Newly Launched - AI Presentation Maker

Researched by Consultants from Top-Tier Management Companies

Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Top 7 Company Credentials Examples with Templates and Samples

Monika Rajput
Every business should have its foundational company credentials. These are the details that no one must overlook because they help define your brand in the market and give an overall idea of your company's vision, achievements, and aspirations. These credentials also contribute to building trust among clients, investors, and partners. Such credentials include your market value, registration number, and headquarters country.
At SlideTeam, we understand how important it is to present these effectively, so we offer templates designed to highlight your company's journey and vision. Using these templates, you can ensure that your company credentials are not just stated but also presented in a way that attracts the target audience. They have a structure yet are versatile, which makes them ideal for emphasizing your journey and vision.
The good news is that our templates are 100% customizable and easy to edit. They come ready to use but can be tweaked to fit your audience perfectly.
Let’s check them out!
Template 1: Procurement Services Provider: Our Procurement Company's Credentials
This PPT template is made to exhibit what sets your procurement process apart from others. It also gives you a clear method for expressing your company vision, market value, presence, and registration number details, which are crucial in building trust. It will take you through sharing the story of your company, relevant procurement services, and why you are different from others. Get this template to talk to new clients, partners, or investors about the best things your company does and how much it would like to be the best in procurement processes. Moreover, it offers editable icons and simple instructions that allow changes as per your needs.

DOWNLOAD TEMPLATE
Template 2: Company Credentials Layout with Central Leaf Icon
A leafy central icon in this template has unique layout. Created as a one-step process, it is quick and easy to present those achievements and other credentials for your company. Being aligned with the values or visions of a company, the centre leaf icon integrates visually appealing elements that also represent growth, progress, and renewal. The versatility of this template lies in that it can be presented according to your needs by leveraging numerous editable icons suitable for different themes. Would you like to have a neat overview? Perfect choice! Get it now if you need an outstanding way to show off what makes your company stand out!
DOWNLOAD TEMPLATE
Make sure to concentrate on the elementary things and express the distinguishing factors of your company for an exceptional procurement company profile. Check this blog out for some examples and tips on how to show your company’s unique aspects better.
Template 3: Company Introduction Moviemaking Company Profile PPT Ideas
This presentation template offers a comprehensive overview of a film production company while emphasizing its commitment to core principles of integrity, innovation, and recognition. It explains the market segment, headquarters and founding year, and where its production houses are situated. We have designed these slides for extended discussions over important issues such as teamwork, innovation, recognition, and authenticity. This template is flexible enough to let you customize your presentation according to your audience's needs. Moreover, you can use this in narrating the story of your company and what principles lie at the heart of the filmmaking process. Download this presentation now and bring your company profile alive by capturing what makes your production house stand out amidst other players within the competitive film industry.

This blog has effective strategies for software companies looking to present innovation that can help you share your company vision and story.
Template 4: Company Profile For Construction Machinery Proposal Template
In order to make a compelling business proposal or company profile, you can highlight your strong points, including company vision, market value, and headquarters country as a construction machinery company in the PPT deck. This turns an international or local presence into a matter of fact. Simultaneously, this adds an element of trust by having the registration number in it. In delivering a concise and focused presentation, this template addresses five stages: Background, Company Vision, Our Focus, Company Mission, and Certifications and Memberships. It is ideal for construction machinery companies that are looking for contracts or expanding their service offerings to clients because it is fully customizable. A company stands out when its unique selling points professionally correspond to the customers. Get this deck for a standout and professional presentation!

Consider this blog for examples and templates on how to give a description of your company in terms of stories and facts.
Template 5: Company Overview Software Company Profile PPT Clipart
The slide is a must-have for software companies. It does a good job of summarizing crucial facts, e.g., name, incorporation year, headquarters country, and industry it operates in. The presentation goes further to provide details about the profile of the CEO, website address, company type, and ticker symbol, as well as financial aspects such as revenue streams, profitability ratios, and market value. More than that, your company's achievements can be seen from some awards or recognition pointing out its superiority. Designed to communicate detailed conversations on the Company Overview, this slide combines informative content with attractive creative design. Obtain a complete overhaul of your company by using this slide; it's fully editable to align with your company's specific branding and messaging needs.

Templae 6: Six Steps Company Credentials Diagram Using Hexagonal Shapes
This PPT deck is perfect for companies who want to present their credentials to the audience in an attractive manner. It has been custom-made with hexagonal shapes. The 6-Step Company Credentials Diagram showcases important company information like credentials, diplomas, and certificates. Moreover, hexagonal shapes also make it easier for businesses to highlight essential parts of their profiles in a coordinated manner, adding beauty to them. The presentation is ideal for your company when you need to communicate qualifications and achievements briefly. Choose this deck as the best solution for displaying your company's qualifications or calling cards in a way that everyone can easily comprehend.

Template 7: Company Credentials Info Graphic Using Rectangular Boxes Having Icons
This template features clarity and efficiency by which you can present your company credentials through rectangular boxes consisting of icons. It is an eight-step process that manages important information about a company, such as credentials, diplomas, and certificates. Each phase has its own icon, which makes it easy to understand what your organization stands for and its main achievements. This method of infographics not only makes complicated information simpler but also ensures that it is visually attractive to the audience so that they can pay attention to it. Download this template if you want to illustrate your company's capabilities and professional success in a clear yet impactful way. This template also helps ensure that the strong points and values are effectively communicated and properly understood.
Improve Your Efficiency
When it comes to making your company stand out, however, most of the attempts are centred on how you tell its narrative as well as the core elements (company vision, credentials, registration number, market value, and location). This is where a solid presentation can really help.
SlideTeam templates are designed just for you. Our templates will give you just what you need at this moment. They can easily be edited according to your style and language requirements, thus talking straight to the target audience. Whether it is about displaying the company vision, its market value, or where it is located, these templates are handy whenever you want to put everything across clearly and easily.
Related posts:
- Must-Have Product Brochure Templates for Advertising and Promotion
- Must-Have Brand Identity Proposal Templates With Examples and Samples!
- Top 10 Business Flyer Templates with Samples and Examples
- The What, Why & How Of Branding Explained
Liked this blog? Please recommend us

Top 10 Introducing Yourself Templates with Examples and Samples
Top 10 Staff Augmentation Templates with Examples and Samples
This form is protected by reCAPTCHA - the Google Privacy Policy and Terms of Service apply.

--> Digital revolution powerpoint presentation slides

--> Sales funnel results presentation layouts
--> 3d men joinning circular jigsaw puzzles ppt graphics icons

--> Business Strategic Planning Template For Organizations Powerpoint Presentation Slides

--> Future plan powerpoint template slide

--> Project Management Team Powerpoint Presentation Slides

--> Brand marketing powerpoint presentation slides

--> Launching a new service powerpoint presentation with slides go to market

--> Agenda powerpoint slide show

--> Four key metrics donut chart with percentage

--> Engineering and technology ppt inspiration example introduction continuous process improvement

--> Meet our team representing in circular format

The Ultimate Guide: Advertising Agency Credentials Presentation Explained
- Post author By support
- Post date September 9, 2023

In today’s competitive business landscape, advertising agencies need to go beyond their creative ideas and stunning campaigns to truly stand out.
Enter the advertising agency credentials presentation, a powerful tool that showcases an agency’s expertise, accomplishments, and unique value proposition.
But what makes a credentials presentation truly effective?
How can agencies captivate their audience and leave a lasting impression?
Join us as we delve into the art of crafting a tailored presentation that not only highlights an agency’s credentials but also connects with the audience on a deeper level.
Get ready to unleash the secrets of a winning credentials presentation, guaranteed to leave your prospective clients begging for more!
advertising agency credentials presentation
The advertising agency credentials presentation is a crucial tool for showcasing the expertise and value of an agency to potential clients.
It aims to give a swift boost to the brand name and emphasizes the importance of tailoring the presentation to the audience’s specific needs and goals.
The advantage of flexibility offered by credentials decks is noted, and nine steps for building a persuasive presentation are provided.
Prioritizing the audience’s interests and motivations is recommended, with personalized touches on the first page and a navigation system that addresses their pain points or offers case studies.
Showcasing the behind-the-scenes process and turning the agency’s offerings into tangible business benefits are emphasized.
Testimonials and a concise, problem-solving approach are powerful in convincing potential clients, while leaving the ‘About Us’ section until the end is suggested.
The presenter’s authenticity, knowledge, tone, body language, confidence, and aura play a significant role in engaging the audience.
Optional extras for the presentation are also mentioned.
Key Points:
- Advertising agency credentials presentation is a crucial tool for showcasing expertise and value to potential clients
- Tailoring the presentation to the audience’s needs is important
- Flexibility of credentials decks is advantageous
- Prioritizing the audience’s interests and motivations is recommended
- Showcasing the behind-the-scenes process and turning offerings into tangible benefits are emphasized
- Testimonials and a problem-solving approach are powerful in convincing potential clients
Sources 1 – 2 – 3 – 4
💡 Did You Know?
1. The first recorded use of advertising can be traced back to ancient Egypt, where papyrus was used to create sales messages and posters to promote goods in marketplaces.
2. The phrase “keeping up with the Joneses” originated from an advertisement campaign by a New York advertising agency in the early 20th century. It popularized the idea of competing with neighbors to own the latest products and keeping a high social status.
3. The “Got Milk?” advertising campaign, which began in 1993, is considered one of the most successful and recognized campaigns in the history of advertising. It increased milk sales in the United States by over 7% within just one year.
4. The first-ever television commercial aired in the United States on July 1, 1941, during a broadcast of a Brooklyn Dodgers baseball game. It was an advertisement for Bulova watches and lasted only 10 seconds.
5. A famous advertising agency in London , Saatchi & Saatchi, created the iconic slogan “Just Do It” for Nike in 1988. The slogan was inspired by the last words of a murderer before he was executed, as the agency wanted to capture the essence of determination and action.
Rebranding Presentation For She World Advertising Agency
In the world of advertising, a rebranding presentation holds immense significance. It is a crucial opportunity for an advertising agency to showcase its abilities and make a lasting impression on potential clients . One such agency that recently underwent a rebranding presentation is She World Advertising Agency .
She World, a name that resonates with power and confidence, chose to emphasize these qualities in their rebranding. The presentation revolved around a bold and arrogant female character , perfectly capturing the essence of the agency’s identity. This character, featured prominently with a striking purple eyeline, symbolized the agency’s willingness to break stereotypes and push boundaries.
Here are some key points about the She World Advertising Agency rebranding presentation:
- A rebranding presentation is crucial in the world of advertising.
- It provides an opportunity to showcase an agency’s abilities and make a lasting impression on potential clients.
- She World Advertising Agency recently underwent a rebranding presentation.
- The presentation focused on a bold and arrogant female character.
- This character symbolized the agency’s willingness to break stereotypes and push boundaries.
“The presentation revolved around a bold and arrogant female character, perfectly capturing the essence of the agency’s identity.”
Emphasizing A Bold And Arrogant Female Character With Purple Eyeline
The choice of a bold and arrogant female character with a purple eyeline as the centerpiece of She World’s rebranding presentation was a strategic move . It aimed to leave a lasting impression on the audience and establish a unique identity for the agency. By embracing these qualities, She World showcased its fearlessness and determination to challenge traditional norms in the advertising industry.
The purple eyeline served as a visual representation of the agency’s creativity and innovation . It symbolized the agency’s ability to think outside the box and create unique and impactful campaigns. This striking visual element caught the attention of the audience and effectively conveyed the agency’s message of empowerment and confidence .
- The choice of a bold and arrogant female character
- The strategic move to leave a lasting impression
- Establishing a unique identity for the agency
- Embracing fearlessness and determination
- Visual representation of creativity and innovation
- Symbolism of thinking outside the box
- Creating unique and impactful campaigns
- Catching the attention of the audience
- Conveying a message of empowerment and confidence.
Swift Boost To Brand Name As The Aim Of The Presentation
The primary objective of She World’s rebranding presentation was to give a swift boost to the agency’s brand name . The agency recognized that in a competitive industry, establishing a strong brand presence is essential for success. Therefore, the presentation was meticulously curated to position She World as a reputable and influential player in the advertising realm.
The presentation showcased the agency’s portfolio of successful campaigns to enhance their credibility and demonstrate their expertise . By highlighting their past achievements , She World aimed to instill confidence in potential clients and showcase their ability to deliver exceptional results . This swift boost to the brand name would ultimately attract new clients and facilitate future business growth .
Importance Of A Tailored Advertising Agency Credentials Presentation
In the world of advertising, a one-size-fits-all approach rarely yields successful results. Therefore, the importance of creating a tailored advertising agency credentials presentation cannot be overstated.
Each potential client has unique needs, goals, and challenges, and tailoring the presentation to address these specific aspects is crucial for capturing their attention and interest .
A tailored presentation demonstrates that the agency has taken the time and effort to understand the client’s industry, market, and target audience. This level of personalized attention creates a sense of trust and confidence in the client, increasing the likelihood of a successful partnership.
By addressing the client’s specific needs and goals, the agency shows its commitment to delivering customized solutions that meet their unique requirements.
- A tailored advertising agency credentials presentation is essential for success .
- Understanding the client’s industry, market, and target audience is crucial in building trust .
- Customized solutions are the key to meeting the client’s unique requirements.
Focusing On Audience’s Specific Needs And Goals
When crafting an advertising agency credentials presentation , it is essential to focus on the audience’s specific needs and goals . By understanding the audience’s challenges and aspirations, the agency can tailor the presentation to address their pain points and offer relevant solutions.
The presentation should begin by capturing the audience’s attention and showcasing the agency’s expertise in their specific industry or market . This creates an immediate connection and establishes the agency as a credible and knowledgeable partner .
As the presentation progresses, it is imperative to align the agency’s offerings with the audience’s goals , demonstrating how the agency can help them achieve success.
• Focus on the audience’s specific needs and goals. • Tailor the presentation to address the audience’s pain points. • Showcase the agency’s expertise in the industry or market. • Establish the agency as a credible and knowledgeable partner. • Align the agency’s offerings with the audience’s goals.
Advantage Of Flexibility Offered By Credentials Decks
One of the advantages of using credentials decks in advertising agency presentations is the flexibility they offer. Credentials decks allow for easy customization and modification , enabling the agency to tailor the presentation to meet the specific requirements of each potential client.
By utilizing credentials decks, an agency can easily update and adapt the content , ensuring that it remains relevant and compelling . The flexibility of credentials decks also allows for easy integration of new case studies or success stories , further strengthening the agency’s credibility and showcasing its ability to deliver tangible results .
With credentials decks, agencies can create a dynamic and engaging presentation that resonates with each audience.
- Advantages of credentials decks in advertising agency presentations :
- Flexibility for customization and modification
- Easy update and adaptation of content
- Integration of new case studies or success stories
- Credentials decks help showcase the agency’s credibility and ability to deliver tangible results.
“Using credentials decks in advertising agency presentations offers flexibility, allowing for easy customization, modification, and adaptation of content. It enables agencies to tailor the presentation to meet the specific requirements of each potential client. With the ability to integrate new case studies or success stories, credentials decks effectively showcase the agency’s credibility and ability to deliver tangible results.”
Nine Steps For Building A Credentials Deck
Building an effective credentials deck requires careful planning and execution. Here are nine essential steps to create a compelling presentation:
- Research your target audience and understand their specific needs and goals .
- Define your agency’s unique selling proposition and core values.
- Structure the presentation in a logical and cohesive manner , with a clear narrative flow.
- Craft a captivating opening that grabs the audience’s attention and sets the tone for the presentation.
- Showcase your agency’s past successful campaigns and highlight the measurable impact they achieved.
- Translate the features of your agency’s offerings into tangible business benefits for the client.
- Incorporate visual elements , such as images, graphics, and videos, to enhance the visual appeal and storytelling of the presentation.
- Incorporate testimonials and endorsements from satisfied customers to build credibility and trust .
- Close the presentation with a strong call-to-action , prompting the audience to take the next step towards a partnership with the agency.
By following these steps, advertising agencies can build a compelling credentials deck that effectively showcases their expertise and convinces potential clients of their capabilities.
- Research target audience and understand their needs and goals.
- Define unique selling proposition and core values.
- Structure presentation with logical flow.
- Craft a captivating opening.
- Showcase successful campaigns and their impact.
- Translate features into tangible benefits.
- Incorporate visual elements.
- Include testimonials and endorsements.
- Close with a strong call-to-action.
Prioritizing Audience And Considering Their Interests And Motivations
When creating an advertising agency credentials presentation , it is crucial to prioritize the audience and consider their interests and motivations. Without a genuine understanding of the audience’s needs and desires, the presentation may fail to resonate with them effectively.
To effectively prioritize the audience, extensive research is necessary to gain insights into their industry, market, competitors, and target audience . By understanding the client’s industry landscape, the agency can tailor the presentation to address specific pain points and offer targeted solutions.
The presentation should focus on showcasing the agency’s ability to meet the client’s objectives and provide tangible value. By communicating the agency’s expertise and aligning it with the client’s goals, the presentation becomes a powerful tool to demonstrate how the agency can contribute to the client’s success .
- Prioritize the audience and consider their interests and motivations.
- Conduct extensive research to gain insights into the industry, market, competitors, and target audience.
- Tailor the presentation to address specific pain points and offer targeted solutions.
- Showcase the agency’s ability to meet the client’s objectives.
- Provide tangible value.
- Demonstrate how the agency can contribute to the client’s success.
“Without a genuine understanding of the audience’s needs and desires, the presentation may fail to resonate with them effectively.”
Advised Personalization On The First Page Of The Presentation
First impressions are critical in advertising agency credentials presentations. Therefore, it is highly recommended to personalize the first page of the presentation to capture the audience’s attention and demonstrate the agency’s commitment to their specific needs.
Personalization can take various forms, such as including the client’s logo or using targeted language that resonates with their industry or market. By tailoring the content of the first page to address the client’s pain points and aspirations, the agency creates an immediate connection and establishes credibility .
Additionally, the first page should showcase a compelling and concise statement of the agency’s unique value proposition . This statement should capture the essence of the agency’s expertise and provide a clear indication of why the potential client should choose to partner with them.
Creating A Navigation System That Addresses Client’s Pain Points Or Offers Case Studies
An effective advertising agency credentials presentation should have a clear and intuitive navigation system that addresses the client’s pain points or offers case studies . This allows the audience to easily navigate through the presentation and find relevant information that addresses their specific concerns.
The navigation system could include sections dedicated to addressing common pain points that clients in the industry face. Each section should present the agency’s unique solutions and demonstrate how they have successfully tackled similar challenges in the past.
Alternatively, the presentation could offer in-depth case studies that highlight the agency’s approach, strategy, and results. Case studies provide tangible evidence of the agency’s capabilities and allow potential clients to visualize how the agency can help them achieve their goals.
By creating a navigation system that focuses on the client’s pain points or showcases real-life success stories, the agency can effectively engage the audience and make a compelling argument for their services.
- A clear and intuitive navigation system
- Address client’s pain points or offer case studies
- Sections dedicated to common pain points and agency’s unique solutions
- In-depth case studies showcasing approach, strategy, and results
An effective advertising agency credentials presentation should have a clear and intuitive navigation system that addresses the client’s pain points or offers case studies. This allows the audience to easily navigate through the presentation and find relevant information that addresses their specific concerns.
What should be included in a credential presentation?
In a credential presentation, it is crucial to include the company’s vision, which should effectively communicate the purpose and drive behind fulfilling the company’s mission. By clearly articulating the vision, the audience will gain a deeper understanding of the company’s goals and aspirations, which can foster trust and engagement. Additionally, highlighting the company’s values is essential to showcase the principles and beliefs that guide the organization’s decision-making process. This not only helps the audience align with the company’s ethos but also demonstrates the company’s commitment to ethical practices and accountability. Overall, a comprehensive credential presentation should provide a clear and compelling vision along with the guiding values of the company to effectively engage and resonate with the audience.
What is a creds presentation?
A creds presentation is a strategic display of a company’s strengths and accomplishments. It serves as a condensed portfolio, presenting the best work of the company in a captivating manner. Its main objective is to highlight the products and services offered, emphasizing the value they bring and substantiating it with compelling evidence. This presentation acts as a powerful tool in establishing credibility and convincing potential clients or partners of the company’s expertise and capabilities.
What are the credentials of an agency?
An agency’s credentials serve as a comprehensive representation of its capabilities and expertise. They should showcase a track record of successful projects and satisfied clients, highlighting the agency’s effectiveness in addressing clients’ needs. These credentials should evoke confidence and trust, demonstrating the agency’s proficiency and competence to deliver desired outcomes. Ultimately, the credentials should articulate a compelling narrative that convinces clients that the agency is uniquely positioned to fulfill their requirements.
What is the presentation by ad agency to a client?
A presentation by an ad agency to a client is an opportunity for the agency to showcase their services and solutions. It is a carefully crafted sales presentation, often referred to as a pitch deck, designed to highlight the agency’s expertise and convince the client to choose their services. The pitch deck can be used to secure a meeting with potential investors or to demonstrate the agency’s capabilities in promoting a particular product. Ultimately, it serves as a persuasive tool to win the client’s trust and business.
Related Posts
- Digital Marketing Industry Size
- Cpm In Software Engineering
- Online Job Advertisement Tips and Tricks
- Online Advertising Courses In India
- Marketing Production Manager
- Aetna Health Insurance Customer Service Phone
- Advertising Networks Aoe2
- Marketing Financial Management
- Video Ads Crash Course 3.0 Review
- Wsi Digital Marketing Franchise Review
- Tags advertising , advertising agency , agency , client testimonials , creative portfolio , credentials , credentials presentation , explained , guide , marketing , marketing strategy , presentation , the , ultimate
Credential Presentation – Five tips for a powerful Company Introduction
Introducing a powerful idea.
A credential presentation gives business owners an opportunity to impress. The credentials PPT is usually the first step when engaging with an audience.
It is the perfect communication tool to start a customer-business relationship. The bigger objective is to sell a product or service. At times, business owners focus on the bigger picture instead of devoting time to improve the equally bigger task of putting out a credentials PPT.
Credential presentations are often neglected, incomplete, and outdated. In such a case, it is best to hire a professional credential presentation design agency . As the credentials PPT is the first line of consumer interaction, it needs to stand out in content, design, and structure.
Let’s look at five tips that can elevate your credentials presentation.
Communicate the vision
Firstly, hire a top presentation design agency . You won’t regret it. Their expertise in creating stunning yet engaging PPTs can help you get the desired credentials presentation.
When presenting a credential presentation, images are everything. The presentation is not designed to blindly shove a product or service to customers.
The goal of a credential presentation is to captivate the audience first and then sell along the way. The credentials presentation needs to communicate the company’s vision to the audience.
The vision must include the purpose and drive for fulfilling the company’s mission . The vision also covers company values. With the company vision set in the background, build the presentation through the company story. Storytelling can cause the company’s vision to resonate in the hearts of customers.
Adapting the slides
Each slide must be memorable. To ensure this, make sure you know the audience well. Identify and profile the credential presentation’s audience.
Refine the content in each slide. Compile, compose, edit, and proofread it before asking a PPT design expert to make it compelling.
The idea is to refine the presentation by removing clutter. This also reduces the size of the presentation. Doing some background research on the audience will help you determine who would be more receptive to visuals, numbers and content.
Focus on the future
Credential PPTs usually talk about a company’s origins. It starts with how the company was formed, its formative years in the industry, the key achievements, the biggest clients, etc.
Although, this is a good way to start a credential presentation , keep in mind this shouldn’t be all that you present. Dedicate only about 30% of your presentation to past and current activities.
Customers or investors want to know about the company’s future plans. Future partnerships, upcoming events, projected revenue, etc. have to be included.
Add visual elements
A credential presentation talks more about vision, goals, plans, and operations. With a deluge of information to be shared, it could become difficult to make the presentation immersive.
This can be fixed by letting a presentation design agency do what they do best. An experienced PPT design agency will come up with innovative ways to make your slide’s content captivating.
With the help of high-quality images, custom fonts, and appropriate animation, your company’s credential presentation will engage its audience with charm.
Call-out instruction
While presenting, make sure you are turning monologues into exchanges. Focus on human interactions.
Dedicate some time to answer questions. Once done, direct the audience to a clearly mentioned call-to-action . This CTA could be a link to the company website, a link to your company’s annual report or just a phone number to call.
Don’t leave the audience hanging. Be crystal clear as to what the purpose of the presentation is and what you expect the audience to do next.
- Scroll to top

9 tips to create a creds deck that connects with potential clients.
A creds deck has the power to back up your bold claims and show potential new clients that you’ve got what it takes to turn their dreams into reality. In just a few short slides, you can prove that your business has been there, done that, and knows exactly how to tackle any challenge that may come your way. So, why do most creds decks suck?
You’ve spent years crafting your skills and sharpening your ideas but now you’re tasked with an entirely different challenge: selling them. You’re not short of leads. The prospects are there and they’re yearning for a solution to their problems. But they’re anxious about making the right decision. There’s so much to consider and vast amounts of information available. And they’ve probably got a lot of options.
So, how do you get them to listen to you? How do you convince them that you are the right partner to take them forward? Cue the creds deck. Creds decks are so much more than a list of previous successes. Done right, they establish credibility and expertise, inspire trust, differentiate you from competitors, and paint an honest picture of your business.
Unfortunately, most creds decks aren’t done right. We’re going to show you how to create a compelling creds deck that truly connects with your audience, shifts their beliefs and makes them wonder why it took them this long to find you.
What is a creds deck?
A creds deck is essentially your company portfolio. It’s a collection of your very best work, presented in the most flattering way. Typically, the messaging of a creds deck focuses on two main areas. Firstly, it needs to showcase your products and services, the difference you make, and the evidence to back it up. These are your demonstrable successes – case studies, results, the impact, previous projects, etc. Second, and just as important, every component, from the visuals to the story, should accurately capture who you are as a business: your personality, your values and your mission. The audience should get a feel for your business identity through every slide. How you present this information depends on who you are and who your audience is, but creds decks need to do both if they’re to successfully persuade someone to invest.
Here comes the tricky bit. While the purpose of a creds deck is to show off your skills, the worst thing you can do is use this opportunity as an excuse to indulge in your success. There’s nothing wrong with being proud of your work, but there’s pride and then there’s outright bragging. No one wants to work with a narcissist. The focus needs to shift from you to your audience. Naturally, you’ll still talk about yourself, but in a client-centric way. So, the emphasis switches from reeling off your successes to how your successes make you qualified to help the person you’re talking to. Fail to make this switch and you risk total audience disconnect.

