IEEE Account
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 01 February 2024
Wireless body area sensor networks based human activity recognition using deep learning
- Ehab El-Adawi 1 ,
- Ehab Essa 1 ,
- Mohamed Handosa 1 &
- Samir Elmougy 1
Scientific Reports volume 14 , Article number: 2702 ( 2024 ) Cite this article
2762 Accesses
2 Citations
9 Altmetric
Metrics details
- Computer science
- Public health
In the healthcare sector, the health status and biological, and physical activity of the patient are monitored among different sensors that collect the required information about these activities using Wireless body area network (WBAN) architecture. Sensor-based human activity recognition (HAR), which offers remarkable qualities of ease and privacy, has drawn increasing attention from researchers with the growth of the Internet of Things (IoT) and wearable technology. Deep learning has the ability to extract high-dimensional information automatically, making end-to-end learning. The most significant obstacles to computer vision, particularly convolutional neural networks (CNNs), are the effect of the environment background, camera shielding, and other variables. This paper aims to propose and develop a new HAR system in WBAN dependence on the Gramian angular field (GAF) and DenseNet. Once the necessary signals are obtained, the input signals undergo pre-processing through artifact removal and median filtering. In the initial stage, the time series data captured by the sensors undergoes a conversion process, transforming it into 2-dimensional images by using the GAF algorithm. Then, DenseNet automatically makes the processes and integrates the data collected from diverse sensors. The experiment results show that the proposed method achieves the best outcomes in which it achieves 97.83% accuracy, 97.83% F-measure, and 97.64 Matthews correlation coefficient (MCC).
Similar content being viewed by others
An improved human activity recognition technique based on convolutional neural network
5G-enabled contactless multi-user presence and activity detection for independent assisted living
Wrapper-based deep feature optimization for activity recognition in the wearable sensor networks of healthcare systems
Introduction.
Wireless body area network (WBAN) is employed as the fundamental network architecture for various sensor types across diverse applications. These sensors are specifically designed to function on, around, and within the human body. They require very little power and do not need any external assistance. In the healthcare sector, a collection of physical and biological sensors is distributed on the patient’s body to collect information about the patient to be used in monitoring their health status and biological physical activities, checking their physiological measurements or any other objectives, through using WBAN architecture. The sensors distributed on-body used in human activity recognition (HAR) domain 1 , 2 . A WBAN consists of movable sensors with communication capabilities, managed by a body area networks (BANs) coordinator. Each sensor can be attached to the body 3 . Healthcare devices have undergone a transformation with advancements in microelectronic technology, enabling them to be less intrusive and more wearable or implantable. The fifth-generation communication system offers greater benefits to users, including higher capacity. However, in the absence of BANs, actuator and sensor functions were isolated, leading to inefficient use of communication resources.
BANs offer numerous advantages, such as providing a solid basis for physical exercise, recuperation, and health tracking 4 . Consequently, it is important to model HAR system in WBAN architecture to achieve high recognition accuracy. In recent years, wearable sensor-based HAR has gained popularity due to the widespread use of mobile devices 5 . Identifying different human activities using sensor data is known as HAR. Due to the Internet of Things (IoT), artificial intelligence (AI), and the rapid development of 6th Generation (6G) mobile networks, HAR is becoming more and more significant in our daily. Particularly in daily activity analysis 6 , video monitoring 7 , identification of gestures 8 , and analysis of gait 9 . While sensor-based activity recognition (AR) is used to evaluate and process data from sensors like accelerometers and gyroscopes, video-based AR primarily processes the video and pictures collected by cameras. Due to its advantages of superior privacy and simplicity, sensor-based AR has become attractive to many researchers’ primary focus. Figure 1 illustrates the HAR framework which consists of four phases: gathering data, preprocessing, and segmentation, extracting features, and classifying activities.
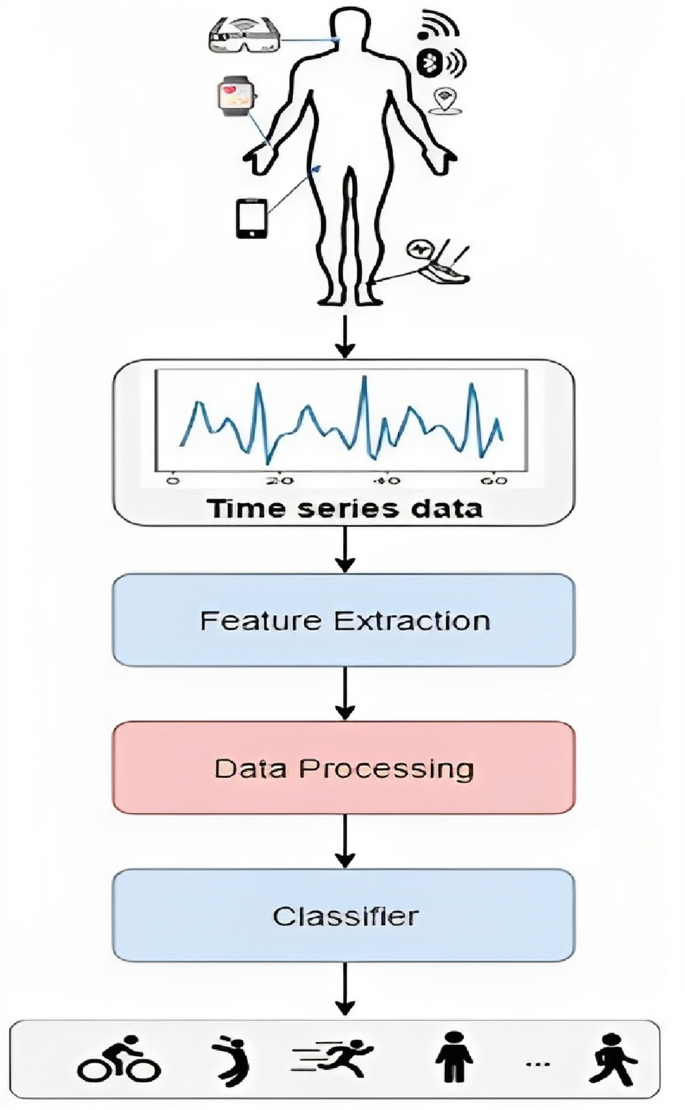
HAR Framework adapted from 10 .
Many recognition models employed in the HAR system are dependence on traditional machine learning (ML) methods, while others are based on deep learning (DL) algorithms. Among the most popular traditional ML algorithms are the decision tree (DT) 11 , random forests (RF) 12 , 13 , and support vector machine (SVM). The classic ML method has undergone a revolution in the last ten years developed by DL, which has increased performance in various areas such as speech recognition, object identification, image recognition, and natural language processing. DL has significantly improved the performance and reliability of HAR, accelerating its acceptance and applicability in wearable sensor-based applications. Unlike traditional ML techniques that often require manual feature extraction or engineering, a process that demands domain expertise and extensive human effort, DL methods can automatically learn robust features from raw data for specific applications.
Utilizing DL, methods can make the HAR process simpler. The architecture of DL algorithms is composed of stacked layers of neurons that derive hierarchical representations. For each layer, a nonlinear function is applied to generate new feature maps based on the input feature maps from the previous layer. This hierarchical representation enables DL algorithms to autonomously identify the most relevant features specific to the application domain. By minimizing a specific loss function, the DL architecture identifies features and classification boundaries. DL-based methods can learn the features autonomously, eliminating the need for manual feature engineering. DL algorithms such as as convolutional neural network (CNN), recurrent neural networks (RNN)s, Deep Belief Networks, and autoencoders are often used for HAR 8 .
Deep neural networks (DNN) demonstrates the ability to learn meaningful features from raw inputs, even with limited domain expertise. Additionally, when equipped with a substantial network and an ample number of observations, DNNs have been shown to be universal function approximators, capable of approximating almost any function 14 . This high expressive capacity has resulted in a significant surge in HAR-based applications for DL. However, despite the numerous benefits offered by DL, it also has inherent issues and drawbacks-for instance, the vanishing gradient problem. Furthermore, many recognition techniques based on CNN employ one-dimensional convolution kernels 15 , 16 , which poses challenges in effectively leveraging the rich high-dimensional data characteristics.
Transfer learning is a technique in DL where a pre-trained model on a large dataset is used as a starting point for a new task. One such pre-trained model is the densely connected convolutional networks (DenseNet) 17 , which is a DNN architecture known for its high accuracy and efficiency in computer vision tasks. Transfer DenseNet refers to the application of transfer learning using a pre-trained DenseNet model. The idea is to take advantage of the learned features and parameters of the pre-trained model and adapt them to a new task by fine-tuning the network on a smaller dataset specific to the new task. By using transfer learning with DenseNet, it is possible to achieve higher accuracy with less training time and fewer training data than training a new model from scratch. This is especially useful in scenarios where there is limited labeled data available or when training a new model from scratch is computationally expensive.
There are numerous techniques employed to transform 1-dimensional sensor data into 2-dimensional data through matrix rearrangement. One of these methods involves a straightforward approach of listing and superimposing the data, but it may lose interpretability 18 , 19 . In 20 , 21 , 22 , the Fourier transform was used to turn the 1-dimensional time series into 2-dimensional time-frequency pictures, which significantly increased the quantity of calculations. In 18 , the Gramian angular field (GAF) transform was used to transform data into a two-dimensional time-frequency image. Sensor-based activity detection systems would inevitably use less computer power and perform calculations more quickly due to wearable sensor devices’ mobility and real-time capabilities.
In this paper, we propose a new HAR system in WBAN based on GAF and DenseNet to convert time series data from one-dimensional into a two-dimensional image and then classify the human activities, that are collected by sensors distributed on the body of the patient, by using DenseNet. The DenseNet offers various appealing benefits, including eliminating the vanishing-gradient issue, enhancing the feature propagation, promoting feature reuse, and much fewer parameters. The GAF method establishes the groundwork for the success of feature extraction while improving the interpretability of the transformation from one-dimensional time series to a 2-dimensional image. The experimental results demonstrate that the proposed HAR approach achieves good performance by combining the GAF algorithm’s features with the structure and benefits of DenseNet, which may significantly increase the multiscale feature extraction capability and the accuracy of activity detection. The contributions of this paper include a AR hybrid approach in WBAN architecture is proposed and developed based on integrating GAF algorithm and DenseNet based on the mobile health (MHEALTH) dataset.
The subsequent sections of this paper are structured as follows: “ Literature review ” presents related works. “ Methods ” presents and discusses the proposed methodology. “ Results ” delves into implementation details. Lastly, “ Conclusions and future works ” presents and discusses the results obtained.
Literature review
Batool et al. 23 proposed an innovative method that employs fused sensors and presents a modified K-Ary entropy classifier algorithm to tackle intricate challenges related to feature selection and classification using RGB-D data. The algorithm is designed to enhance the spacing between intra-substructure nodes within a tree, thereby decreasing the probability of misclassifying the minority class. The proposed model undergoes testing on three benchmark datasets, revealing promising outcomes with performance metrics of 95.05%, 95.56%, and 95.08% for the SYSU-ACTION, PRECIS HAR, and Northwestern-UCLA (N-UCLA) datasets, respectively. K. Abhishek et al. 24 proposed approach entails deploying a CNN model for the examination of videos recorded by surveillance cameras, with the objective of categorizing the existence of humans in the individual frames of the video. The proposed model undergoes testing on three benchmark datasets, revealing promising outcomes with performance metrics of 92.15%, and 92.83% for Sport Videos in the wild, and UT-interaction datasets, respectively. Boga et al. 25 proposed a method for HAR using WBAN and DL. The proposed method involves a multi-objective feature selection approach to select the most relevant features from the sensor data collected by the WBAN. These features are then input to a DL model for AR to recognize human activity (HA). Mishra et al. 26 A system was introduced to facilitate on-device intelligence for Human HAR by utilizing energy harvesting wireless sensor networks (EWSNs). The proposed system utilizes ML algorithms to perform AR on the sensor data collected by the EWSNs. To enable on-device intelligence, the authors propose a hardware platform that integrates the EWSNs with a microcontroller unit and an energy harvesting module. the authors propose present experimental results to demonstrate the effectiveness of the proposed system in accurately recognizing HAs while achieving energy efficiency through the use of energy harvesting. Reich et al. 27 provide an evaluation of the performance of Bluetooth in a WBAN for practical applications. the authors propose the feasibility of using Bluetooth for transmitting physiological data in a WBAN by evaluating its performance in terms of data rate, power consumption, and latency. the authors propose present experimental results to demonstrate the suitability of Bluetooth for practical WBAN applications, including remote patient monitoring and health tracking. Additionally, the authors discuss the potential challenges and limitations of using Bluetooth in a WBAN, such as interference and security concerns, and proposes possible solutions to address these issues. Fan et al. 28 proposed a DNN approach for team training using body-worn inertial sensors for HAR. The system aims to provide real-time feedback to team members during training sessions to improve their performance by identifying and analyzing their movements. The proposed method uses a multi-layer neural network (NN) to recognize different activities performed by team members and provides personalized feedback based on their individual performance. they suggest that the system can be used in various team training scenarios, such as sports, military training, and emergency response, to enhance teamwork and overall performance. He et al. 29 proposed wearable WBAN for HAR. consists of a set of body-worn sensors to detect and measure various physical activities performed by an individual. The gathered data is wirelessly transmitted to a central processing unit, where it undergoes analysis using ML algorithms to discern various activities. The authors propose that the wearable wireless body area network system can be used in various applications, such as healthcare, sports, and elderly care, to monitor and improve human physical activity and overall well-being.
Huan et al. 30 proposed approach involves the development of a hybrid model that combines CNN and bidirectional long short-term memory (BLSTM) architectures. This model is specifically designed to leverage the PAMAP2 dataset for accurate recognition of HA, this model achieves F1 92.23%. Damirchi et al. 31 proposed an ARC-Net net based on PAMAP2, and the RealWorld datasets, to predict the activity performed by the subject. It ranges from 89.81% to 90.51% for the PAMAP2 dataset and 90.51% for the RealWorld dataset. Hongji et al. 18 proposed a new model based on WISDM, UCI HAR, and OPPORTUNITY datasets to improve the HAR method by transforming time-series data into 2D images. By using GAF, they pass the output to the CNN model. The model achieves 95.79%, 89.63%, and 96.04% for the F1 score. and 96.83%, 89.48%, 97.27% for accuracy respectively.
Ahmed et al. 32 proposed a HAR system that calculates the best wearable sensor data based on MOTIONSENSE, MHEALTH, and the proposed self-annotated IM-AccGyro human-machine datasets, by applying a notch filter to 1D signals and looking at the lower/upper cutoff frequencies. Subsequently, it calculates a variety of composite features, which encompass statistical characteristics, Mel frequency cepstral coefficients, and Gaussian Mixture Model features. The model achieves 88.25%, 93.95%, and 96.83%. Nidhi et al. 10 proposed a novel approach called “ICGNet” based on MHEALTH and PAMAP2 datasets that makes use of the advantages of CNN and gated recurrent unit (GRU) and can therefore detect local characteristics and long-term relationships in multivariate time series data. The model achieves 99.25% and 97.64%.
Uddin et al. 33 proposed a solution that leverages CNNs for AR. CNNs are a type of artificial neural network commonly used for analyzing visual data, such as images or video frames. In this paper, the CNN architecture is adapted to process sequential data from body sensors, such as accelerometers or gyroscopes, which provide information about human movements, based on MHEALTH dataset, the model achieves 93.90%. Sheikh et al. 34 proposed HAR system on USC-HAD, IMSB, and MHEALTH datasets, which collects signal data from inertial sensors, such as gyroscopes and accelerometers used as motion node sensors. The inertial data is first processed using a variety of filters. It derives a multifaced model for statistical, wavelet, and binary features to optimize the occurrence of ideal feature values. Then, in the phase of feature optimization, adaptive moment estimation (Adam) and AdaDelta are added to adopt learning rate patterns. this model achieves 91.25%, 90.91%, and 93.66%. Lingjuan et al. 35 proposed a model hybrid of CNN and long short-term memory (LSTM) called RG-RP based on MHEALTH and UCI-HAR datasets, which combines the merits of LSTM and CNN. The model achieves 98% and 96.2%. Ha et al. 36 proposed a CNN-based approach to leverage the spatial and temporal information captured by the accelerometer and gyroscope sensors. By using CNNs, the model can automatically learn relevant features from the raw sensor data without the need for manual feature engineering based on the MEALTH dataset. the model achieved 91.94%. Chen et al. 37 proposed a model for unbalanced activity detection using a semi-supervised deep model from multimodal wearable sensory data based on MHEALTH, PAMPA2, and UCI-HAR datasets. The researchers proposed a pattern-balanced semi-supervised framework aimed at extracting and preserving diverse latent activity patterns. More specifically, their approach suggests using a pattern-balanced semi-supervised framework for extracting and maintaining different latent activity patterns. The model achieves 94.05%, 83.42%, and 81.32%. Qin et al. 38 presented HAR architecture to utilize data from multiple sensors with using a hybrid system of GAF and ResNet model based on heterogeneity human activity recognition (HHAR) and MHEALTH datasets. This model provides an accuracy of 93.41% on HHAR dataset and 98.5% on MHEALTH dataset. Table 1 presents a Comparison between the related work for HAR.
Dataset description
The UCI repository makes the MHEALTH dataset 39 available; it contains information on 12 activities carried out by ten people. This dataset includes the following activities: stair climbing, cycling, frontal arm elevation, jogging, back and front jumps, knee bending (crouching), lying down, running, sitting and relaxing, standing still, forward-bent waist, and walking. The data was collected by using sensors positioned at the body parts: chest, right wrist, and left ankle; Fig. 2 depicts where the locations of these sensors.
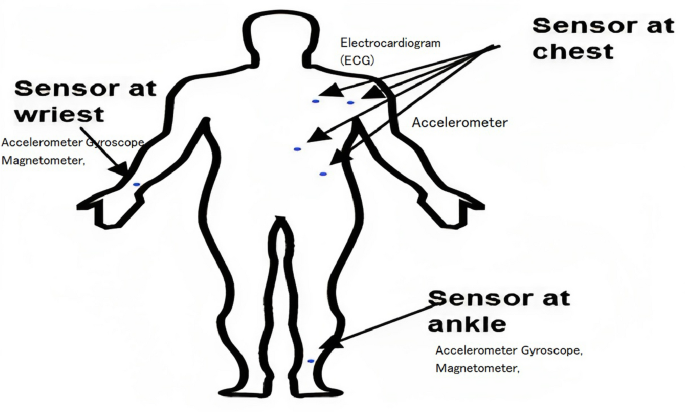
The position of the sensor to collect data for the MHEALTH dataset 40 .
In this work, we use the gyroscope, accelerometer, and magnetometer sensors. The characteristics that are recorded by the accelerometer, gyroscope, magnetometer, and electrocardiogram (ECG) are ( axe , ay , az ), ( gx , gy , gz ), and ( mx , my , mz ), respectively, in all three x, y, and z-direction. The combination of several sensors makes it possible to measure the motion felt by various body parts, like the rate of rotation, acceleration, and magnetic field direction. ECG readings can track your essential health, the effects of certain activities, and more. Additionally, recordings of ECG signals were made. Lead1 and lead2 signals on the ECG have two characteristics. Accelerometer and ECG signals were captured at the chest, and accelerometer, gyroscope, and magnetometer signals were recorded at the right wrist and left ankle. Thus, for all three places’ qualities and features, a total of 23 were recorded. A sampling rate of 50 Hz was used to record all sensing modalities. Then the collected sensor data is transmitted from the individual sensors to a central unit. This central unit could be the user’s smartphone, a dedicated wearable device, or another computing device capable of processing and transmitting data.
Sensors in the MHEALTH dataset typically use wireless communication protocols to transmit data. Common protocols include Bluetooth, Wi-Fi, or other short-range communication technologies. These protocols allow for efficient and wireless data transfer between the sensors and the central unit.
The proposed methodology
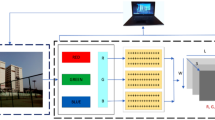
This paper proposes a new HAR hybrid system in WBAN architecture based on GAF algorithm and DenseNet169 model, in which Fig. 3 , shows the main steps of this architecture are as follows:
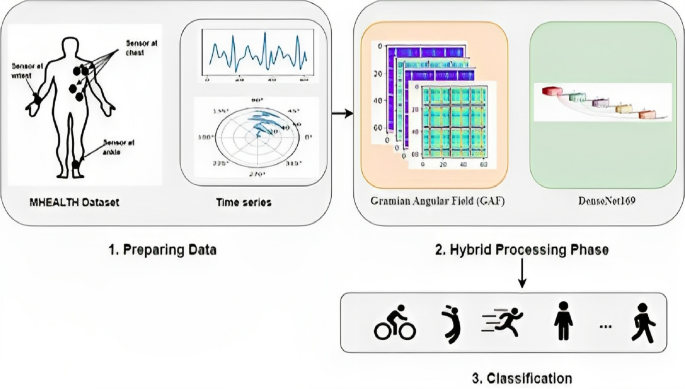
The proposed hybrid HAR system in WBAN architecture based on GAF algorithm and DenseNet169 model.
Preprocessing data
Most of the sensor’s initial data set consists of 1-dimensional time series 18
In the application of 2-dimensional, it is typically necessary to transform 1-dimensional time series into a format resembling 2-dimensional images. In the first step, the mobile health dataset is stored and represented as a CSV file and performs the following steps:
Resampling: The majority class (activity label = 0) in the dataset is downsampled to have 30,000 samples using the resample function from sklearn. utils. This is done to balance the class distribution in the dataset.
Outlier removal: the features in the dataset that have data points outside the 98% confidence interval are dropped using a for loop that iterates over each column except the last two columns (Activity and subject).
Train-test split: The data is divided into train and test sets based on the subject column. Data corresponding to subjects 9 and 10 are considered as the test set, while the remaining data is considered as the train set.
Time series dataset creation: A function named a window, which has a fixed size or a sliding nature, depending on the specific application or task. A fixed-size window selects a predetermined number of consecutive data points, while a sliding window moves across the dataset in steps, selecting a new subset of data for each step
Overall, the data is prepared dataset for time series modeling by balancing class distribution, removing outliers, and creating time series datasets for sequence modeling.
Gramian angular algorithm (GAF)
The bearing vibration signal is periodic in rotating machinery. It is challenging to directly extract the bearing defect features from the time-domain signal because random noise affects the periodic vibration signal. With GAF. Time-domain signals can be separated into characteristic and interference signals while maintaining their temporal link. In terms of human behavior recognition (HAR) and ECG signal monitoring, GAF has made some progress recently 41 . Consider a one-dimensional time series \(X=\{x_1,x_2,\dots , x_N\}\) of N observations. According to the GAF algorithm, the observation \(x_i; i=1,\dots , N\) are normalized to range \([-1,1]\) or [0, 1] such that the normalized observations are given by 18 :
respectively. Thus, a normalized one-dimensional time series is obtained, denoted by \({\hat{X}}\) . Next, \({\hat{X}}\) is converted to the polar coordinate system by taking the inverse cosine of each normalized observation \({\hat{x}}_i; i=1,\dots ,N\) to be the angle and i / N to be the radius. The observations in the polar coordinate system are given by 18 :
Note that, when normalizing the data to the range \([-1,1]\) the rang of \(\theta _i\) is \([0,\pi ]\) , whereas the range of \(\theta _i\) related to the data range [0, 1] is \([0,\pi /2]\) .
Finally, Gramian angular summation field (GASF) and Gramian angular difference field (GADF) are obtained to determine the time correlation between the sampling points from the angle perspective. GAF algorithm is applied for converting the one-dimensional time series into a two-dimensional image. Applying computer vision technology to the study of time involves scaling, coordinate axis transformation, and trigonometric function stages. The time series is converted into a polar coordinate system using ( 3 ). Using ( 4 ) and ( 5 ), you may get the GADF and GASF images, respectively. The GASF and GADF are, respectively, given by 18
DenseNet is a CNN architecture proposed Huang et al. 17 in 2017. It is designed to address the vanishing gradient problem that can occur in very DNNs by densely connecting all layers.
Every layer in DenseNet receives the feature maps of all the preceding layers and passes its own feature maps to all subsequent layers. This creates a dense connectivity pattern between layers, with information flowing through many paths, which helps to reduce the risk of information loss due to vanishing gradients. DenseNet models consist of dense blocks, which are composed of multiple convolutional layers with batch normalization and ReLU activation, followed by a concatenation operation that combines the feature maps from all preceding layers. These dense blocks are connected by transition layers, which include a pooling layer to reduce the spatial dimensions of the feature maps and a convolutional layer to reduce the number of channels. DenseNet models have achieved state-of-the-art performance on a variety of image classification tasks, object detection, and segmentation. The architecture of the DenseNet model consists of dense blocks and transition layers, as described below: 17
Input Layer : The input layer of a DenseNet model takes the image as input.
Convolutional Layer : The input is passed through a single convolutional layer with a small kernel size (that is 3x3), followed by batch normalization and ReLU activation.
Dense Block : The output of the first convolutional layer is passed through a dense block, which consists of multiple convolutional layers with the same kernel size and a number of filters. Each layer in the dense block takes as input the concatenated feature maps of all preceding layers in the block. The output of each layer is passed through batch normalization and ReLU activation before being concatenated with the previous layer’s output.
Transition Layer : After the dense block, a transition layer is added to reduce the number of feature maps by using 1x1 convolution and downsampling the spatial dimensions using average pooling.
Repeat Dense Block and Transition Layer : The above two steps (dense block and transition layer) are repeated multiple times to create a deep neural network architecture.
Global Average Pooling Layer : A global average pooling layer is added after the last dense block to reduce the spatial dimensions of the feature maps to a vector of size 1x1xk, where k is the number of filters in the last dense block.
Fully Connected Layer : Finally, a fully connected layer with softmax activation is added to produce the output probabilities for the different classes.
The dense connectivity pattern between layers in a DenseNet model allows for efficient parameter sharing, which leads to a compact model with fewer parameters compared to other deep neural network architectures. This, in turn, leads to faster training and reduced risk of overfitting 42 . There are several types of DenseNet models that have been proposed, including:
DenseNet-121 : This is the smallest and most widely used DenseNet model, which contains 121 layers. It has about 7 million parameters and is suitable for applications with limited computational resources.
DenseNet-169 : This model contains 169 layers and has about 14 million parameters. It is deeper and more complex than DenseNet-121, which can lead to improved performance on more challenging tasks.
DenseNet-201 : This model contains 201 layers and has about 20 million parameters. It is even deeper and more complex than DenseNet-169, which can provide better accuracy on more complex datasets.
DenseNet-264 : This model is the deepest and most complex DenseNet architecture, with 264 layers and about 33 million parameters. It is designed for very challenging tasks that require a lot of computational power.
The proposed method steps are stated in Algorithm 1.

