
- Apprentice Lawyer

Cyber Fraud in Banking: Key Takeaways from Jaiprakash Kulkarni Case

Fraud in finance and banking is known. The Jaiprakash Kulkarni & Anr. Vs. Banking Ombudsman & Ors. case highlights the increasing risks of cyber fraud faced by individuals and companies. Here’s an analysis of the key aspects of the case law.
On October 1, 2022, unauthorized beneficiaries were added to the petitioners' bank account without any OTP notification. The following day, ₹76,90,017/- was debited through multiple transactions. The petitioners promptly reported the incident to the Cyber Cell at Worli Police Station, Mumbai and blocked the associated SIM card. On October 3, 2022, they formally notified respondent no.2 (the bank) and filed an FIR with the Cyber Crime Police Station. Subsequently, the petitioners requested a Security Incident Report from the bank and sought an update on the refund process as per RBI’s Customer Protection Circular dated July 6, 2017. Despite follow-ups, the bank neither refunded the amount nor provided a satisfactory update. Consequently, the petitioners filed a complaint with the respondent no.1 (banking ombudsman) on October 12, 2022, which was rejected on January 10, 2023, on the grounds that the transactions were completed with valid credentials known only to the account holder.
Issues involved
1) Unauthorized addition of beneficiaries and subsequent transactions from the petitioners' bank account without any OTP being received, resulting in a financial loss of ₹76,90,017/-.
2) The petitioners claimed that no OTP was received for adding the beneficiaries and that respondent no.2 (the bank) failed to adhere to RBI guidelines on limiting customer liability in unauthorized electronic banking transactions .
3) Banking ombudsman’s rejection of complaint , disregarding the absence of OTPs and the unauthorized beneficiary additions.
4) The petitioners sought relief by quashing the ombudsman’s decision and directing respondent no.2 to refund the debited amount along with interest and compensation as per the RBI Circular.
RBI Regulations and Consumer Protection
To address these issues, the Court relied on several important rules and legal principles:
1) RBI Circular on Customer Protection (July 6, 2017): This circular is crucial in determining the liability of customers and banks in unauthorized electronic banking transactions. It mandates that banks must compensate customers for losses if the breach is due to third-party fraud and the customer has reported the fraud promptly without negligence on their part. The onus is on the banks to prove customer negligence or involvement.
2) Consumer Protection Policy (Unauthorized Electronic Banking Transactions) : Under this policy, customers are not liable for losses due to third party breach, if they report unauthorized transactions promptly and there is no negligence on their part.
3) Two-Factor Authentication (2FA): This security measure requires two separate forms of identification (typically something the user knows and something the user has) to authorize a transaction. Failure to implement 2FA can be seen as a security lapse on the bank's part.
Applying the above rules to the facts, the Court scrutinized the actions and responses of both the petitioners and the bank:
1. Failure in Two-Factor Authentication : On October 1, 2022, unauthorized beneficiaries were added to the petitioner's account without any One-Time Password (OTP) or notification sent to his registered mobile or email. The next day, ₹76,90,017 was fraudulently debited through multiple transactions. The Cyber Cell’s investigation confirmed that no OTPs or transaction alerts were received by the petitioners, directly contradicting the bank’s claim that the transactions were authenticated through valid credentials and 2FA.
2. Petitioners’ Prompt Action : Upon discovering the fraudulent transactions, the petitioners promptly reported the incident to both the Cyber Crime Police and the bank on October 3, 2022. They lodged a First Information Report (FIR) and persistently sought redress from the bank, adhering to the RBI's guidelines for reporting unauthorized transactions. This quick reporting played a critical role in establishing their non-negligence and ensuring their claim for compensation.
3. Inadequate Inquiry by the Banking Ombudsman : The Court highlighted the lackluster approach of the banking ombudsman in investigating the fraud. The ombudsman concluded there was no deficiency in the bank’s service without thoroughly examining whether the transactions were truly authorized by the petitioners. The ombudsman’s reliance on the bank’s assurance of 2FA being used, despite contrary evidence from the Cyber Cell, was deemed insufficient and negligent.
4. RBI’s Support on Zero Liability : The RBI’s affidavit supported the stance that in cases of unauthorized transactions due to third-party fraud, customers should have zero liability, provided they report the incidents promptly and have not contributed to the breach through their actions. The Court found that the petitioners had acted diligently and there was no evidence of negligence or collusion with the fraudsters.
Author's Observations
The Bombay High Court’s decision in Jaiprakash Kulkarni vs Banking Ombudsman, Bank of Baroda & Others underscores the paramount importance of robust security measures and diligent customer protection practices in the banking sector. The Court quashed the banking ombudsman’s order and directed the Bank of Baroda to refund the fraudulently debited amount of ₹76,90,017 to the petitioners, with an interest of 6 per cent per annum from October 2, 2022, until the payment date.
This ruling emphasizes several critical points:
1. Customer Protection: The judgment reaffirms the RBI’s guidelines on zero liability for customers in cases of unauthorized transactions due to third-party fraud. It is a strong reminder that customers must be shielded from losses incurred due to security lapses beyond their control.
2. Bank’s Accountability: The case highlights the necessity for banks to enforce stringent security protocols like 2FA effectively. Any lapses in these measures can expose banks to significant liabilities and damages.
3. Prompt Reporting and Vigilance : Customers are encouraged to report unauthorized transactions promptly. This timely action is crucial in limiting their liability and securing their rights to compensation under the RBI’s framework.
4. Need for thorough Investigation : The Court criticized the banking ombudsman’s inadequate investigation, stressing that thorough and diligent inquiries are essential when addressing claims of unauthorized transactions. This sets a precedent for more rigorous scrutiny in similar future cases.
We believe that this judgment is a crucial step in enhancing the protection of customers in the digital banking ecosystem. It sends a clear message to financial institutions about the importance of robust security measures and the necessity of transparent and thorough handling of fraud claims.
For customers, it reinforces the importance of vigilance in monitoring account activities and reporting suspicious transactions immediately. The court's decision serves as a significant precedent, potentially guiding future cases involving cyber fraud and unauthorized banking transactions.
As the digital landscape continues to evolve, the principles laid down in this case will be instrumental in shaping the policies and practices surrounding customer protection and cyber security in the banking industry.
About the author: Vishwas Chitwar is an Associate at NovoJuris Legal.
Chitwar authored the article with inputs from Sharda Balaji, Managing Partner, NovoJuris Legal.
If you would like your Deals, Columns, Press Releases to be published on Bar & Bench, please fill in the form available here .
Cyber Fraud in Banking: Key Takeaways from Jaiprakash Kulkarni Case Author: Vishwas Chitwar is an Associate at @novojuris Legal. https://t.co/VlWHiCsATh — Deals & Firms by Bar & Bench (@dealsandfirms) July 27, 2024
Subscribe Now! Get features like

- 2024 US Elections
- Assembly Elections 2024
- ₹ 10 Lakh,1" data-value="Loan ₹ 10 Lakh">Loan ₹ 10 Lakh

- Entertainment
- Latest News
- Games & Puzzles
- Diwali 2024
- Israel iran attack news live
- Win iPhone 15
- The Taste of Time
- Web Stories
- Mumbai News
- Bengaluru News
- Daily Digest

Financial fraud top cyber crime in India; UPI, e-banking most targeted: Study
Financial frauds accounted for 75% of cyber crimes in india from jan 2020 to jun 2023, according to a study by an iit kanpur-incubated start-up..
Financial frauds accounted for over 75 per cent of cyber crimes in the country from January 2020 till June 2023, with nearly 50 per cent cases related to UPI and internet banking, according to a new study by an IIT Kanpur-incubated start-up.

Social media-related crimes such as cheating by impersonation, cyber-bullying, sexting and email phishing accounted for 12 per cent of the online offences during the period, the study showed.
The findings have been mentioned by the Future Crime Research Foundation (FCRF), a non-profit start-up incubated at the Indian Institute of Technology (IIT)-Kanpur, in its latest comprehensive whitepaper 'A Deep Dive into Cybercrime Trends Impacting India'.
For online financial frauds, which accounted for the maximum 77.41 per cent offences during the period, the FCRF noted that "this category is a dominant concern, covering fraudulent activities related to online financial transactions".
"Subcategories include debit/credit card fraud, business email compromise, internet banking-related fraud, and the alarmingly prevalent UPI (Unified Payments Interface) fraud (47.25 per cent)", it said.
These figures underscore the need for robust cyber security measures to safeguard financial transactions conducted online, the FCRF said.
Social media-related crimes accounted for 12.02 per cent online offences, according to the whitepaper.
"This category encompasses a wide range of crimes associated with online platforms and social media. Subcategories within this domain include cheating by impersonation, cyber-bullying, sexting, email phishing, and more. While cyber-bullying and impersonation accounted for significant percentages, email phishing and provocative speech for unlawful acts had a comparatively lower impact," it noted.
The FCRF stated that "other notable categories" contributed to nine per cent of the online crimes which delve into several other cybercrime categories with smaller but notable percentages, including online cyber-trafficking, online gambling, ransomware, cryptocurrency crime, and cyber terrorism.
Highlighting the diverse methods cybercriminals use to target digital infrastructure, the whitepaper also flagged that 1.57 per cent online crimes pertained to hacking or damage to computer systems such as unauthorised access, data breach, email hacking and website defacement or hacking.
"It is crucial for law enforcement agencies, individuals, businesses, and policymakers to understand the changing landscape of cybercrimes in India. This report not only highlights the distribution of cybercrimes but also underscores the need for collaborative efforts to combat these threats," FCRF co-founder Harshvardhan Singh said.
Singh added that "as technology continues to advance, so do the tactics of cybercriminals, making it essential for all stakeholders to stay informed and vigilant".
- Cyber Crime
Join Hindustan Times
Create free account and unlock exciting features like.
- Terms of use
- Privacy policy
- Weather Today
- HT Newsletters
- Subscription
- Print Ad Rates
- Code of Ethics
- India vs New Zealand Live Score
- India vs Sri Lanka
- Live Cricket Score
- Cricket Teams
- Cricket Players
- ICC Rankings
- Cricket Schedule
- Shreyas Iyer
- Harshit Rana
- Kusal Mendis
- Ravi Bishnoi
- Rinku Singh
- Riyan Parag
- Washington Sundar
- Avishka Fernando
- Charith Asalanka
- Dasun Shanaka
- Khaleel Ahmed
- Pathum Nissanka
- Other Cities
- Income Tax Calculator
- Petrol Prices
- UGC NET Answer Key 2024 Live
- Diesel Prices
- Silver Rate
- Relationships
- Art and Culture
- Telugu Cinema
- Tamil Cinema
- Study Abroad
- Board Exams
- Exam Results
- Admission News
- Employment News
- Competitive Exams
- BBA Colleges
- Engineering Colleges
- Medical Colleges
- BCA Colleges
- Medical Exams
- Engineering Exams
- Love Horoscope
- Annual Horoscope
- Festival Calendar
- Compatibility Calculator
- Career Horoscope
- Manifestation
- The Economist Articles
- Lok Sabha States
- Lok Sabha Parties
- Lok Sabha Candidates
- Explainer Video
- On The Record
- Vikram Chandra Daily Wrap
- Entertainment Photos
- Lifestyle Photos
- News Photos
- Olympics 2024
- Olympics Medal Tally
- Other Sports
- EPL 2023-24
- ISL 2023-24
- Asian Games 2023
- Public Health
- Economic Policy
- International Affairs
- Climate Change
- Gender Equality
- future tech
- HT Friday Finance
- Explore Hindustan Times
- Privacy Policy
- Terms of Use
- Subscription - Terms of Use
- Technology News
RBI data suggests rise in online payment frauds in India: Reasons and what users should do

Reason for online fraud
How to safeguard.
- Do not share personal information, such as card and bank account details, with anyone.
- Do not share the OTP (One Time Password) received on your phone with anyone.
- Ignore calls, messages and emails that offer gifts, prizes, or discounts.
The Economic Times daily newspaper is available online now.
Bank frauds up nearly 300% in last two years, digital frauds up 708%: rbi.
Fraud cases in Indian banks surged to 36,075 in FY24 from 9,046 in FY22, a nearly 300% increase, while the amount involved dropped by 46.7% to Rs 13,930 crore. Most frauds occurred in digital payments, but the highest value frauds were in loan portfolios, with public banks contributing the most by value.

