

Admissions open for online degrees from top Manipal universities
UGC-entitled

AICTE approved
Manipal Universities Prove It Again!

AMONGST ALL UNIVERSITIES
Also, No. 1 Ranked Private University in India
Also, No. 1 Ranked State Pvt. University in Rajasthan
Fast forward your career with in-demand specializations
A 70-year legacy of educational excellence, with 70K+ online learners from 60+ nationalities

Manipal Academy of Higher Education (MAHE)

Manipal University Jaipur (MUJ)

Sikkim Manipal University (SMU)
Explore our online degrees & certifications

Master of Business Administration

Master of Computer Applications (MCA)

Bachelor of Computer Applications

Bachelor of Arts

Bachelor of Business Administration

M.Sc. in Business Analytics

Master of Computer Applications

Bachelor of Commerce

M.Sc. in Data Science

Master of Arts in English

PGCP in Logistics and Supply Chain Management

PGCP in Business Analytics
Online manipal benefits.
Graduate with UGC-entitled & AICTE approved online degrees which are at par with on-campus degree programs.
Avail scholarship benefits under merit, defense, Divyaang, alumni, and other categories.
Become a part of a 1,50,000+ global Manipal alumni network.
Improved affordability with flexible financing and no-cost EMI options.
Boost your employability quotient by acquiring job-ready skills & preparing for interviews to perform well in placement drives.
Stay updated on key industry trends through our weekly webinars by industry experts.
Free access to 10K+ courses & professional certifications from top global universities.
Participate in exclusive in-person meetups at campus with your batchmates and faculty.

Note: The above offerings may differ based on university & program
Career support services
Our experienced team helps you choose the right career path that aligns with your goals, interests, and skills by providing you valuable guidance and support.

Alumni interactions during & after program
Interact and receive first-hand information & guidance from alumni during and after the program..

Career advisory & counselling by industry experts
Make informed decisions while choosing your career path by gaining valuable insights on various career opportunities from our expert career counsellors..

Industry-readiness sessions
Familiarize yourself with industry trends, organizational expectations, and recruiter behavior to develop relevant skills and become job ready..

Employability skill assessment & enhancement
Identify your strengths & weaknesses through skill assessments and build competencies to improve your employability quotient., student speak.

I always wanted to pursue my higher education dream without quitting my job, and MUJ has made it possible for me through their online degrees. My online MCA degree has given me wings to fly and chase my career aspirations.

With one year of work experience in a hospital, I wanted to hone my managerial skills. So, I decided to pursue an online MBA in Healthcare Management. Since I’m also preparing for UPSC, pursuing an online MBA is the perfect choice and Online Manipal is playing a key role in enhancing my knowledge.

I wanted to specialize in marketing, which is why I decided to start by pursuing an online BBA. As a working professional, an online degree was the best choice for me. The faculty at MUJ are experienced & guide us well and the student portal is user-friendly.

I have 2 years of work experience in IT as an Application Engineer. Through this program, I hope to expand my knowledge in business analytics and apply it to my current job role. Online Manipal has enabled me to learn at my convenience and the free access to Coursera content has helped me gain industry-relevant skills.

Having completed my master’s in business, I wanted to switch to the in-demand domain of business analytics, and I found MAHE’s certification program to be one of the best picks for me. The best part about this online certification program is that I can study at my own pace.

With 12 years of work experience in procurement and supply chain, I wanted to upskill in this domain. The curriculum of the online PGCP program by MAHE is industry-relevant and is helping me in applying my skills on the job. The e-tutorials are very helpful and cover in-depth topics.

I have been working as a lab technician in Manipal University Jaipur for 8 years, I have good technical skills like video recording and editing. However, I wanted to improve my knowledge, so I decided to pursue an online MA JMC. I want to pursue my PhD after this online program, and I also hope to become a news anchor one day.
Our stories

Empowerment Ki Shuruaat, Online Manipal Ke Saath | International Women's Day | Online Manipal

Hamari University; Apke Aur Apke Sapnon Ke Liye | #DrivingTheChange | Online Manipal

Brand Film | Online Manipal | #AzadiWaliDegree

Learner Testimonial: Devyani's Journey With Online BBA (MUJ)

Learner Testimonial: Akhil's Journey With Online MBA (MUJ)

Learner Testimonial: Romila's Journey With Online MA JMC (MUJ)
Read our blogs

How our UG learners leveraged online degrees for career growth

How our PG learners leveraged online degrees for career growth

Enhancing online learning with micro-credentials: Shaping the future of education

CAT 2024: Exam dates and expert tips to crack the MBA entrance

Interested in our courses? Share your details and we'll get back to you.
Master of Business Administration Bachelor of Business Administration Bachelor of Computer Applications Bachelor of Commerce Master of Computer Applications Master of Commerce Master of Arts in Journalism & Mass Communication MSc Data Science MSc Business Analytics PGCP Business Analytics PGCP Logistics and Supply Chain PGCP in Entrepreneurship and Innovation Bachelor of Arts MA in English MA in Sociology MA in Political Science
Manipal University Jaipur Manipal Academy of Higher Education Manipal Institute of Technology Sikkim Manipal University
I authorize Online Manipal and its associates to contact me with updates & notifications via email, SMS, WhatsApp, and voice call. This consent will override any registration for DNC / NDNC.
Enter the code sent to your phone number to proceed with the application form
COURSE SELECTED Edit
Bachelor of Business Administration (BBA) Manipal University Jaipur
Please leave this field empty. Submit

CCSP Scenario-Based Interview Questions

Landed that dream Cloud Security Specialist interview? Feeling a mix of excitement and nervousness? Take a deep breath, security champion! This blog post is your secret weapon.
We all know the cloud offers incredible agility and scalability, but robust security remains paramount. This post equips you with the knowledge to confidently answer critical interview questions and showcase your expertise in safeguarding sensitive data and applications in the cloud. We’ll dive into some specific questions that hiring Managers ask, transforming you into an interview powerhouse.
CCSP Scenario Based Interview Question
1. Our company is planning to migrate a critical application to the cloud. We are considering both IaaS and PaaS options. What factors would you consider when making this decision from a security perspective?
Here are the key factors to consider from a security perspective:
- Less control over security: While the cloud provider handles the underlying infrastructure, it is your responsibility to secure the operating system, applications, and data. This includes tasks like access control, patching, and data encryption.
- More responsibility for application security: You are solely responsible for securing your applications running on the IaaS platform.
- Leverage platform security features: The cloud provider offers native security features like Identity and Access Management (IAM) and data encryption. This can simplify security management.
- Shared responsibility model: Security responsibilities are divided between you and the cloud provider. It’s crucial to understand this model and what security aspects the provider handles.
Decision Factors:
- Security Expertise: If your team has strong security expertise and wants granular control, IaaS might be suitable. For those preferring to leverage built-in security features, PaaS can be a good choice.
- Application Security: Consider your existing application security capabilities. PaaS may ease the burden by handling some aspects of application security.
2. We are deploying a new cloud-based e-commerce platform. How would you design the architecture to ensure strong isolation between customer data and other workloads running in the cloud?
Here’s a detailed architecture design approach to achieve strong isolation:
- Network Segmentation: Utilize Virtual Private Clouds (VPCs) or dedicated environments to isolate customer data from other workloads. This creates a logical separation within the cloud environment.
- Traffic Flow Control: Implement security groups or network Access Control Lists (ACLs) to restrict traffic flow between tiers (presentation, application, database) and the Internet. This controls what data can enter and leave each tier.
- Least Privilege IAM: Grant access based on user roles within each tier. Users should only have the minimum permissions needed for their tasks (e.g., read-only access for customer support).
3. A data breach has occurred, and we suspect sensitive customer data stored in the cloud may be compromised. Walk me through your incident response process for investigating and containing this breach.
Here’s a detailed step-by-step approach for investigating and containing the breach:
Isolate the Breach:
- Stop further data exfiltration by isolating compromised systems and accounts.
- Revoke access for potentially compromised credentials.
Investigate the Breach:
- Identify the attack vector (e.g., malware, phishing).
- Determine the compromised data and affected users.
- Analyze logs and forensic evidence to understand the scope of the breach.
Remediate the Breach:
- Patch vulnerabilities exploited in the attack.
- Reset compromised credentials and implement stronger password policies.
- Consider additional security controls to prevent similar attacks in the future.
Report the Breach:
- Inform impacted individuals and regulatory authorities as mandated by applicable laws. This may involve specific timelines depending on regulations.
Recover and Improve:
- Restore affected systems and data from backups (if available).
- Conduct a post-mortem analysis to identify weaknesses and improve security posture.
- Enhance security awareness training for employees.
4. Our cloud provider recently experienced a security incident. What steps would you take to assess the impact on our organization and ensure our data remains secure?
Here’s a systematic approach to handling such a situation:
- Review the provider’s incident report to understand the potential impact on your data and workloads.
- Communicate with the provider to gather details about the incident and affected services.
- Conduct your own security assessments to identify vulnerabilities in your cloud environment that might be exposed due to the provider’s incident.
- Consider additional security controls like data encryption or network segmentation to minimize risk in case your environment is compromised.
- Increase security monitoring and logging to detect any suspicious activity targeting your cloud resources.
5. You’ve been tasked with managing a large dataset containing sensitive customer information (e.g., credit card numbers, social security numbers). Outline the steps you’d take to secure this data at rest within the cloud environment.
Below is a step-by-step outline of how to securely manage sensitive data at rest in the cloud:
- Data Classification: Classify data based on sensitivity (e.g., credit card numbers, social security numbers). This helps prioritize security controls for different data categories.
- Encryption: Encrypt data at rest using industry-standard algorithms like AES-256. Strong encryption keys are crucial for data protection.
- Key Management: Implement secure key management practices with proper access controls and key rotation policies. Regularly rotate encryption keys to minimize the risk of compromised keys.
- Access Controls: Restrict access to sensitive data using IAM policies. Implement the principle of least privilege and limit user access to only the data they need for their jobs.
6. We’re concerned about the potential for unauthorized data exfiltration. Describe your approach to implementing DLP controls in the cloud to prevent sensitive data leaks.
Below is a step-by-step approach to implementing effective DLP controls in the cloud:
- Identify Sensitive Data: Identify and classify sensitive data types like credit card numbers and social security numbers.
- DLP Implementation: Implement cloud-based DLP (Data Loss Prevention) solutions to monitor data transfers across the cloud environment.
- DLP Policy Configuration: Configure DLP rules to detect and block suspicious data movement patterns, such as attempts to transfer large amounts of sensitive data outside authorized channels.
- DLP Policy Reviews: Conduct regular reviews and updates of DLP policies to ensure they remain effective against evolving threats.
7. Our cloud environment has multiple user accounts with varying access needs. How would you implement the principle of least privilege using IAM to ensure users only have the access they absolutely need to perform their jobs?
Here’s how you can implement this principle in a cloud environment:
- Granular Access Control: Define IAM policies with fine-grained permissions for each user role within your cloud environment. This ensures users only have the specific actions and data access required for their job function.
- Just-in-Time (JIT) Access: Grant temporary access for specific tasks when needed, revoking access when the task is completed. This minimizes the window of opportunity for unauthorized actions with elevated privileges.
- Multi-Factor Authentication (MFA): Implement MFA for all user accounts. This adds an extra layer of security by requiring a second verification factor beyond just a username and password.
- Regular Reviews: Conduct periodic reviews of user access privileges. Revoke unnecessary permissions and disable inactive accounts to minimize the attack surface.
8. An alert indicates suspicious activity on a cloud server containing financial data. Walk me through your initial steps in responding to this potential security incident.
Below is a step-by-step outline of the initial response steps:
- Isolate the Server: Disconnect the server from the network to prevent further lateral movement of the attacker or the spread of malware.
- Collect Forensic Evidence: Collect logs, system files, and memory dumps from the server for forensic analysis to understand the nature and scope of the attack.
- Identify the Threat: Analyze the collected evidence to determine the type of attack, how the server was compromised, and what data may be at risk.
- Remediate and Recover: Patch vulnerabilities exploited in the attack. Restore compromised data from backups if available. Consider implementing additional security controls to prevent similar attacks.
- Incident Response Reporting: Follow internal incident response procedures and report the incident to the appropriate authorities if necessary.
9. Our company operates in a heavily regulated industry (e.g., healthcare, finance). How would you approach aligning our cloud security practices with relevant regulatory compliance requirements?
Below is a strategic approach to aligning cloud security with relevant compliance requirements:
- Compliance Mapping: Identify relevant regulations for your industry (e.g., HIPAA for healthcare, PCI DSS for credit cards). Map and implement your cloud security practices to the specific compliance requirements of those regulations.
- Security Assessments: Conduct regular security assessments aligned with regulatory controls to ensure your cloud environment meets compliance standards.
- Data Residency: Understand data residency requirements for your industry. Choose a cloud provider that stores your data in compliance with relevant regulations.
- Audit Trails and Logging: Implement robust logging practices to record all user activity and system events. Maintain audit trails for the required period to demonstrate compliance during audits.
10. We’re negotiating a contract with a Cloud Service Provider (CSP). What security-related elements should we include in the SLA (Service-Level Agreement) to ensure our data and workloads are protected?
Here are the key security elements you should include:
- Security Controls: The SLA should specify the security controls the provider implements to protect your data and workloads. This may include details on encryption standards, access control mechanisms, and intrusion detection systems.
- Incident Response: Clearly define the responsibilities of both you and the cloud provider in the event of a security incident. The SLA should outline the process for incident detection, investigation, and remediation.
- Data Security: Specify data encryption standards, key management practices, and data residency requirements within the SLA.
- Compliance: Ensure the SLA aligns with your compliance obligations. The SLA should outline how the provider assists with audits and reporting requirements.
11. The cloud security landscape is constantly evolving. What are some of the latest cloud security threats you’re aware of, and how would you prepare your organization to mitigate them?
Here are some of the latest cloud security threats and strategies to mitigate them:
- Threat Intelligence: Stay informed about evolving cloud security threats by subscribing to security advisories and threat intelligence feeds from reputable sources.
- Patch Management: Implement automated patching processes to address vulnerabilities promptly in your cloud environment. This minimizes the timeframe in which attackers can exploit vulnerabilities in unpatched systems.
- Cloud Workload Protection Platform (CWPP): Consider deploying a CWPP solution to provide comprehensive threat detection and prevention capabilities for your cloud workloads. CWPPs provide capabilities such as real-time threat detection, anomaly identification, and automated incident response.
12. We plan to deploy a multi-tier application architecture in the cloud. Explain how you would utilize security zones within the cloud environment to segregate different application components based on their security needs.
Here’s how you can design and implement security zones for a multi-tier cloud application:
- Security Zones: Utilize security zones within the cloud environment to logically segregate different application tiers (presentation, application, database) based on their security needs. This creates a layered security approach.
- Zone-Specific Security Controls: Implement appropriate security controls within each zone. For example, the database zone might require stricter access controls compared to the presentation zone.
- Inter-Tier Traffic Control: Restrict traffic flow between zones using security groups or ACLs. Allow only essential communication between tiers, such as the application tier needing access to the database tier.
13. Our cloud environment is rapidly growing. How can we leverage security automation tools and best practices to streamline security processes and reduce manual workloads?
Here’s how you can effectively integrate automation into your cloud security strategy:
- Security Automation Tools: Leverage tools for automated vulnerability scanning, security configuration management, and log analysis. This can streamline security processes and reduce the workload for your security team.
- Security Orchestration, Automation, and Response (SOAR): Consider implementing a SOAR platform to automate incident response workflows. SOAR can automate tasks like collecting evidence, quarantining compromised systems, and notifying stakeholders.
- Security Best Practices: Adopt security best practices like Infrastructure as Code (IaC) to enforce consistent and secure configurations across your cloud environment.
14. Our organization utilizes a hybrid cloud environment with on-premises and cloud-based resources. Describe your approach to managing cryptographic keys across this hybrid environment while ensuring strong key security.
Here’s a detailed approach to managing cryptographic keys in a hybrid cloud environment:
- Centralized Key Management: Implement a centralized Key Management Service (KMS) to manage cryptographic keys across both on-premises and cloud environments. This provides a single point of control and simplifies key management.
- Key Lifecycle Management: Enforce strict key lifecycle management practices. This includes key rotation (changing keys regularly), encryption of keys at rest, and robust access controls to restrict who can access and manage keys.
- Compliance with Regulations: Ensure your key management practices comply with relevant industry regulations and data privacy laws. This may involve specific requirements for key storage, access, and auditability.
15. How would you implement a strategy for regular cloud key rotation to minimize the risk associated with compromised keys?
Here’s a step-by-step approach to implementing an effective cloud key rotation strategy:
- Automated Rotation: Configure automated key rotation at regular intervals (e.g., every 90 days) to minimize the risk associated with compromised keys. Even if an attacker gains access to a key, its usefulness is limited due to frequent rotation.
- Secure Key Storage: Ensure secure storage of encryption keys using Hardware Security Modules (HSMs) or cloud-based KMS offerings with robust access controls. HSMs provide a tamper-resistant environment for storing encryption keys.
- Backup and Recovery: Implement secure backup and recovery processes for your encryption keys. This ensures the availability of keys in case of incidents or accidental deletion.
16. How would you establish a vulnerability management program for identifying and patching vulnerabilities within a cloud environment?
Below is a structured approach to developing an effective vulnerability management program:
- Vulnerability Scanning: Regularly scan your cloud environment for vulnerabilities using automated vulnerability scanning tools. These tools can identify potential security weaknesses in your cloud resources and applications.
- Patch Management: Prioritize and patch vulnerabilities based on severity and risk to your environment. Focus on patching critical vulnerabilities first to minimize the window of exploitability.
- Continuous Monitoring: Implement continuous security monitoring to detect and address vulnerabilities promptly. Security monitoring tools can provide real-time insights into potential security threats.
17. Explain the importance of security logging and SIEM (Security Information and Event Management) in the cloud. How would you utilize these tools for effective cloud security monitoring?
Here’s an explanation of their importance and how to use them effectively for cloud security:
- Centralized Logging: Implement centralized logging to collect logs from all cloud resources and applications. This allows for a comprehensive analysis of security events.
- SIEM for Security Insights: Utilize a Security Information and Event Management (SIEM) solution to aggregate and analyze log data from various sources in your cloud environment. SIEM can help identify security incidents and suspicious activity by correlating events across different logs.
- Log Retention and Compliance: Maintain logs for a defined period to comply with regulations and for forensic analysis purposes. Regulatory requirements may dictate how long you need to retain logs.
18. We’re considering migrating critical business applications to the cloud. Describe your approach to conducting a comprehensive cloud security risk assessment to identify potential threats and vulnerabilities.
Here’s a step-by-step approach to performing a thorough cloud security risk assessment:
- Threat Modeling: Identify potential threats and vulnerabilities to your cloud environment through threat modeling exercises.
- Security Posture Assessment: Conduct a comprehensive security posture assessment to evaluate the effectiveness of your cloud security controls.
- Penetration Testing: Engage in penetration testing to identify exploitable vulnerabilities in your cloud environment.
- Risk Remediation: Prioritize and remediate identified risks based on their severity and potential impact.
19. A natural disaster disrupts our primary cloud data center. How would you utilize Disaster Recovery (DR) strategies to ensure business continuity and minimize downtime?
Here’s how you can implement and utilize effective DR strategies for cloud environments:
- DR Planning: Develop a comprehensive DR plan outlining recovery steps for your cloud-based applications and data in case of a disaster. The plan should detail roles, responsibilities, and recovery procedures.
- Cloud DR Services: Leverage cloud provider-offered DR services like replication and failover to ensure business continuity and minimize downtime during a disaster. Replication keeps a copy of your data in a secondary location for quick recovery. Failover automatically switches to the backup environment if the primary environment becomes unavailable.
20. Our organization is increasingly concerned about insider threats. How can we strengthen our cloud security posture to mitigate the risk of insider attacks?
Here’s a comprehensive approach to strengthening your cloud security posture to address insider threats:
- Reinforce Least Privilege: Enforce granular IAM policies, minimizing user access to sensitive data and functionalities. Users should only have the permissions they absolutely need to perform their jobs.
- Monitor User Activity: Implement user activity monitoring to detect anomalies and potential misuse of access. This can involve monitoring login attempts, file access, and data transfers.
- DLP for Insider Threats: Leverage Data Loss Prevention (DLP) to prevent unauthorized data exfiltration attempts, even by insiders. DLP solutions can monitor data movement and block attempts to transfer sensitive data outside authorized channels.
Explore interview questions of other domains from here: Interview Questions .
CCSP with InfosecTrain
Looking to take your cloud security expertise to the next level? Consider pursuing the Certified Cloud Security Professional (CCSP) certification. InfosecTrain offers a comprehensive CCSP training program designed to equip you with the skills necessary to pass the exam and excel in your cloud security career.

TRAINING CALENDAR of Upcoming Batches For CCSP
- Drop us a Query
- Join Webinars
- Training Calendar
- 1800-843-7890 (IN)
- +1657-221-1127 (USA)
- [email protected]
Request more information

Dear Learner
Take a step closer to glow and grow in your career
Our Course Advisor will give you a call shortly
CS50's Introduction to Cybersecurity
Learn how to protect your own data, devices, and systems from today's threats..
An introduction to cybersecurity for technical and non-technical audiences alike in an online course from Harvard.