Westminster House
The problem with most cred decks.
Speaking of narcissism, most companies try to cram everything into their creds deck, so instead of being a greatest hits album, they become a playlist of everything you’ve ever made. The songs don’t follow on from each other. There’s no harmony. No continuity. No order. This won’t resonate with the listener. They want to hear about how you can address their specific needs and help them attain their personal goals. Clients are smart. If they get a whiff of irrelevance, they’ll lose interest. And if you use generic, nonspecific messaging, they’ll see right through it. Plus, I’m sure you’ll agree that your future clients are worth the effort of a tailored experience.
The home advantage
Creds decks also have the advantage of flexibility: they can be delivered remotely, from the convenience of your home. If for any reason, you can’t present in a face-to-face setting, there’s no reason why you can’t replicate the experience via a video call. You never know when a worldwide contagion’s going to sweep the nation, right? Creds decks give you that flexibility to sell your services in the online and offline spheres, without compromising on impact.
Building a creds deck in 9 steps
1. audience first.
The best way to approach your creds deck is to treat it like any other presentation. And what comes first in any other presentation? The audience. Like we said, too many companies focus on themselves. Before you start detailing how many offices you have and how many employees you’ve got, think about whether your audience even cares.
Companies with a focus on scaling up, for example, will likely see the benefit in your global locations. Others won’t give a toss about how many offices you have, but they may be enticed by the philanthropic string to your bow, seeing an opportunity to boost their CSR credentials. And this is exactly the point, the creds deck needs to be tailored to different audiences.
Think about who you’re pitching to through the lens of “What do they care about?”. Pinpoint their needs, motivations, challenges and expectations, and then use this information to draw parallels between their current reality and your solutions.
2. Personalise that page
Once you’ve thought about your audience, you can begin to piece the creds deck together. Starting unconventionally with… page one. This initial page needs to propose an idea so tempting they can’t click x.
In order to be compelling, your proposal has to resonate with them from the very first page. There’s no shortcut here, the only way to do this is to do your research. Get to know who you’re talking to so you can describe a situation they will identify with. Address a familiar scenario, reference some of their key challenges and set yourself up as the organisation with the keys to unlock their success. Personalise it to fit their situation, while introducing your own overarching value proposition.
Empathy is the driving force of a creds deck. The first page should prove to them that you get it. You understand where they want to go, you understand what’s holding them back and you know how to take them there. It should give them an inviting snapshot of what’s to come and a reason to keep listening.
3. Let the audience dictate their experience
Nothing creates an audience-centric presentation quite like a self-directed experience. Instead of building a linear deck, where audiences have no choice but to sit through every slide politely, give them the option to choose what they want to look at.
If you’d like to keep it simple, opt for a two-route menu system that enables them to jump to a particular slide, and back to the main menu. If you want to create a more dynamic experience, design a navigation system around their challenges. Create a menu that lists a set of pain points, with each one linking to your solution. This way, you can show that you already understand their challenges, and you’ve solved similar challenges before.
If case studies, rather than challenges, are the driving force of your messaging, you could even add layers of navigation for different verticals, or the brands that are most aligned to what they do. Ask them if there’s a company they aspire to be like and show them something similar you’ve worked on, or the real deal if you’ve got that connection under your belt. Navigation in presentation software can be as flexible as you want it to be, just remember to give your audience the power to choose where the conversation goes.
4. Show off what goes on behind the scenes
Your audience aren’t just interested in the final product, they’re keen to know how you got there. Odds are, you’re not the only company offering a solution to their problems, but what will distinguish you is the story you have to tell and the people behind your success.
The human element doesn’t come across in finished products, but in the struggle, the creativity and the development from the original ideas. Be transparent about the process – the highs, the lows, the time pressure, the deadlines, those late nights you spent trying to fix a software malfunction. Show them the mood boards and initial drafts that came before the polished piece. Explain how you overcame what seemed like an insurmountable challenge. In being transparent about the reality of the journey, flaws and all, you’ll evidence just how much passion goes in, from inception to final delivery.
Being honest about the challenges you faced gives you authenticity and shows grit. This will inspire confidence that no matter what, you’ll find an answer and get the job done.
5. Turn features into benefits
Features mean nothing without material business benefits. You should be applauded for devising a solution to their problems, but even if you’ve come up with a revolutionary idea with seven patents and first-of-their-kind features, so what? Features can be read on a specification list. Benefits need to be demonstrated.
Perhaps you’re saving them time, making their processes more efficient, cutting costs or reducing the possibility of downtime. Whatever it is that will change their lives, transpose it into a language that your audience understands, and don’t presume they’ll immediately grasp what these benefits mean for them. Explain the benefits in the context of their working environment, or better yet, show them an angle they may not have considered before. Don’t just say it will solve their challenges, demonstrate how it will and why you can do it better than anybody else.
People buy based on their emotions, but justify their purchases with logic. The features give them the logic, but the benefits stir an emotional response, and it’s this that will feed that motivation to purchase.
6. Let your clients do the selling for you
The purpose of a creds deck is to sell. We know it, you know it, and your potential clients know it. But that doesn’t mean they deserve to sit through soulless marketing spiel and slide after slide of humble brag. And don’t assume they’ll simply take your word for it.
The vast majority of people won’t part with their hard-earned money without some evidence of the tangible successes you’ve had with other companies. And for those who are on the fence, the right testimonial could be the push that lands you a new client. The herd effect is a powerful force. People feel safer making riskier business decisions if others have done it before them. Demonstrating a proven track record of success, with quotes from other people, will reassure prospects of your authenticity and credibility.
The best creds decks give enough evidence to satiate everyone’s appetite. Some are swayed by the human impact; others may be numbers people. A glowing review from a happy customer, placed next to some high-impact data visualisation, could be all it takes to cement your success.
Software presentation
“This might sound cheesy but do believe the Hype! We contacted them with a really urgent requirement and they delivered an amazing presentation and ultra fast. Knowing what we wanted and having the copy already drafted obviously helped but their team got our vision and brought it to life, and better than we expected. We will definitely work with them again and are already thinking about the next idea.”
Colin Brimson
CEO, d-flo Limited
Conference presentation
“Our conference presentation stood out as the best part, and presentation, of the day! The Rockstar section was the talk of the conference, with everyone asking our contact where they’d gone to produce that. Making noise at these events is how the individual brands cut through to the group heads and get more support and confidence where they need it.”
Gordon Donald
Senior Sponsorship and Promotions Manager, AG Barr
Sales presentation
“I highly recommend the team to anyone looking to elevate their communications and take their sales presentations to the next level.”
Stephanie Malham
Chief Operating Officer, Outright Games
CPD presentation
“The team guided us through the step-by-step process with ease, providing great insight and fresh new ideas, to create a more modern and engaging CPD for our audience.”
Andrew Hamilton
UK Specification and Marketing Director, FAAC
Investor deck
“The team helped us to create a first-class investor deck, which was instrumental to the success of our investment round. We ended up securing £585,000, which exceeded our expectations by 30%.”
Kirstine Newton
Co-founder, Altitude Gin
7. Keep it short
It’s good to be passionate about what you do, but try not to let that passion cloud your judgement about audience engagement. You may want to showcase every asset from your highly-successful marketing campaign or every page of a brochure you created, but your prospect probably has other things to be doing. You need to learn to edit. Only show the aspects of your offering that solve a problem for your audience.
Some slides will deserve more attention than others, but that’s your call. Dedicate more time to the topics that matter most for the audience, and to explain the most meaningful components of your overarching argument. Follow a pace that you’re comfortable with, but keep it snappy and stick to the point.
8. Leave the ‘About Us’ section until the end
Out of the hundreds of presentations we’ve seen, one of the most common slipups is talking about yourselves upfront. Imagine you’re a potential client with a niggling pain point. You accept a meeting invitation with a company claiming to have an answer to your problems. The meeting commences and the first thing they do is tell you about their history, awards and company culture, and this ends up eating into most of the meeting time.
Establishing your credibility is vital, but the quality of your ideas and previous successes will do this for you. Leave the ‘ About Us ’ section to the very end and make it optional in your navigation system. Most prospects should be sold on you before you reach this part.
9. You are the driving force of the creds deck
Don’t forget that your slides are there to support you. Think of them as tools that’ll help you get your message across. You, as the presenter, are always the focal point of the presentation.
Ultimately, you’ll convince prospects with your authenticity, knowledge, tone, body language, confidence, and aura. All of this is really important because, together, they’ll shape your prospect’s judgement of you.
Even through a video call, your passion should shine through. This is why practicing is so important. You can use the slides as visual aids or reference points, but when it comes to the moment of delivery, it’s you who’ll be centre stage, with your slides playing a supporting role.
Optional, but recommended, extras
It’s easy for busy companies to dismiss an opportunity to have a face-to-face conversation with you by asking you to send creds deck instead. This is convenient for them, but not so opportune for you, because you run the risk of the deck being lost in a busy inbox. Always try to push for a meeting. Your creds deck alone won’t be enough to persuade your audience. Without an in-person delivery, much of the passion that manifests through tone, gestures and unscripted answers to questions, will be lost.
If there’s no in-person meeting on the horizon, you can still use this to your advantage. Find out as much as you can about them via email, Linkedin or whatever their preferred communication platform is. Ask questions about what they’re currently working on, what’s filling up their time and what would relieve their pressure. Doing this is another way of evidencing that you genuinely care about helping them, and equips you with valuable information that you can use to personalise your creds deck, in preparation for the face-to-face meeting. Building this relationship online could be what charms them into setting up a video call, or making the time to give you that meeting in person.
At times, creating a creds deck may not feel like one of the most enjoyable aspects of self-promotion. Some people worry that a presentation won’t capture the brilliance of what they do, but with our tips, you can make sure every slide does your work justice. Or better yet, give the responsibility to someone else. As a full-service presentation agency , we’re fully equipped to take care of your creds deck for you. There’s no time like the present. Get your creds deck ready now, that next big prospect might be looking for your company as we speak.
Recent Posts

- Posted by hypepresentations
How we structure presentation content.
Your content is the foundation of your presentation, and how you create...

How many slides should I have in my PowerPoint presentation?
When you’re planning out your next big presentation, it can be hard...

Home » Pitching Support » Top ways to make agencies more effective in presenting their credentials
Top ways to make agencies more effective in presenting their credentials

For the past 20 years, I have literally sat through more than a thousand agency credentials presentations . Some were part of a pitch or tender credentials presentation, and others were when I was engaged in providing feedback to help agencies improve their credentials deck and presentation. I can honestly say that initially, less than ten agency credentials examples stood out as memorable.
I remember when this first became apparent after we had spent a day of chemistry meetings with eight back-to-back credentials presentations, where the agencies were asked to provide a maximum 30-minute presentation on “why choose this agency”. In the end, the clients only remembered one of the agencies by name, and the rest were referred to by some other mnemonic, such as the one with the guy with the red spectacles, etc.
So, what is wrong with how many agencies present their credentials? Let me share some common mistakes and solutions to help you hopefully make your credentials presentations more effective.
1. Focus on the purpose of the credentials presentation
Yes, this is like taking a brief about who it is, what they think and feel now, and what we want them to think and feel after seeing the presentation. Usually, it is a new business prospect, and what you want them to think and feel is your agency must either be on their shortlist or appointed at the end of the presentation.
I am not kidding here. In one agency credentials example, the presentation was so powerful that the client was talking about appointing the agency immediately but took them through the process and appointed them in the end. Still, I am sure they had won it at that first meeting.
2. Forget the template and the formula
So many agency credentials appear like a checklist of information. Who we are, what we do, where we are located, how we work, etc, etc, etc. It is predictable and boring and not required. Whoever said there was a checklist, a formula or a format for a credentials presentation?
Remember, I am discussing a presentation here, not a credentials document. Certainly, you need to include the details about you and your company in the document, but the presentation is not simply reading from the document.
3. Make sure you turn features into benefits
This is straight out of Alistair Crompton’s The Craft of Copywriting but applies just as much to agency credentials as to great advertising.
By way of example, I had an agency banging on about their Agency University and how they were committed to the professional development of their employees. It went for about four slides and got into the details of the curriculum and everything – clearly, they were enamoured with it.
The client is sitting there saying that’s all very nice, but “What’s in it for me?” I will tell you, the employees at this agency are training in the latest on business and marketing to advise you on a day-to-day basis better. If the client wants to know more, it is all in the credentials document.
4. Don’t tell them what you do
Tell them what you deliver.
This is an extension of the previous point and one often overlooked. Too often, I find the agency spends too much of the credentials presentation talking about what they do. Have you ever been to a doctor for the first time and had them spend any time telling you what they do? Or an accountant? Or a lawyer? Let’s be honest: most marketers and advertisers broadly know what a media agency does, a creative agency, a public relations firm, or a digital agency. So, telling them what do is potentially the fastest way to commodities yourself because everyone in your category will be saying largely the same thing. Of course, if the audience has no experience or understanding of marketing, you may need to explain what an agency does. But do not waste more than a minute or two on this.
5. If it is too dull or detailed, put it in the ‘leave-behind.’
I am not sure why agencies think they need to answer all of the client’s questions in the presentation. Often, the client may send through a list of questions they want the agency to address in the credentials presentation. Or the agency may invite and elicit questions that the clients are interested in. This is a good strategy. Having been asked, the agency should address these queries, just not necessarily in the presentation.
My favourite is when a client (usually procurement) asks the agency to detail their process. I defy anyone to find a way to present the process in a way that is not sleep-inducing. Remember, the purpose is to build rapport and hopefully get one step closer to getting the business. If something is particularly complex, boring, or potentially confusing, put it in the document the client will take away with them. (Yes, there should always be a document or written follow-up to reference the meeting.) Then, you can reference the details in the leave-behind and move on to more business-winning discussions.
6. Don’t just say it, show it
There is usually a point in the credentials presentation where we get to either the client testimonials, you know, the bit “That’s enough about us, let’s hear what our clients think about us,” or the case studies, which is a chance to show off the work and tell the client prospect how successful you have been.
Unfortunately, these are usually towards the end of the presentation after you have spent the first half talking about how successful you are as an agency and how unique you are. Instead of having a testimonial and case study section, using case studies and testimonials to demonstrate what you are saying is always more powerful.
For example, instead of saying you work collaboratively with other agencies (sure you do), why not have other agencies and your clients talk about your collaboration skills? Or show a case study that could only be achieved through collaboration?
7. What is the outtake of the presentation?
What narrative or story are you telling, and is it memorable and distinctive? Ideally, you want the client to feel that they do not know how they survived to date without you working on their business.
But what makes a marketer think that will depend on his or her own particular needs and circumstances, which is next to impossible to know. But you want to leave them with a powerful impression and a desire to know more. (This is a good measure of a great credentials presentation as it spontaneously has the audience asking you for more information and starting a discussion about how you could or would work together).
But also, when they walk away, what will be their impression of the agency later that day, tomorrow or in a week’s time? And how will they describe you to someone not in the presentation? That is the story or narrative you need to craft.
These are just the top seven most common and perhaps most obvious mistakes I see repeatedly. In 2011, I got so sick of seeing the same formulaic credentials I put together this spoof video of an agency to demonstrate how not to do it. The trouble is I think some agencies have mistaken this as a training video and missed the point.
However, having seen so many agency credentials presentations and how they impact a client looking for a new agency, I am happy to help any agency improve by providing raw and honest feedback. If you are up for it, let us know. Until then, I hope this has helped help you present your agency credentials.
Learn more about how we can help your agency improve its Agency Credentials and Market Positioning here.
By Darren Woolley
This post is by Darren Woolley, Founder and Global CEO of TrinityP3. With his background as an analytical scientist and creative problem solver, Darren brings unique insights and learnings to the marketing process. He is considered a global thought leader in optimizing marketing productivity and performance across marketing agencies and supplier rosters.
You might also like:

Managing Marketing: The State Of The Pitch In Australian Advertising
Creative Agency Pitch Consultation – Case study

100 consideration for marketers to avoid poor pitch performance
To contact us about how we can work with you, or to discuss a specific tailored project.

- Case Studies
- Distributor Search
- USA Development
- Workshops & Speeches
- Export Strategy
- Export Passport
- Prime Prospects
- Fix Problem Markets
- Export Express Newsletter
- Export Guides
- United States
- Distributor Management
- Hot Countries
- Export Handbook
Ten Tips: Your Company Credentials Presentation
Greg Seminara, Export Solutions
Distributors are flooded with requests for representation of brands from around the world. Normally, these presentations are jammed with pretty photos and long stories about the companies history. Brands will receive better response with a fact based, company credentials presentation focused on “What Distributors and Buyers really want to know”. Export Solutions recommends that brands create two versions of your credentials presentation: Ten page detailed presentation and a one page summary. Recapped below are our ten tips on developing a strong company credentials presentation to attract interest from Distributors and Buyers anywhere.
1. Just the Facts: Page 1 should include basic company facts. Annual sales, ownership, number of employees, and key categories and brands.
2. History Tell the story of when and how was the company founded. This is your chance to seduce the audience with a captivating story. Learn to tell the story in one page with no company video’s or DVD’s (boring!). Provide a longer version of your history and milestones on your company web site for those who want more information.
3. Brand USP This is the place for pretty pictures of your brand and the opportunity to demonstrate your category expertise. Why is your brand different ? How do you compare with current category assortment ? List any awards or recognition for your company.
4. Current Export Markets Share countries where your brand is currently available. Segment between core markets where your brand is strong and others where you maintain niche status. What is the rationale for entering the distributors country ?
5. Distributor and Retailer Partners Highlight well known distributors currently serving as your partners. List retailers who currently sell your brand. Logo’s work well.
6. Success Stories Focus on recent examples of your brand building results. Mention specific retailers or distributors if examples are well known retailers or in adjacent countries.
7. Investment Strategy Distributors and buyers demand critical information on how you plan to generate consumer awareness, trial, and repeat purchase of your product. Their interest will match your level of financial commitment.
8. Team Resources Publish photos of your export team. This includes marketing, finance, customer service, and logistics experts. List years of service for each team member to demonstrate that you have a strong support organization to build the business.
9. Sync with Web Site Your credentials presentation should sync with information on your web site. In reality, your web site is the first place that a potential distributor will visit. Modern web sites, with crisp graphics, minimal text, and no music will receive attention. Do you have a page dedicated to international export? When was the last time you updated your web site ?
10. Why is your Company a Good Partner ? This represents a one page summary of your company credentials. What value does your company bring to the partnership ? What is the “size of the prize” ? How will your brand make more money for the distributor or buyer ?
Export Solutions can help ! Export Solutions has participated in more than 300 Distributor identification projects and reviewed web sites of more than 10,000 Distributors and Brand Owners. We are available to review your company presentation or web site to provide timely ideas and suggestions to improve your visibility. Contact us in the USA at (001)-404-255-8387 for more information.

Free: 15 Export Guides and 50 Scorecards. Export Express monthly newsletter dedicated to Best Practices for international development through food distributor networks.

Advertisement
The Drum Awards Festival - Extended Deadline
- d - h - min - sec
What do the perfect agency credentials look like?
- Facebook Messenger

By Stefan Rhys-Williams , Senior account manager
The Future Factory
The Drum Network article
This content is produced by The Drum Network, a paid-for membership club for CEOs and their agencies who want to share their expertise and grow their business.
June 22, 2017 | 6 min read
Listen to article 4 min
Agency credentials and presentations continue to be a hot topic in the world of agency new business. But what makes a credential valuable? The Future Factory spoke to senior figures in the brand world, in search of answers to how agencies can best influence the purchasing decisions of brands. Unfortunately, they explained credentials often fall a little short of the mark…

Get to the point
Everybody thinks they’re busy; not having time to really focus or take anything in has become something of a status symbol. So it’s crucial to make the most of your prospect’s time and get your point across as effectively and concisely as possible.
The chief marketing officer of Rightmove has previously emphasised the importance of brevity and favours credentials which only take up a few slides long per case study. He says if five slides isn't sufficient, then “you’re clearly struggling to sell yourself”.
A director at Sonos is also unequivocal: “creds are far too long, they should be short, snappy and insightful”.
Be results-focused
So if it’s best to keep things short and to the point, what should you include? What eye-catching details help you stand out from the crowd? According to a head of PR at a major automotive brand, evidence of tangible value and results is crucial.
Now, in a world of brand equity, stakeholder engagement and other (more-or-less) intangibles, this can be difficult. But it’s worth bearing in mind that framing a case study in terms of tackling a challenge or solving a problem is preferable to a rambling account of the work you’ve done and what you like most about it. If you can measure the ROI your work has delivered then great – but it’s not always as simple as that. Include relevant testimonials and sector-specific insight too, and you’ll be on your way to leaving a great impression and demonstrating the value your agency can add to the brand team’s work.
Remember, even the sleekest credentials in the industry are best talked through rather than emailed in PDF form – get some face time in the diary by emphasising how much more valuable (for both sides) even a brief meeting tends to be.
Emphasise your culture
In addition to thinking carefully about the content and aiming for a deck that’s pithy and concise, it’s important to bear in mind the limitations of agency credentials. For a director at Bacardi, the agency team can be just as important as their case studies – “people buy people”.
Indeed, an over-reliance on credentials can be to the detriment of chemistry: “bring your personality”, advised another chief marketing officer.
Anything from photos of the office (dog) to a distinct and original tone of voice can help inject a bit of character and differentiate your agency in a vigorously competitive industry.
Acknowledge that credentials have their limitations
Knowing you have your well-thumbed credentials at your disposal can be a real source of comfort. Yes, you may have tailored these for a specific meeting, but you know them like the back of your hand and you might be relying on them too heavily. Don’t be afraid to stray from the path and leave the presentation behind.
A director at Diageo takes a similar view. He comments, “I never see a presentation as a presentation, I see it as a conversation… I don’t want to be talked at”. It’s important to be able to react to remarks and questions you may not have been expecting – and that means your credentials should facilitate, not dictate, the kind of conversation you’re having.
As one of our interviewees put it, “don’t present, engage”. Recognise there’s somebody else in the room: solipsism is off-putting and won’t get you very far.
Get a second opinion
Bear in mind that your favourite case study, or what you deem to be your best work, won’t always be as compelling to your prospect. Remember, even the most creative agencies in the world aren’t always best placed to do their own branding – so get another pair of eyes to look over your deck.
The agency marketplace is littered with companies that deliver great, inventive work for their clients but who neglect their own branding, websites and, in this instance, credentials.
Credentials are hard to get right, time consuming and sometimes don’t feel like an agency’s priority. But our research suggests that a decent set of collateral (as part of a broader marketing strategy) can make all the difference and really change how your business is perceived.
With so many agencies out there, sub-par credentials have become a really easy excuse for disregarding a particular approach or pitch – invest a bit and take them seriously.
The Future Factory is offering agencies the chance to get their creds reviewed for free over June. Click here to find out more.
Stefan Rhys-Williams is senior account manager at The Future Factory .
Content by The Drum Network member:

