
Strengthen your Zero Trust posture—a new, unified approach to security is here

Embrace proactive security with Zero Trust
Accelerate your Zero Trust implementation with best practices, the latest trends, and a framework informed by real-world deployments.
Why Zero Trust
Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the hybrid workplace, and protects people, devices, apps, and data wherever they’re located.
Productivity everywhere
Empower your users to work more securely anywhere and anytime, on any device.
Cloud migration
Enable digital transformation with intelligent security for today’s complex environment.
Risk mitigation
Close security gaps and minimize risk of lateral movement.
Zero Trust principles
Verify explicitly.
Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
Use least-privilege access
Limit user access with just-in-time (JIT) and just-enough access (JEA), risk-based adaptive polices, and data protection to help secure both data and productivity.
Assume breach
Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Build a secure hybrid workforce
Drive business agility with a Zero Trust approach to security.

Securely work from anywhere
Enhance the employee experience with adaptable security policies that help you effectively manage and protect all your devices and identities, no matter where people choose to work.

Safeguard your most critical assets
Secure your data even as it moves beyond your network with unified data protection and governance best practices.

Modernize your security posture
Reduce security vulnerabilities with expanded visibility across your digital environment, risk-based access controls, and automated policies.

Minimize the impact of bad actors
Safeguard your organization from both internal and external risks with a layered defense that explicitly verifies all access requests.

Get ahead of regulatory requirements
Keep up with the evolving compliance landscape with a comprehensive strategy that helps you seamlessly protect, manage, and govern your data.
What’s next in your Zero Trust journey?
Assess the Zero Trust maturity stage of your organization and receive targeted milestone guidance, plus a curated list of resources and solutions to move forward in your comprehensive security posture.