What You'll Learn
This is CS50's introduction to cybersecurity for technical and non-technical audiences alike. Learn how to protect your own data, devices, and systems from today's threats and how to recognize and evaluate tomorrow's as well, both at home and at work. Learn to view cybersecurity not in absolute terms but relative, a function of risks and rewards (for an adversary) and costs and benefits (for you). Learn to recognize cybersecurity as a trade-off with usability itself. Course presents both high-level and low-level examples of threats, providing students with all they need know technically to understand both. Assignments inspired by real-world events.
The course will be delivered via edX and connect learners around the world. By the end of the course, participants will learn:
- hacking, cracking
- social engineering, phishing attacks
- passcodes, passwords, SSO
- brute-force attacks, dictionary attacks
- multi-factor authentication, password managers
- ethical hacking
- (distributed) denial-of-service attacks
- viruses, worms, botnets
- SQL injection attacks
- port-scanning
- proxies, firewalls
- automatic updates
- closed-source, open-source software
- buffer-overflow attacks
- secure deletion
- hashing, salting
- secret-key, public-key encryption, digital signatures
- full-disk encryption, ransomware
- cookies, sessions, incognito mode
- anonymization, de-identification
- verification
- operating systems, app stores
Your Instructors
David J. Malan is Gordon McKay Professor of the Practice of Computer Science at Harvard University in the School of Engineering and Applied Sciences as well as a Member of the Faculty of Education in the Graduate School of Education. He teaches Computer Science 50, otherwise known as CS50, which is among Harvard University's largest courses, one of Yale University's largest courses, and edX's largest MOOC. He also teaches at Harvard Business School, Harvard Law School, Harvard Extension School, and Harvard Summer School.
Ways to take this course
When you enroll in this course, you will have the option of pursuing a Verified Certificate or Auditing the Course.
A Verified Certificate costs $449 and provides unlimited access to full course materials, activities, tests, and forums. At the end of the course, learners who earn a passing grade can receive a certificate.
Alternatively, learners can Audit the course for free and have access to select course material, activities, tests, and forums. Please note that this track does not offer a certificate for learners who earn a passing grade.
Data Science Principles
Data Science Principles gives you an overview of data science with a code- and math-free introduction to prediction, causality, data wrangling, privacy, and ethics.
Cybersecurity: Managing Risk in the Information Age
Develop a personalized mitigation strategy for your organization’s networks, systems, and data to successfully respond to cyberattacks.
Technology Entrepreneurship: Lab to Market
Join us to learn a systematic process for technology commercialization to bring cutting-edge innovations out of the lab and into the world.
Five Actionable Lessons From Recent Top Cybersecurity Incidents
Get the eBook to learn about the top cybersecurity incidents that occurred recently and five actionable lessons from these events.
Download E-Book!
Five Actionable Lessons From Recent Top Cybersecurity Incidents has been emailed to you but feel free to download it now.
Cybercrime and the cost of data breaches are increasing at an alarming rate, raising concerns among business owners and IT practitioners about the security of their business and data. The COVID-19 pandemic and remote work environments provided the perfect opportunity for cybercriminals to compromise business data. The number of high-profile cybersecurity incidents in recent times indicates that cybercriminals took maximum advantage of the situation.
This eBook covers the top cybersecurity incidents that occurred recently, five actionable lessons we can learn from these events and an understanding of the threat landscape from Kaseya’s CISO and ex-FBI Special Agent Jason Manar’s perspective.

Research Topics & Ideas: Cybersecurity

I f you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

How To Choose A Tutor For Your Dissertation
Hiring the right tutor for your dissertation or thesis can make the difference between passing and failing. Here’s what you need to consider.

5 Signs You Need A Dissertation Helper
Discover the 5 signs that suggest you need a dissertation helper to get unstuck, finish your degree and get your life back.

Writing A Dissertation While Working: A How-To Guide
Struggling to balance your dissertation with a full-time job and family? Learn practical strategies to achieve success.

How To Review & Understand Academic Literature Quickly
Learn how to fast-track your literature review by reading with intention and clarity. Dr E and Amy Murdock explain how.

Dissertation Writing Services: Far Worse Than You Think
Thinking about using a dissertation or thesis writing service? You might want to reconsider that move. Here’s what you need to know.
📄 FREE TEMPLATES
Research Topic Ideation
Proposal Writing
Literature Review
Methodology & Analysis
Academic Writing
Referencing & Citing
Apps, Tools & Tricks
The Grad Coach Podcast
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Submit Comment
- Print Friendly
- Products & Services
- Security Operations
- Threat Research
- AI Research
- Naked Security
- Sophos Life
Update on Naked Security
Mom’s Meals issues “Notice of Data Event”: What to know and what to do
S3 Ep149: How many cryptographers does it take to change a light bulb?
Using winrar be sure to patch against these code execution bugs….
Smart light bulbs could give away your password secrets
“snakes in airplane mode” – what if your phone says it’s offline but isn’t, s3 ep148: remembering crypto heroes, fbi warns about scams that lure you in as a mobile beta-tester, “grab hold and give it a wiggle” – atm card skimming is still a thing.
An official website of the United States government
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Publications
- Account settings
- Advanced Search
- Journal List

