

Type to search
Cybersecurity Case Studies and Real-World Examples
image courtesy pixabay.com
Table of Contents
In the ever-evolving landscape of cybersecurity, the battle between hackers and defenders continues to shape the digital domain. To understand the gravity of cybersecurity challenges, one need only examine real-world examples—breaches that have rocked industries, compromised sensitive data, and left organizations scrambling to shore up their defenses. In this exploration, we’ll dissect notable cybersecurity case studies, unravel the tactics employed by cybercriminals , and extract valuable lessons for strengthening digital defenses.
Equifax: The Breach that Shattered Trust
In 2017, Equifax, one of the largest credit reporting agencies, fell victim to a massive data breach that exposed the personal information of nearly 147 million individuals. The breach included sensitive data such as names, Social Security numbers, birthdates, and addresses, leaving millions vulnerable to identity theft and fraud.
Lessons Learned
1. Patch Management is Crucial:
The breach exploited a known vulnerability in the Apache Struts web application framework. Equifax failed to patch the vulnerability promptly, highlighting the critical importance of timely patch management. Organizations must prioritize staying current with security patches to prevent known vulnerabilities from being exploited.
2. Transparency Builds Trust:
Equifax faced severe backlash not only for the breach itself but also for its delayed and unclear communication with affected individuals. Transparency in communication is paramount during a cybersecurity incident. Organizations should proactively communicate the extent of the breach, steps taken to address it, and measures for affected individuals to protect themselves.
Target: A Cybersecurity Bullseye
In 2013, retail giant Target suffered a significant breach during the holiday shopping season. Hackers gained access to Target’s network through a third-party HVAC contractor, eventually compromising the credit card information of over 40 million customers and the personal information of 70 million individuals.
1. Third-Party Risks Require Vigilance:
Target’s breach underscored the risks associated with third-party vendors. Organizations must thoroughly vet and monitor the cybersecurity practices of vendors with access to their networks. Note that a chain is only as strong as its weakest link.
2. Advanced Threat Detection is Vital:
Target failed to detect the initial stages of the breach, allowing hackers to remain undetected for an extended period. Implementing robust advanced threat detection systems is crucial for identifying and mitigating breaches in their early stages.
WannaCry: A Global Ransomware Epidemic
In 2017, the WannaCry ransomware swept across the globe, infecting hundreds of thousands of computers in over 150 countries. Exploiting a vulnerability in Microsoft Windows, WannaCry encrypted users’ files and demanded ransom payments in Bitcoin for their release.
1. Regular System Updates are Non-Negotiable:
WannaCry leveraged a vulnerability that had been addressed by a Microsoft security update months before the outbreak. Organizations fell victim due to delayed or neglected updates. Regularly updating operating systems and software is fundamental to thwarting ransomware attacks .
2. Backup and Recovery Planning is Essential:
Organizations that had robust backup and recovery plans were able to restore their systems without succumbing to ransom demands. Implementing regular backup procedures and testing the restoration process can mitigate the impact of ransomware attacks.
Sony Pictures Hack: A Cyber Espionage Saga
In 2014, Sony Pictures Entertainment became the target of a devastating cyberattack that exposed an array of sensitive information, including unreleased films, executive emails, and employee records. The attackers, linked to North Korea, sought to retaliate against the film “The Interview,” which portrayed the fictional assassination of North Korea’s leader.
1. Diverse Attack Vectors:
The Sony hack demonstrated that cyber threats can come from unexpected sources and employ diverse attack vectors. Organizations must not only guard against common threats but also be prepared for unconventional methods employed by cyber adversaries .
2. Nation-State Threats:
The involvement of a nation-state in the attack highlighted the increasing role of geopolitical motivations in cyber incidents. Organizations should be aware of the potential for state-sponsored cyber threats and implement measures to defend against politically motivated attacks.
Marriott International: Prolonged Exposure and Ongoing Impact
In 2018, Marriott International disclosed a data breach that had persisted undetected for several years. The breach exposed personal information, including passport numbers, of approximately 500 million guests. The prolonged exposure raised concerns about the importance of timely detection and response.
1. Extended Dwell Time Matters:
Marriott’s breach highlighted the significance of dwell time—the duration a threat actor remains undetected within a network. Organizations should invest in advanced threat detection capabilities to minimize dwell time and swiftly identify and mitigate potential threats.
2. Post-Breach Communication:
Marriott faced criticism for the delayed communication of the breach to affected individuals. Prompt and transparent communication is vital in maintaining trust and allowing individuals to take necessary actions to protect themselves.
SolarWinds Supply Chain Attack: A Wake-Up Call
In late 2020, the SolarWinds supply chain attack sent shockwaves through the cybersecurity community. Sophisticated threat actors compromised SolarWinds’ software updates, enabling them to infiltrate thousands of organizations, including government agencies and major corporations.
1. Supply Chain Vulnerabilities:
The incident underscored the vulnerability of the software supply chain. Organizations must conduct thorough assessments of their suppliers’ cybersecurity practices and scrutinize the security of third-party software and services.
2. Continuous Monitoring is Essential:
The SolarWinds attack highlighted the importance of continuous monitoring and threat detection. Organizations should implement robust monitoring systems to identify anomalous behavior and potential indicators of compromise.
Notable Lessons and Ongoing Challenges
1. Human Element:
Many breaches involve human error, whether through clicking on phishing emails or neglecting cybersecurity best practices. Cybersecurity awareness training is a powerful tool in mitigating the human factor. Employees should be educated on identifying phishing attempts, using secure passwords, and understanding their role in maintaining a secure environment.
2. Zero Trust Architecture:
The concept of Zero Trust, where trust is never assumed, has gained prominence. Organizations should adopt a mindset that verifies every user, device, and network transaction, minimizing the attack surface and preventing lateral movement by potential intruders.
3. Cybersecurity Collaboration:
Cybersecurity is a collective effort. Information sharing within the cybersecurity community, between organizations, and with law enforcement agencies is crucial for staying ahead of emerging threats. Collaborative efforts can help identify patterns and vulnerabilities that may not be apparent to individual entities.
4. Regulatory Compliance:
The landscape of data protection and privacy regulations is evolving. Compliance with regulations such as GDPR, HIPAA, or CCPA is not only a legal requirement but also a cybersecurity best practice. Understanding and adhering to these regulations enhances data protection and builds trust with customers.
5. Encryption and Data Protection:
The importance of encryption and data protection cannot be overstated. In various breaches, including those of Equifax and Marriott, the compromised data was not adequately encrypted, making it easier for attackers to exploit sensitive information. Encrypting data at rest and in transit is a fundamental cybersecurity practice.
6. Agile Incident Response:
Cybersecurity incidents are inevitable, but a swift and agile incident response is crucial in minimizing damage. Organizations should regularly test and update their incident response plans to ensure they can respond effectively to evolving threats.
7. User Awareness and Training:
Human error remains a significant factor in many breaches. User awareness and training programs are essential for educating employees about cybersecurity risks , promoting responsible online behavior, and reducing the likelihood of falling victim to phishing or social engineering attacks.
8. Continuous Adaptation:
Cyber threats constantly evolve, necessitating a culture of continuous adaptation. Organizations should regularly reassess and update their cybersecurity strategies to address emerging threats and vulnerabilities.
Conclusion: Navigating the Cybersecurity Landscape
The world of cybersecurity is a battlefield where the landscape is ever-changing, and the adversaries are relentless. Real-world case studies serve as poignant reminders of the importance of proactive cybersecurity measures . As organizations adapt to emerging technologies, such as cloud computing, IoT, and AI, the need for robust cybersecurity practices becomes more pronounced. Real-world case studies offer invaluable insights into the tactics of cyber adversaries and the strategies employed by organizations to defend against evolving threats.

Prabhakar Pillai
I am a computer engineer from Pune University. Have a passion for technical/software blogging. Wrote blogs in the past on SaaS, Microservices, Cloud Computing, DevOps, IoT, Big Data & AI. Currently, I am blogging on Cybersecurity as a hobby.
14 Comments
Hi, I believe your website mmight be having browser compatibility problems. Whenever I lokok att your blog in Safari, it looks fine but when opening in Internet Explorer, it has some overlapping issues. I just wanted to provide you with a quick heads up! Other than that, excellent blog!
Consider opening in chrome or Microsoftedge. Thank you for the comments
Hey! Loved your post.
This was a very insightful read. I learned a lot from it.
This is fantastic! Please continue with this great work.
Thank you for addressing such an important topic in this post Your words are powerful and have the potential to make a real difference in the world
Your writing is so engaging and easy to read It makes it a pleasure to visit your blog and learn from your insights and experiences
Your blog posts are always full of valuable information, thank you! Share the post on Facebook.
This is a must-read article for anyone interested in the topic. It’s well-written, informative, and full of practical advice. Keep up the good work!
I just wanted to say how much I appreciate your work. This article, like many others on your blog, is filled with thoughtful insights and a wonderful sense of optimism. It’s evident that you put a lot of effort into creating content that not only informs but also uplifts. Thank you.
I am so grateful for the community that this blog has created It’s a place where I feel encouraged and supported
Thank you for this insightful article. It’s well-researched and provides a lot of useful information. I learned a lot and will definitely be returning for more.
Security Framework and Defense Mechanisms for IoT Reactive Jamming Attacks – Download ebook – https://mazkingin.com/security-framework-and-defense-mechanisms-for-iot-reactive-jamming-attacks/
Leave a Comment Cancel Comment
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Unpacking Cyber Crime: In-depth Analysis and Case Studies
- By Donald Korinchak, MBA, PMP, CISSP, CASP, ITILv3
In an era characterized by unprecedented digital connectivity, our reliance on the Internet and other digital technologies has grown exponentially. However, this dependence has also opened gates to a nefarious world of crimes committed in cyberspace, known as cyber crimes. Ranging from the theft of an individual’s personal data to crippling nations’ infrastructures, these digital felonies have evolved to become one of the most sophisticated challenges to law enforcement agencies and national security. This in-depth exploration of cybercrime provides an illumination into its diverse forms, historical progression, notorious instances, societal impact, and viable prevention strategies. This discourse aims to furnish the reader with a lucid understanding of the complex web interweaved by cybercriminals, the extensive damage they perpetrate, and, most importantly, how to arm and protect ourselves in this ongoing battle in the digital world.
Types of Cyber Crime
Unmasking the multifaceted threat of cybercrime in our digital society.
As the digital era takes firm root, transcending almost all facets of our daily lives, it unveils an ever-evolving landscape of vulnerability to various types of cyber crimes. Understanding the nuanced complexities of these threats is indispensable in guiding our collective response to safeguard the inviolability of our virtual dwellings.
Imperative for discussion is the specter of identity theft, which involves the unlawful acquisition and utilization of another individual’s personal information for illegitimate financial gains. Cybercriminals exploit various avenues, such as phishing schemes and data breaches, to execute this violation, leading to disastrous personal and financial consequences for the victim.
Malware , a portmanteau of malicious software, lingers as another notable threat. Ruthlessly subtle, this category of cybercrime extends to ransomware , which locks users out of their systems or data, holding it hostage until a ransom is paid. Spyware follows closely, covertly monitoring and transmitting the user’s activities to a third party. Both breed a pervasive sense of violation and create vast economic downstream effects.
Cyberstalking and cyberbullying, while demarcated less by economic impacts, remain potent narcotics in the cocktail of cybersecurity threats. These crimes are characterized by intentional intimidation, harassment, or threat to another individual, utilizing digital mediums. The psychological trauma imparted by these infringements reflects the wider societal repercussions that transcend the digital sphere.
Notably, the list would be incomplete without recognizing cyber-terrorism and cyber-warfare. These acts, striking at the intersection of technology and geopolitical maneuvering, involve the use of Internet-based attacks in terrorist activities and warfare, often targeting critical infrastructures and national security or causing a state of panic and fear.
The rapidly evolving universe of financial technology is not untouched by cybercrime. Crypto-jacking emerges as a salient threat where hackers hijack a computer’s resources to mine for cryptocurrency without the owner’s knowledge or consent— a subtle and yet potent symbol of how technology’s greatest strengths can morph into its most haunting vulnerabilities.
Lastly, the advent of Deepfakes and AI-generated content birthed a new realm of cybercrime. These acts involve the use of artificial intelligence to create or alter video, audio, or image content to depict scenes or convey messages that were never captured or intended, potentially causing severe personal, political, and societal unrest.
In navigating through the labyrinth of cybercrime, it becomes clear that our informational infrastructure functions as a double-edged sword. Heightened awareness and understanding of the multiple types of cyber crimes, corrective measures, and prevention strategies are critical to ensure the security of our accelerated journey into the digital age. As we teeter on the brink of this new epoch, let it be fortified by knowledge, caution, and, above all, a shared responsibility toward a safe and secure online world.

Historical Perspective of Cyber Crime
The evolutionary trajectories of cybercriminal strategies: a deeper dive.
While initial aspects of cybercrime, including identity theft, malware, cyberstalking, and cyber-terrorism, remain relevant, the ingenious adaptability of cybercriminals continues to morph these original paradigms into more complex constructs. Deepfakes and AI-generated content, crypto-jacking, and even cyber warfare itself continue to evolve. More recently, however, these forms of cybercrime are being joined, and in some cases superseded, by other more sophisticated threats.
Spear phishing, a targeted version of phishing, has emerged as one of the most insidious cybercrimes. Cybercriminals no longer toss out a wide net in the hopes of ensnaring an unsuspecting fish but have now shifted to crafting precise, personalized lures to hook specific individuals or organizations. This modality, premised on thorough research and social engineering , typifies today’s cunning adversary, who forgoes brute force for psychological manipulation.
Next in this progression of cybercrime sophistication is the advent of Advanced Persistent Threat s (APTs). Unlike the blitzkrieg assault-style adopted by most traditional cyberattack s, APTs are slow and methodical infiltrations designed to remain undetected for prolonged periods. By leveraging backdoor techniques and a patient, stealthy approach, these threat actors compromise systems to exfiltrate data or create systemic disruption in a silent, protracted manner.
Further underscoring the evolutionary trends, cybercriminals now employ Botnets, networks of compromised devices commanded by a central operator. The damages that can be inflicted range from devastating Distributed Denial-of-Service attacks to enormous volumes of spam mail. Cybercriminals disregard the sanctity of individual autonomy and readily surrender to the collective might of these enslaved devices.
Reflecting a leap from dexterity to craftiness, supply chain attack s represent another ingenious cybercriminal innovation. These comprise a systemic, strategic violation entailing the compromise of trusted software or hardware suppliers. By infiltrating these sources, cybercriminals can lurk undetected, poised to pounce on end-users who implicitly trust their providers and, by extension, become unsuspecting victims.
Lastly, while already touched upon in the subject of deepfakes, weaponized AI and Machine Learning take the potential for harm to unprecedented heights. As these technologies advance, they become double-edged swords, providing enormous potential benefits but also harboring potential hazards. They can be manipulated to carry out highly sophisticated attacks that adapt, learn, and emulate human behaviors, making them harder to detect and counter.
In conclusion, the cybercriminal landscape remains perpetually fluid. It continues to evolve, harboring devastating potential and emphasizing the critical need for robust countermeasures and vigilance. As much as we are captivated by technology’s spell, we must also remain equally committed to fathoming its dark possibilities and approach this evolving challenge with the same unyielding determination.

Depicting Major Cyber Crime Case Studies
When regarding the multifaceted arena of cybercrimes, a few notorious examples have made all the difference in shaping both legislative processes and public perception. These archetypical scenarios paint a stark picture of the danger posed by cybercriminals and the significant, often devastating, consequences for victims.
The infamous Yahoo data breach, which revealed itself from 2013 to 2014, can never be forgotten. It compromised approximately three billion user accounts, rendering it the most prodigious data compromise in history. Personal data, including names, email addresses, and passwords, fell into malevolent hands, leading to a leap in fraudulent activities globally. The ensuing turbulence resulted in the resignation of Yahoo’s CEO, loss of consumer trust, and a $50 million settlement.
Adobe Systems witnessed a devastating blow in October 2013—a data violation exposing approximately 38 million active user accounts. The compromised data included encrypted debit and credit card data paired with user login credentials, creating a substantial identity theft concern. Adobe had to face huge economic losses and significant reputation damage, which took years to recover from.
The Heartland Payment Systems breach in 2008 was another significant incident that stirred the digital world. Dating back to when companies scarcely understood the imminent threat of cybercrime, this attack led to a loss of over 130 million credit and debit card details. Heartland witnessed a significant financial loss of around $140 million in remediation.
In terms of affecting global infrastructure, the WannaCry ransomware attack in May 2017 was a stark example. The ransomware targeted computers running Microsoft Windows, encrypting data and demanding ransom in Bitcoin. Over 200,000 systems across 150 countries, including significant healthcare organizations, were taken hostage. The immense global disruption prompted a surge in infrastructure investment to improve cyber defense capabilities.
While most attacks impact a specific corporation or sector, the Mirai botnet attack of 2016 introduced a broader systemic threat. The malware transformed networked devices such as IP cameras, printers, and routers into a botnet to conduct distributed denial-of-service attacks. With millions of IoT devices compromised, the Mirai botnet was capable of unparalleled distributed destruction, showcasing how vulnerable global digital infrastructure can be.
Cyber espionage provides another multifaceted concern. An example was Operation Aurora in 2009, aiming to steal sensitive information from top companies, including Google and Adobe. This incident underscored the threat toward intellectual property and corporate competitive advantage, galvanizing a reevaluation of digital security measures in businesses across the world.
On the more sinister end of the spectrum, the Stuxnet worm attack showcased how cybercrime could transform into cyber warfare. In 2010, the Stuxnet worm damaged approximately one-fifth of Iran’s nuclear centrifuges, epitomizing how cyber-attacks can transgress the digital realm and enact substantial real-world damage.
Through these examples and more, it becomes perceptibly clear how multifarious the landscape of cybercrimes truly is. It underscores the imperative need for stringent cybersecurity measures, vigorous legislative action, and individual awareness of the perils that lurk in the depths of the digital world. As we further immerse ourselves in an overwhelmingly interconnected society, it is incumbent upon us to study and learn from these sobering lessons of history.

Impact of Cyber Crime on Individuals and Society
Beyond the directly visible forms of cybercrime, such as identity theft, malware, cyberbullying, deepfakes, cyberterrorism, and crypto-jacking, there lies a plethora of repercussions affecting individual victims and wider societal structures. These implications come as a direct result of cybercrime, which infiltrates various sectors, from personal privacy to economic stability, manifesting differently across each strata of society.
When confronted with the repercussions of cybercrime, it is essential to explore the psychological impact on victims. According to research conducted by the American Psychological Association, individuals who have been victims of cyber crimes often suffer from feelings of violation, loss of trust, and feelings of powerlessness. These outcomes equip cybercriminals with a powerful psychological tool – fear, which they can deploy to extort more information or inflict further harm on their victims.
The financial implications of cybercrime are also critical. On an individual level, victims may incur substantial costs to recover from identity theft or ransomware attacks. On a larger scale, businesses are also impacted—with losses in the billions annually due to cyber theft of intellectual property and sensitive corporate information.
Cyber crimes also pose a severe threat to critical infrastructure. A targeted attack, like the Stuxnet worm or the Mirai botnet attack, can disrupt entire networks or systems. This endangerment of critical infrastructures exposes vulnerabilities in sectors such as energy, telecommunications, transportation, and healthcare, upon which our societies heavily rely.
Furthermore, cybercrime disrupts social order by exploiting our increasing reliance on digital platforms. The damage caused by malicious activities in cyberspace can instigate societal tension or even panic. For instance, the spread of false information through deepfakes or AI-generated content can destabilize communities, alter public opinion, and incite fear or chaos within the public domain.
Moreover, the infiltration of educational institutions and exploitation of data breaches, such as those experienced by Adobe Systems and Yahoo, incite concern for the security of personal and academic data, impacting trust in these institutions.
Finally, the global aspect of cyber crime complicates the enforcement of laws and the attribution of criminals. Differing legislation across jurisdictions, coupled with the abstract nature of cyberspace, often leads to perpetrators evading justice, which again amplifies public fear and mistrust.
The increasing sophistication of cyber criminal activities demands a comprehensive, multi-faceted approach to cybersecurity involving not only technological solutions but also legislative measures, international cooperation, and public awareness initiatives. Vigilance remains paramount – for both the individual and the broader social structures at risk.
In conclusion, while the repercussions of cybercrime are manifold and persistently evolving, the driving force behind combating this modern plague remains undeterred – a relentless commitment to understanding, outwitting, and ultimately neutralizing this digital threat. The continuous enhancement of cybersecurity measures, active legislative action on cybercrimes, and individual awareness of cybercrime risks are just several in the legion of dedicated efforts aimed to equip society with the tools necessary to tackle this complex issue.

