- Careers and certifications

Good cybersecurity thesis topics for a master's degree
Writing a master's thesis a strong topic positions you for academic and professional success, while a weak one promises to make an already intensive process arduous at best..

- Alissa Irei, Senior Site Editor
A graduate-level information security project should make a timely, original contribution to an ongoing problem or debate in the field. The best cybersecurity thesis topics will therefore explore issues of current importance to the broader infosec community, ideally with some degree of both academic and practical utility. Topics should be timely -- grounded in current research, challenges and discourse -- and have relevance that promises to extend beyond immediate publication. A security analysis of an electronic voting application , for example, would likely generate both current and long-term interest within the IT community.
Rather than trying to find the ideal subject immediately, however, avoid analysis paralysis by drafting a working list of possible cybersecurity thesis topics, which you can then explore, research and refine as you continue to gather information. To start brainstorming, review recent course materials, academic papers and media articles to see what themes and patterns catch your attention. Certain topics, like security awareness training and testing, are of both perennial and growing interest. Others, such as biometrics and AI, are still emerging.
"If I were working on a thesis right now, I'd focus on the use of AI in security tools ," said Andrew Froehlich, president of analyst firm West Gate Networks. In particular, he suggested exploring AI's ability to review multiple security information streams and form analytical opinions on difficult-to-solve data security issues.
"Another great topic is the concept of fully autonomous security tools that use AI to not only find a root cause, but also have the intelligence to automate the remediation of a security event," Froehlich added.
Håkon Olsen, security engineer and founder of cybersecurity firm Cybehave, weighed in on cybersecurity thesis topics in a recent forum on Quora, where he suggested tackling the subject of identity management .
"Investigate how to maximize security within each user's threshold for usability impact," Olsen wrote, adding that most users don't use two-factor authentication when it's available. "How much security can we inspire them to 'turn on' for a service?"
The evolving position of the CISO provides yet another rich and timely subject area: What is the scope of the CISO's role, relative to both IT and lines of business, and how has it changed? What are predictors of CISO success? How do turnover rates in CISO positions compare with those in other C-level positions? What are the CISO's responsibilities following a security breach? The list continues.
Still another resource for ideas, leads and inspiration is Cybersecurity Canon , a Palo Alto Networks project started in 2013 by then-CSO Rick Howard. Modeled after the baseball and rock-and-roll halls of fame, the Cybersecurity Canon committee recognizes a variety of must-read books for their timely and significant contributions to the infosec field. The group itself consists of security executives, analysts, consultants and practitioners.
Finally, students should think about their professional goals and consider how the right cybersecurity thesis topics could eventually help them land their dream jobs. Some projects might provide the opportunity to acquire deeper expertise in a given subject area, for example, or the chance to gain meaningful, proven experience using a particular toolset or coding language. Ask yourself how you might use this project to not just complete your degree, but also to advance your career. This line of thinking can also help identify potential cybersecurity thesis topics you find particularly interesting -- a prerequisite for a project of this magnitude.
Dig Deeper on Careers and certifications

Cybersecurity career path: 5-step guide to success

CISOs on alert following SEC charges against SolarWinds

Closing the book on RSA Conference 2023

A 'CISO evolution' means connecting business value to security

Related Q&A from Alissa Irei
Wireless access point vs. router: what's the difference.
The choice of a wireless access point vs. a router for wireless network connectivity depends on the physical size of the network, needs of the ... Continue Reading
Fog computing vs. edge computing: What's the difference?
Fog computing vs. edge computing -- while many IT professionals use the terms synonymously, others make subtle but important distinctions between ... Continue Reading
What is the difference between IP telephony and VoIP?
While many IT professionals use VoIP and IP telephony synonymously, some argue for keeping a couple of subtle distinctions between the two terms in ... Continue Reading
Arista highlights its consolidation of network management tools within CloudVision, while HPE extends Aruba Central to include ...
Automation makes networks more efficient, but engineers must first mitigate the risks. With planning and training, enterprises ...
CI/CD processes help deploy code changes to networks. Integrating a CI/CD pipeline into automation makes networks more reliable, ...
To ensure an IT project's long-term success, stakeholders should keep track of certain KPIs to ensure technical debt is as low as...
The U.S. Commerce Department's proposal to ban software and hardware for connected vehicles imported from China or Russia might ...
Apple joined a list of big tech companies voluntarily committing to responsible AI. But without regulation, there is no legal ...
While wiping and reinstalling via a clean install is the simplest way to fix a broken Windows 11 desktop, an ISO file repair can ...
Organizations looking to boost productivity for key Windows users should learn what Copilot+ PCs can offer and what workflows the...
There are numerous generative AI tools that focus on enhancing user productivity, so organizations should survey the market to ...
Uptime. Downtime. Security protections. There are so many things to watch out for. An effective cloud monitoring strategy ...
The author of The Official CompTIA Cloud+ Instructor Guide and Student Guide shares his most interesting takeaways from the ...
If your cloud-based workloads and applications need to move back on premises, you'll need a plan. Start your reverse migration ...
The NCSC and counterpart agencies in the US have issued a new warning over enhanced Iranian spear-phishing activity targeting ...
Study finds desire to improve operational efficiency, digital transformation, changing customer expectations and competitive ...
Security pros need to get in front of a series of vulnerabilities affecting the Cups Linux printing service after an apparently ...

105 Latest Cyber Security Research Topics in 2024
Home Blog Security 105 Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Research Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends .
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
Top 5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorization Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security?
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more cyber security research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Cyber Security Research Topic Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security research topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
| Name | Date | Fee | Know more |
|---|

- Calculators
- Swot Analysis
- Pestle Analysis
- Five Forces Analysis
- Organizational Structure
- Copywriting
- Research Topics
- Student Resources
Services We Provide

Resources We Provide

Login / Register

- 15 Latest Networking Research Topics for Students
Comparative analysis between snort and suricata IDS software(s)
Description of the topic
The main focus of this research is to conduct a comparative analysis between Snort and Suricata software to determine which IDS software can provide better performance. There are various IDS software(s) available that can be used by organizations but it is difficult to identify which one is best (Aldarwbi et al., 2022). Different organizational structures are often facing problems while setting up an IDS system which results in false positives and intrusions. Through this research, it can be identified which IDS software is better and what secure configuration is required to detect intrusions (Waleed et al., 2022).
Research objectives
- To evaluate Snort and Suricata IDS software(s) to determine the most optimal one.
- To identify the false positive rate of Snort and Suricata on the networked environment.
Research questions
RQ1: Which IDS software can perform better on the production network in terms of performance, security, scalability and reliability?
RQ2: What different ways can be followed to deal with false positive problems in IDS technology?
Research methodology
The given research objectives and research questions can be addressed using quantitative research methodology where an experimental approach can be followed. For the given topic, both Snort and Suricata IDS systems should be configured and tested against different attacks. Depending on the findings, it can be analyzed which IDS software can perform better in terms of performance and security (Shuai & Li, 2021).
- Aldarwbi, M.Y., Lashkari, A.H. and Ghorbani, A.A. (2022) “The sound of intrusion: A novel network intrusion detection system,” Computers and Electrical Engineering , 104, p. 108455.
- Shuai, L. and Li, S. (2021) “Performance optimization of Snort based on DPDK and Hyperscan,” Procedia Computer Science , 183, pp. 837-843.
- Waleed, A., Jamali, A.F. and Masood, A. (2022) “Which open-source ids? Snort, Suricata or Zeek,” Computer Networks , 213, p. 109116.
Role of honeypots and honey nets in network security
Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network. For example, honey pots and honeynet approaches look almost the same and have the same purpose but work differently. Under this research topic, the configuration of honeynets and honeypots can be done to check which one can perform better security in terms of trapping cyber attackers. The entire implementation can be carried out in the cloud-based instance for improved security and it can be identified which type of honey pot technology must be preferred (Maesschalck et al., 2022).
- To set up a honey pot system using Open Canary on the virtual instance to protect against cyber attackers.
- To set up a honeynet system on the virtual instance to assure protection is provided against malicious attackers.
- To test honeypots and honeynets by executing DDoS attacks to check which can provide better security.
RQ1: Why is there a need for using honeypots over honey pots in a production networked environment?
RQ2: What are the differences between cloud-based and local honey pot systems for endpoint protection?
This research can be carried out using the quantitative method of research. At the initial stage, the implementation of honeypots and honeypots can be done on the virtual instance following different security rules. Once the rules are applied, the testing can be performed using a Kali Linux machine to check whether honey pots were effective or honeynets (Gill et al., 2020).
- Feng, H. et al. (2023) “Game theory in network security for Digital Twins in industry,” Digital Communications and Networks [Preprint].
- Gill, K.S., Saxena, S. and Sharma, A. (2020) “GTM-CSEC: A game theoretic model for cloud security based on ids and Honeypot,” Computers & Security , 92, p. 101732
- Maesschalck, S. et al. (2022) “Don’t get stung, cover your ICS in honey: How do honeypots fit within industrial control system security,” Computers & Security , 114, p. 102598.
How do malware variants are progressively improving?
This research can be based on evaluating how malware variants are progressively improving and what should be its state in the coming future. Malware is able to compromise confidential user’s information assets which is why this research can be based on identifying current and future consequences owing to its improvements (Deng et al., 2023). In this field, there is no research work that has been carried out to identify how malware variants are improving their working and what is expected to see in future. Once the evaluation is done, a clear analysis can also be done on some intelligent preventive measures to deal with dangerous malware variants and prevent any kind of technological exploitation (Tang et al., 2023).
- To investigate types of malware variants available to learn more about malware's hidden features.
- To focus on future implications of malware executable programs and how they can be avoided.
- To discuss intelligent solutions to deal with all malware variants.
RQ1: How do improvements in malware variants impact enterprises?
RQ2: What additional solutions are required to deal with malware variants?
In this research, qualitative analysis can be conducted on malware variants and the main reason behind their increasing severity. The entire research can be completed based on qualitative research methodology to answer defined research questions and objectives. Some real-life case studies should also be integrated into the research which can be supported by the selected topic (Saidia Fasci et al., 2023).
- Deng, H. et al. (2023) “MCTVD: A malware classification method based on three-channel visualization and deep learning,” Computers & Security , 126, p. 103084.
- Saidia Fasci, L. et al. (2023) “Disarming visualization-based approaches in malware detection systems,” Computers & Security , 126, p. 103062.
- Tang, Y. et al. (2023) “BHMDC: A byte and hex n-gram based malware detection and classification method,” Computers & Security , p. 103118.
Implementation of IoT - enabled smart office/home using cisco packet tracer
The Internet of Things has gained much more attention over the past few years which is why each enterprise and individual aims at setting up an IoT network to automate their processes (Barriga et al., 2023). This research can be based on designing and implementing an IoT-enabled smart home/office network using Cisco Packet Tracer software. Logical workspace, all network devices, including IoT devices can be used for preparing a logical network star topology (Elias & Ali, 2014). To achieve automation, the use of different IoT rules can be done to allow devices to work based on defined rules.
- To set up an IoT network on a logical workspace using Cisco Packet Tracer simulation software.
- To set up IoT-enabled rules on an IoT registration server to achieve automation (Hou et al., 2023).
RQ: Why is the Cisco packet tracer preferred for network simulation over other network simulators?
At the beginning of this research, a quantitative research methodology can be followed where proper experimental set-up can be done. As a packet tracer is to be used, the star topology can be used to interconnect IoT devices, sensors and other network devices at the home/office. Once a placement is done, the configuration should be done using optimal settings and all IoT devices can be connected to the registration server. This server will have IoT rules which can help in achieving automation by automatically turning off lights and fans when no motion is detected (Baggan et al., 2022).
- Baggan, V. et al. (2022) “A comprehensive analysis and experimental evaluation of Routing Information Protocol: An Elucidation,” Materials Today: Proceedings , 49, pp. 3040–3045.
- Barriga, J.A. et al. (2023) “Design, code generation and simulation of IOT environments with mobility devices by using model-driven development: Simulateiot-Mobile,” Pervasive and Mobile Computing , 89, p. 101751.
- Elias, M.S. and Ali, A.Z. (2014) “Survey on the challenges faced by the lecturers in using packet tracer simulation in computer networking course,” Procedia - Social and Behavioral Sciences , 131, pp. 11–15.
- Hou, L. et al. (2023) “Block-HRG: Block-based differentially private IOT networks release,” Ad Hoc Networks , 140, p. 103059.
Comparative analysis between AODV, DSDV and DSR routing protocols in WSN networks
For wireless sensor networks (WSN), there is a major need for using WSN routing rather than performing normal routines. As WSN networks are self-configured, there is a need for an optimal routing protocol that can improve network performance in terms of latency, jitter, and packet loss (Luo et al., 2023). There are often various problems faced when WSN networks are set up due to a lack of proper routing protocol selection. As a result of this, severe downtime is faced and all links are not able to communicate with each other easily (Hemanand et al., 2023). In this research topic, the three most widely used WSN routing protocols AODV, DSDV and DSR can be compared based on network performance. To perform analysis, three different scenarios can be created in network simulator 2 (Ns2).
- To create three different scenarios on ns2 software to simulate a network for 1 to 100 seconds.
- To analyze which WSN routing is optimal in terms of network performance metrics, including latency, jitter and packet loss.
- To use CBR and NULL agents for all wireless scenarios to start with simulation purposes.
RQ: How do AODV, DSR and DSDV routing protocols differ from each other in terms of network performance?
This research can be carried out using a quantitative research method. The implementation for the provided research topic can be based on Ns2 simulation software where three different scenarios can be created (AODV, DSDV and DSR). For each scenario, NULL, CSR and UDP agents can be done to start with simulation for almost 1 to 100 seconds. For all transmissions made during the given time, network performance can be checked to determine which routing is best (Mohapatra & Kanungo, 2012).
- Human and, D. et al. (2023) “Analysis of power optimization and enhanced routing protocols for Wireless Sensor Networks,” Measurement: Sensors , 25, p. 100610. Available at: https://doi.org/10.1016/j.measen.2022.100610.
- Luo, S., Lai, Y. and Liu, J. (2023) “Selective forwarding attack detection and network recovery mechanism based on cloud-edge cooperation in software-defined wireless sensor network,” Computers & Security , 126, p. 103083. Available at: https://doi.org/10.1016/j.cose.2022.103083.
- Mohapatra, S. and Kanungo, P. (2012) “Performance analysis of AODV, DSR, OLSR and DSDV routing protocols using NS2 Simulator,” Procedia Engineering , 30, pp. 69–76. Available at: https://doi.org/10.1016/j.proeng.2012.01.835.
Securing wireless network using AAA authentication and WLAN controller
Wireless networks often face intrusion attempts due to insecure protocols and sometimes open SSIDs. As a result of this, man-in-the-middle and eavesdropping attacks become easier which results in the loss of confidential information assets (Sivasankari & Kamalakkannan, 2022). When it comes to managing networks in a large area, there are higher chances for attacks that enable cyber attackers in intercepting ongoing communication sessions. However, there is currently no research conducted where the use of AAA authentication has been done with WLAN controllers to make sure a higher level of protection is provided (Nashwan, 2021). The proposed research topic can be based on securing wireless networks with the help of AAA authentication and WLAN controllers. The use of AAA authentication can be done to set up a login portal for users whilst the WLAN controller can be used for managing all wireless access points connected to the network (Nashwan, 2021).
- To set up AAA authentication service on the wireless network simulated on Cisco Packet Tracer for proper access control.
- To set up a WLAN controller on the network to manage all wireless access points effortlessly.
- To use WPA2-PSK protocol on the network to assure guest users are only able to access wireless networks over a secure protocol.
RQ1: What additional benefits are offered by AAA authentication on the WLAN networks?
RQ2: Why are wireless networks more likely to face network intrusions than wired networks?
This research topic is based on the secure implementation of a wireless LAN network using a Cisco packet tracer. Hence, this research can be carried out using a quantitative research method. The implementation can be carried out using AAA authentication which can assure that access control is applied for wireless logins. On the other hand, a WLAN controller can also be configured which can ensure that all WAPs are managed (ZHANG et al., 2012).
- Nashwan, S. (2021) “AAA-WSN: Anonymous Access Authentication Scheme for wireless sensor networks in Big Data Environment,” Egyptian Informatics Journal , 22(1), pp. 15–26.
- Sivasankari, N. and Kamalakkannan, S. (2022) “Detection and prevention of man-in-the-middle attack in IOT network using regression modeling,” Advances in Engineering Software , 169, p. 103126.
- ZHANG, J. et al. (2012) “AAA authentication for Network mobility,” The Journal of China Universities of Posts and Telecommunications , 19(2), pp. 81-86.
OWASP's approach to secure web applications from web application exploits
The research can revolve around the development of web applications by considering OWASP's top 10 rules. Usually, web applications are deployed by organizations depending on their requirements and these applications are vulnerable to various exploits, including injection, broken authentication and other forgery attacks (Poston, 2020). Identifying every single vulnerability is difficult when reference is not taken and often organizations end up hosting a vulnerable server that leads to privacy issues and compromises confidential information easily. In this research, OWASP's top 10 approaches can be followed to develop a secure web application that can be able to protect against top web application exploits. This approach is based on emphasizing severe and minor vulnerabilities which must be patched for protecting against web application attacks (Deepa & Thilagam, 2016).
- The first objective can be setting up an insecure web application on the cloud environment which can be exploited with different techniques.
- The second objective can be to consider all techniques and procedures provided by OWASP's top 10 methodologies.
- The last objective can be applying all fixes to insecure web applications to make them resistant to OWASP top 10 attacks (Sonmez, 2019).
RQ1: What are the benefits of using OWASP's top 10 approaches to harden web applications in comparison to other security approaches?
The research methodology considered for this research project can be quantitative using an experimental approach. The practical work can be done for the selected topic using AWS or the Azure cloud platform. Simply, a virtual web server can be configured and set up with a secure and insecure web application. Following OWASP's top 10 techniques and procedures, the web application can be secured from possible attacks. In addition, insecure applications can also be exploited and results can be evaluated (Applebaum et al., 2021).
- Applebaum, S., Gaber, T. and Ahmed, A. (2021) “Signature-based and machine-learning-based web application firewalls: A short survey,” Procedia Computer Science , 189, pp. 359–367. Available at: https://doi.org/10.1016/j.procs.2021.05.105.
- Deepa, G. and Thilagam, P.S. (2016) “Securing web applications from injection and logic vulnerabilities: Approaches and challenges,” Information and Software Technology , 74, pp. 160–180. Available at: https://doi.org/10.1016/j.infsof.2016.02.005.
- Poston, H. (2020) “Mapping the owasp top Ten to the blockchain,” Procedia Computer Science , 177, pp. 613-617. Available at: https://doi.org/10.1016/j.procs.2020.10.087.
- Sonmez, F.Ö. (2019) “Security qualitative metrics for Open Web Application Security Project Compliance,” Procedia Computer Science , 151, pp. 998-1003. Available at: https://doi.org/10.1016/j.procs.2019.04.140.
Importance of configuring RADIUS (AAA) server on the network
User authentication has become significant nowadays as it guarantees that a legitimate user is accessing the network. But a problem is faced when a particular security control is to be identified for authentication and authorization. These controls can be categorized based on mandatory access controls, role-based access control, setting up captive portals and many more. Despite several other security controls, one of the most efficient ones is the RADIUS server (SONG et al., 2008). This server can authenticate users on the network to make sure network resources are accessible to only legal users. This research topic can be based on understanding the importance of RADIUS servers on the network which can also be demonstrated with the help of the Cisco Packet Tracer. A network can be designed and equipped with a RADIUS server to ensure only legal users can access network resources (WANG et al., 2009).
- To configure RADIUS (AAA) server on the network which can be able to authenticate users who try to access network resources.
- To simulate a network on a packet tracer simulation software and verify network connectivity.
RQ1: What are other alternatives to RADIUS (AAA) authentication servers for network security?
RQ2: What are the common and similarities between RADIUS and TACACS+ servers?
As a logical network is to be designed and configured, a quantitative research methodology can be followed. In this research coursework, a secure network design can be done using a packet tracer network simulator, including a RADIUS server along with the DMZ area. The configuration for the RADIUS server can be done to allow users to only access network resources by authenticating and authorizing (Nugroho et al., 2022).
- Nugroho, Y.S. et al. (2022) “Dataset of network simulator related-question posts in stack overflow,” Data in Brief , 41, p. 107942.
- SONG, M., WANG, L. and SONG, J.-de (2008) “A secure fast handover scheme based on AAA protocol in Mobile IPv6 Networks,” The Journal of China Universities of Posts and Telecommunications , 15, pp. 14-18.
- WANG, L. et al. (2009) “A novel congestion control model for interworking AAA in heterogeneous networks,” The Journal of China Universities of Posts and Telecommunications , 16, pp. 97-101.
Comparing mod security and pF sense firewall to block illegitimate traffic
Firewalls are primarily used for endpoint security due to their advanced features ranging from blocking to IDS capabilities and many more. It is sometimes challenging to identify which type of firewall is best and due to this reason, agencies end up setting up misconfigured firewalls (Tiwari et al., 2022). This further results in a cyber breach, destroying all business operations. The research can be emphasizing conducting a comparison between the two most widely used firewalls i.e. Mod Security and pF sense. Using a virtualized environment, both firewalls can be configured and tested concerning possible cyber-attacks (Lu & Yang, 2020).
- To use the local environment to set up Mod security and pF sense firewall with appropriate access control rules.
- To test both firewalls by executing distributed denial of service attacks from a remote location.
- To compare which type of firewall can provide improved performance and robust security.
RQ: How do Mod security and pF sense differ from each other in terms of features and performance?
The practical experimentation for both firewalls can be done using a virtualized environment where two different machines can be created. Hence, this research can be carried out using a quantitative research method . The first machine can have Mod security and the second machine can have pF sense configured. A new subnet can be created which can have these two machines. The third machine can be an attacking machine which can be used for testing firewalls. The results obtained can be then evaluated to identify which firewall is best for providing security (Uçtu et al., 2021).
- Lu, N. and Yang, Y. (2020) “Application of evolutionary algorithm in performance optimization of Embedded Network Firewall,” Microprocessors and Microsystems , 76, p. 103087.
- Tiwari, A., Papini, S. and Hemamalini, V. (2022) “An enhanced optimization of parallel firewalls filtering rules for scalable high-speed networks,” Materials Today: Proceedings , 62, pp. 4800-4805.
- Uçtu, G. et al. (2021) “A suggested testbed to evaluate multicast network and threat prevention performance of Next Generation Firewalls,” Future Generation Computer Systems , 124, pp. 56-67.
Conducting a comprehensive investigation on the PETYA malware
The main purpose of this research is to conduct a comprehensive investigation of the PETYA malware variant (McIntosh et al., 2021). PETYA often falls under the category of ransomware attacks which not only corrupt and encrypt files but can compromise confidential information easily. Along with PETYA, there are other variants also which lead to a security outage and organizations are not able to detect these variants due to a lack of proper detection capabilities (Singh & Singh, 2021). In this research, a comprehensive analysis has been done on PETYA malware to identify its working and severity level. Depending upon possible causes of infection of PETYA malware, some proactive techniques can also be discussed (Singh & Singh, 2021). A separation discussion can also be made on other malware variants, their features, and many more.
- The main objective of this research is to scrutinize the working of PETYA malware because a ransomware attack can impact the micro and macro environment of the organizations severely.
- The working of PETYA malware along with its source code can be reviewed to identify its structure and encryption type.
- To list all possible CVE IDs which are exploited by the PETYA malware.
RQ1: How dangerous is PETYA malware in comparison to other ransomware malware?
This research can be based on qualitative research methodology to evaluate the working of PETYA malware from various aspects, the methodology followed and what are its implications. The research can be initiated by evaluating the working of PETYA malware, how it is triggered, what encryption is applied and other factors. A sample source code can also be analyzed to learn more about how cryptography is used with ransomware (Abijah Roseline & Geetha, 2021).
- Abijah Roseline, S. and Geetha, S. (2021) “A comprehensive survey of tools and techniques mitigating computer and mobile malware attacks,” Computers & Electrical Engineering , 92, p. 107143.
- McIntosh, T. et al. (2021) “Enforcing situation-aware access control to build malware-resilient file systems,” Future Generation Computer Systems , 115, pp. 568-582.
- Singh, J. and Singh, J. (2021) “A survey on machine learning-based malware detection in executable files,” Journal of Systems Architecture , 112, p. 101861.
Setting up a Live streaming server on the cloud platform
Nowadays, various organizations require a live streaming server to stream content depending upon their business. However, due to a lack of proper hardware, organizations are likely to face high network congestion, slowness and other problems (Ji et al., 2023). Referring to the recent cases, it has been observed that setting up a streaming server on the local environment is not expected to perform better than a cloud-based streaming server configuration (Martins et al., 2019). This particular research topic can be based on setting up a live streaming server on the AWS or Azure cloud platform to make sure high network bandwidth is provided with decreased latency. The research gap analysis would be conducted to analyze the performance of live streaming servers on local and cloud environments in terms of network performance metrics (Bilal et al., 2018).
- To set up a live streaming server on the AWS or Azure cloud platform to provide live streaming services.
- To use load balancers alongside streaming servers to ensure the load is balanced and scalability is achieved.
- To use Wireshark software to test network performance during live streaming.
RQ1: Why are in-house streaming servers not able to provide improved performance in comparison to cloud-based servers?
RQ2: What additional services are provided by cloud service providers which help in maintaining network performance?
The implementation is expected to carry out on the AWS cloud platform with other AWS services i.e. load balancer, private subnet and many more (Efthymiopoulou et al., 2017). Hence, this research can be carried out using a quantitative research method. The configuration of ec2 instances can be done which can act as a streaming server for streaming media and games. For testing this project, the use of OBS studio can be done which can help in checking whether streaming is enabled or not. For network performance, Wireshark can be used for testing network performance (George et al., 2020).
- Bilal, KErbad, A. and Hefeeda, M. (2018) “QoE-aware distributed cloud-based live streaming of multi-sourced Multiview Videos,” Journal of Network and Computer Applications , 120, pp. 130-144.
- Efthymiopoulou, M. et al. (2017) “Robust control in cloud-assisted peer-to-peer live streaming systems,” Pervasive and Mobile Computing , 42, pp. 426-443.
- George, L.C. et al. (2020) “Usage visualization for the AWS services,” Procedia Computer Science , 176, pp. 3710–3717.
- Ji, X. et al. (2023) “Adaptive QoS-aware multipath congestion control for live streaming,” Computer Networks , 220, p. 109470.
- Martins, R. et al. (2019) “Iris: Secure reliable live-streaming with Opportunistic Mobile Edge Cloud offloading,” Future Generation Computer Systems , 101, pp. 272-292.
Significance of using OSINT framework for Network reconnaissance
Network reconnaissance is becoming important day by day when it comes to penetration testing. Almost all white hat hackers are dependent on the OSINT framework to start with network reconnaissance and footprinting when it comes to evaluating organizational infrastructure. On the other hand, cyber attackers are also using this technique to start fetching information about their target. Currently, there is no investigation carried out to identify how effective the OSINT framework is over traditional reconnaissance activities (Liu et al., 2022). This research is focused on using OSINT techniques to analyze victims using different sets of tools like Maltego, email analysis and many other techniques. The analysis can be based on fetching sensitive information about the target which can be used for conducting illegal activities (Abdullah, 2019).
- To use Maltego software to conduct network reconnaissance on the target by fetching sensitive information.
- To compare the OSINT framework with other techniques to analyze why it performs well.
RQ1: What is the significance of using the OSINT framework in conducting network reconnaissance?
RQ2: How can the OSINT framework be used by cyber hackers for conducting illegitimate activities?
The OSINT framework is easily accessible on its official website where different search options are given. Hence, this research can be carried out using a quantitative research method. Depending upon the selected target, each option can be selected and tools can be shortlisted for final implementation. Once the tools are shortlisted, they can be used to conduct network reconnaissance (González-Granadillo et al., 2021). For example, Maltego can be used as it is a powerful software to fetch information about the target.
- Abdullah, S.A. (2019) “Seui-64, bits an IPv6 addressing strategy to mitigate reconnaissance attacks,” Engineering Science and Technology , an International Journal, 22(2), pp. 667–672.
- Gonzalez-Granadillo, G. et al. (2021) “ETIP: An enriched threat intelligence platform for improving OSINT correlation, analysis, visualization and sharing capabilities,” Journal of Information Security and Applications , 58, p. 102715.
- Liu, W. et al. (2022) “A hybrid optimization framework for UAV Reconnaissance Mission Planning,” Computers & Industrial Engineering , 173, p. 108653.
Wired and wireless network hardening in cisco packet tracer
At present, network security has become essential and if enterprises are not paying attention to the security infrastructure, there are several chances for cyber breaches. To overcome all these issues, there is a need for setting up secure wired and wireless networks following different techniques such as filtered ports, firewalls, VLANs and other security mechanisms. For the practical part, the use of packet tracer software can be done to design and implement a highly secure network (Sun, 2022).
- To use packet tracer simulation software to set up secure wired and wireless networks.
- Use different hardening techniques, including access control rules, port filtering, enabling passwords and many more to assure only authorized users can access the network (Zhang et al., 2012).
RQ: Why is there a need for emphasizing wired and wireless network security?
Following the quantitative approach, the proposed research topic implementation can be performed in Cisco Packet Tracer simulation software. Several devices such as routers, switches, firewalls, wireless access points, hosts and workstations can be configured and interconnected using Cat 6 e cabling. For security, every device can be checked and secure design principles can be followed like access control rules, disabled open ports, passwords, encryption and many more (Smith & Hasan, 2020).
- Smith, J.D. and Hasan, M. (2020) “Quantitative approaches for the evaluation of Implementation Research Studies,” Psychiatry Research , 283, p. 112521.
- Sun, J. (2022) “Computer Network Security Technology and prevention strategy analysis,” Procedia Computer Science , 208, pp. 570–576.
- Zhang, YLiang, R. and Ma, H. (2012) “Teaching innovation in computer network course for undergraduate students with a packet tracer,” IERI Procedia , 2, pp. 504–510.
Different Preemptive ways to resist spear phishing attacks
When it comes to social engineering, phishing attacks are rising and are becoming one of the most common ethical issues as it is one of the easiest ways to trick victims into stealing information. This research topic is based on following different proactive techniques which would help in resisting spear phishing attacks (Xu et al., 2023). This can be achieved by using the Go-Phish filter on the machine which can automatically detect and alert users as soon as the phished URL is detected. It can be performed on the cloud platform where the apache2 server can be configured along with an anti-phishing filter to protect against phishing attacks (Yoo & Cho, 2022).
- To set up a virtual instance on the cloud platform with an apache2 server and anti-phishing software to detect possible phishing attacks.
- To research spear phishing and other types of phishing attacks that can be faced by victims (Al-Hamar et al., 2021).
RQ1: Are phishing attacks growing just like other cyber-attacks?
RQ2: How effective are anti-phishing filters in comparison to cyber awareness sessions?
The entire research can be conducted by adhering to quantitative research methodology which helps in justifying all research objectives and questions. The implementation of the anti-phishing filter can be done by creating a virtual instance on the cloud platform which can be configured with an anti-phishing filter. Along with this, some phishing attempts can also be performed to check whether the filter works or not (Siddiqui et al., 2022).
- Al-Hamar, Y. et al. (2021) “Enterprise credential spear-phishing attack detection,” Computers & Electrical Engineering , 94, p. 107363.
- Siddiqui, N. et al. (2022) “A comparative analysis of US and Indian laws against phishing attacks,” Materials Today: Proceedings , 49, pp. 3646–3649.
- Xu, T., Singh, K. and Rajivan, P. (2023) “Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks,” Applied Ergonomics , 108, p. 103908.
- Yoo, J. and Cho, Y. (2022) “ICSA: Intelligent chatbot security assistant using text-CNN and multi-phase real-time defense against SNS phishing attacks,” Expert Systems with Applications , 207, p. 117893.
Evaluating the effectiveness of distributed denial of service attacks
The given research topic is based on evaluating the effectiveness of distributed denial of service attacks on cloud and local environments. Hence, this research can be carried out using a quantitative research method. Cyber attackers find DDoS as one of the most dangerous technological exploitation when it comes to impacting network availability (Krishna Kishore et al., 2023). This research can revolve around scrutinizing the impact of DDoS attacks on the local environment and cloud environment. This can be done by executing DDoS attacks on a simulated environment using hoping or other software(s) to check where it has a higher magnitude (de Neira et al., 2023).
- To set up a server on the local and cloud environment to target using DDoS attacks for checking which had experienced slowness.
- To determine types of DDoS attack types, their magnitude and possible mitigation techniques.
RQ: Why do DDoS attacks have dynamic nature and how is it likely to sternly impact victims?
The experimentation for this research can be executed by creating a server on the local and cloud environment. Hence, this research can be carried out using a quantitative research method. These servers can be set up as web servers using apache 2 service. On the other hand, a Kali Linux machine can be configured with DDoS execution software. Each server can be targeted with DDoS attacks to check its effectiveness (Benlloch-Caballero et al., 2023).
- Benlloch-Caballero, P., Wang, Q. and Alcaraz Calero, J.M. (2023) “Distributed dual-layer autonomous closed loops for self-protection of 5G/6G IOT networks from distributed denial of service attacks,” Computer Networks , 222, p. 109526.
- de Neira, A.B., Kantarci, B. and Nogueira, M. (2023) “Distributed denial of service attack prediction: Challenges, open issues and opportunities,” Computer Networks , 222, p. 109553.
- Krishna Kishore, P., Ramamoorthy, S. and Rajavarman, V.N. (2023) “ARTP: Anomaly-based real time prevention of distributed denial of service attacks on the web using machine learning approach,” International Journal of Intelligent Networks , 4, pp. 38–45.
Recommended Readings
Latest Web Development Research Topics
Top Management Research Topics
Newest AI Research Topics

