- Engineering & Technology
- Computer Science
- Data Management

1 Introduction To Information Technology.ppt
Related documents

Add this document to collection(s)
You can add this document to your study collection(s)
Add this document to saved
You can add this document to your saved list
Suggest us how to improve StudyLib
(For complaints, use another form )
Input it if you want to receive answer
- I Tried Both: Apple Watch 9 vs Fitbit Charge 6
- Best Places to Print Photos Online
Introduction to Information Technology (IT)
What information technology professionals do for their work and career
- Massachusetts Institute of Technology
- University of Illinois
:max_bytes(150000):strip_icc():format(webp)/headshot-00415ba557444a8a9b6bb139498b97c5.jpg)
- The Wireless Connection
- Routers & Firewalls
- Network Hubs
- Installing & Upgrading
- Wi-Fi & Wireless
The terms "information technology" and "IT" are widely used in business and the field of computing. People use the terms generically when referring to various kinds of computer-related work, which sometimes confuses their meaning.
What Is Information Technology?
A 1958 article in Harvard Business Review referred to information technology as consisting of three basic parts: computational data processing, decision support, and business software. This time period marked the beginning of IT as an officially defined area of business; in fact, this article probably coined the term.
Over the ensuing decades, many corporations created so-called "IT departments" to manage the computer technologies related to their business. Whatever these departments worked on became the de facto definition of Information Technology, one that has evolved over time. Today, IT departments have responsibilities in areas like computer tech support, business computer network and database administration, business software deployment, and information security.
Especially during the dot-com boom of the 1990s, Information Technology also became associated with aspects of computing beyond those owned by IT departments. This broader definition of IT includes areas like software development, computer systems architecture, and project management.
Information Technology Jobs and Careers
Job posting sites commonly use IT as a category in their databases. The category includes a wide range of jobs across architecture, engineering, and administration functions. People with jobs in these areas typically have college degrees in computer science and/or information systems. They may also possess related industry certifications. Short courses in IT basics can be also be found online and are especially useful for those who want to get some exposure to the field before committing to it as a career.
A career in Information Technology can involve working in or leading IT departments, product development teams, or research groups. Having success in this job field requires a combination of both technical and business skills.
Issues and Challenges in Information Technology
- As computing systems and capabilities continue expanding worldwide, "data overload" has become an increasingly critical issue for many IT professionals. Efficiently processing huge amounts of data to produce useful business intelligence requires large amounts of processing power, sophisticated software, and human analytic skills.
- Teamwork and communication skills have also become essential for most businesses to manage the complexity of IT systems. Many IT professionals are responsible for providing service to business users who are not trained in computer networking or other information technologies but who are instead interested in simply using IT as a tool to get their work done efficiently.
- System and network security issues are a primary concern for many business executives, as any security incident can potentially damage a company's reputation and cost large sums of money.
Computer Networking and Information Technology
Because networks play a central role in the operation of many companies, business computer networking topics tend to be closely associated with Information Technology. Networking trends that play a key role in IT include:
- Network capacity and performance: The popularity of online video has greatly increased the demand for network bandwidth both on the Internet and on IT networks. New types of software applications that support richer graphics and deeper interaction with computers also tend to generate larger amounts of data and hence network traffic. Information technology teams must plan appropriately not just for their company's current needs but also this future growth.
- Mobile and wireless usages: IT network administrators must now support a wide array of smartphones and tablets in addition to traditional PCs and workstations. IT environments tend to require high-performance wireless hotspots with roaming capability. In larger office buildings, deployments are carefully planned and tested to eliminate dead spots and signal interference.
- Cloud services: Whereas IT shops in the past maintained their own server farms for hosting email and business databases, some have migrated to cloud computing environments where third-party hosting providers maintain the data. This change in computing model dramatically changes the patterns of traffic on a company network, but it also requires significant effort in training employees on this new breed of applications.
Get the Latest Tech News Delivered Every Day
- 5 Computer Networking Trends for 2024 and Beyond
- Should You Get a Consumer or Business Class PC?
- Is Linkedin Premium Worth It? 8 Reasons Why You Should Subscribe
- 6G: What It Is & When to Expect It
- How to Build a Career in Computer Networking and IT
- Introduction to Business Computer Networks
- What is a Wireless Network?
- Where Is 5G Available in China? (2024)
- Examining Computer Networking in Today's Schools
- SAN Explained — Storage (Or System) Area Networks
- No Degree? No Problem. Non-Traditional Paths Lead to Great Tech Careers
- Visual Index of Computer Networking Topics
- What Is Computer Networking?
- How to Start a Career in the Database Industry
- Introduction to Client Server Networks
- Data Science vs. Artificial Intelligence: What's the Difference?

- My presentations
Auth with social network:
Download presentation
We think you have liked this presentation. If you wish to download it, please recommend it to your friends in any social system. Share buttons are a little bit lower. Thank you!
Presentation is loading. Please wait.
Introduction Of Information Technology
Published by Shon Marshall Modified over 6 years ago
Similar presentations
Presentation on theme: "Introduction Of Information Technology"— Presentation transcript:

Lecture 2 - Revenue Models

1 of 15 Information Access Internal Information © FAO 2005 IMARK Investing in Information for Development Information Access Internal Information.

Internet Applications

DATA PROCESSING SYSTEMS

Living in a Digital World Discovering Computers 2010.

©2003 Prentice Hall Business Publishing, Accounting Information Systems, 9/e, Romney/Steinbart 18-1 Accounting Information Systems 9 th Edition Marshall.

Living in a Digital World Discovering Computers 2011.

James A. Senn’s Information Technology, 3rd Edition

Introduction To Information Technology. Defining Information What is Information? Information is any knowledge that comes to our attention. That could.

By the end of this, you should be able to state the difference between DATE and INFORMAITON.
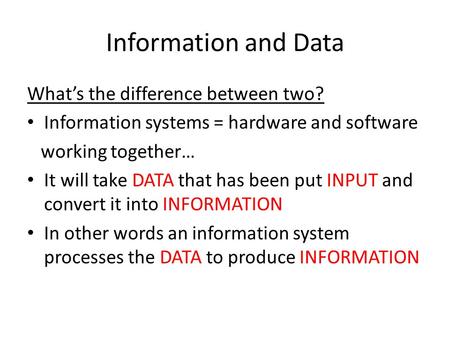
Information and Data What’s the difference between two? Information systems = hardware and software working together… It will take DATA that has been put.