A deeper look into cybersecurity issues in the wake of Covid-19: A survey
Moatsum alawida, abiodun esther omolara, oludare isaac abiodun, murad al-rajab.
- Author information
- Article notes
- Copyright and License information
Corresponding authors.
Received 2022 Apr 27; Revised 2022 Jul 3; Accepted 2022 Aug 2; Issue date 2022 Nov.
Since January 2020 Elsevier has created a COVID-19 resource centre with free information in English and Mandarin on the novel coronavirus COVID-19. The COVID-19 resource centre is hosted on Elsevier Connect, the company's public news and information website. Elsevier hereby grants permission to make all its COVID-19-related research that is available on the COVID-19 resource centre - including this research content - immediately available in PubMed Central and other publicly funded repositories, such as the WHO COVID database with rights for unrestricted research re-use and analyses in any form or by any means with acknowledgement of the original source. These permissions are granted for free by Elsevier for as long as the COVID-19 resource centre remains active.
This study analyzed the Coronavirus (COVID-19) crisis from the angle of cyber-crime, highlighting the wide spectrum of cyberattacks that occurred around the world. The modus operandi of cyberattack campaigns was revealed by analyzing and considering cyberattacks in the context of major world events. Following what appeared to be substantial gaps between the initial breakout of the virus and the first COVID-19-related cyber-attack, the investigation indicates how attacks became significantly more frequent over time, to the point where three or four different cyber-attacks were reported on certain days. This study contributes in the direction of fifteen types of cyber-attacks which were identified as the most common pattern and its ensuing devastating events during the global COVID-19 crisis. The paper is unique because it covered the main types of cyber-attacks that most organizations are currently facing and how to address them. An intense look into the recent advances that cybercriminals leverage, the dynamism, calculated measures to tackle it, and never-explored perspectives are some of the integral parts which make this review different from other present reviewed papers on the COVID-19 pandemic. A qualitative methodology was used to provide a robust response to the objective used for the study. Using a multi-criteria decision-making problem-solving technique, many facets of cybersecurity that have been affected during the pandemic were then quantitatively ranked in ascending order of severity. The data was generated between March 2020 and December 2021, from a global survey through online contact and responses, especially from different organizations and business executives. The result show differences in cyber-attack techniques; as hacking attacks was the most frequent with a record of 330 out of 895 attacks, accounting for 37%. Next was Spam emails attack with 13%; emails with 13%; followed by malicious domains with 9%. Mobile apps followed with 8%, Phishing was 7%, Malware 7%, Browsing apps with 6%, DDoS has 6%, Website apps with 6%, and MSMM with 6%. BEC frequency was 4%, Ransomware with 2%, Botnet scored 2% and APT recorded 1%. The study recommends that it will continue to be necessary for governments and organizations to be resilient and innovative in cybersecurity decisions to overcome the current and future effects of the pandemic or similar crisis, which could be long-lasting. Hence, this study's findings will guide the creation, development, and implementation of more secure systems to safeguard people from cyber-attacks.
Keywords: Cybersecurity, COVID-19 and organization cybersecurity challenges, Trending insight of cyber-attack, Internet security, Business security, Economic disruption, Cyberspace future
1. Introduction
In times of crisis, an upsurge in cyber-attacks is usual. Take for instance, the global economic crisis in 2008 resulted in cyber-attacks as corporation capital declined and citizens became an easy target ( Ng and Kwok, 2017 , Thakur et al., 2016 , Das, 2015 , Watters et al., 2012 ). Cybercriminals take advantage of social flaws, and thus, the coronavirus pandemic, also known as COVID-19, is no exception. The picture of cybersecurity threats in 2020 has mirrored that of the previous economic downturn. With these eye-opening 2020 cybersecurity figures, one can observe the impact of COVID-19 on individuals, businesses, and the entire world, even in its early phases. The COVID-19 outbreak began to make international headlines in January 2020. COVID-19 was declared a worldwide pandemic by the World Health Organization (WHO) on March 11, 2020. That week, everything changed in the world. Bustling streets were deserted, hospital beds were overflowing, and shops were shuttered. COVID-19 has already been dubbed the world's biggest cybersecurity threat. The healthcare and banking industries were the most vulnerable to cyber-attacks. As a result of the COVID-19, email phishing threats were the most common source of data breaches while working from home because of the national lockdown.
Many types of cyber-attack took place day and night during the peak period of the global COVID-19 crisis. Hackers were busy launching and trying their hands on different variants of cyber-attacks such as phishing, malware, distributed-denial-of-service (DDoS), denial-of-service (DoS), advanced persistent threat (APT), malicious social media messaging (MSMM), business email compromise (BEC), botnet, ransomware amongst many others. In the case of the phishing attack, hackers used harmful links hidden in carefully designed emails to target company employees. Unfortunately, when employees click on such links, they ignorantly download keylogging software onto their computers or devices, giving hostile actors access to their credentials. Hackers can then gain unrestricted access to critical business assets and data of the victim’s organization by impersonating a genuine employee.
In the year 2020, there was about 1001 frequency of data breaches in the United States. As a result, over 155.8 million people were affected by data breaches in the same year. According to the Identity Theft Resource Center's (ITRC) data breach study, there were 1,291 data breaches between September 2020 and September 2021. Compared to the 1,108 data breaches reported in 2019, this statistic represents an 8 percent rise. The trend of compromise between 2016 and 2021 is highlighted in Table 1 .
The trend of compromise between 2016 and 2021.
In the year 2020, in the wake of the COVID-19 crisis, there were about 1,872 breaches, compared to 1,108 in 2019. However, in the first quarter of 2022, data compromises caused by physical attacks such as document or device theft and skimming devices fell to single digits (3), totaling 404. In the aftermath of the COVID-19 pandemic, cyber security concerns have arisen from various quarters. In the past two years, the COVID-19 pandemic has been making headlines worldwide. The medical community, as well as governments and citizens around the world, are pooling their resources to stop the spread of the disease. Unfortunately, as healthcare organizations beef up their resources to battle the COVID-19 outbreak, they have become targets of cyber-attacks (McKinsey and Company, 2020, TCS Worldwide, 2020; Orange Cyber Defense, 2020).
In this context, on April 8, 2020, the US Department of Homeland Security (DHS), the UK's National Cyber Security Centre (NCSC), and the Cybersecurity & Infrastructure Security Agency (CISA) issued a joint advisory describing how the COVID-19 pandemic was being exploited by cybercriminals and APT organizations (Deloitte, 2020). Concerns about phishing, malware and other attacks on communication networks were addressed in this advisory from organizations, such as Microsoft Teams and Zoom. As the world focuses on the health and economic concerns posed by COVID-19, cybercriminals around the world are undoubtedly taking advantage of the situation (Abiodun et al., 2022). Recent studies have shown that a plethora of businesses owned by mega organizations, small and medium scale enterprises were victims of cyber-attack with the rise of COVID-19, which also constituted to their collapse ( Lallie et al., 2021 ).
In the wake of COVID-19, cyber-attackers aimed at disrupting and rendering company operations useless for malicious and remunerative purposes. There has been a significant increase in DDoS and DoS activities. Adversaries have been spotted attempting to disrupt business networks and propagate disinformation to weaken pandemic responses involving vaccine research, healthcare distribution, and treatment delivery. Hackers seeking financial gain, as evidenced by the rise in Bitcoin-to-United States Dollar (USD) pricing, are likely the cause of the return to or re-prioritize ransom denial of service (RDoS) and DDoS extortion operations in huge numbers. Threat actor groups with sophisticated tools meant to disrupt or take down enterprise networks are frequently the source of this.
Nowadays, people use Internet platforms to purchase transportation tickets for air, bus, train, and taxi booking. Likewise, the Internet serves as a space for making food orders, recharging mobile phones, paying utility bills with credit/debit cards, and many e-commerce activities. Unfortunately, cybercriminals are attacking these sites to collect personal information for financial rewards. Therefore, the international research community, national research community and stakeholders in ICT must come together to tackle cyber-attack issues to curtail the losses emanating as the end product of the attacks, ranging from financial losses and damages to devices and network infrastructure collapse.
Search keyword
In this study, search keywords, including bibliographic databases, are explored. Overall, 300 papers were used in our study. The number of articles processed is summarized in Table 2 .
Paper organization
Data collection and systematization.
This paper discusses the existing open problems and challenges in cybersecurity during the global COVID-19 crisis. It is divided into several sections: Section 1, covers the introduction, motivation, and search keyword. Section 2, covers contributions and related work - combining previous and current studies, each with its subsections. The methodology is discussed in Section 3, which introduces the main analysis used for the data. It also provides details of how the survey was carried out systematically using a flow chart description. Section 4 showcases the result from the survey, analysis, and interpretation of results, each with their corresponding subsections. Section 5 is the discussion of the result with a presentation of a summary of implications, future research issues, and implications. Section 6 focused on solutions to the current cybersecurity challenges, recommendations and research findings. It also identified research gaps, current trends, future perspectives, directions, and suggestions. Finally, Section 7 concludes this survey and provides highlights of future work.
Contributions
This study explores variants of cybersecurity problems, issues, and challenges encountered at the wake of the COVID-19 pandemic. However, certain types of cybersecurity problems were identified, which were predominant during the COVID-19 pandemic. Fifteen (15) types of cyber-attacks were identified as the most common. Some of the cyber-attack types are; malware, phishing, ransomware, distributed denial-of-service (DDoS), browsing apps, malicious domains, denial-of-service (DoS), mobile apps, and malicious websites. Others are spam emails, malicious social media messaging, business email compromise, APT, botnet attacks and hacking. Then policy conclusions were generated based on data from a comprehensive worldwide study conducted from March 2020 to December 2021. The main contributions of this research, as well as the distinctiveness of its methodology, are summarized in Fig. 1 .
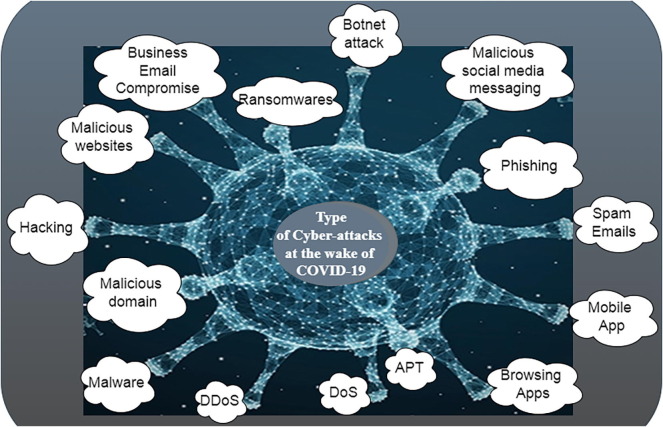
Main Cyber Security Threats in the wake of COVID-19.
The frequency of cyber-attacks has risen dramatically in recent years and has progressively become more dangerous in the wake of COVID-19 as almost every-one has become a target to cybercriminals. Many people have suffered as a result of a lack of personal safety procedures when using the Internet. Cyber attackers now have simple access to some people's data due to the lockdown as a result of the COVID-19 epidemic. During this time, many banking sectors, governmental and non-governmental organizations have been targeted by attackers. Hence, this paper focuses on several security measures that can be taken to protect personal and organizational information from cybercriminals. Thus, Fig. 1 highlights the different angles depicting the main contributions of this paper, which uniquely covered the many incidences of cyber-attack cases in the wake of the COVID-19 pandemic. These main contributions are further discussed as follows;
1.1. Hacking
Malicious scammers went on a rampage to hack people connected to digital networks such as computers, laptops, tablets, and phones. Thereby stealing sensitive data such as passwords, usernames, bank information, and other personal details. Some hackers used the stolen data to withdraw money from people’s accounts. Likewise, bank loan scams spread rapidly at the peak of the COVID-19 crisis, as many of the scams focused on defrauding people of their money and personal information through online shopping. As a result of the pandemic, fraud cases was 42 percent greater than the previous year, 2019, as cybercrooks took advantage of the fact that many physical stores had to close. Some bank clients reported receiving SMS messages instructing them to go online and reschedule a package delivery. At the same time, others filled out their banking information which subsequently led to their accounts being hacked. In other news, two Indonesian hackers were apprehended for a $60 million scam, according to CBS News, on the 16th of April 2021. Following a tip from US authorities, the two suspects were apprehended in Surabaya, Indonesia's second-largest city ( cbsnews, 2021 ).
The scam had been going on for an unknown amount of time, according to the Indonesian police. “Around 30,000 Americans have been duped, and the government has lost up to $60 million,” claimed East Java police head Nico Afinta ( cbsnews, 2021 ). In the United States, thousands of targeted victims have provided personal data to the fraudulent website. These personal details include social security numbers, with the expectation of receiving $2,000 as part of an unemployment relief program to scam the government. Hence, an urgent need for more research on how to counter hackers, especially during a crisis.
1.2. Phishing
Phishing is a method of social engineering exploits frequently used to obtain sensitive information from users, such as online banking login credentials, company login credentials, credit card details, login credentials, or username/passwords. Thus, cybercriminals steal confidential information by sending fraudulent messages to their target. The aim is to get people to expose their financial details, system credentials, and other sensitive data.
Phishing is still the easiest method for hackers to infect a device with malware. Phishing schemes entice victims to open emails or click on links that look to come from a credible company or respectable source. The link may take one to a bogus website that asks people for personal information or to a website that directly infects user computers with malware. Therefore, if one is unsure about a link, do not click the link. During the nationwide lockdown caused by the widespread Coronavirus, hackers took advantage of the situation by sending phishing emails to many people.
Phishing emails contain phony web pages that can acquire a user’s personal information. Since most people now rely on online channels to cope with the pandemic, they have become exposed to phishing attempts. In March 2020, out of 4,67,825 phishing emails, 9,116 were related to COVID-19, accounting for less than 2 % of all phishing emails ( Naidoo, 2020 ). Nevertheless, the reported amount of suspected email attacks provides insight into the United Kingdom (UK) cyber-crime incidence problem faced during the epidemic, where a sizeable number of phishing and smishing attacks occurred.
Smishing is a type of scam that involves sending text messages that appear to be from legitimate and trusted organizations to trick people into divulging personal information like credit card numbers, usernames and passwords. More than 160,000 suspicious emails attacks had been reported to the National Cyber Security Centre (NCSC) by the beginning of May, precisely 7th 2020 ( NCSC, 2020 , Lallie et al., 2021 ), and by the end of May, precisely on the 29th, 2020, about £4.6 million had been lost to COVID-19-related scams, with around 11,206 victims of phishing and/or smishing campaigns (Sky News, 2020 ). In response, the NCSC and Her Majesty's Revenue and Customs (HMRC) brought down 471 fraudulent online shops ( Tidy, 2020 ) and 292 counterfeit websites ( Hill, 2020 ). Vishing and Smishing are two types of cyber-fraud that criminals deploy to deceive people into giving up money or personal information. In the case of vishing, it is by voice, while, in the case of smishing, it is by SMS deception.
1.3. Ransomware
Ransomware is a sort of malicious software that criminals design to prevent users from accessing their computers unless they pay money. Ransomware attacks skyrocketed as the number of people working remotely rose during the pandemic (Chigada and Madzinga, 2021). Ransomware is becoming increasingly sophisticated. Other technologies are now being added to ransomware's armoury, in addition to encryption. The financial sector, in particular, is a common target for ransomware attacks. The ransomware has also grown in scope and intensity, causing damage to corporations, organizations, healthcare providers, and government departments while many countries struggle to respond to the COVID-19 crisis. As ransomware continues to be one of the most severe worldwide cyber threats to healthcare, security staff must be cautious and informed of the methods, techniques, and procedures that criminals will employ to earn a profit. According to cybersecurity experts, in October 2020, ransomware gangs are starting to use DDoS attacks on victims' networks or websites as a supplemental tool to pressure them to pay a ransom. RagnarLocker and SunCrypt were the two operations adopting this novel method at the time. Ransomware gangs now have new attack surfaces to try to exploit and apply debilitating strategies to force enterprises to pay ransom demands as the threat landscape has changed.
Healthcare providers are usually targeted by cybercriminals looking to make the most money in the shortest amount of time. The Avaddon ransomware gang has recently joined the practice of utilizing DDoS assaults to extort money from victims. After launching spam campaigns that targeted people all around the world, the Avaddon ransomware commenced operations in June 2020. The ransomware gang tried their hand at double extortion when they sent an unidentified victim organization a menacing ransom note with a deadline of 240 h to cooperate. Failure to do so would expose the company's database, which includes customer and employee personal details, as well as financial paperwork. According to the ransom message, the victim's website was under a non-stop DDoS attack until Avaddon was contacted. Therefore, there is an urgent need for more research on how to counter ransomware attacks, especially during a crisis.
1.4. Botnet attack
Botnet or a bot is a device like a computer, server, or phone infected with malware such as malicious programs, software, virus, and worms that perform destructive actions without the user's knowledge. Botnets are infected device networks that work collectively under an attacker's command. Botnets are utilized to carry out phishing scams, spam campaigns, and distributed denial of service (DDoS) attacks. Most botnets use distributed denial-of-service to send as many requests as possible to a single Internet computer or resource, overloading it and subsequently preventing it from serving genuine requests. Cybercriminals are swiftly enlisting Internet of Things (IoT) devices ( Abiodun et al., 2021a , Abiodun et al., 2021b ) into their botnet forces, according to the current threat intelligence discoveries from A10 Networks' cybersecurity researchers, boosted by Mozi malware spreading throughout the world. Attackers are increasingly focusing on low-volume, high-frequency attacks that can have a big impact and, in between, avoid being traced, detected or defended by measures put in place by targets.
Thus, in the wake of COVID-19, there are cases of botnet threats like emotet attacks. Emotet is a type of computer malware originally designed as a banking Trojan. Many botnets, such as emotet, are polymorphic in nature. Emotet polymorphism means that the malware's code changes every time it is activated. Usually, most antivirus programs search the computer for existing malware codes. However, a code change may make it more difficult to detect the infection, thus, allowing it to go undetected. Emotet grew in size over time and was responsible for millions of costly cyberattacks worldwide. Emotet's capacity to acquire access to one’s computer got increasingly sneaky, allowing new viruses to infiltrate the target system. Malspam, or spam emails with malware, is the most common way for it to disseminate, hence, the term. Summarily, emotet is a Trojan horse that is disseminated mostly through spam emails, that is, malspam . Malicious scripts, macro-enabled data, files, documents, and malicious links are all possible ways for the infection to spread. To persuade users, its messages frequently contain familiar branding to look like a legitimate email, imitating the email structure of well-known, trusted and popular companies such as DHL or PayPal to convince users.
Emotet was a cybercrime service that was both professional and long-lasting. Emotet, once labelled “the world's most destructive malware,” has resurfaced and is being deployed on Windows systems infected with TrickBot malware during the peak of COVID-19. The emotet Malware infected over 1.6 million computers worldwide, causing damages worth hundreds of millions of dollars. In January 28, 2021, the United States of America Justice Department declared its participation in a worldwide operation encompassing the US, France, Canada, the Netherlands, Germany, and the United Kingdom to disrupt and shut down the infrastructure of the emotet malware and botnet. Officials from Ukraine, Sweden, and Lithuania also participated in this huge cyber operation on emotet. “Regrettably, the emotet malware and botnet infected hundreds of thousands of computers across the United States, such as key infrastructure, and caused millions of dollars in damage to victims around the world”. Emotet can transmit further malware to targeted computers, such as ransomware or spyware that steals financial credentials, once it has infected them. Hence, there is an urgent need for more research on how to counter botnets, especially during a crisis.
Cyber attackers and APT groups took advantage of vulnerable persons and systems during the national lockdown amidst the COVID-19 outbreak. An attack or state-sponsored group known as an APT happens when an unauthorized user uses advanced and sophisticated ways to obtain access to a system or network. APT usually deploy techniques such as ransomware, phishing, malware, and data breaches to launch attacks on their targets ( Mohamed et al., 2018 ). The group focuses typically on telecommunications, military and travel sectors, suggesting that it intends to conduct surveillance, tracking, or monitoring activities on specific individuals. Intention to gather proprietary or customer data for commercial or operational purposes in support of national priorities or to build additional entry points and vectors to aid future campaigns. Targeting government entities reveals a secondary goal of gathering geopolitical data to aid nation-state decision-making. In an incidence case of an APT threat, three members of North Korea's Reconnaissance General Bureau were charged for WannaCry, the Sony Pictures hack, and many other cybercrimes in February 19, 2021. Template injection, Malicious macros, RTF exploits and Malicious LNK files are part of the methods utilized by APT cyber-attackers at the peak of the COVID-19 pandemic. Data exfiltration attacks continue to soar ( Taofeek et al., 2022 ), and organizations are forced to pay huge amounts of money as ransom. Thus, researchers need to focus further research on how to counter APT attacks.
1.6. Malware
Malware is software or code meant to harm computers by encrypting files, damaging, disabling, stealing data, or gaining unauthorized access to a computer. Likewise, malware can replicate itself onto a system like a computer or computer network to cause harm or destroy data. It is one of the common cyber-threats that organizations and businesses face in recent times. The phrase refers to a variety of harmful software, including trojans, worms, and ransomware. COVID-19 peak crisis was Malware's data-gathering season. That is, it has become a period in which cybercriminals have increased their use of data harvesting software such as Remote Access Trojan, info stealers, spyware, and banking Trojans. Threat actors enter systems using COVID-19-related material as a lure to breach networks, steal data, fraudulently transfer money digitally, and construct botnets. During this Coronavirus crisis, cybercriminals are infecting users' gadgets with malware. Malware can open a backdoor in a user's gadgets, allowing cyber attackers to access all of the user's private details, such as username and password. This malware is being propagated using a few internet Corona tracing maps.
More disruptive Malware, such as DDoS and Ransomware were launched during the COVID-19 crisis. Cybercriminals are mercilessly increasingly utilizing disruptive malware against vital infrastructure and healthcare organizations because of the potential for financial gain. For example, multiple threat organizations that had been relatively idle for a few months launched a wave of ransomware attacks in the first two weeks of April 2020. According to law enforcement investigations, most attackers predicted the maximum amount of ransom they might demand from targeted firms pretty accurately. As a result, consumer victims reported total cybercrime-related losses of $4.2 billion in 2020, which was up to 69 percent from 2019, according to the FBI Internet Crime Complaint Center. Malware attacks contributed to some of these losses. Therefore, there is an urgent need for more research on addressing malware attacks even during this crisis period.
1.7. Malicious social media messaging