The steps of the proposed method based on a hybrid GAF + DenseNet169.
Evaluation measures
To evaluate the proposed work, different measures given in ( 6 )–( 7 ) are used based on constructing a confusion matrix that summarized the following terms: Correct prediction is regarded as true positive (TP), while a prediction that is negative and is made as such is viewed as true negative (TN). False Positive is when something is categorized as negative but false positive (FP). This is regarded as False-Negative if it is positive and classified as false negative (FN). Accuracy is the rightly prognosticated sample rate. It’s the rate between rightly prognosticated samples to the total number of samples due to its straightforward meaning. It is considered the most most habituated criteria in the field of machine literacy evaluation, as illustrated in Eq. ( 6 ) 43
Matthews correlation coefficient (MCC) stands for Matthews Correlation Coefficient, used to assess the quality of binary classification models, in which it is computed as presented in Eq. ( 7 ).
F1-measure displays the harmonic mean between recall and precision as presented in Eq. ( 8 ) 43 .
Enivornment and parameters setting
In this section, the parameters to set up the environment of the proposed architecture, as given in Table 2 .
Experimentation and results
The model is implemented using Keras and TensorFlow. The input is concatenated with itself three times (300, 300, 3) using the Concatenate layer to facilitate the use of the transfer learning. This concatenated output is then passed as input to the pre-trained DenseNet169 model, which has been initialized with ImageNet weights. A Dense layer with 355 units and a ReLU activation function is added on top of the output of the DenseNet model. A Dropout layer with a rate of 0.2 is then applied to the output of the Dense layer. The output is then flattened using the Flatten layer. Finally, a Dense layer with 13 units with a softmax activation function is added to the flattened output, which outputs the predicted probabilities for each of the 13 classes as shown in Algorithm 1. The entire model is compiled using the Adam optimizer, and categorical cross-entropy loss function. Figure 4 presented the Confusion matrix.
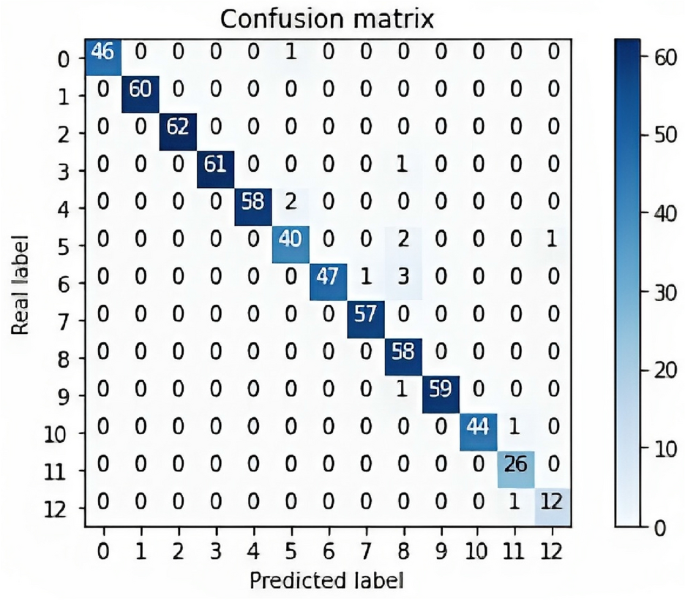
Confusion matrix for the model output.
DenseNet169 model applied to the MHEALTH dataset achieves an accuracy of 97.83% and an F1 of 97.83% and 97.64% for MCC. Figure 5 shows plots of accuracy and loss data curves. Table 3 shows the performance of a GAF + DenseNet169 model on a classification task across different hyperparameter configurations. The model’s accuracy, F1 score, and MCC are reported for each configuration. The results indicate that the best performance was obtained with an image size of 300, a dense layer of 355, and a batch size of 35, resulting in accuracy, F1 score, and MCC of 97.83%, 97.83%, and 97.64%, respectively. This indicates that larger image sizes and dense layers may improve the model’s performance. The lowest accuracy (86.18%), F1 score (86.18%), and MCC (85.21%) are achieved with an image size of 256, dense layer size of 256, and a batch size of 32. Examining the various configurations and their corresponding performance metrics:
When the image size is 300, the models generally perform better, with most configurations achieving high accuracy, F1 score, and MCC. In this image size category, the best configuration has a dense layer size of 355 and a batch size of 35, achieving 97.83% accuracy.
For an image size of 128, the performance tends to be lower compared to the 300 image size category, with the highest accuracy and F1 score of 94.41% achieved by the configuration with a dense layer size of 350 and a batch size of 32. This configuration also has an MCC of 93.98.
In the image size category of 256, the models have varying performances. The best configuration in this category has a dense layer size of 300 and a batch size of 32, achieving 93.32% accuracy, 93.32% F1 score, and 92.78% MCC.
The configurations with a dense layer size of 512 don’t seem to perform as well as those with smaller dense layer sizes. This could be due to overfitting or increased complexity, which might require more training data or a more optimized architecture.
The results also indicate that increasing batch size from 32 to 35 can lead to improving performance, as seen in configurations with image size 300 and dense layer sizes of 375 and 350.
The configurations with an image size of 300 perform consistently better than those with smaller image sizes, which suggests that the increased resolution might be beneficial for the specific task at hand. However, it would be interesting to test even larger image sizes to evaluate if this trend continues or if there is an optimal size for the best performance.
Regarding dense layer size, it seems to be a sweet spot around 350–380 for an image size of 300. For image size 128, the dense layer size of 350 achieves the best performance. However, the performance decreases with a dense layer size of 512 for both image sizes 128 and 256. Depending on the specific task and dataset, this may indicate that the dense layer size should be tuned carefully to avoid overfitting or underfitting.
Batch size has less impact on the performance compared to image size and dense layer size. However, in some configurations, increasing the batch size from 32 to 35 has improved the results, suggesting that it might be worth exploring a wider range of batch sizes to find the optimal value for the specific task.
The GAF+DenseNet169 model is a deep learning model that combines the GAF representation with a DenseNet169 architecture for image classification. The GAF representation is a feature extraction method that transforms a time series signal (such as an image) into an image-like representation that can be used in CNNs. This method has been shown to be effective in capturing the underlying patterns and correlations in time series data. DenseNet169 is a popular CNN architecture that uses densely connected layers to improve gradient flow and reduce the number of parameters compared to other CNN architectures such as visual geometry group (VGG) or ResNet. In this work, the GAF+DenseNet169 model was trained and evaluated on a classification task, with the goal of accurately classifying images. The hyperparameters of the model, such as image size, dense layer size, and batch size, were varied to determine their impact on the model’s performance.
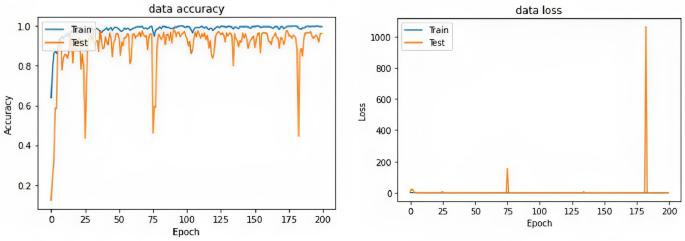
Plots of accuracy curves for the dataset.
Table 4 shows the evaluation results of the test cases for each individual sensor alone. The four sensors from the MHEALTH dataset are evaluated to determine the best sensor that contributes more to the proposed method. The information is presented below in a list as follows:
In experiment 8, Sensor 1 was tested using an image size of 150, a Dense layer of 375, and a batch size of 32. The results showed an ACC. of 77.17%, an F1 score of 77.17%, and an MCC of 75.35%.
For Sensor 2, experiment 3 utilized an image size of 150, a Dense layer of 375, and a batch size of 35. The corresponding metrics were an accuracy of 60.87%, an F1 score of 60.87%, and an MCC of 57.62%.
In the case of Sensor 3, experiment 2 used an image size of 150, a Dense layer of 360, and a batch size of 35. The achieved values were an accuracy of 86.96%, an F1 score of 86.96%, and an MCC of 85.86%.
Lastly, for Sensor 4, experiment 9 involved an image size of 128, a Dense layer of 512, and a batch size of 32. The recorded metrics were an accuracy of 57.92%, an F1 score of 57.92%, and an MCC of 54.49%.
To summarize, Sensor 3 yields the best results compared to other sensors. However, its individual performance is still far behind the combination of all sensors. This indicates that while Sensor 3 is superior, it is the collective data from all sensors that provide the most optimal outcome. The comparison results of the various models are given below for HAR in which each model is evaluated based on accuracy as shown in Table 5
Model 1 combines PCA with a CNN for feature extraction and AR.
Model 2 combines a decision tree classifier with the BGWO optimization algorithm for AR.
Model 3 combines the Adam optimizer with MEMM for AR.
Model 4 model in which no details about the specific architecture or method employed in this model are provided.
Model 5 combines LSTM and CNN architectures for AR.
Model 6 incorporates semisupervised learning techniques to leverage both labeled and unlabeled data for AR.
GAF+ DenseNet169 (the proposed model) utilizes GAF in combination with the DenseNet169 architecture, which is deep convolutional neural networks (DCNN), for AR. It’s worth noting that the table provides limited information, and the performance of the models may depend on various factors, such as the specific dataset used, the size of the training set, the preprocessing techniques applied, and other implementation details. Additionally, the proposed model (GAF+DenseNet169) achieves the highest accuracy, according to the table.
This paper introduces a DL network architecture that aims to recognize human activities using mobile sensor data. The proposed approach focuses on encoding time series into GAF images by combining global and local features. This innovative processing technique allows the training of the model using popular residual networks for image recognition. The obtained results, based on MHEALTH dataset, show that the proposed gives better accuracy and F1-measure than the other compared work.
Conclusions and future works
Nowadays, there is a growing interest in sensor-based HAR has been propelled by the widespread adoption of IoT and wearable technologies. These technological trends not only offer unparalleled convenience in our daily lives but also address concerns related to privacy, making them increasingly integral to modern living. In parallel, the advent of DL algorithms has ushered in a new era of possibilities, particularly in the context of HAR. The inherent capacity of DL algorithms to autonomously extract high-dimensional information has proven to be transformative, enabling end-to-end learning and enhancing the accuracy of AR systems. However, to build robust computer vision, especially in the realm of CNNs, encounters significant challenges. Factors such as external background interference, camera shielding, and other environmental variables can impede the efficacy of these vision-based systems. This highlights a critical gap where sensor-based HAR, with its intrinsic ability to mitigate such challenges, emerges as a compelling alternative.
Our proposed approach seeks to address these challenges through the integration of two DL models tailored specifically for sensor-based HAR. At the core of our methodology is the utilization of the GAF algorithm, a powerful tool for transforming 1-dimensional time series data obtained from sensors into 2-dimensional images. This transformation is pivotal in capturing nuanced patterns and temporal dependencies in the data, providing a comprehensive representation for subsequent analysis. Subsequently, we deploy the DenseNet model, known for its depth and interconnectedness, to perform accurate classification of various human activities. The unique architecture of DenseNet facilitates the automated processing of information acquired from diverse sensors. This integration not only enhances the efficiency of the recognition process but also contributes to the adaptability of the system to different sensor modalities.
In our experimental results, we conducted tests on the MHEALTH public activity dataset, a well-established benchmark for HAR research. The evaluation metrics employed, including accuracy, recall, and F-measure, serve as robust indicators of the effectiveness of our proposed method. The attained results underscore the prowess of our approach, with an impressive accuracy rate of 97.83%, an F-measure of 97.83%, and a MCC of 97.64%.
In future work, we will explore the potential of another DL model augmented with a feature selection optimizer. This strategic enhancement aims to further refine results by selecting and prioritizing relevant features, thereby improving both predictive performance and interpretability. Additionally, this optimization effort seeks to streamline computational complexity, reducing time requirements and minimizing loss in the HAR system. Overall, these endeavors contribute to the ongoing evolution of sensor-based HAR systems, enhancing their reliability and applicability in real-world scenarios.
Data availibility
The dataset used during the current study is available in the UCI Machine Learning Repository, MHEALTH Dataset Link .
Al-Mishmish, H. et al. Critical data-based incremental cooperative communication for wireless body area network. Sensors 18 , 3661 (2018).
Article PubMed PubMed Central ADS Google Scholar
Alkhayyat, A., Gazi, O. & Sadkhan, S. B. The role of delay and connectivity in throughput reduction of cooperative decentralized wireless networks. Math. Probl. Eng. 2015 (2015).
Liu, X., Hu, F., Shao, M., Sui, D. & He, G. Power allocation for energy harvesting in wireless body area networks. China Commun. 14 , 22–31 (2017).
Article ADS Google Scholar
Özyer, T., Ak, D. S. & Alhajj, R. Human action recognition approaches with video datasets-a survey. Knowl.-Based Syst. 222 , 106995 (2021).
Article Google Scholar
Zhang, Y.-D., Satapathy, S. C., Guttery, D. S., Górriz, J. M. & Wang, S.-H. Improved breast cancer classification through combining graph convolutional network and convolutional neural network. Inf. Process. Manag. 58 , 102439 (2021).
Vepakomma, P., De, D., Das, S. K. & Bhansali, S. A-wristocracy: Deep learning on wrist-worn sensing for recognition of user complex activities. In 2015 IEEE 12th International conference on wearable and implantable body sensor networks (BSN) , 1–6 (IEEE, 2015).
Qin, J., Liu, L., Zhang, Z., Wang, Y. & Shao, L. Compressive sequential learning for action similarity labeling. IEEE Trans. Image Process. 25 , 756–769 (2015).
Article MathSciNet PubMed ADS Google Scholar
Tan, C. et al. Research on gesture recognition of smart data fusion features in the iot. Neural Comput. Appl. 32 , 16917–16929 (2020).
Wang, L., Sun, Y., Li, Q., Liu, T. & Yi, J. Two shank-mounted imus-based gait analysis and classification for neurological disease patients. IEEE Robot. Autom. Lett. 5 , 1970–1976 (2020).
Dua, N., Singh, S. N., Semwal, V. B. & Challa, S. K. Inception inspired cnn-gru hybrid network for human activity recognition. Multimed. Tools Appl. 1–35 (2022).
Pärkkä, J., Cluitmans, L. & Ermes, M. Personalization algorithm for real-time activity recognition using pda, wireless motion bands, and binary decision tree. IEEE Trans. Inf Technol. Biomed. 14 , 1211–1215 (2010).
Article PubMed Google Scholar
Feng, Z., Mo, L. & Li, M. A random forest-based ensemble method for activity recognition. In 2015 37th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC) , 5074–5077 (IEEE, 2015).
Uddin, M. T. & Uddiny, M. A. A guided random forest based feature selection approach for activity recognition. In 2015 international conference on electrical engineering and information communication technology (ICEEICT) , 1–6 (IEEE, 2015).
Chen, Z., Zhu, Q., Soh, Y. C. & Zhang, L. Robust human activity recognition using smartphone sensors via ct-pca and online svm. IEEE Trans. Industr. Inf. 13 , 3070–3080 (2017).
Zhou, D.-X. Universality of deep convolutional neural networks. Appl. Comput. Harmon. Anal. 48 , 787–794 (2020).
Article MathSciNet Google Scholar
Zhao, Y., Yang, R., Chevalier, G., Xu, X. & Zhang, Z. Deep residual bidir-lstm for human activity recognition using wearable sensors. Math. Probl. Eng. 2018 , 1–13 (2018).
Huang, G., Liu, Z., Van Der Maaten, L. & Weinberger, K. Q. Densely connected convolutional networks. In Proceedings of the IEEE conference on computer vision and pattern recognition , 4700–4708 (2017).
Xu, H. et al. Human activity recognition based on gramian angular field and deep convolutional neural network. IEEE Access 8 , 199393–199405 (2020).
Jiang, W. & Yin, Z. Human activity recognition using wearable sensors by deep convolutional neural networks. In Proceedings of the 23rd ACM international conference on Multimedia , 1307–1310 (2015).
Ravi, D., Wong, C., Lo, B. & Yang, G.-Z. A deep learning approach to on-node sensor data analytics for mobile or wearable devices. IEEE J. Biomed. Health Inform. 21 , 56–64 (2016).
Zheng, X., Wang, M. & Ordieres-Meré, J. Comparison of data preprocessing approaches for applying deep learning to human activity recognition in the context of industry 4.0. Sensors 18 , 2146 (2018).
Ito, C., Cao, X., Shuzo, M. & Maeda, E. Application of cnn for human activity recognition with fft spectrogram of acceleration and gyro sensors. In Proceedings of the 2018 ACM international joint conference and 2018 international symposium on pervasive and ubiquitous computing and wearable computers , 1503–1510 (2018).
Batool, M. et al. Depth sensors-based action recognition using a modified k-ary entropy classifier. IEEE Access (2023).
Abhishek, K. & ud din Tahir, S. B. Human verification over activity analysis via deep data mining. Comput. Mater. Continua (CMC) 75 , 1391–1409 (2023).
Boga, J. & Kumar, V. D. Human activity recognition by wireless body area networks through multi-objective feature selection with deep learning. Expert. Syst. 39 , e12988 (2022).
Mishra, C. S., Sampson, J., Kandemir, M. T. & Narayanan, V. Origin: Enabling on-device intelligence for human activity recognition using energy harvesting wireless sensor networks. In 2021 Design, Automation & Test in Europe Conference & Exhibition (DATE) , 1414–1419 (IEEE, 2021).
Reich, O., Hübner, E., Ghita, B., Wagner, M. & Schäfer, J. Performance evaluation of bluetooth in a wireless body area network for practical applications. In 2020 IEEE 11th Sensor Array and Multichannel Signal Processing Workshop (SAM) , 1–5 (IEEE, 2020).
Fan, Y.-C., Tseng, Y.-H. & Wen, C.-Y. A novel deep neural network method for har-based team training using body-worn inertial sensors. Sensors 22 , 8507 (2022).
He, Z. & Bai, X. A wearable wireless body area network for human activity recognition. In 2014 Sixth International Conference on Ubiquitous and Future Networks (ICUFN) , 115–119 (IEEE, 2014).
Huan, R. et al. A hybrid cnn and blstm network for human complex activity recognition with multi-feature fusion. Multimedia Tools Appl. 80 , 36159–36182 (2021).
Damirchi, H., Khorrambakht, R. & Taghirad, H. D. Arc-net: Activity recognition through capsules. In 2020 19th IEEE International Conference on Machine Learning and Applications (ICMLA) , 1382–1388 (IEEE, 2020).
Jalal, A., Batool, M. & Kim, K. Stochastic recognition of physical activity and healthcare using tri-axial inertial wearable sensors. Appl. Sci. 10 , 7122 (2020).
Article CAS Google Scholar
Uddin, M. Z. & Hassan, M. M. Activity recognition for cognitive assistance using body sensors data and deep convolutional neural network. IEEE Sens. J. 19 , 8413–8419 (2018).
Tahir, S. B. U. D., Jalal, A. & Kim, K. Wearable inertial sensors for daily activity analysis based on adam optimization and the maximum entropy markov model. Entropy 22 , 579 (2020).
Lyu, L., He, X., Law, Y. W. & Palaniswami, M. Privacy-preserving collaborative deep learning with application to human activity recognition. In Proceedings of the 2017 ACM on Conference on Information and Knowledge Management , 1219–1228 (2017).
Ha, S. & Choi, S. Convolutional neural networks for human activity recognition using multiple accelerometer and gyroscope sensors. In 2016 international joint conference on neural networks (IJCNN) , 381–388 (IEEE, 2016).
Chen, K. et al. A semisupervised recurrent convolutional attention model for human activity recognition. IEEE Trans. Neural Netw. Learn. Syst. 31 , 1747–1756 (2019).
Qin, Z., Zhang, Y., Meng, S., Qin, Z. & Choo, K.-K.R. Imaging and fusing time series for wearable sensor-based human activity recognition. Inf. Fusion 53 , 80–87 (2020).
Banos, O. et al. mhealth dataset. http://archive.ics.uci.edu/ml/datasets/mhealth+dataset (2014). Accessed: [Insert date here].
Dua, N., Singh, S. N., Semwal, V. B. & Challa, S. K. Inception inspired cnn-gru hybrid network for human activity recognition. Multimedia Tools Appl. 82 , 5369–5403 (2023).
Cui, J., Zhong, Q., Zheng, S., Peng, L. & Wen, J. A lightweight model for bearing fault diagnosis based on gramian angular field and coordinate attention. Machines 10 , 282 (2022).
Doe, J., Smith, A. & Brown, R. A comparative analysis of densenet architectures: Performance and applications. In Proceedings of the International Conference on Deep Learning and Computer Vision , 123–130 (2023).
Sokolova, M., Japkowicz, N. & Szpakowicz, S. Beyond accuracy, f-score and roc: a family of discriminant measures for performance evaluation. In AI 2006: Advances in Artificial Intelligence: 19th Australian Joint Conference on Artificial Intelligence, Hobart, Australia, December 4-8, 2006. Proceedings 19 , 1015–1021 (Springer, 2006).
Download references
Open access funding provided by The Science, Technology & Innovation Funding Authority (STDF) in cooperation with The Egyptian Knowledge Bank (EKB).
Author information
Authors and affiliations.
Department of Computer Science, Faculty of Computers and Information, Mansoura University, Mansoura, 35516, Egypt
Ehab El-Adawi, Ehab Essa, Mohamed Handosa & Samir Elmougy
You can also search for this author in PubMed Google Scholar
Contributions
E.A., E.S., M.H., and S.E.: conceptualization, developing the proposed methodology for the analysis, and formal analysis. E.A.: software, validation, and visualization, and prepared an initial draft. E.S., M.H., and S.E.: project administration. E.S., M.H., and S.E.: project directors. All authors review and edit the revised version.
Corresponding authors
Correspondence to Ehab Essa or Samir Elmougy .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
El-Adawi, E., Essa, E., Handosa, M. et al. Wireless body area sensor networks based human activity recognition using deep learning. Sci Rep 14 , 2702 (2024). https://doi.org/10.1038/s41598-024-53069-1
Download citation
Received : 16 June 2023
Accepted : 27 January 2024
Published : 01 February 2024
DOI : https://doi.org/10.1038/s41598-024-53069-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Sensors (Basel)

A Survey on Wireless Wearable Body Area Networks: A Perspective of Technology and Economy
David samuel bhatti.
1 Faculty of Information Technology, University of Central Punjab, Lahore 54590, Pakistan
Shahzad Saleem
2 School of Electrical Engineering and Computer Science, National University of Sciences and Technology, Islamabad 44000, Pakistan
Azhar Imran
3 Faculty of Computing & A.I., Air University, Islamabad 42000, Pakistan
Zafar Iqbal
Abdulkareem alzahrani.
4 Computer Science & Engineering Department, Al Baha University, Al Baha 65799, Saudi Arabia
HyunJung Kim
5 Department of Computer Science and Engineering, Chungnam National University, Daejeon 34134, Korea
Associated Data
Not applicable.
The deployment of wearable or body-worn devices is increasing rapidly, and thus researchers’ interests mainly include technical and economical issues, such as networking, interoperability, security, power optimization, business growth and regulation. To address these issues properly, previous survey papers usually focused on describing the wireless body area network architecture and network protocols. This implies that deployment issues and awareness issues of wearable and BAN devices are not emphasized in previous work. To defeat this problem, in this study, we have focused on feasibility, limitations, and security concerns in wireless body area networks. In the aspect of the economy, we have focused on the compound annual growth rate of these devices in the global market, different regulations of wearable/wireless body area network devices in different regions and countries of the world and feasible research projects for wireless body area networks. In addition, this study focuses on the domain of devices that are equally important to physicians, sportsmen, trainers and coaches, computer scientists, engineers, and investors. The outcomes of this study relating to physicians, fitness trainers and coaches indicate that the use of these devices means they would be able to treat their clients in a more effective way. The study also converges the focus of businessmen on the Annual Growth Rate (CAGR) and provides manufacturers and vendors with information about different regulatory bodies that are monitoring and regulating WBAN devices. Therefore, by providing deployment issues in the aspects of technology and economy at the same time, we believe that this survey can serve as a preliminary material that will lead to more advancements and improvements in deployment in the area of wearable wireless body area networks. Finally, we present open issues and further research direction in the area of wireless body area networks.
1. Introduction
Wireless networks have become an indispensable part of social, defense and healthcare applications. These applications have received very swift support from different wireless network interfaces such as Personal Area Network (PAN), Body Area Networks (BAN), WiFi 802.11, WiMAX and cellular [ 1 , 2 ]. These technologies are extensively being used in healthcare systems [ 3 ]. In addition, they are also very benign in social gatherings, which can be envisioned from the popularity of wireless communication when friends or guests are sitting at a coffee cafe or hotel and share some information using WiFi or Bluetooth; passengers can pay for their tickets at a ticketing booth while connecting their mobile or smartphone to the electronic booth wirelessly. Similarly, it has also been observed that passengers traveling on a train or bus have demonstrated a need to have a hotspot (ad hoc network) of mobiles and smartphones for data sharing. In addition to all that usage, the application market of mobile and smartphones is becoming saturated day by day, and novel paradigms in mobile devices and sensors are arising in different dimensions of human life. These are basically the wireless wearable body area networks [ 4 ], which are assuring the improvement in the quality of human health, which was not possible for smartphones and mobiles to achieve alone. The terms “wearable”, “wearable devices”, “wireless BAN (Body Area Network)” or “wearable technology” are interchangeable. Similarly, wireless wearable body area networks and wearable wireless body area networks are also used interchangeably in the literature. These terms refer to small electronic or mobile devices, microchips, or other computing devices that possess the capability of communicating data wirelessly. Furthermore, these devices are fabricated into gadgets, clothes, or accessories that can be worn, patched on the body, or devices that can be implanted, injected or ingested in the body [ 5 ].
The outstanding use of wearable/body-worn technology is giving rise to new dimensions in textile, sports, medicine, healthcare, and fitness applications, putting them into a bigger category of wireless networks known as Wireless Body Area Networks (WBANS) [ 6 , 7 , 8 , 9 ]. Smartwatches, wristbands, smart glasses, smart jewelry, electronic garments, skin patches, etc., are a few examples of such body-worn or wireless wearable devices [ 10 , 11 ]. They can easily be integrated with smartphones, laptops, or data servers using any of the wireless technologies shown in Figure 1 .

Health monitoring smartwatch [ 13 ].
Figure 1 shows how wearables monitor a person’s health and how the health data can be transferred to smartphones. There are a lot of videos available on YouTube that show how health monitoring smartwatches can be integrated with smartphones, mobiles, or laptops to monitor life-critical information. One such channel that can be found on this topic is “Jimmy is Promo”, which has uploaded a very good video tutorial for connecting a vital sign monitoring smartwatch to a mobile phone [ 12 ].
One of the best surveys on the consumer’s attitude toward the use of connected and wearable BAN health devices was carried out by Victoria Lambert [ 14 ]. This study was carried out on the people of the United Kingdom (UK) to assess how they see these devices being used in healthcare. It is a 2016 study, but it clearly predicts the future perspectives of the adoption of wearable BAN devices at individual, group (troops, BBN, etc.), and organization (hospital) levels. It shows that more than 80% of people want to have wearable BAN devices in healthcare systems. This study shows that different people are using these devices for different purposes, as shown in Figure 2 a. Presently, it can be seen from the data how extensively these devices are being shipped and used.

Wearable WBAN survey. ( a ) Usage and popularity of wearable/connected health devices [ 18 ]. ( b ) reduction in death, visits, admissions, and cost [ 16 ].
The use of wearable BAN devices has been increasing very rapidly for the last couple of years. Different reports have shown the present and future trends of usage of these devices. For instance, a 17% CAGR (Compound Annual Growth Rate) of the wearable BAN market is expected between 2021 and 2025, which was recently reported by Business Wire (UK) [ 15 ]. A separate section ( Section 3 ) is dedicated to a global market of wearable BAN devices whose increased popularity and adoption have resulted in a reduction in mortality rate, patient visits and admissions to emergency departments, and costs per patient. Figure 2 b shows quite encouraging figures of these parameters in terms of reduction in the percentages of the above-mentioned variables [ 16 ]. It affirms the well-being of human health due to the use of wearable BAN devices at personal, mobile (ambulance, travel, troops), and organizational (hospital) levels [ 17 ].
1.1. Research/Survey Methodology
Since this manuscript is a survey article, it may require a lot of citations and references from other journals, conference articles, books, lectures, audio/video tutorials, business reports, blogs, websites, and published and even unpublished material. We believe in a fair and unbiased research methodology. We tried our best to keep ourselves unbiased in citing and referencing the material and include justifiable content regardless of the fame and ranking of the publishers. Our study does not promote any publisher or journals as sometimes observed and heard in research groups. However, the major keywords used to search the contents were “wearable devices”, “body-worn devices”, “wireless wearable body area networks”, “wireless technologies used in WBAN”, “wearable wireless technologies”, “wearable wireless protocols”, “WBAN security threats”, “WBAN wireless security protocols”, “state of the art wearable security protocols”, “WBAN and Wearable regulatory bodies”, “wearable Compound Annual Growth Rate”, “wearable CAGR”, “wearable WBAN challenges”.
1.2. What Questions Does This Survey Answer?
This survey efficiently answers the following questions.
- 1. What is a wireless wearable body area network and its communication architecture?
- 2. What sensors are used in Wearable Wireless BANs, and what end products and solutions are available in the market?
- 3. What are the potential wireless technologies used to develop WWBANs, and what security threats and control measures are available?
- 4. What does the future hold, and what major challenges do the wireless wearable body area devices have to face?
- 5. What are the major projects and research directions in this area?
1.3. Contributions
We believe in contributive and productive studies, which is why we have put in the best of our efforts to make this article productive and cultivatable for the broad spectrum of viewers. We have gone through many survey articles; the majority of them focus on a limited set of WBAN perspectives. For example, Hajar et al. [ 18 ] discussed WBAN security, privacy, and energy harvesting concerns but did not discuss WBAN sensors, medical and non-medical devices, growth rate and regulatory bodies. Some articles, such as that of Kim et al. [ 19 , 20 ], were found to only emphasize the dynamic resource management perspectives of WBANs and the resource allocation at the MAC layer. Asisha et al. [ 21 ] discussed the WBANs MAC layer. Propagation characteristics and channel modeling for Internet of Bodies (IoBs) using human body communication are reviewed by Kadir et al. [ 22 ]. Therefore, the major contributions of this study are listed below, which help a prospective reader to judge the productivity and usefulness of this study. Zhong et al. [ 23 ] only bring WBANs technical requirements and challenges into discussion.
- 1. During our study on WBANs, we found that a majority of the reports focus on only a particular set of viewers as discussed above.
- 2. The present article addresses maximum perspectives of wireless wearable body area networks such as architecture, components, sensors, devices, health systems, wireless technologies, security concerns, projects, regulations, and most important, and Compound Annual Growth Rate (CAGR).
- 3. A special section is added in this survey that focuses on the emerging WBAN technologies, such as energy harvesting, human body communication, quantum computing, graph neural networks (GNN), artificial intelligence (machine and deep learning), blockchain, and digital twins. Such a section is rarely seen in surveys or review articles.
- 4. Since the article is interdisciplinary, technical terms of a particular field are briefly explained on the spot so that a specialist of one field may understand the concepts of another without repetitive switching from this article to another.
2. WBAN Technical Issues
2.1. wban architecture.
WBANs consist of a control unit and sensors. These sensors might be implanted in the body (implanting medical devices IMB) or they might be wearable, body-worn, or body-patched. These sensors can communicate with each other or with the help of a control unit using a wireless link. They can monitor vital health signs such as “Body Temperature”, “Blood Pressure (BP)”, “Respiration Rate (RR)”, “Skin Perspiration”, “Blood Glucose”, “Heart Rate (HR)”, “Oxygen Saturation”, “Electrocardiogram (ECG)” etc. The sensors can also capture similar parameters from the environment, such as pollution, which is directly linked to cardiac and pulmonary diseases [ 24 ].
In the sequel to the figure, Figure 3 shows how data from a smartphone/gateway/ coordinator can be sent to a centralized repository (medical server) for medical and paramedical staff to take necessary decisions. This server might be cloud-based to provide 24 h service to different stakeholders [ 11 ]. A typical architecture of a wireless wearable BAN is shown in Figure 3 . In this architecture, the communication system is divided into three layers as follows [ 25 ].

Wearable body-worn motivational model [ 11 ].
Layer-1: An intra-BAN devices communication tier, where different sensors collect body vital signs such as BP, HR, sugar level, ECG, etc., and they pass it to the control unit or even directly to the gateway depending upon the wireless link.
Layer-2: This layer is a setup of inter-BAN communication in which the body coordinator sends information to a personal server that might be a smartphone, mobile, PDA, or laptop.
Layer-3: From the personal server, the health information is accessed by different medical or paramedical entities such as caregivers, doctors, or health systems/subsystems using an internet connection (Satellite, GPRS).
The evolutionary perspectives of the discussed architecture can be reviewed from the article published by Aleksandr et al. [ 5 ], which provides a very comprehensive overview of state-of-the-art wearables, their communication, history, and challenges.
The following is a list of components that are necessary to make a wireless wearable body area network [ 25 , 26 ].
Sensors are devices that take some input from physical surroundings and respond to it [ 27 ]. Biosensors are concerned with the vital sign monitoring of living beings [ 26 ]. They may be used to collect health information such as BP, HR, ECG, and body temperature and transmit it to a BAN control unit [ 28 ]. The requirement of body sensors is that they must adhere to lightweight, low power consumption and fast switching between sleep and wake-up mode for energy saving. Moreover, the material used to make sensors should not be harmful to the human body. Controller Unit or Sink receives data from the sensor and transmits it to the gateway or personal server. It can also generate alerts upon receiving abnormal values of vital signs [ 28 ]. Antena is responsible for the basic transmission and reception of data. It must be small, lightweight, human-body favored, and operate at high frequencies. The design of a flexible, small size and power-efficient antenna for wireless wearable body area networks is proposed by Karthikeyan et al. [ 29 ]. Similarly, as a key component, a high-performance UWB antenna for WBANS was also designed by Yazdandoost et al. [ 30 ]. The authors used two layers of a substrate to nullify the effect of a human body on the performance of a proposed antenna. Other intelligent antennae designs for wireless wearable body area networks are proposed by Zhang et al. [ 31 , 32 ]. Communication is the major component of WBANs. Wireless mode of communication is used by BAN nodes to make transmissions, but it must lie in those frequency bands that are not resilient to interference caused by the co-existence of similar networks [ 26 ]. Therefore, there should be a barrier that can avoid mixing frequencies while operating in real-time setups. The communication protocol must ensure seamless handover when the BAN user leaves the covering area of one gateway and enters another. Some of the techniques proposed for this component are [ 33 , 34 , 35 ]. Moreover, a detailed survey on vertical handover techniques for integrating wireless body area networks with other heterogeneous is documented by Saurav et al. [ 36 ]. Security is another key part of WBAN communication that must ensure the data do not leak and no malicious entity hacks or cracks it [ 26 ]. Strong access control and encryption techniques need to be applied to BAN data when they are transferred from the body to some centralized repository. Personal Server or Gateway is another important component that resides between BAN controller and the cloud, i.e., internet. It receives data from the BAN control unit and passes it to the cloud or centralized medical server [ 28 ]. Internet link is also a crucial component that is responsible for securely (use of VPN, IPSec, SSL, TLS, etc.) transferring health information from the local gateway to a remote centralized server. The link should be reliable in terms of security, availability, and turnaround time [ 37 ]). There must be a component called alerts mechanism that should generate alerts in different critical conditions, such as reception of abnormal vital sign signals or when the battery power critically goes low, etc. [ 28 ]. There has to be a medical server (centralized repository) where data could be stored and retrieved at any time by caregivers, physicians, or other data consumers [ 28 ]. With only BAN users (such as patient, sportsman) and medical staff (such as caregivers, physicians), the BAN is incomplete. Therefore, all the components discussed above are used to connect BAN users and medical staff.
2.2. Types of Sensors
Wireless Wearable BAN Sensors are the product of collaborative and mutual research efforts of researchers belonging to different fields of science and engineering; Figure 4 represents this well. Each sensor in a wireless wearable body area network is completely provided with communication capabilities and can act as an autonomous device [ 25 ]. Wireless wearable BAN architecture that is used to send health information to remote medical servers can have different types of sensors. In this study, they are discussed on the basis of implantation and their functions. The discussion about them is equally beneficial for the wireless wearable BAN user, practitioners, engineers, and designers.