Prevention and Mitigation Strategies
Effectively addressing the potential risks and outcomes of cybercrimes necessitates a multi-pronged approach that leans heavily on collaboration, education, and the implementation of cutting-edge cybersecurity strategies. this measure rings especially pertinent against the backdrop of a progressively interconnected world, teetering on the precipice of the much-heralded fourth industrial revolution..
Collaborating across sectors and agencies is a vital strategy for tackling cybercrimes. Internationally, creating a shared understanding of cyber threats and fostering cooperation to deal with them can significantly bolster collective security measures. This includes forming partnerships with international police forces, such as INTERPOL and Europol, to expedite the identification, tracking, and prosecution of cybercriminals regardless of their geographical location.
An educated populace is arguably the first line of defense against cybercrime. The general public must be armed with the knowledge necessary to safeguard sensitive information and thwart the attempts of cybercriminals. Robust security awareness programs must be incorporated into our educational institutions, corporations, and public services, acquainting people with the modus operandi of cybercriminals and how best to respond. This includes increased awareness of the intricacies of social engineering attacks to mitigate risks like whaling and pretexting that have not been previously covered in this article.
Implementing progressive cybersecurity protocols plays a pivotal role in curbing cybercrimes. Organizations should strive for a dynamic, proactive approach as opposed to a static, reactive one. Frequent system audits, vulnerability assessments, and penetration testing can unveil potential security loopholes before cybercriminals can exploit them. A zero-trust architecture that presumes no user or process is intrinsically trustworthy, coupled with behavioral-based threat detection, could significantly bolster an organization’s defense.
Moreover, using encrypted communication channels and urging employees to regularly update their passwords and employ two-factor authentication systems can mitigate unauthorized access risks. Leveraging advanced technologies, like quantum cryptography, can offer foolproof data security, rendering any eavesdropping attempts futile.
Lastly, while strengthening legislative measures against cybercrimes, nations must also create an environment conducive to the reporting of such incidents. Victims often shy away from reporting due to fear of reputational damage or lack of faith in the justice system. Ensuring confidentiality and demonstrating stringent punishment against perpetrators could effectively deter the commission of these crimes.
As we tiptoe into an era dominated by Big Data, 5G, and Artificial Intelligence, our strategies against cybercrime must evolve at a concordant, if not more rapid, pace. A synergized effort spanning individuals, organizations, and countries, buttressed by relentless vigilance, is our best hope in the grand scheme of cybersecurity. Striking that balance between advancing technologically and maintaining cyber hygiene will be the perpetual litmus test for our digitized world.
As we continue to tread through this digital age, understanding the insidious nature of cyber crimes not only informs but empowers us as individuals, organizations, and as a society. We have explored in detail the varied forms of these crimes, their evolution through the years, their devastating impacts exemplified through notable case studies, and the undeniably lasting mark they leave on individuals and societies alike. Furthermore, we have offered a glimpse into the strategies that can be employed to fortify our defenses against these invisible aggressors. The key lies in continual awareness, constant vigilance, and strategic preparedness so that we may navigate this intricate digital universe safely. As we move forward, remember the fight against cybercrime isn’t just for those in the corridors of power but for every Internet user who plays a vital role in this digital ecosystem.
Donald Korinchak, MBA, PMP, CISSP, CASP, ITILv3

Cybercrime case studies
On this page, online grooming, online scams, malware and intimate image abuse.
Online child grooming is befriending a child, and sometimes the family, to make the child more open to sexual abuse. A person who is found guilty of grooming in Victoria is liable to 10 years imprisonment.
What happened?
David is a working dad with three children: Daniel and Matilda (7) and Angie (14). Angie has just commenced her second year of high school. Angie begged David for a smartphone. David finally relents and gives Angie his old smartphone. As a condition for receiving the phone, Angie must share her passcode and must leave the phone to charge overnight in the kitchen.
Angie spends a lot of time on her phone. David will often ask Angie what she is doing on the phone. He tries to monitor her use and keeps track of the phone bill. David has to start working long nights on a special project for work. David is not able to monitor Angie’s phone use as closely. Soon, Angie begins to keep her phone in the room overnight.
As the months go by, David notices Angie’s behaviour changes. She becomes withdrawn and irritable. Her school work starts to suffer.
David receives a call from the school principal – the principal needs an urgent meeting with David. The principal tells David that a parent of one of Angie’s friends told the principal that Angie is in contact with a man online who sends Angie inappropriate messages. David talks to Angie and learns that she met this man on a messaging app and they message constantly.
How was David affected?
David is horrified and feels like he has failed Angie. He feels he has neglected his duty as a parent.
David is devastated that Angie did not tell him what was happening.
David feels powerless to keep his child safe. David starts to suffer from anxiety, affecting his work and relationships.
Romance and dating scams involve scammers taking advantage of people looking for romantic partners, often via dating websites, apps or social media, by pretending to be prospective companions. They play on emotional triggers to extract money, gifts or personal details.
Romance baiting encourages victims to take advantage of a fake investment opportunity.
Amara received and accepted a friend request from Ferenc, a Hungarian serviceman on peacekeeping duties in Afghanistan. Ferenc and Amara grew closer together. Ferenc shared pictures with her and told Amara he had lost his wife to cancer. This was similar to Amara’s own experience – her elderly husband died of cancer two years ago.
Ferenc said he was being posted to Cyprus but that his time in the military was nearly finished. Ferenc told Amara he wanted to set up a jewellery store when he retired.
Ferenc told Amara he was coming to see her but had some trouble with his bank card not working in Cyprus and could not get funds to pay for an export tax on his gemstones. Taking out a loan, Amara transferred Ferenc $15,000 to cover the tax bill. Shortly after, Ferenc told Amara that he had been detained by local authorities in Malaysia on the way to Australia. He needed $20,000 to pay his legal and court fees.
Amara contacted the Malaysian police – they had no knowledge of Ferenc. When Amara told Ferenc she could not send the additional money, he responded with very angry messages, and then ceased contact altogether.
How was Amara affected?
Amara was left confused and hurt. She feels betrayed and cheated. She knows in her head that this was a scam, but in her heart still feels that Ferenc might be out there and she has let him down.
Amara had to re-enter the workforce to service the loan she took. She is also at risk of having her identity stolen because she shared a lot of personal information with the scammer calling himself Ferenc.
Ransomware is a form of extortion using malicious software (malware) that prevents users from accessing their system or personal files and demands ransom payment in order to regain access.
Jin and Bella run a family owned accounting firm that provides outsourced bookkeeping and accounts functions for small businesses across Victoria.
The business operates through an online platform—client companies log in through a website portal and can take care of several bookkeeping needs for their businesses, such as tracking their expenses, processing receipts and calculating deductions.
Jin and Bella’s business computers were infected with ransomware via a suspect email just before tax time. This ransomware locked down the business’ platform so that clients were unable use the portal. The cybercriminals demanded $100,000 in Bitcoin, a cryptocurrency, to restore the network. Jin and Bella refused to pay. The cybercriminals threatened to publish the private information of Jin and Bella’s clients. Jin and Bella did not know what to do. They did not have the money to pay the ransomware. Eventually, Jin and Bella contacted Victoria Police to report the crime.
The majority of Jin and Bella’s clients were unable to submit their tax returns on time. Clients were extremely dissatisfied with the service.
The Australian Cyber Security Centre advises against paying ransoms. Payment of the ransom may increase an individual or organisation’s vulnerability to future ransomware incidents. In addition, there is no guarantee that payment will undo the damage.
How were Jin, Bella and their clients affected?
The reputation of Jin and Bella’s business suffered and as a result, they lost clients. Jin and Bella experienced considerable stress and anxiety from the attack.
The Australian Cyber Security Centre advises against paying ransoms. Payment of the ransom may increase an individual or organisation’s vulnerability to future ransomware incidents. In addition, there is no guarantee that payment will undo the damage.
The Australian Cyber Security Centre has observed cybercriminals successfully using ransomware to disrupt operations and cause reputational damage to Australian organisations across a range of sectors:
- State and Territory governments
- Education and research organisations
The Australian Cyber Security Centre reported a 15% increase in ransomware cybercrime reports in the 2020–21 financial year. 21
Image-based sexual abuse is the creation, distribution or threatened distribution of intimate, nude or sexual image or videos, without the consent of the person pictured. This includes images or videos that have been digitally altered using specialised software.
You can also report image-based abuse to the eSafety Commissioner .
Deepfakes use artificial intelligence software to learn from large numbers of images or recordings of a person to create an extremely realistic but false depiction of them doing or saying something that they did not actually do or say. 24
Aisha is a teacher who unknowingly had malware called a Remote Access Trojan (RAT) downloaded onto her smart phone.
Using the RAT, a cybercriminal accessed her email and text messages, and forwarded some private, intimate pictures to colleagues and family members in her contacts.
The cybercriminal also posted these images, as well as some digitally altered “deepfakes”, to several adult websites. Some of these images were found by students at Aisha’s school.
Aisha did not make a report to Victoria Police, but tried to track down the websites where the images were posted to demand that they were taken down. She suspects that her ex-boyfriend – who has a history of control and emotionally abusive behaviour – was behind the attack, but she did not have any way to prove this.
How was Aisha affected?
Aisha has been devastated by these events— both privately and professionally.
Although her school ultimately understood that she was a victim, the damage to her reputation was irreversible. This, coupled with the anxiety that her students had seen these personal and deepfake images of her, led to her giving up her teaching position at the school. This was her primary source of income.
18 Australian Competition & Consumer Commission, 12 February 2021, Romance Baiting Scams on the Rise, https://www.accc.gov.au/media-release/romance-baiting-scams-on-the-rise
19 Australian Competition & Consumer Commission, 12 February 2021, Romance Baiting Scams on the Rise, https://www.accc.gov.au/media-release/romance-baiting-scams-on-the-rise
20 Australian Competition & Consumer Commission, 12 February 2021, Romance Baiting Scams on the Rise, https://www.accc.gov.au/media-release/romance-baiting-scams-on-the-rise
21 Australian Cyber Security Centre, 2021, ACSC Annual Cyber Threat Report: 1 July 2020 to 30 June 2021
22 Office of the eSafety Commissioner, October 2017, Image-Based Abuse, National Survey: Summary Report (October 2017) https://www.esafety.gov.au/sites/default/files/2019-07/Image-based-abus…
23 Office of the eSafety Commissioner, October 2017, Image-Based Abuse, National Survey: Summary Report (October 2017) https://www.esafety.gov.au/sites/default/files/2019-07/Image-based-abus…
24 eSafety Commissioner, Deepfake trends and challenges — position statement, https://www.esafety.gov.au/about-us/tech-trends-and-challenges/deepfakes
Updated 30 March 2023
A Comprehensive Analysis of High-Impact Cybersecurity Incidents: Case Studies and Implications
- October 2023
- Thesis for: Master`s Degree
- Advisor: Dr. Anişoara Pavelea

- Babeş-Bolyai University
Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
- Himani Mittal

- James Womack
- Christopher Brito
- Xavier-Lewis Palmer
- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up

- Hackers and cybercrime prevention

Getty Images
Top 10 cyber crime stories of 2020
Here are computer weekly’s top 10 cyber crime stories of 2020.

- Alex Scroxton, Security Editor
The past 12 months have seen an unprecedented surge in cyber criminal activity, with two key trends explaining much of the increase – the Covid-19 pandemic introduced new attack surfaces and opportunities for malicious actors, while new developments in ransomware extortion tactics saw millions lost to operators such as Maze, Sodinokibi, Egregor and others.
Here are Computer Weekly’s top 10 cyber crime stories of 2020:
1. Cyber gangsters demand payment from Travelex after Sodinokibi attack
Foreign exchange company Travelex is facing demands for payment to decrypt critical computer files after it was hit by one of the most sophisticated ransomware attacks , known as Sodinokibi , which disabled its IT systems on New Year’s Eve .
The company, which has operations in 70 countries, has faced days of disruption after criminal hackers penetrated its computer networks and delivered a devastating attack timed to hit the company when many of its staff were on holiday.
According to security specialists, criminals are demanding a six-figure sum to supply Travelex with decryption tools that will allow it to recover the contents of files across its computer network that have been encrypted by the virus.
2. List of Blackbaud breach victims tops 120
The UK’s National Trust has joined a growing list of education and charity organisations to have had the data of their alumni or donors put at risk in a two-month-old ransomware incident that occurred at US cloud software supplier Blackbaud .
According to the BBC , the Trust, which operates hundreds of important and historical sites across the country, including natural landscapes and landmarks, parks, gardens and stately homes, said that data on its volunteers and fundraisers had been put at risk, but data on its 5.6 million members was secure.
The organisation is conducting an investigation and informing those who may be affected. As per the UK’s data protection rules, it has also reported the incident to the Information Commissioner’s Office, which is now dealing with a high volume of reports, including Blackbaud’s.
3. IT services company Cognizant warns customers after Maze ransomware attack
Cognizant has warned that a cyber attack by the Maze ransomware group has hit services to some customers.
The IT services company, which has a turnover of over $16bn and operations in 37 countries, said the attack, which took place on Friday 17 April, had caused disruption for some of its clients.
Cognizant, which supplies IT services to companies in the manufacturing, financial services, technology and healthcare industries, confirmed the attack in a statement on Saturday 18 April.
4. Phishing scam targets Lloyds Bank customers
Customers of Lloyds Bank are being targeted by a phishing scam that is currently hitting email and text message inboxes.
Legal firm Griffin Law has alerted people to the scam after being made aware of about 100 people who have received the messages.
The email, which looks like official Lloyds Bank correspondence, warns customers that their bank account has been compromised. It reads: “Your Account Banking has been disabled, due to recent activities on your account, we placed a temporary suspension untill [sic] you verify your account.”
5. Coronavirus now possibly largest-ever cyber security threat
The total volume of phishing emails and other security threats relating to the Covid-19 coronavirus now represents the largest coalescing of cyber attack types around a single theme that has been seen in a long time, and possibly ever, according to Sherrod DeGrippo, senior director of threat research and detection at Proofpoint.
To date, Proofpoint has observed attacks ranging from credential phishing, malicious attachments and links, business email compromise, fake landing pages, downloaders, spam, and malware and ransomware strains, all being tied to the rapidly spreading coronavirus.
“For more than five weeks, our threat research team has observed numerous Covid-19 malicious email campaigns, with many using fear to try to convince potential victims to click,” said DeGrippo.
6. Cyber gangsters hit UK medical firm poised for work on coronavirus with Maze ransomware attack
Cyber gangsters have attacked the computer systems of a medical research company on standby to carry out trials of a possible future vaccine for the Covid-19 coronavirus .
The Maze ransomware group attacked the computer systems of Hammersmith Medicines Research , publishing personal details of thousands of former patients after the company declined to pay a ransom.
The company, which carried out tests to develop the Ebola vaccine and drugs to treat Alzheimer’s disease, performs early clinical trails of drugs and vaccines.
7. Cosmetics company Avon offline after cyber attack
Parts of the UK website of Brazilian-owned cosmetics and beauty company Avon remain offline more than a week after an alleged ransomware attack on its IT systems.
The attack is understood to have impacted the back-end systems used by its famous sales representatives in multiple countries besides the UK, including Poland and Romania, which are now back online. This has left people unable to place orders with the company.
Avon disclosed the breach in a notification to the US Securities and Exchange Commission on 9 June 2020 , saying it had suffered a “cyber incident” in its IT environment that had interrupted systems and affected operations.
8. Travelex hackers shut down German car parts company Gedia in massive cyber attack
The criminal group responsible for the cyber attack that has disrupted high-street banks and the foreign currency exchange chain Travelex for more than three weeks has launched what has been described as a “massive cyber attack” on a German automotive parts supplier.
Parts manufacturer Gedia Automotive Group , which employs 4,300 people in seven countries, said today that the attack will have far-reaching consequences for the company, which has been forced to shut down its IT systems and send staff home.
The 100-year-old company, which has its headquarters in Attendorn, said in a statement posted on its website that it would take weeks or months before its systems were fully up and running.
9. Carnival cruise lines hit by ransomware, customer data stolen
Cruise ship operator Carnival Corporation has reported that it has fallen victim to an unspecified ransomware attack which has accessed and encrypted a portion of one of its brand’s IT systems – and the personal data of both its customers and staff may be at risk.
Carnival, which like the rest of the travel industry has been stricken by the Covid-19 pandemic – it also operates Princess Cruises, owner of the ill-fated Diamond Princess , which found itself at the centre of the initial outbreak – reported the incident to the US Securities and Exchange Commission on 17 August.
In its form 8-K filing, the company said the cyber criminals who accessed its systems also downloaded a number of its data files, which suggests it may be at imminent risk of a double extortion attack of the sort perpetrated by the Maze and ReVIL/Sodinokibi groups.
10. Law firm hackers threaten to release dirt on Trump
The cyber criminal gang behind the ReVIL or Sodinokibi ransomware attack on New York celebrity law firm Grubman, Shire, Meiselas and Sacks (GSMS) have doubled their ransom demand to $42m and threatened to publish compromising information on US president Donald Trump , according to reports.
In a statement seen by entertainment news website Page Six , the Sodinokibi group – which has also gone by the name Gold Southfield – said they had found “a ton of dirty laundry” on Trump.
The threat reportedly reads: “Mr Trump, if you want to stay president, poke a sharp stick at the guys [GSMS], otherwise you may forget this ambition forever. And to you voters, we can let you know that after such a publication, you certainly don’t want to see him as president. The deadline is one week.”
Read more on Hackers and cybercrime prevention

Top 10 investigations and national security stories of 2020

Maze ransomware shuts down with bizarre announcement

Cyber attack combined with Covid-19 puts Travelex into administration

Canon said to be latest Maze ransomware victim
The next U.S. president will set the tone on tech issues such as AI regulation, data privacy and climate tech. This guide breaks ...
Minnesota Gov. Tim Walz supports climate action and released a Climate Action Framework detailing steps for the state to become ...
Remedies in the Google online search antitrust case could include eliminating the company's use of distribution contracts that ...
Highlights from Black Hat USA 2024 include a keynote panel on securing election infrastructure as well as several sessions on ...
Although Flashpoint is known for their cybersecurity threat intelligence services, the vendor also provides physical security ...
Cutting through an EDR tool's marketing hype is difficult. Ask vendors questions, and conduct testing before buying a tool to ...
Network architects face challenges when considering a network upgrade, but enterprises can keep problems to a minimum by ...
Wireshark is a useful tool for capturing network traffic data. Network pros can make the most of the tool by analyzing captured ...
IP addressing and subnetting are important and basic elements of networks. Learn how to calculate a subnet mask based on the ...
Tests off coastlines around the world are measuring the feasibility of underwater data centers. With proper maintenance and ...
Sustainable and renewable energy sources are necessary for data centers to meet emissions requirements by 2030. Nuclear power is ...
Intel's failure to profit from the red-hot AI market is behind plans to cut 15,000 jobs. The workforce reduction is part of a $10...
Vector databases excel in different areas of vector searches, including sophisticated text and visual options. Choose the ...
Generative AI creates new opportunities for how organizations use data. Strong data governance is necessary to build trust in the...
Snowpark Container Services aims to provide the vendor's users with a secure environment for deploying and managing models and ...

