- In the News
- Impact Videos and Stories
- Frequently Asked Questions
- Policies, Disclosures and Reports


Confidentiality in the Age of AIDS: A Case Study in Clinical Ethics
Print this case study here: Case Study – Confidentiality in the Age of AIDS
The Journal of Clinical Ethics, Fall 1993
Martin L Smith, STD, is an Associated in the Department of Bioethics, Cleveland Clinic Foundation, Cleveland, Ohio.
Kevin P Martin, MD is a Child and Adolescent Psychiatrist in the Department of Mental Health, Kaiser Permanente, Cleveland.
INTRODUCTION
AIDS (acquired immunodeficiency syndrome), now in pandemic proportions, presents formidable challenges to health-care professionals. The human immunodeficiency virus (HIV) infection and its related diseases have also raised a number of thorny ethical questions about government and social policy, health-care delivery systems, and the very nature of the physician-patient relationship. This article presents the case of an HIV-positive patient who presented the treating physician, a psychiatrist, with an ethical dilemma. We provide the details of the case, identify the ethical issues it raises, and examine the ethical principles involved. Finally, we present a case analysis that supports the physician’s decision. Our process of ethical analysis and decision making is a type of casuistry,1 which involves examining the circumstances and details of the case, considering analogous cases, determining which maxim(s) should rule the case and to what extent, and weighing accumulated arguments and considerations for the options that have been identified. The goal of this method is to arrive at a reasonable, prudent moral judgement leading to action.
The patient, Seth, is a 32-year-old, HIV-positive, gay, white male whose psychiatric social worker had referred him to a community-mental-health-center psychiatrist for evaluation. He had a history of paranoid schizophrenia that went back several years. He had been functioning well for the last two years as an outpatient on antipsychotic medications and was working full time, socializing actively, and sharing an apartment with a female roommate.
The social worker described a gradual deterioration over several months. Seth had become less compliant with his medication and with his appointments at the mental-health center, had lost his job, had been asked to leave his apartment, and was living on the streets. He was described as increasingly disorganized and paranoid. His behavior was increasingly inappropriate, and he had only limited insight into his condition.
On examination, Seth was thin, casually dressed, slightly disheveled, and with poor hygiene. His speech was spontaneous, not pressured, and loose with occasional blocking. [That is, he spoke spontaneously, he could be interrupted, and his speech was unfocused with occasional interruption of thought sequence.] His psychomotor activity was labile [unstable]. His affect was cheerful and inappropriately seductive, and he described his mood as ”mellow.” He denied having hallucinations, systematized delusions and suicidal or homicidal ideation. He admitted having ideas of reference [incorrect interpretation of casual incidents and external events as having direct reference to himself], was clearly paranoid, and at times appeared to be internally stimulated. He made statements such as: “They’re blaming me for everything,” and “I’m scared all the time,” although he was too guarded or disorganized to provide more detail. His cognitive functioning was impaired, and testing was difficult given his distracted, disorganized state. His judgement was significantly impaired, and his insight was quite limited.
At the time of the evaluation, Seth indiscriminately revealed his HIV-positive status to the staff and other patients. He claimed he had been HIV positive for five years, and he denied that he had developed any symptoms of disease or taken any HIV-related medications. He was not considered reliable, and the staff sought confirmation. After he provided the location and approximate date of his most recent HIV test, the physician confirmed that the patient had been HIV positive at least since the test, about a year earlier.
When asked, Seth stated that the was not currently in a relationship. He appeared to be disorganized and could not name his most recent sexual partner(s). He could not remember whether he had been practicing safer sex and whether he had informed his partners of his HIV positive status.
In addition to the information he obtained during the evaluation, the psychiatrist, by chance, had limited personal knowledge of the patient. Through his own involvement as a member of the local gay community, the psychiatrist had briefly met the patient twice – once while attending an open discussion at the lesbian-gay community center, and later, at a worship service in a predominantly lesbian-gay church. The physician recalled that Seth had seemed to be functioning quite adequately, at least superficially. He was somewhat indiscriminately flirtatious, his behavior was otherwise appropriate, and he did not appear to be psychotic or disorganized in his thinking. He was not overtly paranoid and did not publicly reveal his HIV-positive status.
Through the church, the psychiatrist had also become acquainted with Maxwell and Philip, who were partners in a primary sexual relationship. Before Seth’s decompensation [deterioration of existing defenses, leading to an exacerbation of pathologic behavior], but after he was known to have tested HIV positive, Seth and Maxwell had been lovers. Maxwell left Philip and moved in with Seth for about two months, but then left Seth and returned to Philip around the time of Seth’s decompensation.
The psychiatrist was not privy to details of Maxwell and Seth’s or Maxwell and Philip’s sexual practices. He did not know of the HIV status of Maxwell or Philip, or whether either had ever been tested. In addition, he was unaware of whether Maxwell or Philip know of Seth’s HIVpositive status at the time of Maxwell’s relationship with Seth, or at any time thereafter. During the evaluation, Seth did not recall having met the psychiatrist, nor did he mention his relationship with Maxwell.
Seth agreed to enter a crisis stabilization unit and to resume treatment with antipsychotic medications. Free to come and go at will during daylight hours, he left the unit on day two, failed to return, and was lost to follow-up. His mental status had not changed significantly before he left the crisis unit.
In this case, the physician’s duty to maintain physician-patient confidentiality conflicts with his duty as a psychiatrist to warn third parties at risk. Clearly, a patient’s status as HIV positive is a matter of confidentiality between doctor and patient. Just as clear is the risk for third parties to whom the patient may pass the virus via sexual intercourse. It is unknown whether everyone infected with HIV will develop AIDS, or how many months or years may intervene between infection and the appearance of full-blown AIDS. However, once AIDS develops it is always fatal.2 Therefore, there is a potentially lethal risk to a person having intercourse, particularly without employing safer sex-practices, with another infected with the HIV virus.
This ethical conflict raises two questions. Is it permissible to violate confidentiality to warn a third party at risk? Is there a duty to violate confidentiality to warn a third party at risk? The potential benefit to the third parties must be considered, as well as the strength of the principle of confidentiality in the patient-physician relationship. There is also wider societal consideration as to how breaches of confidentiality, even for good reasons, will affect voluntary testing and seeking of prophylactic treatment by HIV-positive persons. This societal consideration must be weighed against the benefit to the individual third party of knowing the risk and then choosing to be tested and treated and choosing to be tested and treated and choosing to take precautions against infecting others.
In this case, another issue arises from the fact that the physicians of at least one third party who may have been placed at risk possibly without his knowledge, was obtained through personal knowledge, outside the professional relationship. Is it appropriate to bring this information into the clinical setting, particularly because it is so central to the primary ethical issue? Does the physician have an obligation to act on this information?
Finally, two additional sets of issues complicate this case. First, the patient’s decompensation and disappearance necessitate the physician’s choosing a course of action without patient consent or cooperation, and with patient-supplied information that is incomplete and probably unreliable. Second, a breach of confidentiality could greatly damage the physician’s position as a psychiatrist and a trusted member of the gay community, offering assistance directly to some and referral to many others. Given these issues, what should the physician do?
BACKGROUND DISCUSSION
Some background information will be useful in analyzing the ethical issues of the case. This information includes basic ethical values and norms, and legal mandates and opinions about confidentiality, the duty to warn, and HIV/AIDS reporting.
Whether privacy is viewed as a derivative value from the principle of autonomy or as a fundamental universal need with its own nature and importance,3 privacy, and the associated issue of confidentiality, is generally accepted as essential to the relationship between physician and patient. The purpose of confidentiality is to prevent unauthorized persons from learning information shared in confidence.4 Stated more positively, confidentiality promotes the free flow of communication between doctor and patient, thereby encouraging patient disclosure, which in turn should lead to more accurate diagnosis, better patient education, and more effective treatment.
The Hippocratic Oath is evidence of the long-standing tradition of confidentiality in Western though: “What I may see or hear in the course of treatment… I will keep to myself, holding such things shameful to be spoken about.” More recently, the American Medical Association,6 the American Psychiatric Association,7 the American College of Physicians, and the Infectious Diseases Society of America8 have reaffirmed the right of privacy and confidentiality, specifically for HIV-positive patients. Without the informed consent of the patient, physicians should not disclose information about their patient. The Center for Disease Control also recommends that patient confidentiality be maintained, because the organization believes that a successful response to the HIV epidemic depend on research and on the voluntary cooperation of infected persons.9That is, the interests of society seem best served if the trust and cooperation of those at greatest risk can be obtained and maintained.10
Within the complexities of clinical care, should patient confidentiality be regarded as absolute, never to be breached under any circumstances (as claimed by the World Medical Association in its 1949 International Code of Medical Ethics11)? Or should confidentiality be regarded as a prima facie duty? (That is, should it be binding on all occasions unless it is in conflict with equal or higher duties?12)
Most commentators and codes conclude that patient confidentiality is not absolute and, therefore, it could – and even should – be overridden under come conditions.13 In other words, in a specific situation in which patient confidentiality is one value at stake, the health-care provider’s actual duty is determined by weighing the various competing prima facie duties and corresponding values, including confidentiality. (As might be expected, not all authors accept this conditional view of confidentiality and argue for its absolute quality.14) There is less unanimity about the circumstances under which patient confidentiality can be justifiably breached. More specifically for HIV-positive patients, the controversy revolves around the premise that some circumstances might create a duty to warn endangered third parties, even at the expense of confidentiality. The potential for harm to HIV-positive patients through breaches of confidentiality is great. Discrimination, isolation, hospitality, and stigmatization are all too real for these patients when their HIV-positive status has become known to others.15 Further, societal harm is possible if these patients – who might ordinarily seek medical attention voluntarily – refrain from doing so, knowing that professional breaches of confidentiality may ensue. Without ignoring this potential societal harm, the majority opinion of professional codes and of ethical and legal experts16 foresee the possibility of a duty to warn through discrete disclosure, especially if others are in clear and imminent danger if the patient cannot be persuaded to change hi behaviors or to notify those at risk of exposure.
Public health regulations often reflect the same conclusion – that confidentiality can be compromised under certain circumstances – and therefore mandate reporting HIV-positive and AIDS patients to public health authorities. Patient confidentiality is not to be upheld so strictly that it obviates an ethically justified (and usually legally mandated) duty to report such cases to authorized health agencies. Those who support such public policies view society’s right to promote its health and safety, and the need for accurate epidemiological information, to be at least as important as an individual’s right to privacy and confidentiality.
In trying to balance patient confidentiality with other professional values, the California Supreme Court decision in Tarasoff v. Regents of the University of California17 has become a guideline for other courts and health-care professionals (although technically this decision applies to only one state and specifically addresses a unique set of circumstances). In this famous and controversial case heard before the California Supreme Court in 1976, the majority opinion held that the duty of confidentiality in psychotherapy is outweighed by the duty to protect an intended victim from a serious danger of violence. The court explained the legal obligation to protect and the potential duty to warn as follows:
When a therapist determines, or pursuant to the standards of his profession should determine that his patient presents a serious danger of violence to another, he incurs an obligation to use reasonable care to protect the intended victim against such danger. The discharge of this duty may require the therapist to take one or more various steps, depending upon the nature of the case. Thus, it may call for him to warn the intended victim or others likely to apprise the victim of the danger, to notify the police, or to take whatever steps are reasonably necessary under the circumstances.18
Regarding the limits placed on confidentiality under these conditions, the court stated: “The protective privilege ends where the public peril begins.” This “Tarasoff Tightrope” identifies for the professional the dual duties of promoting the well-being and interests of the patient and protecting public and private safety.
Given the general jurisdictional autonomy of each state, the duty to protect and the potential duty to warn as adopted in California has been applied differently in different states.20 Although most commentators assume that Tarasoff is relevant for sorting out the issue of confidentiality relative to HIV-positive patients, this assumption is not universally accepted.21
Without a state statute or court case that specifically addresses the tension between patient confidentiality and the right of others to know whether they may have been exposed to HIV infection, and given the conundrum of legal principles relating to AIDS confidentiality, it is unclear as to who must be warned and under what circumstances.22 This lack of clarity is in indication that, in practice, the professional duty to warn is not absolute but always conditioned by the circumstances of the case (that is, the duty to warn is a prima facie value).
The above paragraphs describe an emerging consensus among health-care professionals who face confidentiality dilemmas, although universal agreement has not been fully achieved. Further, this emerging consensus and its contributing principles by no means provide easy answers to ethical quandaries. Each case, with its own specific set of relevant circumstances, must be analyzed and judged individually. Such an analysis of the presented case now follows.
AN ANALYSIS
Seth’s case, perceived as a dilemma by the psychiatrist, could be brushed aside easily if the information obtained outside the therapeutic relationship was simply ignored. But the lethality of HIV infection makes it difficult to dismiss the information either as irrelevant or inadmissible for serious consideration. Had the information been obtained by unethical means (for example, by coercion or deception), a stronger justification for not using the information might be made. Such is not the situation. Without reason to ignore this information, the psychiatrist must incorporate this “data of happenstance” into his decision. To do so, of course, places him precisely at the crossroads of the dilemma: to uphold confidentiality, to warn the third party, or to create an option that supports the values behind these apparently conflicting duties.
Several factors ethically support both a breach of confidentiality and the physician’s duty to warn and protect the third party: the emerging professional consensus that confidentiality is not absolute; the known identity of a third party who stands in harm’s way; the risk to unknown and unidentified sexual partners of the third party; and the deadliness of AIDS. Such a combination of factors is what the professional statements noted above23 have tried to address in their allowance for limits to patient confidentiality. In this case, the risk to the known third party has already been established, but other people may be at risk, including sexual partners of the patient and those of the third party. Individuals infected and unaware will not benefit from prophylactic therapies.
An additional reason for the psychiatrist to warn the third part is the patient’s mental status, which probably renders him incapable of informing his sexual partner(s) or of consenting to the physician’s informing them. On admission, he was not able to name his partner(s), and he was lost to follow-up without significant change in his mental status. Without the decision-making capacity of the likelihood of action on the part of the patient, any warning to the third party would have to come from the physician or through public health officials notified by the physician.
But the duty to warn, incidental information, and mental status are not the only factors that need to be considered here. Patients are subject to the risks of discrimination when their HIV status is disclosed. But for a patient who has indiscriminately revealed his own HIV-positive status, the physician’s contribution to this risk of discrimination through discreet disclosure to one person may be minimal.
Also, to be considered is the societal risk that testing and prophylactic treatment of HIV-positive persons will decrease if confidentiality is not upheld. Members of the lesbian and gay community are often mistrusting of medical and mental health professionals,24 perhaps with valid reason. Mistrust, fear, and nonparticipation in voluntary programs may increase if confidentiality cannot be assured. Persons will be less likely to come forward voluntarily for education, testing, or other assistance if their well-being is threatened as a result. In Tarasoff, the court declared that protective privilege ends where social peril begins. In this case, overriding the protective privilege of the individual could lead to greater societal peril. Trust in this physician by members of the lesbian and gay community benefits individuals and the community as a whole, by improving access to medical and mental health services. A breach of confidentiality, if it became known, could damage this trust, as well as the physician’s reputation, reducing his professional contributions to the community. This professional loss would be significant.
Also, to be considered is the general knowledge of the higher risk among gay and bisexual men for HIV infection, as well as the information in the gay community as to what constitutes high risk behavior and what precautions can decrease risk of infection. Thus, we can reasonably assume that a gay or bisexual male is already aware of his risk and that of his sexual partner(s) for carrying the HIV virus. Warning a probably knowledgeable third party about the HIV-positive status may be of little benefit to the third party, while it risks the greater individual, societal, and professional harms discussed above. Regarding the risk to unknown sexual partners of the patient, whatever their number, the physician is powerless to change their fate precisely because they are unknown to him.
The duty to maintain patient confidentiality and the duty to warn third parties at risk can both be viewed as prima facie duties. In clinical situations such as the one described here, when one duty must be weighed against another to arrive at an ethically supportable solution, the weighing should take place only in the context of the given case. In this case, we found no solution that upholds all the duties; thus, a choice must be made between the two duties.
We submit that, although there is support for the physician to warn the third party, there is greater support for upholding confidentiality in this case. The individual risk of discriminatory harm from disclosure is possible, although admittedly small. Further, it is reasonable to presume the third party’s awareness of his risk and of the risk to his sexual partner(s) of carrying the HIV virus, and thus, his awareness of the need for appropriate precautions.
Even more persuasive is the peril to the local gay community and the wider society if a breach of confidentiality increases mistrust of the healthcare system and decreases the effectiveness of this particular psychiatrist to provide quality professional care. In this case, the confidentiality of the physician-patient relationship should be maintained.
What has been presented here can serve as a model for ethical decision making within the complexities of clinical care. As cases and their accompanying ethical questions arise, the details of each case should be gathered. Any tendency to label the case prematurely as a particular type (for example, a duty-to-warn case) should be resisted. Such a label can divert attention from relevant details that make each case unique. In examining the facts of the case and judging their significance, the values and duties at stake can be identified. If necessary and practical, background material and analogous cases should be researched. Ethical dilemmas present persons with hard choices. While several solutions may have some ethical support, few can be labeled as perfect solutions. Often, choosing one solution over another leaves behind an ethically significant value and regrettably may even produce harm. The circumstances described here presented the psychiatrist with a hard choice and no easy answer. We have suggested an ethically supported solution, but we found no perfect solution for the dilemma.