Computer Jobs 2013 Bob Nielson. Average Wage The average wages of all jobs in America >>>> $45,790 > $80,180.

Computer Jobs 2014 Bob Nielson. Average Wage The average wages of all jobs in America >>>> $45,790 > $80,180.

CHAPTER 1 BUSINESS INFORMATION SYSTEM ; AN OVERVIEW.

Objectives Overview Identify the qualities of valuable information Describe various information systems used in an enterprise Identify the components of.

Module 3: Business Information Systems Chapter 8: Electronic and Mobile Commerce.
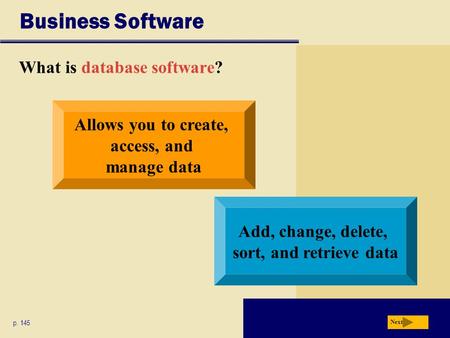
Business Software What is database software? p. 145 Allows you to create, access, and manage data Add, change, delete, sort, and retrieve data Next.

CDP Standard Grade1 Commercial Data Processing Standard Grade Computing Studies.

Chapter 1 Foundations of Information Systems in Business.

Introduction to IT Lecture – 01.
About project
© 2024 SlidePlayer.com Inc. All rights reserved.
Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

15 templates
49 templates

11 templates

39 templates

150 templates

ottoman empire
21 templates
Information Technology Lesson
It seems that you like this template, information technology lesson presentation, premium google slides theme, powerpoint template, and canva presentation template.
You know that we're surrounded by computers. Information technology, or IT, is an essential skill for students and professionals alike. However, teaching this complex topic effectively can be a challenge, especially when it comes to creating engaging and interactive lesson plans. But you have Slidesgo by your side! This template features customizable sections that cover a range of important IT concepts (provided that you later add actual content). It also includes easy-to-understand diagrams and charts that help students visualize complex concepts and data effectively.
Features of this template
- 100% editable and easy to modify
- 35 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides, Canva, and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the resources used
What are the benefits of having a Premium account?
What Premium plans do you have?
What can I do to have unlimited downloads?
Don’t want to attribute Slidesgo?
Gain access to over 25200 templates & presentations with premium from 1.67€/month.
Are you already Premium? Log in
Related posts on our blog