Partner Overview
Join Us for Growth, Innovation and Cybersecurity Excellence.
Become a Channel Partner
Be a Valued Partner and Embark on a Journey of Profitability.
Partner Portal
Unified Security Platform
Latest Content and Resources
Threat Report 2023
NRGi Holding Case Study
The 15 Internet Crime Stories That Make Cybersecurity Measures Essential
Read the best, most fascinating tech stories that cover the risks of the digital landscape and find out how to stay safe
Last updated on February 28, 2024

Internet crime stories are dime a dozen but these examples will show you why online security is essential. From ethical hacking to blackmail and car hijacking, these true stories show how you must act now to secure your well-being in the digital landscape. We carefully curated the best, most fascinating tech stories that cover the risks involved in any digital activity of device, so use the links below to navigate them.
- The mom whose laptop was locked down by a ransomware attack
- Tom was blackmailed because of his hacked Ashley Madison account
- How ethical hackers took over her PC
- They remote hacked his car
- Ransomware deletes 2 years of academic papers
- His WoW account got hacked. Twice
- Your data has been breached
- Catfish isn’t dinner, it’s lies, manipulation, and theft
- Hillary Clinton’s Aides Got Phished And Lost Her The Election
- He fell prey to the same scam twice and lost $1,350
- Who would want to be you? Some can even become You.
- When your workplace, a gaming giant, gets hit
- The casual, public Wi-Fi hack
- Customer support falls prey to a social engineering hack
- Hotel managers and clients had nightmares due to one lock hack posted
Cyber security incidents and getting hacked seem like distant, fascinating things where other people get hurt, but you stay safe. Truth is, getting hacked or scammed can happen to anyone and it might even have happened to you in the past.
The average number of devices used by you and most people have increased exponentially in the recent years. We’re surrounded by IoT devices, wear smart bracelets, have friends who are betting their savings on cryptocurrency, and we sign up to dozens of social media platforms.
This means cyber attacks have a lot of ways to get to you – either by targeting you specifically or by simply compromising your info in large-scale attacks. The best way to learn is through experience, so let’s do just that.
Here are the real stories of people who got hacked and what they learned, plus some actionable tips to enhance your security.
1. The mom whose laptop was locked down by a ransomware attack
Two days before Thanksgiving, Alina’s mother got hit by a ransomware attack. 5,726 files got locked by CryptoWall , an encryption malware so powerful it is almost impossible to recover the information.
Alina’s mom contacted the attacker through the ransomware’s communication feature.
As all ransomware creators, he told her she can either pay to get her files back or lose them forever.
The price to unlock her files was 500$ in the first week and 1000$ in the second one, after which the files would be deleted.
Payment was to be done in Bitcoin, a complicated process which she had to learn on the fly.
Because of a major snowstorm that closed down the banks, Alina’s mom couldn’t pay the ransom in the first week, and ended up having to plead with her attacker to not increase the price to 1,000$.
Surprisingly, he accepted and gave her the key to unlock her files. However, no one should ever pay a ransom, the risks far outweigh the benefits.
T he full story is here: How my mom got hacked & What I’ve learned after my mom got hacked (and her data held for ransom)
Find out what steps to take for your protection: WHAT IS RANSOMWARE AND 9 EASY STEPS TO KEEP YOUR SYSTEM PROTECTED
2. tom was blackmailed because of his hacked ashley madison account.

After the Ashley Madison hack, cyber criminals contacted him and demanded 500$ to remove his name from a publicly searchable registry.
If not, they would also send an email to his family, informing them of Tom’s affair. Tom refused, believing that if he paid them, they would know that he had something to lose and could be blackmailed further.
He was wise, but that didn’t mean he didn’t suffer. In the end, Tom had to live knowing his affairs on AM could be exposed at any time by the hackers.
Moreover, there were also people who took it up upon themselves to impart justice on people in circumstances they couldn’t, or wouldn’t, understand.
The story: In Ashley Madison’s wake, here’s one man’s story of sex, sorrow and extortion
Securing your pc doesn’t have to be expensive: 13 free pc security hacks to build your online protection, 3. how ethical hackers took over her pc.
Sophie is a technology reporter at the Daily Telegraph.
As part of an assignment, she accepted to be part of an ethical hacking experiment. Basically, a group of ethical hackers would try to compromise her system without her knowing how, when and where.

They pretended to be whistleblowers in control of sensitive government information and sent her an email with some of the files attached.
The malware infection occurred the moment she opened the file, and the attackers got access to everything, including email address and web cam. And it wasn’t even that difficult to do.
The story: How hackers took over my computer
This is how you can protect your email address: the complete guide to email security, 4. they remote hacked his car.
Andy Greenberg, a senior writer at Wired, once took part in a groundbreaking experiment which tested how car hacking could be done.

Next, the transmission was cut and finally, they remotely activated the breaks. And they did all of these things with Andy behind the wheel.
The experiment uncovered a massive flaw in Jeep’s cars which was later fixed. Today, this is even easier to achieve, due to the rise of electric cars and the huge push towards autonomous vehicles like trucks, taxis and more.
The story: Hackers Remotely Kill a Jeep on the Highway—With Me in It
Learn more about how software can expose you, something that works the same way whether we’re talking about computers or self-driving cars: 8 vulnerable software apps exposing your computer to cyber attacks, 5. ransomware deletes 2 years of academic papers.
What’s the first thing people do when they get hit by a malware attack? They panic and ask for help in a dedicated forum: “My PC is infected.
Please, can anyone help me? ”
For this user however, it was too little, too late. For 2 years he worked on his academic papers, and then they got encrypted by ransomware.
The timing was awful as well: it happened right before they were due. Antivirus didn’t help and he had no backup.
We hope he didn’t pay.
What we do know is that ransomware attacks are much more frequent that you can imagine and they target individuals and businesses alike.
The story: My PC got hacked by troldesh ransomware. please is there anyone who can help.
Find out how to backup your data so ransomware does not affect you: how to backup your computer – the best advice in one place, 6. his wow account got hacked. twice.
Gamers are favorite targets for cyber criminals, since they don’t want to lose the time and money invested in a character and are willing to pay the ransom.
As a result of a potential phishing attempt, this guy had his WoW account hacked and all his progress lost. And it happened to him not once, but twice!

The same type of attack happens in most popular online games.
League of Legends phishing volumes are truly legendary, so we talked to their security team to find out how to avoid getting your account stolen.
The story: So my WoW account got hacked… twice.
Learn more about security and gaming: gamers, time to take your cyber security to the next level, 7. your data has been breached.
The Office of Personnel Management, OPM for short, can be considered the US Government’s HR Department.
Among other things, it keeps records of employee personal information, such as height, weight, hair and eye color.
In 2014, the OPM got hacked, and the information of 22 million government employees leaked, most likely in the hands of a foreign government.

143 million US consumers had their sensitive personal information exposed. That’s 44% of the population and today we’re still seeing reports of more Equifax leaks.
Odds are, if you’re a US citizen, your info is floating around on the dark web , at the mercy of cyber criminals. What do you think the US government did to deal with the Equifax hack?
After less than one month since the incident, the IRS awarded Equifax a contract for fraud detection. Clearly, it’s up to you and you alone to protect your identity.
The story: OPM got hacked and all I got was this stupid e-mail
Learn how to stay as safe as possible from identity theft: how to prevent identity theft in 20 essential steps, 8. catfish isn’t dinner, it’s lies, manipulation and theft.
Some people hack you not with malware or suspicious links, but by gaining your trust and love.
This journalist’s mother started using the online dating site Match.com, and eventually formed a connection with a soldier on active duty in Afghanistan.
After a while, the soldier asked for a 30,000$ loan to help him clear a sizeable inheritance of gold and jewelry from US customs.
By now, the journalist and her brother intervened, suspecting the soldier was catfishing their mother.

In the Match.com case, the victims confronted the man with their suspicions and other evidence they had accumulated over time.
The supposed soldier revealed he was a man from Ghana trying to support his sisters, and scamming people online was the best way he knew how to do that.
The story: My mom fell for a scam artist on Match.com—and lived to tell the tale
Learn about the top online scams and how to avoid them: top 11 scams used by online criminals to trick you, 9. hillary clinton’s aides got phished and lost her the election.
Unless you’ve been living under a rock, you definitely know why Hillary Clinton lost the US Election to Donald Trump.

When forwarding the phishing email to a computer technician, he wrote “This is a legitimate email” instead of “illegitimate”. This gave hackers from Russia access to about 60,000 emails from Podesta’s private Gmail account.
They stole all that data, gave it to Wikileaks, and the rest is actual history.
“The FBI’s laid-back approach meant that Russian hackers were able to roam inside the DNC’s computer systems for almost seven months before Democratic officials finally realised the gravity of the attack and brought in external cybersecurity experts.”
But it was too late, as the election results have shown.
The story: Top Democrat’s emails hacked by Russia after aide made typo, investigation finds
Learn why phishing is so effective and how you can avoid it: 15 steps to maximize your financial data protection, 10. he fell prey to the same scam twice and lost $1,350.
In 2007, Justin was at a difficult point in his life.
Unemployed, with a weak skill set and verging on alcoholism, Justin decided to turn his life around by moving to Italy.
Determined to find a cheap flight, Justin searched for sellers of frequent flyer miles.
He found two sellers and talked to them over the phone. One of them even sent him a photo of his driver’s license. In a twisted sequence of events, both of them scammed him for a total sum of 1350$.
Sounds unlikely?
Think again. Justin tried to find a cheap shortcut and get that ‘too good to be true’ deal and became blind to any potential scammers.
Plus, the phone conversations and photos helped dispel any suspicions he might have. This is how most scamming attempts succeed, by preying on people who give in to the fear of missing out.
The story: How I Lost $1,350 by Falling for the Same Internet Scam Twice in One Week
Learn more about how social scams work and how to avoid them: social scams – the full breakdown and protection plan, 11. who would want to be you some can even become you..
One day, Laura received a call from her credit card company, saying someone else had tried to obtain a credit card using her name, address and social security number.

Eventually, she guessed the answers and saw the extent of the damage.
The impersonator had created more than 50 accounts in Laura’s name, and got credit for utilities such as heat, cable, electricity and even a newspaper subscription.
What’s more, the companies went after Laura in order to get their money back.
After notifying the police and tracking down the impersonator, Laura got a court order and managed to fix a lot of the damage, but only after a lot of sweat and stress.
While her case was a fortunate one, few people share her luck and this story should act as a reminder to always safeguard your personal information.
Another stolen identity case created a buzz on Reddit . This user had an argument with an old roommate, who then decided to take revenge.
He created social media accounts using the victim’s name, photoshopping the person with an ISIS flag and posting questionable content The story: ‘Someone had taken over my life’
While a scary and multifaceted attack, it is possible to protect yourself against these types of threats. Here are 20 SECURITY STEPS YOU SHOULD TAKE TO PREVENT IDENTITY THEFT.
12. when your workplace, a gaming giant, gets hit.
In late 2014, one of the biggest and most expensive hacks ever recorded took place at Sony and one employee reveals the inside situation.

Half of the companies 6800 computers and servers were rendered dead and had ALL of their information stolen and deleted.
As a result, employees had to rewrite every single deleted file by hand. Paper became the main form of communication, used in written memos and to-do-lists, even their salaries were paid using hand-written checks.
The damage didn’t stop there.
The hackers got a hold of employee personal information. The source of the article had to change all her credit card passwords, Facebook, Amazon and eBay accounts, almost 30 accounts in total.
The story: I work at Sony Pictures. This is what it was like after we got hacked.
Because of their size and income, companies are frequent targets for hackers. here is a list of 10 critical corporate cybersecurity risks, 13. the casual, public wi-fi hack.
Maurits Martijn, a Dutch journalist at De Correspondent, entered a busy Amsterdam café with Wouter Slotboom, an ethical hacker.
Within a few minutes, Slotboom had set up his gear, consisting of a laptop and a small black device and connected to the coffeehouses Wi-Fi.

All you needed was around $80-90 worth of software and equipment, an average intelligence and that was it, a few minutes was all it took to get a hold of a few dozen users personal information.
Slotboom’s small, black device could fool a phone into connecting to his own Wi-Fi network, giving him control over the entire traffic coming and going from a device.
If Slotboom wanted to, he could wait until one user wrote in his email address and password and then take it over.
With it, he could control most of the services registered on that email.
While you don’t need to be paranoid every time you connect to a public Wi-Fi, it’s best if you know the risks of doing so.
The story: Don’t use public Wi-Fi when reading this article.
There are ways in which you can stay safe on public hotspots: 11 security steps to stay safe on public wi-fi networks, 14. customer support falls prey to a social engineering hack.
The impersonator then used Eric’s fake information in a conversation with an Amazon customer support representative and found out his real address and phone number.
Using Eric’s real information, the impersonator got in touch with various services and even managed to issue a new credit card in Eric’s name.
Eric got wind of his impersonator’s efforts by reading the customer support transcripts, and also found out his real purpose: to get the last 4 digits of his credit card.
Amazon didn’t do anything to protect Eric’s account, even though he repeatedly signaled the problem, so he finally decides to switch from Amazon to Google.
As a parting note, he gets an email from Amazon implying they have provided the impersonator with the last 4 digits of his credit card.
This story about this guy’s tumultuous experience with Amazon will make you think twice about storing confidential information in your online accounts.
The fact that Amazon failed to protect his account and look into the matter shows how a lack of cyber security education can endanger users
The story: Amazon’s customer service backdoor
Here is a guide on how to protect yourself against social engineering attacks, 15. hotel managers and clients had nightmares due to one lock hack.
In this Forbes story , reporters chronicles the chaos experienced by hotel managers and the panic felt by their customers after a burglar used online hacking tools to bypass the electronic locks on the doors.

He then used that Onity-lock hack to do a series of break-ins. How did this cautionary tale end?
On a bittersweet note.
The original burglar is serving a prison sentence, but the electronic locks in question can still be easily hacked.
A Wired reporter tried it himself, almost 6 years after the original Onity hack, and it still worked. He managed to break into a hotel room.
His story is amazing and it follows the birth of the original hacking method, how the burglar got to it and what came out of the entire publicized event.
The story: The Hotel Room Hacker
If you rely on electronic locks and other IoT devices to secure your belongings, this guide will be very useful: IOT SECURITY – All You Need To Know And Apply
16. the moderna conundrum.
According to Reuters and other major publications , Moderna Inc, one of the three biotech companies developing an efficient COVID-19 vaccine, has come under attack in late July. US’s Justice Department and the FBI have accused two Chinese nationals in this case.
They have been charged with spying on the American biotech company and three other targets in a bid to slow down or effectively stop the development of the COVID-19 vaccine.
Source from inside the FBI has revealed that the two arrested Chinese citizens are part of a hacking group funded by the Chinese government.
The company has emerged unscathed from the incident. No data has left Moderna’s databanks and the network remains intact.
The story: China-backed hackers ‘targeted COVID-19 vaccine firm Moderna’
These stories may help you realize that not protecting your information and relying on other Internet users to be nice and play fair is not a viable strategy.
Cyber criminals don’t care about the consequences of their attacks.
They only want to reach their purpose, and sometimes that purpose may have nothing to do with you.
You could just be a collateral victim, but the aftermath would be all too real for you.
Ana Dascalescu
Cyber Security Enthusiast
The Atlantic wrote about cyberflâneur and I think that's the best way to describe myself. Or maybe a digital jack-of-all-trades with a long background in blogging, video production and streaming. I spend my waking hours snooping through online communities of all types, from Reddit to security forums, from gaming blogs to banal social media platforms like Instagram. Sometimes I even contribute to those communities.
Related Articles
CHECK OUR SUITE OF 11 CYBERSECURITY SOLUTIONS
- Cyber Resources And Beginners
- Cyber Security Glossary
- The Daily Security Tip
- Cyber Security For Small Business Owners
- Cybersecurity Webinars
- About Heimdal®
- Press Center
- Partner with us
- Affiliate Program
© 2024 Heimdal ®
Vat No. 35802495, Vester Farimagsgade 1, 2 Sal, 1606 København V

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/itl/smallbusinesscyber/cybersecurity-basics/case-study-series
Small Business Cybersecurity Corner
Small business cybersecurity case study series.
Ransomware, phishing, and ATM skimming are just a few very common and very damaging cybersecurity threats that Small Businesses need to watch out for. The following Case Studies were created by the National Cyber Security Alliance , with a grant from NIST, and should prove useful in stimulating ongoing learning for all business owners and their employees.
- Case 1: A Business Trip to South America Goes South Topic: ATM Skimming and Bank Fraud
- Case 2: A Construction Company Gets Hammered by a Keylogger Topic: Keylogging, Malware and Bank Fraud
- Case 3: Stolen Hospital Laptop Causes Heartburn Topic: Encryption and Business Security Standards
- Case 4: Hotel CEO Finds Unwanted Guests in Email Account Topic: Social Engineering and Phishing
- Case 5: A Dark Web of Issues for a Small Government Contractor Topic: Data Breach
Landmark Cyber Law cases in India
- Post author By ashwin
- Post date March 1, 2021