1. A.R. Jonsen, “Casuistry as Methodology in Clinical Ethics,” Theoretical Medicine 12 (1991): 295-307. 2. J.W. Curran, H.W. Jaffee, A.M. Hardy, et al., “Epidemiology of HIV Infection and AIDS in the United States,” Science 239 (1988): 610-16. 3. T.L. Beauchamp and J.F. Childress, Principles of Biomedical Ethics (New York: Oxford University Press, 1983). 4. W.J. Winslade, “Confidentiality,” in Encyclopedia of Bioethics, ed. W.T. Reich (New York: Free Press, 1978). 5. L. Walters, “Ethical Aspects of Medical Confidentiality,” in Contemporary Issues in Bioethics,3rd edition, ed. T.L. Beauchamp and L. Walters (Belmont, Calif.: Wadsworth, 1989). 6. Council on Ethical and Judicial Affairs of the American Medical Association, “Ethical Issues Involved in the Growing AIDS Crisis,” Journal of the American Medical Association 259 (1988): 1360-61. 7. American Psychiatry Association, “AIDS Policy: Confidentiality and Disclosure,” American Journal of Psychiatry 145 (1988): 541-42. 8. Health and Public Policy Committee of the American College of Physicians, and lnfectious Diseases Society of America, “A quired Immunodeficiency Syndrome,” Annals of Internal Medicine 104 (1986): 575-81. 9. Centers for Disease Control, “Additional Recommendations to Reduce Sexual and Drug-Related Transmission of Human T-Lymphotropic Virus Type I I1/L y mph adenopathy-Associated Virus,” Morbidity and Mortality Weekly Report 35 (1986a): 152-55. 10. R. Gillan, “AIDS and Medical Confidentiality,” in Contemporary lssues in Bioethics. Code of Ethics, 1949 World Medical Association,” in Encyclopedia of Bioethics. 11. W.O. Ross, The Foundations of Ethics (Oxford, England: Clarendon Press, 1939). 12. Beauchamp and Childress, Principles of Biomedical Ethics; Winslade, “Confidentiality”; Walters, “Ethical Aspects of Medical Confidentiality”; AMA, “Report on Ethical Issues”; APA, “AIDS Policy”; American College of Physicians and Infectious Diseases Society of America, “Acquired Immunodeficiency Syndrome”; S. Bok, “The Limits of Confidentiality,” Hastings Center Re port 13 (February 1983): 24- 31; H.E. Emson, “Confidentiality: A Modified Value,” Journal of Medical Ethics 14 (1988): 87-90. 13. M.H. Kottow, “Medical Confidentiality: An Intransigent and Absolute Obligation,” Journal of Medical Ethics 12 (1986):117-22. 14. R.J. Blendon and K. Donelan, “Discrimination against People with AIDS,” New England Journal of Medicine 319 (1988): 1022-26; L.O. Gostin, “The AIDS Litigation Project: A National Review of Court and Human Rights Commission Decisions, Part II: Dis crimination,” Journal of American Medical Association 263 (1990): 2086-93. 15. G.J. Annas, “Medicolegal Di lemma: The HIV-Positive Patient Who Won’t Tell the Spouse,” Medical Aspects of Human Sexuality 21 (1987):16; T.A. Brennan, “AIDS and the Limits of Confidentiality: The Physician’s Duty to Warn. Contacts of Seropositive Individuals,” Journal of General Internal Medicine 4 (1989): 242-46: B.M. Dickens, “Legal Limits of AIDS, Confidentiality,” Journal of the American Medical Assoclarion 259 (1988):3449-?1; S.L. Lentz. ”Confidentiality and lnformed Consent and the Acquired Immunodeficiency. Syndro111e. Epidemic,” . Archives of Pathology, & Laboratory Medicine 114 (1990):304 8; D. Seiden, “HIV ·Seropositive Patients and Confidentiality,” Clinical Ethics Report (1987): 1-8H.Zomina, “Warning Third 16. Tarasoff v. Regents of the University of California, 11Cat.3d 425,551 P 2d ht (1,976) 17. Ibid. 18. R.D. Mackay, “Dangerous. Patients: Third Party Safety and Psychiatrists’ Duties: Walking the Tarasoff Tightrope,” Medicine, Science & the Law 3Q (1990): 52-56, 19. LA. Gray and A.R. Harding, “Confidentiality Limits with Clients Who Have the AIDS Virus,” Journal of Counseling and Development 6 (1988):219-23. 20. S. Perry, “Warning Third ‘Parties at Risk of AIDS: APA’s Policy is a Barrier to Treatment,” Hospital and Community Psychiatry 40 {1989):’ i5.8-6I. 21. L.O Gostin, The AIDS Litigation Project: A National Review of Court and Human Rights Commission Decisions. Part 1: The Social Impact of AIDS,” Journal of the American Medical Association 263 (1990), ‘961-7Q 22. AMA; “Report on Ethical Issues”; APA, “AIDS Policy”; American College of Physics and Infectious Diseases Society of America” Acquired lmmunodeficiency Syndrome.” 23. L. Dardick and KE Grady, “Openness between·:Gay Persons and Health Professionals,” Annals of Internal Medicine 93 -(1 80): 115-.19; T.A. DeCrescenzo, Homophobia: A Study of the Attitudes of Mental Health Professionals toward Homosexuality. Journal of Social Work and Homosexuality 2 (198):.84): 115-36.
Print this case study here: Case Study – Gathering Information and Casuistic Analysis
Gathering Information and Casuistic Analysis
Journal of Clinical Ethics By Athena Beldecos and Robert M. Arnold
Athena Beldecos is a graduate student in medical ethics in the Department of History and Philosophy of Science, University of Pittsburgh.
Robert M. Arnold, MD is an Assistant Professor of Medicine, and the Associate Director for Education, Center for Medical Ethics, University of Pittsburgh.
In their article, “Confidentiality in the Age of AIDS,” Martin L. Smith and Kevin P. Martin present a complex case in clinical ethics. Their analysis examines a physician’s quandary when treating a mentally incompetent HIV-positive patient: whether to uphold physician-patient confidentiality or to violate this confidentiality by warning a third party. Out critique focuses on the way the problem is conceptualized and the analytic methods used to resolve the case, rather than on the solution itself. We believe that several problems in the authors’ analysis arise from a misinterpretation of the casuistic method. Furthermore, we argue that Smith and Martin present a case that is insufficiently detailed, thereby precluding the identification of all of the moral problems in the case and the development of creature solutions to the problem(s) identified. We note several reasons why there is a need to gather more information prior to determining the appropriate ethical response. Finally, we suggest ways in which similar problems in clinical ethics might be avoided in the future.
IS THIS CASUISTRY?
The authors conceive of their “process of ethical analysis and decision making” as a “type of casuistry.” Although we agree that casuistry, as outlined by A.R. Josen,1 is a potentially fruitful technique for practical ethical decision making, we believe that certain essential features of such casuistic reasoning are not clearly present in Smith and Martin’s analysis.
The power and scope of casuistry are derived not only from attention to details and careful identification of circumstances in the presentation of individual cases, but – more importantly – from the process of case comparison. Using this method, a case under moral consideration is situated in a family of related cases, whereby the casuist examines the similarities and differences between the cases at hand. The context of an individual case and how its conflicting maxims appear within that particular context are the raw materials of the case-comparison method. The relative weight of conflicting maxims in an individual case is ascertained by comparison to analogous cases. With casuistry, moral judgement does not involve a more traditional retreat to the weighing of conflicting duties or general principles. Rather, moral guidance is provided by an ever-growing body of paradigm cases that represent unambiguous instances in which moral consensus is easily obtained. It is crucial that the casuist place the case under consideration in its proper taxonomic context(s) and that she or he identify the most appropriate paradigm, whether it be real or hypothetical.
The authors do identify a paradigm case, but their analysis departs from casuistry on several interrelated points. The authors do not proceed by analogical reasoning. Had they done so, they might have discovered that their chosen paradigm is inappropriate, due to significant dissimilarities with Seth’s case. Finally, their insufficiently detailed case precludes a thorough measurement of the similarities and differences between the cases at hand. For it is in the details that an individual case may differ from a paradigm case.
The authors’ analytic method has more in common with principle-based ethics2 than casuistry. They do not use a variety of similarly situated cases to point out and balance the relevant moral maxims instead, they extract the conflicting duties and principles from their paradigm, the Tarasoff case,3 and apply them directly to Seth’s case. The authors weigh one prima facie duty “against another to arrive at an ethically supportable solution.” Furthermore, the weighing takes place “only in the context of the given case.” Thus, case comparison, an intrinsic element of casuistry, is not performed. Instead, the authors’ major goal seems to be finding and applying a sufficiently modified principle regarding confidentiality to resolve the case at hand.
WHY TARASOFF IS PROBLEMATIC AS A PARADIGM CASE
By using Tarasoff as a paradigm case in their analysis, Smith and Martin situate their case in the family of “duty-to-warn” (prevention-of-harm) cases. It is reasonable that they identify this particular taxonomy as a starting point for their analysis. However, they do not test the appropriateness of the paradigm by systematically comparing and contrasting it with Seth’s case. The authors note the uniqueness of the circumstances of the Tarasoff case and its limited applicability but nonetheless proceed to use it as a paradigm. Casuistry, however, seeks closest-match paradigms. The use of analogical reasoning would have illuminated the similarities and differences between the two cases and would have helped the authors to determine which morally relevant features a paradigm case should minimally share with its analogous cases.
In the Tarasoff case, the court held that a psychotherapist, to whom a patient had confided a murderous intent, had a duty to protect the intended victim from harm.4 This duty includes warning the third party at risk, among other interventions. The unique circumstances of Tarasoff include the imminence of fatal harm to an identified, yet unsuspecting, individual. Although the authors are correct in noting the precedent-setting value of Tarasoff, the dissimilarities between Tarasoff and Seth’s case are so numerous as to suggest the selection of another paradigm.
First, a critical aspect in Tarasoff is the prevention of future fatal harm. Based on the circumstances of the case, there is no evidence of preventable fatal harm to Maxwell. For this condition to be satisfied, the psychiatrist would have to be assured of Maxwell’s seronegativity and have evidence of a current or an intended sexual relationship between Maxwell and Seth. The preventable harm to Maxwell consists of not allowing him the opportunity to institute early anti-viral therapy or to reconsider his life goals in the face of a fatal disease. A casuist would need to assess, using a series of cases, the moral difference between the fatal harm in Tarasoff and the lesser harms in the case of Seth.
Second, Tarasoff involves a person maliciously intending to harm another person. However, there is no evidence suggesting that Seth intended to harm Maxwell. Here, a casuist might begin the analysis using a paradigm case in which a physician is aware of his HIV-positive patient’s malicious intention to infect a third party from that point, one could progressively change the variables of the case to approach the degree of moral ambiguity and complexity shown in Seth’s case. This process would culminate in a case involving sexual relationship between a patient and his partner.
Third, the notion of harm with respect to HIV transmission is quite different from the harm to be prevented in Tarasoff . One might argue that fatal harm to others is averted by informing Maxwell of his risk for HIV positivity. He can subsequently alter his sexual practices and, thus, prevent the future spread of the virus. Herein lies the problem. In Tarasoff the person warned of the harm is also the person at risk of being harmed. In the case under discussion, however, warning Maxwell might prevent harm to other, yet unnamed individuals. A case analogous to Seth’s should describe a situation in which the possible harm has already occurred and the future harm to be avoided consists of preventing future transmission. An analogous case might involve issues of confidentiality in regard to the (vertical) transmission of a fatal genetic disease that manifests itself after sexual maturity. Imagine, for example, a young man afflicted with a severe and incurable genetic disease who has proceeded to start a family without disclosing his genetic status to his wife. Does his personal physician have a duty to uphold confidentiality in this case, or should he notify the spouse so that she can make informed reproductive decisions?
Fourth, in Tarasoff , the victim was presumably unaware of the intended harm. In Seth’s case, one can argue that Maxwell knows (or can be reasonably expected to know) the potential risk of having sexual relations with a homosexual. The authors mention this factor but do not provide a way to assess its importance. To test the importance of this morally relevant fact, a series of cases in which the third party is more (or less) responsible for knowing about the possibility of risk could be used for comparison. For example, how would our intuitions about physician disclosure in this case differ if Seth were a bisexual male who did not inform his wife of his unprotected extramarital affairs with gay and bisexual men?
Fifth, Seth was reported to have publicly announced his HIV-positive status, whereas the patient in Tarasoff disclosed his intent to kill within a protected doctor-patient relationship. Does the fact that “Seth indiscriminately revealed his HIV-positive status to the staff and other patients” at a community-mental-health-center make it easier for the psychiatrist to justify a violation of confidentiality in the name of protecting potential victims? Unfortunately, there is insufficient information to determine whether Seth’s public disclosure qualifies as a fair warning to potential victims and sanctions a violation of confidentiality. This point is potentially an important difference between Tarasoff and Seth’s case. The authors, however, would need to gather additional information concerning the circumstances of Seth’s public disclosures (when they began, to whom they were addressed, and so forth) before evaluating the weight of this morally relevant feature by comparison to a similar case.
Sixth, Tarasoff does not address the issue of how the duty to uphold confidentiality might be affected when a patient’s mental competence is in question. Seth’s case involves a mentally incompetent patient presumed to be “incapable of informing his sexual partner(s) [of his HIV positivity] or of consenting to the physician’s informing them.” The circumstances of this case raise the question: Does Seth’s physician have the same obligation to respect his patient’s confidences as he would have if Seth were a mentally competent adult patient? Central to this analysis is an understanding of how the underlying justifications for respecting the confidences of incompetent patients might differ from those of competent patients. Although the authors briefly discuss the implications of Seth’s impaired mental status, they could have profitably expanded their analysis of the ethical significance of a patient’s competency in regard to the physician’s duty to maintain confidentiality. The authors neglect to discuss, for example, how the selection of a surrogate to speak on Seth’s behalf might influence the case’s resolution.
Identifying which should be the determining factor(s) in deciding Seth’s case is a difficult moral problem. However, the first step is any casuistic analysis is to determine where the case fits in relation to other cases. Without this basic first step, it is too easy to neglect factors that may be critical in determining the proper course of action or to reply upon ad hoc, intuitive decisions.
THE NEED FOR A RICHLY DETAILED CASE
The casuistic method to which Smith and Martin supposedly subscribe, demands attention to the context of the particular case at hand, so that it may be compared to and contrasted with paradigm cases in which the ethical analysis is clear. A casuist needs sufficiently detailed information to be able to identify all of the moral issues and, thereby, situate an individual case in its appropriate taxonomy.
In Seth’s case, the authors seem to decide prematurely on the ethical issue, inappropriately hindering the search for future data. In the rush to identify and resolve the presumed ethical conflict, the ethicist may neglect to collect critical information.5 Without adequate information, the ethicist is unable to determine accurately what kind of case it is. While obtaining more information might be less interesting than theoretical analysis, often the most prudent course of action is to gather more information from the sources available in order to clarify and embellish the initial facts. Prior to leading the psychiatrist through a philosophical analysis of how to resolve the conflict between the duty to warn and the duty to uphold confidentiality, the authors should have urged the psychiatrist to obtain more information.
It is difficult, for example, to weigh the impact of Seth’s mental incompetency against the duty to maintain confidentiality because of a lack of sufficient information. Information regarding the severity of Seth’s mental illness and the chances of its reversibility would be useful in determining whether Seth should be viewed as only temporarily or permanently incompetent. If Seth is incompetent, it is not clear who should assess the harm done to Seth by a breach of confidentiality. We know too little about Seth’s life to determine who would most appropriately serve as his surrogate. Furthermore, it is not clear that violating Seth’s confidentiality would result in the social harms the authors forecast. In order to make this point, the authors would need to identify a case analogous to Seth’s, in which violating an incompetent person’s confidences is ill-advised because it might lead competent patients to mistrust or fear the health-care system.
In the previous section, we identified a variety of morally relevant factors in Seth’s case and suggested how they might affect one’s analysis. Determining the importance of the various factors in this case, however, requires the ethicist to obtain information concerning the following: the efficacy of antiviral treatment in HIV-positive persons, Seth and Maxwell’s sexual practices, the probability that Maxwell knows of Seth’s seropositivity, the degree to which Maxwell can reasonably be expected to know the risk of homosexual encounters, Seth’s previous comments regarding confidentiality, who is best situated to serve as Seth’s surrogate, and the degree to which violating an incompetent patient’s confidentiality will lead other patients to lose trust in physicians and thus avoid the health-care system. Some of this information might be obtained from Seth’s social worker. Other data, however, can be obtained only by reviewing the empirical literature. We admit that much of this information may be unobtainable. Knowing the limits of one’s knowledge, however, will allow an honest appraisal of how uncertainty regarding various factors affects one’s moral decision making. This is preferable to not attempting to ascertain the information at all.