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access

Register for free and start editing online
- Question Papers
- Scholarships
Information Technology Presentation Topics (Updated)
Below is the list of information technology presentation topics. This updated list of IT-related presentation topics covers general, latest and best trends. Students & researchers can use these IT topics for PowerPoint (PPT) presentations, Webinars, Seminars, Conferences, Oral Speeches, Oral presentations, Individual or Group presentations. These ideas will definitely help students of MBA, MCA, BE, ME, BCA, & other IT courses to make a stunning presentation.
Latest Information Technology Topics For Presentation
Cloud Computing
Table of Contents
Artificial Intelligence
Data Privacy
Adding Intelligence to the Internet
Bio-inspired Networking
Sixth Sense Technology: New Reality
Finger Tracking In Real-Time Human-Computer Interaction
Fiber Distributed Data Interface
Virtualization
Cyberphysical Systems
Internet of Things (IoT)
Visualization Research
IT Governance
Cyberterrorism
3D Password
5G Technology: Hope Vs. Hype
Alphabetical List of IT Presentation Topics
Artificial Neural Network (ANN)
An Identity Based Eco-System
Free Space Laser Communications
Cellular Through Remote Control Switch
Breaking the Memory Wall in MonetDB
Buffer overflow attack : A potential problem and its Implications
Biometrics in SECURE e-transaction
10 Gigabit Ethernet
3D Internet
3D password
3D Printing
3D Television
4G Broadband
4G Technology: 4G Wireless Systems
5 Pen PC Technology
64-Bit Computing
AC Performance Of Nanoelectronics
Access gateways
Airborne Internet
Ambient Intelligence
Ambiophonics
Android: Future of Computing
Anonymous Communication
Asynchronous Chips
Attentionomics
Autonomic Computing
Barcode Technology
Biometric Voting System
Bio-Molecular Computing
BlackBerry Technology
Blu Ray Disc
Bluejacking
Brain Chips
Brain Fingerprinting
Broadband Over Power Line
Cable Modems
Capacitive And Resistive Touch Systems
Cellular Communications
Cellular Neural Network
Chameleon Chip
Cisco IOS Firewall
Cluster Computing
Code Division Duplexing
Combating Link Spam
Compact peripheral component interconnect
Computational Visual Attention Systems
Compute Unified Device Architecture CUDA
Conditional Access System
Content Curation and Aggregation
Content Marketing
corDECT Wireless in Local Loop System
Crusoe Processor
Cybernetic Organism
Data Compression Techniques
CyberTerrorism : New Challenge
Data Leakage Detection
Data Recovery
Data Security
Data Warehousing
Delay Tolerant Networking
Design and Analysis of Algoritms
Desktop Virtualization
Developer Integration
Development of the Intenet
Diamond Chip
Digital Audio Broadcasting
DNA Based Computing
Digital curation
Digital Jewelry
Digital Subscriber Line
Digital Watermarking
Driving Optical Network Evolution
Dual Core Processor
Dynamic Cache Management Technique
Dynamic Data Grid Replication Strategy
Dynamic Domain Name Service
Dynamic Languages
Dynamic Memory Allocation
Dynamic Synchronous Transfer Mode
Dynamic Virtual Private Network
Dynamically Reconfigurability Computing
Ethical Hacking
E Cash Payment Systems
Earth Simulator
E-Cash Payment System
Elastic Quotas
Electronic Banking
Enhancing LAN Using Cryptography and Other Modules
Enterprise social collaboration
Ethernet Passive Optical Network
Extended Mark Up Language
Extreme Programming (XP)
Eye Movement-Based Human Computer Interaction Techniques
Facebook Thrift
Fiber Channel
Fingerprints Technology
Fluorescent Multi-layer Disc
Free Space Optics
Gaming Consoles
Generic Access Network
Generic Framing Procedure
Generic Visual Perception Processor GVPP
Genetic Algorithms
Global Wireless E-Voting
Green Computing
Google Chrome OS
Google Glass Project
Google Strikes Back
Graph Separators
Graphical Password Authentication
Green Cloud
GSM 900 Mobile Jamme
Handheld Computers
High Altitude Aeronautical Platforms
High Performance DSP Architectures
Holographic Data Storage
Human Computer Interface
Holographic Memory
Hyper-Threading technology
Image Identification System
I-Cloud by Apple
In Vehicle Networking
Incognito mode
Infinite Dimensional Vector Space
Instant Messaging
Integer Fast Fourier Transform
Integrated Voice and Data
Intel Centrino Mobile Technology
Keyboard without Keys and Board
Ipv6 – The Next Generation Protocol
In-Vehicle Networking
Intel Core I7 Processor
Intelligent Software Agents
Intelligent Speed Adaptation
Internet Access via Cable TV Network
Internet of Things
Internet Telephony Policy in INDIA
The world of Internet Protocols
Intrusion Tolerance
Intrution Detection System
Intrution Detection Systems
Inverse Multiplexing
IP spoofing
IP Telephony
IPv6 Protocol
Iris Scanning
Java Database Connectivity
JOOMLA and CMS
Laptop Computer
Large Cloud Services
Layer 3 Switching
Light emitting polymers
Location Dependent Query Processing
Low Power UART Design for Serial Data Communication
Media Fragmentation
Migration From GSM Network To GPRS
Mobile Security
Mind Reading Computer
Mind-Reading Computer
MiniDisc system
Mobile Computing
Mobile Phone Cloning
Mobile Virtual Reality Service
Mobile WiMax
Mobile WiMAX
Modems and ISDN
Modular Computing
Money Pad, The Future Wallet
MPEG Video Compression
Multi Touch Technology
Multiterabit Networks
Nano Cars Into The Robotics
Nanorobotics
Network Security Firewalls
NVIDIA Tesla Personal Supercomputer
Network Traffic Analyzer
Neural Interfacing
Neural Networks And Their Applications
Nokia Morph
No-Touch Interfaces
Online Analytical Processing (OLAP)
Online Video Streaming
Open-source
Operating Systems
Optical Computer
Optical Fibre Cable
Optical Free Space Communication
Optical packet switch architectures
Optical Packet Switching Network
Optical Satellite Communication
Optical Switching
Orthogonal Frequency Division Multiplexing
Ovonic Unified Memory
Plagiarism Detection Techniques
Packet Sniffers
Palm Vein Technology
Parallel Computing In India
Parallel Databases
Param 10000
Personal Cloud Services
personal clouds accelerate
Phishing Technology
Pill Camera
Pivot Vector Space Approach in Audio-Video Mixing
Planar Separators
Plastic Memory
Platform Architectures
PON Topologies
Quantum Computing
Project Oxygen
Protein Memory
Public Key Infrastructure
Quantum Cryptography
QoS in Cellular Networks Based on MPT
Quadrics Interconnection Network
Quantum Information Technology
Real-Time Systems and Real-Time Operating Systems
Radio Frequency Light Sources
Radio Network Controller
RAIN technology
Rapid Prototyping
Real-Time Content
Refactoring
Resilient Packet Ring Technology
Robotic Surgery
Rover Technology
Satellite Radio
Seam Carving for Media Retargeting
Search by Image
Search Leads To Sales
Secure ATM by Image Processing
Security Features of ATM
Self Defending Networks
Self Organizing Maps
Self-Managing Computing
Semantic Digital Library
Sense-Response Applications
Sensors on 3D Digitization
Setting up a LAN using Linux
Short Message Service (SMS)
Significance of real-time transport Protocol in VOIP
Silent Sound Technology
Sixth Sense Technology
Social Networks That Are IT Policy Friendly
Skinput Technology
Smart Cards
Smart Fabrics
Smart Note Taker
Smart Pixel Arrays
Smart Quill
Sniffer for detecting lost mobiles
Social Literacy Skills
Social Media Privacy
Social Media Schizophrenia
Social Platforms
Socket Programming
Soft Computing
Software Reuse
Space Communications Protocol
Space Mouse
Speech Application Language Tags
Speed Detection of moving vehicle using speed cameras
Synchronous Optical Networking
Storage Area Networks
Store Management System
Structured Cabling
Surface Computer
Survivable Networks Systems
Swarm intelligence & traffic Safety
Synthetic Aperture Radar System
TCPA / Palladium
Tele Immersion
Tele-immersion
Tempest and Echelon
Terrestrial Trunked Radio
Text Mining
The integration Technology
Tsunami Warning System
The Mobile Revolution
Third Generation
Thought Leadership
Tool Command Language
Touch Screens
Transmedia Storytelling
Ubiquitous Networking
Ubiquitous Social Computing
Unicode And Multilingual Computing
Unified Modeling Language (UML)
Unlicensed Mobile Access
Viruses, vulnerabilities and security holes
Virtual Instrumentation
Virtual keyboard
Virtual LAN Technology
Virtual MArketing
Virtual Private Network
Virtual Reality
Visible Light Communication
Voice morphing
Voice Over Internet Protocol
Voice Portals
Voice Quality
Wearable Bio-Sensors
Wearable Technology
Why did Microsoft Surface fail?
Windows DNA
Evolution & Journey of MS Windows
Wireless Application Protocol
Wireless Fidelity
Wireless Internet
Wireless Networked Digital Devices
Zero-Knowledge Protocols and Proof Systems
Wireless Technology
Wireless USB
Wireless Video Service in CDMA Systems
Wolfram Alpha
Word Sense Disambiguation
Workplace Monitoring
X- Internet
XML Encryption
Yii Framework
Zettabyte FileSystem
ZigBee Technolgy
This is all about the latest information technology presentation topics for students, researchers and other professionals.
You’ll also like:

Share with friends

- Customer Favourites
Information Technology Presentation
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

- You're currently reading page 1

Stages // require(['jquery'], function ($) { $(document).ready(function () { //removes paginator if items are less than selected items per page var paginator = $("#limiter :selected").text(); var itemsPerPage = parseInt(paginator); var itemsCount = $(".products.list.items.product-items.sli_container").children().length; if (itemsCount ? ’Stages’ here means the number of divisions or graphic elements in the slide. For example, if you want a 4 piece puzzle slide, you can search for the word ‘puzzles’ and then select 4 ‘Stages’ here. We have categorized all our content according to the number of ‘Stages’ to make it easier for you to refine the results.
Category // require(['jquery'], function ($) { $(document).ready(function () { //removes paginator if items are less than selected items per page var paginator = $("#limiter :selected").text(); var itemsperpage = parseint(paginator); var itemscount = $(".products.list.items.product-items.sli_container").children().length; if (itemscount.
- 3D Man (655)
- Anatomy (104)
- Animated (1)
- Block Chain (89)
- Branding (167)


- CRLT Consultation Services
- Consultation
- Midterm Student Feedback
- Classroom Observation
- Teaching Philosophy
- Upcoming Events and Seminars
- CRLT Calendar
- Orientations
- Teaching Academies
- Provost's Seminars
- Past Events
- For Faculty
- For Grad Students & Postdocs
- For Chairs, Deans & Directors
- Customized Workshops & Retreats
- Assessment, Curriculum, & Learning Analytics Services
- CRLT in Engineering
- CRLT Players
- Foundational Course Initiative
- CRLT Grants
- Other U-M Grants
- Provost's Teaching Innovation Prize
- U-M Teaching Awards
- Retired Grants
- Staff Directory
- Faculty Advisory Board
- Annual Report
- Equity-Focused Teaching
- Preparing to Teach
- Teaching Strategies
- Testing and Grading
- Teaching with Technology
- Teaching Philosophy & Statements
- Training GSIs
- Evaluation of Teaching
- Occasional Papers

Presentation Technology
- Comparison of Tools
- Related Resources
- Faculty Examples
Presentation technology refers to a wide range of applications that enable instructors to display information during a lecture. Students also use these applications when they make presentations as part of class assignments. Used to help organize presentations, show examples, and provide visual interest, these applications usually allow for some combination of text and graphics as well as embedded video. While Microsoft PowerPoint is the most commonly used, there are a range of applications that fall under this category.
- Displaying lecture outlines, visual examples (photos, graphs, diagrams, videos) and/or instructions for classroom activities
- Displaying sample test questions or concept questions to check student understanding (possibly used with personal response systems)
- Creating opportunities for students to organize content and present to peers as part of a lecture
- Providing "skeletal" outlines that facilitate student notetaking
- Providing a resource that guides students' review of lecture material (alone or in connection with audio/video recordings of lecture)
- Microsoft PowerPoint
- Apple Keynote
- Google Slides
Tips for using slides effectively
While it is easy to create slides, it is also easy to overwhelm students with these programs. Common problems include showing far too many slides in a given time period, text-heavy slides that are often difficult to read, overuse of special effects, and slideshows that are designed to keep the instructor on track rather than supporting student learning.
In addition, slide-based lectures can put students in a very passive mode of trying to absorb and record large amounts of content without having the opportunities for active engagement and processing that are necessary for understanding and long-term retention of information. Finally, processing visuals (particularly text) at the same time as listening to a lecture can create cognitive overload that interferes with learning.
General Recommendations for Formatting Slides
- Use font size large enough to be visible, including captions and legends (look at your slides from the back of your actual classroom to check)
- Use legible color combinations (keep in mind when refering to different color items that some students are color blind)
- Use graphs rather than word-heavy charts when possible
- Display only essential information and limit the number of words/bullets per slide
- Use slides for outlines and examples rather than trying to capture every point you make
- Display only the information that will help students; find other ways to keep yourself on track for the presentation
- Distribute the slides or another outline-style handout in advance to facilitate note taking
- Avoid overly flashy transitions and special effects that can be distracting
- Have a backup plan should the technology fail
Recommendations from Research on Promoting Learning with PowerPoint
- Make slides available to students in advance of the lecture. Students retain more of a lecture when they have access to the instructor’s slides. When they do not have such handouts, students often try to copy down both the words on the slides and the notes from what they hear.
- Minimize the use of animation to introduce new points to a single slide. PowerPoint allows a presenter to reveal each bullet point on a slide separately. However, research indicates that such an approach leads to lower retention of information, possibly because there is less time to absorb all of the material on the slide.
- Use an assertion-evidence approach to constructing slides, instead of using the default format of a title followed by bullet subpoints. With this approach, the title becomes a 1-2 line sentence that makes an assertion. The rest of the slide shows evidence to support that assertion (preferably using visuals or a combination of visuals and short explanatory text). This approach helps avoid oversimplification inherent in PowerPoint’s linear approach.
- Segment your presentation and integrate active learning. This can range from simply pausing to allow the audience time to digest the material, to having students take a moment to write down what was confusing to them, answer “clicker” questions, discuss case studies, etc. CRLT’s website has a few resources for incorporating active learning into lectures. For examples of active learning, visit this page .
- Provide names and definitions of key terms in advance of the lecture. Such “pre-training” allows students to better understand a complex description of a how a system works as a whole.
- Weed out any extraneous information included in the presentation. Such extraneous information puts additional demands on working memory, and decreases the ability to process and retain information.
- Signal to your audience which information is incidental (e.g., an anecdote relating to the topic) and which is essential. This can be helpful in minimizing the cognitive load of the presentation so that students are better able to process important information.
- Make sure that on-screen images and text are well aligned and synchronized, and make explicit which text applies to which image. A mismatch between visuals and verbal explanations can cause interference rather than increasing understanding.
See also References:
- Chen, J., & Lin, T. (2011). Does downloading PowerPoint slides before the lecture lead to better student achievement? International Review of Economics Education, 10(1), 90-93.
- Mahar, S., Yaylacicegi, U., & Janicki, T. N. (2009). Less is more when developing PowerPoint animations. Information Systems Education Journal, 7(82), 1-11. [ http://isedj.org/7/82/ISEDJ.7(82).Mahar.pdf .]
- Mayer, R. E., & Moreno R. (2003). Nine ways to reduce cognitive load in multimedia learning. Educational Psychology, 38(1), 43-52.
- Raver, S. A., Maydosz, A. S. (2010). Impact of the provision and timing of instructor-provided notes on university students’ learning. Active Learning in Higher Education, 3, 189-200.
Tips for using Prezi (or other non-linear presentation technology) creatively
Suggestions on best uses and practices for using Prezi:
- build a resources and links (images, text, video) and build a variety of paths for connecting the material based on the audience and the place of the presentation in the curriculum;
- experiment with a non-linear approach to a presentation in which your path through the material is not predetermined but driven by the interests of the audience;
- use Prezi as an alternative to actually presenting, allowing audience members to work through the Prezi taking notes on important/useful points, and then engaing in a discussion in groups or with the whole class about the topic at hand;
- use Prezi for helping students organize material, either by having them take your Prezi and think about how they’d present it, or by asking them to go through the process of laying out important information and then organizing it into a Prezi (a much less rigidly linear process than using PowerPoint).
PowerPoint, Keynote and Google Slides offer similar linear presentation style defaults (i.e. one primarily works through the slides one-at-time from beginning to end). PowerPoint can work across PC and Mac platforms, while Keynote is Mac specific and also works with iPads. Google Slides is part of the Google Apps suite designed to promote collaboration. This is a very pared down version of a presentation tool that allows multiple people to collaborate on a single presentation and store files on the web so they are available anywhere. Files can be imported into PowerPoint and made more complex.
An alternative to these products is a non-linear presentation tool, Prezi. Prezi is a web-based tool with different logic from those described above. It is based on a non-linear "palette" onto which a presenter can paste up combinations of text, images, video. Nonlinearity allows for different paths through the same information and development of a presentation based on graphic overview and easy embedding of YouTube videos. However, non-linearity can be both a challenge and an opportunity depending on your topic, how you organize your ideas, and your teaching style. In addition, zoom functions can lead to sea sickness if not used well.
For specific information about using these technologies for teaching, see the links below:
PowerPoint Supported by the Science of Learning (1 hour 26 min): A presentation by Rachel Niemer, Assistant Director, CRLT
This video highlights Lola Eniola-Adefeso, Associate Professor in Chemical Engineering, using tablet PC and clickers in a large lecture course.