- A new weapon against online payment frauds: Timely alerts on transactions via UPI, debit card, credit card, Net and mobile banking
Web Development
Intermediate Java Mastery: Method, Collections, and Beyond
By - Metla Sudha Sekhar, IT Specialist and Developer

Artificial Intelligence(AI)
AI for Everyone: Understanding and Applying the Basics on Artificial Intelligence
By - Ritesh Vajariya, Generative AI Expert

Django & PostgreSQL Mastery: Build Professional Web Applications

Master RESTful APIs with Python and Django REST Framework: Web API Development

ESG and Business Sustainability Strategy
By - Vipul Arora, Partner, ESG & Climate Solutions at Sattva Consulting Author I Speaker I Thought Leader

Generative AI for Dynamic Java Web Applications with ChatGPT

Mastering C++ Fundamentals with Generative AI: A Hands-On

Office Productivity
Zero to Hero in Microsoft Excel: Complete Excel guide 2024

Basics of Generative AI : Unveiling Tomorrow's Innovations

Mastering Microsoft Office: Word, Excel, PowerPoint, and 365

Succession Planning Masterclass
By - Nigel Penny, Global Strategy Advisor: NSP Strategy Facilitation Ltd.
Mastering Full Stack Development: From Frontend to Backend Excellence

Intermediate C++ Skills: Master Pointers, Structures and File Stream

Master in Python Language Quickly Using the ChatGPT Open AI

Performance Marketing for eCommerce Brands
By - Zafer Mukeri, Founder- Inara Marketers

ChatGPT Mastery from Zero to Hero: The Complete AI Course

Financial Literacy i.e Lets Crack the Billionaire Code
By - CA Rahul Gupta, CA with 10+ years of experience and Accounting Educator

Human Potential and the Future of Employment
By - Lynda Gratton, Prof. at London Business School, Speaker, Author, Global Thought Leader

JavaScript Essentials: Unlock AI-Driven Insights with ChatGPT

A2Z Of Finance: Finance Beginner Course
By - elearnmarkets, Financial Education by StockEdge
Significant lag
Read more news on.
(Catch all the Business News , Breaking News , Budget 2024 Events and Latest News Updates on The Economic Times .)
Subscribe to The Economic Times Prime and read the ET ePaper online.

Markets are turning volatile, and SME stocks are at maximum risk.

How Elon Musk’s space-age PR will shape the rules of the game in India

Why is one MPC member not sharing the IMF's optimism on growth?

Decoding Nvidia’s and Jensen Huang’s offer to co-develop chip with India

Warehousing is attracting top dollar, but this one factor is hurting developers, investors

In 6 charts: How Ola Electric is losing ground in key EV markets
Find this comment offensive?
Choose your reason below and click on the Report button. This will alert our moderators to take action
Reason for reporting:
Your Reason has been Reported to the admin.

To post this comment you must
Log In/Connect with:
Fill in your details:
Will be displayed
Will not be displayed
Share this Comment:
Uh-oh this is an exclusive story available for selected readers only..
Worry not. You’re just a step away.

Prime Account Detected!
It seems like you're already an ETPrime member with
Login using your ET Prime credentials to enjoy all member benefits
Log out of your current logged-in account and log in again using your ET Prime credentials to enjoy all member benefits.
To read full story, subscribe to ET Prime
₹34 per week
Billed annually at ₹2499 ₹1749
Super Saver Sale - Flat 30% Off
On ET Prime Membership
Unlock this story and enjoy all members-only benefits.
Offer Exclusively For You
Save up to Rs. 700/-
ON ET PRIME MEMBERSHIP
Get 1 Year Free
With 1 and 2-Year ET prime membership
Get Flat 40% Off
Then ₹ 1749 for 1 year
ET Prime at ₹ 49 for 1 month
Diwali Offer
Get flat 20% off on ETPrime
90 Days Prime access worth Rs999 unlocked for you

Exclusive Economic Times Stories, Editorials & Expert opinion across 20+ sectors
Stock analysis. Market Research. Industry Trends on 4000+ Stocks
Get 1 Year Complimentary Subscription of TOI+ worth Rs.799/-
Stories you might be interested in

Role of financial services in the making of Viksit Bharat – Vision 2047

The role of crop-protection industry in driving sustainability in the agriculture sector

From sunrise to sunshine: The contribution of online gaming to the Viksit Bharat journey and India’s cultural power

Decoding the Fifth Industrial Revolution

Climate risk management for financial institutions

Decoding the Uniform Code for Marketing Practices in Medical Devices (UCMPMD)

The three T’s of tax – technology, transparency and trust

Unlocking sustainable value in the oil and gas sector

VIKSIT: An approach for India to achieve USD 1 trillion exports

Chairperson’s Awards: Our Changemakers

Building a better future of work
Loading Results
No Match Found
Combating fraud in the era of digital payments
Introduction.
COVID-19 pandemic, there has been a major spike in the number of digital payments in India. Innovation in the payments landscape, regulatory support, the increase in smartphone penetration and cheaper mobile internet access have played a key role in the adoption of digital transactions and their rapid growth in India. Payment service providers, along with new players and additional investments, have been providing an enhanced seamless user experience at competitive prices, promoting wider adoption of digital payments.
Users have multiple options for digital payments such as cards, wallets, Unified Payments Interface (UPI), mobile banking, QR code and various other methods. UPI has contributed significantly to the growth of digital transactions in India. In 2021–22, UPI accounted for a record 46 billion transactions out of the total volume of 72 billion digital payment transactions. 1 This number was an increase of 109% over the previous year’s volume of 22 billion. Digital payments grew by 64% during the same period.
The increase in the adoption of these advanced payment options, however, has also generated unprecedented opportunities for fraudsters to perpetrate fraud by exploiting digital payment systems and human vulnerabilities.
As per the Reserve Bank of India’s (RBI) Annual Report 2021–22, the volume of frauds reported by financial institutions (FIs) using cards and internet banking was 34% higher at 3,596 in 2021–22 as against 2,677 frauds in 2019–20. The value of fraudulent transactions in 2021–22 was INR 1.55 billion – 20% more than that in 2019–20 (INR 1.29 billion). In terms of value, 01 these card- and internet-related frauds amounted to 0.2% of the total value of fraudulent transactions. Overall, the payment frauds as a percentage of total digital payments in India has increased from 0.008 bps in 2019–20 to 0.0089 bps in 2021–22.
Value of frauds vis-a-vis the digital payments transactions (cards and internet banking)
With the rise in technological advancements, incidents of fraud have also become more organised and sophisticated – for example, targeted hacking into networks and databases, phishing attacks, etc. This has become a major concern among consumers. Specifically, with significant data relating to cards being stored and transferred digitally, fraudsters can attempt to exploit vulnerabilities in the system and gain access to such information for wrongful use.
The changing nature of fraud and increase in fraudulent activities can be attributed to the following factors:
Diversified entry points
Businesses in India have been digitising across their value chains at breakneck speeds. This increases the scope of opportunities for fraudsters and offers them a wider attack surface for exploitation. The common entry points include social media, e-commerce, or services like retail transactions, rideshares and lodging.
Vulnerabilities in the new payment technologies
Due to the expanding digitisation of businesses amid growing competition, the payments industry has come up with multiple payment platform options for customers. However, platforms with weak server-side controls make the payments infrastructure vulnerable to attacks.
Further, the risk of cyberattacks has increased significantly due to more data records – personal and financial information – being stored digitally, and employees connecting remotely through unsecured networks. Customers are also increasingly falling prey to the ‘authorised’ push payment fraud in the new payment technologies.
Lax preparedness of new players
There are multiple new-age digital native start-ups entering the ecosystem, with a lot of customer data at their disposal. However, they lack the wherewithal to handle the muchneeded security aspect.
Lack of customer awareness
Despite increased efforts by payment service providers at customer education, customers often become victims of fraud very easily. This can be attributed to their lack of awareness of the new and advanced payment technologies and fraud tactics associated with them.
Unsecured remote access
With the advent of work from home in the pandemic era, organisations have become more susceptible to payment data leaks owing to remote access to their systems. Default credential setting and open remote access has now become easier outside the firewalled confines of an organisation, thereby helping fraudsters to take control of devices and engage in fraudulent activities.
The advanced techniques used by fraudsters impact customer trust in digital payment instruments. For FIs, fraud may lead to loss of reputation and huge liabilities. Therefore, it is of utmost importance to mitigate and prevent such incidents. Having risk mitigation measures in place can significantly reduce exorbitant operational costs. Such measures eliminate the need to spend time and resources on reviewing every transaction alert. Moreover, these measures safeguard a company’s reputation and, in turn, its customer base, helping it to avoid regulatory actions.
Fraud in digital payments
Frauds, in any country, are driven by multiple factors such as local payment behaviour, customer awareness, security of payment systems, the regulatory environment, maturity of the payments domain, technical advancements and economic development of the country.
The payments ecosystem comprises multiple stakeholders such as banks, networks, payment gateways, channels, sellers, merchants, customers and buyers, which interact with each other. These stakeholders may have risks associated with them.
For example, a single payment from a customer to a merchant involves multiple stakeholders in the payments process flow. When the customer pays the merchant, the relevant information is passed on from the merchant payment gateway and processor to the customer’s issuing bank, through the card association network. Once the customer’s issuing bank authorises the transaction and deems it valid, the payment processor completes the transaction.
During this process, frauds can be perpetrated at any stage. Some common techniques and tricks used by the fraudsters in perpetrating these frauds across the payments ecosystem have been detailed in the following section.
Payments processing cycle using a card
Common fraud typologies.
The RBI's Annual Report 2020—21 suggests a clear increase in the number and value of payment frauds in India. The frauds and mitigation measures for the same have been covered in a press release by the RBI. 2
In the following section, we take a closer look at the common fraud typologies in an Indian context, including common tactics used by fraudsters, along with the payment instruments or channels that are most vulnerable to these types of frauds.
Identity theft/impersonation
Fraudsters acquire users' personal information (e.g. PAN/Aadhaar details or social media credentials) or critical information about their bank accounts in order to gain access and initiate online payments or open a payment account to execute transactions. Personal data of customers is made available on the dark web, enabling fraudsters to carry out this type of fraud. There have been multiple incidents in India involving banks, payments banks and other FinTechs wherein the victims of identity theft have reported that their personal details were used by fraudsters to perform fraudulent transactions, including availing of credit card facility from banks. 3
Fraudsters may also impersonate an authorised official (bank employee, police, Government official, health official, etc.) or the user's trusted acquaintance, and manipulate the user into transferring money.
Phishing/vishing
In India, as the adoption of digital transactions has become more widespread, there has been an increase in the number of phishing and vishing frauds. Fraudsters execute vishing frauds by posing as customer service executives from banks and convincing the unsuspecting customers to complete or update their electronic Know-your-Customer (eKYC) online in order to keep the account active. When the customer performs the process online, the fraudsters obtain confidential information and manage to perform illegal transactions using the OTP shared. Also, the fraudsters do not let the customer hang up the phone lest he/she should come to know about the illegal transaction.
In phishing frauds, the fraudsters send emails or text messages that contain a malicious link which takes the customer to a web page that is deceptively similar in appearance to the actual website of the bank. The customers end up mistaking the fraudulent website for the actual one and enter confidential information, which is then used by the fraudsters to perform illegal transactions.
Web skimming
Web skimming is a hacking technique wherein the fraudsters install malicious software on the payment or checkout pages of an application and obtain confidential payment information. For instance, e-commerce websites employ use of third-party applications, paving the way for fraudsters to install their malicious code into the trusted third-party host site.
There have been multiple reported cases of web skimming in India where fraudsters obtain the card details — such as card number, CW and expiry date — of unsuspecting users through e-commerce websites. The e-commerce websites have been particularly targeted due to their popularity and widespread presence.
By using QR code
The number of Bharat quick response (BQR) codes deployed in India in 2020—21 (49.7 lakh) have increased by 39.3% from 2019—20. At the same time, fraudsters have exploited the use of QR codes for conducting fraudulent transactions.
In many cases, fraudsters send a fake QR code to the unsuspecting customer, scanning which will enable the customer to receive money in his/ her bank account. However, once the code is scanned, the money gets deducted from the customer's account instead. Also, in some cases, the fraudsters replace the physical QR code with their own QR code at shops/ merchant locations, thereby deceiving customers to make payments to the wrong account.
Social engineering
Social engineering attacks generally involve exploiting unsuspecting users by convincing them of a serious issue related to their bank accounts so that the users divulge confidential information. In most cases, the fraudster psychologically manipulates the unsuspecting user into divulging their banking details or convinces them to make payments. The perpetrator generally pretends to be from a trusted organisation or poses as a family member of the user or an employee of an FI.
Account takeover
This type of fraud involves fraudsters trying to take illegitimate control of the user's account by stealing their login credentials and making payments. In most cases, the fraudsters remain unnoticed as they change the details obtained at the first step, before performing payments.
Database breach
Fraudsters, or a group of organised criminals, gain access to the banking systems or payment service provider networks to initiate or alter transactions. The 2016 cyberattack 4 on the Bangladesh Bank, Central Bank of Bangladesh, is a classic example, where organised criminals got access to the bank's credentials and authorised payment transfers.
Remote access assistance
In this type of fraud, the fraudsters convince the user to provide remote access to their device for resolving some technical issues. They often do so by impersonating a member of a laptop servicer's technical support team, or a bank official helping to unblock the user's account or provide KYC support. After gaining remote access, the fraudsters gather all confidential information related to the user's payment accounts and misuse it to make payments.
Several cases have been reported where people receive an SMS asking for the KYC update of their bank account, along with a number to call for assistance. When people call for assistance, the fraudsters ask them to download a remote support application and share a code to receive confidential information and siphon off money from the bank account. 5
Botnet attack
Fraudsters inject malicious software (also known as bots) into a group of computers and link them together to launch coordinated botnet attacks. This allows fraudsters to gain access to the user's devices, and override their existing security methods to record the user's sensitive information. Later, this information is used to conduct fraudulent activities.
Several incidents have taken place where botmasters gained access to private shopping data across various brands and personal computers using bots. These bots are downloaded by an unsuspecting user via pirated software, advertising links, email attachments, etc.
These are some of the common and emerging fraud typologies and methods used by the fraudsters to target various digital payments channels used by Fls in India. Incidents of fraud in digital channels have been on the rise when compared with those in conventional channels. The risks of conventional channels are widely known, and people are aware of the methods to protect themselves against such frauds. However, they lack the experience and awareness when it comes to newer or digital channels.