With a mix of lead generation, board level consultancy and coaching, we help to make the future more predictable for agency Owners, Founder and Directors. www.thefuturefactory.co.uk Since...
More from Marketing
Industry insights.
Tel: 01213 558092
Credentials Documents: Why Every Sales-Driven Business Should Have One
So, what could a credentials document do for you.
A credentials document is an essential part of marketing your business, especially if you work in a highly competitive, business-to-business industry.
Targeting a specific audience, a credentials document will demonstrate the capabilities of your business, the services you provide, the impact your work can and does have, and why your audience should choose to work with you.
What Should a Credentials Document Include?
A credentials document is almost like a CV for your business. It is a document that will be tailored for and sent to your business prospects in the hopes of bringing them on board as a client, demonstrating your past work and expertise.
A significant aspect of the credentials document’s structure is to include examples of your best work – hero pieces you are proud of! The work you’ll want to display should be relevant to the prospect you are approaching, demonstrating how you helped clients in the same industry or those with similar goals achieve their aims.
A great way to further support this is by adding client testimonials taken directly from those you work closest with. This way, prospects can understand the benefits of your services from a proven, external source rather than just from your existing marketing material. They will then be more likely to engage with you – there’s nothing better for business than a good review!
EDGE Creative can help you choose projects that were most successful and display them with clear objectives and results explained, just like our projects page.
Our personalised credentials documents outline who you are and what you do as well as feature case studies of successful projects, testimonials, and an attention-grabbing call to action. We can guide you on what your clients really want to see and piece together the perfect proposal tailored to your target audience.
How Should a Credentials Document Look?
First impressions are crucial, so your credential document needs to be well presented, on-brand, and relevant to your audience. Put yourself in your clients’ shoes for a moment: if you wanted to outsource a service, would you go for the provider with a clean, nicely designed credential document or the one who emailed over some attachments?
There are no rules on exactly how your document should be laid out or presented, but it is always best to ensure it stays true to your brand and expresses all the information clearly and without clutter.
EDGE will work with you to ensure your brand is represented correctly and make you and your company really stand out – it’s what we do best!
How Can We Help You?
At EDGE, we provide a fully integrated marketing service, offering an initial consultation and strategic advice on what approach would work best for your clients, through to on-brand design, copywriting and personalisation to create a unique piece just for you.
Our talented design team can craft your credentials document to suit various marketing channels such as on-screen, printed, digital download and page turning software.
Your credentials document can be edited and personalised for every client individually, so you can be sure that your credentials document has longevity and can evolve as you do, meaning it’s a marketing investment you can’t afford to be without. If you’re still not sure why you need one, check out our case study to see how we have helped Fidelis Group grow their business!
If you’d like to speak to us about starting your credentials document today, please reach us on 0121 355 0892 or email [email protected].
Alternatively, browse our range of services and see how we can help your brand or business with brand development , search engine optimisation , social media marketing and more.
STAY UP TO DATE WITH OUR LATEST UPDATES
Subscribe and get all our updates on our events, activity and news from the digital marketing industry.
By clicking the 'Subscribe' button you agree to the Terms & Conditions and Privacy Policy
Related Blog Posts
8 tips to creating a design credentials pitch for a client
I often get asked from clients as part of a design proposal, “what is the process for?a?design project?” ?to “ how much does it cost to design x?” and “have you done anything similar to what we want?”
In this article I will break down a credentials pitch document into eight sections.
This Credential Pitch document that I have previously used for new clients provided a detailed overview of who we are, what we do, our process, fees and how we work – along with relevant case studies and client testimonials. This was created in an A4 format and sent to the client.
Of course, each one is personally crafted to a new client proposal and this one below is an example based on a website design project for a charity but I’ve used Apple Inc. as a demonstration client in this example.
The following I will break each section down for you with a little explanation and an image.
1. Introductory letter
Firstly, I provide a?signed?introductory letter explaining what the document contains and any other communications.This helps to prepare the client as an opening to what’s involved, giving an overview before going further.
2. Credentials cover page
The cover should contain some branded graphics or imagery that is consistent with your identity, who prepared it and who is it for. And it really helps to have the logo’s partnered together side by side on the cover. This promotes the partnership they will be entering into.
3. Who we are page
A clear, short?and concise?biography of the company gives the client a clear understanding of your approach and why they should choose you. This is then followed by introducing who will be?specifically?working on their design project:
4. What we do page
A?short description about what you specialise in that fits to their design requirements. So following on from the previous page about who you are, go into a little more detail about what you?do:
5. Our process page
This gives the client an insight into how you?will be working with them, what they expect at each stage and what the costs will involve.
6. An idea of our process…
If you take?two or three of your main design services and?briefly detail each process on?what the client will get,?educates and demystifies your services for the client. It also saves you time explaining each time a new client asks you.
7. Case studies
For each individual client, you will need to tailor your case studies so that they are relevant to their design project. In my designs, I have not only selected?case studies from similar?clients, but designs that?showed similar requirements?to this design project.
8. Client testimonials page
On the final page, have relevant, up to date testimonials that backs up all?the content you’ve provided and shows your experience working with a variety of client design projects.
This Credentials Pitch document?is based on The Five C’s from?this article on?the Design Business Association blog
Andy Fuller
Spread the word.
© Designbull. All rights Reserved. | Terms | Privacy | Disclaimer
Made with ❤ by Designbull
Verifiable Credentials Data Model v1.1
W3C Recommendation 03 March 2022
See also translations .
Copyright © 2022 W3C ® ( MIT , ERCIM , Keio , Beihang ). W3C liability , trademark and permissive document license rules apply.
Credentials are a part of our daily lives; driver's licenses are used to assert that we are capable of operating a motor vehicle, university degrees can be used to assert our level of education, and government-issued passports enable us to travel between countries. This specification provides a mechanism to express these sorts of credentials on the Web in a way that is cryptographically secure, privacy respecting, and machine-verifiable.
Status of This Document
This section describes the status of this document at the time of its publication. A list of current W3C publications and the latest revision of this technical report can be found in the W3C technical reports index at https://www.w3.org/TR/.
Comments regarding this specification are welcome at any time, but readers should be aware that the comment period regarding this specific version of the document have ended and the Working Group will not be making substantive modifications to this version of the specification at this stage. Please file issues directly on GitHub , or send them to [email protected] ( subscribe , archives ).
The Working Group has received implementation feedback showing that there are at least two implementations for each normative feature in the specification. The group has obtained reports from fourteen (14) implementations. For details, see the test suite and implementation report .
This document was published by the Verifiable Credentials Working Group as a Recommendation using the Recommendation track .
W3C recommends the wide deployment of this specification as a standard for the Web.
A W3C Recommendation is a specification that, after extensive consensus-building, is endorsed by W3C and its Members, and has commitments from Working Group members to royalty-free licensing for implementations.
This document was produced by a group operating under the W3C Patent Policy . W3C maintains a public list of any patent disclosures made in connection with the deliverables of the group; that page also includes instructions for disclosing a patent. An individual who has actual knowledge of a patent which the individual believes contains Essential Claim(s) must disclose the information in accordance with section 6 of the W3C Patent Policy .
This document is governed by the 2 November 2021 W3C Process Document .
1. Introduction
This section is non-normative.
Credentials are a part of our daily lives; driver's licenses are used to assert that we are capable of operating a motor vehicle, university degrees can be used to assert our level of education, and government-issued passports enable us to travel between countries. These credentials provide benefits to us when used in the physical world, but their use on the Web continues to be elusive.
Currently it is difficult to express education qualifications, healthcare data, financial account details, and other sorts of third-party verified machine-readable personal information on the Web. The difficulty of expressing digital credentials on the Web makes it challenging to receive the same benefits through the Web that physical credentials provide us in the physical world.
This specification provides a standard way to express credentials on the Web in a way that is cryptographically secure, privacy respecting, and machine-verifiable.
For those unfamiliar with the concepts related to verifiable credentials , the following sections provide an overview of:
- The components that constitute a verifiable credential
- The components that constitute a verifiable presentation
- An ecosystem where verifiable credentials and verifiable presentations are expected to be useful
- The use cases and requirements that informed this specification.
1.1 What is a Verifiable Credential?
In the physical world, a credential might consist of:
- Information related to identifying the subject of the credential (for example, a photo, name, or identification number)
- Information related to the issuing authority (for example, a city government, national agency, or certification body)
- Information related to the type of credential this is (for example, a Dutch passport, an American driving license, or a health insurance card)
- Information related to specific attributes or properties being asserted by the issuing authority about the subject (for example, nationality, the classes of vehicle entitled to drive, or date of birth)
- Evidence related to how the credential was derived
- Information related to constraints on the credential (for example, expiration date, or terms of use).
A verifiable credential can represent all of the same information that a physical credential represents. The addition of technologies, such as digital signatures, makes verifiable credentials more tamper-evident and more trustworthy than their physical counterparts.
Holders of verifiable credentials can generate verifiable presentations and then share these verifiable presentations with verifiers to prove they possess verifiable credentials with certain characteristics.
Both verifiable credentials and verifiable presentations can be transmitted rapidly, making them more convenient than their physical counterparts when trying to establish trust at a distance.
While this specification attempts to improve the ease of expressing digital credentials , it also attempts to balance this goal with a number of privacy-preserving goals. The persistence of digital information, and the ease with which disparate sources of digital data can be collected and correlated, comprise a privacy concern that the use of verifiable and easily machine-readable credentials threatens to make worse. This document outlines and attempts to address a number of these issues in Section 7. Privacy Considerations . Examples of how to use this data model using privacy-enhancing technologies, such as zero-knowledge proofs, are also provided throughout this document.
The word "verifiable" in the terms verifiable credential and verifiable presentation refers to the characteristic of a credential or presentation as being able to be verified by a verifier , as defined in this document. Verifiability of a credential does not imply that the truth of claims encoded therein can be evaluated; however, the issuer can include values in the evidence property to help the verifier apply their business logic to determine whether the claims have sufficient veracity for their needs.
1.2 Ecosystem Overview
This section describes the roles of the core actors and the relationships between them in an ecosystem where verifiable credentials are expected to be useful. A role is an abstraction that might be implemented in many different ways. The separation of roles suggests likely interfaces and protocols for standardization. The following roles are introduced in this specification:
Figure 1 above provides an example ecosystem in which to ground the rest of the concepts in this specification. Other ecosystems exist, such as protected environments or proprietary systems, where verifiable credentials also provide benefit.
1.3 Use Cases and Requirements
The Verifiable Credentials Use Cases document [ VC-USE-CASES ] outlines a number of key topics that readers might find useful, including:
- A more thorough explanation of the roles introduced above
- The needs identified in market verticals, such as education, finance, healthcare, retail, professional licensing, and government
- Common tasks performed by the roles in the ecosystem, as well as their associated requirements
- Common sequences and flows identified by the Working Group.
As a result of documenting and analyzing the use cases document, the following desirable ecosystem characteristics were identified for this specification:
- Credentials represent statements made by an issuer .
- Verifiable credentials represent statements made by an issuer in a tamper-evident and privacy-respecting manner.
- Holders assemble collections of credentials and/or verifiable credentials from different issuers into a single artifact, a presentation .
- Holders transform presentations into verifiable presentations to render them tamper-evident.
- Issuers can issue verifiable credentials about any subject .
- Acting as issuer , holder , or verifier requires neither registration nor approval by any authority, as the trust involved is bilateral between parties.
- Verifiable presentations allow any verifier to verify the authenticity of verifiable credentials from any issuer .
- Holders can receive verifiable credentials from anyone.
- Holders can interact with any issuer and any verifier through any user agent.
- Holders can share verifiable presentations , which can then be verified without revealing the identity of the verifier to the issuer .
- Holders can store verifiable credentials in any location, without affecting their verifiability and without the issuer knowing anything about where they are stored or when they are accessed.
- Holders can present verifiable presentations to any verifier without affecting authenticity of the claims and without revealing that action to the issuer .
- A verifier can verify verifiable presentations from any holder , containing proofs of claims from any issuer .
- Verification should not depend on direct interactions between issuers and verifiers .
- Verification should not reveal the identity of the verifier to any issuer .
- The specification must provide a means for issuers to issue verifiable credentials that support selective disclosure, without requiring all conformant software to support that feature.
- Issuers can issue verifiable credentials that support selective disclosure.
- If a single verifiable credential supports selective disclosure, then holders can present proofs of claims without revealing the entire verifiable credential .
- Verifiable presentations can either disclose the attributes of a verifiable credential , or satisfy derived predicates requested by the verifier . Derived predicates are Boolean conditions, such as greater than, less than, equal to, is in set, and so on.
- Issuers can issue revocable verifiable credentials .
- The processes of cryptographically protecting credentials and presentations , and verifying verifiable credentials and verifiable presentations , have to be deterministic, bi-directional, and lossless. Any verification of a verifiable credential or verifiable presentation has to be transformable to the generic data model defined in this document in a deterministic process, such that the resulting credential or presentation is semantically and syntactically equivalent to the original construct, so that it can be processed in an interoperable fashion.
- Verifiable credentials and verifiable presentations have to be serializable in one or more machine-readable data formats. The process of serialization and/or de-serialization has to be deterministic, bi-directional, and lossless. Any serialization of a verifiable credential or verifiable presentation needs to be transformable to the generic data model defined in this document in a deterministic process such that the resulting verifiable credential can be processed in an interoperable fashion. The serialized form also needs to be able to be generated from the data model without loss of data or content.
- The data model and serialization must be extendable with minimal coordination.
- Revocation by the issuer should not reveal any identifying information about the subject , the holder , the specific verifiable credential , or the verifier .
- Issuers can disclose the revocation reason.
- Issuers revoking verifiable credentials should distinguish between revocation for cryptographic integrity (for example, the signing key is compromised) versus revocation for a status change (for example, the driver’s license is suspended).
- Issuers can provide a service for refreshing a verifiable credential .
1.4 Conformance
As well as sections marked as non-normative, all authoring guidelines, diagrams, examples, and notes in this specification are non-normative. Everything else in this specification is normative.
The key words MAY , MUST , MUST NOT , RECOMMENDED , and SHOULD in this document are to be interpreted as described in BCP 14 [ RFC2119 ] [ RFC8174 ] when, and only when, they appear in all capitals, as shown here.
A conforming document is any concrete expression of the data model that complies with the normative statements in this specification. Specifically, all relevant normative statements in Sections 4. Basic Concepts , 5. Advanced Concepts , and 6. Syntaxes of this document MUST be enforced. A serialization format for the conforming document MUST be deterministic, bi-directional, and lossless as described in Section 6. Syntaxes . The conforming document MAY be transmitted or stored in any such serialization format.
A conforming processor is any algorithm realized as software and/or hardware that generates or consumes a conforming document . Conforming processors MUST produce errors when non-conforming documents are consumed.
This specification makes no normative statements with regard to the conformance of roles in the ecosystem, such as issuers , holders , or verifiers , because the conformance of ecosystem roles are highly application, use case, and market vertical specific.
Digital proof mechanisms, a subset of which are digital signatures, are required to ensure the protection of a verifiable credential . Having and validating proofs, which may be dependent on the syntax of the proof (for example, using the JSON Web Signature of a JSON Web Token for proofing a key holder), are an essential part of processing a verifiable credential . At the time of publication, Working Group members had implemented verifiable credentials using at least three proof mechanisms:
- JSON Web Tokens [ RFC7519 ] secured using JSON Web Signatures [ RFC7515 ]
- Data Integrity Proofs [ DATA-INTEGRITY ]
- Camenisch-Lysyanskaya Zero-Knowledge Proofs [ CL-SIGNATURES ].
Implementers are advised to note that not all proof mechanisms are standardized as of the publication date of this specification. The group expects some of these mechanisms, as well as new ones, to mature independently and become standardized in time. Given there are multiple valid proof mechanisms, this specification does not standardize on any single digital signature mechanism. One of the goals of this specification is to provide a data model that can be protected by a variety of current and future digital proof mechanisms. Conformance to this specification does not depend on the details of a particular proof mechanism; it requires clearly identifying the mechanism a verifiable credential uses.
This document also contains examples that contain JSON and JSON-LD content. Some of these examples contain characters that are invalid JSON, such as inline comments ( // ) and the use of ellipsis ( ... ) to denote information that adds little value to the example. Implementers are cautioned to remove this content if they desire to use the information as valid JSON or JSON-LD.
2. Terminology
The following terms are used to describe concepts in this specification.
3. Core Data Model
The following sections outline core data model concepts, such as claims , credentials , and presentations , which form the foundation of this specification.
A claim is a statement about a subject . A subject is a thing about which claims can be made. Claims are expressed using subject - property - value relationships.
The data model for claims , illustrated in Figure 2 above, is powerful and can be used to express a large variety of statements. For example, whether someone graduated from a particular university can be expressed as shown in Figure 3 below.
Individual claims can be merged together to express a graph of information about a subject . The example shown in Figure 4 below extends the previous claim by adding the claims that Pat knows Sam and that Sam is employed as a professor.
To this point, the concepts of a claim and a graph of information are introduced. To be able to trust claims , more information is expected to be added to the graph.
3.2 Credentials
A credential is a set of one or more claims made by the same entity . Credentials might also include an identifier and metadata to describe properties of the credential , such as the issuer , the expiry date and time, a representative image, a public key to use for verification purposes, the revocation mechanism, and so on. The metadata might be signed by the issuer . A verifiable credential is a set of tamper-evident claims and metadata that cryptographically prove who issued it.
Examples of verifiable credentials include digital employee identification cards, digital birth certificates, and digital educational certificates.
Credential identifiers are often used to identify specific instances of a credential . These identifiers can also be used for correlation. A holder wanting to minimize correlation is advised to use a selective disclosure scheme that does not reveal the credential identifier.
Figure 5 above shows the basic components of a verifiable credential , but abstracts the details about how claims are organized into information graphs , which are then organized into verifiable credentials . Figure 6 below shows a more complete depiction of a verifiable credential , which is normally composed of at least two information graphs . The first graph expresses the verifiable credential itself, which contains credential metadata and claims . The second graph expresses the digital proof, which is usually a digital signature.
It is possible to have a credential , such as a marriage certificate, containing multiple claims about different subjects that are not required to be related.
It is possible to have a credential that does not contain any claims about the entity to which the credential was issued. For example, a credential that only contains claims about a specific dog, but is issued to its owner.
3.3 Presentations
Enhancing privacy is a key design feature of this specification. Therefore, it is important for entities using this technology to be able to express only the portions of their persona that are appropriate for a given situation. The expression of a subset of one's persona is called a verifiable presentation . Examples of different personas include a person's professional persona, their online gaming persona, their family persona, or an incognito persona.
A verifiable presentation expresses data from one or more verifiable credentials , and is packaged in such a way that the authorship of the data is verifiable . If verifiable credentials are presented directly, they become verifiable presentations . Data formats derived from verifiable credentials that are cryptographically verifiable , but do not of themselves contain verifiable credentials , might also be verifiable presentations .
The data in a presentation is often about the same subject , but might have been issued by multiple issuers . The aggregation of this information typically expresses an aspect of a person, organization, or entity .
Figure 7 above shows the components of a verifiable presentation , but abstracts the details about how verifiable credentials are organized into information graphs , which are then organized into verifiable presentations .
Figure 8 below shows a more complete depiction of a verifiable presentation , which is normally composed of at least four information graphs . The first of these information graphs , the Presentation Graph , expresses the verifiable presentation itself, which contains presentation metadata. The verifiableCredential property in the Presentation Graph refers to one or more verifiable credentials , each being one of the second information graphs , i.e., a self-contained Credential Graph , which in turn contains credential metadata and claims. The third information graph , the Credential Proof Graph , expresses the credential graph proof, which is usually a digital signature. The fourth information graph , the Presentation Proof Graph , expresses the presentation graph proof, which is usually a digital signature.
It is possible to have a presentation , such as a business persona, which draws on multiple credentials about different subjects that are often, but not required to be, related.
3.4 Concrete Lifecycle Example
The previous sections introduced the concepts of claims , verifiable credentials , and verifiable presentations using graphical depictions. This section provides a concrete set of simple but complete lifecycle examples of the data model expressed in one of the concrete syntaxes supported by this specification. The lifecycle of credentials and presentations in the Verifiable Credentials Ecosystem often take a common path:
- Issuance of one or more verifiable credentials .
- Storage of verifiable credentials in a credential repository (such as a digital wallet).
- Composition of verifiable credentials into a verifiable presentation for verifiers .
- Verification of the verifiable presentation by the verifier .
To illustrate this lifecycle, we will use the example of redeeming an alumni discount from a university. In the example below, Pat receives an alumni verifiable credential from a university, and Pat stores the verifiable credential in a digital wallet.
Pat then attempts to redeem the alumni discount. The verifier , a ticket sales system, states that any alumni of "Example University" receives a discount on season tickets to sporting events. Using a mobile device, Pat starts the process of purchasing a season ticket. A step in this process requests an alumni verifiable credential , and this request is routed to Pat's digital wallet. The digital wallet asks Pat if they would like to provide a previously issued verifiable credential . Pat selects the alumni verifiable credential , which is then composed into a verifiable presentation . The verifiable presentation is sent to the verifier and verified .
Implementers that are interested in understanding more about the proof mechanism used above can learn more in Section 4.7 Proofs (Signatures) and by reading the following specifications: Data Integrity [ DATA-INTEGRITY ], Linked Data Cryptographic Suites Registry [ LDP-REGISTRY ], and JSON Web Signature (JWS) Unencoded Payload Option [ RFC7797 ]. A list of proof mechanisms is available in the Verifiable Credentials Extension Registry [ VC-EXTENSION-REGISTRY ].
4. Basic Concepts
This section introduces some basic concepts for the specification, in preparation for Section 5. Advanced Concepts later in the document.
4.1 Contexts
When two software systems need to exchange data, they need to use terminology that both systems understand. As an analogy, consider how two people communicate. Both people must use the same language and the words they use must mean the same thing to each other. This might be referred to as the context of a conversation .
Verifiable credentials and verifiable presentations have many attributes and values that are identified by URIs [ RFC3986 ]. However, those URIs can be long and not very human-friendly. In such cases, short-form human-friendly aliases can be more helpful. This specification uses the @context property to map such short-form aliases to the URIs required by specific verifiable credentials and verifiable presentations .
In JSON-LD, the @context property can also be used to communicate other details, such as datatype information, language information, transformation rules, and so on, which are beyond the needs of this specification, but might be useful in the future or to related work. For more information, see Section 3.1: The Context of the [ JSON-LD ] specification.
Verifiable credentials and verifiable presentations MUST include a @context property .
Though this specification requires that a @context property be present, it is not required that the value of the @context property be processed using JSON-LD. This is to support processing using plain JSON libraries, such as those that might be used when the verifiable credential is encoded as a JWT. All libraries or processors MUST ensure that the order of the values in the @context property is what is expected for the specific application. Libraries or processors that support JSON-LD can process the @context property using full JSON-LD processing as expected.
The example above uses the base context URI ( https://www.w3.org/2018/credentials/v1 ) to establish that the conversation is about a verifiable credential . The second URI ( https://www.w3.org/2018/credentials/examples/v1 ) establishes that the conversation is about examples.
This document uses the example context URI ( https://www.w3.org/2018/credentials/examples/v1 ) for the purpose of demonstrating examples. Implementations are expected to not use this URI for any other purpose, such as in pilot or production systems.
The data available at https://www.w3.org/2018/credentials/v1 is a static document that is never updated and SHOULD be downloaded and cached. The associated human-readable vocabulary document for the Verifiable Credentials Data Model is available at https://www.w3.org/2018/credentials/ . This concept is further expanded on in Section 5.3 Extensibility .
4.2 Identifiers
When expressing statements about a specific thing, such as a person, product, or organization, it is often useful to use some kind of identifier so that others can express statements about the same thing. This specification defines the optional id property for such identifiers. The id property is intended to unambiguously refer to an object, such as a person, product, or organization. Using the id property allows for the expression of statements about specific things in the verifiable credential .
If the id property is present:
- The id property MUST express an identifier that others are expected to use when expressing statements about a specific thing identified by that identifier.
- The id property MUST NOT have more than one value.
- The value of the id property MUST be a URI .
Developers should remember that identifiers might be harmful in scenarios where pseudonymity is required. Developers are encouraged to read Section 7.3 Identifier-Based Correlation carefully when considering such scenarios. There are also other types of correlation mechanisms documented in Section 7. Privacy Considerations that create privacy concerns. Where privacy is a strong consideration, the id property MAY be omitted.
The example above uses two types of identifiers. The first identifier is for the verifiable credential and uses an HTTP-based URL. The second identifier is for the subject of the verifiable credential (the thing the claims are about) and uses a decentralized identifier , also known as a DID .
As of this publication, DIDs are a new type of identifier that are not necessary for verifiable credentials to be useful. Specifically, verifiable credentials do not depend on DIDs and DIDs do not depend on verifiable credentials . However, it is expected that many verifiable credentials will use DIDs and that software libraries implementing this specification will probably need to resolve DIDs . DID -based URLs are used for expressing identifiers associated with subjects , issuers , holders , credential status lists, cryptographic keys, and other machine-readable information associated with a verifiable credential .
Software systems that process the kinds of objects specified in this document use type information to determine whether or not a provided verifiable credential or verifiable presentation is appropriate. This specification defines a type property for the expression of type information.
Verifiable credentials and verifiable presentations MUST have a type property . That is, any credential or presentation that does not have type property is not verifiable , so is neither a verifiable credential nor a verifiable presentation .
With respect to this specification, the following table lists the objects that MUST have a type specified.
| Object | Type |
|---|---|
| object (a subclass of a object) | and, optionally, a more specific . For example, |
| object | and, optionally, a more specific . For example, |
| object (a subclass of a object) | and, optionally, a more specific . For example, |
| object | and, optionally, a more specific . For example, |
| object | A valid proof . For example, |
| object | A valid status . For example, |
| object | A valid terms of use . For example, ) |
| object | A valid evidence . For example, |
The type system for the Verifiable Credentials Data Model is the same as for [ JSON-LD ] and is detailed in Section 5.4: Specifying the Type and Section 8: JSON-LD Grammar . When using a JSON-LD context (see Section 5.3 Extensibility ), this specification aliases the @type keyword to type to make the JSON-LD documents more easily understood. While application developers and document authors do not need to understand the specifics of the JSON-LD type system, implementers of this specification who want to support interoperable extensibility, do.
All credentials , presentations , and encapsulated objects MUST specify, or be associated with, additional more narrow types (like UniversityDegreeCredential , for example) so software systems can process this additional information.
When processing encapsulated objects defined in this specification, (for example, objects associated with the credentialSubject object or deeply nested therein), software systems SHOULD use the type information specified in encapsulating objects higher in the hierarchy. Specifically, an encapsulating object, such as a credential , SHOULD convey the associated object types so that verifiers can quickly determine the contents of an associated object based on the encapsulating object type .
For example, a credential object with the type of UniversityDegreeCredential , signals to a verifier that the object associated with the credentialSubject property contains the identifier for the:
- Subject in the id property.
- Type of degree in the type property.
- Title of the degree in the name property.
This enables implementers to rely on values associated with the type property for verification purposes. The expectation of types and their associated properties should be documented in at least a human-readable specification, and preferably, in an additional machine-readable representation.
The type system used in the data model described in this specification allows for multiple ways to associate types with data. Implementers and authors are urged to read the section on typing in the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ].
4.4 Credential Subject
A verifiable credential contains claims about one or more subjects . This specification defines a credentialSubject property for the expression of claims about one or more subjects .
A verifiable credential MUST have a credentialSubject property .
It is possible to express information related to multiple subjects in a verifiable credential . The example below specifies two subjects who are spouses. Note the use of array notation to associate multiple subjects with the credentialSubject property.
This specification defines a property for expressing the issuer of a verifiable credential .
A verifiable credential MUST have an issuer property .
It is also possible to express additional information about the issuer by associating an object with the issuer property:
The value of the issuer property can also be a JWK (for example, "https://example.com/keys/foo.jwk" ) or a DID (for example, "did:example:abfe13f712120431c276e12ecab" ).
4.6 Issuance Date
This specification defines the issuanceDate property for expressing the date and time when a credential becomes valid.
It is expected that the next version of this specification will add the validFrom property and will deprecate the issuanceDate property in favor of a new issued property . The range of values for both properties are expected to remain as [ XMLSCHEMA11-2 ] combined date-time strings. Implementers are advised that the validFrom and issued properties are reserved and use for any other purpose is discouraged.
4.7 Proofs (Signatures)
At least one proof mechanism, and the details necessary to evaluate that proof, MUST be expressed for a credential or presentation to be a verifiable credential or verifiable presentation ; that is, to be verifiable .
This specification identifies two classes of proof mechanisms: external proofs and embedded proofs. An external proof is one that wraps an expression of this data model, such as a JSON Web Token, which is elaborated on in Section 6.3.1 JSON Web Token . An embedded proof is a mechanism where the proof is included in the data, such as a Linked Data Signature, which is elaborated upon in Section 6.3.2 Data Integrity Proofs .
When embedding a proof, the proof property MUST be used.
Because the method used for a mathematical proof varies by representation language and the technology used, the set of name-value pairs that is expected as the value of the proof property will vary accordingly. For example, if digital signatures are used for the proof mechanism, the proof property is expected to have name-value pairs that include a signature, a reference to the signing entity, and a representation of the signing date. The example below uses RSA digital signatures.
As discussed in Section 1.4 Conformance , there are multiple viable proof mechanisms, and this specification does not standardize nor recommend any single proof mechanism for use with verifiable credentials . For more information about the proof mechanism, see the following specifications: Data Integrity [ DATA-INTEGRITY ], Linked Data Cryptographic Suites Registries [ LDP-REGISTRY ], and JSON Web Signature (JWS) Unencoded Payload Option [ RFC7797 ]. A list of proof mechanisms is available in the Verifiable Credentials Extension Registry [ VC-EXTENSION-REGISTRY ].
4.8 Expiration
This specification defines the expirationDate property for the expression of credential expiration information.
It is expected that the next version of this specification will add the validUntil property in a way that deprecates, but preserves backwards compatibility with the expirationDate property . Implementers are advised that the validUntil property is reserved and its use for any other purpose is discouraged.
This specification defines the following credentialStatus property for the discovery of information about the current status of a verifiable credential , such as whether it is suspended or revoked.
- id property , which MUST be a URI .
- type property , which expresses the credential status type (also referred to as the credential status method). It is expected that the value will provide enough information to determine the current status of the credential and that machine readable information needs to be retrievable from the URI. For example, the object could contain a link to an external document noting whether or not the credential is suspended or revoked.
The precise contents of the credential status information is determined by the specific credentialStatus type definition, and varies depending on factors such as whether it is simple to implement or if it is privacy-enhancing.
Defining the data model, formats, and protocols for status schemes are out of scope for this specification. A Verifiable Credential Extension Registry [ VC-EXTENSION-REGISTRY ] exists that contains available status schemes for implementers who want to implement verifiable credential status checking.
4.10 Presentations
Presentations MAY be used to combine and present credentials . They can be packaged in such a way that the authorship of the data is verifiable . The data in a presentation is often all about the same subject , but there is no limit to the number of subjects or issuers in the data. The aggregation of information from multiple verifiable credentials is a typical use of verifiable presentations .
A verifiable presentation is typically composed of the following properties:
The example below shows a verifiable presentation that embeds verifiable credentials .
The contents of the verifiableCredential property shown above are verifiable credentials , as described by this specification. The contents of the proof property are proofs, as described by the Data Integrity [ DATA-INTEGRITY ] specification. An example of a verifiable presentation using the JWT proof mechanism is given in section 6.3.1 JSON Web Token .
4.10.1 Presentations Using Derived Credentials
Some zero-knowledge cryptography schemes might enable holders to indirectly prove they hold claims from a verifiable credential without revealing the verifiable credential itself. In these schemes, a claim from a verifiable credential might be used to derive a presented value, which is cryptographically asserted such that a verifier can trust the value if they trust the issuer .
For example, a verifiable credential containing the claim date of birth might be used to derive the presented value over the age of 15 in a manner that is cryptographically verifiable . That is, a verifier can still trust the derived value if they trust the issuer .
For an example of a ZKP-style verifiable presentation containing derived data instead of directly embedded verifiable credentials , see Section 5.8 Zero-Knowledge Proofs .
Selective disclosure schemes using zero-knowledge proofs can use claims expressed in this model to prove additional statements about those claims . For example, a claim specifying a subject's date of birth can be used as a predicate to prove the subject's age is within a given range, and therefore prove the subject qualifies for age-related discounts, without actually revealing the subject's birthdate. The holder has the flexibility to use the claim in any way that is applicable to the desired verifiable presentation .
5. Advanced Concepts
Building on the concepts introduced in Section 4. Basic Concepts , this section explores more complex topics about verifiable credentials .
5.1 Lifecycle Details
Section 1.2 Ecosystem Overview provided an overview of the verifiable credential ecosystem. This section provides more detail about how the ecosystem is envisaged to operate.
The roles and information flows in the verifiable credential ecosystem are as follows:
- An issuer issues a verifiable credential to a holder . Issuance always occurs before any other actions involving a credential .
- A holder might transfer one or more of its verifiable credentials to another holder .
- A holder presents one or more of its verifiable credentials to a verifier , optionally inside a verifiable presentation .
- A verifier verifies the authenticity of the presented verifiable presentation and verifiable credentials . This should include checking the credential status for revocation of the verifiable credentials .
- An issuer might revoke a verifiable credential .
- A holder might delete a verifiable credential .
The order of the actions above is not fixed, and some actions might be taken more than once. Such action-recurrence might be immediate or at any later point.
The most common sequence of actions is envisioned to be:
- An issuer issues to a holder .
- The holder presents to a verifier .
- The verifier verifies .
This specification does not define any protocol for transferring verifiable credentials or verifiable presentations , but assuming other specifications do specify how they are transferred between entities, then this Verifiable Credential Data Model is directly applicable.
This specification also does not define an authorization framework nor the decisions that a verifier might make after verifying a verifiable credential or verifiable presentation , taking into account the holder , the issuers of the verifiable credentials , the contents of the verifiable credentials , and its own policies.
In particular, Sections 5.6 Terms of Use and C. Subject-Holder Relationships specify how a verifier can determine:
- Whether the holder is a subject of a verifiable credential .
- The relationship between the subject and the holder .
- Whether the original holder passed a verifiable credential to a subsequent holder .
- Any restrictions using the verifiable credentials by the holder or verifier .
5.2 Trust Model
The verifiable credentials trust model is as follows:
- Include a proof establishing that the issuer generated the credential (that is, it is a verifiable credential ), or
- Have been transmitted in a way clearly establishing that the issuer generated the verifiable credential and that the verifiable credential was not tampered with in transit or storage. This trust could be weakened depending on the risk assessment of the verifier .
- All entities trust the verifiable data registry to be tamper-evident and to be a correct record of which data is controlled by which entities .
- The holder and verifier trust the issuer to issue true (that is, not false) credentials about the subject , and to revoke them quickly when appropriate.
- The holder trusts the repository to store credentials securely, to not release them to anyone other than the holder , and to not corrupt or lose them while they are in its care.
This trust model differentiates itself from other trust models by ensuring the:
- Issuer and the verifier do not need to trust the repository
- Issuer does not need to know or trust the verifier .
By decoupling the trust between the identity provider and the relying party a more flexible and dynamic trust model is created such that market competition and customer choice is increased.
For more information about how this trust model interacts with various threat models studied by the Working Group, see the Verifiable Credentials Use Cases document [ VC-USE-CASES ].
The data model detailed in this specification does not imply a transitive trust model, such as that provided by more traditional Certificate Authority trust models. In the Verifiable Credentials Data Model, a verifier either directly trusts or does not trust an issuer . While it is possible to build transitive trust models using the Verifiable Credentials Data Model, implementers are urged to learn about the security weaknesses introduced by broadly delegating trust in the manner adopted by Certificate Authority systems.
5.3 Extensibility
One of the goals of the Verifiable Credentials Data Model is to enable permissionless innovation. To achieve this, the data model needs to be extensible in a number of different ways. The data model is required to:
- Model complex multi-entity relationships through the use of a graph -based data model.
- Extend the machine-readable vocabularies used to describe information in the data model, without the use of a centralized system for doing so, through the use of [ LINKED-DATA ].
- Support multiple types of cryptographic proof formats through the use of Data Integrity Proofs [ DATA-INTEGRITY ] and a variety of signature suites listed in the Linked Data Cryptographic Suites Registry [ LDP-REGISTRY ]
- Provide all of the extensibility mechanisms outlined above in a data format that is popular with software developers and web page authors, and is enabled through the use of [ JSON-LD ].
This approach to data modeling is often called an open world assumption , meaning that any entity can say anything about any other entity. While this approach seems to conflict with building simple and predictable software systems, balancing extensibility with program correctness is always more challenging with an open world assumption than with closed software systems.
The rest of this section describes, through a series of examples, how both extensibility and program correctness are achieved.
Let us assume we start with the verifiable credential shown below.
This verifiable credential states that the entity associated with did:example:abcdef1234567 has a name with a value of Jane Doe .
Now let us assume a developer wants to extend the verifiable credential to store two additional pieces of information: an internal corporate reference number, and Jane's favorite food.
The first thing to do is to create a JSON-LD context containing two new terms, as shown below.
After this JSON-LD context is created, the developer publishes it somewhere so it is accessible to verifiers who will be processing the verifiable credential . Assuming the above JSON-LD context is published at https://example.com/contexts/mycontext.jsonld , we can extend this example by including the context and adding the new properties and credential type to the verifiable credential .
This example demonstrates extending the Verifiable Credentials Data Model in a permissionless and decentralized way. The mechanism shown also ensures that verifiable credentials created in this way provide a mechanism to prevent namespace conflicts and semantic ambiguity.
A dynamic extensibility model such as this does increase the implementation burden. Software written for such a system has to determine whether verifiable credentials with extensions are acceptable based on the risk profile of the application. Some applications might accept only certain extensions while highly secure environments might not accept any extensions. These decisions are up to the developers of these applications and are specifically not the domain of this specification.
Developers are urged to ensure that extension JSON-LD contexts are highly available. Implementations that cannot fetch a context will produce an error. Strategies for ensuring that extension JSON-LD contexts are always available include using content-addressed URLs for contexts, bundling context documents with implementations, or enabling aggressive caching of contexts.
Implementers are advised to pay close attention to the extension points in this specification, such as in Sections 4.7 Proofs (Signatures) , 4.9 Status , 5.4 Data Schemas , 5.5 Refreshing , 5.6 Terms of Use , and 5.7 Evidence . While this specification does not define concrete implementations for those extension points, the Verifiable Credentials Extension Registry [ VC-EXTENSION-REGISTRY ] provides an unofficial, curated list of extensions that developers can use from these extension points.