Research in every field is becoming more and more essential because of constant developments around the world. Similar is the case in the field of networking. This is the reason; students who are preparing to master the field of networking need to keep their knowledge of the current state of the art in the field up to date.
However, choosing the right research topic often becomes a tough task for students to carry out their research effectively. That being the case, this list contains 15 latest research topics in the field of networking. Whether you are a seasoned researcher or just starting, this list can provide you with ample inspiration and guidance to drive your research forward in the dynamic and evolving field of Networking.
Copyright © 2023 CrowJack. All Rights Reserved

Click here to place an order for topic brief service to get instant approval from your professor.
99+ Cyber Security Dissertation Topics for master’s and PhD students
Table of Contents
Choosing the right topic for your cyber security dissertation or thesis is crucial for success in your academic journey. There are numerous cyber security dissertation topics to explore, catering to both master’s and PhD levels of research.
Delving into cyber security research topics for masters can lead you to investigate current trends and challenges in the field, such as data breaches, ransomware attacks, and emerging technologies like artificial intelligence and blockchain.
Similarly, cyber security research topics for PhD candidates often involve in-depth analyses and innovative solutions to complex security issues, such as network intrusion detection systems, secure software development practices, or privacy-preserving techniques.
Exploring interesting topics in cyber security can spark new ideas and insights, leading to valuable contributions to the field. Whether you’re interested in cryptography, cloud security, or cyber threat intelligence, there’s a vast array of potential research avenues to explore.
By carefully selecting cyber security dissertation topics that align with your interests and expertise, you can embark on a fulfilling academic journey while making meaningful contributions to the ever-evolving landscape of cyber security .
Remember to consider the relevance, novelty, and feasibility of your chosen topic, ensuring that it offers ample opportunities for original research and scholarly inquiry. With dedication and perseverance, your cyber security dissertation or thesis can become a cornerstone of knowledge in this critical and dynamic field.
List of cybersecurity dissertation topics

Top 15 Cyber Security Dissertation topics
- Cybersecurity Challenges on the Internet of Things (IoT) : Investigate the unique security threats posed by IoT devices and propose strategies to mitigate risks and enhance security in IoT ecosystems.
- Machine Learning for Cyber Threat Detection : Explore the application of machine learning algorithms for detecting and preventing cyber threats, such as malware, phishing attacks, and insider threats.
- Blockchain Technology for Secure Data Management : Examine how blockchain can be leveraged to ensure the integrity, confidentiality, and availability of sensitive data in various domains, including finance, healthcare, and supply chain management.
- Privacy-Preserving Techniques in Data Analytics : Investigate methods for conducting data analytics while preserving user privacy, addressing concerns related to data anonymization, encryption, and differential privacy.
- Cybersecurity in Cloud Computing Environments : Analyze the security challenges inherent in cloud computing infrastructures and propose solutions for securing data, applications, and services hosted in the cloud.
- Securing Critical Infrastructure Systems : Explore the vulnerabilities of critical infrastructure systems, such as energy grids, transportation networks, and healthcare systems, and develop strategies for protecting them against cyber-attacks.
- Cybersecurity Governance and Policy : Examine the role of government regulations, industry standards, and organizational policies in shaping cybersecurity practices and fostering a culture of security awareness.
- Threat Intelligence and Cyber Threat Hunting : Investigate methodologies for gathering, analyzing, and operationalizing threat intelligence to proactively identify and neutralize cyber threats.
- Cybersecurity Awareness and Education Programs : Assess the effectiveness of cybersecurity awareness and education initiatives in reducing security incidents and improving overall cyber hygiene among individuals and organizations.
- Securing Internet of Medical Things (IoMT) Devices : Explore the security challenges associated with medical devices connected to the internet and propose strategies to safeguard patient data and ensure the integrity of medical treatments.
- Cybersecurity Implications of Artificial Intelligence ( AI ) and Machine Learning (ML) : Examine the potential security risks posed by AI and ML technologies, such as adversarial attacks, data poisoning, and algorithmic biases, and propose methods for enhancing their security.
- Cybersecurity in Smart Cities : Analyze the security implications of interconnected smart city infrastructure, including smart grids, transportation systems, and public services, and develop strategies for protecting against cyber threats.
- Cybersecurity in Autonomous Systems : Investigate the security challenges associated with autonomous vehicles, drones, and robots, and propose solutions to ensure the safety and security of these systems in real-world scenarios.
- Digital Forensics and Incident Response : Explore methodologies for conducting digital forensics investigations and orchestrating incident response activities to effectively mitigate the impact of cyber-attacks and attribute them to perpetrators.
- Ethical Hacking and Penetration Testing : Examine the role of ethical hacking and penetration testing in identifying and remedying security vulnerabilities within organizations’ IT infrastructures, applications, and networks.
Top 15 Cyber Security Thesis topics
- Cybersecurity in the Age of Artificial Intelligence : Explore the intersection of cybersecurity and artificial intelligence, examining the use of AI for both offensive and defensive cyber operations, as well as the implications for security and privacy.
- Securing Internet of Things (IoT) Ecosystems : Investigate the unique security challenges posed by the proliferation of IoT devices, and propose strategies to ensure the integrity, confidentiality, and availability of IoT systems.
- Privacy-Preserving Techniques in Big Data Analytics : Examine methods for conducting large-scale data analytics while preserving user privacy, including techniques such as homomorphic encryption, secure multiparty computation, and differential privacy.
- Blockchain Technology for Cybersecurity : Explore the applications of blockchain technology in cybersecurity, such as secure authentication, decentralized identity management, and tamper-resistant audit trails.
- Cyber Threat Intelligence and Information Sharing : Analyze the role of threat intelligence in enhancing cybersecurity posture and evaluate mechanisms for sharing threat intelligence among organizations to facilitate proactive threat detection and response.
- Cybersecurity Governance and Compliance : Investigate the regulatory landscape of cybersecurity, including compliance frameworks such as GDPR, HIPAA, and NIST, and assess their effectiveness in improving cybersecurity posture and promoting organizational resilience.
- Securing Cloud-Native Applications : Examine the security challenges associated with cloud-native development practices, such as containerization, microservices architecture, and serverless computing, and propose techniques for securing cloud-native applications.
- Cybersecurity in Critical Infrastructure Systems : Analyze the vulnerabilities of critical infrastructure systems, including energy grids, transportation networks, and healthcare systems, and develop strategies for protecting them against cyber threats and attacks.
- Digital Forensics and Incident Response : Explore methodologies for conducting digital forensics investigations and orchestrating incident response activities, including techniques for gathering and preserving digital evidence, and attributing cyber-attacks to perpetrators.
- Cybersecurity in Healthcare Systems : Investigate the security challenges specific to healthcare IT environments, such as protecting electronic health records (EHRs), medical devices, and telemedicine platforms, and propose strategies for enhancing security and privacy.
- Cybersecurity in Industrial Control Systems (ICS) : Examine the security risks posed by cyber-attacks on industrial control systems, such as SCADA and PLC systems, and propose techniques for securing critical infrastructure assets in industrial environments.
- Securing Next-Generation Networks (5G/6G) : Analyze the security implications of next-generation wireless networks, including 5G and future iterations like 6G, and propose strategies for mitigating emerging threats and vulnerabilities in these network architectures.
- Cybersecurity Challenges in Autonomous Systems : Investigate the security risks associated with autonomous vehicles, drones, and robots, and propose techniques for ensuring the safety and security of these systems in real-world deployments.
- Cybersecurity Awareness and Training Programs : Assess the effectiveness of cybersecurity awareness and training initiatives in reducing human error and improving cybersecurity hygiene among individuals and organizations and propose best practices for designing and implementing such programs.
- Ethical Hacking and Penetration Testing : Examine the role of ethical hacking and penetration testing in identifying and remedying security vulnerabilities within organizations’ IT infrastructures, applications, and networks, and propose methodologies for conducting comprehensive security assessments.
Top 15 cyber security research topics for masters
- Machine Learning for Intrusion Detection : Explore the application of machine learning algorithms for detecting and preventing intrusions in computer networks, considering both supervised and unsupervised learning approaches.
- Privacy-Preserving Data Sharing in Cloud Environments : Investigate techniques for securely sharing sensitive data in cloud computing environments while preserving user privacy, focusing on methods such as homomorphic encryption and secure multiparty computation.
- Blockchain-Based Secure Identity Management : Examine the use of blockchain technology for secure and decentralized identity management, addressing issues such as identity theft and unauthorized access to personal information.
- Threat Intelligence Platforms and Analysis : Evaluate the effectiveness of threat intelligence platforms in aggregating and analyzing cyber threat data and propose enhancements to improve threat detection and response capabilities.
- Security Challenges in Internet of Things (IoT) Networks : Analyze the security vulnerabilities inherent in IoT devices and networks and propose strategies for securing IoT ecosystems against cyber-attacks and data breaches.
- Secure Software Development Practices : Investigate best practices for integrating security into the software development lifecycle, including secure coding techniques, vulnerability assessment tools, and threat modeling methodologies.
- Cybersecurity for Critical Infrastructure Protection : Examine the security risks faced by critical infrastructure systems, such as energy grids and transportation networks, and propose measures to safeguard these systems against cyber threats and attacks.
- Secure Mobile Device Management : Evaluate approaches for managing the security of mobile devices in enterprise environments, including mobile device management (MDM) solutions, containerization, and app sandboxing.
- Cybersecurity Challenges in Healthcare Information Systems : Analyze the unique security challenges of healthcare IT systems, such as electronic health records (EHRs) and medical devices and propose solutions to enhance patient data security and privacy.
- Securing Industrial Control Systems (ICS) : Investigate the security risks associated with industrial control systems, such as SCADA and PLC systems, and propose strategies for protecting critical infrastructure assets in industrial environments.
- Cyber Threat Hunting and Incident Response : Explore methodologies for proactively hunting for cyber threats within organizational networks, as well as best practices for incident response and mitigation.
- Security Assessment of Cloud-Native Applications : Evaluate the security posture of cloud-native applications built on microservices architecture, containerization, and serverless computing, and propose techniques for identifying and remediating security vulnerabilities.
- Secure Authentication and Access Control Mechanisms : Investigate novel authentication methods, such as biometrics, multi-factor authentication (MFA), and zero-trust security models, and assess their effectiveness in preventing unauthorized access to systems and data.
- Cybersecurity Awareness Training Programs : Assess the impact of cybersecurity awareness training on reducing human error and improving cybersecurity hygiene within organizations and propose strategies for designing effective training programs.
- Cybersecurity Governance and Compliance Frameworks : Examine the role of governance and compliance frameworks, such as GDPR, NIST, and ISO 27001, in shaping cybersecurity practices and ensuring regulatory compliance within organizations.
Top 15 cyber security research topics for PhD
- Adversarial Machine Learning in Cybersecurity : Investigate techniques for defending against adversarial attacks on machine learning models used in cybersecurity applications, considering both evasion and poisoning attacks.
- Quantum Cryptography and Post-Quantum Cryptography : Explore the security implications of quantum computing on cryptographic protocols and algorithms and develop quantum-resistant cryptographic solutions for future-proof cybersecurity.
- Cyber-Physical System Security : Analyze the security challenges of cyber-physical systems (CPS), such as smart grids and autonomous vehicles, and propose strategies for protecting CPS against cyber-attacks that can have physical consequences.
- Secure Multi-Party Computation (MPC) : Investigate advanced MPC protocols for securely computing functions over distributed data while preserving privacy and apply MPC to practical cybersecurity scenarios such as secure data sharing and collaborative threat analysis.
- Zero-Day Vulnerability Discovery and Exploitation : Develop novel techniques for identifying and exploiting zero-day vulnerabilities in software and network systems and explore the implications for defensive cybersecurity measures such as patch management and intrusion detection.
- Secure Hardware Design and Trustworthy Computing : Investigate techniques for designing hardware platforms with built-in security features, such as secure enclaves and hardware-based root of trust, to enhance the security of computing systems at the hardware level.
- Cyber Threat Intelligence Fusion and Analysis : Develop methods for aggregating, correlating, and analyzing diverse sources of cyber threat intelligence to provide actionable insights for proactive threat detection and response.
- Privacy-Enhancing Technologies (PETs) : Explore the design and implementation of PETs such as differential privacy, secure multi-party computation, and homomorphic encryption, and evaluate their effectiveness in protecting user privacy in various cybersecurity applications.
- Cybersecurity in the Internet of Medical Things (IoMT) : Investigate the security challenges of interconnected medical devices and healthcare systems, and develop strategies for ensuring the integrity, confidentiality, and availability of patient data and medical treatments.
- Automated Vulnerability Analysis and Exploitation : Develop automated techniques for discovering, analyzing, and exploiting software vulnerabilities, including vulnerability scanning, fuzzing, and exploit generation, to improve the security of software systems.
- Secure Software-defined Networking (SDN) : Analyze the security implications of SDN architectures and protocols, and propose methods for securing SDN controllers, switches, and network services against cyber-attacks and unauthorized access.
- Behavioral Biometrics and Continuous Authentication : Investigate the use of behavioral biometrics, such as keystroke dynamics and gait analysis, for continuous user authentication in cybersecurity applications, and assess their effectiveness in detecting unauthorized access and insider threats.
- Cybersecurity Resilience and Risk Management : Develop frameworks and methodologies for assessing and enhancing the resilience of organizations to cyber threats, including risk assessment, incident response planning, and business continuity management.
- Secure Internet of Things (IoT) Infrastructure : Design and evaluate secure IoT architectures, protocols, and communication mechanisms to mitigate security risks in IoT ecosystems, including device authentication, data encryption, and access control.
- Cybersecurity for Autonomous Systems : Investigate the security challenges of autonomous systems, such as unmanned aerial vehicles (UAVs) and autonomous vehicles and develop techniques for ensuring the safety and security of autonomous operations in dynamic environments.
More interesting topics in cyber security in other Categories
Exploring the realm of cyber security dissertation topics, students can delve into areas such as Network Security, focusing on intrusion detection systems, firewalls, and secure communication protocols. Cryptography offers a rich field, where research can encompass encryption algorithms, cryptographic protocols, and key management techniques.
Privacy and Data Protection invite investigation into legal frameworks like GDPR, alongside technical solutions such as data anonymization and privacy-enhancing technologies. Cybercrime and Digital Forensics provide opportunities to study incident response methodologies, digital evidence collection, and cybercriminal profiling.
Additionally, Human Factors in Cybersecurity examines the role of human behavior and psychology in security breaches and awareness training effectiveness.
Below is the list of cyber security dissertation topics in various categories:
Network Security:
- Analysis of Intrusion Detection Systems for Detecting Advanced Persistent Threats (APTs)
- Evaluation of Next-Generation Firewalls in Enterprise Network Environments
- Enhancing Security in Wireless Networks: Challenges and Solutions
- Comparative Study of Secure Communication Protocols for IoT Devices
- Machine Learning Approaches for Anomaly Detection in Network Traffic
Cryptography:
- Performance Analysis of Elliptic Curve Cryptography in Resource-Constrained Environments
- Quantum Cryptography: Exploring Quantum Key Distribution Protocols
- Homomorphic Encryption for Secure Cloud Computing: Implementation and Performance Evaluation
- Post-Quantum Cryptography: Cryptographic Algorithms Resilient to Quantum Attacks
- Analysis of Blockchain-Based Cryptographic Protocols for Secure Transactions
Privacy and Data Protection:
- Compliance with GDPR: Challenges and Strategies for Organizations
- Differential Privacy Techniques for Privacy-Preserving Data Analysis
- Privacy-Preserving Machine Learning: Techniques and Applications
- Secure Multiparty Computation for Collaborative Data Analysis
- Legal and Ethical Implications of Data Protection Laws in Cross-Border Data Transfers
Cybercrime and Digital Forensics:
- Advanced Persistent Threats (APTs): Analysis, Detection, and Mitigation Strategies
- Digital Forensics Techniques for Investigating Cyber Attacks on Industrial Control Systems (ICS)
- Behavioral Analysis of Cybercriminals: Profiling and Attribution Techniques
- Malware Analysis and Reverse Engineering: Tools and Methodologies
- Cyber Incident Response Planning: Developing Effective Incident Response Frameworks
Human Factors in Cybersecurity:
- Phishing Awareness Training: Effectiveness and Best Practices
- Psychological Factors in Insider Threats: Identifying and Addressing Insider Risks
- Usable Security: Designing Secure Systems with User Experience in Mind
- Security Culture in Organizations: Assessing and Cultivating a Culture of Security Awareness
- Human-Centric Approaches to Cybersecurity Education and Training: Improving Cyber Hygiene Practices
Cloud Security:
- Security Challenges in Multi-Cloud Environments: Risk Assessment and Mitigation Strategies
- Identity and Access Management (IAM) in Cloud Computing: Role-Based Access Control and Federation
- Secure Cloud Migration: Best Practices and Challenges for Enterprises
- Data Encryption and Key Management in Cloud Storage Services
- Cloud Security Posture Assessment: Tools and Frameworks for Evaluating Cloud Security Controls
Mobile Security:
- Mobile Application Security Assessment: Vulnerability Analysis and Penetration Testing
- Secure Mobile Device Management (MDM) Solutions: Implementation and Performance Evaluation
- Threats and Countermeasures in Mobile Payment Systems: Securing Transactions on Mobile Platforms
- Biometric Authentication on Mobile Devices: Challenges and Solutions for Ensuring Security and Usability
- Mobile Threat Intelligence and Detection: Machine Learning Approaches for Mobile Threat Analysis
IoT Security:
- Security Challenges in Industrial IoT (IIoT) Environments: Protecting Critical Infrastructure Systems
- IoT Device Authentication and Access Control Mechanisms: Secure Bootstrapping and Provisioning
- Privacy-Preserving Techniques for IoT Data Analytics: Preserving Anonymity and Confidentiality in IoT Systems
- Secure Firmware Update Mechanisms for IoT Devices: Ensuring Integrity and Authenticity of Updates
- Blockchain-Based Solutions for IoT Security: Decentralized Trust and Immutable Audit Trails
Cyber Warfare and National Security:
- Cyber Threat Intelligence Sharing among Nation States: Challenges and Opportunities
- Offensive Cyber Operations: Legal and Ethical Considerations in Conducting Cyber Warfare
- Critical Infrastructure Protection in the Age of Cyber Warfare: Strategies for Resilience and Recovery
- Cyber Deterrence Strategies: Assessing the Effectiveness of Deterrence in Cyberspace
- Cyber Espionage and Cyber Attribution: Techniques for Identifying State-Sponsored Cyber Attacks
Artificial Intelligence and Cybersecurity:
- Adversarial Machine Learning: Defending Against Adversarial Attacks on AI Models
- AI-Driven Cyber Threat Hunting: Leveraging Machine Learning for Proactive Threat Detection
- Explainable AI (XAI) in Cybersecurity: Interpretable Models for Transparent Decision Making
- AI-Enabled Security Orchestration, Automation, and Response (SOAR) Platforms: Enhancing Incident Response Capabilities
- Ethical Considerations in AI-Driven Cybersecurity: Addressing Bias, Fairness, and Accountability
More Related Posts:
- Information Systems Dissertation Topics Ideas
- Which topics are best for thesis in Computer Science?
- Science Research Topics Ideas and Examples
In conclusion, the diverse landscape of cyber security dissertation topics offers ample opportunities for academic exploration and practical contributions to the field. From network security and cryptography to privacy protection, cybercrime investigation, and emerging areas like cloud security, mobile security, and IoT security, the breadth and depth of research possibilities are vast.
By addressing these cyber security dissertation topics, researchers can not only advance our understanding of cyber threats and vulnerabilities but also develop innovative solutions to safeguard digital assets, protect privacy, and ensure the resilience of critical infrastructure.
Moreover, as cyber threats continue to evolve, ongoing research in areas such as AI-driven security, cyber warfare, and the human factor in cybersecurity remains essential to staying ahead of adversaries. Ultimately, through rigorous inquiry and interdisciplinary collaboration, cyber security researchers can play a pivotal role in shaping a more secure and resilient digital future.
Customize Cyber Security Dissertation Topics Brief Service
WhatsApp and Get 35% off promo code now!
ADVANCES IN NETWORK SECURITY: A COMPREHENSIVE ANALYSIS OF MEASURES, THREATS, AND FUTURE RESEARCH DIRECTIONS
- August 2023