Use of fraud typologies to perpetrate payments channels
As discussed in the previous section, fraudsters make use of various methods and techniques to carry out malicious activities using various payments channels in India. These activities are often aimed at attacking the payments infrastructure and result in financial losses. Some of the payments channels used by fraudsters are listed below:
UPI payments and wallets
UPI offers multiple payment flows such as QR code scanning, UPI ID- enabled payments or phone number-based payments. Fraudsters often employ various methods in order to trick unsuspecting users. A common method involves sending the user a malicious link guised as a collect request to pay for a product/service.
Many fraudsters create UPI handles with a valid-looking or genuine- appearing name, such as ‘BHEM’/’BHEEM’ or ‘NPIC’, in order to deceive the user, who believes these handles to be authentic and disclose their account details. Most UPI frauds are driven by users’ ignorance and lack of awareness of the platform.
Other common fraud methods used in UPI payments include fraud by using fake QR codes and remote access assistance.
ATMs /point-of-sale (PoS) machines
By using personal data obtained via remote access assistance or skimming devices installed at ATMs/POS machines, fraudsters execute transactions from the user's account. In addition, fraudsters may claim false chargebacks using cards. The common types of fraud perpetrated in ATMs/PoS machines include card skimming and unauthorised access.
Aadhaar-enabled payment system (AePS)
AePS is another mode of payment wherein customers use their Aadhaar for identification at a business correspondent (BC) equipped with a biometric POS in order to perform cash withdrawals. Corrupt BCs can withdraw more than the amount the customer has requested without providing a receipt, and siphon the excess amount. Fraudsters can also clone the fingerprints (biometrics) of customers and withdraw money from the AePS.
Several cases of fraud involving siphoning of Government welfare funds meant for underprivileged beneficiaries using AePS have surfaced in the recent past in the country. Most AePS-enabled frauds are perpetrated due to customers' lack of knowledge and awareness regarding the use of AePS. Fraudsters also hack the database and get unauthorised access to the customer information and perform fraudulent activities through AePS.
Internet banking
Using confidential data such as login credentials obtained through various fraud methods like phishing or remote access assistance, fraudsters execute illegitimate internet banking transactions.
Mobile banking
With an increase in the availability of smartphones and internet penetration, mobiles phones have become the most opted instrument to perform digital transactions. Users have the option of downloading the applications of banking service providers on their mobile device to perform such transactions easily. However, as such channels are vulnerable to fraud, the fraudsters can misuse the user's credentials or personal data to penetrate into the user's banking application.
Prepaid cards
Stolen prepaid card information can be easily used by the fraudsters to make transactions or buy a prepaid card with stolen payment credentials. Prepaid cards preloaded with money are often not linked to any account. Thus, they cannot be tied to any specific user, which makes them vulnerable to fraud.
Future fraud risks
The advancement of new-age technologies has taken the delivery of financial services and the customer experience to the next level. Fls are actively using artificial intelligence, machine learning, big data and natural language processing to redefine their products, service delivery models and the overall customer engagement. However, these emerging technologies are not immune to fraud risks. A few potential fraud risks associated with these technologies are detailed below:
Frauds related to near-field communication (NFC) technology
NFC-enabled cards for contactless payments are comparatively more secure as they employ radio frequency waves instead of internet connectivity. However, one major drawback associated with such cards is the lack of password protection. Fraudsters will exploit this technology as the payment acceptance limit on such transactions continues to increase.
Cryptocurrency frauds
With the increasing public interest around cryptocurrencies, it is only expected that this currency will also be susceptible to malicious attacks and be exploited by attackers and cybercriminals. According to a report released by the Federal Trade Commission (FTC) consumer sentineI, 6 scams in crypto are seeing an exponential rise in the United States, with losses of around USD 80 million from Oct 2020—Mar 2021, which is ten times that of the previous year. The most common and emerging cryptocurrency frauds can be classified as below:
a. Investment scams: With little knowledge of the digital currency market, users or investors are easily tricked into believing the authenticity of a cryptocurrency. New types of coins are introduced every day and released in the market as an initial coin offering (ICO). Fraudsters are creating fake websites that draw investors in these currencies with the promise of substantial returns. As more and more investments come in — inflating the value of the currency — the initial investors pull out their holdings in an act frequently termed as a ‘rug pull’. Once the scammer's money has been pulled out, the platform is taken down, leaving investors with no option to sell their assets.
b. Wallet scams: There are two types of wallets in the crypto world, commonly distinguished by the mode of storage of the currency — online or offline. These are known as hot and cold wallets respectively. Hot wallets are susceptible to potential phishing scams, whereas cold wallets are susceptible to loss of currency when the storage device is lost or the passkey to access it is forgotten.
Phishing scams related to crypto wallets are similar to those involving other types of wallets. In both cases, fraudsters try to retrieve personal information and authentication keys to gain access and steal money from the wallet.
With the increasing use of cryptocurrencies, such frauds are expected to grow in the coming years.
Frauds with the advent of 5G technology
In terms of future technologies, incorporating 5G technology into the payments ecosystem will lead to faster payments. However, it may also present a larger attack surface to fraudsters. The ability of Fls to scale up fraud prevention and detection also be tested. In June 2022, 7 the Indian Government Union Cabinet claimed that the 5G network will provide speed and capacity that would be 10 times higher than that of 4G. As a result, the traditional fraud-identification measures will not be sufficient to combat 5G-initiated frauds. The number of devices with a single credential, speed and low latency of 5G technology will require more advanced methods of fraud detection in order to mitigate and prevent attacks.
Fraud risk management
Fls have started taking a holistic approach towards fraud risk management by gradually shifting from static and standalone fraud detection and monitoring systems to a dynamic enterprise-wide fraud risk management approach that supports them throughout the life cycle of customer transactions. The pandemic increased the volume of digital payments. As a result, the evolving multiple channels of customer engagement and accelerated adoption of new technologies in payments have had a profound impact on how an FI manages its fraud risk.
Fls are increasingly adopting a framework that integrates the people, policy and process, and technology aspects together for a more effective, agile and dynamic anti-fraud response.
The people aspect emphasises the importance of the human aspect in the operationalisation and implementation of a robust fraud risk management framework. The process aspect emphasises the tone at the top — which refers to the commitment of the top management towards robust fraud risk management policy —and enables a strong, anti-fraud response by setting up strategies, policies and procedures. The technology aspect plays a key role in the implementation of a strong fraud risk management framework by using the right technology and tools for fraud prevention and detection.
The end-to-end fraud risk management response of an FI must balance customer experience with fraud control priorities. However, managing fraud risk while improving the customer experience is a major challenge faced by Fls amid the evolving payments landscape. The key aspects of fraud risk management are explained in detail below:
Dedicated fraud control unit (FCU)
Fls should have a dedicated and independent fraud control unit staffed with resources having skills and experience in fraud risk management. Knowledge of all business units, products and services, technologies involved, and complexities of business is equally important for the FCU staff. Specifically, the FCU staff should be familiar with technology, fraud risk and security.
Regular training and awareness
The FCU staff need to get regular training and attend awareness sessions on fraud risk management. This training should cover the following areas:
- governance framework, policies and procedures to prevent and detect fraud risks
- updates on new payments channels and the specific risks associated with them • traditional and emerging fraud risks
- technologies used by Fls for fraud prevention and detection
- fraud detection methods and techniques
- fraud reporting for internal and regulatory compliance perspective.
In addition, an FI should look at the following aspects:
- The audit committee and board of directors should have sufficient oversight of the management's anti-fraud programmes and controls.
- The personnel in the Fls should respond in a timely and appropriate manner to significant control deficiencies, allegations or concerns of fraud, and violations of the code of ethics/conduct.
- The organisation must have an accountability and authority matrix (RACI matrix), and people should be assigned responsibilities to mitigate fraud risks.
Customer awareness
Fls must adopt nuanced measures to enlighten their customers and make them aware of new digital payments channels, products, fraud risks and how to safeguard their payments. As per regulatory directives, Fls should create relevant usage guidelines and training materials for customers to help them use their products. They should also provide all details regarding the process to complain about a digital product or to report any fraudulent or suspicious activity in the account immediately. Moreover, Fls must ensure that their customers are aware of the types of threats that could occur while using digital products and know how to take necessary precautionary measures. Information about the common fraud techniques — such as phishing, vishing, remote access and account takeover — used by criminals to gain fraudulent access to payment and sensitive information about customers must also be provided. Such training and customer awareness programmes will help people to understand the ongoing security concerns in the payments ecosystem and how to minimise fraud risks by staying alert.
It is also important that the customers read the mandated agreements and agree to the terms and conditions before using any payment product and remain vigilant.
Fraud risk governance framework
Setting up a fraud risk governance framework entailing the tone at the top, strategy, risk appetite, roles and responsibilities, accountability fraud mitigation, and fraud reporting is crucial for any FI. The fraud risk management policies and procedures should comprehensively:
- define the fraud risk drivers for Fls (product and services risks, channels, etc.)
- set risk mitigation controls (preventive and detective) in transaction monitoring, risk assessment and testing
- facilitate reporting and customer management.
Risk assessment
It is important for an FI to assess the likelihood and impact and mitigate the fraud risks associated with its business, products and services, and channels. Different areas of business are susceptible to different levels and types of frauds. A typical fraud risk assessment exercise of an FI would involve conducting a detailed assessment of its:
- business risks
- customer risks
- product and services risks
- technology risks
- channel risks
- employee-related risks.
Every new product should undergo a fraud risk vulnerability assessment. For example, fraud risks associated with a new digital account-opening service should be assessed in detail before its given a go-ahead.
Regular fraud risk assessments will provide Fls with the understanding to tailor their anti-fraud programmes in order to mitigate emerging threats, improve customer experience and complement and support business growth.
Overall, the fraud mitigation framework should help an FI identify, prevent, detect and respond to fraud risks. This will also help the organisation to reduce the overall cost of managing fraud risks.
To summarise, Fls need to check that they:
- have a formal and regularly scheduled procedure to perform fraud risk assessments
- assess the design and operating effectiveness of anti-fraud control activities.
Fraud simulation testing
Fraud simulation testing is another proactive measure to assess the process and system's vulnerability to fraud risk. Pseudo fraud scenarios are developed based on the emerging fraud risks and simulated on actual, select transactions to assess if the monitoring controls can detect them.
Investigation and reporting
An independent incident response or investigation team as part of the FCU with investigation skills and experience is key for investigation, identification of control breaches and liaison with regulatory and law enforcement agencies. The team should have knowledge of the current and emerging channels and products. Also, the team should be proactive, and report new risks and frauds identified to senior management on a timely basis. This can be done by leveraging the data obtained from the risk assessments conducted.
Having a technology-enabled risk management system ensures easy identification, management and further mitigation of frauds. Below are some of the technology-enabled measures that Fls can adopt for better fraud risk management.
Advanced analytics
With the help of behavioural analytics, data of the known frauds, customer behaviour, risk and transaction profile can be translated into scenarios to monitor the risks effectively by reducing the response time.
Real-time monitoring
Traditionally, rule-based systems were used to detect fraudulent transactions. However, this methodology yields a high number of false positives, which impacts customer experience due to the long lead times required to prove the authenticity of transactions. In this era where transactions happen in milliseconds, having a real-time fraud detection system becomes a necessity for firms operating in the financial sector. Such a system would help in proactively identifying potential security lapses caused by hackers and fraudsters, and block such transactions to ensure the safety of customers.
Technology plays a pivotal role in real-time monitoring of transactions and subsequent detection of fraudulent activities. AI-/ML-enabled technology systems, along with the rules and scenarios driven by analytics, play a crucial role in proactive risk identification and mitigation in real time while balancing the superior customer experience of a seamless transaction.
Dynamic customer data monitoring
Fls can leverage AI, ML data-driven techniques and high-performing analytical models that work on in-memory computing and use dynamic customer data — such as customer behaviour, profile updates transaction pattern and services availed — to visualise the hidden data patterns and create a risk management tool to highlight the anomalies in the payments.
Data used to build the models is not limited to the transaction data available with Fls. Fls also leverage third-party services to get customers' non- transactional data such as utility payments, salary statements and credit scores to build a 360-degree view of the customer. Hence, this approach will have higher accuracy in flagging any abnormal activity when compared to a traditional rule-based system.
Multi-factor authentication and biometrics
Embedding additional security features such as multi-factor authentication and biometrics during the product design and development stage is effective in ensuring the security of payment systems.
Device monitoring:
Fls can conduct transaction monitoring using device legitimacy monitoring which involves keeping track of the device IP, device geolocation, etc. Such identification techniques add a layer of security to real-time fraud scoring of a transaction. Such methods analyse information related to the device the transaction is requested from and flag any abnormal activity such as a new device login, login from an unusual location, configuration of the device, and IP address changes. This monitoring helps in proactively reaching out to customers to verify transaction authenticity, thereby reducing the associated payment risks. Before setting up a fraud monitoring tool, it is important for an FI to consider the following: • whether the fraud monitoring tool is integrated with all data sources
- whether the fraud monitoring tool implemented is used to detect financial stress/potential fraud across all channels and services
- whether the fraud monitoring tool is configurable — based on financial and non-financial parameters
- whether the fraud monitoring tool has data transformation capabilities (has functionalities around how data from various sources should be transformed/enriched to run the analysis).
Regulatory initiatives for fraud prevention and detection
Regulators in India have also been engaged with Fls in understanding the data and challenges, and supporting a technology-driven framework for effective fraud risk management. There are guidelines for fraud prevention, detection and fraud reporting. The Central Bank regularly publishes guidance for the entities operating in the payments ecosystem to help curb frauds. The RBI master circular for fraud risk management in digital payments is one such recent regulatory guidance. It provides Fls with certain key factors and parameters that they need to consider as part of their fraud monitoring function. Reporting to the Central Payments Fraud Information Registry (CPFIR) is another measure by the RBI to gather insights and data from the industry on frauds, which enables better regulatory framework and decision making regarding fraud monitoring. Regulators also conduct regular workshops to raise fraud management awareness.
Likewise, a group of organisations or industry specialists define industry standards such as Payment Card Industry Data Security Standard (PCI-DSS), Payment Application Data Security Standard (PA-DSS), and ISO27000. Fls are expected to abide by these regulations, standards or policies, as well as have internal policies or frameworks in place to prevent, detect and combat frauds.
Based on the fraud trends over the past few years, Fls must adopt a dynamic fraud risk management framework that balances risk management and customer experience. Further, as Fls adopt new channels for customer engagement, launch new products and services and make new alliances, the alignment of the fraud risk management process, data and systems and the integration of all of these elements will enhance the overall customer experience. Therefore, embedding the fraud management process into overall customer engagement and experience should be the first step forward.
The rapid adoption of new-age payment instruments continues to pose security challenges to Fls. To protect themselves and their customers, Fls must have an agile fraud risk management framework and invest in newer and safer tools and technologies.
Safety of digital payments, assessment of anti-fraud controls, and collection of fraud data to analyse patterns and red flags have been emphasised by the regulators and law enforcement agencies along with the use of new technologies to mitigate fraud risk. The pandemic and increased penetration of internet and mobile phones have only accelerated the use of digital payments, and the dependency on them will continue to increase in future. Thus, spreading knowledge and awareness of new payment technologies, channels and products, and the risks involved — to both customers and employees — is a crucial part of a fraud prevention strategy.
Effective fraud management requires a combination of different measures along the payment value chain. Fls are using fraud orchestration techniques in parallel with their prevention, detection and response measures. Fraud orchestration helps Fls mitigate fraud holistically by providing a comprehensive view of the situation at hand. This is done by gathering information from all payment channels, creating a transparent interface, analysing the payments information using the latest technology, and helping to manage fraud by letting the investigation team take appropriate decisions. This process helps define automated strategies for a better fraud risk management framework.
It is important for Fls to understand the basic building blocks of any payments ecosystem in order to be able to ask the right questions for mitigating fraud and work on the three key elements — people, policy and process, and technology. Also, it is important to continuously review the framework and perform risk assessments to update risk profiles and controls for fraud mitigation.
Payment fraud threats have provided a useful opportunity to Fls to strategically collaborate with technology firms offering new-age solutions in areas related to security, data privacy and fraud risk management. These firms leverage the power of big data, AI and advanced predictive modelling to detect security risks and frauds at various touchpoints in the payments life cycle and help to mitigate them.
As a popular saying goes, ‘risk cannot be eliminated, it can only be mitigated’. Therefore, it is necessary for Fls to continuously assess risks and provide a secure and future-ready transaction environment to customers.
Download Combating fraud in the era of digital payments
With inputs from induvant tomar, neha dharurkar, mayank tiwari, rohit mishra, shashank gupta, nishi sureka and manvitha syamala..
Subscribe to our newsletters
- RBI Annual Report 2021–22
- Consumer Awareness - Cyber Threats and Frauds
- https://rbidocs.rbi.org.in/rdocs/content/pdfs/BEAWARE07032022.pdf
- Information Technology & Cyber Risk in Banking Sector
- FTC Data Shows Huge Spike in Cryptocurrency Investment Scams
- Cabinet approves Auction of IMT/5G Spectrum