Zero Trust defined
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. Microsegmentation and least-privilege access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real time.
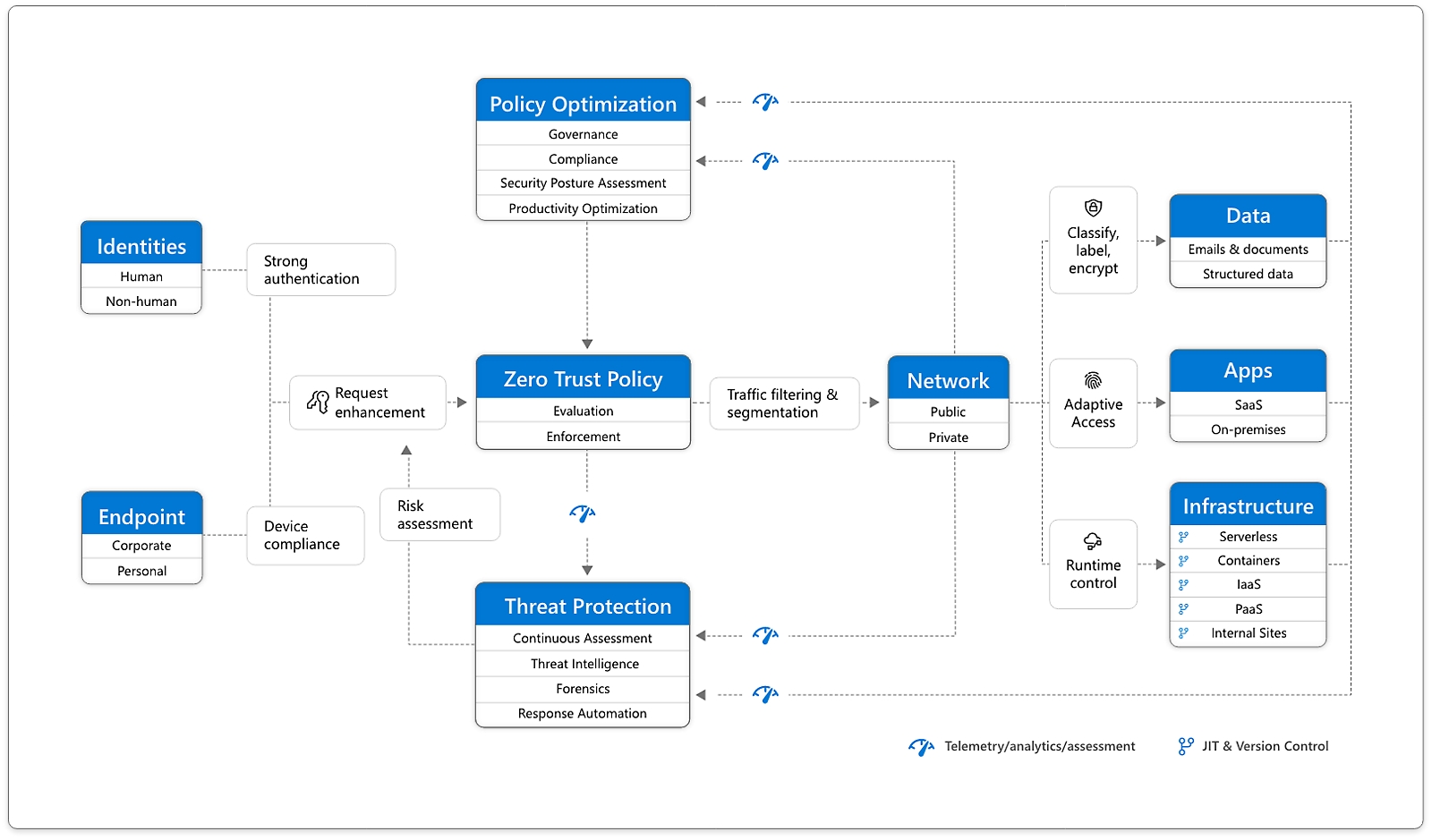
A holistic approach to Zero Trust should extend to your entire digital estate—inclusive of identities, endpoints, network, data, apps, and infrastructure. Zero Trust architecture serves as a comprehensive end-to-end strategy and requires integration across the elements.
The foundation of Zero Trust security is identities. Both human and non-human identities need strong authorization, connecting from either personal or corporate endpoints with compliant devices, requesting access based on strong policies grounded in Zero Trust principles of explicit verification, least-privilege access, and assumed breach.
As a unified policy enforcement, the Zero Trust policy intercepts the request, explicitly verifies signals from all six foundational elements based on policy configuration, and enforces least-privilege access. Signals include the role of the user, location, device compliance, data sensitivity, and application sensitivity. In addition to telemetry and state information, the risk assessment from threat protection feeds into the policy engine to automatically respond to threats in real time. Policy is enforced at the time of access and continuously evaluated throughout the session.
This policy is further enhanced by policy optimization. Governance and compliance are critical to a strong Zero Trust implementation. Security posture assessment and productivity optimization are necessary to measure the telemetry throughout the services and systems.
Telemetry and analytics feed into the threat protection system. Large amounts of telemetry and analytics enriched by threat intelligence generate high-quality risk assessments that can be either manually investigated or automated. Attacks happen at cloud speed and, because humans can’t react quickly enough or sift through all the risks, your defense systems must also act at cloud speed. The risk assessment feeds into the policy engine for real-time automated threat protection and additional manual investigation if needed.
Traffic filtering and segmentation is applied to the evaluation and enforcement from the Zero Trust policy before access is granted to any public or private network.
Data classification, labeling, and encryption should be applied to emails, documents, and structured data. Access to apps should be adaptive, whether SaaS or on-premises. Runtime control is applied to infrastructure with serverless, containers, IaaS, PaaS, and internal sites with JIT and version controls actively engaged. Finally, telemetry, analytics, and assessment from the network, data, apps, and infrastructure are fed back into the policy optimization and threat protection systems.
Zero Trust defense areas

Verify and secure each identity with strong authentication across your entire digital estate.

Gain visibility into devices accessing the network. Ensure compliance and health status before granting access.

Discover shadow IT, ensure appropriate in-app permissions, gate access based on real-time analytics, and monitor and control user actions.

Move from perimeter-based data protection to data-driven protection. Use intelligence to classify and label data. Encrypt and restrict access based on organizational policies.

Infrastructure
Use telemetry to detect attacks and anomalies, automatically block and flag risky behavior, and employ least-privilege access principles.