- Ajay Kumar Garg Engineering College

- Galgotias College of Engineering and Technology (GCET)
Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
- Hussein Ahmad Al-Ofeishat

- NEURAL NETWORKS

- Preeti Sinha

- Victor Clincy

- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up

Network Security Research Topics for MS PhD
Network security research topic ideas for ms, or ph.d. degree.
I am sharing with you some of the research topics regarding Network Security that you can choose for your research proposal for the thesis work of MS, or Ph.D. Degree.
- CompTIA security+ guide to network security fundamentals
- A survey of moving target defenses for network security
- Modeling network security: Case study of email system
- Programmable In-Network Security for Context-aware {BYOD} Policies
- Composite metrics for network security analysis
- Network security analysis using big data technology and improved neural network
- CPT‐TODIM method for bipolar fuzzy multi‐attribute group decision making and its application to network security service provider selection
- Optical network security management: requirements, architecture, and efficient machine learning models for detection of evolving threats
- Classifying anomalies for network security
- Cloud integrated IoT enabled sensor network security: research issues and solutions
- Bio-Inspired Network Security for 5G-Enabled IoT Applications
- Computer Network Security and Preventive Measures in the Age of Big Data
- Scalable Game-Focused Learning of Adversary Models: Data-to-Decisions in Network Security Games.
- Challenges and Novel Solutions for 5G Network Security, Privacy and Trust
- A Review in Recent Development of Network Threats and Security Measures
- Patterns and Interactions in Network Security
- A Study of Network Security Situational Awareness in Internet of Things
- Data-driven network layer security detection model and simulation for the Internet of Things based on an artificial immune system
- Quantification of distribution network security with high penetration of distributed generators
- NSAPs: A novel scheme for network security state assessment and attack prediction
- Network security and privacy evaluation scheme for cyber physical systems (CPS)
- What to Make of the Huawei Debate? 5G Network Security and Technology Dependency in Europe
- An efficient method for network security situation assessment
- Application of information communication network security management and control based on big data technology
- Augmenting smart home network security using blockchain technology
- Sdn/nfv-based security service function tree for cloud
- Multiple pattern matching for network security applications: Acceleration through vectorization
- Machine Learning, Image Processing, Network Security and Data Sciences: Second International Conference, MIND 2020, Silchar, India, July 30-31, 2020 …
- Network intrusion detection combined hybrid sampling with deep hierarchical network
- An Assessment of Practical Hands-On Lab Activities in Network Security Management
- Cyber Deception for Computer and Network Security: Survey and Challenges
- Computer Network System Security Management and Maintenance Strategy
- Deep Learning for Security Problems in 5G Heterogeneous Networks
- Reference architecture of the telecom network security protection system for cloud network convergence
- Fortified Network Security Perception: A Decentralized Multiagent Coordination Perspective
- Network security prediction model using neural networks
- Machine learning enhanced network security
- Prediction of network security based on DS evidence theory
- Quantitative Evaluation Model of Network Security Situation Based on DS Evidence Theory
- Computer Network Security Based on GABP Neural Network Algorithm
- Decision Support for Mission-Centric Network Security Management
- Strategy of Enterprise Network Security Protection Based on Cloud Computing
- A systematic comparison of mobile Ad-hoc network security attacks
- Research on the Quantitative Assessment and Security Measures of Hierarchical Network Security Threat Situation
- Computer network security countermeasures based on big data
- Network Security-Security Methods in Transnational Corporations (TNC)
- Application of Computer Information Management Technology in Network Security
- Research on network security protection technology of energy industry based on blockchain
- A Comprehensive Study on Machine Learning Algorithms for Wireless Sensor Network Security
- Security Technology of Wireless Sensor Network Based on IPSEC
- Research on Computer Network Security Analysis Modeling Based on Artificial Intelligence Technology
- Network security situation prediction based on grey relational analysis and support vector machine Algorithm
- HMMs based masquerade detection for network security on with parallel computing
- Analysis of Computer Network Security Threat Defense Measures under the Environment of Internet of Things
- Composite Metrics for Network Security Analysis
- Exploiting Channel Distortion for Transmitter Identification for In-Vehicle Network Security
- Network Security Policy for Higher Education Institutions based on ISO Standards
- Implementation of Machine Learning in Network Security
- Research on Computer Network Security Problems and Protective Measures under the Background of Big Data
- Discussion on the Countermeasures of Network Security in Computer Application
- 5G Network Security for IoT Implementation: A Systematic Literature Review
- Research on Enterprise Computer Network Security Protection Technology Based on Information Technology
- Long Term Evolution Network Security and Real-Time Data Extraction
- Computer Network Security Hazards and Preventive Strategies
- Research on Wireless Sensor Network Security Location Based on Received Signal Strength Indicator Sybil Attack
- Research on Industrial Control Network Security Data Acquisition System
- Network Security Issues of Data Link Layer: An Overview
- Multi-source and multi-dimensional network security situational awareness model
- Security Analysis of Public Security Terminal Network and Its Peripheral Equipment
- A novel security model for cooperative virtual networks in the IoT era
- Comprehensive fault simulation method in active distribution network with the consideration of cyber security
- Research on Network Security Trend Prediction Based on Exponential Smoothing Algorithm
- Security monitoring and network management for the power control network
- A Research Journey of Full-Duplex at University of California from Self-Interference Cancellation to Wireless Network Security
- Identifying the Best Network Security Using EDAS
- Improving architectures for automating network security using specification-based protocols
- A Logical Controller Architecture for Network Security
- Network security situation analysis based on a dynamic Bayesian network and phase space reconstruction
- Investigating the Filter Capacity of Linecouplers in KNX regarding network security
- of Network Security: An End-to-End Panorama
- CRYPTOGRAPHY TECHNOLOGY WITH NETWORK SECURITY
- Improving Network Security through Collaborative Sharing
- Information network security construction based on depth learning and modulus algorithm
- Communications and Network Security
- Construction of network security job service model based on rough set data analysis algorithm
- Principles of Adaptive Corporate Network Security Management
- Improvement of network security with the help of security key (Yubikey)
- Reform of Network Security Technology Practice Teaching System Based on Virtual Simulation Training Platform
- Analysis and Evaluation on the Network Security Defense in Power Marketing Industrial Control System
- REAL-TIME TRAFFIC DETECTION AND ANALYSIS OF NETWORK SECURITY INTRUSION ATTACK: SNORT INTRUSION PREVENTION SYSTEM
- Research on Computer Network Security Vulnerabilities and Preventive Measures Based on Multi-Platform
- DEMILITARIZED ZONE AND PORT KNOCKING METHODS FOR COMPUTER NETWORK SECURITY
- Research on Ad Hoc Network Security Risk Assessment Method
- Research on Network Optimization and Network Security in Power Wireless Private Network
- Research on Network Security Active Defense System Oriented to Electric Power Monitoring System
- Development of trusted network and challenges it faces
- Design of College Network Security Management System Based on SNMP Management Model
- High-Performance and Range-Supported Packet Classification Algorithm for Network Security Systems in SDN
- ULTRA-HIGH-SPEED NETWORK SECURITY APPLICATIONS
- Network Security Intelligence Centres for Information Security Incident Management
- Study on Experimental Teaching Virtual Simulation for Network Security and Law Enforcement Major
- Real-time Network Intrusion Detection System with Supporting Cyber Security Regulations for Nuclear Power Plants
- An Analytical Framework for Evaluation of Reliability and Security in Advanced Network Systems
- A Review on Security and Privacy Issues and Challenges in Internet of Things
- Research on the Security Strategy and Technology of Information Resource Network of Chinese Academy Library
- Smart Pillboxes with Network Security
- Network Security using Notable Cryptographic Algorithm for IoT Data
- Security, Controllability, Manageability and Survivability in Trustworthy Network
- A Remote Access Security Model based on Vulnerability Management
- Computer and Network Security
- Network Security Situation Prediction in Software Defined Networking Data Plane
- A Data Fusion Framework of Multi-Source Heterogeneous Network Security Situational Awareness Based on Attack Pattern
- Software-Defined Network Security over OpenStack Clouds: A Systematic Analysis.
- Research on the Application of Deep Learning in Computer Network Information Security
- Research on the game of network security attack‐defense confrontation through the optimal defense strategy
- Leveraging Virtual Labs for Personalised Group-based Assessment in a Postgraduate Network Security and Penetration Testing Module
- On the Improvement of the Stipulation of the Crime of Refusing to Fulfill the Obligation of Information Network Security Management
- The Exploration and Research of the Network Security Offense and Defense Laboratory Cooperated by Schools and Enterprises under the Background of New …
- Network Layer Security Detection Model of Internet of Things Based on Immune System
- Security Analysis of Wireless Local Area Network (WLAN) Network with the Penetration Testing Method
- Network Security Enabled Arduino Devices for Military Communication
- Research on Information Security Monitoring and Early Warning Mechanism of Internet Application Network Based on Particle Swarm Optimization
- Key Technology Analysis of Malicious Code Emergency Response in Computer Communication Network Security
- Network Security Cryptographic Protocols and Lattice Problems
- Network Security Situation Prediction based on Combining 3D-CNNs and Bi-GRUs.
- Intelligent detection system of asset security vulnerability hidden danger under multiple and heterogeneous Web network
- Construction of Compound DDOS Network Security System Based on PKI and CA Authentication
- Construction and Research of Comprehensive Management Platform for Network Security of China University Information System
- A Quantitative Study: Using the Latin Square Design Model in the Prioritization of Network Security Threats
- Topological Data Analysis for Evaluation of Network Security Data
- Quadratic Poly Certificateless Inductive Signcryption for Network Security
- Research on Network Information Security Issues and Strategies under the Internet Plus Environment
- A Review paper on Network Security and Cryptography
- Research Productivity of Publications towards IoT in Network Security
- Application of target tracking and abnormal target detection algorithm in power network security
- A New Experiment Teaching Mode for Network Security & Law Enforcement Major to Meet the Need of New Engineering Talent Training
- Analysis of Information Security Protection of Power System Computer Network
- A Conceptual Model for the Implementation of Cyber Security Measures in a Process Control Network Environment
- Network security defense model based on firewall and IPS
- Encryption and Decryption for Network Security Using Reverse Context-Free Grammar Productions
- Wireless Sensor Network Security for Smart Home IoT Systems
- Security in SDN: A comprehensive survey
- Zero Trust Network Security Model in containerized environments
- Research on Situation Awareness of Universities’ Network Information Security in the Big Data Environment
- Applying network analysis to explore the global scientific literature on food security
- ” 5G network security”.
- Study on the Training Mode of Network Security Practical Talent in Vocational and Technical College Based on Gamification and Leveling up
- Exploring Network Security Using Vigenere Multiplicative Cipher Encryption and Implementation
- Adversarial detection games in network security applications with imperfect and incomplete information
- Learning to upgrade internet information security and protection strategy in big data era
- Computer Network Information Security and Protection Strategy
- Information Encryption Algorithm in Power Network Communication Security Model
- Research on Campus Network Security Problem and Protection Strategy
- Anonymization of Event Logs for Network Security Monitoring
- Self-corrected coefficient smoothing method based network security situation prediction
- CS 646-102: Network Protocols Security (Revised for Remote Learning)
- Special issue on security and privacy in network computing
- Security region of natural gas network in electricity-gas integrated energy system
- Forecasting Security Alerts Based on Time Series
- A composable security treatment of the lightning network
- Cloud Security Issues &Network Security in Private Cloud
- 5G carrier network data collection and security management evolution ideas
- UNSW-NB15 Computer Security Dataset: Analysis through Visualization
- 5G network slicing: a security overview
- New Security Management Scheme for Software-Defined-Networks
- In-vehicle network intrusion detection using deep convolutional neural network
- Security for mobile edge cloud
- Critical infrastructure under attack: lessons from a honeypot
- The Development of Artificial Intelligence Technology And Its Application in Communication Security
- Moving Target Defense to set Network Slicing Security as a KPI
- Computer Security Vulnerabilities and Preventive Measures
- Security-aware virtual network embedding algorithm based on reinforcement learning
- A cloud-fog-edge closed-loop feedback security risk prediction method
- A Matter of Life and Death: Analyzing the Security of Healthcare Networks
- Security Risk Analysis based on Data Criticality
- Security and privacy in vehicular ad hoc network and vehicle cloud computing: a survey
- Powerless Security
- Security design and application of Internet of things based on asymmetric encryption algorithm and neural network for COVID-19
- Research on intelligent cyber security protection for electric power dispatching and control system
- Machine learning threatens 5G security
- Technological Tools for Data Security in the Treatment of Data Reliability in Big Data Environments
- Blockchain-Enabled Distributed Security Framework for Next-Generation IoT: An Edge Cloud and Software-Defined Network-Integrated Approach
- Real-time task scheduling and network device security for complex embedded systems based on deep learning networks
- Management Innovation of Network Society Based on Big Data
- Who’s that knocking at the door? The problem of credential abuse
- Consumer IoT: Security vulnerability case studies and solutions
- New Security System Development Universally Applicable and Enforceable
- The state‐of‐the‐art in container technologies: Application, orchestration and security
- Network slicing in 5G and the security concerns
- Research on Computer Security Protection Technology Based on Information
- Research of Security Routing Protocol for UAV Communication Network Based on AODV
- Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study
- Hybrid analysis of android apps for security vetting using deep learning
- Mobility enabled security for optimizing IoT based intelligent applications
- Providing Information Security on the Base of Artificial Immune System for Industrial Internet of Things
- A Survey of The Design and Security Mechanisms of The Wireless Networks and Mobile Ad-Hoc Networks
- An enhanced anonymity resilience security protocol for vehicular ad-hoc network with scyther simulation
- LSWBVM: A lightweight security without using batch verification method scheme for a vehicle ad hoc network
- The limitations in the state-of-the-art counter-measures against the security threats in H-IoT
- Deepopf: A deep neural network approach for security-constrained dc optimal power flow
- Security and privacy challenges in 5G-enabled vehicular networks
- A Zero Trust Network Research Based on Overlay Technology
- 6g white paper: Research challenges for trust, security and privacy
- Blockchains, Cryptocurrency, and Smart Contracts Technology: Security Considerations
- Security information transmission algorithms for IoT based on cloud computing
- The four biggest malware threats to UK businesses
- Are your IT staff ready for the pandemic-driven insider threat?
- Smart security audit: Reinforcement learning with a deep neural network approximator
- Analysis and Research of Enterprise Information System Security Based on e-Commerce
- NETWORK SECURITY & INTERKONEKSI JARINGAN DENGAN L2TP+ IPSEC
- Anomaly Detection for Network Flow Using Immune Network and Density Peak.
- Routing, Wavelength and Time-Slot Assignment Approaches with Security Level in QKD-Enabled Optical Networks
- An intelligent cross layer security based fuzzy trust calculation mechanism (CLS-FTCM) for securing wireless sensor network (WSN)
- A review on IoT security architecture: attacks, protocols, trust management issues, and elliptic curve cryptography
- New Model and Application of Security Region for Metering Device Status Estimation
- Cyber-Physical Security of Powertrain Systems in Modern Electric Vehicles: Vulnerabilities, Challenges and Future Visions
- Accounting Informationization in Computer Network Environment
- TUGAS RESUME SEMINAR ACHIEVING A QUANTUM LEAP IN NETWORK SECURITY
- Research on Security Protection Technology Based on Terminal Information Jump
- Through the lens of code granularity: A unified approach to security policy enforcement
- Discussion and Analysis of Computer Information Data Security and Encryption Technology
- ZSM security: Threat surface and best practices
- Optimal network defense strategy selection based on Bayesian game
- Architecture of Security Protection technology for Aviation Cyberspace
- Selection of intermediate routes for secure data communication systems using graph theory application and grey wolf optimisation algorithm in MANETs
- Hybrid intrusion detection system using machine learning
- Cyber-security on smart grid: Threats and potential solutions
- Information Security Applications
- Comparative analysis of ML classifiers for network intrusion detection
- A Network Traffic Classification Method Based on Hierarchical Clustering
- Security architecture for defining and enforcing security profiles in dlt/sdn-based iot systems
- Exploring the Storj Network: a Security Analysis
- Designing a cyber-security culture assessment survey targeting critical infrastructures during covid-19 crisis
- Security and trust in blockchains: Architecture, key technologies, and open issues
- Efficient signal and protocol level security for network communication
- Intrudtree: a machine learning based cyber security intrusion detection model
- Self-aware networks that optimize security, QoS, and energy
- Network Traffic Control Using AI
- Predicting the adoption of a mobile government security response system from the user’s perspective: An application of the artificial neural network approach
- A Hybrid Framework for Security in Cloud Computing Based on Different Algorithms
- Modeling the impact of network connectivity on consensus security of Proof-of-Work blockchain
- Software-defined network (SDN) data plane security: issues, solutions, and future directions
- Intelligent security and optimization in Edge/Fog Computing
- 5G network slicing with QKD and quantum-safe security
- Safety Situation Assessment of Underwater Nodes Based on BP Neural Network
- Security and Privacy Concerns in Wireless Networks-A Survey
- Federating Tactical Edge Networks: Ways to Improve Connectivity, Security, and Network Efficiency in Tactical Heterogeneous Networks
- Critical analysis of security and privacy challenges for the Internet of drones: a survey
- Towards a Security Enhanced Virtualised Network Infrastructure for Internet of Medical Things (IoMT)
- Robust detection for network intrusion of industrial IoT based on multi-CNN fusion
- Smart city-based e-commerce security technology with improvement of SET network protocol
- Security issues in cloud computing
- New Ways of Implementing Cyber Security to Help in Protecting America
- Spacechain: a three-dimensional blockchain architecture for IoT security
- Effective attack detection in internet of medical things smart environment using a deep belief neural network
- Innovation and risk walk hand-in-hand with 5G and IoT
- A Comprehensive Mechanism of MANET Network Layer Based Security Attack Prevention
- Managing endpoints, the weakest link in the security chain
- Power system reserve scheduling with wind farm integration considering robust security constraints
- IoT Security: Simulation and Analysis of TCP SYN Flooded DDOS Attack using WireShark
- Machine learning based solutions for security of Internet of Things (IoT): A survey
- An efficient Lightweight integrated Blockchain (ELIB) model for IoT security and privacy
- Targeted cyber attacks: how to mitigate the increasing risk
- Data Security Risk and Preventive Measures of Virtual Cloud Server Based on Cloud Computing
- Attacks and Security Measures in Wireless Sensor Network
- The Exploration of the Training Mode in the Major of Information Security in University
- Towards {HTTPS} Everywhere on Android: We Are Not There Yet
- Comprehensive analysis of MQTT 5.0 susceptibility to network covert channels
- Analysing and forecasting the security in supply-demand management of Chinese forestry enterprises by linear weighted method and artificial neural network
- Image transformation network for privacy-preserving deep neural networks and its security evaluation
- TLS-level security for low power industrial IoT network infrastructures
- A comprehensive report on security and privacy challenges in Software as a Service
- Big data analytics in cyber security: Network traffic and attacks
- Security of HyperLogLog (HLL) cardinality estimation: Vulnerabilities and protection
- Security Clustering Algorithm Based on Integrated Trust Value for Unmanned Aerial Vehicles Network
- Solving the security problem of intelligent transportation system with deep learning
- Analysis of security and energy efficiency for shortest route discovery in low‐energy adaptive clustering hierarchy protocol using Levenberg‐Marquardt neural network …
- Topological analysis of bitcoin’s lightning network
- Modeling network architecture: a cloud case study
- Security architectures in wireless sensor network
- Physical layer security of a two way relay based mixed FSO/RF network in the presence of multiple eavesdroppers
- Research on Model of Assessing Security Situation for Industrial IoT
- Physical Layer Security for UAV Communications
- Methods and Techniques for Dynamic Deployability of Software-Defined Security Services
- Security Analysis of Two Unbalancing Pairing-free Identity-based Authenticated Key Exchange Protocols
- Research on Ideological and Political Education of College Students Based on Network Information Security
- Security and privacy challenges in vehicular ad hoc networks
- Security of RPL based 6LoWPAN Networks in the Internet of Things: A Review
- ATTDC: An active and trace-able trust data collection scheme for industrial security in smart cities
- TD²SecIoT: Temporal, Data-Driven and Dynamic Network Layer Based Security Architecture for Industrial IoT.
- A review of machine learning approaches to power system security and stability
- Review on the security threats of internet of things
- Internet of Things: A Secure Cloud-Based MANET Mobility Model
- Research on the technology of artificial intelligence in computer network under the background of big data
- IoT security: Advances in authentication
- Open source and security: why transparency now equals strength
- Exploration on the Diversified Cultivation of Cyber Space Security Talent in Higher Vocational Colleges under the Background of the Fusion of Production and …
- Deep recurrent neural network for IoT intrusion detection system
- Social network analysis and mining: privacy and security on Twitter
- An efficient XGBoost–DNN-based classification model for network intrusion detection system
- Modified zone based intrusion detection system for security enhancement in mobile ad hoc networks
- How data can be the lingua franca for security and IT
- A comprehensive survey: Benefits, services, recent works, challenges, security, and use cases for sdn-vanet
- Securing of Unmanned Aerial Systems (UAS) against security threats using human immune system
- TNSR security networking software: Basic configuration of a security solution
- A support system for civil aviation navigation equipment security management
- Unmanned Systems Security: Models, Challenges, and Future Directions
- Study of artificial neural networks in information security risk assessment
- Identifying and mitigating security risks for secure and robust NGI networks
- Wireless Sensor Network in Agriculture: Model of Cyber Security
- Automated Deployment of a Security Operations Center
- Deep Q-Network for Enhanced Data Privacy and Security of IoT Traffic
- 12th International Symposium on Foundations and Practice of Security, Toulouse, 05/11/19-07/11/19
- Security challenges of Internet of Underwater Things: A systematic literature review
- Methodology for complex security
- Security and channel noise management in cognitive radio networks
- Review of Physical Layer Security Technology in Battlefield Network
- Survey on the internet of vehicles: Network architectures and applications
- iOS, Your {OS}, Everybody’s {OS}: Vetting and Analyzing Network Services of iOS Applications
- Demystifying internet of things security: successful iot device/edge and platform security deployment
- Research on Index System Construction and Assessment Methods of Distribution Network CPS Security Against Cyber Attack
- Stochastic two-stage reliability-based Security Constrained Unit Commitment in smart grid environment
- Integrating complex event processing and machine learning: An intelligent architecture for detecting IoT security attacks
- Optimising storage processes to reduce the risk of ransomware
- An ANP-GRA-based evaluation model for security features of IoT systems
- SDARP: Security based Data Aware Routing Protocol for ad hoc sensor networks
- Convolutional neural network-based feature extraction using multimodal for high security application
- Security offloading network system for expanded security coverage in IPv6-based resource constrained data service networks
- Security-Aware Carrier Network Planning
- Addressing security and privacy issues of IoT using blockchain technology
- Ensuring security framework for WBANs
- Network information theoretic security
- Improving CAN bus security by assigning dynamic arbitration IDs
- A Canvass of 5G Network Slicing: Architecture and Security Concern
- Operational technology security–a data perspective
- Towards security-Aware 5G slice embedding
- Review of security challenges in healthcare internet of things
- Mobile Payment Security in the Context of Big Data: Certificateless Public Key Cryptography
- Practical Security for Cooperative Ad Hoc Systems
- Improving the Security and Reliability of Embedded Networks With TTMAC-CAN
- A Voice Signal Interpreter using Machine Learning Techniques
- The 2020 Data Breach Investigations Report–a CSO’s perspective
- Security and Privacy for Mobile Edge Caching: Challenges and Solutions
- On Development of a Game‐Theoretic Model for Deception‐Based Security
- Advanced malicious beaconing detection through AI
- What does ‘secure by design’actually mean?
- Advanced metering infrastructures: security risks and mitigation
- Sdn-based vanets, security attacks, applications, and challenges
- On the Security of a Practical Constant-Size Ring Signature Scheme.
- DecChain: A decentralized security approach in Edge Computing based on Blockchain
- Evaluating the performance of the OSCORE security protocol in constrained IoT environments
- LoRaWAN protocol: specifications, security, and capabilities
- Security Approaches in Machine Learning for Satellite Communication
- Keyloggers: silent cyber security weapons
- Security of Cryptocurrencies in blockchain technology: State-of-art, challenges and future prospects
- INSPIRE-5Gplus: Intelligent security and pervasive trust for 5G and beyond networks
- The future of blockchain technology in healthcare internet of things security
- Security and privacy in 6G networks: New areas and new challenges
- Security and Privacy of Lightning Network Payments with Uncertain Channel Balances
- Security and Communication Network Automatic Analysis Architecture of IoT Malware Samples
- Optimized image processing and clustering to mitigate security threats in mobile ad hoc network.
- A survey on boosting IoT security and privacy through blockchain