By:-Muskan Sharma
Introduction
Cyber Law, as the name suggests, deals with statutory provisions that regulate Cyberspace. With the advent of digitalization and AI (Artificial Intelligence), there is a significant rise in Cyber Crimes being registered. Around 44, 546 cases were registered under the Cyber Crime head in 2019 as compared to 27, 248 cases in 2018. Therefore, a spike of 63.5% was observed in Cyber Crimes [1] .
The legislative framework concerning Cyber Law in India comprises the Information Technology Act, 2000 (hereinafter referred to as the “ IT Act ”) and the Rules made thereunder. The IT Act is the parent legislation that provides for various forms of Cyber Crimes, punishments to be inflicted thereby, compliances for intermediaries, and so on.
Learn more about Cyber Laws Courses with Enhelion’s Online Law Course !
However, the IT Act is not exhaustive of the Cyber Law regime that exists in India. There are some judgments that have evolved the Cyber Law regime in India to a great extent. To fully understand the scope of the Cyber Law regime, it is pertinent to refer to the following landmark Cyber Law cases in India:
- Shreya Singhal v. UOI [2]
In the instant case, the validity of Section 66A of the IT Act was challenged before the Supreme Court.
Facts: Two women were arrested under Section 66A of the IT Act after they posted allegedly offensive and objectionable comments on Facebook concerning the complete shutdown of Mumbai after the demise of a political leader. Section 66A of the IT Act provides punishment if any person using a computer resource or communication, such information which is offensive, false, or causes annoyance, inconvenience, danger, insult, hatred, injury, or ill will.
The women, in response to the arrest, filed a petition challenging the constitutionality of Section 66A of the IT Act on the ground that it is violative of the freedom of speech and expression.
Decision: The Supreme Court based its decision on three concepts namely: discussion, advocacy, and incitement. It observed that mere discussion or even advocacy of a cause, no matter how unpopular, is at the heart of the freedom of speech and expression. It was found that Section 66A was capable of restricting all forms of communication and it contained no distinction between mere advocacy or discussion on a particular cause which is offensive to some and incitement by such words leading to a causal connection to public disorder, security, health, and so on.
Learn more about Cyber Laws with Enhelion’s Online Law firm certified Course!
In response to the question of whether Section 66A attempts to protect individuals from defamation, the Court said that Section 66A condemns offensive statements that may be annoying to an individual but not affecting his reputation.
However, the Court also noted that Section 66A of the IT Act is not violative of Article 14 of the Indian Constitution because there existed an intelligible difference between information communicated through the internet and through other forms of speech. Also, the Apex Court did not even address the challenge of procedural unreasonableness because it is unconstitutional on substantive grounds.
- Shamsher Singh Verma v. State of Haryana [3]
In this case, the accused preferred an appeal before the Supreme Court after the High Court rejected the application of the accused to exhibit the Compact Disc filed in defence and to get it proved from the Forensic Science Laboratory.
The Supreme Court held that a Compact Disc is also a document. It further observed that it is not necessary to obtain admission or denial concerning a document under Section 294 (1) of CrPC personally from the accused, the complainant, or the witness.
- Syed Asifuddin and Ors. v. State of Andhra Pradesh and Anr. [4]
Facts: The subscriber purchased a Reliance handset and Reliance mobile services together under the Dhirubhai Ambani Pioneer Scheme. The subscriber was attracted by better tariff plans of other service providers and hence, wanted to shift to other service providers. The petitioners (staff members of TATA Indicom) hacked the Electronic Serial Number (hereinafter referred to as “ESN”). The Mobile Identification Number (MIN) of Reliance handsets were irreversibly integrated with ESN, the reprogramming of ESN made the device would be validated by Petitioner’s service provider and not by Reliance Infocomm.
Questions before the Court: i) Whether a telephone handset is a “Computer” under Section 2(1)(i) of the IT Act?
- ii) Whether manipulation of ESN programmed into a mobile handset amounts to an alteration of source code under Section 65 of the IT Act?
Decision: (i) Section 2(1)(i) of the IT Act provides that a “computer” means any electronic, magnetic, optical, or other high-speed data processing device or system which performs logical, arithmetic, and memory functions by manipulations of electronic, magnetic, or optical impulses, and includes all input, output, processing, storage, computer software or communication facilities which are connected or related to the computer in a computer system or computer network. Hence, a telephone handset is covered under the ambit of “computer” as defined under Section 2(1)(i) of the IT Act.
(ii) Alteration of ESN makes exclusively used handsets usable by other service providers like TATA Indicomm. Therefore, alteration of ESN is an offence under Section 65 of the IT Act because every service provider has to maintain its own SID code and give its customers a specific number to each instrument used to avail the services provided. Therefore, the offence registered against the petitioners cannot be quashed with regard to Section 65 of the IT Act.
- Shankar v. State Rep [5]
Facts: The petitioner approached the Court under Section 482, CrPC to quash the charge sheet filed against him. The petitioner secured unauthorized access to the protected system of the Legal Advisor of Directorate of Vigilance and Anti-Corruption (DVAC) and was charged under Sections 66, 70, and 72 of the IT Act.
Decision: The Court observed that the charge sheet filed against the petitioner cannot be quashed with respect to the law concerning non-granting of sanction of prosecution under Section 72 of the IT Act.
- Christian Louboutin SAS v. Nakul Bajaj & Ors . [6]
Facts: The Complainant, a Luxury shoes manufacturer filed a suit seeking an injunction against an e-commerce portal www.darveys.com for indulging in a Trademark violation with the seller of spurious goods.
The question before the Court was whether the defendant’s use of the plaintiff’s mark, logos, and image are protected under Section 79 of the IT Act.
Decision: The Court observed that the defendant is more than an intermediary on the ground that the website has full control over the products being sold via its platform. It first identifies and then promotes third parties to sell their products. The Court further said that active participation by an e-commerce platform would exempt it from the rights provided to intermediaries under Section 79 of the IT Act.
- Avnish Bajaj v. State (NCT) of Delhi [7]
Facts: Avnish Bajaj, the CEO of Bazee.com was arrested under Section 67 of the IT Act for the broadcasting of cyber pornography. Someone else had sold copies of a CD containing pornographic material through the bazee.com website.
Decision: The Court noted that Mr. Bajaj was nowhere involved in the broadcasting of pornographic material. Also, the pornographic material could not be viewed on the Bazee.com website. But Bazee.com receives a commission from the sales and earns revenue for advertisements carried on via its web pages.
The Court further observed that the evidence collected indicates that the offence of cyber pornography cannot be attributed to Bazee.com but to some other person. The Court granted bail to Mr. Bajaj subject to the furnishing of 2 sureties Rs. 1 lakh each. However, the burden lies on the accused that he was merely the service provider and does not provide content.
- State of Tamil Nadu v. Suhas Katti [8]
The instant case is a landmark case in the Cyber Law regime for its efficient handling made the conviction possible within 7 months from the date of filing the FIR.
Facts: The accused was a family friend of the victim and wanted to marry her but she married another man which resulted in a Divorce. After her divorce, the accused persuaded her again and on her reluctance to marrying him, he took the course of harassment through the Internet. The accused opened a false e-mail account in the name of the victim and posted defamatory, obscene, and annoying information about the victim.
A charge-sheet was filed against the accused person under Section 67 of the IT Act and Section 469 and 509 of the Indian Penal Code, 1860.
Decision: The Additional Chief Metropolitan Magistrate, Egmore convicted the accused person under Section 469 and 509 of the Indian Penal Code, 1860 and Section 67 of the IT Act. The accused was subjected to the Rigorous Imprisonment of 2 years along with a fine of Rs. 500 under Section 469 of the IPC, Simple Imprisonment of 1 year along with a fine of Rs. 500 under Section 509 of the IPC, and Rigorous Imprisonment of 2 years along with a fine of Rs. 4,000 under Section 67 of the IT Act.
- CBI v. Arif Azim (Sony Sambandh case)
A website called www.sony-sambandh.com enabled NRIs to send Sony products to their Indian friends and relatives after online payment for the same.
In May 2002, someone logged into the website under the name of Barbara Campa and ordered a Sony Colour TV set along with a cordless telephone for one Arif Azim in Noida. She paid through her credit card and the said order was delivered to Arif Azim. However, the credit card agency informed the company that it was an unauthorized payment as the real owner denied any such purchase.
A complaint was therefore lodged with CBI and further, a case under Sections 418, 419, and 420 of the Indian Penal Code, 1860 was registered. The investigations concluded that Arif Azim while working at a call center in Noida, got access to the credit card details of Barbara Campa which he misused.
The Court convicted Arif Azim but being a young boy and a first-time convict, the Court’s approach was lenient towards him. The Court released the convicted person on probation for 1 year. This was one among the landmark cases of Cyber Law because it displayed that the Indian Penal Code, 1860 can be an effective legislation to rely on when the IT Act is not exhaustive.
- Pune Citibank Mphasis Call Center Fraud
Facts: In 2005, US $ 3,50,000 were dishonestly transferred from the Citibank accounts of four US customers through the internet to few bogus accounts. The employees gained the confidence of the customer and obtained their PINs under the impression that they would be a helping hand to those customers to deal with difficult situations. They were not decoding encrypted software or breathing through firewalls, instead, they identified loopholes in the MphasiS system.
Decision: The Court observed that the accused in this case are the ex-employees of the MphasiS call center. The employees there are checked whenever they enter or exit. Therefore, it is clear that the employees must have memorized the numbers. The service that was used to transfer the funds was SWIFT i.e. society for worldwide interbank financial telecommunication. The crime was committed using unauthorized access to the electronic accounts of the customers. Therefore this case falls within the domain of ‘cyber crimes”. The IT Act is broad enough to accommodate these aspects of crimes and any offense under the IPC with the use of electronic documents can be put at the same level as the crimes with written documents.
The court held that section 43(a) of the IT Act, 2000 is applicable because of the presence of the nature of unauthorized access that is involved to commit transactions. The accused were also charged under section 66 of the IT Act, 2000 and section 420 i.e. cheating, 465,467 and 471 of The Indian Penal Code, 1860.
- SMC Pneumatics (India) Pvt. Ltd. vs. Jogesh Kwatra [9]
Facts: In this case, Defendant Jogesh Kwatra was an employee of the plaintiff’s company. He started sending derogatory, defamatory, vulgar, abusive, and filthy emails to his employers and to different subsidiaries of the said company all over the world to defame the company and its Managing Director Mr. R K Malhotra. In the investigations, it was found that the email originated from a Cyber Cafe in New Delhi. The Cybercafé attendant identified the defendant during the enquiry. On 11 May 2011, Defendant was terminated of the services by the plaintiff.
Decision: The plaintiffs are not entitled to relief of perpetual injunction as prayed because the court did not qualify as certified evidence under section 65B of the Indian Evidence Act. Due to the absence of direct evidence that it was the defendant who was sending these emails, the court was not in a position to accept even the strongest evidence. The court also restrained the defendant from publishing, transmitting any information in the Cyberspace which is derogatory or abusive of the plaintiffs.
The Cyber Law regime is governed by the IT Act and the Rules made thereunder. Also, one may take recourse to the provisions of the Indian Penal Code, 1860 when the IT Act is unable to provide for any specific type of offence or if it does not contain exhaustive provisions with respect to an offence.
However, the Cyber Law regime is still not competent enough to deal with all sorts of Cyber Crimes that exist at this moment. With the country moving towards the ‘Digital India’ movement, the Cyber Crimes are evolving constantly and new kinds of Cyber Crimes enter the Cyber Law regime each day. The Cyber Law regime in India is weaker than what exists in other nations.
Hence, the Cyber Law regime in India needs extensive reforms to deal with the huge spike of Cyber Crimes each year.
[1] “Crime in India – 2019” Snapshots (States/UTs), NCRB, available at: https://ncrb.gov.in/sites/default/files/CII%202019%20SNAPSHOTS%20STATES.pdf (Last visited on 25 th Feb; 2021)
[2] (2013) 12 SCC 73
[3] 2015 SCC OnLine SC 1242
[4] 2005 CriLJ 4314
[5] Crl. O.P. No. 6628 of 2010
[6] (2018) 253 DLT 728
[7] (2008) 150 DLT 769
[8] CC No. 4680 of 2004
[9] CM APPL. No. 33474 of 2016
- Tags artificial intelligence courses online , aviation law courses india , best online law courses , business law course , civil courts , civil law law courses online , civil system in india , competition law , corporate law courses online , covaxin , covid vaccine , diploma courses , diploma in criminal law , drafting , fashion law online course , how to study law at home , indian law institute online courses , innovation , Intellectual Property , international law courses , international law degree online , international law schools , introduction to law course , invention , knowledge , labour law course distance learning , law , law certificate courses , law certificate programs online , law classes , law classes online , law college courses , law courses in india , law firms , law schools , lawyers , learn at home , legal aid , legal courses , online law courses , online law courses in india , pfizer , pleading , space law courses , sports law , sports law courses , study criminal law online , study later , study law at home , study law by correspondence , study law degree online , study law degree online australia , study law distance education , study law distance learning , study law online , study law online free , study law online uk , study legal studies online , teach law online , technology law courses , trademark
- Open access
- Published: 24 April 2019
Responding to victimisation in a digital world: a case study of fraud and computer misuse reported in Wales
- Sara Giro Correia ORCID: orcid.org/0000-0003-0261-6872 1
Crime Science volume 8 , Article number: 4 ( 2019 ) Cite this article
13k Accesses
16 Citations
15 Altmetric
Metrics details
This paper presents the early results of a study exploring computer misuse and fraud victimisation in Wales, United Kingdom (UK). The results presented here describe the quality of the data available to local forces, the characteristics and heterogeneity of the victims who report incidents and the nature of the police response at a local level. The significance of these results is considered within the enforcement and victimisation policy context that surrounds computer misuse and fraud. It is argued that while Action Fraud data provides a rich source of data with respect to victims’ needs, specific improvements in data collection and processing could aid local forces in the delivery (or facilitation) of a more victim-focused response. Alongside this, the results highlight how an adequate police response must take victim heterogeneity into account, both at national and local levels. Finally, better understandings of vulnerability (both theoretically informed and empirically tested) are necessary, on which to build an adequate victim-response to these crime types.
Introduction
Experiences of computer misuse (CM) and fraud victimisation have increasingly occupied the public sphere. Their significance was highlighted in the United Kingdom (UK) from 2017, as these crimes integrated the yearly crime estimates produced by the Office for National Statistics (ONS). Recent estimates indicate that there were 3.25 million incidents of fraud and 1.24 million incidents of CM Footnote 1 in the year ending March 2018 (ONS 2018a ), increasing the grand total from 6.01 to 10.57 million estimated crimes ( Ibid. ). Alongside these figures stands the considerable investment government has committed to cyber security—£1.9 billion by 2021 (HM Government 2016 ). Footnote 2 Finally, the threat and harm posed by these crime types have also attracted attention. Cases such as the 2007 cyber-attack on Estonia and the Stuxnet worm aimed at Iran stand as examples of large national infrastructure attacks. Recently, 2017 was characterised by ransom ware attacks including WannaCry, which disrupted organisations across the world, including UK hospitals. Since, data-breaches have made successive headlines, with millions of personal data records lost. However, it has been suggested that the mass media’s attention often focuses on ideal victims and perpetrators (Christie 1986 ) and fails to properly scrutinise ‘official’ narratives, primarily put forward by criminal justice institutions and large business victims (Jarvis et al. 2015 ; Levi 2006 , 2008 ). As such, better and empirically grounded understandings of these crime types are necessary.
At the same time, the process by which victims report CM and fraud and the ways in which victim services are delivered have changed significantly in the UK. Firstly, the reporting of cybercrime and fraud has improved with the introduction of the national reporting centre, Action Fraud (AF). Its introduction mirrored the equivalent in the USA and Canada and had been recommended by The Fraud Review (2006) and academic experts (Button et al. 2009a ; Levi and Burrows 2008 ). Additionally, victim support services have been considerably decentralised from their previous model (Hall 2018 ). These services became (or reverted to) local delivery, with the addition of competitive bidding for service providers wishing to deliver those services, funded through the Office of the Police and Crime Commissioners (PCCs) ( Ibid. ). These changes have taken place in the context of a computer crime and fraud policing strategy which, following the counter-terrorism ‘CONTEST’ model, is divided into ‘4 Ps’: ‘Pursue’ offenders through prosecution and disruption, ‘Prepare’ to mitigate against the impact of incidents, ‘Protect’ individuals, organisations and systems against being victimised and ‘Prevent’ people from engaging in crime (City of London Police 2015b ; HM Government 2013 , 2018). The ‘Protect’ strand is the one that is more clearly linked to a victim-focused response. Here, discussions with stakeholders revealed a policy of local delivery supported by national resources such as the NFIB. The responsibility of ‘volume’ crime prevention (i.e. that which is not considered ‘serious organised crime’) falls to local police forces, following prioritisation by PCCs and Chief Constables (City of London Police 2015a ). Third sector organisations such as Victim Support are meant to lead on addressing victim impact and reducing repeat victimisation (Draft NPFS 2015a , b ). In addition, at the local level Police and Crime Reduction Plans often strategically focus ‘Protect’ activity on ‘vulnerable’ victims (e.g. Dyfed Powys PCC 2017 ; Gwent PCC 2017 ; North Wales PCC 2017 ; South Wales PCC 2017 ). Thus, this area of crime control requires the interaction of UK law enforcement agencies across three levels: the National Fraud Intelligence Bureau (NFIB) determines what is investigated, the Regional Organised Crime Units (ROCUs) support strategic delivery and large-scale investigations and the local forces investigate and deliver victim-response ‘on the ground’.
In this context, this paper seeks to critically engage with challenges of responding the computer misuse and fraud victimisation by considering three questions: (1) How can data collection be improved to best enable local forces to meet victim needs? (2) How heterogeneous are victims who report CM and fraud in Wales? And (3) How is law enforcement responding to these crimes at a local level? It does so by drawing on the early results of the quantitative element of a larger mixed-methods study, utilising a sample of crimes reported via AF, for a period of 2 years (1st of October 2014 to the 30th of September 2016), within the four Welsh police forces. In answering these questions, this paper also concludes by pointing to avenues for future research. This paper focuses on fraud and CM for two reasons. Firstly, except for some important contributions (Buchanan and Whitty 2014 ; Button et al. 2009b , 2014 ; Whitty 2015 ) there remains limited academic study of victimisation in this area. Secondly, the initial scoping research indicated that the overall impact of these crimes on victims, especially in terms of their volume and associated costs, as well as the vulnerability of victims were priorities in public discourse and academic literature (Anderson et al. 2013 ; Blakeborough and Correia 2018 ; Buchanan and Whitty 2014 ; Button et al. 2009b , 2014 ; Home Office 2018b ; McGuire and Dowling 2013 ; Whitty 2015 ).
Finally, what is meant by computer misuse and fraud in this paper should be clarified and the author’s avoidance of the term ‘cybercrime’ explained. ‘Cybercrime’ is used to refer to a diverse range of illegal activity which occurs primarily within an electronic environment, enabled by the Internet (Yar 2006 ). Footnote 3 Given the wide scope of the term however, it is useful to break ‘cybercrime’ down further into sub-categories. As such, the author started this enquiry by drawing on several existing typologies (particularly Home Office 2018a , b ; Levi et al. 2017 ; Levi and Burrows 2008 ; McGuire and Dowling 2013 ; Yar 2006 ), to identify what types of (cyber) crime may be of interest (see Fig. 1 ). However, ‘cybercrime’ is a contested term and its usefulness may be questioned altogether (Grabosky and Smith 1998 ), especially where the aim is to understand victims’ perspective and the extent to which victim policy is adequate and effectively implemented. Crucially for this study, the boundaries between “cyber” and “traditional” crime were found to be blurred. In line with previous research (Levi et al. 2017 ), Footnote 4 it became apparent that the author’s attempt at coding data according to an on/offline dichotomy was impossible. Footnote 5 Furthermore, the Modus Operandi (MO) of a crime should not substantially change the principles that inform victim response. As such, this article will not exclusively consider crimes with a “cyber” element, but instead cases of victimisation associated with crimes of fraud and computer misuse, as defined by the Fraud Act 2006 and the Computer Misuse Act 1990 respectively, whether they have on/offline elements or both. Footnote 6
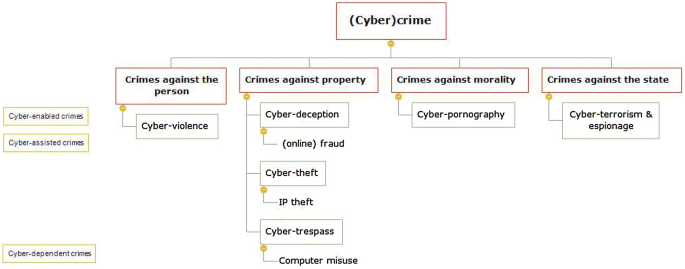
Cybercrime typology, based on Home Office ( 2018a , b ), Levi et al. ( 2017 ), Levi and Burrows ( 2008 ), McGuire and Dowling ( 2013 ) and Yar ( 2006 )
This paper reports on a sub-set of early results from a study based on N = 17,049 computer misuse (CM) and fraud reports, made by victims within the Welsh police forces (Dyfed/Powys, Gwent, North Wales and South Wales), via the UK‘s national reporting centre Action Fraud (AF). The data relating to all crimes Footnote 7 reported over a 2-year period between the 1st October 2014 and the 30th September 2016 were returned to the respective forces who agreed to share this with the researcher via the Southern Wales Regional and Organised Crime Unit (ROCU), a partner organisation in this project. While it was possible to access the full population of AF victim reports at the time the data was collected, insights from crime reports collected prior to October 2014 were considered less reliable due to the transition into the AF reporting system. As such, all records available at the point of data collection from October 2014 were collected.
To undertake this research, the author underwent a process of security vetting, enabling her to access, clean and anonymise the data within the ROCU’s secure environment. The anonymised dataset was then further analysed at Swansea University, whose Ethics Board reviewed and approved the project prior to its commencement. Given the project’s aim to improve the response to victims of CM and fraud, a strong public-interest rationale justified the use of this administrative dataset. Nonetheless, as the original dataset identified victims of crime, the handling of this sensitive information carried the risk of loss of anonymity and subsequent harm to participants. As such, a strict protocol for data access, anonymisation, storage and reporting was followed in order ensure these risks were mitigated.
A data-driven mixed methods methodology was employed. Mixed-methods is understood as “the type of research in which a researcher… combines elements of qualitative and quantitative research approaches… for the purposes of breadth and depth of understanding and corroboration” (Johnson et al. 2007 , p. 123). AF reports contained both quantitative and qualitative data, each suited to different methods of analysis and to answer different research questions. As such, a mixed-methods approach was appropriate and a sequential explanatory design used (Creswell et al. 2003 ; Ivankova et al. 2006 ). This paper reports on the first stage in this sequence, where structured data from the AF database was quantitatively analysed, to explore reported incidents and police response.
A descriptive statistical analysis of the dataset was undertaken at first instance, including an exploration and testing of variables’ distribution and measures of central tendency. This enabled a better understanding of the quality of the data and the characteristics of the population of reporting victims. Subsequently, several theoretically informed statistical hypotheses were tested using inferential frequentist methods. Given that the dataset contained a variety of categorical (e.g. gender), interval (e.g. number of repeats) and ratio data (e.g. loss and age), statistical tests were carried as appropriate. In this paper results relating to Pearson Chi squared tests (χ 2 ) are reported to identity significant differences between sub-groups of victims. The odds ratio and Cramèr’s V are reported where appropriate as measures of effect size. Finally, where χ 2 was found to provide limited insight, generalised linear models (GLMs) were used to aid visualisation and interpretation of results. GLMs replicate or replace many of the traditional statistical tests, while allowing the researcher to focus on interpretation of models through a standard (visual) method (Field et al. 2012 ; Fox 2003 ; Fox and Weisberg 2011 ; Hutcheson and Schaefer 2012 ; Hutcheson and Sofroniou 1999 ).
There are several limitations when using police recorded crime (PRC) for statistical analysis, and some are particular to CM and fraud (Flatley 2013 ; Levi and Burrows 2008 ). PRC only captures crime which was reported to and recorded by the police. As such, it provides an insight into reporting/recording rather than crime patterns or victimisation risk. This limitation is especially relevant with respect to the crime types under consideration as they are comparatively under-reported. It is estimated that only 14.5% of CM and fraud experienced by individuals were reported to the police in the year ending September 2018 (ONS 2019 , Tables A1 and A4). Footnote 8 In comparison, 55.9% of thefts were reported to the police in the same period ( Ibid. ). Footnote 9 In addition, concerns have been raised over the process of “criming”, i.e. attributing a crime label to a reported incident in accordance with the UK’s Home Office Counting Rules (HOCR) (Home Office 2015 ). Issues regarding compliance with HOCR and recording practices led to PRC losing its status as approved national statistics in 2014 (UKSA 2014 ). Footnote 10 Finally, high levels of ‘attrition’ have been reported in the recording of fraud and CM (Scholes 2018 ) and, as with administrative data more broadly, AF data was collected for the administration of justice and is thus not optimised for the purposes for which it was analysed here.
Nonetheless, AF data remains useful where the focus of the enquiry is the CJS response towards victims. While enquiry is limited to reported crime, it is also the case that responding to victim needs must start with those who come forward to report. Previous research has shown that trust in the police and a belief that the police can do something about the issue are important factors influencing whether victims report crime (MacDonald 2001 ; Skogan 1984 ; Zawitz et al. 1993 ). As such, an adequate police response is a factor in driving reporting behaviour. Previous research has also indicated that the victims’ perception of the seriousness of the crime, is the most important factor leading to a decision to report crime (Skogan 1984 ; Tarling and Morris 2010 ). Similarly, a cost–benefit analysis or the opportunity-costs for the victim involved in reporting also constitute factors in decisions to report crime (Goudriaan 2006 ; Skogan 1984 ). In fact, the seriousness of the crime and/or a cost–benefit rationale were given as prominent reasons for not reporting to AF—although lack awareness of the service was the most common reason cited for not reporting. Footnote 11 Finally, per the Victims’ Code, the seriousness and impact of the crime, victim characteristics such as living with a disability and circumstances such as being a repeat victim require an enhanced response from criminal justice agencies (MOJ 2015 ). The code extends to all victims of crime, the ‘right’ to be assessed according to such ‘vulnerability’ criteria. As such, one would expect to be able to identify within AF data significant detail to enable an adequate prioritisation and response to victims’ needs, as well as discharge victims’ service and procedural rights (Hall 2018 ).
As such, this paper will consider the quality of AF data in terms of two quality dimensions set out within the European Statistical System (Eurostat 2017 ; ONS 2018b ): (1) relevance and (2) accuracy and reliability. Relevance is the degree to which data meet the users existing and emerging needs. Accuracy and reliability concern whether the sourced data is accurately recorded and reliably reflect the reality they seek to capture. While PRC does not currently carry the quality seal of UK ‘official’ statistics, these principles remain are useful in considering the quality of AF data.
Results and discussion
Data quality.
Issues affecting the accuracy and reliability of AF data include data ‘missingness’ as well as errors in processing, measurement and coding. The level of missing data in salient AF variables was high and is summarised in Table 2 . Missingness was highly prevalent in the original variables, but also in the variables derived/coded by the author, due to lack of detail and inconsistencies in some records. For example, several variables were coded based on the free-text incident description. However, some descriptions were missing and the level of detail variable. In addition, 664 duplicates were found within the dataset, indicating some processing error before the data was shared with the local forces. Finally, the author’s manual coding exercise identified some inconsistencies with respect to the original AF coding, particularly in the attribution of crime type category to incidents e.g. a ‘Denial of Service attack’ (DOS) recorded where ‘Hacking’ would have been a more appropriate category.
Action Fraud data shared with local forces could be much improved in terms of its ‘fitness’ to be used to conduct victim vulnerability assessments. Extra fields which may enable local forces to develop a better picture of local victims’ needs include the type of victim (e.g. individual, business, charity or public sector organisation), gender, whether there is an on-line element to the incident, victim’s gender, whether the victim has accessibility needs or is a repeat victim. The author could derive some of this information from the dataset through a combination of automated and manual linkage and coding. However, this was a resource-intensive exercise which local forces may be unable to carry out. Finally, in discussions with stakeholders it transpired that some of this information is collected centrally by AF/NFIB but is not shared with local forces. Even within the arguably limited terms within which ‘vulnerability’ is defined in the Victims’ Code (MOJ 2015 ), Footnote 12 the data collected by AF and shared with local police forces appears insufficient to conduct a victim vulnerability assessment.
Victim heterogeneity
Significant differences were found with respect to crime types reported across victim characteristics, but the effect sizes were generally small. Differences in the crime types reported across victim groups are highlighted in Fig. 2 . Among individual victims, a significant difference was found with respect to crime types reported across gender (χ 2 (7) = 73.57, p < 0.01). However, in this case Cramer’s V (0.075) indicates that the effect size is small. Footnote 13 Nonetheless, the standardized residuals suggest that the difference is driven by females being significantly more likely to report Advance fee fraud (p < 0.01) and males significantly more likely to report Investment fraud (p < 0.01). Based on the odds ratio, the odds of a victim of Advance fee fraud being female are 1.24 times higher, while the odds of a victim of Investment fraud being male are 2.35 times higher. In terms of ethnicity, a significant difference was found between crime categories reported by victims identified as White and Other (χ 2 (7) = 18.17, p = 0.001, Cramér’s V = 0.05). The standardized residuals revealed that this was driven by the White ethnic group reporting significantly more advance fee fraud while conversely, the Other group reported significantly less. Finally, a derived variable for age category grouping age data into UK Census categories was created and a significant association between victim’s age category and the crime types they reported (χ 2 (84) = 525.63, p < 0.001 Footnote 14 ). However, the detail of what drives a significant χ 2 result becomes difficult to interpret where multiple categories result in large contingency tables. As such, the age category was re-coded into a new age variable split over four categories according to the age values for the first quartile, median (52) and third quartiles and a GLM predicting the logit of the probability of age category based on the crime reported was run in R statistics. The overall model significantly reduced residual deviance (χ 2 (21) = 375.1, p < 0.0001) and the model’s effect display (Fig. 3 ) clearly demonstrates that victims reporting Investment and Advance fee fraud are more likely to be older, whereas those reporting Hacking, service fraud and Malware/DDOS/Virus more likely to be younger victims. This result is confirmed in the table summarising the statistical parameters (Table 3 ).
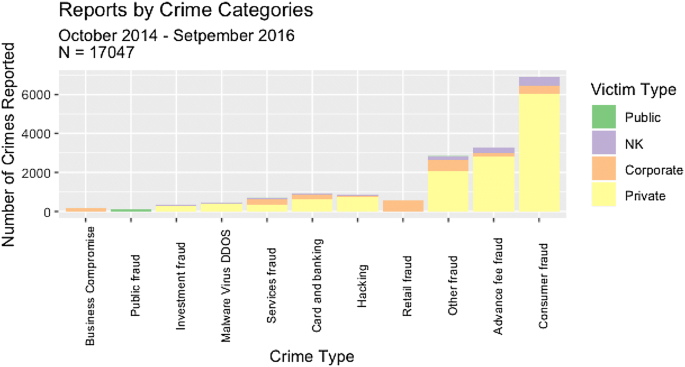
Frequency of type of crime (analytical categories) by victim type (N = 17,049)