Ensure that devices and users aren’t trusted just because they’re on an internal network. Encrypt all internal communications, limit access by policy, and employ microsegmentation and real-time threat detection.
Demos and expert insights
Episode 1: zero trust essentials.
Learn about Zero Trust, the six areas of defense, and how Microsoft products can help in the first episode of Microsoft Mechanics’ Zero Trust Essentials series with host Jeremy Chapman.
Episode 2: Identity Controls
Get tips and watch demos of the tools for implementing the Zero Trust security model for identity and access management.
Episode 3: Endpoints and Applications
Learn more about defending endpoints and apps with Zero Trust, including product demonstrations from Microsoft.
Episode 4: Network and Infrastructure
Host Jeremy Chapman explains how to apply Zero Trust principles to your network and infrastructure using Microsoft Azure.
Episode 5: Data
Protect data across your files and content - in transit, in use and wherever it resides - with the Zero Trust security model.
Discover how customers are making Zero Trust a reality
Inform your strategy and adoption.

Implementing Zero Trust at Microsoft
Microsoft has adopted a Zero Trust strategy to secure corporate and customer data. The implementation centers on strong user identity, device health verification, validation of app health, and least-privilege access to resources and services.

Deploy, integrate, and develop
Take the next steps in your organization’s end-to-end implementation. with ourGo to the Zero Trust Guidance Center docs for deployment, integration, and app development documentation and best practices.

Compare your progress
Get the latest research on how and why organizations are adopting Zero Trust to help inform your strategy, uncover collective progress and prioritizations, and gain insights on this rapidly evolving space.
More resources
Zero Trust security blogs
Learn about the latest trends in Zero Trust in cybersecurity from Microsoft.
Microsoft Security Blog
Discover successful security strategies and valuable lessons learned from top experts.

US Executive Order
Explore resources for federal agencies to improve national cybersecurity through cloud adoption and Zero Trust.
Security Partners
Browse solution providers and independent software vendors to help you bring Zero Trust to life.

Zero Trust solutions
Learn about Microsoft solutions that support Zero Trust.
Frequently asked questions
What is zero trust.
Zero Trust is a modern security strategy based on the principle never trust, always verify. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network.
What are the main pillars of Zero Trust?
The three main pillars of Zero Trust are:
- Verify explicitly: always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least-privilege access: limit user access with just-in-time and just-enough-access, risk-based adaptive polices, and data protection to help secure data and improve productivity.
- Assume breach: verify end-to-end encryption and use analytics to gain visibility, detect threats, and improve defenses.
Why do organizations need Zero Trust solutions?
Organizations need Zero Trust solutions because security has become more complex. As increasing numbers of employees work remotely, it’s no longer sufficient to just protect the network perimeter. Organizations need adaptive solutions that fully authenticate and verify every access request and quickly detect and respond to threats both inside and outside the network.
What problem does Zero Trust solve?
Zero Trust helps solve the problem of greater complexity. Today’s organizations need to protect a growing volume of data across a multiplatform, multicloud environment. Risks to that data have increased as more companies turn to hybrid work and attacks become more sophisticated. Zero Trust helps simplify security with a strategy, processes, and automated tools that verify every transaction, enforce least-privilege access, and apply advanced detection and response to threats.
What is an example of Zero Trust network?
A Zero Trust network fully authenticates, authorizes, and encrypts every access request, applies microsegmentation and least-privilege access principles to minimize lateral movement, and uses intelligence and analytics to detect and respond to anomalies in real time.
What is an example of Zero Trust policy?
One of the most effective Zero Trust policies is multifactor authentication. Requiring that every user perform two or more forms of authentication (such as using a PIN on a known device) every time they sign in significantly decreases the risk that a bad actor with stolen credentials will gain access.
How do you implement a Zero Trust strategy?
Implementing a Zero Trust strategy starts with identifying business priorities and gaining leadership buy-in. It may take many years to complete the rollout, so it helps to start with easy wins and prioritize tasks based on business goals. An implementation plan will typically include the following steps:
- Roll out identity and device protection, including multifactor authentication, least-privilege access, and conditional access policies.
- Enroll endpoints in a device-management solution to ensure devices and apps are up to date and meet organizational requirements.
- Deploy an extended detection and response solution to detect, investigate, and respond to threats across endpoints, identities, cloud apps, and emails.
- Protect and govern sensitive data with solutions that provide visibility into all data and apply data loss prevention policies.
Go to the Zero Trust Guidance Center for additional resources.
What is the difference between Zero Trust and secure access service edge (SASE)?
SASE is a security framework that combines software-defined wide area networking (SD-WAN) and Zero Trust security solutions into a converged cloud-delivered platform that securely connects users, systems, endpoints, and remote networks to apps and resources.
Zero Trust, which is a modern security strategy that centers on verifying each access request as though it originates from an open network, is one component of SASE. SASE also includes SD-WAN, Secure web gateway, cloud access security broker, and firewall as a service, all centrally managed through a single platform.
What is the difference between Zero Trust and a virtual private network (VPN)?
A VPN is a technology that enables remote employees to connect to the corporate network.
Zero Trust is a high-level strategy that assumes that individuals, devices, and services that are attempting to access company resources, even those inside the network, cannot automatically be trusted. To enhance security these users are verified every time they request access, even if they were authenticated earlier.
Follow Microsoft Security
- Chat with sales
Available M-F 6 AM to 6 PM PT.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Zero Trust adoption framework overview
- 5 contributors

