Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.

OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
Sase specific application service element, layer 7 application layer, layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
What is OSI Model? – Layers of OSI Model
The OSI (Open Systems Interconnection) Model is a set of rules that explains how different computer systems communicate over a network. OSI Model was developed by the International Organization for Standardization (ISO) . The OSI Model consists of 7 layers and each layer has specific functions and responsibilities.
This layered approach makes it easier for different devices and technologies to work together. OSI Model provides a clear structure for data transmission and managing network issues. The OSI Model is widely used as a reference to understand how network systems function.
In this article, we will discuss the OSI Model and each layer of the OSI Model in detail. We will also discuss the flow of data in the OSI Model and how the OSI Model is different from the TCP/IP Model.
For those preparing for competitive exams like GATE, a strong understanding of networking concepts, including the OSI model, is crucial. To deepen your knowledge in this area and other key computer science topics, consider enrolling in the GATE CS Self-Paced course . This course offers comprehensive coverage of the syllabus, helping you build a solid foundation for your exam preparation.
Layers of the OSI Model
There are 7 layers in the OSI Model and each layer has its specific role in handling data. All the layers are mentioned below:
Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
Application Layer
Layer 1 – Physical Layer
The lowest layer of the OSI reference model is the Physical Layer . It is responsible for the actual physical connection between the devices. The physical layer contains information in the form of bits. Physical Layer is responsible for transmitting individual bits from one node to the next. When receiving data, this layer will get the signal received and convert it into 0s and 1s and send them to the Data Link layer, which will put the frame back together. Common physical layer devices are Hub , Repeater , Modem , and Cables .

Functions of the Physical Layer
- Bit Synchronization: The physical layer provides the synchronization of the bits by providing a clock. This clock controls both sender and receiver thus providing synchronization at the bit level.
- Bit Rate Control: The Physical layer also defines the transmission rate i.e. the number of bits sent per second.
- Physical Topologies: Physical layer specifies how the different, devices/nodes are arranged in a network i.e. bus topology , star topology , or mesh topology .
- Transmission Mode: Physical layer also defines how the data flows between the two connected devices. The various transmission modes possible are Simplex, half-duplex and full-duplex .
Layer 2 – Data Link Layer (DLL)
The data link layer is responsible for the node-to-node delivery of the message. The main function of this layer is to make sure data transfer is error-free from one node to another, over the physical layer. When a packet arrives in a network, it is the responsibility of the DLL to transmit it to the Host using its MAC address . Packet in the Data Link layer is referred to as Frame. Switches and Bridges are common Data Link Layer devices.
The Data Link Layer is divided into two sublayers:
- Logical Link Control (LLC)
- Media Access Control (MAC)
The packet received from the Network layer is further divided into frames depending on the frame size of the NIC(Network Interface Card) . DLL also encapsulates Sender and Receiver’s MAC address in the header.
The Receiver’s MAC address is obtained by placing an ARP(Address Resolution Protocol) request onto the wire asking “Who has that IP address?” and the destination host will reply with its MAC address.
Functions of the Data Link Layer
- Framing: Framing is a function of the data link layer. It provides a way for a sender to transmit a set of bits that are meaningful to the receiver. This can be accomplished by attaching special bit patterns to the beginning and end of the frame.
- Physical Addressing: After creating frames, the Data link layer adds physical addresses ( MAC addresses ) of the sender and/or receiver in the header of each frame.
- Error Control: The data link layer provides the mechanism of error control in which it detects and retransmits damaged or lost frames.