Vivek Belgavi
Partner and Leader – FinTech, Alliances and Ecosystems, PwC India

Mihir Gandhi
Partner, Payments Transformation, PwC India

Dhruv Chawla
Partner, Advisory Services, PwC India

© 2018 - 2024 PwC. All rights reserved. PwC refers to the PwC network and/or one or more of its member firms, each of which is a separate legal entity. Please see www.pwc.com/structure for further details.
- Cookies info
- About Site Provider
Cyberfraud, usage intention, and cybersecurity awareness among e-banking users in India: an integrated model approach
- Original Article
- Published: 06 May 2024
Cite this article

- Mohammed Afzal ORCID: orcid.org/0009-0004-0174-5394 1 ,
- Mohd. Shamim Ansari 1 ,
- Naseem Ahmad 2 ,
- Mohammad Shahid 1 &
- Mohd. Shoeb 1
105 Accesses
Explore all metrics
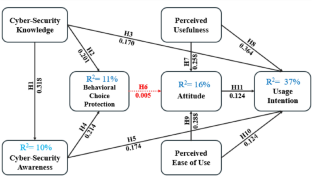
Cyberfraud knows no boundaries and increases with the emergence of technology adoption. The remarkable rise of cybercrime and its catastrophic consequences pose a significant threat to financial institutions in India. Existing literature proves that banks are most affected among other sectors due to their resilience on the Internet, particularly e-Banking platforms. This study incorporates cybersecurity knowledge and awareness with the Technology Acceptance Model (TAM) to examine the association to usage intention among e-Banking users in India. Co-variance-based structural equation modelling (CB-SEM) was used to analyse the sample size of 428 responses. The findings suggested that e-Banking users’ cybersecurity knowledge and awareness positively influence e-Banking usage intention. Users’ behavioural protection is influenced by knowledge and awareness. It was also observed that cybersecurity knowledge, awareness, and behavioural choice protection were consistent with TAM theory. Emerging cyberfraud has become a significant challenge in accepting e-banking platforms. The structural model suggests that cybersecurity awareness among e-Banking users against cyberfraud could help safeguard users’ bank accounts and positively influence usage intention. Cybersecurity awareness must be taught to e-Banking users to counter rising cyberfraud incidents.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Source : Author’s calculation based on survey
Similar content being viewed by others

Appraisal of Electronic Banking Acceptance in Nigeria Amidst Cyber Attacks Using Unified Theory of Acceptance and Use of Technology

