Stanford Computer Ethics Case Studies and Interviews
Case studies.
- Algorithmic Decision-Making and Accountability
- Autonomous Vehicles
- Facial Recognition
- Power of Private Platforms
- Joshua Browder interview
- LOGIN & Help

A case study-based cybersecurity ethics curriculum
- Education Policy, Organization and Leadership
- Unit for Criticism and Interpretive Theory
- Coordinated Science Lab
- Siebel School of Computing and Data Science
- Information Trust Institute
- School of Information Sciences
- Industrial and Enterprise Systems Engineering
- European Union Center
Research output : Contribution to conference › Paper › peer-review
This paper describes the rationale for and implementation of an experimental graduate-level cybersecurity ethics course curriculum recently piloted at the at the University of Illinois at Urbana-Champaign. This case study-based ethics curriculum immerses students in real-life ethical dilemmas within cybersecurity and engages in open dialogue and debate within a community of ethical practice. We uphold the importance of preparing students for a future that is truly unknown and uncertain and note that this requires a push beyond some established curricular guidelines for cybersecurity that underlie a rule and compliance-based approach to ethics education. Details of the course layout are offered as well as results from a student-evaluation survey.
| Original language | English (US) |
|---|---|
| State | Published - 2018 |
| Event | - Baltimore Duration: Aug 13 2018 → … |
| Conference | 2018 USENIX Workshop on Advances in Security Education, ASE 2018, co-located with USENIX Security 2018 |
|---|---|
| City | Baltimore |
| Period | 8/13/18 → … |
ASJC Scopus subject areas
- Computer Networks and Communications
- Hardware and Architecture
- Information Systems
Library availability
Related links.
- Link to publication in Scopus
- Link to the citations in Scopus
Fingerprint
- Ethics Curriculum Keyphrases 100%
- Cybersecurity Keyphrases 100%
- Case Study Social Sciences 100%
- Student Evaluation Social Sciences 50%
- Ethical dilemmas Social Sciences 50%
- Ethical Issues Keyphrases 25%
- Ethics Education Keyphrases 25%
- Graduate Level Keyphrases 25%
T1 - A case study-based cybersecurity ethics curriculum
AU - Blanken-Webb, Jane
AU - Palmer, Imani
AU - Deshaies, Sarah Elizabeth
AU - Burbules, Nicholas C.
AU - Campbell, Roy H.
AU - Bashir, Masooda
N1 - Publisher Copyright: © ASE 2018 - 2018 USENIX Workshop on Advances in Security Education, co-located with USENIX Security 2018. All rights reserved.
N2 - This paper describes the rationale for and implementation of an experimental graduate-level cybersecurity ethics course curriculum recently piloted at the at the University of Illinois at Urbana-Champaign. This case study-based ethics curriculum immerses students in real-life ethical dilemmas within cybersecurity and engages in open dialogue and debate within a community of ethical practice. We uphold the importance of preparing students for a future that is truly unknown and uncertain and note that this requires a push beyond some established curricular guidelines for cybersecurity that underlie a rule and compliance-based approach to ethics education. Details of the course layout are offered as well as results from a student-evaluation survey.
AB - This paper describes the rationale for and implementation of an experimental graduate-level cybersecurity ethics course curriculum recently piloted at the at the University of Illinois at Urbana-Champaign. This case study-based ethics curriculum immerses students in real-life ethical dilemmas within cybersecurity and engages in open dialogue and debate within a community of ethical practice. We uphold the importance of preparing students for a future that is truly unknown and uncertain and note that this requires a push beyond some established curricular guidelines for cybersecurity that underlie a rule and compliance-based approach to ethics education. Details of the course layout are offered as well as results from a student-evaluation survey.
UR - http://www.scopus.com/inward/record.url?scp=85072795885&partnerID=8YFLogxK
UR - http://www.scopus.com/inward/citedby.url?scp=85072795885&partnerID=8YFLogxK
AN - SCOPUS:85072795885
T2 - 2018 USENIX Workshop on Advances in Security Education, ASE 2018, co-located with USENIX Security 2018
Y2 - 13 August 2018
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

A Case Study-based Cybersecurity Ethics Curriculum

This paper describes the rationale for and implementation of an experimental graduate-level cybersecurity ethics course curriculum recently piloted at the at the University of Illinois at Urbana-Champaign. This case study-based ethics curriculum immerses students in reallife ethical dilemmas within cybersecurity and engages in open dialogue and debate within a community of ethical practice. We uphold the importance of preparing students for a future that is truly unknown and uncertain and note that this requires a push beyond some established curricular guidelines for cybersecurity that underlie a rule and compliance-based approach to ethics education. Details of the course layout are offered as well as results from a student-evaluation survey.
Related Papers
Alla Skyrda
The article is devoted to the analysis of the problem of teaching professional ethics to future cybersecurity specialists. It is stated that professional tasks of cybersecurity specialists nowadays cannot always be solved using the identified procedures and guidelines. The dilemmas that arise are not always supported by the corresponding laws, rules or codified standards due to the much faster development of the technological basis compared to the legislative support of the professional activity. Thus, the cybersecurity specialists can face unpredictable problems that can require ethical awareness. The article analyses three international educational efforts in creating educational standards for the cybersecurity course: the National Initiative for Cybersecurity Education (NICE), the Cyber Education Project (CEP), Cybersecurity Curricula 2017 and the role of ethics in each. As well as that, the article looks at the national educational standard for this course and the international ...
Springer International Publishing eBooks
Zouheir Trabelsi
International Journal of Information and Communication Technology Education
Margaret McCoey
Teaching offensive security (ethical hacking) is becoming a necessary component of information security curricula with a goal of developing better security professionals. The offensive security components extend curricula beyond system defense strategies. This paper identifies and discusses the learning outcomes achieved as a result of hands-on lab exercises which focus on attacking systems. The paper includes the ethical implications associated with including such labs. The discussion is informed by analyses of log data on student malicious activities, and student survey results. The examination of student behavior after acquiring these skills demonstrates that there is potentially a high risk of inappropriate and illegal behavior associated with this type learning. While acknowledging these risks and problems, the paper recommends that curricula should opt for a teaching approach that offers students both offensive and defensive hands-on lab exercises in conjunction with lecture m...
MWAIS 2017 Proceedings
Jacob Young
Information security education in higher education has made substantial progress. However, despite advancements in pedagogy and the technology used in the classroom, students often yearn for more applied opportunities. Further, small businesses are likely to have inadequate information security postures due to limited budgets and expertise. In order to address both issues, we have developed and are currently piloting an advanced course in ethical hacking which allows students to perform security assessments for local businesses. This paper will assist academics in the implementation of similar courses, which not only improves security education for students, but can also increase opportunities for local businesses to receive affordable security assessments.
DIVYANSH JAIN
Because of financial losses, brand harm, consumer confidence loss, and personal effects of fraudulent activities, businesses, governments, and individuals are all aware of the value of information security today. Because of the gravity of these acts, students interested in information security should obtain a degree that will enable them to interact with the entire user community. Ethical hacking education will help potential professionals develop the awareness and skills they need to combat current and future cybersecurity threats. This research will identify ethical hacking, address current information security patterns, present pedagogical approaches, provide an overview of information security training, and conclude with best practises in the field. Keywords--Ethical hacking knowledge, information security instruction, ethical hacking teaching and learning.
Organizational Cybersecurity Journal: Practice, Process and People
Bakhtiar Sadeghi
Purpose Cybersecurity vulnerabilities are often due to human users acting according to their own ethical priorities. With the goal of providing tailored training to cybersecurity professionals, the authors conducted a study to uncover profiles of human factors that influence which ethical principles are valued highest following exposure to ethical dilemmas presented in a cybersecurity game.Design/methodology/approach The authors’ game first sensitises players (cybersecurity trainees) to five cybersecurity ethical principles (beneficence, non-maleficence, justice, autonomy and explicability) and then allows the player to explore their application in multiple cybersecurity scenarios. After playing the game, players rank the five ethical principles in terms of importance. A total of 250 first-year cybersecurity students played the game. To develop profiles, the authors collected players' demographics, knowledge about ethics, personality, moral stance and values.Findings The authors...
arXiv (Cornell University)
Harjinder Lallie
Diverse Contemporary Issues Facing Business Management Education
Ghassan Al-Qaimari
Aury Curbelo
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Computer Communication Review
Erin Kenneally
Proceedings of IS2003, …
Janusz Zalewski
Information Security Education for a Global Digital Society
Herbert Mattord
54th ACM Technical Symposium on Computing Science Education V. 1 (SIGCSE 2023)
Trystan S Goetze
International Journal of Ethics Education
Ioannis Stavrakakis
Carlos Alejandro Herrera Cristain
Hershey H Friedman
Nicholas Evans
Wendy Ceccucci
Ali Bicak , Diane Murphy
Matthew Charlesworth SJ
SSRN Electronic Journal
Michele Loi
Journal of US-China Public Administration
Donna Schaeffer
EPiC Series in Computing
minhaz chowdhury
Lecture Notes in Computer Science
2014 47th Hawaii International Conference on System Sciences
James Ramsay
Jeff Hearn , Aljeane (AJ) Alfiler , Paul Brooks , Lydia Zeman , Qingzhao Li , Ravi Patadiya
2017 IEEE World Engineering Education Conference (EDUNINE)
Henrique Santos
Journal of Computing Sciences in Colleges
Don Gotterbarn
Social Science Research Network
John P Sullins
Proceedings of the 2011 conference on Information technology education - SIGITE '11
Robert Strikwerda
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024