Wireless wearable BAN field.
On the basis of implantation, wireless wearable BAN sensors are categorized into five main types to assure the success of a healthcare system [ 25 , 38 ].
2.2.1. Type-I Implantable
These are sensor nodes that are implanted inside the human body, such as pacemakers (e.g., Medtronic Micra) [ 39 , 40 ]. The importance of these sensors can be understood from research efforts being made to help blind people to see [ 41 ]. One of the fruitful outcomes of this effort is the retina prosthesis chip, which is implanted inside the human eye, and persons who are visually impaired may be able to see at a reasonable level [ 42 ]. Pacemakers are the most widely implanted devices in the human body under the chest or abdomen. The sensors of pacemakers are used to monitor cardiovascular irregularities. Medtronic Micra is one of the examples of pacemakers that have quite a long life (12 years) and can be scanned by MRI (Magnetic Resonance Imaging). Intra-Cranial Pressure Monitoring Sensors monitor the pressure that rises up due to the irregularities of cerebrospinal fluid, head injuries, or as a consequence of cerebral edema. These may lead to severe brain damage, nervous breakdown, or death. The most popular sensor used implanted in the human body for detecting the irregular changes in the value of ICP and IOP are MEMS pressure sensors and RF oscillators. Both types operate at 2.4 GHz. IOP stands for Intra-Ocular Pressure whose irregularity may cause intraocular pressure, which is carefully regulated, and disturbances often result in issues such as glaucoma, uveitis, and retinal detachment [ 43 ]. Glaucoma is a set of eye conditions that may break an optic nerve; it is often caused by high blood pressure and may lead to vision loss. Uveitis is an eye inflammation that causes glaucoma. Retinal detachment is an emergency eye condition in which the retina becomes detached from blood vessels, stopping oxygen supply to it. Cardiovascular Pressure Sensors observe the narrowing of the blood artery even after angioplasty, which is called restenosis. Continuous monitoring of chronic blood pressure that may cause heart failure, hypertension, or restenosis is very necessary. One of the recent developments in this regard is the FDA-approved chronic blood pressure monitoring device from CardioMEMs that helps detect heart failure. In addition to this, other recommended devices for chronic blood pressure monitoring are MEMS capacitive sensors, surface acoustic wave resonators, and accelerometers. Neurosensors have received a lot of interest from the research community for dealing with addiction, epilepsy (brain disorder), Parkinson’s (neurological movement disorder), and Alzheimer’s (gradual loss of memory) disease, etc. One of the reported cases is the RFID-inspired neurosensor considered for a wireless brain–machine interface, which is battery-less and the energy storage is accomplished using the concept of RF energy harvesting [ 44 ]. Similar research work is presented by Xiang et al. in which authors have proposed and tested a self-powered brain machine that harvests energy from the movements of a human body part and sends a signal to the brain to cease some action [ 45 ]. Glucose sensors/meters are mostly referred to as amperometric sensors. Glucose sensors are meant to determine the blood sugar level of a person while playing an important role in dealing with diabetes mellitus. Most people in their homes use a finger-pricking method to test their blood sugar level. However, with the progression of research in wireless communication, computer science, engineering, chemistry and material sciences, the dream of under-skin wearable devices has become a reality [ 46 ]. These sensors can be used for 90 days [ 47 ]. The registered devices being used for continuous monitoring of sugar levels in the blood are GlucoWatch ® Biographer, CGMS ® and GlucoDay ® [ 48 ]. There was a breakthrough in wearable smart textiles with the production of lightweight and mechanically robust wearable electronics that are based upon bio-inspired muscle fibers [ 49 ].
2.2.2. Type-II Ingestibles
These sensors are small in size and can be ingested similarly to pills. These sensors are mostly used in ingestible capsules that are disposable and used to diagnose the correlation between ingested pharmaceutical drugs and physical activities of body responses such as heartbeat, quality of sleep and blood pressure, etc. [ 39 ]. Imaging capsules are the sensors that are passed through the gastrointestinal tract as disposable capsules. These can provide real-time data in the form of images or videos about the small bowel, gastrointestinal tract, esophagus, and large intestine at a rate of a maximum of 2 Mbps. Transmitted data by these imaging capsules can be used for different diagnostic purposes. For example, these devices are one of the best alternatives to aggressive endoscopic procedures, which may cause the generation of different gases in the human body (gut) revealing a strong correlation to gastrointestinal disorders [ 39 ].
2.2.3. Type-III Injectables
Nano-technology is now going to bring a great revolution in bio-medical technology. This is a predicted future of biomedical devices with such a small size that would allow them to be injected with the help of a syringe [ 39 ]. Injectable micro-sensors are very small-sized sensors with a thickness of a few human hairs and the length of a rice grain. Recently, a demonstration of injectable bio-sensors was given by Profusa Inc. [ 50 ]. In their demonstration, they injected bio-sensors called Lumee Oxygen sensors using a needle. The injected sensor has the capability of observing oxygen levels in the tissues around it [ 39 ]. pH sensors have significant importance in monitoring tumor growth and the effectiveness of anticancer treatments. American scientists have developed pH sensors that are based on nanocrystal quantum dots and operate in the human pH range. These are injectable devices that can monitor the growth of tumors on a real-time basis [ 51 ].
2.2.4. Type-IV Patchable: Body Surfaced/Patched
Sensor nodes that can be patched on the surface of a human body in their direct contact with it for establishing the communication network of on-body devices are termed as patched or surfaced wearable or simply patchable. The attraction of patchable devices is increasing in the biomedical industry due to their interfacing with skin on a cellular to molecular level. They are spatiotemporally precise in terms of bio-sensing for diagnostic and therapeutic purposes [ 52 , 53 ]. High blood sugar is a disease, but if monitored regularly, the chronic effects can be mitigated. Patchables are playing a very key role in achieving this [ 54 ]. A very promising study has been carried out on measuring the effects of ultra-violet radiations on the body using patchables [ 55 ]. A very brief but smart study on patchable sensors can be seen in [ 56 , 57 ]. This setup is used for providing an ambulance-based health monitoring system for a person [ 40 ].
2.2.5. Type-V Proximity-Based Devices
Sensor nodes that are installed in close proximity (5–10 cm) to the body surface, e.g., smartphones and smartwatches, help in monitoring body fitness, where the values and results of vital signs are displayed on smart devices. Sweat-powered wearable electrochromic biosensors are one great contribution that provides a non-invasive way of monitoring lactate concentration (high means lack of oxygen) in the body [ 58 ]. WBAN devices are very diverse in nature. To monitor the same life sign in humans, they can be found in different forms such as implantable (in-body), body-surfaced (on-body), and wearable. This provides a great choice for a person trying to select a health monitoring sensor for a particular vital sign observation [ 59 ].
Oximeter sensors are used to find the oxygen absorption (saturation) level in body cells. Devices make use of the human fingertip to find the values. Oxygen absorption level is one of the critical vital signs that determines how well the oxygen is being provided to body cells by the red blood cells to keep them alive [ 60 ]. Low oxygen supply turns the red color of the tissue to blue, which means their life is shortening. It also greatly damages the functionality of your brain. The World Health Organization (WHO) has also provided a very good tutorial on using an oximeter on its website [ 61 ]. However, the detailed principles of the oximeter are beyond the scope of this study but can be retrieved from [ 62 ]. A well-known example of this device is the Welue O 2 Ring Oxygen Monitor, which is shown in Figure 5 .

Wellue ® O2 TM Ring—continuous oxygen monitor [ 63 ].
2.2.6. Type-VI Textile Structured Devices
These are the structures and materials that sense and react to environmental factors. They are being used in the textile industry, telecommunications, biochemistry, bio and information technology, etc. Textile-based sensors have obtained significant attention in smart wearable technology. They are low-cost, comfortable, and flexible. They can be used remotely to observe the physiological parameters of the human body [ 64 ]. The development of textile-based energy storage devices are outstanding research works that can be used in wearable technology to address the power consumption issues [ 65 ]. Advances in wearable electronics are going to replace spacey, non-flexible and uncomfortable wearable electronics [ 66 ]. In addition, printed textile batteries are also being researched for wearables, which will mitigate energy problems of these devices [ 67 ].
This diversity is summarized in Table 1 . In addition to this, one of the surveys reports that based on transducing mechanisms of biosensors, we can categorize them into optical and thermal detectors, resonant, Ion-Sensitive FETs (ISFETs) and electro-chemical biosensors [ 68 ]. Another survey that sheds light on the biosensor and their state-of-the-art development is carried out by Naresh et al. [ 69 ]. These articles are good enough to review.
Diversity of WBAN sensors used for life sign monitoring.
| Sensor | Implantation | Observation |
|---|---|---|
| Guardian Real-time | inside the body | Sugar |
| MiniMed 530G with Enlite | wearable, injectable | Sugar |
| FreeStyle | inside the body | Sugar |
| Eyeglasses biosensor | body-worn | Sugar |
| Eyeglasses biosensor | body-surface | Sugar |
| Guardian Real-time | inside the body | Sugar |
| IFever | body-worn | Temperature |
| ISense | body-worn | Temperature |
| Ran’s Night | body-worn | Temperature |
| FeverFrida thermometer | body-surfaced | Temperature |
| STEMP sensor | body-surfaced | Temperature |
| Aranet medical thermometer | body-worn | Temperature |
| Propeller | body-worn | Asthma |
| AirSonea | body-worn | Asthma |
| Wing | body-worn | Asthma |
| BH1790GLC | body-worn | HR |
| TCRT 1000 | body-worn | HR |
| Smart QHeart Rate Sensor | body-worn | HR |
| Polar H10 | body-worn | HR |
| Pulse sensor | body-worn | HR |
| MPU-9250 Invensense | body-worn | Motion |
| MMA 8451Q, accelerometer | body-worn | Motion |
| LSM 303 DLHC | body-worn | Motion |
| BNO055 | body-worn | Motion |
| MPU-9250 Invensense | body-worn | BP |
| Biosignals plux | body-worn | BP |
| Proven BPM-337BT | body-worn | BP |
| Omron M7 Intelli IT | body-worn | BP |
2.3. Wireless Technologies
Wireless body area networks are found in the form of sensing devices implanted on or inside the body of a living organism. These devices are extensively used for monitoring vital signs of the body using wireless transmission protocols. However, the researchers agree that Wearable WBANs are different from the WSNs, and their requirements vary from the WSNs as well. This is the reason that present protocols that are designed for WSNs are not compatible with the needs and requirements of wearable WBANs. These differences are: the number of nodes deployed in WSNs is considerably higher than the WBANs, and there are no duplicated or redundant nodes placed in WBANs but deployed in WSNs. Such differences create communication complications at different layers of the network protocol stack. Similarly, there are hard and fast limits on device size and power consumption in the case of WBANs as compared to WSNs. In addition to that, because WBANs are concerned with the collection and transmission of critical life information, the reliability, security, throughput, and delay of such scenarios are of high importance compared to other wireless network applications [ 70 ]. One of the distinguished aspects of wearable WBAN devices is that each device is deployed or implanted to perform a different task. There is a high level of heterogeneity in WBAN, which ultimately asks for different designs and implementations, whereas in WSNs, the nodes are supposed to perform tasks of a similar type or nature, showing a great homogeneous feature. Application of body-worn devices may include capturing of health data and transferring it to a processing server, collecting acceleration information to control robots, or giving commands and instructions to the game controller or console.
Looking at the above discussion on the nature of the WBAN devices, it can be concluded that the selection of wireless technology to be inducted for wearable or WBAN devices is very critical. Bandwidth, power, range limitation, and the nature of the application of wearable WBAN devices determine the type of wireless technology to be decided. Therefore, no single wireless technology satisfies all wearable WBAN applications and scenarios [ 71 ]. The most dominating wireless protocols in the WBANs, wearable or body-worn industry are Near Field Communication (NFC), Bluetooth Low Energy (BLE), Bluetooth Classic, Zigbee, 802.15.6 WBAN, WiFi, LoRa, ANT, ANT+, and Cellular [ 70 , 71 , 72 , 73 ].
Figure 6 gives a quick glimpse of all these protocols. We would like to mention that these wireless technologies can be considered the candidates for intra-BAN (e.g., UWB, Bluetooth, Zigbee, WiFi), inter-BAN (Bluetooth, Zigbee, WiFi, Universal Mobile Telecommunications System (UMTS/GPRS), and/or beyond-BAN (GPRS/UMTS, Internet, WiFi, Cellular Networks, multi-hop 802.11 internets, Global System for Mobile Communications (GSM)) communication [ 74 ].

Wearable, body-worn wireless protocols.
NFC stands for Near Field Communication and highly suits the wearables that are extremely power-constrained and required to transfer data for a range of a few centimeters, that is, about 4cm-10cm. The NFC device operates in two modes, i.e., passive and active. In passive mode, the NFC does not consume any energy, whereas in active mode, it draws energy almost equal to BLE. NFC-enabled smart devices can be paired with body wearers such as smart suits and jackets to process cardless payments. Similarly, they can be used to open doors and even transmit health information. NFC is also being used extensively in smart jewelry, wrist-worn wearables, E-Skin and E-tattoos [ 72 ]. Attacks on NFC-shared secret keys and certificate-based solutions have been proposed in [ 73 ].
ANT is one of the emerging wireless protocols for WBAN health monitoring applications. ANT stands for “Advanced and Adaptive Network Technology”. It is suitable only for low-speed and low-power WBAN applications. Several health monitoring sensor manufacturers are using this protocol. Different wearables are also operating in ANT, Bluetooth 4.0 or WiFi mode [ 72 ].
2.3.3. RuBee IEEE 1902.1
RuBee is one of the strong contestants of WBAN wireless protocols due to its low energy consumption, long-life battery, security, and stability. It sends small-size data packets of 128 bytes using long-wave magnetic signals. It makes use of low-frequency waves, i.e., 131 kHz, and is considered to be a slower technology compared to other wireless communication technologies, such as 802.11. The frequency at which this wireless technology works is not vulnerable to attenuation induced by metallic or liquid substances. This is the reason why RuBee devices can be sustained in harsh environments [ 74 ].
2.3.4. Sensium
Sensium is a low-power on-body technology for steady monitoring and observing of patient health [ 75 ]. It can send information to smartphones, mobile phones, laptops, and PC devices wirelessly, which is sent to a medical entity (medical servers, doctors, paramedical staff) for further action. Sensium sensors become alive only when they have reached a time slot to transmit data; otherwise, they keep themselves in sleep mode to save energy [ 74 ]. Presently, Sensium is one of the most widely adopted patient health monitoring systems. Figure 7 is the real Sensium copyright picture in which the Sensium patch is being placed on the patient’s body for vital sign monitoring. We reproduced this picture from the open access article [ 57 ]. From this figure, the importance of wearable WBAN devices in terms of patient health monitoring can be imagined. This acted as one of the most promising technologies for remotely treating patients with COVID-19, where people were required to stay at home as much as possible.

Sensium patch is being placed on the patient’s body [ 57 ].
2.3.5. Zarlink
Zarlink is energy efficient, one of the pioneering wireless protocols used in health care and diagnostic applications, and is equally good in implanting cases of WBANs. The cameras swallowed by a patient for the purpose of diagnosis and deep investigation of the gastrointestinal tract usually use Zarlink technology. The Zarlink-based camera is also used to send back videos of the tract in a timely manner with good quality [ 74 ]. It can operate in one of the two modes, i.e., IMD (Implantable Medical Device) mode and base mode. It consumes minute power ( μ W) in IMD mode and was announced as an energy-efficient device [ 76 ].
2.3.6. Z-Wave and Insteon
Both are open and proprietary wireless mesh technologies developed for home automation. Z-wave operates at 2.4 GHz, whereas Insteon leveraged the features of powerlines and the 900 Mhz ISM band [ 77 ]. It is used for smart homes but can be discussed as a candidate of WBAN wireless protocol for being the competitor of X10, UPB, Z-Wave, ZigBee, Bluetooth, BLE, and WiFi. Z-Wave is the next-generation wireless technology that makes use of low-powered and reliable waves, which have the capability of passing through walls and solid objects. It is believed that these are quite good protocols for wireless body area networks that are based on these technologies [ 74 ].
2.3.7. Bluetooth Classic
IEEE 802.15.1 Bluetooth is one of the successful wireless technologies for short-range communication with high security [ 78 ]. The compelling feature of Bluetooth is that it permits a large variety of Bluetooth-supported devices to make connections and establish communication with one another. One active device called a master can connect itself to seven active slave devices in a single ad hoc network called a piconet. It connects to 255 inactive slave devices, also called parked nodes, which can be activated by the master at any time. Parked nodes are kept in low power mode for energy conservation. Bluetooth-enabled devices operate in the 2.4 GHz band [ 79 ]. Their transmission range may vary from 1 to 100 m, and the maximum data rate could be 3 Mbps. Bluetooth is observed to be used in different areas of telemedicine and e-health systems. In addition, high bandwidth requirement, high energy consumption, longer pairing times, and a small number of devices in the network make this technology less suitable for wearable WBANs [ 70 ].
2.3.8. Bluetooth Low Energy (BLE)
BLE is an advanced and improved version of the classic Bluetooth that claims to be quite suitable for the WBAN devices due to its fewer energy requirements and low duty cycling rate [ 71 ]. It was designed to connect tiny devices with mobile devices, but due to low energy consumption, it is considered to be a great wireless technology for wearable and healthcare devices. Its synchronization time is less than the classic Bluetooth, and it uses adaptive frequency hopping and fewer channels for pairing. It also operates in the 2.4GHz (ISM) band as that of classic Bluetooth, which may cause interference with other devices operating in the same band. It suits the scenarios where a high data rate is required for a short period with low power consumption such as peer–peer communication between the wearable sensors and the access point (AP) or between WBAN devices connected in an ad hoc mode or between two WBAN devices or between a WBAN device and the mobile, laptop or personal computer. However, it cannot be ignored that in critical scenarios where frequent and steady reporting of health parameters is required, BLE seems to lack behind in the race of other favorable wireless technologies for WBANs devices [ 70 ]. In addition to this, BLE has not become common among the different vendors of wireless technology.
2.3.9. Zigbee
Zigbee is the combination of two technologies, Zigbee Alliance and the IEEE 802.15.4. Zigbee Alliance defines the application layer, i.e., network, security and applications software. The IEEE 802.15.4 module specifies the MAC and physical layer. Every Zigbee network consists of three types of devices, which are coordinator, router, and end-device. The job of a coordinator is to start and manage all sorts of connectivity and routing operations [ 78 ]. Its transmission range is a few hundred meters, but power consumption is higher than BLE [ 71 ]. This technology is highly suitable for applications where the device needs to run for several years [ 79 ]. The energy consumption of ANT > Zigbee > BLE [ 80 ]. However, at the same time, BLE has a very low data rate and operates in 868 MHz, 915 MHz, and 2.4 GHz bands, which may cause interference with devices that are already operating at 2.4 GHz. It is not suitable for large-scale real-time wearable WBAN scenarios, but it is good for single-user personal use. The Zigbee rate of suffering from channel fading is high, implies long delays in transmission of health data, which declares it unsuitable for critical WBAN application and is required to carry urgent data without such delays [ 70 ].
2.3.10. Ultra-Wideband (UWB)
UWB has been standardized by IEEE 802.15.3, providing wider bandwidth for high data rate WPAN applications designed for transmitting multi-media data (images and videos) [ 81 ]. The high data rate features of UWB make it very supportive for a number of wearables and body sensors that are used for remotely monitoring the patient’s health. These are not the only features that make it a good candidate for wearable and BAN applications, it is also a power-efficient technology. Low energy consumption increases the life period of wearable and BAN devices while helping to transmit more data. UWB can be applied in two forms, multi-band OFDM (Orthogonal Frequency Division Multiplexing) UWB and IR (Impulse Radio) UWB [ 82 , 83 ]. IR-UWB is more suitable for low-resource wearables and WBAN devices because it consumes less energy compared to multi-band OFDM UWB. IR-UWB uses a very short pulse to transmit data, which makes it energy efficient and very suitable for short-range WBAN data transmission [ 25 ].
2.3.11. LORA
LORA stands for Long Range, which is long-range low-power wireless communication technology. It was developed by Semtech and has become a de-facto standard for IOT networks [ 71 ]. It is extensively being used for low power wide area networks (LPWAN). The open source feature of LORA enables organizations to build an autonomous, low-power, and long-range communication system at a very economical cost [ 84 ]. The standard LORA follows security features, as shown in Table 2 .
LoRaWAN security features [ 85 ].
| Scheme | Standard LoRaWAN | Improved DO-SEO [ ] |
|---|---|---|
| Mutual Authentication | ✓ | ✓ |
| Secure Key Exchange | ✓ | ✓ |
| Perfect Forward Secrecy | ✓ | |
| End-to-End Security | ✓ | |
| Thwart Replay Attack | ✓ |
2.3.12. WBAN IEEE 802.15.6
The first standard that was designed especially for the WBANs was IEEE 802.15.6. In some cases, WiFi technology is being used for information acquisition in such a way that fixes the direct communication between the sensors (for data acquisition) and directly transfers it to mobile or PC without the intervention of any intermediate relaying or routing devices [ 78 ]. Most medical, non-medical wearable and on-body WBAN devices have adopted this standard for communication. Similarly, different wearable wireless devices have been attracted toward this technology due to its support for a wide range of data rates, low transmission power, low range, and connecting a quite reasonable number of wireless devices (256) on the body in a single WBAN. It operates in different frequency bands, for instance, Narrow Band, Ultra-Wide Band, and 2.3 GHz and 2.4 GHz bands. No doubt, this standard fulfills most of the requirements laid out by the WBANs. However, the standard is unable to fit in the emerging scenarios of WBANs such as running, sleeping, jogging, sitting, laying, etc. In addition to this, BANs substandard HBC (Human Body Communication) is not a promising wireless communication technology for the WBAN applications, which are required to transmit audio or video data [ 70 , 79 ]. Similarly, some of the bands, such as UWB, can be used only by authorized users. Now, the research community has united on this point that the 2.4 GHz band is the most appealing one for wearable, body-worn, and WBAN medical applications. In addition, all other properties are discussed in Section 2.3.13 , and it has the capability of guarding against channel interference. The IEEE 802.15.6 working group has defined Physical and MAC layer modules of the WBANs that are ultra-low power, low cost, less complex, and short range. They provide communication services inside and over the human body. IEEE 802.15.6 central node can interact with Bluetooth, BLE, ZigBee, UWB, NFC, RFID, Zarlink, RuBee, Sensium, Insteon, Z-wave, and ANT/ANT+ [ 86 ].
2.3.13. WiFi
IEEE 802.11 named WLAN or WiFi is a widely adopted wireless technology in mobiles, smartphones, tablets, PCs, laptops, PDAs, etc. [ 71 , 79 ]. We believe 2.4 GHz is also the most suitable wireless technology to be adopted at a large scale for wireless wearable and WBAN medical applications [ 70 ]. It is highly appropriate for large data transfers at higher bit rates [ 78 ]. However, at the same time, we cannot ignore the energy consumption of this technology. Fortunately, at the same time, a modified version of WiFi called Low Power WiFi has been researched in wireless sensor networks. This low-power WiFi has been outfitted with reduced transmission power, low-duty cycling operation, and optimized energy consumption features. WiFi is already positively acknowledged for its security and QoS traits. WiFi technology is commonly observed in homes, marts, hospitals, banks, and handheld smart devices. Therefore, it can be concluded that the integration of these low-power WiFi-enabled devices with the networks in their vicinity is quite compatible and easy. WiFi is the only wireless technology, which in addition to lower transmission power and energy optimization capabilities, supports multimedia applications such as live audio/video streaming, which is not possible with NFC, Bluetooth, Zigbee, LORA, and ANT. The prime logic for inducing low-power WiFi in wireless sensor networks is to bring about the concept of the Internet of Things. The materialization of this concept affirms WiFi to be an encouraging wireless technology for WBAN or body-worn devices [ 70 ].
2.3.14. Cellular
As far as cellular networks are concerned, smart wearable WBAN devices can directly connect and communicate with the cellular network instead of engaging themselves in bridging to communicate with them. At the same time, it can not be ignored that previous network technologies were more human-oriented. However, they have to face a lot of issues and challenges in the cases of wearable WBAN devices, especially when applications vary from low-end vital sign monitoring to high-end virtual or augmented reality applications. An example of such an application is virtual/augmented reality helmets for entertainment [ 87 ]. These applications require data rates in Gbps, which the present wireless technologies are not supporting, except the 802.11ac, which claims a data rate of 1GBps. The 5G wireless technologies have promised a data rate of Gb per second. However, due to the hardware cost and complexity, a wearable would not be able to take full advantage of these wireless technologies. Thus, due to the requirement of low energy consumption, no bright use of cellular wireless technology is observed in the perspective of wearable, body-worn WBAN devices. However, in the future, we hope to have such technology for the wearable, body-worn types of WBAN applications.
In addition to discussing these wireless technologies in detail, for simplicity and quick review, the summarized features of these technologies are also given in Table 3 [ 3 ].
Wireless protocols adopted by wearables industry.
| Protocol | Distance Range | Data Rate | Power Consumption | Frequency Band | Suitability |
|---|---|---|---|---|---|
| ANT (from Garmins) | 100 m outer door | 1 Mbps | 15 mA Tx 17 mA Rx | 2.40–2.483 GHz | used in sports, fitness and health devices |
| RuBee (IEEE 1902.1) | 30 m | 9.6 k | emits energy in nanoWatts, battery lasts for many years | operates below 450 kHz | considered to be a strong contestant for WBAN application |
| Insteon | 30 m | 9.6 k | Battery life is 10+ years | operates below 450 kHz | considers being a good protocol for WBAN applications |
| Sensium | home area | 13 k | 5 days | 131.65 KHz, 902–924 MH | extensively used in health care and diagnostic application, worthy of medical implanting cases, gastrointestinal [ ]. |
| Bluetooth Classic (IEEE 802.15.1) | 100 m | 1–3 Mbps | 2.5–100 mW | 2400–2483.5 MHz range within the ISM 2.4 GHz frequency band | used in different area of tele-medicine and e-health systems, but unfit for WBANs [ ]. |
| BLE (Bluetooth 4.2) | 50–150 m | 1 Mbps | 10 mW | 2.4 GHz | But, not suitable for frequent and steady reporting of health parameters [ ]. At the |
| IEEE 802.11 | 150–200 m | 54 Mbps | 1 W | 2.4 GHz (WiFi), 5 GHz | encouraging wireless technology for WBANs [ ] |
| Zigbee 3.0, 802.15.4 | 10–100 m | 250 kbps | 35 mW | 2.4 GHz mostly; though some devices use 784 MHz (China), 868 MHz (Europe), 915 MHz (USA, Australia) | unsuitable for critical WBAN application which are required to carry urgent data without delays [ ]. |
| LoRa (LoRa Alliance) | urban 2–5, suburban 15, rural 45 | 0.3–50 kbps | (customizable), battery life more than 10 Years | 169 MHz, 433 MHz, 868 MHz (Europe) and 915 MHz (North America) | used as LPWAN [ ] |
| NFC (ISO/IEC 18000-3) | 10 cm | 106, 100–420 kbps | 15 mA or less | 13.56 MHz | smart suits, jackets, jewelry, wrist worns, e-skin, [ ] |
| Z-wave | 30 cm | 106, 212 or 424 kbps | it uses 23 mA in transmission mode, battery lasts for decades even | 900 MHz (ISM), (Z-Wave Alliance ZAD12837/ITU-T G.9959) | considered to be a good protocol for WBAN applications [ ]. |
| SigFox | 2–5 (urban), 15 (suburban), 45 (rural) | 10–100 kbps | battery life more that 10 years | 433/868/780/915 MHz | used as LPWAN, no mobility and location support [ ] |
| NBIoT | 2.5–5 km | more than 250 kbps | battery life more than 10 years | Cellular (Licensed Band) | used as LPWAN, needs GPS for location support, mobility [ ] |
| LTECatM1 | 2.5–5 km | 1 Mbps | battery life more than 10 years | Cellular (Licensed Band) | used as LPWAN, needs GPS for location support, supports mobility [ ] |
| WBAN (802.15.6) | suitable for short-range human body communication | MICS (75–455, 75–187, 101–607), (101–607) Mbps, (121–971) | 0.1 W | MICS (402–405, 420–450, 863–870), ISM (902–928, 950–958), ISM (2360–2400, 2400–2483.5) | Most of the medical, non-medical, and on-body WBAN devices have adopted this standard for communication, support for location and mobility |
2.4. Application of Wearable WBANS
The applications of WBANS, body-worn or wearable, range from medical, health, fitness, defense, and military to sports and entertainment. A simple view of the different applications of wearable/body-worn devices is given in Figure 8 . Research communities believe in the great acquisition of wearables in medical health care, military, and sports, as they have undoubtedly been proven to bring about positive shifts in these and similar domains of life. These devices are extremely helpful in rehabilitation, monitoring and prevention of diseases, reminding patients to take medicine on time, and monitoring daily activities such as eating, sleeping, walking, and running, and most importantly, they provide timely feedback on health parameters to the centralized system [ 24 , 89 ]. Experts are anticipating that in the very near future, we will be able to buy such wireless wearable gadgets in medical stores.

Wearable, body-worn applications.
Wearable and WBAN are also applied to Sports and Entertainment to measure the blood pressure, heartbeat, and temperature of the sportsman along with his state of motion [ 38 , 90 ]. There is a non-medical application of WBAN devices in the entertainment industry that supports real-time audio/video streaming, gaming, virtual reality, etc., available in the form of smart MP3 players, smart microphones and smart cameras [ 38 , 90 ]. BBN stands for Body-to-Body network, which is a group of wearable WBANs that communicate with one another. These WBANs are usually connected with a gateway, which plays an important role in sharing of data among these WBANs. It is a theoretical mobile ad hoc network that is emerging as a key technology for sharing data between patients and medical teams [ 91 ]. If we consider the sports field, this application can be easily deployed with the help of smart devices such as smartwatches, smart glasses, and smart helmets that can be used to perform estimation and prediction of athlete health. The simple model of BBN is shown in Figure 9 . In this figure, every cyclist has a WBAN; all these BANs are connected to the ambulance.

Body-to-Body network [ 91 ]: group of wearable wireless body area networks.
With respect to disaster incidents, such as fires, earthquakes, cyclones (e.g., Tsunamis), tornado, bomb blasts, etc., it is believed that wearable WBANs is one of the technologies that could help people make themselves prepared for such incidents; equipping them with the tools to react against such incidents in a more effective way [ 92 ]. For example, rescue teams could be fitted out with wearables, which could gather and transmit back the exact environmental condition (such as heat, the toxicity of gases, lightning, fire, smoke, etc.) and life-critical information (such as BP, HR, body temperature, etc.). Military and Defence applications of WBANs, wearable and body-worn, include the detection of life-threatening factors regarding soldiers and assessing the fatigue thresholds of the soldier [ 90 ], whereas WBAN devices are being used for fire, injurious, smoke, and gas detection, which could prevent the death of military men in danger [ 38 ]. The most recent development of a wrist band with a 4.3 inch bendable OLED (Organic Light Emitting Diodes) display has transformed fiction into a reality. The wristband has been tested by the US army. It was funded project of the US Department of Defence to develop a thin lightweight and flexible communication device. This device has the capability to show different sources of information such as Unmanned Air Vehicle (UAV) video and images received through a computer that runs different military applications. Moreover, the device is also capable of reducing risks on the battlefield while improving the operational efficiency of troops at the same time. The rest of the technical detail can be viewed from [ 93 ]. For motivation, the band is shown in Figure 10 .