5.3.1 Semantic Interoperability
This specification ensures that "plain" JSON and JSON-LD syntaxes are semantically compatible without requiring JSON implementations to use a JSON-LD processor. To achieve this, the specification imposes the following additional requirements on both syntaxes:
- JSON-based processors MUST process the @context key, ensuring the expected values exist in the expected order for the credential type being processed. The order is important because keys used in a credential , which are defined using the values associated with @context , are defined using a "first defined wins" mechanism and changing the order might result in a different key definition "winning".
- JSON-LD-based processors MUST produce an error when a JSON-LD context redefines any term in the active context . The only way to change the definition of existing terms is to introduce a new term that clears the active context within the scope of that new term. Authors that are interested in this feature should read about the @protected feature in the JSON-LD 1.1 specification.
A human-readable document describing the expected order of values for the @context property is expected to be published by any implementer seeking interoperability. A machine-readable description (that is, a normal JSON-LD Context document) is expected to be published at the URL specified in the @context property by JSON-LD implementers seeking interoperability.
The requirements above guarantee semantic interoperability between JSON and JSON-LD for terms defined by the @context mechanism. While JSON-LD processors will use the specific mechanism provided and can verify that all terms are correctly specified, JSON-based processors implicitly accept the same set of terms without testing that they are correct. In other words, the context in which the data exchange happens is explicitly stated for both JSON and JSON-LD by using the same mechanism. With respect to JSON-based processors, this is achieved in a lightweight manner, without having to use JSON-LD processing libraries.
5.4 Data Schemas
Data schemas are useful when enforcing a specific structure on a given collection of data. There are at least two types of data schemas that this specification considers:
- Data verification schemas, which are used to verify that the structure and contents of a credential or verifiable credential conform to a published schema.
- Data encoding schemas, which are used to map the contents of a verifiable credential to an alternative representation format, such as a binary format used in a zero-knowledge proof.
It is important to understand that data schemas serve a different purpose from the @context property, which neither enforces data structure or data syntax, nor enables the definition of arbitrary encodings to alternate representation formats.
This specification defines the following property for the expression of a data schema, which can be included by an issuer in the verifiable credentials that it issues:
The credentialSchema property provides an opportunity to annotate type definitions or lock them to specific versions of the vocabulary. Authors of verifiable credentials can include a static version of their vocabulary using credentialSchema that is locked to some content integrity protection mechanism. The credentialSchema property also makes it possible to perform syntactic checking on the credential and to use verification mechanisms such as JSON Schema [ JSON-SCHEMA-2018 ] validation.
In the example above, the issuer is specifying a credentialSchema , which points to a [ JSON-SCHEMA-2018 ] file that can be used by a verifier to determine if the verifiable credential is well formed.
For information about linkages to JSON Schema [ JSON-SCHEMA-2018 ] or other optional verification mechanisms, see the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
Data schemas can also be used to specify mappings to other binary formats, such as those used to perform zero-knowledge proofs. For more information on using the credentialSchema property with zero-knowledge proofs, see Section 5.8 Zero-Knowledge Proofs .
In the example above, the issuer is specifying a credentialSchema pointing to a zero-knowledge packed binary data format that is capable of transforming the input data into a format, which can then be used by a verifier to determine if the proof provided with the verifiable credential is valid.
5.5 Refreshing
It is useful for systems to enable the manual or automatic refresh of an expired verifiable credential . For more information about expired verifiable credentials , see Section 4.8 Expiration . This specification defines a refreshService property , which enables an issuer to include a link to a refresh service.
The issuer can include the refresh service as an element inside the verifiable credential if it is intended for either the verifier or the holder (or both), or inside the verifiable presentation if it is intended for the holder only. In the latter case, this enables the holder to refresh the verifiable credential before creating a verifiable presentation to share with a verifier . In the former case, including the refresh service inside the verifiable credential enables either the holder or the verifier to perform future updates of the credential .
The refresh service is only expected to be used when either the credential has expired or the issuer does not publish credential status information. Issuers are advised not to put the refreshService property in a verifiable credential that does not contain public information or whose refresh service is not protected in some way.
Placing a refreshService property in a verifiable credential so that it is available to verifiers can remove control and consent from the holder and allow the verifiable credential to be issued directly to the verifier , thereby bypassing the holder .
In the example above, the issuer specifies a manual refreshService that can be used by directing the holder or the verifier to https://example.edu/refresh/3732 .
5.6 Terms of Use
Terms of use can be utilized by an issuer or a holder to communicate the terms under which a verifiable credential or verifiable presentation was issued. The issuer places their terms of use inside the verifiable credential . The holder places their terms of use inside a verifiable presentation . This specification defines a termsOfUse property for expressing terms of use information.
The value of the termsOfUse property tells the verifier what actions it is required to perform (an obligation ), not allowed to perform (a prohibition ), or allowed to perform (a permission ) if it is to accept the verifiable credential or verifiable presentation .
Further study is required to determine how a subject who is not a holder places terms of use on their verifiable credentials . One way could be for the subject to request the issuer to place the terms of use inside the issued verifiable credentials . Another way could be for the subject to delegate a verifiable credential to a holder and place terms of use restrictions on the delegated verifiable credential .
In the example above, the issuer (the assigner ) is prohibiting verifiers (the assignee ) from storing the data in an archive.
Warning: The termsOfUse property is improperly defined within the VerifiablePresentation scoped context. This is a bug with the version 1 context and will be fixed in the version 2 context. In the meantime, implementors who wish to use this feature will be required to extend the context of their verifiable presentation with an additional term that defines the termsOfUse property, which can then be used alongside the verifiable presentation type property, in order for the term to be semantically recognized in a JSON-LD processor.
In the example above, the holder (the assigner ), who is also the subject , expressed a term of use prohibiting the verifier (the assignee , https://wineonline.example.org ) from using the information provided to correlate the holder or subject using a third-party service. If the verifier were to use a third-party service for correlation, they would violate the terms under which the holder created the presentation .
This feature is also expected to be used by government-issued verifiable credentials to instruct digital wallets to limit their use to similar government organizations in an attempt to protect citizens from unexpected usage of sensitive data. Similarly, some verifiable credentials issued by private industry are expected to limit usage to within departments inside the organization, or during business hours. Implementers are urged to read more about this rapidly evolving feature in the appropriate section of the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
5.7 Evidence
Evidence can be included by an issuer to provide the verifier with additional supporting information in a verifiable credential . This could be used by the verifier to establish the confidence with which it relies on the claims in the verifiable credential .
For example, an issuer could check physical documentation provided by the subject or perform a set of background checks before issuing the credential . In certain scenarios, this information is useful to the verifier when determining the risk associated with relying on a given credential .
This specification defines the evidence property for expressing evidence information.
For information about how attachments and references to credentials and non-credential data might be supported by the specification, see the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
In this evidence example, the issuer is asserting that they physically matched the subject of the credential to a physical copy of a driver's license with the stated license number. This driver's license was used in the issuance process to verify that "Example University" verified the subject before issuance of the credential and how they did so (physical verification).
The evidence property provides different and complementary information to the proof property . The evidence property is used to express supporting information, such as documentary evidence, related to the integrity of the verifiable credential . In contrast, the proof property is used to express machine-verifiable mathematical proofs related to the authenticity of the issuer and integrity of the verifiable credential . For more information about the proof property , see Section 4.7 Proofs (Signatures) .
5.8 Zero-Knowledge Proofs
A zero-knowledge proof is a cryptographic method where an entity can prove to another entity that they know a certain value without disclosing the actual value. A real-world example is proving that an accredited university has granted a degree to you without revealing your identity or any other personally identifiable information contained on the degree.
The key capabilities introduced by zero-knowledge proof mechanisms are the ability of a holder to:
- Combine multiple verifiable credentials from multiple issuers into a single verifiable presentation without revealing verifiable credential or subject identifiers to the verifier . This makes it more difficult for the verifier to collude with any of the issuers regarding the issued verifiable credentials .
- Selectively disclose the claims in a verifiable credential to a verifier without requiring the issuance of multiple atomic verifiable credentials . This allows a holder to provide a verifier with precisely the information they need and nothing more.
- Produce a derived verifiable credential that is formatted according to the verifier's data schema instead of the issuer's , without needing to involve the issuer after verifiable credential issuance. This provides a great deal of flexibility for holders to use their issued verifiable credentials .
This specification describes a data model that supports selective disclosure with the use of zero-knowledge proof mechanisms. The examples below highlight how the data model can be used to issue, present, and verify zero-knowledge verifiable credentials .
For a holder to use a zero-knowledge verifiable presentation , they need an issuer to have issued a verifiable credential in a manner that enables the holder to derive a proof from the originally issued verifiable credential , so that the holder can present the information to a verifier in a privacy-enhancing manner. This implies that the holder can prove the validity of the issuer's signature without revealing the values that were signed, or when only revealing certain selected values. The standard practice is to do so by proving knowledge of the signature, without revealing the signature itself. There are two requirements for verifiable credentials when they are to be used in zero-knowledge proof systems.
- The verifiable credential MUST contain a Proof, using the proof property , so that the holder can derive a verifiable presentation that reveals only the information than the holder intends to reveal.
- If a credential definition is being used, the credential definition MUST be defined in the credentialSchema property , so that it can be used by all parties to perform various cryptographic operations in zero-knowledge.
The following example shows one method of using verifiable credentials in zero-knowledge. It makes use of a Camenisch-Lysyanskaya Signature [ CL-SIGNATURES ], which allows the presentation of the verifiable credential in a way that supports the privacy of the holder and subject through the use of selective disclosure of the verifiable credential values. Some other cryptographic systems which rely upon zero-knowledge proofs to selectively disclose attributes can be found in the [ LDP-REGISTRY ] as well.
The example above provides the verifiable credential definition by using the credentialSchema property and a specific proof that is usable in the Camenisch-Lysyanskaya Zero-Knowledge Proof system.
The next example utilizes the verifiable credential above to generate a new derived verifiable credential with a privacy-preserving proof. The derived verifiable credential is then placed in a verifiable presentation , so that the verifiable credential discloses only the claims and additional credential metadata that the holder intended. To do this, all of the following requirements are expected to be met:
- Each derived verifiable credential within a verifiable presentation MUST contain all information necessary to verify the verifiable credential , either by including it directly within the credential, or by referencing the necessary information.
- A verifiable presentation MUST NOT leak information that would enable the verifier to correlate the holder across multiple verifiable presentations .
- The verifiable presentation SHOULD contain a proof property to enable the verifier to check that all derived verifiable credentials in the verifiable presentation were issued to the same holder without leaking personally identifiable information that the holder did not intend to share.
Important details regarding the format for the credential definition and of the proofs are omitted on purpose because they are outside of the scope of this document. The purpose of this section is to guide implementers who want to extend verifiable credentials and verifiable presentations to support zero-knowledge proof systems.
5.9 Disputes
There are at least two different cases to consider for an entity wanting to dispute a credential issued by an issuer :
- A subject disputes a claim made by the issuer . For example, the address property is incorrect or out of date.
- An entity disputes a potentially false claim made by the issuer about a different subject . For example, an imposter claims the social security number for an entity .
The mechanism for issuing a DisputeCredential is the same as for a regular credential except that the credentialSubject identifier in the DisputeCredential property is the identifier of the disputed credential .
For example, if a credential with an identifier of https://example.org/credentials/245 is disputed, the subject can issue the credential shown below and present it to the verifier along with the disputed credential .
In the above verifiable credential the issuer is claiming that the address in the disputed verifiable credential is wrong.
If a credential does not have an identifier, a content-addressed identifier can be used to identify the disputed credential . Similarly, content-addressed identifiers can be used to uniquely identify individual claims.
This area of study is rapidly evolving and developers that are interested in publishing credentials that dispute the veracity of other credentials are urged to read the section related to disputes in the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
5.10 Authorization
Verifiable credentials are intended as a means of reliably identifying subjects . While it is recognized that Role Based Access Controls (RBACs) and Attribute Based Access Controls (ABACs) rely on this identification as a means of authorizing subjects to access resources, this specification does not provide a complete solution for RBAC or ABAC. Authorization is not an appropriate use for this specification without an accompanying authorization framework.
The Working Group did consider authorization use cases during the creation of this specification and is pursuing that work as an architectural layer built on top of this specification.
6. Syntaxes
The data model as described in Sections 3. Core Data Model , 4. Basic Concepts , and 5. Advanced Concepts is the canonical structural representation of a verifiable credential or verifiable presentation . All serializations are representations of that data model in a specific format. This section specifies how the data model is realized in JSON-LD and plain JSON. Although syntactic mappings are provided for only these two syntaxes, applications and services can use any other data representation syntax (such as XML, YAML, or CBOR) that is capable of expressing the data model. As the verification and validation requirements are defined in terms of the data model, all serialization syntaxes have to be deterministically translated to the data model for processing, validation , or comparison. This specification makes no requirements for support of any specific serialization format.
The expected arity of the property values in this specification, and the resulting datatype which holds those values, can vary depending on the property. If present, the following properties are represented as a single value:
- id property
- issuer property
- issuanceDate property
- expirationDate property .
All other properties, if present, are represented as either a single value or an array of values.
The data model, as described in Section 3. Core Data Model , can be encoded in JavaScript Object Notation (JSON) [ RFC8259 ] by mapping property values to JSON types as follows:
- Numeric values representable as IEEE754 SHOULD be represented as a Number type.
- Boolean values SHOULD be represented as a Boolean type.
- Sequence value SHOULD be represented as an Array type.
- Unordered sets of values SHOULD be represented as an Array type.
- Sets of properties SHOULD be represented as an Object type.
- Empty values SHOULD be represented as a null value.
- Other values MUST be represented as a String type.
As the transformations listed herein have potentially incompatible interpretations, additional profiling of the JSON format is required to provide a deterministic transformation to the data model.
6.2 JSON-LD
[ JSON-LD ] is a JSON-based format used to serialize Linked Data . The syntax is designed to easily integrate into deployed systems already using JSON, and provides a smooth upgrade path from JSON to [ JSON-LD ]. It is primarily intended to be a way to use Linked Data in Web-based programming environments, to build interoperable Web services, and to store Linked Data in JSON-based storage engines.
[ JSON-LD ] is useful when extending the data model described in this specification. Instances of the data model are encoded in [ JSON-LD ] in the same way they are encoded in JSON (Section 6.1 JSON ), with the addition of the @context property . The JSON-LD context is described in detail in the [ JSON-LD ] specification and its use is elaborated on in Section 5.3 Extensibility .
Multiple contexts MAY be used or combined to express any arbitrary information about verifiable credentials in idiomatic JSON. The JSON-LD context , available at https://www.w3.org/2018/credentials/v1 , is a static document that is never updated and can therefore be downloaded and cached client side. The associated vocabulary document for the Verifiable Credentials Data Model is available at https://www.w3.org/2018/credentials .
6.2.1 Syntactic Sugar
In general, the data model and syntaxes described in this document are designed such that developers can copy and paste examples to incorporate verifiable credentials into their software systems. The design goal of this approach is to provide a low barrier to entry while still ensuring global interoperability between a heterogeneous set of software systems. This section describes some of these approaches, which will likely go unnoticed by most developers, but whose details will be of interest to implementers. The most noteworthy syntactic sugars provided by [ JSON-LD ] are:
- The @id and @type keywords are aliased to id and type respectively, enabling developers to use this specification as idiomatic JSON.
- Data types, such as integers, dates, units of measure, and URLs, are automatically typed to provide stronger type guarantees for use cases that require them.
- The verifiableCredential and proof properties are treated as graph containers . That is, mechanisms used to isolate sets of data asserted by different entities. This ensures, for example, proper cryptographic separation between the data graph provided by each issuer and the one provided by the holder presenting the verifiable credential to ensure the provenance of the information for each graph is preserved.
- The @protected properties feature of [ JSON-LD ] 1.1 is used to ensure that terms defined by this specification cannot be overridden. This means that as long as the same @context declaration is made at the top of a verifiable credential or verifiable presentation , interoperability is guaranteed for all terms understood by users of the data model whether or not they use a [ JSON-LD ] processor.
6.3 Proof Formats
The data model described in this specification is designed to be proof format agnostic. This specification does not normatively require any particular digital proof or signature format. While the data model is the canonical representation of a credential or presentation , the proofing mechanisms for these are often tied to the syntax used in the transmission of the document between parties. As such, each proofing mechanism has to specify whether the verification of the proof is calculated against the state of the document as transmitted, against the possibly transformed data model, or against another form. At the time of publication, at least two proof formats are being actively utilized by implementers and the Working Group felt that documenting what these proof formats are and how they are being used would be beneficial to implementers. The sections detailing the current proof formats being actively utilized to issue verifiable credentials are:
- Section 6.3.1 JSON Web Token , and
- Section 6.3.2 Data Integrity Proofs .
6.3.1 JSON Web Token
JSON Web Token (JWT) [ RFC7519 ] is still a widely used means to express claims to be transferred between two parties. Providing a representation of the Verifiable Credentials Data Model for JWT allows existing systems and libraries to participate in the ecosystem described in Section 1.2 Ecosystem Overview . A JWT encodes a set of claims as a JSON object that is contained in a JSON Web Signature (JWS) [ RFC7515 ] or JWE [ RFC7516 ]. For this specification, the use of JWE is out of scope.
Relation to the Verifiable Credentials Data Model
This specification defines encoding rules of the Verifiable Credential Data Model onto JWT and JWS. It further defines processing rules how and when to make use of specific JWT-registered claim names and specific JWS-registered header parameter names to allow systems based on JWT to comply with this specification. If these specific claim names and header parameters are present, their respective counterpart in the standard verifiable credential and verifiable presentation MAY be omitted to avoid duplication.
JSON Web Token Extensions
This specification introduces two new registered claim names, which contain those parts of the standard verifiable credentials and verifiable presentations where no explicit encoding rules for JWT exist. These objects are enclosed in the JWT payload as follows:
- vc : JSON object, which MUST be present in a JWT verifiable credential . The object contains the credential according to this specification.
- vp : JSON object, which MUST be present in a JWT verifiable presentation . The object contains the presentation according to this specification.
JWT and JWS Considerations
Jwt encoding.
To encode a verifiable credential as a JWT, specific properties introduced by this specification MUST be either:
- Encoded as standard JOSE header parameters, or
- Encoded as registered JWT claim names, or
- Contained in the JWS signature part.
If no explicit rule is specified, properties are encoded in the same way as with a standard credential , and are added to the vc claim of the JWT. As with all JWTs, the JWS-based signature of a verifiable credential represented in the JWT syntax is calculated against the literal JWT string value as presented across the wire, before any decoding or transformation rules are applied. The following paragraphs describe these encoding rules.
If a JWS is present, the digital signature refers either to the issuer of the verifiable credential , or in the case of a verifiable presentation , to the holder of the verifiable credential . The JWS proves that the iss of the JWT signed the contained JWT payload and therefore, the proof property can be omitted.
If no JWS is present, a proof property MUST be provided. The proof property can be used to represent a more complex proof, as may be necessary if the creator is different from the issuer , or a proof not based on digital signatures, such as Proof of Work. The issuer MAY include both a JWS and a proof property . For backward compatibility reasons, the issuer MUST use JWS to represent proofs based on a digital signature.
The following rules apply to JOSE headers in the context of this specification:
- alg MUST be set for digital signatures. If only the proof property is needed for the chosen signature method (that is, if there is no choice of algorithm within that method), the alg header MUST be set to none .
- kid MAY be used if there are multiple keys associated with the issuer of the JWT. The key discovery is out of the scope of this specification. For example, the kid can refer to a key in a DID document , or can be the identifier of a key inside a JWKS.
- typ , if present, MUST be set to JWT .
For backward compatibility with JWT processors, the following registered JWT claim names MUST be used, instead of or in addition to, their respective standard verifiable credential counterparts:
- exp MUST represent the expirationDate property , encoded as a UNIX timestamp ( NumericDate ).
- iss MUST represent the issuer property of a verifiable credential or the holder property of a verifiable presentation.
- nbf MUST represent issuanceDate , encoded as a UNIX timestamp ( NumericDate ).
- jti MUST represent the id property of the verifiable credential or verifiable presentation .
In bearer credentials and presentations , sub will not be present.
- aud MUST represent (i.e., identify) the intended audience of the verifiable presentation (i.e., the verifier intended by the presenting holder to receive and verify the verifiable presentation ).
Other JOSE header parameters and JWT claim names not specified herein can be used if their use is not explicitly discouraged. Additional verifiable credential claims MUST be added to the credentialSubject property of the JWT.
For more information about using JOSE header parameters and/or JWT claim names not specified herein, see the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
This version of the specification defines no JWT-specific encoding rules for the concepts outlined in Section Advanced Concepts (for example, refreshService , termsOfUse , and evidence ). These concepts can be encoded as they are without any transformation, and can be added to the vc JWT claim .
Implementers are warned that JWTs are not capable of encoding multiple subjects and are thus not capable of encoding a verifiable credential with more than one subject . JWTs might support multiple subjects in the future and implementers are advised to refer to the JSON Web Token Claim Registry for multi-subject JWT claim names or the Nested JSON Web Token specification.
JWT Decoding
To decode a JWT to a standard credential or presentation , the following transformation MUST be performed:
- Create a JSON object.
- Add the content from the vc or vp claim to the new JSON object.
- Transform the remaining JWT specific headers and claims , and add the results to the new credential or presentation JSON object.
To transform the JWT specific headers and claims , the following MUST be done:
- If exp is present, the UNIX timestamp MUST be converted to an [ XMLSCHEMA11-2 ] date-time , and MUST be used to set the value of the expirationDate property of credentialSubject of the new JSON object.
- If iss is present, the value MUST be used to set the issuer property of the new credential JSON object or the holder property of the new presentation JSON object.
- If nbf is present, the UNIX timestamp MUST be converted to an [ XMLSCHEMA11-2 ] date-time , and MUST be used to set the value of the issuanceDate property of the new JSON object.
- If sub is present, the value MUST be used to set the value of the id property of credentialSubject of the new credential JSON object.
- If jti is present, the value MUST be used to set the value of the id property of the new JSON object.
In the example above, the verifiable credential uses a proof based on JWS digital signatures, and the corresponding verification key can be obtained using the kid header parameter.
In the example above, vc does not contain the id property because the JWT encoding uses the jti attribute to represent a unique identifier. The sub attribute encodes the information represented by the id property of credentialSubject . The nonce has been added to stop a replay attack.
In the example above, the verifiable presentation uses a proof based on JWS digital signatures, and the corresponding verification key can be obtained using the kid header parameter.
In the example above, vp does not contain the id property because the JWT encoding uses the jti attribute to represent a unique identifier. verifiableCredential contains a string array of verifiable credentials using JWT compact serialization. The nonce has been added to stop a replay attack.
6.3.2 Data Integrity Proofs
This specification utilizes Linked Data to publish information on the Web using standards, such as URLs and JSON-LD, to identify subjects and their associated properties. When information is presented in this manner, other related information can be easily discovered and new information can be easily merged into the existing graph of knowledge. Linked Data is extensible in a decentralized way, greatly reducing barriers to large scale integration. The data model in this specification works well with Data Integrity and the associated Linked Data Cryptographic Suites which are designed to protect the data model as described by this specification.
Unlike the use of JSON Web Token, no extra pre- or post-processing is necessary. The Data Integrity Proofs format was designed to simply and easily protect verifiable credentials and verifiable presentations . Protecting a verifiable credential or verifiable presentation is as simple as passing a valid example in this specification to a Linked Data Signatures implementation and generating a digital signature.
For more information about the different qualities of the various syntax formats (for example, JSON+JWT, JSON-LD+JWT, or JSON-LD+LD-Proofs), see the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
7. Privacy Considerations
This section details the general privacy considerations and specific privacy implications of deploying the Verifiable Credentials Data Model into production environments.
7.1 Spectrum of Privacy
It is important to recognize there is a spectrum of privacy ranging from pseudonymous to strongly identified. Depending on the use case, people have different comfort levels about what information they are willing to provide and what information can be derived from what is provided.
For example, most people probably want to remain anonymous when purchasing alcohol because the regulatory check required is solely based on whether a person is above a specific age. Alternatively, for medical prescriptions written by a doctor for a patient, the pharmacy fulfilling the prescription is required to more strongly identify the medical professional and the patient. Therefore there is not one approach to privacy that works for all use cases. Privacy solutions are use case specific.
Even for those wanting to remain anonymous when purchasing alcohol, photo identification might still be required to provide appropriate assurance to the merchant. The merchant might not need to know your name or other details (other than that you are over a specific age), but in many cases just proof of age might still be insufficient to meet regulations.
The Verifiable Credentials Data Model strives to support the full privacy spectrum and does not take philosophical positions on the correct level of anonymity for any specific transaction. The following sections provide guidance for implementers who want to avoid specific scenarios that are hostile to privacy.
7.2 Personally Identifiable Information
Data associated with verifiable credentials stored in the credential.credentialSubject field is susceptible to privacy violations when shared with verifiers . Personally identifying data, such as a government-issued identifier, shipping address, and full name, can be easily used to determine, track, and correlate an entity . Even information that does not seem personally identifiable, such as the combination of a birthdate and a postal code, has very powerful correlation and de-anonymizing capabilities.
Implementers are strongly advised to warn holders when they share data with these kinds of characteristics. Issuers are strongly advised to provide privacy-protecting verifiable credentials when possible. For example, issuing ageOver verifiable credentials instead of date of birth verifiable credentials when a verifier wants to determine if an entity is over the age of 18.
Because a verifiable credential often contains personally identifiable information (PII), implementers are strongly advised to use mechanisms while storing and transporting verifiable credentials that protect the data from those who should not access it. Mechanisms that could be considered include Transport Layer Security (TLS) or other means of encrypting the data while in transit, as well as encryption or data access control mechanisms to protect the data in a verifiable credential while at rest.
7.3 Identifier-Based Correlation
Subjects of verifiable credentials are identified using the credential.credentialSubject.id field. The identifiers used to identify a subject create a greater risk of correlation when the identifiers are long-lived or used across more than one web domain.
Similarly, disclosing the credential identifier ( credential.id ) leads to situations where multiple verifiers , or an issuer and a verifier , can collude to correlate the holder . If holders want to reduce correlation, they should use verifiable credential schemes that allow hiding the identifier during verifiable presentation . Such schemes expect the holder to generate the identifier and might even allow hiding the identifier from the issuer , while still keeping the identifier embedded and signed in the verifiable credential .
If strong anti-correlation properties are a requirement in a verifiable credentials system, it is strongly advised that identifiers are either:
- Bound to a single origin
- Not used at all, but instead replaced by short-lived, single-use bearer tokens.
7.4 Signature-Based Correlation
The contents of verifiable credentials are secured using the credential.proof field. The properties in this field create a greater risk of correlation when the same values are used across more than one session or domain and the value does not change. Examples include the verificationMethod , created , proofPurpose , and jws fields.
If strong anti-correlation properties are required, it is advised that signature values and metadata are regenerated each time using technologies like third-party pairwise signatures, zero-knowledge proofs, or group signatures.
Even when using anti-correlation signatures, information might still be contained in a verifiable credential that defeats the anti-correlation properties of the cryptography used.
7.5 Long-Lived Identifier-Based Correlation
Verifiable credentials might contain long-lived identifiers that could be used to correlate individuals. These types of identifiers include subject identifiers, email addresses, government-issued identifiers, organization-issued identifiers, addresses, healthcare vitals, verifiable credential -specific JSON-LD contexts, and many other sorts of long-lived identifiers.
Organizations providing software to holders should strive to identify fields in verifiable credentials containing information that could be used to correlate individuals and warn holders when this information is shared.
7.6 Device Fingerprinting
There are mechanisms external to verifiable credentials that are used to track and correlate individuals on the Internet and the Web. Some of these mechanisms include Internet protocol (IP) address tracking, web browser fingerprinting, evercookies, advertising network trackers, mobile network position information, and in-application Global Positioning System (GPS) APIs. Using verifiable credentials cannot prevent the use of these other tracking technologies. Also, when these technologies are used in conjunction with verifiable credentials , new correlatable information could be discovered. For example, a birthday coupled with a GPS position can be used to strongly correlate an individual across multiple websites.
It is recommended that privacy-respecting systems prevent the use of these other tracking technologies when verifiable credentials are being used. In some cases, tracking technologies might need to be disabled on devices that transmit verifiable credentials on behalf of a holder .
7.7 Favor Abstract Claims
To enable recipients of verifiable credentials to use them in a variety of circumstances without revealing more PII than necessary for transactions, issuers should consider limiting the information published in a credential to a minimal set needed for the expected purposes. One way to avoid placing PII in a credential is to use an abstract property that meets the needs of verifiers without providing specific information about a subject .
For example, this document uses the ageOver property instead of a specific birthdate, which constitutes much stronger PII. If retailers in a specific market commonly require purchasers to be older than a certain age, an issuer trusted in that market might choose to offer a verifiable credential claiming that subjects have met that requirement instead of offering verifiable credentials containing claims about specific birthdates. This enables individual customers to make purchases without revealing specific PII.
7.8 The Principle of Data Minimization
Privacy violations occur when information divulged in one context leaks into another. Accepted best practice for preventing such violations is to limit the information requested, and received, to the absolute minimum necessary. This data minimization approach is required by regulation in multiple jurisdictions, including the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in the European Union.
With verifiable credentials , data minimization for issuers means limiting the content of a verifiable credential to the minimum required by potential verifiers for expected use. For verifiers , data minimization means limiting the scope of the information requested or required for accessing services.
For example, a driver's license containing a driver's ID number, height, weight, birthday, and home address is a credential containing more information than is necessary to establish that the person is above a certain age.
It is considered best practice for issuers to atomize information or use a signature scheme that allows for selective disclosure . For example, an issuer of driver's licenses could issue a verifiable credential containing every attribute that appears on a driver's license, as well as a set of verifiable credentials where every verifiable credential contains only a single attribute, such as a person's birthday. It could also issue more abstract verifiable credentials (for example, a verifiable credential containing only an ageOver attribute). One possible adaptation would be for issuers to provide secure HTTP endpoints for retrieving single-use bearer credentials that promote the pseudonymous usage of verifiable credentials . Implementers that find this impractical or unsafe, should consider using selective disclosure schemes that eliminate dependence on issuers at proving time and reduce temporal correlation risk from issuers .
Verifiers are urged to only request information that is absolutely necessary for a specific transaction to occur. This is important for at least two reasons. It:
- Reduces the liability on the verifier for handling highly sensitive information that it does not need to.
- Enhances the privacy of the individual by only asking for information required for a specific transaction.
While it is possible to practice the principle of minimum disclosure, it might be impossible to avoid the strong identification of an individual for specific use cases during a single session or over multiple sessions. The authors of this document cannot stress how difficult it is to meet this principle in real-world scenarios.
7.9 Bearer Credentials
A bearer credential is a privacy-enhancing piece of information, such as a concert ticket, which entitles the holder of the bearer credential to a specific resource without divulging sensitive information about the holder . Bearer credentials are often used in low-risk use cases where the sharing of the bearer credential is not a concern or would not result in large economic or reputational losses.
Verifiable credentials that are bearer credentials are made possible by not specifying the subject identifier, expressed using the id property , which is nested in the credentialSubject property . For example, the following verifiable credential is a bearer credential :
While bearer credentials can be privacy-enhancing, they must be carefully crafted so as not accidentally divulge more information than the holder of the bearer credential expects. For example, repeated use of the same bearer credential across multiple sites enables these sites to potentially collude to unduly track or correlate the holder . Likewise, information that might seem non-identifying, such as a birthdate and postal code, can be used to statistically identify an individual when used together in the same bearer credential or session.
Issuers of bearer credentials should ensure that the bearer credentials provide privacy-enhancing benefits that:
- Are single-use, where possible.
- Do not contain personally identifying information.
- Are not unduly correlatable.
Holders should be warned by their software if bearer credentials containing sensitive information are issued or requested, or if there is a correlation risk when combining two or more bearer credentials across one or more sessions. While it might be impossible to detect all correlation risks, some might certainly be detectable.
Verifiers should not request bearer credentials that can be used to unduly correlate the holder .
7.10 Validity Checks
When processing verifiable credentials , verifiers are expected to perform many of the checks listed in Appendix A. Validation as well as a variety of specific business process checks. Validity checks might include checking:
- The professional licensure status of the holder .
- A date of license renewal or revocation.
- The sub-qualifications of an individual.
- If a relationship exists between the holder and the entity with whom the holder is attempting to interact.
- The geolocation information associated with the holder .
The process of performing these checks might result in information leakage that leads to a privacy violation of the holder . For example, a simple operation such as checking a revocation list can notify the issuer that a specific business is likely interacting with the holder . This could enable issuers to collude and correlate individuals without their knowledge.
Issuers are urged to not use mechanisms, such as credential revocation lists that are unique per credential , during the verification process that could lead to privacy violations. Organizations providing software to holders should warn when credentials include information that could lead to privacy violations during the verification process. Verifiers should consider rejecting credentials that produce privacy violations or that enable bad privacy practices.
7.11 Storage Providers and Data Mining
When a holder receives a verifiable credential from an issuer , the verifiable credential needs to be stored somewhere (for example, in a credential repository). Holders are warned that the information in a verifiable credential is sensitive in nature and highly individualized, making it a high value target for data mining. Services that advertise free storage of verifiable credentials might in fact be mining personal data and selling it to organizations wanting to build individualized profiles on people and organizations.
Holders need to be aware of the terms of service for their credential repository, specifically the correlation and data mining protections in place for those who store their verifiable credentials with the service provider.
Some effective mitigations for data mining and profiling include using:
- Service providers that do not sell your information to third parties.
- Software that encrypts verifiable credentials such that a service provider cannot view the contents of the credential .
- Software that stores verifiable credentials locally on a device that you control and that does not upload or analyze your information beyond your expectations.
7.12 Aggregation of Credentials
Holding two pieces of information about the same subject almost always reveals more about the subject than just the sum of the two pieces, even when the information is delivered through different channels. The aggregation of verifiable credentials is a privacy risk and all participants in the ecosystem need to be aware of the risks of data aggregation.
For example, if two bearer credentials , one for an email address and then one stating the holder is over the age of 21, are provided across multiple sessions, the verifier of the information now has a unique identifier as well as age-related information for that individual. It is now easy to create and build a profile for the holder such that more and more information is leaked over time. Aggregation of credentials can also be performed across multiple sites in collusion with each other, leading to privacy violations.
From a technological perspective, preventing aggregation of information is a very difficult privacy problem to address. While new cryptographic techniques, such as zero-knowledge proofs, are being proposed as solutions to the problem of aggregation and correlation, the existence of long-lived identifiers and browser tracking techniques defeats even the most modern cryptographic techniques.
The solution to the privacy implications of correlation or aggregation tends not to be technological in nature, but policy driven instead. Therefore, if a holder does not want information about them to be aggregated, they must express this in the verifiable presentations they transmit.
7.13 Usage Patterns
Despite the best efforts to assure privacy, actually using verifiable credentials can potentially lead to de-anonymization and a loss of privacy. This correlation can occur when:
- The same verifiable credential is presented to the same verifier more than once. The verifier could infer that the holder is the same individual.
- The same verifiable credential is presented to different verifiers , and either those verifiers collude or a third party has access to transaction records from both verifiers . An observant party could infer that the individual presenting the verifiable credential is the same person at both services. That is, the accounts are controlled by the same person.
- A subject identifier of a credential refers to the same subject across multiple presentations or verifiers . Even when different credentials are presented, if the subject identifier is the same, verifiers (and those with access to verifier logs) could infer that the holder of the credential is the same person.
- The underlying information in a credential can be used to identify an individual across services. In this case, using information from other sources (including information provided directly by the holder ), verifiers can use information inside the credential to correlate the individual with an existing profile. For example, if a holder presents credentials that include postal code, age, and gender, a verifier can potentially correlate the subject of that credential with an established profile. For more information, see [ DEMOGRAPHICS ].
- Passing the identifier of a credential to a centralized revocation server. The centralized server can correlate the credential usage across interactions. For example, if a credential is used for proof of age in this manner, the centralized service could know everywhere that credential was presented (all liquor stores, bars, adult stores, lottery purchases, and so on).
In part, it is possible to mitigate this de-anonymization and loss of privacy by:
- Using a globally-unique identifier as the subject for any given credential and never re-use that credential .
- If the credential supports revocation, using a globally-distributed service for revocation.
- Designing revocation APIs that do not depend on submitting the ID of the credential . For example, use a revocation list instead of a query.
- Avoiding the association of personally identifiable information with any specific long-lived subject identifier.
It is understood that these mitigation techniques are not always practical or even compatible with necessary usage. Sometimes correlation is a requirement.
For example, in some prescription drug monitoring programs, usage monitoring is a requirement. Enforcement entities need to be able to confirm that individuals are not cheating the system to get multiple prescriptions for controlled substances. This statutory or regulatory need to correlate usage overrides individual privacy concerns.
Verifiable credentials will also be used to intentionally correlate individuals across services, for example, when using a common persona to log in to multiple services, so all activity on each of those services is intentionally linked to the same individual. This is not a privacy issue as long as each of those services uses the correlation in the expected manner.
Privacy risks of credential usage occur when unintended or unexpected correlation arises from the presentation of credentials .
7.14 Sharing Information with the Wrong Party
When a holder chooses to share information with a verifier , it might be the case that the verifier is acting in bad faith and requests information that could be used to harm the holder . For example, a verifier might ask for a bank account number, which could then be used with other information to defraud the holder or the bank.
Issuers should strive to tokenize as much information as possible such that if a holder accidentally transmits credentials to the wrong verifier , the situation is not catastrophic.
For example, instead of including a bank account number for the purpose of checking an individual's bank balance, provide a token that enables the verifier to check if the balance is above a certain amount. In this case, the bank could issue a verifiable credential containing a balance checking token to a holder . The holder would then include the verifiable credential in a verifiable presentation and bind the token to a credit checking agency using a digital signature. The verifier could then wrap the verifiable presentation in their digital signature, and hand it back to the issuer to dynamically check the account balance.
Using this approach, even if a holder shares the account balance token with the wrong party, an attacker cannot discover the bank account number, nor the exact value in the account. And given the validity period for the counter-signature, does not gain access to the token for more than a few minutes.
7.15 Frequency of Claim Issuance
As detailed in Section 7.13 Usage Patterns , usage patterns can be correlated into certain types of behavior. Part of this correlation is mitigated when a holder uses a verifiable credential without the knowledge of the issuer . Issuers can defeat this protection however, by making their verifiable credentials short lived and renewal automatic.
For example, an ageOver verifiable credential is useful for gaining access to a bar. If an issuer issues such a verifiable credential with a very short expiration date and an automatic renewal mechanism, then the issuer could possibly correlate the behavior of the holder in a way that negatively impacts the holder .
Organizations providing software to holders should warn them if they repeatedly use credentials with short lifespans, which could result in behavior correlation. Issuers should avoid issuing credentials in a way that enables them to correlate usage patterns.
7.16 Prefer Single-Use Credentials
An ideal privacy-respecting system would require only the information necessary for interaction with the verifier to be disclosed by the holder . The verifier would then record that the disclosure requirement was met and forget any sensitive information that was disclosed. In many cases, competing priorities, such as regulatory burden, prevent this ideal system from being employed. In other cases, long-lived identifiers prevent single use. The design of any verifiable credentials ecosystem, however, should strive to be as privacy-respecting as possible by preferring single-use verifiable credentials whenever possible.
Using single-use verifiable credentials provides several benefits. The first benefit is to verifiers who can be sure that the data in a verifiable credential is fresh. The second benefit is to holders , who know that if there are no long-lived identifiers in the verifiable credential , the verifiable credential itself cannot be used to track or correlate them online. Finally, there is nothing for attackers to steal, making the entire ecosystem safer to operate within.
7.17 Private Browsing
In an ideal private browsing scenario, no PII will be revealed. Because many credentials include PII, organizations providing software to holders should warn them about the possibility of revealing this information if they wish to use credentials and presentations while in private browsing mode. As each browser vendor handles private browsing differently, and some browsers might not have this feature at all, it is important for implementers to be aware of these differences and implement solutions accordingly.
7.18 Issuer Cooperation Impacts on Privacy
It cannot be overstated that verifiable credentials rely on a high degree of trust in issuers . The degree to which a holder might take advantage of possible privacy protections often depends strongly on the support an issuer provides for such features. In many cases, privacy protections which make use of zero-knowledge proofs, data minimization techniques, bearer credentials, abstract claims, and protections against signature-based correlation, require the issuer to actively support such capabilities and incorporate them into the verifiable credentials they issue.
It should also be noted that, in addition to a reliance on issuer participation to provide verifiable credential capabilities that help preserve holder and subject privacy, holders rely on issuers to not deliberately subvert privacy protections. For example, an issuer might sign verifiable credentials using a signature scheme that protects against signature-based correlation. This would protect the holder from being correlated by the signature value as it is shared among verifiers . However, if the issuer creates a unique key for each issued credential , it might be possible for the issuer to track presentations of the credential , regardless of a verifier 's inability to do so.
8. Security Considerations
There are a number of security considerations that issuers , holders , and verifiers should be aware of when processing data described by this specification. Ignoring or not understanding the implications of this section can result in security vulnerabilities.
While this section attempts to highlight a broad set of security considerations, it is not a complete list. Implementers are urged to seek the advice of security and cryptography professionals when implementing mission critical systems using the technology outlined in this specification.
8.1 Cryptography Suites and Libraries
Some aspects of the data model described in this specification can be protected through the use of cryptography. It is important for implementers to understand the cryptography suites and libraries used to create and process credentials and presentations . Implementing and auditing cryptography systems generally requires substantial experience. Effective red teaming can also help remove bias from security reviews.
Cryptography suites and libraries have a shelf life and eventually fall to new attacks and technology advances. Production quality systems need to take this into account and ensure mechanisms exist to easily and proactively upgrade expired or broken cryptography suites and libraries, and to invalidate and replace existing credentials . Regular monitoring is important to ensure the long term viability of systems processing credentials .
8.2 Content Integrity Protection
Verifiable credentials often contain URLs to data that resides outside of the verifiable credential itself. Linked content that exists outside a verifiable credential , such as images, JSON-LD Contexts, and other machine-readable data, are often not protected against tampering because the data resides outside of the protection of the proof on the verifiable credential . For example, the following highlighted links are not content-integrity protected but probably should be:
While this specification does not recommend any specific content integrity protection, document authors who want to ensure links to content are integrity protected are advised to use URL schemes that enforce content integrity. Two such schemes are the [ HASHLINK ] specification and the [ IPFS ]. The example below transforms the previous example and adds content integrity protection to the JSON-LD Contexts using the [ HASHLINK ] specification, and content integrity protection to the image by using an [ IPFS ] link.
It is debatable whether the JSON-LD Contexts above need protection because production implementations are expected to ship with static copies of important JSON-LD Contexts.
While the example above is one way to achieve content integrity protection, there are other solutions that might be better suited for certain applications. Implementers are urged to understand how links to external machine-readable content that are not content-integrity protected could result in successful attacks against their applications.
8.3 Unsigned Claims
This specification allows credentials to be produced that do not contain signatures or proofs of any kind. These types of credentials are often useful for intermediate storage, or self-asserted information, which is analogous to filling out a form on a web page. Implementers should be aware that these types of credentials are not verifiable because the authorship either is not known or cannot be trusted.
8.4 Token Binding
A verifier might need to ensure it is the intended recipient of a verifiable presentation and not the target of a man-in-the-middle attack . Approaches such as token binding [ RFC8471 ], which ties the request for a verifiable presentation to the response, can secure the protocol. Any unsecured protocol is susceptible to man-in-the-middle attacks.
8.5 Bundling Dependent Claims
It is considered best practice for issuers to atomize information in a credential , or use a signature scheme that allows for selective disclosure. In the case of atomization, if it is not done securely by the issuer , the holder might bundle together different credentials in a way that was not intended by the issuer .
For example, a university might issue two verifiable credentials to a person, each containing two properties , which must be taken together to to designate the "role" of that person in a given "department", such as "Staff Member" in the "Department of Computing", or "Post Graduate Student" in the "Department of Economics". If these verifiable credentials are atomized to put only one of these properties into each credential , then the university would issue four credentials to the person, each containing one of the following designations: "Staff Member", "Post Graduate Student", "Department of Computing", and "Department of Economics". The holder might then transfer the "Staff Member" and "Department of Economics" verifiable credentials to a verifier , which together would comprise a false claim .
8.6 Highly Dynamic Information
When verifiable credentials are issued for highly dynamic information, implementers should ensure the expiration times are set appropriately. Expiration periods longer than the timeframe where the verifiable credential is valid might create exploitable security vulnerabilities. Expiration periods shorter than the timeframe where the information expressed by the verifiable credential is valid creates a burden on holders and verifiers . It is therefore important to set validity periods for verifiable credentials that are appropriate to the use case and the expected lifetime for the information contained in the verifiable credential .
8.7 Device Theft and Impersonation
When verifiable credentials are stored on a device and that device is lost or stolen, it might be possible for an attacker to gain access to systems using the victim's verifiable credentials . Ways to mitigate this type of attack include:
- Enabling password, pin, pattern, or biometric screen unlock protection on the device.
- Enabling password, biometric, or multi-factor authentication for the credential repository .
- Enabling password, biometric, or multi-factor authentication when accessing cryptographic keys.
- Using a separate hardware-based signature device.
- All or any combination of the above.
9. Accessibility Considerations
There are a number of accessibility considerations implementers should be aware of when processing data described in this specification. As with implementation of any web standard or protocol, ignoring accessibility issues makes this information unusable by a large subset of the population. It is important to follow accessibility guidelines and standards, such as [ WCAG21 ], to ensure that all people, regardless of ability, can make use of this data. This is especially important when establishing systems utilizing cryptography, which have historically created problems for assistive technologies.
This section details the general accessibility considerations to take into account when utilizing this data model.
9.1 Data First Approaches
Many physical credentials in use today, such as government identification cards, have poor accessibility characteristics, including, but not limited to, small print, reliance on small and high-resolution images, and no affordances for people with vision impairments.
When utilizing this data model to create verifiable credentials , it is suggested that data model designers use a data first approach. For example, given the choice of using data or a graphical image to depict a credential , designers should express every element of the image, such as the name of an institution or the professional credential , in a machine-readable way instead of relying on a viewer's interpretation of the image to convey this information. Using a data first approach is preferred because it provides the foundational elements of building different interfaces for people with varying abilities.
10. Internationalization Considerations
Implementers are advised to be aware of a number of internationalization considerations when publishing data described in this specification. As with any web standards or protocols implementation, ignoring internationalization makes it difficult for data to be produced and consumed across a disparate set of languages and societies, which limits the applicability of the specification and significantly diminishes its value as a standard.
Implementers are strongly advised to read the Strings on the Web: Language and Direction Metadata document [ STRING-META ], published by the W3C Internationalization Activity, which elaborates on the need to provide reliable metadata about text to support internationalization. For the latest information on internationalization considerations, implementers are also urged to read the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
This section outlines general internationalization considerations to take into account when utilizing this data model and is intended to highlight specific parts of the Strings on the Web: Language and Direction Metadata document [ STRING-META ] that implementers might be interested in reading.
10.1 Language and Base Direction
Data publishers are strongly encouraged to read the section on Cross-Syntax Expression in the Strings on the Web: Language and Direction Metadata document [ STRING-META ] to ensure that the expression of language and base direction information is possible across multiple expression syntaxes, such as [ JSON-LD ], [ JSON ], and CBOR [ RFC7049 ].
The general design pattern is to use the following markup template when expressing a text string that is tagged with a language and, optionally, a specific base direction.
Using the design pattern above, the following example expresses the title of a book in the English language without specifying a text direction.
The next example uses a similar title expressed in the Arabic language with a base direction of right-to-left.
The text above would most likely be rendered incorrectly as left-to-right without the explicit expression of language and direction because many systems use the first character of a text string to determine text direction.
Implementers utilizing JSON-LD are strongly urged to extend the JSON-LD Context defining the internationalized property and use the Scoped Context feature of JSON-LD to alias the @value , @language , and @direction keywords to value , lang , and dir , respectively. An example of a JSON-LD Context snippet doing this is shown below.
10.2 Complex Language Markup
When multiple languages, base directions, and annotations are used in a single natural language string, more complex mechanisms are typically required. It is possible to use markup languages, such as HTML, to encode text with multiple languages and base directions. It is also possible to use the rdf:HTML datatype to encode such values accurately in JSON-LD.
Despite the ability to encode information as HTML, implementers are strongly discouraged from doing this because it:
- Requires some version of an HTML processor, which increases the burden of processing language and base direction information.
- Increases the security attack surface when utilizing this data model because blindly processing HTML could result in executing a script tag that an attacker injected at some point during the data production process.
If implementers feel they must use HTML, or other markup languages capable of containing executable scripts, to address a specific use case, they are advised to analyze how an attacker would use the markup to mount injection attacks against a consumer of the markup and then deploy mitigations against the identified attacks.
A. Validation
While this specification does not provide conformance criteria for the process of the validation of verifiable credentials or verifiable presentations , readers might be curious about how the information in this data model is expected to be utilized by verifiers during the process of validation . This section captures a selection of conversations held by the Working Group related to the expected usage of the data fields in this specification by verifiers .
A.1 Credential Subject
In the verifiable credentials presented by a holder , the value associated with the id property for each credentialSubject is expected to identify a subject to the verifier . If the holder is also the subject , then the verifier could authenticate the holder if they have public key metadata related to the holder . The verifier could then authenticate the holder using a signature generated by the holder contained in the verifiable presentation . The id property is optional. Verifiers could use other properties in a verifiable credential to uniquely identify a subject .
For information on how authentication and WebAuthn might work with verifiable credentials , see the Verifiable Credentials Implementation Guidelines [ VC-IMP-GUIDE ] document.
The value associated with the issuer property is expected to identify an issuer that is known to and trusted by the verifier .
Relevant metadata about the issuer property is expected to be available to the verifier . For example, an issuer can publish information containing the public keys it uses to digitally sign verifiable credentials that it issued. This metadata is relevant when checking the proofs on the verifiable credentials .
A.3 Issuance Date
The issuanceDate is expected to be within an expected range for the verifier . For example, a verifier can check that the issuance date of a verifiable credential is not in the future.
A.4 Proofs (Signatures)
The cryptographic mechanism used to prove that the information in a verifiable credential or verifiable presentation was not tampered with is called a proof . There are many types of cryptographic proofs including, but not limited to, digital signatures, zero-knowledge proofs, Proofs of Work, and Proofs of Stake. In general, when verifying proofs, implementations are expected to ensure:
- The proof is available in the form of a known proof suite.
- All required proof suite properties are present.
- The proof suite verification algorithm, when applied to the data, results in an acceptable proof.
Some proofs are digital signatures. In general, when verifying digital signatures, implementations are expected to ensure:
- Acceptably recent metadata regarding the public key associated with the signature is available. For example, the metadata might include properties related to expiration, key owner, or key purpose.
- The key is not suspended, revoked, or expired.
- The cryptographic signature is expected to verify.
- If the cryptographic suite expects a proofPurpose property , it is expected to exist and be a valid value, such as assertionMethod .
The digital signature provides a number of protections, other than tamper resistance, which are not immediately obvious. For example, a Linked Data Signature created property establishes a date and time before which the credential should not be considered verified . The verificationMethod property specifies, for example, the public key that can be used to verify the digital signature. Dereferencing a public key URL reveals information about the controller of the key, which can be checked against the issuer of the credential . The proofPurpose property clearly expresses the purpose for the proof and ensures this information is protected by the signature. A proof is typically attached to a verifiable presentation for authentication purposes and to a verifiable credential as a method of assertion.
A.5 Expiration
The expirationDate is expected to be within an expected range for the verifier . For example, a verifier can check that the expiration date of a verifiable credential is not in the past.
If the credentialStatus property is available, the status of a verifiable credential is expected to be evaluated by the verifier according to the credentialStatus type definition for the verifiable credential and the verifier's own status evaluation criteria. For example, a verifier can ensure the status of the verifiable credential is not "withdrawn for cause by the issuer ".
A.7 Fitness for Purpose
Fitness for purpose is about whether the custom properties in the verifiable credential are appropriate for the verifier's purpose. For example, if a verifier needs to determine whether a subject is older than 21 years of age, they might rely on a specific birthdate property , or on more abstract properties , such as ageOver .
The issuer is trusted by the verifier to make the claims at hand. For example, a franchised fast food restaurant location trusts the discount coupon claims made by the corporate headquarters of the franchise. Policy information expressed by the issuer in the verifiable credential should be respected by holders and verifiers unless they accept the liability of ignoring the policy.
B. Contexts, Types, and Credential Schemas
B.1 base context.
The base context, located at https://www.w3.org/2018/credentials/v1 with a SHA-256 digest of ab4ddd9a531758807a79a5b450510d61ae8d147eab966cc9a200c07095b0cdcc , can be used to implement a local cached copy. For convenience, the base context is also provided in this section.
B.2 Differences between Contexts, Types, and CredentialSchemas
The verifiable credential and verifiable presentation data models leverage a variety of underlying technologies including [ JSON-LD ] and [ JSON-SCHEMA-2018 ]. This section will provide a comparison of the @context , type , and credentialSchema properties, and cover some of the more specific use cases where it is possible to use these features of the data model.
The type property is used to uniquely identify the type of the verifiable credential in which it appears, i.e., to indicate which set of claims the verifiable credential contains. This property, and the value VerifiableCredential within the set of its values, are mandatory. Whilst it is good practice to include one additional value depicting the unique subtype of this verifiable credential , it is permitted to either omit or include additional type values in the array. Many verifiers will request a verifiable credential of a specific subtype, then omitting the subtype value could make it more difficult for verifiers to inform the holder which verifiable credential they require. When a verifiable credential has multiple subtypes, listing all of them in the type property is sensible. While the semantics are the same in both a [ JSON ] and [ JSON-LD ] representation, the usage of the type property in a [ JSON-LD ] representation of a verifiable credential is able to enforce the semantics of the verifiable credential better than a [ JSON ] representation of the same credential because the machine is able to check the semantics. With [ JSON-LD ], the technology is not only describing the categorization of the set of claims, the technology is also conveying the structure and semantics of the sub-graph of the properties in the graph. In [ JSON-LD ], this represents the type of the node in the graph which is why some [ JSON-LD ] representations of a verifiable credential will use the type property on many objects in the verifiable credential .
The primary purpose of the @context property, from a [ JSON-LD ] perspective, is to convey the meaning of the data and term definitions of the data in a verifiable credential , in a machine readable way. When encoding a pure [ JSON ] representation, the @context property remains mandatory and provides some basic support for global semantics. The @context property is used to map the globally unique URIs for properties in verifiable credentials and verifiable presentations into short-form alias names, making both the [ JSON ] and [ JSON-LD ] representations more human-friendly to read. From a [ JSON-LD ] perspective, this mapping also allows the data in a credential to be modeled in a network of machine-readable data, by enhancing how the data in the verifiable credential or verifiable presentation relates to a larger machine-readable data graph. This is useful for telling machines how to relate the meaning of data to other data in an ecosystem where parties are unable to coordinate. This property, with the first value in the set being https://www.w3.org/2018/credentials/v1 , is mandatory.
Since the @context property is used to map data to a graph data model, and the type property in [ JSON-LD ] is used to describe nodes within the graph, the type property becomes even more important when using the two properties in combination. For example, if the type property is not included within the resolved @context resource using [ JSON-LD ], it could lead to claims being dropped and/or their integrity no longer being protected during production and consumption of the verifiable credential . Alternatively, it could lead to errors being raised during production or consumption of a verifiable credential . This will depend on the design choices of the implementation and both paths are used in implementations today, so it's important to pay attention to these properties when using a [ JSON-LD ] representation of a verifiable credential or verifiable presentation .
The primary purpose of the credentialSchema property is to define the structure of the verifiable credential , and the datatypes for the values of each property that appears. A credentialSchema is useful for defining the contents and structure of a set of claims in a verifiable credential , whereas [ JSON-LD ] and a @context in a verifiable credential are best used only for conveying the semantics and term definitions of the data, and can be used to define the structure of the verifiable credential as well.
While it is possible to use some [ JSON-LD ] features to allude to the contents of the verifiable credential , it's not generally suggested to use @context to constrain the data types of the data model. For example, "@type": "@json" is useful for leaving the semantics open-ended and not strictly defined. This can be dangerous if the implementer is looking to constrain the data type of the claims in the credential , and is expected not to be used.
When the credentialSchema and @context properties are used in combination, both producers and consumers can be more confident about the expected contents and data types of the verifiable credential and verifiable presentation .
C. Subject-Holder Relationships
This section describes possible relationships between a subject and a holder and how the Verifiable Credentials Data Model expresses these relationships. The following diagram illustrates these relationships, with the subsequent sections describing how each of these relationships are handled in the data model.
C.1 Subject is the Holder
The most common relationship is when a subject is the holder . In this case, a verifier can easily deduce that a subject is the holder if the verifiable presentation is digitally signed by the holder and all contained verifiable credentials are about a subject that can be identified to be the same as the holder .
If only the credentialSubject is allowed to insert a verifiable credential into a verifiable presentation , the issuer can insert the nonTransferable property into the verifiable credential , as described below.
C.1.1 nonTransferable Property
The nonTransferable property indicates that a verifiable credential must only be encapsulated into a verifiable presentation whose proof was issued by the credentialSubject . A verifiable presentation that contains a verifiable credential containing the nonTransferable property , whose proof creator is not the credentialSubject , is invalid.
C.2 Credential Uniquely Identifies a Subject
In this case, the credentialSubject property might contain multiple properties , each providing an aspect of a description of the subject , which combine together to unambiguously identify the subject . Some use cases might not require the holder to be identified at all, such as checking to see if a doctor (the subject ) is board-certified. Other use cases might require the verifier to use out-of-band knowledge to determine the relationship between the subject and the holder .
The example above uniquely identifies the subject using the name, address, and birthdate of the individual.
C.3 Subject Passes the Verifiable Credential to a Holder
Usually verifiable credentials are presented to verifiers by the subject . However, in some cases, the subject might need to pass the whole or part of a verifiable credential to another holder . For example, if a patient (the subject ) is too ill to take a prescription (the verifiable credential ) to the pharmacist (the verifier ), a friend might take the prescription in to pick up the medication.
The data model allows for this by letting the subject issue a new verifiable credential and give it to the new holder , who can then present both verifiable credentials to the verifier . However, the content of this second verifiable credential is likely to be application-specific, so this specification cannot standardize the contents of this second verifiable credential . Nevertheless, a non-normative example is provided in Appendix C.5 Subject Passes a Verifiable Credential to Someone Else .
C.4 Holder Acts on Behalf of the Subject
The Verifiable Credentials Data Model supports the holder acting on behalf of the subject in at least the following ways. The:
- Issuer can include the relationship between the holder and the subject in the credentialSubject property .
- Issuer can express the relationship between the holder and the subject by issuing a new verifiable credential , which the holder utilizes.
- Subject can express their relationship with the holder by issuing a new verifiable credential , which the holder utilizes.
The mechanisms listed above describe the relationship between the holder and the subject and helps the verifier decide whether the relationship is sufficiently expressed for a given use case.
The additional mechanisms the issuer or the verifier uses to verify the relationship between the subject and the holder are outside the scope of this specification.
In the example above, the issuer expresses the relationship between the child and the parent such that a verifier would most likely accept the credential if it is provided by the child or the parent.
In the example above, the issuer expresses the relationship between the child and the parent in a separate credential such that a verifier would most likely accept any of the child's credentials if they are provided by the child or if the credential above is provided with any of the child's credentials .
In the example above, the child expresses the relationship between the child and the parent in a separate credential such that a verifier would most likely accept any of the child's credentials if the credential above is provided.
Similarly, the strategies described in the examples above can be used for many other types of use cases, including power of attorney, pet ownership, and patient prescription pickup.
C.5 Subject Passes a Verifiable Credential to Someone Else
When a subject passes a verifiable credential to another holder , the subject might issue a new verifiable credential to the holder in which the:
- Issuer is the subject .
- Subject is the holder to whom the verifiable credential is being passed.
- Claim contains the properties being passed on.
The holder can now create a verifiable presentation containing these two verifiable credentials so that the verifier can verify that the subject gave the original verifiable credential to the holder .
In the above example, a patient (the original subject ) passed a prescription (the original verifiable credential ) to a friend, and issued a new verifiable credential to the friend, in which the friend is the subject , the subject of the original verifiable credential is the issuer , and the credential is a copy of the original prescription.
C.6 Issuer Authorizes Holder
When an issuer wants to authorize a holder to possess a credential that describes a subject who is not the holder , and the holder has no known relationship with the subject , then the issuer might insert the relationship of the holder to itself into the subject's credential .
Verifiable credentials are not an authorization framework and therefore delegation is outside the scope of this specification. However, it is understood that verifiable credentials are likely to be used to build authorization and delegation systems. The following is one approach that might be appropriate for some use cases.
C.7 Holder Acts on Behalf of the Verifier, or has no Relationship with the Subject, Issuer, or Verifier
The Verifiable Credentials Data Model currently does not support either of these scenarios. It is for further study how they might be supported.
D. IANA Considerations
This section will be submitted to the Internet Engineering Steering Group (IESG) for review, approval, and registration with IANA in the "JSON Web Token Claims Registry".
- Claim Name: "vc"
- Claim Description: Verifiable Credential
- Change Controller: W3C
- Specification Document(s): Section 6.3.1.2: JSON Web Token Extensions of Verifiable Credentials Data Model 1.0
- Claim Name: "vp"
- Claim Description: Verifiable Presentation
E. Revision History
This section contains the substantive changes that have been made since the publication of v1.0 of this specification as a W3C Recommendation.
Changes since the Recommendation :
- Add this revision history section.
- Update previous normative references that pointed to RFC3339 for datetime details to now normatively reference the datetime details described in XMLSCHEMA11-2 which more accurately reflects the usage in examples and libraries.
- Loosen the requirement to use URLs to use URIs in the id property of the credentialStatus and refreshService sections of the data model.
- Loosen normative statements in the zero-knowledge proofs section to enable compliance of new zero-knowledge proof schemes, such as BBS+, that have been created since the v1.0 specification was published as a Recommendation.
- Update all references to point to the latest version of the referenced specifications. Fix broken links to papers that have become unavailable to updated locations where the papers are available.
- Increase accessibility of SVG diagrams.
- Fix editorial bugs in a few examples related to issuer , issuanceDate , credentialStatus , dates, dead links, and minor syntax errors.
- Move acknowledgements from Status of the Document section into the Acknowledgements appendix.
F. Acknowledgements
The Working Group thanks the following individuals not only for their contributions toward the content of this document, but also for yeoman's work in this standards community that drove changes, discussion, and consensus among a sea of varied opinions: Matt Stone, Gregg Kellogg, Ted Thibodeau Jr, Oliver Terbu, Joe Andrieu, David I. Lehn, Matthew Collier, and Adrian Gropper.
Work on this specification has been supported by the Rebooting the Web of Trust community facilitated by Christopher Allen, Shannon Appelcline, Kiara Robles, Brian Weller, Betty Dhamers, Kaliya Young, Manu Sporny, Drummond Reed, Joe Andrieu, Heather Vescent, Kim Hamilton Duffy, Samantha Chase, and Andrew Hughes. The participants in the Internet Identity Workshop, facilitated by Phil Windley, Kaliya Young, Doc Searls, and Heidi Nobantu Saul, also supported the refinement of this work through numerous working sessions designed to educate about, debate on, and improve this specification.
The Working Group also thanks our Chairs, Dan Burnett, Matt Stone, Brent Zundel, and Wayne Chang, as well as our W3C Staff Contacts, Kazuyuki Ashimura and Ivan Herman, for their expert management and steady guidance of the group through the W3C standardization process.
Portions of the work on this specification have been funded by the United States Department of Homeland Security's Science and Technology Directorate under contract HSHQDC-17-C-00019. The content of this specification does not necessarily reflect the position or the policy of the U.S. Government and no official endorsement should be inferred.
The Working Group would like to thank the following individuals for reviewing and providing feedback on the specification (in alphabetical order):
Christopher Allen, David Ammouial, Joe Andrieu, Bohdan Andriyiv, Ganesh Annan, Kazuyuki Ashimura, Tim Bouma, Pelle Braendgaard, Dan Brickley, Allen Brown, Jeff Burdges, Daniel Burnett, ckennedy422, David Chadwick, Chaoxinhu, Kim (Hamilton) Duffy, Lautaro Dragan, enuoCM, Ken Ebert, Eric Elliott, William Entriken, David Ezell, Nathan George, Reto Gmür, Ryan Grant, glauserr, Adrian Gropper, Joel Gustafson, Amy Guy, Lovesh Harchandani, Daniel Hardman, Dominique Hazael-Massieux, Jonathan Holt, David Hyland-Wood, Iso5786, Renato Iannella, Richard Ishida, Ian Jacobs, Anil John, Tom Jones, Rieks Joosten, Gregg Kellogg, Kevin, Eric Korb, David I. Lehn, Michael Lodder, Dave Longley, Christian Lundkvist, Jim Masloski, Pat McBennett, Adam C. Migus, Liam Missin, Alexander Mühle, Anthony Nadalin, Clare Nelson, Mircea Nistor, Grant Noble, Darrell O'Donnell, Nate Otto, Matt Peterson, Addison Phillips, Eric Prud'hommeaux, Liam Quin, Rajesh Rathnam, Drummond Reed, Yancy Ribbens, Justin Richer, Evstifeev Roman, RorschachRev, Steven Rowat, Pete Rowley, Markus Sabadello, Kristijan Sedlak, Tzviya Seigman, Reza Soltani, Manu Sporny, Orie Steele, Matt Stone, Oliver Terbu, Ted Thibodeau Jr, John Tibbetts, Mike Varley, Richard Varn, Heather Vescent, Christopher Lemmer Webber, Benjamin Young, Kaliya Young, Dmitri Zagidulin, and Brent Zundel.
G. References
G.1 normative references, g.2 informative references.
Referenced in:
- § 1.4 Conformance (2)
- § 1.1 What is a Verifiable Credential?
- § 1.2 Ecosystem Overview (2) (3)
- § 1.3 Use Cases and Requirements (2)
- § 2. Terminology (2) (3) (4) (5) (6)
- § 3. Core Data Model
- § 3.1 Claims (2) (3) (4) (5) (6) (7) (8) (9)
- § 3.2 Credentials (2) (3) (4) (5) (6) (7)
- § 3.4 Concrete Lifecycle Example
- § 4.2 Identifiers
- § 4.4 Credential Subject (2)
- § 4.10.1 Presentations Using Derived Credentials (2) (3) (4) (5) (6) (7)
- § 5.8 Zero-Knowledge Proofs (2)
- § 6.3.1 JSON Web Token (2)
- § Relation to the Verifiable Credentials Data Model (2)
- § JSON Web Token Extensions
- § JWT Encoding (2) (3) (4)
- § JWT Decoding (2) (3)
- § 7.7 Favor Abstract Claims
- § 8.5 Bundling Dependent Claims
- § A.7 Fitness for Purpose (2)
- § C.5 Subject Passes a Verifiable Credential to Someone Else
- § Abstract (2)
- § 1. Introduction (2) (3) (4) (5)
- § 1.1 What is a Verifiable Credential? (2) (3) (4) (5) (6) (7) (8)
- § 1.3 Use Cases and Requirements (2) (3) (4)
- § 2. Terminology (2) (3)
- § 3.2 Credentials (2) (3) (4) (5) (6) (7) (8) (9) (10)
- § 3.3 Presentations
- § 4.3 Types (2) (3) (4) (5)
- § 4.5 Issuer
- § 4.6 Issuance Date (2) (3)
- § 4.7 Proofs (Signatures) (2)
- § 4.8 Expiration (2)
- § 4.9 Status (2) (3) (4) (5)
- § 4.10 Presentations
- § 5.1 Lifecycle Details
- § 5.2 Trust Model (2) (3) (4) (5)
- § 5.3 Extensibility
- § 5.3.1 Semantic Interoperability (2)
- § 5.4 Data Schemas (2)
- § 5.5 Refreshing (2) (3)
- § 5.6 Terms of Use
- § 5.7 Evidence (2) (3) (4) (5)
- § 5.8 Zero-Knowledge Proofs (2) (3)
- § 5.9 Disputes (2) (3) (4) (5) (6) (7) (8) (9) (10)
- § 6.3 Proof Formats
- § JWT Encoding
- § JWT Decoding (2) (3) (4)
- § 7.3 Identifier-Based Correlation
- § 7.7 Favor Abstract Claims (2)
- § 7.8 The Principle of Data Minimization
- § 7.10 Validity Checks (2) (3) (4)
- § 7.11 Storage Providers and Data Mining (2) (3)
- § 7.12 Aggregation of Credentials
- § 7.13 Usage Patterns (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14) (15) (16) (17)
- § 7.14 Sharing Information with the Wrong Party
- § 7.15 Frequency of Claim Issuance (2)
- § 7.17 Private Browsing (2)
- § 7.18 Issuer Cooperation Impacts on Privacy (2)
- § 8.1 Cryptography Suites and Libraries (2) (3)
- § 8.3 Unsigned Claims (2) (3)
- § 8.5 Bundling Dependent Claims (2) (3) (4)
- § 8.7 Device Theft and Impersonation
- § 9.1 Data First Approaches (2) (3)
- § A.4 Proofs (Signatures) (2)
- § B.2 Differences between Contexts, Types, and CredentialSchemas (2)
- § C.4 Holder Acts on Behalf of the Subject (2) (3) (4) (5) (6) (7) (8)
- § C.6 Issuer Authorizes Holder (2)
- § 1. Introduction (2) (3)
- § 1.1 What is a Verifiable Credential? (2) (3) (4) (5) (6)
- § 1.2 Ecosystem Overview (2) (3) (4) (5) (6) (7) (8) (9) (10) (11)
- § 1.3 Use Cases and Requirements (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14) (15) (16) (17) (18) (19) (20)
- § 1.4 Conformance (2) (3) (4)
- § 2. Terminology (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14) (15) (16) (17) (18) (19) (20) (21) (22)
- § 3.2 Credentials (2) (3) (4) (5) (6)
- § 3.3 Presentations (2) (3) (4) (5) (6)
- § 3.4 Concrete Lifecycle Example (2) (3) (4) (5) (6) (7) (8) (9)
- § 4.1 Contexts (2) (3) (4) (5)
- § 4.2 Identifiers (2) (3) (4) (5) (6) (7) (8)
- § 4.3 Types (2) (3) (4) (5) (6)
- § 4.4 Credential Subject (2) (3) (4)
- § 4.5 Issuer (2)
- § 4.9 Status (2)
- § 4.10 Presentations (2) (3) (4) (5)
- § 4.10.1 Presentations Using Derived Credentials (2) (3) (4) (5)
- § 5. Advanced Concepts
- § 5.1 Lifecycle Details (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14) (15) (16)
- § 5.2 Trust Model (2) (3) (4)
- § 5.3 Extensibility (2) (3) (4) (5) (6) (7)
- § 5.4 Data Schemas (2) (3) (4) (5) (6)
- § 5.5 Refreshing (2) (3) (4) (5) (6) (7) (8) (9)
- § 5.6 Terms of Use (2) (3) (4) (5) (6) (7) (8) (9)
- § 5.7 Evidence (2) (3) (4)
- § 5.8 Zero-Knowledge Proofs (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14) (15) (16) (17) (18) (19) (20) (21) (22) (23) (24) (25)
- § 5.9 Disputes (2)
- § 5.10 Authorization
- § 6. Syntaxes
- § 6.2 JSON-LD
- § 6.2.1 Syntactic Sugar (2) (3)
- § Relation to the Verifiable Credentials Data Model
- § JSON Web Token Extensions (2)
- § JWT Encoding (2) (3) (4) (5) (6) (7) (8)
- § JWT Decoding (2)
- § 6.3.2 Data Integrity Proofs (2)
- § 7.2 Personally Identifiable Information (2) (3) (4) (5) (6) (7)
- § 7.3 Identifier-Based Correlation (2) (3) (4)
- § 7.4 Signature-Based Correlation (2)
- § 7.5 Long-Lived Identifier-Based Correlation (2) (3)
- § 7.6 Device Fingerprinting (2) (3) (4) (5)
- § 7.7 Favor Abstract Claims (2) (3)
- § 7.8 The Principle of Data Minimization (2) (3) (4) (5) (6) (7) (8)
- § 7.9 Bearer Credentials (2)
- § 7.10 Validity Checks
- § 7.11 Storage Providers and Data Mining (2) (3) (4) (5) (6) (7)
- § 7.13 Usage Patterns (2) (3) (4) (5)
- § 7.14 Sharing Information with the Wrong Party (2)
- § 7.15 Frequency of Claim Issuance (2) (3) (4)
- § 7.16 Prefer Single-Use Credentials (2) (3) (4) (5) (6)
- § 7.18 Issuer Cooperation Impacts on Privacy (2) (3) (4)
- § 8.2 Content Integrity Protection (2) (3) (4)
- § 8.5 Bundling Dependent Claims (2) (3)
- § 8.6 Highly Dynamic Information (2) (3) (4) (5)
- § 8.7 Device Theft and Impersonation (2)
- § 9.1 Data First Approaches
- § A. Validation
- § A.1 Credential Subject (2) (3)
- § A.2 Issuer (2)
- § A.3 Issuance Date
- § A.5 Expiration
- § A.6 Status (2) (3)
- § B.2 Differences between Contexts, Types, and CredentialSchemas (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14) (15) (16) (17) (18) (19) (20) (21) (22) (23)
- § C.1 Subject is the Holder (2) (3)
- § C.1.1 nonTransferable Property (2)
- § C.3 Subject Passes the Verifiable Credential to a Holder (2) (3) (4) (5) (6) (7)
- § C.4 Holder Acts on Behalf of the Subject (2)
- § C.5 Subject Passes a Verifiable Credential to Someone Else (2) (3) (4) (5) (6) (7) (8)
- § 2. Terminology
- § 1.2 Ecosystem Overview (2) (3) (4)
- § 2. Terminology (2) (5) (6)
- § 3.2 Credentials (2)
- § 3.3 Presentations (2)
- § 5.2 Trust Model (2)
- § 5.9 Disputes (2) (3)
- § 7.2 Personally Identifiable Information (2)
- § 3.1 Claims (2)
- § 3.2 Credentials (2) (3) (4)
- § 3.3 Presentations (2) (3) (4) (5) (6) (7) (8) (9) (10) (11)
- § 1.2 Ecosystem Overview (2) (3) (4) (5)
- § 1.3 Use Cases and Requirements (2) (3) (4) (5) (6) (7) (8) (9) (10)
- § 1.4 Conformance
- § 3.2 Credentials
- § 4.10.1 Presentations Using Derived Credentials (2)
- § 5.1 Lifecycle Details (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13)
- § 5.2 Trust Model (2) (3)
- § 5.5 Refreshing (2) (3) (4) (5) (6) (7)
- § 5.6 Terms of Use (2) (3) (4) (5) (6) (7) (8)
- § 5.8 Zero-Knowledge Proofs (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14)
- § 6.2.1 Syntactic Sugar
- § JWT Encoding (2)
- § 7.2 Personally Identifiable Information
- § 7.3 Identifier-Based Correlation (2) (3)
- § 7.5 Long-Lived Identifier-Based Correlation (2)
- § 7.6 Device Fingerprinting
- § 7.9 Bearer Credentials (2) (3) (4) (5) (6)
- § 7.10 Validity Checks (2) (3) (4) (5) (6) (7)
- § 7.12 Aggregation of Credentials (2) (3)
- § 7.13 Usage Patterns (2) (3) (4)
- § 7.14 Sharing Information with the Wrong Party (2) (3) (4) (5) (6) (7)
- § 7.16 Prefer Single-Use Credentials (2)
- § 7.17 Private Browsing
- § 8. Security Considerations
- § 8.5 Bundling Dependent Claims (2)
- § 8.6 Highly Dynamic Information
- § A.1 Credential Subject (2) (3) (4) (5) (6)
- § A.7 Fitness for Purpose
- § C. Subject-Holder Relationships
- § C.1 Subject is the Holder (2) (3) (4)
- § C.2 Credential Uniquely Identifies a Subject (2)
- § C.3 Subject Passes the Verifiable Credential to a Holder (2)
- § C.5 Subject Passes a Verifiable Credential to Someone Else (2) (3) (4) (5)
- § C.6 Issuer Authorizes Holder (2) (3) (4)
- § 5.2 Trust Model
- § 1.2 Ecosystem Overview
- § 2. Terminology (2) (3) (4)
- § 5.1 Lifecycle Details (2) (3) (4)
- § 5.2 Trust Model (2) (3) (4) (5) (6) (7)
- § 5.4 Data Schemas (2) (3)
- § 5.5 Refreshing (2) (3) (4) (5)
- § 5.6 Terms of Use (2) (3) (4)
- § 5.8 Zero-Knowledge Proofs (2) (3) (4) (5)
- § 5.9 Disputes (2) (3) (4)
- § 7.3 Identifier-Based Correlation (2)
- § 7.8 The Principle of Data Minimization (2) (3) (4) (5) (6)
- § 7.9 Bearer Credentials
- § 7.10 Validity Checks (2) (3)
- § 7.11 Storage Providers and Data Mining
- § 7.15 Frequency of Claim Issuance (2) (3) (4) (5)
- § 7.18 Issuer Cooperation Impacts on Privacy (2) (3) (4) (5) (6) (7) (8)
- § A.6 Status
- § C.1 Subject is the Holder
- § C.4 Holder Acts on Behalf of the Subject (2) (3) (4) (5)
- § C.5 Subject Passes a Verifiable Credential to Someone Else (2)
- § 4.3 Types (2)
- § 4.10 Presentations (2) (3) (4) (5) (6)
- § 5.6 Terms of Use (2)
- § 5.8 Zero-Knowledge Proofs
- § 7.13 Usage Patterns
- § 7.18 Issuer Cooperation Impacts on Privacy
- § 8.1 Cryptography Suites and Libraries
- § 1. Introduction (2)
- § 1.1 What is a Verifiable Credential? (2) (3) (4)
- § 1.2 Ecosystem Overview (2)
- § 2. Terminology (2) (3) (4) (5) (6) (7)
- § 3.3 Presentations (2) (3) (4) (5) (6) (7) (8)
- § 3.4 Concrete Lifecycle Example (2) (3) (4) (5)
- § 4.1 Contexts (2) (3)
- § 4.7 Proofs (Signatures)
- § 4.10 Presentations (2) (3) (4)
- § 5.5 Refreshing (2)
- § 5.6 Terms of Use (2) (3) (4) (5)
- § 5.8 Zero-Knowledge Proofs (2) (3) (4) (5) (6) (7) (8) (9) (10)
- § JWT Decoding
- § 8.4 Token Binding (2)
- § A.1 Credential Subject
- § B.2 Differences between Contexts, Types, and CredentialSchemas (2) (3) (4) (5)
- § C.1 Subject is the Holder (2)
- § 7.8 The Principle of Data Minimization (2)
- § 1.1 What is a Verifiable Credential? (2)
- § 2. Terminology (2) (3) (4) (5) (6) (7) (8) (9) (10) (11)
- § 3.1 Claims (2) (3)
- § 4.2 Identifiers (2)
- § 4.3 Types
- § 4.4 Credential Subject (2) (3) (4) (5) (6)
- § 4.10 Presentations (2)
- § 4.10.1 Presentations Using Derived Credentials (2) (3) (4)
- § 5.1 Lifecycle Details (2)
- § 5.7 Evidence (2)
- § 5.10 Authorization (2)
- § 6.3.2 Data Integrity Proofs
- § 7.5 Long-Lived Identifier-Based Correlation
- § 7.12 Aggregation of Credentials (2)
- § 7.13 Usage Patterns (2) (3) (4) (5) (6)
- § C.2 Credential Uniquely Identifies a Subject (2) (3) (4) (5)
- § C.3 Subject Passes the Verifiable Credential to a Holder (2) (3) (4)
- § C.4 Holder Acts on Behalf of the Subject (2) (3) (4) (5) (6)
- § C.6 Issuer Authorizes Holder (2) (3)
- § 6. Syntaxes (2)
- § A. Validation (2)
- § 1. Introduction
- § 1.3 Use Cases and Requirements (2) (3) (4) (5) (6)
- § 2. Terminology (2)
- § 3.4 Concrete Lifecycle Example (2)
- § 4.10 Presentations (2) (3)
- § 4.10.1 Presentations Using Derived Credentials
- § 8.3 Unsigned Claims
- § 2. Terminology (3)
- § 3.4 Concrete Lifecycle Example (2) (3) (4)
- § 5.1 Lifecycle Details (2) (3) (4) (5) (6) (7)
- § 5.2 Trust Model (2) (3) (4) (5) (6)
- § 5.5 Refreshing (2) (3) (4) (5) (6)
- § 5.8 Zero-Knowledge Proofs (2) (3) (4) (5) (6) (7) (8)
- § 5.9 Disputes
- § 7.8 The Principle of Data Minimization (2) (3) (4)
- § 7.10 Validity Checks (2)
- § 7.13 Usage Patterns (2) (3) (4) (5) (6) (7) (8) (9) (10)
- § 7.14 Sharing Information with the Wrong Party (2) (3) (4) (5) (6)
- § 7.16 Prefer Single-Use Credentials (2) (3)
- § 8.4 Token Binding
- § A.1 Credential Subject (2) (3) (4)
- § A.3 Issuance Date (2)
- § A.5 Expiration (2)
- § A.7 Fitness for Purpose (2) (3) (4)
- § C.2 Credential Uniquely Identifies a Subject
- § C.3 Subject Passes the Verifiable Credential to a Holder (2) (3)
- § 4.1 Contexts (2) (3) (4) (5) (6) (7) (8) (9) (10)
- § 4.2 Identifiers (2) (3)
- § 4.3 Types (2) (3) (4)
- § 4.9 Status
- § 5.4 Data Schemas
- § 5.5 Refreshing
- § E. Revision History
- § 4.1 Contexts (2) (3) (4) (5) (6) (7) (8)
- § 4.2 Identifiers (2) (3) (4) (5) (6) (7) (8) (9)
- § 4.4 Credential Subject (2) (3)
- § 4.5 Issuer (2) (3) (4)
- § 4.6 Issuance Date (2) (3) (4) (5) (6) (7) (8)
- § 4.7 Proofs (Signatures) (2) (3) (4)
- § 4.8 Expiration (2) (3) (4) (5)
- § 4.9 Status (2) (3) (4)
- § 4.10 Presentations (2) (3) (4) (5) (6) (7)
- § 5.5 Refreshing (2) (3) (4)
- § 5.6 Terms of Use (2) (3)
- § 5.7 Evidence (2) (3) (4) (5) (6) (7) (8)
- § 5.8 Zero-Knowledge Proofs (2) (3) (4)
- § 6. Syntaxes (2) (3) (4)
- § JWT Encoding (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12)
- § JWT Decoding (2) (3) (4) (5) (6) (7) (8) (9)
- § 7.4 Signature-Based Correlation
- § 10.1 Language and Base Direction (2)
- § A.4 Proofs (Signatures) (2) (3) (4) (5) (6)
- § A.7 Fitness for Purpose (2) (3)
- § C.4 Holder Acts on Behalf of the Subject
- § 4.3 Types (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12) (13) (14) (15)
- § 7.9 Bearer Credentials (2) (3) (4) (5) (6) (7) (8) (9) (10) (11)
Skip to content