Effect plot of GLM model of age category ~ crime category
With respect to reported financial loss, Table 4 shows that loss data is highly spread, highlighting considerable differences between victims. A considerable number of reports (2682 or 21%) indicated a reported loss of £0. This observation should be interpreted with caution for two reasons. Firstly, there was a considerable amount of missing data with respect to loss (30%). Secondly, where the victim has declared an estimation of loss at the time of reporting, this may not reflect longer term and/or indirect losses. On one hand these factors may result in an under-estimation of no-loss reports as the researcher noted that many no-loss reports were recorded as “missing data” in the loss variable (as opposed to “£0”). Footnote 15 On the other, there may be some instances where the victim reports the crime before the (total) loss is known to them. Nonetheless, this sample is indicative that a considerable proportion of reports made relate to ‘unsuccessful’ frauds or hacks. Footnote 16 The impact of financial loss being relative to the means of the victim, prioritising cases where there is some loss may help focus a victim response. Currently, only cases reporting losses over £100,000 should be automatically picked up for further action at NFIB (Scholes 2018 , p. 6). However, this amount is far beyond a typical loss being reported by individuals (or even businesses) and research has previously shown that cybercrime and fraud may result in victim-impacts beyond financial loss. These may include feelings of stress, physical or mental health problems, strain on relationships and worsening personal credit rating, among others (Button et al. 2012 ). As such, to adequately prioritise cases for a victim-focused response, the reporting system may also need to capture victim-impacts beyond financial loss.
Finally, victim heterogeneity was found in terms of the level of repeat victimisation within the sampled data. In order to assess repeat victimisation, two new variables were computed from the original dataset prior to anonymisation: ‘repeat premises’ is a count of the number of repeat reports from the same premises by matching victims’ first line of address and postcode (including all victims), ‘repeat victim’ is a count of how many reports from the same individual (excluding corporations) could be found by matching on victim’s name, date of birth and address. Footnote 17 Overall, 30% of business reports were associated with repeat premises and 10% of individual reports emanated from repeat victims. In addition, as indicated in Tables 5 and 6 , there was some variation in the number of times a business/individual repeatedly reported.
Police demand and response
Of all the reports received from victims within the four Welsh police forces for the period under study (N = 17,049), most crimes were reported by victims within the jurisdiction of South Wales police force (41%). This is unsurprising as this is the area with the largest population as well as the most internet access. Of the reports received, 19% were ‘actioned’ in some way (N = 3225), as indicated by having been recorded as referred to a police force, a partner agency, classified with an outcome or progressed in some way on the AF dataset. In approximately 5% of all cases, the force by whom the case of actioned is known. Table 3 provides a summary of the various categories of outcome identified in this dataset. Of the 19% of cases that were actioned, most were referred for enforcement-type actions. In contrast, fewer cases were actioned to address victim support needs as indicated by the lower percentage of cases referred to a partner agency (1%) and victim care (0.25%).
On one level, this is in line with the policy priorities set by the UK government in the National Cyber Security Strategy 2016–2021 (HM Government 2016 ) and the Serious and Organised Crime Strategy (HM Government 2013 , 2018). Both these strategies emphasise investigation of organised and persistent offenders and the protection of national critical infrastructure, while having less of a focus on victim support and what is referred to as high volume and/or low sophistication crime. In fact, the way in which Action Fraud reports are prioritised and selected for manual review by the NFIB for possible dissemination inherently favours investigation over other outcomes such as victim services or intelligence (Scholes 2018 ). At this crucial stage of the victim journey, AF reports are collected in the NFIB’s “Known Fraud” database, whereby a computer programme selects cases for review and dissemination based on the existence of potential lines of enquiry ( Ibid. ). Victim vulnerability is not assessed centrally in the same way. However, if victim-response is left for local forces to lead on, they would benefit from more guidance and better quality data (Table 7 ).
This paper considered the quality of the data which UK law enforcement agencies gather from victims of computer misuse and fraud offences, with respect to their information needs to provide an adequate victim response. Furthermore, it considered the heterogeneity of the victims who report and the level of police response. The analysis presented draws on the early results from a mixed-methods sequential study based on a sample of crime reports made within the four Welsh police forces to Action Fraud (AF), the UK’s national reporting centre.
It is argued that AF data provides a rich data source to identify victim needs. At the same time, specific improvements in data collection and processing could aid local forces in the delivery of a victim-focused response, thereby properly addressing the government’s priorities as set out in the Victims Charter. As it stands, the data collected by AF and shared with local police forces appears insufficient to conduct a victim vulnerability assessment. In addition, quality issues and under-reporting will negatively impact on the strategic insight that can be drawn from this data.
While no large differences were found with respect to the types of crimes reported across demographic characteristics, there was some heterogeneity in terms of the financial losses and level of repeat victimisation. The proportion of no-loss reports suggests that a victim-focused response needs to capture victim-impacts beyond financial loss. In addition, a small number of victims reported repeatedly over the time-period in question. Further research is needed to substantiate the link between repeat victimisation and vulnerability.
The meaning of ‘vulnerability’ also needs to be better understood in relation to victims of CM and fraud. The Code of Practice for Victims of Crime (MOJ 2015 ) and the crime plans developed by the Police and Crime Commissioners for each of the Welsh police forces (Dyfed Powys PCC 2017 ; Gwent PCC 2017 ; North Wales PCC 2017 ; South Wales PCC 2017 ) all commit to protecting and responding to the needs of vulnerable victims. However, little is currently done in the way of analysing AF data for indicators of vulnerability. To achieve this, further research is needed into what these factors and indicators are. Once vulnerability is properly understood with respect to these crime types, it is suggested that applying the latest technology such as machine learning to developing a referral system for victim support services would go some way to putting the victim at the centre of computer crime and fraud policy. This would require however, a higher level of accuracy in the recording of these crime types. Alongside this, it is important to ensure that the various levels of policing and victim support responsibility do not result in a lack of ownership of victim support services.
Including computer virus and unauthorised access to personal information.
Up from £860 million in the previous 5-year term. To illustrate de enormity of this investment, this sum would be sufficient to give every individual in the UK over £6000 over the same period.
This includes new crimes which did not exist prior to networked computers (cyber-dependent crimes), as well as crimes which pre-date the Internet but have been significantly “transformed” by it (cyber-enabled) (Wall 2001 ). To these we may also add cyber-assisted crimes, where ICT is used “in the course of criminal activity which would take place anyway” (Levi et al. 2017 , p. 81).
In a study that analysed 106,681 crime reports made to Action Fraud across police forces in England and Wales, between October to December 2014, the authors identified that the most common mode by which offenders first contacted their victims was by phone or text (35%), followed by contact after the victim visited a website (18%), contact in person (12%), by letter and fax (11%) and by email (8%) (Levi et al. 2017 , p. 82).
This was not surprising with respect to fraud as many Modus Operandi (MO) have been found to straddle the on/offline divide (e.g. Button et al. 2012 ; Gini et al. 2017 ; Levi 2017 ; Levi et al. 2017 ).
At the time of writing, Home Office Counting Rules define 15 fraud categories relevant to individual and business victims (containing a further 24 sub-categories between them) and three computer misuse categories (with a further seven sub-categories between them). In total, this amounts to eight unique categories of computer misuse offences and 41 unique fraud categories. Given that working with 49 categories would be impractical and of limited statistical use, the crime categories in the original dataset was combined and re-coded into nine fraud categories and two computer misuse categories as specified in Table 1 .
‘Crimes’ include all cases reported and recorded as crimes by Action Fraud, following the Home Office Counting Rules.
Calculation based on a total number of fraud and computer misuse offences estimated at 4,477,000 for the UK population in the year ending September 2018 (Table A1), against the number of such offences reported to the police for the same period at 650,051 (Table A4). The count including reports from industry bodies was used as some cases captured in the CSEW are unlikely to be recorded by Action Fraud, as a result of the application of Home Office Counting Rules.
Calculation based on a total number of theft offences estimated at 3,574,000 for the UK population in the year ending September 2018 (Table A1), against the number of theft offences reported to the police for the same period at 1,998,876 (Table A4).
The removal of the designation of “national statistics” from police recorded crime can therefore be interpreted to mean that police recorded crime—which includes the crime data supplied by police forces and Action Fraud (now run by a private provider for the National Fraud Investigative Bureau) to the Home Office—does not meet identified user needs; are not produced, managed and disseminated to high standards; and its limitations not well explained.
While ONS provided respondents with a wider selection of reasons (ONS 2017 , Table 2 ), these were combined for ease of analysis by this researcher into “never heard of Action Fraud” (66%), “cost–benefit rationale” (19%), “crime reported elsewhere” (14%), “private matter” (8%), “other” (8%) and “don't know” (1%).
The Victims Code defines a victim as “a natural person who has suffered harm, including physical, mental or emotional harm or economic loss which was directly caused by a criminal offence” (2015, p. 2). Furthermore, there are three categories of victims which are entitled to an enhanced service under the code: (1) victims of the most serious crimes, (2) persistently targeted victims and (3) vulnerable or intimidated victims. While victims of cybercrime and fraud are unlikely to fall under the first sub-category of victim entitled to enhanced service, they may fit the categories of persistently targeted, vulnerable or intimidated victims.
Cramér’s V varies from 0 to 1, with a 1 indicting a perfect association.
There were two cells with minimum expected frequencies below 5 and the minimum expected frequency overall was 4.4. However, as previously noted, with a larger contingency table it is acceptable to have up to 20% of expected frequencies below 5, given that no expected frequencies are below 1 (Field et al. 2012 , p. 818).
At the same time, the researcher also found instances where a loss amount was recorded by Action Fraud within free-text field for the incident description, but this was not recorded in the appropriate numerical variable. Issues of data accuracy and usefulness are returned to in the conclusion to this paper.
Although according to the Fraud Act 2006 the offence of fraud is complete when a false representation is made, regardless of its outcome.
In order to maximise accuracy, all discrepancies between these two variables were manually checked as differences in spelling could lead to errors in the automated counts.
Abbreviations
Action Fraud
computer misuse
Crime Survey for England and Wales
generalised linear model
Modus Operandi
Ministry of Justice (UK)
National Fraud Intelligence Bureau
Office for National Statistics
Police and Crime Commissioners
police recorded crime
Regional Organised Crime Unit
United Kingdom
Anderson, R., Barton, C., Böhme, R., Clayton, R., van Eeten, M. J. G., Levi, M., et al. (2013). Measuring the cost of cybercrime (pp. 265–300). Berlin: Springer. https://doi.org/10.1007/978-3-642-39498-0_12 .
Book Google Scholar
Blakeborough, L., & Correia, S. (2018). The scale and nature of fraud: A review of the evidence . Retrieved from https://www.gov.uk/government/publications/the-scale-and-nature-of-fraud-a-review-of-the-evidence . Accessed 11 Apr 2019.
Buchanan, T., & Whitty, M. T. (2014). The online dating romance scam: causes and consequences of victimhood. Psychology, Crime & Law, 20 (3), 261–283.
Article Google Scholar
Button, M., Lewis, C., & Tapley, J. (2009a). Fraud typologies and victims of fraud literature review . Retrieved from https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/118469/fraud-typologies.pdf . Accessed 11 Apr 2019.
Button, M., Lewis, C., & Tapley, J. (2009b). A better deal for fraud victims: Research into victims’ needs and experiences , London. Retrieved from https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/118468/better-deal-for-fraud-victims.pdf . Accessed 11 Apr 2019.
Button, M., Lewis, C., & Tapley, J. (2012). Not a victimless crime: the impact of fraud on individual victims and their families. Security Journal, 27 (1), 36–54.
Button, M., Nicholls, C. M., Kerr, J., & Owen, R. (2014). Online frauds: Learning from victims why they fall for these scams. Australian & New Zealand Journal of Criminology, 47 (3), 391–408.
Christie, N. (1986). The ideal victim. In E. A. Fattah (Ed.), From crime policy to victim policy . Macmillan: Simon Fraser University.
Google Scholar
City of London Police. (2015a). (Draft) National Fraud “Protect” Strategy. In N. P. C. f. E. Crime (Ed.).
City of London Police. (2015b). (Draft) National Policing Fraud Strategy. In N. P. C. f. E. Crime (Ed.).
Creswell, J. W., Plano Clark, V. L., Gutmann, M., & Hanson, W. (2003). Advanced mixed methods research designs. In A. Tashakkori & C. Teddlie (Eds.), Handbook on mixed methods in the behavioral and social sciences (pp. 209–240). London: Sage.
Dyfed Powys PCC. (2017). Police and crime plan 2017 – 2021 .
Eurostat. (2017). European Statistics Code of Practice. For the National Statistical Authorities and Eurostat (EU statistical authority) . Luxembourg.
Field, A., Miles, J., & Field, Z. (2012). Discovering statistics using R . Beverly Hills: SAGE Publications.
Flatley, J. (2013). The measurement of fraud and cyber - crime and their implications for crime statistics , Report to the Crime Statistics Advisory Committee. London: Office for National Statistics.
Fox, J. (2003). Effect displays in R for generalised linear models. Journal of Statistical Software, 8 (15), 1–27.
Fox, J., & Weisberg, S. (2011). An R companion to applied regression (2nd ed.). London: Sage Publications.
Gini, G., Card Noel, A., & Pozzoli, T. (2017). A meta-analysis of the differential relations of traditional and cyber-victimization with internalizing problems. Aggressive Behavior, 44 (2), 185–198.
Goudriaan, H. (2006). Reporting crime: Effects of social context on the decision of victims to notify the police. (Doctoral thesis), Leiden University, Leiden. Retrieved from https://openaccess.leidenuniv.nl/handle/1887/4410 . Accessed 11 Apr 2019.
Grabosky, P. N., & Smith, R. G. (1998). Crime in the digital age: Controlling telecommunications and cyberspace illegalities . New Brunswick: Transaction Publishers/The Federation Press.
Gwent PCC. (2017). Gwent police and crime plan 2017 – 2021 .
Hall, M. (2018). Supporting victims of crime in England and Wales: Local commissioning meeting local needs? International Review of Victimology, 24 (2), 219–237.
HM Government. (2006). Fraud review . Serious and Organised Crime Strategy, 8715 (2013). Retrieved from.
HM Government. (2016). National cyber security strategy 2016–2021. Serious and Organised Crime Strategy, 9718 . Retrieved 1 November 2018 from https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/567242/national_cyber_security_strategy_2016.pdf .
Home Office. (2015). Counting rules for recorded crime: Fraud . Retrieved from https://www.gov.uk/government/publications/counting-rules-for-recorded-crime . Accessed 11 Apr 2019.
Home Office. (2018a). Street-level crime . Retrieved from https://data.police.uk/data/fetch/970d8acd-0749-43d5-9f59-e83aa51133e9/ . Accessed 11 Apr 2019.
Home Office. (2018b). Understanding the costs of cyber crime; a report of key findings from the Costs of Cyber Crime Working Group (Research Report 96). Retrieved from London: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/674046/understanding-costs-of-cyber-crime-horr96.pdf . Accessed 11 Apr 2019.
Hutcheson, G., & Schaefer, L. (2012). Test selection in the 21st century. Journal of Modelling in Management, 7 (3), 375–387.
Hutcheson, G., & Sofroniou, N. (1999). The multivariate social scientist: Introductory statistics using generalized linear models . London: Sage.
Ivankova, N. V., Creswell, J. W., & Stick, S. L. (2006). Using mixed-methods sequential explanatory design: From theory to practice. Field Methods, 18 (1), 3–20.
Jarvis, L., Macdonald, S., & Whiting, A. (2015). Constructing cyberterrorism as a security threat a study of international news media coverage. Perspectives on Terrorism, 9 (1), 60–75. Retrieved from http://www.jstor.org/stable/26297327 .
Johnson, R. B., Onwuegbuzie, A. J., & Turner, L. A. (2007). Toward a definition of mixed methods research. Journal of Mixed Methods Research, 1 (2), 112–133.
Levi, M. (2006). White-collar, organised and cyber crimes in the media: Some contrasts and similarities. Crime Law and Social Change, 49 (6), 365–377. https://doi.org/10.1007/s10611-008-9111-y .
Levi, M. (2008). Suite revenge?: The shaping of folk devils and moral panics about White-Collar crimes. The British Journal of Criminology, 49 (1), 48–67.
Levi, M. (2017). Assessing the trends, scale and nature of economic cybercrimes: Overview an dissues. Crime, Law and Social Change, 67 (1), 3–20. https://doi.org/10.1007/s10611-016-9645-3 .
Levi, M., & Burrows, J. (2008). Measuring the impact of fraud in the UK: A conceptual and empirical journey. British Journal of Criminology, 48 (3), 293–318.
Levi, M., Doig, A., Gundur, R., Wall, D., & Williams, M. (2017). Cyberfraud and the implications for effective risk-based responses: Themes from UK research. Crime, Law and Social Change, 67 (1), 77–96.
MacDonald, Z. (2001). Revisiting the dark figure: A microeconometric analysis of the under-reporting of property crime and its implications. The British Journal of Criminology, 41 (1), 127–149.
McGuire, M., & Dowling, S. (2013). Cyber crime: A review of the evidence . Retrieved from https://www.gov.uk/government/publications/cyber-crime-a-review-of-the-evidence . Accessed 11 Apr 2019.
MOJ. (2015). Code of practice for victims of crime . Ministry of Justice. Retrieved from https://www.cps.gov.uk/legal/assets/uploads/files/OD_000049.pdf . Accessed 11 Apr 2019.
North Wales PCC. (2017). Police and crime plan 2017 – 2021 .
ONS. (2017). Percentage of incidents of fraud and computer misuse reported to Action Fraud, and reasons for not reporting incidents to Action Fraud, year ending September 2016 CSEW ( Experimental Statistics ). Retrieved from https://www.ons.gov.uk/peoplepopulationandcommunity/crimeandjustice/adhocs/006626percentageofincidentsoffraudandcomputermisusereportedtoactionfraudandreasonsfornotreportingincidentstoactionfraudyearendingseptember2016csewexperimentalstatistics . Accessed 11 Apr 2019.
ONS. (2018a). Crime in England and Wales: Appendix tables . Retrieved from https://www.ons.gov.uk/releases/crimeinenglandandwalesyearendingmarch2018 . Accessed 11 Apr 2019.
ONS. (2018b). Quality defined; the work we are doing to monitor and improve quality.
ONS. (2019). Crime in England and Wales: Appendix tables. Retrieved from https://www.ons.gov.uk/peoplepopulationandcommunity/crimeandjustice/datasets/crimeinenglandandwalesappendixtables . Accessed 11 Apr 2019.
Scholes, A. (2018). The scale and drivers of attrition in reported fraud and cyber crime . London. Retrieved from https://www.gov.uk/government/publications/the-scale-and-drivers-of-attrition-in-reported-fraud-and-cyber-crime . Accessed 11 Apr 2019.
Skogan, W. G. (1984). Reporting crimes to the police: The status of world research. Journal of Research in Crime and Delinquency, 21 (2), 113–137.
South Wales PCC. (2017). Police & crime reduction plan 2017 – 2021 .
Tarling, R., & Morris, K. (2010). Reporting crime to the police. The British Journal of Criminology, 50 (3), 474–490.
UKSA. (2014). Statistics on crime in England and Wales , London. Retrieved from.
Wall, D. S. (2001). Crime and the internet . London: Routledge.
Whitty, M. T. (2015). Anatomy of the online dating romance scam. Security Journal, 28 (4), 443–455.
Yar, M. (2006). Cybercrime and society (1st ed.). London: SAGE Publications.
Zawitz, M. W., Klaus, P. A., Bachman, R., Bastian, L. D., DeBerry, M. M., Rand, M. R., & Taylar, B. M. (1993). Highlights from 20 years of surveying crime victims. The National crime victimization survey 1973 – 92 . Retrieved from https://www.ncjrs.gov/pdffiles1/bjs/144525.pdf . Accessed 11 Apr 2019.
Download references
Authors’ contributions
Not applicable as it is a single author publication. The author read and approved the final manuscript.
Authors’ information
Sara Giro Correia is a doctoral researcher at the Hillary Rodham Clinton School of Law at Swansea University. During her PhD programme, Sara has interned with the Cybercrime Unit at the Southern Wales Regional Organised Crime Unit, as well as with the Office for Security and Counter-Terrorism: Research and Analysis (OSCT R&A) at the UK Home Office.
Acknowledgements
The author would like to thank everyone at the cyber unit in the Southern Wales Regional Organised Crime Unit (ROCU) for their support in making this project possible. This piece is also indebted to the constructive feedback of Prof. Stuart Macdonald at Swansea University, as well as the extensive feedback of the two independent reviewers. I am very grateful for their time and consideration.
Competing interests
The author declares no competing interests.
Availability of data and materials
The data cannot be shared at present as agreement for this has not been provided by the research partners.
This research was funded by an Economic and Social Research Council (ESRC) Ph.D. studentship.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Author information
Authors and affiliations.
Swansea University, Singleton Park, Swansea, SA2 8PP, UK
Sara Giro Correia
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Sara Giro Correia .
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated.
Reprints and permissions
About this article
Cite this article.
Correia, S.G. Responding to victimisation in a digital world: a case study of fraud and computer misuse reported in Wales. Crime Sci 8 , 4 (2019). https://doi.org/10.1186/s40163-019-0099-7
Download citation
Received : 06 June 2018
Accepted : 06 April 2019
Published : 24 April 2019
DOI : https://doi.org/10.1186/s40163-019-0099-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Computer misuse
- Victimisation
- Repeat victims
- Vulnerability
- Online crime
Crime Science
ISSN: 2193-7680
- General enquiries: [email protected]