During the climax of the COVID-19 attack and the lockdown period, there was a lot of malicious social media messaging and misinformation. Malicious social media messaging and misinformation to people and fake news grew to an alarming proportion. Unverified information, a lack of understanding of dangers, and a plethora of conspiracy theories have all led to community fear and, in some circumstances, aided in the execution of cyberattacks. Nearly 30 % of countries participating in the worldwide cybercrime study reported that incorrect material about COVID-19 was being circulated. A country recorded 290 postings in a month, the bulk of which contained hidden spyware. According to reports, misinformation has also been related to the unlawful trafficking of fake medical supplies. Other incidents of disinformation also reported scams, including 'too great to be true' offers like free food. Hence, there is an urgent need for research on how to address the issue of malicious social media messaging attacks that is fast growing as a means of cyber-attacks.
1.8. Business email compromise
Business Email Compromise (BEC) threats are one of the most financially devastating types of cybercrime ( Greathorn.com, 2021 , Cross and Gillett, 2020 , Cross and Kelly, 2016 ). They often use social engineering strategies and phishing emails to infiltrate organizations and fool unwary employees and executives into performing tasks that appear to come from a trustworthy sender, frequently posing as legitimate business activities. BEC attacks increased by 14 % in 2020 due to the massive cyber-attack surge prompted by the COVID-19 issue and worldwide lockdown measures. Profit will likely continue to drive this category forward; in 2020, hostile actors received compensation that was 30 % higher than the previous year, 2019. Hackers masquerading as the World Health Organization (WHO) send messages to people's emails that an attached file explains how to stop the sickness from spreading. They say that “ one small measure can cure you .” However, according to Proofpoint, the email attachment contains no relevant information and instead infects Personal computers (PCs) with malicious software known as AgentTesla Keylogger. AgentTesla Keylogger could record every keystroke and sends it to the attackers, allowing them to track their victims' online activities.
In a recent BEC report by “Cybersecurity Insiders” found in Greathorn.com, 2021 , Cross and Gillett, 2020 : (i) the most popular type of BEC attack is a spoofed email accounting for 71 %, followed by spear-phishing, which was 69 %. Furthermore, (ii) more than half of links received via email lead to a malicious site (iii) 57 % of malicious links in phishing emails intend to steal credentials. (iv) the finance sector has a target on its back, according to 34 % of respondents. (v) in the last 12 months, 3 % of firms have had a security event, with BEC/phishing attacks accounting for more than 50 % of those occurrences, according to 35 %. Regrettably, the rate of financial crime ( Omolara et al., 2018a , Omolara et al., 2018b ), has increased in recent times ( Achim et al., 2021 , Ünvan, 2020 , Hasham et al., 2019 , Reid, 2018 , Masciandaro, 2017 , Gottschalk, 2008 , Sakurai and Smith, 2003 ).
Financial loss is the most evident consequence of BEC fraud. Fraud is successful when the perpetrator can tailor the details of their approach to the target's individual vulnerabilities or shortcomings. To do so, criminals can extensively study the organization and its linked individuals to imitate a believable attack. Information about some organizations is freely available on the internet ( Burns et al., 2019 ). Perpetrators may gather information about an organization and its employees by using public information or infiltrating social networking platforms. Therefore, individuals, organizations and governments must begin to invest more in cybersecurity to mitigate cyber-attacks such as BEC in crisis conditions.
1.9. Distributed denial-of-service (DDoS) attack
DDoS attack is a type of attack that cybercriminals deploy to render online services unavailable to users by generating a large amount of traffic. The number of DDoS attacks has surged thrice in the last three months compared to the prior three months. The overall number of reported DDoS attacks in the first quarter of 2020 was 242, while the number grew to 300 in the second quarter ( Wu et al., 2020 , Mansfield-Devine, 2015 ). The COVID-19 crisis has resulted in a considerable increase in fraudulent behavior. Many people's lives changed dramatically, making them more vulnerable: working from home rather than in an office, balancing childcare, and being concerned about health, financial resources and the future. The healthcare industry is particularly the hardest hit by COVID-19 since it has the most vulnerable and targeted systems. For instance, attackers launched a DDoS attack against the United States Department of Health and Human Services, causing significant damage to its servers (Stein et al., 2020). More also, financial sectors, like banks are equally affected as the healthcare industries.
As more heterogeneous devices connect online through Internet of Things (IoT) devices and enterprises build remote networking systems to augment pre-existing infrastructure, it unwittingly gives room for denial-of-service attacks to escalate.
Denial-of-Service attacks increased as more devices came online and organizations speedy-up remote access for their employees. In addition, the methods used by attackers are becoming more sophisticated as information systems get more advanced and digital. As a result, criminal and nationwide actors have long valued denial-of-service cyberattacks, which may create major economic interruptions for any organization connected to the internet.
DDoS attacks that interrupt critical healthcare operations can lead to patient death. Disruption of essential care and supplies to vulnerable patients due to a DDoS attack can result in the worst outcome of a disruption of healthcare operations leading to death. When assessing potential implications on health operation services, patients admitted to hospitals in critical condition and in need of quick access to treatment, as well as the safety and integrity of surgical procedures, are highly considered to be in danger. Therefore, more research is needed to mitigate DDoS attacks, especially during a crisis.
1.10. Denial-of-service (DoS) attack
Denial of Service (DoS) attacks are a type of cybercrime that is frequently used by more technical criminals. The attacker of DoS attempts to temporarily or permanently make certain services not available to users through Internet resources, such as paying for utility, paying for goods purchased, and paying for airline tickets online. Hacking entails jeopardizing a system's confidentiality or integrity, and it necessitates a decent level of skill. Tactics may include exploiting system flaws to gain access to systems. As more heterogeneous devices connect to the internet through the Internet of Things (IoT) devices, denial-of-service cyberattacks have increased, and enterprises have bolstered remote connectivity technologies to support pre-existing infrastructure. In addition, as telework grows in reaction to the new coronavirus and initiatives to foster social separation, threat actors seek to profit from the present danger scenario.
Organizations of all sizes frequently fail to follow asset and inventory organization best practices that would allow them to gain full awareness of their attack surface. Additionally, many IoT devices use default passwords and lack solid security postures, making them open to penetration and exploitation. Users are typically unaware that IoT devices have been infected, and an attacker may simply compromise many of these devices to launch a massive attack. DoS attacks disrupt system availability by flooding important services with unauthorized requests. The purpose is to take up all of the bandwidth allocated to genuine server queries in order to bring the server down. Hence, researchers need to urgently focus on preventing DoS attacks, especially during a crisis.
1.11. Malicious websites
Any act by a malicious attacker to undermine the security of a Web-based application is referred to as a malicious website apps attack. Web application or website apps attack can either target the application itself in order to get access to sensitive data, or they can use the application as a staging area for attacks against the application users. At the pinnacle of COVID-19, the use of the web to cause harm increased dangerously. As the number of people infected with coronavirus continues to rise, so do dangerous cyber-attacks such as spam emails, phishing, malware, ransomware, and malicious domains that utilize the virus as bait ( French et al., 2021 ). As a result, businesses of all sizes are under increasing pressure to tackle the obstacles posed by Covid-19-based cyber threats.
In reality, attackers are constantly devising new ways to assault and con people to profit from the fear and uncertainty surrounding the ongoing pandemic, keeping a step ahead. According to new Malwarebytes data, web skimming increased by 26 % in March 2020 compared to the prior month of February 2020. Another interesting discovery is that the number of people skimming the internet climbed slowly from January 2020 to February 2020 by 2.5 % and then increased dramatically between February and March 2020 by 26 %. While this is still a small increase, Malwarebytes feels it indicates a pattern that will become more visible in the months ahead. Hence, to move business, the executives should plan to prioritize operational capability towards eliminating malicious websites over the next two years. Similarly, researchers need to investigate how to block malicious websites for resiliency in digital business.
1.12. Malicious domains
Malicious domains are a type of cyber security breach that poses a serious threat to people's privacy and property by delivering malicious services such as phishing websites, spam servers, and command & control servers to Internet users. Cybercriminals have been exploiting, developing, and boosting their attacks at an alarming rate, taking advantage of the anxiety and uncertainty induced by COVID-19′s precarious social and economic bad conditions. The lockdown measures had particularly accelerated the creation of malicious web domains to make fictitious and concocted money from their target ( Interpol., 2020 ). Thus Malicious websites (URLs) are used by threat actors to deceive the public, collect confidential data, and propagate malware to harm or corrupt systems and devices. A COVID-19 cybercrime assessment by INTERPOL revealed a considerable shift in target from individuals and small enterprises to major organizations, governments, and key infrastructure using malicious domains. Criminals are using new security weaknesses to steal data, create money, and cause disruption as organizations and companies rapidly deploy remote systems and networks to enable workers to work from home. One of INTERPOL's partner organizations detected 907,000 spam communicated messages, then 737 malware events, and 48,000 harmful Web links – all associated with COVID-19, over a four-month period, from January to April.
Malicious domains proliferated during the rise of COVID-19 and global lockdown countermeasures. Cybercriminals have begun registering domain names with keywords such as “coronavirus” or “COVID” to take advantage of the increasing demand for medical supplies and data about COVID-19. These phony websites support a wide range of criminal operations, such as C 2 servers, malware deployment, and phishing. A private organization partner noticed and reported to INTERPOL a 569 % increase in illegal registrations, including phishing and malware, and a 788 % increase in high-risk registrations between February and March 2020. Therefore, researchers need to focus more on how to tackle malicious domains for resiliency in digital business. Likewise, to move businesses forward, the organization’s executives must plan to prioritize operational capability toward eliminating malicious domains over the next two years.
1.13. Spam emails
Unsolicited or anonymous messages sent in bulk by email are known as email spam, sometimes known as junk email or simply spam. The name stems from a Monty Python joke in which the packaged pork product's name is mentioned. Spam is pervasive, inevitable, and monotonous. The amount of spam emails has risen by 300 times, and the number of harmful URLs has increased by 300 percent, especially at the peak of the COVID-19 crisis. The United States is the top country for spam and malware detection; most target consumers come from there (Cook, 2020). For instance, Google claims to have detected over 100 million phishing emails and 18 million daily spyware related to Covid-19 through its Gmail service. This is on top of the 240 million coronavirus-related spam emails sent daily. In addition, a study conducted by RiskIQ identified the top dangers for 2020 and found that cybercrime costs businesses roughly $24.70 per minute, while a malicious assault costs $4.95 per minute. As a result, cybercrime was forecasted to cost $11.4 million (£8.7 million) each minute globally by 2021, a 100 percent rise when relatively compared to the incidences of the year 2015.
Statistics have shown that 375 new threats of cyber-attacks are discovered every minute, and also a new vulnerability is discovered every 24 min, and more also, 16,172 records are compromised every minute. Every 16 min, there is a new Magecart cyber-attack. For example, the credit card skimmer attack vector, RiskIQ was first discovered in 2018. “The world have seen thousands of new COVID-19 domains standing up daily, ” said Steve Ginty, director of threat intelligence at RiskIQ. He stated this when asked how many COVID-19 domains they generally see in a day. Attackers usually leverage current events in their operations. Something as widespread and disruptive as COVID-19 has proven to be especially valuable to them, which is why we're seeing such a large-scale growth of COVID-19-related threat infrastructure“.
Therefore, to move business, the executives must plan to prioritize operational capability towards eliminating malicious spam emails over the next two years. Likewise, researchers need to focus more on how to address malicious spam emails for resiliency in digital business.
1.14. Browsing apps
The COVID-19 pandemic has added new complexities to constraints in marketing, advertising and selling of business (Gursoy and Chi, 2021; Boiral et al., 2021; DiResta et al., 2020). It is difficult to break through the online clutter due to cautious consumers’ opinions and a digital landscape inundated with an onslaught of news. As consumers stay at home, out-of-home marketing, advertising and selling become obsolete, and significant events are pushed back or pushed into a virtualized environment, a robust digital strategy is essential. The following use cases are gaining traction to enhance marketing, advertising, and sales for businesses:
Live transaction data, consumer intent information, usage, and other digital datasets are used in real-time churn analytics (common in B2C, increasing use in B2B).
AI-based lead creation and prioritization to find top customers and the relevant product/service requirement (B2B technology, professional services).
AI-based pricing that takes into account dynamic cost changes (labor, materials, etc), market trends (competition, sector preferences), and internal price history (B2B technology, industrial goods, and telecommunications).
Using webcasting as a vital marketing tool from home, by staff, with influencers to shift buyers online and distinguishing companies from home, through staff, with influencers, that is retail, food & beverage.
Given WFH and rising online demand, hyper-local online marketing is extremely important across sectors of businesses.
AI-assisted sales assistants assist customers who are mostly first-time buyers with buying online (retail) and a simple walkthrough of technical requirements of industrial equipment.
Therefore, research should focus on managers to plan operational ability in the direction of developing digital browsing apps towards marketing, advertising, and selling in order to take the organization forward and enhance cyber efficiency and safety for advancement in business.
1.15. Mobile apps
A mobile application, often known as an app, is a software application or computer program that runs on a mobile device such a laptop, tablet, phone, or smartwatch. Some organizations use mobile device management systems (MDMS) applications to manage their employees' mobile devices by allowing system administrators to remotely deliver certificates, programs, access-control lists, and wipe stolen devices. After a security researcher told the vendor about issues patched in July 2020, many threat actors attacked one MDM, particularly MobileIron. CVE-2020-15505 and CVE-2020-15506, two of the three vulnerabilities, were rated critical with a CVSSv3 score of 9.8. The other vulnerability, CVE-2020-15507, was given a strong grade and a CVSSv3 score of 7.5. Exploiting these CVEs would result in remote code execution, authentication bypass, and unauthorized file reading, among other security problems.
During the spike of COVID-19 and the lockdown, cyber-attackers target mobile phones. For example, the computer emergency response team of India (CERT-In). The federal organization charged with combating cyber threats and protecting India's cyber space, has published a new advisory containing over a dozen recommendations for keeping personal mobile phones safe and secure.
2. Existing work
Many aspects of life have gone online as a result of the widespread adoption of digital technologies, ranging from commerce and social connections to business, industry, and, sadly, criminality. According to the most recent reports, cybercrime is increasing in frequency and severity ( Lallie et al., 2021 , Auyporn et al., 2020 ), with a forecast of $6 trillion in revenue by 2021 up from $3 trillion in 2015 ( Adeyoju, 2019 ). It may even overtake traditional crime in terms of volume and cost ( Netherlands, 2020 ). It is apparent that cybercrime may continue due to its profitable nature ( McGuire, 2018 ) and low-risk level since cyber-criminals can launch assaults from anywhere on the planet.
Cybercrime, like traditional crime, is usually portrayed by the crime triangle ( Khweiled et al., 2021 ), which stipulates that three variables must exist for cybercrime to happen: a victim, a motive, and an opportunity. The victim is the person who will be attacked, the motive is what motivates the criminal to perform the crime, and the opportunity is when the crime will be committed. For instance, it can be an innate vulnerability in the network or an unprotected system. Other criminological models include Routine Activity Theory ( Yar, 2005 ) and the fraud triangle ( Cressey, 1953 ). Employ similar factors to characterize crimes, with some replacing the victim with the attacker's means, which can be viewed as part of the opportunity.
Phishing attacks can take several forms, including email phishing, phishing websites, and phone phishing, popularly referred to as vishing. There are various types of phishing attacks, which are; Email phishing, Domain spoofing, Vishing, Smishing, Search engine phishing, Whaling, CEO fraud, spear phishing, Deceptive phishing, Pharming attack and Malware-based phishing.
2.1. The different types of phishing Cyber-attacks
The following are the most popular types of phishing cyber-attacks. They have been used in the past and are still being used to target unsuspecting people and organizations.
Email phishing: Email phishing is a type of phishing assault. They frequently include harmful attachments and URLs that are designed to steal a victim's personal information.
Domain spoofing: In this form of phishing attack, attackers imitate prominent domains and aim to deceive users.
Vishing: In Vishing, the attacker calls the target on the phone and pretends to be someone from an organization with whom the victim is affiliated to obtain information from their target.
Smishing: Smishing is similar to Vishing; however, it occurs via text messaging.
Spear Phishing: One of the most dreaded but powerful phishing strategies is spear phishing. Instead of arbitrarily targeting people, it selects individuals, conducts detailed studies on them, and then sends phishing emails to obtain related information from an organization.
Search engine phishing: This entails constructing bogus websites and webpages that can be accessed by typing specified keywords into search engines. People rarely hesitate to enter their private details on these pages since they look completely trustworthy.
Whaling: Whaling is similar to spear-phishing in that it targets the organization's top executives rather than simply any employee. It usually targets high-profile members of a company, such as the CEO and CFO.
The Chief executive officer (CEO) fraud: is a deception in which cybercriminals spoof business email accounts and impersonate CEOs in order to dupe an accounting or human resources (HR) employee into giving out private tax information or making illicit wire transfers.
The Federal Bureau of Investigation (FBI) refers to this type of scam as “BEC,” or “Business Email Compromise.” It defines it as “a sophisticated scam targeting firms that engage with international suppliers and/or make frequent wire transfer payments.” The fraud is carried out by using computer intrusion or social engineering tactics to compromise legitimate company email accounts to make illicit financial transfers”.
Deceptive phishing: The most common phishing fraud is deceptive phishing. Fraudsters pose as a real company to obtain people's personal information or login passwords. Attacks and a sense of urgency are used in these emails to terrify recipients into doing what the attackers want.
Phishing based on malware. This technique occurs when a thief attaches a destructive computer program that appears to be useful to websites, emails, and other electronic documents on the Internet. Phishing based on malware or Malware based phishing is a form of a computer program that is also known as malware.
Phone phishing or voice phishing: is the practice of making false phone calls in order to dupe individuals into donating money or divulging personal information. It's a new label for a problem that's been around for a long time: phone scams. A common phishing method is for a criminal to pose as a trustworthy institution, organization, or government agency.
Pharming attack is a type of cyberattack in which users are directed to a false website that appears to be a genuine website. When users type in a legitimate web URL, they are led to a false website that looks exactly like the original one.
Phishing websites: A phishing website is a domain with a name and appearance similar to an official website. They are designed to deceive someone into thinking it's real. Some pointers on how to spot a phishing website include; (a) visiting the website directly, (b) avoiding pop-ups and insecure sites. (c) keeping a close eye on the URL or web address. (d) Entering a fictitious password. (e) examine the website's content and design. (f) looking at online reviews and the payment options available on a website.
2.2. A monthly cyber-attacks during the COVID-19 pandemic
On a monthly basis there are incidences of cyber-attack during the global crisis of COVID-19. These incidences of cyber-attack include phishing, DDoS, malware, ransomware, botnet, etc. A summary of monthly cyber-attacks is presented in Table 3 .
A Summary of Monthly Cyber-attacks during the Covid-19 Pandemic.
Table 3 proved that the year 2020 was a tumultuous one, with daily life disrupted and huge changes in the corporate environment, all of which were exacerbated by increased Internet fraud as a result of the COVID-19 disaster. Most organizations are more reliant on the Internet than ever because many people are working from home or relying on their digital devices to keep them connected and entertained. However, the current cybersecurity trends demonstrate that hackers are taking full advantage of these COVID-19 crisis times, wreaking havoc on different organizations and their data more than ever before. Therefore, the year 2020 has had a huge impact on the most recent cyberattacks, including deadly phishing, malware, DDoS, botnet, APT and ransomware.
2.3. Timeline of cyber-attacks related to COVID-19
The cyber-crime episodes resulting from the COVID-19 pandemic constitute a severe threat to the global population's safety and socio-economy development. Therefore, understanding their mechanics, as well as their propagation and reach, is critical. Many techniques for understanding how such events evolve have been offered in the literature, ranging from formal definitions to systematic approaches to examining the nature of threats. However, while these methods allow for the categorization of an attack, they frequently lack the ability to map bigger, spread events like the ones described in this paper when the pandemic causes a slew of unconnected occurrences.
People increasingly work from home, attend digital school, and conduct business online to prevent the spread of the Coronavirus; practically every country in the globe proclaimed a state of emergency. However, during the COVID-19 crisis, almost all economic sectors were constantly under cyber security threats. Cyber-security most affected economic sectors are highlighted and discussed in the subsection below;
2.4. Cyber-security most affected economy sectors
Hackers also use credential stuffing tactics to get access to employees' credentials, and the stolen information is again sold to other criminals in the digital black market. One of the effects is that firms that rely significantly on videoconferencing platforms will be severely disrupted. Credential stuffing is a type of cyberattack in which hackers utilize stolen login and password combinations to obtain access to all other accounts. Because it is fairly usual for people to use the same password and username for many accounts, this is conceivable. Cyber-attack most affected economic sectors are highlighted in Fig. 2 .
Cyber-attack: most affected economy sectors at the wake of COVID-19 health crisis.
The war on the digital economy during the lockdown caused by the COVID-19 health crisis cannot be over-emphasized. Therefore, cyber-attack most affected economic sectors are discussed as follows;
Financial sector
The financial industry faced numerous cyber security attacks during the COVID-19 crisis. At 5.85 million dollars, the mean cost of cybercrime in the financial services business is also among the highest of any industry ( ibm.com, 2020 , Najaf et al., 2020 , Bossler, 2021 ). It has compelled financial institutions like banks and insurance firms to continue providing online assistance to their customers. Again, the majority of employees worked from home in an insecure network. Once employees are at work, they are bound by certain security measures, which were not there before and which became the new normal practice. Employees were more vulnerable to cyber risks when using an insecure network ( Babulak et al., 2020 ). Customers increasingly rely on online banking, which exposes them to hackers. Hackers commonly target the financial sector with distributed denial of service (DDoS), phishing, and malware cyberattacks. ATM transactions ( Omolara et al., 2019a , Omolara et al., 2019b , Omolara et al., 2019c ) were visited by hackers that stole bank credit cards to withdraw money. During the Covid-19 crisis, there was an increase in credit card fraud (Zhu et al., 2021; Payne and Morgan, 2020). Therefore, there is an urgent need to protect data from intruders by developing a hybrid cipher ( Omolara et al., 2014 ) and up-to-date safe encryption algorithms to secure data in online transactions.