Type to search
Cybersecurity Case Studies and Real-World Examples
image courtesy pixabay.com
Table of Contents
In the ever-evolving landscape of cybersecurity, the battle between hackers and defenders continues to shape the digital domain. To understand the gravity of cybersecurity challenges, one need only examine real-world examples—breaches that have rocked industries, compromised sensitive data, and left organizations scrambling to shore up their defenses. In this exploration, we’ll dissect notable cybersecurity case studies, unravel the tactics employed by cybercriminals , and extract valuable lessons for strengthening digital defenses.
Equifax: The Breach that Shattered Trust
In 2017, Equifax, one of the largest credit reporting agencies, fell victim to a massive data breach that exposed the personal information of nearly 147 million individuals. The breach included sensitive data such as names, Social Security numbers, birthdates, and addresses, leaving millions vulnerable to identity theft and fraud.
Lessons Learned
1. Patch Management is Crucial:
The breach exploited a known vulnerability in the Apache Struts web application framework. Equifax failed to patch the vulnerability promptly, highlighting the critical importance of timely patch management. Organizations must prioritize staying current with security patches to prevent known vulnerabilities from being exploited.
2. Transparency Builds Trust:
Equifax faced severe backlash not only for the breach itself but also for its delayed and unclear communication with affected individuals. Transparency in communication is paramount during a cybersecurity incident. Organizations should proactively communicate the extent of the breach, steps taken to address it, and measures for affected individuals to protect themselves.
Target: A Cybersecurity Bullseye
In 2013, retail giant Target suffered a significant breach during the holiday shopping season. Hackers gained access to Target’s network through a third-party HVAC contractor, eventually compromising the credit card information of over 40 million customers and the personal information of 70 million individuals.
1. Third-Party Risks Require Vigilance:
Target’s breach underscored the risks associated with third-party vendors. Organizations must thoroughly vet and monitor the cybersecurity practices of vendors with access to their networks. Note that a chain is only as strong as its weakest link.
2. Advanced Threat Detection is Vital:
Target failed to detect the initial stages of the breach, allowing hackers to remain undetected for an extended period. Implementing robust advanced threat detection systems is crucial for identifying and mitigating breaches in their early stages.
WannaCry: A Global Ransomware Epidemic
In 2017, the WannaCry ransomware swept across the globe, infecting hundreds of thousands of computers in over 150 countries. Exploiting a vulnerability in Microsoft Windows, WannaCry encrypted users’ files and demanded ransom payments in Bitcoin for their release.
1. Regular System Updates are Non-Negotiable:
WannaCry leveraged a vulnerability that had been addressed by a Microsoft security update months before the outbreak. Organizations fell victim due to delayed or neglected updates. Regularly updating operating systems and software is fundamental to thwarting ransomware attacks .
2. Backup and Recovery Planning is Essential:
Organizations that had robust backup and recovery plans were able to restore their systems without succumbing to ransom demands. Implementing regular backup procedures and testing the restoration process can mitigate the impact of ransomware attacks.
Sony Pictures Hack: A Cyber Espionage Saga
In 2014, Sony Pictures Entertainment became the target of a devastating cyberattack that exposed an array of sensitive information, including unreleased films, executive emails, and employee records. The attackers, linked to North Korea, sought to retaliate against the film “The Interview,” which portrayed the fictional assassination of North Korea’s leader.
1. Diverse Attack Vectors:
The Sony hack demonstrated that cyber threats can come from unexpected sources and employ diverse attack vectors. Organizations must not only guard against common threats but also be prepared for unconventional methods employed by cyber adversaries .
2. Nation-State Threats:
The involvement of a nation-state in the attack highlighted the increasing role of geopolitical motivations in cyber incidents. Organizations should be aware of the potential for state-sponsored cyber threats and implement measures to defend against politically motivated attacks.
Marriott International: Prolonged Exposure and Ongoing Impact
In 2018, Marriott International disclosed a data breach that had persisted undetected for several years. The breach exposed personal information, including passport numbers, of approximately 500 million guests. The prolonged exposure raised concerns about the importance of timely detection and response.
1. Extended Dwell Time Matters:
Marriott’s breach highlighted the significance of dwell time—the duration a threat actor remains undetected within a network. Organizations should invest in advanced threat detection capabilities to minimize dwell time and swiftly identify and mitigate potential threats.
2. Post-Breach Communication:
Marriott faced criticism for the delayed communication of the breach to affected individuals. Prompt and transparent communication is vital in maintaining trust and allowing individuals to take necessary actions to protect themselves.
SolarWinds Supply Chain Attack: A Wake-Up Call
In late 2020, the SolarWinds supply chain attack sent shockwaves through the cybersecurity community. Sophisticated threat actors compromised SolarWinds’ software updates, enabling them to infiltrate thousands of organizations, including government agencies and major corporations.
1. Supply Chain Vulnerabilities:
The incident underscored the vulnerability of the software supply chain. Organizations must conduct thorough assessments of their suppliers’ cybersecurity practices and scrutinize the security of third-party software and services.
2. Continuous Monitoring is Essential:
The SolarWinds attack highlighted the importance of continuous monitoring and threat detection. Organizations should implement robust monitoring systems to identify anomalous behavior and potential indicators of compromise.
Notable Lessons and Ongoing Challenges
1. Human Element:
Many breaches involve human error, whether through clicking on phishing emails or neglecting cybersecurity best practices. Cybersecurity awareness training is a powerful tool in mitigating the human factor. Employees should be educated on identifying phishing attempts, using secure passwords, and understanding their role in maintaining a secure environment.
2. Zero Trust Architecture:
The concept of Zero Trust, where trust is never assumed, has gained prominence. Organizations should adopt a mindset that verifies every user, device, and network transaction, minimizing the attack surface and preventing lateral movement by potential intruders.
3. Cybersecurity Collaboration:
Cybersecurity is a collective effort. Information sharing within the cybersecurity community, between organizations, and with law enforcement agencies is crucial for staying ahead of emerging threats. Collaborative efforts can help identify patterns and vulnerabilities that may not be apparent to individual entities.
4. Regulatory Compliance:
The landscape of data protection and privacy regulations is evolving. Compliance with regulations such as GDPR, HIPAA, or CCPA is not only a legal requirement but also a cybersecurity best practice. Understanding and adhering to these regulations enhances data protection and builds trust with customers.
5. Encryption and Data Protection:
The importance of encryption and data protection cannot be overstated. In various breaches, including those of Equifax and Marriott, the compromised data was not adequately encrypted, making it easier for attackers to exploit sensitive information. Encrypting data at rest and in transit is a fundamental cybersecurity practice.
6. Agile Incident Response:
Cybersecurity incidents are inevitable, but a swift and agile incident response is crucial in minimizing damage. Organizations should regularly test and update their incident response plans to ensure they can respond effectively to evolving threats.
7. User Awareness and Training:
Human error remains a significant factor in many breaches. User awareness and training programs are essential for educating employees about cybersecurity risks , promoting responsible online behavior, and reducing the likelihood of falling victim to phishing or social engineering attacks.
8. Continuous Adaptation:
Cyber threats constantly evolve, necessitating a culture of continuous adaptation. Organizations should regularly reassess and update their cybersecurity strategies to address emerging threats and vulnerabilities.
Conclusion: Navigating the Cybersecurity Landscape
The world of cybersecurity is a battlefield where the landscape is ever-changing, and the adversaries are relentless. Real-world case studies serve as poignant reminders of the importance of proactive cybersecurity measures . As organizations adapt to emerging technologies, such as cloud computing, IoT, and AI, the need for robust cybersecurity practices becomes more pronounced. Real-world case studies offer invaluable insights into the tactics of cyber adversaries and the strategies employed by organizations to defend against evolving threats.