- Construction of Innovation and Entrepreneurship Training System for Network Information Security Talents
- Secure Socket Layer (SSL) in the Network and Web Security
- ANALYZING AND EVALUATING THE SECURITY STANDARDS IN WIRELESS NETWORK: A REVIEW STUDY
- Discussion on the Application of 5G Network UAV in Public Security of Smart Cities
- Security Architecture and Protocols for Secure MQTT-SN
- Internet of Things (IoT) enabling technologies, requirements, and security challenges
- Sustainable Infrastructure Monitoring for Security-Oriented Purposes
- Modbus Protocol Based on the Characteristics of the Transmission of Industrial Data Packet Forgery Tampering and Industrial Security Products Testing
- HELAD: A novel network anomaly detection model based on heterogeneous ensemble learning
- Research on term extraction technology in computer field based on wireless network technology
- A Proposed Approach for Wireless Sensor Networks Security
- Network and System Security
- Sports and health big data system based on 5G network and Internet of Things system
- Cloud Computing Security Challenges and Threats
- A Security Protection Method for In-Vehicle Millimeter Wave Radar Network Based on Digital Watermarking Technology
- A security policy model transformation and verification approach for software defined networking
- Data presentation in security operations centres: exploring the potential for sonification to enhance existing practice
- BAT: deep learning methods on network intrusion detection using NSL-KDD dataset
- Secure data storage and recovery in industrial blockchain network environments
- Internet of Things: Evolution and technologies from a security perspective
- Bot mitigation–how gapsin understanding and ownership are exposingbusinesses to greater threats
- Truck platoon security: State-of-the-art and road ahead
- Expansion of {ICS} testbed for security validation based on {MITRE} atT&Ck techniques
- Research and implementation of information security for intelligent distribution network
- Enhancing medical data security via combining elliptic curve cryptography and image steganography
- Security analysis of an automobile controller area network bus
- Towards blockchain-based software-defined networking: security challenges and solutions
- Security Analysis of Hybrid Multi-Carrier Energy Systems
- IoT-KEEPER: Detecting malicious IoT network activity using online traffic analysis at the edge
- Source-Grid-Load Combined Security Assessment of PV-Penetrated Distribution Network
- Fast key-frame image retrieval of intelligent city security video based on deep feature coding in high concurrent network environment
- Enhancing the Robustness and Security Against Various Attacks in a Scale: Free Network
- 5G network-based Internet of Things for demand response in smart grid: A survey on application potential
- Security/stability-based Pareto optimal solution for distribution networks planning implementing NSGAII/FDMT
- POSTER: A Survey of Security Challenges with 5G-IoT
- Computer Network Information Security in the Big Data Era
- Blockchain technology in the future of business cyber security and accounting
- A secure fuzzy extractor based biometric key authentication scheme for body sensor network in Internet of Medical Things
- Identifying the attack surface for IoT network
- Cyber security threats and vulnerabilities: a systematic mapping study
- Security and privacy in social networks: data and structural anonymity
- Nozomi Networks: OT/IoT Security Report
- Analysis of wireless sensor network multi-sensor data fusion security method
- Overview of the mobility related security challenges in LPWANs
- Behavioral and game-theoretic security investments in interdependent systems modeled by attack graphs
- Security provision for vehicular fog computing
- Towards a reliable comparison and evaluation of network intrusion detection systems based on machine learning approaches
- Deep reinforcement learning approach for autonomous vehicle systems for maintaining security and safety using LSTM-GAN
- Security Issues in Fog Environment: A Systematic Literature Review
- A taxonomy of network threats and the effect of current datasets on intrusion detection systems
- Overview and prospect of 5G security
- Ensuring information security as an ideological problem
- A Review on the Security of the Internet of Things: Challenges and Solutions
- Ddosnet: A deep-learning model for detecting network attacks
- Security implications of underlying network technologies on industrial internet of things
- SecONet: A Security Framework for a Photonic Network-on-Chip
- Towards an Insightful Computer Security Seminar
- Bitcoin and blockchain: Security and privacy
- Multidomain security authentication for the Internet of things
- Computer Network Information Security Protection Based on Virtual Private Network
- Addressing cyber security skills: the spectrum, not the silo
- Data Security in Mobile Cloud Computing: A State of the Art Review.
- Security of Wi-Fi as a Key Factor for IoT
- Blockchain technology, improvement suggestions, security challenges on smart grid and its application in healthcare for sustainable development
- What Email Servers Can Tell to Johnny: An Empirical Study of Provider-to-Provider Email Security
- On the security of networked control systems in smart vehicle and its adaptive cruise control
- Smart city development in Taiwan: From the perspective of the information security policy
- Conditional Privacy-Preserving Anonymous Authentication Scheme With Forward Security in Vehicle-to-Grid Networks
- Adhering to privacy by design with identity-as-a-service
- Intelligence, security, and vehicular sensor networks in internet of things (IoT)-enabled smart-cities: An overview
- A survey of DDoS attacking techniques and defence mechanisms in the IoT network
- Overcoming the Security Shortcomings Between Open vSwitch and Network
- Software-Defined Network (SDN) Architecture and Security Considerations for 5G Communications
- Significant Role of Security in IOT Development and IOT Architecture
- Design of a Security Service Orchestration Framework for NFV
- Distb-sdoindustry: Enhancing security in industry 4.0 services based on distributed blockchain through software defined networking-iot enabled architecture
- A Lightweight Internet Sharing Scheme for Sectional Medical Images according to Existing Hospital Network Facilities and Basic Information Security Rules
- Orchestrating SDN Control Plane towards Enhanced IoT Security
- Secure D2D communication for 5G IoT network based on lightweight cryptography
- Security on Blockchain Technology
- Research on security situation assessment algorithm under virtual technology of cloud platform
- A survey on security challenges in cloud computing: issues, threats, and solutions
- An efficient approach for enhancing security in Internet of Things using the optimum authentication key
- Technology Architecture of Smart Grid Information Security Defense System
- Design and implementation of automated IoT security testbed
- DMASK-BAN: Improving the security of body area networks
- A Deep Learning Approach for Detecting Security Attacks on Blockchain.
- Network slicing: Recent advances, taxonomy, requirements, and open research challenges
- Security monitoring of heterogeneous networks for big data based on distributed association algorithm
- When wireless security meets machine learning: Motivation, challenges, and research directions
- Salsa20 based lightweight security scheme for smart meter communication in smart grid
- Security Analysis of Power System Network Based on Complex Network
- A blockchain-enabled deduplicatable data auditing mechanism for network storage services
- A Mobile Crowdsensing Data Security Delivery Model Based on Tangle Network
- Research on Information Security Evaluation Based on Artificial Neural Network
- A study on a security model for the establishment of a non-face-to-face smart work working environment in a physical network separation environment of public …
- Borders of Digital Network Freedom in Public Security Space
- Multilevel Security Framework for NFV Based on Software Defined Perimeter
- Security in low-power wide-area networks: state-of-the-art and development toward the 5G
- Artificial intelligence models in power system analysis
- Random linear network coding based physical layer security for relay-aided device-to-device communication
- Dynamic patterns of terrorist networks: Efficiency and security in the evolution of eleven islamic extremist attack networks
- Comments on “Dropping Activation Outputs with Localized First-Layer Deep Network for Enhancing User Privacy and Data Security”
- Security Method for Internet of Things Using Machine Learning Against Cyber Attacks
- A Study on Wireless Network Management for Security Enhancement
- Convolutional Neural Network Based Sound Recognition Methods for Detecting Presence of Amateur Drones in Unauthorized Zones
- The Security Issues in IoT-Cloud: A Review
- Data Security System for A Bank Based on Two Different Asymmetric Algorithms Cryptography
- Keeping a secure hold on data through modern electronic content management
- Trustworthy image security via involving binary and chaotic gravitational searching within PRNG selections
- Security Concerns during Photo Sharing in Social Network Platforms
- Security schemes based conditional privacy-preserving in vehicular ad hoc networks
- Security Vulnerabilities, Attacks, Threats and the Proposed Countermeasures for the Internet of Things Applications
- Roadmap Toward a Network Infrastructure for Public Safety and Security
- Bluetooth Low Energy Mesh Networks: Survey of Communication and Security Protocols
- A survey on security and privacy issues in edge computing-assisted internet of things
- Energy efficient protocol in wireless sensor network: optimized cluster head selection model
- Security in wireless sensor networks: Issues and challenges
- Computer network simulation with ns-3: A systematic literature review
- Stable Multi-agent Clustering Method to Improve the Security in VANET
- Research on Data Security of Wireless Body Area Network
- Plaintext-related image encryption algorithm based on perceptron-like network
- CS 646-852: Network Protocols Security
- AI-driven zero touch network and service management in 5G and beyond: Challenges and research directions
- Technique for Information Security Based on Controls Established by the SysAdmin Audit, Networking and Security Institute
- Integrating Smartphone Network Architecture and Data Security Techniques to Mitigate Sharp Practices in Non-Profit Organizations
- A study of ensemble methods for cyber security
- Security problems of 5G voice communication
- Security and privacy issues in fog computing for healthcare 4.0
- Applying Smart Security Model to Protect Client Services From the Threats of the Optical Network
- A crowdsourcing method for online social networks security assessment based on human-centric computing
- Security mechanism building for big data based on Trusted Computing
- A stacking ensemble for network intrusion detection using heterogeneous datasets
- Security in a mobile learning environment
- Using the security triad to assess blockchain technology in public sector applications
- Cognitive Radio Network-Based Design and Security Challenges in 5G Communication
- A real-time and ubiquitous network attack detection based on deep belief network and support vector machine
- Entity identification and security solutions in IoT based on PKI and Blockchain technology
- SEPAD–Security Evaluation Platform for Autonomous Driving
- Security of Distributed Machine Learning
- Key business drivers for IoT development and security principles
- LD2FA-PSO: A novel Learning Dynamic Deterministic Finite Automata with PSO algorithm for secured energy efficient routing in Wireless Sensor Network
- A dynamic event-triggered approach to observer-based PID security control subject to deception attacks
- Physical Layer Security for in-Body Wireless Cardiac Sensor Network
- Physical layer security for massive access in cellular Internet of Things
- A Clustering TDMA and Code Block Binding Algorithms to Enhance the Node Energy and Security of the Network
- Critical risk considerations in auto-ID security: Barcode vs. RFID
- SCADA (Supervisory Control and Data Acquisition) systems: Vulnerability assessment and security recommendations
- The IoT security gap: a look down into the valley between threat models and their implementation
- IGAN-IDS: An imbalanced generative adversarial network towards intrusion detection system in ad-hoc networks
- Analyzing the Effects of Ad Hoc Security in MANET with AODV
- Towards the Impact of Security Vunnerabilities in Software Design: A Complex Network-Based Approach
- On the placement of security-related Virtualised Network Functions over data center networks
- Security Issues and Challenges in Cloud Computing-Review
- A Bayesian learning based scheme for online dynamic security assessment and preventive control
- Security threats and countermeasures in software defined network using efficient and secure trusted routing mechanism
- Security issues in IoT and their countermeasures in smart city applications
- Offline witness encryption with semi-adaptive security
- An Overview on Cyber Security Paradigms
- Security Risks and Challenges in IoT-Based Applications
- Adaptive data and verified message disjoint security routing for gathering big data in energy harvesting networks
- Internet of things architecture and security challenges
- Network Power: China’s efford to reshape Asia’s Regional Security Architecture
- Cyber-physical systems security education through hands-on lab exercises
- A Security Concept Based on Scaler Distribution of a Novel Intrusion Detection Device for Wireless Sensor Networks in a Smart Environment
- Testbeds, attacks, and dataset generation for big data cluster: A system application for big data platform security analysis
- Improving Internet of Things (IoT) security with software-defined networking (SDN)
- Evolving deep learning architectures for network intrusion detection using a double PSO metaheuristic
- Riskio: A serious game for cyber security awareness and education
- Cyber Security Risk Analysis and Protection Structure Design for Power Distribution IoT
- Security, privacy and trust of different layers in Internet-of-Things (IoTs) framework
- Hardware Security of the Controller Area Network (CAN Bus)
- The Risk of Facebook Social Media Network on Social Security
- Artificial Intelligence Techniques for Information Security in 5G IoT Environments
- Security and Performance Evaluation of Master Node Protocol in the Bitcoin Peer-to-Peer Network
- How Can IoT Services Pose New Security Threats In Operational Cellular Networks?
- Bio-inspired security analysis for IoT scenarios
- Information Security of Power Plants
- Security and the smart city: A systematic review
- Security Access Solution of Cloud Services for Trusted Mobile Terminals Based on TrustZone.
- Security challenges over cloud environment from service provider prospective
- Development of testbed for cyber-manufacturing security issues
- Image Processing and Post-Data Mining Processing for Security in Industrial Applications: Security in Industry
- Effectiveness of SCADA System Security Used Within Critical Infrastructure
- Statistical in-depth security analysis for Vehicle to everything communication over 5g network
- Security Properties of Light Clients on the Ethereum Blockchain
- Application Research of “Edge-Cloud Collaboration” Architecture in Security Protection of Ubiquitous Power Internet of Things
- IoT Security Using Deception–Measuring Improved Risk Posture
- A systematic literature review of blockchain cyber security
- A Review on Security and Privacy of Internet of Medical Things
- A Security Enhanced 5G Authentication Scheme for Insecure Channel
- Security Attacks In MANET–A Comprehensive Study
- Understanding security in the government’s use of blockchain technology with value focused thinking approach
- A survey of network virtualization techniques for internet of things using sdn and nfv
- A security Assessment of Distribution Network CPS Based on Association Matrix Modeling Analysis
- A methodology for security classification applied to smart grid infrastructures
- Design and Implementation of Full-Scale Industrial Control System Test Bed for Assessing Cyber-Security Defenses
- Improving information security risk analysis by including threat-occurrence predictive models
- Security-enhanced OFDM-PON with two-level coordinated encryption strategy at the bit-level and symbol-level
- Cyber ranges and security testbeds: Scenarios, functions, tools and architecture
- Towards fuzzy anomaly detection-based security: a comprehensive review
- Security issues and challenges in V2X: A Survey
- A multi-stage anomaly detection scheme for augmenting the security in IoT-enabled applications
- … network modeling to estimate upscaled parameters for the Topopah Spring, lava flow, and Tiva Canyon Aquifers at Pahute Mesa, Nevada National Security …
- Regulation and Security Modelling of Essential Services in Network of Information Systems
- Survey on IoT: Security Threats and Applications
- Deep learning and big data technologies for IoT security
- A Concept for Establishing a Security Operations and Training Centre at the Bulgarian Naval Academy
- Analysis of the Information Security Risk Assessment Mechanism Based on the Power System
- Security, cybercrime and digital forensics for IoT
- A Systematic Survey on Software-Defined Networks, Routing Protocols and Security Infrastructure for Underwater Wireless Sensor Networks (UWSNs)
- Feature Selection for Deep Neural Networks in Cyber Security Applications
- Design and implementation of a security system based on ADSL access technology
- Improved Security Particle Swarm Optimization (PSO) Algorithm to Detect Radio Jamming Attacks in Mobile Networks
- Security Threats in 5G Edge Computing Environments
- A Research Paper on Social Engineering and Growing Challenges in Cyber Security
- Has the global expansion of energy markets truly improved energy security?
- Study on Stochastic Differential Game Model in Network Attack and Defense
- Security overhead of random linear network coding in multicast relay networks
- Development of security mechanisms for a remote sensing system based on opportunistic and mesh networks
- Ethereum smart contract security research: survey and future research opportunities
- Cyber-physical security and resiliency analysis testbed for critical microgrids with ieee 2030.5
- Research on Application of Internet of Things Information Security Using Blockchain Technology
- Virtualization Construction of Security Components of Edge IoT Agent Based on Security Requirements
- Assessment of Security Issues in Banking Sector of Libya
- The Technique of Implementation Security into Clinical Internet of Things
- Enlisting human resources to mitigate information security risks
- Understanding the MANET Security Using Various Algorithms and Types
- On the Application of Computer Archives Management System and the Path of Security Maintenance
- Vehicle communication network in intelligent transportation system based on internet of things
- Design and modeling an Adaptive Neuro-Fuzzy Inference System (ANFIS) for the prediction of a security index in VANET
- Analysis of Segregated Witness Implementation for Increasing Efficiency and Security of the Bitcoin Cryptocurrency
- Improved lightweight security approach routing protocol in internet of things
- Understanding the role of incentives in security behavior
- A Sharding Scheme based Many-objective Optimization Algorithm for Enhancing Security in Blockchain-enabled Industrial Internet of Things
- Co-design of dual security control and communication for nonlinear CPS under DoS attack
- Physical layer security in vehicular networks with reconfigurable intelligent surfaces
- SECURING OF THE AD HOC NETWORK BY USING SECURITY PROTOCOL FOR RELIABLE DATA DELIVERY
- A survey on the security of blockchain systems
- Fast image encryption algorithm with high security level using the Bülban chaotic map
- Security Fundamentals for E-Commerce
- A Security Trust Mechanism for Data Collection with Mobile Vehicles in Smart City
- Randomly Elected Blockchain System based on Grouping Verifiers for Efficiency and Security
- 5G vehicular network resource management for improving radio access through machine learning
- Five Years of Cyber Security Education Reform in China
- Maintenance and Security System for PLC Railway LED Sign Communication Infrastructure
- Privacy and security issues in the future: A social media
- Mix Networks: Existing Scenarios and Future Directions on Security and Privacy
- SDN Based Security in Mobile Ad hoc Networks
- On safeguarding privacy and security in the framework of federated learning
- Security in cognitive radio network: defense against primary user emulation attacks using genetic artificial bee colony (GABC) algorithm
- Security and privacy for green IoT-based agriculture: Review, blockchain solutions, and challenges
- 6G: Opening new horizons for integration of comfort, security, and intelligence
- Topology-free optimal power dispatch for distribution network considering security constraints and flexible building thermal inertia
- MARGINAL PROBABILITIES OF PERSONAL DATA SECURITY AND USER INTERACTION IN THE SOCIAL NETWORK
- Region model and application of regional integrated energy system security analysis
- Performance of the Transport Layer Security Handshake Over 6TiSCH
- The role of computer security management in preventing financial technology risks
- SECURITY RISK ASSESSMENT OF TURKEY’S ROAD NETWORK
- Critical success factors to create 5G networks in the smart cities of India from the security and privacy perspectives
- Comparative analysis of a new VSC‐optimal power flow formulation for power system security planning
- A comprehensive insight into game theory in relevance to cyber security
- An experimental analysis of security vulnerabilities in industrial IoT devices
- Enhancing SCADA System Security Via Spiking Neural Network
- Cyber security awareness, knowledge and behavior: a comparative study
- A security‐driven network architecture for routing in industrial Internet of Things
- Scope and Limitations of Ethical Hacking and Information Security
- ANALYSIS OF SECURITY FOR CLOUD COMPUTING
- An anomaly detection framework for cyber-security data
- Cyber-Physical Systems Security Introductory Course for STEM Students
- A Research of Distributed Security and QoS Testing Framework
- Using deep learning to solve computer security challenges: a survey
- A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT
- Independent Co-Assurance using the Safety-Security Assurance Framework (SSAF): A Bayesian Belief Network Implementation for IEC 61508 and Common …
- Towards 5G-based IoT security analysis against Vo5G eavesdropping
- Context-Aware Autonomous Security Assertion for Industrial IoT
- Combination of D-AHP and Grey Theory for the Assessment of the Information Security Risks of Smart Grids
- Security architecture for cloud-based command and control system in IoT environment
- Convergence of blockchain and artificial intelligence in IoT network for the sustainable smart city
- Cyber-physical systems security: Limitations, issues and future trends
- Security Control Mechanism for Safety Critical Functions Operating on Automotive Controller Area Network
- A novel security protocol for wireless sensor networks with cooperative communication
- Towards a new thermal monitoring based framework for embedded CPS device security
- Improvised Guard for Next Level Security Automated Vehicle Security system using Artificial intelligence and Convolutional Neural Network
- The Development of Method for Evaluation of Information Security Threats in Critical Systems
- Scalability, Consistency, Reliability and Security in SDN Controllers: A Survey of Diverse SDN Controllers
- Security, Privacy Research issues in Various Computing Platforms: A Survey and the Road Ahead.
- Analysis of energy security level in the Baltic States based on indicator approach
- Bobtail: improved blockchain security with low-variance mining
- Moving from blocker to enabler: cloud security and the modern CISO
- Work-in-Progress: Compromising Security of Real-time Ethernet Devices by means of Selective Queue Saturation Attack
- Robust Transmission Network Expansion Planning with Nk Security Criterion and Uncertainty Factors
- DATA, INFORMATION AND IT SECURITY-SOFTWARE SUPPORT FOR SECURITY ACTIVITIES
- The method of Internet of Things access and network communication based on MQTT
- An Intrusion Detection Model for Wireless Sensor Network Based on Information Gain Ratio and Bagging Algorithm.
- A survey on smart agriculture: Development modes, technologies, and security and privacy challenges
- A decentralized scalable security framework for end‐to‐end authentication of future IoT communication
- E-COMMERCE: TRUSTED THIRD PARTY SECURITY MODELS
- Security Challenges in Software Engineering for the Cloud: A Systematic Review
- Packet analysis for network forensics: A comprehensive survey
- Security Information Sharing in Smart Grids: Persisting Security Audits to the Blockchain
- Automation of information security audit in the Information System on the example of a standard “CIS Palo Alto 8 Firewall Benchmark”
- Empirical Use of Network Time Protocol in Internet of Things Devices: Vulnerabilities and Security Measures
- A Survey on Security Mechanisms in IoT
- A survey on internet of things: Applications, recent issues, attacks, and security mechanisms
- A Survey on Wireless Security protocols (WEP, WPA and WPA2)
- Cyber security analysis on a production environment featuring software defined networks.
- Pathways toward a decarbonized future—Impact on security of supply and system stability in a sustainable German energy system
- OREA for improving data packet transmission in wireless sensor networks with cloud security mechanism
- New Frontiers in IoT: Networking, Systems, Reliability, and Security Challenges
- AFLNet: a greybox fuzzer for network protocols
- SADM-SDNC: security anomaly detection and mitigation in software-defined networking using C-support vector classification
- Security of IoT application layer protocols: Challenges and findings
- Access control method using electrocardiogram signal for fog computing security
- Introduction to IoT security
- UDP-Based Active Scan for IoT Security (UAIS).
- ENTERPRISE INFORMATION SECURITY MANAGEMENT SYSTEM BASED ON THE MODERN OBFUSCATION TECHNIQUE FOR MOBILE NETWORK OPERATORS
- Security Concepts Based on IEEE 802.1 X for G. hn Broadband PLC Access Networks
- A Model on IoT Security Method and Protocols for IoT Security Layers
- Mapping Obfuscation-Based PHY Security Scheme for Resource-Constrained Wireless Sensor Network
- A Mode Study on the Integration of Computer Network Technology and College English Curriculum
- MuLViS: multi-level encryption based security system for surveillance videos
- Overview on the Security in 5G Phase 2
- Security of power line communication systems: issues, limitations and existing solutions
- Security Issues in Internet of Things (IoT): A Comprehensive Review
- Does internet security matter for foreign direct investment? A spatial econometric analysis
- A Hybrid Security System for Unmanned Aerial Vehicles
- Security and Performance in IoT: A Balancing Act
- A new network forensic framework based on deep learning for Internet of Things networks: A particle deep framework
- A comprehensive model of information security factors for decision-makers
- A Blockchain-based security model for SDNs
- Computer Security-ESORICS 2020: 25th European Symposium on Research in Computer Security, ESORICS 2020, Guildford, UK, September 14-18, 2020 …
- A taxonomy of Sybil attacks in vehicular ad-hoc network (VANET)
- Research progress on big data security technology
- Network-Mediated Knowledge Spillovers in ICT/Information Security January 2020 Neil Gandal Nadav Kunievsky
- Security of communication in the special communications systems
- Secrecy transmission capacity in mobile ad hoc networks with security-aware Aloha protocol
- A survey of IoT security based on a layered architecture of sensing and data analysis
- On the Assessment of Information Security Ensuring Models of Critical Information Infrastructure Facilities
- A lightweight security scheme for advanced metering infrastructures in smart grid
- Vulnerability Analysis and Security Research of Docker Container
- Security and privacy issues in fog computing
- TBM: A trust-based monitoring security scheme to improve the service authentication in the Internet of Things communications
Research Topics Computer Science
Topic Covered
Top 10 research topics of Network Security | list of research topics of Network Security | trending research topics of Network Security | research topics for dissertation in Network Security | dissertation topics of Network Security in pdf | dissertation topics in Network Security | research area of interest Network Security | example of research paper topics in Network Security | top 10 research thesis topics of Network Security | list of research thesis topics of Network Security| trending research thesis topics of Network Security | research thesis topics for dissertation in Network Security | thesis topics of Network Security in pdf | thesis topics in Network Security | examples of thesis topics of Network Security | PhD research topics examples of Network Security | PhD research topics in Network Security | PhD research topics in computer science | PhD research topics in software engineering | PhD research topics in information technology | Masters (MS) research topics in computer science | Masters (MS) research topics in software engineering | Masters (MS) research topics in information technology | Masters (MS) thesis topics in Network Security.