- Flow Control: The data rate must be constant on both sides else the data may get corrupted thus, flow control coordinates the amount of data that can be sent before receiving an acknowledgment.
- Access Control: When a single communication channel is shared by multiple devices, the MAC sub-layer of the data link layer helps to determine which device has control over the channel at a given time.
Layer 3 – Network Layer
The network layer works for the transmission of data from one host to the other located in different networks. It also takes care of packet routing i.e. selection of the shortest path to transmit the packet, from the number of routes available. The sender and receiver’s IP address are placed in the header by the network layer. Segment in the Network layer is referred to as Packet. Network layer is implemented by networking devices such as routers and switches .
Functions of the Network Layer
- Routing: The network layer protocols determine which route is suitable from source to destination. This function of the network layer is known as routing.
- Logical Addressing: To identify each device inter-network uniquely, the network layer defines an addressing scheme. The sender and receiver’s IP addresses are placed in the header by the network layer. Such an address distinguishes each device uniquely and universally.
Layer 4 – Transport Layer
The transport layer provides services to the application layer and takes services from the network layer. The data in the transport layer is referred to as Segments . It is responsible for the end-to-end delivery of the complete message. The transport layer also provides the acknowledgment of the successful data transmission and re-transmits the data if an error is found. Protocols used in Transport Layer are TCP , UDP NetBIOS , PPTP .
At the sender’s side , the transport layer receives the formatted data from the upper layers, performs Segmentation , and also implements Flow and error control to ensure proper data transmission. It also adds Source and Destination port number in its header and forwards the segmented data to the Network Layer.
- Generally, this destination port number is configured, either by default or manually. For example, when a web application requests a web server, it typically uses port number 80, because this is the default port assigned to web applications. Many applications have default ports assigned.
At the Receiver’s side, Transport Layer reads the port number from its header and forwards the Data which it has received to the respective application. It also performs sequencing and reassembling of the segmented data.
Functions of the Transport Layer
- Segmentation and Reassembly: This layer accepts the message from the (session) layer, and breaks the message into smaller units. Each of the segments produced has a header associated with it. The transport layer at the destination station reassembles the message.
- Service Point Addressing: To deliver the message to the correct process, the transport layer header includes a type of address called service point address or port address. Thus by specifying this address, the transport layer makes sure that the message is delivered to the correct process.
Services Provided by Transport Layer
- Connection-Oriented Service
- Connectionless Service
Layer 5 – Session Layer
Session Layer in the OSI Model is responsible for the establishment of connections, management of connections, terminations of sessions between two devices. It also provides authentication and security. Protocols used in the Session Layer are NetBIOS, PPTP.
Functions of the Session Layer
- Session Establishment, Maintenance, and Termination: The layer allows the two processes to establish, use, and terminate a connection.
- Synchronization: This layer allows a process to add checkpoints that are considered synchronization points in the data. These synchronization points help to identify the error so that the data is re-synchronized properly, and ends of the messages are not cut prematurely and data loss is avoided.
- Dialog Controller: The session layer allows two systems to start communication with each other in half-duplex or full-duplex.
Let us consider a scenario where a user wants to send a message through some Messenger application running in their browser. The “ Messenger ” here acts as the application layer which provides the user with an interface to create the data. This message or so-called Data is compressed, optionally encrypted (if the data is sensitive), and converted into bits (0’s and 1’s) so that it can be transmitted.