CREATIVE SOLUTIONS
The failure to gather sufficient information often leads to an impoverished understanding of the ethical issues that a case raises. In Seth’s case, the authors present the case as though there were one question: Is it permissible/obligatory to violate Seth’s confidentiality to warn Maxwell? Asked this way, there appears to be only two resolutions to the case: either a physician protects Seth’s confidentiality by failing to warn Maxwell o the risk, or he violates Seth’s confidentiality by warning Maxwell. Upon collection of sufficient data, one might discover ways to resolve the case that would allow all relevant values to be promoted. In some cases, additional information may provide the ethicist with an “end run” around the presumed ethical problem. For instance, if the ethicist learns that Maxwell is already aware of Seth’s seropositivity, then the ethical quandary vanishes. There is strong pedagogical justification for the authors to provide us with sufficient information to conclude that the quandary could have been resolved by seeking additional information and to help us develop innovative solutions that might promote the competing values.
Even if more information does not allow one to avoid the ethical conflict, it may prove useful in determining how best to resolve the case. It is simplistic to view the outcome of ethical analysis as a hierarchical ranking of two competing values or principles. Intermediate solutions often exist, which allow one to respect both competing values. Even in those cases where it is justified to promote one value over another, one is nevertheless obligated to consider alternative courses of action that respect, as much as possible, the other value. The authors neglect an important step in ethical problem solving – attempting to develop creative solutions that, if they cannot perfectly respect all values, at least cause as little damage as possible. This approach, known in American law as “the least restrictive alternative,”6 recognizes that solutions can be more or less respectful of ethical principles. Thus, for example, one might decide that the risk to Maxwell is sufficiently high so that some violation of Seth’s confidentiality is permissible. A variety of options would still be open. (1) The psychiatrist could call Maxwell (or have the public health department do so) and inform him that he may have been exposed to the HIV virus and thus, he should be tested. (2) The psychiatrist could call Maxwell, identify himself as Seth’s physician, and attempt to ascertain what Maxwell knows about Seth’s serostatus and what the nature of their sexual relationship was. That evidence could then be used to determine whether further actions are in order. (3) The psychiatrist could call Maxwell and tell him that he is Seth’s physician, hat he knows of Maxwell and Seth’s sexual relationship, and that Seth is HIV positive. He could then urge Maxwell to be tested. A similar range of alternatives could be developed if one decides that respecting Seth’s confidentiality is the most important value.
PREVENTIVE ETHICS
A final question is simply why this problem arose. If we assume, as the authors do, that “choosing one solution [in an ethical dilemma] over another leaves behind an ethically significant value and regrettably may even produce harm,” we should attempt to prevent ethical dilemmas from occurring.7 However, typically, case discussions focus on how to “solve” the problem at hand without determining how and why the problem arose, and how it might be avoided in the future. As E. Haavi Morreim points out: “Our moral lives are comprised, not of terrible hypotheticals from which there are no escapes, but of complex situations whose constituent elements are often amenable to considerable alterations.”8 The psychiatrist in this case may not have been able to anticipate Seth’s disappearance, but perhaps he could have asked additional questions on his initial encounter to prevent the resulting ethical quandary. For instance, it would have been useful if the psychiatrist had gathered information about Seth’s values and desires prior to his decompensation. Furthermore, if the physician had asked Seth for permission to talk to his friends, whether others knew of his seropositivity, whether the doctor could release this information to Seth’s sexual partners. or to identify his moral surrogate, this additional information could have ameliorated the quandary that subsequently arose.
In the final analysis, we may well agree with Smith and Martin about how the psychiatrist should handle this case. In this article we have tried to criticize not the answer, but the process by which the answer was reached. We urge ethicists who are dealing with a challenging case to use the process of case comparison in their analysis, examining a variety of analogous cases; to seek sufficient information to be able to identify all the moral issues in a case and situate the case in its proper taxonomic family; to attempt to develop creative, “least-restrictive” alternatives to ethical dilemmas; and to determine if there are ways that the ethical problem can be prevented in the future. Close attention to these points is likely to improve ethical decision making in the clinical setting and ethical analyses of cases presented in the bioethics literature.
ACKNOWLEDGMENTS
We would like to thank our friends and colleagues for their helpful comments on this paper: Lisa Parker, PhD; Joel Frader, MD; Peter Ubel, MD; and Shawn Wright. JD, MPH.
1. A.R. Jonsen, “Casuistry as Methodology in Clinical Ethics,” Theoretical Medicine 12 (1991): 295-307.
2. T.L Beauchamp and J.F. Childress, Principles of Biomedical Ethics (New York: Oxford University Press, 1989).
3. 3c. Tarasoff v. Regents of the University of California, 17 Cal. 3d 425. 551 P.2d 334 (1976}.
5. N. Whitman, Creative Medical Teaching (SaIt Lake City: University of Utah School of Medicine, 1990).
6. Lake v. Cameron. 364 F. 2d 657 (D.C. Cir. 1966).
7. L. Forrow R.M. Arnold and L.S. Parker, “Preventive Ethics: Expanding the Horizons of Clinical Ethics:· The Journal of Clinical Ethics (forthcoming).
8. E.H. Morreim, “Philosophy Lessons from the Clinical Sening.” Theoretical Medicine 7 (1986): 47-63.
TARASOFF: Discussion Questions
1. Traditionally, the Tarasoff case pits two goods or values against each other: confidentiality between therapist and patient vs. protection of an intended victim. Why is each a value?
2. Confidentiality is not only a value, but it has been called a duty which is incumbent on health care professionals to maintain secrecy about information gained in the course of interaction with a patient or client. Confidentiality derives from the more fundamental value of autonomy, the right each person has to be one’s own self-decider, one’s own intentional agent.
Protection of an intended victim likewise becomes a duty. To discharge that duty, the court argued, the therapist is obliged to warn the intended victim or others, to notify the police, or to take steps which are reasonably necessary to guard the intended victim.
Formulate an argument that supports the duty of confidentiality over the duty to warn an intended victim. Then formulate an argument which supports the duty to warn over the duty to protect confidentiality. (Being able to make good cases for each of the values shows the ambiguity involved here. Bring into your arguments the issue of the foreseeability of violence (is violence clearly foreseeable, probably foreseeable or unforseeable?) and the element of control over the patient by the therapist.)
3. One can easily use the Tarasoff decision to show the two principal ways of argument, consequentialist and non-consequentialist. Formulate an argument from a utilitarian (consequentialist) perspective, i.e., emphasize risk over benefit in arguing for safety and again, in arguing for confidentiality.
Next, consider confidentiality and the right to be protected as goods in themselves, regardless of consequences. Show how each value is tied to the meaning of being human and indicate how such a value can be argued for without consideration of consequences.
4. Notice how the arguments being proposed by the committee deny the absolute nature of either value. Rather, the committee is attempting to justify an action that is indicated in favor of one value over another, while acknowledging that both values are human goods. How would one attempt to argue when faced with the position that confidentiality or protection were absolute values?
Further Readings
Beauchamp, Tom and LeRoy Walters (eds.) 1994. “The Management of Medical Information” in Contemporary Issues in Bioethics. Fourth Edition. Belmont, CA: Wadsworth:123-186.
Kleinman, Irwin. 1993. “Confidentiality and the Duty to Warn.” Canadian Medical Association Journal 149: 1783-1785.
Perlin, Michael L. 1992. “Tarasoff and the Dilemma of the Dangerous Patient: New Directions for the 1990’s.” Law and Psychology Review 16: 29-63.
- Open access
- Published: 14 March 2022
Health professionals' knowledge and attitude towards patient confidentiality and associated factors in a resource-limited setting: a cross-sectional study
- Masresha Derese Tegegne 1 ,
- Mequannent Sharew Melaku 1 ,
- Aynadis Worku Shimie 2 ,
- Degefaw Denekew Hunegnaw 3 ,
- Meseret Gashaw Legese 4 ,
- Tewabe Ambaye Ejigu 5 ,
- Nebyu Demeke Mengestie 1 ,
- Wondewossen Zemene 1 ,
- Tirualem Zeleke 1 &
- Ashenafi Fentahun Chanie 1
BMC Medical Ethics volume 23 , Article number: 26 ( 2022 ) Cite this article
34k Accesses
15 Citations
6 Altmetric
Metrics details
Respecting patients’ confidentiality is an ethical and legal responsibility for health professionals and the cornerstone of care excellence. This study aims to assess health professionals’ knowledge, attitudes, and associated factors towards patients’ confidentiality in a resource-limited setting.
Institutional based cross-sectional study was conducted among 423 health professionals. Stratified sampling methods were used to select the participants, and a structured self-administer questionnaire was used for data collection. The data was entered using Epi-data version 4.6 and analyzed using SPSS, version 25. Bi-variable and multivariable binary logistic regression analyses were used to measure the association between the dependent and independent variables. Odds ratio with 95% confidence intervals and P value was calculated to determine the strength of association and to evaluate statistical significance.
Out of 410 participants, about 59.8% with [95% CI (54.8–68.8%)] and 49.5% with [95% CI (44.5–54.5%)] had good knowledge and favorable attitude towards patents confidentiality respectively. Being male (AOR = 1.63, 95% CI [1.03–2.59]), taking training on medical ethics (AOR = 1.73, 95% CI = [1.11–2.70]), facing ethical dilemmas (AOR = 3.07, 95% CI [1.07–8.79]) were significantly associated factors for health professional knowledge towards patients’ confidentiality. Likewise, taking training on medical ethics (AOR = 2.30, 95% CI [1.42–3.72]), having direct contact with the patients (AOR = 3.06, 95% CI [1.12–8.34]), visiting more patient (AOR = 4.38, 95% CI [2.46–7.80]), and facing ethical dilemma (AOR = 3.56, 95% CI [1.23–10.26]) were significant factors associated with attitude of health professionals towards patient confidentiality.
The findings of this study revealed that health professionals have a limited attitude towards patient confidentiality but have relatively good knowledge. Providing a continuing medical ethics training package for health workers before joining the hospital and in between the working time could be recommended to enhance health professionals’ knowledge and attitude towards patient confidentiality.
Peer Review reports
Introduction
Confidentiality refers to the restriction of access to personal information from unauthorized persons and processes at authorized times and in an authorized manner [ 1 , 2 ]. When we say patients have the right to confidentiality, it refers to keeping privileged communication secret and cannot be disclosed without the patient’s authorization [ 3 , 4 ].
Health professionals have a legal obligation to handle patients' information privately and securely [ 5 ]. As a result, patients and professionals develop trust and a positive relationship. If such highly sensitive data is improperly disclosed, it could threaten patients' safety [ 6 ]. Hence confidentiality needs to be respected to protect patients’ well-being and maintain society’s trust in the physician–patient relationship. The issue of confidentiality has been recognized as a global concern. As a result, several internationally agreed on principles and guidelines for maintaining the sanctity of patients’ private lives during treatment. This law, known as Data Protection Act, was enacted in 1998 and was last revised in 2018 [ 7 , 8 ]. The Data Protection Act was created to provide protection and set guidelines for handling personal data [ 7 ]. There is no comprehensive data protection law in Ethiopia that covers health data protection [ 9 ]. Ethiopia's only confidentiality-oriented policy is the healthcare administration law, which requires health practitioners to maintain confidentiality. This law mandates health providers to keep patients' health information confidential [ 10 ]. Furthermore, only a few research have looked into health professionals' awareness of ethical rules and data security and sharing laws in Ethiopia [ 9 ].
Confidentiality is the basis of the legal elements of health records and an ethical cornerstone of excellent care [ 11 ]. More importantly, the quality of information shared with healthcare experts is determined by their capacity to keep it private. Otherwise, the patient may withhold important information, lowering the quality of care offered.
Although information sharing is essential in an interdisciplinary health team, each professional should limit information disclosure to an unauthorized health professional to plan and carry out procedures in the patient's best interests [ 12 ]. The exchange of patient medical records and data with an unauthorized person continues to be a common occurrence in a variety of clinical settings [ 5 ]. Breaches of confidentiality in clinical practice due to negligence, indiscretion, or sometimes even maliciously jeopardize a duty inherent in the physician–patient relationship [ 8 ]. Breaches of confidentiality and sharing data with unauthorized parties may have the potential to harm the patients’ health [ 13 ]. Health care quality declines due to a loss of confidence in the professional-patient relationship [ 14 ]. Patients become hesitant to seek care and attend follow-up appointments due to their mistrust of health providers [ 7 , 8 ].
Until recently, the standard curricula of Ethiopia's recent medical schools did not include a medical ethics course. Nevertheless, following proposals from the Ethiopian Medical Association and curriculum review committees, the medical ethics course was first established at Addis Ababa University's Faculty of Medicine in 2004 [ 15 ]. Despite the existence of a medical ethics course, patients' concern about maintaining their confidentiality has grown, and reports of unethical behavior by health professionals on patient confidentiality are familiar [ 15 ].
There are so many problems regarding patient medical record confidentiality and data sharing [ 16 ]. The loss of patient medical records due to handling by unauthorized staff without consent and transporting to another department is a big issue in Ethiopia. That can affect patients’ quality of care by consuming time, harming patient satisfaction, causing improper diagnosis, and making it difficult to get the previous history.
The significance of this research is that it addresses the rapidly growing trend of patient data sharing and confidentiality among health practitioners in developing countries taking Ethiopia as an example. There is limited evidence regarding health professional knowledge and attitude related to patients’ confidentiality in resources limited settings. Therefore, this study will fill evidence gaps on health professional knowledge, attitude, and associated factors related to patient confidentiality in Ethiopia. This study will provide policymakers with up-to-date information on health professionals' knowledge and attitude towards patient confidentiality. Aside from that, the outcomes of this study may aid legislators in developing plans to improve health professionals' knowledge and attitude toward patient confidentiality.
Study design and setting
An Institutional based cross-sectional study was conducted among health professionals from August–September 2021. Gondar is a historical town situated in the northwestern part of Ethiopia, 772 km far from the capital Addis Ababa and 168 km from Bahir Dar [ 17 ]. The University of Gondar specialized hospital is one of the largest teaching hospitals in the Amhara region providing tertiary level care for more than seven million people in the northwest part of the country coming from Amhara, Tigray, and Benishangul Gumuz regions [ 18 ]. It has 960 health professionals distributed over 30 services units responsible for delivering healthcare services to an average of 800 patients per day.
Study subjects and eligibility criteria
All healthcare professionals working in the University of Gondar specialized hospital and those available during the study period were the sources and study population. The study excluded health professionals with less than six months of experience, those who had not been found in the hospital for various reasons, and those on yearly leave during the data collection period.
Sample size determination and sampling procedure
The sample size was calculated using the single population proportion formula, n = Z(α/2) 2 pq/d 2 [ 19 ]. We assumed: n = the required sample size, Z = the value of standard normal distribution corresponding to α/2, 1.96, p = proportion of health professionals who had good knowledge and attitude towards confidentiality, q = proportion of health professionals who had unfavorable knowledge and attitude towards confidentiality, and d = precision assumed as 0.05. To our knowledge, no study has been conducted in Ethiopia to determine the knowledge and attitude of health professionals towards patient confidentiality. Therefore, we assumed p (proportion of health professionals who had good knowledge and attitude towards confidentiality) to be 0.5. Hence, the required sample size was calculated to be 384. After adding a 10% non-response rate, 423 health care professionals were enrolled in the study.
Stratified with a simple random sampling method was used to select the 423 participants. Firstly, the sample was stratified based on their department. Then the selection was proportionally allocated in each stratum depending on the numbers of healthcare providers in each stratum or department to assess their knowledge, attitude, and associated factors related to patients' confidentiality. After allocating samples in each stratum proportionally, a computer-generated simple random sampling technique was employed to select the study subjects in each department (Fig. 1 ).
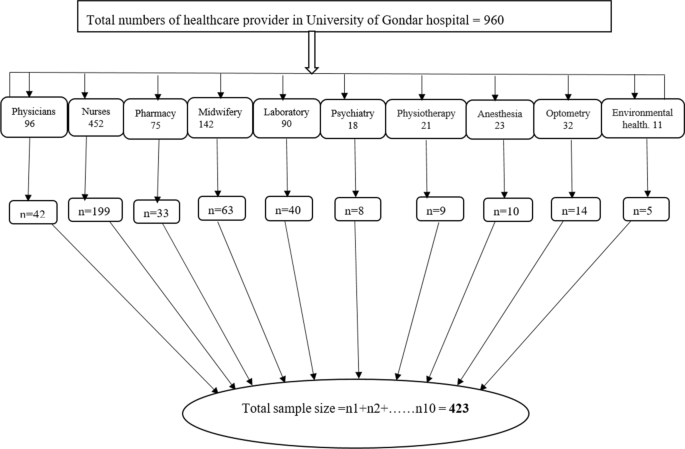
Sampling procedure and sample allocation in University of Gondar hospital
Study variables
The primary outcome variable of this study was knowledge and attitude towards patient confidentiality. The questionnaires used in this study were developed based on a review of related literature [ 20 , 21 ]. Socio-demographic and work-related characteristics were used as independent variables in this study.