In the case of insurance firm cyber-attack, the Avaddon gang attacked the European insurance business AXA in May 2020. The incident occurred shortly after the corporation announced significant insurance policy modifications. In essence, AXA said it would no longer reimburse many of its clients for ransomware charges. The hacker group acquired access to a colossal 3 TB of data in this one-of-a-kind (and rather ironic) threat on a cyber-insurance corporation that made the news. Another significant insurance firm was hit by ransomware earlier in March 2020. On March 21, 2020, a hacker group targeted CNA's network, encrypting 15,000 devices, including many computers used by remote employees. The hacking group Evil Corp is suspected of being behind the attack, which uses a new strain of malware known as Phoenix CryptoLocker.
Healthcare sector
A typical computer systems shutdown case occurred at Brno University Hospital due to a cyber-attack. The Brno University Hospital, is a significant Covid-19 testing site in the Czech Republic, was one of the first medical facilities obliged to turn away patients with serious illnesses and postpone surgeries. The World Health Organization (WHO) declared that cyber-attacks surged to fivefold during the COVID-19, causing public fear. Nearly 450 functional email addresses with a WHO username and passwords were compromised in the third week of April 2020 ( World Health Organization. 2020 ). Hackers and invaders are well aware that the global healthcare system is in disarray as a result of the epidemic. Since more people use the remote care system, hackers were increasingly active in gaining access to healthcare systems all over the globe for financial benefit. Hackers attempted to gain access to a huge series of individual data and credentials of patients, according to the United States cybersecurity and infrastructure security agency and the United Kingdom's national cyber security centre ( Lallie et al., 2021 ).
Throughout the pandemic, telemedicine became the only means to receive care. The treatment has made it easier for hackers to gather the needed information from specific patients. Before the pandemic, only 95 people in New York used telemedicine on a daily basis. However, during the disease outbreak, the number of patients surged by a factor of 44.30 times, and on a daily basis, nearly 4209 people used telemedicine. Ransomware assaults have increased dramatically as a result of these staggering numbers ( Jalali et al., 2021 ). Different Cyber-attacks / data breaches in healthcare and academic organizations at the peak of the COVID-19 crisis, in Summary, is presented in Table 4 .
Education sector
Different Cyber-attacks / data breaches in healthcare and academic organizations at the peak of COVID-19 crisis in summary as reported.
The abrupt transformation induced by the COVID-19 crisis significantly impacted educational systems. Most students at all levels now rely on e-learning, putting them at risk of cybercrime. In addition, most educational institutions use applications like Zoom for their e-learning processes. However, because of the attack, for instance, some schools in California were compelled to suspend their program activities for a few periods ( Harris and Jones, 2020 ). COVID-19′s dreadful status jeopardized schooling at all levels. Education was also at risk as the pandemic spreads. Homebound students took classes through online e-tech systems, e-learning environments, and video-conferencing. Cybercriminals have hijacked video and teleconference sessions (known as Zoom-bombing) in the past to distribute unpleasant or dangerous content. Educational institutions should keep private information out of e-learning platforms. They should use a software-as-a-service (SaaS) solution rather than a local client. Furthermore, they should prevent third-party providers from having direct access, and evaluate vendors and their security documents on a regular basis.
In some countries like the United Arab Emirates (UAE), e-learning tools were deployed in higher education. For example, UNESCO supplied a variety of distant learning resources to assist many schools and organizations in adjusting to continuing their work during COVID-19 ( UNESCO, 2020 ). Popular applications utilized to deliver lecture include WebEx, Zoom, Google Classroom, Ultra Collaborative, Skye, Blackboard Learn, GoToMeeting, Monitor Lockdown Browser, Respondus, amongst others. There are also many occasions where academic and non-academic staff and students communicate via social media platforms like Facebook, YouTube, WhatsApp, and others that offer online services that were used to promote education during the COVID-19 pandemic crisis. Thus, expert-led online courses were made available in English, French, Spanish, Italian, Portuguese, and other languages during the COVID-19 crisis.
Military sector
A coronavirus-themed malware has been reported to overwrite a computer's Master Boot Record (MBR), rendering it unbootable. “Coronavirus Installer” is written in the malware file's description. Thus, the Covid-19 crisis and lockdown regulation was used as a trap by another Coronavirus-themed malicious HTA file (HTML executable file). It is most likely from the infamous SideWinder organization, which is known for targeting military targets. A pop-up PDF enticement with click-bait headlines and photographs of the Pakistan army is included in this HTA file. The CEOs and top executives of energy providers face a unique set of cyber and safety threats. Employees who use their residences to access crucial plant production and grid networks increase the likelihood of a second-wave crisis; rolling power outages and safety occurrences parallel when keeping the electricity or lights on is critical. The rush to remote systems, understaffed facilities, and new working modes will be exploited by attackers.
Energy sector
In the energy sector, in times of crisis, such as COVID-19, the focus is on how to protect the public and how to maintain power flowing to customers. Working remotely is the most important priority for utility companies, but this fact also exposes the energy business to threats from inside and outside its cyber defenses. Energy companies must protect their employees and concurrently avoid outages since lives are on the line. Energy companies are facing new cyber-risks as a result of remote working. Attackers will look for new weaknesses in an energy's infrastructure to exploit. Utilities are fundamentally changing their power generation workflows, and cybersecurity approaches and structures will need to be updated as well. New operational models will be required for distributed energy sources. Likewise, remote work and automation will boost productivity. Energy businesses will have to educate and train the next generation of workers. The frequency and sophistication of cyberattacks against electricity will continue to rise. As each trend forms the new reality, electricity companies will need to iteratively update cybersecurity policies to protect operations. Then keep the lights on both in the short, middle and long term.
The hack of Colonial Pipeline in late April received the most media attention of all the cyber and ransomware assaults in 2021. “The Colonial Pipeline attack had such an impact because the pipeline is an integral part of the national critical infrastructure system,” says Joe Giordano, director of Touro College Illinois' Cybersecurity Program. Gas supplies were disrupted all along the East Coast of the United States as a result of the system's downtime, producing confusion and panic.“ Due to the fact that most Americans are directly affected by gasoline shortages, this strike touched close to home for many people. The attack was carried out the DarkSide gang, which targeted the company's billing system and internal business network, causing major shortages across many states. Colonial Pipeline finally caved in to the cyber-attacker's demands and paid the group $4.4 million in bitcoin to avert additional disruption. Luckily, much of the $4.4 million ransom collected was recovered by US law enforcement. The money was traced thanks to the FBI's monitoring of bitcoin transactions and digital wallets.
Manufacturing sector
If manufacturing sectors were under the impression that they were protected from cyberattacks, that belief is gradually disproving, especially in 2020. In the years 2017 and 2018, more people became cognizant of Industry 4.0 and the rise of cybercrime. However, many companies in the sector were completely uninformed of the risks. By 2019, the manufacturing industry had risen to the eighth most targeted sector by cyber criminals. Due to the pandemic restrictions, many organizations were compelled to rely nearly entirely on remote labor in 2020, which exacerbated the problem. While most of the world was unprepared for COVID-19′s impact, cyber attackers were prepared. The industrial industry has slipped from eighth to second place in terms of cyber-attacks. Monitoring the company's network ecosystem for anomalies is highly significant in protecting against cyber-attack. Some security procedures are impossible to implement when working from home during the COVID-19 crisis. For example, both legitimate and illegitimate directives came from outside the company. It is difficult to tell what they are and their intention. As a result, monitoring becomes even more important to distinguish between attackers and employees.
Some monitoring and surveillance can be automated, allowing relevant employees to spend more time investigating suspected activity. Nevertheless, the threat to the nation's essential infrastructure and government organizations has not flown under the radar. Public institutions such as government parastatals are beginning to implement stronger restrictions for corporations that secure sensitive data, despite their poor response to cyber threats in the past. The Cybersecurity Maturity Model Certification and the IoT Cybersecurity Act were introduced in 2020 as ways to implement minimal cybersecurity rules for enterprises that deal with government organizations. Even so, the full impact of these laws will not be felt until 2022 or 2026. Meanwhile, cybercriminals will continue targeting organizations that have ignored warnings and failed to implement cybersecurity solutions.
However, there is just one answer for industrial companies looking to avoid risks. They need to learn about the potential cybersecurity risks for manufacturing companies and how to create a comprehensive cybersecurity solution to identify and prevent attack vectors before they breach the company network.
Technology sector
The year 2020 and 2021 are years of the top significant data breaches ever globally. These breaches badly affected technology industries (information technology) such as Google, Twitter, Zoom, Amazon, Finastra, CDProjekt Red, SolarWind supply chain, etc. On its Chrome update page, Google stated that it is aware of exploits for two vulnerabilities, CVE-2021–38000 and CVE-2021–38003. However, both issues have been resolved, but only if Chrome users upgrade their browsers. “The Stable channel has been updated to 95.0,” Google verified the upgrade. Some well-known and well-respected Twitter accounts were hacked and exploited to spread false information about Bitcoin. The accounts asked for Bitcoin from their followers in exchange for a double reward. Despite the tweets being only active for a brief period, they made more than $100,000 in Bitcoin. Those who were tricked into transferring Bitcoin got nothing in return.
Zoom moved from a little-known boutique business to one of the most well-known and frequently used videos and audio conferencing systems almost overnight because of the quick increase in individuals working from home due to COVID-19. In Q2 2020, it had a factor of 3.55 times increase in revenue year over year. With such rapid expansion, Zoom had multiple security incidents, the most notable of which was the sale of over 500,000 user accounts on a dark web forum. According to reports, the accounts were accessed by utilizing user IDs and passwords that had previously been exposed in other breaches, a practice known as credential stuffing.
Finastra, a provider of software solutions company to financial institutions in many parts of the world, notably 90 of the top 100 banks, was hit by a ransomware attack that interrupted operations and forced the company to temporarily isolate compromised servers from the world wide web. Finastra has the US $1.9 billion in revenue, 9,000 + employees, and about 8,600 customers, with a global footprint and a broad set of financial technology products. Finastra likely have been a victim because of a history of issues pertaining to obsolete security practices and devices, like having four Citrix (NetScaler) servers vulnerable to CVE-2019–19781 operating in early January 2020, according to Bad Packets. This company monitors and helps in identifying cyber-security threats. Finastra said it employed “isolation, inquiry, and containment” to bring the case to court.
Other attacks were launched on CDProjekt Red, a well-known videogame studio in Poland. The HelloKitty gang hacked the company in February of this year. The hacker group gained access to source code for in-development games as well as encrypted gadgets. CDProjekt, on the other hand, has declined to pay the ransom and has backups in place to salvage the lost data.
In April 2020, REvil gang requested a $50 million ransom from computer manufacturer Quanta, similar to the Acer computer hack. Although Quanta is not a household name, it is one of Apple's most important business partners. REvil went after Apple when the company declined to negotiate with the hacker organization. They threatened to reveal more sensitive documents and data after disclosing Apple product blueprints taken from Quanta. REvil seems to have halted the offensive by May.
The biggest cyberattack in the year 2020 was the SolarWind supply chain attack that affected prominent private companies, including Microsoft, FireEye, Cisco, and NVidia, as well as multiple United States government organizations. Additionally, Amazon was the target of a massive DDoS attack by attackers.
Tourism sector
Marriott hotel disclosed that personal information of about 5.2 million hotel guests was improperly obtained in 2020, marking the company's second major data breach in less than two years. Marriott is one of the leading hotels, with 7,300 hotel and resort locations in 134 countries. The visitor information was hacked in mid-January using login credentials from personnel at a franchised location, according to the firm, which was notified at the end of February 2020. Marriott has deactivated those logins and is cooperating with investigators. However, according to a statement, Marriott claims that the data breach did not affect their Marriott Bonvoy account passwords or PINs, emails, passport information, credit card information, address, and driver's license numbers.
Food and Agricultural sectors
Ransomware victims in the food and agriculture sector face enormous financial losses as a result of ransom payments, lost output, and remediation costs. Companies may potentially lose proprietary data and personally identifiable information (PII) as a result of a ransomware assault, as well as suffer reputational damage. For example, JBS S.A., a Brazilian meat processing corporation, was hit by a cyberattack on May 30, 2021, rendering its pork and beef slaughterhouses inoperable. Facilities in Australia, the United States, and Canada, were all hit by the attack. A ransomware attack on an unidentified US farm in January 2021 resulted in a $9 million loss because of the temporary closure of their farming operations. The identified adversary targeted their internal servers by getting full administrator access via hacked credentials. In another incidence, a United States bakery firm lost access to its server, data, and apps in July 2021, disrupting production, shipping, and receiving (MSP) due to the Sodinokibi/REvil ransomware attack. The ransomware was delivered using software used by an IT support managed service provider. The bakery was closed for about a week, causing delays in customer orders and ruining the company's reputation.
In the case of agricultural farm cyber-attacks, for example, a popular agricultural farm in the United States lost $9 million in productivity after being forced to shut down due to a ransomware threat. It is ultimately up to the firm whether or not to pay the ransom, but it is crucial to note that paying does not mean the problem is solved. According to the FBI, up to 80 % of ransomware victims who paid the blackmail experienced a repeated attack, either from the same criminals or from a new group, after paying the ransom. Likewise, Australia's agricultural business faced cyber-threat according to a new AgriFutures Australia research that examines the cyber hazards following two major cyber assaults in the last 12 months. Most rural agricultural industries that fail to protect themselves from cyber threats endanger not only themselves but also Australia's food security.
Transportation sector
The number of ransomware cyberattacks is rising across all industries, but the transportation industry appears to be the hardest hit. Transportation organizations are more adversely affected by the global cybersecurity gap than others because they have not traditionally deployed significant security teams to defend their digital assets. According to Cybertalk.org , the transport sector saw a 186 % spike in weekly ransomware attacks between June 2020 and June 2021. For example, new York's Metropolitan Transportation Authority (MTA), North America's largest transportation network, had been targeted by a cyber-attacker, according to sources in June 2021. Downstate New York is served by the MTA, as are two counties in southwestern Connecticut. The transportation system handles about 11 million passengers on weekdays, and over 850,000 automobiles pass through the MTA's seven toll bridges. The MTA’s network cyber-incidence was reportedly perpetrated by the Chinese attackers that allegedly used a zero-day vulnerability in a remote access product from Pulse Connect Secure.
Commerce sector
The demand for goods and services has shifted to e-commerce. While the number of e-commerce in total retail in the United States climbed modestly from 9.6 % to 11.8 % between the first and second quarters of 2020, that is, from 9.6 % to 11.8 %, it jumped to 16.1 % between the first and second quarters of 2020. The trend in the United Kingdom is similar: between the first quarter of 2018 and the first quarter of 2020, the share of e-commerce in retail increased from 17.3 % to 20.3 %, before increasing dramatically to 31.3 percent between the first and second quarters of 2020. Similar trends can be seen in other places, such as the People's Republic of China, in which the share of online retail sales in cummulative net retail sales increased to 24.6 % from January to August 2020, from 19.4 % in August 2019 and 17.3 % in August 2018.
3. Methodology
Methodologically, this study started by looking for articles that looked at the overall ontology between COVID-19 and cybersecurity. Then, it was narrowed down to articles that looked at each affected economic sector, such as finance, healthcare, education, military, energy, manufacturing, tourism, technology, transportation, commerce, food, and agriculture. It searched various databases for papers connected to coronavirus OR COVID-19, including Science Direct, IEEE Xplore, Springer Link, PubMed, Willey, Emerald insight, Elsevier, and others, between March 2020 and December 2021. The period under review was the peak period of the COVID-19 incidence. Thus, we explore literature for material that had been published regarding cybersecurity issues in organizations during the lockdown, movement restriction and COVID-19 crisis. However, this study eliminates any epidemiological articles and research that were replicated.
We used 300 articles covering a wide range of economic sectors mentioned earlier. It also encompasses changes in consumer behavior and business practices, employees, managers, ethical issues, and policy-related challenges. The goal of this study was to learn how organizations reacted during the outset of the COVID-19 pandemic, identify cyber-attacks, and analyze them in order to provide solutions based on best working and management practices. It delivers the following answers to the research questions: What is the impact of the COVID-19 epidemic on organization cybersecurity? What are the best cybersecurity techniques that corporations utilize for early pandemic response? How can organizations deal with a cybersecurity problem during a crisis?
Based on a scoping examination of relevant literature published on the subject, this research aimed to analyze the cybersecurity problems faced by various organizations. That is, published articles in journals, letters, newspapers, and magazines between March 2020 and December 2021. A scoping review, rather than a systematic review, is better for fast covering of broader subjects from publications with a variety of study designs without judging the quality of the studies considered (Arksey and O'Malley 2005). This strategy is also well suited to examining new challenges and informing policy changes (Colquhoun et al., 2014; Kastner et al., Peters et al., 2014). Therefore, the approach developed by Arksey and O'Malley was also applied in this study, which consists of five steps.
3.1. Identifying relevant articles
Two complementary search strategies were utilized to find relevant published articles; from mid-March 2020 to December 2021, a state-of-the-art examination of reports was conducted. Search engines: The table and timeline were created using a variety of search engines. These search engines were Google, Baidu, Yahoo, Qwant, DuckDuckGo, Bing, AOL., Ask.com , and Excite. Likewise, we utilized Search engines for research such as Google Scholar, Educational Resources Information Center, Microsoft Academic, Worldwide Science, Wolfram Alpha, and Refseek.
Keywords utilized: When compiling cyber-attack reports, a number of keywords have been used. The Google translation tool was utilized to translate non-English phrases (Google Translate, 2020). Additionally, independent sources were employed to validate the translation ( Prates et al., 2020 , Suhono et al., 2020 ). The criteria for locating reports have been established and presented in a manner comparable to existing evaluations in the cyber security literature. A search was conducted in the English language using the Eureka database, which specializes in print media, using the following keywords:
“COVID-19 OR coronavirus,” “Organization and Cybersecurity” OR “Companies and Cybersecurity,” “SME and Cybercrime and COVID-19″ OR ”business and Cybersecurity or COVID-19,“ ”manager and employee and COVID-19 and Cybercrime“ OR ”COVID-19 and Cybercrime,“ ”COVID-19 and Cybercrime,“ Second, using the same terms, a Google News search was run to find other relevant articles. The first search results returned 4,874 potentially relevant articles. However, 3,012 of them were irrelevant, while 1,862 were included. The articles were examined again, and 1,102 duplicates were found. The methodical screening was the third step. The methodological screened number was 760. As a result of the methodological screening, 460 articles were found to be irrelevant for the study, and the final excluded articles were 60 because they were epidemiological studies. Therefore, 300 articles were found to be relevant for the study, as shown in Fig. 3 .
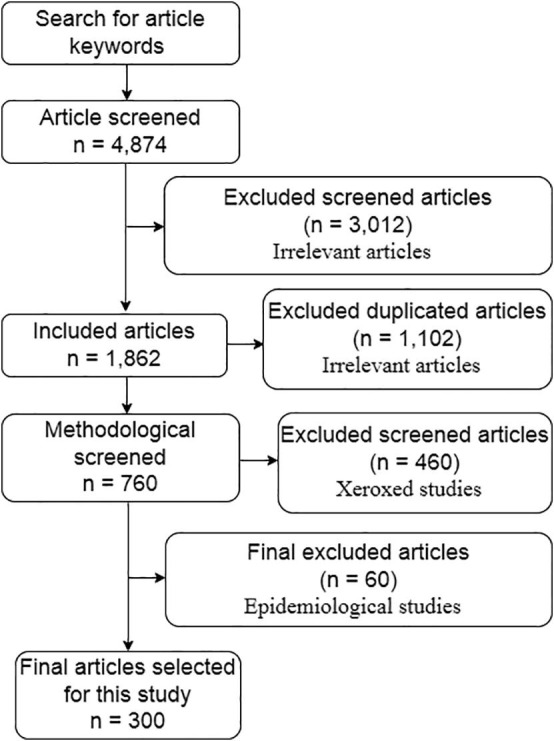
Shows the screening and selection procedure for the articles.
3.2. Selecting relevant articles
The exclusion and inclusion criteria were created to aid in removing articles unrelated to the core study issue of analyzing the best practices used by organizations to manage the COVID-19 pandemic. Articles in the research describe corporate policies implemented expressly to address the COVID-19 crisis, focusing on North America, Europe, South America, Australia, Africa, and Asia. Furthermore, in order to be considered for the study, the article had to provide at least one concrete example of an organization's behavior, as well as the organization's name. Articles that only discussed broad corporate, social, or political topics or examined management perspectives on COVID-19-related issues were omitted. Finally, 60 articles were removed throughout the selection process, while 300 relevant articles were included out of 4,874 evaluated.
3.3. Selection criteria
The articles discussed in this paper are all mentioned in the 'References' section. Meanwhile, exclusion and inclusion criteria for reviewed articles are described in Table 5 .
Study exclusion and inclusion criteria.
3.4. Data visualization
The data was analyzed and a data extraction grid was created using Microsoft Excel. Then, the sheet was divided into six sections: (i) general characteristics; (ii) design and (iii) cyber crisis impacts; (iv) organizational techniques for cybersecurity management practices; (v) organizational methods for cyber-attack management; and (iv) preventive measures. Likewise, several articles were analyzed to develop the first draft of the list of cyber-attack types in the study.
3.5. Getting information, processing, and reporting
Meanwhile, an online questionnaire was taken to address the cybersecurity issues in many types of attacks. Then, 900 organization executives responded to the online questionnaire plan to prioritize operational capabilities to address the cybersecurity issues in many types of attacks. The information gathered from the corporate executives was analyzed. In the following sections, figures and tables were developed to reveal the study's primary findings. The percentage of articles discussing a given item under each category was also assessed, and the results are presented in the Figures and Tables in the next section.
4.1. Result on the number of articles processed in the study
The article mapping gives an overview of the topic's publications, notably in terms of organizational cybersecurity challenges during the global Covid-19 crisis. The article's goals and emphasis on specific subjects, most notably business sustainability, are also important considerations. The examination of the sectors covered in the articles reveals a diverse variety of activities and organizations involved in managing the COVID-19 problem and cybersecurity issues, as shown in Table 3 . The analysis also highlights the crisis' breadth, as it impacts all sectors of the economy. The result of the number of articles processed in the review is summarized in Table 6 .
Result on the number of articles processed in the study.
Thus, Table 6 highlights the number of papers studied. After filtering and subsequent selection, three hundred (3 0 0) articles have been surveyed.
4.2. Result based on the percentages of screened and selected articles
The study removed 4,874 articles and 4,574 articles throughout the selection process. In comparison, 300 relevant articles were included, thus, accounting for 6 % of the included articles and 94 % of excluded articles, as shown in Fig. 4 .
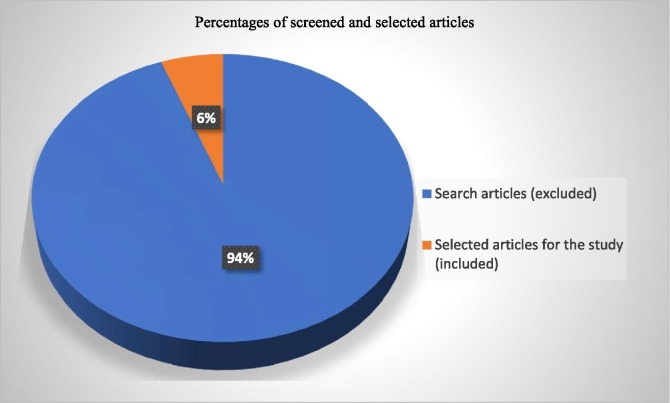
Percentages of Included and Excluded Articles in the Study.