Digital transformation is shaping a new normal. Organizations are embracing digital transformation to manage continuous business environment changes by tracking:
- Shifting business models and partnerships.
- Technology trends.
- Regulatory, geopolitical, and cultural forces.
Additionally, COVID-19 remote work accelerated this transformation and is shifting security from a cost center to a strategic driver for growth.
Zero Trust is security for digital business. Digital transformation requires updating traditional security models because traditional security approaches don’t meet current requirements for business agility, user experiences, and continuously evolving threats. Organizations are implementing Zero Trust to address these challenges and enable the new normal of working anywhere, with anyone, at any time.
However, shifting from a traditional security model to Zero Trust represents a significant transformation that requires buy-in, adoption, and change management across an entire organization. Business leaders, technology leaders, security leaders, and security practitioners all play critical parts in creating an agile Zero Trust security approach.
Many security architects and IT teams ask for help with communicating to business leaders, tracking progress, and driving adoption. This guidance helps security and technology teams collaborate with business leaders on Zero Trust by providing:
- Recommended Zero Trust objectives for business leaders across organizations.
- A methodical and phased approach to implementing a Zero Trust architecture.
- A systematic way to track progress, scoped to business leaders.
- Curation of the most relevant resources for adoption of Zero Trust from slides that are ready to present to business leaders to technical implementation guidance and user infographics.
"Our goal is to help every organization strengthen its security capabilities through a Zero Trust architecture built on our comprehensive solutions that span identity, security, compliance, and device management across all clouds and platforms." –Satya Nadella, executive chairman and CEO of Microsoft
As a Microsoft partner, NBConsult contributed to and provided material feedback to this adoption guidance.
Zero Trust requires buy-in at the highest level
Zero Trust protects business assets wherever they are located and wherever they go. Zero Trust is a proactive, integrated approach to security that requires knowing what business assets and processes are most important to protect, and securing these while preserving business agility.
Adopting a Zero Trust approach requires buy-in across the C-suite. As the threat landscape expands, and critical attacks become more common, business leaders across functional areas are increasingly concerned with the cybersecurity approach their organization's take.
Zero Trust allows the entire C-suite and business to embrace a measurable business outcome that is aligned to reducing threats and increasing productivity.
Zero Trust adds value to two predominant scenarios that are seen in the marketplace:
- A formal security strategy aligned to business outcomes. This Zero Trust approach provides a holistic view on security to the entire business, through values that are shared across the business and adopted at every level from the top down. This is often CISO-led and business outcomes are tracked as part of the reporting function of Zero Trust in an ongoing manner.
- Delegated security to IT functions where security is treated as another technology vertical with minimal C-suite input and integration. This often focuses on short term cost optimization for security rather than managing it as a business risk, often further separating security into non-integrated "best of breed" independent solutions.
Zero Trust provides a way of integrating the vertical solutions into a single vision. This vision supports consistent business capabilities and outcomes and provides ongoing measurable metrics on the state of security.
Traditionally the CISO or IT/Security manager sets strategy, or at least security technology choices. However, buy-in from the other C-level leaders is required to justify additional "security" spending. Under the Zero Trust security strategy, other C-suite members are required to take part in the Zero Trust journey, understanding that security is a shared business responsibility aligned to business outcomes.
The following is a generalized view of the possible functions taken by various C-level functions and how they align to an integrated vision of security using Zero Trust.
| Role | Responsibility | Zero Trust interest |
|---|---|---|
| Chief Executive Officer (CEO) | Responsible for the business | Zero Trust provides an integrated approach to security across all digital layers. |
| Chief Marketing Officer (CMO) | Responsible for the marketing vision and execution | Zero Trust allows for the rapid recovery from breach and empowers the responsible reporting function for a public-facing organization, allowing breaches to be contained without reputational loss. |