Operational definitions
Knowledge about patients' confidentiality was assessed using seven items with “yes” and “no” responses. Each correct answer was equal to one point, while each incorrect answer was equal to zero points, with a height possible score of 7 for the knowledge part. A mean of 7 questions regarding Knowledge towards patient confidentiality was calculated. And those above the mean score were categorized as ‘good’ knowledge, and those below were categorized as ‘poor’ knowledge [ 20 ].
Attitudes toward patient confidentiality were assessed by using 14 questions with a 5 point Likert scale from ‘strongly disagree’ (score 1) to ‘strongly agree’ (score 5) [ 20 ]. The final score in the attitude section ranges from 14 to 70. A mean of the 14 questions of attitude towards patient’s confidentiality was calculated. Those above the mean value were categorized as ‘favorable’ attitude, and those below the mean value were categorized as ‘unfavorable’ attitude [ 20 ].
Data collection tool and quality control
A self-administered, organized, and pre-tested questionnaire was created in English. The data collection process included two supervisors and ten data collectors. One-day training was given to the data collectors to eliminate ambiguities. A pre-test was conducted outside of the study area, in Gondar town health centers, with 10% of the study population. The validity and reliability of the data collection instrument were assessed using the pre-test results. The Cronbach alpha value for the attitude questions was 0.82, whereas the Cronbach alpha value for the knowledge questions was 0.76. These figures show that the questionnaire is highly reliable.
Data processing and analysis
The data entry was performed using Epi Data version 4.6 software packages and analyzed using Statistical Package for Social Sciences (SPSS) version 25. Descriptive statistics were computed to describe the socio-demographic variables and health professionals’ knowledge and attitudes about patient confidentiality and data sharing. Bi-variable and multivariable binary logistic regression analyses were done to measure the association between the dependent and independent variables. In the bi-variable regression analysis, variables with a p value of less than 0.2 were included in the multivariable regression analysis to assess their adjusted impacts on the dependent variables. Odds ratio with 95% confidence level and P value were calculated to ascertain the strength of association and to decide statistical significance. For all significantly associated variables, the cut-off value was p < 0.05. Before conducting the logistic regression model, assumptions of multi-collinearity were checked. The result revealed all the variance inflation factor (VIF) values less than three, which confirmed the absence of multi-collinearity.
Description of participant’s socio-demographic and work-related characteristics
Of 423 participants, 410 responded to a questionnaire with a 96.9% response rate. The mean age of the participants was 28.12(SD ± 5.16) years which ranges from 21 to 50 years. The majority 271(66.1%) of the study participants were male and most of them 334 (81.5%) were orthodox religious followers. In terms of the educational level of the health professional, more than half 228 (55.6%) of participants have a BSc degree (Table 1 ). Of the total respondents, above three fourth 79.8% health professionals had below five years of work experience. A majority 47.8% of respondents were nurse professionals. Almost all 95.4% health professionals had direct contact with the patients and around 39% had visits above 40 patients per day. The results showed that about 5.9% of health professionals faced more than two ethical dilemmas daily while treating patients. In addition, 44.1% of the participants were taking training on medical ethics (Table 1 ).
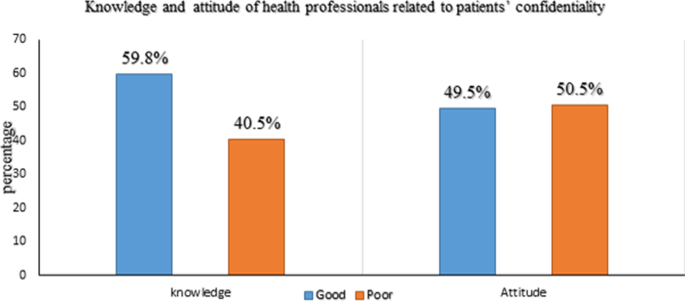
Health professionals’ knowledge about patients’ confidentiality
Of the total participants, 59.8% with [95% CI (54.9–64.5%)] had good knowledge about confidentiality with a mean score of 3.91(SD ± 1.39) (out of a maximum of 7 points) (Fig. 2 ). From the knowledge questionnaire, most of the respondents 358(87.3%) were said ‘access to medical records should be governed by law’ and 183(44.6%) argued that non-medical information is also confidential. Furthermore, 291(71%) health professionals were aware that third-party insurance companies did not access patient examination results (such as insurance companies) without patient consent. However, only 115(28.0%) of participants knew that policies were not allowed to access medical records freely (Table 2 ).
Health professional knowledge and attitude related to patients’ confidentiality
Health professionals attitude towards patients’ confidentiality
Of the total participants, 49.5% with [95% CI (44.6–54.3%)] had a favorable attitude towards confidentiality with a mean score of 42.8(SD ± 8.90) (out of a maximum of 70 points) (Fig. 2 ). Table 3 illustrates that about 126(30.7%) of participants agreed that confidentiality affects the patient in any way, and 299(72.9%) believed they don’t allow non-medical personnel to enter the examination room while they are discussing with patients. Of all respondents, 220(53.7%) and 162(39.5%) participants use lock systems and computers to store patient information.
Factors associated with health professionals’ knowledge about patients’ confidentiality
Bi-variable and multivariable binary logistic regression analyses were done to measure the association between Health professionals’ knowledge towards patients’ confidentiality and independent variables. In bi-variable regression, Sex of participants, Age of the respondents, Work experience, Training on medical ethics, Numbers of the patient served, Direct contact with the patients, Numbers of ethical dilemmas faced, Income of participants were the candidates’ variables for health professionals’ knowledge towards confidentiality for the multivariable regression analysis ( P < 0.2). With the multivariable regression model sex of respondents, training on medical ethics, number of ethical dilemmas faced were significantly associated factors for health professional knowledge towards patients’ confidentiality (Table 4 ). This means that being male was (AOR = 1.63, 95% CI [1.03–2.59]) times more likely to have good knowledge towards patient confidentiality as compared to females after controlling for other factors. Health professionals taking training on medical ethics were (AOR = 1.73, 95% CI = [1.11–2.70]) times more likely to have a good knowledge towards patients’ confidentiality as compared to their counterparts. Similarly, health professionals who faced more ethical dilemmas were (AOR = 3.07, 95% CI [1.07–8.79]) times more likely to have good knowledge than those who faced fewer ethical dilemmas.
Factors associated with health professionals’ attitude towards patients’ confidentiality
In both bi-variable and multivariable analysis training on medical ethics, direct contact with the patients, Numbers of patient visits, and numbers of ethical dilemmas faced were significant variables to the attitude of health professionals towards patient confidentiality (Table 5 ).
Health professionals taking on medical ethics were (AOR = 2.30, 95% CI [1.42–3.72]) times more likely to have a favorable attitude towards patient confidentiality when compared to those who didn’t take any pieces of training on medical ethics. Health professionals who had direct contact with the patients were (AOR = 3.06, 95% CI [1.12–8.34]) times more likely to have a favorable attitude towards patient confidentiality than those who didn’t have direct contact with the patients. Health professionals who visited more patients daily (more than 40 and 30–40) were approximately (AOR = 4.38, 95% CI [2.46–7.80]) and (AOR = 1.96, 95% CI [1.12–3.43]) times more likely to have a favorable attitude towards patients’ confidentiality when compared to those who visited less than 30 patients daily. Additionally, respondents who faced more ethical dilemmas were (AOR = 3.56, 95% CI [1.23–10.26]) times more likely to have a favorable attitude towards patients’ confidentiality than those who faced fewer ethical dilemmas.
This study examines health professionals’ knowledge and attitude towards patient confidentiality and associated factors in Northwest Ethiopia.
This study revealed that around 59.8% of respondents had good knowledge related to patient confidentiality. The finding is in line with two studies conducted in Iran 56.6% [ 22 ], 63% [ 23 ]. However, the results of this study demonstrated that health professionals’ good knowledge towards patient confidentiality was lower than studies conducted in Spain 68% [ 24 ] and Tehran university medical school 65% [ 25 ]. The difference could be that health professionals working in high-resource countries are more informed about patients' privacy in their daily lives and recognize the relative benefit of patient confidentiality [ 26 ]. The other reasons for the disparity could be explained by the fact that approximately 75% of participants had less than 5 years of professional experience in the current study, and they were also considerably younger than in the Spanish study [ 24 ]. Furthermore, the participants in Spain were all physicians, who are supposed to have better clinical data management and specific training [ 24 ].
In this study, 49.5% of participants had a favorable attitude towards patient confidentiality. This finding is supported by the study conducted in northern Jordan 52.4% [ 20 ]. However, this finding is lower than the study conducted in Turkey (64.4%) physicians strongly agreed to protect patient confidentiality [ 27 ]. The possible reason could be that difference awareness among health professionals in different countries results in a good level of attitude.
The study also found factors associated with health professionals’ knowledge and attitude regarding patient confidentiality. The sex of respondents, training on medical ethics, and the number of ethical dilemmas faced was all significantly associated factors of health professional knowledge towards patients’ confidentiality. Likewise, training on medical ethics, direct contact with the patients, Numbers of patient visits, and numbers of ethical dilemmas faced were significant variables to the attitude of health professionals towards patient confidentiality.
Among the factors associated with knowledge, being males were more likely to have good knowledge towards patient confidentiality than females. This finding is consistent with study findings from Jordan [ 20 , 21 ], Spain [ 24 ], and the United States [ 28 ]. This might be due to males were more access to information and technology and there is high information sharing between them [ 21 ]. Furthermore, the number of ethical dilemmas experienced and training on medical ethics were revealed to be predictive variables for both knowledge and attitude. Health professionals taking training on medical ethics were more likely to have a good knowledge and attitude related to patients’ confidentiality than those who had not taken the training. The greatest strategy to ensure adherence to confidentiality laws was to provide training on medical ethics, where health organizations would routinely update all health professionals on guidelines and strategies to prevent sensitive information disclosure [ 21 , 29 , 30 ]. Furthermore, the legislature's role is critical, not just in terms of legal norms to safeguard patient confidentiality, but also in terms of punishments when inappropriate behavior occurs [ 31 ]. And this finding is supported by a study conducted in Barbados [ 32 ], Vietnam [ 33 ]. Besides this, this study also found that health professionals who faced more ethical dilemmas were more likely to have good knowledge and attitude as compared to those who faced a less ethical dilemma. According to Hariharan et al. suggestions, health professionals may not report such problems to their seniors and try to solve them [ 32 ]. This may be the possible reasons for facing more ethical dilemma and trying to solve by themselves to have positive knowledge and attitude towards patient confidentiality.
In addition, direct contact with the patients and the number of patient visits were associated with a favorable attitude towards patient confidentiality. Respondents who have direct contact with the patients were more aware of confidentiality. This could be because the health of practitioners that deal with patients regularly are more familiar with confidentiality rules and strategies[ 22 ]. Besides this, health professionals who visit more patients per day were more likely to have a favorable attitude related to patient confidentiality. This might be because when health professionals serve more patients per day, they get a lot of challenges which helps to change their attitude to maintain the patient's information confidentially.
The findings of this study revealed that health professionals have a limited attitude towards patient confidentiality but have relatively good knowledge. The sex of respondents, training on medical ethics, and many ethical dilemmas faced were significantly associated factors of health professional knowledge towards patients’ confidentiality. Likewise, training on medical ethics, direct contact with the patients, Numbers of patient visits, and numbers of ethical dilemmas faced were significant variables to the attitude of health professionals towards patient confidentiality. Providing a continuing medical ethics training package for health workers before joining the hospital and in between the working time could be recommended to improve health professionals' knowledge and attitude towards patient confidentiality.
Strength and limitations
The findings from this study provide valuable information on health professionals' knowledge and attitude related to patients' confidentiality in resources limited countries. There are some limitations to this study. First, this study was an institution-based cross-sectional survey; only health professionals who came during the data collection period were interviewed.
Availability of data and materials
All the data generated or analyzed during this study are included in this published article and supplementary information [SPSS Data Knowledge and SPSS Data Attitude].
Abbreviations
Adjusted odds ratio
Confidence interval
Epidemiological information
Information communication technology
Statistical package for social science
de Sousa Costa R, de Castro Ruivo I, editors. Preliminary remarks and practical insights on how the whistleblower protection directive adopts the GDPR principles. Annual Privacy Forum; 2020. Springer.
Štarchoň P, Pikulík T. GDPR principles in data protection encourage pseudonymization through most popular and full-personalized devices-mobile phones. Procedia Comput Sci. 2019;151:303–12.
Article Google Scholar
Drogin EY. Confidentiality, privilege, and privacy. 2019.
Romeo C. Enciclopedia de Bioderecho y Bioética. Cuad Med Forense. 2012;18(3–4):144–5.
Google Scholar
Beltran-Aroca CM, Girela-Lopez E, Collazo-Chao E, Montero-Pérez-Barquero M, Muñoz-Villanueva MC. Confidentiality breaches in clinical practice: what happens in hospitals? BMC Med Ethics. 2016;17(1):1–12.
Parsa M. Privacy and confidentiality in medical field and its various aspects. J Med Ethics Hist. 2009;4:1–14.
Spencer A, Patel S. Applying the data protection act 2018 and general data protection regulation principles in healthcare settings. Nurs Manag. 2019;26(1):34.
Act DP. Data protection act. London Station Off. 2018;5.
Yilma DKM. Privacy and personal data protection in Africa A rights-based survey of legislationin eight countries 2020 [cited 2021 January 23]. https://www.apc.org/sites/default/files/PrivacyDataProtectionAfrica_CountryReports.pdf .
Organization Wh. Policy - Food, Medicine and Health Care Administration and Control Council of Ministers Regulation (Regulation No. 299/2013) 2014 [cited 2022 January 23]. https://extranet.who.int/nutrition/gina/en/node/26274 .
Adeleke I, Adekanye A, Adefemi S, Onawola K, Okuku A, Sheshi E, et al. Knowledge, attitude and practice of confidentiality of patients’ health records among health care professional at federal medical centre. Bida Niger J Med. 2011;20(2):228–35.
Cas G, Aji G. Analysis of the ethical aspects of professional confidentiality in dental practice. Br Dent J. 2008;205(5):257.
Blightman K, Griffiths S, Danbury C. Patient confidentiality: When can a breach be justified? Contin Educ Anaesth Critical Care Pain. 2014;14(2):52–6.
Bartlett YK, Coulson NS. An investigation into the empowerment effects of using online support groups and how this affects health professional/patient communication. Patient Educ Couns. 2011;83(1):113–9.
(EMA) EMA. medical ethics for doctorsin Ethiopia 2010 [cited 2022 January 23]. http://www.ethiopianorthopaedics-esot.org/index.php/ethics/send/4-ethics/8-ethics-code .
Ayalew NA. Duty of confidentiality in arbitration process in Ethiopia. Int J Soc Sci Econ Rev. 2019;1:92–100.
Wikipedia. Gondar 2020 [cited 2021 October 16]. https://en.wikipedia.org/wiki/Gondar .
Abdella NM, Tefera MA, Eredie AE, Landers TF, Malefia YD, Alene KA. Hand hygiene compliance and associated factors among health care providers in Gondar University Hospital, Gondar, North West Ethiopia. BMC Public Health. 2014;14(1):1–7.
Naing L, Winn T, Rusli B. Practical issues in calculating the sample size for prevalence studies. Arch Orofac Sci. 2006;1:9–14.
Karasneh R, Al-Mistarehi A-H, Al-Azzam S, Abuhammad S, Muflih SM, Hawamdeh S, et al. Physicians’ knowledge, perceptions, and attitudes related to patient confidentiality and data sharing. Int J General Med. 2021;14:721.
Abuhammad S, Alzoubi KH, Al-Azzam SI, Karasneh RA. Knowledge and practice of patients’ data sharing and confidentiality among nurses in Jordan. J Multidiscip Healthc. 2020;13:935.
Hosseini-Ghavam-Abad L, Asghari F, Bandehagh A, Najafipour S, Bigdeli S. Patient privacy: awareness and attitudes of Iran University of Medical Sciences medical students. Med J Islam Repub Iran. 2019;33:12.
Rangrazr F, Rabie R. Evaluation of patients’ rights in public hospitals in Kashan in 2002. J Kermanshah Uni Med Sci. 2005;1(9):62–71.
Beltran-Aroca CM, Labella F, Font-Ugalde P, Girela-Lopez E. Assessment of doctors’ knowledge and attitudes towards confidentiality in hospital care. Sci Eng Ethics. 2019;25(5):1531–48.
Sheikh-Taheri AK, BaratiMarnani KA. Knowledge of physicians, nurses and staff of medical records of the legal aspects of medical records in hospitals affiliated to Tehran University of Medical Sciences. Health Inf Manag. 2010;89(7):136–46.
Privacy_International. Medical privacy and security in developing countries and emergency situations 2012 [cited 2022 January 25]. https://privacyinternational.org/report/726/medical-privacy-and-security-developing-countries-and-emergency-situations .