Wrist band with a 4.3 inch flexible OLED display [ 93 ].
Usually, people are aware of wearable BAN devices that are used by civilians, but they know less about the same types of products being used for research in the military. There are different military projects, such as “The Army’s Program Executive Office”, “FLIR SYSTEM”, etc., that have developed or are endeavoring to design more sophisticated products. There is a very good system study on the analysis of military-based wearables, which is carried out by Han et al. [ 94 ]. Some of the military projects and their products are given in Table 4 .
Military wearables.
| Product | Project | Product Type | Features |
|---|---|---|---|
| Life- BEAM | LifeBEAM | Helmet | Monitors beating heartrate using optical sensor |
| Combat- Connect | The Army’s Program Executive Office | Wearable electronics system | disseminate information to/from WBAN using smart hub fixed with military vest/jacket |
| Black Hornet | 3 FLIR SYSTEM | Automatic Pocket-sized helicopter | camera that can be fixed with armor/vest; works as elevated binocular |
| Ground Warfare Acoustical Combat System | Gwacs Defense | A wearable tactical system | Identifies and locates hostile fire; detects and tracks Small UAVs |
| Exo- Atlet | ExoAtlet | Lower body powered exoskeletons | Mobility assistant, reduce troop’s movement cost |
| SPaRK | Spring Active | Energy-scavenging exoskeletons | Performs energy harvesting to recharge devices |
Vital Sign Monitoring
WBAN is a network of body-worn or wearable computing devices that can be fixed inside the human body or can be implanted or worn on the body. With respect to vital sign monitoring, WBANs have two different types of uses in the healthcare sector ; one is medical and the other is non-medical. For medical purposes, they are deployed to measure ECG, EEG, EMG SPO 2 , BP and drug injection [ 90 ]. Devices are also implanted in the body to control different diseases such as diabetes. WBAN devices are being used in non-medical areas for motion detection, for example, walking, running, jogging, etc. [ 38 , 95 ]. However, in the case of manpower safety , wearable WBAN not only monitors the vital signs such as BP, body temperature, pulse rate, and remaining energy but also carry out motoring of life-critical environment parameters such as carbon dioxide and carbon mono-oxide, ammonia, heat, humidity, etc. [ 92 ]. Wearables are classified into different categories based on their application in the real environment such as smartwatches, fitness trackers, smart clothing, smart jewelry, head-mounted devices, smart glasses, wearable cameras, location trackers, body sensors, implants, exoskeleton, and gesture control wearable [ 5 , 96 ]. For simplicity and brevity, wearables are categorized into different types.
The major smart and state-of-the-art vital sign monitoring solutions are Visi Mobile System, Aingeal, VitalSense-VS100, Zensor, QUASAR, EQ02 LifeMonitor, VitaPart-3, PERFORM, Physiodroid, etc. [ 97 ]. For more simplicity, details of these devices are given in Table 5 , and their detail can be viewed from the respective reference.
Vital sign monitoring systems.
| Monitoring Device/System | Vital Signs | Provider | Ref. |
|---|---|---|---|
| Visi Mobile System | It is (Continuous Beat-by-Beat Blood Pressure) CNiBP, Non-Invasive Blood Pressure (NiBP), ECGs, Respirations, HR, PR, SPO2, Motions and Postures. Visi Mobile System continuously leveraging on hospital’s existing WiFi infrastructure Sotera Wireless | Sotera Wireless, Inc. | [ ] |
| Mobile Cardiac Outpatient Telemetry (MCOT) Patch System | MCOT collects medical information using Bluetooth from sensors, transmits ECG wirelessly to BioTel Heart all the time | Bio-Tel Heart | [ , ] |
| MCT 3 Lead (MCT 3L) Cardiac Telemetry | LifeWatch MCT 3 is very smart in nature, giving a distinct picture of the heart in addition to the rhythms of a heartbeat. | Bio-Tel Heart | [ ] |
| ePatch Extended Holter Monitoring | Records and stores heartbeats | Bio-Tel heart | [ ] |
| wEvent | Wireless Cardiac Event Monitor, wEvent supports arrhythmia detection with high precision | BIO-Tel Heart | [ ] |
| Wireless Connector for BPA-060 | Wireless Blood Pressure Monitor | Ambio Health | [ ] |
| Wireless Connector for Presto | Blood Glucose Monitor | Ambio Health | [ ] |
| WiCap | Capnography device, monitors expired (EtCO2), inspired (FiCO2) breath, respiration rate (RR), SpO2, and pulse rate (PR) | Athena GTX | [ ] |
| Tac Pac | Measures NIBP, HR, SpO2, and ECG | Athena GTX | [ ] |
| Athena Device Management Suite (ADMS) | ADMS connects different wireless vital-sign monitoring devices and is also adaptable to mobiles and smartphones, alarming, awareness, etc. | Athena GTX | [ ] |
| Wireless Vital Signs Monitor | Wirelessly monitors Sp02, HR, NIBP, and ECG within a range of 200 yards, ADMS compatible | Athena GTX | [ ] |
| Caretaker | measure CNiBP, Heart Rate, and other vital signs, android compatible | Caretaker Medical | [ ] |
| SmartSense | Temperature, blood pressure, pulse, SpO2, respiration, pain level, SMD, etc., via any mobile PC, draw plots of vital signs | Cadi Scientific Pte Ltd. | [ ] |
| HealthPatch/Vital Patch, Vista Solutions | Health monitoring system, which can measure HR, RR, temperature, posture, activity, and fall detection | Vital Connect | [ ] |
| Fitbit Premium+Health | It is a personalized health monitoring system that helps a person manage stress, have a sound sleep, and stay active. It provides a daily score of these signs. Users can download their data at any time | Fitbit LLC. | [ ] |
| Garmin Connect | Garmin Connect can track, analyze and share your health data on mobile or web | Garmin Ltd. | [ ] |
| Samsung Health | Galaxy smartwatch-based health solution that scores sleep and blood oxygen during sleep. It can also detect snoring and monitor running performance | Samsung Ltd. | [ ] |
| Apple Health Kit | It assesses the steadiness of walking, falling probability, and goodness of sleep that help helps to assess changes in health. The health data can be shared with concerned people | Apple | [ ] |
| Wireless Implantable Cardioverter and Defibrillators | Cardioverter and defibrillators give weak and strong electrical shocks to the heart to maintain rhythm and beating. FD approved such devices a long time ago [ , ]. Each manufacturer has introduced its remote monitoring system, pacemakers and ICDs, such as Home Monitoring , CareLink Network , Latitude Patient Management system , and Merlin.net (St Jude Medical, Sylmar, USA). [ ] | Biotronik, Medtronic, Boston Scientific, Merlin.net | [ , , , ] |
| EEG, ECG, EMG, EOG, EGG monitoring devices such as Bittium Faros —Cardiac Monitoring | These devices can measure ECG, EMG, EEG, etc., TSE Systems, Lepu Medical Technology, Bittium Corporation, BIOPAC Systems, Inc. are major providers. Stellar Implants, NEO ECG, and Mobita are also good monitoring systems | Fabric-embedded devices available at [ ] | [ , , , ] |
In addition to vital sign monitoring devices mentioned in Table 5 , there are a lot of other useful wearable and WBAN devices, which are making human lives healthier. The devices in this list may be Google Glass, Withings Scale, Sense Mother, Moto 360, Septimu Earbuds, Smart Diapers, Electronic Fork, etc. [ 122 ]. Some of the leading wearable hardware and application developers, manufacturers, and software developers are Fitbit, Medtronic, Nokia, and Philips [ 123 ]. Fit-Bit-Flex, Jawbones-Up, Nike+FuelBand, Spire are a few of the top listed wearable solutions among the popular fitness trackers. All these devices have two following common functionalities.
- 1. They use sensors to determine heart beat rate, walking or running steps and number of calories burned.
- 2. These devices can be connected to a computer, laptop, or mobile to communicate the results wirelessly.
In addition to these two common functions, Fit-Bit-Flex can also track (i) how many hours a person slept the previous night, (ii) the food intake, (iii) how much exercise one has performed, etc. Nike+FuelBand can track sleep hours in addition to the functions mentioned above. Similarly, Jawbones-Up is a good choice to improve sleep habits and achieve dietary goals as well. It can be interfaced with a number of third-party applications, such as MapMyFitness, Sleepio, MyFitnessPal, RunKeeper, etc. Aspire, however, is one of the most expensive devices that determines a person’s fitness based on the measured patterns of breathing instead of the activities. Garmin is one of the leading manufacturers of body-worn and wearable devices. It has launched different smartwatches, specially focusing on the fitness and performance of different sportsmen, such as divers, sail-men, pilots, and aviators, etc. [ 124 ]. Therefore, it can be concluded that wearable WBAN devices are accelerating the growth of wireless communication equipment at a rapid rate.
It is observed that most users are naive to the physiological values given by medical wearables. Some results of medical wearables, such as the values of ECG, are life-critical, and only the expert can comprehend and deduce concrete results. That is why the purpose of this study is not to make people capable of comprehending such complicated results of the medical wearable. However, on the other hand, some readings are simple, and the user can understand, comprehend and take some measures such as BP, HR, temperature, oxygen absorption, hydration and sugar level, and fall distance, etc. Therefore, the normal ranges of these physiological parameters are given in Table 6 . In the absence of medical staff, the users can detect abnormalities and take necessary first aid action on the basis of measured and reference values. These values are important and must be known to the common person, which is why they are extracted and reproduced in this article instead of referring the reader to [ 125 ]. The readers who belong to the medical domain may refer to [ 126 , 127 ] for an in-depth study of human physiology, but it is beyond the scope of our study.
Normal ranges of commonly known physiological parameters [ 125 ].
| Parameters | Normal Range |
|---|---|
| Body Temperature | 37–37 Degrees Celsius |
| Hear Beat | Rate 60–100 beats per minute |
| Breathing Rate | 12–20 breaths per minute |
| Oxygen Saturation | 94–99% |
| Blood Sugar | 4–6 mmol/dL (72–108 mmol/dL) |
| Blood Pressure | 120/80 |
| Hydration level | 90–100% |
| Fall Detection | 0–20 cm |
2.5. WBAN Security Issues
Applications of wearable WBANs are discussed in Section 2.4 , and the scenarios similar to these applications put wearable WBANs at higher risk of being attacked by adversaries. The broadcast nature of wireless networks plays a major role in exploiting and compromising them. Because these devices carry military and life information, swift security systems must be developed to prevent data leakage, hacking and stealthy ransomware attacks [ 123 ].
2.5.1. Major Security Requirements
In addition to the device and user authentication, security is built upon a triad CIA that is a combination of three pillars. These are the major security requirements that any communication is required to fulfill, i.e., confidentiality, integrity, and availability, as discussed below.
- 1. Device Authenticity: This is a very critical issue. Adversaries can implant a malevolent node in a non-line-of-sight (NLOS) location that can inject fake data and even receive legal data while acting as a legal device [ 128 ]. Thus, it is very important to validate the authenticity of the BAN devices that they claim to be [ 129 ].
- 2. Confidentiality: Confidentiality ensures that the information should not be disclosed to unauthorized entities while moving from wearable WBAN source to destination [ 130 ]. However, due to the open and broadcast nature of WBAN transmission, the data can be eavesdropped and disclosed to an unauthorized party. Therefore, it is always advised to encrypt data before transmission [ 128 ].
- 3. Integrity: It claims that information must reach the destination in its original form as was sent by the body-worn or wearable WBAN source; it must not be altered during its transfer. Due to the free-flying of wireless BAN frames, they can be intercepted and tampered with by the attacker, which may harm the health system or even the patient’s life [ 128 , 130 ]. That is why it is required to ensure the integrity of data using some message authentication techniques such as hashing or CRC. They ensure the data are not modified during the transition from one BAN device to another.
- 4. Availability: One of the most disturbing attacks is DOS (Denial of Service), which is launched against a body controller unit, cloud server, or medical server. Thus, the attack can even cause a shutdown of medical services, which may impose serious life threats on patients [ 128 , 130 ]. For ensuring life safety and timely treatment of the patient, health network communication systems must be available whenever a WBAN source is required to send data.
- 5. User Authentication/Authorization: In remotely controlled healthcare WBAN systems, only the authentic and authorized medical staff members must be able to access the data of a particular patient. User authentication can be established using well-informed mechanisms, such as username/password, PINs, fingerprints, etc. Similarly, a proper access control mechanism (e.g., Access Control Lists) must be devised to ensure authorized access to data [ 129 ].
2.5.2. Importance of Security
We have seen a number of wireless technologies being used in the WBAN industry for life-critical data collection and dissemination. If such information is stolen, it can be used for illegal activities that could result in losses to the owner in the shape of mental disturbance or financial blackmailing. For brevity, a generic set of WBANS attacks, security requirements and measures have been given in Table 7 [ 131 , 132 , 133 , 134 ].
Security threats and possible solutions in WBAN [ 131 , 133 ].
| Security Issues | Secure System Requirements | Potential Security Measures |
|---|---|---|
| Illegitimate access to information | Dynamic secure key agreement and trust establishment | Random ephemeral key generation and distribution, use of public key cryptography |
| Information Disclosure | Confidentiality and privacy | Link/network layer encryption and access control |
| Data Modification | Integrity and authenticity | Keyed secure hash function and Digital signature |
| Denial of Service | Availability | Intrusion detection systems and redundancy |
| Compromised/Hijacked Node | Cryptosystem must be resilient to node-compromise | Anomaly detection, comprising nodes isolation |
| Routing vulnerabilities | Protection of routing information | Use of secure routing algorithms |
| Intrusions/Unauthorized Access to Network System | Intrusion detection and prevention, secure data aggregation, group communication and management | Intrusion detection and prevention systems |
Another perspective of the attacks and issues is to view them from a WBAN network stack point of view. We have observed from [ 131 , 133 ] that jamming and tampering are major issues at the physical layer. On the link layer, collision, unfairness, denial of sleep, traffic analysis, spoofing, eavesdropping and exhaustion are some of the issues that affect the security of WBAN devices. Similarly, the network layer also has to face different attacks such as selective forwarding, blackhole, rushing, wormhole, sinkhole, sybil, homing, neglect, misdirection, etc. Flooding and desynchronization are the most havoc attacks that are usually projected on the transport layer of the WBANs. Some of the solutions that are recommended to take control measures on the physical layer are frequency hopping, spread spectrum, tamper-proofing, and link hiding. Similarly, the link layer can be protected against mentioned security issues by using error correction codes, rate limitation and adaptation, or making use of small frames. For the protection of network layer probing, packet filtering, authorization monitoring and encryption can be used. Similarly, energy-efficient secure routing protocols are required for the long life of WBAN networks [ 135 ]. Client puzzles and authentication techniques can be used to protect from flooding and desynchronization issues on the transport layer. For a detailed review of these attacks, a reader is advised to read [ 136 ]. Unfortunately, due to its wireless nature, WBANs are highly susceptible to different network threats and attacks. For simplicity, these attacks have been categorized into active and passive. Passive attacks are designed just to listen to network traffic, whereas active attacks can make harmful changes to the WBAN data in transition or storage. Some of the common attacks are eavesdropping, data corruption and modification, replay, masquerade and impersonation [ 74 ]. WBAN wireless protocols have been reported to face different attacks, which are summarized in Table 8 .
Attacks on WBAN wireless technologies.
| Protocol | Security Risks | Proposed Control Measures |
|---|---|---|
| ANT | by default ANT+ is not encrypted, AES128 support in special cases, provided in single channel communication only, lack of authentication, MITM [ ]. | network key along with network number provides different options for access control and security level [ , ] |
| Rubee | no eavesdropping, high packet security due to date and time stamp [ ]. | eavesdropping range is similar to that of tag range; such a close eavesdropper can be detected easily, it meets a high standard of security also being used in many US Govt. owned departments [ ] of USA |
| Sensium | Sensium is vulnerable to all those attacks, launched on body sensor networks, such as insider attacks, DOS, wormhole, replay, jamming, etc. [ ] | per hop encryption can reduce the chances of attacks, also reduces overload over the network as well [ ] |
| Zigbee | insufficient integrity protection due to sending unencrypted key; location privacy, an initialization vector (or Nonce), and key management are susceptible to high-security risks; improper support of group keying [ ]. Due to default weak password, misconfiguration of the Zigbee IP network, and the gateway or lack of security an attacker can bypass Zigbee authentication check [ ]; replay attack, device identification attack, and packet interception are a few of the other ones [ ] | time stamping, AES, and Message Integrity Codes (MIC) can be used to mitigate the risks [ ]. In addition to this, since the security keys are stored in memory, adversaries can directly steal them. Therefore, it is advised to use a microcontroller for secure authentication and to eliminate the threat of physical corruption of security keys [ ]. |
| Bluetooth | intrusion in pico-net, MITM (Man-in-the-Middle)/Impersonation, DOS attacks, Bluejacking [ , ]. A few other reported attacks are MAC-spoofing, PIN cracking, BlueSnarfing, BlueBugging, BluePrinting, Blue over, off-line PIN recovery attack, brute-force, reflection, backdoor, Cabir worm, Skulls worm, and Lasco worm [ ]. | use long PIN Codes, do not pair in public areas, and turn on non-discoverable mode after use, at the corporate level proper policies and guidelines be devised for Bluetooth pairing [ ] |
| WiFi | cipher attack is used to attain the encryption key through processing information exchanged between sender and receiver. WEP, WPA-PSK Dictionary, WPA/TKIP, and LEAP are a few of the cipher attacks. WiFi also faces, jamming, flooding, evil-twin threats [ , ] | separating the guest network from actual, encrypting traffic with WPA2 or WPA3, updating firmware timely, creating secure SSID, restricting WiFi to business hours only, all these measures can mitigate the attacks on WiFi [ ]. |
| LORA | attacker can obtain access to physical LORA device, jamming-communication channel can block with the high power radio signal, replay, beacon synchronization, traffic analysis, MITM are a few threats to LORA [ ]. DOS, Bit-flipping, ACK spoofing. LoRa vulnerability survey can be viewed from [ , ]. | dynamic or ephemeral key generation, of large size can prevent join attacks [ ], Block-chain is also good for powered limited devices [ ]. Use Over-The-Air-Activation (OTAA) [ ] |
| NFC | eavesdropping, cloning of ticket, spoofing, a man in the middle attack, corruption of data, insertion of malicious data, relay, ghost and leech, DOS, phishing, a threat to ID, PIN, credentials of credit card, etc. | shared secret keys, certificate-based authentication WEP based security can be used to reduce the probability of these attacks [ ] |
| Z-Wave | Z-Wave device pairing process with the controller can run many times, which attracts “key reset attack” [ , ] | vulnerability has not been fixed, more than one million devices are in the market with this vulnerability [ ] |
| WBAN | Key-Compromise Impersonation (KCI), Impersonation, WBAN security protocols do not forward secrecy as well [ ] | using certified keys KCI can be avoided, but it is not recommended in standards due low resources of WBAN devices [ ] |
2.5.3. Technical Approaches
Encryption is a basic tool to provide confidentiality and integrity. It is achieved through the encryption key, which is a shared secret between the source and the destination. It is widely believed that security lies in the secret key’s size and in its strength, which means how much a secret key is random or uncertain in its nature. Presently, two or more nodes can agree upon a shared secret using state-of-the-art protocols such as DH (Diffie–Hellan), ECDH and RSA [ 154 , 155 ]. These techniques are just computationally secure methods with a sufficient amount of resources, and the adversary can breach the security implemented by DH, ECDH and RSA. Furthermore, PKI technology does not suit resource-constrained networks such as WBANs, body-worn or wearable. It has been observed that in some scenarios, wireless wearable body area network technology is very sensitive, and the information in these cases is highly classified and critical. That is why the protection of information and keeping it consistent for different stakeholders and users is very important. Different state-of-the-art security solutions are unleashed in this article to save the sensitive information of wearable WBAN technology. For more clarity, the security support of different wireless wearable BAN technologies is discussed individually and separately.
TinySec Security Solution
Wireless technology is inherently insured due to its broadcast nature. TinySec is a link layer security architecture for wireless sensor networks and is the first fully implemented security protocol for these networks [ 156 ]. It ensures authentication, integrity, and confidentiality. However, it does not deal with resource consumption, tampering and node theft attacks. For access control and integrity, it makes use of MAC (Message Authentication Codes) and encryption for privacy, and the encryption keys are pre-configured. It makes use of single a network-wide, group, and pair-wise secret key for network, group and peer–peer communication. Instead of using software-based encryption as in the case of TinySec, hardware-based encryption can also be coded with the help of ChipCon-2420 ZigBee compliant Radio Frequency (RF) transceiver. The ChipCon-2420 can execute security operations of Zigbee 802.15.4 with AES using a secret key of length 128-bit [ 157 ].
Elliptic Curve Cryptography (ECC) is one of the suitable choices for public key encryption for wireless body area networks. This suits WBAN because its small key size has been proven to be highly secure. In addition to this, it also generates a small signature. Moreover, tremendous amount of computation power is required to breach ECC. Such computation power will not exist until quantum computing becomes a reality. However, it cannot be ignored that ECC demands a significant amount of energy compared with other contemporary approaches, which provides an alternative solution for high system security [ 158 ]. An energy efficient solution based on ECC for WBAN was presented by Tianchan et al. [ 159 ]. It is worth mentioning that there are different types of encryption schemes such as symmetric key encryption, public key encryption (e.g., identity-based encryption (IBE), and attribute-based encryption (ABE)). From the list of public key-based authentication types, ABE and IBE are well-known techniques for encryption purposes. For the security of WBANs, attribute-based encryption was presented by Tian et al. [ 160 ], whereas ID-based encryption was proposed by Chu et al. [ 161 ] for wireless sensor networks. IBE reduces the computational costs of encryption and decryption.
Biometric-Based Security Solution
This is quite an innovative approach for providing security solutions in low-power wireless devices. Encryption is one of the most accepted ways of protecting information that needs encryption and a decryption key. A symmetric key can be established among different BAN or wearable devices. In the biometric-based security method, the human body endeavors to achieve a secret key by using EEG/ECG values measured by different body sensors, which are attached or embedded in different parts of that body. Since all EEG/ECG devices observe similar values, they can agree on a shared symmetric key between them [ 162 , 163 , 164 ]. This key, later on, can be used in encryption and decryption processes.
WBAN and wearable technology can be protected with the help of different encryption mechanisms, which may provide a high level of security using symmetric, asymmetric, and identity-based encryption. Symmetric Encryption is a type of encryption in which symmetric keys are used for encryption and decryption. For simplicity, Figure 11 shows a message that is encrypted and decrypted by two parties, Alice and Bob, using an identical shared secret.

Symmetric key encryption.
Asymmetric Encryption is a type of encryption in which two different keys are used for the encryption/decryption process. One key is used for encryption, while the other is used for decryption. This mechanism is also called Public Key Cryptography, where each party holds a pair of public/private keys. The sender encrypts a message with the public key of the receiver. The receiver upon receiving the encrypted message used its private key to decrypt it. Public keys are shared, while private keys are kept secret and are not disclosed to anybody. Figure 12 shows that each encryption and decryption key is different, i.e., Alice encrypts a message, with the public key of Bob and Bob decrypts the encrypted message with his private key.

Asymmetric key encryption.
IBE is the singleton of ABE in the sense that IBE uses a single attribute to link a secret/private key with a public parameter, e.g., email that works as an ID. In this case, the owner of the secret/private key can decode the message, whereas ABE makes use of multiple attributes. e.g., name, rollno, class, city, etc., and links these attributes with a secret/private key. The owner of the private key who matches these attributes can only decrypt the message encrypted by a sender.
2.5.4. Wireless Security Fixes
Ant/ant+/ant+s.
ANT is a network protocol that is designed for IoTs. Like the other protocols, such as 802.11, it also operates in the 2.4 GHz frequency band. ANT+ is based on ANT and was developed by Dynastream Innovations. By default, ANT+ is an unencrypted protocol. However, it provides security with the help of RF Frequency/Channel ID and network key. Communication on a unique channel-ID or frequency prevents legal devices from receiving data from unintended devices. However, it does not stop illegal devices from malicious interception of legitimate communication. A 64-Bit network key is used to encrypt ANT+ packets, but this size does not provide adequate security. Security threats can be overcome with ANT+s optional encryption, that is, AES-128 in CTR mode. Discussing ANT+ data acquisition and processing are goals of this article but can be seen from [ 165 ].
RuBee IEEE 1902.1
RuBee is the commercial name of IEEE 1902.1, which is known as Long-Wavelength ID (LWID) [ 166 ]. RuBee provides a secure physical communication layer, flexible asset flow layer, and asset visibility. It provides secure asset flow and security while not depending upon encryption only. It has four layers that are used to implement the security of visible assets and data packets. These layers are (i) Asset Flow Layer, (ii) Physical Asset Layer, (iii) Packet Data Layer and (iv) Physical Communication Layer. Layer-i and layer-ii deal with the secure flow of visible assets, whereas layer-iii and layer-iv handle the secure flow of information. Moreover, RuBee is capable of providing a controlled physical layer security with almost no interceptions. Similarly, it is not affected by water, steel, or other harsh environmental factors. Rubee tags support the packet security layer using advanced encryption standards such as AES and Public/Private Key Cryptography [ 167 ].
Sensium is a wireless radio protocol specially designed and optimized for vital sign monitoring. It is a robust, reliable and secure wireless patient monitoring system. It is implemented in the form of a miniature and disposable patch [ 168 ]. Sensium makes use of the public key cryptography for information security [ 169 ].
An early version of Z-Wave employed S0 security, which was vulnerable to eavesdropping, message manipulation, and injection. However, a later version of security S2 was quite a lot stronger due to leveraging the strength of the Elliptic Curve Diffie–Hellman (ECDH) curve called Curve25519 and a public key length of 256 bits. S2 is also based on AES-128-CCM for authenticated encryption and AES-128-CBC for secret key derivation [ 170 ].
Zarlink makes use of Reed-Solomon Codes with CRC (Cyclic Redundancy Check) for establishing a reliable communication link [ 76 ].
Insteon provides CRC and FEC (Forward Error Correction). It provides a higher level of security with a unique addressing mechanism (unique ID code), AES encryption, and secure channel allocation. Actually, it has multiple encryption methods, such as rolling-code, managed-key and public-key [ 169 , 171 ].
LR-WPANs IEEE 802.15.4 Security Services
LR-WPANs stands for Low-Rate Wireless Personal Area Networks. The link layer security protocol of 802.15.4 supports four basic features, which are access control, data integrity, data privacy, and data protection from replay attack [ 131 , 172 ].
WBAN IEEE 802.15.6 Security
IEEE 802.15.6 is accompanied by three different security levels, which are (i) Unsecured Communication Level, (ii) Authentication Level, (iii) Authentication and Encryption Level. Level-1 provides no security, Level-2 supports only authentication, while Level-3 comes up with authentication and encryption [ 173 , 174 ]. Moreover, the master key is always pre-shared; temporary pairwise and group keys are generated as per the communication requirement. A detailed security analysis of IEEE 802.15.6 can be reviewed from [ 175 ].
ZigBee Security Services
Zigbee is lower power wireless technology that establishes an ultra-lower communication setup in an existing spectrum of a wireless world. Zigbee inherits the security services of 802.15.4 and adds extra features to an existing set. The extra services provided by Zigbee at the network layer are in the form of authentication and key exchange. Zigbee network nodes make use of network and link keys for communicating messages secretly. Receiving nodes always know what keys are used for securing the messages [ 176 ]. The current standards of Zigbee provide a trust center that is an application that allows the zigbee nodes and router to be configured and authenticated for joining the network [ 177 ]. Zigbee security is good, but ZiCoskun et al. [ 178 ] showed the security comparison of Zigbee, Bluetooth, and NFC; they concluded that Zigbee and Bluetooth security levels are lower than NFC.
BLE Security
BLE stands for Bluetooth Low Energy, and it uses periodic transmission for small data packets. The older versions of this protocol such as BLE 4.0, and BLE 4.1 used a simple procedure connection in which BLE devices exchange a temporary key that is used to generate a short-term secret key. This short-term key is used for the authorization of the connection. These connections are not secure but can be made secure with the help of a protected pairing process. In BLE 4.2, secure connections were introduced, which are not compatible with the legacy version. Elliptic-curve Diffie–Hellman (ECDH) is used to generate a more complex secret key, which introduces a robust process of key authentication [ 179 ]. It prevents passive eavesdropping. BLE devices can be further secured with the help of a secure pairing process [ 180 ].
Bluetooth Security Protocols
Classic Bluetooth protocol stack consists of different protocols such as Baseband, Logical Link Control and Adaptation (L2CAP) and Link Manager Protocol (LMP), Service Discovery Protocol (SDP). The establishment of a link between different Bluetooth devices and the exchange of information using packets is the responsibility of a baseband protocol. LMP protocol induces security features such as encryption, authentication, and key exchange in Bluetooth. As far as the L2CAP is concerned, it provides support for multiplexing at a higher level. This protocol also supports reassembling of packets that, in turn, support quality of service. Similarly, SDP is used to discover services that are hosted on all Bluetooth devices. Jini and UpnP are a few service discovery protocols that can be used in combination with the SDP protocol. Bluetooth operates in three modes: (i) silent: device only monitors traffic and is undiscoverable, (ii) private: device is undiscoverable and accepts connections from only known MAC-Addresses, (iii) public: device is discoverable and accepts connection from any device [ 181 ]. A careful selection of an operating mode also elevates security. In addition to these operating modes, Bluetooth supports four security modes whose functionalities are given below [ 146 , 181 ].
- 1. Non-secure: No security.
- 2. Service-level enforced security mode A non-secure ACL (Asynchronous Connection Link) can be established using this mode. Security functions run only after the L2CAP connection-oriented or connection-less channel request is placed.
- 3. Link-level enforced security mode Security primitives are started before making any request for a channel is initiated and the ACL link is established.
- 4. Service-level enforced security mode (SSP) This is similar to service-level enforced security mode; the only difference is that only the Bluetooth devices that use secure simple pairing (SSP) can be set in this mode.
Security comparison of Zigbee, Bluetooth, and NFC can be seen from [ 178 ], which indicated that NFC provides better security than Zigbee and Bluetooth.
802.11 Security
Since the discussion on different versions of 802.11 is beyond the scope of this study, we used 802.11 security protocols irrespective of the 802.11/a/b/g/n. The most popular security protocols that have been used to protect 802.11 networks are Wired Equivalent Privacy (WEP), WiFi Protected Access (WPA), WiFi Protected Access version 2 (WPA-2), and WiFi Protected Access version 3 (WPA-3). WPA-2 is also known as 802.11i. WEP was the original security protocol developed in the late 1990s for achieving confidentiality. Due to security flaws, in 2003, WiFi Alliance declared it superseded by WPA. In 2004, with the ratification of WPA-2, WEP was set to phase out by the same alliance. WEP used RC-4 for authentication and encryption. WPA also uses RC-4 stream cipher for encryption, but it is enhanced with the help of Temporal Key Integrity Protocol (TKIP). WPA-Extensible Authentication Protocol (WPA-EAP) is an enterprise mode that uses 802.1x for authentication. Whereas in personal mode (WPA-PSK), it makes use of pre-shared keys for security purposes. WPA-2 is more robust and reliable; it uses Advanced Encryption Standard (AES) instead of RC-4. It uses CCMP protocols for authentication [ 182 ]. CCMP stands for Counter Mode with Cipher Block Chaining Message Authentication Code Protocol. WPA-3 is considered to be the most recent and secure 802.11 security solution. In 2018, WiFi Alliance started looking for the certification of WPA-3, and by July, 2020, they inquired about devices seeking certification of WPA-3. WPA-3 provides support of security for personal and enterprise networks. WPA3-Personal provides natural password selection, ease of use and forward secrecy. WPA3-Enterprise provides a very high level of security using advanced cryptography algorithms. Authentication is achieved by using EAP; AES-CCMP 128-bit is used in encryption. For key derivation and verification, 256-bit HMAC-SHA is used. Similarly, for robust frame protection, 128-bit Broadcast/Multicast Integrity Protocol Cipher-based Message Authentication Code (BIP-CMAC-128) is used. WPA3-Enterprise with 192-bit is optional and provides more advanced level of security with the combination of a selection of security primitives [ 183 ].
3. WBAN Economical Issues
3.1. wban/wearable compound annual growth rate.
The global market of wireless wearable BAN devices is usually assessed with the help of CAGR, which stands for Compound Annual Growth Rate. It is defined as the annual growth rate of investment between two years, assuming the growth is increasing exponentially and one year profit is reinvested in the next year. CAGR is one of the most accurate ways of calculating returns on investment that can increase or decrease over a period of time. Equation ( 1 ) is used to calculate CAGR [ 184 ]. The purpose of explaining CAGR in this article is that most computer, material and life scientists and engineering professionals do not know the concepts of commerce.
where EV and BV are ending and beginning values, and n is the number of years. We believe this brief explanation of CAGR can help the reader to understand it better from the perspective of global investment in wireless wearable body area networks. It is forecasted by “Transparency Market Research” that the global body area network market will touch USD 62,120.9 Million in 2025. This information was broadcasted by Cision PR Newswire who the mentioned market is expected to grow at the CAGR rate of 24.7% from 2017 to 2025 [ 185 ]. According to recently reported information by James Hayward [ 186 ], the market of wearable BANs devices was $80 Billion in 2020, which was thrice the market of 2014 in terms of annual revenue. It is predicted that the market of wearable BANs could reach USD 138 billion by 2025 [ 187 ]. According to a very recently published technical survey on wearable technology, 20% annual growth rate of this technology is expected, and its market is predicted to touch EUR 150 Billion by 2028 [ 5 ]. It can be analyzed from the shipment of wireless wearable BAN devices, which was EUR 113.2 million in 2017 and was estimated to reach EUR 223.3 million every year by 2021. One of the driving factors was COVID-19 during this period [ 5 ]. As for the global enterprise market of wireless wearables is concerned, alone it was over EUR 18 billion in 2017, which is estimated to grow at a CAGR of 11.8%, taking 2017 as the beginning and 2026 as the ending year [ 5 , 188 ]. Similarly, a business research organization named “360 Research Reports” published its analysis result in June 2021, which forecasts that the global market of wireless wearable body area networks, which was at USD 11950 million in the year 2021 will increase with the compound annual growth rate of 6.6% from 2021 to 2027 [ 189 ]. In addition to this, an organization named “Market Research Future” also forecasts that the market of body area network devices can rise up to USD 21 billion at a CAGR of 13% by 2025 [ 190 , 191 ].
Return on investment in the wearable BAN industry can also be assessed from a report recently released by a leading provider of wearable BAN devices named Gartner [ 192 ]. The report shows a continuous increasing trend in the use of wearable devices, as shown in Figure 13 . The report discloses that the spending on ear-worns rose from USD 14,583 million to USD 32,724 million from 2019 to 2022, and it is predicted that it will rise from USD 39,220 million to USD 44,160 from 2021 to 2022. It is observed that consumer spending on Smartwatch increased from USD 18,501 million to USD 21,758 million during the period of 2019 to 2020, and it has a chance to rise from USD 25,827 million to USD 31,337 million from 2021 to 2022. According to this report, smartwatches and bands collectively captured 51% share of the market in 2019. In 2021, ear-worns were the leading wearable with a market share of 48%, and smartwatches and wristbands are at the second number with a collective market share of 37%. Similar trends are predicted for the year 2022 in this report.