| Chief Information Officer (CIO) | Responsible for IT as a whole | Zero Trust principles eliminate vertical security solutions that aren't aligned to business outcomes and enables Security as a Platform, which does align to business outcomes. |
| Chief Information Security Officer (CISO) | Responsible for security program implementation | Zero Trust principles provide a sufficient foundation for the organization to comply with various security standards and enables the organization to secure data, assets, and infrastructure. |
| Chief Technology Officer (CTO) | Chief Architect in the business | Zero Trust helps with defensible technology alignment aligned to business outcomes. Using Zero Trust, security is baked into every architecture. |
| Chief Operations Officer (COO) | Responsible for operational execution | Zero Trust helps with operational governance; the "how to" of the security vision and the surfacing of who did what and when. Both are aligned to business outcomes. |
| Chief Financial Officer (CFO) | Responsible for governance and spend | Zero Trust helps with the accountability of spend and the defensibility of spend; a measurable way of gaining a risk-based measure against security and Zero Trust spending aligned to business outcomes. |
Zero Trust principles for the C-suite
Zero Trust is a strategy and architecture based on three principles.
| Principle | Technical description | Business description |
|---|---|---|
| Verify explicitly | Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies. | This principle requires users to verify who they are, using more than one method, so that compromised accounts gained by hackers aren't allowed to access your data and apps. This approach also requires devices to be recognized as being allowed to access the environment and, ideally, to be managed and healthy (not compromised by malware). |
| Use least privileged access | Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive policies, and data protection to help secure both data and productivity. | This principle limits the blast radius of a potential breach so that if an account is compromised, the potential damage is limited. For accounts with greater privileges, such as administrator accounts, this involves using capabilities that limit how much access these accounts have and when they have access. It also involves using higher-levels of risk-based authentication policies for these accounts. This principle also involves identifying and protecting sensitive data. For example, a document folder associated with a sensitive project should only include access permissions for the team members who need it. These protections together limit how much damage can be caused by a compromised user account. |
| Assume breach | Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses. | This principle assumes the likelihood that an attacker will gain access to an account, identity, endpoint, application, API, or other asset. To respond, Microsoft protects all of the assets accordingly to limit the damage. This principle also involves implementing tools for ongoing threat detection and rapid response. Ideally these tools have access to signals integrated across your environment and can take automated actions, such as disabling an account, to reduce the damage as soon as possible. |
Zero Trust functional areas and technical architecture
The three principles of Zero Trust are applied across defense areas. These are sometimes referred to as functional areas or disciplines of IT management. Many organizations are structured around these areas with teams of specialized individuals.
Zero Trust requires taking an integrated approach across these areas and teams, which is why it's so important to have buy-in across the C-suite and a well-orchestrated strategy and plan across your organization.
| Functional area | Technical definition | Business translation |
|---|---|---|
| Identities | Human and non-human identities, including users, computers, and service principals. Anything that can authenticate. | Anything human or machine based that is able to sign in or use your services. |
| Endpoints | End user computing devices, including computers, laptops, mobile phones, and tablets. | The devices our users use to connect to your services and operate on your data. |
| Apps | Cloud or datacenter-based applications that require users to sign in and consume those services or applications. | All apps that are used by your organization, including SaaS apps that you subscribe to and other applications, whether in the cloud or on-premises. |
| Infrastructure | Infrastructure as a Service (IaaS) or datacenter-based infrastructure, including network components, servers, and data storage. | These are the technical foundations and components that support your organization, including physical and virtual servers hosted in your datacenter or a cloud service. |
| Data | Structured, unstructured, and application- contained data. | Your businesses data contained in files, databases, or other applications (such as CRM). |