Demirsoy N, Kirimlioglu N. Protection of privacy and confidentiality as a patient right: physicians’ and nurses’ viewpoints. Biomed Res. 2016;27(4):1437–48.
Wandrowski J, Schuster T, Strube W, Steger F. Medizinethische Kenntnisse und moralische Positionen von Ärztinnen und Ärzten aus Bayern. Dtsch Ärztebl. 2012;109(8):141–7.
Noor MM, Hassan WH. Wireless networks: developments, threats and countermeasures. Int J Dig Inf Wirel Commun (IJDIWC). 2013;3(1):125–40.
Nejad EM, Begjani J, Abotalebi G, Salari A, Ehsani SR. Nurses awareness of patients rights in a teaching hospital. J Med Ethics History Med. 2011;4:2.
Veerus P, Lexchin J, Hemminki E. Legislative regulation and ethical governance of medical research in different European Union countries. J Med Ethics. 2014;40(6):409–13.
Hariharan S, Jonnalagadda R, Walrond E, Moseley H. Knowledge, attitudes and practice of healthcare ethics and law among doctors and nurses in Barbados. BMC Med Ethics. 2006;7(1):1–9.
Khac Hai N, Lawpoolsri S, Jittamala P, Thi Thu Huong P, Kaewkungwal J. Practices in security and confidentiality of HIV/AIDS patients’ information: a national survey among staff at HIV outpatient clinics in Vietnam. PLoS ONE. 2017;12(11):e0188160.
Download references
Acknowledgements
We are very grateful to the University of Gondar, Institute of Public Health for providing this opportunity to conduct the research. Our acknowledgment also extends to the managing board of the University of Gondar specialized hospital for giving all the necessary information and support. We also forward our thanks to the study participants, data collectors, and supervisors.
Funding was not granted.
Author information
Authors and affiliations.
Department of Health Informatics, Institute of Public Health, College of Medicine and Health Sciences, University of Gondar, Gondar, Ethiopia
Masresha Derese Tegegne, Mequannent Sharew Melaku, Nebyu Demeke Mengestie, Wondewossen Zemene, Tirualem Zeleke & Ashenafi Fentahun Chanie
Department of Health Informatics, College of Medicine and Health Sciences, Debre Markos University, Debre Markos, Ethiopia
Aynadis Worku Shimie
Department of Health Information Technology, Debre Berhan Health Science College, Debre Berhan, Ethiopia
Degefaw Denekew Hunegnaw
Health Management Information System Unit, Mekaneselam Hospital, Mekaneselam, Ethiopia
Meseret Gashaw Legese
Department of Health Information Technology, Teda Health Science College, Teda, Ethiopia
Tewabe Ambaye Ejigu
You can also search for this author in PubMed Google Scholar
Contributions
MDT made significant contributions in conception, design, data collection supervision, data analysis, interpretation, and manuscript write-up. MSM & AFC have contributed extensively to revising the manuscript, analysis, and interpretation. AWS, DDH, MGL, TAE, ND, WZ, and TZ have drafted proposals, analyses, and interpretation. All authors have approved the final version of this manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Masresha Derese Tegegne .
Ethics declarations
Ethics approval and consent to participate.
We confirm that all procedures utilized in this study were conducted following the principles of the Helsinki Declaration. Ethical clearance and approval letters were secured from the Institutional Review Board (IRB) of the University of Gondar (Reference number H/I/D 656/9/21). Written consent was obtained from each health professional after telling the objective of the study. A supporting letter was also obtained from the University of Gondar hospital. During the data collection, the issue of confidentiality and privacy was assured by maintaining the anonymity of participants. Health professionals were voluntary, and participants could withdraw from the study at any time if they were not happy with the survey.
Consent for publication
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Additional file 1:.
Supplementary SPSS data on Knowledge of Patient Confidentiality.
Additional file 2:
Supplementary SPSS data on attitude towards Patient Confidentiality.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Tegegne, M.D., Melaku, M.S., Shimie, A.W. et al. Health professionals' knowledge and attitude towards patient confidentiality and associated factors in a resource-limited setting: a cross-sectional study. BMC Med Ethics 23 , 26 (2022). https://doi.org/10.1186/s12910-022-00765-0
Download citation
Received : 08 December 2021
Accepted : 07 March 2022
Published : 14 March 2022
DOI : https://doi.org/10.1186/s12910-022-00765-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Health professional
- Confidentiality
BMC Medical Ethics
ISSN: 1472-6939
- General enquiries: [email protected]
- Open access
- Published: 15 August 2024

Balancing confidentiality and care coordination: challenges in patient privacy
- Ateya Megahed Ibrahim 1 , 2 ,
- Hassanat Ramadan Abdel-Aziz 1 , 3 ,
- Heba Ali Hamed Mohamed 4 ,
- Donia Elsaid Fathi Zaghamir 1 , 5 ,
- Nadia Mohamed Ibrahim Wahba 1 , 6 ,
- Ghada. A. Hassan 7 ,
- Mostafa Shaban 8 ,
- Mohammad EL-Nablaway 9 ,
- Ohoud Naif Aldughmi 10 &
- Taghreed Hussien Aboelola 11
BMC Nursing volume 23 , Article number: 564 ( 2024 ) Cite this article
4928 Accesses
3 Citations
Metrics details
In the digital age, maintaining patient confidentiality while ensuring effective care coordination poses significant challenges for healthcare providers, particularly nurses.
To investigate the challenges and strategies associated with balancing patient confidentiality and effective care coordination in the digital age.
A cross-sectional study was conducted in a general hospital in Egypt to collect data from 150 nurses across various departments with at least six months of experience in patient care. Data were collected using six tools: Demographic Form, HIPAA Compliance Checklist, Privacy Impact Assessment (PIA) Tool, Data Sharing Agreement (DSA) Framework, EHR Privacy and Security Assessment Tool, and NIST Cybersecurity Framework. Validity and Reliability were ensured through pilot testing and factor analysis.
Participants were primarily aged 31–40 years (45%), with 75% female and 60% staff nurses. High compliance was observed in the HIPAA Compliance Checklist, especially in Administrative Safeguards (3.8 ± 0.5), indicating strong management and training processes, with an overall score of 85 ± 10. The PIA Tool showed robust privacy management, with Project Descriptions scoring 4.5 ± 0.3 and a total score of 30 ± 3. The DSA Framework had a mean total score of 20 ± 2, with Data Protection Measures scoring highest at 4.0 ± 0.4. The EHR assessments revealed high scores in Access Controls (4.4 ± 0.3) and Data Integrity Measures (4.3 ± 0.3), with an overall score of 22 ± 1.5. The NIST Cybersecurity Framework had a total score of 18 ± 2, with the highest scores in Protect (3.8) and lower in Detect (3.6). Strong positive correlations were found between HIPAA Compliance and EHR Privacy ( r = 0.70, p < 0.05) and NIST Cybersecurity ( r = 0.55, p < 0.05), reflecting effective data protection practices.
The study suggests that continuous improvement in privacy practices among healthcare providers, through ongoing training and comprehensive privacy frameworks, is vital for enhancing patient confidentiality and supporting effective care coordination.
Peer Review reports
Digital technology has significantly transformed healthcare, enhancing care coordination and improving patient outcomes. However, this transformation brings forth critical challenges, particularly in balancing the imperatives of confidentiality and efficient care coordination [ 1 ]. The intersection of these essential elements, patient privacy and the seamless sharing of information among healthcare providers requires a nuanced approach to ensure ethical and legal compliance while optimising patient care [ 2 ].
Confidentiality in healthcare is foundational, rooted in bioethics principles and protected by laws such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States [ 3 ]. HIPAA establishes national standards to safeguard individuals' medical records and other personal health information, emphasising the importance of privacy in the digital age [ 4 ]. As digital technologies become more embedded in healthcare practices, ensuring compliance with these standards while facilitating the necessary flow of information for care coordination becomes increasingly complex [ 5 ]. Care coordination, defined as the deliberate organisation of patient care activities to facilitate the appropriate delivery of health services, is essential for achieving high-quality healthcare [ 6 ]. Effective care coordination requires timely and accurate sharing of patient information among various healthcare providers, which can be challenging when strict confidentiality rules are in place [ 7 , 8 ].
Nurses are responsible for ensuring patient information is shared accurately and promptly with other healthcare team members to facilitate effective care coordination [ 9 ]. However, they must also strictly adhere to confidentiality protocols to protect patient privacy. This dual responsibility can create significant tension and complexity in their daily practice. Nurses must navigate varying levels of digital literacy, differing institutional policies on information sharing, and the ever-present risk of data breaches or inadvertent disclosures [ 10 ]. Furthermore, the pressure to use electronic health records (EHRs) efficiently while maintaining patient trust and confidentiality adds to the complexity of their role [ 11 ]. These challenges highlight the need for robust training, clear guidelines, and support systems to help nurses effectively manage the delicate balance between confidentiality and care coordination.
Introduction
Electronic Health Records (EHRs) are central to enhancing care coordination by providing comprehensive, real-time access to patient health information, facilitating more informed decision-making and continuity of care [ 12 ]. However, digitising health records also raises significant privacy concerns, increasing the risk of unauthorised access and data breaches [ 13 ]. Thus, healthcare providers must implement robust security measures to protect patient data while ensuring it is accessible to authorised personnel when needed [ 14 ].
Although telehealth offers significant benefits in terms of accessibility and convenience, particularly for patients in remote or underserved areas, it further complicates the balance between confidentiality and care coordination [ 15 , 16 ]. It introduces challenges in maintaining patient privacy, preventing breaches, and safeguarding patient data [ 17 ]. Additionally, there is a critical issue concerning who has access to this information, which raises justice concerns about equitable access and safeguarding patient data. Addressing these concerns involves implementing robust access controls and consistently applying privacy measures across all telehealth platforms [ 18 ]. Patient consent is another critical factor for maintaining patient trust and ensuring that individuals know how their information will be used and shared [ 19 ]. However, the complexity of digital health systems can make it difficult for patients to fully understand the implications of consent, particularly regarding sharing their data across multiple platforms and providers [ 20 , 21 , 22 ].
Nurses play a pivotal role in balancing confidentiality and care coordination in the digital age, acting as guardians of patient privacy and key facilitators of information sharing. Their unique position on the front lines of patient care requires them to navigate complex ethical and practical challenges. Nurses are often responsible for inputting and accessing data within EHRs, making their adherence to privacy protocols crucial for protecting patient information [ 23 ]. Additionally, they serve as critical links in the care coordination chain, ensuring that relevant health information is accurately communicated among various healthcare providers to support comprehensive patient care [ 24 ]. As the healthcare landscape becomes increasingly digital, ongoing education and training for nurses in the technological aspects of EHRs and the ethical implications of data handling are essential [ 25 ].
Healthcare institutions must adopt comprehensive policies and technological solutions to manage the dual imperatives of confidentiality and care coordination [ 26 ] to help mitigate the risks associated with data breaches and unauthorised access [ 27 ]. Interoperability between different healthcare systems is another significant challenge, and efforts to develop and implement interoperable systems are essential for balancing the need for information sharing with protecting patient privacy [ 28 , 29 ] ensuring that patient welfare remains the primary focus [ 30 ]. In addition, empowering patients to take an active role is crucial, and education and communication strategies are essential for helping patients understand their rights and measures to protect their privacy [ 31 ].
Healthcare institutions must adopt comprehensive policies and frameworks to manage the dual imperatives of confidentiality and care coordination. These policies should include guidelines for data security, patient consent, and the ethical use of health information [ 26 ]. Technological solutions such as encryption, anonymisation, and secure access controls are crucial for protecting patient data in digital systems. These technologies help mitigate the risks associated with data breaches and unauthorised access, ensuring that sensitive information remains secure while being accessible to those who need it for patient care [ 27 ].
Interoperability between different healthcare systems is another significant challenge. The lack of standardised protocols for data exchange can hinder effective care coordination and increase the risk of privacy breaches [ 28 ]. Efforts to develop and implement interoperable systems are essential for balancing the need for information sharing with the protection of patient privacy [ 29 ]. Ethical frameworks must account for the potential benefits and harms of information sharing, ensuring that patient welfare remains the primary focus [ 30 ].
Patient engagement is also crucial in this context. Empowering patients to take an active role in their healthcare, including decisions about their information, can enhance trust and improve outcomes. Education and communication strategies are essential for helping patients understand their rights and the measures in place to protect their privacy [ 31 ].
In conclusion, balancing confidentiality and care coordination in the digital age is a complex but essential task for modern healthcare. Ensuring patient privacy while facilitating the necessary flow of information for care coordination requires a multifaceted approach that includes robust technological solutions, comprehensive policies, ongoing education and training, and active patient engagement. By addressing these challenges, healthcare providers can improve patient outcomes and maintain public trust in the healthcare system.
Significance of the study
This study is significant as it addresses the critical intersection of confidentiality and care coordination in the rapidly evolving digital healthcare landscape. By examining the practices and perceptions of healthcare professionals, particularly nurses, the research sheds light on how effectively these individuals face challenges posed by digital technologies while ensuring patient privacy. Understanding the dynamics of confidentiality and care coordination informs best practices and enhances the development of training programs and institutional policies to improve patient outcomes.
The findings of this study have several practical applications. Institutions can design targeted training programs focusing on both technical skills and ethical considerations to educate nurses on safeguarding patient information while ensuring efficient care coordination. Insights can inform the creation or revision of data security and patient consent guidelines, ensuring staff understand the importance of maintaining patient privacy and secure data sharing. Additionally, the study promotes integrating advanced security features in Electronic Health Record (EHR) systems, balancing data protection with necessary access for care coordination. This research can build patient trust by highlighting best practices and effective strategies for balancing confidentiality and care coordination, leading to better cooperation and health outcomes. Furthermore, these findings can support the development of standardised protocols for telehealth services, ensuring consistent privacy measures across platforms and improving equitable access to care.
Aim of the study:
Research questions:.
What are healthcare providers' primary challenges in maintaining patient confidentiality while utilising digital health technologies for care coordination?
How do different privacy assessment tools and frameworks impact the balance between patient confidentiality and the efficiency of care coordination in digital healthcare environments?
What best practices can be implemented to maintain patient privacy without compromising care coordination in the digital age?
Theoretical framework
The theoretical framework for this study incorporates several key theories to understand the balance between confidentiality and care coordination in the context of digital health technologies.
Privacy Regulation Theory, proposed by Westin32, emphasises that privacy is a fundamental human right involving control over the extent, timing, and circumstances of sharing oneself with others. This theory is crucial for understanding the importance of maintaining patient confidentiality in healthcare settings. It underscores the need for stringent privacy measures to build and maintain trust between patients and healthcare providers. Using this theory, the study addresses the first research question concerning healthcare providers' challenges in maintaining patient confidentiality. It offers a conceptual foundation for exploring the importance of privacy in patient-provider relationships and the implications of privacy breaches in digital health environments.
Health Information Technology (HIT) Adoption Framework, as described by Venkatesh et al.33, examines factors influencing the adoption of health information systems, such as perceived usefulness, ease of use, and institutional support. This framework is relevant for understanding how healthcare professionals, particularly nurses, adopt and utilise digital technologies while managing patient privacy. It addresses the second research question about how privacy assessment tools and frameworks impact the balance between patient confidentiality and care coordination. The framework provides insights into the factors that facilitate or hinder the adoption of digital health technologies, which is essential for effective care coordination.
The Technology Acceptance Model (TAM), proposed by Davis 34, explains how users accept and use technology, emphasising perceived ease of use as primary determinants. TAM is pertinent for understanding healthcare professionals' attitudes toward digital health technologies and how these attitudes influence their adoption and usage. This model supports the exploration of the third research question regarding best practices for ensuring patient privacy without compromising care coordination. It provides a basis for developing strategies to enhance the acceptance and effective use of digital health technologies among healthcare providers.
Ethical Decision-Making Framework, based on Beauchamp and Childress's principles of biomedical ethics—autonomy, beneficence, non-maleficence, and justice—guides ethical considerations in healthcare [ 35 ]. This framework is integral for evaluating the ethical implications of maintaining confidentiality while promoting care coordination. It helps address the ethical challenges identified in the first research question. It supports the development of best practices outlined in the third research question. This framework ensures that ethical principles guide decisions about information sharing and patient privacy in digital health environments. Additionally, Grady's Ethical Framework for Health Informatics emphasises integrating ethical considerations into the design and use of health information technologies, ensuring that privacy and care coordination are complementary goals [ 36 ].
Diffusion of Innovations Theory, proposed by Rogers [ 37 ], explains how new ideas and technologies spread within a social system, focusing on communication channels, social systems, and the attributes of innovations. This theory is relevant for understanding how digital health innovations are adopted in healthcare settings and their impact on confidentiality and care coordination. It helps explore the challenges of adopting digital health technologies addressed in the first research question. It supports identifying best practices for integrating new technologies into healthcare practice, as addressed in the third research question. The theory provides insights into the adoption process and the factors influencing the successful integration of innovations into healthcare practice.