Contact CRLT
location_on University of Michigan 1071 Palmer Commons 100 Washtenaw Ave. Ann Arbor, MI 48109-2218
phone Phone: (734) 764-0505
description Fax: (734) 647-3600
email Email: [email protected]
Connect with CRLT

directions Directions to CRLT
group Staff Directory
markunread_mailbox Subscribe to our Blog
MIT Technology Review
- Newsletters
Five ways criminals are using AI
Generative AI has made phishing, scamming, and doxxing easier than ever.
- Melissa Heikkilä archive page

Artificial intelligence has brought a big boost in productivity—to the criminal underworld.
Generative AI provides a new, powerful tool kit that allows malicious actors to work far more efficiently and internationally than ever before, says Vincenzo Ciancaglini, a senior threat researcher at the security company Trend Micro.
Most criminals are “not living in some dark lair and plotting things,” says Ciancaglini. “Most of them are regular folks that carry on regular activities that require productivity as well.”
Last year saw the rise and fall of WormGPT , an AI language model built on top of an open-source model and trained on malware-related data, which was created to assist hackers and had no ethical rules or restrictions. But last summer, its creators announced they were shutting the model down after it started attracting media attention. Since then, cybercriminals have mostly stopped developing their own AI models. Instead, they are opting for tricks with existing tools that work reliably.
That’s because criminals want an easy life and quick gains, Ciancaglini explains. For any new technology to be worth the unknown risks associated with adopting it—for example, a higher risk of getting caught—it has to be better and bring higher rewards than what they’re currently using.
Here are five ways criminals are using AI now.
The biggest use case for generative AI among criminals right now is phishing, which involves trying to trick people into revealing sensitive information that can be used for malicious purposes, says Mislav Balunović, an AI security researcher at ETH Zurich. Researchers have found that the rise of ChatGPT has been accompanied by a huge spike in the number of phishing emails .
Spam-generating services, such as GoMail Pro, have ChatGPT integrated into them, which allows criminal users to translate or improve the messages sent to victims, says Ciancaglini. OpenAI’s policies restrict people from using their products for illegal activities, but that is difficult to police in practice, because many innocent-sounding prompts could be used for malicious purposes too, says Ciancaglini.
OpenAI says it uses a mix of human reviewers and automated systems to identify and enforce against misuse of its models, and issues warnings, temporary suspensions and bans if users violate the company’s policies.
“We take the safety of our products seriously and are continually improving our safety measures based on how people use our products,” a spokesperson for OpenAI told us. “We are constantly working to make our models safer and more robust against abuse and jailbreaks, while also maintaining the models’ usefulness and task performance,” they added.
In a report from February, OpenAI said it had closed five accounts associated with state-affiliated malicous actors.
Before, so-called Nigerian prince scams, in which someone promises the victim a large sum of money in exchange for a small up-front payment, were relatively easy to spot because the English in the messages was clumsy and riddled with grammatical errors, Ciancaglini. says. Language models allow scammers to generate messages that sound like something a native speaker would have written.
“English speakers used to be relatively safe from non-English-speaking [criminals] because you could spot their messages,” Ciancaglini says. That’s not the case anymore.
Thanks to better AI translation, different criminal groups around the world can also communicate better with each other. The risk is that they could coordinate large-scale operations that span beyond their nations and target victims in other countries, says Ciancaglini.
Deepfake audio scams
Generative AI has allowed deepfake development to take a big leap forward, with synthetic images, videos, and audio looking and sounding more realistic than ever . This has not gone unnoticed by the criminal underworld.
Earlier this year, an employee in Hong Kong was reportedly scammed out of $25 million after cybercriminals used a deepfake of the company’s chief financial officer to convince the employee to transfer the money to the scammer’s account. “We’ve seen deepfakes finally being marketed in the underground,” says Ciancaglini. His team found people on platforms such as Telegram showing off their “portfolio” of deepfakes and selling their services for as little as $10 per image or $500 per minute of video. One of the most popular people for criminals to deepfake is Elon Musk, says Ciancaglini.
And while deepfake videos remain complicated to make and easier for humans to spot, that is not the case for audio deepfakes. They are cheap to make and require only a couple of seconds of someone’s voice—taken, for example, from social media—to generate something scarily convincing.
In the US, there have been high-profile cases where people have received distressing calls from loved ones saying they’ve been kidnapped and asking for money to be freed, only for the caller to turn out to be a scammer using a deepfake voice recording.
“People need to be aware that now these things are possible, and people need to be aware that now the Nigerian king doesn’t speak in broken English anymore,” says Ciancaglini. “People can call you with another voice, and they can put you in a very stressful situation,” he adds.
There are some for people to protect themselves, he says. Ciancaglini recommends agreeing on a regularly changing secret safe word between loved ones that could help confirm the identity of the person on the other end of the line.
“I password-protected my grandma,” he says.
Bypassing identity checks
Another way criminals are using deepfakes is to bypass “know your customer” verification systems. Banks and cryptocurrency exchanges use these systems to verify that their customers are real people. They require new users to take a photo of themselves holding a physical identification document in front of a camera. But criminals have started selling apps on platforms such as Telegram that allow people to get around the requirement.
They work by offering a fake or stolen ID and imposing a deepfake image on top of a real person’s face to trick the verification system on an Android phone’s camera. Ciancaglini has found examples where people are offering these services for cryptocurrency website Binance for as little as $70.
“They are still fairly basic,” Ciancaglini says. The techniques they use are similar to Instagram filters, where someone else’s face is swapped for your own.
“What we can expect in the future is that [criminals] will use actual deepfakes … so that you can do more complex authentication,” he says.