Consumer spendings on wearables [ 192 ].
Fortunately, we have data available about the major wearable global market players that show that Apple is the top shareholder in the market of smartwatches [ 193 ]. According to the reported data, CAGR of the wearable BAN market could be seen as 19.48% from 2019 to 2026. Figure 14 shows the share of a few other players as well.

Year 2020 major players of smartwatches [ 193 ].
Similarly, IDC Corporate USA reported that Apple retained the first position with about 34.9% of the wearable shipment market share from 2020 to 2021 (4 rth ), whereas Xiaomi, Samsung, Huawei, Imagine Marketing, and others had an 8.5%, 7.9%, 5.6%, 5.4% and 36.6% wearable market share in the fourth quarter of 2021 [ 194 ]. Wearables that were included in the survey is earwear, watches, wristbands, and others. The information from 2020 and 2021 is given in Figure 15 .

Year 2020 and 2021 major players of wearable shipment [ 194 ].
Similar to a business survey on wearable major players presented in [ 194 ], Federica Laricchia [ 195 ] published a similar report but with greater coverage of wearable vendors and the time span, i.e., from 2014 to the third quarter of 2021. Year-wise average percentage shipment share of wearable devices is shown in Figure 16 , but complete quarter-wise information can be obtained from [ 195 ].

Year 2020, 2021 Major Players of Wearable Shipment [ 195 ].
3.2. WEARABLE/WBAN Regulatory for Body
It has been observed that people know less about the regulatory bodies and their guiding principles regarding medical devices. That is why we decided to include this section as a part of this study. The production, shipment, and uses of wearable BAN devices are increasing exponentially; due to this, manufacturers are required to comply with different factors or parameters of health, environment, and data protection laws, standards, and regulations. In addition to this, they are supposed to follow the different regulatory requirements of wireless connectivity, cybersecurity, product safety, chemical ingredients of the product, electromagnetic compatibility, device interoperability, one-time-use of plastic, e-waste, disposal, and many more [ 196 ]. Due to the exponential growth of wearable BAN devices across the world, their range and complexity have also increased. This growth rate triggered the evolution of more stringent and robust policies, standards, rules and regulations for wearable BAN devices. They must be obeyed by the manufacturers. However, it has been observed that the regulation of such devices significantly varies all around the world, which is very strict to none [ 197 ]. These regulations help manufacturers sell their products in multiple countries of the world that follow predefined sets of rules and regulations for wearable BAN and medical devices.
The purpose of developing standards, policies, rules and regulations is to ensure the safety of consumers because they are not capable of deciding which medical device to buy, which to use, how to use it, and how to assess the potential risks behind the use of particular device or medicine [ 196 ]. It means the BANs medical devices cannot obtain success if they do not comply with the regulations and standards set by regulatory and standardizing authorities. That is why device manufacturing companies focus on different requirements and parameters of health-related devices in light of guidelines that are provided by regulatory bodies and authorities. The generic names are given to such requirements, as shown in Figure 17 . However, respective stakeholders such as manufacturers or importers can obtain information about standard requirements, guidelines, rules/regulations, and procedures, from the respective regulatory authority of that region for manufacturing, launching, promoting/marketing, and disposing-off of such wearable BAN devices. Regulatory authorities or standardizing organizations provide all sorts of technical documents that are required to be submitted to activities. Furthermore, the devices may be medical or non-medical.

Focus of medical device companies [ 196 ].
It is not possible to discuss the rules and regulations of different regulatory bodies that are active in different countries of the world for regulating the manufacturing, use, and disposal of wireless wearable BAN devices. Therefore, we have decided to only provide authentic and useful links to different regulatory organizations and their guidelines, policies, standards, rules, and regulations. For instance, Canadian rules and regulations for medical devices are devised and consolidated by Medical Device Regulation (MDR). They are published by the Canadian health minister on the official law website of the Govt. of Canada [ 198 ]. This is a very recent document that was updated on 20 October 2021. It is a very useful document for the manufacturers of wearable medical BAN devices because it contains the latest guidelines concerning the regulation of such devices. Regulatory bodies are working on regulations in which a manufacturer should submit a single report that must meet the requirements of all regulatory bodies. There are different authorities who are responsible for the regulation and standardization of health-related devices (medical or non-medical), which may be wireless wearable body area network devices or they may be conventional medical equipment. Authority-wise, major multinational regulatory bodies are given in Table 9 . In addition to this, country or region-wise, they are given in Table 10 . There are some organizations that cover multiple countries or states, but they are placed in Table 9 considering the limitation of their application areas. This is just for the ease of a reader; otherwise, it does not matter too much whether they are placed in Table 9 or Table 10 .
National and international regulatory bodies.
| Regulatory Body | Year and Location | Members | Comments |
|---|---|---|---|
| WHO [ ] | 1948, Geneva (Switzerland) | Globe is a member of the Word Health Organization (WHO) | Looks into global health concerns. , Accessed on: 14 April 2022 |
| Global Harmonization Task Force (GHTF), its website is ceased, visit [ ] | 1992, USA | USA, European Union (EU), Japan, Australia and Canada, AHWP, International Organization for Standardization (ISO), and the International Electrotechnical Commission (IEC) | Volunteer, the original group of people from MDR formed it for the regulation of medical. GHTF was replaced by International Medical Device Regulators Forum (IMDRF) in 2012 with the aim build a strong foundation of GHTF. , Accessed on: 14 April 2022, , Accessed on: 14 April 2022, , Accessed on: 14 April 2022 |
| IMDRF [ ] | 1911, NA | Australia, Brazil, Canada, China, Europe, Japan, Russia, Singapore, South Korea, USA | Successor of GHTF |
| ISO [ ] | 1947, Geneva Switzerland | 163 countries are members International Organization for Standardization (ISO) | largest organization in the world for formulating standards , Accessed on: 14 April 2022 |
| Emergency Care Research Institute (ECRI) [ ] | 1968, Pennsylvania USA | USA, European Free Trade Association (EFTA), But USA and Canada mutually developed Universal Medical Device Nomenclature System (UMDNS) | ECRI maintained UMDNS, the development of Asian Medical Device Nomenclature System (AMDNS) is also based UMDNS , Accessed on: 14 April 2022 |
| APEC [ ] | 1989, Singapore | Australia, Brunei Darussalam, Canada, Indonesia, Japan, Korea, Malaysia, New Zealand, the Philippines, Singapore, Thailand, USA, China, Hong Kong, Chinese Taipei (Taiwan), Mexico, Papua New Guinea, Chile, Peru, Russia and Vietnam | Asia-Pacific Economic Cooperation (APEC) provides forum for free trade among member countries , Accessed on: 14 April 2022 |
| Asian Harmonisation Working Party (AHWP) [ ] | 1996–97, Hong Kong (Asia) | Abu Dhabi (UEA), Brunei Darussalam, Cambodia, Chile, China, Chinese Taipei (Taiwan), Hong Kong SAR, India, Indonesia, Jordan, Saudi Arabia, Korea, Laos, Malaysia, Myanmar, Pakistan, Philippines, Singapore, South Africa, Thailand, and Vietnam | It ensures the regulation of medical devices in Asia, now working on Safety Alert Dissemination System. , Accessed on: 14 April 2022 |
| Association of Southeast Asian Nations (ASEAN) [ ] | 1967, Jakarta (South Asia) | Bangkok, Indonesia, Malaysia, Philippines, Singapore, Thailand, Brunei Darussalam, Vietnam, Laos, Myanmar and Cambodia. Within ASEAN The Medical Device Product Working Group (MDPWG) is responsible for the regulations of medical devices. | The ASEAN Medical Device Directive (AMDD) formulate basic requirements for the safety, performance and efficiency of medical devices that include a device classification and post-marketing alert system that should be circulated throughout the ASEAN. , Accessed on: 14 April 2022 |
| NICE [ ] | 1999, UK. | European Union. UK is a member of The National Institute for Health and Care Excellence (NICE) | regulates the use health technologies and clinical practices in the UK. Also provides guidance on health care services and promotion. , Accessed on: 14 April 2022 |
| ETSI [ ] | 1988, Sophia Antipolis, France | European Union | ETSI regulates technical standards of ICT (Information and Communications Technologies) enabled devices, systems and services , Accessed on: 14 April 2022 |
| FCC [ ] | 1934, USA | US States comply with Federal Communications Commission (FCC) | FCC regulates radio, TV, satellite and cable communication in USA. FCC and other regulatory bodies look into the issues such as how much radio frequency/ energy absorption is harmful for humans , Accessed on: 14 April 2022 |
| HIPPA [ ] | Act of 1936, USA | US States follows Health Insurance Portability and Accountability Act (HIPPA) | In the USA, HIPPA is responsible for ensuring that the privacy, integrity and access controls are meeting defined standards, rules and regulation. , Accessed on: 14 April 2022 |
Country-wise regulatory bodies.
| Country | Regulatory Body | Year | Purpose |
|---|---|---|---|
| USA | The Food and Drug Administration [ ] | 1906, Maryland (USA) | oversees radio and non-radio based medical devices, medicines and drugs, cosmetics, and biologics in the USA |
| Russia | Roszdravnadzor (Federal Service on Surveillance in Healthcare and Social Development | 2004, Moscow (Russia) | it handles registration, clinical safety and efficiency of medical devices. It also oversees post-market surveillance of these devices |
| Russia | Gosstandart (Federal Agency for Technical Regulation and Meteorology) | 2004, Moscow (Russia) | ensures that imported devices meet all Russian standards. Its parent body is Ministry of Industry and Trade |
| Russia | Rospotrebnadoz (Federal Service for Supervision in the Area of Consumer Rights and Welfare Protection) | 1922, Moscow | ensures that BAN devices meet hygienic and epidemiological regulations |
| China | State Food and Drug Administration (SFDA), China Food and Drug Administration (CFDA) in 2013 China: Also a member of AHWP and APEC | CFDA (2013), NMPA (2018), Beijing (China) | accountable for the regulation of locally manufactured and imported BAN medical devices. CFDA was renamed as National Medical Products Administration in 2018 |
| Hong Kong | Device Administrative Control System (MDACS), Hong Kong is also also a member of AHWP and APEC | 2004, Hong Kong | The Medical Device Division (MDD) is accountable for implementing MDACS and developing a long-term statutory regulatory framework for local and imported medical devices. The old name of MDD was Medical Device Control Office (MDCO) formed in 2004. |
| India | Central Drug Standards Control Organization (CDSCO) India: Also a member of AHWP, Based on The Drugs and Cosmetics Act 1940 and Rules 1945, India | NA | works under Ministry of Health and Family Welfare. Carries regulation of medical devices, imported implantable, diagnostic kits and sterile devices require registration under the current system, registration will follow the GHTF, Central Licensing Approval Authority (CLAA) |
| Iran | Ministry of Health and Medical Education—Food and Drug Administration, National Medical Device Directorate [ ] | NA, NA | device classification follows GHTF, registration is similar to FDA or EU. |
| Israel | Medical Device Division of the Ministry of Health (AMAR) [ ] | NA, NA | devices regulation strictly follows US FDA and EU CE. |
| Jordan | The Jordan Food and Drug Administration (JFDA) [ ], Jordan is also a member of AHWP | 2003, Amman (Jordan) | enforces laws and regulation for medical device, if the device is approved from USA FDA and EU CE it does need clearance in Jordan |
| Saudi Arabia | The Saudi Food and Drug Authority (SFDA) [ ], Saudi Arabia is also a member of AHWP | 2003 | only those devices are permitted that have approval from any one of the GHTF member |
| UAE | UAE Ministry of Health Drug Registration and Control Department [ ], United Arab Emirates (UAE) is also a member of AHWP | NA, NA | UAE adopts guidelines of GHTF, EU, Australian TGA and USA FDA in addition to UAE Pharmacy Law No4 for 1983 |
| Africa | National Medicines Regulatory Authorities (NMRA) [ , ], African Organization for Standardization (ARSO) [ ], The African Network for Drugs and Diagnostic Innovation (ANDI), African Union (AU) and United Nations Economic Commission for Africa (UNECA) [ ] | ARSO (1970, Kenya), UNECA (1958) | Only 7% of African countries have NMRA, 63% have minute regulations, and 31% are without regulations. ANDI was developed in phases by WHO in collaboration with TDR, AFRO and EMRO, African Development Bank, etc. [ ]. More on regulatory authorities in African and East African countries can be seen from [ , ]. |
| Caribbean | Pan American Health Organization (PAHO) [ ], also operates in Central and South America | 1902, Washington DC | PAHO has assigned a task to ECRI to develop and coordinate programs for medical device safety and regulation |
| South America | Mercado Común del Sur (MERCOSÚR) [ ], Argentina, Brazil, Paraguay, Uruguay, Venezuela Chile, Bolivia, Colombia, Ecuador and Peru | 1991, Montevideo (Uruguay) | regulation for medical devices, single approval scheme similar to EU, Products with FDA/EU marks having Free Sale Certificate (FSC) or a Certificate to Foreign Government (CFG) affirm they can be sold |
| Mexico | Federal Commission for the Protection against Sanitary Risk (COFEPRIS) [ ] | 2001, Mexico | regulation of medical devices and IVDs. Mexico is also a member of APEC and HAFTA |
| Cuba | left for the State Control of Medicines, Equipment and Medical Devices (CEMED) [ ], Cuba is also a member of GHTF | NA, La Habana | regulation of medical devices based on GHTF. CCEEM is in La Habana (Cuba) |
3.3. WEARABLE/WBAN Feasible Projects
Human life is always in the process of improvement and betterment. From this study, we have come to know that wireless wearable BAN devices are playing a vital role in this regard. However, the researchers are still working hard to design and develop more sophisticated devices for the well-being of human life. One such effort is the recent development of OvulaRing, Vitalpatch, FreeStyle Libre, and Zio XT ® [ 74 ]. OvulaRing is for doctors and ladies; it can find the most suitable time of fertility. VitalPatch can measure HR (Hear Rate), RR (Respiratory Rate), and temperature. It can also detect falls and perform ECG. Similarly, FreeStyle Libre is implanted under the skin; it can monitor sugar levels. Similarly, Zio XT ® can detect irregular activities of the heart.
One of the leading projects in the direction of a future wearable is H2020 A-WEAR ITN/EJD. It is a four-year project (2019–2022) whose target is to educate, train and supervise 15 researchers to face the future challenges of wearable technology. This project is funded by European Union’s Horizon 2020 (H2020) Marie Sklodowska-Curie Innovative Training Networks H2020-MSCA-ITN-2018 call https://projects.tuni.fi/a-wear/ , accessed on 14 April 2022 [ 5 ].
Hospital Without Walls is another attempt made by Australia’s Commonwealth Scientific and Industrial Research Organization (CSIRO) whose target is to provide continuous vital sign monitoring information of the person to medical experts through telephone lines or using the internet. This healthcare system makes use of miniature low-power wearable radio technology to transmit health information to the home server and then to suitable medical experts using WAN technology [ 227 ].
The pace of wearable technology can be imagined from the data that are being uploaded on PatientsLikeMe72 and the evolution of self-governed healthcare community projects such as Nightscout and the Open Artificial Pancreas73, which gives a clear indication of future research and development perspectives of a wireless wearable healthcare system [ 228 ].
Selective information has been extracted from the article written by Luis et al. [ 229 ] and Rahat et al. [ 74 ] and given in Table 11 . The military projects have not been added to this table as their information is already provided in Table 4 .
Wireless wearable body area networks projects [ 74 , 229 ].
| Project | Application | Communication |
|---|---|---|
| Body Inertial Sensing | Meant for hospitals, where it provides information to measure three degrees of freedom | Body Sensor Networks (BSN) ZigBee/Bluetooth |
| Code Blue | Targets medical care to provide pulse rate, BP, and motion information | Intra-BAN (Wired), Inter-BAN (Zigbee, Mesh), Beyond-BAN (N/A) |
| LOBIN | Measures HR, BP, Temperature | Wireless Sensor Networks (IEEE 802.15.4) |
| MEDISN | Used in hospitals for emergency detection | WSN for monitoring patient physiological data and multi-hop wireless backbone for carrying these data |
| Unobstructive BAN | Applied in hospital and disaster events to generate alarms based on identified movements and postures | Intra-BAN is Low-power and short-range WBAN, Inter-BAN is Bluetooth, and or Beyond BAN is GSM |
| WPWS | Measures temperature, humidity, and velocity of air flow | RFID like system |
| BASUMA | Targeted application area is health monitoring for measuring ECG, Respirate/Breath Rate SpO | Intra-BAN (UWB), Inter-BAN (N/A), Beyond-BAN (N/A) |
| MobileHealth | Monitoring of patients ECG in ambulance | Intra-BAN (Manual), Inter-BAN (Zigbee, Bluetooth), Beyond-BAN (GPRS, UMTS) |
| AID-N | Reply BP, ECG, Pulse Rate in emergency systems | Intra-BAN (Wired), Inter-BAN (Zigbee, Bluetooth), Beyond-BAN (WiFi, Internet, Cellular Networks) |
| MAHS | Targets health application to provide information about breathing and pulse rate, body motion, temperature, pressure and SpO . | Intra-BAN (Bluetooth), Inter-BAN (Zigbee), Beyond-BAN (Internet) |
| LifeMinder | Targets self-care applications. Used to report pulse rate, ECG, SpO , temperature, body movement, emotional state intensity | Intra-BAN (Bluetooth), Inter-BAN (Bluetooth), Beyond-BAN (Internet) |
| SMART | Monitor patients ECG, SpO while sitting in waiting room | Intra-BAN (Wired), Inter-BAN (Bluetooth), Beyond-BAN (N/A) |
| CareNet | Targets remote healthcare applications to report BP, temperature and body inertial (posture and movement) information | Intra-BAN (N/A), Inter-BAN (Zigbee), Beyond-BAN (Internet, Multi-hop 802.11) |
| ASNET | Targets remote healthcare applications for providing patient BP, temperature information | Intra-BAN (Wired, WiFi), Inter-BAN (Wired, WiFi), Beyond-BAN (Internet, GSM,) |
| WHMS | Used in health for monitoring ECG/EKG | Intra-BAN (Wired), Inter-BAN (Wired, WiFi), Beyond-BAN (N/A) |
| Human++ | Provides entertaino-medical living standard with ECG, EMG, EEG facility | Intra-BAN (UWB), Inter- BAN (N/A), Beyond-BAN (N/A) |
| WiMoCA | Provides gesture detection in sports | Intra-BAN, Inter-BAN (Bluetooth), Beyond-BAN (WiFi, Cellular Networks) |
| Ayushman | Used in health monitoring and provides information about EKG, BP, SpO and body gesture | Intra-BAN (Zigbee), Inter-BAN (WiFi), Beyond-BAN (Internet) |
| Lifeguard | Applied in space and terrestrial applications to monitor ECG, respiration and pulse rate, SpO and body motion | Intra-BAN (Wired), Inter-BAN (Bluetooth, Internet), Beyond-BAN (Bluetooth/Internet) |
| IBBT IM3 | Used in Telemedicine and Telecare application and measures patient ECG, respiration and heart rate | Intra-BAN (N/A), Inter-BAN (N/A), Beyond-BAN (Internet) |
| MITHrl | Used in healthcare applications and measures patient ECG and EKG | Intra-BAN (Wired), Inter-BAN (WiFi), Beyond-BAN (N/A) |
| UbiMon | Used in healthcare application and measures patient ECG and EKG, SpO | Intra-BAN (Zigbee), Inter-BAN (WiFi/GPRS), Beyond-BAN (WiFi/GPRS) |
| H2020 MCSA ITN/EJD A-WEAR | Used in healthcare application and measures patient ECG and EKG, SpO | Intra-BAN (Zigbee), Inter-BAN (WiFi/GPRS), Beyond-BAN (WiFi/GPRS) |

4. Open Issues
4.1. research challenges.
Wireless wearable body area networks encounter some interesting challenges that might be easily resolved in resource-enriched networks but difficult to resolve in low-power devices such as wearable and BANs. These issues greatly affect the efficiency, deployment and social acceptance of wireless wearable BAN devices. They are briefly discussed below to attract the attention of scholars, scientists and researchers so that they may address them while designing the security and privacy solution for wireless wearable BANs.
4.1.1. Security vs. Efficiency
For data security of wearable and WBANs, efficiency is one of the most stringent requirements. However, due to limited resources for computation, storage and data rate, it is very hard to achieve high efficiency. That is why it is recommended to make use of lightweight cryptographic functions as much as possible for data security. These functions must be low-cost in terms of processing, memory, transmission and power consumption because complex security primitives may lead to high computational load, which may also lead to early drainage of battery [ 5 , 38 ].
4.1.2. Security vs. Safety
It is very difficult to prioritize between security and safety, especially in emergency conditions when the patient is unconscious and cannot respond. Very strict security in terms of accessing patient data may prevent the medical staff from acquiring it well on time. Thus, it can create an adverse situation when giving medical treatment to the patient. However, at the same time, loose and flexible access control may open back doors for malicious users to illegally play with the patient’s medical information with evil intentions in mind. Therefore, it is difficult to provide good security with loose data access rights.
4.1.3. Security vs. Usability
The users of wireless wearable BAN devices may not be experts, which is why these devices must be easy to operate, configure and integrate with other interfaces such as mobiles, laptops, cloud servers, etc. In order to avoid human errors, it is required that there must be a minimum possible human interaction in data security procedures. For example, the technique of automatic device pairing can be used to establish initial secure communication between wireless wearable BAN devices. Similarly, it is well-advised to provide security services at different phases of data collection, processing, storage, and retrieval.
4.1.4. Device Interoperability
Device interoperability is one of the key factors for the social, technical, and industrial acceptance of the wireless wearable WBAN devices [ 5 ]. There might be different vendors and manufacturers of these and similar devices. However, the devices must be compatible and interoperable with one another. For example, it is appealing when someone connects a Samsung Galaxy health monitoring Watch-3 with an Apple iPhone [ 230 ]. The views of wearable and BAN users might be adverse due to the lack of device interoperability.
4.1.5. Device Authentication
In addition to the data or message authentication, device authentication in the case of wearable and BAN devices is also one of the critical issues that have attracted significant attention from security researchers. Devices claiming their legitimacy by rendering that they are honest and belong to the same wearable/BAN network need validation. Different research studies are observed in the literature regarding BAN device authentication meaning whether a claimant really hosted on the same body or not. However, this area is still in its infancy and requires more research work.
4.1.6. Secret Key Acquisition
We do not advocate the employment of public key cryptography algorithms for low-resource wearable BAN as they are resource-hungry and conflict with the limited resources of devices. We believe in unleashing new methods of secret key acquisition compared with traditional DH key exchange protocols. Different wireless information-theoretic security approaches are proposed that exploit the natural process of the physical and MAC layers for establishing the shared secret. The shared secret can be used for authentication and encryption.
4.1.7. Strict Regulations
Wireless wearable BANs have to pass through the strict regulation of the FCC and other health regulatory and standardization bodies.
4.2. Research Directions
The field of wireless wearable body area networks calls for different open research contributions to improve its usage. Key research challenges are given below.
- 1. Global RF Design: The Radio Frequency of the Wireless Wearable BAN must be such that the devices can operate in any part of the world because it is observed that some wireless channels are allowed to operate in the USA but not in other parts of the world or some channels are used in one part of the world but not in other. Thus, RF design must be able to cope with heterogeneous wearable BAN devices [ 38 ].
- 2. Performance: Other high-power ISM wireless devices operating in the surrounding may degrade the performance of low-power wearable and WBAN devices making them less attractive and appealing for high-quality medical and healthcare applications. For instance, Wireless Medical Telemetry Service (WMTS) frequency bands are extensively being used, but unfortunately, their use is limited to healthcare applications in the USA. Moreover, UWB is a good candidate technology for wireless wearable devices, but at the same time, it is badly affected by the interference of the co-existence of high data rate applications such as wireless multi-media.
- 3. 2360–2400 MHz Band: Federal Communication Commission (FCC) has opened the 2360–2400 MHz band for medical WBAN. It is believed that the band will be used to devise an artificial nervous system to reinstate sensation and mobility and regain the functionality of paralyzed limbs and organs. However, the devices based on this medical WBAN frequency band are required to test and validate against the FCC health-related rules and regulations [ 231 ]. Therefore, designing devices that exactly meet the FCC regulations is also one of the great challenges.
- 4. Channel Model Design: Another research challenge is the designing of the RF channel model because it plays an important part in the designing of PHY (Physical Layer) technologies. PHY is an abbreviation of the Physical Layer of TCP/IP or OSI Model. PHY is implemented to connect the MAC layer with the physical medium; in this, it is a wireless Radio Frequency (RF). PHY consists of RF, Transceiver, DSP (Digital Signal Processor), communication protocol, and channel codes. PHY is integrated with MAC in SOC (System on a Chip) technology. Examples of wireless PHY are 3G, 4G, LTE, WiMAX, and UWB.
- 5. Radio Antenna Design: Designing an antenna for wireless wearable BAN devices is also very critical due to restrictions on size, shape and choice of material [ 232 , 233 ]. Since the devices are wearable, patched on the body or implanted inside the body, the size of these antennae must be miniaturized. Designers do not have too many choices for the shape of antennae; it is the organ that puts restrictions on the shape. The material that can be used to design antennae should be harmless for the human body such as titanium or platinum. However, antennae made of such material result in low performance when compared with the antennae made up of copper.
- 6. Physical Layer Protocols: Physical layer protocols of wearable and BAN devices must assure low power consumption without compromising reliability, connectivity, throughput and turnaround time [ 5 , 38 ]. Fast wake-up from sleep mode and speedy turnaround time can significantly save the power of wearable/WBAN devices. Presently, energy efficiency is being achieved through duty cycling, but researchers are endeavoring to find new ways of energy saving such as low-power listening harvesting [ 234 ].
- 7. MAC Design: It is always required to have a wearable BAN MAC (Medium Access Control) layer that should be resilient to interference experienced due to the co-existence of multiple WBANs in crowded areas such as hospitals. MAC layer protocols should be adaptable to frequent topology changes. Moreover, MAC protocol of the WBAN should be able to switch to a silent channel in the case of severe interference due to the co-existence of similar networks operating in the surrounding using the same frequency band [ 38 ].
4.3. Emerging Techniques in WBAN
4.3.1. human body communication (hbc).
After IoTs, a new concept is emerging in BANs called Internet of Bodies (IOBs) that makes use of conductive features of our tissues to make human body communication, but completely benefiting from IoBs is still a topic of hot discussion related to risks and challenges, such as HBC channel modeling [ 22 ].
4.3.2. Energy Harvesting
It is one of the emerging concepts in WBANs, which, in addition to working on power optimization, aims to extend the battery life by harvesting light/solar, motion, thermal or RF energy [ 235 , 236 ].
4.3.3. Quantum Computing
It is believed that quantum computing will solve many problems in large-scale WBAN calculations such as magnetic resonance imaging (MRI), computed tomography (CT) and nuclear medicine (e.g., positron emission tomography (PET)) [ 235 ].
4.3.4. Graph Neural Networks (GNN)
Recently, GNN has had wonderful secure applications in social networks, recommendation and knowledge systems and life sciences. In computer science, a graph is a data structure in which the two components are named vertex and edge. GNN is a neural network that operates on a graph structure to produce desired results. In wearable WBANs, they are being used for human action recognition [ 237 , 238 ].
4.4. Artificial Intelligence: Machine and Deep Learning
Machine learning is one of the key emerging technology for processing health data for diagnosis purposes and is playing an important role in enhancing the performance of WBANs [ 239 , 240 ]. Communication networks are also benefiting from technology [ 241 ].
4.4.1. Blockchain
Blockchain is a distributed database shared among the different nodes of the network. Blockchain is an innovative technology in the sense that it ensures the security of records and assurance of trust without using a third party. WBAN data can be stored and protected using blockchain [ 242 , 243 ]. Blockchain integration with WBANS, its trends and future opportunities can be seen from [ 243 , 244 ].
4.4.2. Digital Twins
It is an outstanding technology that simulates what-if scenarios for products, and processes that need to be changed and tested before deploying into the real/physical world [ 245 ]. Digital racing is one of the best examples that can be given to understand this concept. Digital twin technology is being applied in the healthcare industry for developing new methods of diagnosis and prognosis of remaining life, tear and wear and injury locations, etc. [ 246 ].
5. Conclusions and Future Work
The following are a few points that conclude our present study concisely.
- 1. Wireless wearable BAN devices are one of the marvelous inventions in human history that improves the apex quality of human life.
- 2. There is great investment potential in the global industry of wireless body area networks that have also been observed from the different CAGR values reported in many global market analysis reports.
- 3. On the other hand, a lot of work is still required to make those devices whose manufacturing ingredients involve radio or electromagnetic waves and frequencies safe for the living body cells and tissues.
- 4. Wireless body area networks consist of very low-resource devices, which is why it is demanded that communication and security protocols must be light in computation, storage, and transmission because these factors are directly linked with the lifetime of BAN nodes as they are battery powered.
While considering the resource limitations of wearable wireless BAN devices, it is highly desired to look for security measures that must be lightweight with respect to time (processing), space (memory), and messaging (bandwidth). That is why, in the future, we have planned to use some probabilistic space-efficient data structures, such as hyperloglog, count-min sketch, bloom filters, cuckoo hashing, to achieve device authentication, data confidentiality, and integrity. We believe our future research work will prove to be a groundbreaking step in the acquisition of secret keys and carrying device authentication not only in wearable WBANs but also in IOTs.
Acknowledgments
This research was supported by the Institute for Information and Communications Technology Planning and Evaluation (IITP) grant funded by the Korean government (Ministry of Science and ICT, South Korea) (No. 2022-0-01200, Training Key Talents in Industrial Convergence Security).
Funding Statement
This research received no external funding.
Author Contributions
Conceptualization, D.S.B. and A.I.; methodology, D.S.B. and H.K.; validation, S.S; formal analysis, Z.I.; resources, K.-I.K.; data curation, A.A., H.K.; writing—original draft preparation, D.S.B.; writing—review and editing, A.I.; visualization, K.-I.K.; supervision, A.A.; project administration, S.S. and K.-I.K.; funding acquisition, K.-I.K. All authors have read and agreed to the published version of the manuscript.
Institutional Review Board Statement
Informed consent statement, data availability statement, conflicts of interest.
The authors declare no conflict of interest.
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Recommended Articles
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Wireless body area network (wban): a survey on architecture, technologies, energy consumption, and security challenges.