Adoption of electronic banking services in India: an extension of UTAUT2 model

Factors Influencing the Adoption of Online Banking in South Africa: An UTAUT Study
ATM banking , short for Automated Teller Machine banking, is a financial service that allows customers to conduct various transactions using automated machines (Nigatu et al. 2023 ). It also offers enhanced accessibility, making banking services more readily available to people in remote or underserved areas. Moreover, ATM banking expedites routine transactions, minimizing queues and wait times, resulting in a smoother and more efficient banking experience for users.
Internet banking , or online banking, refers to the digital banking service that allows customers to manage their finances and conduct various online transactions (A. Bhattacherjee, 2001) . Internet banking also reduces paperwork, minimizes the use of physical resources, and enhances security through encryption and multi-factor authentication, ensuring a safe and efficient banking experience for users.
Mobile banking is a financial service that enables customers to conduct banking transactions and access account information through their mobile devices, such as smartphones or tablets (Shaikh and Karjaluoto 2015 ). Mobile banking also improves financial control by enabling users to track expenses and manage budgets effectively. It allows users to manage their finances anytime and anywhere, providing flexibility and reducing the need to visit a physical bank branch.
Encompasses the importance of users' comprehension to adhering to information security practices.
Behavioural aspects encompass preventive control, predictability, ease of reduction, observability, reversibility and the catastrophic potential of cybersecurity threats, as identified in the study conducted by Huang et al. ( 2011 ). Individuals often emphasize cybersecurity risks as a means to anticipate potential threats, fostering a sense of security imagination and fictional fear (Bruijn and Janssen 2017 ).
It represents the extent to which users believe that using electronic banking will enhance their banking transactions.
It denotes positive or negative perception of a particular behaviour (Ajzen 1991 ; Davis 1989 ). It is influenced by an individual's beliefs and can lead to positive or negative attitudes towards the outcomes of their actions.
Abawajy, J. 2014. User preference of cyber security awareness delivery methods. Behaviour & Information Technology 33 (3): 237–248. https://doi.org/10.1080/0144929X.2012.708787 .
Article Google Scholar
Abikari, M., P. Öhman, and D. Yazdanfar. 2023. Negative emotions and consumer behavioural intention to adopt emerging e-banking technology. Journal of Financial Services Marketing 28 (4): 691–704. https://doi.org/10.1057/s41264-022-00172-x .
Adaba, G.B., D.A. Ayoung, and P. Abbott. 2019. Exploring the contribution of mobile money to well-being from a capability perspective. The Electronic Journal of Information Systems in Developing Countries 85 (4): e12079. https://doi.org/10.1002/isd2.12079 .
Adholiya, A., and S. Adholiya. 2019. A study on cyber security practices and tips awareness among e-banking services users of Udaipur, Rajasthan. International Journal of Scientific Research in Multidisciplinary Studies 5 (8): 148–154.
Google Scholar
Ahamed, B., M.R.H. Polas, A.I. Kabir, A.SMd. Sohel-Uz-Zaman, A.A. Fahad, S. Chowdhury, and M. Rani Dey. 2024. Empowering students for cybersecurity awareness management in the emerging digital era: the role of cybersecurity attitude in the 4.0 industrial revolution era. SAGE Open 14 (1): 21582440241228920. https://doi.org/10.1177/21582440241228920 .
Ajzen, I. 1991. The theory of planned behavior. Organizational Behavior and Human Decision Processes 50: 179–211. https://doi.org/10.1016/0749-5978(91)90020-T .
Ajzen, I., and M. Fishbein. 1980. Understanding attitudes and predicting social behavior (Pbk. ed). Prentice-Hall.
Al-Ajam, A.S., and K. Md Nor. 2015. Challenges of adoption of internet banking service in Yemen. International Journal of Bank Marketing 33 (2): 178–194. https://doi.org/10.1108/IJBM-01-2013-0001 .
Albaroodi, H.A., M. Abomaali, and S. Manickam. 2020. Iraqi’s organizations awareness to prompt open source cloud computing (OSCC) in their service: a study. In Advances in cyber security , ed. M. Anbar, N. Abdullah, and S. Manickam, 305–319. Springer. https://doi.org/10.1007/978-981-15-2693-0_22 .
Chapter Google Scholar
Albastaki, Y.A. 2023. Toward a cashless society: assessing the acceptance of Bahrain BenefitPay using TAM and SEM. Competitiveness Review: an International Business Journal . https://doi.org/10.1108/CR-12-2022-0184 .
Aldiabat, K., A. Al-Gasaymeh, and A. Kwekha Rashid. 2019. The effect of mobile banking application on customer interaction in the jordanian banking industry. International Journal of Interactive Mobile Technologies (iJIM) 13: 37. https://doi.org/10.3991/ijim.v13i02.9262 .
Alfadda, H.A., and H.S. Mahdi. 2021. Measuring students’ use of zoom application in language course based on the technology acceptance model (TAM). Journal of Psycholinguistic Research 50 (4): 883–900. https://doi.org/10.1007/s10936-020-09752-1 .
Ali, M., S.A. Raza, F. Hakim, C.-H. Puah, and L.Y. Chaw. 2022. An integrated framework for mobile payment in Pakistan: drivers, barriers, and facilitators of usage behavior. Journal of Financial Services Marketing . https://doi.org/10.1057/s41264-022-00199-0 .
Almaiah, M.A., A. Al-Zahrani, O. Almomani, and A.K. Alhwaitat. 2021. Classification of cyber security threats on mobile devices and applications. In Artificial intelligence and blockchain for future cybersecurity applications , ed. Y. Maleh, Y. Baddi, M. Alazab, L. Tawalbeh, and I. Romdhani, 107–123. Springer International Publishing. https://doi.org/10.1007/978-3-030-74575-2_6 .
Alshurideh, M.T., B. Al Kurdi, R. Masa’deh, and S.A. Salloum. 2021. The moderation effect of gender on accepting electronic payment technology: a study on United Arab Emirates consumers. Review of International Business and Strategy 31 (3): 375–396. https://doi.org/10.1108/RIBS-08-2020-0102 .
Ananda, S., S. Devesh, and A.M. Al Lawati. 2020. What factors drive the adoption of digital banking? An empirical study from the perspective of Omani retail banking. Journal of Financial Services Marketing 25 (1): 14–24. https://doi.org/10.1057/s41264-020-00072-y .
Anderson, C.L., and R. Agarwal. 2010. Practicing safe computing: a multimethod empirical examination of home computer user security behavioral intentions. MIS Quarterly 34 (3): 613–643. https://doi.org/10.2307/25750694 .
Anderson, J.C., and D.W. Gerbing. 1988. Structural equation modeling in practice: a review and recommended two-step approach. Psychological Bulletin 103 (3): 411–423. https://doi.org/10.1037/0033-2909.103.3.411 .
Arpaci, I. 2017. Antecedents and consequences of cloud computing adoption in education to achieve knowledge management. Computers in Human Behavior 70: 382–390. https://doi.org/10.1016/j.chb.2017.01.024 .
Asadi, Z., M. Abdekhoda, and H. Nadrian. 2020. Cloud computing services adoption among higher education faculties: development of a standardized questionnaire. Education and Information Technologies . https://doi.org/10.1007/s10639-019-09932-0 .
Aslam, W., M. Ham, and I. Arif. 2017. Consumer behavioral intentions towards mobile payment services: an empirical analysis in Pakistan. Tržište/market 29 (2): 161–176.
Asnakew, Z.S. 2020. Customers’ continuance intention to use mobile banking: development and testing of an integrated model. The Review of Socionetwork Strategies 14 (1): 123–146. https://doi.org/10.1007/s12626-020-00060-7 .
Ayo, C.K., A.A. Oni, O.J. Adewoye, and I.O. Eweoya. 2016. E-banking users’ behaviour: E-service quality, attitude, and customer satisfaction. International Journal of Bank Marketing 34 (3): 347–367. https://doi.org/10.1108/IJBM-12-2014-0175 .
Bada, M., A. M. Sasse, and J. R. C. Nurse. 2019. Cyber security awareness campaigns: why do they fail to change behaviour? ( arXiv:1901.02672 ). arXiv. https://doi.org/10.48550/arXiv.1901.02672 .
Basu, B., M.P. Sebastian, and A.K. Kar. 2024. What affects the promoting intention of mobile banking services? Insights from mining consumer reviews. Journal of Retailing and Consumer Services 77: 103695. https://doi.org/10.1016/j.jretconser.2023.103695 .
Zee Business. 2023, May 30. RBI Annual Report 2022–23: Number of frauds in banking sector rose in FY23, amount involved halved to Rs 30,252 crore . Zee Business. https://www.zeebiz.com/personal-finance/banking/news-rbi-reserve-bank-of-india-rbi-annual-report-economy-indian-economy-rbi-governor-rbi-shaktikanta-das-rbi-data-rbi-private-sector-banks-digital-payments-237869 .
Cain, A.A., M.E. Edwards, and J.D. Still. 2018. An exploratory study of cyber hygiene behaviors and knowledge. Journal of Information Security and Applications 42: 36–45. https://doi.org/10.1016/j.jisa.2018.08.002 .
Campbell, C.C. 2018. Solutions for counteracting human deception in social engineering attacks. Information Technology & People 32 (5): 1130–1152. https://doi.org/10.1108/ITP-12-2017-0422 .
Chauhan, V., and D. V. Choudhary. 2015. Internet banking: challenges and opportunities in indian context. https://www.semanticscholar.org/paper/Internet-Banking-%3A-Challenges-and-Opportunities-in-Chauhan-Choudhary/4512db0b85d533ee7a28105e013b5391abfe4bf1 .
Cybercrimemag.com. 2020, November 13. Cybercrime to cost the world $10.5 trillion annually By 2025. Cybercrime Magazine . https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021/ .
Dangaiso, P., P. Mukucha, F. Makudza, T. Towo, K. Jonasi, and D.C. Jaravaza. 2024. Examining the interplay of internet banking service quality, e-satisfaction, e-word of mouth and e-retention: a post pandemic customer perspective. Cogent Social Sciences 10 (1): 2296590. https://doi.org/10.1080/23311886.2023.2296590 .