Prabhakar Pillai
I am a computer engineer from Pune University. Have a passion for technical/software blogging. Wrote blogs in the past on SaaS, Microservices, Cloud Computing, DevOps, IoT, Big Data & AI. Currently, I am blogging on Cybersecurity as a hobby.
Hi, I believe your website mmight be having browser compatibility problems. Whenever I lokok att your blog in Safari, it looks fine but when opening in Internet Explorer, it has some overlapping issues. I just wanted to provide you with a quick heads up! Other than that, excellent blog!
Consider opening in chrome or Microsoftedge. Thank you for the comments
Leave a Comment Cancel Comment
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.


- Advanced Search
Predicting and Explaining Cyber Ethics with Ethical Theories
New citation alert added.
This alert has been successfully added and will be sent to:
You will be notified whenever a record that you have chosen has been cited.
To manage your alert preferences, click on the button below.
New Citation Alert!
Please log in to your account
Information & Contributors
Bibliometrics & citations, view options, index terms.
Human-centered computing
Human computer interaction (HCI)
Security and privacy
Human and societal aspects of security and privacy
Social and professional topics
Computing / technology policy
Privacy policies
Professional topics
Computing profession
Codes of ethics
Recommendations
Beyond kant and bentham: how ethical theories are being used in artificial moral agents.
From robots to autonomous vehicles, the design of artificial moral agents (AMAs) is an area of growing interest to HCI, and rising concern for the implications of deploying moral machines raises questions about which ethical frameworks are being used in ...
Moral luck and computer ethics: Gauguin in cyberspace
I argue that the problem of `moral luck' is an unjustly neglected topic within Computer Ethics. This is unfortunate given that the very nature of computer technology, its `logical malleability', leads to ever greater levels of complexity, unreliability ...
Necessity for ethics in social engineering research
Social engineering is deeply entrenched in the fields of both computer science and social psychology. Knowledge is required in both these disciplines to perform social engineering based research. Several ethical concerns and requirements need to be ...
Information
Published in.
United States
Publication History
Author tags.
- Academic Integrity
- Consequentialism
- Cyber Ethics
- Cyber Security
- Ethical Theory
- Intellectual Property
- Virtue Ethics
Contributors
Other metrics, bibliometrics, article metrics.
- 0 Total Citations
- 0 Total Downloads
- Downloads (Last 12 months) 0
- Downloads (Last 6 weeks) 0
View options
Login options.
Check if you have access through your login credentials or your institution to get full access on this article.
Full Access
Share this publication link.
Copying failed.
Share on social media
Affiliations, export citations.
- Please download or close your previous search result export first before starting a new bulk export. Preview is not available. By clicking download, a status dialog will open to start the export process. The process may take a few minutes but once it finishes a file will be downloadable from your browser. You may continue to browse the DL while the export process is in progress. Download
- Download citation
- Copy citation
We are preparing your search results for download ...
We will inform you here when the file is ready.
Your file of search results citations is now ready.
Your search export query has expired. Please try again.
McCombs School of Business
- Español ( Spanish )
Videos Concepts Unwrapped View All 36 short illustrated videos explain behavioral ethics concepts and basic ethics principles. Concepts Unwrapped: Sports Edition View All 10 short videos introduce athletes to behavioral ethics concepts. Ethics Defined (Glossary) View All 58 animated videos - 1 to 2 minutes each - define key ethics terms and concepts. Ethics in Focus View All One-of-a-kind videos highlight the ethical aspects of current and historical subjects. Giving Voice To Values View All Eight short videos present the 7 principles of values-driven leadership from Gentile's Giving Voice to Values. In It To Win View All A documentary and six short videos reveal the behavioral ethics biases in super-lobbyist Jack Abramoff's story. Scandals Illustrated View All 30 videos - one minute each - introduce newsworthy scandals with ethical insights and case studies. Video Series
Case Study UT Star Icon
Cyber Harassment
After a student defames a middle school teacher on social media, the teacher confronts the student in class and posts a video of the confrontation online.
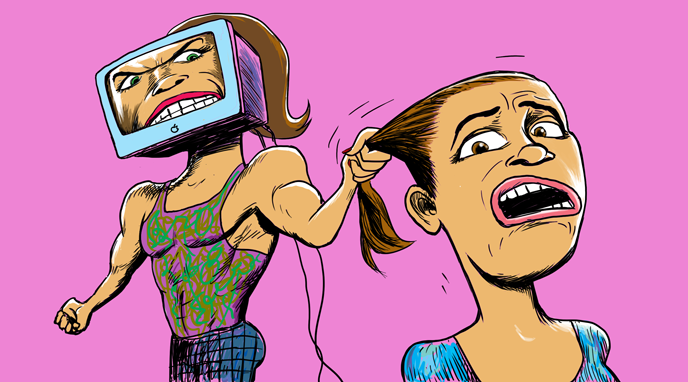
In many ways, social media platforms have created great benefits for our societies by expanding and diversifying the ways people communicate with each other, and yet these platforms also have the power to cause harm. Posting hurtful messages about other people is a form of harassment known as cyberbullying. Some acts of cyberbullying may not only be considered slanderous, but also lead to serious consequences. In 2010, Rutgers University student Tyler Clementi jumped to his death a few days after his roommate used a webcam to observe and tweet about Tyler’s sexual encounter with another man. Jane Clementi, Tyler’s mother, stated:
“In this digital world, we need to teach our youngsters that their actions have consequences, that their words have real power to hurt or to help. They must be encouraged to choose to build people up and not tear them down.”
In 2013, Idalia Hernández Ramos, a middle school teacher in Mexico, was a victim of cyber harassment. After discovering that one of her students tweeted that the teacher was a “bitch” and a “whore,” Hernández confronted the girl during a lesson on social media etiquette. Inquiring why the girl would post such hurtful messages that could harm the teacher’s reputation, the student meekly replied that she was upset at the time. The teacher responded that she was very upset by the student’s actions. Demanding a public apology in front of the class, Hernández stated that she would not allow “young brats” to call her those names. Hernández uploaded a video of this confrontation online, attracting much attention.
While Hernández was subject to cyber harassment, some felt she went too far by confronting the student in the classroom and posting the video for the public to see, raising concerns over the privacy and rights of the student. Sameer Hinduja, who writes for the Cyberbullying Research Center, notes, “We do need to remain gracious and understanding towards teens when they demonstrate immaturity.” Confronting instances of a teenager venting her anger may infringe upon her basic rights to freedom of speech and expression. Yet, as Hinduja explains, teacher and student were both perpetrators and victims of cyber harassment. All the concerns of both parties must be considered and, as Hinduja wrote, “The worth of one’s dignity should not be on a sliding scale depending on how old you are.”
Discussion Questions
1. In trying to teach the student a lesson about taking responsibility for her actions, did the teacher go too far and become a bully? Why or why not? Does she deserve to be fired for her actions?
2. What punishment does the student deserve? Why?
3. Who is the victim in this case? The teacher or the student? Was one victimized more than the other? Explain.
4. Do victims have the right to defend themselves against bullies? What if they go through the proper channels to report bullying and it doesn’t stop?
5. How should compassion play a role in judging other’s actions?
6. How are factors like age and gender used to “excuse” unethical behavior? (ie. “Boys will be boys” or “She’s too young/old to understand that what she did is wrong”) Can you think of any other factors that are sometimes used to excuse unethical behavior?
7. How is cyberbullying similar or different from face-to-face bullying? Is one more harmful than the other? Explain.
8. Do you know anyone who has been the victim of cyber-bullying? What types of harm did this person experience? Why or why not? Does she deserve to be fired for her actions?
Related Videos