1. Introduction
1.1. related work, 1.2. contribution.
- WBAN, its architecture, tasks, and communication technology, with a particular focus on new generation sensors to improve the quality of communication with different devices;
- The main challenges facing WBAN including security and power consumption;
- Accurate classification of attacks and threats affecting the WBAN;
- A detailed review (M. ATTEMPT, SIMPLE, HPOR, HEAT, GACA) of the essential routing algorithms proposed or used on existing medical devices and sensors in the network.
1.3. Article Structure
2. wireless body sensor networks, 2.1. using sensors for health control, 2.2. iot healthcare, 3. body sensor network architecture, 3.1. sensor network architecture, 3.2. how to run the body sensor network, 4. the body sensor network function, the performance of wban, 5. wban challenges and implementation problems, 5.1. wban challenges, 5.1.1. challenges related to the mac layer, 5.1.2. challenges related to the network layer, 5.1.3. challenges related to the transportation layer, 5.1.4. application layer challenges, 5.2. implementation problems in wban, physical problems, 6. wireless communication technologies, 6.1. zigbee technology, 6.2. bluetooth technology, 6.3. ultrawideband (uwb) technology, 6.4. wi-fi—ieee 802.11, 7. new generations of sensors for body sensor networks, 7.1. obtrusive nodes, 7.2. parasitic nodes, 7.3. symbiotic nodes, 7.4. bio-inspired nodes, 8. energy consumption reduction in body sensor networks, 8.1. monitoring patients, 8.2. discussion of energy conservation in body sensor networks.
Click here to enlarge figure
9. Security in WBAN
9.1. wban security requirements, 9.2. security threats, different types of information delivery attacks, 9.3. security mechanisms, 9.3.1. cryptography, 9.3.2. key management, 9.3.3. secure routing, 9.3.4. trust management, 9.3.5. blockchain technology, 10. security attacks on wireless sensor network, 10.1. active attacks, active attacks on wsns are described below, 10.2. passive attacks.
- Monitoring and Eavesdropping
- Traffic Analysis
- Hidden Enemies
10.3. Attacks on The Physical Layer
11. methods presented for health monitoring systems of wireless body sensor networks, 11.1. m-attempt routing protocol, 11.2. simple routing protocol, 11.5. ant-based genetic algorithm routing protocol, 11.6. absorbing markov chain model (amc), 11.7. scheduling sensor nodes using phase logic.
- The average distance between live nodes and the main station;
- Residual energy (in living nodes).
12. Limitation
13. conclusions, institutional review board statement, informed consent statement, data availability statement, conflicts of interest.
- Bangash, J.I.; Abdullah, A.H.; Anisi, M.H.; Khan, A.W. A survey of routing protocols in wireless body sensor networks. Sensors 2014 , 14 , 1322–1357. [ Google Scholar ] [ CrossRef ] [ PubMed ] [ Green Version ]
- Mainanwal, V.; Gupta, M.; Upadhayay, S.K. A survey on wireless body area network: Security technology and its design methodology issue. In Proceedings of the 2015 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India, 19–20 March 2015. [ Google Scholar ]
- Tavera, C.A.; Ortiz, J.H.; Khalaf, O.I.; Saavedra, D.F.; Aldhyani, T.H. Wearable wireless body area networks for medical applications. Comput. Math. Methods Med. 2021 , 2021 , 5574376. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Javaid, N.; Khan, N.A.; Shakir, M.; Khan, M.A.; Bouk, S.H.; Khan, Z.A. Ubiquitous healthcare in wireless body area networks-a survey. arXiv 2013 , arXiv:1303.2062s. [ Google Scholar ]
- Kour, P.; Kang, S.S. Hybrid Routing Protocol for Wireless Body Area Networks. Int. J. Innov. Technol. Explor. Eng. 2019 , 8 , 1926–1932. [ Google Scholar ] [ CrossRef ]
- Nadeem, A.; Hussain, M.A.; Owais, O.; Salam, A.; Iqbal, S.; Ahsan, K. Application specific study, analysis and classification of body area wireless sensor network applications. Comput. Netw. 2015 , 83 , 363–380. [ Google Scholar ] [ CrossRef ]
- Gupta, M.; Tanwar, S.; Rana, A.; Walia, H. Smart Healthcare Monitoring System Using Wireless Body Area Network. In Proceedings of the 2021 9th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 3–4 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–5. [ Google Scholar ]
- Saleh, Y.N.; Chibelushi, C.C.; Abdel-Hamid, A.A.; Soliman, A.H. Privacy Preservation for Wireless Sensor Networks in Healthcare: State of the Art, and Open Research Challenges. arXiv 2020 , arXiv:2012.12958. [ Google Scholar ]
- Rahangdale, H. A Review on WMSN (Wireless Medical Sensor Networks) for Health Monitoring Systems. ECS Trans. 2022 , 107 , 1973. [ Google Scholar ] [ CrossRef ]
- Adarsh, A.; Kumar, B. Wireless medical sensor networks for smart e-healthcare. In Intelligent Data Security Solutions for e-Health Applications ; Academic Press: Cambridge, MA, USA, 2020; pp. 275–292. [ Google Scholar ]
- Qu, Y.; Zheng, G.; Ma, H.; Wang, X.; Ji, B.; Wu, H. A Survey of Routing Protocols in WBAN for Healthcare Applications. Sensors 2019 , 19 , 1638. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Abidi, B.; Jilbab, A.; Mohamed, E.H. Wireless body area network for health monitoring. J. Med. Eng. Technol. 2019 , 43 , 124–132. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Rady, A.; El-Rabaie, E.S.M.; Shokair, M.; Abdel-Salam, N. Comprehensive survey of routing protocols for Mobile Wireless Sensor Networks. Int. J. Commun. Syst. 2021 , 34 , e4942. [ Google Scholar ] [ CrossRef ]
- Xu, G.; Wang, M. An energy-efficient routing mechanism based on genetic ant colony algorithm for wireless body area networks. J. Netw. 2014 , 9 , 3366. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Zou, S.; Xu, Y.; Wang, H.; Li, Z.; Chen, S.; Hu, B. A Survey on Secure Wireless Body Area Networks. Secur. Commun. Netw. 2017 , 2017 , 3721234. [ Google Scholar ] [ CrossRef ]
- Huanan, Z.; Suping, X.; Jiannan, W. Security and application of wireless sensor network. Procedia Comput. Sci. 2021 , 183 , 486–492. [ Google Scholar ] [ CrossRef ]
- Salau, A.O.; Marriwala, N.; Athaee, M. Data security in wireless sensor networks: Attacks and countermeasures. In Mobile Radio Communications and 5G Networks ; Springer: Singapore, 2021; pp. 173–186. [ Google Scholar ]
- Naik, M.R.K.; Samundiswary, P. Wireless body area network security issues—Survey. In Proceedings of the 2016 International Conference on Control, Instrumentation, Communication and Computational Technologies (ICCICCT), Kumaracoil, India, 16–17 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 190–194. [ Google Scholar ]
- Zhong, L.; He, S.; Lin, J.; Wu, J.; Li, X.; Pang, Y.; Li, Z. Technological Requirements and Challenges in Wireless Body Area Networks for Health Monitoring: A Comprehensive Survey. Sensors 2022 , 22 , 3539. [ Google Scholar ] [ CrossRef ]
- Ananthi, J.V.; Jose, P. A perspective review of security challenges in body area networks for healthcare applications. Int. J. Wirel. Inf. Netw. 2021 , 28 , 451–466. [ Google Scholar ] [ CrossRef ]
- Naresh, V.S.; Pericherla, S.S.; Murty, P.S.R.; Sivaranjani, R. Internet of things in healthcare: Architecture, applications, challenges, and solutions. Comput. Syst. Sci. Eng. 2020 , 35 , 411–421. [ Google Scholar ] [ CrossRef ]
- Kateretse, C.; Lee, G.W.; Huh, E.N. A practical traffic scheduling scheme for differentiated services of healthcare systems on wireless sensor networks. Wirel. Pers. Commun. 2013 , 71 , 909–927. [ Google Scholar ] [ CrossRef ]
- Hanson, M.A.; Powell, H.C., Jr.; Barth, A.T.; Ringgenberg, K.; Calhoun, B.H.; Aylor, J.H.; Lach, J. Body area sensor networks: Challenges and opportunities. Computer 2009 , 42 , 58–65. [ Google Scholar ] [ CrossRef ]
- Vera, D.; Costa, N.; Roda-Sanchez, L.; Olivares, T.; Fernández-Caballero, A.; Pereira, A. Body area networks in healthcare: A brief state of the art. Appl. Sci. 2019 , 9 , 3248. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Al-Saud, K.A.; Mohamed, A.; Mahmuddin, M. Survey on Wireless Body Area Sensor Networks for healthcare applications: Signal Processing, data analysis and feedback. In Proceedings of the 3rd International Conference on Computing and Informatics (ICOCI 2011), Bandung, Indonesia, 8–9 June 2011. [ Google Scholar ]
- Liu, Q.; Mkongwa, K.G.; Zhang, C. Performance issues in wireless body area networks for the healthcare application: A survey and future prospects. SN Appl. Sci. 2021 , 3 , 155. [ Google Scholar ] [ CrossRef ]
- Huynh, D.T.; Chen, M. An energy efficiency solution for WBAN in healthcare monitoring system. In Proceedings of the 2016 3rd International Conference on Systems and Informatics (ICSAI), Shanghai, China, 19–21 November 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 685–690. [ Google Scholar ]
- Moungla, H.; Touati, N.; Mehaoua, A. Efficient heterogeneous communication range management for dynamic WBAN topology routing. In Proceedings of the 2013 First International Symposium on Future Information and Communication Technologies for Ubiquitous HealthCare (Ubi-HealthTech), Jinhua, China, 1–3 July 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1–5. [ Google Scholar ]
- Cornet, B.; Fang, H.; Ngo, H.; Boyer, E.W.; Wang, H. An Overview of Wireless Body Area Networks for Mobile Health Applications. IEEE Netw. 2022 , 36 , 76–82. [ Google Scholar ] [ CrossRef ]
- Ullah, S.; Shen, B.; Islam, S.R.; Khan, P.; Saleem, S.; Kwak, K.S. A study of MAC protocols for WBANs. Sensors 2009 , 10 , 128–145. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Kurian, A.; Divya, R. A survey on energy efficient routing protocols in wireless body area networks (WBAN). In Proceedings of the 2017 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India, 17–18 March 2017; IEEE: Piscataway, NJ, USA, 2007; pp. 1–6. [ Google Scholar ]
- Sagar, A.K.; Banda, L.; Sahana, S.; Singh, K.; Singh, B.K. Optimizing quality of service for sensor enabled Internet of healthcare systems. Neurosci. Inform. 2021 , 1 , 100010. [ Google Scholar ] [ CrossRef ]
- Filipe, L.; Fdez-Riverola, F.; Costa, N.; Pereira, A. Wireless body area networks for healthcare applications: Protocol stack review. Int. J. Distrib. Sens. Netw. 2015 , 11 , 213705. [ Google Scholar ] [ CrossRef ]
- Asam, M.; Jamal, T.; Adeel, M.; Hassan, A.; Butt, S.A.; Ajaz, A.; Gulzar, M. Challenges in wireless body area network. Int. J. Adv. Comput. Sci. Appl. 2019 , 10 , 336–341. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Channa, A.; Popescu, N.; Skibinska, J.; Burget, R. The rise of wearable devices during the COVID-19 pandemic: A systematic review. Sensors 2021 , 21 , 5787. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Darwish, A.; Hassanien, A.E. Wearable and implantable wireless sensor network solutions for healthcare monitoring. Sensors 2011 , 11 , 5561–5595. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Barakah, D.M.; Ammad-uddin, M. A survey of challenges and applications of wireless body area network (WBAN) and role of a virtual doctor server in existing architecture. In Proceedings of the 2012 3th International Conference on Intelligent Systems Modelling and Simulation, Kota Kinabalu, Malaysia, 8–10 February 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 214–219. [ Google Scholar ]
- Bouhassoune, I.; Saadane, R.; Chehri, A. Wireless body area network based on RFID system for healthcare monitoring: Progress and architectures. In Proceedings of the 2019 15th International Conference on Signal-Image Technology Internet-Based Systems (SITIS), Sorrento-Naples, Italy, 26–29 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 416–421. [ Google Scholar ]
- Bedi, R.K. An improved energy efficient TDMA based MAC protocol for WBAN. Int. J. Comput. Eng. 2018 , 6 , 34–39. [ Google Scholar ]
- Aishwarya, C. Wireless Body Area Networks–A Review. Int. J. Res. Eng. Sci. Manag. 2022 , 5 , 88–91. [ Google Scholar ]
- Abbas, A.M. Body Sensor Networks for Healthcare: Advancements and Solutions. In Pervasive Healthcare ; Springer: Cham, Switzerland, 2022; pp. 87–102. [ Google Scholar ]
- Hajar, M.S.; Al-Kadri, M.O.; Kalutarage, H.K. A survey on wireless body area networks: Architecture, security challenges and research opportunities. Comput. Secur. 2021 , 104 , 102211. [ Google Scholar ] [ CrossRef ]
- Kołodziej, J.; Grzonka, D.; Widłak, A.; Kisielewicz, P. Ultra wide band body area networks: Design and integration with computational clouds. In High-Performance Modelling and Simulation for Big Data Applications ; Springer: Berlin/Heidelberg, Germany, 2019; pp. 279–306. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Dhawankar, P.; Kumar, A.; Crespi, N.; Busawon, K.; Qureshi, K.N.; Javed, I.T.; Kaiwartya, O. Next-Generation Indoor Wireless Systems: Compatibility and Migration Case Study. IEEE Access 2021 , 9 , 156915–156929. [ Google Scholar ] [ CrossRef ]
- Khan, R.A.; Pathan, A.S.K. The state-of-the-art wireless body area sensor networks: A survey. Int. J. Distrib. Sens. Netw. 2018 , 14 , 1550147718768994. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Mile, A.; Okeyo, G.; Kibe, A. Hybrid IEEE 802.15. 6 wireless body area networks interference mitigation model for high mobility interference scenarios. Wirel. Eng. Technol. 2018 , 9 , 34–48. [ Google Scholar ] [ CrossRef ]
- Chugh, A.; Panda, S. Energy efficient techniques in wireless sensor networks. Recent Pat. Eng. 2019 , 13 , 13–19. [ Google Scholar ] [ CrossRef ]
- Junaid, M. Wireless network sensors applications and challenges in a real-life environment. IEEE-SEM 2020 , 7 , 111–117. [ Google Scholar ]
- Khriji, S.; El Houssaini, D.; Kammoun, I.; Kanoun, O. Energy-efficient techniques in wireless sensor networks. In Energy Harvesting for Wireless Sensor Networks: Technologies, Components and System Design ; De Gruyter Oldenbourg: Berlin, Germany, 2018. [ Google Scholar ]
- Akram, J.; Munawar, H.S.; Kouzani, A.Z.; Mahmud, M.P. Using Adaptive Sensors for Optimised Target Coverage in Wireless Sensor Networks. Sensors 2022 , 22 , 1083. [ Google Scholar ] [ CrossRef ]
- Xiong, C.W.; Tang, M.; Wang, X.H.; Liu, Y.; Shi, J. Evolution model of high quality of service for spatial heterogeneous wireless sensor networks. Phys. A Stat. Mech. Appl. 2022 , 596 , 127182. [ Google Scholar ] [ CrossRef ]
- Roselin, J.; Latha, P.; Benitta, S. Maximizing the wireless sensor networks lifetime through energy efficient connected coverage. Ad Hoc Netw. 2017 , 62 , 1–10. [ Google Scholar ] [ CrossRef ]
- Kargar, M.J.; Ghasemi, S.; Rahimi, O. Wireless body area network: From electronic health security perspective. Int. J. Reliab. Qual. E-Healthc. 2013 , 2 , 38–47. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Fatema, N.; Brad, R. Security requirements, counterattacks and projects in healthcare applications using WSNs-A review. arXiv 2014 , arXiv:1406.1795. [ Google Scholar ]
- Han, N.D.; Han, L.; Tuan, D.M.; In, H.P.; Jo, M. A scheme for data confidentiality in cloud-assisted wireless body area networks. Inf. Sci. 2014 , 284 , 157–166. [ Google Scholar ] [ CrossRef ]
- Kavitha, T.; Sridharan, D. Security vulnerabilities in wireless sensor networks: A survey. J. Inf. Assur. Secur. 2010 , 5 , 31–44. [ Google Scholar ]
- Kumar, R.; Mukesh, R. State of the art: Security in wireless body area networks. Int. J. Comput. Sci. Eng. Technol. 2013 , 4 , 622–630. [ Google Scholar ]
- Li, J.; Ren, K.; Zhu, B.; Wan, Z. Privacy-aware attribute-based encryption with user accountability. In Proceedings of the International Conference on Information Security, Pisa, Italy, 7–9 September 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 347–362. [ Google Scholar ]
- Ferdous, M.S.; Chowdhury, F.; Moniruzzaman, M. A taxonomy of attack methods on peer-to-peer network. In Proceedings of the 1st Indian Conference on computational intelligence and information security (ICCIIS, 07), Pune, India, 1 January 2007; pp. 132–138. [ Google Scholar ]
- ur Rehman, O.; Javaid, N.; Bibi, A.; Khan, Z.A. Performance study of localization techniques in wireless body area sensor networks. In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 1968–1975. [ Google Scholar ]
- Sharma, D. Wireless health care monitoring system with data security and privacy. Int. J. Res. Comput. Eng. Electron. 2013 , 2 , 1–2. [ Google Scholar ]
- Javadi, S.S.; Razzaque, M.A. Security and privacy in wireless body area networks for health care applications. In Wireless Networks and Security ; Springer: Berlin/Heidelberg, Germany, 2013; pp. 165–187. [ Google Scholar ]
- Malik, M.S.A.; Ahmed, M.; Abdullah, T.; Kousar, N.; Shumaila, M.N.; Awais, M. Wireless body area network security and privacy issue in e-healthcare. Int. J. Adv. Comput. Sci. Appl. 2018 , 9 , 2018. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Li, M.; Lou, W.; Ren, K. Data security and privacy in wireless body area networks. IEEE Wirel. Commun. 2010 , 17 , 51–58. [ Google Scholar ] [ CrossRef ]
- Al Ameen, M.; Liu, J.; Kwak, K. Security and privacy issues in wireless sensor networks for healthcare applications. J. Med. Syst. 2012 , 36 , 93–101. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Narwal, B.; Mohapatra, A.K. A survey on security and authentication in wireless body area networks. J. Syst. Archit. 2021 , 113 , 101883. [ Google Scholar ] [ CrossRef ]
- Jabeen, T.; Ashraf, H.; Ullah, A. A survey on healthcare data security in wireless body area networks. J. Ambient. Intell. Humaniz. Comput. 2021 , 12 , 9841–9854. [ Google Scholar ] [ CrossRef ]
- Ren, Y.; Leng, Y.; Zhu, F.; Wang, J.; Kim, H.J. Data storage mechanism based on blockchain with privacy protection in wireless body area network. Sensors 2019 , 19 , 2395. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Al-Janabi, S.; Al-Shourbaji, I.; Shojafar, M.; Shamshirband, S. Survey of main challenges (security and privacy) in wireless body area networks for healthcare applications. Egypt. Inform. J. 2017 , 18 , 113–122. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Commun. Surv. Tutor. 2019 , 22 , 616–644. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Usman, M.; Asghar, M.R.; Ansari, I.S.; Qaraqe, M. Security in wireless body area networks: From in-body to off-body communications. IEEE Access 2018 , 6 , 58064–58074. [ Google Scholar ] [ CrossRef ]
- Chen, C.Y.; Chao, H.C. A survey of key distribution in wireless sensor networks. Secur. Commun. Netw. 2014 , 7 , 2495–2508. [ Google Scholar ] [ CrossRef ]
- Tropea, M.; Spina, M.G.; De Rango, F.; Gentile, A.F. Security in Wireless Sensor Networks: A Cryptography Performance Analysis at MAC Layer. Future Internet 2022 , 14 , 145. [ Google Scholar ] [ CrossRef ]
- Zhang, J.; Zhong, S.; Wang, J.; Yu, X.; Alfarraj, O. Alfarraj: A Storage Optimization Scheme for Blockchain Transaction Databases. Comput. Syst. Sci. Eng. 2021 , 36 , 521–535. [ Google Scholar ] [ CrossRef ]
- Farooq, S.; Prashar, D.; Jyoti, K. Hybrid Encryption Algorithm in Wireless Body Area Networks (WBAN). In Intelligent Communication, Control and Devices ; Advances in Intelligent Systems and Computing; Singh, R., Choudhury, S., Gehlot, A., Eds.; Springer: Singapore, 2018; Volume 624. [ Google Scholar ] [ CrossRef ]
- Gautam, A.K.; Kumar, R. A comprehensive study on key management, authentication and trust management techniques in wireless sensor networks. SN Appl. Sci. 2021 , 3 , 50. [ Google Scholar ] [ CrossRef ]
- Hashemi, S.M. Secure routing of WBAN with Monarchy Butterfly Optimization. In Proceedings of the 2017 2nd International Conference on Communication and Information Systems, Wuhan, China, 7–9 November 2017; pp. 155–158. [ Google Scholar ]
- Remu, S.R.H.; Faruque, M.O.; Ferdous, R.; Arifeen, M.M.; Sakib, S.; Reza, S.S. Naive Bayes based Trust management model for wireless body area networks. In Proceedings of the International Conference on Computing Advancements, Dhaka, Bangladesh, 10–12 January 2020; pp. 1–4. [ Google Scholar ]
- Butun, I. Prevention and Detection of Intrusions in Wireless Sensor Networks. Ph.D. Thesis, University of South Florida, Tampa, FL, USA, 2013. [ Google Scholar ]
- Ali, M.H.; Jaber, M.M.; Abd, S.K.; Rehman, A.; Awan, M.J.; Damaševičius, R.; Bahaj, S.A. Threat Analysis and Distributed Denial of Service (DDoS) Attack Recognition in the Internet of Things (IoT). Electronics 2022 , 11 , 494. [ Google Scholar ] [ CrossRef ]
- Han, T.; Jan, S.R.U.; Tan, Z.; Usman, M.; Jan, M.A.; Khan, R.; Xu, Y. A comprehensive survey of security threats and their mitigation techniques for next-generation SDN controllers. Concurr. Comput. Pract. Exp. 2020 , 32 , e5300. [ Google Scholar ] [ CrossRef ]
- Butani, B.; Shukla, P.K.; Silakari, S. An exhaustive survey on physical node capture attack in WSN. Int. J. Comput. Appl. 2014 , 95 , 32–39. [ Google Scholar ] [ CrossRef ]
- Virmani, D.; Soni, A.; Chandel, S.; Hemrajani, M. Routing attacks in wireless sensor networks: A survey. arXiv 2014 , arXiv:1407.3987. [ Google Scholar ]
- Zhu, Q.; Clark, A.; Poovendran, R.; Başar, T. Deceptive routing games. In Proceedings of the 2012 IEEE 51st IEEE Conference on Decision and Control (CDC), Maui, HI, USA, 10–13 December 2012; pp. 2704–2711. [ Google Scholar ]
- Baviskar, B.R.; Patil, V.N. Black hole attacks mitigation and prevention in wireless sensor network. Int. J. Innov. Res. Adv. Eng. 2014 , 1 , 167–169. [ Google Scholar ]
- Majid, M.; Habib, S.; Javed, A.R.; Rizwan, M.; Srivastava, G.; Gadekallu, T.R.; Lin, J.C.W. Applications of wireless sensor networks and internet of things frameworks in the industry revolution 4.0: A systematic literature review. Sensors 2022 , 22 , 2087. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Wadii, J.; Rim, H.; Ridha, B. Detecting and preventing Sybil attacks in wireless sensor networks. In Proceedings of the 2019 IEEE 19th Mediterranean Microwave Symposium (MMS), Hammamet, Tunisia, 31 October–2 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [ Google Scholar ]
- Teng, Z.; Du, C.; Li, M.; Zhang, H.; Zhu, W. A Wormhole Attack Detection Algorithm Integrated with the Node Trust Optimization Model in WSNs. IEEE Sens. J. 2022 , 22 , 7361–7370. [ Google Scholar ] [ CrossRef ]
- Ouafaa, I.; Salah-ddine, K.; Jalal, L.; Said, E.H. Review on the attacks and security protocols for wireless sensor networks. Eur. J. Sci. Res. 2013 , 101 , 455. [ Google Scholar ]
- Srinivas, T.A.S.; Manivannan, S.S. Prevention of hello flood attack in IoT using combination of deep learning with improved rider optimization algorithm. Comput. Commun. 2020 , 163 , 162–175.1. [ Google Scholar ] [ CrossRef ]
- Dhakne, A.R.; Chatur, P.N. Detailed Survey on attacks in wireless sensor network. In Proceedings of the International Conference on Data Engineering and Communication Technology, Maharashtra, India, 15–16 December 2017; Springer: Singapore, 2017; pp. 319–331. [ Google Scholar ]
- Hussain, M.; Mehmood, A.; Khan, S.; Khan, M.A.; Iqbal, Z. Authentication techniques and methodologies used in wireless body area networks. J. Syst. Archit. 2019 , 101 , 101655. [ Google Scholar ] [ CrossRef ]
- Patil, R.A.; Dhanvijay, M.R.; Patil, S.M.; Dhanvijay, M.M. Comparative Analysis and Simulation of Routing Protocols for Wireless Body Area Networks. In Recent Advances in Manufacturing Modelling and Optimization ; Springer: Singapore, 2022; pp. 107–119. [ Google Scholar ]
- Alrajeh, N.A.; Khan, S.; Campbell, C.E.; Shams, B. Multi-channel framework for body area network in health monitoring. Appl. Math. Inf. Sci. 2013 , 7 , 1743. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Daia, A.S.A.; Ramadan, R.A.; Fayek, M.B.; AETiC, A. Sensor networks attacks classifications and mitigation. In Annals of Emerging Technologies in Computing (AETiC) ; International Association of Educators and Researchers: Paris, France, 2018; pp. 28–43. ISSN 2516-0281. [ Google Scholar ]
- Sen, J. A survey on wireless sensor network security. arXiv 2010 , arXiv:1011.1529. [ Google Scholar ]
- Bangash, Y.A.; Al-Salhi, Y.E. Security Issues and Challenges in Wireless Sensor Networks: A Survey. IAENG Int. J. Comput. Sci. 2017 , 44 , 94–108. [ Google Scholar ]
- Keerthika, M.; Shanmugapriya, D. Wireless Sensor Networks: Active and Passive attacks Vulnerabilities and Countermeasures. Glob. Transit. Proc. 2021 , 2 , 362–367. [ Google Scholar ] [ CrossRef ]
- Wahid, A.; Kumar, P. A survey on attacks, challenges and security mechanisms in wireless sensor network. Int. J. Innov. Res. Sci. Technol. 2015 , 1 , 189–196. [ Google Scholar ]
- Shi, E.; Perrig, A. Designing secure sensor networks. IEEE Wirel. Commun. 2004 , 11 , 38–43. [ Google Scholar ]
- Wang, X.; Gu, W.; Chellappan, S.; Schosek, K.; Xuan, D. Lifetime optimization of sensor networks under physical attacks. In Proceedings of the IEEE International Conference on Communications, ICC 2005, Seoul, Korea, 16–20 May 2005; IEEE: Piscataway, NJ, USA, 2005; Volume 5, pp. 3295–3301. [ Google Scholar ]
- Shin, I.; Cho, M. On Localized Countermeasure against reactive jamming attacks in smart grid wireless mesh networks. Appl. Sci. 2018 , 8 , 2340. [ Google Scholar ] [ CrossRef ]
- Jouini, O.; Sethom, K. Physical Layer Security Proposal for Wireless Body Area Networks. In Proceedings of the 2020 IEEE 5th Middle East and Africa Conference on Biomedical Engineering (MECBME), Amman, Jordan, 27–29 October 2020; pp. 1–5. [ Google Scholar ]
- Ahnn, J.H.; Potkonjak, M. Toward energy-efficient and distributed mobile health monitoring using parallel offloading. In Proceedings of the 2013 35th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), Osaka, Japan, 3–7 July 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 7257–7261. [ Google Scholar ]
- Bhanumathi, V.; Sangeetha, C.P. A guide for the selection of routing protocols in WBAN for healthcare applications. Hum.-Cent. Comput. Inf. Sci. 2017 , 7 , 24. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Jiang, Q.; Ma, J.; Ma, Z.; Li, G. A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 2013 , 37 , 9987. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Kumari, S.; Khan, M.K.; Kumar, R. Cryptanalysis and improvement of ‘a privacy enhanced scheme for telecare medical information systems’. J. Med. Syst. 2013 , 37 , 9952. [ Google Scholar ] [ CrossRef ]
- Rahman, H.U.; Ghani, A.; Khan, I.; Ahmad, N.; Vimal, S.; Bilal, M. Improving network efficiency in wireless body area networks using dual forwarder selection technique. Pers. Ubiquitous Comput. 2022 , 26 , 11–24. [ Google Scholar ] [ CrossRef ]
- Javaid, N.; Abbas, Z.; Fareed, M.S.; Khan, Z.A.; Alrajeh, N. M-ATTEMPT: A new energy-efficient routing protocol for wireless body area sensor networks. Procedia Comput. Sci. 2013 , 19 , 224–231. [ Google Scholar ] [ CrossRef ] [ Green Version ]
- Selem, E.; Fatehy, M.; Abd El-Kader, S.M. mobthe (mobile temperature heterogeneity energy) aware routing protocol for wban iot health application. IEEE Access 2021 , 9 , 18692–18705. [ Google Scholar ] [ CrossRef ]
- Renu, B. An Energy Efficient Routing protocol in Wireless Body Area Networks. Sci. Eng. Res. J. 2014 , 2 , 101–106. [ Google Scholar ]
- Afridi, A.; Javaid, N.; Jamil, S.; Akbar, M.; Khan, Z.A.; Qasim, U. Heat: Horizontal moveable energy-efficient adaptive threshold-based routing protocol for wireless body area networks. In Proceedings of the 2014 28th International Conference on Advanced Information Networking and Applications Workshops, Victoria, BC, Canada, 13–16 May 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 474–478. [ Google Scholar ]
- Udoh, E.; Getov, V. Performance analysis of denial-of-sleep attack-prone MAC protocols in wireless sensor networks. In Proceedings of the 2018 UKSim-AMSS 20th International Conference on Computer Modelling and Simulation (UKSim), Cambridge, UK, 27–29 March 2018; pp. 151–156. [ Google Scholar ]
- Moudni, H.; Er-rouidi, M.; Mouncif, H.; El Hadadi, B. Black hole attack detection using fuzzy based intrusion detection systems in MANET. Procedia Comput. Sci. 2019 , 151 , 1176–1181. [ Google Scholar ] [ CrossRef ]
- Boubiche, D.E.; Bilami, A.; Athmani, S. A Cross Layer Energy Efficient Security Mechanism for Denial of Sleep Attacks on Wireless Sensor Network. In Proceedings of the International Conference on Networked Digital Technologies, Dubai, United Arab Emirates, 24–26 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 151–164. [ Google Scholar ]
- Bagci, H.; Yazici, A. An energy aware fuzzy unequal clustering algorithm for wireless sensor networks. In Proceedings of the International Conference on Fuzzy Systems, Barcelona, Spain, 18–23 July 2010; pp. 1–8. [ Google Scholar ]
| Sensor | Description |
|---|---|
| ECG | The heart’s electrical activity |
| Blood flow | Measurement of accelerating forces in three-dimensional space of the body |
| Blood pressure | The force applied by the circulation of blood on the walls of the blood vessels |
| Body temperature | An indicator of the body’s ability to create and release heat |
| Respiration rate | Number of inhale and exhale movements per unit time |
| Oxygen level | Indicates the oxygen that is flowing in the patient’s blood |
| Heart rate | The frequency of the cardiac cycle |
| Blood sugar | Measures the amount of sugar (type, source, energy) in the blood |
| Muscle signal | The electrical activity of skeletal muscles (nervous, muscular system) |
| Electroencephalography | Measures automatic brain activity and other brain capacities |
| Challenges | Challenges in WBAN |
|---|---|
| Range | The WBAN range is limited, a few meters away from the body. Hence, reliable wireless communication is performed inside or close to the human body [ ]. |
| Energy consumption | WBAN requires constant energy to work properly, which necessitates a constant power supply [ ]. |
| Security | Due to the low power supply, it is difficult to add complex security mechanisms [ ]. |
| Service quality | One of the most important challenges in WBAN is to improve service quality [ ]. |
| Placement | It is difficult to put many nodes in a limited space [ ]. |
| Subject of Comparison | Wireless Sensor Networks | Wireless Body Sensor Network |
|---|---|---|
| Sensor node number | Many nodes in a wide range | Fewer than 10 nodes in a human body |
| Topology | Hybrid | Star |
| Sensor node type | Often homogeneous | Heterogeneous |
| Nodes’ physical properties | Without special restrictions | Tiny, light, wearable, or implantable |
| Energy supply sources | Limited | Very limited |
| Energy efficacy | Requires high efficiency | Requires very high efficiency |
| Security | Unrestricted security | Patients’ data requires high security |
| Communication | Less sensitive to service quality | Requires service quality |
| Example of node | MicaZ. IMote2 | Sensium |
| Issue | Papers | Method | |
|---|---|---|---|
| 1 | Cryptography | Hybrid encryption algorithm in wireless body area networks (WBANs) | This paper introduced a new concept, the hybrid encryption algorithm (HEA), which is suitable for ad hoc networks as well as wired networks. This algorithm not only considers data security, but also considers various limitations of sensor networks such as battery power, bandwidth, limited processing capability, and dynamic topology [ ]. |
| 2 | Key management | Trust key management scheme for wireless body area networks | In this paper, the authors presented an approach that uses physiological signals (electrocardiograms (ECGs)) to address security issues in the WBAN: a trusted key management scheme for the body area wireless network. This approach manages the production and distribution of symmetric cryptographic keys to the sensors of a WBAN (using an ECG signal) and protects privacy [ ]. |
| 3 | Secure routing | Secure routing of WBAN with monarchy butterfly optimization | Transfer of healthcare data was centralized in this paper. The WBAN is a mobile ad hoc network (MANET) used to transmit healthcare data. Efficient parameters for secure routing in the WBAN are specified and then optimized simultaneously. Secure routing in the WBAN is modeled as an optimization problem. Because the secure routing parameters are individual and the WBAN structure is dynamic, the optimization is performed simultaneously. Multi-objective optimization algorithms can optimize multivariate simultaneously. Monarchy butterfly optimization was used as a new and powerful multi-objective optimization algorithm in this paper [ ]. |
| 4 | Trust management | Naïve Bayes-based trust management model for wireless body area networks | In this paper, the authors proposed a trust management model based on the naïve Bayes classifier to classify a sensor node as trustworthy or malicious. On the basis of the classification, the trusted node selects a trusted node for data exchange. The authors trained the proposed model in MATLAB, and the experimental results showed that the proposed model can successfully classify a sensor node as malicious or reliable [ ]. |
| Node No. | X Coordinate (CM) | Y Coordinate (CM) |
|---|---|---|
| 1 | 40 | 90 |
| 2 | 60 | 90 |
| 3 | 50 | 60 |
| 4 | 50 | 60 |
| 5 | 50 | 30 |
| 6 | 50 | 30 |
| 7 | 50 | 08 |
| 8 | 50 | 08 |
| Distance to Base | Residual Energy | Competition Radius |
|---|---|---|
| Close | Low | Very small |
| Close | Medium | Small |
| Close | High | Rather small |
| Medium | Low | Medium small |
| Medium | Medium | Medium |
| Medium | High | Medium large |
| Far | Low | Rather large |
| Far | Medium | Large |
| Far | High | Very large |
| MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
Share and Cite
Yaghoubi, M.; Ahmed, K.; Miao, Y. Wireless Body Area Network (WBAN): A Survey on Architecture, Technologies, Energy Consumption, and Security Challenges. J. Sens. Actuator Netw. 2022 , 11 , 67. https://doi.org/10.3390/jsan11040067
Yaghoubi M, Ahmed K, Miao Y. Wireless Body Area Network (WBAN): A Survey on Architecture, Technologies, Energy Consumption, and Security Challenges. Journal of Sensor and Actuator Networks . 2022; 11(4):67. https://doi.org/10.3390/jsan11040067
Yaghoubi, Mohammad, Khandakar Ahmed, and Yuan Miao. 2022. "Wireless Body Area Network (WBAN): A Survey on Architecture, Technologies, Energy Consumption, and Security Challenges" Journal of Sensor and Actuator Networks 11, no. 4: 67. https://doi.org/10.3390/jsan11040067
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
- Login To RMS System
- About JETIR URP
- About All Approval and Licence
- Conference/Special Issue Proposal
- Book and Dissertation/Thesis Publication
- How start New Journal & Software
- Best Papers Award
- Mission and Vision
- Reviewer Board
- Join JETIR URP
- Call For Paper
- Research Areas
- Publication Guidelines
- Sample Paper Format
- Submit Paper Online
- Processing Charges
- Hard Copy and DOI Charges
- Check Your Paper Status
- Current Issue
- Past Issues
- Special Issues
- Conference Proposal
- Recent Conference
- Published Thesis
Contact Us Click Here
Whatsapp contact click here, published in:.
Volume 7 Issue 3 March-2020 eISSN: 2349-5162
UGC and ISSN approved 7.95 impact factor UGC Approved Journal no 63975
Unique identifier.
Published Paper ID: JETIR2003277
Registration ID: 230080
Page Number
Post-publication.
- Downlaod eCertificate, Confirmation Letter
- editor board member
- JETIR front page
- Journal Back Page
- UGC Approval 14 June W.e.f of CARE List UGC Approved Journal no 63975
Share This Article
Important links:.
- Call for Paper
- Submit Manuscript online