Related Posts:
- Software Security Research Topics Ideas [MS PhD]
- Network Security topics for presentation
- How to maintain software security and application security
- Network Security MCQs
- Top Selling Famous Recommended Books of Network Security
- List of Journals on Network Security
You must be logged in to post a comment.
- thesis help
- topics to stay away from
- developing a strong topic
- education thesis prompts
- marketing problems to explore
- writing on anaesthesia
- health & psychology
- learning & development
- nursing education problems
- sports history topics
- risk management problems
- writing about wildlife
- good topics on nutrition
- writing on emotional intelligence
- good topics in astrophysics
- great topic suggestions
- dissertation topics in law
- computer engineering topics
- thesis topic solutions in finance
- IR dissertation titles
- Art dissertation topic ideas
- Environmental law thesis title
- Picking topics on interior design
- Business topic ideas to explore
- Chemical engineering topics
- Graphic design thesis titles
- 15 topics on pediatric nursing
- Ideas about network security
- Topics on structural engineering
- Economics dissertation topics
- Selection of topics in finance
- Financial markets topic ideas
- Women's studies thesis topics
- deciding on a title
- the secrets of good writing
- writing a thesis in 5 steps
- structuring your paper
- medical paper samples
- Master's paper samples
- writing a purpose statement
- writing a literature review
- PhD thesis methodology
- Doctoral thesis formatting
- tips for undergraduates
- creating a law dissertation
- writing a medical college thesis
- drafting the conclusion
- PhD thesis paper writing hints
- MBA dissertation writing tips
- A thesis on Martin Luther King
- A thesis paper in criminal justice
- Getting a custom dissertation
- Writing a proposal in history
- How to format a cover page
- Finding a finance thesis sample
- APA format bibliography section
- How to make in-text citations
- Marketing thesis writing guide
- Preparing a defense presentation
- Getting a biology thesis sample
- Marketing dissertation proposal
- Purchasing a thesis on the web
- Writing on evaluation of training
- APA thesis acknowledgements
- Using a dissertation database
- Order a dissertation safely
- writing services