What Are Credentials? Types and Examples (For Resumes)
Adding credentials to your resume will make your application stand out when looking for a job or planning a career change. Credentials connect professionals to credible organisations and provide a verifiable way to ensure employees have the proper knowledge to perform a job.
But what exactly can be considered a credential?
Credentials are any certificate, diploma or licence you may have received throughout your career. They indicate your abilities to perform specific tasks, are proof of your academic achievements or certify your authority when training others, for example. They are issued by an organisation with the competence to attest to your qualifications.
For certain jobs, presenting the correct credentials is more than ideal; they might be indispensable.
This article will explain the most common types of credentials and indicate how and when you should add them to your resume, LinkedIn profile or job application.
Credentials you should include in your resume
Since credentials can cover an array of documents and certificates – including driving licenses, for example – it is essential to assess which information you need to add to your resume and what is unnecessary.
Essentially, there are four types of credentials you should always list on your CV. They will provide recruiters with a better understanding of your academic achievements, training and abilities.
However, before you add every course certificate you ever took or every document you ever received, why not consider your professional goals first? Being aware of how you want to grow is the first step in deciding what you should portray. Your resume is nothing more than an advertisement for yourself, so make sure you know what you want to sell.
From that, you can decide which information you give peers and recruiters the tools to paint a picture of who you are.
Degrees or diplomas are the most common type of credential you’ll find in resumes. In many cases, a university degree is required to take on a particular job. This is undoubtedly the case for physicians, engineers and lawyers, but it is not uncommon for recruiters to indicate what kind of diploma they are looking for.
Including your diploma as one of your credentials in your resume will indicate your interests and background, an excellent introduction to your professional aspirations.
If you have continued your higher education with a post-graduate degree or a PhD, make sure you include them in your CV. This sort of credential is valued in the job market, showing you have the discipline and dedication most companies will be looking for.
Licences are more specific than a diploma but equally or even more critical. Some careers require professionals to own a license to perform particular tasks, especially if these tasks present risks to you or others.
Licences are the perfect example of a credential that should be part of a resume with a very specific goal. For instance, there is no need to list your driver’s license in your resume if you are not applying for a position as a driver. If you are looking for a career change, you don’t necessarily have to list the licences that helped you perform at your old job.
By the same token, if you are planning to completely transform your professional future, getting the necessary licences to perform that job – even before you get it – is essential. Take the courses and prepare yourself for what you want.
Certificates
Certificates are different from diplomas and degrees. While diplomas are received after a university course, certificates are achieved following a shorter course or training.
You can get certificates for participating in a summit, for studying a different language or for taking a free course on LinkedIn, for example. And they are all valuable. They will reveal your interest and are a great way of demonstrating your constant pursuit of professional development.
Just like with licences, it is recommended that you acquire the proper certificates before changing your career. Having the correct credentials on your resume will help you advance professionally.
Certifications
Certifications are different from certificates and licences. They demonstrate someone’s training and dedication to a more specific subject than a course. People might have certifications attesting to their ability to work with a software or tool, for example, an ability that will not necessarily be transferable to another area of expertise.
These certifications might appear in your resume or LinkedIn profile as a badge.
What are digital credentials?
Most often used on social media pages like LinkedIn, badges are an example of a digital credential. They can also be a representation of an association with a company or organisation that will attest to your expertise.
In an increasingly digital world, presenting certificates in a digital format can be easier, cheaper, and better for the environment. Companies like Diplomasafe ensure credentials issued by educational businesses and organisations are verifiable and credible, as demonstrated by our dashboard that helps manage and showcase these digital credentials effectively.
One of the benefits of having digital credentials is how easy it is to share them on multiple mediums. Badges and seals can quickly become a conversation starter, sending peers and recruiters straight to the source of your achievement.
If listing your credentials on your resume is extremely important, having them in the digital format displayed on social media pages or professional websites is just as relevant.
Digital credentials also provide recruiters and future employers with a trusted source of information about your certifications. They are easier to verify and create an increased sense of transparency in the hiring process.
Why are resume credentials so important?
As we’ve discussed, adding credentials to your resume improves your chances of getting noticed by recruiters. It is also an essential step towards a career change, especially if you are committed to improvement and seek the proper qualifications.
Resumes are, after all, a long list of credentials. Your CV should reflect what you have done professionally, but also everything you have achieved academically and intellectually. They are an opportunity for you to showcase your expertise. Therefore, you should boast about your credentials.
More importantly, having credentials – and relevant credentials – will help you get the proper attention, improve your chances of making more money, and develop your professional goals.
Digital credentials can be even more beneficial to your career goals, as they will connect you to credible organisations in a way that is easy to verify and confirm.
Credentials are essential pieces of information to add to any resume. They can indicate a variety of goals, interests and purposes, and they are relevant for employees, recruiters and companies.
Adding your credentials to your resume will improve your chances of getting hired and reveal your commitment to your craft. Having digital credentials available on your social media pages will also give recruiters an easy way to verify that you have the knowledge and expertise they are looking for.
It is a must to present credible credentials from institutions that are well-regarded in their area of expertise. In a digital environment, digital credentials are also a source of positive attention for professionals and for the businesses that issue them.
Related articles
ANS: Published by Lippincott, Williams & Wilkins
- ANS Blog Home
- ANS Web Site
- Editorial Manager
- Information for Authors
- ANS on Facebook
- ANS on Twitter
- Peggy Chinn’s Website & Blog
How to list your credentials and title when you publish
Updated resource (Sept. 12, 2019) APA “Misuse of the PhD(c) “