| Network | LAN, WAN, wireless, or internet connection, including mobile (such as 3G and 5G) or even the coffee shop wireless network. | The network used to connect your users to the services they need. This might be a corporate-run local area network (LAN), the wider network encompassing access to your digital estate, or the internet connections used by your workers to connect. |
When applying Zero Trust strategy across a digital estate, it’s less helpful to think about tackling each of these domain areas independently. It’s not as if the identity team can accomplish all the recommendations and then the Zero Trust focus can move to the team that manages endpoints. Zero Trust strategy applies these functional areas together to secure an area within a digital estate and then broaden the scope of the protection across it.
For example, the identity team can only make so much progress in utilizing Microsoft Entra Conditional Access policies before coordinating with the endpoints team to weave together protection.
The following diagram integrates these functional areas into a unified Zero Trust architecture.
In the diagram:
- Each of the functional areas is represented: Identities, Endpoints, Network, Data, Apps, Infrastructure
- Zero Trust integrates protection across all the functional areas through policies and Policy Optimization.
- Threat protection brings together signals across the organization in real-time to provide visibility into attacks and to streamline remediation through automated actions and incident response tracking.
The next section discusses how to get started on the Zero Trust journey. We’ll use the Identities functional area as an example.
The Zero Trust adoption motion
Customers who are familiar with the Cloud Adoption Framework for Azure have asked, "Where’s the Zero Trust adoption framework?"
The Cloud Adoption Framework for Azure is a methodical process for introducing new apps and services into an organization. The focus is primarily on a proven process an organization can follow to introduce an app or service into the environment. The scale motion is repeating the process for each app that is added to a digital estate.
Adoption of a Zero Trust strategy and architecture requires a different scope. It's about introducing new security configurations across an entire digital estate . The scale motion is two dimensional:
- Taking a piece of the Zero Trust architecture, such as data protection, and scaling out this protection across the entire digital estate.
- Repeating the process with each additional piece of the Zero Trust architecture, starting with strategic quick wins and foundational pieces, and then advancing to more complex pieces.
Like the Cloud Adoption Framework for Azure, this Zero Trust adoption guidance addresses the work through adoption scenarios as described in the next section.
The following diagram summarizes the differences between these two types of adoption motions.
This Zero Trust adoption guidance uses the same lifecycle phases as the Cloud Adoption Framework for Azure but adapted for Zero Trust.
The following table describes the lifecycle phases.
| Lifecycle phase | Description |
|---|---|
| Define strategy | Build a business case focused on the outcomes most closely aligned with your organization’s risks and strategic goals. |
| Plan | |
| Ready | |
| Adopt | Incrementally implement the strategy across functional areas. |
| Govern | Track and measure the success of your deployment. |
| Manage |
Business scenarios
This Zero Trust adoption guidance recommends building a Zero Trust strategy and architecture through these business scenarios:
- Rapidly modernize your security posture
- Secure remote and hybrid work
- Identify and protect sensitive business data
- Prevent or reduce business damage from a breach
- Meet regulatory and compliance requirements
Each business scenario is described in an article that describes how to progress the technical work through each of the lifecycle phases, starting with building the business case. The most appropriate resources are provided along the way.
Each of these business scenarios breaks down the work of Zero Trust into manageable pieces that can be implemented over four implementation stages. This helps you prioritize, move forward, and track work as you move through the different layers of implementing a Zero Trust architecture.
This guidance includes a PowerPoint slide deck with progress slides that you can use to present the work and track your progress at a high level for business leaders and other stakeholders. The slides include features that help you keep track of and present progress to stakeholders. Here's an example.
This guidance also includes an Excel workbook with worksheets for each business scenario that you can use to assign owners and track progress for each stage, objective, and task. Here's an example.
Across the business scenarios, the implementation stages are roughly aligned so that accomplishing the objectives of Stage 1 across the scenarios help keep your organization progressing on all fronts together.
Starting a Zero Trust journey