4.3. Results based on the types of cybersecurity questionaries’ to participants’
The cybersecurity questionaries’ to participants’ was based on providing enough cyber threat knowledge. Every-one needs to be aware of the cyber security attack and risks in today's world. However, most people are uninformed of this issue, and many are unaware of the potential cyber risks. This is creating a vacuum in terms of preventing cyber-attacks, and cyber criminals are seizing the opportunity to further their nefarious goals. On a hundred persons, a survey was conducted to assess their understanding of cyber dangers. The outcome is displayed in Table 7 .
Result of the survey based on the types of cybersecurity questionnaires to the participants.
Given the survey results in Table 6 , it is evident that the majority of people are unaware of these issues, making it necessary to educate digital users on cyber insecurity. Users' awareness of cyber-security issues is urgently required to enable them protect and secure sensitive details in their devices. Likewise, organizations should prepare to educate their employees on cyber security problems by conducting training or workshops regularly. The government and agencies should provide similar training regularly for public consumption on radio and television. Furthermore, banks should help their customers take precautions against cyber criminals through constant text messages. To avoid losing their personal or organizational information, the general public should endeavor to gain a basic understanding of cyber security concerns and practise safety measures suggested by experts.
4.4. The background of the participants
Executives of organizations were among the respondents to the online questionnaire on plans to prioritize operational capabilities in order to address the cybersecurity challenges in many types of attacks. The analysis of the characteristics of the survey is shown in Table 8 .
Result of characteristics of the survey.
Table 8 reveals the background of the participants in the survey. Generally, there are more male participants than their female counterparts. The number of males accounts for 61 %, while that of females accounts for 39 %. The age group between 18 and 30 have the least participants, accounting for 10 %. However, the age group between 56 and above has the most participants, accounting for 30 %. The highest level of educational qualification of the participants was master’s degree. But it was interesting to know that many of them are graduates and some participants have obtained doctorate degrees. Experts and non-experts in cybersecurity both participated in the survey. However, it was observed that cybersecurity experts are business executives with significant numbers who made valuable contributions to the validity of this study.
4.5. Result on economic sectors and number of articles reviewed in percentage
Several economic sectors hit by the pandemic have been identified in the literature and by online interaction with the organization executives for the period under study, that is, from March 2020 to December 2021. This study explores the business types affected and the number of articles in percentage is presented in Table 9 .
The result on the economy business sector and the number of articles reviewed in percentage.
Table 9 revealed the main sectors of the global economy affected by cyber-attack during the COVID-19 crisis. The number of articles reviewed in percentage was calculated as follows; Finance (14 %), Healthcare (13 %), Information technology companies (12 %), Manufacturing (11 %), Transportation (10 %), and Education (9 %). Others include Energy (8 %), Food and Agriculture (7 %), Tourism (6 %), Commerce (4 %), Military (3 %), and Other sectors (3 %). The sudden lockdown of these industries for months has adversely affected their operational capabilities, but they have had to adjust rapidly, especially by creating telework, online sales, and delivery services.
4.6. Result of the number of articles reviewed continentally and their percentages
This coverage on specific continents was due largely to the inclusion and specific criteria for the articles, specifically in terms of English language online contact. Notwithstanding, approximately-one-third of the articles had a global outlook and focused on measures put in place against cyber-attacks by big organizations and businesses in different countries or on the worldwide platform.
The articles primarily covered continent by continent and are arranged in alphabetical order: Africa, Asia, Australia, Europe, North America, and South America. The continental distribution of the organizations cited in the articles is shown in Table 10 .
Alphabetical order of continents, number of articles reviewed and their percentages.
Furthermore, the number of articles in percentage per continent is highlighted in Fig. 5 .
Percentages of continental distribution of the organizations cited in the articles.
Fig. 5 reveals the percentages of continental distribution of the organizations cited in the articles. North America top the number of articles studied with 28 %. The next is Europe-based articles with 23 %, then Asia with 19 %, Australia with 12 %, Africa with 9 %, and South America with 9 % respectively.
4.7. Result of some cyber-attacks reported cases during the Covid-19 pandemic per month
A result of some cyber-attack cases reported globally during the COVID-19 pandemic between March 2020 and December 2021 can be presented in Table 11 .
Result of some cyber-attack cases reported during the Covid-19 pandemic per month.
Furthermore, the result of some cyber-attack during the COVID-19 crisis, as highlighted in Table 10 , between March 2020 and December 2021 is clearly shown in Fig. 6 .
Cyber-attacks during the COVID-19 crisis between March 2020 and December 2021.
Table 9 and Fig. 6 revealed that cyber-attacks on the global economy were severe in certain months within 2020 and 2021. For example, cyber-attacks were severe between April and July 2020 and then slowed down from August to November but rose again in December of that year. In the following year, 2021, it became severe in January and February, then slowed down in March but rose again in April and May. Then, it slowed down gradually between June and September, then picked up again in October; and finally slowed down in.
4.8. Result of the respondents to the questionnaires on the main types of cyber-attack experienced during the COVID-19 crisis
This study explored the types of cybersecurity problems encountered at the wake of the COVID-19 crisis and analyzed the frequency of cyber-attack obtained from the respondent questionnaire. The analysis results are as follows: Malware was 7 %, phishing was 7 %, ransomware 2 %, distributed denial-of-service 6 %, browsing apps 6 %, malicious domains 9 %, denial-of-service 10 %, mobile apps 8 %, and malicious websites 10 %. Others are spam emails, capped at 13 %, malicious social media messaging 6 %, business email compromise at 4 %, APT at 1 %, Botnet attack at 2 %, and hacking attacks at 37 %. Therefore, the main types of cyber-attack reported, their frequency and percentages at the peak of the COVID-19 phenomena are summarized in Table 12 .
Results on the main types of cyber-attacks, frequency of attack and percentages between March 2020 and December 2021.
Thus, organization executives look forward to prioritizing operational capabilities in cybersecurity and IT resiliency to boost business in diverse areas, as well as to increase profit. Even though many cyber-attack prevention mechanisms have been implemented, attackers often come up with some out-of-the-box scheme that can attack the network at all times. Some of the negative repercussions of falling victim to cyber-attacks include; (i) identity theft (ii) financial losses (iii) ransomware attack (iv) network slowdown (v) communication breakdown (vi) data loss breakdown (vii) data leak (viii) information breach (ix) network breakdown (x) loss of customer (xi) business bankruptcy and failure, etc.
Many types of cyber-attacks that occurred during the COVID-19 crisis were analyzed, and the result is presented as follows;
4.9. Result on the types of most common cyber-attack between March 2020 and December 2021
Different organization executives responded to the online questionnaires, which investigated the plan to prioritize operational capabilities in addressing cybersecurity issues in the next two years. The questionnaire’s data was evaluated and the result was obtained. About 900 organization executives were contacted online to answer questionnaires designed on plans to prioritize operational capabilities to address the cybersecurity issues in the next two years. Interestingly, a large proportion of them responded. That is, 895 out of 900 organization executives responded to the online questionnaire plan to prioritize operational capabilities to address the cybersecurity issues in many types of attacks as listed in Table 13 .
Result of the number of organizations' executives plan to minimize certain types of cyber-attacks in the next two years.
895 out of 900 organization executives that responded to the online questionnaires planned to prioritize operational capabilities to address the cybersecurity issues in many attacks, as listed in Table 13 .
Table 13 was further analyzed to produce a graph for more clarity. Therefore, organizations' executives planning to curb certain types of cyber-attack in the next two years was in the following hierarchical order as presented in Fig. 7 .
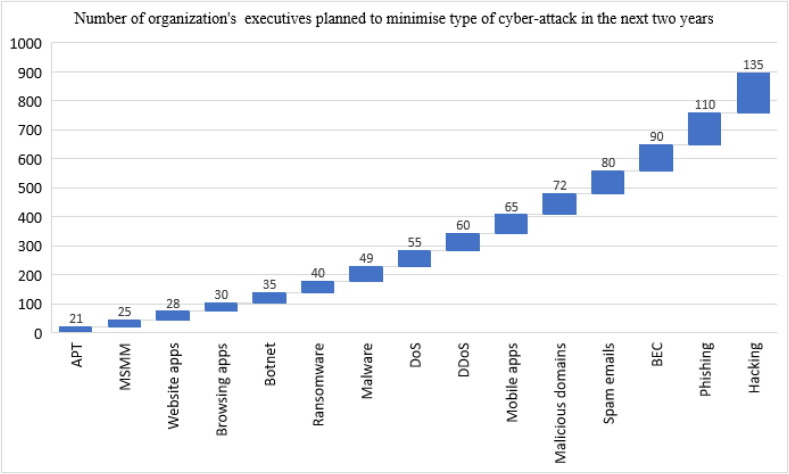
Number of organization executives planned at minimizing difference cyber-attacks to advance ICT resilient.
Fig. 7 demonstrates that business executives plan to prioritize operational capabilities in cybersecurity to advance ICT resilience, sustain business and maximize profit. According to the analysis of the collated questionnaire, about 135 respondents out of 900 business executives that participated in the online interview planned to mitigate cyber-hacking in their organizations. In contrast, 110 business executives want to focus on reducing cyber-phishing that affected their operations during the COVID-19 crisis. Meanwhile, 90 business executives want to concentrate on tackling business email compromise (BEC) attacks that paralyzed business activities in their organization during the COVID-19 crisis. Moreover, 80 business executives want to address the issue of spam emails that are predominant in their organization’s network during the COVID-19 crisis. Likewise, 72 business executives promised to eliminate common malicious domain network attacks that have beclouded their organization’s cloud computing.
Similarly, 65 business executives vow to stop malicious mobile apps causing vulnerability in their organization’s Internet infrastructure. DDoS and DoS are other cyber-attacks that 115 business executives planned to extenuate within the next two years. Malware is a deadly type of cyber weapon that 49 business executives plan to palliate in their different organizations over the next two years. Ransomware is also an exploitative type of cyber-attacks that 40 business executives are planning to counter in their organizations within the next two years. Finally, botnets are a dangerous type of cyber-attacks that 35 business executives planned to mitigate in their various organizations in the next two years. Interestingly, 30 business executives wanted to resolve the problem of malicious browsing apps, and 28 planned to prioritize operational capabilities to curtail vulnerable website apps.
Moreover, over the next two years, 25 organization executives planned to handle malicious social media messaging (MSMM) troubling their digital network. Furthermore, 21 business executives seek to address the challenges of APT attacks in their organizations in the next two years.
4.10. Result on types of most common phishing attack
Many types of phishing attacks that occurred at the peak of the COVID-19 crisis were analyzed, and the result is summarized in Table 14 .
Types of phishing attacks between March 2020 and December 2021.
Although many email phishing prevention mechanisms have been implemented, attackers often come up with some out-of-the-box email phishing scheme that manages to mislead people at all times. The following are some of the negative repercussions of falling victim to phishing emails: (i) identity theft, (ii) financial losses, (iii) ransomware attack, (iv) economic slowdown, and (v) communication breakdown.
Therefore, the types of phishing attacks that occurred throughout the epidemic and their percentages are depicted in Fig. 8 .
Various Types of Phishing Attacks.
Therefore, the various types of phishing attacks that occurred throughout the epidemic, as well as their percentages, is presented in Fig. 8 . According to the data breach investigations report, one out of every 14 people clicked on a link or opened an attachment in a phishing message. Likewise, a report from the BBC news on April 13, 2020, focused on how hackers are preying on Covid-19′s fears, as phishing emails were discovered and used in French, English, Italian, Turkish, and Japanese to attack people. As a result, individuals, as well as businesses such as aircraft, transportation, manufacturing, hospitality, healthcare, and insurance, are being targeted by cybercriminals. In addition, security experts noted that an increase in email frauds tied to the coronavirus is the worst in recent years.
4.11. Result of the main objectives of the articles reviewed
The main objectives of the articles reviewed can be summarized with analyzed results. The result of the main objectives of the articles reviewed can be summarized as depicted in Table 15 .
Result of the main objectives of the articles reviewed.
5. Discussion
The goal of this study was to examine the effect of cybersecurity on organizations during the global COVID-19 crisis using a scoping review of relevant articles published on this topic in journals, conferences, magazines, media broadcasts and newspapers between March 2020 and December 2021. The study's analysis of the 300 articles provides the challenges faced by organizations, companies, small and medium scale (SMEs), as well as a global view of the major initiatives in this new and unusual situation, which frequently calls into question the possibility of “business as usual” and may even threaten companies' survival.
The article contributes significantly to the emerging literature on pandemic management in organizations. To our knowledge, it is the first systematic study of the practical measures implemented by businesses during the pandemic, based on a large number of concrete examples. The current literature on the COVID-9 crisis is based on health and medical rather than a business managerial perspective, and studies focusing specifically on business are still few. These studies tend to concentrate on specific industries and economic sectors, such as finance, healthcare, education, manufacturing, transportation, IT, energy, commerce, tourism, etc.
The data was generated from the global survey through online contact and responses, especially from the distinct organizations and business executives, revealed differences in cyber-attack techniques. After evaluation, the result showed that hacking attack was most frequent, with a record of 330, accounting for 37 % of the overall attacks. The second was spam emails with an attack frequency of 250, which account for 13 %. The third was Malicious domains, with 168 attacks accounting for 9 %. Finally, mobile apps with 150 attacks accounted for 8 % of the total attack, as earlier presented in Table 2 . However, APT attacks recorded 2 % as the least common type of attacks leveraged during the global COVID-19 crisis for the period under study.
In general, 99 % of organizations and their executives intend to prioritize cybersecurity over the next two years. However, 15 % of organizations and their executives intend to focus on reducing hacking attacks, which were most frequent in the period under review. Then, 12 % of the respondent vowed to concentrate on reducing Phishing attacks, and 10 % set priority on BEC attacks. Next was spam emails with 9 %, which executives intend to reduce, followed by Malicious domains 8 % which they planned to minimize as presented in Table 8 . However, 2 % are ready to minimize APT attacks in the next two years. In the future, the organizations and their executives equally plan to use artificial intelligence to improve cybersecurity. Therefore, it is not surprising that the hacking rate was the highest type of cyber-attacks, which organizations and their executive priority is built upon in the next two years.
Similarly, 27 % of the respondents believed that email phishing was the most common among different phishing attacks and must be most critical. Mobile phone phishing was also found scary with 14 %, Domain spoofing and Website phishing attacks were each 10 %. However, search engine phishing and whaling recorded 5 % as the least common type of phishing threats during the global COVID-19 crisis for the period under study. A summary of implications, future research issues, and actionable insights of COVID-19 and cybersecurity is presented in Table 16 .
COVID-19 and the Cybersecurity: A Summary of Implications, Future Research Issues, and Actionable Insights.
6. Solution to the identified cybersecurity challenges
(i) Phishing: When malicious communications pass via the computer, anti-spam software and anti-phishing security can be employed to protect users. Other forms of threats are protected by anti-malware. anti-malware software, like anti-spam software, can be designed by software security experts to detect even the most evasive malware. Phishing is the leading cause of all cyber-attacks, and it continues to be one of the easiest ways to steal sensitive information and spread malware. MetaPhish, on the other hand, was built to provide an effective defense against these threats and allow businesses to determine how vulnerable they are to phishing.
(ii) Malware: Installing anti-virus software is one of the most fundamental strategies to protect against malware. Anti-virus software can safeguard valuable devices against harmful viruses that could compromise the system. It will run a scan on the computer to detect and remove malware such as viruses, as well as give automatic updates to improve protection against newly generated malware or viruses. Likewise, purchasing software applications from reputable sources reduce the risk of malware infection on the device. Big companies will take great care to avoid tarnishing their reputation by disseminating malware. One may verify a source's validity by looking at the entire name, list of published apps, and contact information in the app description on Apple or Google Play. The Malwarebytes Threat Intelligence Team (MTIT) needs to keep an eye on the threat landscape, especially for attempts that try to capitalize on the public's concern over the COVID-19 problem.
(iii) DDoS: Distributed denial of service (DDoS) attack prevention solutions can help protect IT infrastructure. Multi-level protection techniques are also required for computer networks and applications. This could include DDoS prevention management systems that include firewalls, content filtering, anti-spam, VPNs, and other security layers to monitor malicious activities and identify traffic anomalies.
Primary technical tools used to mitigate DDoS attacks are (1) Loading scripts onto load balancers to filter malicious traffic, (2) Web Application Firewalls, (3) Third-party BGP-based scrubbing, (4) Third-party DNS-based scrubbing, (5) Network blocks based on Layer 3 or 4 characteristics, (6) Upstream Filtering, (7) Connection rate-limiting, (8) Blackhole and sinkhole routing, (9) Packet/Session Time-to-Live (TTL) Restrictions and (10) Protocol/Port Filtering.
Operational control to mitigate DDoS attacks: The following operational controls should be employed to prevent DDoS attacks. (1) Attribution – organizations should engage their law enforcement partners and work with them during DDoS botnet takedown missions, which will increase understanding of adversary TTPS and aid in preventing future attacks.
(2) Lessons learned – organizations should prepare a detailed post-incident report, discuss lessons learned, and update incident response plans as necessary. Furthermore, lessons learned from the DDoS attack should be used to legislate on cyber-crime.
(iv) DoS: Firewalls are effective in preventing DoS attacks because they can help block the offending internet protocol (IP) addresses or the ports the adversary is attacking. However, this has the disadvantage of preventing genuine queries through those ports. Intrusion prevention systems (IPS) detect and refuse non-legitimate server requests. Another DoS attack prevention strategy is to scan the hard drive to detect Trojans on network connections and backdoors, as well as, educate users about the dangers of installing unknown software.
(v) Malicious Social Media Messaging: To avoid being hacked on social media, it is crucial to be aware of what is available to the general population on phone. Examine one’s privacy options. Strangers should not be accepted as friends. There should be caution when checking in or sharing one’s whereabouts with others. Tags for Personal review information should not be shared over the internet. Anything you would not want others to see should not be shared.
(vi) Hacking: Hackers masquerading as the world health organization (WHO) send messages to people's emails that an attached file explains how to stop the sickness from spreading. They say that “one small measure can cure the infected person.” However, according to Proofpoint, the email attachment contains no relevant information, and instead, it will infect personal computers with malicious software known as AgentTesla Keylogger. AgentTesla Keylogger could record every keystroke and send it to the attackers, allowing them to track their victims' online activities. Therefore, to prevent falling victim to this kind or other variants of such scams, users or organizations must be skeptical of emails purporting to come from WHO, as they are sometimes fraudulent. Instead, users or organizations are advised to go to the organization's official website or social media outlets for the most up-to-date information. Individuals, organizations, and the government must invest more in cybersecurity to mitigate cyber-attack and better protect themselves during a crisis.
(vii) Business Email Compromise (BEC): Spear phishing or impersonating an internal email account is the most common BEC tactic. IT measures such as virtual private networks (VPNs) and application-based multi-factor authentication (MFA) can help to curtail, prevent or detect BEC.
(viii) APT: Selecting a firewall as the first line of security against APT operations is critical. The three most prevalent forms of firewalls are software firewalls, hardware firewalls, and cloud firewalls, all of which can help prevent APTs.
(ix) Mobile apps: Hackers deploy their own apps in the form of utilities, games, and other items that will monitor user behaviors and inputs behind the scenes. It enables them to steal various information, including what other apps the user has installed, network activities, the user's keyboard, and so on. However, to ensure the security of mobile apps, users must encrypt source code, conduct penetration tests, conduct a thorough question and answer, ensure security check, and secure data in transit. Similarly, users should encrypt files and databases, provide data security provisions, apply the latest cryptography techniques, implement high-level authentication, and secure the backend.
(x) Browsing apps: Working in tandem with the behavioural firewall, intelligent browsing apps such as web application firewall (WAF) can protect against these weaknesses, preventing sophisticated and hazardous cyberattacks.
(xi) Spam emails: Marking spam emails as spam, deleting spam emails, and marking as spam are all simple techniques to help remove spam emails. Also, using a third-party spam filter and keeping email addresses private is a sure way to avoid spam mail attacks.
(xii) Botnet: re-install software, especially the operating system. Email attachments from suspicious or unknown sources should also be avoided. Most botnet malware will be prevented from ever being installed on a computer by a reliable antivirus, and it will typically be easy to delete if the computer is already infected. Some recommended brands are TotalAV, Norton, Bitdefender, and Malwarebytes.
(xiii) Website apps: Web applications frequently feature a whitelist and blacklist of requests to prevent these attacks, although these can also be evaded. The simplest approach to prevent this particular type of attack is to program web applications so that code cannot be executed or injected.
(xiv) Malicious domains: The attacker can construct their new malicious domains to put malware and avoid using the original websites of an organization to put malware. The term “custom or fake malicious domains” refers to domains established by attackers themselves that are unknown or well-known to most people and only exist for a brief time to avoid discovery.
Therefore, in order to avoid infection or attack from malicious domains, users must maintain their computers and update software regularly. When necessary, the user can use a non-administrator account before clicking on any links or downloading anything. When opening email attachments or photos, they need to take precautions. Pop-up windows that ask the user to download software are not to be trusted and must be scanned. Importantly, file-sharing should be limited.
(xv) Ransomware: A variety of good monitoring applications, frequent file backups, anti-malware software, and user training is required for effective ransomware attack prevention. Although no cyber-defense can totally eliminate threats, one can considerably lower the chances of an adversary succeeding. File recovery is one of the most remarkable ways to recover from a ransomware attack. Maintaining a safe, up-to-date backup of all important files is the most reliable strategy to evade a ransomware attack. For example, a known Acronis cyber protect home office can be used to back up files; it could actively strive to detect and prevent ransomware attacks.
7. Future projections
The study's key topics of projection and worry for the future are as follows:
(1) In the foreseeable future, there is a strong likelihood of an increase in cybercrime. Cyber attackers will continue to ratchet in their malicious activities and develop more sophisticated and advanced modi operandi due to the vulnerabilities associated with working from home and the opportunity for higher financial gain.
(2) To capitalize on public worry over the pandemic, cyber actors are expected to continue spreading coronavirus-themed internet frauds and phishing tactics.
(3) Due to the economic slump and shift in the business climate, business email compromise techniques are likely to increase, creating new opportunities for criminal activity.
(4) Once a COVID-19 vaccine is ready, there will undoubtedly be another surge in phishing attacks targeting medical products.
(5) People all around the world are becoming more reliant on the internet, which is opening up new chances for many businesses and individuals who are not keeping their cyber defenses up to date.
(6) There is a need for more private to public sector collaboration to effectively combat the threat COVID-19 brings to cyber security.
(7) BEC fraud is a constant threat to all enterprises, people, law enforcement, and society as a whole. Perpetrators' tactics are dubiously effective, and the financial losses sustained by businesses can be crippling. According to the information presented in this analysis, there is a global upsurge of fraud victimization and losses associated with fraud Internet Crime Complaint Centre (ICCC) and BEC fraud seem to be adopting that trend ( Cross and Gillett, 2020 ).
(8) In addition, studies on the human consequences of BEC fraud are scarce. While the financial losses sustained by BEC fraud are well-known, little is known about the human and professional consequences of victimization. Currently, there is inadequate knowledge of how businesses handle BEC fraud in terms of both internal and external messaging. This is an area where best practice concepts that might be supported to improve an organization's reaction to BEC fraud could be identified. Analogous to data breaches, denial of the situation is unlikely to result in a successful future recovery.
(9) Data breaches have become an unwelcome aspect of the present world, and BEC fraud is no exception. Unfortunately, this will, without a doubt, continue to rise in the future.
(10) To more successfully tackle this crime category of BEC in the new decade, there is indeed a fundamental need for organizations and governments to invest in knowledge and research across both technology and human factors.
(11) Intelligence-gathering methods. Organizations should encourage the proactive use of cyber threat information to identify and address important indications of attacks (IOC).
(12) Risk control. Organizations can use governance, risk, and compliance (GRC) systems for better risk management. GRC solutions give you a clear picture of your company's risk exposure and help you connect the dots between different risk disciplines, for example, cybersecurity, operational risks, and business continuity.
(13) Be ready for an attack. Companies are recommended to conduct frequent cyber crisis simulation exercises to prepare for a cyberattack in these high-risk times.
(14) There is no such thing as zero trust. Organizations such as CISOs and CIOs should think about creating a zero-trust cybersecurity strategy. Only authorized and authenticated users and devices are allowed access to apps and data in this security paradigm.
(15) Another ransomware strain that could emerge in the future is one that explicitly targets backups. This would be quite troublesome because they are the only sure-fire ways to avoid malware. Ransomware has been discovered to attack intelligent thermostats, according to researchers. This ransomware could lock one’s home or business's thermostat and only allow you to modify it if you pay a ransom.
(16) Immutable and distributed ledgers with auditable records are available with blockchain technology, making it suitable for tracking every asset in supply chain management. It relies on a distributed, private, secure, and immutable record-keeping system ( Khurshid, 2020 ). Using blockchain, governments and hospitals may find COVID-19 suspected cases, places linked to reported cases, and infected areas with high risks. Blockchain has also been used to ensure healthcare data security ( Hossain et al., 2020 ). Keeping track of patients and analyzing their symptoms or reactions to the disease is critical during the COVID-19 epidemic. Many countries affected by COVID-19, notably in healthcare, have found blockchain to be a helpful platform.
(17) Research should also focus on data exfiltration prevention, such as developing a cognitive model ( Taofeek et al., 2022 , Omolara et al., 2019a , Omolara et al., 2019b , Omolara et al., 2019c ) that can deceive attackers who intend to steal data for ransoms, terrorism or any other purposes.
(18) More also different encryption schemes and techniques such as honey encryption techniques ( Omolara et al., 2019a , Omolara et al., 2019b , Omolara et al., 2019c ), enhanced one-time pad algorithms, quantum-based algorithms, amongst other state-of-the-art encryption schemes can be used to safeguide communicated and non-communicated data ( Omolara et al., 2018a , Omolara et al., 2018b ).
(19) Furthermore, more encryption schemes can be applied to secure patient information to thwart electronic health record threats based on decoys messages ( Esther Omolara et al., 2020 ) to prevent access to malicious attackers, especially during a crisis. Therefore, more research should be focused on different encryption paradigms that address the challenges of unauthorized data theft and penetration by malicious attackers.
(20) Contact tracing or tracing based on quantum computing will be exponentially powerful in future studies ( Slussarenko and Pryde, 2019 ). Artificial learning techniques and powerful computational intelligence tools like Monte-Carlo or particle filter tracking solutions may be included. Quantum sensing uses quantum entanglements' sensitivities to increase the timing, network synchronization, location precision, and accelerometer accuracy ( Degen et al., 2017 ). Thus, leveraging such technologies will be a good line of action in these unprecedented times.
8. Recommendations
The following recommendations are considered as additional solutions to the cybersecurity initially identified for users of digital systems, which include first prevention strategies and second prevention strategies:
A. The First Steps in Preventing Cyber-Attacks.
(1) Step 1: The user should ensure that anti-virus software is updated on all devices.
(2) Step 2: Ensure the device’s firewall is turned on.
(3) Step 3: Do away with any software that has been pirated.
(4) Step 4: Avoid accessing unfamiliar websites that may include phishing material.
(5) Step 5: The user should not save their username or password in the browser.
(6) Step 6: The user should not click on any email links until they have been ascertained safe.
(7) Step 7: Users can find security-certified websites; that is, those that begin with 'HTTPS://' are safe.
(8) Step 8: The user should not save credit/debit card information in the browser.
(9) Step 9: The user should always review the website address and double-check the address, whether it is a phishing site or not, before making a credit and debit card payment.
(10) Step 10: Users should not use the same password for all accounts.
(11) Step 11: Passwords must be sufficiently strong and not contain notable dates or numerals such as date of birth or private numbers.
(12) Step 12: Users should maintain the habit of installing a commercial operating system rather than pirated software.
(13) Step 13: Users should ensure that the system’s operating system is updated.
9. Practitioner recommendations
It is important to know that the COVID-19 crisis period is for a limited time as huge measures are being taken to find a vaccine that will address the debilitating health issue. Nevertheless, the crisis period could compound an already difficult situation for information technology (IT) and cybersecurity.professionals. Therefore, it is necessary to adhere to several professional advice from experts that could assist in preserving the digital ecosystem during the COVID-19 health crisis following the cybersecurity implications.
(1) Protection against DDoS attacks. An organization must maintain the firewall turned on to minimize DDoS attacks. In addition, Ingress and Egress filtering can assist control overflow by detecting the origin of the Internet protocol range ( Balas et al., 2020 ).
(2) Protection against phishing. Phishing attacks continue to unfold as a new danger for internet users. Cyber attackers send phishing emails with counterfeit website links to collect personal information and utilize it for financial gain. To minimize the risk of such attacks, having a good understanding of the modus operandi of phishing emails is essential. For example, clicking on phishing links is a bad idea. In addition, users should not provide their login information to vulnerable websites.
(3) Anti-malware protection. Malware attacks can be reduced by using up-to-date anti-virus gadgets. Nevertheless, there is a need for firmware updates to reflect the latest patch, and firewalls need to be enabled ( Gounder and Farik, 2017 ).
(4) Anti-ransomware protection. Ransomware steals data from a device solely for financial gain. End-users have the option of using updated anti-virus software. Then, to avoid ransomware attacks, an upgraded operating system can give an updated patch file.
(5) Anti-hacking measures. The following precautions can be taken to avoid hacking. User must not reveal their login details or password to people. However, they should ensure that their Passwords are complex enough that they cannot be easily guessed. Account information should not be shared.
(6) It is necessary for educational institutions to keep private information out of e-learning platforms; the use of a software-as-a-service (SaaS) solution rather than a local client prevents third-party providers from having direct access. More so, vendors and their security documents should be evaluated regularly.
(7) A novel blockchain-based system might be provided to connect intercountry for COVID-19 and track infected or tested patients internationally. Similarly, developing a blockchain-based system for secure home quarantine administration may help curtail some of the challenges.