Causing Harm
Causing harm explores the types of harm that may be caused to people or groups and the potential reasons we may have for justifying these harms.
Bibliography
Teacher suspended after giving student a twitter lesson http://www.cnn.com/2013/09/12/world/americas/mexico-teacher-twitter/index.html
Pros and Cons of Social Media in the Classroom http://campustechnology.com/Articles/2012/01/19/Pros-and-Cons-of-Social-Media-in-the-Classroom.aspx?Page=1
How to Use Twitter in the Classroom http://thenextweb.com/twitter/2011/06/23/how-to-use-twitter-in-the-classroom/
Twitter is Turning Into a Cyberbullying Playground http://www.takepart.com/article/2012/08/08/twitter-turning-cyberbullying-playground
Can Social Media and School Policies be “Friends”? http://www.ascd.org/publications/newsletters/policy-priorities/vol17/num04/Can-Social-Media-and-School-Policies-be-%C2%A3Friends%C2%A3%C2%A2.aspx
What Are the Free Expression Rights of Students In Public Schools Under the First Amendment? http://www.firstamendmentschools.org/freedoms/faq.aspx?id=12991
Teacher Shames Student in Classroom After Student Bullies Teacher on Twitter http://cyberbullying.us/teacher-shames-student-in-classroom-after-student-bullies-teacher-on-twitter/
Stay Informed
Support our work.
- DOI: 10.4018/978-1-4666-5880-6.CH004
- Corpus ID: 1764982
CyberEthics Case Study
- Georgia Sakka , Iliada Spyrou
- Published 2014
- Computer Science, Law, Philosophy
2 Citations
Opportunities for enhancing ethical climates in online courses: best practices for reducing student cheating, a customised dataset to assist legal and ethical governance of seaports, 30 references, cyber stalking: an analysis of online harassment and intimidation, the future of cyber criminology: challenges and opportunities1, cyber hate: antisocial networking in the internet, digital image bullying among school students in belgium: an exploration of the characteristics of bullies and their victims, establishing a theory of cyber crimes, cyber criminology: evolving a novel discipline with a new journal, ethical issues of ‘morality mining': moral identity as a focus of data mining, cyberbullying: its nature and impact in secondary school pupils., sexting: a new form of victimless crime, a contingency framework for understanding ethical decision making in marketing, related papers.
Showing 1 through 3 of 0 Related Papers
Cyber Ethics: Short Answer Type Questions | Computer Application: Class 10 PDF Download
| 1 Crore+ students have signed up on EduRev. Have you? |
Q.1. What is software license? (2 Marks) Ans: A software license is a legal document that describes the legal rights pertaining to the authorized use or redistribution of software. It defines the responsibilities of the parties entering into the license agreement and may impose restrictions on how the software can be used. Q.2. Write a short note on DRM. (2 Marks) Ans:
- Digital Rights Management (DRM) is a systematic approach to copyright protection for digital media. The purpose of DRM is to prevent unauthorized redistribution of digital media and restrict the ways consumers can copy content they’ve purchased.
- Digital rights refers to the relationship between copyrighted digital works (such as film, music and art) and user permissions and rights related to computers, networks and electronic devices.
- Digital rights also refers to the access and control of digital information. The definition of digital rights and responsibilities is having the right and freedom to use all types of digital technology while using the technology in an acceptable and appropriate manner. As a user of digital technology, you also have the right to privacy and the freedom of personal expression.
Q.3. What is open source software? (2 Marks) Ans: Open source software is a software that any programmer can download from the internet free and modify with suggested improvements. The changes must be made available to all. Any programmer can make improvements, which can result in better quality software Example: Firefox web browser, Linux OS etc. Q.4. Can we use open source software (OSS) for all organisations? (2 Marks) OR What are the disadvantages of open source software? (2 Marks) Ans: The open source software:
- May not provide long term support
- May not be secure enough
- May not be scalable
So, they cannot be recommended for all organizations. Though, OSS software suite (LAMP – Linux, Apache, MySQL and PHP) can be used even for military organisations as they have community-development groups, security and scalability. Q.5. What is proprietary software? (2 Marks) Ans: Proprietary softwares are commercial or packaged softwares, It is copyrighted software that prohibits the redistribution or modification of its program. Example: Microsoft Office, Adobe Photoshop etc. Q.6. Kuhu has just learnt how to do online banking. Name any two precautions that she should take to prevent online fraud. (2 Marks) Ans:
- Do not share user id and password with anyone.
- Avoid doing transactions from cyber cafe and other public places.
Detailed Answer:
- Use bigger and strong password.
- Do not use predictable passwords like mobile number, date of birth.
Q.7. What is freedom of information? (2 Marks) Ans: Freedom of information refers to a citizen’s right to access information that is held by the government. The right to information is a fundamental right. It helps in creating a more open and democratic society, challenging corruption and enhancing transparency. Q.8. What is free open source software movement? (2 Marks) Ans: Free/open-source software movement (FOSSM) or free/libre open-source software movement (FLOSSM) is a social movement with the goal of obtaining and guaranteeing certain freedoms for software users, namely the freedom to run the software, to study and change the software, and to redistribute copies with or without changes. Richard Stallman formally founded the movement in 1983 by launching the GNU Project. Stallman, later established the Free Software Foundation in 1985 to support the movement. Q.9. What are digital property rights? (2 Marks) Ans: Digital property rights includes data, internet accounts and other rights in the digital world. Intellectual property rights can also exist in digital property such as pictures, music, movies, literary works, web pages, computer code. It refers to access and control of digital information. Q.10. What do you mean by e-Commerce? How has it benefitted the customer? (2 Marks) Ans: e-Commerce is the ability to do business online via internet. Consumers no longer need to travel to shops or stores to get their daily needs. All they have to do in browse through the Internet and purchase the product needed using their computer connected to the Internet and save their time and energy. Q.11. What is online fraud? (2 Marks) Ans: Fraud committed using the Internet is called online fraud. Online fraud may occur in many forms such as:
- Non-delivered goods
- Stealing information
- Fraudulent payments
- Non-existent companies
| |49 docs|18 tests |
Top Courses for Class 10

FAQs on Cyber Ethics: Short Answer Type Questions - Computer Application: Class 10
| 1. What is cyber ethics? |
| 2. Why is cyber ethics important? |
| 3. What are some common cyber ethics violations? |
| 4. How can individuals practice cyber ethics? |
| 5. What are the consequences of not following cyber ethics? |
| Rating | |
mock tests for examination
Extra questions, video lectures, practice quizzes, important questions, shortcuts and tricks, study material, semester notes, sample paper, previous year questions with solutions, cyber ethics: short answer type questions | computer application: class 10, objective type questions, past year papers, viva questions.

Cyber Ethics: Short Answer Type Questions Free PDF Download
Importance of cyber ethics: short answer type questions, cyber ethics: short answer type questions notes, cyber ethics: short answer type questions class 10, study cyber ethics: short answer type questions on the app.
| cation olution |
| Join the 10M+ students on EduRev |
Welcome Back
Create your account for free.

Forgot Password
Unattempted tests, change country, practice & revise.