Conceptual framework
The conceptual framework for this study explores the dynamic interaction between confidentiality, care coordination, and the utilisation of digital health technologies, with insights drawn from several theoretical perspectives. Confidentiality protects patient information from unauthorised access, which is critical for maintaining trust in healthcare settings [ 38 ]. Privacy Regulation Theory emphasises that privacy is a fundamental human right, focusing on controlling the extent, timing, and circumstances of sharing personal information. This theory underlines the necessity of robust privacy measures to ensure patient data security and build trust between patients and healthcare providers [ 32 ].
Care coordination refers to effectively managing and integrating patient care across different healthcare providers and settings. It involves ensuring that care is seamless and that information is shared appropriately among various stakeholders to provide comprehensive and continuous care [ 39 ]. The Health Information Technology (HIT) Adoption Framework sheds light on how factors such as perceived usefulness, ease of use, and institutional support influence the adoption of health information systems. This framework helps us understand how healthcare professionals integrate digital technologies into their workflows while managing patient privacy and enhancing care coordination [ 33 ].
Using digital health technologies includes tools such as electronic health records (EHRs) and telehealth platforms that facilitate communication, information sharing, and care coordination. These technologies are critical for modern healthcare delivery but also raise challenges related to confidentiality [ 1 , 2 ]. The Technology Acceptance Model (TAM) provides a lens through which to examine how perceived ease of use and perceived usefulness affect the acceptance and effective use of these technologies. Understanding healthcare professionals' attitudes towards these tools is crucial for improving their integration and addressing potential barriers to technology adoption, which impacts confidentiality and care coordination [ 34 ].
The Ethical Decision-Making Framework, guided by Beauchamp and Childress's principles—autonomy, beneficence, non-maleficence, and justice—offers a foundation for evaluating the ethical implications of maintaining confidentiality while promoting care coordination. This framework helps ensure that information-sharing decisions respect patient autonomy and adhere to ethical standards, balancing privacy with the need for effective care [ 35 , 36 ].
The Code of Ethics for Nurses further reinforces the importance of privacy by setting ethical guidelines for protecting patient information. This code ensures that nurses' practices align with ethical and legal standards, providing a practical framework for maintaining confidentiality while coordinating care effectively [ 14 , 17 ].
Lastly, Diffusion of Innovations Theory explains how new technologies spread within healthcare systems, emphasising the roles of communication channels, social systems, and the attributes of innovations. This theory helps us understand how digital health innovations are adopted and how they impact the balance between confidentiality and care coordination. It provides insights into the factors influencing the successful integration of new technologies [ 37 ].
The conceptual framework integrates these theories to comprehensively understand how confidentiality, care coordination, and digital health technologies interact. Each theory provides unique insights into the challenges and solutions of maintaining patient privacy while improving care coordination in a digital healthcare environment (Fig. 1 ).
Balancing confidentiality and care coordination in digital health
This cross-sectional study was conducted at General Hospital in Egypt to evaluate the balance between patient confidentiality and care coordination in the digital age. Data was collected from a sample of nurses working in various departments in the hospital. The recruitment process entailed inviting all eligible nurses through internal communication channels, such as email and notice boards, with detailed information about the study and the importance of their participation. A total of 150 nurses were needed to achieve a representative sample, calculated using the formula for sample size estimation for a finite population: n = z2 * p * (1—p)/e2 [ 40 ], where Z was the Z-value (1.96 for a 95% confidence level), p was the expected prevalence (assumed at 0.5 for maximum sample size), and e was the margin of error (0.05). The inclusion criteria for the study included nurses working at Damietta General Hospital for at least six months, directly involved in patient care, and consented to participate. Nurses on extended leave, such as maternity or sick leave, or those involved in administrative roles without direct patient care responsibilities were excluded from the study.
Data collection tools
Six tools were used for data collection.
Demographic form
The demographic questionnaire for this study was designed following a comprehensive review of relevant literature and studies and included variables such as age, gender, marital status, current job title/position at General Hospital, years of nursing experience, highest nursing qualification attained, training received on patient confidentiality and digital health technologies, and primary language of communication in the workplace. These variables were chosen to provide a comprehensive profile of the participating nurses, enabling a deeper analysis of their perceptions and practices concerning patient confidentiality and care coordination in the digital healthcare environment.
Health insurance portability and cccountability act (HIPAA) compliance checklist
The Health Insurance Portability and Accountability Act (HIPAA) is a regulatory framework enforced by the U.S. Department of Health and Human Services (HHS) to safeguard patient privacy and secure health information [ 41 ]. Healthcare providers use the HIPAA Compliance Checklist to ensure adherence to regulations, protecting patient information from unauthorised access and breaches. The HIPAA Compliance Checklist was chosen for its comprehensive approach to ensuring regulatory compliance and its ability to provide quantifiable data on privacy practices to identify best practices for maintaining patient confidentiality and enhancing care coordination by evaluating how well healthcare facilities implement privacy measures in the context of digital technologies. Components include administrative safeguards, such as security management processes and workforce training; physical safeguards, like facility access controls and workstation security, and technical safeguards including access control and audit controls. The checklist also covers organisational requirements such as business associate contracts and documentation of policies and procedures. The checklist evaluates adherence using a scoring system that rates each component from 0 (non-compliant) to 4 (fully compliant), with a total score ranging from 0 to 100.
Privacy impact assessment (PIA) tool
The Privacy Impact Assessment (PIA) tool, as detailed by Wright and De Hert [ 42 ], is used to identify and mitigate risks and ensure compliance with data protection regulations by thoroughly evaluating how information is collected, used, shared, and stored. The PIA tool typically includes sections on project descriptions, methods of data collection, practices for data usage and sharing practices, data storage and security strategies, identification of potential privacy risks, and methods for mitigating these risks. Each section is scored on a scale from 0 (non-compliant) to 5 (fully compliant), resulting in a total score range from 0 to 35. The PIA tool is chosen to identify and manage privacy risks, which aligns with the study's aim to balance confidentiality and care coordination. It helps evaluate how effectively privacy measures are integrated into new systems, thus ensuring that privacy concerns are proactively addressed and managed.
Data sharing agreement (DSA) framework
The Data Sharing Agreement (DSA) framework [ 43 ] establishes clear protocols to ensure data privacy and security while facilitating effective care coordination to enhance patient care and comply with legal requirements. Key components of the DSA framework include defining the purpose of data sharing, specifying the types of data to be shared, outlining the roles and responsibilities of involved parties, implementing robust data protection measures, managing consent appropriately, and establishing terms for data use and retention. Regarding compliance evaluation, each section of the DSA framework was assessed on a scale from 0 (indicating non-compliance) to 4 (indicating full compliance), resulting in a total score range from 0 to 24. The DSA framework is chosen for its structured approach to managing data sharing while ensuring privacy and security. It supports the study's aim of balancing confidentiality with effective care coordination by providing a comprehensive system for managing data-sharing agreements.
Electronic health record (EHR) privacy and security assessment tool
The Electronic Health Record (EHR) Privacy and Security Assessment Tool [ 44 ] is critical for evaluating EHR systems' privacy and security features. This tool ensures that EHR systems adhere to regulations and best practices, protecting patient information against unauthorised access and breaches. Key components evaluated by the assessment tool include access controls, encryption methods, audit trail functionalities, measures for maintaining data integrity, and protocols for incident response. In terms of scoring, each component was typically rated on a scale from 0 (indicating non-compliance) to 5 (indicating full compliance), resulting in a total score range from 0 to 25. This assessment tool is chosen for its comprehensive approach to evaluating EHR systems' security and privacy features, aligning with the study's aim of ensuring effective privacy protection while facilitating care coordination.
National institute of standards and technology (NIST) cybersecurity framework
The National Institute of Standards and Technology (NIST) Cybersecurity Framework [ 45 ] is a foundational tool healthcare organisations, including nursing staff, use to enhance and assess their cybersecurity measures. Key components of the NIST Cybersecurity Framework include five core functions: Identify, Protect, Detect, Respond, and Recover. Each function incorporates specific categories and subcategories detailing activities and best practices for cybersecurity. Each core function can be assessed on a scale from 0 (indicating not implemented) to 4 (indicating fully implemented), resulting in a total score range from 0 to 20. This framework is selected for managing cybersecurity risks, aligning with the study's aim of safeguarding patient information while ensuring effective care coordination.
Validation and reliability
In the preliminary phase of this study, a pilot test was conducted involving 10% of the total nurses, equivalent to 10 individuals, using the newly introduced data sharing agreement (DSA) framework, the electronic health record (EHR) privacy and security assessment tool, and the National Institute of Standards and Technology (NIST) Cybersecurity Framework. These participants were excluded from the final sample size to mitigate any potential bias from their prior exposure to the research instruments, ensuring the integrity of the results. During the pilot phase, a crucial step involved implementing factor analysis. This statistical technique was employed to rigorously examine the relevance and accuracy of each component within the research instruments. Following the pilot study, the insights gained from factor analysis informed the decision-making process for the final study. The same factor analysis methodology was applied to the remaining nurses who were not part of the pilot study.
Additionally, content validity was rigorously employed as a methodological approach to validate the measurement instruments used in this study. Specifically, for the data sharing agreement (DSA) framework, electronic health record (EHR) privacy and security assessment tool, and National Institute of Standards and Technology (NIST) Cybersecurity Framework, content validity procedures were implemented to ensure that the items within these instruments accurately and comprehensively captured the intended constructs. Experts possessing considerable knowledge and experience in healthcare data sharing, cybersecurity, and relevant research methodologies critically evaluated the items to ensure that they effectively measured the key dimensions of data sharing protocols, EHR privacy and security features, and cybersecurity practices.
Reliability, a fundamental aspect of measurement accuracy in research, was meticulously assessed for each tool employed in this study. The data sharing agreement (DSA) framework underwent thorough scrutiny, with the calculation of Cronbach's alpha as a robust indicator of its internal consistency. The results revealed an impressive Cronbach's alpha value of 0.87, signifying a high level of Reliability. Similarly, the electronic health record (EHR) privacy and security assessment tool comprehensively evaluated its internal consistency using Cronbach's alpha. The findings were notably robust, with a calculated alpha value of 0.88. This high degree of internal consistency underscores the tool's Reliability in assessing EHR privacy and security features, indicating that it consistently measures these aspects stably and dependably. The Cronbach's alpha value of 0.88 signifies a strong level of agreement among the tool's items, further enhancing the credibility of the data generated from this instrument.
Ethical approval and consideration
This study adhered to stringent ethical standards and received approval from the Research Ethics Committee (REC) at the Faculty of Nursing, Zagazig University, Egypt under the code ID/Zu.Nur.REC#:0067. Nurses were described the study's objectives, methodologies, potential risks, and benefits and provided written, informed consent before participation, signifying their understanding of the study's purpose and their voluntary decision to contribute. Strict confidentiality measures were implemented, ensuring all collected data was anonymised and securely stored to protect participant privacy.
Statistical analysis
Statistical analysis was conducted using SPSS 26. Descriptive statistics, including counts, percentages, mean scores and standard deviations (mean ± SD), were systematically employed to offer a detailed overview of demographic characteristics and the usage status of the Privacy Impact Assessment (PIA) Tool, Data Sharing Agreement (DSA) Framework, Electronic Health Record (EHR) Privacy and Security Assessment Tool, and National Institute of Standards and Technology (NIST) Cybersecurity Framework. These statistical measures provided a nuanced understanding of the respondents' backgrounds, contributing valuable insights into the diverse composition of the sample and the distribution of tools' utilisation among participants. Spearman's rank correlation coefficient (r) was utilised to unveil significant associations among the tools, highlighting the interconnected nature of these critical constructs within the nursing context.
Furthermore, the study integrated inferential statistics, including ANOVA and t-tests, to add depth to the analysis of the tools. These statistical methods uncovered associations and significant differences related to demographic variables, contributing to a holistic understanding of the factors influencing nurses' attitudes and behaviours towards privacy, security, and data-sharing practices. This multifaceted statistical approach, executed with the aid of SPSS 26, captured the distribution of key attributes and explored relationships and patterns across variables pertinent to the tools' implementation and impact.
Table 1 shows the demographic profile of study participants. Most participants were between 31 and 40 (45%), followed by those aged 20–30 (35%). Female participants comprised 75% of the sample, while males comprised 25%. Most participants were married (55%), with 40% being single and 5% divorced or in other categories. Regarding job titles, 60% were staff nurses, 20% were nurse managers, 10% were nurse educators, and 10% were nurse practitioners. Experience-wise, 30% had 0–5 years, 25% had 6–10 years, 20% had 11–15 years, and 25% had over 16 years of nursing experience. Regarding qualifications, 40% held a diploma, 35% a bachelor's degree, 20% a master's degree, and 5% a doctorate. A significant majority had received training on confidentiality (70%), while half had training on digital health technologies. The primary language of communication was Arabic (80%), with English used by 20% of the participants.
Table 2 presents the mean scores and standard deviations for the components of the HIPAA Compliance Checklist. The results indicate that the highest compliance was observed in Administrative Safeguards, with a mean score of 3.8 ± 0.5. Technical Safeguards follow this with a mean score of 3.7 ± 0.6. Physical Safeguards had a mean score of 3.5 ± 0.7. In contrast, Organisational Requirements had a mean score of 3.6 ± 0.8. The overall total score was 85 with a standard deviation of 10, suggesting generally high compliance with some variability among the components.
Table 3 displays the mean scores and standard deviations for each Privacy Impact Assessment (PIA) Tool section. Across all sections, high scores were observed, indicating robust compliance with privacy standards. Project Descriptions received the highest mean score of 4.5 ± 0.3, reflecting clear and comprehensive project documentation. Data Storage and Security Strategies also scored a mean of 4.4 ± 0.4, highlighting strong measures for protecting data integrity and security. The total score of 30 ± 3 underscores overall high adherence to privacy protocols, albeit with some variability across specific assessment criteria.
Table 4 presents the mean scores and standard deviations (mean ± SD) for each Data Sharing Agreement (DSA) Framework component. The assessment reveals solid compliance across all components, with Data Protection Measures achieving the highest mean score of 4.0 and a standard deviation of 0.4, indicating robust safeguards for data security. Purpose of Data Sharing and Roles and Responsibilities both received a mean score of 3.8, demonstrating clarity in defining the objectives and delineating roles in data-sharing activities. Consent Management and Data Use and Retention Terms also scored well, reflecting comprehensive practices in managing consent and outlining data use and retention terms. The total score of 20 with a standard deviation of 2 indicates strong adherence to data-sharing protocols, with minor variability in assessment outcomes.
Table 5 presents the mean scores and standard deviations for each Electronic Health Record (EHR) Privacy and Security Assessment Tool component. Access Controls received the highest mean score of 4.4, indicating strong implementation of measures to control access to patient information. Encryption Methods and Data Integrity Measures scored 4.3, highlighting robust practices in securing and maintaining the integrity of EHR data. Audit Trail Functionalities and Incident Response Protocols scored 4.2, indicating effective mechanisms for tracking access to records and responding to security incidents. The total score of 22 ± 1.5 suggests high overall compliance with EHR privacy and security requirements, with minimal variability in assessment outcomes.
Table 6 displays the mean scores and standard deviations for each function of the National Institute of Standards and Technology (NIST) Cybersecurity Framework. The framework is designed to enhance cybersecurity practices across healthcare settings, focusing on five core functions: Identify, Protect, Detect, Respond, and Recover. Protect achieved the highest mean score of 3.8, indicating strong implementation of measures to protect against cybersecurity threats. Identify, Respond, and Recover scored similarly at 3.7, highlighting robust capabilities in identifying assets, responding to incidents, and recovering from cybersecurity events. Detect scored slightly lower at 3.6, suggesting areas for potential improvement in detecting and mitigating threats. The total score of 18 ± 2 reflects generally effective cybersecurity practices with moderate variability in implementation across functions.
The correlation matrix (Table 7 ) reveals significant relationships among key frameworks for assessing healthcare data security and privacy measures. These tools include the Health Insurance Portability and Accountability Act (HIPAA) Compliance Checklist, Privacy Impact Assessment (PIA) Tool, Data Sharing Agreement (DSA) Framework, Electronic Health Record (EHR) Privacy and Security Assessment Tool, and the National Institute of Standards and Technology (NIST) Cybersecurity Framework. Strong positive correlations were found between HIPAA Compliance and both EHR Privacy and Security ( r = 0.70, p < 0.05) and NIST Cybersecurity Framework ( r = 0.55, p < 0.05), indicating that adherence to HIPAA regulations often coincides with robust electronic health record protections and cybersecurity practices. The PIA Tool demonstrated moderate positive correlations with the DSA Framework ( r = 0.55, p < 0.05) and EHR Privacy and Security ( r = 0.60, p < 0.05), underscoring the alignment between thorough privacy impact assessments and effective data sharing agreements and EHR security measures. These findings highlight the interconnectedness of regulatory compliance and proactive privacy measures in ensuring comprehensive healthcare data protection across organisational settings.