Financial crime and fraud in the age of cybersecurity
In 2018, the World Economic Forum noted that fraud and financial crime was a trillion-dollar industry, reporting that private companies spent approximately $8.2 billion on anti–money laundering (AML) controls alone in 2017. The crimes themselves, detected and undetected, have become more numerous and costly than ever. In a widely cited estimate, for every dollar of fraud institutions lose nearly three dollars, once associated costs are added to the fraud loss itself. 1 World Economic Forum Annual Meeting, Davos-Klosters, Switzerland, January 23–26, 2018; LexisNexis risk solutions 2018 True Cost of Fraud study, LexisNexis, August 2018, risk.lexisnexis.com. Risks for banks arise from diverse factors, including vulnerabilities to fraud and financial crime inherent in automation and digitization, massive growth in transaction volumes, and the greater integration of financial systems within countries and internationally. Cybercrime and malicious hacking have also intensified. In the domain of financial crime, meanwhile, regulators continually revise rules, increasingly to account for illegal trafficking and money laundering, and governments have ratcheted up the use of economic sanctions, targeting countries, public and private entities, and even individuals. Institutions are finding that their existing approaches to fighting such crimes cannot satisfactorily handle the many threats and burdens. For this reason, leaders are transforming their operating models to obtain a holistic view of the evolving landscape of financial crime . This view becomes the starting point of efficient and effective management of fraud risk.
The evolution of fraud and financial crime
Fraud and financial crime adapt to developments in the domains they plunder. (Most financial institutions draw a distinction between these two types of crimes: for a view on the distinction, or lack thereof, see the sidebar “Financial crime or fraud?”) With the advent of digitization and automation of financial systems, these crimes have become more electronically sophisticated and impersonal.
Financial crime or fraud?
For purposes of detection, interdiction, and prevention, many institutions draw a distinction between fraud and financial crime. Boundaries are blurring, especially since the rise of cyberthreats, which reveal the extent to which criminal activities have become more complex and interrelated. What’s more, the distinction is not based on law, and regulators sometimes view it as the result of organizational silos. Nevertheless, financial crime has generally meant money laundering and a few other criminal transgressions, including bribery and tax evasion, involving the use of financial services in support of criminal enterprises. It is most often addressed as a compliance issue, as when financial institutions avert fines with anti–money laundering activities. Fraud, on the other hand, generally designates a host of crimes, such as forgery, credit scams, and insider threats, involving deception of financial personnel or services to commit theft. Financial institutions have generally approached fraud as a loss problem, lately applying advanced analytics for detection and even real-time interdiction. As the distinction between these three categories of crime have become less relevant, financial institutions need to use many of the same tools to protect assets against all of them.
One series of crimes, the so-called Carbanak attacks beginning in 2013, well illustrates the cyber profile of much of present-day financial crime and fraud. These were malware-based bank thefts totaling more than $1 billion. The attackers, an organized criminal gang, gained access to systems through phishing and then transferred fraudulently inflated balances to their own accounts or programmed ATMs to dispense cash to waiting accomplices (Exhibit 1).
Significantly, this crime was one simultaneous, coordinated attack against many banks. The attackers exhibited a sophisticated knowledge of the cyber environment and likely understood banking processes, controls, and even vulnerabilities arising from siloed organizations and governance. They also made use of several channels, including ATMs, credit and debit cards, and wire transfers. The attacks revealed that meaningful distinctions among cyberattacks, fraud, and financial crime are disappearing. Banks have not yet addressed these new intersections, which transgress the boundary lines most have erected between the types of crimes (Exhibit 2).
A siloed approach to these interconnected risks is becoming increasingly untenable; clearly, the operating model needs to be rethought.
As banks begin to align operations to the shifting profile of financial crime, they confront the deepening connections between cyber breaches and most types of financial crime. The cyber element is not new, exactly. Until recently, for example, most fraud has been transaction based, with criminals exploiting weaknesses in controls. Banks counter such fraud with relatively straightforward, channel-specific, point-based controls. Lately, however, identity-based fraud has become more prevalent, as fraudsters develop applications to exploit natural or synthetic data. Cyber-enabled attacks are becoming more ambitious in scope and omnipresent, eroding the value of personal information and security protections.
In a world where customers infrequently contact bank staff but rather interact almost entirely through digital channels, “digital trust” has fast become a significant differentiator of customer experience. Banks that offer a seamless, secure, and speedy digital interface will see a positive impact on revenue, while those that don’t will erode value and potentially lose business. Modern banking demands faster risk decisions (such as real-time payments) so banks must strike the right balance between managing fraud and handling authorized transactions instantly.
The growing cost of financial crime and fraud risk has also overshot expectations, pushed upward by several drivers. As banks focus tightly on reducing liabilities and efficiency costs, losses in areas such as customer experience, revenue, reputation, and even regulatory compliance are being missed (Exhibit 3).
Bringing together financial crime, fraud, and cyber operations
At leading institutions the push is on to bring together efforts on financial crime, fraud, and cybercrime. Both the front line and back-office operations are oriented in this direction at many banks. Risk functions and regulators are catching on as well. AML, while now mainly addressed as a regulatory issue, is seen as being on the next horizon for integration. Important initial steps for institutions embarking on an integration effort are to define precisely the nature of all related risk- management activities and to clarify the roles and responsibilities across the lines of defense. These steps will ensure complete, clearly delineated coverage—by the businesses and enterprise functions (first line of defense) and by risk, including financial crime, fraud, and cyber operations (second line)—while eliminating duplication of effort.
All risks associated with financial crime involve three kinds of countermeasures: identifying and authenticating the customer, monitoring and detecting transaction and behavioral anomalies, and responding to mitigate risks and issues. Each of these activities, whether taken in response to fraud, cybersecurity breaches or attacks, or other financial crimes, are supported by many similar data and processes. Indeed, bringing these data sources together with analytics materially improves visibility while providing much deeper insight to improve detection capability. In many instances it also enables prevention efforts.
In taking a more holistic view of the underlying processes, banks can streamline business and technology architecture to support a better customer experience, improved risk decision making, and greater cost efficiencies. The organizational structure can then be reconfigured as needed. (Exhibit 4).
From collaboration to holistic unification
Three models for addressing financial crime are important for our discussion. They are distinguished by the degree of integration they represent among processes and operations for the different types of crime (Exhibit 5).
Generally speaking, experience shows that organizational and governance design are the main considerations for the development of the operating model. Whatever the particular choice, institutions will need to bring together the right people in agile teams, taking a more holistic approach to common processes and technologies and doubling down on analytics—potentially creating “fusion centers,” to develop more sophisticated solutions. It is entirely feasible that an institution will begin with the collaborative model and gradually move toward greater integration, depending on design decisions. We have seen many banks identify partial integration as their target state, with a view that full AML integration is an aspiration.
- Collaborative model. In this model, which for most banks represents the status quo, each of the domains—financial crime, fraud, and cybersecurity—maintain their independent roles, responsibilities, and reporting. Each unit builds its own independent framework, cooperating on risk taxonomy and data and analytics for transaction monitoring, fraud, and breaches. The approach is familiar to regulators, but offers banks little of the transparency needed to develop a holistic view of financial-crime risk. In addition, the collaborative model often leads to coverage gaps or overlaps among the separate groups and fails to achieve the benefits of scale that come with greater functional integration. The model’s reliance on smaller, discrete units also means banks will be less able to attract top leadership talent.
- Partially integrated model for cybersecurity and fraud. Many institutions are now working toward this model, in which cybersecurity and fraud are partially integrated as the second line of defense. Each unit maintains independence in this model but works from a consistent framework and taxonomy, following mutually accepted rules and responsibilities. Thus a consistent architecture for prevention (such as for customer authentication) is adopted, risk-identification and assessment processes (including taxonomies) are shared, and similar interdiction processes are deployed. Deeper integral advantages prevail, including consistency in threat monitoring and detection and lower risk of gaps and overlap. The approach remains, however, consistent with the existing organizational structure and little disrupts current operations. Consequently, transparency is not increased, since separate reporting is maintained. No benefits of scale accrue, and with smaller operational units still in place, the model is less attractive to top talent.
- Unified model. In this fully integrated approach, the financial crimes, fraud, and cybersecurity operations are consolidated into a single framework, with common assets and systems used to manage risk across the enterprise. The model has a single view of the customer and shares analytics. Through risk convergence, enterprise-wide transparency on threats is enhanced, better revealing the most important underlying risks. The unified model also captures benefits of scale across key roles and thereby enhances the bank’s ability to attract and retain top talent. The disadvantages of this model are that it entails significant organizational change, making bank operations less familiar to regulators. And even with the organizational change and risk convergence, risks remain differentiated.
The imperative of integration
The integration of fraud and cybersecurity operations is an imperative step now, since the crimes themselves are already deeply interrelated. The enhanced data and analytics capabilities that integration enables are now essential tools for the prevention, detection, and mitigation of threats.
Most forward-thinking institutions are working toward such integration, creating in stages a more unified model across the domains, based on common processes, tools, and analytics. AML activities can also be integrated, but at a slower pace, with focus on specific overlapping areas first.
The starting point for most banks has been the collaborative model, with cooperation across silos. Some banks are now shifting from this model to one that integrates cybersecurity and fraud. In the next horizon, a completely integrated model enables comprehensive treatment of cybersecurity and financial crime, including AML. By degrees, however, increased integration can improve the quality of risk management, as it enhances core effectiveness and efficiency in all channels, markets, and lines of business.
Strategic prevention: Threats, prediction, and controls
The idea behind strategic prevention is to predict risk rather than just react to it. To predict where threats will appear, banks need to redesign customer and internal operations and processes based on a continuous assessment of actual cases of fraud, financial crime, and cyberthreats. A view of these is developed according to the customer journey. Controls are designed holistically, around processes rather than points. The approach can significantly improve protection of the bank and its customers (Exhibit 6).
To arrive at a realistic view of these transgressions, institutions need to think like the criminals. Crime takes advantage of a system’s weak points. Current cybercrime and fraud defenses are focused on point controls or silos but are not based on an understanding of how criminals actually behave. For example, if banks improve defenses around technology, crime will migrate elsewhere—to call centers, branches, or customers. By adopting this mind-set, banks will be able to trace the migratory flow of crime, looking at particular transgressions or types of crime from inception to execution and exfiltration, mapping all the possibilities. By designing controls around this principle, banks are forced to bring together disciplines (such as authentication and voice-stress analysis), which improves both efficacy and effectiveness.
Efficiencies of scale and processes
The integrated fraud and cyber-risk functions can improve threat prediction and detection while eliminating duplication of effort and resources. Roles and responsibilities can be clarified so that no gaps are left between functions or within the second line of defense as a whole. Consistent methodologies and processes (including risk taxonomy and risk identification) can be directed toward building understanding and ownership of risks. Integrating operational processes and continuously updating risk scores allow institutions to dynamically update their view on the riskiness of clients and transactions.
Data, automation, and analytics
Through integration, the anti-fraud potential of the bank’s data, automation, and analytics can be more fully realized. By integrating the data of separate functions, both from internal and external sources, banks can enhance customer identification and verification. Artificial intelligence and machine learning can also better enable predictive analytics when supported by aggregate sources of information. Insights can be produced rapidly—to establish, for example, correlations between credential attacks, the probability of account takeovers, and criminal money movements. By overlaying such insights onto their rules-based solutions, banks can reduce the rates of false positives in detection algorithms. This lowers costs and helps investigators stay focused on actual incidents.
The aggregation of customer information that comes from the closer collaboration of the groups addressing financial crime, fraud, and cybersecurity will generally heighten the power of the institution’s analytic and detection capabilities. For example, real-time risk scoring and transaction monitoring to detect transaction fraud can accordingly be deployed to greater effect. This is one of several improvements that will enhance regulatory preparedness by preventing potential regulatory breaches.
The customer experience and digital trust
The integrated approach to fraud risk can also result in an optimized customer experience. Obviously, meaningful improvements in customer satisfaction help shape customer behavior and enhance business outcomes. In the context of the risk operating model, objectives here include the segmentation of fraud and security controls according to customer experience and needs as well as the use of automation and digitization to enhance the customer journey. Survey after survey has affirmed that banks are held in high regard by their customers for performing well on fraud.
Unified risk management for fraud, financial crime, and cyberthreats thus fosters digital trust, a concept that is taking shape as a customer differentiator for banks. Security is clearly at the heart of this concept and is its most important ingredient. However, such factors as convenience, transparency, and control are also important components of digital trust. The weight customers assign to these attributes varies by segment, but very often such advantages as hassle-free authentication or the quick resolution of disputes are indispensable builders of digital trust.
A holistic view
The objective of the transformed operating model is a holistic view of the evolving landscape of financial crime. This is the necessary standpoint of efficient and effective fraud-risk management, emphasizing the importance of independent oversight and challenge through duties clearly delineated in the three lines of defense. Ultimately, institutions will have to integrate business, operations, security, and risk teams for efficient intelligence sharing and collaborative responses to threats.
How to proceed?
The target fraud-risk operating model: key questions for banks.
In designing their target risk operating model for financial crimes, fraud, and cybersecurity, leading banks are probing the following questions.
Processes and activities
- What are the key processes or activities to be conducted for customer identification and authentication, monitoring and detection of anomalies, and responding to risks or issues?
- How frequently should specific activities be conducted (such as reporting)?
- What activities can be consolidated into a “center of excellence”?
People and organization
- Who are the relevant stakeholders in each line of defense?
- What skills and how many people are needed to support the activities?
- What shared activities should be housed together (for example, in centers of excellence)?
- What is the optimal reporting structure for each type of financial crime—directly to the chief risk officer? To the chief operations officer? To IT?
Data, tools, and technologies
- What data should be shared across cybersecurity, fraud, and other financial-crime divisions? Can the data sit in the same data warehouses to ensure consistency and streamlining of data activities?
- What tools and frameworks should converge (for example, risk-severity matrix, risk-identification rules, taxonomy)? How should they converge?
- What systems and applications do each of the divisions use? Can they be streamlined?
- What are the governance bodies for each risk type? How do they overlap? For example, does the same committee oversee fraud and cybersecurity? Does committee membership overlap?
- What are the specific, separate responsibilities of the first and second lines of defense?
- What measurements are used to set the risk appetite by risk type? How are they communicated to the rest of the organization?
When banks design their journeys toward a unified operating model for financial crime, fraud, and cybersecurity, they must probe questions about processes and activities, people and organization, data and technology, and governance (see sidebar “The target fraud-risk operating model: Key questions for banks”).
Most banks begin the journey by closely integrating their cybersecurity and fraud units. As they enhance information sharing and coordination across silos, greater risk effectiveness and efficiency becomes possible. To achieve the target state they seek, banks are redefining organizational “lines and boxes” and, utility.
Most have stopped short of fully unifying the risk functions relating to financial crimes, though a few have attained a deeper integration. A leading US bank set up a holistic “center of excellence” to enable end-to-end decision making across fraud and cybersecurity. From prevention to investigation and recovery, the bank can point to significant efficiency gains. A global universal bank has gone all the way, combining all operations related to financial crimes, including fraud and AML, into a single global utility. The bank has attained a more holistic view of customer risk and reduced operating costs by approximately $100 million.
As criminal transgressions in the financial-services sector become more sophisticated and break through traditional risk boundaries, banks are watching their various risk functions become more costly and less effective. Leaders are therefore rethinking their approaches to take advantage of the synergies available in integration. Ultimately, fraud, cybersecurity, and AML can be consolidated under a holistic approach based on the same data and processes. Most of the benefits are available in the near term, however, through the integration of fraud and cyber operations.
Explore a career with us
Related articles.