Ethical Dilemmas in Cybersecurity
- Markkula Center for Applied Ethics
- Focus Areas
- Internet Ethics
- Internet Ethics: Views From Silicon Valley

A Learning Lab at RSA
Inviting cybersecurity experts to a conversation about ethical dilemmas

binary code on a screen
Irina Raicu is the director of the Internet Ethics program at the Markkula Center for Applied Ethics at Santa Clara University. Views are her own.
On April 17, I was one of three facilitators of a Learning Lab as part of the RSA conference in San Francisco —joining Sean Brooks of the Center for Long-term Cybersecurity at U.C. Berkley and Jeff Klaben of SRI International . The Learning Lab discussed a number of ethical dilemmas in cybersecurity and introduced ways to address those dilemmas. In anticipation of that discussion, we asked potential participants to rank the ones listed below, and invited them to add other dilemmas to the list.
Vulnerability disclosur e: When and how should researchers inform the public about vulnerabilities in widely-used products? What steps should be taken before any such notification?
Encryption : What should companies do in response to legal law enforcement requests for encrypted data? Should known vulnerabilities in systems be used to comply with requests that would otherwise be impossible? Should law enforcement agencies use such vulnerabilities themselves if they suspect a formal legal request will not bear fruit?
Research : How should researchers balance the use of potentially aggressive penetration testing techniques against the legal rights of the owners of systems they are researching? Does that balance change in cases where those system owners are not implementing reasonably strong security methods?
Automated security tools : Is it ethical to release tools that can automate attacks on a broad array of systems into the wild?
Sale restrictions : What (if any) is the responsibility of cybersecurity professionals to try to prevent the sale of products they have developed to autocratic governments that would use them to harm their citizens?
The role of the CISO : What kinds of personal risk should a Chief Information Security Officer or manager-level security officer accept on behalf of an organization? It is not uncommon for CISOs to be fired or forced out when a cybersecurity breach occurs; should organizations offer CISOs employment agreements that include provisions for relief from personal legal liability or other protections? How should organizational deficiencies (under-investment, bad practices, etc.) factor in this analysis?
Cybersecurity incident response : How much time and energy should be spent investigating a breach? What is an appropriate level of incident detail to share with customers and other stakeholders? How thick is the line between satisfying organizational obligations and finding the complete truth behind an incident?
Have you considered the ethical dimensions of these issues? What other cybersecurity-related ethical questions would you add to that list?
Related materials:
- "A Framework for Ethical Decision Making": https://www.scu.edu/ethics/ethics-resources/a-framework-for-ethical-decision-making/
- "An Introduction to Cybersecurity Ethics" (a free teaching module for cybersecurity courses): https://www.scu.edu/ethics/focus-areas/technology-ethics/resources/an-introduction-to-cybersecurity-ethics/
Image by Christiaan Colen, cropped, used under a Creative Commons license .
Subscribe to Our Blogs
- All About Ethics
- Benison: The Practice of Ethical Leadership
- Center News
- Ethical Dilemmas in the Social Sector
- Internet Ethics: Views from Silicon Valley
Cyberethics
Class 10 - sumita arora cbse computer code 165, objective type questions.
Policies of companies related to protection of personal information of users online are meant to safeguard ............... of users.
Reason — By implementing privacy policies, companies protect personal information of users, such as their name, contact details, financial data, or browsing history from unauthorized access, use, or disclosure, thus, maintaining their privacy rights and preventing misuse or exploitation of their data.
Credit card fraud may include :
- Stealing of credit card
- Unauthorized and illegal use of credit card
Both of the above
Reason — Credit card fraud may include both stealing of credit card and unauthorized and illegal use of credit card.
Using someone else's twitter handle to post something, will be termed as :
Identity theft
- Online stealing
Reason — Using someone else's twitter handle to post something, will be termed as identity theft .
Standard security protocol that establishes encrypted links between a web server and a browser is called ............... .
- Online safety technology
- SDT technology
- Web encryption technology
Secure sockets layer technology
Reason — Standard security protocol that establishes encrypted links between a web server and a browser is called Secure sockets layer technology .
Things like these, e.g., online email account, social media account or handle, online shopping account, online photo sharing account, trademarks, patents, own registered domain name etc. are collectively called ............... .
- Online identity
- Online estate
- Digital identity
Digital property
Reason — Things like these, e.g., online email account, social media account or handle, online shopping account, online photo sharing account, trademarks, patents, own registered domain name etc. are collectively called digital property .
A ............... is an economic and social inequality with regard to access to, use of, or impact of ICT.
- Digital inequality
- Difference of services
Digital divide
- Differential divide
Reason — A digital divide is an economic and social inequality with regard to access to, use of, or impact of ICT.
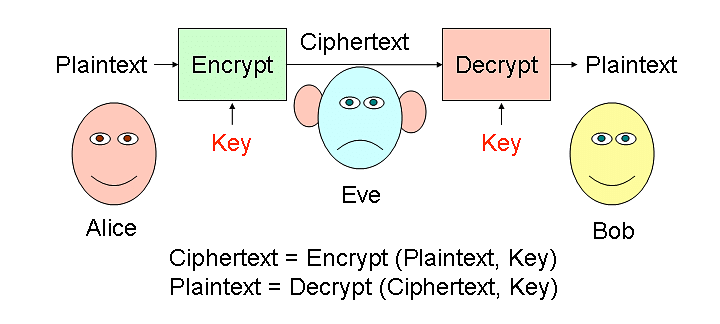
Preeti needs to send a very confidential message to her colleague in office over a secure channel. She uses a technique wherein an actual message (which is in readable form) can be converted into an unreadable message. This concept is known as ................ .
- Data Security
Reason — The concept of converting a readable message into an unreadable form is known as encryption.
Which of the following techniques can be used for security of data ?
- Authentication
- Authorisation
All of the Above
Reason — Authentication, authorisation and encryption techniques can be used for security of data.
Which of the following is not a cybercrime ?
Using licensed software
Reason — Using licensed software is not a cyber crime. Plagiarism, phishing and hacking are cyber crimes.
Question 10
Secure data transmission means :
- Data is accessible by any unauthorized person during transmission.
Data cannot be accessed by any unauthorized person during transmission.
- Transmission of data happens easily
- No one can access it
Reason — Secure data transmission means the data can not be accessed by any unauthorized person during transmission.
Question 11
Which of the following is NOT an example of Intellectual Property rights ?
- Industrial Design
Reason — Password is not an example of Intellectual Property rights because it does not represent a legal protection for creations or inventions. Patent, Trademark and Industrial Design can be used to protect one's intellectual property rights.
Question 12
A ............... is the right given by the government to an inventor to protect his/her invention from being used/copied for a fixed period of time.
- Intellectual Property
Reason — A patent is the right given by the government to an inventor to protect his/her invention from being used/copied for a fixed period of time.
Question 13
Arun clicks on a link received in a message on his phone which promises him a complimentary trip to a destination of his choice. He forwarded this message to his friend, Panshul and asked him to do the same. But Panshul refuses and tells Arun that his personal and private information, such as online account names, login information and passwords can be stolen and he should be careful of such ............... attacks.
Reason — Phishing is a deceptive technique used by cybercriminals to trick individuals into revealing sensitive information, such as usernames, passwords, or financial details.
Question 14
Charlene is an artist. She displays her artwork on the Internet using her website to attract buyers. One day while browsing the Internet she discovers that another artist has displayed her painting portraying it as his own. Which right of Charlene was infringed ?
- Digital Privacy right
Intellectual Property right
- Digital Property right
- Intellectual Privacy right
Reason — Intellectual property rights are the rights of the owner of information to decide how much information is to be exchanged, shared or distributed. Also it gives the owner a right to decide the price for doing so. Here, the artwork is the intellectual right of Charlene.
Question 15
Which of these is NOT an example of Cyber bullying ?
- Copying a classmate's personal photo against his/her permission from his social media account and sending it to other friends on their emails
Bullying a classmate in the school corridor
- Threatening someone on whatsapp
- Posting mean messages about someone on their social media
Reason — Cyber bullying refers to an act of bullying on internet. Bullying a classmate in the school corridor doesn't involve internet. Hence, it cannot be considered as cyber bullying.
The other three acts involve the use of internet for bullying. Hence, they come under cyber bullying.
Question 16
Which of the following is NOT a reason for the digital divide in different demographic regions ?
- Cost of Technology
- Lack of information
Lack of access to high performance computers
- Lack of access to the disabled
Reason — Cost of Technology, lack of information and lack of access to the disabled are reasons of digital divide. Lack of access to high performance computers is not a reason for digital divide as information can be accessed even through a normally functioning computer or mobile phone.
Question 17
One of the most popular methods of encrypting data is Caesar cipher where original data is replaced by a key character like if key is -2 than 'a' will be replaced by ' y' , 'b' is replaced by 'z' and so on. If the key is 2 i.e., every letter is replaced by its next to next letter means the letter 'A' will be replaced by 'C', the letter 'B' is replaced by 'D', and so on then what will be the replacement of the word 'CoMpUtEr'.
Reason — According to the key, each letter of CoMpUtEr is replaced as follows:
C → E o → q M → O p → r U → W t → v E → G r → t
Question 18
Which of the following is a way to avoid Plagiarism when using material from the Internet ?
(ii) Paraphrasing
(iii) Referencing
(iv) Embedding
Choose the correct option :
- (i) and (ii) only
(i), (ii) and (iii) only
- (ii) and (iv) only
Reason — To avoid plagiarism, while referring to someone's else's creation, we must always give credit whenever we use:
- Another person's idea, opinion, or theory
- Quotations of another person's actual spoken or written words
- Paraphrase of another person's spoken or written words.
Question 19
............... is a software for which exclusive rights of modification in the source code remain with the owner.
- Free Open-Source Software
- Open-Source Software
Proprietary Software
Reason — Proprietary Software is a software for which exclusive rights of modification in the source code remain with the owner.
Question 20
Pratham is excited to use a new software which is freely available to download but he cannot modify or change the source code. Pratham is using :
- Both (1) and (2)
- None of the above
Reason — A freeware software is available free of cost and allows copying and further distribution, but not modification and its source code is not available.
Question 21
Which one of the following software comes under Open-Source Software category ?
Reason — The source code of Linux is available to customers and it can be modified and redistributed without any limitation.
Theoretical Questions
What do you understand by privacy of data in e-commerce context ?
In e-commerce context, privacy of data is related to a company's policies on the use of user data. An e-commerce company must clearly state how it intends to use the data collected from the customer and whether the customer can restrict the use of personal information.
What role does consumer consent play in implementing the privacy of user data ?
Consumer consent plays a vital role in implementing the privacy of consumer data. Consumer consent decides what information can and cannot be used. The consent also relates to whether the given information can be further exploited.
What is the responsibility of e-commerce merchant to ensure before getting user's consent about his/her details' usage ?
Before getting user's consent about his/her details' usage, the e-commerce merchant must ensure the following:
- The merchant must clearly state about how the user data will be used, in the terms and conditions of its site.
- The merchant must ensure that the user has gone through the terms and conditions given on its site prior to making any transactions.
- The merchant must assure the user about data safety by implementing proper data safety and security measures such as https protocol and other security mechanism so that users' data is safe from hackers too.
What is online fraud ? Give some examples.
Fraud committed using the Internet is called Online fraud. Online fraud may occur in many forms such as :
- Non-delivered goods
- Non-existent companies
- Stealing information
- Fraudulent payments
Some examples of online fraud are:
- Credit card fraud where credit card details are stolen from a user's online activities and the money is used without the user's knowledge.
- Using someone's credentials to watch an online show or movie.
- Non-delivery of goods after payment is another example. On investigation, a user may find that the company or website was fraud.
What is credit card fraud ?
In credit card frauds, the credit card details of a user such as his credit card number, name, CVV, transaction pin, etc., are stolen from his/her online activities and then some payment frauds are carried out with this stolen information.
What is identity theft ?
Online identity theft refers to an act of stealing someone's personal information such as name, login details etc. and then posing as that person online. Malicious activities like fraudulent posts, rumour mongering, riots fueling, fraudulent financial transactions, etc. can be carried out through identity theft.
What measures can you take to curb online frauds ?
The measures that can be taken to curb online frauds are as follows:
- A monitoring official body that ensures the authenticity of e-commerce company and delivery of goods/services as promised.
- Strong security mechanism by the e-commerce site and payment gateways to prevent stealing of crucial information.
- Official guidelines and safeguards on the selling of users' data to third parties.
What is safe data transmission ? How can you ensure secure data transmission ?
Secure data transmission means applying enough technical safeguards so that data travels safely to its target, without being compromised or eavesdropped. To ensure secure data transmission, following techniques are applied:
- SSL secure data transmission — SSL (Secure Sockets Layer) is a standard security protocol which ensures data security by establishing encrypted online links between a web server and a browser.
- Data encryption — Encrypted data when sent over Internet is hard to steal and hence is safer.
- Using Safe protocols — such as for files, secure FTP protocol.
What is intellectual property ? What do you understand by intellectual property rights ?
Any piece of information is produced or created with a lot of efforts and it consumes a lot of time. Creative creations of mind such as patents, literary and creative arts, copyrights, trademarks etc. are known as intellectual property.
Intellectual property rights are the rights of the owner of information to decide how much information is to be exchanged, shared or distributed. Also it gives the owner a right to decide the price for doing so.
What is plagiarism ? How can you avoid plagiarism while referring to someone's else's creation ?
Plagiarism is stealing someone else's intellectual work, such as an idea, literary work or academic work etc., and representing it as our own work without giving credit to creator or without citing the source of information.
To avoid plagiarism while referring to someone else's creation, we must give credit whenever we use:
- Another person's idea, opinion, or theory;
- Quotations of another person's actual spoken or written words; or
- Paraphrase of another person's spoken or written words
What is digital property ? What are the threats to digital properties ?
Digital property (or digital assets) refers to any information about us or created by us that exists in digital form, either online or on an electronic storage device.
For example, any online personal accounts such as email, personal websites and blogs, domain names registered in our name, intellectual properties etc.
The common threats to digital properties are as follows:
- Digital software penetration tools — There are many software penetration tools such as cracks and keygens which enable unauthorized users to freely access a software without actually paying for it.
- Stealing and plagiarizing codes of digital properties — Other developers may steal a software's source code and use it to build their own versions of it, and then sell it under their own company name.
How can you protect your digital properties ?
The following ways to ensure protection of your digital properties:
- Anti-Tamper Solutions — They use a host of advanced technologies to prevent hacking, reverse-engineering or manipulating digital properties such as utility tools, software, apps, video games and so forth.
- Legal Clauses — There must be a transparent clause in the software's Terms of Service that prohibits the scraping of the software's source code for reuse.
- Limit the sharing of software code — One should share software code only with trusted individuals who are part of development team. Digital Rights Management (DRM) solution can protect a software from being scraped for source code using decompilers etc.
Expand the terms:
- OSI — Open Source Initiative.
- FLOSS — Free Libre/Livre and Open Source Software.
- FSF — Free Software Foundation.
- GNU — GNU is Not Unix.
- GPL — General Public Licence.
- W3C — World Wide Web Consortium.
- OSS — Open Source Software.
What are open source based software ?
Open source software is the software whose source code is available and which can be copied, modified and redistributed as well. There may or may not be charges payable for open source software.
In open source software, the source code is freely available to the customer. For example, Linux.
Question 15(i)
Compare and Contrast: Free software and Open source software
Free software is the software which is free of cost, which can be copied, modified and redistributed as well and whose source code is available. No charges are payable for free software.
Open source software, on the other hand, is the software, whose source code is available and which can be copied, modified and redistributed as well. There may or may not be charges payable for open source software.
Question 15(ii)
Compare and Contrast: OSS and FLOSS
OSS refers to Open Source Software whose source code is made available to the public, allowing anyone to view, modify, and distribute the code. However, OSS does not necessarily mean that the software is completely free of charge. It only means that the source code is available for others to access and modify.
FLOSS refers to Free Libre/Livre and Open Source Software. The term FLOSS is used to refer to a software which is both free software as well as open source software. In addition to being Open Source, FLOSS also emphasises that no charges are applicable to the user for using and distributing the software.
Question 15(iii)
Compare and Contrast: Proprietary software and Free software
Proprietary software is the software that is neither open nor freely available. Its use is regulated and further distribution and modification is either forbidden or requires special permission by the supplier or vendor. Source code of proprietary software is normally not available. These softwares need to be purchased before they can be used.
Free software means that the software is freely accessible and can be freely used, changed, improved, copied and distributed by all who wish to do so. No payments are needed to be made for free software.
Question 15(iv)
Compare and Contrast: Freeware and Shareware
The term freeware is generally used for software, which is available free of cost and which allows copying and further distribution, but not modification and whose source code is not available. The right to use the software is limited to certain types of users for instance, for private and non-commercial purposes.
Shareware is a software which is made available with the right to redistribute copies, but it is stipulated that if one intends to use the software, often after a certain period of time then a license fee should be paid. The source code of shareware is not available and modifications to the software are not allowed.
Question 15(v)
Compare and Contrast: Freeware and Free software.
What is public domain software ?
Public-domain software is free and can be used without restrictions. It is, by its very nature, outside the scope of copyright and licensing.
Name some common public domain software licenses.
Some open source licenses are Creative Commons License, General Public License and Apache License.
What is GPL software license ? How is it different from LGPL software license ?
General Public Licence (GPL) grants and guarantees a wide range of rights to developers who work on open-source projects. With GPL, users can do the following:
- Copy the software as many times as needed.
- Distribute the software in any way
- Charge a fee to distribute the software after modifying it but the software should still be under GNU GPL.
- Make any type of modifications to the software
The LGPL and GPL licenses differ with one major exception. With LGPL the requirement that you have to release software extensions in open GPL has been removed.
What is freedom of information ?
Freedom of information refers to the right to access information available on public platforms.
What are the major factors behind digital divide ?
The major factors behind digital divide are:
- Technology reach — Technological reach is not the same all across India, especially in rural and remote areas.
- Digital Literacy — The rate of digital literacy is far less in rural areas as compared to urban areas. People in remote areas and rural areas are picking up with digital literacy, now.
Write any one application each of e-Governance and e-commerce.
An application of e-Governance is filing of online application forms for Aadhaar card, passport, etc.
An application of e-commerce is that we can do online shopping.
Application Oriented Questions
Kuhu has just learnt how to do online banking. Name any two precautions that she should take to prevent online fraud.
Two precautions that Kuhu should take to prevent online fraud are:
- She should not share her user id and password with anyone.
- She should avoid doing transactions from cyber cafe and other public places.
Companies spend a lot on secure data transmission that requires enough technical safeguards.
(a) What do you understand by secure data transmission ?
(b) Why do you think companies spend so much on secure data transmission ?
(c) What are common technical safeguards that are applied to ensure secure data transmission ?
(a) Secure data transmission means applying enough technical safeguards so that data travels safely to its target, without being compromised or eavesdropped.
(b) Companies spend heavily on secure data transmission due to the following reasons:
- Protection of sensitive information such as customer information, trade secrets, financial records, or intellectual property.
- Many industries have stringent regulatory requirements regarding data protection and privacy. They invest in secure data transmission to comply with these regulations and avoid penalties.
- Companies demonstrate their commitment to protecting customer data and maintaining trust.
- Implementing secure data transmission helps mitigate potential financial implications.
(c) To ensure secure data transmission, following techniques are applied :
- SSL secure data transmission — SSL (Secure Sockets Layer) is a standard security protocol which ensures data security by establishing encrypted online links between a web server and a browser. It encrypts the transmitted data and keeps it secure.
- Use Safe protocols — Use safe FTP protocol for files wherever possible, as safe protocols use some safety shells such as SSH.
These days it is equally important to safeguard digital properties:
(a) What are digital properties?
(b) Why is above given statement/fact important?
(c) What are possible threats to digital properties?
(d) How can digital properties be safeguarded?
(a) Digital property (or digital assets) refers to any information about us or created by us that exists in digital form, either online or on an electronic storage device.
(b) Digital property rights lie with the owner. Legally a person who has created it or the owner who has got it developed by paying legally is the legal owner of a digital property. Only the owner can use and decide who all and in what form can his/her digital asset may be used by others, whether by making payments or by buying it or by obtaining its license or usage rights etc. Thus, it is important to safeguard digital properties.
(c) The common threats to digital properties are as follows:
(d) The following are the ways to ensure protection of digital properties:
Freedom of information refers to right to access information available on public platforms.
(a) What are the problems that are a hinderance in freedom of information for all?
(b) What are the ways to ensure freedom of information for all?
(a) There are several problems that hinder freedom of information for all:
- Language and literacy barriers — Limited availability of information in different languages or low literacy rates can hinder individuals from accessing and understanding relevant information.
(b) To ensure freedom of information for all, the following approaches can be taken:
- Legal safeguards — Enact and uphold laws that protect freedom of information.
- Open data initiatives — Governments and institutions can proactively make information available to the public through open data initiatives, ensuring transparency and accessibility.
- Strengthening digital infrastructure — Bridge the digital divide by expanding internet access, providing affordable connectivity, and promoting digital literacy programs.
- Fact-checking and media literacy — Promote media literacy and critical thinking skills to help individuals identify and evaluate reliable sources of information.
- International cooperation — Encourage collaboration between countries and organizations to promote freedom of information.