Daragmeh, A., J. Sági, and Z. Zéman. 2021. Continuous intention to use e-wallet in the context of the COVID-19 pandemic: integrating the health belief model (HBM) and technology continuous theory (TCT). Journal of Open Innovation: Technology, Market, and Complexity 7 (2): 2. https://doi.org/10.3390/joitmc7020132 .
Darem, A.A., A.A. Alhashmi, T.M. Alkhaldi, A.M. Alashjaee, S.M. Alanazi, and S.A. Ebad. 2023. Cyber threats classifications and countermeasures in banking and financial sector. IEEE Access 11: 125138–125158. https://doi.org/10.1109/ACCESS.2023.3327016 .
Davis, F.D. 1989. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly 13 (3): 319–340. https://doi.org/10.2307/249008 .
Davis, F.D., R.P. Bagozzi, and P.R. Warshaw. 1989. User acceptance of computer technology: a comparison of two theoretical models. Management Science 35 (8): 982–1003.
de Bruijn, H., and M. Janssen. 2017. Building cybersecurity awareness: the need for evidence-based framing strategies. Government Information Quarterly 34 (1): 1–7. https://doi.org/10.1016/j.giq.2017.02.007 .
Deb, M., and E. Lomo-David. 2014. An empirical examination of customers’ adoption of m-banking in India. Marketing Intelligence & Planning 32 (4): 475–494. https://doi.org/10.1108/MIP-07-2013-0119 .
Fahad, and M. Shahid. 2022. Exploring the determinants of adoption of unified payment interface (UPI) in India: a study based on diffusion of innovation theory. Digital Business 2 (2): 100040. https://doi.org/10.1016/j.digbus.2022.100040 .
Farzianpour, F., M. Pishdar, M.D. Shakib, and M.R.S.H. Toloun. 2014. Consumers’perceived risk and its effect on adoption of online banking services. American Journal of Applied Sciences 11 (1): 47–56. https://doi.org/10.3844/ajassp.2014.47.56 .
Fatokun Faith, B., Z.A. Long, and S. Hamid. 2024. Promoting cybersecurity knowledge via gamification: an innovative intervention design. Third International Conference on Distributed Computing and High Performance Computing (DCHPC) 2024: 1–8. https://doi.org/10.1109/DCHPC60845.2024.10454080 .
Fornell, C., and D.F. Larcker. 1981. Evaluating structural equation models with unobservable variables and measurement error. Journal of Marketing Research 18 (1): 39–50. https://doi.org/10.2307/3151312 .
Gefen, D., E. Rigdon, and D. Straub. 2011. An update and extension to sem guidelines for administrative and social science research. Editorial comment. MIS Quarterly . https://doi.org/10.2307/23044042 .
Giovanis, A.N., S. Binioris, and G. Polychronopoulos. 2012. An extension of TAM model with IDT and security/privacy risk in the adoption of internet banking services in Greece. EuroMed Journal of Business 7 (1): 24–53. https://doi.org/10.1108/14502191211225365 .
Glanz, K., B.K. Rimer, and K. Viswanath. 2008. Health behavior and health education: theory, research, and practice . John Wiley & Sons.
Gopi, M., and T. Ramayah. 2007. Applicability of theory of planned behavior in predicting intention to trade online: some evidence from a developing country. International Journal of Emerging Markets 2 (4): 348–360. https://doi.org/10.1108/17468800710824509 .
Hadlington, L. 2017. Human factors in cybersecurity; examining the link between Internet addiction, impulsivity, attitudes towards cybersecurity, and risky cybersecurity behaviours. Heliyon 3 (7): e00346. https://doi.org/10.1016/j.heliyon.2017.e00346 .
Hair, J.F., G.T.M. Hult, C.M. Ringle, M. Sarstedt, and K.O. Thiele. 2017. Mirror, mirror on the wall: a comparative evaluation of composite-based structural equation modeling methods. Journal of the Academy of Marketing Science 45 (5): 616–632. https://doi.org/10.1007/s11747-017-0517-x .
Hakimi, T.I., J.A. Jaafar, and N.A.A. Aziz. 2023. What factors influence the usage of mobile banking among digital natives? Journal of Financial Services Marketing 28 (4): 763–778. https://doi.org/10.1057/s41264-023-00212-0 .
Hanafizadeh, P., M. Behboudi, A. Abedini Koshksaray, and M. Jalilvand Shirkhani Tabar. 2014. Mobile-banking adoption by Iranian bank clients. Telematics and Informatics 31 (1): 62–78. https://doi.org/10.1016/j.tele.2012.11.001 .
Hassan, H., and V. Wood. 2019. Does country culture influence consumers’ perceptions toward mobile banking? A comparison between Egypt and The United States. Telematics and Informatics 46: 101312. https://doi.org/10.1016/j.tele.2019.101312 .
Ho, J.C., C.-G. Wu, C.-S. Lee, and T.-T.T. Pham. 2020. Factors affecting the behavioral intention to adopt mobile banking: an international comparison. Technology in Society 63: 101360. https://doi.org/10.1016/j.techsoc.2020.101360 .
Hong, Y., M. Xu, and S. Furnell. 2023. Situational support and information security behavioural intention: a comparative study using conservation of resources theory. Behaviour & Information Technology . https://doi.org/10.1080/0144929X.2023.2177825 .
Hu, L., and P.M. Bentler. 1999. Cutoff criteria for fit indexes in covariance structure analysis: conventional criteria versus new alternatives. Structural Equation Modeling: A Multidisciplinary Journal 6 (1): 1–55. https://doi.org/10.1080/10705519909540118 .
Huang, D.-L., P.-L. Patrick Rau, G. Salvendy, F. Gao, and J. Zhou. 2011. Factors affecting perception of information security and their impacts on IT adoption and security practices. International Journal of Human-Computer Studies 69 (12): 870–883. https://doi.org/10.1016/j.ijhcs.2011.07.007 .
Hui, S.C., M.Y. Kwok, E.W.S. Kong, and D.K.W. Chiu. 2023. Information security and technical issues of cloud storage services: a qualitative study on university students in Hong Kong. Library Hi Tech, Ahead-of-Print(Ahead-of-Print) . https://doi.org/10.1108/LHT-11-2022-0533 .
Hwang, I., R. Wakefield, S. Kim, and T. Kim. 2021. Security awareness: the first step in information security compliance behavior. Journal of Computer Information Systems 61 (4): 345–356. https://doi.org/10.1080/08874417.2019.1650676 .
Ismail Hussien, M., and R. Abd El Aziz. 2013. Investigating e-banking service quality in one of Egypt’s banks: a stakeholder analysis. The TQM Journal 25 (5): 557–576. https://doi.org/10.1108/TQM-11-2012-0086 .
Iyengar, S.S., and M.R. Lepper. 2000. When choice is demotivating: can one desire too much of a good thing? Journal of Personality and Social Psychology 79 (6): 995–1006. https://doi.org/10.1037/0022-3514.79.6.995 .
Jibril, A.B., M.A. Kwarteng, R.K. Botchway, J. Bode, and M. Chovancova. 2020a. The impact of online identity theft on customers’ willingness to engage in e-banking transaction in Ghana: a technology threat avoidance theory. Cogent Business & Management 7 (1): 1832825. https://doi.org/10.1080/23311975.2020.1832825 .
Jibril, A.B., M.A. Kwarteng, M. Chovancová, and R. Denanyoh. 2020b. Customers’ perception of cybersecurity threats toward e-banking adoption and retention: a conceptual study. Academic Conferences and Publishing International Limited. https://doi.org/10.34190/ICCWS.20.020 .
Jibril, A.B., M.A. Kwarteng, F. Nwaiwu, C. Appiah-Nimo, M. Pilik, and M. Chovancova. 2020c. Online identity theft on consumer purchase intention: a mediating role of online security and privacy concern. In Responsible design, implementation and use of information and communication technology , ed. M. Hattingh, M. Matthee, H. Smuts, I. Pappas, Y.K. Dwivedi, and M. Mäntymäki, 147–158. Switzerland: Springer International Publishing. https://doi.org/10.1007/978-3-030-45002-1_13 .
Kala Kamdjoug, J.R., S.-L. Wamba-Taguimdje, S.F. Wamba, and I.B. Kake. 2021. Determining factors and impacts of the intention to adopt mobile banking app in Cameroon: case of SARA by afriland First Bank. Journal of Retailing and Consumer Services 61: 102509. https://doi.org/10.1016/j.jretconser.2021.102509 .
Kashyap, S., S. Gupta, and T. Chugh. 2023. An empirical assessment of customer satisfaction of internet banking service quality—Hybrid model approach. International Journal of Quality & Reliability Management 41 (1): 360–391. https://doi.org/10.1108/IJQRM-04-2022-0125 .
Kaur, J., and N. Mustafa. 2013. Examining the effects of knowledge, attitude and behaviour on information security awareness: a case on SME. International Conference on Research and Innovation in Information Systems (ICRIIS) 2013: 286–290. https://doi.org/10.1109/ICRIIS.2013.6716723 .
Kaur, S.J., L. Ali, M.K. Hassan, and M. Al-Emran. 2021. Adoption of digital banking channels in an emerging economy: exploring the role of in-branch efforts. Journal of Financial Services Marketing 26 (2): 107–121. https://doi.org/10.1057/s41264-020-00082-w .
Khalek, S.A., C.K. Behera, and T. Samanta. 2023. An integrated framework for understanding information disclosure behaviour in mobile payment services. Journal of Financial Services Marketing . https://doi.org/10.1057/s41264-023-00257-1 .
Khan, E.A., and M. Quaddus. 2015. Examining the influence of business environment on socio-economic performance of informal microenterprises: content analysis and partial least square approach. International Journal of Sociology and Social Policy 35 (3/4): 273–288. https://doi.org/10.1108/IJSSP-02-2014-0016 .
Kopp, E., L. Kaffenberger, and C. Wilson. 2017. Cyber risk, market failures, and financial stability. IMF. https://www.imf.org/en/Publications/WP/Issues/2017/08/07/Cyber-Risk-Market-Failures-and-Financial-Stability-45104 .
Krejcie, R.V., and D.W. Morgan. 1970. Determining sample size for research activities. Educational and Psychological Measurement . https://doi.org/10.1177/001316447003000308 .
Kruzikova, A., M. Muzik, L. Knapova, L. Dedkova, D. Smahel, and V. Matyas. 2024. Two-factor authentication time: how time-efficiency and time-satisfaction are associated with perceived security and satisfaction. Computers & Security 138: 103667. https://doi.org/10.1016/j.cose.2023.103667 .
Kumar, R.P., A. Banerjee, Z. Al-Salti, and S. Ananda. 2023. Technology acceptance model and customer engagement: mediating role of customer satisfaction. Journal of Financial Services Marketing . https://doi.org/10.1057/s41264-023-00256-2 .
Lee, M.-C. 2009. Factors influencing the adoption of internet banking: an integration of TAM and TPB with perceived risk and perceived benefit. Electronic Commerce Research and Applications 8 (3): 130–141. https://doi.org/10.1016/j.elerap.2008.11.006 .