Nurses are pivotal in the healthcare system, and their expertise spans various domains, from clinical practice to administrative roles, influencing the quality and delivery of healthcare services. In recent years, the evolving healthcare landscape has underscored the need for nurses to navigate complex challenges such as patient privacy, data security, and regulatory compliance, are crucial for safeguarding patient information and maintaining trust and integrity within healthcare settings. This study explored the efficacy of several frameworks and tools designed to enhance data privacy and security measures, aiming to empower nurses with comprehensive strategies that align with regulatory standards and promote optimal patient care outcomes [ 46 , 47 ].
The high mean scores in administrative safeguards (mean = 3.8, SD = 0.5) and technical safeguards (mean = 3.7, SD = 0.6) reflected a strong commitment to data privacy and security within the healthcare sector. These findings indicated that some healthcare organisations are implementing measures to secure electronic protected health information (ePHI) and manage access controls effectively. However, there remains variability that needs addressing. The lower scores in physical safeguards (mean = 3.5, SD = 0.7) and organisational requirements (mean = 3.6, SD = 0.8) highlight areas where further attention is needed. The variability in these scores suggests potential challenges in implementing physical security measures and ensuring consistent policy documentation and workforce training. Previous studies highlighted the importance of comprehensive physical security measures and consistent organisational policies in maintaining overall compliance [ 48 , 49 , 50 , 51 , 52 , 53 , 54 , 55 , 56 ].
Regarding the Privacy impact assessment, high scores in project descriptions (mean = 4.5, SD = 0.3) and data storage and security strategies (mean = 4.4, SD = 0.4) suggested thorough documentation and robust security measures are in place, effectively identifying and mitigating privacy risks associated with new projects and data handling practices. However, the variability in scores across different sections of the PIA Tool indicated a need for continuous improvement in data usage, sharing practices, and risk mitigation methods, where consistent implementation may vary. These findings are consistent with previous studies that emphasised the need for comprehensive project documentation and secure data handling practices [ 57 , 58 , 59 , 60 , 61 , 62 , 63 , 64 , 65 ].
Concerning the data sharing agreement, the high scores in Data Protection Measures (mean = 4.0, SD = 0.4) indicated robust safeguards for data security. The purpose of data sharing and roles and responsibilities also performed well, reflecting clear definitions of data sharing objectives and roles. However, the moderate score variability indicated challenges in uniformly implementing consent management practices and data use terms. Prior studies also support the critical role of well-defined data-sharing agreements in balancing data utility and privacy protection [ 66 , 67 , 68 , 69 ].
In terms of electronic health record privacy and security assessment, high scores in access controls (mean = 4.4, SD = 0.3), encryption methods, and data integrity measures (mean = 4.3) reflected advancements in technology and policies aimed at enhancing data protection in healthcare settings, highlighting effective implementation of access management protocols. However, the minor variability in scores suggested room for improvement in incident response protocols. These findings were consistent with literature advocating for robust access controls and encryption methods to mitigate risks associated with EHR breaches [ 70 , 71 , 72 , 73 , 74 , 75 ].
With respect to the NIST Cybersecurity Framework , the high scores in the Protect function (mean = 3.8) indicated strong measures to protect healthcare information systems from cybersecurity threats. The identify, respond, and recover functions also scored well (mean = 3.7), highlighting robust capabilities in identifying assets, responding to incidents, and recovering from cyber-attacks. However, the slightly lower score in the detect function (mean = 3.6) suggested areas for improvement in detecting and mitigating cybersecurity threats. These results were supported by research emphasising the effectiveness of the NIST framework in enhancing cybersecurity resilience across various sectors, including healthcare [ 76 , 77 , 78 , 79 , 80 , 81 , 82 ].
Moreover, the current study revealed significant relationships among key frameworks used to assess healthcare data security and privacy measures, underscoring the interconnectedness of regulatory compliance efforts and proactive privacy measures. For instance, strong positive correlations were found between HIPAA Compliance and both EHR Privacy and Security ( r = 0.70, p < 0.05) and the NIST Cybersecurity Framework ( r = 0.55, p < 0.05), indicating that adherence to HIPAA regulations often coincides with robust electronic health record protections and cybersecurity practices. The PIA Tool demonstrated moderate positive correlations with the DSA Framework ( r = 0.55, p < 0.05) and EHR Privacy and Security ( r = 0.60, p < 0.05), highlighting the alignment between thorough privacy impact assessments and effective data sharing agreements and EHR security measures. These findings suggested that while certain frameworks complement each other well, there may be specific areas where improvements could enhance overall data security posture [ 83 , 84 , 85 ].
Study Limitations
This study has several notable limitations. Firstly, the cross-sectional design captures data at a single point in time, which may not fully reflect the dynamic nature of digital healthcare environments and evolving privacy challenges. Future research could address this by employing a longitudinal design to track how privacy and care coordination evolve with changes in technology and regulations. Secondly, the study was conducted at a single hospital, which may limit the generalizability of the findings to other healthcare settings with different digital infrastructures and privacy practices. Including multiple healthcare settings with diverse digital systems and privacy practices in future studies could enhance the applicability of the findings.
Additionally, the reliance on self-reported data from nurses introduces potential response bias, as participants may overstate their adherence to privacy and security protocols, resulting in inflated compliance rates. The exclusion of nurses on extended leave or those in administrative roles also limits the study's comprehensiveness. These groups might have unique insights or experiences related to confidentiality and care coordination that are not captured in the current study. Finally, while the study used validated tools, the rapid evolution of digital health technologies means that these tools may quickly become outdated. The changing landscape of technology and privacy standards can affect the relevance and accuracy of the assessment instruments. Addressing these limitations in future studies will provide more comprehensive understanding of privacy and care coordination in digital healthcare environments and improve the relevance and applicability of the findings across different contexts and periods.
Conclusion and recommendations
In conclusion, this study underscores the crucial role of nurses in ensuring robust data privacy and security within healthcare settings. The findings reveal high compliance with HIPAA regulations, particularly in administrative and technical safeguards, and strong performance in project descriptions and data storage strategies. The adherence to data privacy and sharing protocols, effective EHR security measures, and alignment with the NIST Cybersecurity Framework reflect a comprehensive approach to data protection. However, the variability in certain areas, such as physical safeguards, organisational requirements, and detection measures, highlights the need to continuously enhance data security practices to maintain the integrity and trust essential in healthcare. Investing in continuous training programs for nurses is crucial. Healthcare organisations should provide regular, specialised training addressing emerging privacy regulations, cybersecurity threats, and best practices. Upgrading physical security measures, such as access controls and surveillance, and ensuring that all organisational policies and procedures are up-to-date with current regulations will help achieve comprehensive HIPAA compliance.
Another key recommendation is to standardise and enhance consent management practices and data use terms. Organisations should develop clear, standardised consent forms and data use agreements, implement automated systems for tracking and managing consent, and regularly review and update these policies to reflect regulation changes. Additionally, conducting regular audits and updating detection measures is vital for improving overall cybersecurity posture. Lastly, fostering a culture of continuous improvement and proactive privacy management within healthcare organisations is essential. Encouraging open communication about privacy and security concerns, rewarding compliance and proactive measures, and engaging staff in regular discussions about privacy and security initiatives will contribute to a robust privacy management culture.
Study Implications
The findings of this study offer several actionable insights for healthcare practice, policy, and future research.
Healthcare Practice: The study highlights the critical need for continuous and comprehensive training for nurses on digital health privacy and security protocols. Specific recommendations include developing targeted training programs that address emerging privacy threats and technologies. Additionally, integrating privacy and security training into onboarding processes for new staff can ensure that all personnel are up-to-date with best practices from the start.
Policy: Policymakers should prioritise the development of detailed guidelines that address the specific challenges posed by these technologies, such as data sharing and electronic health records. Recommendations include establishing clear standards for data encryption, access controls, and consent management. Regular policy reviews and updates are necessary to keep pace with technological advancements and ensure ongoing protection of patient confidentiality.
Future Research: Longitudinal studies are needed to assess how implementing digital health technologies impacts patient privacy and care coordination over time. Future studies could also focus on developing and validating new assessment tools that reflect the latest technological advancements and privacy challenges. Investigating the role of interdisciplinary approaches, combining insights from cybersecurity experts and healthcare practitioners, could further enhance privacy and security measures in digital health environments.
Availability of data and materials
Data sharing is not applicable to this article as no datasets were generated or analysed during the current study.
Data availability
No datasets were generated or analysed during the current study.
Stoumpos AI, Kitsios F, Talias MA. Digital Transformation in Healthcare: Technology Acceptance and Its Applications. Int J Environ Res Public Health. 2023;20(4):1–44. https://doi.org/10.3390/ijerph20043407 .
Article PubMed PubMed Central Google Scholar
Yigzaw, K. Y., Olabarriaga, S. D., Michalas, A., Marco-Ruiz, L., Hillen, C., Verginadis, Y., ... & Chomutare, T. (2022). Health data security and privacy: Challenges and solutions for the future. Roadmap to Successful Digital Health Ecosystems, 335–362.
Varkey B. Principles of Clinical Ethics and Their Application to Practice. Medical principles and practice : international journal of the Kuwait University, Health Science Centre. 2021;30(1):17–28. https://doi.org/10.1159/000509119 .
Article PubMed Google Scholar
McGraw D, Mandl KD. Privacy protections to encourage use of health-relevant digital data in a learning health system. NPJ digital medicine. 2021;4(1):2.
Mumtaz H, Riaz MH, Wajid H, Saqib M, Zeeshan MH, Khan SE, Chauhan YR, Sohail H, Vohra LI. Current challenges and potential solutions to the use of digital health technologies in evidence generation: a narrative review. Frontiers in digital health. 2023;5:1203945. https://doi.org/10.3389/fdgth.2023.1203945 .
Karam M, Chouinard MC, Poitras ME, Couturier Y, Vedel I, Grgurevic N, Hudon C. Nursing Care Coordination for Patients with Complex Needs in Primary Healthcare: A Scoping Review. Int J Integr Care. 2021;21(1):16. https://doi.org/10.5334/ijic.5518 .
Albertson EM, Chuang E, O’Masta B, Miake-Lye I, Haley LA, Pourat N. Systematic Review of Care Coordination Interventions Linking Health and Social Services for High-Utilizing Patient Populations. Popul Health Manag. 2022;25(1):73–85. https://doi.org/10.1089/pop.2021.0057 .
Househ M, Grainger R, Petersen C, Bamidis P, Merolli M. Balancing Between Privacy and Patient Needs for Health Information in the Age of Participatory Health and Social Media: A Scoping Review. Yearb Med Inform. 2018;27(1):29–36. https://doi.org/10.1055/s-0038-1641197 .
Abuhammad S, Alzoubi KH, Al-Azzam SI, Karasneh RA. Knowledge and Practice of Patients’ Data Sharing and Confidentiality Among Nurses in Jordan. J Multidiscip Healthc. 2020;13:935–42. https://doi.org/10.2147/JMDH.S269511 .
Shah SM, Khan RA. Secondary use of electronic health record: Opportunities and challenges. IEEE access. 2020;8:136947–65.
Article Google Scholar
Butler JM, Gibson B, Lewis L, Reiber G, Kramer H, Rupper R, Herout J, Long B, Massaro D, Nebeker J. Patient-centered care and the electronic health record: exploring functionality and gaps. JAMIA open. 2020;3(3):360–8. https://doi.org/10.1093/jamiaopen/ooaa044 .
Paul M, Maglaras L, Ferrag MA, Almomani I. Digitisation of healthcare sector: A study on privacy and security concerns. ICT Express. 2023;9(4):571–88.
Jawad LA. Security and Privacy in Digital Healthcare Systems: Challenges and Mitigation Strategies. Abhigyan. 2024;42(1):23–31.
Google Scholar
Haleem A, Javaid M, Singh RP, Suman R. Telemedicine for healthcare: Capabilities, features, barriers, and applications. Sensors international. 2021;2: 100117. https://doi.org/10.1016/j.sintl.2021.100117 .
Anawade PA, Sharma D, Gahane S. A Comprehensive Review on Exploring the Impact of Telemedicine on Healthcare Accessibility. Cureus. 2024;16(3): e55996. https://doi.org/10.7759/cureus.55996 .
Houser SH, Flite CA, Foster SL. Privacy and Security Risk Factors Related to Telehealth Services - A Systematic Review. Perspect Health Inf Manag. 2023;20(1):1f.
PubMed PubMed Central Google Scholar
Sherman KA, Kilby CJ, Pehlivan M, Smith B. Adequacy of measures of informed consent in medical practice: A systematic review. PLoS ONE. 2021;16(5): e0251485.
Article CAS PubMed PubMed Central Google Scholar
Madanian S, Nakarada-Kordic I, Reay S. Patients’ perspectives on digital health tools. PEC innovation. 2023;2: 100171.
Ewuoso, C., Hall, S., & Dierickx, K. (2021). How do healthcare professionals respond to ethical challenges regarding information management? A review of empirical studies. Global bioethics = Problemi di bioetica , 32 (1), 67–84. https://doi.org/10.1080/11287462.2021.1909820
Bhati D, Deogade MS, Kanyal D. Improving Patient Outcomes Through Effective Hospital Administration: A Comprehensive Review. Cureus. 2023;15(10): e47731. https://doi.org/10.7759/cureus.47731 .
Wang C, Chen X, Yu T, Liu Y, Jing Y. Education reform and change driven by digital technology: a bibliometric study from a global perspective. Humanities and Social Sciences Communications. 2024;11(1):1–17.
Ryan T. Facilitators of person and relationship-centred care in nursing. Nurs Open. 2022;9(2):892–9. https://doi.org/10.1002/nop2.1083 .
Habibi-Koolaee M, Safdari R, Bouraghi H. Nurses readiness and electronic health records. Acta informatica medica : AIM : journal of the Society for Medical Informatics of Bosnia & Herzegovina : casopis Drustva za medicinsku informatiku BiH. 2015;23(2):105–7. https://doi.org/10.5455/aim.2015.23.105-107 .
Khatri R, Endalamaw A, Erku D, Wolka E, Nigatu F, Zewdie A, Assefa Y. Continuity and care coordination of primary health care: a scoping review. BMC Health Serv Res. 2023;23(1):750.
Alderwick H, Hutchings A, Briggs A, Mays N. The impacts of collaboration between local health care and non-health care organisations and factors shaping how they work: a systematic review of reviews. BMC Public Health. 2021;21:1–16.
Awais M, Ali A, Khattak MS, Arfeen MI, Chaudhary MAI, Syed A. Strategic Flexibility and Organisational Performance: Mediating Role of Innovation. SAGE Open. 2023;13(2):21582440231181430.
Oh SR, Seo YD, Lee E, Kim YG. A Comprehensive Survey on Security and Privacy for Electronic Health Data. Int J Environ Res Public Health. 2021;18(18):9668. https://doi.org/10.3390/ijerph18189668 .
Martin LT, Nelson C, Yeung D, Acosta JD, Qureshi N, Blagg T, Chandra A. The Issues of Interoperability and Data Connectedness for Public Health. Big data. 2022;10(S1):S19–24. https://doi.org/10.1089/big.2022.0207 .
Torab-Miandoab A, Samad-Soltani T, Jodati A, Rezaei-Hachesu P. Interoperability of heterogeneous health information systems: a systematic literature review. BMC Med Inform Decis Mak. 2023;23(1):18. https://doi.org/10.1186/s12911-023-02115-5 .
Raab CD. Information privacy, impact assessment, and the place of ethics. Comput Law Secur Rev. 2020;37: 105404.
Westin AF. Privacy and Freedom. Atheneum; 1967.
Venkatesh V, Morris MG, Davis GB, Davis FD. User acceptance of information technology: Toward a unified view. MIS Q. 2010;27(3):425–78.
Davis FD. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q. 1989;13(3):319–40.
Beauchamp, T. L., & Childress, J. F. (2013). Principles of biomedical ethics (7th ed.). Oxford University Press.
Grady C. Ethical issues in health informatics. Health Information Science and Systems. 2015;3(1):1–7.
Rogers, E. M. (2003). Diffusion of innovations (5th ed.). Free Press.
Conlon D, Raeburn T, Wand T. Nurses’ understanding of their duty of confidentiality to patients in mental health care: A qualitative exploratory study. Collegian. 2024;31(3):144–53.
Karam, M., Chouinard, M. C., Poitras, M. E., Couturier, Y., Vedel, I., Grgurevic, N., & Hudon, C. (2021). Nursing care coordination for patients with complex needs in primary healthcare: a scoping review. International Journal of Integrated Care, 21(1):16. https://ijic.org/articles/10.5334/ijic.5518 .
Daniel WW. Biostatistics: a foundation for analysis in the health sciences. þWiley, 1978.
U.S. Department of Health and Human Services. (2022). Health Insurance Portability and Accountability Act (HIPAA). Retrieved from https://www.hhs.gov/hipaa/index.html
Wright D, De Hert P. Privacy Impact Assessment. Springer. 2012. https://doi.org/10.1007/978-94-007-2543-0 .
