FBI, the lead federal agency for investigating cyber crime. Here on our website, you can take two vital steps to protecting cyberspace and your own online security.
According to a press release from the Philippine National Police Anti-Cybercrime Group (PNP ACG), a total of 1,211 cybercrime complaints were filed with them from 2013-2015. The top five complaints received were online scams (366), online libel (240), online threats (129), identity theft (127), and photo and video voyeurism (89).
12981. The Cybercrime Law of the Philippines (also known as the Cybercrime Prevention Act of 2012 or Republic Act 10175) is a newly-signed act that gives us a true legal tool to combat cybercrime. A better definition is given by a press release from the Senate, a part of which says, "The Cybercrime Prevention Act lays down a comprehensive legal ...
Cyberbullying is when someone uses the internet, mobile phones, or other digital technologies to harm others. It is a type of bullying that happens online. Unlike regular bullying, cyberbullying can happen at any time and reach a person even when they are alone. It can include things like sending mean or threatening messages, spreading rumors ...
It comprised 26.49% of the 1,865 cybercrime complaints for 2016. Meanwhile, online scam complaints came in at second place, with 444 complaints in 2016, up from the 334 complaints recorded in 2015.
This scoping review was conducted by considering 815 papers. It showed the possibilities that can be achievedif quantum technologies are implemented in cyber environments. This scoping review discusses various domains such as algorithms and applications, bioinformatics, cloud and edge computing, the organization of complex systems, application ...