Lee, J., J. Kim, and J.Y. Choi. 2019. The adoption of virtual reality devices: the technology acceptance model integrating enjoyment, social interaction, and strength of the social ties. Telematics and Informatics 39: 37–48.
Lewis, J. A., and S. Baker. 2013. The economic impact of cybercrime and cyber espionage . https://www.csis.org/analysis/economic-impact-cybercrime-and-cyber-espionage .
Liao, Y.-K., H.-L.T. Nguyen, T.C. Dao, P.-T.T. Nguyen, and H. Sophea. 2023. The antecedents of customers’ attitude and behavioral intention of using e-banking: the moderating roles of social influence and customers’ traits. Journal of Financial Services Marketing . https://doi.org/10.1057/s41264-023-00254-4 .
Limna, P., T. Kraiwanit, and S. Siripipattanakul. 2022. The relationship between cyber security knowledge, awareness and behavioural choice protection among mobile banking users in Thailand. International Journal of Computing Sciences Research 7: 1133–1151.
Limna, P., T. Kraiwanit, S. Siripipattanakul, P. Limna, T. Kraiwanit, and S. Siripipattanakul. 2023. The relationship between cyber security knowledge, awareness and behavioural choice protection among mobile banking users in Thailand. International Journal of Computing Sciences Research 7: 1133–1151.
Lin, H.-F. 2011. An empirical investigation of mobile banking adoption: the effect of innovation attributes and knowledge-based trust. International Journal of Information Management—INT J INFORM MANAGE 31: 252–260. https://doi.org/10.1016/j.ijinfomgt.2010.07.006 .
Lisha, C., C.F. Goh, S. Yifan, and A. Rasli. 2017. Integrating guanxi into technology acceptance: an empirical investigation of WeChat. Telematics and Informatics 34 (7): 1125–1142. https://doi.org/10.1016/j.tele.2017.05.003 .
Lu, Y., S. Yang, P.Y.K. Chau, and Y. Cao. 2011. Dynamics between the trust transfer process and intention to use mobile payment services: a cross-environment perspective. Information & Management 48 (8): 393–403. https://doi.org/10.1016/j.im.2011.09.006 .
Lynn, T., G. Fox, A. Gourinovitch, and P. Rosati. 2020. Understanding the determinants and future challenges of cloud computing adoption for high performance computing. Future Internet 12 (8): 8. https://doi.org/10.3390/fi12080135 .
Maalem Lahcen, R.A., B. Caulkins, R. Mohapatra, and M. Kumar. 2020. Review and insight on the behavioral aspects of cybersecurity. Cybersecurity 3 (1): 10. https://doi.org/10.1186/s42400-020-00050-w .
Mamonov, S., and R. Benbunan-Fich. 2018. The impact of information security threat awareness on privacy-protective behaviors. Computers in Human Behavior 83: 32–44. https://doi.org/10.1016/j.chb.2018.01.028 .
Martins, C., T. Oliveira, and A. Popovič. 2014. Understanding the Internet banking adoption: a unified theory of acceptance and use of technology and perceived risk application. International Journal of Information Management 34 (1): 1–13. https://doi.org/10.1016/j.ijinfomgt.2013.06.002 .
McAfee. (2020). Study: $100 billion lost annually to cyber attacks | 2013–07–22 | Security Magazine . https://www.securitymagazine.com/articles/84549-study-100-billion-lost-annually-to-cyber-attacks .
McCrohan, K.F., K. Engel, and J.W. Harvey. 2010. Influence of awareness and training on cyber security. Journal of Internet Commerce 9 (1): 23–41. https://doi.org/10.1080/15332861.2010.487415 .
Melović, B., D. Šehović, V. Karadžić, M. Dabić, and D. Ćirović. 2021. Determinants of Millennials’ behavior in online shopping—implications on consumers’ satisfaction and e-business development. Technology in Society 65: 101561. https://doi.org/10.1016/j.techsoc.2021.101561 .
Mishra, B., and A. Prashar. 2021. Customers’ readiness for a paradigm shift towards cyberspace: an exploratory investigation in Indian retail banking. International Journal of Financial Innovation in Banking 3 (1): 1–25. https://doi.org/10.1504/IJFIB.2021.114924 .
Mishra, A., Y.I. Alzoubi, M.J. Anwar, and A.Q. Gill. 2022. Attributes impacting cybersecurity policy development: an evidence from seven nations. Computers & Security 120: 102820. https://doi.org/10.1016/j.cose.2022.102820 .
Montazemi, A.R., and H. Qahri-Saremi. 2015. Factors affecting adoption of online banking: a meta-analytic structural equation modeling study. Information & Management 52 (2): 210–226. https://doi.org/10.1016/j.im.2014.11.002 .
Mou, J., D.-H. Shin, and J. Cohen. 2017. Understanding trust and perceived usefulness in the consumer acceptance of an e-service: a longitudinal investigation. Behaviour & Information Technology 36 (2): 125–139. https://doi.org/10.1080/0144929X.2016.1203024 .
Muñoz-Leiva, F., S. Climent-Climent, and F. Liébana-Cabanillas. 2017. Determinants of intention to use the mobile banking apps: an extension of the classic TAM model. Spanish Journal of Marketing - ESIC 21 (1): 25–38. https://doi.org/10.1016/j.sjme.2016.12.001 .
Naeem, M., S.T. Jawaid, and S. Mustafa. 2022. Evolution of modified TAM associated with e-banking services adoption: a systematic PRISMA review from 1975 to 2021. Journal of Modelling in Management 18 (3): 942–972. https://doi.org/10.1108/JM2-10-2021-0251 .
Namahoot, K.S., and T. Laohavichien. 2018. Assessing the intentions to use internet banking: the role of perceived risk and trust as mediating factors. International Journal of Bank Marketing 36 (2): 256–276. https://doi.org/10.1108/IJBM-11-2016-0159 .
Naz, Z. 2023, July 14. Cybersecurity in banking sector: importance, threats, challenges . https://www.knowledgehut.com/blog/security/cyber-security-in-banking .
Nazaritehrani, A., and B. Mashali. 2020. Development of E-banking channels and market share in developing countries. Financial Innovation 6 (1): 12. https://doi.org/10.1186/s40854-020-0171-z .
Nigatu, A.G., A.A. Belete, and G.M. Habtie. 2023. Effects of automated teller machine service quality on customer satisfaction: Evidence from commercial bank of Ethiopia. Heliyon 9 (8): e19132. https://doi.org/10.1016/j.heliyon.2023.e19132 .
Ntsiful, A., M.A. Kwarteng, A.B. Jibril, B. Popesko, and M. Pilik. 2020. Factors driving the adoption of mobile banking app: an empirical assessment in the less digitalized economy. In Re-imagining diffusion and adoption of information technology and systems: a continuing conversation , ed. S.K. Sharma, Y.K. Dwivedi, B. Metri, and N.P. Rana, 114–125. Switzerland: Springer International Publishing. https://doi.org/10.1007/978-3-030-64861-9_11 .
Nwaiwu, F., M. A. Kwarteng, A. B. Jibril, L. Burita, and M. Pilik. 2020. Impact of security and trust as factors that influence the adoption and use of digital technologies that generate, collect and transmit user data. In Proceedings of the 15th International Conference on Cyber Warfare and Security , ICCWS 2020. https://doi.org/10.34190/ICCWS.20.016 .
O’Leary-Kelly, S.W., and R.J. Vokurka. 1998. The empirical assessment of construct validity. Journal of Operations Management 16 (4): 387–405. https://doi.org/10.1016/S0272-6963(98)00020-5 .
Pal, A., T. Herath, R. De’, and H. Raghav Rao. 2021. Why do people use mobile payment technologies and why would they continue? An examination and implications from India. Research Policy 50 (6): 104228. https://doi.org/10.1016/j.respol.2021.104228 .
Paltayian, G., A. Georgiou, and K. Gotzamani. 2023. A combined QFD-AHP decision-making tool for the investigation and improvement of e-banking usage. International Journal of Quality & Reliability Management 41 (1): 150–172. https://doi.org/10.1108/IJQRM-02-2021-0030 .
Patidar, N., and A. Sen. 2022. A study of cyber-defense strategies adopted by major public and private sector banks of India. International Conference on Decision Aid Sciences and Applications (DASA) 2022: 551–555. https://doi.org/10.1109/DASA54658.2022.9765304 .
Paullay, I.M., G.M. Alliger, and E.F. Stone-Romero. 1994. Construct validation of two instruments designed to measure job involvement and work centrality. Journal of Applied Psychology 79 (2): 224–228. https://doi.org/10.1037/0021-9010.79.2.224 .
Podsakoff, P.M., S.B. MacKenzie, J.-Y. Lee, and N.P. Podsakoff. 2003. Common method biases in behavioral research: a critical review of the literature and recommended remedies. Journal of Applied Psychology 88 (5): 879–903. https://doi.org/10.1037/0021-9010.88.5.879 .
Precedence Research. 2022. E-banking market size, share, growth, trends|report 2022–2030. https://www.precedenceresearch.com/e-banking-market .
Rajput, B. 2020. Cyber economic crime typology. In Cyber economic crime in India: an integrated model for prevention and investigation , ed. B. Rajput, 79–96. Switzerland: Springer International Publishing. https://doi.org/10.1007/978-3-030-44655-0_5 .
Ranjan, S., D. R. Gupta, and D. A. Gupta. 2020. Artificial intelligence in financial acumen: challenges and opportunities.
Raza, S.A., A. Umer, and N. Shah. 2017. New determinants of ease of use and perceived usefulness for mobile banking adoption. International Journal of Electronic Customer Relationship Management 11 (1): 44–65. https://doi.org/10.1504/IJECRM.2017.086751 .
Rehman, Z.U., and F.A. Shaikh. 2020. Critical factors influencing the behavioral intention of consumers towards mobile banking in Malaysia. Engineering, Technology & Applied Science Research 10 (1): 5265–5269. https://doi.org/10.48084/etasr.3320 .
Rekha, I.S., S. Basri, and T.C. Kavitha. 2020. Acceptance of internet banking: comparing six theoretical models. Indian Journal of Finance 14 (3): 3. https://doi.org/10.17010/ijf/2020/v14i3/151073 .
Rodríguez-Ardura, I., A. Meseguer-Artola, I. Rodríguez-Ardura, and A. Meseguer-Artola. 2020. Editorial: how to prevent, detect and control common method variance in electronic commerce research. Journal of Theoretical and Applied Electronic Commerce Research 15 (2): i–v. https://doi.org/10.4067/S0718-18762020000200101 .
Roy, B.K. 1982. Population regionals—A perspective in geographic space of India. GeoJournal 6 (2): 173–182. https://doi.org/10.1007/BF00185540 .