(8) One of the most advanced quantum applications is quantum communications ( Manzalini, 2020 ). Therefore, improved cybersecurity in communications and greater privacy protection will almost certainly be one of its key benefits for tracing susceptible applications ( Ahmed et al., 2020 ).
(9) Nowadays, cyber terrorism has increased. Therefore, there is an urgent need on how to prevent cyber-terrorism using modern scientific approaches such as AI ( Dilek et al., 2015 ), machine learning algorithms ( Salih et al., 2021 , Zhang et al., 2021 , Naik et al., 2021 ), mathematical models (Oludare et al., 2018), forensic DNA profiling (Oludare et al., 2018) amongst others. Likewise, there is a need for increasing forensic investigation ( Arshad et al., 2022 , Arshad et al., 2020 ) into crime scene to searching for evidence that can be used for justice.
(10) Some businesses will have to switch to new operating models. To overcome the barriers in providing secure procedures for staff who work from home or are remotely linked, IT and cybersecurity rights would involve a careful investigation and prompt attention. Staff assistance and remote control would be essential. Before permitting the upgraded equipment to rejoin to the network, cybersecurity experts must ensure that people transferring from home to office are subjected to serious systems and access controls.
(11) Businesses will have to reset their security networks to ensure that there are no outliers. To assess any digital gaps in the firewall, physical and digital components must be reset. In order to support remote work, device and data access rights granted during the pandemic would need to be examined to see if they might be canceled or altered. IT infrastructure would have to be checked for flaws, improper routes, and forged identities. This is based on the discussion and findings from previous sections, as cybercriminals may have devised methods to gain access to regular security systems.
(12) Emerging cyber threats that have unfolded as a result of the outbreak must be understood. Security specialists would need to review their digital capabilities to ensure that key business activities can withstand cyber-attacks during a lockout. In addition, in order to ensure sustainability amid a health emergency, they will look into crucial supply linkages, particularly digital distribution networks.
(13) Organizations' security infrastructures should be reevaluated. This comprises re-assessing secure authentication tools, substantial remote access frameworks, risk and context-based secure authentication strategies.
(14) The security architecture of organizations should be re-evaluated. Secure authentication technologies, robust remote access mechanisms, and risk and context-based authenticating user procedures are all part of this.
(15) The security team would also have to share the lessons learned throughout the incident. This will help them design effective countermeasures in the case of a future epidemic. According to experts, security systems need to be re-calibrated, especially in terms of provision, scalability, remote management capabilities, and cloud-based dependability.
(16) Security team should collaborate with trusted stakeholders ahead of time in order to prepare for dynamic scaling, service delivery, and solution offering. Planning involves both creative and methodical thinking. Leaders are increasingly expected to use innovative methods and evaluate new functioning technology. Automation, especially, boosts operational efficiency while reducing the need for human interaction.
(17) Organizations will be forced to optimize expenditures and accelerate their digital revolutions as they adjust to the new normal post-crisis. These initiatives would need security leaders to adopt evolving technologies such as the Internet, IoT, Blockchain, 5G, and service models that have been adjusted to do more with less. That is crucial to operating in the most cost-effective way feasible.
(18) Anti-malware software detects and disables malware using behavioral heuristics analysis, signature detection, and, in certain cases, artificial intelligence. Anti-malware software should be deployed across every digital endpoint of an organization's network. However, ensuring that current anti-malware is properly deployed within all devices with network connectivity in today's age of bringing your own device (BYOD) workplaces might be challenging.
(19) Educational institutions should introduce courses on cyber security to create awareness for young students and researchers in the field of computer science in order to meet the future need on how to address the cyber-attacks challenges.
(20) Some essential ‘ must know ’ cyber security measures must be introduced in a syllabus as a general mandatory cybersecurity course for students in all the higher education programme to provide more solutions in the field.
10. Conclusion
The contribution of this paper should, however, be considered in light of some limitations. First, our research is a general literature review with an informative purpose, which might suggest that there is a possibility of a subjective selection of literature. Notwithstanding, the databases we have used, such as PubMed, IEEE Xplore, Emerald insight, Willey, ACM Digital Library, Google Scholar, Semantic Scholar, and EBSCO, represent the most cited articles. Asides, the purpose and the informative nature of this paper do not require a systematic review of the literature. Secondly, during the conception and development of this paper, the COVID-19 pandemic is still ravaging. Therefore, it was not possible to accurately identify the long-term challenges and opportunities. Therefore, future research should be directed toward longitudinal analysis to identify these challenges and opportunities.
Selected articles included in the survey were from March 2020 to December 2021. Following the COVID-19 pandemic, it is vital for top executives to look internally rather than outwardly to prioritize operational competencies across key areas for the recovery of their businesses in the next two years. The data explored for this study came from an online global poll, and the responses, particularly from different organizations and business executives, highlighted variances in cyber-attack strategies. After analysis, it was discovered that hacking attacks were the most common, accounting for 17 percent of all incidents, with a total of 330 attacks. The second was spam emails, which accounted for 13 % of all attacks with a frequency of 250. Finally, malicious domains came in third with 168 attacks, accounting for 9 % of all attacks.
As seen in Table 3 , mobile apps with 150 attack occurrences account for 8 % of all attacks. Throughout the global COVID-19 crisis, however, APT attacks were the least common sort of attack, accounting for 2 % of all attacks during the research period. Moreover, over the next two years, 99 percent of firms and their CEOs plan to emphasize on emanating cybersecurity issues. Also, 15 % of firms and their leaders plan to work on lowering hacking attacks, which were the most common throughout the study period.
With the proliferation of IoT devices, technological advancements, demand for access to sophisticated systems, and historical trends, DDoS attacks will expectedly grow in volume and frequency. Cybercriminals are expected to continue to seek and exploit vulnerabilities within these systems in an attempt to weaponize them for DDoS and RDoS campaigns. Plans to implement 5G capabilities coupled with recent and ongoing shifts to digitization by organizations have provided new grounds for intrusion by threat actors. It is imperative for organizations to remain vigilant in securing critical infrastructure by monitoring pre-existing and new technologies, ensuring new policies are being followed, and adhering to security best practices for managing enterprise networks and remote workforces.
The study focuses on current cyber challenges in the context of the COVID-19 pandemic. This pandemic has seen the most Internet usage and attack ever. Many people worldwide use the Internet to continue their contact, businesses, education, and medical care, amongst others. This pandemic has put every-one's stress levels to the test. Likewise, people have also used the Internet to reduce their stress levels. This epidemic has demonstrated that people can perform their duty at home, go to school, and participate in other activities. However, cybercriminals have seized the opportunity to profit from the general public's widespread usage of the Internet. But due to a lack of awareness of the tactics, dynamism and complexity of cyber security and its associated loopholes, cyber security attacks have escalated dramatically during this epidemic.
Every digital user must understand and engage with the digital world with a proactive approach as if an impending cyber threat is looming. Considering that cyber-attacks constitute a severe danger to individuals, government and private organizations, it has become a top priority to provide every internet-connected individual with a basic understanding of cyber security to prevent crucial data from falling into the hands of cyber thieves.
COVID-19 is only the start. In the future, the globe may be confronted with an increasing number of viruses like this. As a result, it's time to start thinking about the future. We should all learn from the COVID-19 epidemic so that every-one can better prepare well for the future and ensure that Cyber Security does not cause any more problems for the world at large. Cybersecurity concerns must be on the agendas of executive committee meetings of organizations; they should be given special attention in light of the increased threats during crisis scenarios. Rather than reacting to successful cyberattacks, organizations should be proactive in dealing with them and devise strategies to prevent them. Although prevention measures are crucial, cyber-attack detection, response, and recovery skills are also required. Future research will focus on executives prioritizing operational capabilities in the direction of cost management, health and cybersecurity.
Declaration of Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgments
Acknowledgements.
While accepting sole accountability for the article's substance, the authors want to thank the reviewers for their important remarks in this survey research efforts.
Compliance with ethical standards
Funding information: This work has been fully supported by Abu Dhabi University under Grant No 19300635.
Human and animal’s rights: This article does not contain any studies with human participants or animals performed by any of the authors.
Informed consent: Informed consent was not required in this article as no humans or animals were involved.
Peer review under responsibility of King Saud University.
- Abiodun O.I., Abiodun E.O., Alawida M., Alkhawaldeh R.S., Arshad H. A review on the security of the internet of things: challenges and solutions. Wireless Pers. Commun. 2021;119(3):2603–2637. [ Google Scholar ]
- Abiodun E.O., Alabdulatif A., Abiodun O.I., Alawida M., Alabdulatif A., Alkhawaldeh R.S. A systematic review of emerging feature selection optimization methods for optimal text classification: the present state and prospective opportunities. Neural Comput. Appl. 2021;33(22):15091–15118. doi: 10.1007/s00521-021-06406-8. [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Achim, M. V., Văidean, V. L., Borlea, S. N., & Florescu, D. R. (2021). The impact of the development of society on economic and financial crime. Case Study for European Union Member States. Risks, 9(5), 97.
- Adeyoju, A. (2019). Cybercrime and Cybersecurity: FinTech’s Greatest Challenges. Available at SSRN 3486277.
- Ahmed N., Michelin R.A., Xue W., et al. A survey of covid-19 contact tracing apps. IEEE Access. 2020;8:134577–134601. [ Google Scholar ]
- Arshad H., Omlara E., Abiodun I.O., Aminu A. A semi-automated forensic investigation model for online social networks. Comp. Security. 2020;97 [ Google Scholar ]
- Arshad H., Abdullah S., Alawida M., Alabdulatif A., Abiodun O.I., Riaz O. A multi-layer semantic approach for digital forensics automation for online social networks. Sensors. 2022;22(3):1115. doi: 10.3390/s22031115. [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Auyporn W., Piromsopa K., Chaiyawat T. ISPIM Conference Proceedings. The International Society for Professional Innovation Management (ISPIM); 2020. Critical Factors in Cybersecurity for SMEs in Technological Innovation Era; pp. 1–10. [ Google Scholar ]
- Babulak E., Hyatt J., Seok K.K., Ju J.S. COVID-19 & cyber security challenges US, Canada & Korea. Int. J. Trans. Machine Learn. Data Mining. 2020;2020(2):43–59. [ Google Scholar ]
- Balas V.E., Kumar R., Srivastava R., editors. Recent trends and advances in artificial intelligence and internet of things. Springer; 2020. pp. 389–425. [ Google Scholar ]
- Bossler A.M. Neutralizing cyber attacks: techniques of neutralization and willingness to commit cyber attacks. Am. J. Criminal Justice. 2021;46(6):911–934. [ Google Scholar ]
- Burns A.J., Johnson M.E., Caputo D.D. Spear phishing in a barrel: Insights from a targeted phishing campaign. J. Organiz. Comp. Electr. Commerce. 2019;29(1):24–39. [ Google Scholar ]
- Cbsnews (2021). https://www.cbsnews.com/news/us-covid-relief-hacking-hackers-arrested-indonesia-aid-program-scam/.
- Cressey, D. R. (1953). Other people's money; a study of the social psychology of embezzlement.
- Cross C., Gillett R. Exploiting trust for financial gain: An overview of business email compromise (BEC) fraud. J. Financial Crime. 2020 [ Google Scholar ]
- Cross C., Kelly M. The problem of ‘white noise’: examining current prevention approaches to online fraud. J. Financial Crime. 2016;23(4):806–828. [ Google Scholar ]
- Das S. Springer; New Delhi: 2015. The Cyber Security Ecosystem: Post-Global Financial Crisis. In Managing in Recovering Markets; pp. 453–459. [ Google Scholar ]
- Degen C.L., Reinhard F., Cappellaro P. Quantum sensing. Rev. Mod. Phys. 2017;89 [ Google Scholar ]
- Dilek, S., Çakır, H., Aydın, M., 2015. Applications of artificial intelligence techniques to combating cyber crimes: A review. arXiv preprint arXiv:1502.03552.
- Esther Omolara A., Jantan A., Abiodun O.I., Arshad H., Dada K.V., Emmanuel E. HoneyDetails: A prototype for ensuring patient’s information privacy and thwarting electronic health record threats based on decoys. Health Inf. J. 2020;26(3):2083–2104. doi: 10.1177/1460458219894479. [ DOI ] [ PubMed ] [ Google Scholar ]
- French G., Hulse M., Nguyen D., Sobotka K., Webster K., Corman J., Ewing M. Impact of hospital strain on excess deaths during the COVID-19 pandemic—United States, July 2020–July 2021. Morb. Mortal. Wkly Rep. 2021;70(46):1613. doi: 10.15585/mmwr.mm7046a5. [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Gottschalk P. Stages of financial crime by business organizations. J. Financial Crime. 2008 [ Google Scholar ]
- Gounder M.P., Farik M. New ways to fight malware. Int. J. Sci. Technol. Res. 2017;6 [ Google Scholar ]
- Greathorn.com (2021). Cybersecurity Insiders. https://info.greathorn.com/hubfs/Reports/2021-Business-Email-Compromise-Report-GreatHorn.pdf.
- Harris A., Jones M. COVID 19–school leadership in disruptive times. School Leadership Manage. 2020;40(4):243–247. [ Google Scholar ]
- Hasham S., Joshi S., Mikkelsen D. McKinsey & Company; 2019. Financial crime and fraud in the age of cybersecurity; pp. 1–11. [ Google Scholar ]
- Hill, M., 2020. HMRC Shuts Down Almost 300 COVID19 Phishing Scam Sites, 2020, https://www.infosecuritymagazine.com/news/hmrc-covid19-phishing-scams/, (Accessed 10 June 2020).
- Hossain M.S., Muhammad G., Guizani N. Explainable AI and mass surveillance system-based healthcare framework to combat COVID-I9 like pandemics. IEEE Network. 2020;34:126–132. [ Google Scholar ]
- ibm.com (2020). https://www.ibm.com/annualreport/.
- Interpol. (2020). INTERPOL report shows alarming rate of cyberattacks during COVID-19.
- Jalali M.S., Landman A., Gordon W.J. Telemedicine, privacy, and information security in the age of COVID-19. J. Am. Med. Inform. Assoc. 2021;28(3):671–672. doi: 10.1093/jamia/ocaa310. [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Kaspersky, (2020). Coronavirus phishing, 2020.
- Khan, N. A., Brohi, S. N., & Zaman, N. (2020). Ten deadly cyber security threats amid COVID-19 pandemic.
- Khurshid A. Applying blockchain technology to address the crisis of trust during the COVID-19 pandemic. JMIR Med. Inf. 2020;8:e20477. doi: 10.2196/20477. [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Khweiled R., Jazzar M., Eleyan D. Cybercrimes during COVID-19 Pandemic. Int. J. Inf. Eng. Electr. Business. 2021;13(2) [ Google Scholar ]
- Lallie H.S., Shepherd L.A., Nurse J.R., Erola A., Epiphaniou G., Maple C., Bellekens X. Cyber security in the age of COVID-19: A timeline and analysis of cyber-crime and cyber-attacks during the pandemic. Comp. Security. 2021;105 doi: 10.1016/j.cose.2021.102248. [ DOI ] [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Mansfield-Devine S. The growth and evolution of DDoS. Network Security. 2015;2015(10):13–20. [ Google Scholar ]
- Manzalini A. Quantum communications in future networks and services. Quantum Rep. 2020;2:221–232. [ Google Scholar ]
- Masciandaro D., editor. Global financial crime: terrorism, money laundering and offshore centres. Taylor & Francis; 2017. [ Google Scholar ]
- McGuire, M., 2018. Understanding the growth of the cybercrime economy. In RSA conference, USA.
- Mertoiu G.B., Mesnita G. Global crises and cybersecurity atacks–an analysis during the covid-19 pandemic. Acta Scient. Polonorum Oeconomia. 2021;20(4):39–48. [ Google Scholar ]
- Mohamed, N. A., Jantan, A., Abiodun, O. I., 2018. An improved behaviour specification to stop advanced persistent threat on governments and organizations network. In proceedings of the International MultiConference of Engineers and Computer Scientists (Vol. 1, pp. 14-16).
- Naidoo R. A multi-level influence model of COVID-19 themed cybercrime. Eur. J. Inf. Syst. 2020;29(3):306–321. [ Google Scholar ]
- Naik B., Mehta A., Yagnik H., Shah M. The impacts of artificial intelligence techniques in augmentation of cybersecurity: a comprehensive review. Complex Intelligent Syst. 2021:1–18. [ Google Scholar ]
- Najaf K., Schinckus C., Yoong L.C. VaR and market value of fintech companies: an analysis and evidence from global data. Managerial Finance. 2020 [ Google Scholar ]
- NCSC, (2020). NCSC Shines Light on Scams Being Foiled via Pioneering New Reporting Service, 2020, https://www.actionfraud.police.uk/news/cyber-expertsshine-light-on-online-scams-as-british-public-flag-over160000-suspect-emails, (Accessed 7 May 2020).
- Netherlands, C. B. S. (2020). Less traditional crime, more cybercrime.
- Sky News, (2020). Coronavirus: Fraud victims have lost more than £4.6m to virus-related scams, 2020. https://news.sky.com/story/coronavirus-fraud-victimshave-lost-more-than-4-6m-to-virus-related-scams11996721.
- Ng A.W., Kwok B.K. Emergence of Fintech and cybersecurity in a global financial centre: Strategic approach by a regulator. J. Financial Regul. Compliance. 2017 [ Google Scholar ]
- Omolara, A. E., Jantan, A., Abiodun, O. I., & Arshad, H. (2018). An enhanced practical difficulty of one-time pad algorithm resolving the key management and distribution problem. In proceedings of the International MultiConference of Engineers and Computer Scientists (Vol. 1).
- Omolara A.E., Jantan A., Abiodun O.I., Singh M.M., Anbar M., Kemi D.V. State-of-the-art in big data application techniques to financial crime: a survey. Int. J. Comp. Sci. Network Security. 2018;18(7):6–16. [ Google Scholar ]
- Omolara A.E., Jantan A., Abiodun O.I. A comprehensive review of honey encryption scheme. Indonesian J. Electr. Eng. Comp. Sci. 2019;13(2):649–656. [ Google Scholar ]
- Omolara A.E., Jantan A., Abiodun O.I., Dada K.V., Arshad H., Emmanuel E. A deception model robust to eavesdropping over communication for social network systems. IEEE Access. 2019;7:100881–100898. [ Google Scholar ]
- Omolara, A. E., Jantan, A., Abiodun, O. I., Arshad, H., & Mohamed, N. A. (2019). Fingereye: improvising security and optimizing ATM transaction time based on iris-scan authentication. Int. J. Electr. Comp. Eng. (2088–8708), 9(3).
- Omolara O.E., Oludare A.I., Abdulahi S.E. Developing a modified hybrid caesar cipher and vigenere cipher for secure data communication. Comp. Eng. Intelligent Syst. 2014;5(5):34–46. [ Google Scholar ]
- Pras I.A. University OF Twente); 2021. Investigating an Association Between DDoS and Phishing Attacks. Doctoral dissertation. [ Google Scholar ]
- Prates M.O., Avelar P.H., Lamb L.C. Assessing gender bias in machine translation: a case study with google translate. Neural Comput. Appl. 2020;32(10):6363–6381. [ Google Scholar ]
- Reid A.S. Financial crime in the twenty-first century: the rise of the virtual collar criminal. Palgrave Macmillan; London: 2018. pp. 231–251. [ Google Scholar ]
- Rosso, K. D. (2020). New threat discovery shows commercial surveillanceware operators latest to exploit covid-19.
- Sakurai, Y., Smith, R. G. (2003). Gambling as a motivation for the commission of financial crime.
- Salih A., Zeebaree S.T., Ameen S., Alkhyyat A., Shukur H.M. 2021 7th International Engineering Conference “Research & Innovation amid Global Pandemic“(IEC) IEEE; 2021. A survey on the role of artificial intelligence, machine learning and deep learning for cybersecurity attack detection; pp. 61–66. [ Google Scholar ]
- Särökaari, N. (2020). Phishing attacks and mitigation tactics.
- Slussarenko S., Pryde G.J. Photonic quantum information processing: A concise review. Appl. Phys. Rev. 2019;6 [ Google Scholar ]
- Smzdm.com, Hackers are using the ”coronavirus” fear for phishing 2020.
- Suhono S., Zuniati M., Pratiwi W., Hasyim U.A.A. Clarifying google translate problems of Indonesia-English translation of abstract scientific writing. EAI. 2020;24–25:1–13. [ Google Scholar ]
- Sultana J., Jilani A.K. Springer; Cham: 2021. Classifying Cyberattacks Amid Covid-19 Using Support Vector Machine. In Security Incidents & Response Against Cyber Attacks; pp. 161–175. [ Google Scholar ]
- Taofeek O.T., Alawida M., Alabdulatif A., Omolara A.E., Abiodun O.I. A cognitive deception model for generating fake documents to curb data exfiltration in networks during cyber-attacks. IEEE Access. 2022 [ Google Scholar ]
- Thakur, K., Ali, M. L., Jiang, N., & Qiu, M. (2016, April). Impact of cyber-attacks on critical infrastructure. In 2016 IEEE 2nd International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS) (pp. 183–186). IEEE.
- Tidy J. Coronavirus: Israel enables emergency spy powers. BBC News. 2020;17 [ Google Scholar ]
- UNESCO: (2020). Distance Learning Solutions (2020).
- Ünvan, Y. A. (2020). Financial Crime: A Review of Literature. Contemporary Issues in Audit Management and Forensic Accounting.
- Walter J. Threat intel| cyber-attacks leveraging the covid-19/coronavirus pandemic. SentinelLABS. 2020;Sep:4. [ Google Scholar ]
- Watters P.A., McCombie S., Layton R., Pieprzyk J. Characterising and predicting cyber attacks using the Cyber Attacker Model Profile (CAMP) J. Money Laundering Control. 2012 [ Google Scholar ]
- World Health Organization. (2020). WHO reports fivefold increase in cyber attacks, urges vigilance. News release), April, 23.
- Wu S., Chen Y., Li M., Luo X., Liu Z., Liu L. Survive and thrive: A stochastic game for DDoS attacks in bitcoin mining pools. IEEE/ACM Trans. Networking. 2020;28(2):874–887. [ Google Scholar ]
- Yar M. The novelty of ‘cybercrime’ an assessment in light of routine activity theory. Eur. J. Criminol. 2005;2(4):407–427. [ Google Scholar ]
- Zahra S.R., Chishti M.A., Baba A.I., Wu F. Detecting Covid-19 chaos driven phishing/malicious URL attacks by a fuzzy logic and data mining based intelligence system. Egypt. Inf. J. 2021 [ Google Scholar ]
- Zhang Z., Ning H., Shi F., Farha F., Xu Y., Xu J., Choo K.K.R. Artificial intelligence in cyber security: research advances, challenges, and opportunities. Artif. Intell. Rev. 2021:1–25. [ Google Scholar ]
- View on publisher site
- PDF (2.1 MB)
- Collections
Similar articles
Cited by other articles, links to ncbi databases.
- Download .nbib .nbib
- Format: AMA APA MLA NLM
Add to Collections
Safeguarding against cyberattack in an increasingly digital world
All industries face the threat of cyberattack. According to a prior McKinsey survey, 75 percent of experts, across many industries, consider cyberrisk to be a top concern .
Until recently, financial firms were the primary targets. Risks for banks arise from diverse factors including vulnerabilities to fraud and financial crime inherent in automation and digitization; massive growth in transaction volumes; and greater integration of financial systems within countries and internationally.
Today, due to digitization and automation, the threat is universal. Added to this, the recent COVID-19 pandemic has intensified the danger of cyberattack, across all industries. Changes in working conditions have made it harder for companies to maintain security. Large-scale adoption of work-from-home technologies, heightened activity on customer-facing networks, and greater use of online services all present fresh openings, which cyberattackers have been quick to exploit.
The overarching challenge for chief information security officers (CISOs) and cybersecurity teams will be protecting their institutions against cyberthreats while maintaining business continuity.
Digitization increases the risk of cyberattack, and this is exacerbated by the COVID-19 pandemic
75 percent of experts, across many industries, consider cyberrisk to be a top concern.
All industries face greater exposure to cyberthreats due to increasing digitization. For example, in the airline industry, digital innovation across the value chain—combined with the sheer volume of customer data airlines possess—has made them a hot target for cybercriminals. Various cyberincidents have demonstrated the need for airlines to upgrade IT and operational technology systems to reduce risk and build resiliency into their heavily digitized operating models. In 2019, the United Kingdom imposed a $230 million fine on a European airline for a breach caused by security vulnerabilities in its website. And in 2018, hackers penetrated unpatched servers and access controls of an Asian airline to steal the personal data of 9.4 million customers.
Additionally, more airlines are moving to the public cloud, for example, to harness data analytics and optimize customer experience and operations. As airlines integrate a wider array of ecosystems—such as those facilitated by the International Air Transport Association New Distribution Capability Standard—to personalize their offerings further and exchange more granular information with partners, they may have less control over the security environment and become more prone to digital attacks.
Exhibit 1 shows a snapshot of recent, publicly reported IT and cyberincidents in the airline industry.
According to Identity Theft Resource Center statistics for the United States, despite a recent decline in the total number of data breaches to about 1.2 billion, the number of records exposed has grown by about 15 percent a year since 2005 to more than 447 million in 2018 (Exhibit 2).
Given the industry’s low margins, airlines also continuously look for cost-cutting opportunities, including in IT. Many try to optimize vendor contracts for unit costs rather than acquire the agility or innovation required to evaluate new business concepts and respond quickly to new threats or opportunities.
The response to COVID-19 has increased cyberrisk
Physical distancing means many workers are staying home and making greater use of videoconferencing services, collaboration platforms, and other digital tools to do business. In their free time, they are also going online more frequently to shop, read, chat, play, and stream. All these behaviors put immense stress on cybersecurity controls and operations. Several major vulnerabilities stand out:
First, a broad shift toward work-from-home arrangements has amplified long-standing cybersecurity challenges and opened multiple vectors for cyberattacks (Exhibit 3). Second, social-engineering ploys—to gain information, money, or access to protected systems—are on the rise, such as attackers posing as help-desk teams, health workers, or investors in virus-related response activities. Finally, cyberattackers are using websites with weak security to deliver malware, in some instances using domains and websites created to spread information and resources to combat COVID-19.
As the COVID-19 outbreak progresses and alters the functioning of our socioeconomic systems, cyberattackers will continue their efforts to exploit our fears and our digital vulnerabilities. To remain vigilant and effective, CISOs will need new tactics, particularly in two areas: securing work-from-home arrangements at scale; and supporting high levels of consumer-facing network traffic.
How leaders can manage cyberrisk
Given the gravity, complexity, and growing number of risks that businesses face, executives need ways to set priorities and sequence their cybersecurity and digitization investments. Based on our experience in serving leaders in industries from consumer lending to national defense, we recommend that senior teams step back and consider their overall situations from a business perspective. Digitization requires a powerful, reliable backbone that has security and resilience built in. Managing cyberrisk requires focus in four main areas: assessing vulnerabilities with a quantitative risk analysis; reviewing cloud architecture and security capabilities; muscling up incident response and recovery capabilities; and prioritizing a cybersecurity budget, including building a skilled talent pool and optimizing resources through automation.
Assess your vulnerabilities by performing a detailed quantitative risk analysis
Cybersecurity should be central to every strategic decision and an essential component of every IT product in the organization. Cybersecurity initiatives should be prioritized based on business-risk scenarios. By looking across the business through a cybersecurity lens, companies can transform their decision making and make wiser investments based on risk. Reviewing potential attack vectors from a risk perspective and evaluating the effectiveness of current cybersecurity activities could help identify areas that put the company at risk but are not yet covered by existing cyberactivities.
We recommend that cybersecurity leaders assess their organization’s current vulnerability through a quantitative risk analysis including patch management practices; and build metrics and a dashboard to report regularly on the identified vulnerabilities and patch releases to the CISO.
Review cloud architecture and security capabilities
A company should build an IT architecture and operating model that best supports its growth, digitization, and business model. In reviewing cloud architecture, it is important to first understand what data you are putting in the cloud now and to minimize the presence of sensitive information there. CISOs should also implement a holistic cloud security strategy—emphasizing access management, threat monitoring, and incident response. Additionally, it is advisable to conduct regular penetration and vulnerability testing and audit reviews to ensure your cloud environment is secure.
Muscle up incident response and recovery capabilities
The tragic COVID-19 pandemic has shown that it is critical for companies to have robust incident response and recovery capabilities. All companies should have systems in place for monitoring and developing a response plan for supply chain cyberdisruptions. It is also advisable to continuously assess and refresh the incident response and recovery program based on your particular business risks and emerging threats, for example by hosting regular table-top exercises on emerging threats, and conducting comprehensive resilience exercises to test response and recovery capacities.
In the context of the pandemic, new tactics can help cybersecurity leaders to safeguard their organizations. The COVID-19 response has presented CISOs and their teams with two immediate priorities: One is securing work-from-home arrangements on an unprecedented scale; the other is maintaining the confidentiality, integrity, and availability of consumer-facing network traffic as volumes spike—partly as a result of the additional time people are spending at home. Recent discussions with cybersecurity leaders suggest that certain actions are particularly helpful in fulfilling these two priorities, in three areas: technology, people, and processes.
Work-from-home arrangements. Make sure required controls are in place—for example, accelerate patching for critical systems, scale up multifactor authentication, and install controls for facility-based applications that have been migrated to remote access.
Consumer-facing network traffic. Ensure sufficient capacity by putting in place technical building blocks such as a web-application firewall, secure-sockets-layer (SSL) certification, network monitoring, anti-distributed denial of service, and fraud analytics.
Even with stronger technology controls, employees working from home must still exercise good judgment to maintain security. To help employees understand the risks, businesses need to communicate effectively and creatively. Focus on what to do—rather than what not to do—and increase awareness of social engineering ploys. Also identify and monitor high-risk users such as those working with confidential data.
Work-from-home arrangements. Few business processes are designed to support extensive work from home, so most lack the right embedded controls. Promote resilience by supporting secure remote-working tools, testing and adjusting IR and BC/DR capabilities, and securing physical documents. Also, take steps to expand monitoring and clarify incident-response protocols.
Consumer-facing network traffic. Customers, employees, and vendors all play some part in maintaining the confidentiality, integrity, and availability of web-facing networks. Integrate and standardize security activities, by, for example, integrating fraud prevention capabilities with the SOC, and offer guidelines to help consumers solve some problems themselves, particularly during periods of peak use.
Prioritize cybersecurity budget, build a skilled talent pool, and optimize resources through automation
Post pandemic, it will be even more critical for organizations to find ways to cover the rising costs of IT to meet innovation and cybersecurity requirements. To generate true cost savings, the operating model needs to be adjusted. In the case of public cloud, standardizing and automating IT-infrastructure operations can significantly reduce costs.
To keep their organization on track and make the right investments, cybersecurity executives should ask and answer the following questions regarding budget, talent, and automation:
How do we focus on the right topics and spend the right amount of money?
By evaluating cyber spending against key risks and its impact on them, making sure this is proportional.
How do we measure effectiveness and evaluate how much our cyberefforts reduce our actual cyberrisks?
By assessing ROI for cyber investments based on risk reduction.
How do we know we have the right team to meet the cybersecurity challenge?
By reviewing your cyber and risk teams’ RACI, the complexity of your solutions and identifying skillset gaps. Also, by providing continuous learning opportunities to help employees adapt to new tools and technologies.
- What is our future IT-infrastructure strategy, and what are its implications for the business areas?
What benefits can the business expect from modernization, and are we set up to meet these expectations?
To answer these questions, identify operational processes that can be transformed through automation to reduce human overhead.
All businesses, across all industries, face the risk of cyberattack. The COVID-19 pandemic may have exacerbated this risk as changes in working conditions have made it harder for companies to maintain security. But there are steps businesses can take to manage security breaches, increase cyberresilience, and improve operational stability. Tactics to help businesses safeguard their organizations while ensuring business continuity center on two priorities: securing work-from-home arrangements at scale; and supporting high levels of consumer-facing network traffic.
Jim Boehm is a partner in McKinsey ’s Washington, DC, office, James Kaplan is a partner in the New York office, and Wolf Richter is a partner in the Berlin office.
The authors wish to thank Amine Aït-Si-Selmi, Marion Castel, and Mathilde Castet for their contributions to this article.
Explore a career with us
Related articles.