Here is a topic that is not often discussed, but remains a persistent issue for many! “What is the proper way to list my credentials? Which should come first, RN, PhD, MS?” Most folks have very strong opinions about this and will most certainly object if you list their credentials in an order other than what they prefer. They will typically give you very good reasons for why they feel one credential or another should be first. Therefore, as an Editor, my guideline for this is that each person’s credentials should be listed exactly as they prefer them to be listed!
However, there is one “credential” that is frequently indicated that we will not use — the non-credential “PhD(c).” I am not sure how this convention started, but it is one of my particular pet peeves. And in many formal and informal polls of other editors, by far the majority agree — this is not an acceptable credential. Yes, the little (c) does indicate that a person has passed
into “candidacy,” meaning that the person has completed all coursework requirements, and (in a U.S. system of doctoral education) the person now only has to complete the dissertation to be awarded the degree. This is also known as the “ABD” – “All But Dissertation!” Perhaps the trend to use the little (c) was an attempt to overcome this negative connotation.
There are many problems with using any designation to indicate candidacy as a credential. The foremost is that simply put, it is not a credential. It is simply an institutional right of passage. If a person surpasses the time limit to complete the dissertation, their journey in pursuit of an actual degree ends, and they are left with whatever other credentials they had when they entered the doctoral program.
Do not get me wrong here … we are delighted when an author has achieved this right of passage. You should acknowledge this, but in an acknowledgement, not as a credential. If you are a master’s or a doctoral student, or candidate, indicate your status in your acknowledgements and also include the name of the institution where you are enrolled. But do not include any initials like “PhD(c).” Another detail that I encourage you to consider — name your primary faculty advisor or advisors – the people who are giving you encouragement and guidance.
Do you have other opinions or questions about this issue? Leave a comment here! I am always delighted to hear from you!
Share this:
Recently someone challenged my position on the use of the PhD(c) designation, so I looked into the matter further. It is true that some Universities do sanction the use of this designation by those who have reached candidacy, but none that I found award this as a degree. A few do award a Candidate in Philosophy (C.Phil) designation, also referred to as an “intermediate degree” but this designation is only good for 7 years, which is the typical time period after which any “candidacy” expires. There is no indication that I can find that affirms the use of this designation as a title. If it is the practice of an institution to use the designation internally, then certainly a doctoral candidate is well advised to use it in that context. However, given that candidacy does expire, its use on a published work, which will survive the time frame of the designation, my policy not to use the designation in article published in ANS remains in place.
I agree that PhD(c) is not a credential and should not be used. I know someone who was a PhD(C) for 10 years, and only because her dean threatened her with firing did she finally write her dissertation and finish her PhD.
Also, candidacy typically expires after 7 to 10 years, at which time any designation involving this status would no longer be valid. Bottom line, there is no justification for using this, particularly in the context of publishing. Published works extend far into the future, and well beyond the time frame of candidacy!
I agree with Peggy. I am seeing this used quite a bit. In fact it is confusing to students. One person who uses PhDc even allows students to refer to her as Dr. I think this is devalues those who earned their PhD. But, most of all this is unethical.
I couldn’t agree more that this is a non-credential and its use needs to be halted immediately if not sooner. It makes us look foolish trying to inflate credentials to give the impression that one has achieved a status, ranking, or degree that has not yet been accomplished. We simply cannot legitimately fabricate credentials or titles at will or it all becomes meaningless. It is incumbent upon faculty to provide good direction to students in how to present themselves and their accomplishments. Perhaps it will stimulate more expedient completion of the degree and subsequent use of the legitimate title! Thank you for bringing much needed attention to this troublesome tradition in nursing.
Thank you so much for this feedback! I am not sure how to halt this practice, but I do hope that by brining attention to this matter more and more people will be discouraged from its use!
I concur. I’m a PhD student myself. I never really understood why people use the ABD designation anyway. I saw the PhD(c) for the first time today also, and stumbled across your page. I vociferously concur with your statements and reasons. I list my Masters in my credentials, but don’t list anything with my PhD degree because I haven’t earned it yet.
Thank you so much for your feedback, Johnathan! Please stay in touch with ANS – we may have some issue topics you might consider for publishing as your work develops!
I also agree with not using this designation. In the 8 years of part-time work it took me to complete my PhD, I never once thought of advertising or informing others where I was in that process through some kind of designation. This was way back in the 1980’s [last century!] so I don’t think anyone thought about doing this designation. 🙂
Are we talking about American or Europe? I am in my 50s and those who hold a Doctoral Degree are referred to as Dr. So and So. When they write their credentials after their name, it is usually listed as Joe Smith, PhD or Sue Smith, M.Ed, etc. Whatever the abbreviation for their degree is. I have NEVER heard of a PhD as someone who has NOT completed their Doctoral degree.
I disagree with the positions here. I will be the devil’s advocate, as is my wont. I feel that the PhD (c) designation clarifies the position and social standing of the individual. I am not advocating posturing for a fraudulent claim rather recognizing a social reality. It takes a lot of hard work and dedication to get to the point of a PhD (C) and this is no way deters from the value and prestige of those who have been accorded the prestigious honor. I therefore argue that the use appropriate with one caveat, the individual must actual be actively working upon and seeking the degree and be a registered student t a recognized institution. This abbreviation is particularly useful in a business environment where individuals are judged according t their academic progress as long as the truth is clearly indicated and no misrepresentation is intended I see no harm.
Please avoid ad hominem attacks and exhibit the same respect I have shown you
JW PhD (c) Expected graduation 2016 MA American Military University Summa cum laude MA University of Oklahoma magna cum laude BS University of Maryland University College magna cum laude AA Adirondack Community College
thanks for your perspective, and of course, it seems that you have occasions when you can use this to good advantage. But in the publishing realm, journal Editors (myself included) will not accept this designation as a degree. You can accomplish the same thing by indicating in your affiliations that you are a PhD Candidate at such-and-such an institution. This is actually a more complete acknowledgement of your position and social standing, in that it also designates the institution where the degree is being earned. Your published article will far outlive your designation as a candidate for a degree – candidacy is not permanent. I might also mention that the PhD is not a designation of an honor – it designates an earned degree. An honorary doctoral degree is always indicated by an abbreviation showing that it is honorary, not earned. Best wishes, Peggy
Phdc is acceptable for me . There is a diffrent between studying in Europe and USA . In Europe, U.K., New Zealand, I’m required to study two or three courses, but I don’t have any examination! I do present my thesis once a year to show the progress , nothing more and to get comments to improve my work or repeat a few parts.
I don’t see it non ethical at all. There should be a difference between a MA holder and a PhD holder. A PhDc is for sure studying more.
I think it’s either you have it or you don’t. If you are unable to finish the PhD course, you don’t have it yet. So writing PhD (c) would be inappropriate and can be misleading. The last part in any program (e.g., dissertation is there because it is part of the whole, thus it is a necessary part of having the degree. At the same time, it doesn’t give you more credibility if you write attach (c) after, it just mean you are not finish yet.
Well Stated! Thank you for adding to this dicussion!
I think PhD(c) seems extraordinarily misleading to those of use who haven’t the slightest what the (c) stands for (until reading it here). How would you like to have a surgical consult with an MD(c) and not have the slightest that the fellow went to school but somehow just decided to claim the credential; however, he never took or passed the board exams. Perhaps the person was not even suitable or capable of it! Whereas us plain folk wouldn’t know the difference in the credential, for the sake of impressing other scholars like themselves the person just went on and used it while in a professional capacity. It’s fraudulently misleading to do so! While a person may be a dissertation away from the PhD, perhaps they are just not capable. The PhD MEANS YOU ARE, not that you ALMOST ARE!!! This goes along with what Kathy mentioned, “back in the 1980’s [last century!] so I don’t think anyone thought about doing this designation,” whereas today people want to be whatever they want whenever they want whether it is earned or not, it’s just not soon enough or to their liking and they feel entitled. Tsk tsk.
thank you Melissa! Great points about this still-vexing issue!
I read all the comments with keen interest and noticed that there was real mention that, in essence, using the (c) in the PhD invites more curiosity in the person’s ability to (c)omplete the degree. Absent a drop of the “c” one would wonder if the candidate failed and should now use PhD(f)
I am going to add a new dimension… DNPc. Since there is no dissertation I am confused by this designation. Dr Chinn can you comment?
Any “c” as part of any degree designation is totally inappropriate. Especially when it is used in a document that is permanent- as in a published article. It is not a degree. And you are correct, I am not aware of a point in time when a DNP student becomes a “candidate.” Candidacy is determined by the graduate school of a University – the graduate school also awards the PhD degree. The DNP is a professional degree that does not have oversight by the graduate school – the oversight of the degree is only the resopnsibility of the School or College awarding the degree.
Dr. Chinn, I am happy to see the DNP addressed here as that is what brought me to the discussion. I agree that a PhD and a DNP are not equivalent in education or stature, but it is a terminal degree (much like a JD, or MD). While I am not sure about the concept of “candidacy” the DNP that I am working toward IS awarded by a graduate school. When I graduate I will be hooded, wear a tam, and have three stripes on the sleeves of my robe, like any other individual that has earned a doctorate degree. I will have earned the right to refer to myself as “Doctor”, and use the honorific “Dr.” in front of my name. Yes, the DNP is a clinical degree and, unless I am misunderstanding your use of the term “graduate school”, it does have oversight by the graduate school.
Hi Peggy, here is another perspective to Always keep in mind … since you are discussing PhD candidates. Up and down the West Coast, while visiting some “interesting” locations, I have came across multiple Individuals that are/were offering services as: Counselors, Life coaches, Yoga instructors, Feng-shui, Ayurveda practitioners, etc, etc. All claiming a PhD degree, but couldn’t provide an answer as to which higher institution they attended, others mentioned “schools” I’ve never heard of. It wasn’t until later, that I found out that they were purchasing “Degree’s” from a On-line company. I believe that there should be a Public Law against this type of deception, don’t you? DSM
Of course there should be such a law. The bottom line is that there are 2 things we all can do – be aware of practices of deception and check out all credentials, and second, be clear about our own credentials and how we represent them to others to assure them of our legitimate standards.
What is the proper way to list an honorary affiliation such as “visiting Research Fellow or honorary lecturer” in a publication??
Good question – these are not credentials, but they are, as you note, affiliations that tupically appear on the line following your name and credentials. So my “signature” for example, is Peggy L. Chinn, RN, PhD Professor Emerita, University of Connecticut Editor, Advances in Nursing Science
My name is followed by my credentials on the same line, my affiliation with the Unviersity of Connecticut on the second line, and my Editorship of ANS on the third line.
What is the proper way to list an honorary affiliation such as “visiting Research Fellow or honorary lecturer” in a publication??
Many apologies – your question got lost in a string of comments. But I found it -and here is my answer – just list it on a line below your name – much as you would indicate your employment or professional affiliation in your signature block. Example: Peggy L Chinn, RN, PhD Professor Emerita, University of Connecticut
I disagree. A DNPc has reached a point where they have completed their defense successfully and earned that title
To stand by your opinion on this, you need to provide a reasonable argument that completing the defense bestows a titile on the person. Is there a certificate of completion that is awarded by the institution? Is this title permanent? As far as I know, both of these questions yields a “No” response. One does not use the “c” title once the requirements for the degree are completed, at which time the institution awards the degree. Completing the defense is the same thing as passing a course that is required for the degree – it is indeed an accomplishment, and might even lead to more accomplishments! But it is not a degree, and it is not a title.
What about if you have multiple degrees and professional credentials? How do I list them and what do I omit when I submit for a journal publication?
PA, AT, MMS, MSEd
Yes, particularly if the degrees all represent a different focus. I do not recommend listing all the degrees in the same field such asBS, MS, PhD all in nursing; you can but it is typically only the highest degree that you list. If you have two graduate degrees in two different fileds, you can list them as follows: PhD (nursing), PhD (education) for example.
How would one enter their credentials if they have a PhD in Education with specialization in Nursing Education with a MHA, MSN, and BSN.
How you list your credentials (in which order, even which credentials to include) varies depending on where you are listing them, for what purpose. The important point is making sure that you indicate each credential correctly – the exact credential(s) you were awarded. A PhD is a research/theory degree/credential – meaning the degree focused on the theory and research methods that are central to the development of knowledge in the discipline. The area in which the PhD was earned (e.g. nursing, education, sociology, anthropology, etc.) is not indicated as part of the credential. An EdD is both a degree and an indicator that the doctorate is a professional degree focused on the application of knowledge in the discipline, and appropriate approaches to teaching the knowledge of the discipline. However, these conceptual distinctions are imprecise – the main point to know is the accurate representation of any credential that you earned.
Hi, there. I’m not sure this post will still receive responses. I’ve only recently stumbled across it, so I’m going to take a chance.
I am actively in pursuance of a dual master’s degree that will be completed within the year. I am also currently publishing chapters in two textbooks and freelancing/contracting on other projects. I was recently discussing my credentials with a colleague, and she suggested I find a way to include my dual master’s degrees in my upcoming publishings. I brought this suggestion to two of my professors and both felt that it was a good idea for my career outlook. Is there a way to appropriately and professionally include this information in a transparent way that clearly identifies these degrees are in progress and that I don’t currently hold these degrees?
I appreciate your responses. Thank you.
Excellent question,Kayla! Once the degrees are both complete you can list both of them with the discipline in parenthesis – like this: MS (Nursing), MS (Sociology) – for sure both need to be on your CV. And you can show both when this is relevant. But until they are completed, you can use the “author information” section for a published article, or for a presentation, to say that these are in process.
Trackbacks & Pingbacks
- PhD(c) – Open Learning, Editing Team
What do you think? Cancel reply