Article PubMed Central Google Scholar
European Union Agency for Cybersecurity. (2018). Data Sharing Agreements: A Practical Guide. Retrieved from https://www.enisa.europa.eu/publications/data-sharing-agreements
Centers for Medicare & Medicaid Services. (2023). EHR Privacy and Security Requirements. Retrieved from https://www.cms.gov/Regulations-and-Guidance/Legislation/EHRIncentivePrograms/PrivacyandSecurity
National Institute of Standards and Technology. (2018). Framework for Improving Critical Infrastructure Cybersecurity. Retrieved from https://www.nist.gov/cyberframework
Swanson M, Wong ST, Martin-Misener R, Browne AJ. The role of registered nurses in primary care and public health collaboration: A scoping review. Nurs Open. 2020;7(4):1197–207. https://doi.org/10.1002/nop2.496 .
Ten Ham-Baloyi W. (2022). Nurses’ roles in changing practice through implementing best practices: A systematic review. Health SA = SA Gesondheid, 27, 1776. https://doi.org/10.4102/hsag.v27i0.1776
Parks R, Xu H, Chu CH, Lowry PB. Examining the intended and unintended consequences of organisational privacy safeguards. Eur J Inf Syst. 2017;26(1):37–65.
Mehraeen E, Ayatollahi H, Ahmadi M. Health Information Security in Hospitals: the Application of Security Safeguards. Acta informatica medica : AIM : journal of the Society for Medical Informatics of Bosnia & Herzegovina : casopis Drustva za medicinsku informatiku BiH. 2016;24(1):47–50. https://doi.org/10.5455/aim.2016.24.47-50 .
Sharma, P., Bir, J., & Prakash, S. (2023, December). Navigating Privacy and Security Challenges in Electronic Medical Record (EMR) Systems: Strategies for Safeguarding Patient Data in Developing Countries–A Case Study of the Pacific. In International Conference on Medical Imaging and Computer-Aided Diagnosis (pp. 375–386). Singapore: Springer Nature Singapore. Peikari, H. R., Shah, M. H., & Lo, M. C. (2018). Patients' perception of the information security management in health centers: The role of organisational and human factors. BMC medical informatics and decision making, 18, 1–13.
Choudhury A. Toward an ecologically valid conceptual framework for the use of artificial intelligence in clinical settings: need for systems thinking, accountability, decision-making, trust, and patient safety considerations in safeguarding the technology and clinicians. JMIR Hum Factors. 2022;9(2): e35421.
Okolo CA, Ijeh S, Arowoogun JO, Adeniyi AO, Omotayo O. Reviewing the impact of health information technology on healthcare management efficiency. International Medical Science Research Journal. 2024;4(4):420–40.
Solbakken R, Bondas T, Kasén A. Safeguarding the patient in municipal healthcare—A hermeneutic focus group study of Nordic nursing leadership. J Nurs Manag. 2019;27(6):1242–50.
Hoffman S, Podgurski A. Balancing Privacy, Autonomy, and Scientific Needs In Electronic Health Records Research. SMU law review : a publication of Southern Methodist University School of Law. 2012;65(1):85–144.
PubMed Google Scholar
Landoll, D. (2021). The security risk assessment handbook: A complete guide for performing security risk assessments . CRC press.
Kessler SR, Pindek S, Kleinman G, Andel SA, Spector PE. Information security climate and the assessment of information security risk among healthcare employees. Health Informatics J. 2020;26(1):461–73.
Brotherston, L., Berlin, A., & Reyor III, W. F. (2024). Defensive security handbook . "O'Reilly Media, Inc.".
Bennett, C. J., & Raab, C. D. (2017). The governance of privacy: Policy instruments in global perspective . Routledge.
Fawzy, A., Tahir, A., Galster, M., & Liang, P. (2024). Data Management Challenges in Agile Software Projects: A Systematic Literature Review. arXiv preprint arXiv:2402.00462 .
Humayun M, Niazi M, Almufareh MF, Jhanjhi NZ, Mahmood S, Alshayeb M. Software-as-a-service security challenges and best practices: A multivocal literature review. Appl Sci. 2022;12(8):3953.
Article CAS Google Scholar
Li ZS, Werner C, Ernst N, Damian D. Towards privacy compliance: A design science study in a small organisation. Inf Softw Technol. 2022;146: 106868.
Stanciu, A. (2023). Data Management Plan for Healthcare: Following FAIR Principles and Addressing Cybersecurity Aspects. A Systematic Review using InstructGPT. medRxiv, 2023–04.
European Commission. (2018). General Data Protection Regulation (GDPR). https://ec.europa.eu/info/law/law-topic/data-protection_en
Duckert, M., & Barkhuus, L. (2022). Protecting Personal Health Data through Privacy Awareness: A study of perceived data privacy among people with chronic or long-term illness. Proceedings of the ACM on Human-Computer Interaction, 6(GROUP), 1–22.
Khalid N, Qayyum A, Bilal M, Al-Fuqaha A, Qadir J. Privacy-preserving artificial intelligence in healthcare: Techniques and applications. Comput Biol Med. 2023;158: 106848.
Ducato R. Data protection, scientific research, and the role of information. Comput Law Secur Rev. 2020;37: 105412.
Xiang D, Cai W. Privacy Protection and Secondary Use of Health Data: Strategies and Methods. Biomed Res Int. 2021;2021:6967166. https://doi.org/10.1155/2021/6967166 .
Keshta I, Odeh A. Security and privacy of electronic health records: Concerns and challenges. Egyptian Informatics Journal. 2021;22(2):177–83.
Fernández-Alemán JL, Señor IC, Lozoya PÁO, Toval A. Security and privacy in electronic health records: A systematic literature review. J Biomed Inform. 2013;46(3):541–62.
Banerjee, S., Barik, S., Das, D., & Ghosh, U. (2023, October). EHR Security and Privacy Aspects: A Systematic Review. In IFIP International Internet of Things Conference (pp. 243–260). Cham: Springer Nature Switzerland.
Negro-Calduch E, Azzopardi-Muscat N, Krishnamurthy RS, Novillo-Ortiz D. Technological progress in electronic health record system optimisation: Systematic review of systematic literature reviews. Int J Med Informatics. 2021;152: 104507. https://doi.org/10.1016/j.ijmedinf.2021.104507 .
Negro-Calduch E, Azzopardi-Muscat N, Krishnamurthy RS, Novillo-Ortiz D. Technological progress in electronic health record system optimisation: Systematic review of systematic literature reviews. Int J Med Informatics. 2021;152: 104507.
He Y, Aliyu A, Evans M, Luo C. Health Care Cybersecurity Challenges and Solutions Under the Climate of COVID-19: Scoping Review. J Med Internet Res. 2021;23(4): e21747. https://doi.org/10.2196/21747 .
Coventry L, Branley D. Cybersecurity in healthcare: A narrative review of trends, threats and ways forward. Maturitas. 2018;113:48–52.
Javaid M, Haleem A, Singh RP, Suman R. Towards insighting cybersecurity for healthcare domains: A comprehensive review of recent practices and trends. Cyber Security and Applications. 2023;1: 100016.
Argaw, S. T., Troncoso-Pastoriza, J. R., Lacey, D., Florin, M. V., Calcavecchia, F., Anderson, D., ... & Flahault, A. (2020). Cybersecurity of Hospitals: discussing the challenges and working towards mitigating the risks. BMC medical informatics and decision making , 20 , 1–10.
Alanazi AT. Clinicians’ Perspectives on Healthcare Cybersecurity and Cyber Threats. Cureus. 2023;15(10): e47026. https://doi.org/10.7759/cureus.47026 .
Kruse CS, Frederick B, Jacobson T, Monticone DK. Cybersecurity in healthcare: A systematic review of modern threats and trends. Technology and health care : official journal of the European Society for Engineering and Medicine. 2017;25(1):1–10. https://doi.org/10.3233/THC-161263 .
Roland D, Spurr J, Cabrera D. Preliminary evidence for the emergence of a health care online community of practice: using a netnographic framework for Twitter hashtag analytics. J Med Internet Res. 2017;19(7): e252.
Tse J, Schrader DE, Ghosh D, Liao T, Lundie D. A bibliometric analysis of privacy and ethics in IEEE Security and Privacy. Ethics Inf Technol. 2015;17:153–63.
Tawalbeh LA, Muheidat F, Tawalbeh M, Quwaider M. IoT Privacy and security: Challenges and solutions. Appl Sci. 2020;10(12):4102.
Download references
Acknowledgements
The authors thank all the nurses who participated in our study. This study is supported via funding from Prince Sattam bin Abdulaziz University project number (PSAU/2024/R/1445). Also; The authors would like to thank Al-Maarefa University, Riydah, Saudi Arabia for supporting this research.
This study is supported via funding from Prince Sattam bin Abdulaziz University project number (PSAU/2024/R/1445).
Author information
Authors and affiliations.
College of Nursing, Prince Sattam Bin Abdulaziz University, Alkarj, Saudi Arabia
Ateya Megahed Ibrahim, Hassanat Ramadan Abdel-Aziz, Donia Elsaid Fathi Zaghamir & Nadia Mohamed Ibrahim Wahba
Family and Community Health Nursing Department, Faculty of Nursing, Port Said University, Port Said City, Port Said, 42526, Egypt
Ateya Megahed Ibrahim
Gerontological Nursing Department, Faculty of Nursing, Zagazig University, Zagazig, Egypt
Hassanat Ramadan Abdel-Aziz
Community Health Nursing Department, Faculty of Nursing, Mansoura University, Mansoura City, Dakahlia, Egypt
Heba Ali Hamed Mohamed
Pediatric Nursing Department, Faculty of Nursing, Port Said University, Port Said City, 42526, Egypt
Donia Elsaid Fathi Zaghamir
Psychiatric Nursing and Mental Health Department, Faculty of Nursing, Port Said University, Port Said, 42526, Egypt
Nadia Mohamed Ibrahim Wahba
Pediatric Nursing Department, Faculty of Nursing, Menoufia University, Shibin el Kom, Egypt
Ghada. A. Hassan
Community Health Nursing Department, College of Nursing, Jouf University, Sakaka, Al Jouf, 72388, Saudi Arabia
Mostafa Shaban
Department of Basic Medical Sciences, College of Medicine, AlMaarefa University, P.O.Box 71666, 11597, Riyadh, Saudi Arabia
Mohammad EL-Nablaway
Department of Medical and Surgical Nursing, Northern Border University, Arar, Saudi Arabia
Ohoud Naif Aldughmi
Nursing Leadership Department, Nursing College, Northern Border University, Arar, Saudi Arabia
Taghreed Hussien Aboelola
You can also search for this author in PubMed Google Scholar
Contributions
A.I. made the conception and design of the study; acquisition of data; or analysis and interpretation of data. H.A. made the conception and design of the study; acquisition of data; or analysis and interpretation of data. H.M.D.Z. and N.W. G.H. M.S. M.E. drafted the article, revising it critically for important intellectual content. A.I. O.A. and T.A. Wrote the paper and edition. All the authors revised and agreed on publication.
Corresponding author
Correspondence to Ateya Megahed Ibrahim .
Ethics declarations
Ethics approval and consent to participate.
Ethical approval was obtained from the Research Ethics Committee (REC) at the Faculty of Nursing, Zagazig University, Egypt. The study protocol was reviewed and granted ethical clearance under code ID/Zu.Nur.REC#:0067.
Consent for publication
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Ibrahim, A.M., Abdel-Aziz, H.R., Mohamed, H.A.H. et al. Balancing confidentiality and care coordination: challenges in patient privacy. BMC Nurs 23 , 564 (2024). https://doi.org/10.1186/s12912-024-02231-1
Download citation
Received : 17 July 2024
Accepted : 06 August 2024
Published : 15 August 2024
DOI : https://doi.org/10.1186/s12912-024-02231-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Care coordination
- Digital health
- HIPAA compliance
- Patient confidentiality
- Privacy frameworks
BMC Nursing
ISSN: 1472-6955
- General enquiries: [email protected]

IMAGES
VIDEO
COMMENTS
1.1 You must treat service users and carers as individuals, respecting their privacy and dignity. 5.1 You must treat information about service users as confidential. 5.2 You must only disclose confidential information if: - you have permission; - the law allows this; - it is in the service user's best interests; or.
The first chapter was an overview of your obliga7ons and accountabili7es related to maintaining the privacy and confiden7ality of clients' personal health informa7on. In this chapter, we will review some case studies and reflect on how to apply the concepts we learned in the first chapter to situa7ons that could result in privacy breaches.
This article presents the case of an HIV-positive patient who presented the treating physician, a psychiatrist, with an ethical dilemma. We provide the details of the case, identify the ethical issues it raises, and examine the ethical principles involved. In their article, "Confidentiality in the Age of AIDS," Martin L. Smith and Kevin P. Martin present a complex case in clinical ethics ...
Health and Social Care Act 2008. Death of a person who has been receiving a health or social care service. Death or unauthorised absence of someone detained (or liable to be detained) under the Mental Health Act 1983. Application to deprive a person of their liberty (under the Mental Capacity Act 2005) Placement of a child on an adult ...
Background Respecting patients' confidentiality is an ethical and legal responsibility for health professionals and the cornerstone of care excellence. This study aims to assess health professionals' knowledge, attitudes, and associated factors towards patients' confidentiality in a resource-limited setting. Methods Institutional based cross-sectional study was conducted among 423 health ...
of confidentiality in the use and disclosure of information. Principle 3. Preserve, protect, and secure personal health information in any form or medium and hold in the highest regard health information and other information of a confidential nature obtained in an official capacity, taking into account the applicable statutes and regulations.
In the interim, the Health and Social Care Act 2012 renamed the Council of Healthcare Regulatory Excellence 44 as the Professional Standards Authority for Health and Social Care ... by the Professional Standards Authority investigating perspectives on consistency in healthcare regulation used confidentiality as a case study to prompt discussion ...
Case Study. The use of digital communication such as EHR, email, social media, or the internet has become the norm in healthcare (Lo, 2013). However, the use of digital communication poses risks of breaching patient privacy and confidentiality. The following case study illustrates inappropriate use of digital communication: Trista was a new ...
Background In the digital age, maintaining patient confidentiality while ensuring effective care coordination poses significant challenges for healthcare providers, particularly nurses. Aim To investigate the challenges and strategies associated with balancing patient confidentiality and effective care coordination in the digital age. Methods A cross-sectional study was conducted in a general ...
The social worker claimed that he acted pursuant to the exception provided for in Section 8 (a) (3) of the SWA, which permits a breach of the duty of confidentiality when "the social worker is convinced that the information is required for the care of that person's minor children."According to the social worker, he violated the duty of ...
Confidentiality ultimately respects an individual's privacy and thus describes the disclosure or non-disclosure of private information. Relatedly, informed consent, in the context of privacy, describes an individual permitting information disclosure.With the development of so-called 'eHealth' and linked computer records, patients should consent to this, often automatic, sharing of information.
Here are some case studies additional to those in the code. Data sharing to improve outcomes for disadvantaged children and families. Sharing with partners in the voluntary or private sector. Landlord and tenant data sharing. Sharing medical records of care home residents. Ensuring children's welfare: data sharing by local authorities with ...
Confidentiality is important in health care because some personal information may be discomfiting or has negative repercussions for a patient or others (Barloon & Hilliard, 2016). Therefore, there is a public interest in ensuring the duty of confidentiality is maintained (Kämpf & McSherry, 2006). The term 'public interest' is not defined ...
The duty of confidentiality is based on four major arguments: The principle of respect for autonomy or respect for persons. Respect for autonomy, or respect for persons, calls for us to allow others to decide who they want to know certain details about themselves. Respecting others and caring for them should create in us a disposition to ...
Dalrymple J., Burke B. (2006) Anti-Oppressive Practice: Social Care and the Law. London: Open University Press. ... 'Issues of Power in Social Work Practice in Mental Health Services for People from Black and Minority ... A Case Study using Foucault's Disciplinary Power', Critical Social Work 15(1): 30-40. Google Scholar. Lipsky M ...
care in health and social services" (Cairns et al., 2018, p. 350; cf. Devlieghere et al., ... case recordings. Previous studies highlight the construction of a case during record-ing (Berg, 1996; Garfinkel, 1967; Taylor, 2008) and emphasize that this case con- ... Confidentiality in professional social work practice is one of the core values and
Confidentiality means protecting personal information. This information might include details of a service user's lifestyle, family, health or care needs which they want to be kept private. Service users expect the health and care professionals who are involved in their care or treatment, or have access to information about them, to protect ...
Benefits of Confidentiality in Health and Social Care. The main benefit to maintaining confidentiality in health and social care is to build trust and rapport amongst care staff and service users. Doing so leads to more open and honest communication, which can benefit the health and well-being of individuals. Respecting the dignity and personal ...
2. Doctors are under both ethical and legal duties to protect patients' personal information from improper disclosure. But appropriate information sharing is an essential part of the provision of safe and effective care. Patients may be put at risk if those who are providing their care do not have access to relevant, accurate and up-to-date ...
tell service users when you have disclosed their information (if this is practical and possible); keep appropriate records of disclosure; keep up to date with relevant law and good practice; if appropriate, ask for advice from colleagues, professional bodies, unions, legal professionals or us; and. make your own informed decisions about ...