- Get IGI Global News

- All Products
- Book Chapters
- Journal Articles
- Video Lessons
- Teaching Cases
- Recommend to Librarian
- Recommend to Colleague
- Fair Use Policy

- Access on Platform
Export Reference

- e-Book Collection Select

CyberEthics Case Study
Literature review.
“Ethical consideration now is generally declared to be indispensable in shaping technology in a socially acceptable and sustainable way” (Grunwald, 2000, p.181). The word ethics comes from the ancient Greek word eche which means character and is thus best defined by a set of theories that are based on certain rules and principles helping people distinguish right from wrong (Kizza, 2011). Consequently, cyber ethics is based on the code that gives guidelines for the proper behaviour on the Internet, for the good to be achieved on both an individual and societal basis (Bawa & Marwah, 2011). Similarly, Baird et. al., (2000, p.10), defined cyber ethics as the: “exploration of the entire range of the ethical and moral issues that arise in the cyberspace”. As cyberspace becomes broader and more popular, its meaning increases in importance.
Complete Chapter List
CBSE Python
CS-IT-IP-AI and Data Science Notes, QNA for Class 9 to 12
Society Laws and Ethics Assertion Reasoning Case Study Questions
1. Which of the following are the best security measures that should be taken against phishing attacks ?
a) Never open unknown or suspicious email attachments.
b) Never share your personal information such as email, credit card number, etc on unknown sites.
c) Both a and b
d) None of these
2. When a person is harassed repeatedly by being followed, called or be written to he/ she is a target of
a) Bullying
b) Stalking
c) identity theft
d) phishing
3. IT Act of the Indian Parliament notified on ___________
a) 17 January 2001
b) 25 October 2002
c) 17 October 2000
d) 25 April 2000
4. What is the name of the IT Law that India is having in the Indian legislature ?
a) India’s Technology (IT) Act, 2000
b) India’s Digital Information Technology (DIT) Act, 2000
c) India’s Information Technology (IT) Act, 2000
d) The Technology Act, 2008
5. Sarah’s classmate sent her a message on Facebook “You are a Loser”. Sarah is a victim of:
a) Phishing
b) Eavesdropping
c) Cyberbullying
d) Trolling
6. What can happen when you give your personal data (email, address, photos you post…) in exchange for free apps and services?
a) Nothing can happen. Your data is not allowed to be passed on to anyone
b) It isn’t really used, it’s just compulsory to ask for that information
c) When giving your email you’re automatically entered in a lottery where you can win something
d) Everything you do online is of value and is used by companies looking to target their advertising
Assertion Reason Based Questions.
1. Assertion (A) : The information which was posted by you in online can be seen by everyone who is online because internet is the world’s biggest information exchange tool.
Reason (R) : Don’t give or post any personal information like your name, address of the school/office / home, phone numbers, age, sex, credit card details etc.,
Choose the correct answer:
a) Both A and R are true and R is correct explanation of A
b) Both A and R are true and R is not correct explanation of A
c) A is true but R is false.
d) A is false but R is True
2. Assertion (A): According to research conducted by Symantec, nearly 8 out of 10 individuals are subject to the different types of cyber bullying in India.
3. Assertion (A): The digital footprint is created automatically when you work on internet and providing data in any form.
Reason (R) : The active digital footprint is created unintentionally without the user’s consents.
True and False Question
1. Cyberbullying is the act of intimidating, harassment, defaming, or any other form of mental degradation through the use of electronic means or modes such as social media.
Ans: (a) True
2. Rohan said some abusive words for Shyam in the class. This a type of cyber bullying.
Ans: (b) False
3. It is okay to post some negative comments about someone to defame him/ her.
4. It is a better way to dispose off the e-waste in an open field area.
5. Cyber law helps protect users from harm by enabling the investigation and prosecution of online criminal activity.
Case study based questions
1. Smridh has recently changed his school so he is not aware of the people, but someone is posting negative ,demeaning comments on his social media profile. He is also getting repeated mails from unknown people. Everytime he goes online, he finds someone chasing him online.
i) Smridh is a victim of …………. :
a) Eavesdropping
b) Stolen identity
c) Phishing
d) Cyber stalking
ii) The action that Smridh should take :
a) He should ONLY share with his friends
b) He should NOT share with anyone as it can cause serious problem
c) He should immediately report to the police
d) He should bring to the notice of his parents and school authorities.
iii) …………………….. is a set of moral principles that governs the behaviour of a group or individual and regulates the use of computers.
a) Copyright
b) Computer ethics
c) Property rights
d) Privacy law
2. After practicals, Atharv left the computer laboratory but forgot to sign off from his email account. Later, his classmate Revaan started using the same computer. He is now logged in as Atharv. He sends inflammatory email messages to few of his classmates using Atharv’s email account.
i) Revaan’s activity is an example of which of the following cyber crime?
b) Identity theft
c) Cyber bullying
d) Plagiarism
ii) If you post something mean about someone, you can just delete it and everything will be Ok .
iii) Anonymous online posts/comments can _________ be traced back to the author.
c) Sometimes
d) Many Times
Related Post
Class 12 computer science board question paper 2024 with answer key, python function arguments and parameters notes class 12 (positional, keyword, default), class 12 computer science notes topic wise.