If you're embarking on a Zero trust journey that is aligned to a business scenario or looking to embrace Zero Trust as a strategic defense doctrine, success can be difficult to measure. This is because security doesn't pass a simple pass/fail type of evaluation. Rather, security is a commitment and a journey, to which Zero Trust supplies guiding principles.
Using this adoption guidance as a process framework, first establish and document our security strategy, very similar to a Project Initiation Document (PID). Using the principles that apply to strategy, at minimum, you should document:
- What are you doing?
- Why are you doing it?
- How do you agree on and measure success?
Each business scenario encompasses a different set of assets with different tools to take inventory. Methodically, you begin with an inventory and classification of the assets for each business scenario:
- Asset Identification: What assets do you want to protect, such as identities, data, apps, services, and infrastructure? You might use the functional areas called out above as a guide of where to start. Asset identification forms part of your Define strategy and Plan lifecycle phases. The Define strategy phase can articulate a specific scenario, while the Plan phase documents the digital estate.
- Asset Classification: How important is each one of the identified assets, such as identities, business critical data, and human resources data? Asset classification is part of the Ready phase where you begin to identify the protection strategy for each asset.
- Asset Management: How do you choose to protect (govern) and administer (manage) these assets?
- Asset Recovery: How do you recover from compromise or loss of control of an asset (govern)?
Each business scenario recommends how to take inventory as well as how to protect the assets and report on progress. While there's inevitably some overlap across the business scenarios, this adoption guidance attempts to simplify as much as possible by addressing asset types in predominantly one business scenario.
Tracking progress
Tracking your progress throughout the Zero Trust adoption process is crucial as it allows your organization to monitor and measure strategic goals and objectives.
What to track and measure
Microsoft recommends taking two approaches to tracking your progress:
- Measure your progress against mitigating risks to your business.
- Measure your progress towards achieving strategic objectives across the Zero Trust architecture.
Many organizations use International Organization for Standardization (ISO) standards resources and tools to gauge an organization’s risk. Specifically:
ISO/IEC 27001:2022
- Information security, cybersecurity, and privacy protection
- Information security management systems
- Requirements
- Risk management
The requirements and guidelines in these standards are generic and can apply to any organization. They provide a structured and comprehensive way for you to review and gauge the risks that apply to your organization, as well as mitigations.
Identifying and understanding the specific risks that apply to your organization will help you prioritize your most strategic objectives across the Zero Trust architecture.
How to track and measure
Once your organization has identified and prioritized your most strategic technical objectives, you can map out a staged roadmap for implementation. You can then track your progress by using various tools.
Customizable tracking reports
Microsoft provides customizable PowerPoint and Excel tracking tools. These are pre-populated with objectives and tasks, organized by Zero Trust business scenarios. You can customize these with your own priorities, objectives, and team members.
- Business leader tracker — A downloadable PowerPoint slide deck with progress tracking slides. These are designed to help you track and communicate progress at a high level. Customize these slides for your own use.
- Implementer tracker — A downloadable Excel workbook to assign ownership and track your progress through the stages, objectives, and tasks. For business scenario project leads, IT leads, and IT implementers.
In-product dashboards
Microsoft Security Exposure Management is a security solution that provides a unified view of security posture across company assets and workloads. Within this tool, Security Initiatives help you assess readiness and maturity in specific areas of security risk. Security Initiatives take a proactive approach to managing security programs towards specific risk or domain-related objectives.
Use the Zero Trust initiative to track your organization’s progress toward implementing Zero Trust security. This initiative is aligned with this Microsoft Zero Trust adoption framework, allowing you to track your progress with metrics aligned with business scenarios. These metrics capture your resource coverage across prioritized actionable recommendations to help security teams protect their organization. The initiative also provides real-time data on your Zero Trust progress that can be shared with stakeholders.