- Mr. Aniruddha P. Kshirsagar
- Mr. Gopal R. Chandangole
- Mr. Pravin Suryakant Patil
- Mr. Pradip Nanasaheb Shendage
- Ms. Sonal Avinash Kadav
Cite This Article
2349-5162 | Impact Factor 7.95 Calculate by Google Scholar An International Scholarly Open Access Journal, Peer-Reviewed, Refereed Journal Impact Factor 7.95 Calculate by Google Scholar and Semantic Scholar | AI-Powered Research Tool, Multidisciplinary, Monthly, Multilanguage Journal Indexing in All Major Database & Metadata, Citation Generator
Publication Details
Download paper / preview article.
Download Paper
Preview this article, download pdf, print this page.
Impact Factor:
Impact factor calculation click here current call for paper, call for paper cilck here for more info important links:.
| --> |
|
|
|
- Follow Us on
- Developed by JETIR
- DOI: 10.15623/IJRET.2015.0401032
- Corpus ID: 62454932
NETWORKING-HUMAN AREA NETWORK
- Tehseen Bano Mohd Anis , Subha Subramaniam
- Published 25 January 2015
- Computer Science
- International Journal of Research in Engineering and Technology
Figures from this paper

13 Citations
A study on networks and comparison of wired, wireless and optical networks, research of the calculation scheme for the brake lever transmission and construction of the load model for the brake pads of freight cars, force characteristics analysis for linear machine with dc field excitations, the results of brake tests of the dpkr-3 diesel train, determination of parameters of abnormal wear of brake pads of freight cars, determination of forces in the elements of the brake rigging of bogies of freight cars, identification of the conditions of a mine locomotive brake system as well as its functional and morphological model with the stressed closed kinematic circuit, climatic chamber testing of innovative brake system for rolling stock, analytical and experimental investigation of composite pads created by using coke dust against the fading problem in railway vehicles, determination of the thermal stress state for the composite brake pad of a wagon at operational loads, 11 references, human-area networking technology as a universal interface, a comparative study of wireless protocols: bluetooth, uwb, zigbee, and wi-fi, a near-field-sensing transceiver for intra-body communication based on the electro-optic effect, research based on osi model, osi reference model - the iso model of architecture for open systems interconnection, key concepts, personal area networks: near-field intrabody communication, related papers.
Showing 1 through 3 of 0 Related Papers
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