IMAGES
VIDEO
COMMENTS
a case-study based ethics curriculum to engage students in open dialogue and debate within a community of eth-ical practice. Being proactive is important in order to make any system more secure and in the realm of cy-bersecurity ethics, we are concerned with the system of people (i.e. cybersecurity professionals) who are situ-
Markkula Center for Applied Ethics. Focus Areas. Internet Ethics. Internet Ethics Cases. Find ethics case studies on topics in Internet ethics including privacy, hacking, social media, the right to be forgotten, and hashtag activism. (For permission to reprint articles, submit requests to [email protected] .)
A recent article in Wired magazine details the anticipated re-release of a tool called PunkSpider. While constantly scanning the web, PunkSpider "automatically identifies hackable vulnerabilities in websites, and then allows anyone to search those results"—by URL keywords, or type or severity of vulnerability.
Their original use is for an undergraduate course on ethics, public policy, and technology, and they have been designed to prompt discussion about issues at the intersection of those fields. These works are licensed under a Creative Commons Attribution 4.0 International License. Case Studies. Algorithmic Decision-Making and Accountability
the ethical textbook by Manjikian [39] is a prominent example. The second category aims to outline a series of mid-level and domain-specific principles, an approach known as "principlism". In both categories, Formosa et al. [25] note that casuistry (an applied ethics approach that uses case-based reasoning to derive ethical insights) is ...
Urgent discussion regarding the ethics of cybersecurity research is needed. This paper critiques existing governance in cyber-security ethics through providing an overview of some of the ethical issues facing researchers in the cybersecurity community and highlighting shortfalls in governance practice. We separate these issues into those facing ...
The principles of cyber ethics listed on the following slide have been adapted and adopted by CyberTaipan as the ethical guidelines for competition. These principles recognise that as part of CyberTaipan, you may be given access to tools and skills that others are not given. This responsibility carries with it increased ethical weight and these ...
This case study-based ethics curriculum immerses students in real-life ethical dilemmas within cybersecurity and engages in open dialogue and debate within a community of ethical practice. We uphold the importance of preparing students for a future that is truly unknown and uncertain and note that this requires a push beyond some established ...
In the remaining sections of this module, you will have the opportunity to learn more about: Part 1: Important ethical issues in cybersecurity. ontexts Part 5: Ethical 'best practices' for cybersecurity professionalsIn each section of the module, you will be asked to fill in answers to specific questions and/or e.
View PDF. A Case Study-based Cybersecurity Ethics Curriculum Jane Blanken-Webb, Imani Palmer, Sarah-Elizabeth Deshaies Nicholas C. Burbules, Roy H. Campbell, Masooda Bashir University of Illinois at Urbana-Champaign Abstract This paper describes the rationale for and implementation of an experimental graduate-level cybersecurity ethics course ...
In the ever-evolving landscape of cybersecurity, the battle between hackers and defenders continues to shape the digital domain. To understand the gravity of cybersecurity challenges, one need only examine real-world examples—breaches that have rocked industries, compromised sensitive data, and left organizations scrambling to shore up their ...
The study develops conceptual and predictive models to test a set of hypotheses. The results show consequential ethics as the most significant predictor of computer ethics, cyber privacy, and academic integrity. Deontological ethics most significantly predict intellectual property rights but is not a significant predictor of academic integrity.
Cyber Harassment. After a student defames a middle school teacher on social media, the teacher confronts the student in class and posts a video of the confrontation online. In many ways, social media platforms have created great benefits for our societies by expanding and diversifying the ways people communicate with each other, and yet these ...
The chapter is based on a case study and examines the existing literature review in correlation to the existing practices of the Cyprus Safer Internet Center operating in Cyprus - CyberEthics. ... This chapter analyses the role of cyber ethics and other related issues such as electronic commerce (e-commerce) and customers' protection, privacy ...
Introduction of Cyber Ethics: Short Answer Type Questions in English is available as part of our Computer Application: Class 10 for Class 10 & Cyber Ethics: Short Answer Type Questions in Hindi for Computer Application: Class 10 course. Download more important topics related with notes, lectures and mock test series for Class 10 Exam by signing ...
On April 17, I was one of three facilitators of a Learning Lab as part of the RSA conference in San Francisco —joining Sean Brooks of the Center for Long-term Cybersecurity at U.C. Berkley and Jeff Klaben of SRI International. The Learning Lab discussed a number of ethical dilemmas in cybersecurity and introduced ways to address those dilemmas.
A Case Study-based Cybersecurity Ethics Curriculum. Jane Blanken-W ebb, Imani Palmer, Sarah-Elizabeth Deshaies. Nicholas C. Burbules, Roy H. Campbell, Masooda Bashir. University of Illinois at ...
CyberEthics Case Study: 10.4018/978-1-4666-5880-6.ch004: This chapter analyses the role of cyber ethics and other related issues such as electronic commerce (e-commerce) and customers' protection, privacy ... Consequently, cyber ethics is based on the code that gives guidelines for the proper behaviour on the Internet, for the good to be ...
A Case Study-based Cybersecurity Ethics Curriculum ... we maintain that cyber-security ethics now merits its own curricular focus in ... sis that raise substantial ethical questions [14, 28, 31]. ...
Reason — Cyber bullying refers to an act of bullying on internet. Bullying a classmate in the school corridor doesn't involve internet. Hence, it cannot be considered as cyber bullying. The other three acts involve the use of internet for bullying. Hence, they come under cyber bullying. Question 16
CyberEthics Case Study: 10.4018/978-1-4666-6433-3.ch036: This chapter analyses the role of cyber ethics and other related issues such as electronic commerce (e-commerce) and customers' protection, privacy ... Consequently, cyber ethics is based on the code that gives guidelines for the proper behaviour on the Internet, for the good to be ...
5. Cyber law helps protect users from harm by enabling the investigation and prosecution of online criminal activity. a) True. b) False. Ans: (a) True . Case study based questions. 1. Smridh has recently changed his school so he is not aware of the people, but someone is posting negative ,demeaning comments on his social media profile.