List Of 15 Great Dissertation Topics About Network Security
With the rise of the Internet, many people are asking themselves if the have the best network security or even how it works. That is why this kind of topic has become so popular with graduate students that are preparing their dissertation. Here is a list of fifteen topics that you can use in your dissertation.
15 Network Security Topics
- Pick a hacker and explain their attack and how they did it.
- How was the Rotor Machine developed and how was its algorithm used in World War II.
- How does anti-virus software work and what is the best one to buy?
- How does NIST develop security algorithms?
- How are security algorithms verified?
- Should the United States and the rest of the world have different standards for encryption?
- How can wireless connections and devices be made safer?
- What went on developing the algorithm for MD4?
- What should the steganography be used for in the modern day?
- How well do random number generation algorithms work today and what can be done to improve them?
- How is biometrics going to be used in security in the future?
- What does the future look like with parallel machines network security if they become commonplace in society?
- Are your security algorithms in your web browser good enough to protect you?
- What is the best way to protect copyright on movies and video games and are digital signatures enough?
- Secure passwords are the best to protect you from prying eyes but can be difficult to remember. Is there a difference between convenience and security when you create a password?
Network security is a great topic to cover for your dissertation and if you pick the right topic, you will engage your audience and keep them thinking about their own network security as they read it. The great thing about this topic is that there are millions of topic to cover and if you start your search online, you will find almost all of the information you need. We use electronic devices every day that are connected to the Internet and we are all vulnerable to security attacks on all of our devices. These kinds of attacks can change lives and that is why you need to know as much as you can on network security to keep all of your information safe from hackers that want to steal it.
Popular Blogs
Tips and tricks.
- Thesis proposal sample related to tourism
- Where to get affordable assistance
- Crafting the introductory section
- 5 places to get free samples
- A winning results section
- Writing a paper in physics
- Where to find sample Master's proposals
- MBA dissertation proposal examples
- Discovering US history topics
- How to stay on the right track
- Free dissertation prospectus examples
- Working on an HRM degree paper
- APA formatting instructions
- Getting a dissertation template
- Creating a solid paper in a month
- Hiring a dissertation writer
- Writing a report on marketing
- Writing an introduction
- 3 places to get MBA paper samples
- How to buy papers at a low cost
- Professional thesis writing manual
- Creating the discussion section
- Searching for thesis paper writing help
- Where to find someone who will do my thesis
- Organizing a law thesis methods section
- Studying history questions
- PhD paper prospectus samples
- Custom writing services
- How to select an academic writing company
- Acknowledgement templates
- Geography thesis conclusion section
2024 ©. All Rights Reserved. Morey-Editions.com.
283 Hottest Cybersecurity Research Topics & Questions [2024]
Your computer stores your memories, contacts, and study-related materials. It’s probably one of your most valuable items. But how often do you think about its safety?
Cyber security is something that can help you with this. Simply put, it prevents digital attacks so that no one can access your data. Do you want to write a research paper related to the modern challenges of cyberspace? This article has all you need. In here, you’ll find:
- An overview of cyber security’s research areas.
- A selection of compelling cyber security research topics.
And don’t hesitate to contact our custom writing team in case you need any assistance!
- 🔝 Top 10 Topics
- ✅ Research Areas
- ⭐ Top 10 Cybersecurity Topics
- 🔒 Technology Security Topics
- 🖥️ Cybercrime Topics
- ⚖️ Cyber Law & Ethics Topics
- 👨💻 Thesis Topics
- 🎓 Research Paper Topics
- 💽 Topics for Presentation
- ❓ Research Questions
- 💡 Debate Topics
- ✨ Interesting Topics
🔍 References
🔝 top 10 cyber security research topics.
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- The importance of end-user education
- Cloud security posture management
- Do biometrics ensure security of IPhones?
- Can strong passwords protect information?
- Is security in critical infrastructure important?
✅ Cyber Security Topics & Research Areas
Cyber security is a vast, constantly evolving field. Its research takes place in many areas. Among them are:
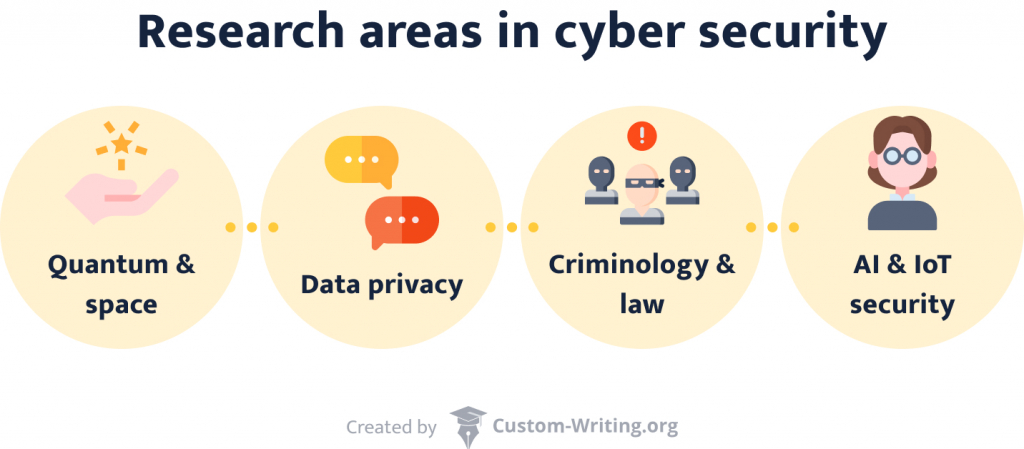
- Safe quantum and space communications . Progress in quantum technologies and space travel calls for extra layers of protection.
- Data privacy. If someone’s personal information falls into the wrong hands, the consequences can be dire. That’s why research in this area focuses on encryption techniques.
- (Inter)national cyberethics, criminology, and law. This branch analyzes how international legal frameworks work online.
- AI and IoT security . We spend more and more of our daily lives online. Additionally, our reliance on AI increases. This scientific field strives to ensure a safe continuation of this path.
As you can see, cyber security extends in various exciting directions that you can explore. Naturally, every paper needs a cover page. We know that it’s one of the more annoying parts, so it’s not a bad thing to use a title page generator for your research paper . Now, let’s move on to our cyber topics list.
⭐ Top 10 Cybersecurity Topics 2024
- Is removable media a threat?
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How to prevent phishing attacks
- Physical security measures in banks
- Security breaches of remote working
- How does two-factor authentication work?
- How to prevent social engineering attacks
- Cybersecurity standards for automotive
- Privacy settings of social media accounts
🔒 Computer Security Topics to Research
Safe computer and network usage is crucial. It concerns not only business but also individuals. Security programs and systems ensure this protection. Explore them with one of our topics:
- How do companies avoid sending out confidential information? Sending an email to the wrong person has happened to the best of us. But what happens if the message’s contents were classified? For your paper, you can find out what technologies can prevent such slip-ups.
- What are the best ways to detect malicious activity? Any organization’s website gets plenty of daily traffic. People log in, browse, and interact with each other. Among all of them, it might be easy for an intruder to slip in.
- Internet censorship: classified information leaks. China takes internet censorship to the next level. Its comprehensive protection policies gave the system the nickname Great Firewall of China . Discuss this technology in your essay.
- Encrypted viruses as the plague of the century. Antivirus programs are installed on almost every computer. They prevent malicious code from tampering with your data. In your paper, you can conduct a comparison of several such programs.
- What are the pros and cons of various cryptographic methods? Data privacy is becoming more and more critical. That’s why leading messaging services frequently advertise with their encryption technologies.
- What makes blockchain secure? This technique allows anonymity and decentralization when working with cryptocurrencies. How does it work? What risks are associated with it?
- What are the advantages of SIEM? Security Incident and Event Management helps organizations detect and handle security threats. Your essay can focus on its relevance for businesses.
- What are the signs of phishing attempts?
- Discuss unified cyber security standards in healthcare.
- Compare and contrast various forms of data extraction techniques.
- What do computers need protocols for?
- Debate the significance of frequent system updates for data security.
- What methods does HTTPS use that make it more secure than HTTP?
- The role of prime numbers in cryptography.
- What are public key certificates, and why are they useful?
- What does a VPN do?
- Are wireless internet connections less secure than LAN ones? If so, why?
- How do authentication processes work?
- What can you do with IP addresses?
- Explain the technology of unlocking your phone via facial recognition vs. your fingerprint.
- How do you prevent intrusion attempts in networks?
- What makes Telnet vulnerable?
- What are the phases of a Trojan horse attack?
- Compare the encryption technologies of various social networks.
- Asymmetric vs. symmetric algorithms.
- How can a person reach maximum security in the computer networking world ?
- Discuss autoencoders and reveal how they work.
💾 Information Security Topics to Research
Information security’s goal is to protect the transmission and storage of data. On top of that, network security topics are at the forefront of infosec research. If you’re looking for inspiration on the subject, check out these ideas.
- What are the mechanics of password protection? Passwords are a simple tool to ensure confidentiality. What do users and developers need to keep in mind when handling passwords?
- What are the safest ways to ensure data integrity ? Everybody wants their data to be intact. Accidental or malicious modifications of data can have dire consequences for organizations and individuals. Explore ways to avoid it.
- How can one establish non-repudiation? Non-repudiation proves the validity of your data. It’s essential in legal cases and cyber security.
- How did the advent of these new technologies impact information security ? Mobile networks have changed the way we access information. On a smartphone , everything is permanently available at your fingertips. What adverse consequences did these technologies bring?
- How do big corporations ensure that their database environment stays conflict-free? We expect our computers to always run fast and without errors. For institutions such as hospitals, a smooth workflow is vital. Discuss how it can be achieved.
- Describe solid access control methods for organizations. In a company, employees need access to different things. This means that not everyone should have an admin account. How should we control access to information?
- Medical device cyber security. For maximum safety, it’s best to employ several measures. Protection on the hard- and software side is just a part of it. What are some other means of security?
- Write an argumentative essay on why a career in information security doesn’t require a degree.
- Pros and cons of various infosec certificates.
- Cybersecurity in cruise ship industry
- The influence of remote work on a businesses’ infosec network .
- What should everyone be aware of when it comes to safeguarding private information?
- Select a company and calculate how much budget they should allocate on cyber security.
- What are the dangers of public Wi-Fi networks?
- How secure are cloud services?
- Apple vs. Microsoft : whose systems offer better security?
- Why is it important to remove a USB flash drive safely?
- Is it possible to create an unguessable password?
- Intranet security: best practices.
- Does the use of biometrics increase security?
- Face recognition vs. a simple code: what are the safest locking options for smartphones ?
- How do you recover data from a broken hard drive?
- Discuss the functions and risks of cookies and cache files.
- Online privacy regulations in the US and China.
- Physical components of InfoSec.
- Debate security concerns regarding electronic health records .
- What are unified user profiles, and what makes them potentially risky?
🖥️ Cybercrime Topics for a Research Paper
Knowledge is one of today’s most valuable assets. Because of this, cybercrimes usually target the extraction of information. This practice can have devastating effects. Do you want to learn more about the virtual world’s dark side? This section is for you.
- Give an overview of the various types of cybercrimes today . Cybercriminals are becoming more and more inventive. It’s not easy to keep up with the new threats appearing every day. What threats are currently the most prominent?
- How does cryptojacking work, and why is it problematic? Cryptocurrency’s value explosion has made people greedy. Countries such as Iceland have become a haven for datamining. Explore these issues in your essay.
- Analyze the success rate of email frauds. You’ve probably seen irrelevant ads in your spam folder before. They often sound so silly it’s hard to believe they work. Yet, unfortunately, many people become victims of such scams.
- How did the WannaCry malware work? WannaCry was ransomware that caused global trouble in 2017. It led to financial losses in the billions. What made it so dangerous and hard to stop?
- Give famous examples of cybercrimes that targeted people instead of money. Not all cybercrimes want to generate profit. Sometimes, the reasons are political or personal. Explore several instances of such crimes in your essay. How did they pan out?
- Analyze the implications of the Cyberpunk 2077 leak. The game’s bugs and issues made many people angry. Shortly after its flop, hackers released developer CD Projekt Red’s source codes. What far-reaching consequences could this have?
- Why do hackers commit identity theft? Social media has made it easy to steal identities. Many like to display their lives online. In your paper, research what happens to the victims of identity thefts.
- Should governments punish cybercrimes like real-life crimes?
- How does ransomware work?
- Describe the phases of a DDoS attack.
- What cybercrime cases led to changes in the legislature?
- Track the evolution of online scams.
- Online grooming: how to protect children from predators.
- Are cybercrimes “gateway crimes” that lead to real-life misbehavior?
- What are man-in-the-middle attacks?
- Big data and the rise of internet crimes.
- Are cybercrimes more dangerous to society than they are to corporations?
- Is the internet increasing the likelihood of adolescents engaging in illegal activities?
- Do the downsides of cyberlife outweigh its positives?
- Is constantly checking your crush’s Facebook page cyberstalking?
- How do you recognize your online date is a scam?
- Describe what happens during a Brute Force attack.
- What’s the difference between pharming and phishing?
- The Lehman Bank cybercrimes.
- Should the punishments for cybercriminals be harsher than they are now?
- Compare various types of fraud methods .
- How do you mitigate a denial-of-service attack?
🕵️ Topics for a Research Paper on Hacking
Blinking screens and flashing lines of code: the movie industry makes hacking look fascinating. But what actually happens when someone breaks into another person’s computer’s system? Write a paper about it and find out! The following prompts allow you to dive deeper into the subject.
- Is it vital to keep shutting down online movie streaming sites? Many websites offer free movie streaming. If one of their domains gets closed down, they just open another one. Are they a threat to the industry that must be stopped? Or should cyber law enforcement rather focus on more serious crimes?
- Explore the ethical side of whistleblowing. WikiLeaks is a platform for whistleblowers. Its founder, Julian Assange, has been under arrest for a long time. Should whistleblowing be a crime? Why or why not?
- How did Kevin Mitnick’s actions contribute to the American cyber legislature? Mitnick was one of the US’s first most notorious hackers. He claimed to have broken into NORAD’s system. What were the consequences?
- Examine how GhostNet operates. GhostNet is a large organization attacking governments. Its discovery in 2009 led to a major scandal.
- Describe how an SQL injection attack unfolds. Injection attacks target SQL databases and libraries. This way, hackers gain unauthorized access to data.
- What political consequences did the attack on The Interview imply? In 2014, hackers threatened to attack theaters that showed The Interview . As a result, Sony only showed the movie online and in limited releases.
- Write about cross-site request forgery attacks. Every website tells you that logging out is a crucial step. But what can happen if you don’t do it?
- What is “Anonymous,” and what do they do?
- Is it permissible to hack a system to raise awareness of its vulnerabilities?
- Investigate the origins of the hacking culture.
- How did industrial espionage evolve into hacking?
- Is piracy destroying the music and movie industries ?
- Explain the term “cyberwarfare.”
- Contrast different types of hacking.
- Connections between political protests and hacking.
- Is it possible to create an encryption that can’t be hacked?
- The role of hackers in modern warfare .
- Can hacking be ethical?
- Who or what are white hat hackers?
- Discuss what various types of hackers do.
- Is jailbreaking a crime?
- How does hacking a phone differ from hacking a computer?
- Is hacking your personal home devices problematic?
- What is clickjacking?
- Why would hackers target newspapers?
- Examine the consequences society would have to bear if a hacker targeted the state.
- Compare and analyze different hacking collectives.
⚖️ Topics on Cyber Law & Ethics to Look Into
Virtual life needs rules just like the real one does. The online world brings a different set of values and issues to the table. And, naturally, cyberlife has a legal framework. That’s where researching cyber law and ethics comes into play.
- Is it ethical that governments can always access their citizens’ data? In some countries, online platforms for personal information are standard. From medical exams to debts, everything is available with a click. The system is inarguably convenient. But what about its downsides?
- Is it still morally permissible to use Spotify ? Spotify has made listening to music more accessible than ever. However, artists only receive a tiny fraction of the company’s profits. Discuss the implications of this fact.
- Should internet forums require users to display their real names? Online harassment is a widespread problem. Nicknames hide the identities of ordinary users as well as perpetrators. Can the mandatory use of real names change the situation?
- Analyze online gaming behavior from a psychological standpoint. If one wants to play online games, one needs to have a thick skin. The community can be harsh. You can dedicate your paper to exploring these behaviors. Or you might want to ponder what game publishers can do to reduce hate speech.
- What type of restrictions should sellers implement to prevent domain speculation? Some people buy domains hoping that they will sell them later for more money. This practice makes registering a new website trickier.
- Does the internet need regulations to make adult content less visible? Every computer without parental control can access pornographic websites. Most of them don’t require registration. Their contents can be disturbing, and their ads can appear anywhere. What can be done about it?
- What are cyber laws still missing in America? The US has established many laws to regulate internet usage. Select the most significant ones and explain their relevance.
- Why should cyber ethics be different from real-world norms?
- Are there instances in which illegal downloading is justified?
- The rule of law in real life vs. in cyberspace.
- Does the internet need a government?
- What is cyber terrorism, and what makes it dangerous?
- Who is responsible for online misbehavior?
- How binding are netiquettes?
- What did the implementation of the GDPR change?
- Compare and contrast Indian vs. Venezuelan internet regulations.
- What does the CLOUD entail?
- How should law enforcement adapt to online technologies?
- AI applications: ethical limits and possibilities.
- Discuss trending topics in cyber law of the past ten years.
- Should schools teach online etiquette?
- Does internet anonymity bring out the worst in people?
- Is data privacy more important than convenience and centralization?
- Debate whether bitcoins could become the currency of the future.
- How can online consumers protect themselves from fraud?
- Is buying from websites like eBay and Craigslist more ethical than buying from other online marketplaces?
- Present RSF’s Minecraft library and discuss its moral implications.
🖱️ Cyberbullying Topics for Essays and Papers
On the web, everyone can remain anonymous. With this added comfort, bullying rises to another level. It’s a serious issue that’s getting more and more problematic. Cyber security measures can alleviate the burden. Do you want to address the problem? Have a look at our cyberbullying topics below.
- Cyberbullying prevention in online learning environments . Online classes increase the possibility of cyberbullying. What can teachers do to watch out for their students?
- What makes online emotional abuse particularly difficult to bear? Bullying doesn’t necessarily have to be physical to hurt. Statistics show increased suicide rates among students who were harassed online. Explore the reasons behind this phenomenon.
- How can victims of identity theft reclaim their lives? Identity theft leads not only to mental distress. Thieves also have access to credit card information and other essential assets.
- What are the best methods to stay safe online? When surfing the internet, one always has to be on one’s toes. Avoiding harassment and bullying is a particularly challenging task.
- How can parents monitor their children’s behavior on the web? Children are particularly vulnerable online. They might enter dangerous online relationships with strangers if they feel lonely. They are also more susceptible to scams. What can parents do to protect them?
- Cyberbullying among university students. Online abuse in such websites is very common. Everyone can be a potential target, regardless of age or gender. Discuss whether the structure of social networks helps to spread cyberbullying.
- What societal factors contribute to online bullying? Not everyone who uses the internet becomes an abuser. It’s possible to establish several psychological characteristics of cyberbullies. Explore them in your paper.
- Define how cyberbullying differs from in-person harassment.
- Establish a link between feminism and the fight against cyberstalking.
- The emotional consequences of physical vs. verbal abuse.
- The effects of cyberbullying and academics.
- Short vs. long-term mental health effects of internet bullying .
- What are the most widespread means of cyberbullying?
- Should people who want to play video games online get over the fact that the community is toxic?
- Is defending the freedom of speech more important than preventing the spread of hate speech?
- Reasons and consequences of Amanda Todd’s suicide.
- The dangers of pro-ana/-mia communities for adolescents.
- What are effective strategies to cope with online harassment ?
- Would cyber communism decrease bullying?
- How enhanced cyber security measures can help reduce abuse.
- The importance of parental control mechanisms on children’s computers.
- Traditional vs. cyberbullying in children.
- Do image-heavy websites such as Tumblr and Instagram affect one’s mental state similarly to active abuse?
- What kind of people does cyber abuse affect the most, and why?
- Analyze how the stalker uses the internet in Netflix’s series You .
- Catfishing: effects and solutions.
👨💻 Cyber Security Thesis Topics
- Analysis of ethical hacking. Analyze ethical hacking, its key features, and types. Research real-world cases of ethical hacking along with the legal and ethical issues surrounding it.
- Redefining privacy in the age of cloud reliance. Since more and more people are relying on cloud services for communication and storing information, concerns about data privacy grow. Examine potential regulations and societal changes required to balance privacy and convenience.
- Privacy concerns across key industries. Discuss the implications for personal privacy in sectors like healthcare, finance, and law enforcement. Dwell on the new methods used to bypass biometric authentication systems, such as facial recognition or fingerprint scanners.
- The human cost of cryptocurrency breaches. Explore the economic and psychological consequences of successful attacks on the crypto market. Showcase the efforts of experts to bolster crypto security.
- Potential impact of law enforcement and tech cooperation on cyberattacks. Propose a scenario for a global collaboration between law enforcement agencies and tech companies to track cybercriminals. Analyze the feasibility, logistical challenges, and potential impact of such collaboration.
- The issue of employing weak protocols for encryption.
- Flexible and adaptive electronics and their role in cybersecurity.
- The use of penetration testing in mitigating cyber threats.
- Analyze emerging attacks in the cybersecurity field.
- Risk assessment in cyber-physical systems.
- The ethical side of popular cybersecurity measures.
- Cybersecurity in educational institutions and its characteristics.
- Study the use of smart wearable sensors for protecting user data and ensuring device integrity.
- The laws and regulations of mobile cybersecurity.
- Cybersecurity challenges in the medical industry: protection strategies.
- Suggest possible solutions to digital payment information theft.
- Inefficient data sharing techniques and their consequences.
🎓 Cyber Security Research Paper Topics
- The impact of quantum technologies on cybersecurity. Analyze how the development of quantum technologies could affect the cybersecurity industry. Investigate the possible risks and opportunities.
- Cybersecurity evolution: trends shaping our digital future. In your research paper, discuss the latest trends in the cybersecurity field. Focus on their potential impact on individuals, organizations, and society.
- The security vulnerabilities of IoT. Investigate common security flaws in IoT devices and potential attack vectors. Consider the consequences of using weak passwords and insecure communication protocols.
- Humans and AI as partners in cyber defense. Dwell on the future of human-AI partnership in cybersecurity and the skills required for this collaboration. Discuss potential discrimination risks in AI-driven security systems.
- Personal consequences of cyberattacks. Research how cyberattacks can affect people. Consequences can include financial loss to identity theft and even physical harm. We recommend selecting a specific attack type and clarifying its personal consequences.
- The most effective countermeasures against cyberattacks.
- Network traffic analysis and its role in cyber security.
- Basic procedures for computer forensics and investigations.
- The effectiveness of international cooperation in combating cyber threats.
- Cybersecurity in the field of public administration.
- The nature and dangers of cyber terrorism.
- Anti-phishing technologies and their role in email security.
- The use of machine learning to detect and prevent cyberattacks.
- Ways of optimizing cyber risk management by addressing human vulnerabilities.
- The role of cybersecurity in ensuring industrial safety.
- Wireless hacking techniques and possible ways to counter them.
- The role of blockchain in future wireless mobile networks
💽 Cyber Security Topics for Presentation
- Ethical dilemmas in the digital age. In your presentation, illustrate the potential challenges and ethical considerations associated with cybersecurity. Provide examples of how these technologies can protect against new types of attacks.
- The psychological effects of using the dark web. Show the psychological impact of using the dark web. You can analyze its potential to manipulate, exploit, or offer refuge and support. Find real-life examples to explain how extremist groups and criminal organizations use the dark web to radicalize and recruit vulnerable individuals.
- The role of encryption in protecting information and IoT. Study the fundamental principles of encryption and their role in securing digital information. Discuss how encryption contributes to the security of IoT devices and networks.
- The evolving role of firewalls in cybersecurity. Review the key trends in the evolution of firewall technology and explain how it has adapted to address cyber threats. Highlight the impact of firewalls on cybersecurity for individuals, businesses, and critical infrastructure.
- Measure the cost of cyberattacks across borders. Compare different countries, and industries affected by cyberattacks. Quantify the cost of cybercrime, including stolen funds, business disruption, and downtime.
- The structure of the dark web and its key characteristics.
- Strategies for safe use of public Wi-Fi networks.
- The impact of cybercrime on the economy.
- Popular antivirus programs and their effectiveness in protecting computer systems.
- Trace the development of standards and certifications in the field of cybersecurity.
- Ways of combating fake news and disinformation in cyberspace.
- The effective methods of generating strong passwords.
- Strategies to combat cybercrime in business.
- Cybersecurity professions and their challenges.
- Evaluate the effectiveness of two-factor authentication in account protection.
- Cybersecurity trends: new information protection technologies.
- Principles and types of encryption algorithms in cryptography.
❓ Cyber Security Research Questions
- How can we optimize cybersecurity in schools? Investigate the main factors influencing the effectiveness of cybersecurity in the educational field. Provide actionable tips to protect personal information within the school environment.
- What are the most promising and cost-effective methods to prevent attacks on critical infrastructure? Research innovative methods that prevent attacks on critical infrastructure and ensure its security. Examine the aspects of implementing these innovative methods, including cost and infrastructure compatibility.
- What are the key risks associated with cloud-based platforms in supply chain management? Analyze the risks associated with cloud-based platforms in supply chain management. Then, propose effective security measures for data protection.
- Do legal frameworks adequately address the complexities of state-sponsored cyberattacks? Compare and contrast the legal frameworks surrounding state-sponsored cyberattacks across different countries. Explore the potential for escalation of state-sponsored cyberattacks into armed conflict.
- What are the best practices for secure mobile data exchange on public Wi-Fi? Evaluate the risks associated with public Wi-Fi networks and review the best practices for secure mobile data exchange in these environments. Investigate the role of mobile network operators and device manufacturers in ensuring the security of mobile data exchange.
- How can we ensure security when working with cloud data storage?
- What is the value of continuous user authentication on mobile devices?
- What are the effects of RSA on network security?
- How can we ensure the responsible use of AI in cybersecurity?
- How does using cyberattacks in armed conflicts complicate international norms and legal frameworks?
- What are the benefits of application logging?
- What are the most effective methods for companies to guarantee data security with a remote workforce?
- How can we effectively ensure cybersecurity in the IoT?
- What are the most secure methods of maintaining data integrity?
- What are the best practices for mitigating cyber risks in digital supply chains?
- How can blockchain technologies improve reliability and transparency in cybersecurity?
- What trends and new threats in cyberspace should we expect in the coming years?
💡 Cyber Security Debate Topics
- Face ID: friend or foe? Research the technical security of Face-ID, its strengths and weaknesses. Explain why you consider this technology safe or unsafe, supporting your arguments with statistics and expert opinions.
- How should self-driving cars be regulated? Provide your view on the measures and regulations that should be implemented to ensure the cybersecurity of self-driving cars. Clarify why prioritizing passenger safety and public trust in this emerging technology is essential.
- Unrestricted AI deployment in cybersecurity: benefits and risks. Highlight the potential advantages and disadvantages associated with unrestricted AI deployment in cybersecurity. Can this process speed up threat detection?
- Mandatory reporting of cybersecurity incidents: pros and cons. Provide your opinion on the benefits and drawbacks of compulsory reporting to the public when a company experiences a cybersecurity incident. Support your argument with a real-life example.
- Penalties for cybercriminals: is there room for improvement? Examine the effectiveness of current penalties for cybercriminals. Add your view on how they can be improved, considering the evolving nature of cyber threats.
- Should hackers be helping the FBI?
- What should be done to secure self-driving cars from cyber-attacks?
- Should companies pay ransom to recover stolen data?
- Should international standards be introduced in the field of cyber security?
- Are biometric authentication methods more secure than passwords?
- Should governments use “cyberweapons” as a preventive measure?
- Will synthetic media impact the future of trust and identity in the digital age?
- Should there be restrictions on the use of AI in cybersecurity?
- Is standardized cybersecurity training necessary for all employees?
- Should educational programs include cybersecurity training at all levels?
- Is it ethical for the government to collect information about its citizens?
- Should companies tell the public when they get hacked?
✨ Interesting Topics in Cyber Security
- Security challenges in immersive virtual worlds. Analyze the unique security challenges posed by such environments. Consider technical vulnerabilities and potential social engineering exploits within them.
- Email threats in large companies. Discuss the challenges of identifying and mitigating email-based threats in large organizations. Propose innovative solutions for securing email communication and educating users about email safety.
- Deepfake technology in cyberattacks. Explore the evolving capabilities of deepfake technology and its potential future applications in cyberattacks. Additionally, discuss the challenges of detecting and mitigating deepfakes.
- Strong privacy practices in famous companies. Choose a well-known company that has successfully implemented strong privacy practices. Analyze its methods and explain how they can come in handy for other organizations.
- Private sector partnerships in global cybersecurity. Investigate the role of private sector partnerships in international cybersecurity efforts. Take into account their benefits and potential conflicts of interest.
- Email attacks and their characteristics.
- Study the issue of cybersecurity workforce shortage.
- AI-generated images and their role in the evolution of cyber threats.
- The importance of data privacy discipline.
- Ways to stay safe during online video calls and conferencing.
- The use of synthetic data in creating fake identities.
- Cybersecurity risks of remote working.
- Ways to protect privacy online as a business.
- The rise of ransomware and possible solutions.
- International cooperation in cyber security and its effectiveness.
- Evaluate the weaknesses of cloud-based services.
- The psychological aspects of cyberattacks.
Thanks for reading through our article. If you found it helpful, consider sharing it with your friends. We wish you good luck with your project!
Further reading:
- 220 Best Science and Technology Essay Topics to Write About
- 204 Research Topics on Technology & Computer Science
- A List of 580 Interesting Research Topics [2024 Edition]
- A List of 179 Problem Solution Essay Topics & Questions
- 193 Interesting Proposal Essay Topics and Ideas
- 226 Research Topics on Criminal Justice & Criminology
- What Is Cybersecurity?: Cisco
- Cyber Security: Research Areas: The University of Queensland, Australia
- Cybersecurity: National Institute of Standards and Technology
- What Is Information Security?: CSO Online
- Articles on Cyber Ethics: The Conversation
- What Is Cybercrime?: Kaspersky
- Types of Cybercrime and How to Protect Yourself Against Them: Security Traits
- Hacking: Computing: Encyclopedia Britannica
- Hacking News: Science Daily
- Cyberbullying and Cybersecurity: How Are They Connected?: AT&T
- Cyberbullying: What Is It and How to Stop It: UNICEF
- Current Awareness: Cyberlaw Decoded: Florida State University
- Share to Facebook
- Share to LinkedIn
- Share to email

Have you ever wondered why everyone has a unique set of character traits? What is the connection between brain function and people’s behavior? How do we memorize things or make decisions? These are quite intriguing and puzzling questions, right? A science that will answer them is psychology. It’s a multi-faceted...
![thesis topics for network security Student Exchange Program (Flex) Essay Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/student-exchange-program-284x153.jpg)
Participating in a student exchange program is a perfect opportunity to visit different countries during your college years. You can discover more about other cultures and learn a new language or two. If you have a chance to take part in such a foreign exchange, don’t miss it. Keep in...

How can you define America? If you’ve ever asked yourself this question, studying US history will help you find the answer. This article will help you dive deeper into this versatile subject. Here, you will find:
![thesis topics for network security 380 Powerful Women’s Rights & Feminism Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Womens-Rights-284x153.jpg)
Are you looking for perfect feminist topics? Then you’ve come to the right place. With our help, you can be sure to craft a great essay. Here, you can find feminist topics for discussion, feminism research topics and other ideas and questions for students. Some people think all feminists hate...

If you have an assignment in politics, look no further—this article will help you ace your paper. Here, you will find a list of unique political topics to write about compiled by our custom writing team. But that’s not all of it! Keep reading if you want to: Now, without further ado, let’s get started! Below, you’ll find political topics and questions for your task. 🔝 Top 10 Political...

It’s not a secret that our health largely depends on nutrition. A balanced and wholesome diet improves our immune system. It lowers the risk of getting sick and makes us more productive. But if we don’t eat right, our overall well-being and performance worsen. You see, nutrition topics are more...

A presentation is a speech in which you explain a topic to an audience. It usually includes visuals done in a program such as PowerPoint. Teachers in schools and in colleges love to assign presentations for various reasons: In this article, you’ll find a list of 625 presentation topics in...

In modern societies, people do everything to live peacefully. Still, tensions often arise. We call them social issues when they start negatively impacting a specific group of people. Poverty, discrimination, and addiction are examples of such problems. We need to confront them to ensure equal treatment for everyone.

There are many ways to define popular culture. Here’s one of them: pop culture includes mainstream preferences in society within a specific time frame. It covers fashion, music, language, and even food. Pop culture is always evolving, engaging in new trends, and leaving the old ones behind.
![thesis topics for network security 500 Sociology Questions and Topics [Examples & Tips]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Sociology-Questions-284x153.jpg)
Sociology is a study that focuses on people’s interactions. It looks at structures and changes in social life. Any situation involving people can become a topic of sociology. This article is designed to help high school and college students with sociology assignments. Whether you’re writing an essay, creating a presentation,...