The new frontier in anti–money laundering
Flushing out the money launderers with better customer risk-rating models
Cybersecurity and the risk function
- Quick links
- Global Technology Outage and Implications for Businesses
- Why High-Quality Data is Crucial to Fighting Financial Crime
- Kroll Lowers Its Recommended U.S. Equity Risk Premium to 5.0%
- Popular topics
- Valuation Advisory Services
- Compliance and Regulation
- Corporate Finance and Restructuring
- Investigations and Disputes
- Digital Technology Solutions
- Business Services
- Environmental, Social and Governance Advisory Services (ESG)
- Environmental, Social and Governance
- Consumer and Retail
- Financial Services
- Industrials
- Technology, Media and Telecom
- Energy and Mining
- Healthcare and Life Sciences
- Real Estate
- Our Experts
- Client Stories
- Transactions
- Restructuring Administration Cases
- Settlement Administration Cases
- Anti-Money Laundering
- Artificial Intelligence
- Cost of Capital
- Cryptocurrency
- Financial Crime
- M&A Updates
- Valuation Outlook
- Blogs / Publications
- Webcasts and Videos
Cyber Security Case Studies
Managed detection and response case studies, building cyber resilience amid microsoft azure migration.

Seamless Response to Ransomware and a Cyber Resilience Upgrade

Reducing a Hospitality Company’s Cyber Risk Surface

Enhancing Security Visibility for a Leading Asset Management Firm

Elevating Cyber Security Maturity of a Housebuilding Company

Protecting the 2008 U.S. Presidential Election from Cyber Attacks
by Alan Brill

Endpoint Detection and Response to Increase Plastics Manufacturer’s Cyber Posture

Stronger Threat Detection and Response for UK Bank: Reduced False Positives, Swifter Response

Enhanced Ransomware Defences for Global Shipping Business with Robust MDR

Large Hospital Leverages Managed Detection and Response for Increased Resilience and Compliance Reporting

Defending Healthcare Organization Against Persistent Trickbot Attacks

Optimized Security Operations and Cyber Governance for Asset Management Firm

Digital Forensics and Incident Response Case Studies
Online skimming attack facilitated by work-from-home arrangements.

Electronic Gift Card Fraud Investigation Uncovers Contractual Risks

Spearphishing Compromises Fuel Chain Credit Card Transactions, Ends in Ransomware

Insider Threat Case Study: Digital Forensics Reveals Fraud, Potential Regulatory Concerns
by Kevin Wong, Ben Hawkins

Kroll Contains, Remediates SWIFT System Cyber Fraud for Middle Eastern Bank
by Kevin Wong, Imran Khan

Transatlantic Cyber Investigation Unmasks Insider Threat, Preempts Ransom Attempt
by Michael Quinn, Ben Hawkins, Justin Price

Office 365 Business Email Compromise Investigation Leads to Stronger Security

Business Email Compromise Attack Investigation and Remediation for Insurance Broker

Proactive Services Case Studies
Continuous penetration testing optimizes security in agile product development for software startup.

Scaling Up Application Security for a Global Telecommunications Company
by Rahul Raghavan, Rob Deane

Safeguarding Election Security Through Penetration Testing

AWS Penetration Testing Gives In-Depth Cyber Risk Insight to Specialist Bank

State of Arkansas Cyber Security Assessment
by Frank Marano, Jeff Macko

Red Team Exercise Helps International Trade Organization Comply with FCA Cyber Security Mandates

Other Cyber Security Case Studies
Gdpr assessment and u.s. data privacy laws action plan for a global biopharmaceutical company.

Uncovering Critical Historical Data to Progress a Complex Legal Case

Taking an Underwriter’s Security Posture From At-Risk to Resilient

Kroll Assists Entertainment Conglomerate in Achieving Holistic Digital Transformation with Cloud Native Security Platform Implementation
by Frank Marano, Rahul Raghavan, Rob Deane

Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
Agile Penetration Testing Program
Integrated into your software development lifecycle (SDLC), Kroll’s agile penetration testing program is designed to help teams address security risks in real time and on budget.
Penetration Testing Services
Validate your cyber defenses against real-world threats. Kroll’s world-class penetration testing services bring together front-line threat intelligence, thousands of hours of cyber security assessments completed each year and a team of certified cyber experts — the foundation for our sophisticated and scalable approach.
Application Threat Modeling Services
Kroll helps development teams design and build internal application threat modeling programs to identify and manage their most pressing vulnerabilities.
Application Security Services
Kroll’s product security experts upscale your AppSec program with strategic application security services catered to your team’s culture and needs, merging engineering and security into a nimble unit.
Cloud Security Services
Kroll’s multi-layered approach to cloud security consulting services merges our industry-leading team of AWS and Azure-certified architects, cloud security experts and unrivalled incident expertise.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Connect With Us

Chief Financial Officers Ignoring Cyber Risk Worth Millions of Dollars According to Kroll Report

Kroll Acquires Crisp, Trusted Provider of Real-time Risk Intelligence
Kroll Partners with Armis to Extend Preparedness and Response for OT and ICS Environments

Kroll Acquires Resolver, a Leader in Risk Intelligence Technology

Webinar – Q2 2024 Cyber Threat Landscape Virtual Briefing
Our quarterly threat landscape reports are fuelled by frontline incident response intel and elite analysts.

Webinar – AI Security Testing: Prompt Injection Everywhere
Kroll offers a glimpse into the security vulnerabilities faced by businesses adopting Artificial Intelligence (AI), Machine Learning (ML) and Large Language Model (LLM) following eight months of LLM penetration testing.

ALTLOOK – Valuation Quarterly Update–September 2024
On Thursday, September 5, 2024, please join Kroll’s quarterly ALTLOOK discussion of key market and regulatory considerations that are expected to impact September 30 valuations.

Kroll is headquartered in New York with offices around the world.
More About Kroll
- Trending Topics
- Find an Expert
- Media Inquiry

- Accessibility
- Code of Conduct
- Data Privacy Framework
- Kroll Ethics Hotline
- Modern Slavery Statement
- Privacy Policy
- +1-(855) 647-4474
- [email protected]
- Contact Us

Phishing Case Studies: Learning From the Mistakes Of Others
by Brad | Mar 25, 2021 | Phishing

Phishing remains one of the oldest and the most commonly used modus operandi by cyber adversaries to access network systems globally . Though phishing attacks can be of many types, BEC or Business Email Compromise causes the most significant threat to businesses. Verizon’s 2020 DBIR (Data Breach Investigations Report ) states that 22% of data breaches in 2019 involved phishing . ESET’s Threat Report highlights that malicious email detections rose by 9% between the second and third quarters in 2020.
Here are some critical statistics related to the above points.
- As malicious actors rely more on phishing to access network systems, there is a decrease of 40% on breaches involving malware , further shifting the cybersecurity focus from anti-malware solutions to anti-phishing solutions .
- Nearly 65% of the active phishing attacks relied on spear-phishing in 2019.
- A whopping 96% of phishing attacks arrive by email .
Despite organizations employing the most effective anti-phishing solutions in their network systems, phishing attacks are growing relentlessly worldwide due to employee negligence . Employee training is one way to deal with such problems. Learning from the mistakes of others is also an effective remedial measure. Here are some phishing case examples caused by employee negligence that cost their organizations heavily.
Case No 1: Upsher-Smith Laboratories – Loss Of Nearly $39 Million
Though this incident happened sometime in 2014, it has tremendous significance because it is one of the classic email examples of the CEO Fraud category. CEO fraud is a cyber-attack carried out by malicious actors wherein they send phishing email s to the organization’s employees by posing as the organization’s CEO.
In this case, cyber adversaries pretending to be the organization’s CEO emailed the Accounts Payable Coordinator at Upsher-Smith Laboratories, a Maple Grove-based drug establishment, to follow the instructions from the CEO and the organization’s lawyer. The instructions were to make nine wire transfers to the fraudster’s accounts for amounts exceeding $50 million . Though the organization managed to stop one of the bank transfers, its loss was upwards of $39 million.
Employee Negligence Factor
In this case, the employee was negligent in taking the emails at face value. He/she could have contacted the CEO’s office to confirm the origin of such emails , especially if they were not following the standard procedures. The bank handling the transfer is also negligent of missing the multiple red flags, especially the amounts and the frequency of transfers, suspicious beneficiaries, and the failure to include a second signatory to the requests.
Lessons Learned From The Case
Here are some lessons one can learn from this case.
- Generally, CEOs do not directly ask employees to make urgent transfer s. Even if they do, the employee could have dropped an email to confirm the request. A precautionary phone call could have stopped this crime from happening .
- Such phishing emails come with an urgency factor. They also insist on confidentiality. Generally, such requests are departures from the organization’s regular procedures.
- The primary lesson one can learn from this attack is not to take any email at face value. It does not cost much to confirm .
Case No 2: Twitter Phishing Case – 2020
The Twitter Phishing case of July 2020 should be fresh on everyone’s mind. It is a classic case of threat actors compromising the employees’ passwords to gain unauthorized access .
In July 2020, several Twitter employees became victims of spear phishing attacks enabling the malicious actors to access the administrator’s tools. Malicious actors posed as Twitter IT administrators and emailed/phoned Twitter employees working from home, asking them to share user credentials. Using these compromised accounts, the cyber adversaries gained access to the administrator’s tools . It enabled them to reset the Twitter accounts of celebrities like Elon Musk, Barack Obama, Jeff Bezos, Apple, Uber, and many more to tweet scam messages asking for Bitcoin contributions.
As these celebrity accounts have a massive following, many Twitter users transferred at least $180,000 in Bitcoins to scam accounts . Luckily, the scam messages were published and noticed by the press. It forced Twitter to take immediate action.
Twitter did not follow proper cybersecurity strategies as the compromised employees did not have appropriate email phishing protection solutions installed on their devices. Privileged access management solutions and monitoring user and entity behavior could have prevented this scam from happening.
Twitter experienced a 4% fall in its share price due to its failure in detecting and mitigating the scam in time . Twitter also had to stop its release of the new API to update security protocols. Educating employees on social engineering attacks is crucial to prevent such frauds from occurring. Though the financial loss was insignificant, Twitter lost its reputation of being one of the most secure social media platforms.
How To Manage Such Phishing Attacks?
Though employee negligence is one of the primary reasons for such phishing attacks , organizations can take remedial steps to thwart such crimes in the future.
- Educating employees on how a phishing attack looks and emphasizing aspects like not clicking on suspicious email links or downloading malicious attachment files can help prevent many phishing attacks right at the initial stage.
- Investing in efficient anti-phishing and anti-ransomware solutions and ensuring the best phishing protection should be the first things an organization should do to manage phishing scams.
- Other remedial measures include changing passwords regularly, installing security updates on time, not sharing information on unsecured sites, and investing in a robust data security platform to help organizations deal with such issues.
Final Words
Phishing attacks will continue to happen in the future. It is up to the organization and its employees to learn from past mistakes and not repeat them . Employees can educate themselves on how to stop phishing emails. Organizations can deploy the best phishing protection solutions to deal with such situations effectively. Furthermore, organizations must include case studies related to past incidents in the employee education and training programs .
Join the thousands of organizations that use Phish Protection
Find out how easy and effective it is for your organization today.
- Advanced Threat Defense (3)
- Advanced Threat Protection (5)
- Announcements (192)
- Cybersecurity (99)
- Office 365 (6)
- Phishing (216)
- Phishing Awareness (123)
- Time of Click Protection (1)
- Uncategorized (7)
Privacy Overview
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
Cell: +91 9510122995 Tel: 079-40030031 E-mail : [email protected] [email protected]