Jailbreak-as-a-service
If you ask most AI systems how to make a bomb, you won’t get a useful response.
That’s because AI companies have put in place various safeguards to prevent their models from spewing harmful or dangerous information. Instead of building their own AI models without these safeguards, which is expensive, time-consuming, and difficult, cybercriminals have begun to embrace a new trend: jailbreak-as-a-service.
Most models come with rules around how they can be used. Jailbreaking allows users to manipulate the AI system to generate outputs that violate those policies—for example, to write code for ransomware or generate text that could be used in scam emails.
Services such as EscapeGPT and BlackhatGPT offer anonymized access to language-model APIs and jailbreaking prompts that update frequently. To fight back against this growing cottage industry, AI companies such as OpenAI and Google frequently have to plug security holes that could allow their models to be abused.
Jailbreaking services use different tricks to break through safety mechanisms, such as posing hypothetical questions or asking questions in foreign languages. There is a constant cat-and-mouse game between AI companies trying to prevent their models from misbehaving and malicious actors coming up with ever more creative jailbreaking prompts.
These services are hitting the sweet spot for criminals, says Ciancaglini.
“Keeping up with jailbreaks is a tedious activity. You come up with a new one, then you need to test it, then it’s going to work for a couple of weeks, and then Open AI updates their model,” he adds. “Jailbreaking is a super-interesting service for criminals.”
Doxxing and surveillance
AI language models are a perfect tool for not only phishing but for doxxing (revealing private, identifying information about someone online), says Balunović. This is because AI language models are trained on vast amounts of internet data, including personal data, and can deduce where, for example, someone might be located.
As an example of how this works, you could ask a chatbot to pretend to be a private investigator with experience in profiling. Then you could ask it to analyze text the victim has written, and infer personal information from small clues in that text—for example, their age based on when they went to high school, or where they live based on landmarks they mention on their commute. The more information there is about them on the internet, the more vulnerable they are to being identified.
Balunović was part of a team of researchers that found late last year that large language models, such as GPT-4, Llama 2, and Claude, are able to infer sensitive information such as people’s ethnicity, location, and occupation purely from mundane conversations with a chatbot. In theory, anyone with access to these models could use them this way.
Since their paper came out, new services that exploit this feature of language models have emerged.
While the existence of these services doesn’t indicate criminal activity, it points out the new capabilities malicious actors could get their hands on. And if regular people can build surveillance tools like this, state actors probably have far better systems, Balunović says.
“The only way for us to prevent these things is to work on defenses,” he says.
Companies should invest in data protection and security, he adds.
Artificial intelligence
Sam altman says helpful agents are poised to become ai’s killer function.
Open AI’s CEO says we won’t need new hardware or lots more training data to get there.
- James O'Donnell archive page
An AI startup made a hyperrealistic deepfake of me that’s so good it’s scary
Synthesia's new technology is impressive but raises big questions about a world where we increasingly can’t tell what’s real.
Taking AI to the next level in manufacturing
Reducing data, talent, and organizational barriers to achieve scale.
- MIT Technology Review Insights archive page
Is robotics about to have its own ChatGPT moment?
Researchers are using generative AI and other techniques to teach robots new skills—including tasks they could perform in homes.
Stay connected
Get the latest updates from mit technology review.
Discover special offers, top stories, upcoming events, and more.
Thank you for submitting your email!
It looks like something went wrong.
We’re having trouble saving your preferences. Try refreshing this page and updating them one more time. If you continue to get this message, reach out to us at [email protected] with a list of newsletters you’d like to receive.