Cybersecurity in a digital era

Cybersecurity tactics for the coronavirus pandemic

Cybersecurity’s dual mission during the coronavirus crisis
Cyber Security ( 272 )

CISA Exam Prep Questions - Free Practice Test
Get yourself exam ready. Take this free CISA practice test now!

Free COBIT 5 Exam Practice Test
Are you ready for the COBIT exam? Take the test and find out!

Free CISM Exam Prep Practice Test
Get in shape for the CISM certification exam. Take the test now!

Free CISSP Exam Prep Practice Test
Test yourself. Ace the CISSP Certification exam!
Browse Categories
- PMP, PMI, PMBOK, CAPM, PgMP, PfMP, ACP, PBA, RMP, SP, OPM3 and the PMI ATP seal are the registered marks of the Project Management Institute, Inc.
- System Defined Security Questions
- Clickjacking Defense
- Content Security Policy
- Credential Stuffing Prevention
- Cross-Site Request Forgery Prevention
- Cross Site Scripting Prevention
- Cryptographic Storage
- DOM Clobbering Prevention
- DOM based XSS Prevention
- Database Security
- Denial of Service
- Deserialization
- Django REST Framework
- Django Security
- Docker Security
- DotNet Security
- Error Handling
- File Upload
- Forgot Password
- HTML5 Security
- HTTP Headers
- HTTP Strict Transport Security
- Infrastructure as Code Security
- Injection Prevention
- Injection Prevention in Java
- Input Validation
- Insecure Direct Object Reference Prevention
- JSON Web Token for Java
- Java Security
- Key Management
- Kubernetes Security
- LDAP Injection Prevention
- Legacy Application Management
- Logging Vocabulary
- Mass Assignment
- Microservices Security
- Microservices based Security Arch Doc
- Mobile Application Security
- Multifactor Authentication
- NPM Security
- Network Segmentation
- NodeJS Docker
- Nodejs Security
- OS Command Injection Defense
- PHP Configuration
- Password Storage
- Prototype Pollution Prevention
- Query Parameterization
- REST Assessment
- REST Security
- Ruby on Rails
- SAML Security
- SQL Injection Prevention
- Secrets Management
- Secure Cloud Architecture
- Secure Product Design
- Securing Cascading Style Sheets
- Server Side Request Forgery Prevention
- Session Management
- Software Supply Chain Security
- TLS Cipher String
- Third Party Javascript Management
- Threat Modeling
- Transaction Authorization
- Transport Layer Protection
- Transport Layer Security
- Unvalidated Redirects and Forwards
- User Privacy Protection
- Virtual Patching
- Vulnerability Disclosure
- Vulnerable Dependency Management
- Web Service Security
- XML External Entity Prevention
- XML Security
- XSS Filter Evasion
Choosing and Using Security Questions Cheat Sheet ¶
Introduction ¶.
WARNING: Security questions are no longer recognized as an acceptable authentication factor per NIST SP 800-63 . Account recovery is just an alternate way to authenticate so it should be no weaker than regular authentication. See SP 800-63B sec 5.1.1.2 paragraph 4 : Verifiers SHALL NOT prompt subscribers to use specific types of information (e.g., “What was the name of your first pet?”) when choosing memorized secrets .
If you are curious, please have a look at this study by Microsoft Research in 2009 and this study performed at Google in 2015. The accompanying Security blog update includes an infographic on the issues identified with security questions.
Please Note: While there are no acceptable uses of security questions in secure software, this cheat sheet provides guidance on how to choose strong security questions for legacy purposes.
Choosing Security Questions ¶
Desired characteristics ¶.
Any security questions presented to users to reset forgotten passwords must meet the following characteristics:
Types of Security Questions ¶
Security questions fall into two main types. With user defined security questions, the user must choose a question from a list, and provide an answer to the question. Common examples are "What is your favourite colour?" or "What was your first car?"
These are easy for applications to implement, as the additional information required is provided by the user when they first create their account. However, users will often choose weak or easily discovered answers to these questions.
System defined security questions are based on information that is already known about the user. This approach avoids having to ask the user to provide specific security questions and answers, and also prevents them from being able to choose weak details. However it relies on sufficient information already being stored about the user, and on this information being hard for an attacker to obtain.
User Defined Security Questions ¶
Bad questions ¶.
Any questions that do not have all of the characteristics discussed above should be avoided. The table below gives some examples of bad security questions:
Additionally, the context of the application must be considered when deciding whether questions are good or bad. For example, a question such as "What was your maths teacher's surname in your 8th year of school?" would be very easy to guess if it was using in a virtual learning environment for your school (as other students probably know this information), but would be much stronger for an online gaming website.
Good Questions ¶
Many good security questions are not applicable to all users, so the best approach is to give the user a list of security questions that they can choose from. This allows you to have more specific questions (with more secure answers), while still providing every user with questions that they can answer.
The following list provides some examples of good questions:
- What is the name of a college you applied to but didn’t attend?
- What was the name of the first school you remember attending?
- Where was the destination of your most memorable school field trip?
- What was your maths teacher's surname in your 8th year of school?
- What was the name of your first stuffed toy?
- What was your driving instructor's first name?
Much like passwords, there is a risk that users will re-use recovery questions between different sites, which could expose the users if the other site is compromised. As such, there are benefits to having unique security questions that are unlikely to be shared between sites. An easy way to achieve this is to create more targeted questions based on the type of application. For example, on a share dealing platform, financial related questions such as "What is the first company you owned shares in?" could be used.
Allowing Users to Write Their Own Questions ¶
Allowing users to write their own security questions can result in them choosing very strong and unique questions that would be very hard for an attacker to guess. However, there is also a significant risk that users will choose weak questions. In some cases, users might even set a recovery question to a reminder of what their password is - allowing anyone guessing their email address to compromise their account.
As such, it is generally best not to allow users to write their own questions.
Restricting Answers ¶
Enforcing a minimum length for answers can prevent users from entering strings such as "a" or "123" for their answers. However, depending on the questions asked, it could also prevent users from being able to correctly answer the question. For example, asking for a first name or surname could result in a two letter answer such as "Li", and a colour-based question could be four letters such as "blue".
Answers should also be checked against a denylist, including:
- The username or email address.
- The user's current password.
- Common strings such as "123" or "password".
Renewing Security Questions ¶
If the security questions are not used as part of the main authentication process, then consider periodically (such as when they are changing their passwords after expiration) prompting the user to review their security questions and verify that they still know the answers. This should give them a chance to update any answers that may have changed (although ideally this shouldn't happen with good questions), and increases the likelihood that they will remember them if they ever need to recover their account.
System Defined Security Questions ¶
System defined security questions are based on information that is already known about the user. The users' personal details are often used, including the full name, address and date of birth. However these can easily be obtained by an attacker from social media, and as such provide a very weak level of authentication.
The questions that can be used will vary hugely depending on the application, and how much information is already held about the user. When deciding which bits of information may be usable for security questions, the following areas should be considered:
- Will the user be able to remember the answer to the question?
- Could an attacker easily obtain this information from social media or other sources?
- Is the answer likely to be the same for a large number of users, or easily guessable?
Using Security Questions ¶
When to use security questions ¶.
Applications should generally use a password along with a second authentication factor (such as an OTP code) to authenticate users. The combination of a password and security questions does not constitute MFA , as both factors as the same (i.e. something you know)..
Security questions should never be relied upon as the sole mechanism to authenticate a user . However, they can provide a useful additional layer of security when other stronger factors are not available. Common cases where they would be used include:
- Logging in.
- Resetting a forgotten password.
- Resetting a lost MFA token.
Authentication Flow ¶
Security questions may be used as part of the main authentication flow to supplement passwords where MFA is not available. A typical authentication flow would be:
- The user enters their username and password.
- If the username and password are correct, the user is presented with the security question(s).
- If the answers are correct, the user is logged in.
If the answers to the security questions are incorrect, then this should be counted as a failed login attempt, and the account lockout counter should be incremented for the user.
Forgotten Password or Lost MFA Token Flow ¶
Forgotten password functionality often provides a mechanism for attackers to enumerate user accounts if it is not correctly implemented. The following flow avoids this issue by only displaying the security questions once the user has proved ownership of the email address:
- The user enters email address (and solves a CAPTCHA).
- The application displays a generic message such as "If the email address was correct, an email will be sent to it".
- An email with a randomly generated, single-use link is sent to the user.
- The user clicks the link.
- The user is presented with the security question(s).
- If the answer is correct, the user can enter a new password.
How to Use Security Questions ¶
Storing answers ¶.
The answers to security questions may contain personal information about the user, and may also be re-used by the user between different applications. As such, they should be treated in the same way as passwords, and stored using a secure hashing algorithm such as Bcrypt. The password storage cheat sheet contains further guidance on this.
Comparing Answers ¶
Comparing the answers provided by the user with the stored answer in a case insensitive manner makes it much easier for the user. The simplest way to do this is to convert the answer to lowercase before hashing the answer to store it, and then lowercase the user-provided answer before comparing them.
It is also beneficial to give the user some indication of the format that they should use to enter answers. This could be done through input validation, or simply by recommending that the user enters their details in a specific format. For example, when asking for a date, indicating that the format should be "DD/MM/YYYY" will mean that the user doesn't have to try and guess what format they entered when registering.
Updating Answers ¶
When the user updates the answers to their security questions, this should be treated as a sensitive operation within the application. As such, the user should be required to re-authenticate themselves by entering their password (or ideally using MFA), in order to prevent an attacker updating the questions if they gain temporary access to the user's account.
Multiple Security Questions ¶
When security questions are used, the user can either be asked a single question, or can be asked multiple questions at the same time. This provides a greater level of assurance, especially if the questions are diverse, as an attacker would need to obtain more information about the target user. A mixture of user-defined and system-defined questions can be very effective for this.
If the user is asked a single question out of a bank of possible questions, then this question should not be changed until the user has answered it correctly. If the attacker is allowed to try answering all of the different security questions, this greatly increases the chance that they will be able to guess or obtain the answer to one of them.
Introducing Cloud Defense Free Enterprise Scale CSPM. No Cost. No Strings. No Kidding
Security Posture Management for Hybrid Enterprise Environments
Our security policy management platform from 2001 is the only real-time solution that reduces firewall and cloud security policy related risks, manages policy changes, and enforces compliance.
Real-time detection
Easily customizable
Scale and performance
Flexible integrations
Discover how FireMon can help you
Improve Security Operations. Improve Security Outcomes.
Security policy management
Cloud security management
Cyber asset management
Increase visibility, reduce risk, enforce compliance, and speed change for your cloud and firewall network security policies
Reduce risk
Manage change, enforce compliance, free assessment.
Reduce risk, speed response, and streamline cloud security operations
Manage hybrid network policies
Discover cloud assets, detect and mitigate risk in the cloud.
Improve visibility by finding and securing unknown, rogue, and shadow clouds, network infrastructure, and endpoints
Network discovery
Endpoint identification, leak path detection.
ELIMINATE BLIND SPOTS
Increase visibility
across hybrid environments
UNIFIED VIEW
for every policy from every vendor
policies across your organization
Trusted by over 1700 customers in more than 70 countries
Health Care
Financial Services
Manufacturing
With FireMon tracking compliance for us, we were able to shrink our overall audit time by two-thirds of our original schedule. Additionally, we were able to clean and push out almost 300 rules that had not been reviewed in over three years.”
Manager, Network Services
We always knew we weren’t using the latest and greatest to handle our audit reports, but we thought we were doing enough to get by. A failed audit told us otherwise. I wish we went with FireMon earlier as the time and manpower savings have been incredible.”
Director of InfoSec

FireMon ensures that not a single policy change goes unnoticed or introduces vulnerabilities. Our security posture, once a concern, is now a point of pride.”
Head of Security Engineering
The ROI of going with FireMon was a real eye-opener for us. After learning how much we’d save by automating our manual processes and gaining real time, single pane-of-glass management across our entire network, including Zscaler, it was an absolute no brainer.”
Manager of IT Security Engineering
Given the complexity of our environment we were skeptical that any vendor could deliver on a solution that could unite policies across our mix of on-premises firewalls, Azure, and AWS. FireMon not only promised they could, they demonstrated it in a POC that took less than a week.”
Security Operations Manager

Connect over 100 integrations
Data Center, Enterprise Networks, and Branches
On Premises
Includes firewalls, routers, load balancers, and proxies
Also includes VPCs, VNets and network ACLs
Remote Users
Integrations.
Industry-leading API-first approach that uses a modular plug-and-play framework
Award winning services

Featured resources

3 Ways to Streamline Network Security Automation That Will Transform Your Organization
A Paramedic’s Top 2 Tips for Cloud Incident Response
A Practical History of the Firewall – Part 1: Early Days
A Practical History of the Firewall – Part 2: The Value of Management
Asset Discovery: A Must Have for Understanding Your Complete Attack Surface
Advanced Techniques for Defending AWS ExternalID and Cross-Account AssumeRole Access
Stay ahead of change
Explore our research, insights, and examples of real client impact, designed to help you embrace the key forces of change and get to value faster.
- Editor's picks
We didn’t find a match...
...but check out our insights into everything from industries to AI to stay ahead of change.
Get Foresight on the go
Download the Accenture Foresight app to read, watch, or listen to our best thinking—and join our exclusive “Foresight in 15” live digital events for quick takes on big ideas.
Explore Security
Data protection, unified threat management, cyber attacks, cyber crime, data breaches.

Latest about Security

Energy firms need to up their game to protect against supply chain risks
By Emma Woollacott published 24 October 24
News A new report highlights the risks to the sector from software and IT vendors

Multi-layered security is the key to keeping data safe – here’s why
By ITPro published 23 October 24
A robust cyber resilience strategy requires multiple layers of defense to safeguard business-critical data against an increasingly sophisticated threat landscape

Exploitation of Docker remote API servers has reached a “critical level”
By Solomon Klappholz published 23 October 24
News Hackers are targeting Docker’s remote access API as it allows them to pivot from a single container to the host and deploy malware with ease

Hackers are stepping up ‘qishing’ attacks by hiding malicious QR codes in PDF email attachments
News Malicious QR codes hidden in email attachments may be missed by traditional email security scanners, with over 500,000 qishing attacks launched in the last three months.

Cisco confirms attackers stole data, shuts down access to compromised DevHub environment
By Solomon Klappholz published 22 October 24
News The tech giant insists that no sensitive customer information has been compromised

Ethical hackers are flocking to AI tools, but the technology may be causing more problems than it solves
By Emma Woollacott published 22 October 24
News A survey of security researchers points to an escalating AI arms race along with a growing threat from hardware hacking

Cyber criminal underground “thriving” as weekly attacks surge by 75% in Q3 2024
By Solomon Klappholz published 21 October 24
Cyber attacks reached another all-time high this quarter as digital crime continues to be a highly profitable industry for threat actors

Enterprises are struggling to fill senior cybersecurity roles — and it's causing staff burnout to skyrocket
By Emma Woollacott published 21 October 24
News Many senior roles take months to fill, creating cumbersome workloads for mid-level staff and increased burnout

Why choosing the right business cybersecurity and networking partner is key to your future safety and success
By Rory Bathgate published 21 October 24
Cloud architectures such as SASE can greatly improve organizational security – but leaders should lean on trusted partners to deliver them

What is Zero Trust?
By Drew Turney last updated 19 October 24
In-depth Zero Trust is the protection framework sweeping the cyber security industry. Here's what you need to know
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
- 2 This new AI jailbreaking technique lets hackers crack models in just three interactions
- 3 Europe needs more energy and better grids to meet data center power demands
- 4 Four tech firms fined by SEC for downplaying SolarWinds impact
- 5 ROI from AI projects has nosedived – how can IT leaders deliver success?

IMAGES
VIDEO
COMMENTS
These case studies illustrate how cybersecurity threats vary across industries, with each sector facing unique challenges and adopting specific mitigation strategies. For MCA students in cybersecurity , understanding these cases provides insights into how different industries approach cybersecurity, emphasizing the need for adaptive, robust ...
We tackle the paradox of why data breaches continue to occur despite heightened awareness and security measures. From the crafty nature of social engineering attacks, phishing, and AI-enhanced phone scams to minor configuration mistakes that lead to major vulnerabilities, we uncover the layers of complexity organizations face today.
Security Expertise: If your team has strong security expertise and wants granular control, IaaS might be suitable. For those preferring to leverage built-in security features, PaaS can be a good choice. Application Security: Consider your existing application security capabilities. PaaS may ease the burden by handling some aspects of ...
What You'll Learn. This is CS50's introduction to cybersecurity for technical and non-technical audiences alike. Learn how to protect your own data, devices, and systems from today's threats and how to recognize and evaluate tomorrow's as well, both at home and at work.
Cybercrime and the cost of data breaches are increasing at an alarming rate, raising concerns among business owners and IT practitioners about the security of their business and data. The COVID-19 pandemic and remote work environments provided the perfect opportunity for cybercriminals to compromise business data.
These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice. Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022) Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022) Overview of Cyber Security (Yadav, 2022)
Naked Security Insights, education and and advice on cybersecurity issues and threats September 26, 2023 Update on Naked Security. To consolidate all of our security intelligence and news in one location, we have migrated Naked Security to the Sophos News platform. Naked Security ...
In the case of insurance firm cyber-attack, the Avaddon gang attacked the European insurance business AXA in May 2020. ... A Study of Security Threats in Cloud: Passive Impact of COVID-19 Pandemic ... Cyber security in the age of COVID-19: A timeline and analysis of cyber-crime and cyber-attacks during the pandemic: 8: 3: 33: Cyber Security ...
In the case of public cloud, standardizing and automating IT-infrastructure operations can significantly reduce costs. To keep their organization on track and make the right investments, cybersecurity executives should ask and answer the following questions regarding budget, talent, and automation: Budget
Access free practice tests on Cyber Security and test out your skills. Our practice exams simulate the actual certification exam and helps you to become exam ready. All Courses. All Courses. Reviews; ... CISA Exam Prep Questions - Free Practice Test. Get yourself exam ready. Take this free CISA practice test now! 8416 Tests taken. Free Practice ...
The accompanying Security blog update includes an infographic on the issues identified with security questions. Please Note: While there are no acceptable uses of security questions in secure software, this cheat sheet provides guidance on how to choose strong security questions for legacy purposes. Choosing Security Questions¶
Cyber Security vs. Information Assurance Computer Science 103 - Assignment 1: Cybersecurity Paper Computer Science 331 - Assignment 1: Cybersecurity Research Paper
We are a world-leading authority on global security, political risk and military conflict. ... The International Institute for Strategic Studies is a world-leading authority on global security, political risk and military conflict. ... IISS launches IISS Cyber Power Matrix. 10th October 2024. 10th October 2024. Cyber Power Matrix IISS Cyber ...
Industry-leading solutions for firewall policy management, cloud security operations, and cyber asset discovery and identification. Security Policy Management. Reduce Risk. Manage Change. Enforce Compliance. Free Assessment. ... Case Studies. Blog. Events. Webinars. Newsroom. Solution Guides. Learning Center. Cloud Center of Excellence. Service ...
Virtualization and container security are key topics in the Certificate of Cloud Security Knowledge credential. Test your knowledge with these CCSK practice questions. Continue Reading. Test your cyber-smarts with this network security quiz. Show what you know about the topics covered in the May 2020 issue of Information Security magazine.
Blog Case Study Live Interview News Article Perspective Podcast Research Report. Show results. Filter by topics Topic Industry Content Type Cloud Cybersecurity Data ...
The University of Manchester wants to set an example for cyber after being attacked While the cyber attack on the university was a damaging incident, it could've been a lot worse Four tech firms fined by SEC for downplaying SolarWinds impact Unisys, Avaya Holdings, Check Point Software, and Mimecast haven't admitted any wrongdoing, but have ...
The right decisions require the right data. That's why Carbon Black is here to help you see targeted threats and prevent repeated attacks.
Many British companies will need to adhere to NIS2's cyber security risk management and reporting requirements if they want to continue operating in the EU market and avoid huge fines Continue ...