Enter your email address to subscribe to this blog and receive notifications of new posts by email.
Email Address:
Sign me up!

ANS Peer Review Mentoring
Interested in becoming a nursing journal editor.
We accept applications for this innovative journal editor immersion program each year on April 1st. Download the 2021-22 ANS Editor Immersion Program Description to learn more!
ANS Purposes and Scope
The essential purposes of ANS are to advance the development of nursing knowledge and to promote the integration of nursing philosophies, theories and research with practice. We expect high scholarly merit and encourage innovative, cutting edge ideas that challenge prior assumptions and that present new, intellectually challenging perspectives. We seek works that speak to global sustainability and that take an intersectional approach, recognizing class, color, sexual and gender identity, and other dimensions of human experience related to health.

This journal is a member of, and subscribes to the principles of, the Committee on Publication Ethics (COPE) www.publicationethics.org
From the Editor on Scholarship
- The “C’s” of Scholarship
- How to list your credentials
- Changes in scholarly publishing
- Self-plagiarism
- Evaluating your sources
From the Editor on Publishing
- Overcoming Roadblocks
- Finding a home for your manuscript
- Open Access: What it is and what it is not
- Standing Up for Science
- Updated ANS Author’s Guide: Anti-racist Guidelines
ANS on “Evidence”
Search this blog, search by category, about the ans blog.
The ANS Blog provides a forum for discussion of issues raised in the articles published in Advances in Nursing Science . We welcome all authors and readers to post your comments and ideas on the blog! If you would like to be an author on this blog, let us know!
The journal Editor is Peggy L. Chinn, RN, PhD, FAAN. Dr Chinn founded the journal in 1978.

Did you know you can write your own about section just like this one? It's really easy. Navigate to Appearance → Widgets and create a new Text Widget. Now move it to the Footer 1 sidebar.
A wonderful serenity has taken possession of my entire soul, like these sweet mornings of spring which I enjoy with my whole heart. I am alone, and feel the charm of existence in this spot, which was created for the bliss of souls like mine. I am so happy, my dear friend, so absorbed in the exquisite sense of mere tranquil existence, that I neglect my talents. I should be incapable of drawing a single stroke at the present moment; and yet I feel that I never was a greater artist than now.
- Call for ANS Editor
- Concept Analysis
- Conferences
- Continuing Education
- Editor's Picks
- Editorial opinion
- Emancipatory Nursing
- Environment
- Featured Articles
- Future issue topics
- Future Issues
- Instrument Development
- Journal Collections
- Journal Information
- Journal News
- Knowledge Synthesis
- Letters to the Editor
- Nursing Practice
- Open Access
- Opposing Views
- Published Ahead of Print
- Publishing Ethics
- Scholarship
- social justice
- Table of Contents
- Uncategorized
- Visions: Scholarship of Rogerian Nursing Science
Blog at WordPress.com.

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar
- Identity & Security
- Engineering
- Announcements
- Try Auth0 For Free Talk To Sales

What are Verifiable Credentials and Why You Should Care About Them
Verifiable Credentials can be stored on digital devices, and you can use cryptography to verify their data and authorship. Let's learn more about them and why you should care about them.

February 05, 2024
We often use physical credentials such as our passports or driver's licenses as proof of identity. Until recent years, these types of credentials have usually been used in-person or offline, but nowadays, it's possible to prove your identity through digital credentials on the web in a cryptographically secure, privacy-respecting, and machine-verifiable way. In this blog post, you'll learn about these verifiable credentials, why you should use them, and when.
What are Verifiable Credentials?
When you think about a credential, you can often think of a physical credential like a passport, a driver's license, or an employee badge. A credential refers to a set of one or more claims made by an issuer ; in the passport example, the photo, name, or identification number are the claims made by a government to identify a subject.
When we talk about Verifiable Credentials (VCs), we are referring to a W3C standard for digital, cryptographically verifiable credentials. These credentials can represent the same information as a physical credential, but they add the use of digital signatures, making them more trustworthy than their physical version. You can store them on your device, which makes them more convenient and available almost everywhere.
In the verifiable credentials context, there are a few important roles:
- Holder : it's the entity that possesses the verifiable credential. Holders could be, for example, students, employees, and customers.
- Issuer : the entity that asserts claims about the subject, creates and transmits the verifiable credential to the holder. For example, governments, corporations, and non-profit organizations can be issuers.
- Often, the holder of a verifiable credential and subject can be the same, but only sometimes. For example, a parent can be the holder of the verifiable credential of their child (subject)
- Verifier : the entity that receives and processes verifiable credentials, such as employers, security personnel, and websites.
- Verifiable Data Registry : the system that creates and verifies verifiable credentials schemas. For example, government ID databases and trusted databases.
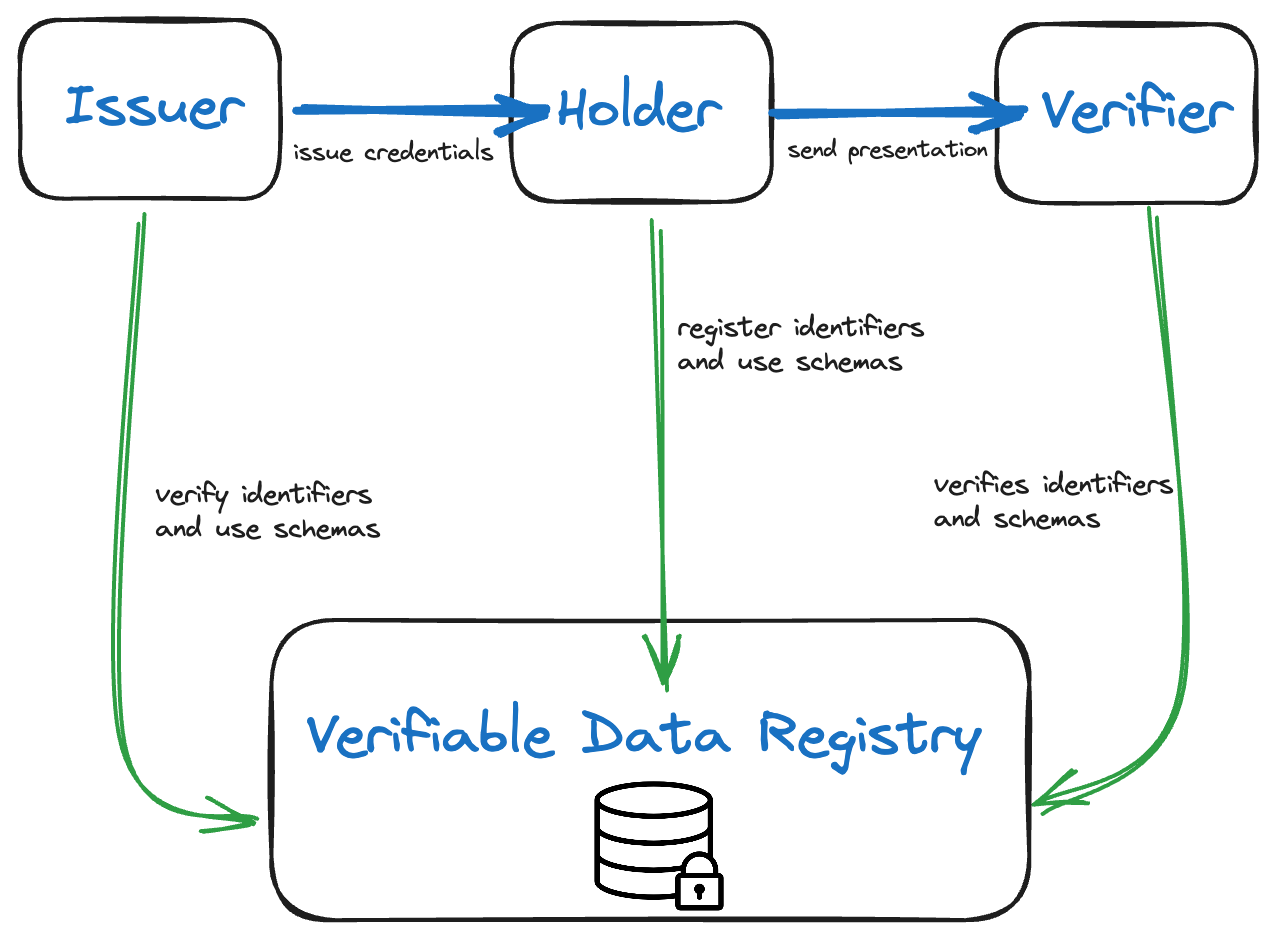
The image above shows how each entity interacts with each other. The issuer issues credentials to the holder as well as identifies and verifies the verifiable credentials. The holder acquires, stores, and presents VCs to the verifier. The verifier verifies VCs against the Verifiable Data Registry, which maintains identifiers and schemas.
If we think of an example, let's say you are a citizen of the Asgard country. Asgard's government can issue a verifiable credential so you can prove your identity.
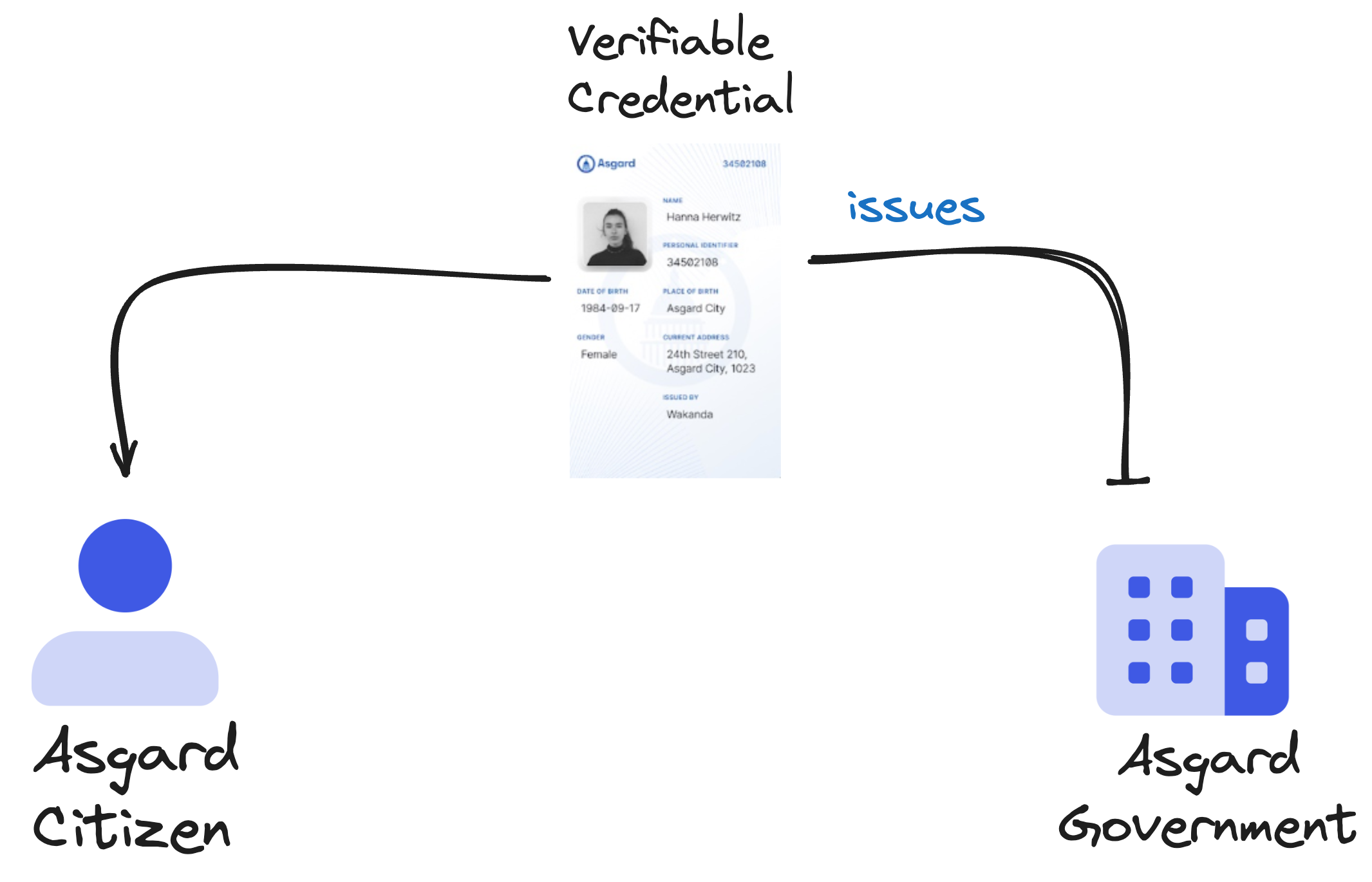
In this example, the holder of the verifiable credential would be you because you are the owner of it and Asgard's government would be the issuer . This would be one of those scenarios where the subject would be the same as the holder because Asgard's government created claims for you, such as full name, identification number, and so on.
Later on, let's say the Asgard police stop you and ask you for your ID. You decide to use your VC, and you have it in your wallet, so you present it to them. In this case they'd act as the verifier and check against Asgard's government database (the Verifiable Data Registry ) that the VC is legit.
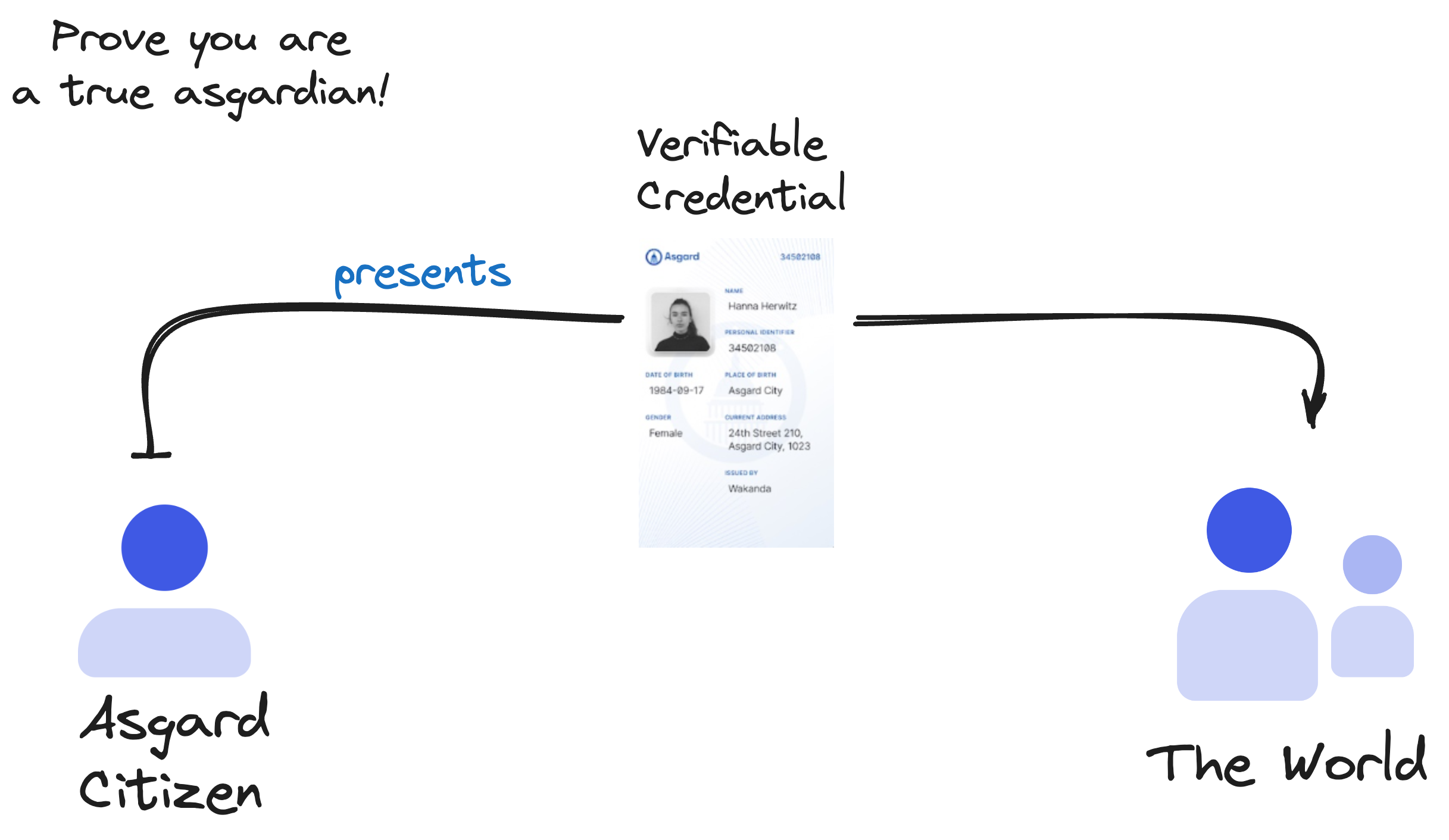
Verifiable Credentials Are Necessary
Verifiable Credentials have many use cases in our day-to-day life, and as we move more into an online world, we need to be able to disclose our identity without issuers knowing . Because VCs are available in your wallet, you can use them "offline", meaning the issuer doesn't know when and how often you use them. This is what makes VCs so powerful: they are convenient, and having them available in your wallet removes a lot of friction from a user's life. So, let's go ahead and explore some use cases.
Legal Identity
It's essential that you're able to prove your identity in a way that can be quickly verified, and governments are in the position to provide such identification in a verifiable digital form. Some examples are:
- You get stopped over a traffic violation; with a digital driver's license, you always have access to it, and you can use it to prove to the officers both your identity and that you can drive.
- The electronic passport can contain a list of all the places you've visited and visas, so immigration officers can quickly and easily evaluate your suitability when visiting a new country.
- Imagine asking for refuge in a country in such desperate conditions that you don't have your physical credentials. Still, you were issued a self-sovereign proof of birth, and attached to this is the proof of birth and marriage of your parents; since it's verifiable, you can show this at the border controls of the country you're seeking refuge.
In finance, we can think of banking, brokerage, insurance, etc. Some example use cases are:
- Let's say you want to send money to your family abroad; you can share your identity profile as well as your family member's with the money transfer service. This allows them to verify the source and destination of funds automatically.
- If you want to open an account, you can use your government-issued certificate to prove your identity. Later on, when you want to close the account, the bank needs to revoke the "account owner" claim as part of the closing account process.
In the healthcare industry, privacy is extremely important, and with VCs, we can guarantee that the holder of the credential can disclose only the information they need. Let's understand some use cases in this area:
- A pharmacy can receive a prescription for medication for a patient. The pharmacy can automatically verify the doctor's ability to write prescriptions and the patient's insurance coverage.
- You can have government-issued disability credentials without having to disclose your specific disability to the service or entity you're providing. Issuers can issue verifiable credentials that support selective disclosure so holders can present proof of claims without revealing the entire verifiable credential.
Professional Credentials
You may need a prove that an entity is who they say they are, and they can do what they say. This allows you to trust universities, doctors, companies, etc.
- Health providers could provide information about the doctors they have on staff, including verifiable credentials about their education, board certification, etc.
- You could verify someone's obtained degree from a university that has a digital certificate to issue verifiable credentials.
- You can have an electronic badge that proves your identity to your company.
How Does a VC Look Like?
Let's take a look at what a verifiable credential looks like. Let's think of someone's ID card:
This JSON represents the digital version of Hanna Herwitz's ID card. Let's take a look at some of the most relevant parts of the VC:
The credential type can be used to determine if a specific credential is appropriate for a particular use case. In the example above, the type value is [ "VerifiableCredential" , "IDCard" ] .
Represents the issuer of the credential and has to be a URI or an object containing an ID property. The example above is the Asgard government with the value did : web : asgard - state . auth0lab . com . Note that the value starts with did ; this is a Decentralized Identifier , a new identifier enabling verifiable, decentralized digital identity. However, it's not mandatory to use DIDs.
Credential Subject
Refers to the subject of the verifiable credential; it can be a DID or an object containing an id property. In the example above, the subject data is:
Cryptographic Proof
It is one of the most essential parts and what makes this credential verifiable . Refers to cryptographic proofs (can be an object or an array) that can be used to detect tampering and verify the authorship of a credential or the data derived from the VC. In the example above:
Verifiable Credentials in Action
Now that you know what a VC looks like, let's look at them in action.
We've developed a site, verifiablecredentials.dev , where you can play around and debug verifiable credentials.
To obtain a new verifiable credential, navigate to wallet.verifiablecredentials.dev , where you'll see a demo wallet where you can start by adding your first VC.
Follow the steps, and you'll create your verifiable credential! 🎉
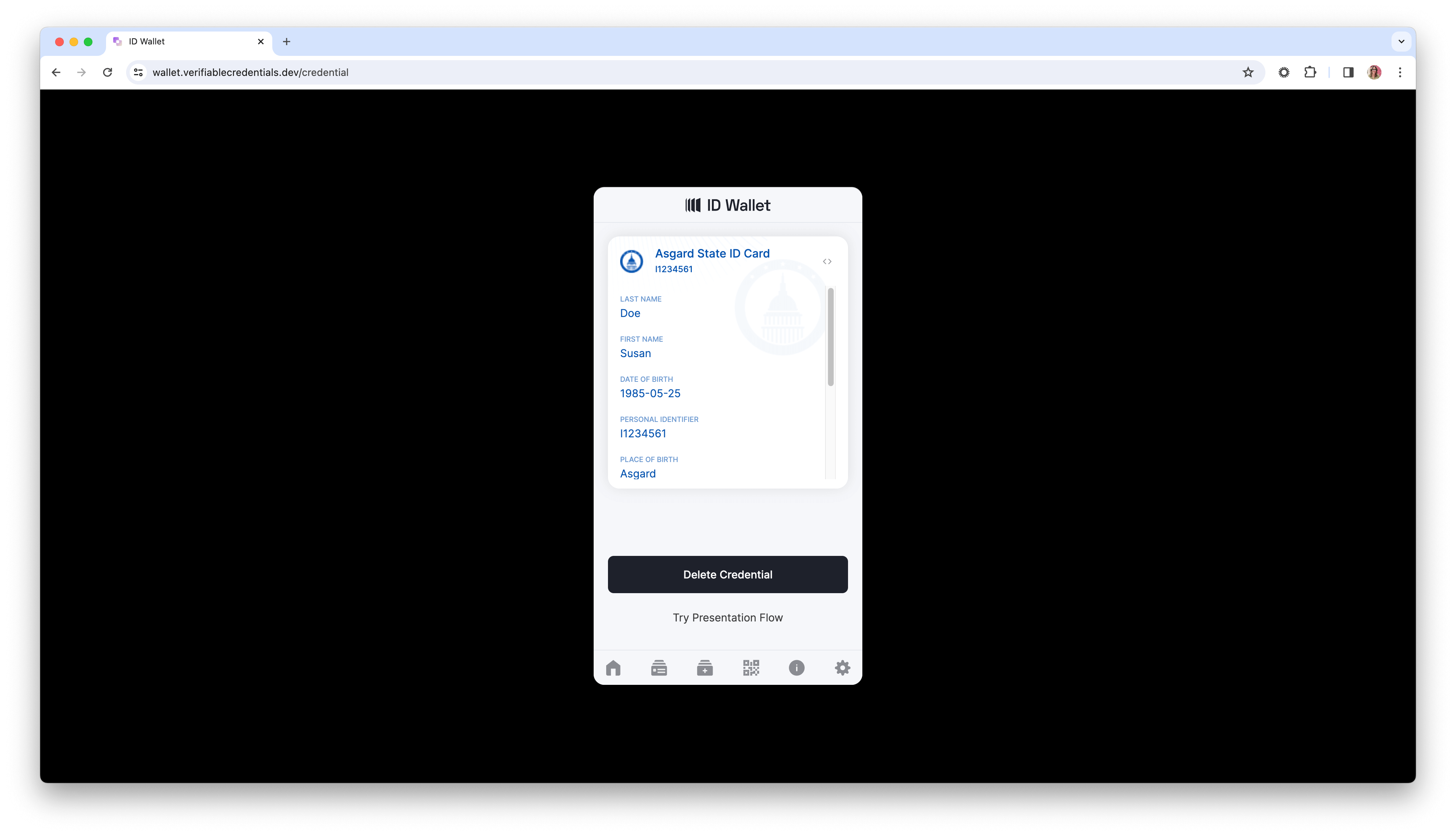
Present a VC
You can use the Presentation Debugger tool to create a request that defines the characteristics you want a Verifiable Presentation to meet.
You can use ID Wallet to see your verifiable credential data in the Presentation Debugger tool.
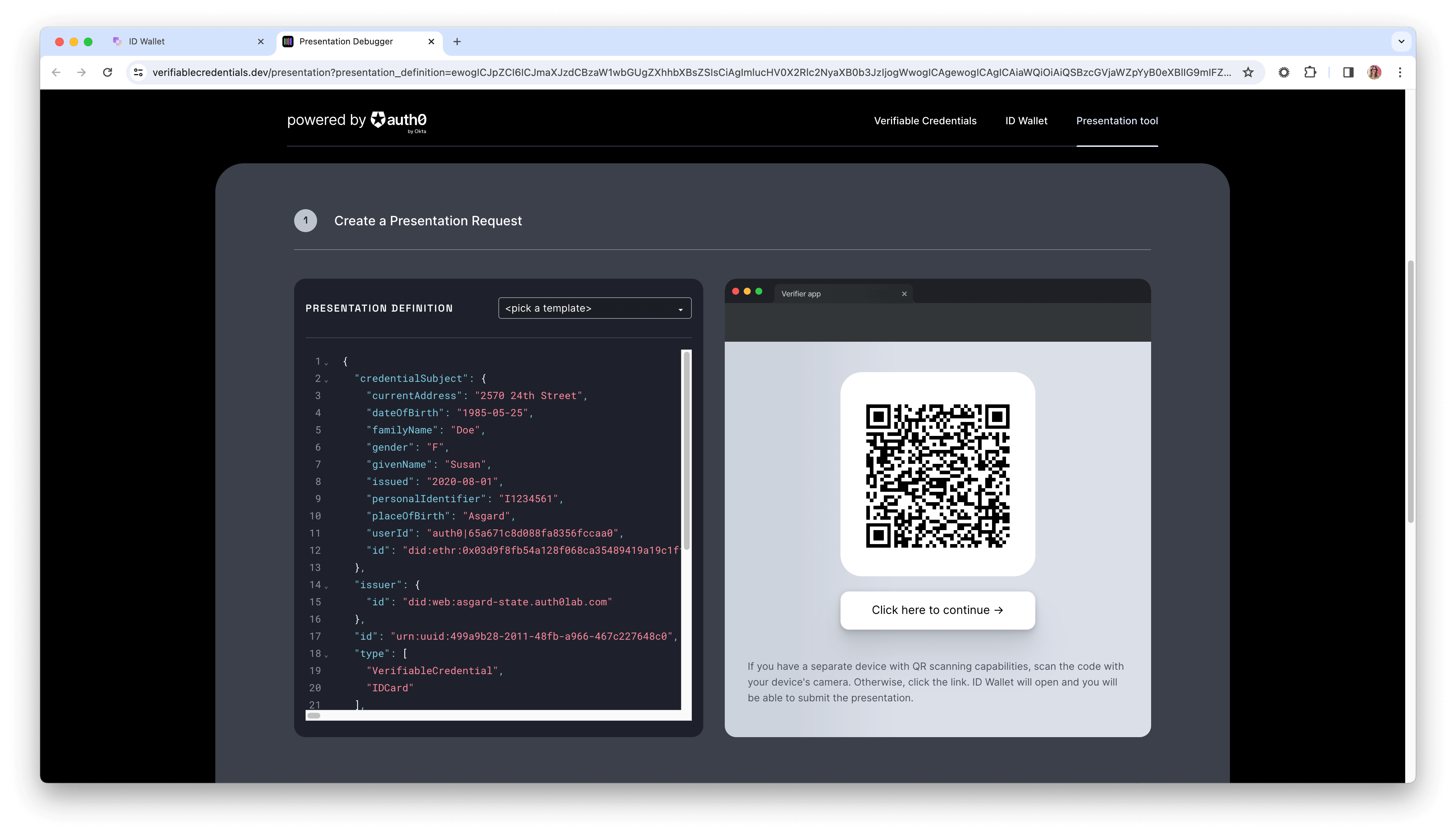
Verifiable Credentials are digital, cryptographically signed credentials that you can use in many aspects of your life. There are many use cases in healthcare, education, and legal contexts where VCs are extremely useful.
Users need the means to exercise their identity and disclose their claims without issuers knowing, the same way they do offline.
If you want to learn more about VCs, go to verifiablecredentials.dev , where you can play around and create and present verifiable credentials.
Protocol and NGO Liaison Office