The Bartlett School of Architecture
- Exhibitions
- Publications
- Equality, Diversity and Inclusion

Disguise Media Server Presentation: Industry Leading Solutions for Visual Experiences
28 May 2024, 5:00 pm–6:00 pm

An industry talk from visual experience platform Disguise, discussing their projects at the intersection of media, entertainment and technology, and the trends shaping these sectors.
This event is free.
Event Information
Availability.
We are in a new era of visual experiences. Disguise is a Emmy award-winning media/tech company whose technology platform delivers culturally impactful and large scaled immersive shows, productions and experiences. The company has worked on events from U2 at the Sphere, Taylor Swift and Beyoncé’s global tours, Coachella and Glastonbury main stages, and has over 400 virtual production studios globally delivering content for Apple, Warner Bros Discovery, Disney and Netflix and the largest immersive attractions and entertainment experiences.
In this industry talk, discover more about the company, its technology platform and groundbreaking projects and also hear more about the key macro and industry trends that are shaping the media, entertainment & technology sectors right now, from generative AI to spatial computing and the creator economy.
The event will feature talks from Alex Wills (Chief Experience Officer) and Roman Seling (Commercial Manager, Cloud, Platform and Software), with a short Q&A session at the end.
This event is open to all Bartlett students and staff.
Image: Disguise
Advertisement
Supported by
Nvidia, Powered by A.I. Boom, Reports Soaring Revenue and Profits
The Silicon Valley company was again lifted by sales of its artificial intelligence chips, but it faces growing competition and heightened expectations.
- Share full article

By Don Clark
Reporting from San Francisco
Nvidia, which makes microchips that power most artificial intelligence applications, began an extraordinary run a year ago.
Fueled by an explosion of interest in A.I., the Silicon Valley company said last May that it expected its chip sales to go through the roof. They did — and the fervor didn’t stop, with Nvidia raising its revenue projections every few months. Its stock soared, driving the company to a more than $2 trillion market capitalization that makes it more valuable than Alphabet, the parent of Google.
On Wednesday, Nvidia again reported soaring revenue and profits that underscored how it remains a dominant winner of the A.I. boom, even as it grapples with outsize expectations and rising competition.
Revenue was $26 billion for the three months that ended in April, surpassing its $24 billion estimate in February and tripling sales from a year earlier for the third consecutive quarter. Net income surged sevenfold to $5.98 billion.
Nvidia also projected revenue of $28 billion for the current quarter, which ends in July, more than double the amount from a year ago and higher than Wall Street estimates.
“We are fundamentally changing how computing works and what computers can do,” Jensen Huang, Nvidia’s chief executive, said in a conference call with analysts. “The next industrial revolution has begun.”
Nvidia’s shares, which are up more than 90 percent this year, rose in after-hours trading after the results were released. The company also announced a 10-for-1 stock split.
Nvidia, which originally sold chips for rendering images in video games, has benefited after making an early, costly bet on adapting its graphics processing units, or GPUs, to take on other computing tasks. When A.I. researchers began using those chips more than a decade ago to accelerate tasks like recognizing objects in photos, Mr. Huang jumped on the opportunity. He augmented Nvidia’s chips for A.I. tasks and developed software to aid developments in the field.
The company’s flagship processor, the H100, has enjoyed feverish demand to power A.I. chatbots such as OpenAI’s ChatGPT. While most high-end standard processors cost a few thousand dollars, H100s have sold for anywhere from $15,000 to $40,000 each, depending on volume and other factors, analysts said.
Colette Kress, Nvidia’s chief financial officer, said on Wednesday that it had worked in recent months with more than 100 customers that were building new data centers — which Mr. Huang calls A.I. factories — ranging from hundreds to tens of thousands of GPUs, with some reaching 100,000. Tesla, for example, is using 35,000 H100 chips to help train models for autonomous driving, she said.
Nvidia will soon begin to ship a powerful successor to the H100, code-named Blackwell, which was announced in March. Demand for the new chips already appears to be strong, raising the possibility that some customers may wait for the speedier models rather than buy the H100. But there was little sign of such a pause in Nvidia’s latest results.
Ms. Kress said demand for Blackwell was well ahead of supply of the chip, and “we expect demand may exceed supply well into next year.” Mr. Huang added that the new chips should be operating in data centers late this year and that “we will see a lot of Blackwell revenue this year.”
The comments may ease fears of a slowdown in Nvidia’s momentum.
“Lingering concerns investors had in the short term regarding an ‘air bubble’ for GPU demand seem to have vanished,” Lucas Keh, an analyst at the research firm Third Bridge, said in an email.
Wall Street analysts are also looking for signs that some richly funded rivals could grab a noticeable share of Nvidia’s business. Microsoft, Meta, Google and Amazon have all developed their own chips that can be tailored for A.I. jobs, though they have also said they are boosting purchases of Nvidia chips.
Traditional rivals such as Advanced Micro Devices and Intel have also made optimistic predictions about their A.I. chips. AMD has said it expects to sell $4 billion worth of a new A.I. processor, the MI300, this year.
Mr. Huang frequently points to what he has said is a sustainable advantage: Only Nvidia’s GPUs are offered by all the major cloud services, such as Amazon Web Services and Microsoft Azure, so customers don’t have to worry about getting locked into using one of the services because of its exclusive chip technology.
Nvidia also remains popular among computer makers that have long used its chips in their systems. One is Dell Technologies, which on Monday hosted a Las Vegas event that featured an appearance by Mr. Huang.
Michael Dell, Dell’s chief executive and founder, said his company would offer new data center systems that packed 72 of the new Blackwell chips in a computer rack, standard structures that stand a bit taller than a refrigerator.
“Don’t seduce me with talk like that,” Mr. Huang joked. “That gets me superexcited.”
Explore Our Coverage of Artificial Intelligence
News and Analysis
OpenAI said that it has begun training a new flagship A.I. model that would succeed the GPT-4 technology that drives its popular online chatbot, ChatGPT.
Elon Musk’s A.I. company, xAI, said that it had raised $6 billion , helping to close the funding gap with OpenAI, Anthropic and other rivals.
Google’s A.I. capabilities that answer people’s questions have generated a litany of untruths and errors — including recommending glue as part of a pizza recipe and the ingesting of rocks for nutrients — causing a furor online.
The Age of A.I.
D’Youville University in Buffalo had an A.I. robot speak at its commencement . Not everyone was happy about it.
A new program, backed by Cornell Tech, M.I.T. and U.C.L.A., helps prepare lower-income, Latina and Black female computing majors for A.I. careers.
Publishers have long worried that A.I.-generated answers on Google would drive readers away from their sites. They’re about to find out if those fears are warranted, our tech columnist writes .
A new category of apps promises to relieve parents of drudgery, with an assist from A.I. But a family’s grunt work is more human, and valuable, than it seems.
- My View My View
- Following Following
- Saved Saved
Elon Musk plans xAI supercomputer, The Information reports
- Medium Text

Sign up here.
Reporting by Mrinmay Dey in Bengaluru; Editing by Josie Kao
Our Standards: The Thomson Reuters Trust Principles. New Tab , opens new tab

Technology Chevron
Byd unveils new hybrid tech as battle with gasoline rivals heats up.
China's BYD launched on Tuesday the latest version of a plug-in hybrid technology that improves fuel and cost savings, intensifying competition with the likes of Toyota and Volkswagen that still sell mainly gasoline cars.