Controversial issues are the ones that evoke a variety of opinions. They often cause heated debates. And, as you can guess, controversial research topics are not easy to handle. Luckily, we’ve got you covered. This article will: We gathered controversial topics for research paper on medical, science, education, and other...

Plates break when you drop them. Glasses help you see better. Have you ever wondered why? Physics has the answer. It studies the observable as well as invisible aspects of nature. An essential part of this is examining the structure and interactions of matter.

PhD Thesis Topics on Information Security
Network simulation plays a crucial role in the realm of computer science and engineering, serving as a valuable tool for exploring and developing network technologies and procedures. In recent times, the field of network simulation has experienced significant growth, leading to an increase in network simulation projects. If you find yourself struggling to find the perfect PhD thesis topics in network simulation, look no further than networksimulationtools.com. Our platform offers excellent services and comprehensive PhD guidance across all domain areas. When selecting a topic for your PhD thesis in network simulation, it is important to delve into current technological challenges and advancements. Here are some of the promising areas that we focus on when considering a PhD thesis, with a strong emphasis on network simulation.
- 5G and Beyond Wireless Networks:
- In terms of different constraints, we develop simulation of 5G network Procedures and performance investigation.
- Our work is to examine the possibility and difficulties of combining 6G technologies into previous network frameworks.
- Internet of Things (IOT) Network Simulations:
- For extensive achievements, we develop and test IoT network procedures.
- We simulate IoT networks for smart cities, concentrating on performance and scalability.
- Software Defined Networking (SDN) and Network Function Virtualization (NFV):
- To optimize network traffic flow and resource management, we simulate SDN surroundings.
- In cloud computing surroundings, our work estimates the achievements of NFV.
- Cybersecurity in Networked System:
- Our work improves cybersecurity procedures by simulating network impacts and defenses.
- In terms of different cybersecurity threat situations, we examine the flexibility of networks.
- Quantum Networking:
- We simulate quantum network frameworks and quantum key distribution procedures.
- Our work examines the combination of quantum networks with classical networks.
- Satellite Communication Networks:
- For global coverage, our work simulates next-generation satellite interaction frameworks.
- By offering internet facilities in remote regions, our work examines the performance of satellite networks.
- Mobile Ad-hoc Networks (MANETs) and Vehicular Ad-hoc Networks (VANETs):
- Utilizing network simulations, we learn the action of MANETs in different situations.
- For optimizing traffic control and road safety framework, our work simulates VANETs.
- Wireless Sensor Networks (WSNs):
- We utilize network simulation for effective energy management in WSNs.
- For surrounding control or agricultural applications, our work achieves and tests WSN procedures.
- Underwater Acoustic Networks:
- Particularly for underwater sensor networks, we simulate interaction procedures.
- In our work, we examine the underwater network achievement for marine study and discover.
- Edge Computing Networks:
- In managing large data from IoT devices, we estimate the achievement of edge computing frameworks.
- Our work is to simulate network delay and data processing at the edge of the network.
- Machine Learning Applications in Network Optimization:
- To test machine learning methods for network traffic forecasting and management, we utilize network simulation.
- We examine AI-driven methods for automated network structure and optimization.
- Multicast and Broadcast Networks:
- In large-capacity network surroundings, we carry out simulation research on effective multicast and extensive mechanisms.
- For video streaming and content distribution, our work estimates the achievements of different procedures.
Every topic must need an in-depth interpretation of network protocols and the capacity to utilize network simulation equipment efficiently, namely NS2/NS3, OPNET, GNS3, or OMNeT++. The selected topic must not only be suitable with present technological style and difficulties but also with our private passion and the specialization present at our academy.
How do I choose a PhD Topic?
Selecting a PhD topic in network simulation contains some essential considerations; make sure that the topic is not only passionate about it but also similar and possible within the aim of a PhD program. We offer an organized method that assists you to choose a relevant topic:
- Identify Your Interests: Consider which region of network simulation you are more interested in. This will be whatever ranging from wireless networks to cybersecurity, IoT connectivity or enhanced network procedures.
- Literature Review: Carry out an extensive literature survey in your region of passion. The literature survey assists you to interpret the present state of study, finding limitations in skills, and identify regions that need future discoveries.
- Evaluate Relevance and Impact: Select a topic which is similar to present technological difficulties and improvements. Examine if the topic is possible to create an essential influence in the domain, namely enhancing network effectively, privacy or scalability.
- Consult with Experts and Advisors: Converse your thoughts with institutional mentors, business experts, or other investigators in the domain. They provide understanding into the possibility of your proposed study and recommend possible regions that you must not have examined.
- Consider Resources and Tools Available: Make sure that you have accessibility to essential materials like network simulation equipments (e.g. NS2, NS3, OPNET, GNS3, and OMNeT++), hardware and data. Your education’s services and help will play an important part in your study.
- Technical Feasibility and Skill Set: Examine whether the topic suits your present technical knowledge or if it needs learning novel equipment and techniques. A PhD topic must be difficult to you but also be attainable within the duration and materials you have.
- Future Career Aspirations: Learn how the topics suit your professional aims. If you are targeting a professional in academia, the topic which dedicates essentially to theoretical factors must be aligned. For a profession in the business, implement research that must be most significant.
- Scalability and Scope: Confirm the topic that is not too extensive and too small. It must be particularly sufficient to be controllable but extensive enough to permit for broad study and important outcomes.
- Potential for Original Contribution: Your PhD topic must permit you to create a novel dedication to the field. This must be through the construction of novel network simulation methods, improving previous procedures, or executing simulation methods to new regions.
- Regulatory and Ethical Considerations: If your research contains data security problems, ensure your topic fulfills the moral instructions and administrative rules.

PhD Thesis Writing Using Network Simulation Tools
We take pride in offering PhD Thesis Writing services that utilize Network Simulation Tools, enabling scholars to excel in their careers. Over 4000+ scholars have already benefited from our expertise. Our team of well-trained writers provides comprehensive guidance and explanations to ensure scholars’ success. Rest assured; we not only deliver the correct source code but also provide paper reference details. Here are a few examples of our outstanding work:
- Nexus of 6G and Blockchain for Authentication of Aerial and IoT Devices
- A Blockchain-Based Distributed Pruning Deep Compression Approach for Cooperative Positioning in Internet of Vehicles
- A New Network Model for Cyber Threat Intelligence Sharing using Blockchain Technology
- Research on Logistics Information Blockchain Data Query Algorithm Based on Searchable Encryption
- Demand Response Service Certification and Customer Baseline Evaluation Using Blockchain Technology
- Proposal for Server Integrated Management System Using Zabbix for Blockchain-Based NTMobile
- Hybrid Consensus Approach for Blockchain based Vehicular Communication
- Performance Improvement of Blockchain-based IoT Applications using Deep Learning Techniques
- BTS: A Blockchain-Based Trust System to Deter Malicious Data Reporting in Intelligent Internet of Things
- A Review on Blockchain Technologies for an Advanced and Cyber-Resilient Automotive Industry
- Block – NID: A Conceptual Secure Blockchain Based National Identity Management System Model
- Industrial Intelligence of Things (IIoT 2.0) based Automated Smart Factory Management System using Blockchain
- Resource Allocation of IoT systems Integrated with Blockchain and Mobile Edge Computing
- User-centric In-network Caching Mechanism for Off-chain Storage with Blockchain
- DS2PM: A Data-Sharing Privacy Protection Model Based on Blockchain and Federated Learning
- Framework for User-Centered Access to Electric Charging Facilities via Energy-Trading Blockchain
- New Function and Configuration of Future Network for Blockchain Platform Operation
- Blockchain Based IIoT Data Sharing Framework for SDN-Enabled Pervasive Edge Computing
- Joint Transaction Transmission and Channel Selection in Cognitive Radio Based Blockchain Networks: A Deep Reinforcement Learning Approach
- Blockchain-enabled workflow management system for fine-grained resource sharing in E-commerce logistics
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |
Related Pages
YouTube Channel
Unlimited Network Simulation Results available here.

- Advisers & Contacts
- Bachelor of Arts & Bachelor of Science in Engineering
- Prerequisites
- Declaring Computer Science for AB Students
- Declaring Computer Science for BSE Students
- Class of '25, '26 & '27 - Departmental Requirements
- Class of 2024 - Departmental Requirements
- COS126 Information
- Important Steps and Deadlines
- Independent Work Seminars
- Guidelines and Useful Information
- Undergraduate Research Topics
- AB Junior Research Workshops
- Undergraduate Program FAQ
- Minor Program
- Funding for Student Group Activities
- Mailing Lists and Policies
- Study Abroad
- Jobs & Careers
- Admissions Requirements
- Breadth Requirements
- Pre-FPO Checklist
- FPO Checklist
- M.S.E. Track
- M.Eng. Track
- Departmental Internship Policy (for Master's students)
- General Examination
- Fellowship Opportunities
- Travel Reimbursement Policy
- Communication Skills
- Course Schedule
- Course Catalog
- Research Areas
- Interdisciplinary Programs
- Technical Reports
- Computing Facilities
- Researchers
- Technical Staff
- Administrative Staff
- Graduate Students
- Undergraduate Students
- Graduate Alumni
- Climate and Inclusion Committee
- REU on AI and Machine Learning
- Resources for Undergraduate & Graduate Students
- Outreach Initiatives
- Resources for Faculty & Staff
- Spotlight Stories
- Job Openings
A Formal Approach to Practical Network Security Management (thesis)
When a system administrator configures a network so it is secure, he understands very well the users, data, and most importantly the intent—what he is trying to do. However,he has a limited understanding of the mechanisms by which components interact and the details of each component. He could easily miscongure the network so a hacker could steal confidential data. In addition to this complexity, about one hundred new security vulnerabilities are found each week, which makes it even more difficult to manage the security of a network installation---because of the large number of program vulnerabilities and challenging time constraints. Even professional administrators find this a difficult (impossible) task. How does one enable the system administrator to securely congure the network with a limited understanding of its components, program bugs and their interactions? The solution is a security analysis framework that modularizes information flow between the system administrator, security expert and the bug expert. The administrator specifies what he is trying to do, the security expert specifies component behavior, the bug expert specifies known bugs. We developed a rule based framework—---Multihost, Multistage, Vulnerability Analysis (MulVAL)---to perform end-to-end, automatic analysis of multi-host, multi-stage attacks on a large network where hosts run on different operating systems. The MulVAL framework has been demonstrated to be modular, flexible, scalable and efficient. We used the framework to find serious configuration vulnerabilities in software from several major vendors for the Windows XP platform.
Trending Top 15 Cybersecurity Thesis Topics
Cybersecurity is delivering services to protect the software, hardware, and networks against cyber-attacks / illegal access for misuse. The intention to develop cybersecurity thesis topics is to ensure the safety, privacy, trust, and integrity of the cyberinfrastructure. For this purpose, it determinedly fights against malicious cyber-attacks, threats, and vulnerabilities . However, it is a robust security mechanism to defeat the known attacks, and it is unbalanced in the case of emerging attacks.
Generally, the attack problem in the interaction is classified into two portions as south and northbound. Below, we have mentioned few reasons behinds the cybersecurity model,
- For optimizing and assessing the network performance
- For avoiding the data / firmware harm and theft
- For managing security compliance and auditing of the network to assist the system admin
- For controlling the efficiency of the network in terms of quality of service and service level agreement
- For preventing the interruption while service request
As a matter of fact, security is classified into different types based on their focused responsibilities. And they are network security, system output security, and information security . So, it is easy to recognize the security issues for providing appropriate defensive measures

Major Types of Cybersecurity
- Network / Host-assisted Intrusion Detection
- Event Management
- Anti-Malware
- Access Control
- User Accessibility
- Print Verification
- Encryption or Information Driven
- Information Wiping Cleaning
- Database Integrity and Gateway
- Scanning of Information Storage (Database)
- Data Loss Prevention (DLP)
In order to interpret the cybersecurity features and configuration, here we have given you the instances of cybersecurity.
What are the 3 security domains?
Based on the functionality of the cybersecurity model, the system design is classified into 3 phases in sequential order such as hardware, network, and software / API. Here we can see the functions of the three domains.
- It is the network of hardware / devices that are used to execute the software / application based on the custom needs
- In this, few devices are furnished with capability to sense the environment and others are used to note down the up-to-date values
- Then, pass the collected data to the server via next-level of model i.e., network phase
- It comprises the more communication technologies for accessing different networks
- Further, it launches the communication among other two phases that is hardware and software / application phases
- For instances: WiMAX, Satellite, WLAN, UTRAN, xDSL, GERAN and many more
- It is comprised with servers which stores the data obtained from hardware phase and network phases
- Then, it provides the data to the end-users once the request is received from different applications
Next, we can see the development of the cybersecurity models, which begins from authentication to code analysis . In this, we have mentioned the functionalities of each stage. Overall, you can get an idea of how cybersecurity is established, how the risk is analyzed, and how the programmable code is verified to improve security.
Cybersecurity Model Lifecycle
- Execute the penetration and internal penetration test
- Perform the cloud and network testing
- Carry out other security processes
- Essential needs of security
- Examine the privacy through security test
- Analyze the risk and threat
- Perform the security processes
- Inspect the static code
Furthermore, we are also like to give information on the key entities required to build the cybersecurity model . The core elements of cybersecurity models are framework, operations, rules/procedure, and assessment.
Nowadays, cyber-attacks have become the biggest threat in digital data communication. So, all the individuals and organizations are moving in the direction of cybersecurity to protect their sensitive information. The security analyst monitors the system to safeguard the central /distributed server against cyber-attacks in an organization. These attacks have the capability to penetrate the network either through new technologies or vulnerable systems. Then, it performs malicious activities such as eavesdrop, data theft, system shutdown, compromise network, data manipulation, deletion , etc. Here, we have specified few important aspects of cybersecurity.
Highlights of Cybersecurity
- In what way the personal information is accessed by the private organization? Is the government must access data in static or dynamic movement?
- By what means we know the cyber attacker? And what we do if can’t attribute attack?
- What are the input and output that participate in the physical and embedded system?
- How the trust will be built among network/system and how we measure the variation?
- In what manner, we evaluate in real-time? For whom, we are watching and What we are seeking for?
So far, we have discussed the cybersecurity types, instances, phases, lifecycle, components, and importance in real-world applications . Now, we can see the list of research holes that are not addressed in an effective manner. Our research team has found all these areas as new dimensions of cybersecurity in current and future research . Here, we have given you the list of research holes followed by cybersecurity threats and solutions.
Research Gaps in Cybersecurity
- Deficient Privacy Mechanisms
- Tracing of Remote Location
- Security Defects on Software / Hardware
- Illegitimate User Resource Access
- Traffic Analysis and Classification
- Prevention against Malicious Activities
- Analyzing the Signal Integrity
- Achieving Integrity of Communication Metadata
Cybersecurity Threats and Solutions
- Filter / Drop Packets Techniques
- Tamper Proofing
- Routing Technique by Secure Way
- Threatening the integrity of network information and adapt to environs with censored modification
- Possibly ignore the traffic congestion
- Create malicious activity which add to the blacklist
- Keep the trace about quantity of clones
Our resource teams are experienced in both standalone and hybrid security research areas . On the one hand, standalone security areas are identified as network/host security, web-application security, forensics, cryptography , software/hardware security , etc. On the other hand, hybrid areas are referred to as system security using cryptography techniques and system security using machine learning in digital forensics
- Generate security policies and arrange training program for employee in an organization. And, make them aware about the security threats.
- Monitor the entire network against insiders and outsiders. Then, extract the malicious access and data for controlling the system
- Build the security policy and baseline for all hardware. Next, train and safe-guard the data in rest / motion.
- Build the anti-malware policies to the organization data / network
- Implement the generated security policies in real-time information and communication system. Next, build the security baseline for every deployed device
- To monitor / analyze the ICS system and their logs, generate efficient policies and procedures
- Generate policies for managing removable media such as restricting, scanning, detecting malware, etc.
- Create incident response and recovery plan and train the employee. Then, notify the law enforcement about the criminal incidents immediately
- Monitor and control the user accounts and their rights to access resources

Emerging Technologies of Cybersecurity
In recent days, cybersecurity is found many evolving technologies to enhance their application security level. In specific, virtual/augmented reality has gained trust in cybersecurity. Our technical professionals have long-standing practice in handling different sorts of interesting cybersecurity research and developments. Currently, we are working on many cybersecurity thesis topics with respect to information security ( forensics, bio-authentication, cyber criminalities and etc.).
In addition, other current research fields are also holding their hands with cybersecurity & cyber warfare research topics. And, some of them are given as follows,
- Internet of Things
Software Defined Networks
- Mobile Edge Computing
- 5G Beyond and 6G Cellular Networks
- Blockchain based Security System
Here we have listed few attention-gaining research areas in cybersecurity that encompasses best Cybersecurity Thesis Topics f or your references.
Trending Top 15 Cybersecurity Thesis Topics Research Areas
- IoT Network Security
- Cyberwarfare
- Developments of Threat Intelligence
- Artificial Intelligence for Cybersecurity
- Digital Forensics in Cybersecurity
- Advance Cyber-Physical System (CPS)
- Enhanced Security Mechanism for Sensitive Data
- Mining of Attack Signature in Big Data
- Construction of Privacy Engineering Model
- Risk Prediction, Analysis and Control
- New Design of Security Policies for Cyber System
- Advances in Quantum Mechanics and Computing
- Improving Security by Multi-Level Techniques
- Trustable Security Strategies for Software / System
- Zero-day attack detection using improved Heuristics Algorithms
- Increasing Trust on IoT enabled M2M Communication
- Security Analytics Challenges in Artificial Intelligence
- End-to-End Analysis of Network / System Weakness
How do we frame a format for cybersecurity thesis topics writing?
So far, we have debated on cybersecurity enabling technologies, research areas, and cybersecurity thesis topics . Now, we can see about our thesis writing service. The well-organized thesis mirrors your whole research work, which is done to this point. By the by, it has the chronological order to write the research question and solving answers. Refer to the following for more clarity,
- Handpick the well-intentioned research question which is not solved yet
- Perform the survey to on other related research work and find the both positive and negative aspects of those researches
- Model and develop your research work by means of quantitative, qualitative and combined analysis techniques
- Present your experimental results and findings with suitable evidences to meet your research aim
Further, if you are looking for the best research guidance on up-to-date Cybersecurity Thesis Topics , then you can find the best solution without any doubt. Surely, we will be with you throughout your research path, from area identification to thesis submission.
Why Work With Us ?
Senior research member, research experience, journal member, book publisher, research ethics, business ethics, valid references, explanations, paper publication, 9 big reasons to select us.
Our Editor-in-Chief has Website Ownership who control and deliver all aspects of PhD Direction to scholars and students and also keep the look to fully manage all our clients.
Our world-class certified experts have 18+years of experience in Research & Development programs (Industrial Research) who absolutely immersed as many scholars as possible in developing strong PhD research projects.
We associated with 200+reputed SCI and SCOPUS indexed journals (SJR ranking) for getting research work to be published in standard journals (Your first-choice journal).
PhDdirection.com is world’s largest book publishing platform that predominantly work subject-wise categories for scholars/students to assist their books writing and takes out into the University Library.
Our researchers provide required research ethics such as Confidentiality & Privacy, Novelty (valuable research), Plagiarism-Free, and Timely Delivery. Our customers have freedom to examine their current specific research activities.
Our organization take into consideration of customer satisfaction, online, offline support and professional works deliver since these are the actual inspiring business factors.
Solid works delivering by young qualified global research team. "References" is the key to evaluating works easier because we carefully assess scholars findings.
Detailed Videos, Readme files, Screenshots are provided for all research projects. We provide Teamviewer support and other online channels for project explanation.
Worthy journal publication is our main thing like IEEE, ACM, Springer, IET, Elsevier, etc. We substantially reduces scholars burden in publication side. We carry scholars from initial submission to final acceptance.
Related Pages
Our benefits, throughout reference, confidential agreement, research no way resale, plagiarism-free, publication guarantee, customize support, fair revisions, business professionalism, domains & tools, we generally use, wireless communication (4g lte, and 5g), ad hoc networks (vanet, manet, etc.), wireless sensor networks, network security, internet of things (mqtt, coap), internet of vehicles, cloud computing, fog computing, edge computing, mobile computing, mobile cloud computing, ubiquitous computing, digital image processing, medical image processing, pattern analysis and machine intelligence, geoscience and remote sensing, big data analytics, data mining, power electronics, web of things, digital forensics, natural language processing, automation systems, artificial intelligence, mininet 2.1.0, matlab (r2018b/r2019a), matlab and simulink, apache hadoop, apache spark mlib, apache mahout, apache flink, apache storm, apache cassandra, pig and hive, rapid miner, support 24/7, call us @ any time, +91 9444829042, [email protected].
Questions ?
Click here to chat with us
Network Security Thesis Topics
Network Security Thesis Topics is our surprising service with the vision of provide highly confidential research for you to create knowledge revolution among students and research scholars. We provide complete guidance and support for you to implement your dream of research to attain grand scientific achievement in the technological world. And also, we are experts of experts in both the technical and conceptual side.
We also revise hundreds of related research papers to prepare your research thesis with the best quality. Do you want the best guidance also for prepare your thesis yourself? Contact us. We are also ready to provide the best thesis preparation service for you to prepare your network security research proposal by own. Today, we also serve uncountable students and research colleagues all over the world. If you aspire to utilize our Network Security service and get our best guidance, you can immediately approach us.
Our Dedicated Network Topics Service
Problem analysis.
Analyze new problem for your research based on the following:
- Domain Specification
- Definition of Problem
- Bibliography
- Analysis Tool and software
Solution Identification
Find novel solution for identified problems in your research also based on the following:
- Solution for Problem
- Algorithm Procedure
- Design Protocol
Data Analysis
Implementation process
Solution based development carryout in this phase based on the following:
- Language Specification
- Code Implementation
- Algorithm Design
- Implementation Proof
- Error Debugging
Result and Proof
Final outcome of development results in your research also based on the following:
- Results and Graphs
- Statistical Proof
- Future Enhancement
Support Thesis and Journals
Research Report Preparation stage based on the following:
- Thesis Material Preparation
- Journal Paper Preparation [SCI, SCOPUS and also Normal]
- Journal Publication
- Proof Materials
- Conference Paper Preparation
Network Thesis Topics
Network Security Thesis Topics provides novel ideas also for you to chosen ground breaking research topics to accomplish your academic research journey with the grand accomplishment.Our certified professionals also train you in each and every stage of your record-breaking research. Research is discovering the knowledge about various technological and scientific concepts to develop highly valuable research emerging in this scientific world .
We have also completed hundreds of networking researches in a vast array of research areas with our 10+ years of experience. And We also provide our admirable support in your project implementation phase with a full practical explanation. Now, we also discuss some of the important information about network security.
Network Security Concepts
- Malware Analysis
- Network Security Monitoring
- Packet Analysis
- Stegnography
- Cryptography
- Network Resource Security
- Log-file Analysis
- Continuous Security Monitoring
- Privacy and Trust Management
- Computational Intelligence also in Network Security
- Network Defense
- Virus and Worm Analysis
- Security Aware Software Engineering
- Security Ontology and Models
- Endpoint Security Management
Goal of Network Security
- Authentication
- Confidentiality
- Authorization
- Availability
- No-Reputation
Factors to Avoid Security Threats
- Virtual Private Network (Secure Private connections)
- Real-Time Packet Decryption (Malware Filtering)
- Application Filtering or controls (Block Unwanted Applications)
- E-mail Handling (Detect and also Remove Malware)
- Stateful Packet Inspection (Known Malicious Communication)
- Intrusion Detection and Blocks (Detect and also Respond to DoS)
- Deep Packet Inception (Production Against Malware)
- Proxy Service (Block revealing details (IP Address) )
- Circuit Gateways (Block Packets in TCP or UDP Connection)
- Packet Filtering (Against IP Spoofing and also DoS)
- Configuration Management (Network Attack)
Advanced Applications in Information Forensics and Security Application
- Big Data Approach to Banking Monitoring, Alerts and also Decision Making
- Real Time Security Algorithms also for Cyber Security Data
- Robust Malware Detection Framework also for Mobile Based Platform
- Ensuring Patient Privacy given also for IoT Health Data Transmission from Wearable Sensors
- Real Time Security approaches and also Optimal Adaptive Security for their Solution
- Mobile OS and also Forensics
- Detect Android Piggybacked Apps also through Sensitive Sub-Graph Analysis
Network Security Algorithms and Techniques
- Multi-Pattern Hash Binary Hybrid Algorithm
- Hybrid Signature also Based Iterative Disaggregation Algorithm
- Hybrid Algorithm (DES and also IDEA)
- Tree Searching Heuristic Algorithm
- Hybrid cryptographic Algorithm (DES and also AES)
- Visual Cryptography also Based Password Processing Algorithm
- Post Quantum Cryptographic Algorithm
- Hybrid Artificial Intelligence also Based Handover Decision Algorithm
- Path Redundancy Based Security Algorithm
- Elliptic Curve Cryptography Technique
- Hybrid Cryptography (AES, RC6, Blowfish and also BRA)
- Hybrid Quantum Inspired Genetic Algorithm
- Equilibrium also Based Business Intelligence Technique
- BESA Cryptography also in Algorithm
- Hybrid Multi-Agent Discovering Algorithm
Latest Network Security Thesis Topics
- Adaptive Secure Communication in Cooperative Wireless Networks also for Adaptive Secure Transmission
- Maximum Connectivity Based Channel Allocation algorithm also for Medical Applications in Cognitive Wireless Networks
- Hybrid BBO-LP Algorithm with Extracted Time Current Characteristics Curve also for Directional Over-current relays Optimal Coordination
- Anomaly Detection in Internet of Things Sensors Using Accuracy and also Performance Trade-off Analysis Techniques
- Extract Security Key also Using Wireless Link Dynamics in Vehicular Scenarios
- Reach-ability Specifications Using Minimum Resource Commitment also in Discrete Time Linear Setting
- Vehicular Ad Hoc Networks also Using Efficient Anonymous Authentication Scheme with Conditional Privacy Preserving Scheme
We also previously highlighted some of the important aspects of network security, including the concept of network security, goal of network security, factor to avoid network security, information forensic & network applications, algorithms, techniques, and also latest research topics. For more information, you can also call or send mail within 24 hours.
“Journey of thousand miles begins with one step…..”
“today you take one step for come to join with us…………….”, “attain the pinnacle of everest in your dream of research……”, related pages, services we offer.
Mathematical proof
Pseudo code
Conference Paper
Research Proposal
System Design
Literature Survey
Data Collection
Thesis Writing
Rough Draft
Paper Collection
Code and Programs
Paper Writing
Course Work
M.Tech/Ph.D Thesis Help in Chandigarh | Thesis Guidance in Chandigarh