Important Cyber Law Case Studies
1.Pune Citibank MphasiS Call Center Fraud Some ex-employees of BPO arm of MPhasiS Ltd MsourcE defrauded US Customers of Citibank to the tune of Rs 1.5 crores. It was one of those cyber crime cases that raised concerns of many kinds including the role of "Data Protection". The crime was obviously committed using "Unauthorized Access" to the "Electronic Account Space" of the customers. It is therefore firmly within the domain of "Cyber Crimes". ITA-2000 is versatile enough to accommodate the aspects of crime not covered by ITA-2000 but covered by other statutes since any IPC offence committed with the use of "Electronic Documents" can be considered as a crime with the use of a "Written Documents". "Cheating", "Conspiracy", "Breach of Trust", etc. are therefore applicable in the above case in addition to the section in ITA-2000. Under ITA-2000 the offence is recognized both under Section 66 and Section 43. Accordingly, the persons involved are liable for imprisonment and fine as well as a liability to pay damages to the victims to the maximum extent of Rs 1 crore per victim for which the "Adjudication Process" can be invoked.
2.SONY.SAMBANDH.COM CASE India saw its first cybercrime conviction in 2013. It all began after a complaint was filed by Sony India Private Ltd, which runs a website called www.sony-sambandh.com, targeting Non-Resident Indians. The website enables NRIs to send Sony products to their friends and relatives in India after they pay for it online. The company undertakes to deliver the products to the concerned recipients. In May 2002, according to the cybercrime case study, someone logged onto the website under the identity of Barbara Campa and ordered a Sony Colour Television set and a cordless headphone. She gave her credit card number for payment and requested the products to be delivered to Arif Azim in Noida. The payment was duly cleared by the credit card agency, and the transaction was processed. After following the relevant procedures of due diligence and checking, the company delivered the items to Arif Azim. At the time of delivery, the company took digital photographs showing the delivery being accepted by Arif Azim. The transaction closed at that, but after one and a half months the credit card agency informed the company that this was an unauthorized transaction as the real owner had denied having made the purchase. The company lodged a complaint about online cheating at the Central Bureau of Investigation which registered a case under Section 418, 419 and 420 of the Indian Penal Code. The matter was investigated, and Arif Azim was arrested. Investigations revealed that Arif Azim while working at a call centre in Noida gained access to the credit card number of an American national which he misused on the company's site. The CBI recovered the colour television and the cordless headphone, in this one of a kind cyber fraud case. In this matter, the CBI had evidence to prove their case, and so the accused admitted his guilt. The court convicted Arif Azim under Section 418, 419 and 420 of the Indian Penal Code - this being the first time that cybercrime has been convicted. The court, however, felt that as the accused was a young boy of 24 years and a first-time convict, a lenient view needed to be taken. The court, therefore, released the accused on probation for one year. The judgment is of immense significance for the entire nation. Besides being the first conviction in a cybercrime matter, it has shown that the Indian Penal Code can be effectively applied to certain categories of cyber crimes which are not covered under the Information Technology Act 2000. Secondly, a judgment of this sort sends out a clear message to all that the law cannot be taken for a ride.
3. The Bank NSP Case One of the leading cybercrime cases is the Bank NSP case is the one where a management trainee of the bank was engaged to be married. The couple exchanged many emails using the company computers. After some time the two broke up and the girl created fraudulent email ids such as "indianbarassociations" and sent emails to the boy's foreign clients. She used the bank’s computer to do this. The boy's company lost a large number of clients and took the bank to court. The bank was held liable for the emails sent using the bank's system.
4. Andhra Pradesh Tax Case Dubious tactics of a prominent businessman, from Andhra Pradesh, were exposed after officials of the department got hold of computers, used by the accused in one of the many cyber fraud cases in India. The owner of a plastics firm was arrested and Rs 22 crore cash, was recovered from his house by sleuths of the Vigilance Department. They sought an explanation from him regarding the unaccounted cash within 10 days. The accused submitted 6,000 vouchers, to prove the legitimacy of trade and thought his offence would go undetected but after careful scrutiny of vouchers and contents of his computers, it was revealed that all of them were made after the raids were conducted. It was later revealed that the accused was running five businesses under the guise of one company and used fake and computerised vouchers to show sales records and save tax.
5.SMC Pneumatics (India) Pvt. Ltd. vs. Jogesh Kwatra In India's first case of cyber defamation, the High Court of Delhi assumed jurisdiction over a matter where a corporation's reputation was being defamed through emails and passed an important ex-parte injunction. Amongst the many cyber cases in India, in this case, the defendant Jogesh Kwatra being an employee of the plaintiff company started sending derogatory, defamatory, obscene, vulgar, filthy and abusive emails to his employers as also to different subsidiaries of the said company all over the world with the aim to defame the company and its Managing Director Mr. R K Malhotra. The plaintiff filed a suit for permanent injunction restraining the defendant from doing his illegal acts of sending derogatory emails to the plaintiff. On behalf of the plaintiff, it was contended that the emails sent by the defendant were distinctly obscene, vulgar, abusive, intimidating, humiliating and defamatory in nature. Counsel further argued that the aim of sending the said emails was to malign the high reputation of the plaintiff all over India and the world. He further contended that the acts of the defendant in sending the emails had resulted in an invasion of the legal rights of the plaintiff. Further, the defendant is under a duty not to send the aforesaid emails. It is pertinent to note that after the plaintiff company discovered the said employee could be indulging in the matter of sending abusive emails, the plaintiff terminated the services of the defendant. After hearing detailed arguments of Counsel for Plaintiff, Hon'ble Judge of the Delhi High Court passed an ex-parte ad interim injunction, observing that a prima facie case had been made out by the plaintiff. Consequently, in this cyber fraud case in India, the Delhi High Court restrained the defendant from sending derogatory, defamatory, obscene, vulgar, humiliating and abusive emails, either to the plaintiff or to its sister subsidiaries all over the world, including their Managing Directors and their Sales and Marketing departments. Further, Hon'ble Judge also restrained the defendant from publishing, transmitting or causing to be published any information in the actual world, as also in cyberspace, which is derogatory or defamatory or abusive. This order of Delhi High Court assumes tremendous significance as this is the first time that an Indian Court assumes jurisdiction in a matter concerning cyber defamation and grants an ex-parte injunction restraining the defendant from defaming the plaintiff by sending derogatory, defamatory, abusive and obscene emails either to the plaintiffs or their subsidiaries.
6. Bazee.com case CEO of Bazee.com was arrested in December 2004 because a CD with objectionable material was being sold on the website. The CD was also being sold in the markets in Delhi. The Mumbai Police and the Delhi Police got into action. The CEO was later released on bail. This opened up the question as to what kind of distinction we draw between Internet Service Provider and Content Provider. The burden rests on the accused that he was the Service Provider and not the Content Provider. It also raises a lot of issues regarding how the police should handle cybercrime cases.
7. State of Tamil Nadu Vs Suhas Katti The Case of Suhas Katti is notable for the fact that the conviction was achieved successfully within a relatively quick time of 7 months from the filing of the FIR, making it one of the notable cyberlaw cases in India. Considering that similar cases have been pending in other states for a much longer time, the efficient handling of the case which happened to be the first case of the Chennai Cyber Crime Cell going to trial deserves a special mention. The case is related to the posting of obscene, defamatory and annoying message about a divorced woman in the Yahoo message group. E-mails were also forwarded to the victim for information by the accused through a false e-mail account opened by him in the name of the victim. The posting of the message resulted in annoying phone calls to the lady in the belief that she was soliciting. Based on a complaint made by the victim in February 2004, the Police traced the accused to Mumbai and arrested him within the next few days. The accused was a known family friend of the victim and was reportedly interested in marrying her. She, however, married another person. This marriage later ended in divorce, and the accused started contacting her once again. On her reluctance to marry him, the accused took up harassment through the Internet. On 24-3-2004, a Charge Sheet was filed, u/s 67 of the IT Act 2000, 469 and 509 IPC before The Hon'ble Addl. CMM Egmore by citing 18 witnesses and 34 documents and material objects. The same was taken on file in C.C.NO.4680/2004. On the prosecution side, 12 witnesses were examined, and entire documents were marked as Exhibits. The Defence argued, in this cyber crime case, that the offending emails would have been given either by the ex-husband of the complainant or the complainant herself to implicate the accused as accused alleged to have turned down the request of the complainant to marry her. Further, the defence counsel argued that some of the documentary evidence was not sustainable under Section 65 B of the Indian Evidence Act. However, the court relied upon the expert witnesses, and other evidence produced before it, including the witnesses of the Cyber Cafe owners, and came to the conclusion that the crime was proved. Ld. Additional Chief Metropolitan Magistrate, Egmore, delivered the judgement on 5-11-04 as follows: "The accused is found guilty of offences under section 469, 509 IPC and 67 of the IT Act 2000, and the accused is convicted and sentenced for the offence to undergo RI for 2 years, under 469 IPC, and to pay a fine of Rs.500/- and for the offence u/s 509 IPC sentenced to undergo 1 year simple imprisonment and to pay a fine of Rs.500/- and for the offence u/s 67 of the IT Act 2000 to undergo RI for 2 years and to pay a fine of Rs.4000/-. All sentences to run concurrently." The accused paid the fine amount, and he was lodged at Central Prison, Chennai. This is considered as the first case convicted under section 67 of the Information Technology Act 2000 in India.
8. Nasscom vs. Ajay Sood & Others In a landmark judgment in the case of National Association of Software and Service Companies vs. Ajay Sood & Others, delivered in March, '05, the Delhi High Court declared 'phishing' on the internet to be an illegal act, entailing an injunction and recovery of damages. A cybercrime case study has been conducted on the same. Elaborating on the concept of 'phishing', in order to lay down a precedent in India, the court stated that it is a form of internet fraud where a person pretends to be a legitimate association, such as a bank or an insurance company in order to extract personal data from a customer such as access codes, passwords, etc. Personal data so collected by misrepresenting the identity of the legitimate party is commonly used for the collecting party's advantage. The court also stated, by way of an example, that typical phishing scams involve persons who pretend to represent online banks and siphon cash from e-banking accounts after conning consumers into handing over confidential banking details. The Delhi HC stated that, even though there is no specific legislation in India to penalize phishing, it held phishing to be an illegal act, by defining it under Indian law as "a misrepresentation made in the course of trade, leading to confusion, as to the source and origin of the email causing immense harm, not only to the consumer, but even to the person whose name, identity or password is misused." The court held the act of phishing as passing off and tarnishing the plaintiff's image. The plaintiff, in this case, was the National Association of Software and Service Companies (Nasscom), India's premier software association. The defendants were operating a placement agency involved in headhunting and recruitment. In order to obtain personal data, which they could use for purposes of headhunting, the defendants composed and sent emails to third parties, in the name of Nasscom. The high court recognised the trademark rights of the plaintiff and passed an ex-parte ad interim injunction restraining the defendants from using the trade name or any other name deceptively similar to Nasscom. The court further restrained the defendants from holding themselves out as being associated with or a part of Nasscom. The court appointed a commission to conduct a search at the defendants' premises. Two hard disks of the computers, from which the fraudulent e-mails were sent by the defendants to various parties, were taken into custody by the local commissioner appointed by the court. The offending emails were then downloaded from the hard disks and presented as evidence in court. During the progress of the cyberlaw case in India, it became clear that the defendants, in whose names the offending e-mails were sent, were fictitious identities created by an employee on defendants' instructions, to avoid recognition and legal action. On discovery of this fraudulent act, fictitious names were deleted from the array of parties as defendants in the case. Subsequently, defendants admitted to their illegal acts and the parties settled the matter through the recording of a compromise in the suit proceedings. According to the terms of compromise, the defendants agreed to pay a sum of Rs1.6 million to the plaintiff as damages for violation of the plaintiff's trademark rights. The court also ordered the hard disks seized from the defendants' premises to be handed over to the plaintiff who would be the owner of the hard disks. This case achieves clear milestones: It brings the act of "phishing" into the ambit of Indian laws, even in the absence of specific legislation; it clears the misconception that there is no "damages culture" in India for violation of IP rights. this case reaffirms IP owners' faith in the Indian judicial system's ability and willingness to protect intangible property rights and send a strong message to IP owners that they can do business in India without sacrificing their IP rights.
9. Cyber Attack on Cosmos Bank In August 2018, the Pune branch of Cosmos bank was drained of Rs 94 crores, in an extremely bold cyber attack. By hacking into the main server, the thieves were able to transfer the money to a bank in Hong Kong. Along with this, the hackers made their way into the ATM server, to gain details of various VISA and Rupay debit cards. The switching system i.e. the link between the centralized system and the payment gateway was attacked, meaning neither the bank nor the account holders caught wind of the money being transferred. According to the cybercrime case study internationally, a total of 14,000 transactions were carried out, spanning across 28 countries using 450 cards. Nationally, 2,800 transactions using 400 cards were carried out. This was one of its kinds, and in fact, the first malware attack that stopped all communication between the bank and the payment gateway.
10. Tampering with Computer Source Documents In a case of manipulation, Tata Indicom employees were taken into custody in relation to the tampering of the electronic 32-bit number (ESN) that is programmed into cell phones. The theft was for Reliance Intercom. In a verdict on a later date, the court said that since the source code was manipulated, it calls the use of Section 65 under the Information Technology Act.
11. BSNL, Unauthorized Access In a leading cybercrime case, the Joint Academic Network (JANET) was hacked by the accused, after which he denied access to the authorized users by changing passwords along with deleting and adding files. Making it look like he was authorized personnel, he made changes in the BSNL computer database in their internet users’ accounts. When the CBI carried out investigations after registering a cybercrime case against the accused, they found that the broadband Internet was being used without any authorization. The accused used to hack into the server from various cities like Chennai and Bangalore, amongst others. This investigation was carried after the Press Information Bureau, Chennai, filed a complaint. In the verdict by the Additional Chief Metropolitan Magistrate, Egmore, Chennai, the accused from Bangalore would be sent to prison for a year and will have to pay a fine of Rs 5,000 under Section 420 IPC and Section 66 of the IT Act.
12. BPO Fraud In another incident involving MphasiS, India, four call centre employees gained the PIN codes, from four of the MphasiS’s client, Citi Group, in spite of not being authorized to do so. Various accounts were opened in Indian banks, under false names and within two months, they managed to transfer money to these accounts from Citigroup customers accounts using their PINs and other personal information. This cyber fraud case occurred in December 2004, but it wasn’t until April 2005 that the Indian police were able to identify the individuals to make an arrest. It was made possible with a tip provided by a U.S. bank when the accused tried to withdraw cash from these fake accounts. From the $426,000 that was stolen, only $230,000 were recovered. The accused were charged under Section 43(a), unauthorized access involved to carry transactions.
13. Bomb Hoax Mail In an email hoax, sent by a 15-year-old boy from Bangalore, the Cyber Crime Investigation Cell (CCIC) arrested him in 2009. The boy was accused of sending an email to a private news company saying, “I have planted 5 bombs in Mumbai, you have two hours to find them”. The concerned authorities were contacted immediately, in relation to the cyber case in India, who traced the IP address (Internet Protocol) to Bangalore.
14. A Look-alike Website A 9-person crime, was registered under Sections 65, 66, 66A, C and D of the Information Technology Act, along with Sections 419 and 420 of the Indian Penal Code. Under the complaint of this cyber fraud case in India, a company representative in the business of trading and distribution of petrochemicals in India and abroad had filed the report against the 9 accused of using a similar looking website to carry on the trade. The accused ran a defamation campaign against the company, causing them crores of rupees of loss from their customers, suppliers and even producers.
15. Cyber Terrorism Since the changes were carried out in the Information Technology Act in Mumbai, this case of cyber terrorism was its first project. A threat email had been delivered to the BSE and NSE, at 10:44 am on Monday. With the MRA Marg police and the Cyber Crime Investigation Cell (CCIC) working together on the cyber crime case, the accused has been detained. The IP address had been traced to Patna, Bihar. When checked for any personal details, two contact numbers were found, which belonged to a photo frame maker in Patna.
Personal Cases
- Cyber Police has arrested a Husband for misusing his wife’s FB account, in a cyber case in India. He hired an ethical hacker to hack into his wife’s FB account so that he can find pieces of evidence regarding her bad character.
- Using the trojan or malware, a woman’s webcam was accessed to capture her private videos and posted on an illegal website. The incident came into light when the Mumbai resident appeared for an interview.
- The cyber fraud case of duplication of a SIM card was registered with the police when a businessman from Ahmedabad caught wind of it. He registered a complaint under the cyber and financial crime since the defrauders had submitted fake documents with the mobile company to gain the businessman’s personal details.
- In a social media related cybercrime complaint, a famous Gujarati singer claimed that her photos were being used by an unknown man, saying they were married and had a child together.
- To gain personal revenge, an ex-boyfriend, working as a software engineer, posted his ex’s personal phone number on a 24*7 dating service helpline, was arrested in a leading cybercrime case.

IMAGES
COMMENTS
Here are Computer Weekly's top 10 cyber crime stories of 2021: 1. Colonial Pipeline ransomware attack has grave consequences. Though it did not trouble the fuel supply at petrol stations in the ...
Case in Point. FBI Anthrax Investigation (Arredondo, 2008) Doctor Bruce Ivins, a biodefense researcher at the US Army Medical Research Institute of Infectious Diseases, was suspected of mailing anthrax-contaminated letters causing 5 deaths and injury to dozens of more people.
Major cyber crime cases over the years. Melissa Virus. A few decades ago, computer viruses were still relatively new notions to most Americans, but the fast-moving and destructive Melissa virus ...
In the ever-evolving landscape of cybersecurity, the battle between hackers and defenders continues to shape the digital domain. To understand the gravity of cybersecurity challenges, one need only examine real-world examples—breaches that have rocked industries, compromised sensitive data, and left organizations scrambling to shore up their ...
New data protection and privacy laws and recent cyber security regulations, such as the General Data Protection Regulation (GDPR) that went into effect in Europe in 2018, ... To properly understand the chain of events that led to the incident related to this case study, the MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge ...
Depicting Major Cyber Crime Case Studies. When regarding the multifaceted arena of cybercrimes, a few notorious examples have made all the difference in shaping both legislative processes and public perception. These archetypical scenarios paint a stark picture of the danger posed by cybercriminals and the significant, often devastating ...
The Australian Cyber Security Centre reported a 15% increase in ransomware cybercrime reports in the 2020-21 financial year. 21 Malware and intimate image abuse Image-based sexual abuse is the creation, distribution or threatened distribution of intimate, nude or sexual image or videos, without the consent of the person pictured.
Firstly, over the span of a decade, from 2011 to 2020, 50 significant cyber incidents have served as pivotal studies in the realm of cyber threats and security. Examining these case studies ...
Case study: To examine the network structure, criminal cooperation, and external interactions of cybercriminal networks ... By selecting cybertransactions and cyberfinance as the two main types of computer-related crime using machines, this study found two main criminal motives: "making money from fake sales" accounted for 57.58% (19 cases ...
The IC3 was established in May 2000 to receive complaints of internet related crime and has received more than 6.5 million complaints since its inception. Its mission is to provide the public with a reliable and convenient reporting mechanism to submit information to the FBI concerning suspected cyber enabled
Although it is universally agreed that cybercrime exists, there is no universal definition of what it means (Holt and Bossler, 2014; Kshetri, 2010; Wall, 2017a).Terms including cybercrime, cyber-crime, computer crime, cloud-crime and computer misuse are often used interchangeably and can refer to any internet- or computer-related criminal activity (Goodman and Brenner, 2002).
6. Uber suffers major cyber attack. Ride-sharing service Uber was one of 2022's high-profile cyber attack victims in September, when it suffered a supposed social engineering attack on an ...
Here are Computer Weekly's top 10 cyber crime stories of 2020: 1. Cyber gangsters demand payment from Travelex after Sodinokibi attack. Foreign exchange company Travelex is facing demands for ...
15. Hotel managers and clients had nightmares due to one lock hack. In this Forbes story, reporters chronicles the chaos experienced by hotel managers and the panic felt by their customers after a burglar used online hacking tools to bypass the electronic locks on the doors. "I had dreams about it for many nights.
The extent of the cyber-security related problems faced in the UK was quite exceptional, and in this section we use the UK as a case study to analyse COVID-19 related cyber-crime. The discussion herein demonstrates that as expected and outlined above, there was a loose correlation between policy/news announcements and associated cyber-crime ...
The following Case Studies were created by the National Cyber Security Alliance, with a grant from NIST, and should prove useful in stimulating ongoing learning for all business owners and their employees. Case 1: A Business Trip to South America Goes South Topic: ATM Skimming and Bank Fraud; Case 2: A Construction Company Gets Hammered by a ...
Around 44, 546 cases were registered under the Cyber Crime head in 2019 as compared to 27, 248 cases in 2018. Therefore, a spike of 63.5% was observed in Cyber Crimes [1]. The legislative framework concerning Cyber Law in India comprises the Information Technology Act, 2000 (hereinafter referred to as the " IT Act ") and the Rules made ...
This paper presents the early results of a study exploring computer misuse and fraud victimisation in Wales, United Kingdom (UK). The results presented here describe the quality of the data available to local forces, the characteristics and heterogeneity of the victims who report incidents and the nature of the police response at a local level. The significance of these results is considered ...
In 2018, the World Economic Forum noted that fraud and financial crime was a trillion-dollar industry, reporting that private companies spent approximately $8.2 billion on anti-money laundering (AML) controls alone in 2017. The crimes themselves, detected and undetected, have become more numerous and costly than ever. In a widely cited estimate, for every dollar of fraud institutions lose ...
In August 2016, Cruz was sentenced to 22 months in prison after having been found guilty of cyberstalking. "Even while Cruz was being driven to jail, she still wanted to talk to the victim ...
Penetration Testing Services. Validate your cyber defenses against real-world threats. Kroll's world-class penetration testing services bring together front-line threat intelligence, thousands of hours of cyber security assessments completed each year and a team of certified cyber experts — the foundation for our sophisticated and scalable approach.
Case No 1: Upsher-Smith Laboratories - Loss Of Nearly $39 Million. Though this incident happened sometime in 2014, it has tremendous significance because it is one of the classic email examples of the CEO Fraud category. CEO fraud is a cyber-attack carried out by malicious actors wherein they send phishing email s to the organization's ...
Detailed cyber crime case studies by a salient cyber law firm in Ahmedabad. Learn about various cyber frauds in India through our cyber crime case studies. Cell: +91 9510122995 Tel: 079-40030031 E-mail : ... The case is related to the posting of obscene, defamatory and annoying message about a divorced woman in the Yahoo message group. ...