NETWORKING-HUMAN AREA NETWORK
This paper grabs the detail study on information about Computer Networking. Two distinct electronic media communicating between themselves and forming a group within its area can be termed as Computer Networking. In the modern globe, communication is the most essential part of living creatures and the need of communication, from one end of the world to the other end, gave rise to the system of Networking. There are various types of forming of the network. Networking and its different types and uses will be studied throughout the paper. Further part of the paper will deal in detail on the topic of networking devices that forms the base of a successful network. We propose a methodology to use human body as a transmitting medium to pass data in a Human Area Network (HAN).
Related Papers
eSAT Journals
Today's world has become very advanced with smart appliances and devices like laptops, tablets, televisions. smart phones with different features and their usage has been enormously increasing in our day-today life. The technology advancement in Digital Electronics and Micro Electro Mechanical Systems. In this scenario the most important role is played by Wireless Sensor Networks and its development and usage in heterogeneous fields and several contexts. the home automation field and process control systems and health control systems widely uses wireless sensor networks. Moreover with WSN we can monitor environments and its conditions also. We are designing a protocol to monitor the environmental temperature and humidity at different conditions. The architecture is simple to construct and ease to implement and also has an advantage of low power consumption. The aim of our paper to describe and show how to create a simple protocol for environment monitoring using a wireless development kit. we are using advanced technology of crossbow motes and NESC Language Programming.
Editor IJRET
The demand of wireless system in home is increasing day by day due to its cost and easy placement and also it is easy to connect with our computer or phone [1]. This project demonstrates about the control of home appliances wirelessly using computer and Zigbee wireless communication protocol. We can control the home appliance like refrigerator, fan, and air conditioner etc. by sending command through the computer. Input will be given from the computer through serial communication. By this technique we can also control all electrical appliances within a room in a building. We extent the concept of controlling the power supply for the devices at remote location at home or industry.
This paper presents the simulation and test result of a project for Wireless Data transmission through UART Port using ARM & RF Transceiver in license free band of frequencies 2.4GHz to 2.4835 GHz. It uses ARM7 and MRF24J40 for Wireless Data transmission through UART Port for short-range up to 500 meters. The speed of data transmission is of 250 kbps. The Output power of source module for 500 meters is 0 dBm to 22 dBm. The Receiver sensitivity of the receiver module is-95dBm
International Journal IJRITCC
This paper proposes an integrated approach towards Transmission of moderate Quality of Voice Data through Zigbee. Here Zigbee technology is used because it provides seamless(smooth, continuous with no interruption) addressable connectivity (IP based), simple and low cost wireless communication and networking solution for low data rate and for those applications which consumes low power. These prototypes have complex/large circuitry and because of this these become very expensive. In near future everything will be network connected, so we need a IP based voice enabled platform for communication purpose and with high performance for defense, physically handicapped. At present there are wireless embedded devices but not voice enabled (remote controlled are there), if so then there are not centralized server. Because of this, the costs of these types of devices are very high. Main objective of this thesis is to develop a communication system in WSN over Zigbee between two nodes and encryption algorithm at transmitter side for security of data in the air(medium), and also to reduce equipment cost as well as communication cost with some sort of compromising the data, that can work even with low power micro-controller.
Present group of mobile systems afford access to a wide range of services and permit mobile users to join irrespective of their environmental position and their roaming features. Due to growing the number of mobile users, global connectivity and the small size of cells, one of the most serious matters regarding these networks is position management. In current years, several schemes have been proposed to improve the performance of the location management. In the Proposed work a predefined geographical area is considered. For Every base station and it should maintain geographical data base such as blocking area. The base station should warn the mobile station when it moves towards the blocking area. The different speed mobile stations are safeguarded from dropping out. The high speed nodes are warned many a times before it enters the blocking area. This is carried out to reduce call dropping and encourage complete utilization of resources hence we can improve the services provided by the service provider.
Spatially distributed Wireless Sensor Networks (WSN) comprising low-cost components (sensors, Microcontrollers, wireless communication devices) provide a way to measure several quantitative variables of nature and the human environment (air, temperature, soil temperature, precipitation and water quality). Owing to the increased human intervention in nature, there is a rise in unpredictability of weather and natural environment. This causes human induced disasters such as long dry periods, flash floods,subsequent landslides, heat-island effect, sea-level rise, beach erosion. Very often the effects of disasters natural or manmade are regional and early warning infrastructure may not be sufficient. In this paper we address disaster preparedness and prevention by utilizing low cost WSNs to monitor the region and designingfreeAndroid cloud application to instantly notify users, an occurrence of a disaster. The deployment of the WSN is done using various interconnected nodes across the region. Each node consists of a low cost Arduino Microcontroller, Xbee radio communication module and sensors which measure data substantial to detect a disaster. Each node collects data and sends through line of sight to a central station. This station is a server which collects and sends the data to the cloud where it is stored and inspected for detecting a dangerous situation. The cloud also maintains the sensor data in an online database periodically. We will demonstrate a smartphone application which communicates with the cloud so that notifications are sent in real time when a disaster is detected to alert the users located within the WSN area, helping in early evacuation, finding nearby safety shelters etc. We show that by establishing a synergy between Smartphone and reliable modern sensors like ground motion sensors(for early warning of earthquakes), soil moisture sensors (for early warning of drought), flow sensors (for early warning offloods) in WSN will improve the quality of life by ensuring safety against disasters.
There is a rapid development in sensor devices as well as increase in communication range with various low power wireless radio transmitter and receiver using wireless mesh network. Wireless mesh networking is useful to collect the information from different sensors that are widely distributed over a large area. In this survey, we mainly focus on open source module that is shown by various authors. For this purpose many authors use Zigbee module for the development of sensor systems with capability of mesh networking. In this survey, we mainly focus on wireless mesh networking, for that we studied different wireless sensors to transmit and receive the data from them and can monitor the output at regular interval on our screen. WSN consist of different sensors that are distributed with the capabilities of computing, processing and communication can continuouslysense the data in terms of packets and transmit that data at regular interval. They design such model in which integrates the various functions such as type of network, data routing and scheduled of transmission data. Also design wireless mesh network structure for various monitoring application such as industrial, agricultural, medical and so many with a good average packet delivery ratio upto 93%. This proposed system has the advantage of low cost combined with high reliable information of transmitter without complications of wireless mesh networking. And finally we conclude from that study of WMN, the range of communication can be increased by Using Pro-Zigbee module (up to 1.6Km) as well as we can monitor that, if one of the node is fail to transmit a data ,then their data will automatically stored in neighboring node as backup.
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Kamini Jaswal
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- Open access
- Published: 06 August 2024
Factors influencing the research impact in cancer research: a collaboration and knowledge network analysis
- Shuang Liao ORCID: orcid.org/0000-0002-1016-6149 1 ,
- Christopher Lavender 1 &
- Huiwen Zhai 1
Health Research Policy and Systems volume 22 , Article number: 96 ( 2024 ) Cite this article
94 Accesses
Metrics details
Cancer is a major public health challenge globally. However, little is known about the evolution patterns of cancer research communities and the influencing factors of their research capacity and impact, which is affected not only by the social networks established through research collaboration but also by the knowledge networks in which the research projects are embedded.
The focus of this study was narrowed to a specific topic – 'synthetic lethality’ – in cancer research. This field has seen vibrant growth and multidisciplinary collaboration in the past decade. Multi-level collaboration and knowledge networks were established and analysed on the basis of bibliometric data from ‘synthetic lethality’-related cancer research papers. Negative binomial regression analysis was further applied to explore how node attributes within these networks, along with other potential factors, affected paper citations, which are widely accepted as proxies for assessing research capacity and impact.
Our study revealed that the synthetic lethality-based cancer research field is characterized by a knowledge network with high integration, alongside a collaboration network exhibiting some clustering. We found significant correlations between certain factors and citation counts. Specifically, a leading status within the nation-level international collaboration network and industry involvement were both found to be significantly related to higher citations. In the individual-level collaboration networks, lead authors’ degree centrality has an inverted U-shaped relationship with citations, while their structural holes exhibit a positive and significant effect. Within the knowledge network, however, only measures of structural holes have a positive and significant effect on the number of citations.
Conclusions
To enhance cancer research capacity and impact, non-leading countries should take measures to enhance their international collaboration status. For early career researchers, increasing the number of collaborators seems to be more effective. University–industry cooperation should also be encouraged, enhancing the integration of human resources, technology, funding, research platforms and medical resources. Insights gained through this study also provide recommendations to researchers or administrators in designing future research directions from a knowledge network perspective. Focusing on unique issues especially interdisciplinary fields will improve output and influence their research work.
Peer Review reports
Cancer is a major public health challenge globally [ 1 ]. According to WHO in 2019, cancer is estimated to be one of the top two leading causes of death in 112 out of 183 countries. To address this challenge, plenty of efforts have been made to accelerate progress and output in various field of cancer research, including cancer aetiology, vaccines and anti-cancer drug development, precision cancer medicine and treatment strategy innovations. However, little is known about the evolution patterns of cancer research communities and the influencing factors of their research capacity and impact, which is vital for establishing the reputation of cancer researchers and advancing their careers.
Although tumour mutational analysis has largely been exhausted for the identification of conventionally druggable targets, functional genomic screening based on synthetic lethality provides new avenues for discovering drug targets that were previously considered undruggable owing to their molecular structure or resulting functional loss [ 2 ]. In this study, we sought to reveal the factors that influence cancer research capacity, impact and the underlying logic through social network (research collaboration network) and knowledge network analysis based on synthetic lethality-related cancer research papers.
We focused our study in this area for several reasons. First, recent advances, such as CRISPR-based gene editing promoted the systematic screening for synthetic lethality-based cancer drug targets, resulting in unprecedented growth in this area. Second, an increasing number of researchers are contributing a wealth of knowledge elements in this area, along with the emergence of research achievements with high clinical value, such as the clinical use of PARP inhibitors in patients with BRCA mutant ovarian cancer. Third, there is a high level of collaboration in this field, including institutional, international and collaborations between academic institutions and industries, such as big pharmaceutical companies.
In the era of globalization, collaboration is the key to success in the fight against cancer, especially in the field of cancer research. Collaboration has been known to have an important influence in research capacity, output and impact [ 3 ]. Social networks, such as research collaboration networks, reflect the relationships and interactions among different levels of agents within the network – individuals, organizations or countries [ 4 ]. Their collaborative relationships serve as social capital [ 5 ]. According Li et al. [ 4 ], betweenness centrality, one of the structural social capital indicators, plays the most important role in leveraging resources in a co-authorship network. The positions of agents in the research collaboration network are vital for gaining and exchanging resources, ideas, knowledge and information from collaborating partners, thereby affecting their performance and innovative outputs [ 6 ]. Social network analysis is widely used to reveal the pattern of research collaboration and its impact on research citations.
Besides social capital, knowledge is also a vital resource for individuals and organizations in establishing competitiveness during innovation [ 7 ]. In addition to social networks, individuals and research organizations are also embedded in knowledge networks formed by the coupling of knowledge elements [ 8 ]. Formed through the combination of knowledge elements during the innovation process, knowledge networks serve as conduits for knowledge flow and influence future searches, the recombination of knowledge elements and, ultimately, the outcomes of innovation [ 9 ]. Therefore, the positions of individuals’ or organizations’ knowledge elements within the knowledge network will also impact their innovation outcomes.
In the fields of nano-energy and wind energy, studies have been conducted on the structural properties of both collaborative and knowledge networks, confirming the impact of node attributes in both networks on innovation performance, such as paper citation counts and patent counts [ 8 , 10 ]. To the best of our knowledge, no studies have been conducted on the structural properties of both social and knowledge networks as well as their impact on research capacity and performance in the field of cancer research.
In our study, negative binomial regression analysis was applied to explore how collaboration and knowledge networks, together with other potential factors, affected the research capacity and impact in the field of ‘synthetic lethality’-related cancer research. Regression model analysis was performed at the paper level, with citation number as the dependent variable. As greater research capacity and impact naturally leads to increased publication citations, citation-based measures are widely accepted as proxies for assessing the research capacity and impact of academic researchers [ 10 , 11 ]. The positive influence of international collaboration on the research impact of publications has been documented in former studies; although, the effects may vary across disciplines and countries [ 12 , 13 ]. We assume that the status of papers’ corresponding countries within the international collaboration network may also influence their research impact in general, as cooperation between scholars from specific countries may exhibit some clustering in the field of cancer research. Therefore, instead of simply categorizing the papers into ‘with’ or ‘without’ international collaboration, we further included the ‘country level international collaboration status’ as a potential influencing factor, based on metrics from country level collaboration networks.
In the preliminary analysis, we also established institutional level collaboration networks too, but they failed to reveal any significant correlation between their node attributes and paper citations. Then, we analysed the impact of institution types on citations and found that the existence of a company within the affiliation list was significantly related to citations, with P < 0.01. Therefore, industry involvement was further included in our final model.
Node attributes in both social and knowledge networks, as well as other potential factors, including journal impact factors (IF), country level international collaboration status, publication duration and industry involvement, were taken as the independent variables. Some of these factors have been proposed in previous studies as relevant to the citation impact of papers [ 12 , 14 , 15 ].
In the collaboration network, degree centrality indicated the number of direct ties (partners) one researcher had. A structural hole was originally considered to be a lack of linkage between any pair of nodes in the network [ 16 ]. Specifically, an author occupies structural holes in the collaboration/social network if they connect with other collaborators who are not connected themselves [ 17 ]. Therefore, structural hole values in the co-authoring networks in this study illustrate the degree to which an author’s partners are disconnected from each other, indicating non-redundant and efficient access to information for the focal author. Both metrics reflect an author’s degree of prestige among their collaboration partners for efficient access of information, knowledge and resources [ 18 ]. We reasoned that the average node attributes of a paper’s ‘research guarantors’ within the collaboration network would affect their research capacity and impact, making it an important factor for regression analysis.
Similarly, in the knowledge network, degree centrality indicates the number of direct linkages of a certain knowledge element, while structural holes represent the degree of disconnectedness among elements linked to a focal knowledge element, indicating information control advantages of the latter as researchers who study these uncombined elements are likely to use information in the focal element [ 19 ]. Besides, surprising combinations of research content from distant disciplines are also revealed as related to impactful research [ 20 ]. Differences in node attributes among knowledge elements of a certain paper reflect the author’s choice of research topic. A project with a frontier, multi-disciplinary research topic might have a higher measure in structural holes, while an ordinary and popular research topic might increase the measure of degree centrality.
For both networks, only local metrics such as degree centrality and structural holes were included. Global-level centrality metrics, such as closeness and betweenness centrality, were not considered to avoid a possible suppressor effect, as revealed in previous studies [ 4 , 21 ].
Data collection
The bibliographic data used in this study were extracted in March 2023 from Web of Science (WoS) and Journal Citation Report (JCR) databases. The following search terms were used in the WoS Core Collection to retrieve records of synthetic lethality-based cancer research papers:
1 : (((((((TS = (cancer*)) OR TS = (tumor*)) OR TS = (tumour*)) OR TS = (carcinoma*)) OR TS = (neoplasm*)) OR TS = (Glioblastoma)) OR TS = (Melanoma)) OR TS = (Adenocarcinoma).
2 : TS = ("Synthetic lethal*").
3 : #2 AND #1
4 : TS = ("correction:").
5 : (#3) NOT #4
Only documents classified as ‘articles’ were included. A total of 2074 papers were collected from WoS, along with the title, journal, abstract, authors and their affiliations, keywords, publication year, citation count and other information. The 5-year impact factors of the journals were downloaded from the Journal Citation Report (JCR) database. For all the journals listed in the dataset, the 5-year impact factors for the corresponding year were added manually.
Measurements
Collaboration and knowledge networks were created on the basis of 5-year moving windows (2009–2013, 2010–2014, 2011–2015, 2012–2016, 2013–2017), following previous approaches [ 10 , 22 ]. For example, if a paper was published in 2014, the metrics of its author and keywords were measured within the collaboration and knowledge networks for the years 2010–2014.
Dependent variables
The dependent variable was the number of citations for each paper in the sample, which was directly retrieved from the WoS dataset.
Independent variables
The Independent variables included degree centrality and structural holes in the collaboration and knowledge networks.
Construction of the collaboration and knowledge networks
In this study, the collaborative and knowledge networks were constructed on the basis of paper-level data following previous approaches [ 10 ].
The collaboration networks were established on the basis of co-author data of the papers included in each 5-year time frame, with authors serving as nodes and co-authorship experiences as the ties. Authors who co-published a paper were considered collaboration partners. Sci2 software was used for data cleaning and constructing the collaboration (co-author) network [ 23 ]. Manual unification of author names was conducted using the merge table function of Sci2 before the final construction of the network.
In addition to the individual level, a national-level international collaboration network was further constructed on the basis of bibliometric data to classify different countries based on their node attributes within the network.
Based on the papers included in each 5-year time frame, co-keyword networks were established in the study as the knowledge networks, with article keywords suggested by Web of Science (ISI keywords) considered as the knowledge elements and their co-appearance in the same paper served as a tie between them. Manual unification of keywords, including synonyms, singular and plural forms, abbreviations and so on, was performed on the extracted file before the final network construction.
Measurement of degree centrality and structural holes
For both the collaboration and knowledge networks, the measurement of degree centrality and structural holes followed previous approaches as adopted by Guan et al. [ 10 ]. The normalized degree centrality proposed by Freeman [ 24 ] employed in previous studies [ 10 , 21 , 25 ] was utilized to account for the size effect of different networks.
For the calculation of structural holes, we used Burt’s constraint measure to determine the network constraint C i . This measure indicates how strongly i can be constrained by its neighbours (Burt, 2009, 2004) [ 19 , 26 ]. Subsequently, the network constraint measure ( C i ) was subtracted from two to indicate the control advantage of each node in spanning structural holes, as based on previous studies [ 10 , 25 ]. Both metrics, degree centrality and structural holes, were calculated using Pajek software [ 27 ].
In this formula, i is the focal element, p ij indicates the proportion at which an element j accounts for element i ’s contacts. For instance, if i connects with j and five other elements, then p ij is 1/6. Additionally, k is the third element which connects with both i and j . Therefore, the focal element i would have lower p ij values if it connects with more elements, thereby being less constrained.
Aggregating the measures into paper level
Since this study was conducted at the paper level, we needed to aggregate the degree centrality and structural holes values for each publication. For the knowledge network, the values of degree centrality and structural holes of all the keywords of a specific paper were averaged to obtain its paper-level measure. However, in the collaboration network, two different approaches were initially adopted for data aggregation. The first approach, termed the ‘lead author’ approach, entailed averaging only the measures of the first author and the corresponding/co-corresponding authors for each paper. The other approach, termed the ‘all-author’ approach, involved averaging the measures of all authors for the regression analysis. The ‘lead author’ approach is based on the academic consensus regarding the order of authorship in the field of biomedical research and the concept of a ‘research guarantor’. We assume that the first and corresponding authors contribute the most to these papers, and therefore, their node attributes might be more relevant to the research impact of the publications than those of the other authors. A similar approach of allocating credits to corresponding authors, institutions or countries has also been adopted and proven to be useful in previous studies [ 28 , 29 , 30 ]. Regression results for the two models are compared in the results section of this article.
Control variables
The following variables were controlled for in the regression analysis: a journal’s 5-year impact factor, year since publication, industry involvement and status in international collaboration (for countries). Dummy variables were created for the last two variables.
To classify different countries according to their status in international collaboration, country-level collaboration networks were further created on the basis of co-author data from the papers included in each 5-year network. In these networks, countries served as nodes, and co-authorship experiences formed the ties. Degree centrality and structural holes were calculated for each country, using the same approaches adopted in individual networks.
In the preliminary analysis, no significant relationship was found between country level degree centrality/structural holes (both as continuous variables) and paper citations. This is unsurprising, as significant variations exist in the number of citations among papers from the same country. To improve statistical power, countries were subsequently ranked and classified into two categories. Leading countries were defined as those with structural holes ranked in the top 20%, while the remaining countries were categorized as non-leading countries. The 20% cutoff was selected to ensure the stability of relevant metric values for leading countries over time, as well as good discrimination power between the leading countries and others. When calculating the international collaboration status for each paper, only the corresponding country was considered Table 1 .
Structural characteristics and evolution patterns of collaboration and knowledge networks
The structural characteristics of the collaboration network and knowledge network in the synthetic lethality-based cancer research field are presented in Table 2 by time period and visualized in Fig. 1 and Fig. 2 , to illustrate the evolution pattern and parameter changes over time. Both networks are weighted, with edge attributes also presented in Table 2 .
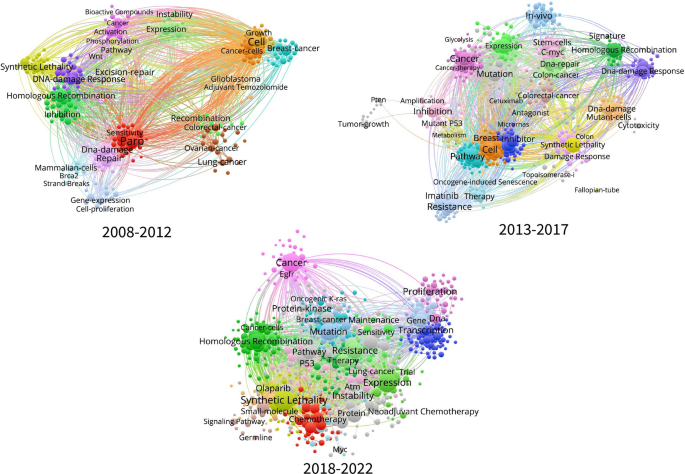
Evolution and pattern of the knowledge network in synthetic lethality-based cancer research papers (2008–2022). The main component of the knowledge network in synthetic lethality-based cancer research papers (2008–2022) are presented for each 5-year duration. The nodes represent keywords, which are further clustered according to relatedness. Nodes from the same cluster are presented in the same colour. The size of each node indicates the frequency of occurrence. Only items with a total link strength above 10 are included. VOSviewer was used for visualization [ 31 ]
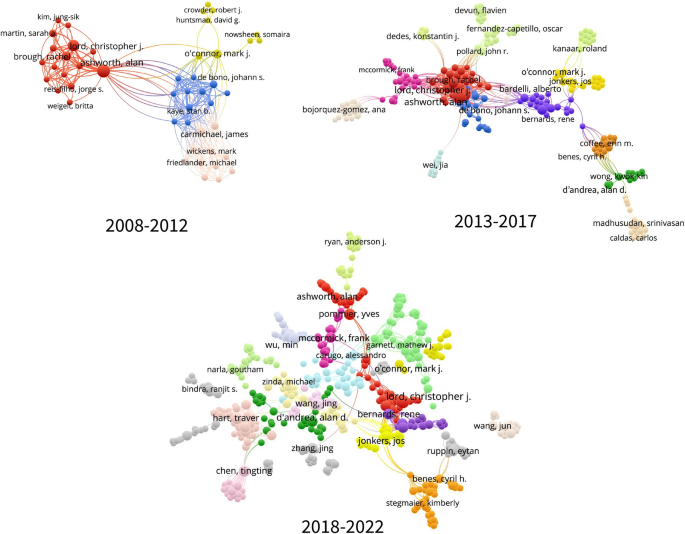
Evolution and pattern of the collaboration network in synthetic lethality-based cancer research papers (2008–2022). The main component of the collaboration network of authors in synthetic lethality-based cancer research papers (2008–2022) are presented for each 5-year duration. The nodes represent authors, who are further clustered according to relatedness. Nodes from the same cluster are presented in the same colour. The size of each node indicates the number of publications by the author, and the strongest collaboration links are represented by lines. Only the largest set of connected items (authors) is included. VOSviewer was used for visualization
In the knowledge network, a rapid increase in network size and edge number was observed in both period 2 and period 3 (as presented in Table 2 ), indicating fast growth and high integration of knowledge in this area. A decreasing trend was observed in clustering coefficients in both period 2 and period 3, revealing an evolution pattern of the knowledge network towards lower integration and clustering (as shown in Fig. 1 ), which may be due to the expansion of knowledge fields involved and the growing importance of interdisciplinary research.
For the collaboration network, period 2 and period 3 also saw a dramatic increase in network size and edge number, revealing fast growth of the co-authoring network. Despite a moderate increase in period 2, the typical number of co-authoring relationships (average degree) and frequency (mean weight) remained relatively stable across the three periods compared to network growth, resulting in a drop in network density from 0.009 to 0.002. High network clustering coefficients were observed in all three periods, with the highest in period 2 (0.948), confirming vigorous and tight research cooperation in this field, as shown in Fig. 2 .
When examining the country-level collaboration network (Fig. 3 ), the USA is undoubtedly at the centre of international cooperation, taking top priority. The most robust links are found between the USA and China, the USA and England, the USA and Germany and the USA and Canada, which align precisely with previous studies on global scientific collaboration networks [ 32 ]. European countries have also developed an important cluster within the network, with high density and integration, which is unsurprising considering their scientific advancements and the short geographic distances between them.
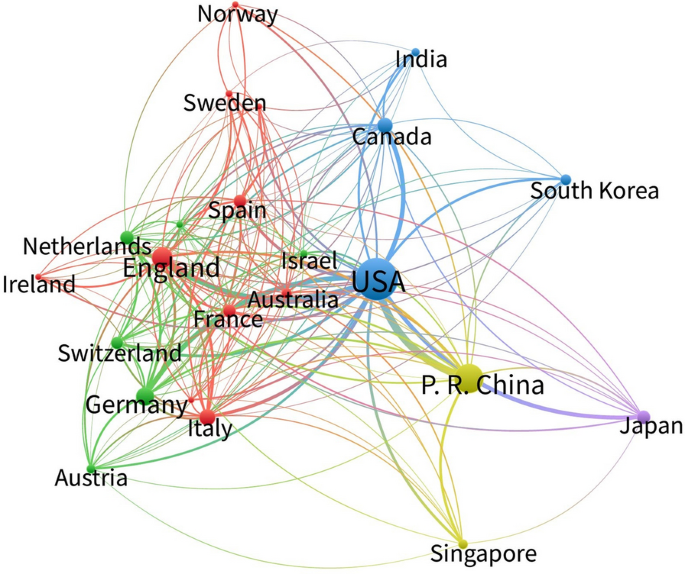
Main component of the collaboration network of countries in synthetic lethality-based cancer research papers (2018–2022). The nodes represent countries, and the size of each node indicates the number of publications from that country. Nodes from the same cluster are presented in the same colour. Only countries with a total link strength above 10 are included. VOSviewer was used for visualization
Regression analysis and results
Table 3 displays the descriptive statistics of the variables and their correlation data.
To address the issue of over-dispersion, a negative binomial regression model was used in this study for data analysis. VIF (variance inflation factor) values of all the variables were found to be below 2, indicating the absence of significant multicollinearity. Five regression models were constructed: model 1 includes only the control variables and models 2 and 3 incorporate the independent variables from the collaboration networks based on the lead author approach and the all-author approach, respectively. Models 4 and 5 encompass all the variables, with collaboration networks based on the lead author approach and the all-author approach, respectively. Table 4 presents the regression results for the number of citations for each paper.
We first compared the regression results between different aggregation approaches for collaboration network parameters, one based on lead author data (model 2 and model 4) and one on all author data (model 3 and model 5). The regression results based on ‘lead author’ and ‘all-author’ approaches are quite consistent regarding the influence of the author’s degree centrality on citations. However, a notable difference was observed in the coefficient significance for structural holes. In the lead author models, the author’s structural holes value is significantly related to the citation number, regardless of whether knowledge network parameters are included. However, no significant relationship was found between the author’s structural holes value and the citation number in either of the all-author models. We believe that the all-author aggregation method might have smoothed out the significant correlation between lead author structure holes and citation number. Therefore, we chose the lead author aggregation method over the all-author one for the final model (model 4).
As shown in model 2 and model 4, the coefficient for degree centrality in the collaboration network is positive and significant ( P < 0.05 in model 2, P < 0.1 in model 4). Conversely, the coefficient for (degree centrality in the collaboration network) 2 is negative at the significance level of P < 0.05 in both models. According to an analysis on this phenomenon in a previous study in the field of wind energy [ 10 ], this indicates that the average degree centrality of the lead authors in the collaboration network has an inverted U-shaped relationship with the number of citations for the paper. To assess the validity of this relationship, we set all other variables to their average values and presented the inverted U-shaped relationship between author degree centrality and citation number in Fig 4 , following a previous approach. Utilizing the delta method, we calculated the turning point to be 0.0418 (95% confidence interval [CI] 0.0211–0.0626), which falls within our normalized degree centrality data range of 0.0000–0.0743. Consequently, a moderate number of ties among the lead authors in a collaboration network could increase the paper’s citation count (the academic influence) to some extent, while degree centrality beyond a certain threshold can have a negative impact on citations.
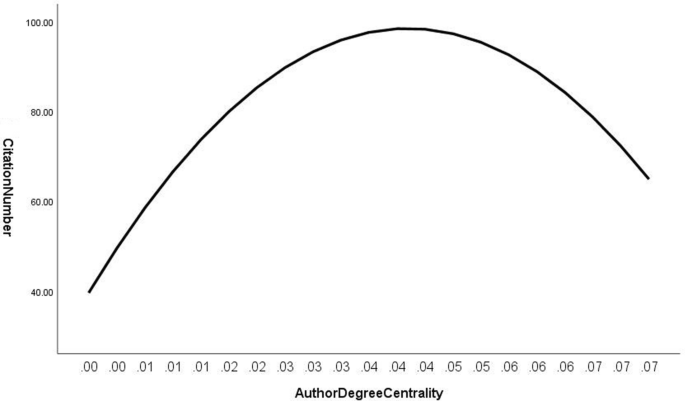
The relationship between author degree centrality and citation number
Furthermore, the coefficient for structural holes in the collaboration network is positive and significant (adjusted odds ratio 1.32, 95% CI 0.96–1.81; P = 0.09 in model 2 and adjusted odds ratio 1.32, 95% CI 0.97–1.81; P = 0.08 in model 4). This suggests that the average structural holes of the lead authors in the collaboration network are positively associated with the number of citations for the paper.
Unlike in the collaboration network, the coefficients for degree centrality in knowledge networks are negative and non-significant in model 4, suggesting that there is no significant relationship between a paper’s knowledge element’s average degree centrality in the knowledge network and its number of citations. However, positive and significant coefficients are found for structural holes in knowledge network in model 4 (adjusted odds ratio 4.37, 95% CI 1.28–14.96; P = 0.02 in model 4). This indicates that a paper’s knowledge element’s average structural holes in the knowledge network are positively related to its number of citations.
It is worth noting that the Akaike information criterion (AIC) for model 4 is the lowest among all models. Therefore, the addition of the independent variables based on the paper’s degree centrality and structural holes in both the collaboration and knowledge networks successfully improved the model.
All the control variables included in this study are significantly associated with the number of paper citations, indicating the important influence of journal reputation, citation duration, the international collaboration status of the corresponding country and collaboration with pharmaceutical companies.
It has been well-documented that academic collaboration in the form of co-authorship may influence research capacity and impact [ 33 ], but the extent varies across countries, research fields and even research topics [ 34 ]. To eliminate the potential influence of ‘hot’ or ‘cold’ research topics, this study narrowed its focus to a specific topic within the field of cancer research – synthetic lethality-based cancer research.
Regression model establishment
Based on the regression results, the inclusion of node attributes of lead authors in the collaboration network and knowledge elements in the knowledge network effectively improved the regression model. Therefore, we have demonstrated that centrality and structural holes in these two networks are highly influential factors for the research impact of synthetic lethality-based cancer research papers. Additionally, all of the control variables in the regression model are statistically significant. Aside from journal IF and publication year, which have long been recognized as vital factors affecting a paper’s citation count, this study also reveals a strong relationship between international collaboration status and industry involvement with paper citations.
Initially, no significant variance was observed between papers with or without international collaboration in the regression models (data not shown). We attribute this to the intricate nature of the relationship between international collaboration, specifically international co-authorship and cancer research impact, in terms of citation count, for different entities. At the national level, the proportion of internationally co-authored cancer research papers by a country may be influenced by factors such as its stage of scientific development, country size, economic development level, funding policies and medical resource availability [ 11 ].
More importantly, it is crucial to consider the different roles of the collaborating institutions/countries when analysing the impact of international collaboration, especially the role of the lead collaborators (research guarantors) [ 35 ]. We found that papers authored by leading countries (according to the corresponding country), which ranked high in structural holes ranking, not degree centrality, in the international collaboration network, exhibited significantly higher citation counts compared with others. Therefore, bridging structural holes can increase a country’s paper citation count. It is the status of a country within the cancer research network that matters, not the number of collaborators.
As shown in Fig 3 , in the field of synthetic lethality-based cancer research, the collaboration network at the country level exhibits a pattern with noticeable clustering. We speculate that leading countries prioritize obtaining non-redundant cancer research information, ideas and resources across these clusters, enhancing their overall research capacity and influence more effectively. Despite having some collaborators, non-leading countries may have limited access to resources and information beyond their own cluster due to barriers such as geographical distance, language difficulties or a lack of cooperation history. To improve overall research capacity and influence by enhancing positions in the cancer research network, governments should consider offering more international research fund supporting leadership in cancer research or taking a more active role in international health/cancer research organizations, such as the World Health Organization and the Union of International Cancer Control (UICC).
Moreover, the significant relationship between industry involvement and citations underscores the importance of integrating industry and academic researchers in cancer research. Since most companies involved in synthetic lethality-based cancer research are pharmaceutical or biotechnology companies, we conducted literature searches on university-industry collaborations in related fields.
Pharmaceutical involvement not only signifies the profound integration of human resources, knowledge, technology, funding, research platforms and medical resources but also serves as a robust predictor of the clinical experimentation of basic research findings [ 36 ]. In a study on university–industry collaborations within the Irish pharmaceutical industry, the significance of government funding was emphasized in motivating collaborations during the initiation phase, while the establishment of intellectual property (IP) agreements was identified as the impetus for knowledge sharing in the engagement phase [ 37 ]. This is supported by a survey of 105 university–industry collaborations within the US biotechnology industry, where researchers found that transparent IP policies enabled the formation of trust, which is vital for effective knowledge transfer and achieving success in university–industry collaborations [ 38 ]. To encourage university–industry cooperation in synthetic lethality-based cancer research, attention should be paid to the establishment of reasonable research policies and efficient processes, such as those for the establishment of intellectual property rights protection. Government investment is also crucial, with more national funds for university–industry led cooperation needed.
The relationship between lead authors’ average degree centrality in the collaboration network and paper citations
The observed inverted U-shaped relationship between the average degree centrality of lead authors in the collaboration network and the number of paper citations is consistent with previous research [ 10 ]. Central authors typically have numerous connections with others, enabling them priority in acquiring ideas, the latest information and resources, which can effectively promote their own research [ 39 ]. As indicated from the rising part of the inverted U-shaped curve before reaching the vertex, engaging in cancer research collaboration, whether in a leading or supporting role, enhances an author's academic research capacity, influence and reputation, ultimately contributing to increased paper citations.
However, when the inverted U-shaped curve reaches its peak, citations will start to decline as degree centrality increases. As in our study, if an author’s centrality exceeds a certain threshold, the surplus of information can overwhelm them, resulting in a decrease in the quality of knowledge, which, in turn, negatively impacts research output and influence. The above result again emphasizes the importance of encouraging cancer research collaboration, especially for young cancer researchers at an early stage of their careers.
The relationship between lead authors’ average structural holes in the collaboration network and paper citations
Based on the regression results, a positive relationship between the average structural holes of lead authors in the collaboration network and paper citation counts was found in both model 2 and model 4, although at a lower significant level compared with degree centrality. This suggests that by connecting with unique and diverse collaborators, central authors bridging structural holes can enhance the efficiency of their information acquisition, when conducting research on synthetic lethality-related cancer projects. Authors who bridge more structural holes have access to more non-redundant information and gain more control benefits [ 40 ], resulting in increased research capacity and impact and higher citation rates for their papers, as found in our study.
A significant difference was also observed between country and individual level collaboration networks. While degree centrality is the most important factor for individuals, the value of structural holes seems to be more influential at the country level. This reflects differences in the impact of social networks at different dimensions. At the macro level, the overall international collaboration status of a country is more important than the number of cooperating partners, while at the individual level, especially for young researchers, the number of collaborators directly determines the quality of resources and information obtained, thereby affecting the building of their research capabilities and the influence of research achievements.
The relationship between structural holes in the knowledge network and paper citations
This study revealed a positive relationship between the average structural holes of the knowledge elements in the knowledge network and paper citations, at the significance level of P < 0.05 in model 4. However, degree centrality showed no significant influence on citation counts. We posit that knowledge elements bridging rich structural holes in the knowledge network offer non-redundant information to cancer researchers who explore them. Additionally, they also create combinatorial opportunities between unconnected knowledge elements during the searching process, ultimately increasing citations from researchers across various disciplines. Therefore, elements bridging structural holes enjoy advantages in controlling the flow of knowledge during searches, thereby enhancing the citation opportunities for the papers involved. The above results provide suggestions for the selection of cancer research directions and keywords. Focusing on unique issues that connect with diverse information in cancer, especially interdisciplinary fields, will improve citations and the influence of research work.
These finding aligns with a previous study that analysed the influence of collaboration and knowledge network structures on organizational exploratory innovations in the field of nano-energy [ 8 ]. Although the two studies differ in terms of research field, level of analysis, variables and regression model design, they both reveal that in the context of exploratory research practices, the centrality of researchers/organizations in collaboration networks and the structural holes in their knowledge elements have a significant positive impact on their academic achievements and influence.
There are several innovations of this study.
A new method in aggregating collaboration network measures at the paper level was adopted in this paper. In previous studies, the ‘all-author’ approach was typically used for data aggregation at the paper level in social network analysis [ 10 , 41 , 42 ]. As a result, an inverted U-shaped relationship was revealed between authors’ centrality and paper citations, while the effects from the structural holes value remained non-significant [ 10 ].
After comparing the regression results of the ‘all-author’ and ‘lead author’ approaches, this study focused solely on the degree centrality and structural holes values of the lead authors, specifically the first and corresponding authors. Our regression results confirm the significant relationship between the authors’ structural holes value and paper citations, which might have been smoothed out by the ‘all-author’ approach. This choice reflects a distinctive characteristic of the biomedical research field, where the first and corresponding authors typically make core contributions to the article and better represent the research strengths compared with the other authors. This method has broad generalizability to other bibliometric studies based on biomedical data.
Multi-level collaboration networks were established, including individual-level collaboration networks based on authors and national-level collaboration networks. To account for the influence of a corresponding country’s international collaboration status, countries were ranked and categorized on the basis of their structural holes values.
We revealed the vital importance of collaboration and knowledge networks, international collaboration status and university–industry cooperation in influencing cancer research capacity and impact, as well as the differences in their contributing factors. For non-leading countries, measures should be taken to enhance the international collaboration status – to become connected with unique collaborators across various clusters. For individuals, especially early career researchers, increasing the number of their collaborators seems to be sufficiently effective. University–industry cooperation should also be encouraged, enhancing the integration of human resources, technology, funding, research platforms and medical resources in the fight against cancer.
Insights gained through this study provide recommendations to research workers or administrators for the design of research directions through a knowledge network perspective. Focusing on unique issues especially interdisciplinary fields, will ultimately improve output and the influence of their research work.
Limitations and follow-up research
This study is based on a relatively limited number of articles published on one specific topic within the field of cancer research: synthetic lethality, which is characterized by rapid growth and multi-disciplinary interaction from around the world. Future research may explore other cancer research fields or topics and the various patterns of collaboration and knowledge networks, as well as other potential factors affecting the impact of cancer research, such as unexpected combinations of keywords[ 20 ].
Analyses may also be conducted to explore the availability of funding and its impact on citations. Considering the rise of gold open access publishing, it may also be necessary to consider the impact of access modality while carrying-out regression analysis based on citation data.
Finally, this study averaged only the measures of the first and corresponding authors while calculating the collaboration network metrics for each publication, emphasizing their significant contributions and impact on the related article. Future studies may further analyse the impact of other authors in different positions on the author list.
Availability of data and materials
The datasets used and/or analyzed during the current study are available from the corresponding author upon reasonable request.
Abbreviations
Impact factor
Deo SVS, Sharma J, Kumar S. GLOBOCAN 2020 report on global cancer burden: challenges and opportunities for surgical oncologists. Ann Surg Oncol. 2022;29:6497–500.
Article CAS PubMed Google Scholar
Huang A, Garraway LA, Ashworth A, Weber B. Synthetic lethality as an engine for cancer drug target discovery. Nat Rev Drug Discovery. 2020;19:23–38.
Bailie J, Matous P, Bailie R, Passey ME. Patterns of collaboration and knowledge generated by an Australian rural research centre over 20 years: a co-authorship network analysis. Health Res Policy Syst. 2023;21:87.
Article PubMed PubMed Central Google Scholar
Li EY, Liao CH, Yen HR. Co-authorship networks and research impact: a social capital perspective. Res Policy. 2013;42:1515–30.
Article Google Scholar
Nahapiet J, Ghoshal S. Social capital, intellectual capital, and the organizational advantage. Academy Manag Rev. 1998;23:242–66.
Phelps C, Heidl R, Wadhwa A. Knowledge, networks, and knowledge networks: a review and research agenda. J Manag. 2012;38:1115–66.
Google Scholar
Moorthy S, Polley DE. Technological knowledge breadth and depth: performance impacts. J Knowl Manag. 2010;14:359–77.
Guan JC, Liu N. Exploitative and exploratory innovations in knowledge network and collaboration network: a patent analysis in the technological field of nano-energy. Res Policy. 2016;45:97–112.
Yayavaram S, Ahuja G. Decomposability in knowledge structures and its impact on the usefulness of inventions and knowledge-base malleability. Adm Sci Q. 2008;53:333–62.
Guan JC, Yan Y, Zhang JJ. The impact of collaboration and knowledge networks on citations. J Informet. 2017;11:407–22.
de Moya-Anegon F, Guerrero-Bote VP, Lopez-Illescas C, Moed HF. Statistical relationships between corresponding authorship, international co-authorship and citation impact of national research systems. J Informet. 2018;12:1251–62.
Khor KA, Yu LG. Influence of international co-authorship on the research citation impact of young universities. Scientometrics. 2016;107:1095–110.
Article CAS PubMed PubMed Central Google Scholar
Moed HF. Citation analysis in research evaluation. Berlin: Springer; 2005.
Tahamtan I, Afshar AS, Ahamdzadeh K. Factors affecting number of citations: a comprehensive review of the literature. Scientometrics. 2016;107:1195–225.
Wang L, Thijs B, Glänzel W. Characteristics of international collaboration in sport sciences publications and its influence on citation impact. Scientometrics. 2015;105:843–62.
Abbasi A, Wigand RT, Hossain L. Measuring social capital through network analysis and its influence on individual performance. Libr Inf Sci Res. 2014;36:66–73.
Burt RS. The contingent value of social capital. Adm Sci Q. 1997;42:339–65.
Tsai W. Knowledge transfer in intraorganizational networks: effects of network position and absorptive capacity on business unit innovation and performance. Acad Manag J. 2001;44:996–1004.
Burt RS. Structural holes: the social structure of competition. Cambridge: Harvard University Press; 2009.
Shi F, Evans J. Surprising combinations of research contents and contexts are related to impact and emerge with scientific outsiders from distant disciplines. Nat Commun. 2023. https://doi.org/10.1038/s41467-023-36741-4 .
Abbasi A, Altmann J, Hossain L. Identifying the effects of co-authorship networks on the performance of scholars: a correlation and regression analysis of performance measures and social network analysis measures. J Informet. 2011;5:594–607.
Wang J. Knowledge creation in collaboration networks: effects of tie configuration. Res Policy. 2016;45:68–80.
Science of Science (Sci2) Tool [ http://sci.slis.indiana.edu ]
Freeman LC. Centrality in social networks conceptual clarification. Soc Networks. 1978;1:215–39.
Wang CL, Rodan S, Fruin M, Xu XY. Knowledge networks, collaboration networks, and exploratory innovation. Acad Manag J. 2014;57:484–514.
Burt RS. Structural holes and good ideas. Am J Sociol. 2004;110:349–99.
Exploratory social network analysis with Pajek (2nd ed.) [ http://mrvar.fdv.uni-lj.si/pajek/ ]
Gazni A, Ghaseminik Z. Author practices in citing other authors, institutions, and journals. J Asso Info Sci Technol. 2016;67:2536–49.
Article CAS Google Scholar
Cova T, Jarmelo S, Formosinho SJ, de Melo JSS, Pais A. Unsupervised characterization of research institutions with task-force estimation. J Informet. 2015;9:59–68.
Guerrero-Bote VP, Olmeda-Gómez C, Moya-Anegón F. Atlas of scientific institutions in food science (Scopus, 2003–2013). Lwt-Food Science And Technology. 2016;67:133–42.
van Eck NJ, Waltman L. Software survey: VOSviewer, a computer program for bibliometric mapping. Scientometrics. 2010;84:523–38.
Article PubMed Google Scholar
Isfandyari-Moghaddam A, Saberi MK, Tahmasebi-Limoni S, Mohammadian S, Naderbeigi F. Global scientific collaboration: a social network analysis and data mining of the co-authorship networks. J Inf Sci. 2023;49:1126–41.
Polyakov M, Polyakov S, Iftekhar MS. Does academic collaboration equally benefit impact of research across topics? the case of agricultural, resource, environmental and ecological economics. Scientometrics. 2017;113:1385–405.
Sud P, Thelwall M. Not all international collaboration is beneficial: the mendeley readership and citation impact of biochemical research collaboration. J Asso Infor Sci Technol. 2016;67:1849–57.
Moya-Anegón F, Guerrero-Bote VP, Bornmann L, Moed HF. The research guarantors of scientific papers and the output counting: a promising new approach. Scientometrics. 2013;97:421–34.
Contopoulos-Ioannidis DG, Ntzani EE, Ioannidis JPA. Translation of highly promising basic science research into clinical applications. Am J Med. 2003;114:477–84.
O’Dwyer M, Filieri R, O’Malley L. Establishing successful university-industry collaborations: barriers and enablers deconstructed. J Technol Transfer. 2023;48:900–31.
Bstieler L, Hemmert M, Barczak G. Trust formation in university-industry collaborations in the us biotechnology industry: ip policies, shared governance, and champions. J Prod Innov Manag. 2015;32:111–21.
Abbasi A, Hossain L, Leydesdorff L. Betweenness centrality as a driver of preferential attachment in the evolution of research collaboration networks. J Informet. 2012;6:403–12.
Rodan S, Galunic C. More than network structure: how knowledge heterogeneity influences managerial performance and innovativeness. Strateg Manag J. 2004;25:541–62.
Zhang Y, Ding JL, Yan H, He M, Wang W. A study of the influence of collaboration networks and knowledge networks on the citations of papers in sports industry in china. Complexity. 2022. https://doi.org/10.1155/2022/9236743 .
Colladon AF, D’Angelo CA, Gloor PA. Predicting the future success of scientific publications through social network and semantic analysis. Scientometrics. 2020;124:357–77.
Download references
Acknowledgements
Not applicable.
This work was supported by the Department of Science and Technology of Guangdong Province of China under the grant 2020A1414010027.
Author information
Authors and affiliations.
State Key Laboratory of Oncology in South China, Guangdong Provincial Clinical Research Center for Cancer, Sun Yat-sen University Cancer Center, No. 651 Dongfeng East Road, Guangzhou, 510060, Guangdong, People’s Republic of China
Shuang Liao, Christopher Lavender & Huiwen Zhai
You can also search for this author in PubMed Google Scholar
Contributions
S.L. conceived of and designed the study and contributed to the study design, data analysis, data interpretation and writing of the manuscript. C.L. contributed to writing of the manuscript. H.W.Z. contributed to data acquisition.
Corresponding author
Correspondence to Shuang Liao .
Ethics declarations
Ethics approval and consent to participate.
Ethics approval was not required as the material is publicly available.
Consent for publication
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Cite this article.
Liao, S., Lavender, C. & Zhai, H. Factors influencing the research impact in cancer research: a collaboration and knowledge network analysis. Health Res Policy Sys 22 , 96 (2024). https://doi.org/10.1186/s12961-024-01205-8
Download citation
Received : 13 March 2024
Accepted : 30 July 2024
Published : 06 August 2024
DOI : https://doi.org/10.1186/s12961-024-01205-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Research capacity and impact
- Collaboration network
- Knowledge network
- Paper citations
- Synthetic lethality
- International collaboration
- Cancer research
Health Research Policy and Systems
ISSN: 1478-4505
- Submission enquiries: Access here and click Contact Us
- General enquiries: [email protected]

IMAGES
COMMENTS
Abstract: We have developed a human-area networking technology that uses the surface of the human body as a data transmission path and an AC electric-field signal with a frequency below the resonant frequency of the human body. This paper describes the intra-body communication technologies we are developing to promote the further evolution of a human-area network in support of ubiquitous services.
Red Tacton technology is a Human Area Networking. (HAN) which was introduced by Nippon telegraph and. Telephone Corporation (NTT‟s) that uses the human body. surface as an high speed and safe ...
A wearable wireless body area network for human activity recognition. In 2014 Sixth International Conference on Ubiquitous and Future Networks (ICUFN) , 115-119 (IEEE, 2014). Huan, R. et al.
In this paper, we highlight applications of HBC as (1) Social Networking (e.g. LinkedIn/Facebook friend request sent during Handshaking in a meeting/party), (2) Secure Authentication using human ...
This paper describes the intra-body communication technologies we are developing to promote the further evolution of a human-area network in support of ubiquitous services.
A survey of the WBAN technology and its security concerns is presented. ... A Wireless Body Area Network (WBAN) is a wireless network that consists of a set of tiny bio-medical nodes distributed on the body surface, underneath the skin, inside the body, or in the vicinity of the body. ... In this survey paper, a review of the current research ...
Abstract. The increasing use of wireless networks and the constant miniaturization of electrical invasive/non-invasive devices have empow- ered the development of Wireless Body Area Networks (WBANs). A WBAN provides a continuous health monitoring of a patient without any constraint on his/her normal daily life activities.
This article describes human area networking technology that enables communication by touching, which the authors call RedTacton, and here, the human body acts as a transmission medium supporting IEEE 802.3 half-duplex communication at 10 Mbit/s. ... This paper introduces a new secure device pairing concept that involves using the human body ...
Similarly, a business research organization named "360 Research Reports" published its analysis result in June 2021, which forecasts that the global market of wireless wearable body area networks, which was at USD 11950 million in the year 2021 will increase with the compound annual growth rate of 6.6% from 2021 to 2027 .
In this paper I have described features, applications advantages, disadvantages of red Tacton, a new Human Area Networking technology that enables reliable high- speed HAN for the first time. As electronic devices become smaller, lower in power requirements, and less expensive, we have begun to adorn our bodies with personal information and communication appliances.
Red Tacton is a break-through technology that uses the surface of the human body as a safe, high speed network transmission path. So we, in this paper are explaining the unique new functional features and enormous potential of Red Tacton as a Human Area networking technology.
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 08 Issue: 03 | Mar 2021 www.irjet.net p-ISSN: 2395-0072 ... A Human Area Network Technology Meet Kevadiya1, 4Asst.Prof. Smita Pawar2, Shivam Shrivastav3, ... This paper proclaims model of an human area networking technologies
Arguably, the field of wireless body area sensor network (WBASN) was first introduced by Van Dam et al. 28 in 2001. Even before that time, with the increasing popularity of portable devices in 1996, Zimmerman 29 focused on how these portable devices would operate surrounding human body. Initially, personal area network (PAN) was the term used for these types of networks.
The deployment of wearable or body-worn devices is increasing rapidly, and thus researchers' interests mainly include technical and economical issues, such as networking, interoperability, security, power optimization, business growth and regulation. To address these issues properly, previous survey papers usually focused on describing the wireless body area network architecture and network ...
Abstract and Figures. RED TACTON" is the new innovative technology used in human body as a communication network. It is named as Human Area Networking (HAN). It is developed by NTT (Nippon ...
Feature papers represent the most advanced research with significant potential for high impact in the field. ... One of the major usages of wireless sensor networks in human healthcare systems is wireless body sensor networks. ... S.K. A survey on wireless body area network: Security technology and its design methodology issue. In Proceedings ...
The intra-body communication technologies the authors are developing to promote the further evolution of a human-area network in support of ubiquitous services are described. We have developed a human-area networking technology that uses the surface of the human body as a data transmission path and an AC electric-field signal with a frequency below the resonant frequency of the human body.
International Journal of Computer Science Trends and Technology (IJCST) - Volume 5 Issue 2, Mar - Apr 2017 ISSN: 2347-8578 www.ijcstjournal.org Page 497 Red TACTON-Innovation of Human Area Networking M.Bobby [1], V.Ajantha Devi [2], C. Madhubala [3] Head of the Department [1], Assistant Professor [2], Research Scholar [3]
An Overview: RedTacton- Human Area Networking (HAN)", International Journal of Trend in Research and Development, Volume 4(1), ISSN: 2394-9333 www.ijtrd.com Vidhu Rawal1, Sonam Gupta - Advanced Communication Through Flesh Red Tacton -Human Area Networking Technology International Journal of Advanced Research in Computer Science and Software ...
Technology is making many things easier; we can say that our concept is standing example for like that only. So far we have seen LAN, MAN, WAN, INTERNET & many more but here a new concept of "RED TACTON" has been introduced which makes the human body as a communication network named by HAN (Human Area Network). Human Body Communication (HBC) is a novel communication method between devices ...
A methodology to use human body as a transmitting medium to pass data in a Human Area Network (HAN) that forms the base of a successful network is proposed. This paper grabs the detail study on information about Computer Networking. Two distinct electronic media communicating between themselves and forming a group within its area can be termed as Computer Networking. In the modern globe ...
RedTacton is a new ISSN: 2231-5381 Human Area Networking technology which was introduced by Nippon telegraph and Telephone Corporation (NTT's) that uses the human body surface is a high speed and safe network transmission path. RedTacton is a Break-through technology that enables reliable high-speed HAN for the first time.
View PDF. IJRET: International Journal of Research in Engineering and Technology eISSN: 2319-1163 | pISSN: 2321-7308 NETWORKING-HUMAN AREA NETWORK Tehseen Bano Mohd Anis1, Subha Subramaniam2 1 2 Dept. of Electronics, Shah & Anchor Kutchhi Engineering College, Mumbai, India Dept. of Electronics, Shah & Anchor Kutchhi Engineering College, Mumbai ...
University-industry cooperation should also be encouraged, enhancing the integration of human resources, technology, funding, research platforms and medical resources. Insights gained through this study also provide recommendations to researchers or administrators in designing future research directions from a knowledge network perspective.
The increase in the use of wireless networks and pervasive computing have given rise to research on Wireless Body Area Network (WBAN). WBAN is a collection of sensors in, on, or around the human ...