+91-9465330425

Thesis and Research Topics in Computer Networking
Students who find programming complex and challenging mostly go for networking field in computer science engineering. But even after indulging in this field they are often confused about which topic to choose for the project or for an M.Tech thesis. Here is the list of some of the good topics in computer networking with a basic introduction which you can choose for your project or thesis. You can also get thesis help and thesis guidance on these topics from experts. In the infographic below you will find the list of latest thesis and research topics in computer networking .
List of the best thesis topics in networking:
Wireless Sensor Networks
Wireless Ad hoc Network
Vehicular Ad hoc Networks
Network Security
- Evaluate and implement energy efficient protocol for data aggregation in wireless sensor networks
- Node Localization Approach in underwater acoustic network using bio-inspired method
- Evaluate and implement sink hole attack isolation method in wireless sensor networks
- The three level hierarchical routing protocol for data aggregation in wireless sensor networks
- Design and implement black hole attack isolation method in wireless sensor networks
- The clock synchronization method in wireless sensor network for the efficient data transmission method
- The efficient channel sensing scheme for wireless body area network
- Design secure scheme for data transmission in opportunistic routing in wireless sensor networks
- The misdirection attack isolation scheme in multilevel hierarchical routing protocol in WSN
- To propose fault tolerance scheme for wireless sensor networks
- To propose novel approach to maintain quality of service in the network for link failure
- To propose hybrid routing protocol based on the bio-inspired methods in mobile ad hoc network
- The threshold based mechanism for the isolation of worm hole attack in mobile ad hoc networks
- Evaluate and implement clustering based method for the isolation of black hole attack in mobile ad hoc network
- The novel method for the congestion avoidance in mobile ad hoc network to maintain quality of service in the network ‘
- The multicasting scheme for the path establishment in mobile ad hoc networks
- Implement and evaluate Sybil attack isolation scheme for vehicular ad hoc networks ‘
- To propose novel scheme for the detection of DDOS attack in vehicular ad hoc networks
- The zonal based routing scheme for path establishment in vehicular ad hoc networks
- The secure and efficient message authentication scheme for vehicular ad hoc networks
- The location based routing scheme for path establishment in vehicular ad hoc networks
- The tree based multicasting scheme in vehicular ad hoc network for data transmission
TCP/IP Protocol
Now our systems computer, laptop, mobiles, and other internet devices are connected to one node to communicate with each other and to get internet access, and this whole process called a network system. They all are connected with the physical medium so that’s why they can be guided as wireless network system or copper wire network system to provide calculated data speed in the notes time frame. It spreads motions as electromagnetic waves or light pulses. The direct connection between two nodes are considered as guided medium and is more reliable and the occurrence of error has very less as compared to another medium. Un-guided medium is used in so many systems to provide multiple outputs at the same time. But in this system error rate is high.
To send or receive the internet signal, the two nodes follow a set of protocol which is known as IP (internet protocol). Each system is designed to follow this set of rules itself to generate maximum speed with a time limit. These protocols are designed in a manner that they follow these rules one by one. Each layer follows the protocol of the upper layer to provide services and then that layer follows the upper layer, this process will continue until data is transmitted or received. Lower layer always follows the basic set of rules and upper layer follows the advanced set of rules. Service provided by both layer will be different in terms of protocol instructions.
First data is sent or received in the application layer and then in the transport layer, after following the set of rules data then is sent to network layer to link layer and after that data has been sent to physical layer to the user. Data is divided into small packet format to provide consistency. Common internet protocol is RTP (Real-time Transport Protocol). which is used to provide information at the time of gaming, movie or music streaming. first two-layer are used to transmit or receive the information in small data packets.
Two main internet protocols are UDP (user datagram protocol) and TCP (transport control protocol). UDP and TCP both have their advantages and disadvantages of use. UDP is used because of their simplicity and with the use of UDP data can be sent immediately. But at the same time, it is unreliable as compared to TCP. TCP, then again, directs the sending rate concerning the client’s ability – stream control – and with respect to the limit of the system – clog control. It conveys the information altogether and guarantees that all information achieve the beneficiary. The hidden layers, similar to the system layer, are not required to perform solid conveyance.
TCP(Transmission Control Protocol) is a set of rules to access the Internet with the interconnection of various Internet-based devices. We can say it is a communication protocol in which there is a host with access to the Internet. This is a good topic for an M.Tech thesis in networking. If you are planning to choose this networking topic for research, then here is some basic introduction to this.
TCP/IP provides end to end data transmission between devices along with some other functionalities like addressing, mapping and acknowledgment. TCP/IP is a combination of two protocols. TCP controls the messages by dividing them into packets. IP controls the transmission of these packets from the sender to the receiver.
TCP/IP protocol layers
Following are the four layers of TCP/IP:
Application layer
Transport layer
Internet layer
Physical layer
Working of TCP/IP protocol
Client/Server model is used as a mode of communication by TCP/IP. It works in the following way:
Application layer consists of various applications for data exchange with use of protocols like HTTP(Hypertext Transfer Protocol), FTP(File Transfer Protocol), SMTP(Simple Mail Transfer Protocol)
The transport layer provides end-to-end communication between the host and the user. It uses protocol UDP(User Datagram Protocol).
Internet layer is responsible for the transfer of packets over the network and uses IP(Internet Protocol) for this purpose.
The physical layer provides interconnection between the nodes.
Advantages of TCP/IP protocol
It can be easily modified.
It is compatible with all the operating systems.
It is scalable in determining the most appropriate path.
Thus it is a good topic for M.Tech thesis as well as for research. A student can get thesis help on this topic from experts specialized in thesis guidance. You can also explore the Internet for further details on this topic.
Network Simulation Tools
Here is the list of commonly used network simulators having different features:
Another good computer networking topic for an M.Tech thesis is NS2 . NS stands for Network Simulator. It is an open-source, discrete-event based network simulator mainly used for research purpose and for teaching. It provides help in simulating routing protocols like IP, TCP, UDP, etc. It creates a simulation environment for studying the network. Following steps are followed while creating a simulation environment:
Topology Definition
Development of the model
The configuration of the link
Analysis of the problem
Visualization
NS2 create network topologies and then examines the behavior of the network under any event. The behavior is analyzed by tracing down the events. NS2 provides text-based as well as animation-based simulations.
Advantages of NS2
It has the ability to support multiple protocols.
It can represent network traffic graphically.
It can also support multiple algorithms for routing and queuing.
NS2 is a very good topic for an M.Tech thesis in the computer networking field. You will not only get theoretical knowledge but also practical experience of network simulator tool. You can get thesis guidance about NS2 from an expert who has practical knowledge about how to use this tool.
MANET stands for mobile ad hoc Network and is another good choice for an M.Tech thesis topic in networking. In MANET, the nodes are self-configurable and have the ability to move freely in any direction and can link with other devices frequently. MANET was originally used as a military project in defense. MANET have the challenges of weak signal strength, reliability, power consumption along with some other problems.
Characteristics of MANET
Each node is independent in nature i.e. each node act as the host as well as the router.
It is based on the distributed nature of operation for security and configuration.
The network is dynamic in nature i.e each node can join and exit the network at any time.
The nodes in the network are associated with less memory and power.
In MANET, the bandwidth remains fluctuating.
MANET creates a symmetric environment such that all the nodes have identical features like responsibilities and capabilities.
Hurdles in the path of MANET
There are certain hurdles in the path of MANET, which it has to overcome. Some of these are:
The reliability of the transmission is affected by certain factors like data loss, interference, and blockage.
The rate of transmission is limited to a certain range thus there is a reduced data rate.
Packet loss can occur while transmission of data.
Frequent path breaks.
Lack of firewall results in security issues in the network.
This was just the introduction to MANET to give an overview of what it is if you are going with this topic for your M.Tech thesis.
Network Security is the set of rules to ensure the safety of the network of an organization or personal network. You can choose this topic for your M.Tech thesis if you have a complete understanding of how the data is transferred over the network. Network Security also include security of physical hardware devices. Network Security in software means providing authorized access to the network by means of ids and passwords.
Whenever a user tries to access the network, his authenticity is checked by means of ids and passwords. This is done to prevent any malicious user from entering the network by the motive of hacking it.
Types of attacks to network
Active Attack – In this type of attack, a hacker tries to make changes to data while it is being sent from one node to another.
Passive Attack – In this type of attack, an outsider monitors system of the organization consistently to find vulnerable ports.
Network Security Tools
Following are some of the tools employed in network security:
Thus if you really have significant knowledge(practical + theoretical) of networking tools, security
measures then you should choose this topic for M.Tech thesis. Besides, you will get thesis help as well as guidance on this topic from computer networking experts.
Network Topologies
Network Topology is the arrangement of nodes in the network both physical and logical. It is an easy topic for M.Tech thesis. Following are some of the common physical topologies:
Bus – In the bus topology, each node is connected to the main cable known as bus such that every node is directly connected to every other node.
Star – In the star topology, each node is connected to a central hub such that all the nodes are indirectly connected to each other.
Ring – In this topology, the nodes form a closed loop such that the adjacent nodes are in direct connection with each other.
Token Ring – In the token ring topology, a protocol is used. A token is passed from one node to another. A node that wants to transfer data should acquire the token.
Mesh – In the mesh network, each node is directly connected to every other node. It can be a full mesh or partial mesh network.
Tree – It is the interconnection of bus topology and star topology.
Daisy Chain – In this topology, each node is connected to two other nodes but do not form a closed loop like ring topology.
Hybrid – It is a combination of two or more topologies.
If you are afraid of complex topics in networking for M.Tech thesis, then this topic is for. It is relatively simple to understand and work on. Just go for it.
It is another major topic in computer networking and also a good choice for a thesis or project. Ipv4 is the fourth version of Internet protocol while Ipv6 is the sixth version of Internet protocol.
Characteristics of IPv4
It uses a 32-bit address.
The address is written in decimal separated by dots.
The header includes a checksum.
Broadcast addresses are used to send data packets to other nodes.
In this the Internet Protocol Security is optional.
Characteristics of Ipv6
It uses a 128-bit address.
The address is written in hexadecimal separated by colons.
The header does not include a checksum.
Broadcast addresses are not used to send data packets.
The Internet Security Protocol is compulsory.
It is a good area to study how data transfer takes place over the internet. You will study the IP data packets of Ipv4 and Ipv6. You can select this as your M.Tech thesis topic.
OSI stands for open system interconnection. It is another good topic for an M.Tech thesis in the computer networking field. It provides a networking framework to implement protocols in layers. There are seven layers of OSI Model:
Physical Layer – This layer is responsible for transferring digital data from the source to the destination.
Data Link Layer – This layer checks error in data along with the MAC address. It turns bits into data frames.
Network Layer – This layer checks whether the data has reached the destination or not by examining the source and the destination address.
Transport Layer – This layer transfers data over the network by using the TCP protocol.
Session Layer – This layer manages the events and keeps them in sequence. It supports multiple types of connections.
Presentation Layer – It looks after the syntax along with encryption and decryption for the application layer above it.
Application Layer – It provides end-to-end user applications using protocols like HTTP, FTP, SMTP.
It is different from the TCP/IP model. You will get a thesis guide on this topic from computer networking experts.
However, with the change of social economy, computer networking system changes a lot and have also changed people’s lifestyle in a lot of aspects. As we know with the increasing demand for network speed, a number of network provider has been also increased. Due to the maximum number of the provider, one can easily access the high speed of the internet at a low cost. Local area network which is used in lots more other sectors like medical, military, education and science. Now we can see every-one need their own personal LAN (Local Area Network). Now LAN is not only for big enterprises but it is also available for small schools and families which are looking for high speed of data in the minimum amount.
The current speed of LAN is not enough for a user so that’s why companies are doing more research and study to provide the data at higher speed without the use of high bandwidth. But as we know if we want higher speed in a short time with a wide area, bandwidth will be increased to 30% to 300%. Now one of the very well known company called Huawei launched its 5G network, which is faster than the USA 5G network. So with this network Bandwidth also increased by 300%. It is beneficial for us but at the same time, a higher bandwidth is also not good for human life.
Various exploratory and early business LAN innovations were created during the 1970s. But then a new term called WLAN is introduced to the world in 1997 to provide a wireless network. This technology got famous in a very short span of time with the name of WiFi (Wireless Fidelity).
It stands for Wireless Local Area Network. It can be another good choice for an M.Tech thesis topic in computer networking. It is a wireless distribution method that uses high-frequency radio waves with a single access point to the Internet. In other words, it is wireless communication between two or more devices such that users can move around in a limited range area. It is most commonly used in homes or offices. The component connected to WLAN is referred to as the station. There are two types of stations – Access Point, Client.
Access Points are the base stations that transmit and receive radio frequencies for wireless-enabled devices. Clients are mobile phones, laptops, desktops connected to the wireless network.
Modes of Operation of WLAN
There are two modes of operation of WLAN:
Infrastructure – In infrastructure mode, base station act as the access point and all the nodes communicate through this point.
Ad hoc – In Ad hoc mode, mobile devices transmit data directly using peer to peer method. In this, there is no base station.
WLAN Advantages
It can support a large number of devices.
It is easy to set up wireless LAN than installing cables for the wired network.
It is easier to access a wireless network than a wired network.
WLAN Disadvantages
It is difficult to expand the network.
It faces security issues like hacking.
Interference is another problem with WLAN.
WLAN is another easier topic for an M.Tech thesis. It is used everywhere. You can take thesis help on this topic from networking professionals.
Cryptography
It is the science of maintaining the privacy of data. It is also an easy topic to choose for your M.Tech thesis in networking. There are three main objectives of cryptography used in transferring data over the network:
Confidentiality
Authentication

Cryptography employs two techniques for maintaining the privacy of data:
Encryption – In encryption, the plain text is converted into some other form known as ciphertext.
Decryption – In this technique, the converted text i.e the ciphertext is translated back to the original text.
There are two algorithms for cryptography. In a symmetric key, both the sender and the receiver share the same key for encryption and decryption.
In an asymmetric key, both the users have different keys respectively for encryption and decryption.
This is a familiar topic and very easy to understand. Take the guidance of a thesis expert about this area to start with this topic.
IEEE stands for Institute of Electrical and Electronics Engineers. IEEE 802 is a very challenging and a very good topic for your thesis. IEEE 802 comes under IEEE and deal with LAN(Local Area Network) and MAN(Metropolitan Area Network). It specifies certain services and protocols for the data link layer and physical layer of the OSI model. IEEE is further subdivided into 22 parts that cover a wide range of services.
IEEE 802 subdivides data link layer into two layers namely: Logical Link Layer(LLC)
Media Access Control(MAC)
You can choose any of its subfields as a part of your project or thesis. It is a very good area to explore.
These were some of the few topics for an M.Tech thesis in computer networking. You can also choose any one of these for research in networking or for your project. You can explore more on these topics.
If you need help with thesis topics in computer networking, you can contact us . You can call us on this number +91-9465330425 or email us at [email protected] for M.Tech and Ph.D. thesis help in computer networking. You can also fill the query form on the website.
For more details Contact Us. You can call us on this number +91-9465330425 or drop an email at [email protected] for any type of dissertation help in India. You can also fill the query form on the website.
You can also visit our website Techsparks and follow us on Pinterest , Facebook , Twitter, YouTube and Linkedin for latest thesis blog.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Quick Enquiry
Get a quote, share your details to get free.

COMMENTS
Network security threats are patented to cause monetary loss. The data gathered in a network are used to identify the security threats like vulnerabilities and intrusions. Such data are called the data related to network security. Research Scholars can reach us in developing network security thesis topics based on data collection and detection ...
Håkon Olsen, security engineer and founder of cybersecurity firm Cybehave, weighed in on cybersecurity thesis topics in a recent forum on Quora, where he suggested tackling the subject of identity management. "Investigate how to maximize security within each user's threshold for usability impact," Olsen wrote, adding that most users don't use ...
Criminal Law. Cyber Security Future Research Topics. Developing more effective methods for detecting and responding to cyber attacks. Investigating the role of social media in cyber security. Examining the impact of cloud computing on cyber security. Investigating the security implications of the Internet of Things.
Description of the topic. Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network.
Top 15 Cyber Security Thesis topics. Cybersecurity in the Age of Artificial Intelligence: Explore the intersection of cybersecurity and artificial intelligence, examining the use of AI for both offensive and defensive cyber operations, as well as the implications for security and privacy. Securing Internet of Things (IoT) Ecosystems ...
Techsparks offer thesis and research help in network security topics. You can call us at +91-9465330425 or email us at [email protected] for thesis and research help in network security. You can also fill the contact form the website. We will get back to you as soon as possible.
The purpose of network security is to protect the network and its components from unauthorized access and abuse in order to provide a safe and secured communication device for the users.
Network Security Research Topic ideas for MS, or Ph.D. Degree. I am sharing with you some of the research topics regarding Network Security that you can choose for your research proposal for the thesis work of MS, or Ph.D. Degree. CompTIA security+ guide to network security fundamentals. A survey of moving target defenses for network security.
List Of 15 Great Dissertation Topics About Network Security. With the rise of the Internet, many people are asking themselves if the have the best network security or even how it works. That is why this kind of topic has become so popular with graduate students that are preparing their dissertation. Here is a list of fifteen topics that you can ...
This thesis looks into vulnerabilities and mitigations of wireless networks. Many problems small companies are facing due to intruders and attackers are also discussed. Basically, the vulnerabilities and mitigation this thesis examines will be very useful in the ... Network security is a very large topic of networking; I decided to write this
204 Research Topics on Technology & Computer Science. A List of 580 Interesting Research Topics [2024 Edition] A List of 179 Problem Solution Essay Topics & Questions. 193 Interesting Proposal Essay Topics and Ideas. 226 Research Topics on Criminal Justice & Criminology.
Network Security Dissertation Topics. We have compiled a selection of captivating network security dissertation topics, considering the extensive scope of this field. Moreover, we are open to exploring additional dissertation ideas that may arise. Furthermore, we eagerly propose innovative research proposals for both students and scholars at ...
When selecting a topic for your PhD thesis in network simulation, it is important to delve into current technological challenges and advancements. Here are some of the promising areas that we focus on when considering a PhD thesis, with a strong emphasis on network simulation. 5G and Beyond Wireless Networks:
repetitive security tasks. In this thesis, employees at If insurance company who work with network monitoring and network security were interviewed. The purpose of the interviews was to find out what sort of problems they have encountered in their tasks. Additionally, possible AI-based solutions for the defined problems are represented in this ...
The administrator specifies what he is trying to do, the security expert specifies component behavior, the bug expert specifies known bugs. We developed a rule based framework—---Multihost, Multistage, Vulnerability Analysis (MulVAL)---to perform end-to-end, automatic analysis of multi-host, multi-stage attacks on a large network where hosts ...
Currently, we are working on many cybersecurity thesis topics with respect to information security (forensics, bio-authentication, cyber criminalities and etc.). In addition, other current research fields are also holding their hands with cybersecurity & cyber warfare research topics. And, some of them are given as follows, Internet of Things.
Network Thesis Topics. Network Security Thesis Topics provides novel ideas also for you to chosen ground breaking research topics to accomplish your academic research journey with the grand accomplishment.Our certified professionals also train you in each and every stage of your record-breaking research. Research is discovering the knowledge ...
Network Security. Network Security is the set of rules to ensure the safety of the network of an organization or personal network. You can choose this topic for your M.Tech thesis if you have a complete understanding of how the data is transferred over the network. Network Security also include security of physical hardware devices.
Network Security Thesis Topics deals with we offer an extensive range of technical and knowledgeable experts research views to enhance research career.https:...