Communication in Session Layer

Layer 6 – Presentation Layer
The presentation layer is also called the Translation layer . The data from the application layer is extracted here and manipulated as per the required format to transmit over the network. Protocols used in the Presentation Layer are JPEG , MPEG , GIF , TLS/SSL , etc.
Functions of the Presentation Layer
- Translation: For example, ASCII to EBCDIC .
- Encryption/ Decryption: Data encryption translates the data into another form or code. The encrypted data is known as the ciphertext and the decrypted data is known as plain text. A key value is used for encrypting as well as decrypting data.
- Compression: Reduces the number of bits that need to be transmitted on the network.
Layer 7 – Application Layer
At the very top of the OSI Reference Model stack of layers, we find the Application layer which is implemented by the network applications. These applications produce the data to be transferred over the network. This layer also serves as a window for the application services to access the network and for displaying the received information to the user. Protocols used in the Application layer are SMTP , FTP , DNS , etc.
Functions of the Application Layer
The main functions of the application layer are given below.
- Network Virtual Terminal(NVT): It allows a user to log on to a remote host.
- File Transfer Access and Management(FTAM): This application allows a user to access files in a remote host, retrieve files in a remote host, and manage or control files from a remote computer.
- Mail Services: Provide email service.
- Directory Services: This application provides distributed database sources and access for global information about various objects and services.
How Data Flows in the OSI Model ?
When we transfer information from one device to another, it travels through 7 layers of OSI model. First data travels down through 7 layers from the sender’s end and then climbs back 7 layers on the receiver’s end.
Data flows through the OSI model in a step-by-step process:
- Application Layer: Applications create the data.
- Presentation Layer: Data is formatted and encrypted.
- Session Layer: Connections are established and managed.
- Transport Layer: Data is broken into segments for reliable delivery.
- Network Layer : Segments are packaged into packets and routed.
- Data Link Layer: Packets are framed and sent to the next device.
- Physical Layer: Frames are converted into bits and transmitted physically.
Each layer adds specific information to ensure the data reaches its destination correctly, and these steps are reversed upon arrival.
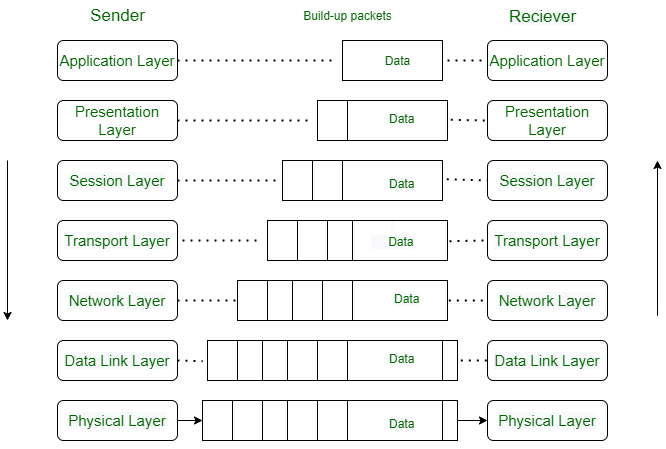
We can understand how data flows through OSI Model with the help of an example mentioned below.
Let us suppose, Person A sends an e-mail to his friend Person B .
Step 1: Person A interacts with e-mail application like Gmail , outlook , etc. Writes his email to send. (This happens at Application Layer ).
Step 2: At Presentation Layer, Mail application prepares for data transmission like encrypting data and formatting it for transmission.
Step 3: At Session Layer, There is a connection established between the sender and receiver on the internet.
Step 4: At Transport Layer , Email data is broken into smaller segments. It adds sequence number and error-checking information to maintain the reliability of the information.
Step 5: At Network Layer, Addressing of packets is done in order to find the best route for transfer.
Step 6: At Data Link Layer, d ata packets are encapsulated into frames, then MAC address is added for local devices and then it checks for error using error detection.
Step 7: At Physical Layer, Frames are transmitted in the form of electrical/ optical signals over a physical network medium like ethernet cable or WiFi.
After the email reaches the receiver i.e. Person B , the process will reverse and decrypt the e-mail content. At last, the email will be shown on Person B email client.
Protocols Used in the OSI Layers
Why does the osi model matter.
The OSI Model matters because it provides the user a clear structure of “how the data moves in the network?”. As the OSI Model consists of 7 layers, each layer has its specific role, and due to which it helps in understanding, identifying and solving the complex network problems easily by focusing on one of the layers not the entire network.
As the modern Internet does not prefer the OSI Model, but still, the OSI Model is still very helpful for solving network problems. It helps people understanding network concepts very easily.
Difference Between OSI and TCP/IP Model

OSI vs TCP/IP
Advantages of OSI Model
The OSI Model defines the communication of a computing system into 7 different layers. Its advantages include:
- It divides network communication into 7 layers which makes it easier to understand and troubleshoot.
- It standardizes network communications, as each layer has fixed functions and protocols.
- Diagnosing network problems is easier with the OSI model.
- It is easier to improve with advancements as each layer can get updates separately.
Disadvantages of OSI Model
- The OSI Model has seven layers, which can be complicated and hard to understand for beginners.
- In real-life networking, most systems use a simpler model called the Internet protocol suite (TCP/IP), so the OSI Model is not always directly applicable.
- Each layer in the OSI Model adds its own set of rules and operations, which can make the process more time-consuming and less efficient.
- The OSI Model is more of a theoretical framework, meaning it’s great for understanding concepts but not always practical for implementation.
In conclusion, the OSI (Open Systems Interconnection) model helps us understand how data moves in networks. It consists of seven distinct layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. Each layer has specific responsibilities and interacts with the layers directly above and below it. Since it is a conceptual model, but the OSI framework is still widely used to troubleshoot and understand networking issues.
Frequently Asked Questions on OSI Model – FAQs
Can osi layers work independently.
No, OSI layers do not work independently. Each layer depends on the services provided by the layer below it and, in turn, provides services to the layer above it. This layered approach ensures that data is transmitted smoothly from the source to the destination.
How does the OSI Model help in troubleshooting network issues?
By breaking down communication into layers, the OSI Model helps network administrators isolate problems more easily.
What happens if a layer in the OSI Model fails?
If a particular OSI layer fails, data transmission may be disrupted or fail entirely. Network administrator will check layer by layer to identify and resolve the issue, make sure that each layer is functioning correctly or not.
How does DNS fit into the OSI Model?
The Domain Name System (DNS) operates at Layer 7 (Application Layer). It translates domain names into IP addresses, facilitating communication between users and services across the network.
Similar Reads
Improve your coding skills with practice.
What kind of Experience do you want to share?