IMAGES
VIDEO
COMMENTS
This document provides an overview of information technology, including its history, present role, hardware and software components, advantages and disadvantages, and benefits. It traces the development of IT from the 1960s-1970s when the term was first used in banks and hospitals for data storage, to the 1980s introduction of personal ...
In general, information technology is a broad term that encompasses elements like digital communication, network administration, software components, and physical devices. Many of these hardware and software systems aim to accomplish one of the following three processes: Data mining. Data mining is the process of sorting and analyzing large ...
Information technology (IT) is the use of any computers, storage, networking and other physical devices, infrastructure and processes to create, process, store, secure and exchange all forms of electronic data.
Information technology is a broad term that involves the use of technology to communicate, transfer data and process information. The different trends within information technology include, but aren't limited to: Analytics. Automation. Artificial intelligence. Cloud computing. Communications.
Defining Information Technology. • Information Technologies are. systems of hardware and/or. software that capture, process, exchange, store and/or present. information using electrical, magnetic and/or electromagnetic. energy. IT Example: Cellular Telephony.
Information technology (IT)is a general term that describes any technology that helps to produce, manipulate, store, communicate, and/or disseminate information.IT merges computing with high-speed communications links carrying data, sound, and video. Examples of information technology include personal computers but also new forms of
Information Technology, more often referred to as IT, is about using technology to organize, store, share, and process information. Most people use IT every single day. You're using IT each time you connect to the internet, send an email, or print a document. 7 articles.
Information Technology, commonly referred to as IT, refers to the use of technology to organize, store, share, and process information. The IT industry is growing quickly as companies become more technology-based and the need to manage information becomes increasingly vital. Introduction to IT is geared towards complete beginners looking to ...
A 1958 article in Harvard Business Review referred to information technology as consisting of three basic parts: computational data processing, decision support, and business software. This time period marked the beginning of IT as an officially defined area of business; in fact, this article probably coined the term.
Information technology (IT) is a set of related fields that encompass computer systems, software, programming languages, and data and information processing, and storage. IT forms part of information and communications technology (ICT). An information technology system (IT system) is generally an information system, a communications system, or, more specifically speaking, a computer system ...
17 The Functions Of Information Technology By: L.Norah alsufyan =) Generation: The process of organizing information into a useful form, whether as numbers, text, sound, or visual image. Storage and Retrieval: Storage is the computer process of retaining information for future use. Retrieval is the process by which a computer locates and copies stored data or information for further processing ...
Lecture 1 Introduction to Information Technology.PPT.ppt - Free download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. This document provides an introduction to information technology and the history of computers. It discusses that information technology uses computers and communication links to spread information.
Premium Google Slides theme, PowerPoint template, and Canva presentation template. You know that we're surrounded by computers. Information technology, or IT, is an essential skill for students and professionals alike. However, teaching this complex topic effectively can be a challenge, especially when it comes to creating engaging and ...
4. Dyfo Technology Theme PowerPoint Template. A stark purple and black color scheme brings the audience's focus to your technology slide designs. Dyfo also includes one of the best bonuses for a tech PowerPoint template: p lenty of charts and graphs to show data.
Information Technology Security Ppt PowerPoint Presentation Complete Deck With Slides. This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of eighty one slides, this complete deck can help you persuade your audience.
Below is the list of information technology presentation topics. This updated list of IT-related presentation topics covers general, latest and best trends. Students & researchers can use these IT topics for PowerPoint (PPT) presentations, Webinars, Seminars, Conferences, Oral Speeches, Oral presentations, Individual or Group presentations.
The Technology presentations at SlideTeam cover all the latest and advanced technologies such as big data analytics, cloud computing, data centers, and many more. These technology presentations are created by conducting deep research about every topic to serve you with high-quality technology ppts. So explore and download Free Information ...
Information Technology Presentation found in: Information technology business documents processing management innovation communication, Information Technology Examples Business Powerpoint Presentation And Google Slides ICP,..
Presentation technology refers to a wide range of applications that enable instructors to display information during a lecture. Students also use these applications when they make presentations as part of class assignments. Used to help organize presentations, show examples, and provide visual interest, these applications usually allow for some ...
Learn Information Technology or improve your skills online today. Choose from a wide range of Information Technology courses offered from top universities and industry leaders. Our Information Technology courses are perfect for individuals or for corporate Information Technology training to upskill your workforce.
4. Information A form of communication that provides understandable and useful knowledge. Technology Is the sum of techniques, skills, methods, and processes used in the production of goods or services. Information Technology Is the use of computers, software and telecommunications to store, retrieve, transmit data. 5.
Bypassing identity checks. Another way criminals are using deepfakes is to bypass "know your customer" verification systems. Banks and cryptocurrency exchanges use these systems to verify that ...
Unleash the power of the dragon with our dynamic Powerpoint and Google Slides templates. Ideal for marketers and educators looking to make an impact in 2024, the Year of the Dragon. The illustrative design, coupled with vibrant hues of red and yellow, is sure to captivate your audience. Perfect for creating compelling marketing strategies or ...
We are in a new era of visual experiences. Disguise is a Emmy award-winning media/tech company whose technology platform delivers culturally impactful and large scaled immersive shows, productions and experiences. The company has worked on events from U2 at the Sphere, Taylor Swift and Beyoncé's ...
Mr. Huang frequently points to what he has said is a sustainable advantage: Only Nvidia's GPUs are offered by all the major cloud services, such as Amazon Web Services and Microsoft Azure, so ...
Information you can trust. Reuters, the news and media division of Thomson Reuters, is the world's largest multimedia news provider, reaching billions of people worldwide every day.
4. Systems and Process Specialist. Must have at least a Bachelor's degree in Computer Science, Information Technology, Engineering, or equivalent discipline/ course. With 10 years of relevant experience in application systems and process/software development for 5 projects.