Presentation of credentials - guidelines
The letter of credentials.
The letter of credentials of permanent representatives to the United Nations Office at Vienna are issued either by the Head of State or Government or by the Minister for Foreign Affairs of the sending country and are addressed to the Secretary-General of the United Nations by name and presented to the Director General of UNOV/ Executive Director of UNODC, who represents the Secretary-General and receives credentials on his or her behalf. Separate credentials should not be issued for the funds and programs and subsidiary entities affiliated with the United Nations Office at Vienna.
For a standard form of letters of credentials, please consult the example given.
Download | Standard letter of credentials
The presentation of credentials
When a new permanent representative assumes office, the mission should request the UNOV Protocol Service to make arrangements for the presentation of credentials.
Once a time and date for the presentation of credentials has been arranged, the Chief of Protocol welcomes the newly appointed permanent representative to the Vienna International Centre Rotunda (C-building). The permanent representative will then be escorted to the office of the Director-General/ Executive-Director by the Chief of Protocol and a courtesy Security Officer. The permanent representative may be accompanied by one or two members of his or her delegation as well as an interpreter provided by the mission, if necessary.
The presentation of credentials usually takes place in the office of the Director-General/ Executive Director. During the presentation, photographs of the Director-General/ Executive Director with the newly appointed permanent representative are taken by a photographer. Electronic copies of the photographs will be sent to the mission concerned.Then, less formally, the Director-General/ Executive-Director briefs the new permanent representative on present and forthcoming activities of the organisation with the represented country.
According to established practice, the meeting will usually not take longer than 30 minutes. Permanent representatives are not expected to make formal speeches during the presentation ceremony.
- Fraud Alert
- Legal Notice
Watch CBS News
Trump and Biden's first presidential debate of 2024, fact checked
By Arden Farhi , Hunter Woodall , Jui Sarwate , Julia Ingram , Layla Ferris , Laura Doan , James LaPorta , Daniel Klaidman , Alexander Tin , Pete Villasmil, Sierra Sanders
Updated on: June 28, 2024 / 12:26 AM EDT / CBS News
Here's the fact check of some of the statements made by President Biden and former President Donald Trump during the first 2024 presidential debate , which took place in Atlanta on Thursday, June 27. The two tangled on topics including immigration, the economy, abortion and their respective records. Mr. Biden seemed to ramble during many of his
CBS News covered the debate live as it happened .
Trump claims "we had the greatest economy in the history of our country": False
Trump : "We had the greatest economy in the history of our country. And we have never done so well. Every- everybody was amazed by it. Other countries were copying us."
Details : Trump's claim is false that during his presidency the U.S. had the greatest economy in the history of the country by many of the common metrics used to judge economic performance. The claim struggles when looking at GDP. If the 2020 pandemic is excluded, growth after inflation under Trump averaged 2.49%, according to figures from the World Bank . This is far from the GDP growth under Democratic President Bill Clinton of 3.88%, according to World Bank data . Including the time period after COVID spread, that average drops to 1.18%.
Trump's claim also falls short when compared to historical figures. Growth between 1962 to 1966 ranged from 4.4% to 6.6%. In 1950 and 1951, GDP ranged between 8.7% and 8%.
Under Mr. Biden, annual GDP growth is averaging 3.4%, according to the Associated Press .
*An earlier version of this fact check misstated World Bank figures for growth after inflation under Trump at 2.65%, rather than 2.49%, and 1.45%, instead of 1.18%, and also rounded the growth number for Clinton. This has been updated.
Unemployment
Trump's claim is also false even when evaluating the unemployment rate. In February 2020, a month before the COVID pandemic affected the economy, the unemployment rate stood at 3.5% — which was the lowest since December 1969 — but not the lowest ever. When Trump's term ended, the unemployment rate was 6.3%.
In 1953, the unemployment rate fell as low as 2.5%. Under Mr. Biden, the unemployment rate is 4%, according to the most recent data from May 2024.
In January 2023 and again in April 2023, the unemployment rate was 3.4%, lower than the best month during Trump's term.
Stock market performance
On Jan. 19, 2021, the S&P 500-stock average closed at 67.8% above where it had been the day before Trump was inaugurated in 2017.
According to Investopedia , at the end of President Barack Obama's first term in office, the S&P closed 84.5% higher. Additionally the S&P gained 79% during President Bill Clinton's first term, and 70% during President Dwight Eisenhower's first term. So far, under President Biden, the S&P 500 has increased almost 40% , according to calculations on June 13.
By Laura Doan and Hunter Woodall
Biden claims he's the only president this century that doesn't have troops dying anywhere in the world: False
Biden: "I'm the only president this century that doesn't have any — this decade — that doesn't have any troops dying anywhere in the world."
Details : At least 16 U.S. service members have died while serving overseas during Mr. Biden's presidency. Thirteen U.S. service members died in an attack at the Kabul airport in Afghanistan in August 2021. Three soldiers were killed in an attack in Jordan in January of this year.
By Layla Ferris
Trump claims he did not refer to U.S. soldiers who were killed as "suckers and losers": False
Trump: "First of all, that was a made-up quote. 'Suckers and losers,' they made it up."
Details : Current and former U.S. military service members have detailed to CBS News multiple instances when Trump made disparaging remarks about members of the U.S. military who were captured or killed, including referring to the American war dead at the Aisle-Marne American Cemetery in France in 2018 as "losers" and "suckers."
A senior Defense Department official and a former U.S. Marine Corps officer with direct knowledge of what was said detailed how Trump said he did not want to visit the cemetery because it was "filled with losers." These accounts were backed independently by two other officials — a former senior U.S. Army officer and a separate, former senior U.S. Marine Corps officer.
In another conversation on the trip, Trump referred to the 1,800 Marines who died in the World War I battle of Belleau Wood as "suckers" for getting killed. The Atlantic was first to report Trump's comments in 2020. His former chief of staff John Kelly later confirmed to CNN the essence of what Trump had said.
By James LaPorta and Sierra Sanders
Biden claims 40% fewer people are crossing border illegally, better than when Trump was in office: Partially true
Biden: "I've changed it in a way that now you're in a situation where there 40% fewer people coming across the border illegally; it's better than when he left office."
Details : Since Mr. Biden issued a proclamation banning most migrants from asylum at the U.S.-Mexico border in early June, illegal crossings there have dropped. In the past week, daily illegal border crossings have averaged roughly 2,000, according to internal Department of Homeland Security data obtained by CBS News. That's a 47% drop from the 3,800 daily average in May.
During the height of a spike in migration faced by the Trump administration in 2019, Border Patrol recorded an average of 4,300 daily illegal crossings, government data show. But there were months during the Covid-19 pandemic when the Trump administration averaged fewer than 2,000 illegal border crossings.
By Camilo Montoya-Galvez
Trump claims migrants coming to U.S. and "killing our citizens at a level...we've never seen before": Misleading
Trump: "People are coming in and killing our citizens at a level like we've never seen before."
Details : Some migrants who are believed to have entered the U.S. along the southern border in recent years have been charged with murder and other heinous crimes in different parts of the country. They include the suspect in the high-profile murder of Georgia nursing student Laken Riley .
But while the data on this question is not comprehensive, available studies have found that migrants living in the country illegally do not commit crimes at a higher rate than native-born Americans.
Government statistics also show a very small fraction of migrants processed by Border Patrol have criminal records in the U.S. or other countries that share information with American officials.
On COVID, Trump claims more people died under Biden administration than his: True, but needs context
Trump: "Remember, more people died under his administration — even though we had largely fixed it — more people died under his administration than our administration, and we were right in the middle of it, something which a lot of people don't like to talk about. But [Biden] had far more people dying in his administration."
Details : More than 460,000 people had died from COVID-19 by the end of the week that Biden was inaugurated in 2021, while more than 725,000 have died in the three years since then, according to data from the CDC . However, research has found that the counts of COVID-19 deaths, especially in the early days of the pandemic, were likely undercounted .
By Julia Ingram and Jui Sarwate
In discussing abortion, Trump claims former Virginia governor, a Democrat, supported killing babies: False
Trump: "If you look at the former governor of Virginia, he was willing to do this — he said 'we'll put the baby aside and we'll determine what we'll do with the baby'.. .meaning we'll kill the baby."
Details : In a 2019 radio interview then-governor of Virginia Ralph Northam, in discussing late-term abortions, addressed a hypothetical scenario in which a fetus was severely deformed or wasn't otherwise viable. He said, "the infant would be delivered, the infant would be kept comfortable, the infant would be resuscitated if that's what the mother and the family desired."
Northam did not say the fetus should be killed. Killing a newborn baby — or infanticide — is illegal in every state, and not a single state is trying to change that.
By Laura Doan and Daniel Klaidman
Trump claims Biden "went after" his political opponent in New York "hush money" case to damage him: False
Trump: "[Biden] basically went after his political opponent (Trump) because he thought it was going to damage me, but when the public found out about these cases, 'cause they understand it better than he does, he has no idea what these cases are, but when they found out about these cases, you know what they did? My poll numbers went up, way up."
Details : There is no federal jurisdiction over a state case. The Manhattan district attorney's office is a separate entity from the U.S. Department of Justice. The department does not supervise the work of the Manhattan D.A.'s office, does not approve its charging decisions, and it does not try the D.A.'s cases.
By Pete Villasmil
Trump claims he brought insulin prices down for seniors: Misleading
Trump: "I'm the one that got the insulin down for the seniors. I took care of the seniors."
Details : During Trump's time as president, Medicare created a voluntary program in 2020 between some plans and insulin manufacturers that agreed to cap out-of-pocket costs for insulin at $35 per month. Around half of Medicare Advantage or stand-alone prescription drug plans ended up participating by 2021.
David Ricks, CEO of insulin drugmaker Eli Lilly, has taken credit for pioneering the idea with Trump administration officials at a congressional hearing and in an interview . In the same interview with STAT, Seema Verma, former Medicare agency chief in the Trump administration, gave Ricks the credit for the cap: "He is an unsung hero. He was actually the mastermind of all of this."
Medicare ended the policy in 2023, after Mr. Biden signed into law the Inflation Reduction Act , which capped insulin costs for Medicare beneficiaries — not just for the portion of plans participating in the program. The law capped insulin costs at the same amount of $35 per month.
By Alexander Tin and Hunter Woodall
Trump claims Biden wants open borders: False
Trump: "He wants open borders. He wants our country to either be destroyed or he wants to pick up those people as voters."
Details : When he took office, Mr. Biden reversed numerous Trump-era immigration policies, including a program that required migrants to await their asylum hearings in Mexico. U.S. Border Patrol has also reported record numbers of migrant apprehensions along the southern border during Mr. Biden's presidency. But Mr. Biden has never endorsed or implemented an "open borders" policy.
In fact, Mr. Biden has embraced some restrictive border policies that mirror rules enacted by his predecessor. In 2023, his administration published a regulation that disqualified migrants from asylum if they crossed into the country illegally after not seeking protection in a third country.
Earlier this month, Mr. Biden enacted an even stricter policy: a proclamation that has partially shut down asylum processing along the border. His administration has also carried out over 4 million deportations, expulsions and returns of migrants since 2021, according to government data .
Only U.S. citizens can vote in federal elections. Most who cross into the U.S. illegally are not on a path to permanent legal status, let alone citizenship. Even those who apply and win asylum — a process that typically takes years to complete — have to wait five years as permanent U.S. residents before applying for American citizenship. There's no evidence to suggest that the Biden administration's border policy is based on a desire to convert migrants into voters.
Biden claims Trump wants to get rid of Social Security: False
Biden "[Trump] wants to get rid of Social Security. He thinks there's plenty to cut in social security. He's wanted to cut Social Security and Medicare, both times."
Details : Trump has repeatedly said he will try to protect Medicare and Social Security. Trump said in a March 21 Truth Social post that he would not "under any circumstance" allow Social Security to "be even touched" if he were president. Trump had said in a CNBC interview on March 11 that "there is a lot you can do" in terms of "cutting" spending under Social Security. Mr. Biden said the comments were proof Trump aimed to make cuts in the programs, but a Trump campaign spokesman said Trump was referring to "cutting waste and fraud," not Social Security entitlements.
Trump claims Biden has the "largest deficit" in history of U.S.: False
Trump: "But he's (Biden) got the largest deficit in the history of our country."
Details : The national deficit was the largest it had been in over two decades under Trump's administration, not Mr. Biden's, according to data from the U.S. Treasury . The deficit peaked in fiscal year 2020 at $3.13 trillion, and declined to $1.7 trillion by the end of fiscal year 2023.
By Julia Ingram
- Presidential Debate
- Donald Trump
Arden Farhi is the senior White House producer at CBS News. He has covered several presidential campaigns and the Obama, Trump and Biden administrations. He also produces "The Takeout with Major Garrett."
More from CBS News

How to watch the first presidential debate between Biden and Trump

Biden struggles early in presidential debate with hoarse voice

When the next presidential debate of 2024 takes place

Biden campaign, DNC highlight democracy, Jan. 6 in lead-up to debate
NTRS - NASA Technical Reports Server
Available downloads, related records.
Docker overview
Docker is an open platform for developing, shipping, and running applications. Docker enables you to separate your applications from your infrastructure so you can deliver software quickly. With Docker, you can manage your infrastructure in the same ways you manage your applications. By taking advantage of Docker's methodologies for shipping, testing, and deploying code, you can significantly reduce the delay between writing code and running it in production.
The Docker platform
Docker provides the ability to package and run an application in a loosely isolated environment called a container. The isolation and security lets you run many containers simultaneously on a given host. Containers are lightweight and contain everything needed to run the application, so you don't need to rely on what's installed on the host. You can share containers while you work, and be sure that everyone you share with gets the same container that works in the same way.
Docker provides tooling and a platform to manage the lifecycle of your containers:
- Develop your application and its supporting components using containers.
- The container becomes the unit for distributing and testing your application.
- When you're ready, deploy your application into your production environment, as a container or an orchestrated service. This works the same whether your production environment is a local data center, a cloud provider, or a hybrid of the two.
What can I use Docker for?
Fast, consistent delivery of your applications.
Docker streamlines the development lifecycle by allowing developers to work in standardized environments using local containers which provide your applications and services. Containers are great for continuous integration and continuous delivery (CI/CD) workflows.
Consider the following example scenario:
- Your developers write code locally and share their work with their colleagues using Docker containers.
- They use Docker to push their applications into a test environment and run automated and manual tests.
- When developers find bugs, they can fix them in the development environment and redeploy them to the test environment for testing and validation.
- When testing is complete, getting the fix to the customer is as simple as pushing the updated image to the production environment.
Responsive deployment and scaling
Docker's container-based platform allows for highly portable workloads. Docker containers can run on a developer's local laptop, on physical or virtual machines in a data center, on cloud providers, or in a mixture of environments.
Docker's portability and lightweight nature also make it easy to dynamically manage workloads, scaling up or tearing down applications and services as business needs dictate, in near real time.
Running more workloads on the same hardware
Docker is lightweight and fast. It provides a viable, cost-effective alternative to hypervisor-based virtual machines, so you can use more of your server capacity to achieve your business goals. Docker is perfect for high density environments and for small and medium deployments where you need to do more with fewer resources.
Docker architecture
Docker uses a client-server architecture. The Docker client talks to the Docker daemon, which does the heavy lifting of building, running, and distributing your Docker containers. The Docker client and daemon can run on the same system, or you can connect a Docker client to a remote Docker daemon. The Docker client and daemon communicate using a REST API, over UNIX sockets or a network interface. Another Docker client is Docker Compose, that lets you work with applications consisting of a set of containers.
The Docker daemon
The Docker daemon ( dockerd ) listens for Docker API requests and manages Docker objects such as images, containers, networks, and volumes. A daemon can also communicate with other daemons to manage Docker services.
The Docker client
The Docker client ( docker ) is the primary way that many Docker users interact with Docker. When you use commands such as docker run , the client sends these commands to dockerd , which carries them out. The docker command uses the Docker API. The Docker client can communicate with more than one daemon.
Docker Desktop
Docker Desktop is an easy-to-install application for your Mac, Windows or Linux environment that enables you to build and share containerized applications and microservices. Docker Desktop includes the Docker daemon ( dockerd ), the Docker client ( docker ), Docker Compose, Docker Content Trust, Kubernetes, and Credential Helper. For more information, see Docker Desktop .
Docker registries
A Docker registry stores Docker images. Docker Hub is a public registry that anyone can use, and Docker looks for images on Docker Hub by default. You can even run your own private registry.
When you use the docker pull or docker run commands, Docker pulls the required images from your configured registry. When you use the docker push command, Docker pushes your image to your configured registry.
Docker objects
When you use Docker, you are creating and using images, containers, networks, volumes, plugins, and other objects. This section is a brief overview of some of those objects.
An image is a read-only template with instructions for creating a Docker container. Often, an image is based on another image, with some additional customization. For example, you may build an image which is based on the ubuntu image, but installs the Apache web server and your application, as well as the configuration details needed to make your application run.
You might create your own images or you might only use those created by others and published in a registry. To build your own image, you create a Dockerfile with a simple syntax for defining the steps needed to create the image and run it. Each instruction in a Dockerfile creates a layer in the image. When you change the Dockerfile and rebuild the image, only those layers which have changed are rebuilt. This is part of what makes images so lightweight, small, and fast, when compared to other virtualization technologies.
A container is a runnable instance of an image. You can create, start, stop, move, or delete a container using the Docker API or CLI. You can connect a container to one or more networks, attach storage to it, or even create a new image based on its current state.
By default, a container is relatively well isolated from other containers and its host machine. You can control how isolated a container's network, storage, or other underlying subsystems are from other containers or from the host machine.
A container is defined by its image as well as any configuration options you provide to it when you create or start it. When a container is removed, any changes to its state that aren't stored in persistent storage disappear.
Example docker run command
The following command runs an ubuntu container, attaches interactively to your local command-line session, and runs /bin/bash .
When you run this command, the following happens (assuming you are using the default registry configuration):
If you don't have the ubuntu image locally, Docker pulls it from your configured registry, as though you had run docker pull ubuntu manually.
Docker creates a new container, as though you had run a docker container create command manually.
Docker allocates a read-write filesystem to the container, as its final layer. This allows a running container to create or modify files and directories in its local filesystem.
Docker creates a network interface to connect the container to the default network, since you didn't specify any networking options. This includes assigning an IP address to the container. By default, containers can connect to external networks using the host machine's network connection.
Docker starts the container and executes /bin/bash . Because the container is running interactively and attached to your terminal (due to the -i and -t flags), you can provide input using your keyboard while Docker logs the output to your terminal.
When you run exit to terminate the /bin/bash command, the container stops but isn't removed. You can start it again or remove it.
The underlying technology
Docker is written in the Go programming language and takes advantage of several features of the Linux kernel to deliver its functionality. Docker uses a technology called namespaces to provide the isolated workspace called the container. When you run a container, Docker creates a set of namespaces for that container.
These namespaces provide a layer of isolation. Each aspect of a container runs in a separate namespace and its access is limited to that namespace.
- Install Docker
- Get started with Docker

IMAGES
VIDEO
COMMENTS
A credential presentation gives business owners an opportunity to impress. The credentials PPT is usually the first step when engaging with an audience. It is the perfect communication tool to ...
Agencies use their credentials decks too early in the sales process and expect them to do more than it's designed to do. ... Don't assign the definition of next steps to your client. ... 2020 creds deck, agency creds deck, credentials, credentials presentation, agency credentials, agency pitch, pitch meeting, pitch deck, ...
Template 1: Procurement Services Provider: Our Procurement Company's Credentials. This PPT template is made to exhibit what sets your procurement process apart from others. It also gives you a clear method for expressing your company vision, market value, presence, and registration number details, which are crucial in building trust.
The advertising agency credentials presentation is a crucial tool for showcasing the expertise and value of an agency to potential clients.. It aims to give a swift boost to the brand name and emphasizes the importance of tailoring the presentation to the audience's specific needs and goals.
A credential presentation gives business owners an opportunity to impress. The credentials PPT is usually the first step when engaging with an audience. It is the perfect communication tool to start a customer-business relationship. The bigger objective is to sell a product or service. At times, business owners focus on the bigger picture ...
5. Create impactful slides. A credentials presentation do not have to be a deluge of information and written content. In other words, focus on visual and immersive presentation with less text. Two reasons: By writing what you want to say, you move your audience's attention on the screen as opposed to looking at you.
The features give them the logic, but the benefits stir an emotional response, and it's this that will feed that motivation to purchase. 6. Let your clients do the selling for you. The purpose of a creds deck is to sell. We know it, you know it, and your potential clients know it.
Let me share some common mistakes and solutions to help you hopefully make your credentials presentations more effective. 1. Focus on the purpose of the credentials presentation. Yes, this is like taking a brief about who it is, what they think and feel now, and what we want them to think and feel after seeing the presentation.
Recapped below are our ten tips on developing a strong company credentials presentation to attract interest from Distributors and Buyers anywhere. 1. Just the Facts: Page 1 should include basic company facts. Annual sales, ownership, number of employees, and key categories and brands. 2.
Agency credentials and presentations continue to be a hot topic in the world of agency new business. But what makes a credential valuable? The Future Factory spoke to senior figures in the brand ...
At the end of your presentation or document, you need to include a clear and concise call-to-action which highlights how exactly how you want the potential customer or client to respond. Use this last page of the credentials document and give them a reason to pick up the phone or send an email. Don't have a generic call-to-action.
A credentials document is an essential part of marketing your business, especially if you work in a highly competitive, business-to-business industry. Targeting a specific audience, a credentials document will demonstrate the capabilities of your business, the services you provide, the impact your work can and does have, and why your audience ...
2. Credentials cover page. The cover should contain some branded graphics or imagery that is consistent with your identity, who prepared it and who is it for. And it really helps to have the logo's partnered together side by side on the cover. This promotes the partnership they will be entering into. 3.
A verifiable credential is a tamper-evident credential that has authorship that can be cryptographically verified. Verifiable credentials can be used to build verifiable presentations, which can also be cryptographically verified. The claims in a credential can be about different subjects . data minimization.
Credentials are any certificate, diploma or licence you may have received throughout your career. They indicate your abilities to perform specific tasks, are proof of your academic achievements or certify your authority when training others, for example. They are issued by an organisation with the competence to attest to your qualifications.
Here is a list of steps you can use to write your resume credentials: 1. Identify the best credentials for the job. When you apply for a job, it's important to identify the credentials that are most relevant to the position. This allows the employer to see how you can be a strong fit for their company while keeping your resume short and focused.
• Keep credentials and documentation easily accessible in electronic format • Keep track of malpractice carrier and liability coverage information throughout your career • Pull and review your AMA profile • Self-query the National Practitioner Data Bank (NPDB) • When in doubt -disclose • Leverage your assigned analyst or
A PhD is a research/theory degree/credential - meaning the degree focused on the theory and research methods that are central to the development of knowledge in the discipline. The area in which the PhD was earned (e.g. nursing, education, sociology, anthropology, etc.) is not indicated as part of the credential.
Credential Presentation. In the verifiable credential world, presentation involves the generation of a VP - a verifiable presentation. A VP is generated by a holder - it is a document that wraps a verifiable credential with a new credential that is both fresh and which proves a relationship in the moment between the holder and the original VC ...
You can use ID Wallet to see your verifiable credential data in the Presentation Debugger tool. Conclusion. Verifiable Credentials are digital, cryptographically signed credentials that you can use in many aspects of your life. There are many use cases in healthcare, education, and legal contexts where VCs are extremely useful.
The presentation of credentials. When a new permanent representative assumes office, the mission should request the UNOV Protocol Service to make arrangements for the presentation of credentials. Once a time and date for the presentation of credentials has been arranged, the Chief of Protocol welcomes the newly appointed permanent ...
Examples of Presentation of credentials in a sentence. Presentation of credentials - a government issued form of identification, if in person; or (ii) providing name, position and purpose of inspection if request to enter is made via telephone, email or other form of electronic communication.. Presentation of credentials means the display of the document designating a person as an EPA ...
Define Credentials Presentation. means an oral and/or written presentation made by a Member to a potential client which is limited to information concerning the Member's ownership structure, historical facts concerning the Member, types of services offered by the Member, professional qualifications and/or experience of employees of the Member, information concerning current clients of the ...
Trump: "We had the greatest economy in the history of our country. And we have never done so well. Every- everybody was amazed by it. Other countries were copying us." Trump's claim also falls ...
BACKGROUND: Physical deconditioning induced via spaceflight is most effectively attenuated through in-flight exercise training. Throughout its evolution, NASA has implemented advancements to in-flight exercise countermeasures, culminating in the triad of devices currently used aboard the International Space Station (ISS): a treadmill (T2), cycle ergometer (CEVIS), and resistance exercise ...
The Docker daemon. The Docker daemon (dockerd) listens for Docker API requests and manages Docker objects such as images, containers, networks, and volumes.A daemon can also communicate with other daemons to manage Docker services. The Docker client. The Docker client (docker) is the primary way that many Docker users interact with Docker.When you use commands such as docker run, the client ...