For more information about how to use the Zero Trust initiative within the Exposure Management tool, see Rapidly modernize your security posture — Track and measure .
Additionally, several other portals and reports can assist you in creating an overview of risk within your business, including:
- The Critical Asset Protection initiative in Microsoft Security Exposure Management brings together critical asset risk across Defender products and areas.
- Reports within Microsoft Defender XDR provide information regarding security trends and track the protection status of your identities, data, devices, applications, and infrastructure.
- The Cloud Security Explorer allows you to proactively hunt for security risks.
For example, within Microsoft Defender XDR, the device inventory provides a clear view into newly discovered devices in your network that aren't yet protected. At the top of each Device inventory tab, you can see the total number of devices that aren't onboarded. Here's an example.

For more information on using Microsoft Defender XDR to track your progress, see Strengthen your security posture with Microsoft Defender XDR .
Note that the progress percentages provided by in-product tools might not be accurate for organizations that aren't willing to implement all controls due to reasons such as:
- Scope of the business
Additional articles for adoption
- Secure remote and hybrid work with Zero Trust
Progress tracking resources
For each business scenario, you can use the following progress tracking resources.
| Progress tracking resource | That helps you… | Designed for… |
|---|---|---|
| Adoption Scenario Plan Phase Grid downloadable or | Easily understand the security enhancements for each business scenario and the level of effort for the stages and objectives of the Plan phase. | Business scenario project leads, business leaders, and other stakeholders. |
| Zero Trust adoption tracker | Track your progress through the stages and objectives of the Plan phase. | Business scenario project leads, business leaders, and other stakeholders. |
| Business scenario objectives and tasks | Assign ownership and track your progress through the stages, objectives, and tasks of the Plan phase. | Business scenario project leads, IT leads, and IT implementers. |
For additional resources, see Zero Trust assessment and progress tracking resources .
Additional Zero Trust documentation
See additional Zero Trust content based on a documentation set or your role in your organization.
Documentation set
Follow this table for the best Zero Trust documentation sets for your needs.
| Documentation set | Helps you... | Roles |
|---|---|---|
| for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. | IT teams and security staff |
| Apply Zero Trust principles to small business customers. | Customers and partners working with Microsoft 365 for business | |
| for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. | Security architects and IT implementers |
| for stepped and detailed design and deployment guidance | Apply Zero Trust protections to your Microsoft 365 tenant. | IT teams and security staff |
| for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. | IT teams and security staff |
| for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. | IT teams and security staff |
| for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. | Partner developers, IT teams, and security staff |
| for application development design guidance and best practices | Apply Zero Trust protections to your application. | Application developers |
Follow this table for the best documentation sets for your role in your organization.
| Role | Documentation set | Helps you... |
|---|---|---|
| Member of an IT or security team | for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. |
| Customer or partner for Microsoft 365 for business | Apply Zero Trust principles to small business customers. | |
| Security architect IT implementer | for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. |
| Member of an IT or security team for Microsoft 365 | for stepped and detailed design and deployment guidance for Microsoft 365 | Apply Zero Trust protections to your Microsoft 365 tenant. |
| Member of an IT or security team for Microsoft Copilots | for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. |
| Member of an IT or security team for Azure services | for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. |
| Partner developer or member of an IT or security team | for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. |
| Application developer | for application development design guidance and best practices | Apply Zero Trust protections to your application. |
Was this page helpful?
Additional resources

IMAGES
VIDEO
COMMENTS
This new business plan provides a practical guide to implementing a Zero Trust framework. Our Zero Trust deployment guidance provides clear technical implementation guidance.
This article provides a deployment plan for building Zero Trust security with Microsoft 365. Zero Trust is a new security model that assumes breach and verifies each request as though it originated from an uncontrolled network.
Get the Zero Trust Business Plan. Zero Trust principles. Verify explicitly. Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies. Use least-privilege access.
Develop a multiyear business plan to: Prioritize quick wins. and incremental progress for each initiative. Embrace existing technologies. already deployed or licensed. Structure coherent initiatives. with clear outcomes, benefits, and ownership. Adopting Zero Trust.
This article describes Zero Trust deployment guidance and resources for customers and partners working with Microsoft 365 Business Premium and other technologies commonly used by small- to medium-sized business customers.
This guidance helps security and technology teams collaborate with business leaders on Zero Trust by providing: Recommended Zero Trust objectives for business leaders across organizations. A methodical and phased approach to implementing a Zero Trust architecture.