Ru, X., S. Wang, Q. Chen, and S. Yan. 2018. Exploring the interaction effects of norms and attitudes on green travel intention: an empirical study in eastern China. Journal of Cleaner Production 197: 1317–1327. https://doi.org/10.1016/j.jclepro.2018.06.293 .
Sadhya, D., and T. Sahu. 2024. A critical survey of the security and privacy aspects of the Aadhaar framework. Computers & Security 140: 103782. https://doi.org/10.1016/j.cose.2024.103782 .
Saeed, S. 2023. A customer-centric view of e-commerce security and privacy. Applied Sciences 13 (2): 2. https://doi.org/10.3390/app13021020 .
Sandhu, S., and S. Arora. 2020. Customers’ usage behaviour of e-banking services: interplay of electronic banking and traditional banking. International Journal of Finance & Economics 27 (2): 2169–2181. https://doi.org/10.1002/ijfe.2266 .
Sayyah Gilani, M., M. Iranmanesh, D. Nikbin, and S. Zailani. 2017. EMR continuance usage intention of healthcare professionals. Informatics for Health and Social Care 42 (2): 153–165. https://doi.org/10.3109/17538157.2016.1160245 .
Senarak, C. 2021. Cybersecurity knowledge and skills for port facility security officers of international seaports: perspectives of IT and security personnel. The Asian Journal of Shipping and Logistics 37 (4): 345–360. https://doi.org/10.1016/j.ajsl.2021.10.002 .
Shaikh, A.A., and H. Karjaluoto. 2015. Mobile banking adoption: a literature review. Telematics and Informatics 32 (1): 129–142. https://doi.org/10.1016/j.tele.2014.05.003 .
Sharma, P., and K. Kim. 2013. A comparison of PLS and ML bootstrapping techniques in SEM: a monte carlo study. Springer Proceedings in Mathematics and Statistics . https://doi.org/10.1007/978-1-4614-8283-3_13 .
Shaw, N., and K. Sergueeva. 2019. The non-monetary benefits of mobile commerce: extending UTAUT2 with perceived value. International Journal of Information Management 45: 44–55. https://doi.org/10.1016/j.ijinfomgt.2018.10.024 .
Singh, B., and B. Kumar. 2024. A comprehensive analysis of key factors causing various kinds of cyber-attacks in higher educational institute’s. Journal of Research Administration 6 (1): 1.
Singh, S., and R.K. Srivastava. 2018. Predicting the intention to use mobile banking in India. International Journal of Bank Marketing 36 (2): 357–378. https://doi.org/10.1108/IJBM-12-2016-0186 .
Singh, S., and R.K. Srivastava. 2020. Understanding the intention to use mobile banking by existing online banking customers: an empirical study. Journal of Financial Services Marketing 25 (3): 86–96. https://doi.org/10.1057/s41264-020-00074-w .
Sinha, I., and S. Mukherjee. 2016. Acceptance of technology, related factors in use of off branch e-banking: an Indian case study. The Journal of High Technology Management Research 27 (1): 88–100. https://doi.org/10.1016/j.hitech.2016.04.008 .
Taylor, D.G., and D. Strutton. 2010. Has e-marketing come of age? Modeling historical influences on post-adoption era Internet consumer behaviors. Journal of Business Research 63 (9): 950–956. https://doi.org/10.1016/j.jbusres.2009.01.018 .
Thakur, R., and M. Srivastava. 2014. Adoption readiness, personal innovativeness, perceived risk and usage intention across customer groups for mobile payment services in India. Internet Research 24 (3): 369–392. https://doi.org/10.1108/IntR-12-2012-0244 .
The Hindu. 2017, April 15. Hacked: How $171 mn stolen from Union Bank was recovered. The Hindu . https://www.thehindu.com/news/national/hacked-how-171-mn-stolen-from-union-bank-was-recovered/article18063938.ece .
The Times of India. 2018, August 15. Cosmos Bank hit by cyber hack, loses Rs 94 crore in 2 days. The Times of India . https://timesofindia.indiatimes.com/city/pune/cosmos-bank-hit-by-cyber-hack-loses-rs-94-crore-in-2-days/articleshow/65409441.cms .
The New York Times. 2022, September 16. Uber Investigating Breach of Its Computer Systems. The New York Times . https://www.nytimes.com/2022/09/15/technology/uber-hacking-breach.html .
Hindustan Times. 2023, September 18. Financial fraud top cyber crime in India; UPI, e-banking most targeted: Study. Hindustan Times. https://www.hindustantimes.com/business/financial-fraud-top-cyber-crime-in-india-upi-e-banking-most-targeted-study-101695036325725.html .
India Today. 2017. WannaCry: Hundreds of ATMs shut down across India to escape ransomware attack, RBI denies. India Today. https://www.indiatoday.in/india/story/atms-shut-down-india-wanna-cry-ransomware-attack-977191-2017-05-15 .
India Today. 2023, February 15. Cyber fraud incidents rising in India: how to file a complaint online on Cyber Crime portal; New Delhi, UPDATED: Feb 15, 2023 17:11 IST. https://www.indiatoday.in/technology/features/story/cyber-fraud-incidents-rising-in-india-how-to-file-a-complaint-online-on-cyber-crime-portal-2335149-2023-02-15 .
Tsai, H.S., M. Jiang, S. Alhabash, R. LaRose, N.J. Rifon, and S.R. Cotten. 2016. Understanding online safety behaviors: a protection motivation theory perspective. Computers & Security 59: 138–150. https://doi.org/10.1016/j.cose.2016.02.009 .
Venkatesh, V., J. Thong, and X. Xu. 2012. Consumer acceptance and use of information technology: extending the unified theory of acceptance and use of technology. MIS Quarterly 36: 157–178. https://doi.org/10.2307/41410412 .
Vijayasarathy, L.R. 2004. Predicting consumer intentions to use on-line shopping: the case for an augmented technology acceptance model. Information & Management 41 (6): 747–762. https://doi.org/10.1016/j.im.2003.08.011 .
Vimal, M., CISA, CISM, & Six Sigma, B. B. 2019. Cybersecurity and Fintech at a Crossroads . https://www.isaca.org/resources/isaca-journal/issues/2019/volume-1/cybersecurity-and-fintech-at-a-crossroads .
Whittaker, Z. 2019, January 30. India’s largest bank SBI leaked account data on millions of customers. TechCrunch . https://techcrunch.com/2019/01/30/state-bank-india-data-leak/ .
Yang, S., Y. Lu, S. Gupta, Y. Cao, and R. Zhang. 2012. Mobile payment services adoption across time: an empirical study of the effects of behavioral beliefs, social influences, and personal traits. Computers in Human Behavior 28 (1): 129–142. https://doi.org/10.1016/j.chb.2011.08.019 .
Yoon, H.S., and L.M. Barker Steege. 2013. Development of a quantitative model of the impact of customers’ personality and perceptions on Internet banking use. Computers in Human Behavior 29 (3): 1133–1141. https://doi.org/10.1016/j.chb.2012.10.005 .
Zwilling, M., G. Klien, D. Lesjak, Ł Wiechetek, F. Çetin, and H.N. Basım. 2022. Cyber security awareness, knowledge and behavior: a comparative study. Journal of Computer Information Systems 62: 82–97. https://doi.org/10.1080/08874417.2020.1712269 .
Download references
Author information
Authors and affiliations.
Department of Commerce, Aligarh Muslim University, Aligarh, India
Mohammed Afzal, Mohd. Shamim Ansari, Mohammad Shahid & Mohd. Shoeb
Department of Agricultural Economics and Management, Aligarh Muslim University, Aligarh, India
Naseem Ahmad
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Mohammed Afzal .
Ethics declarations
Conflict of interest.
The authors declared no potential conflict of interest concerning this article's research, authorship, and/or publication.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Afzal, M., Ansari, M.S., Ahmad, N. et al. Cyberfraud, usage intention, and cybersecurity awareness among e-banking users in India: an integrated model approach. J Financ Serv Mark (2024). https://doi.org/10.1057/s41264-024-00279-3
Download citation
Received : 12 October 2023
Revised : 23 March 2024
Accepted : 08 April 2024
Published : 06 May 2024
DOI : https://doi.org/10.1057/s41264-024-00279-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cybersecurity awareness
- Protection behaviour
- Usage intention
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
Corporate banking frauds in digital world: an analysis. Case study no.1 : the case of VMC systems limited, Hyderabad. Case study no.2: the case of Nirav Modi and Mehul Choksi: PNB scam 2018. Case study no. 3: the case of Vijay Mallya. Case study no.4: Yes Bank fraud case and DHLF.
The Jaiprakash Kulkarni & Anr. Vs. Banking Ombudsman & Ors. case highlights the increasing risks of cyber fraud faced by individuals and companies. Here’s an analysis of the key aspects of the case law.
Financial frauds accounted for over 75 per cent of cyber crimes in the country from January 2020 till June 2023, with nearly 50 per cent cases related to UPI and internet banking, according...
The findings revealed that online banking fraud, mobile banking fraud, and A TM fraud are the current E-banking fraud risks relevant to Indian banks. This study will help banks and...
Digital payment frauds in India saw a more than fivefold jump to Rs 14.57 billion (Rs 1,457 crore) in the year that ended in March 2024 as compared to the previous period, a report has said, citing Reserve Bank of India 's (RBI) data.
Fraud cases in Indian banks surged to 36,075 in FY24 from 9,046 in FY22, a nearly 300% increase, while the amount involved dropped by 46.7% to Rs 13,930 crore. Most frauds occurred in digital payments, but the highest value frauds were in loan portfolios, with public banks contributing the most by value.
As per the Reserve Bank of India’s (RBI) Annual Report 2021–22, the volume of frauds reported by financial institutions (FIs) using cards and internet banking was 34% higher at 3,596 in 2021–22 as against 2,677 frauds in 2019–20.
Cybercrime in India: A detailed analysis of digital financial frauds, prevention strategies, and challenges faced by law enforcement agencies.
As per the study conducted by IIT Kanpur-based start-up, financial frauds from January 2020 to June 2023 comprised more than 75% of cybercrimes cases in India, out of which 50% of cases are linked to UPI and e-Banking (Hindustan Times 2023).
1) To study modern ways of banking fraud in online mode. 2) To evaluate the international law relating to e-banking frauds. 3) To analyze the efficiency and weaknesses of Indian laws...